#critical infrastructure cybersecurity
Explore tagged Tumblr posts
Link

Most cyberattacks start from human error and the majority of the time, that error stems from a lack of awareness about the cyber risks faced by the industry. So insurance employees must understand their role in the fight against cyberattacks.
#Cybersecurity#Cybersecurity Solutions#cybersecurity partner#Protection Solutions#critical infrastructure cybersecurity#cybersecurity infrastructure
0 notes
Link

Lack of expertise in managing end-point devices and inadequate risk assessment communication at the highest level of the healthcare sector has also contributed to these cybersecurity vulnerabilities.
Today, healthcare institutions have become the preferred target for many cybercriminals.
#Cybersecurity#Cybersecurity Solutions#cybersecurity partner#Protection Solutions#critical infrastructure cybersecurity#cybersecurity infrastructure
0 notes
Text
AI, Cybersecurity, and National Sovereignty
Introduction: The Role of AI in Cybersecurity
As artificial intelligence (AI) becomes integral to national security, cyber threats increasingly exploit AI-driven vulnerabilities. Both India and China face the challenge of securing their cyber infrastructure while mitigating espionage and offensive cyber operations. The risks include large-scale data breaches, intellectual property theft, and attacks on critical infrastructure. With AI enhancing the scope and speed of cyberattacks, national sovereignty is increasingly threatened by cyber vulnerabilities that transcend borders.
AI-Driven Cyber Threats and Espionage
China has heavily integrated AI into its cyber capabilities, using it to enhance espionage, cyber warfare, and information manipulation. AI-enabled cyber operations allow China to gather vast amounts of intelligence data through advanced hacking techniques. These tools are often deployed through state-sponsored groups, exploiting zero-day vulnerabilities and penetrating government and corporate networks worldwide.
For example, in 2021, China was accused of orchestrating a large-scale cyber-attack targeting Microsoft Exchange servers, affecting over 30,000 organizations globally. This attack was designed to facilitate espionage, capturing sensitive information ranging from corporate intellectual property to government data. China's cyber operations underscore the increasing use of AI in orchestrating sophisticated, large-scale intrusions that threaten national sovereignty.
India, while lagging behind China in offensive cyber capabilities, faces persistent cyber espionage threats from Chinese state-sponsored actors. The most notable incidents occurred during the 2020 India-China border standoff, where Chinese hackers targeted India's critical infrastructure, including power grids and government networks. These attacks highlight the vulnerabilities in India's cybersecurity architecture and its need to enhance AI-driven defenses.
Vulnerabilities and National Sovereignty
AI-driven cyber threats pose significant risks to national sovereignty. For India, the challenges are magnified by the relatively underdeveloped nature of its cybersecurity infrastructure. Although the establishment of the Defence Cyber Agency in 2018 marked a step forward, India still lacks the offensive cyber capabilities and AI sophistication of China. India's defensive posture primarily focuses on securing critical infrastructure and mitigating cyber intrusions, but it remains vulnerable to cyber espionage and attacks on its digital economy.
China's integration of AI into both military and civilian cyber systems, through its Military-Civil Fusion policy, has bolstered its ability to conduct large-scale cyber operations with deniability. This fusion allows China to leverage private sector innovations for military purposes, making it a formidable cyber power in the Indo-Pacific region.
Case Studies: Cyber Confrontations
In 2019, a significant cyberattack targeted India's Kudankulam Nuclear Power Plant, which was traced back to North Korea, but was believed to be part of a broader effort involving Chinese actors. This incident highlighted the potential for AI-enhanced malware to target critical infrastructure, posing severe risks to national security.
Similarly, the 2020 Mumbai blackout, reportedly linked to Chinese hackers, emphasized how AI-driven cyberattacks can disrupt essential services, creating chaos in times of geopolitical tension. These incidents illustrate how AI-driven cyber capabilities are increasingly weaponized, posing severe risks to India's sovereignty and its ability to protect critical infrastructure.
Implications for Future Conflicts
As AI continues to evolve, the cyber domain will become a primary battleground in future conflicts between India and China. AI-enhanced cyber operations provide both nations with the ability to conduct espionage, sabotage, and information warfare remotely, without direct military engagement. For China, these tools are integral to its broader geopolitical strategy, while India must develop its AI and cybersecurity capabilities to protect its national sovereignty and counteract cyber threats.
