#apple software installation service
Explore tagged Tumblr posts
Text
How I ditched streaming services and learned to love Linux: A step-by-step guide to building your very own personal media streaming server (V2.0: REVISED AND EXPANDED EDITION)
This is a revised, corrected and expanded version of my tutorial on setting up a personal media server that previously appeared on my old blog (donjuan-auxenfers). I expect that that post is still making the rounds (hopefully with my addendum on modifying group share permissions in Ubuntu to circumvent 0x8007003B "Unexpected Network Error" messages in Windows 10/11 when transferring files) but I have no way of checking. Anyway this new revised version of the tutorial corrects one or two small errors I discovered when rereading what I wrote, adds links to all products mentioned and is just more polished generally. I also expanded it a bit, pointing more adventurous users toward programs such as Sonarr/Radarr/Lidarr and Overseerr which can be used for automating user requests and media collection.
So then, what is this tutorial? This is a tutorial on how to build and set up your own personal media server using Ubuntu as an operating system and Plex (or Jellyfin) to not only manage your media, but to also stream that media to your devices both at home and abroad anywhere in the world where you have an internet connection. Its intent is to show you how building a personal media server and stuffing it full of films, TV, and music that you acquired through indiscriminate and voracious media piracy various legal methods will free you to completely ditch paid streaming services. No more will you have to pay for Disney+, Netflix, HBOMAX, Hulu, Amazon Prime, Peacock, CBS All Access, Paramount+, Crave or any other streaming service that is not named Criterion Channel. Instead whenever you want to watch your favourite films and television shows, you’ll have your own personal service that only features things that you want to see, with files that you have control over. And for music fans out there, both Jellyfin and Plex support music streaming, meaning you can even ditch music streaming services. Goodbye Spotify, Youtube Music, Tidal and Apple Music, welcome back unreasonably large MP3 (or FLAC) collections.
On the hardware front, I’m going to offer a few options catered towards different budgets and media library sizes. The cost of getting a media server up and running using this guide will cost you anywhere from $450 CAD/$325 USD at the low end to $1500 CAD/$1100 USD at the high end (it could go higher). My server was priced closer to the higher figure, but I went and got a lot more storage than most people need. If that seems like a little much, consider for a moment, do you have a roommate, a close friend, or a family member who would be willing to chip in a few bucks towards your little project provided they get access? Well that's how I funded my server. It might also be worth thinking about the cost over time, i.e. how much you spend yearly on subscriptions vs. a one time cost of setting up a server. Additionally there's just the joy of being able to scream "fuck you" at all those show cancelling, library deleting, hedge fund vampire CEOs who run the studios through denying them your money. Drive a stake through David Zaslav's heart.
On the software side I will walk you step-by-step through installing Ubuntu as your server's operating system, configuring your storage as a RAIDz array with ZFS, sharing your zpool to Windows with Samba, running a remote connection between your server and your Windows PC, and then a little about started with Plex/Jellyfin. Every terminal command you will need to input will be provided, and I even share a custom #bash script that will make used vs. available drive space on your server display correctly in Windows.
If you have a different preferred flavour of Linux (Arch, Manjaro, Redhat, Fedora, Mint, OpenSUSE, CentOS, Slackware etc. et. al.) and are aching to tell me off for being basic and using Ubuntu, this tutorial is not for you. The sort of person with a preferred Linux distro is the sort of person who can do this sort of thing in their sleep. Also I don't care. This tutorial is intended for the average home computer user. This is also why we’re not using a more exotic home server solution like running everything through Docker Containers and managing it through a dashboard like Homarr or Heimdall. While such solutions are fantastic and can be very easy to maintain once you have it all set up, wrapping your brain around Docker is a whole thing in and of itself. If you do follow this tutorial and had fun putting everything together, then I would encourage you to return in a year’s time, do your research and set up everything with Docker Containers.
Lastly, this is a tutorial aimed at Windows users. Although I was a daily user of OS X for many years (roughly 2008-2023) and I've dabbled quite a bit with various Linux distributions (mostly Ubuntu and Manjaro), my primary OS these days is Windows 11. Many things in this tutorial will still be applicable to Mac users, but others (e.g. setting up shares) you will have to look up for yourself. I doubt it would be difficult to do so.
