#blackenergy
Explore tagged Tumblr posts
Text
Evil Malware
Welcome back to another episode of An Actual Post. As usual, no prior computer science education needed. Today I'm going to talk about the worst of the worst malware. A lot of things has happened since what the general population consider to be viruses; annoying and maybe steals some money or logins. Unfortunately it's nowadays way way way worse than that so prepare for some uncomfortable reading!
Since the dawn of Stuxnet (which I wrote about here), malware has gotten increasingly more real-life, with real-life complications. It could be the Pegasus spyware, that targets political activists in authoritarian regimes, or disruptive infections that put a stop to Copenhagens metro trains for a few hours. But we're merely in the beginning, because in the last few years, some nasty shit has been going down. I'm going to write about two (technically three but I'll group the first two together for obvious reasons) of the worst incidents we've seen today.
BlackEnergy and CrashOverride
This piece of malware has been around since early 2000's, for the intention of creating DDoS attacks (which I wrote about here) from infected computers. It has since then branched out in its usage, particularly into targeting infrastructure environments. Most notable is the 2015 Ukrainian powergrid incident, which occured when the Russian hacking group known as "Sandworm", infected three Ukrainian energy companies, wiping out systems and causing a power outage for over 250 000 households during winter. The attack began with just one infected document being opened in the affected companies. When BlackEnergy infected their systems, it opened up a remote connection to the attackers, making them able to control the entire powergrid opreation from inside Russia, and thereby switching it off.
That was not enough though, as the attackers also implanted another piece of malicious software known as KillDisk, which wiped out many of the ciritical operation systems, as well as cutting off the connection to the UPS units, which are backup generators in case of system outage. To add a cherry on top, BlackEnergy did what it was originally intended to do - DDoS attacks - towards the energy companies call-centers, so that customers were not able to call and ask what was happening.
The Ukrainian powergrid is quite outdated, which made the attack easier, but it was also the saving grace, as they still had manual power-switches (as opposed to purely digital, which were under the attackers control), so power was eventually restored before they had to rebuild all of their digital systems. This is more concerning for countries with modern powergrids, as manual switches have all been replaced by only digital, meaning power restoration could take weeks or months in case of a similar attack.
Besides the energy companies, three other critical Ukrainian infrastructure organisations were hit by BlackEnergy, but did not result in any operational outages.
But it didn't stop there. Just one year later, in December 2016, a similar attack struck Kiev, successfully taking down one-fifth of the countrys electrical power. Like with the BlackEnergy incident, it was quite quickly restored, but there was a far more horrifying infection this time. Named CrashOverride, the malware was much more sophisticated than BlackEnergy, did more things automatically without the need of input from a remote attacker. It was also modular, meaning that functionalities could just be added to it like lego-pieces, adapting it to whatever kind of electrical grid it was entering. This meant that it wouldn't just be able to infect only Ukranian electrical grids, but just about any country's. Furthermore, evidence points to the 2016 CrashOverride infection only being a test-run.
Triton
Last but definitely not least - Triton, the first (known) malware designed to kill.
But before we talk about it, we need to look at what happened in Bhopal, India in 1984 when what has since been considered the worst industrial disaster of all time occured. At the Union Carbide India Limited pesticide plant in December 2nd, one of the gas tanks had a fatal malfunction, creating a massive gas leak of methyl isocyanate, which is extremely toxic. The leak spread to the surrounding city of Bhopal, resulting in almost 600 000 injured people, 40 000 temporary injuries, 4 000 permanent or severe injuries and over 8 000 people died within the first two weeks, with an estimated additional 8 000 deaths following due to injuries in the time after.
This was of course not caused by Triton, but it became the inspiration for the creation of the malware In 2017, a new piece of malware was discovered in Schneider Electrics industrial control system (called Triconex) at a Saudi Arabian petrochemical facility, which unravelled a horrible and complex secret. The infection chain for Triton contains many steps, so let's start with a brief overview of what the Triconex ICS and SIS is. ICS (Industrial Control System) are computers that handles all the industrial processes, computers that are programmed to do one thing and one specific thing only, unlike our regular PCs which you can play games or surf the internet and whatever. ICS will be computers who control valves, releases chemicals into vats, spins stuff around, or whatever automated processes may happen at an industrial facility.