Conclusion
The integration of AI into cybersecurity poses both opportunities and challenges for India and China. While China has aggressively developed AI-driven cyber capabilities, India faces an urgent need to enhance its defenses and develop its offensive cyber tools. As cyberattacks become more sophisticated, driven by AI, both nations will continue to grapple with the implications of these developments on national sovereignty and global security.
#AI and cybersecurity#National sovereignty#Cyber espionage#India China cyber conflict#AI driven threats#Cyber warfare#Critical infrastructure#Cyber defense#China cyber strategy#India cybersecurity#AI and national security#Cyberattacks#Espionage operations#AI vulnerabilities#Military Civil Fusion#Cyber sovereignty#Cyber espionage India#AI in geopolitics#AI enhanced malware#Data security
0 notes
Text
OT Security: The Achilles’Heel for Manufacturing.

In an era where digital transformation is reshaping industries, the manufacturing sector faces a unique set of cybersecurity challenges. As manufacturers increasingly integrate advanced technologies into their operations, the convergence of Operational Technology (OT) and Information Technology (IT) introduces both opportunities and vulnerabilities. This blend of legacy systems with modern innovations has made cybersecurity a critical concern, as the sector grapples with complex threats ranging from ransomware attacks to supply chain vulnerabilities.
ALSO READ MORE- https://apacnewsnetwork.com/2024/07/ot-security-the-achillesheel-for-manufacturing/
#A Critical Examination of OT Security Challenges#AGM-IT and CISO#Alok Shankar Pandey#Alok Shankar Pandey AGM-IT and CISO Dedicated Freight Corridor Corporation of India#Amarish Kumar Singh#Amarish Kumar Singh CISO Godrej#Apollo Tyres#Baidyanath Kumar Chief Data Protection Officer JK Lakshmi Cement#Boyce Manufacturing#CISO Godrej#cybersecurity leaders#Dedicated Freight Corridor Corporation of India#Head of Global Cybersecurity#IT systems#Mansi Thapar Head of Global Cybersecurity Apollo Tyres#Mansi Thaper#OT Security#Sanjay Sharma Head of IT Infrastructure and Cybersecurity Shram Pistons#Sudipto Biswas CISO Emami#The Achilles’Heel for Manufacturing#Top cybersecurity leaders#Top cybersecurity leaders India#Top cybersecurity leaders of India
0 notes
Text
The Median Recovery Costs for 2 Critical Infrastructure Sectors, Energy and Water, Quadruples to $3 Million in 1 Year, Sophos Survey Finds
Sophos, a global leader of innovative security solutions for defeating cyberattacks, recently released a sector survey report, “The State of Ransomware in Critical Infrastructure 2024,” which revealed that the median recovery costs for two critical infrastructure sectors, Energy and Water, quadrupled to $3 million over the past year. This is four times higher than the global cross-sector median.…
0 notes
Text
When Cyber Attacks Are the Least of Our Worries: 5 Shocking Threats to Critical Infrastructure
Introduction paragraph explaining the significance of the list. Use key phrases related to the topic for SEO optimization. Imagine a world where the things we rely on every day suddenly vanish. No power, no water, no internet—sounds like a bad sci-fi movie, right? But it’s more real than you might think. The importance of critical infrastructure can’t be overstated. These systems are the backbone…
#Critical Infrastructure#Cybersecurity#Emerging Threats#Infrastructure Protection#Infrastructure Vulnerabilities#National Security#Public Safety#Risk Management#Security Events#Technological Threats
0 notes
Text
Mandatory Cybersecurity Incident Reporting: The Dawn of a New Era for Businesses
A significant shift in cybersecurity compliance is on the horizon, and businesses need to prepare. Starting in 2024, organizations will face new requirements to report cybersecurity incidents and ransomware payments to the federal government. This change stems from the U.S. Department of Homeland Security’s (DHS) Cybersecurity Infrastructure and Security Agency (CISA) issuing a Notice of Proposed…

View On WordPress
#CIRCIA#CISA#Cyber Incident Reporting for Critical Infrastructure Act of 2022#Cybersecurity#Cybersecurity Infrastructure and Security Agency#Department Of Homeland Security#DHS#Information Protection#notice of proposed rulemaking#NPRM#reporting
0 notes
Text
a failed update from billion-dollar cybersecurity firm crowdstrike has crashed windows machines worldwide today (july 19th 2024), leaving everything from airport terminals to checkout machines to delivery apps to banks stuck with a blue screen of death. here's a screenshot from downdetector (au) to illustrate:


the issue appears to be with crowdstrike falcon, a form of antivirus software widely used in the corporate world -- with emphasis on the world. there have been reports from the us, uk, australia, germany, india, france, japan and more. places affected include (but are not limited to) supermarkets, banks, basically every airline, public transport networks, major broadcasters, emergency services, corporate offices, healthcare providers and stock exchanges.