Nothing in this tutorial will require feats of computing expertise. All you will need is a basic computer literacy (i.e. an understanding of what a filesystem and directory are, and a degree of comfort in the settings menu) and a willingness to learn a thing or two. While this guide may look overwhelming at first glance, it is only because I want to be as thorough as possible. I want you to understand exactly what it is you're doing, I don't want you to just blindly follow steps. If you half-way know what you’re doing, you will be much better prepared if you ever need to troubleshoot.
Honestly, once you have all the hardware ready it shouldn't take more than an afternoon or two to get everything up and running.
(This tutorial is just shy of seven thousand words long so the rest is under the cut.)
Step One: Choosing Your Hardware
Linux is a light weight operating system, depending on the distribution there's close to no bloat. There are recent distributions available at this very moment that will run perfectly fine on a fourteen year old i3 with 4GB of RAM. Moreover, running Plex or Jellyfin isn’t resource intensive in 90% of use cases. All this is to say, we don’t require an expensive or powerful computer. This means that there are several options available: 1) use an old computer you already have sitting around but aren't using 2) buy a used workstation from eBay, or what I believe to be the best option, 3) order an N100 Mini-PC from AliExpress or Amazon.
Note: If you already have an old PC sitting around that you’ve decided to use, fantastic, move on to the next step.
When weighing your options, keep a few things in mind: the number of people you expect to be streaming simultaneously at any one time, the resolution and bitrate of your media library (4k video takes a lot more processing power than 1080p) and most importantly, how many of those clients are going to be transcoding at any one time. Transcoding is what happens when the playback device does not natively support direct playback of the source file. This can happen for a number of reasons, such as the playback device's native resolution being lower than the file's internal resolution, or because the source file was encoded in a video codec unsupported by the playback device.
Ideally we want any transcoding to be performed by hardware. This means we should be looking for a computer with an Intel processor with Quick Sync. Quick Sync is a dedicated core on the CPU die designed specifically for video encoding and decoding. This specialized hardware makes for highly efficient transcoding both in terms of processing overhead and power draw. Without these Quick Sync cores, transcoding must be brute forced through software. This takes up much more of a CPU’s processing power and requires much more energy. But not all Quick Sync cores are created equal and you need to keep this in mind if you've decided either to use an old computer or to shop for a used workstation on eBay
Any Intel processor from second generation Core (Sandy Bridge circa 2011) onward has Quick Sync cores. It's not until 6th gen (Skylake), however, that the cores support the H.265 HEVC codec. Intel’s 10th gen (Comet Lake) processors introduce support for 10bit HEVC and HDR tone mapping. And the recent 12th gen (Alder Lake) processors brought with them hardware AV1 decoding. As an example, while an 8th gen (Kaby Lake) i5-8500 will be able to hardware transcode a H.265 encoded file, it will fall back to software transcoding if given a 10bit H.265 file. If you’ve decided to use that old PC or to look on eBay for an old Dell Optiplex keep this in mind.
Note 1: The price of old workstations varies wildly and fluctuates frequently. If you get lucky and go shopping shortly after a workplace has liquidated a large number of their workstations you can find deals for as low as $100 on a barebones system, but generally an i5-8500 workstation with 16gb RAM will cost you somewhere in the area of $260 CAD/$200 USD.
Note 2: The AMD equivalent to Quick Sync is called Video Core Next, and while it's fine, it's not as efficient and not as mature a technology. It was only introduced with the first generation Ryzen CPUs and it only got decent with their newest CPUs, we want something cheap.
Alternatively you could forgo having to keep track of what generation of CPU is equipped with Quick Sync cores that feature support for which codecs, and just buy an N100 mini-PC. For around the same price or less of a used workstation you can pick up a mini-PC with an Intel N100 processor. The N100 is a four-core processor based on the 12th gen Alder Lake architecture and comes equipped with the latest revision of the Quick Sync cores. These little processors offer astounding hardware transcoding capabilities for their size and power draw. Otherwise they perform equivalent to an i5-6500, which isn't a terrible CPU. A friend of mine uses an N100 machine as a dedicated retro emulation gaming system and it does everything up to 6th generation consoles just fine. The N100 is also a remarkably efficient chip, it sips power. In fact, the difference between running one of these and an old workstation could work out to hundreds of dollars a year in energy bills depending on where you live.
