#cyberlibel
Explore tagged Tumblr posts
Text

i will sue this FB identity theft and intellectual property rights and cyberlibel im a marcos supporter im the only one who has blue aereal robotics my twitter has been hacked my IG joy_santosbagus100781 password blueuscia100781 my social media my color is blue caloocan city my motorbike is honda wave 110 with blue black red flairings but my favorite color is blue reg. plate 1303-0752840 now its 826 NCL my FB Jovelyn Santos Bagus if you want to get in to my FB just type my globe prepaid 09950677083 password blueuscia100781
0 notes
Text
Rappler was barely four years old when President Duterte was elected. There were very few of us, but we did what we could to report on corruption and abuses of power, along with the war on drugs. President Duterte gave Rappler another name. He called us fake news. He said we were paid hacks. We were charged with tax evasion and cyberlibel and ownership violations. Rappler’s license to operate was revoked. It remains under appeal. Our reporters were banned from covering the president. We were threatened daily on social media. Because we were women, the threats included rape.
from Some People Need Killing: A Memoir of Murder in My Country, by Patricia Evangelista
#quotes#some people need killing#patricia evangelista#nonfiction#journalism#history#politics#crime#books#filipino history#filipino politics#filipino literature#filipino author
0 notes
Text
Rappler was barely four years old when President Duterte was elected. There were very few of us, but we did what we could to report on corruption and abuses of power, along with the war on drugs. President Duterte gave Rappler another name. He called us fake news. He said we were paid hacks. We were charged with tax evasion and cyberlibel and ownership violations. Rappler’s license to operate was revoked. It remains under appeal. Our reporters were banned from covering the president. We were threatened daily on social media. Because we were women, the threats included rape.
from Some People Need Killing: A Memoir of Murder in My Country, by Patricia Evangelista
#quotes#some people need killing#patricia evangelista#nonfiction#journalism#history#politics#crime#books#filipino history#filipino politics#filipino literature#filipino author
0 notes
Note
im genuinely curious if cyberlibel is a thing in the uk? im not in the legal profession so i wouldnt really know but it seems like a situation that calls for it imo, what they are doing to mason is too much (as well as other footballers). in my country, cyberliber is a thing and most peoples been free scoring on it because the law is kind of vague its practically like if anyone says the wrong word u get a case everyone gets a case scenario its almost hilarious 😭😭 look up maria ressa's case they got sued for fixing up a typo error some time later on an article that was published before the law was even in place like its a different scenario and this case is more of a state attack on journalism but like if i was a famous person id probably suing people who talk shit too much yk??
Ooo I’ve never heard of this I’ll have a look into it
I feel like I’m the uk thought they just say what they like
0 notes
Text
Blog about Ethical Principles of New Media
As a student of Writing for New Media, I learned a lot of things in terms of creating essays about the relevant issue nowadays. We created a podcast to train our skills for vocal voice and to tackle the topic we chose, but the topic I most interested is in Final Topic which is talks about the Ethical Principles of New Media Writing including the topics of Libel, Slander, Copyright, Plagiarism, Cybercrime Law and the Data Privacy Act of 2012. It gives me more ideas to have knowledge and to know the differences and what we should and shouldn’t do because for me this is one of taking advantage if we knew it, Why? Because nowadays many people and youth they’re active on social media, they post everything and it also causes war or fights between two people, besides there are a lot of students or individuals does copyright not only music or what so ever but also copy statements, content, and some logo’s without giving a credit to the owner. Libel or Cyberlibel is still happening now personally or even through social media, so we should be wise about what we say personally or what we posted online without proof of accusing someone or even spreading a piece of fake news that can cause their mental health or to put them into ashamed. We should be aware of what were doing. So, why did I choose a topic for my blog? Because I want to spread the thoughts of many people and for their awareness of what they should and shouldn’t do and for the sake of themselves. In my own perspective for this blog, I know the many readers relating to this topic because of the social media that we should be aware of in our every or daily post, and it can help the many readers and they will benefit because of this blog just to be wise that not at all times we will put our thoughts, were going to fight through social media without any consent of someone and I know if we read this blog their mind will open and they will be an incentive and conservative person to make them self better and to be a professional because you should think before you click.
0 notes
Photo







“A Thousand Cuts”, a documentary by Filipina-American director Ramona S. Diaz , begins with Rodrigo Duterte’s ascent to power in 2015 and concludes with a June 2020 coda. Under his policy of extra-judicial killing of addicts and low-level dealers, an estimated 20,000 Filipinos have been murdered, with an average of 8 new corpses turning up nightly on the streets of Manila alone. Maria Ressa states, and Diaz depicts, that this has panned out as a war on the poor, as drug lords skate through unpunished.
Most of “A Thousand Cuts” focuses on the erosion of the free press and the concurrent run-up to the 2019 elections.
The moves against Rappler have drawn international concern and made Ressa globally renowned as one of the people standing up against authoritarian governments. Time magazine named Ressa a Person of the Year in 2018, and she was named a laureate in the 2020 Four Freedoms Awards. (READ: Maria Ressa among TIME’s most influential women of the century)
Philippines: CFWIJ condemns Maria Ressa's cyber libel conviction June 15, 2020
2022 Philippine presidential election
#philippine#press#freedom#maria ressa#duterte#frontline#icfj#documentary#2020#ramona diaz#a thousand cuts#cyberlibel
3 notes
·
View notes
Text
Twitter Video, Live Interview: An hour before promulgation cyberlibel case against journalists: ABS-CBN Headstart anchor Karen Davila asks detailed questions on prescriptive period (time limit to prohibit prosecution) of libel and “republication” “theory” of prosecution to apply cyberlaw to article published before cyberlaw enacted
Twitter Video, Live Interview: An hour before promulgation cyberlibel case against journalists: ABS-CBN Headstart anchor Karen Davila asks detailed questions on prescriptive period (time limit to prohibit prosecution) of libel and “republication” “theory” of prosecution to apply cyberlaw to article published before cyberlaw enacted