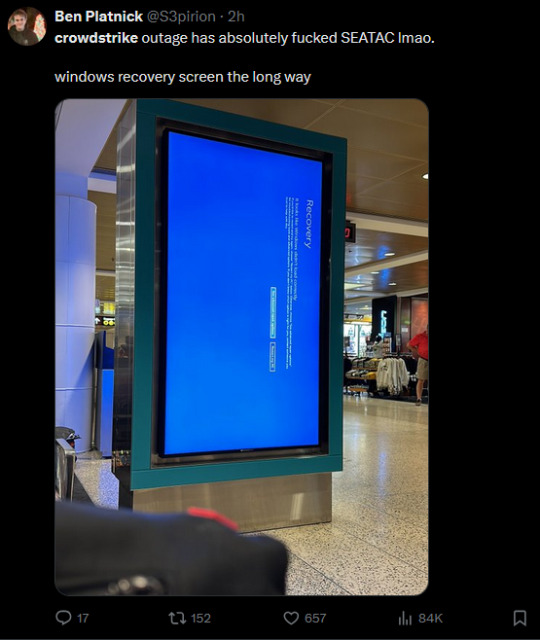

(woolies pic via archiestaines9 on twitter; s3pirion; akothari. yes that is masahiro sakurai of smash bros fame)
emergency service lines are currently experiencing problems within the american states of alaska, arizona, indiana, minnesota, new hampshire and ohio. similar problems likely plague other areas of the world, they just haven't been reported on yet. australian emergency services are operating, and critical infrastructure remains stable. be sure to check in with the local news stations still online for more updates.
welcome to y2k............................. 2!!!!!!!!!!!!!

13K notes
·
View notes
Text
The evolution of healthcare ransomware attacks - CyberTalk
New Post has been published on https://thedigitalinsider.com/the-evolution-of-healthcare-ransomware-attacks-cybertalk/
The evolution of healthcare ransomware attacks - CyberTalk


By Zac Amos, Features Editor, Rehack.com.
In recent years, ransomware has emerged as a critical threat to the healthcare industry, with attacks growing in frequency, sophistication and impact. These cyber assaults disrupt hospital operations, compromise patient safety and undermine data integrity.
Understanding how ransomware tactics have evolved — from basic phishing schemes to complex, multi-faceted attacks — enables healthcare organizations to develop more robust defenses. Staying informed about the latest trends and techniques that cyber criminals use allows healthcare providers to safeguard their systems and ensure the continuity of care.
Initial ransomware attacks
Early ransomware tactics in healthcare were relatively rudimentary but still impactful. The first known ransomware attack — the PC Cyborg or AIDS Trojan — occurred in 1989 and targeted roughly 20,000 researchers and medical institutions. This attack involved distributing infected floppy disks that encrypted file names and paying a ransom to unlock them.
Although primitive by today’s standards, this attack highlighted the vulnerability of healthcare systems. Hospitals faced significant disruptions, affecting patient care and operations. This early incident underscored the potential havoc that ransomware could wreak on the healthcare sector. It set the stage for more sophisticated future threats.
Evolution of attack vectors
The evolution of ransomware in healthcare has seen a significant shift; from simple phishing attacks to sophisticated social engineering techniques. Initially, attackers used basic phishing emails to trick individuals into downloading malicious software.
However, as defenses improved, cyber criminals adapted by using more advanced social engineering tactics. These methods involve conducting detailed research on targets, the creation of personalized messages and placing phone calls, as to gain trust and infiltrate systems.
Alongside this, Remote Desktop Protocol (RDP) exploits have surged. These exploits allow attackers to access healthcare networks remotely by exploiting weak passwords and unpatched systems.
The healthcare sector has also seen a rise in exploited vulnerabilities in medical devices and the IoT. Cyber criminals have increasingly targeted these interconnected systems — which often lack robust security measures — to launch attacks.