You can find these Mini-PCs all over Amazon or for a little cheaper on AliExpress. They range in price from $170 CAD/$125 USD for a no name N100 with 8GB RAM to $280 CAD/$200 USD for a Beelink S12 Pro with 16GB RAM. The brand doesn't really matter, they're all coming from the same three factories in Shenzen, go for whichever one fits your budget or has features you want. 8GB RAM should be enough, Linux is lightweight and Plex only calls for 2GB RAM. 16GB RAM might result in a slightly snappier experience, especially with ZFS. A 256GB SSD is more than enough for what we need as a boot drive, but going for a bigger drive might allow you to get away with things like creating preview thumbnails for Plex, but it’s up to you and your budget.
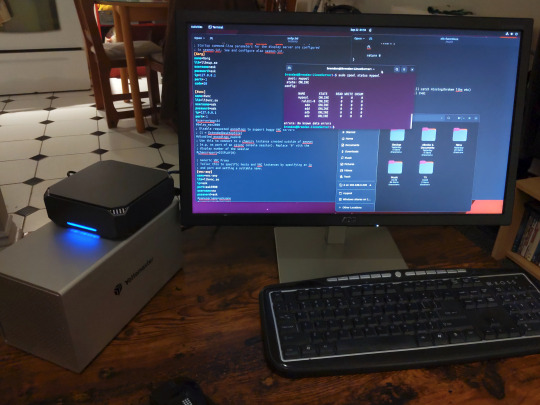
The Mini-PC I wound up buying was a Firebat AK2 Plus with 8GB RAM and a 256GB SSD. It looks like this:

Note: Be forewarned that if you decide to order a Mini-PC from AliExpress, note the type of power adapter it ships with. The mini-PC I bought came with an EU power adapter and I had to supply my own North American power supply. Thankfully this is a minor issue as barrel plug 30W/12V/2.5A power adapters are easy to find and can be had for $10.
Step Two: Choosing Your Storage
Storage is the most important part of our build. It is also the most expensive. Thankfully it’s also the most easily upgrade-able down the line.
For people with a smaller media collection (4TB to 8TB), a more limited budget, or who will only ever have two simultaneous streams running, I would say that the most economical course of action would be to buy a USB 3.0 8TB external HDD. Something like this one from Western Digital or this one from Seagate. One of these external drives will cost you in the area of $200 CAD/$140 USD. Down the line you could add a second external drive or replace it with a multi-drive RAIDz set up such as detailed below.
If a single external drive the path for you, move on to step three.
For people with larger media libraries (12TB+), who prefer media in 4k, or care who about data redundancy, the answer is a RAID array featuring multiple HDDs in an enclosure.
Note: If you are using an old PC or used workstatiom as your server and have the room for at least three 3.5" drives, and as many open SATA ports on your mother board you won't need an enclosure, just install the drives into the case. If your old computer is a laptop or doesn’t have room for more internal drives, then I would suggest an enclosure.
The minimum number of drives needed to run a RAIDz array is three, and seeing as RAIDz is what we will be using, you should be looking for an enclosure with three to five bays. I think that four disks makes for a good compromise for a home server. Regardless of whether you go for a three, four, or five bay enclosure, do be aware that in a RAIDz array the space equivalent of one of the drives will be dedicated to parity at a ratio expressed by the equation 1 − 1/n i.e. in a four bay enclosure equipped with four 12TB drives, if we configured our drives in a RAIDz1 array we would be left with a total of 36TB of usable space (48TB raw size). The reason for why we might sacrifice storage space in such a manner will be explained in the next section.
A four bay enclosure will cost somewhere in the area of $200 CDN/$140 USD. You don't need anything fancy, we don't need anything with hardware RAID controls (RAIDz is done entirely in software) or even USB-C. An enclosure with USB 3.0 will perform perfectly fine. Don’t worry too much about USB speed bottlenecks. A mechanical HDD will be limited by the speed of its mechanism long before before it will be limited by the speed of a USB connection. I've seen decent looking enclosures from TerraMaster, Yottamaster, Mediasonic and Sabrent.