Twitter Video, Live Interview: An hour before promulgation cyberlibel case against journalists: ABS-CBN Headstart anchor Karen Davila asks detailed questions on prescriptive period (time limit to prohibit prosecution) of libel and “republication” “theory” of prosecution to apply cyberlaw to article published before cyberlaw enacted
CODE
"It's a threat to all of us."
The cyber libel case against…
View On WordPress
0 notes
Text
PLEASE READ!!

link to original tweet
https://t.co/NeGFVeCQiK <- LINK TO THE DOCUMENT WITH THE SIM CARD REGISTRATION ACT
For using fictitious identities to register SIM cards or social media accounts. - The penalty of imprisonment of no less than six (6) years or a fine of up to Two hundred thousand pesos (P200,000.00) [note: this is about $3888.] or both, shall be imposed upon anyone who uses a fictitious identity to purchase and register a SIM cards or social media account.
saw this on twitter, not sure if anyone has here yet.
https://t.co/eVe3puxdHq <- LINK TO AN ARTICLE ABOUT THE "ANTITROLL" BILL
It is described as an “antitroll” bill as it will require all social media networks such as Facebook and Twitter to get the real name and phone number of users during the creation of an account.
According to Drilon, the requirement to use real names was aimed at “fight(ing) the anonymity that provides the environment for trolls and other malicious attacks to thrive in the age of social media."
The Philippine government, specifically Senate Minority Franklin Drilon specifically sought the insertion of the part that REQUIRES USERS TO USE THEIR REAL NAMES online to "fight against online trolls and cyberlibel."
The Philippine government also has a history of red-tagging anybody who says anything in opposition to them.
If you don't know what red-tagging is, it's basically "labeling people as terrorists, communists, etc." by the government, should you be percieved as a threat.
Victims of red-tagging may be subject to
having their communication, spoken, written, online, whatever, being monitored
arrested for simply being suspected of terrorism (which in the documents, the description of what a terrorist is is written very vaguely)
restricted travel, house arrest, prohibited from using any means of communication with those outside the victim's home, such as cell phones, computers, etc.
With this information, this law puts the Philippine citizens with barely any defense against red-tagging, much less doxxing from other users.
If the president decides to sign this, all Filipino citizens will be forced to use our real identities online.
As of now, I do not know any way to stop this, but it would help greatly if you shared this to spread the information.
If you find any way to oppose it, please share it to the best of your ability. Thank you.
Edit: this post has a pretty good explanation! there are links to petitions on there too
#philippines#sim card registration#i don't know how to tag this...#boost this#signal boost#philippine government#god. i'm so angry...
333 notes
·
View notes
Text
Our President And The Issue Of EJKs In The Philippines by Santino Fernandez
"Power tends to corrupt, and absolute power corrupts absolutely-Lord Acton”
These words to me are important as they reflect a huge societal issue happening right now in The Philippines. This issue has to deal with the police and how they abuse their power towards the people of my country. It is no secret that Police Brutality is running rampant in some countries right now. Just last May, America experienced a great tragedy with the murder of George Floyd. The cop killings in the US are rampant but in the Philippines they are as bad if not worse.
Ever since 2016 our president Rodrigo Duterte has been on the so called “War on Drugs.” In this campaign he promised to rid the country of dangerous substances by the end of his six year term. However all it has done is create more damage as this so called “Drug War” targets the poor and less fortunate. In the years since Duterte has taken office he has implemented Extra Judicial Killings also known as EJKs in the country. An EJK is when the government sanctions the killing of people or drug addicts in the country as long as there is evidence. There is no due process any more and these addicts are not taken to a court of law. These addicts are shot in the streets in cold blood without any hesitation or remorse.
Since the implementation of EJK in our country there have been up to 5000 deaths caused by the EJKs. However human rights groups say it is way beyond 12,000 already. Human rights groups have been siding with the people because it is a violation of democracy. According to our democratic law everyone deserves their day in court but Duterte prefers to not do that and instead kill the offenders. In a direct quote from the man himself he says that he will protect the cops who commit the EJKs. Duterte says- “That’s our deal. When I said that you go and destroy the drug industry, destroying means destroying, including human life.” He said police officers who have faced difficulties in carrying out their duties should never stress over it as he says "I'll take care of you.”
This has caused many corrupt cops to abuse the power and protection given by the president. Because of this protection the deaths caused by the EJKs have risen rapidly claiming the lives of men, women, and children alike. One of the many victims was Kian De Los Santos a 17 year old boy in high school who was gunned down by cops. The official statement by the police was that allegedly Kian drew a firearm on the cops and it prompted them to fire back. Witness reports and a closed-circuit TV, though, showed two men pulling Kian around a basketball court in civilian wear. At the site of the confrontation, two small sachets of alleged shabu, a .45 calibre firearm and four shot cartridge cases were found. Witnesses have reported that they ordered Kian to run and handed him a gun. The Caloocan policemen believed Kian was a drug runner, but the accusation was vehemently refuted by the teenager's parents.
However it is not just physical damage and the loss of life that these EJKs cause but mental damage as well. Human Rights watcher Carlos H. Conde has investigated the trauma caused by the EJKs. One of Carlos’s subjects was a girl whose father was gunned down by the police which has created massive trauma. In a direct quote from Carlos-“What struck me deeply was the level of trauma that these kids have, When I talked to her about that, she was very articulate and forthright, but you could sense the deep psychological trauma that she suffered in witnessing the violence and also being reminded every day of what happened to her father”
These children paint a harrowing picture of the long-lasting consequences of the murders. Another harrowing example of how EJK effects children are three anonymous brothers. These three brothers, who were 15, 13 and 10 when their father was killed over two years ago, now live on the streets, after being essentially deserted by their mother, do not attend school and work menial jobs for rent. A 5-year-old boy's mother said he threatened to kill one of his friends and cover him in packing tape. "It's the same way the boy's father was discovered 19 times after being stabbed, his head wrapped in tape and a sign placed near him reading, "I'm a drug pusher. Don’t emulate me.”
From July 1, 2016 to June 30, 2019, the Philippine National Police announced that 5,526 criminals were killed during police operations. However, according to reports by domestic human rights organizations, this figure does not include the thousands of suspected gunmen killed in incidents that are not seriously investigated by the authorities, raising the death toll to as high as 27,000. Human Rights Watch reports and reputable media sources such as Rappler and Reuters say that these vigilante-style shootings were committed either by police officers themselves or by police-related killers. This has resulted in many cases with regards to the violation of human rights but only one case was brought to justice and it was the case of Kian.