SIS (Safety Instrumented System) are a kind of ICS that are responsible to check that everything is going alright and, if needed, will take over the process in case some ICS is failing and may result in damage, fire, injury or other disasters. So a SIS are monitoring failsafes, meant to prevent what happened in Bhopal.
Unless, of course, you program a malware intended to make the SIS malfunction.
What happened in the Saudi Arabian petrochemical facility started as follows:
The attackers successfully implanted a remote access trojan, which just like in the BlackEnergy case, makes the attackers able to control infected machines remotely. However, you can't infect a ICS or SIS this way, you need to enter a regular computer with internet access first, which is what they did. The initial machine was an engineering station, on which ICS and SIS computers are controlled. From there, the attackers wanted to plant their own software on the ICS and SIS machines, but there was a problem; the software can't be installed without someone turning a physical key on the Triconex devices, as a security measure. A second problem is that every time new software changes are made to a Triconex device, the old software will be deleted and replaced entirely by the new, which meant that the malware was at risk of being deleted if any engineer made any software changes.
So a second piece of Triton malware was made to overcome those hurdles. Instead of being save where the software should be saved in the Triconex devices, it saved itself where the firmware was installed (the piece of software that's made to have the Triconex work as opposed to where the software that tells the Triconex what to do), this not only gave Triton persistence even if new software was loaded, but also overrides the physical key as firmware always has administrator privileges. With all this in place, the attacker could execute any commands at the comfort of their home to both the ICS and SIS systems in the facility.
As luck would have it, before the attackers were able to cause any harm, the facility experienced a safety incident, prompting shutdown of the whole operation, and an investigation later uncovered the malware in the systems. Had Triton not been discovered in time, it would have been able to cause catastrophic failures similar to what happened in Bhopal. But just because it was thwarted this time, doesn't mean it's gone for good. There will always be some actor who is willing to try again.
Thank you for reading and sorry if I scared you, but honestly I think people need to be aware of the situation, as for some bisarre reason, events like these are not reported in the news. If you have any questions, feel free to send an ask!
267 notes
·
View notes
Text
LockBit Ransomware Group Threatens Federal Reserve Board with Data Leak

As of June 25, 2024, the notorious LockBit ransomware group has allegedly breached the Fed's systems and is threatening to release 33 terabytes of sensitive government data if their ransom demands are not met. The Threat and Its Implications LockBit, a ransomware group with suspected ties to Russia, posted on their dark website: "33 terabytes of juicy banking information containing Americans' banking secrets. You better hire another negotiator within 48 hours, and fire this clinical idiot who values Americans' bank secrecy at $50,000." This threat, if genuine, could have severe implications for national security and the financial sector. The Federal Reserve Board, being a crucial component of the U.S. financial system, holds vast amounts of sensitive data. A breach of this magnitude could potentially expose confidential information about American banking operations and individual financial records.
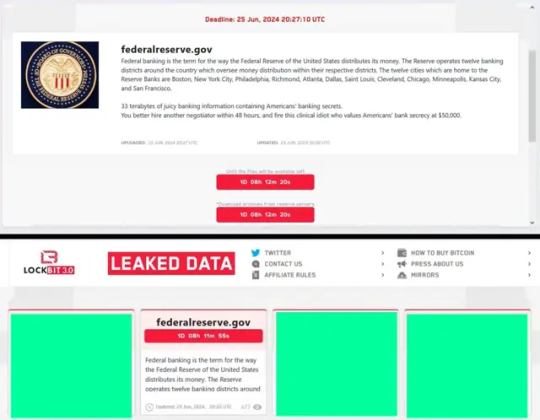