When it comes to selecting the drives, as of this writing, the best value (dollar per gigabyte) are those in the range of 12TB to 20TB. I settled on 12TB drives myself. If 12TB to 20TB drives are out of your budget, go with what you can afford, or look into refurbished drives. I'm not sold on the idea of refurbished drives but many people swear by them.
When shopping for harddrives, search for drives designed specifically for NAS use. Drives designed for NAS use typically have better vibration dampening and are designed to be active 24/7. They will also often make use of CMR (conventional magnetic recording) as opposed to SMR (shingled magnetic recording). This nets them a sizable read/write performance bump over typical desktop drives. Seagate Ironwolf and Toshiba NAS are both well regarded brands when it comes to NAS drives. I would avoid Western Digital Red drives at this time. WD Reds were a go to recommendation up until earlier this year when it was revealed that they feature firmware that will throw up false SMART warnings telling you to replace the drive at the three year mark quite often when there is nothing at all wrong with that drive. It will likely even be good for another six, seven, or more years.

Step Three: Installing Linux
For this step you will need a USB thumbdrive of at least 6GB in capacity, an .ISO of Ubuntu, and a way to make that thumbdrive bootable media.
First download a copy of Ubuntu desktop (for best performance we could download the Server release, but for new Linux users I would recommend against the server release. The server release is strictly command line interface only, and having a GUI is very helpful for most people. Not many people are wholly comfortable doing everything through the command line, I'm certainly not one of them, and I grew up with DOS 6.0. 22.04.3 Jammy Jellyfish is the current Long Term Service release, this is the one to get.
Download the .ISO and then download and install balenaEtcher on your Windows PC. BalenaEtcher is an easy to use program for creating bootable media, you simply insert your thumbdrive, select the .ISO you just downloaded, and it will create a bootable installation media for you.
Once you've made a bootable media and you've got your Mini-PC (or you old PC/used workstation) in front of you, hook it directly into your router with an ethernet cable, and then plug in the HDD enclosure, a monitor, a mouse and a keyboard. Now turn that sucker on and hit whatever key gets you into the BIOS (typically ESC, DEL or F2). If you’re using a Mini-PC check to make sure that the P1 and P2 power limits are set correctly, my N100's P1 limit was set at 10W, a full 20W under the chip's power limit. Also make sure that the RAM is running at the advertised speed. My Mini-PC’s RAM was set at 2333Mhz out of the box when it should have been 3200Mhz. Once you’ve done that, key over to the boot order and place the USB drive first in the boot order. Then save the BIOS settings and restart.
After you restart you’ll be greeted by Ubuntu's installation screen. Installing Ubuntu is really straight forward, select the "minimal" installation option, as we won't need anything on this computer except for a browser (Ubuntu comes preinstalled with Firefox) and Plex Media Server/Jellyfin Media Server. Also remember to delete and reformat that Windows partition! We don't need it.
Step Four: Installing ZFS and Setting Up the RAIDz Array
Note: If you opted for just a single external HDD skip this step and move onto setting up a Samba share.
Once Ubuntu is installed it's time to configure our storage by installing ZFS to build our RAIDz array. ZFS is a "next-gen" file system that is both massively flexible and massively complex. It's capable of snapshot backup, self healing error correction, ZFS pools can be configured with drives operating in a supplemental manner alongside the storage vdev (e.g. fast cache, dedicated secondary intent log, hot swap spares etc.). It's also a file system very amenable to fine tuning. Block and sector size are adjustable to use case and you're afforded the option of different methods of inline compression. If you'd like a very detailed overview and explanation of its various features and tips on tuning a ZFS array check out these articles from Ars Technica. For now we're going to ignore all these features and keep it simple, we're going to pull our drives together into a single vdev running in RAIDz which will be the entirety of our zpool, no fancy cache drive or SLOG.