This trend was particularly evident in the fourth quarter of 2023. The healthcare industry accounted for 16% of all ransomware attacks, making it the second-most targeted sector during this period. Exploitation of vulnerabilities can disrupt medical services and poses significant risks to patient safety. In turn, this highlights the urgent need for enhanced cyber security measures in healthcare.
Advanced encryption and evasion techniques
As ransomware has evolved, attackers have developed more complex encryption methods to secure healthcare data more effectively. One notable tactic is double extortion, where cyber criminals encrypt data and threaten to release sensitive information if the victim doesn’t meet their demands. This dual threat has increased the pressure on targeted organizations.
Further, 74% of Chief Information Security Officers believe that AI-powered cyber threats, including advanced ransomware, significantly impact their organizations. Attackers are also implementing polymorphic malware, which constantly changes its code to avoid detection by traditional security systems. Techniques like this make it challenging to combat sophisticated threats.
Targeting larger and more critical institutions
Ransomware attackers have shifted from targeting small clinics to targeting large hospitals and extensive healthcare networks, resulting in more significant disruptions and higher ransom demands than previously. Larger institutions have substantial financial resources, which makes them attractive targets for cyber criminals seeking substantial payouts.
The financial impact of the attacks on larger healthcare organizations is profound. In 2023, experts reported data breaches costing an average of $10.93 million each. This cost increase underscores ransomware’s severe financial strain on healthcare providers. It affects their ability to deliver essential services and invest in further security measures.
Ransomware-as-a-service
The rise of Ransomware-as-a-Service (RaaS) platforms has contributed to the proliferation of ransomware attacks in the healthcare sector. These RaaS groups operate on various business models, including monthly subscriptions, one-time license fees, affiliate programs or pure profit-sharing arrangements.
Offering user-friendly interfaces and comprehensive support, RaaS has lowered the barrier to entry for cyber criminals. It even enables those with zero technical expertise to launch sophisticated attacks. This democratization of ransomware has led to an increase in the frequency and diversity of attacks. It poses a more significant threat to healthcare organizations that must now defend against an extremely broad range of adversaries.
Collaboration and sophistication of cyber criminals
The formation of ransomware syndicates and partnerships has further expanded the threat landscape in healthcare. Cyber criminal groups now share resources and intelligence, enhancing their capabilities and effectiveness. In fact, some RaaS operators provide ongoing technical support and grant access to private forums where hackers exchange tips and information, fostering a collaborative environment.
This collective effort allows more sophisticated attacks, as cyber criminals leverage advanced threat intelligence and surveillance to identify vulnerabilities and tailor their strategies. Consequently, healthcare organizations face increasingly coordinated and informed adversaries, making securing their systems even more challenging.
Countermeasures and mitigation strategies
In response to the evolution of advanced ransomware, healthcare organizations have had to enhance their defensive measures. Adopting multi-layered security approaches — involving a combination of firewalls, intrusion detection systems, regular software updates and employee training — has become paramount.
Additionally, AI and machine learning are crucial in detecting and preventing attacks. These technologies can analyze vast amounts of data in real time and identify unusual patterns more accurately than traditional methods. Leveraging AI-driven tools lets healthcare providers anticipate and mitigate ransomware attacks more effectively than otherwise. It also helps bolster their overall cyber security posture.
Adapting to an evolving threat
The need for continuous adaptation in cyber security strategies is critical as ransomware threats evolve and become more sophisticated. The future landscape of ransomware in healthcare will likely see more advanced tactics. This makes it essential for healthcare organizations to stay vigilant and proactive in their defense measures.
For more insights from Rehack Features Editor, Zac Amos, click here. Lastly, to receive practical cyber insights, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#000#2023#adversaries#affiliate#ai#AI-powered#analyses#attackers#barrier#Business#CNI#code#Collaboration#collaborative#Collective#comprehensive#compromise#continuous#critical infrastructure#cyber#cyber criminals#cyber security#Cyber Threats#cybersecurity#data#Data Breaches#data integrity#defense#defenses#democratization
0 notes
Text
Safeguarding Our Nation: The Imperative of Critical Infrastructure Protection

In an interconnected world where technology reigns supreme, the protection of our critical infrastructure is paramount. Critical infrastructure forms the backbone of our society, encompassing systems and assets vital for national security, economic stability, and public health and safety. From power grids to transportation networks, water supplies to telecommunications, each component plays a crucial role in sustaining our way of life. Thus, the concept of Critical Infrastructure Protection (CIP) emerges as a cornerstone in ensuring the resilience and security of our nation.