LockBit's Track Record LockBit has a history of high-profile attacks across various sectors, including: - Small businesses - Multinational corporations - Hospitals - Schools - Nonprofit organizations - Critical infrastructure - Government and law-enforcement agencies Notable targets have included the Thales Group, the Toronto Hospital for Sick Children, and the U.S. subsidiary of the Industrial and Commercial Bank of China. Escalating Cybersecurity Tensions This alleged attack comes amid rising cybersecurity tensions between the United States and Russia. Recent actions by the U.S. government include: - Banning the use of Kaspersky anti-virus software - Placing 12 Kaspersky executives on the Specially Designated National List - Indicting Dimitry Yuryevich Khoroshev, alleged mastermind behind LockBit, by the Treasury Department on May 7 Morgan Wright, chief security advisor to SentinelOne and SC Media columnist, noted that Russian cyberattacks often serve as retaliation for perceived or actual actions by other nations. He cited the BlackEnergy attack on Ukraine in 2015 as an example of such retaliatory measures. Ongoing Investigation and Response As of the latest update, the Federal Reserve Board has not confirmed the breach. When contacted, the FBI declined to comment on the situation, stating, "The FBI declines to comment. Agnidipta Sarkar, vice president, and CISO Advisory at ColorTokens, emphasized the need for further updates and potential regulatory intervention. He stated, "If this is indeed true, regulators will need to intervene to ensure that (potentially impacted) businesses are breach-ready, and banks will need to prioritize foundational cybersecurity by isolating critical operations from other systems." Despite recent law enforcement actions against LockBit, including infrastructure seizures and the exposure of its alleged leader, the group appears to have continued its criminal activities. This persistence underscores the ongoing challenges in combating sophisticated ransomware operations. Read the full article
0 notes
Text
「宮崎正弘の国際情勢解題」
令和六年(2024)2月7日(水曜日)
通巻第8120号
『サイバー真珠湾』、『デジタル911』って何?
大がかりなサイバー攻撃でインフラが麻痺する懸念拡がる
*************************
「サイバー真珠湾」を最初に造語したのはレオン・バネッタ元国防長官とされ、重要なインフラを機能不全に陥れ、国家の安全保障、経済、社会に重大な損害を与える、仮想的なサイバー攻撃が大規模の行われる事態を意味する。
バネッタはオバマ政権下でCIA長官から国防長官に横滑りした。中国への強硬発言で知られ、令和元年には日本政府が勲章を授与している。
こうしたサイバー攻撃の能力を持つのはロシア、中国、イラン、北朝鮮といった国家単位だけではなくテロリスト集団、裁判犯罪集団などである。送電網、発電所、緊急医療機関、港湾、鉄道、電話局、交通機関、金融機関、通信ネットワークなどのインフラ・システムを標的に国家の安定、経済、安全を混乱させ、弱体化させる。
たとえば2020年にイランの核施設を標的とした、米国とイスラエルによって実行されたと推定され���サイバー攻撃で、イランのコンピュータ・システムがウイルスに感染し、遠心分離プロセスを制御不能にした。
何者かのウクライナの送電網への攻撃 (2015 年12月)では、ウクライナの送電網が破壊された。23 万人以上の住民が停電による影響を受けた。使用されたマルウェア「BlackEnergy」とよばれ、ロシアによるものとの疑惑が残った。
ランサムウェアの大規模な攻撃は2017 年 5 月で『ワナクライ』と呼ばれるランサムウェアの攻撃により、150ケか国以上、20万台のコンピューターが感染した。犯行グループはファイルを暗号化しており、被害に遭った国家や機関、組織に巨額の身代金を要求した。とくに英国の医療機関が攻撃され、国民への保健サービスに深刻な影響がでた。
『サイバー真珠湾』を『デジタル真珠湾』と呼び変えたのはカーネギー財団の報告書だった。たしかに日本人から見れば後者の銘々のほうが適切だろう。また『サイバー911』と呼ぶ学者やシンクタンクもある。
すでに日本でも工場や病院が攻撃され、あるいは最近では名古屋港のコンピュータ・システムが攻撃され、輸出港のコンテナターミナルが機能不全となって大型トラックの長い劣ができた。
身代金の金額や、方法(ビットコインだったか?)などは公表されていない。
半導体がさらに発展し細密化しAIが高度化したとき、某国が仕掛ける大規模なサイバー攻撃が深刻に懸念されている。げんに筆者は1997年に『中国台湾電脳大戦』(講談社)を世に問うている。中国語版もでて、台湾で大きな反響があった。
1 note
·
View note
Text
البنية التحتية تحت الهجوم السيبراني لفترة أطول مما تعتقد
قبل شهور قليلة تعرضت شبكة الكهرباء في أوكرانيا للهجوم عندما حاولت مجموعة Sandworm نشر برامج ضارة تسمى Industroyer2 ضد عمليات مورد الطاقة في البلاد، Industroyer2 الذي تم الكشف عنه خلال جهود استجابة شملت ESET و CERT-UA هو نوع جديد من البرامج الضارة المعقدة تسمى Industroyer والتي أطفأت الأنوار في أجزاء من كييف في ديسمبر 2016. بالإضافة إلى ذلك و في ديسمبر 2015 ، قطع مشغلو BlackEnergy إمدادات الطاقة…

View On WordPress
0 notes
Photo

Guo O Dong, “The Persistence of Chaos” (2019)
A laptop running 6 pieces of malware that have caused financial damages totaling $95B.