Open up the terminal and type the following commands:
sudo apt update
then
sudo apt install zfsutils-linux
This will install the ZFS utility. Verify that it's installed with the following command:
zfs --version
Now, it's time to check that the HDDs we have in the enclosure are healthy, running, and recognized. We also want to find out their device IDs and take note of them:
sudo fdisk -1
Note: You might be wondering why some of these commands require "sudo" in front of them while others don't. "Sudo" is short for "super user do”. When and where "sudo" is used has to do with the way permissions are set up in Linux. Only the "root" user has the access level to perform certain tasks in Linux. As a matter of security and safety regular user accounts are kept separate from the "root" user. It's not advised (or even possible) to boot into Linux as "root" with most modern distributions. Instead by using "sudo" our regular user account is temporarily given the power to do otherwise forbidden things. Don't worry about it too much at this stage, but if you want to know more check out this introduction.
If everything is working you should get a list of the various drives detected along with their device IDs which will look like this: /dev/sdc. You can also check the device IDs of the drives by opening the disk utility app. Jot these IDs down as we'll need them for our next step, creating our RAIDz array.
RAIDz is similar to RAID-5 in that instead of striping your data over multiple disks, exchanging redundancy for speed and available space (RAID-0), or mirroring your data writing by two copies of every piece (RAID-1), it instead writes parity blocks across the disks in addition to striping, this provides a balance of speed, redundancy and available space. If a single drive fails, the parity blocks on the working drives can be used to reconstruct the entire array as soon as a replacement drive is added.
Additionally, RAIDz improves over some of the common RAID-5 flaws. It's more resilient and capable of self healing, as it is capable of automatically checking for errors against a checksum. It's more forgiving in this way, and it's likely that you'll be able to detect when a drive is dying well before it fails. A RAIDz array can survive the loss of any one drive.
Note: While RAIDz is indeed resilient, if a second drive fails during the rebuild, you're fucked. Always keep backups of things you can't afford to lose. This tutorial, however, is not about proper data safety.
To create the pool, use the following command:
sudo zpool create "zpoolnamehere" raidz "device IDs of drives we're putting in the pool"
For example, let's creatively name our zpool "mypool". This poil will consist of four drives which have the device IDs: sdb, sdc, sdd, and sde. The resulting command will look like this:
sudo zpool create mypool raidz /dev/sdb /dev/sdc /dev/sdd /dev/sde
If as an example you bought five HDDs and decided you wanted more redundancy dedicating two drive to this purpose, we would modify the command to "raidz2" and the command would look something like the following:
sudo zpool create mypool raidz2 /dev/sdb /dev/sdc /dev/sdd /dev/sde /dev/sdf
An array configured like this is known as RAIDz2 and is able to survive two disk failures.
Once the zpool has been created, we can check its status with the command:
zpool status
Or more concisely with:
zpool list
The nice thing about ZFS as a file system is that a pool is ready to go immediately after creation. If we were to set up a traditional RAID-5 array using mbam, we'd have to sit through a potentially hours long process of reformatting and partitioning the drives. Instead we're ready to go right out the gates.
The zpool should be automatically mounted to the filesystem after creation, check on that with the following:
df -hT | grep zfs
Note: If your computer ever loses power suddenly, say in event of a power outage, you may have to re-import your pool. In most cases, ZFS will automatically import and mount your pool, but if it doesn’t and you can't see your array, simply open the terminal and type sudo zpool import -a.
By default a zpool is mounted at /"zpoolname". The pool should be under our ownership but let's make sure with the following command:
sudo chown -R "yourlinuxusername" /"zpoolname"
Note: Changing file and folder ownership with "chown" and file and folder permissions with "chmod" are essential commands for much of the admin work in Linux, but we won't be dealing with them extensively in this guide. If you'd like a deeper tutorial and explanation you can check out these two guides: chown and chmod.
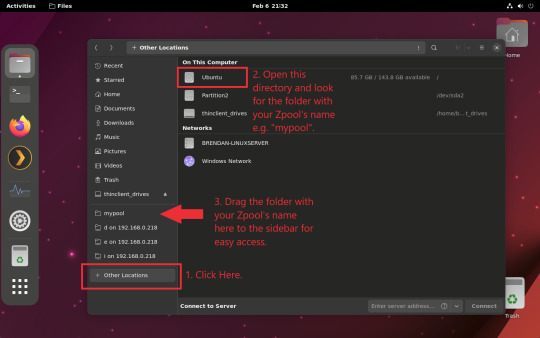
You can access the zpool file system through the GUI by opening the file manager (the Ubuntu default file manager is called Nautilus) and clicking on "Other Locations" on the sidebar, then entering the Ubuntu file system and looking for a folder with your pool's name. Bookmark the folder on the sidebar for easy access.