At its core, Critical Infrastructure Protection (CIP) entails the proactive measures taken to safeguard essential assets and systems against a myriad of threats. These threats encompass a broad spectrum, ranging from natural disasters and cyberattacks to physical sabotage and terrorism. The interconnected nature of modern infrastructure magnifies the potential impact of such threats, underscoring the need for comprehensive and robust protection strategies. By prioritizing CIP efforts, we aim to mitigate vulnerabilities, enhance resilience, and minimize the cascading effects of disruptions across critical sectors.
One of the fundamental challenges in Critical Infrastructure Protection lies in the recognition of interdependencies among various infrastructure sectors. A disruption in one sector can often trigger ripple effects, causing widespread consequences across interconnected systems. For instance, a cyberattack targeting financial institutions can disrupt not only the banking sector but also impact transportation, energy, and communication networks. Therefore, a holistic approach to CIP is essential, encompassing cross-sector collaboration, information sharing, and risk management practices.
Get More Insights On This Topic: Critical Infrastructure Protection
Explore More Related Topic: Singapore Meetings, Incentives, Conferences and Exhibitions (MICE) Market
#Critical Infrastructure#Protection#Security#Resilience#Risk Management#Homeland Security#Cybersecurity#Emergency Preparedness
0 notes
Text
Don’t let flaws compromise the integrity of the app!

In the modern digital era, where cyberattacks are getting more complex and frequent, application security is essential. App vulnerabilities can compromise the integrity of your app and put your users’ sensitive information at risk. Therefore, ensuring your application is secure and protected from potential cyber threats is essential. This blog will discuss how application security protects your apps by attaining, fixing, and strengthening the security once we deploy them. Read More: Don’t let flaws compromise the integrity of the app!
#app encryption#cloud app security#cloud security#critical infrastructure protection#cybersecurity and infrastructure security agency#data encryption#data encryption standard#data loss prevention#data security#database activity monitoring#endpoint security#firewall in computer network#infrastructure security#network admission control#network firewall security#Network Security#prisma cloud#secure cloud storage#security on the internet#web application security
0 notes
Text
White House looks to increase regulation of critical industries by adopting basic cybersecurity practices
The White House has released a new Cybersecurity strategy on Thursday. This new plan involves requiring critical infrastructure, such as water sanitation plants. This builds on previous guidance to regulate and require pipeline and rail industries to use basic cybersecurity measures to protect their infrastructure.
Having basic requirements and guidelines such as these is crucial in building public trust and support for our critical infrastructure. In the event of an attack on something as crucial as water supplies, there should be a swift and strong response that mitigates the damages as quickly as possible. As it can be seen from E Coli outbreaks from food processing plants, even if the response is quick, too many people can be affected by such an oversight. Preparing for potential bio terrorism attacks will hopefully prevent something similar from happening.
0 notes
Text
US Agencies Told to Assess IoT/OT Security Risks to Boost Critical Infrastructure Protection
US Agencies Told to Assess IoT/OT Security Risks to Boost Critical Infrastructure Protection
Home › ICS/OT US Agencies Told to Assess IoT/OT Security Risks to Boost Critical Infrastructure Protection By Eduard Kovacs on December 05, 2022 Tweet The US Government Accountability Office (GAO) has urged several federal agencies to conduct cybersecurity-related assessments in an effort to improve the protection of certain critical infrastructure sectors. The GAO pointed out that the DHS, CISA…
View On WordPress
0 notes
Text
Tumblr New Word Dictionary
I love new words. So here's a list of recently created words and idioms I have learned through tumblr (not all of these terms were invented on tumblr but that's where I learned them--the citations specify whether the term was coined by a specific post, or cite a source for where I first heard the term even if that is not necessarily where the term originated):
blorbo: a fictional character you're a fan of. Coined by thelustiestargonianmaid.
"I'm so hungry I could get banned from facebook": coined by babyslime in response to a Wil Wheaton post
GORIMM: Gross Older Relation I Must Marry. Source: bethanydelleman
hlep: when a disabled person asks for a specific kind of help and "they do something that is not what you ask for but is what they think you should have asked for ... Sure, it looks like help; it kind of sounds like help too; and if it was adjusted just a little bit, it could be help. But it's not help. It's hlep." Source: giantkillerjack's therapist.
horse fantasy: something that is theoretically possible unicorn fantasy: something that is definitely (or almost definitely) impossible. Source: bemusedlybespectacled.
zomancy: soup divination. Source: cryptotheism.