The piece is isolated and airgapped to prevent against spread of the malware.
Malware:
ILOVEYOU
The ILOVEYOU virus, distributed via email and file sharing, affected 500,000+ systems and caused $15B in damages total, with $5.5B in damages being caused in the first week.
MyDoomMyDoom,
potentially commissioned by Russian e-mail spammers, was one of the fastest spreading worms. It's projected that this virus caused $38B in damages.
SoBigSoBig
was a worm and trojan that circulated through emails as viral spam. This piece of malware could copy files, email itself to others, and could damage computer software/hardware. This piece of malware caused $37B in damages and affected hundreds of thousands of PCs.
WannaCry
WannaCry was an extremely virulent ransomware cryptoworm that also set up backdoors on systems. The attack affected 200,000+ computers across 150 countries, and caused the NHS $100M in damages with further totals accumulating close to $4B.
DarkTequila
A sophisticated and evasive piece of malware that targeted users mainly in Latin America, DarkTequila stole bank credentials and corporate data even while offline. DarkTequila costed millions in damages across many users.
BlackEnergy
BlackEnergy 2 uses sophisticated rootkit/process-injection techniques, robust encryption, and a modular architecture known as a "dropper". BlackEnergy was used in a cyberattack that prompted a large-scale blackout in Ukraine in December 2015.
NC10-14GB 10.2-Inch Blue Netbook (2008), Windows XP SP3, 6 pieces of malware, power cord, restart script, malware
10.3” x 1.2” x 7.3” 2.8Lbs
(Final bid received: $1,345,000)
Courtesy of the artist and Deep Instinct
#art#conceptual#conceptual art#i love you#mydoom#sobig#virus#wannacry#blackenergy#fun#samsung#deepimpact#cybersecurity#cyberpunk#guo o dong#chaos#airgapped#windows xp#malware#darktequila#auction#bid#surreal
9 notes
·
View notes
Photo

Great feeling to be successful | Beautiful & confident : Loc Hair Care | link in bio : Dm for 🗣 : @kimmipeta : : : #blackwomanmagic#blackgoddess#sunkissedskin#sunkissedhair#locqueen#blackenergy (at New Jersey) https://www.instagram.com/p/CZMnF6buf8S/?utm_medium=tumblr
0 notes
Photo




THINK AND ENGAGE CHANGE.
BRAVE the album has been out for more than a week now and GIL is still busy.