Your storage pool is now ready to go. Assuming that we already have some files on our Windows PC we want to copy to over, we're going to need to install and configure Samba to make the pool accessible in Windows.
Step Five: Setting Up Samba/Sharing
Samba is what's going to let us share the zpool with Windows and allow us to write to it from our Windows machine. First let's install Samba with the following commands:
sudo apt-get update
then
sudo apt-get install samba
Next create a password for Samba.
sudo smbpswd -a "yourlinuxusername"
It will then prompt you to create a password. Just reuse your Ubuntu user password for simplicity's sake.
Note: if you're using just a single external drive replace the zpool location in the following commands with wherever it is your external drive is mounted, for more information see this guide on mounting an external drive in Ubuntu.
After you've created a password we're going to create a shareable folder in our pool with this command
mkdir /"zpoolname"/"foldername"
Now we're going to open the smb.conf file and make that folder shareable. Enter the following command.
sudo nano /etc/samba/smb.conf
This will open the .conf file in nano, the terminal text editor program. Now at the end of smb.conf add the following entry:
["foldername"]
path = /"zpoolname"/"foldername"
available = yes
valid users = "yourlinuxusername"
read only = no
writable = yes
browseable = yes
guest ok = no
Ensure that there are no line breaks between the lines and that there's a space on both sides of the equals sign. Our next step is to allow Samba traffic through the firewall:
sudo ufw allow samba
Finally restart the Samba service:
sudo systemctl restart smbd
At this point we'll be able to access to the pool, browse its contents, and read and write to it from Windows. But there's one more thing left to do, Windows doesn't natively support the ZFS file systems and will read the used/available/total space in the pool incorrectly. Windows will read available space as total drive space, and all used space as null. This leads to Windows only displaying a dwindling amount of "available" space as the drives are filled. We can fix this! Functionally this doesn't actually matter, we can still write and read to and from the disk, it just makes it difficult to tell at a glance the proportion of used/available space, so this is an optional step but one I recommend (this step is also unnecessary if you're just using a single external drive). What we're going to do is write a little shell script in #bash. Open nano with the terminal with the command:
nano
Now insert the following code:
#!/bin/bash CUR_PATH=`pwd` ZFS_CHECK_OUTPUT=$(zfs get type $CUR_PATH 2>&1 > /dev/null) > /dev/null if [[ $ZFS_CHECK_OUTPUT == *not\ a\ ZFS* ]] then IS_ZFS=false else IS_ZFS=true fi if [[ $IS_ZFS = false ]] then df $CUR_PATH | tail -1 | awk '{print $2" "$4}' else USED=$((`zfs get -o value -Hp used $CUR_PATH` / 1024)) > /dev/null AVAIL=$((`zfs get -o value -Hp available $CUR_PATH` / 1024)) > /dev/null TOTAL=$(($USED+$AVAIL)) > /dev/null echo $TOTAL $AVAIL fi
Save the script as "dfree.sh" to /home/"yourlinuxusername" then change the ownership of the file to make it executable with this command:
sudo chmod 774 dfree.sh
Now open smb.conf with sudo again:
sudo nano /etc/samba/smb.conf
Now add this entry to the top of the configuration file to direct Samba to use the results of our script when Windows asks for a reading on the pool's used/available/total drive space:
[global]
dfree command = /home/"yourlinuxusername"/dfree.sh
Save the changes to smb.conf and then restart Samba again with the terminal:
sudo systemctl restart smbd
Now there’s one more thing we need to do to fully set up the Samba share, and that’s to modify a hidden group permission. In the terminal window type the following command:
usermod -a -G sambashare “yourlinuxusername”
Then restart samba again:
sudo systemctl restart smbd
If we don’t do this last step, everything will appear to work fine, and you will even be able to see and map the drive from Windows and even begin transferring files, but you'd soon run into a lot of frustration. As every ten minutes or so a file would fail to transfer and you would get a window announcing “0x8007003B Unexpected Network Error”. This window would require your manual input to continue the transfer with the file next in the queue. And at the end it would reattempt to transfer whichever files failed the first time around. 99% of the time they’ll go through that second try, but this is still all a major pain in the ass. Especially if you’ve got a lot of data to transfer or you want to step away from the computer for a while.