Even today there are victims of this abuse in power. On Dec 20 2020 a mother and her son were killed by a policeman in Pampanga. This policeman by the name of Jonel Nuezca shot a middle aged woman by the name of Sonya Gregorio and her son by the name of Frank Gregorio. This whole incident was recorded on video and shows Nuezca take out a gun and shoot Sonya in the head, then shoots her son while they clutch each other, then shoots each of them a second time. The video soon went viral, prompting an internal investigation of the police officer and murder charges. He has handed himself in to the police but this is again a harsh reminder of how rampant this abuse of power is.
The presidents reach of power also extends over to the media and government. The United Nations Human Rights Council adopted a resolution in July 2019 urging the Office of the High Commissioner for Human Rights to send a briefing on the human rights situation in the Philippines in June 2020, putting international pressure for transparency to bear. The Duterte administration reacted by demanding the termination of all financial aid talks from the 18 countries adopting the resolution.
Journalists are also being silenced as well. This is the case with the company of ABS-CBN news network and the famous journalist Maria Ressa. In the case of ABS-CBN the company was accused of political bias. Duterte accused ABS-CBN of not being impartial or fair during the 2016 elections. These accusations go even further when the President accused ABS-CBN of aiding Duterte’s political competition. During the hearing for the franchise’s renewal the house of representatives voted on closing ABS-CBN after 25 years of news. Critics of the president say he's gone after media outlets who have closely reported his drug war, which since he took office in 2016 has left thousands of people dead. By government order, ABS-CBN ceased operations of its free TV and radio channels after its 25-year franchise expired in May.
This has caused massive repercussions amongst the Philippine society as 11,000 workers were left without a job and let go.
However there are massive long term effects as well. ABS-CBN was the number one news network in the country and their network reached across the various provinces. With no news network most of the country is not informed on the various events in the country. This was the case in November 2020 when Typhoon Ulysses hit the Cagayan Valley. Since there was no news of the upcoming Typhoon the residents of that province were unprepared and not ready. The result was a staggering amount of deaths in the Cagayan valley as well as a massive amount of damage. All this is the result of Duterte wanting to silence his critics because of his actions in the drug war.
Another example of Journalism being silenced is the case of Maria Ressa. Maria Ressa was the CEO of the news website Rappler. This news website vehemently criticized and watched Duterte’s movements and approached towards the drug war. Ever since the 2016 election Rappler has been a harsh critic for Duterte but in 2020 Maria Ressa was jailed. The allegations according to the court were “cyberlibel” which is equivalent to 200,000 pesos in damages plus a few years in jail. Ressa’s arrest sparked anger in millions including famous journalist Amal Clooney. Many have stated that this is an act that takes away the freedom of speech. A right that we Filipinos have because of our democratic government. Amal has said her self that “the court had become complicit in a sinister action to silence a journalist for exposing corruption and abuse”.
Rappler scrutinized Philippine President Rodrigo Duterte's government, revealed bot armies and corruption, and reported his ruthless anti-drug campaign, which, by some reports, has resulted in tens of thousands of extrajudicial killings. In exchange, Rappler was criticized as trading "fake news" by the president, and his administration launched multiple lawsuits against him. In addition to the cyber-libel allegations, Ressa is also facing further prosecution for libel, two court proceedings alleging unlawful foreign ownership of her enterprises, and inquiries into her old tax returns. The numerous allegations made against Ressa could lead to prison sentences of about 100 years.
Various journalists have also been victims to Duterte’s silencing. In November, one journalist had been killed: news anchor Eduardo Dizon of Mindanao's Kidapawan City, who was shot dead on July 10. At least one of them, Brandon Lee, was seriously wounded in an assault by a gunman in the northern Philippines in August. But it doesn't stop there as Duterte has passed an Anti Terror Bill which at close examination controls our freedom of speech. Under the statute, a criminal suspect can be arrested without trial for 14 days, a duration which may be extended to 24 days. Human rights lawyers argue that it breaks a constitutional requirement that after three days of arrest, an individual must be convicted. The anti terror law also will monitor any social media discourse related to offending the president or his administration.
Even today the ruthless reign of Duterte continues as the police are given more power while the masses suffer. During the lockdown the president has stated that he will kill anyone who violates it. “My orders to the police and the military, if anyone creates trouble, and their lives are in danger: shoot them dead.” This has created fear amongst the masses as well as a new view on how the people see our government.
In my personal opinion this is not what a leader is supposed to be. Before I started on this essay I put a quote about power and I feel this is more relevant now than ever. Duterte’s absolute power has corrupted the government absolutely. It has made the police think they are untouchable and has caused the poor people to suffer. Our president is waging a war on drugs that is not effective at all and the Filipino people are paying the price. A good leader in my opinion is one who puts the people first and not his agendas. A good leader is someone who takes the Filipino people’s lives into consideration and does not murder them in cold blood. So with this current societal issue happening in our country I ask that you spread the awareness of how bad our president is. Hopefully this country will change for the better and it will see a brighter tomorrow. In the end it is really up to the Filipino people and if they want their country to change.
“People should not be afraid of their governments, governments should be afraid of their people.”
V from V for Vendetta
Sources-
https://www.hrw.org/world-report/2020/country-chapters/philippines
https://humanrightsmeasurement.org/extrajudicial-killings-in-the-philippines/
https://newsinfo.inquirer.net/961396/duterte-to-cops-kill-criminals-if-you-have-to-ill-protect-you
https://www.pbs.org/wgbh/frontline/article/what-happens-to-the-families-left-behind-in-dutertes-deadly-campaign-against-drugs/
https://www.washingtonpost.com/world/asia_pacific/philippines-police-brutality-mother-shot/2020/12/21/0a5f9762-4358-11eb-ac2a-3ac0f2b8ceeb_story.html
https://www.statista.com/statistics/585152/people-shot-to-death-by-us-police-by-race/
https://www.hrw.org/tag/philippines-war-drugs
https://www.bbc.com/news/world-asia-46381697
https://cnnphilippines.com/news/2018/11/29/Kian-delos-Santos-murder-Caloocan-police-guilty.html
https://www.aljazeera.com/news/2020/4/2/shoot-them-dead-duterte-warns-against-violating-lockdown
https://www.nytimes.com/2020/07/10/world/asia/philippines-congress-media-duterte-abs-cbn.html
https://www.theguardian.com/world/2020/jun/15/maria-ressa-rappler-editor-found-guilty-of-cyber-libel-charges-in-philippines
https://reliefweb.int/report/philippines/philippines-typhoon-vamco-ulysses-cagayan-valley-region-impact-and-response-24
https://www.npr.org/2020/07/21/893019057/why-rights-groups-worry-about-the-philippines-new-anti-terrorism-law
28 notes
·
View notes
Text