The album is now available for streaming and download on Spotify and Bandcamp.com
Spotify : https://open.spotify.com/album/2mxzps0a4CKcIujXIC9qEH?si=kBAAwbSHTpedZHMaDJ4AfQ
Bandcamp: isgil.bandcamp.com/brave
#BRAVE#GIL#Bandcamp#Spotify#Ottawa#Toronto#Hiphop#Rap#Newmusic#Excerptstimuli#Ottawaartists#Nigerianartists#Newalbum#nikonphotography#nikonnofilter#canada#blackenergy#beyondspace#beyondspacestudios
5 notes
·
View notes
Photo

Black Energy Samurai Energy Drink Can 250ml - 32mg / 100ml Can manufactured by Canpack
I’m confused by this can. I think it may be the massive word “Black” on a red can but then I think this is one of the brands to suffer from naming themselves after their first product and then struggling to branch out without it being weird. I quite like the design aesthetic of the Hanzi (which my phone tells me say “Samurai”, rather predictably) but the rest of the can is somewhat standard and not particularly interesting. The other point of interest is the slightly strange flavour of “Cherry, Ginger and Sake”
https://energydrinkcans.uk/cans/black-energy-samurai/
0 notes
Photo

#EmpowerYourself #VictoryWithHonor #MikeTyson #BlackEnergy #BlueBerry (at Poland) https://www.instagram.com/p/CBnk7MYCy8K/?igshid=115at71hapxk0
0 notes
Photo

"Never apologize for being a powerful woman." Swipe left to view all forms and little bit of details...because this one is different from my other medium of art.....#glitterwork Shines in the blue light...... Heyaa to the audience 🙋 .......I took long to design and post this piece. There was so much disturbing going on out there in #bollywood .... learn that goal is to be happy and #notglamorous I don't know where I can relate this artwork to ! I just draw and colour what speaks to my soul.....everything relatable almost......but everyone have different point of view ! I don't know why I made this #darkartworks .....may be its dark art(as demanded) ...may b its not ....but I found this relatable to some pains... the world is suffering from. How this art speaks to you ....or what relatibility it might have with your thoughts ...do let me know through your comment so that I can write a better caption...... #wiccanfamily #wiccaritual #wiccan #wiccaspells #wiccansofinstagram #girlwithbun #purpleportrait #waxcolor #fabercastelcolorpencils Inspired by her hands @sandrarclemente #spreadbeautywithkindness #powerfulwomenrising #darkartsofficial #darkartists #darkartandcraft #darkartsubmission #blackenergy #powerfulyou #purplediamond #motivationartworkers #sketchingcharcoal #glitterartwork #glamorousnails #glamorousqueen #wicca (at Rajasthan) https://www.instagram.com/p/CBlP9LonLl9/?igshid=1ny2wlimnwhmt
#glitterwork#bollywood#notglamorous#darkartworks#wiccanfamily#wiccaritual#wiccan#wiccaspells#wiccansofinstagram#girlwithbun#purpleportrait#waxcolor#fabercastelcolorpencils#spreadbeautywithkindness#powerfulwomenrising#darkartsofficial#darkartists#darkartandcraft#darkartsubmission#blackenergy#powerfulyou#purplediamond#motivationartworkers#sketchingcharcoal#glitterartwork#glamorousnails#glamorousqueen#wicca
0 notes
Photo

Fight the power #mrhoundztooth #facemask #facemaskhomemade #powertothepeople#blacklivesmatter #designer #artist #custommade #tailoring #blackfist #paintedmask #artistsoninstagram #revolution #blackenergy https://www.instagram.com/p/CBQ7ruapExP/?igshid=dzqi2xt0d81e
#mrhoundztooth#facemask#facemaskhomemade#powertothepeople#blacklivesmatter#designer#artist#custommade#tailoring#blackfist#paintedmask#artistsoninstagram#revolution#blackenergy
0 notes
Video
instagram
And to the #haters really! #dontcare #lordhelpem #Blackenergy #fuckem #Kiz1beats #Charlotte (at Charlotte, North Carolina) https://www.instagram.com/p/B9kChZLl4QU/?igshid=a3zgzm8si44m
0 notes
Photo

“Unity” - Queen Latifah Tones: 3-2-1Y12 #BlackExcellence #Season2 #MondayMotivation #BlackMenLove #black #blacklovemagic #blackpositivevibes #blackenergy #reparations #blackskin #BlackWomenMatter #BlackMenMatter #MyBlackHistory #beauty #faith #love #blck #blackart #justice #peace #art #AllPower #BlackFacts #BlackChicago #BlackHistory #BlackLivesMatter #skincollect https://www.instagram.com/p/Bzqi4zNnEH3/?igshid=mu2kvr8hv6mk
#blackexcellence#season2#mondaymotivation#blackmenlove#black#blacklovemagic#blackpositivevibes#blackenergy#reparations#blackskin#blackwomenmatter#blackmenmatter#myblackhistory#beauty#faith#love#blck#blackart#justice#peace#art#allpower#blackfacts#blackchicago#blackhistory#blacklivesmatter#skincollect
0 notes
Text
Cyberattacks attributed to Russia from as far back as *2015* mirror their kinetic war in Ukraine
Yes, even regarding their occupation of a nuclear plant.
Here are relevant excerpts from the full article I wrote on the topic of malware & industrial control systems some time ago, which you can read in full here. I copy pasted it so if links are weird check the original I am too tired to perfect it for a tumblr upload.