It turns out samba can act a little weirdly with the higher read/write speeds of RAIDz arrays and transfers from Windows, and will intermittently crash and restart itself if this group option isn’t changed. Inputting the above command will prevent you from ever seeing that window.
The last thing we're going to do before switching over to our Windows PC is grab the IP address of our Linux machine. Enter the following command:
hostname -I
This will spit out this computer's IP address on the local network (it will look something like 192.168.0.x), write it down. It might be a good idea once you're done here to go into your router settings and reserving that IP for your Linux system in the DHCP settings. Check the manual for your specific model router on how to access its settings, typically it can be accessed by opening a browser and typing http:\\192.168.0.1 in the address bar, but your router may be different.
Okay we’re done with our Linux computer for now. Get on over to your Windows PC, open File Explorer, right click on Network and click "Map network drive". Select Z: as the drive letter (you don't want to map the network drive to a letter you could conceivably be using for other purposes) and enter the IP of your Linux machine and location of the share like so: \\"LINUXCOMPUTERLOCALIPADDRESSGOESHERE"\"zpoolnamegoeshere"\. Windows will then ask you for your username and password, enter the ones you set earlier in Samba and you're good. If you've done everything right it should look something like this:

You can now start moving media over from Windows to the share folder. It's a good idea to have a hard line running to all machines. Moving files over Wi-Fi is going to be tortuously slow, the only thing that’s going to make the transfer time tolerable (hours instead of days) is a solid wired connection between both machines and your router.
Step Six: Setting Up Remote Desktop Access to Your Server
After the server is up and going, you’ll want to be able to access it remotely from Windows. Barring serious maintenance/updates, this is how you'll access it most of the time. On your Linux system open the terminal and enter:
sudo apt install xrdp
Then:
sudo systemctl enable xrdp
Once it's finished installing, open “Settings” on the sidebar and turn off "automatic login" in the User category. Then log out of your account. Attempting to remotely connect to your Linux computer while you’re logged in will result in a black screen!
Now get back on your Windows PC, open search and look for "RDP". A program called "Remote Desktop Connection" should pop up, open this program as an administrator by right-clicking and selecting “run as an administrator”. You’ll be greeted with a window. In the field marked “Computer” type in the IP address of your Linux computer. Press connect and you'll be greeted with a new window and prompt asking for your username and password. Enter your Ubuntu username and password here.
If everything went right, you’ll be logged into your Linux computer. If the performance is sluggish, adjust the display options. Lowering the resolution and colour depth do a lot to make the interface feel snappier.
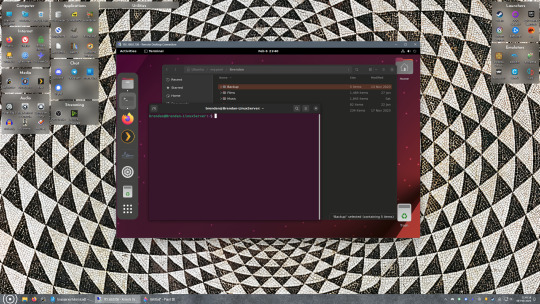
Remote access is how we're going to be using our Linux system from now, barring edge cases like needing to get into the BIOS or upgrading to a new version of Ubuntu. Everything else from performing maintenance like a monthly zpool scrub to checking zpool status and updating software can all be done remotely.

This is how my server lives its life now, happily humming and chirping away on the floor next to the couch in a corner of the living room.
Step Seven: Plex Media Server/Jellyfin
Okay we’ve got all the ground work finished and our server is almost up and running. We’ve got Ubuntu up and running, our storage array is primed, we’ve set up remote connections and sharing, and maybe we’ve moved over some of favourite movies and TV shows.