i will sue this FB identity theft and intellectual property rights and cyberlibel im a marcos supporter im the only one who has blue aereal robotics my twitter has been hacked my IG joy_santosbagus100781 password blueuscia100781 my social media my color is blue caloocan city my motorbike is honda wave 110 with blue black red flairings but my favorite color is blue reg. plate 1303-0752840 now its 826 NCL my FB Jovelyn Santos Bagus if you want to get in to my FB just type my globe prepaid 09950677083 password blueuscia100781
0 notes
Text
https://news.abs-cbn.com/amp/news/07/03/20/duterte-signs-into-law-anti-terror-bill-despite-growing-opposition?__twitter_impression=true
apparently some Filipinos are locking down or deleting their social media because of this, and other recent events like govt shutting down tv nework abs-cbn, and maria ressa's cyberlibel conviction.
121 notes
·
View notes
Note
Yooooo, have you seen what's in Twitter? An account that translates questions made to isayama posted one about levihan, they asked him what levi thought about the "living together" of hanji and isayama said that he would want to draw it!!!! OMG if this is true... the implications!!!!! I screamed when I read it >w<
Hello Anon,
Thank you for your question! To answer your first one, yes I have a Twitter but I keep it private because our government sucks and can accuse us of cyberlibel and I'm incredibly vocal about the government so yeh.
I think I saw what you were talking about. (Apologies for the font.)
Rough translation of tweet below.
Question and Answer with Mr. Isayama in my head:
Q: What do you think about the scene when Hange suggested to Levi they live together in the forest?
Yams: I think I'd want to draw more about that Relationship.
Key word: 脳内 or the japanese equivalent of headcanon.
As painful as it is, this is probably just a Japanese version of "incorrect quotes."
Either way, still gonna hold on to the beast titan theory and risk getting my heart shattered like the idiot I am.