This is an art blog but I have been trying to make people read about these things for eons and it is, unfortunately, more relevant than ever right now.
Cyberattacks say a lot about intentions of the offender. They are not trapped in the cyber world. I think of them as a promise, not a test.
It was December 23rd 2015, and 200,000 Ukrainians were left without electricity for up to six hours. The attack shut off 30 distribution substations located in the Kyiv and western Ivano-Frankivsk region [1][21]. The malware forced manual power restoration since the SCADA equipment was inoperable, elongating the delay. The attack was not especially sophisticated, which makes it especially alarming — breakers were being tripped manually through remote control software. A variation of the BlackEnergy malware was identified as what facilitated the power outage. It too was introduced to the company network through spear-phishing emails.
Then on December 17th 2016, another power outage occurred in Ukraine as the consequence of a cyberattack, six days short of a year after the first. Approximately 225,000 customers were affected [1] though power was restored much faster this time around — within three hours. Only one transmission substation was impacted, located in Kyiv [21].
The most disturbing difference is the 2016 attack demonstrated an escalation in technique — it is believed to have been facilitated by direct SCADA manipulation malware. The malware became known as CRASHOVERRIDE, the first of its kind: crafted to disrupt electrical grids [1].
CRASHOVERRIDE was the fourth piece of malware directed specifically at ICSs. Preceded only by Stuxnet, BlackEnergy-2 and Havex. Havex and BlackEnergy are suspected to be the work of a group known as GRIZZLEY STEPPES, or occasionally Dragonfly/energetic bear. Evidence suggests they are a threat actor group with ties to Russian intelligence and military agencies [1]. Both attacks on Ukrainian power grids have been attributed to Russia [21].
A year later, In the early hours of June 27th 2017, malware not unlike Slammer spread around the world with unprecedented speed. Its crosshair was locked on Ukraine, and it nearly entirely crippled them.
It began with the CEO of Dragos — an ICS cybersecurity firm — tweeting a report indicating that an electric power supplier to Kyiv had been hacked. Maersk announces its IT systems are down not long after, with countless other companies subsequently being incapacitated. Their screens displayed nothing but a ransom note demanding payment to unencrypt the now inaccessible files. Around five hours pass and Kaspersky tweets a statement detailing that the ransomware is not that of any previously identified.
At the time of the Kaspersky report it had infected approximately 2,000 organizations [16]. The ransomware was credited with being the fastest propagating piece of software to date. It took 45 seconds to bring down the network of a large Ukrainian bank. In a major Ukrainian transit hub, it took 16 seconds. The attack cost more than $10 billion in damage [12]. The malware had the appearance of the ransomware Petya, but files were not unencrypted once the ransom was paid — that appearance was a distraction. The malware was a worm designed to cause immeasurable disruption. The malware was named NotPetya.
The list of victims is long and varied; It hit four hospitals in Kyiv, six power companies, two airports and more than twenty two Ukrainian banks. It managed to escape Ukranian networks, hamstringing hospitals in Pennsylvania and a chocolate factory in Tasmania, Australia. It incapacitated multinational companies including a pharmaceutical giant, a European subsidiary of FedEx and the Danish shipping company AP Moller-Maersk. Maersk was responsible for 76 ports all over the world and nearly 800 seafaring vessels. This attack rendered them inoperable — close to a fifth of the entire world’s shipping capacity had been immobilized [12].
Even Chernobyl nuclear power plant operations were impacted; they were forced to switch to manual radiation monitoring since its windows-based sensors had been shut down. ATMs and point-of-sale terminals were infected rendering citizens unable to pay for essential goods or transport if they did not have cash on hand. Even if they did, many vendors were equally as paralysed [12][13].
Some evidence suggests that the source of the infection was a Ukrainian software company pushing an update for their accounting software Me Doc. It was suspected to be the accidental conduit from which the worm propagated, though they deny this claim [17]. The attack has been attributed to Russia by the Five Eyes and Canada [15]. Possibly due to the fact that it also compromised Ukrenego, the energy company rendered inoperable by the 2016 power grid attack [12]. According to a spokesperson, the NotPetya attack did not affect the power supply [13]. The way in which NotPetya impacted the Chernobyl nuclear plant illustrates that such an attack may be equally as dangerous as a direct attack on ICS safety controls.