UFOs: unfinished objects--"something that is unfinished but in hibernation," as distinct from WIPs. Source: knitting community and bylambd.
autoenshittification: turning cars into digital extraction machines to steal your data and money through digital infrastructure and microchips, and the endless repair nightmare of digital car systems and cybersecurity vulnerabilities. Source: mostlysignssomeportents
nude: "when your clothes are off." naked: "when you're clothes are off when you're up to something." nakey: "when you are an animal and your collar has been removed." Source.
sideways fan: following a fandom second-hand. Source: capricorn-0mnikorn.
spoken Garamond: "the over-emphasized voice people use to read poems." Source: Frances Klein's friend.
nongry/nungry: when you're starving but also don't want to eat any of the food in your kitchen. Coined by tathrin.
scrumbling: scrolling on tumblr. Coined by the mum of anti-terf-posts.
window shipping: "any shipping done without actually watching/reading the work in question." Coined by lurker-no-more.
friend John / a Friend John answer: "when someone asks a relatively reasonable question in context and the enquiree 1) speaks at length without answering the question, and 2) implies the enquirer has injured the enquiree by even asking such a thing how could you." Coined by sileana.
bitism: a new school of media criticism which asks the simple question: is the work committed to the bit? Coined by linecoveredinjellyfish
snors d'oeuvre: having a little nap on the sofa before taking onseself to bed for main sleep. Coined by SJKSalisbury (can't find the tumblr repost now).
socratic terror: "what every athenian felt when they went down to the agora in the 5th century and saw an old man with a beard approaching them." Coined by lesbianshepard.
introvirtuous: "when you're introverted but have taken on numerous leadership and outgoing roles in your life." "I'm here to help. But I'd rather not be." "Someone around here has to get things done. and unfortunately it's going to be me." Coined by soundslikerhetorical.
grundlous: "of or pertaining to grundle." Coined by IMLIZY.
concretes: specific aspects of a character that persist across interpretations. The essential, structural essence that makes a character recognizable as the same person. Rarely physical traits; subjective. Coined by Ladylark and kayanem.
skeletonin: "the happiness chemical released when you see a ghoul or perhaps a ghost." Coined by gwentrification.
broflakes: "the weak, fragile 'alpha' males who are so easily threatened by strong women." Source: rickladd (can't find the tumblr reblog atm).
the planet of hats: "the thing where a people only have one thing going for them, like 'everyone wears a silly hat.'" Source: Star Trek fandom & TV tropes, learned via homonculus-argument.
feelings yakuza: "those who turn their personal discomfort into a social evil and try to erase the target completely." Source: Japanese fandom via マロミチャン.
Ship of Thesaurus / Rogetism: "When a student copies an essay online instead of writing it and then painstakingly changes every word to a synonym until the text no longer makes any sense." Coined by trek-tracks and Chris Sadler respectively.
Flemming's law / vibe dysphoria: "the most toxic person you've ever met over-relates to woodland creatures on social media." Coined by Chris Flemming and canadianwheatpirates.
fight with a gorilla: "any secret or invisible struggle." Coined by punksandcannonballers.
squimbus from my polls: the poll version of blorbo except for obscure fan favorite characters. Coined by yardsards.
pebbling: "the act of sending your friends & family little videos and tweets and memes you find online, like how penguins bring back pebbles to their little penguin loved ones." Source: NurseKelsey (can't find the tumblr reblog atm).
serpentineabouts: roundabouts that aren't round. Coined by paulgadzikowski.
luft: air equivalent of wet. Coined by questbedhead.
getting the good bologna: "when you experience something of better quality and then you’re doomed to no longer be satisfied." Coined by the family of kelssiel.
hypofixation: "the kind of things that you've autisticly decided you Do Not Care About." Antonym of hyperfixation. Coined by animate-mush.
57 notes
·
View notes
Text
Congress is moving closer to putting US election technology under a stricter cybersecurity microscope.
Embedded inside this year’s Intelligence Authorization Act, which funds intelligence agencies like the CIA, is the Strengthening Election Cybersecurity to Uphold Respect for Elections through Independent Testing (SECURE IT) Act, which would require penetration testing of federally certified voting machines and ballot scanners, and create a pilot program exploring the feasibility of letting independent researchers probe all manner of election systems for flaws.