33 notes
·
View notes
Link
Maria Ressa, the founder of award-winning news site Rappler, was charged with her second cyber libel case at the Makati Regional Trial Court, several media reported today.
The case stems from a tweet that Ressa shared on Feb. 16, 2019, where she shared screenshots of a 2002 Philippine Star article that linked businessman Wilfredo Keng with the killing of Manila councilor Chika Go. The same report, which said that Keng was involved in several illegal activities, was taken down by Philippine Star from its website in 2019 after “the camp of Mr. Wilfredo Keng raised the possibility of legal action.”
Keng is the same complainant behind Ressa’s first cyberlibel case. Along with former Rappler reporter Reynaldo Santos, she was sentenced in June by a Manila court to at least six months in jail. This stemmed from a May 2012 Rappler article written by Santos, which said that Keng loaned vehicles to the late former Chief Justice Renato Corona.
Santos’ Rappler story used the now-deleted 2002 Philippine Star article as one of its sources.
Makati Senior Assistant City Prosecutor Mark Anthony Nuguit filed the second cyber libel case against Ressa on Nov. 23. He said that Ressa’s tweet that included screenshots of the Philippine Star article was done “willfully, unlawfully, feloniously, publicly and maliciously – with the intention of attacking the honesty, virtue, honor, integrity, character, and reputation” of Keng.
Ressa has filed a motion to quash the cyber libel case, saying that she is not the author of the Philippine Star article and should not be charged for tweeting screenshots of it.
“By any reasonable and unbiased reading, the sentence is not defamatory—read singly, none of the words are; read together, the sentence is not,” her petition read.
However, the prosecutor said that Ressa did not bother to get Keng’s side, and she “acted with reckless disregard whether the contents of the Twitter post was false or not.” He also recommended the journalist’s arrest and a bail of PHP48,000 (US$999).
Ressa is facing a string of other charges and has also been indicted for tax evasion and allegedly violating the anti-dummy law. She believes the charges are politically motivated because of Rappler’s critical coverage of President Rodrigo Duterte’s government.
Rappler was once called a “fake news” outlet by Duterte when it published a 2018 article that said his then-assistant and now Senator Christopher “Bong” Go intervened during the billion-peso procurement of Combat Management Systems for the Philippine Navy.
Republic Act 10175 or the Cybercrime Prevention Act of 2012, which the prosecution used as its basis for convicting Ressa and Santos for cyberlibel, was signed on Sept. 12, 2012 — four months after the Keng article was first published. The government said that Rappler could still be indicted because it was supposedly republished in February 2014 due to typographical errors.
9 notes
·
View notes
Text
Lesson 3: Online Safety and Security, Ethics and Netiquettes
Online Security is the knowledge of maximizing the user's personal safety and security risk to private information, and self-protection from computer crime in general.
10 Safety Tips
1. Know the Scam
2. Think before you click
3. Safety Peruse
4. Shop Safety
5. Kick-butt Password
6. Protect your infos
7. Watch your Wi-Fi Connectivity
8. Install a Fire wall
9. Keep up to Date
10. Use your noggin
COMMON ISSUES AND CRIMES IN THE INTERNET
Cyberbullying or cyberharassment is a form of bullying or harassment using electronic means. Cyberbullying and cyberharassment are also known as online bullying
The Anti-Bullying Act of 2013 (RA 10627)
(Sec. 2, RA 10627) These acts are collectively called “cyber bullying” when committed online. (Sec. 2-D, RA 10627) This covers social bullying aiming to belittle another individual or group or gender-based bullying that humiliates another on the basis of perceived or actual sexual orientation and gender identity. (Sec. 3, B-1, RA 10627, Implementing Rules).
The Revised Penal Code and the Cybercrime Prevention Act
One who publicly or maliciously imputes to another a crime, vice, defect, real or imaginary, or any act, omission, condition, status or circumstance tending to cause the dishonor, discredit or contempt of a natural or juridical person, or blacken the memory of one who is dead may be liable for libel under this Code. (Art. 353, RPC) These acts are more severely punished when done online in addition to the civil action for damages which may be brought by the offended party. (Sec. 4(c-4), RA 10175) Cyberlibel holds liable only the original author of the post (Sec. 5(3), Implementing Rules of RA 10175). Likers or sharers of a post cannot be held liable under this law.
HACKING
Hacking generally refers to unauthorized intrusion into a computer or a network. The person engaged in hacking activities is known as a hacker. This hacker may alter system or security features to accomplish a goal that differs from the original purpose of the system.
IDENTITY THEFT
Identity theft, also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information, such as Social Security or driver's license numbers, in order to impersonate someone else.
PLAGIARISM
Plagiarism is an act of fraud. It involves both stealing someone else's work and lying about it afterward.
NETIQUETTE
Is a combination of the word net and etiquette.
The Core Rules of Netiquette
Rule 1. Remember the human.
Rule 2. Adhere to the same standards of behavior online that you follow in real life.
Rule 3. Know where you are in cyberspace.
Rule 4. Respect other people's time and bandwidth.
Rule 5. Make yourself look good online.
Rule 6. Share expert knowledge.
Rule 7. Help keep flame wars under control.
Rule 8. Respect other people's privacy.
Rule 9. Don't abuse your power.
Rule 10. Be forgiving of other people's mistakes.
I learned about this lesson that we shoul be careful when we are surfing the net, because we might put ourselves in trouble if we just keep on clicking sites to sites without thinking about the consequences. We should learn to control ourselves when it comes to the internet. Just like they say "Think before you Click.".
Thank you!

Credits to the owner of the photo.
4 notes
·
View notes
Text
PORTFOLIO IN EMPOWERMENT TECHNOLOGY
CHAPTER 1 LESSON 1: INFORMATION AND COMMUNICATIONS TECHNOLOGY - Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. CONTENT STANDARD
- The learners demonstrate an understanding of ICT in the context of global communication for specific professional track.
Performance Standards
- The learners shall be able to: at the end of the 2-week period independently compose an insightful reflection paper on the nature of ICT in the context of their lives, society, and professional tracks (Arts, Tech Vocational, Sports and Academic)
Most essential learning competencies
The learners should be able to:
1. Compare and contrast the nuances of varied online platforms, sites, and content to best achieve specific class objectives or address situational challenges.
2. Apply online safety, security, ethics, and etiquette standards and practice in the use of ICTs as it would relate to their professional tracks. 3. Use the internet as a tool for credible research and information gathering to best achieve specific class objectives or address situational.
1.1 INFORMATION AND COMMUNICATION TECHNOLOGY