Then in the summer of 2017, not even a year later, an attack of that exact nature was discovered. It used the first known piece of malware that specifically targeted industrial safety systems designed to protect human lives [1] [9] [10].
In a worst-case scenario, the code could have resulted in an explosion or a release of toxic hydrogen sulphide gas. The 1984 Bhopal gas tragedy, amongst the world’s worst industrial disasters, involved a leak of poisonous gases and it killed thousands [10]. The malware was first discovered at an anonymous Saudi Arabian petrochemical plant. It earned the name TRITON, after the Triconex safety controller model it targeted.
TRITON’s most alarming characteristic was its focus on manipulating industrial safety systems and it was built to communicate using the proprietary TriStation protocol, of which there is no public documentation. It targeted the safety instrumental system with precision, with no manipulation of the DCS beyond using it to gain access [9]. The threat actor knew precisely what they were there to target and no time was wasted in doing so.
Evidence suggests the hackers had been inside the company’s corporate IT networks since 2014. It is suspected that they worked their way into an EWS through the network, potentially through a vulnerability or via employee login credentials. This allowed them to identify the make and models and firmware versions of the hardware controllers [10].
The attacker persisted even after failed attempts due to one of their script’s conditional checks [9]. In June 2017 a flaw in the code triggered a response from a safety system which brought the plant to a halt, first attributed to a mechanical glitch. In August, several more systems were tripped which caused a shutdown. This instigated an investigation to be called upon [10].
TRITON was suspected to be the work of Iran, but a FireEye report details evidence that suggests the attack may have been the work of The Central Scientific Research Institute of Chemistry and Mechanics, Moscow- a Russian government-owned organization. There is evidence of recent activity by this same threat actor [11] [36].
#notpetya#ukraine#cybersecurity#malware#cyber attacks#history#IT#ukraine crisis#ukraine war#i stand with ukraine
5 notes
·
View notes
Photo

The U.S. government has charged 6 Russian intelligence officers for carrying out destructive malware attacks—including BlackEnergy, Industroyer, KillDisk, NotPetya, and Olympic Destroyer. Details: https://t.co/TqyzLT2egL #infosec #cybersecurity (via Twitter http://twitter.com/TheHackersNews/status/1318438742047141888)
2 notes
·
View notes
Text
Russian hackers are hacking major email servers
New Post has been published on https://techneptune.com/tech-news/russian-hackers-are-hacking-major-email-servers/
Russian hackers are hacking major email servers
NSA: Russian hackers are hacking major email servers
NSA He says Russian hackers are Hack major email servers. The National Security Agency has issued a security warning saying that this feat has been rampant since last year.
NSA: Russian hackers are hacking major email servers
NSA warns of Russian hackers exploiting EXIM exploit
The National Security Agency has said that hackers of Unit 74455 of the GRU Main Center for Special Technologies (GTsST), a division of the Russian military intelligence service, has hacked major email servers using the mail transfer agent EXIM.
The group is known as Sand worm, has been exploiting the vulnerability CVE-2019-10149, which involves EXIM servers that would cause the victim’s computer to download and run a shell script from a Sandworm-controlled domain. The shell script would be Add privileged users, Disable network security settings, Update SSH settings to allow additional remote accessand Execute an additional script to allow trace exploitation.
EXIM servers generally run a UNIX-based operating system, and many companies and governments widely use that their alternative, which is Microsoft’s proprietary Exchange, is not widely known.
The Sandworm group has been infamous for the past decade with famous feats like the BlackEnergy Malware that infected nuclear servers in Ukraine in December 2015 and December 2016. The group also participated in the US presidential election. USA From 2016 they attacked the emails from the Democratic National Committee and entered the voter registration databases.
The CVE-2019-10149 vulnerability was revealed in June 2019 with many malicious actors who abused it as soon as it was made public. Microsoft also issued an alert after two weeks at the time, warning Azure customers that a threat actor had created a self-expanding Exim worm that exploited this vulnerability to take over servers running on the Azure infrastructure.
Almost half of the servers that handle SMTP, which are email servers, are vulnerable to this vulnerability with statistics showing that half of all Exim servers have been updated to version 4.93 or later, leaving a large number of instances Exim exposed to attack.
1 note
·
View note