The SECURE IT Act—originally introduced by US senators Mark Warner, a Virginia Democrat, and Susan Collins, a Maine Republican—could significantly improve the security of key election technology in an era when foreign adversaries remain intent on undermining US democracy.
“This legislation will empower our researchers to think the way our adversaries do, and expose hidden vulnerabilities by attempting to penetrate our systems with the same tools and methods used by bad actors,” says Warner, who chairs the Senate Intelligence Committee.
The new push for these programs highlights the fact that even as election security concerns have shifted to more visceral dangers such as death threats against county clerks, polling-place violence, and AI-fueled disinformation, lawmakers remain worried about the possibility of hackers infiltrating voting systems, which are considered critical infrastructure but are lightly regulated compared to other vital industries.
Russia’s interference in the 2016 election shined a spotlight on threats to voting machines, and despite major improvements, even modern machines can be flawed. Experts have consistently pushed for tighter federal standards and more independent security audits. The new bill attempts to address those concerns in two ways.
The first provision would codify the US Election Assistance Commission’s recent addition of penetration testing to its certification process. (The EAC recently overhauled its certification standards, which cover voting machines and ballot scanners and which many states require their vendors to meet.)
While previous testing simply verified whether machines contained particular defensive measures—such as antivirus software and data encryption—penetration testing will simulate real-world attacks meant to find and exploit the machines’ weaknesses, potentially yielding new information about serious software flaws.
“People have been calling for mandatory [penetration] testing for years for election equipment,” says Edgardo Cortés, a former Virginia elections commissioner and an adviser to the election security team at New York University’s Brennan Center for Justice.
The bill’s second provision would require the EAC to experiment with a vulnerability disclosure program for election technology—including systems that are not subject to federal testing, such as voter registration databases and election results websites.
Vulnerability disclosure programs are essentially treasure hunts for civic-minded cyber experts. Vetted participants, operating under clear rules about which of the organizer’s computer systems are fair game, attempt to hack those systems by finding flaws in how they are designed or configured. They then report any flaws they discover to the organizer, sometimes for a reward.
By allowing a diverse group of experts to hunt for bugs in a wide range of election systems, the Warner–Collins bill could dramatically expand scrutiny of the machinery of US democracy.
The pilot program would be a high-profile test of the relationship between election vendors and researchers, who have spent decades clashing over how to examine and disclose flaws in voting systems. The bill attempts to assuage vendors’ concerns by requiring the EAC to vet prospective testers and by prohibiting testers from publicly disclosing any vulnerabilities they find for 180 days. (They would also have to immediately report vulnerabilities to the EAC and the Department of Homeland Security.)
Still, one provision could spark concern. The bill would require manufacturers to patch or otherwise mitigate serious reported vulnerabilities within 180 days of confirming them. The EAC—which must review all changes to certified voting software—would have 90 days to approve fixes; any fix not approved within that timetable would be “deemed to be certified,” though the commission could review it later.
A vendor might not be able to fix a problem, get that fix approved, and get all of its customers to deploy that fix before the nondisclosure period expires.
“Updates to equipment in the field can take many weeks, and modifying equipment close to an election date is a risky operation,” says Ben Adida, the executive director of the vendor VotingWorks.
Some vendors might also chafe at the bill’s legal protections for researchers. The legislation includes a “safe harbor” clause that exempts testing activities from the prohibitions of the Computer Fraud and Abuse Act and the Digital Millennium Copyright Act, and bars vendors from suing researchers under those laws for accidental violations of the program’s terms.
There is also a funding question. The SECURE IT Act doesn’t authorize any new money for the EAC to run these programs.
“I hope Congress accounts for the necessary funding needed to support the increased responsibilities the EAC will take on,” says EAC chair Ben Hovland. “Investments in programs like this are critical to maintaining and strengthening the security of our elections.”
Meanwhile, the bill’s prospects are unclear. Even if it passes the Senate, there is no sign of similar momentum in the House.
23 notes
·
View notes
Text
i don’t really get the people jumping to liken this incident to y2k. not to say there were never any incidents caused by calendar formatting or anything, but what we’re talking about here is the result of the aggressive normalization of auto-pushing improperly tested non-critical software updates and a company who practically attained a partial monopoly on cybersecurity software having the power to, without warning, singlehandedly put a shocking amount of corporate and infrastructure PCs into a boot loop state because they’re just allowed to automatically push a non-staggered corrupted update at kernel level.
25 notes
·
View notes