- ICT is the technology required for information processing, in particular, the use of the electronic computers, communication devices and software applications to convert, store, protect, process, transmit and retrieve information from anywhere, anytime.
- Information refers to the knowledge obtained from reading, investigation, study or research. The tools to transmit information are the telephone, television and radio. Information is knowledge and helps us to fulfill our daily tasks. - Communication is an act of transmitting messages. It is a process whereby information was exchanged between individuals using symbols, signs or verbal interactions. Communication is important in order to gain knowledge. Technology is the use of scientific knowledge, experience and resources to create processes products that fulfill human needs. Technology is vital in communication.
- ICT nowadays has also widened the horizon in developing new tools or emerging technologies. Mobile devices can communicate through wireless fidelity (Wifi), Bluetooth, third generation 3g & 4g, data services and dial up services and virtual private networks. EMERGING TECHNOLOGIES

- Artificial Intelligence (AI) - is the ability of a digital computer or computer controlled robot to perform tasks commonly associated with intelligent beings. The term is frequently applied to the project of developing systems endowed with the intellectual processes characteristics of humans, such as the ability to reason, discover meaning, generalize or learn from past experience. ROBOTICS

- Is a branch of engineering that involves the conception, design, manufacture, and operation of robots. This field overlaps with electronics, computer science, artificial intelligence, mehcatronics, nanotechonology and bioengineering. BIOMETRICS

- Are a way to measure a person’s physical characteristics to verify their identity. These can include physiological traits, such as fingerprints and eyes, or behavioral characteristics, such as the unique way you’d complete a security-authentication puzzle. QUANTUM CRYPTOGRAPHY

- Also called quantum encryption, applies principles of quantum mechanics to encrypt messages in a way that it is never read by anyone outside of the intended recipient. COMPUTER ASSISTED TRANSLATION

- Involves the use of software programs to translate both verbal and written texts. Also known as machine-assisted or machine aided translation. 3D IMAGING AND HOLOGRAPHY

- Is defined as a 3D projection that exists freely in space and is visible to everyone without the need for 3D glasses. VIRTUAL REALITY

- Refers to the computer generated simulation in which a person can interact within an artificial 3D environment using special electronic devices that can be similar to or completely different from the real world. ONLINE SAFETY

- Is the knowledge of maximizing the user’s personal safety and security and risk to private information, and self-protection from computer crime in general. 1. Know the scams - Learn about different kinds of scams and what you can do to avoid them.

2. Think before you click - Think twice, thrice and zillion time before click any link or buttons.

3. Safety Peruse - These sites may have an Address that’s very similar to a legitimate site, but the page can have misspelling, Bad Grammar, or low resolution Images.

4. Shop Safety - Don’t shop on a site unless it has “https” and a padlock icon on the left or right in the URL.

5. Kick-butt passwords - Use an Extremely uncrackable password One like “9&4thkel965#”.
6. Protect your info’s - Keep your guard up, Back up all your data on your computer, smartphone and tablet, theft or a cash.

7. Watch your Wi-Fi Connectivity - Protect your network by changing your router’s setting and making sure that you have the connection password protected.

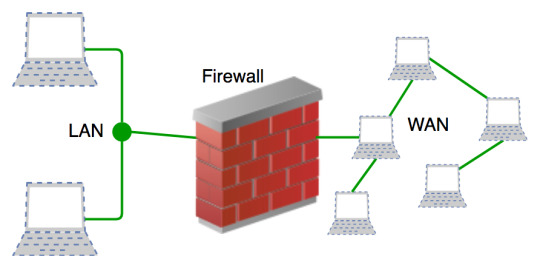
8. Install a Firewall - A firewall is a grate line of defense against cyber attracts.
9. Keep up to date - The best security updates automatically to protect your computer. - Use the manufacturer’s latest security patches to make regular updates and make that you have the software set to do routine scam.

10. Use your Noggin - Use your common sense while surfing the web.

COMMON ISSUES AND CRIMES IN THE INTERNET - CYBERBULLYING - HACKING - IDENTITY THEFT - PLAGIARISM - COPYRIGHT ISSUES CYBERBULLYING - Is a form of bullying or harassment using electronic means. Cyberbullying and Cyber Harassment are also known as online bullying. - Cyberbullying is when someone, typically teens, bully or harass others on the internet, particularly on social media sites. Harmful bullying behavior can include posting rumors, threats, sexual remarks, a victims’ personal information, or pejorative labels. THE ANTI-BULLYING ACT OF 2013 ( RA 10627 )
(Sec. 2, RA 10627) These acts are collectively “called cyber bullying” when committed online. (Sec. 2-D, RA 10627) This covers social bullying aiming to belittle another individual or group or gender-based bullying that humiliates another on the basis of perceived or actual sexual orientation and gender identity. (Sec. 3, B-1 RA 10627. Implementing Rules). THE REVISED PENAL CODE AND THE CYBERCRIME PREVENTION ACT. - One who publicly or maliciously imputes to another a crime, vice, defect, real or imaginary, or any act, omission, condition, status or circumstance tending to cause the dishonor, discredit or contempt of a natural or juridical person, or blacken the memory of one who is dead may be liable for libel under this Code. (Art, 353, RPC) These acts are more severely punished when done online in addition to the civil action for damages which may be brought by the offended party. (Sec. 4(c-4), RA 10175) Cyberlibel holds liable only the original author of the post (Sec. 5(3), Implementing Rules of RA 10175) Likers or shares of a post cannot be held liable under this law. - Slander may also be applicable to one who, in heat of anger, utters statements that are highly defamatory in character. (Art 358, RPC) Intriguing Against Honour may also find applicability when the principal purpose is to blemish the honour or reputation of a person. Hence, a blind ite is not as actionable as a named-post in social media. HACKING

- Hacking generally refers to unauthorized intrusion into a computer or a network. The person engaged in hacking activities is known as a hacker. This hacker may alter system or security features to accomplish a goal that differs from the original purpose of the system. - Hacking can also refer to non-malicious activities, usually involving unusual or improvised alterations to equipment or processes.
IDENTITY THEFT

- Also known as identity fraud, is a crime in which an imposter obtains key pieces of personally identifiable information, such as Social Security or driver's license numbers, in order to impersonate someone else. TYPES AND EXAMPLES OF IDENTITY THEFT 1. True-name identity theft means the thief uses personal information to open new accounts. The thief might open a new credit card account, establish cellular phone service or open a new checking account in order to obtain blank checks. 2. Account-takeover identity theft means the imposter uses personal information to gain access to the person's existing accounts. PLAGIARISM

- Is an act of fraud. It involves both stealing someone else's work and lying about it afterward. The following are considered plagiarism - turning in someone else's work as your own - copying words or ideas from someone else without giving credit - failing to put a quotation in quotation marks - giving incorrect information about the source of a quotation - changing words but copying the sentence structure of a source without giving credit - copying so many words or ideas from a source that it makes up the majority of your work, whether you give credit or not (see our section on "fair use" rules) Republic Act No. 8293 [An Act Prescribing the Intellectual Property Code and Establishing the Intellectual Property Office, Providing for Its Powers and Functions, and for Other Purposes]otherwise known as the Intellectual Property Code of the Philippines. Intellectual property rights under the I. P. Code: The intellectual property rights under the Intellectual Property Code are as follows: 1. Copyright and related rights; 2. Trademarks and service marks; 3. Geographic indications; 4. Industrial designs; 5. Patents; 6. Layout designs [topographies] of integrated circuits; and 7. Protection of undisclosed information. The scheme of penalties for infringement has also been changed. From the previous fine of Php200 to Php2,000 and/or imprisonment of 1 year, the current range of penalties are as follows: - For first offenders - fine of PhP50,000 to PhP150,000 and/or imprisonment of 1 to 3 years - For second offenders - fine of PhP150,000 to PhP500,000 and/or imprisonment of 3 to 6 years - For third and subsequent offenders - fine of PhP500,000 to PhP1.5 Million and/or imprisonment of 6 to 9 years. - In case of insolvency, the offender shall furthermore suffer subsidiary imprisonment. NETIQUETTE - Is a combination of the word net and etiquette.It focuses on the acceptable behavior of a person while using the internet resource. - It focuses on the acceptable behavior of a person while using the internet resource. The Core Rules of Netiquette Rule 1. Remember the human. - Never forget that the person reading your mail or posting is, indeed, a person, with feelings that can be hurt. - Corollary 1 to Rule #1: It's not nice to hurt other people's feelings. - Corollary 2: Never mail or post anything you wouldn't say to your reader's face. - Corollary 3: Notify your readers when flaming. Rule 2. Adhere to the same standards of behavior online that you follow in real life. Corollary 1: Be Ethical Corollary Corollary 2: Breaking the law is bad Netiquette. Rule 3. Know where you are in cyberspace. Corollary 1: Netiquette varies from domain to domain. Corollary 2: Lurk before you leap. Rule 4. Respect other people's time and bandwidth. Corollary 1: It's OK to think that what you're doing at the moment is the most important thing in the universe, but don't expect anyone else to agree with you Corollary 2: Post messages to the appropriate discussion group.Corollary 3: Try not to ask stupid questions on discussion groups Corollary 4: Read the FAQ (Frequently Asked Questions) document Corollary 5: When appropriate, use private email instead of posting to the group Corollary 6: Don't post subscribe, unsubscribe, or FAQ requests Corollary 7: Don't waste expert readers' time by posting basic information Corollary 8: If you disagree with the premise of a discussion group, don't waste the time and bandwidth of the members by telling them how stupid they are.Just stay away Corollary 9: Conserve bandwidth when you retrieve information from a host or server. Rule 5. Make yourself look good online. Corollary 1: Check grammar and spelling before you post Corollary 2: Know what you're talking about and make sense Corollary 3: Don't post flame-bait Rule 6. Share expert knowledge. Corollary 1: Offer answers and help to people who ask questions on discussion groups Corollary 2: If you've received email answers to a posted question, summarize them and post the summary to the discussion group. Rule 7. Help keep flame wars under control. Corollary 1: Don't respond to flame-bait Corollary 2: Don't post spelling or grammar flames Corollary 3: If you've posted flame-bait or perpetuated a flame war, apologize Rule 8. Respect other people's privacy. - Don't read other people's private email. Rule 9. Don't abuse your power. - The more power you have, the more important it is that you use it well Rule 10. Be forgiving of other people's mistakes. CONTEXTUALIZED ONLINE SEARCH AND RESEARCH SKILLS

- Online search is the process of interactively searching for and retrieving requested information via a computer from databases that are online. Interactive searches became possible in the 1980s with the advent of faster databases and smart terminals. Advantages and Disadvantages Advantages: - Ability to obtain a large sample, which increases statistical power - Data is automatically coded so no data entry errors - Reduced cost of conducting research Disadvantages: Online is not totally secure and theft is one of the numerous danger it poses, researchers personal information is at risk of being access by rogue persons. - Some of the materials on the internet have not been evaluated by experts or thoroughly screened - Lack of accreditation and low quality
RESEARCH SKILLS “Research” sometimes just means finding out information about a topic.You can certainly develop advanced information retrieval skills in Working with Sources. However, in specific understandings of “research” carry a lot of weight. The classic definition is that “research” leads to an original contribution to knowledge in a particular field of inquiry by defining an important question or problem and then answering or solving it in a systematic way. - So you will need to read on to develop a relevant understanding of what research means in your subject. - Research skills can be anything from looking at competitors and seeing what they do well to producing a written report on how your department could work better. Doing research in the world of work is all about stepping back from your day-to-day work and looking at ways you can improve. Important aspects of research: - Research design covers the key issues in developing a successful research project. - Research methods takes you to resources on essential techniques for carrying out convincing research. - Working with data will provide resources on the use of statistics and other numerical skills in research. Improving Your Research Skills Online 1. Know your sources. Make sure to find the most reliable information which can be found in multiple sources or, better, to have the original source. 2. Use your web browser properly. Know the capabilities of your preferred browser to help make your search faster and easier. 3. Organize your bookmarks. It is to organize the links you have marked. 4. Learn to use advanced search engines. Practice using advanced search techniques which are available in Google. 5. Follow the web. Follow the web information in the web. Just make sure to read and be critical in every link you click. SIX STRATEGIES THAT CAN HELP ONLINE STUDENTS PRODUCE STRONGER RESEARCH. 1. Contact a librarian before getting stuck sifting through piles of online information. 2. Consider that when in doubt, it's wiser to over-cite sources than risk plagiarism. 3. Use Google and other reliable resources at the beginning of a research process, not the end. 4. Don't think that the Web is your only source of information. 5. Understand the professor's expectations for citation format. 6. Understand why professors still assign research projects. Some examples of research skills that you may have include: 1. Report writing. 2. Analyzing lots of information from different sources. 3. Finding information off the internet. 4. Critical thinking. CHAPTER 2 APPLIED PRODUCTIVITY TOOLS Productivity Tools - It is a tools that can be a freeware or shareware. Freeware - is copyrighted, which can be used for free and for an unlimited time. Shareware - is a commercial software that is copyrighted, which can be copied for trial but needs to be purchased for continued use. Advanced Techniques Using Microsoft Word Microsoft Office Word

- One of the software of Microsoft Office 2013 suite. - Offers a set of tools that is compared to its previous versions. - Along with its new features are advanced techniques including hyperlinks, macros and mail merge. Hyperlink
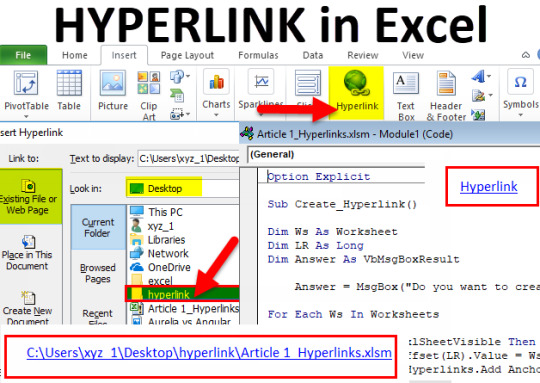
- A link that will direct you to another page or part of the same document. Creating a Hyperlink to an Existing Document - Suppose you are to link a part of your document to an existing document. - Click your mouse on the location in the document where you want to insert the hyperlink. - On the Insert Tab, click the Hyperlink button on the Links group. - On the Insert Hyperlink dialog box, click Existing File or Web Page and then select the File name where the source file is located and then hyperlink will be created on your document. - Press Ctrl+ click on the Hyperlink to open the linked file. Mail Merge
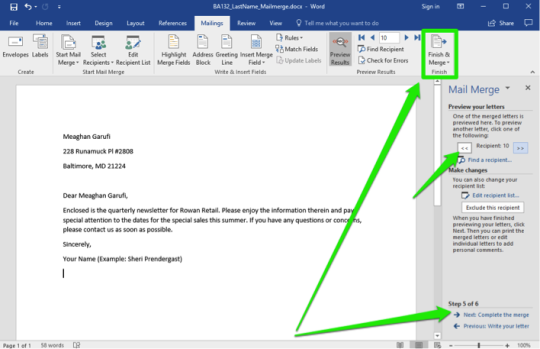
- Is a useful tool that allows you to quickly produce and send information, newsletter, resumes, or brochures to many people. Creating a Mail Merge 1. Open the word document that you want to Mail Merge. 2. On the Ribbon, click the Mailings tab, go to the Start Mail Merge group and click Start Mail Merge and select Step by Step Mail Merge Wizard. 3. The task pane will show the Mail Merge steps 1 to 6. PowerPoint

- It allows you to create slide show presentations wherein you can format the texts and images, adding also animations and other multimedia components interactively. Excel

- One of the applications created by Microsoft, used to simulate a paper worksheet.
- It is composed of cells that are represented in rows and columns design to perform basic arithmetic operations. - Widely used in accounting and financial applications, as well as statistics and engineering calculations. The following are the common Excel Functions: = SUM – Calculates the sum of the values of a range of cells = AVERAGE – Calculates the arithmetic mean of a range of cells = MAX - Gives the maximum value in a range of cells = MIN - Gives the minimum value in a range of cells = COUNT - Counts the number of cells in a range of cells BENIFITS OF ONLINE SOFTWARE Convenience - The applications should be intuitive and easy to use to ensure everyone can use them without spending a lot of time learning how. Scalability - The applications should be able to be used in all areas of your business and also work effectively no matter how much demand there is to use them or how much your business grows. Safety - All the applications should be safe to use with all existing systems and should have the ability to fully integrate with all other software and not inhibit the workers ability to do their job. Sustainability - All consumer-based software should be flexible and adaptable to have the ability to last for up to 10 years, but they must be able to expand functionally with other developments in software and operating systems. PRINCIPLES OF GRAPHICS AND DESIGN BALANCE UNITY MOVEMENT REPITITION PROXIMITY CONTRAST WHITESPACE BALANCE

- Describes the placement of elements of equal weight on the page. MOVEMENT

- Describes the flow of elements on the page.
1 note
·
View note