Now we need to decide on the media server software to use which will stream our media to us and organize our library. For most people I’d recommend Plex. It just works 99% of the time. That said, Jellyfin has a lot to recommend it by too, even if it is rougher around the edges. Some people run both simultaneously, it’s not that big of an extra strain. I do recommend doing a little bit of your own research into the features each platform offers, but as a quick run down, consider some of the following points:
Plex is closed source and is funded through PlexPass purchases while Jellyfin is open source and entirely user driven. This means a number of things: for one, Plex requires you to purchase a “PlexPass” (purchased as a one time lifetime fee $159.99 CDN/$120 USD or paid for on a monthly or yearly subscription basis) in order to access to certain features, like hardware transcoding (and we want hardware transcoding) or automated intro/credits detection and skipping, Jellyfin offers some of these features for free through plugins. Plex supports a lot more devices than Jellyfin and updates more frequently. That said, Jellyfin's Android and iOS apps are completely free, while the Plex Android and iOS apps must be activated for a one time cost of $6 CDN/$5 USD. But that $6 fee gets you a mobile app that is much more functional and features a unified UI across platforms, the Plex mobile apps are simply a more polished experience. The Jellyfin apps are a bit of a mess and the iOS and Android versions are very different from each other.
Jellyfin’s actual media player is more fully featured than Plex's, but on the other hand Jellyfin's UI, library customization and automatic media tagging really pale in comparison to Plex. Streaming your music library is free through both Jellyfin and Plex, but Plex offers the PlexAmp app for dedicated music streaming which boasts a number of fantastic features, unfortunately some of those fantastic features require a PlexPass. If your internet is down, Jellyfin can still do local streaming, while Plex can fail to play files unless you've got it set up a certain way. Jellyfin has a slew of neat niche features like support for Comic Book libraries with the .cbz/.cbt file types, but then Plex offers some free ad-supported TV and films, they even have a free channel that plays nothing but Classic Doctor Who.
Ultimately it's up to you, I settled on Plex because although some features are pay-walled, it just works. It's more reliable and easier to use, and a one-time fee is much easier to swallow than a subscription. I had a pretty easy time getting my boomer parents and tech illiterate brother introduced to and using Plex and I don't know if I would've had as easy a time doing that with Jellyfin. I do also need to mention that Jellyfin does take a little extra bit of tinkering to get going in Ubuntu, you’ll have to set up process permissions, so if you're more tolerant to tinkering, Jellyfin might be up your alley and I’ll trust that you can follow their installation and configuration guide. For everyone else, I recommend Plex.
So pick your poison: Plex or Jellyfin.
Note: The easiest way to download and install either of these packages in Ubuntu is through Snap Store.
After you've installed one (or both), opening either app will launch a browser window into the browser version of the app allowing you to set all the options server side.
The process of adding creating media libraries is essentially the same in both Plex and Jellyfin. You create a separate libraries for Television, Movies, and Music and add the folders which contain the respective types of media to their respective libraries. The only difficult or time consuming aspect is ensuring that your files and folders follow the appropriate naming conventions:
Plex naming guide for Movies
Plex naming guide for Television
Jellyfin follows the same naming rules but I find their media scanner to be a lot less accurate and forgiving than Plex. Once you've selected the folders to be scanned the service will scan your files, tagging everything and adding metadata. Although I find do find Plex more accurate, it can still erroneously tag some things and you might have to manually clean up some tags in a large library. (When I initially created my library it tagged the 1963-1989 Doctor Who as some Korean soap opera and I needed to manually select the correct match after which everything was tagged normally.) It can also be a bit testy with anime (especially OVAs) be sure to check TVDB to ensure that you have your files and folders structured and named correctly. If something is not showing up at all, double check the name.
Once that's done, organizing and customizing your library is easy. You can set up collections, grouping items together to fit a theme or collect together all the entries in a franchise. You can make playlists, and add custom artwork to entries. It's fun setting up collections with posters to match, there are even several websites dedicated to help you do this like PosterDB. As an example, below are two collections in my library, one collecting all the entries in a franchise, the other follows a theme.

My Star Trek collection, featuring all eleven television series, and thirteen films.
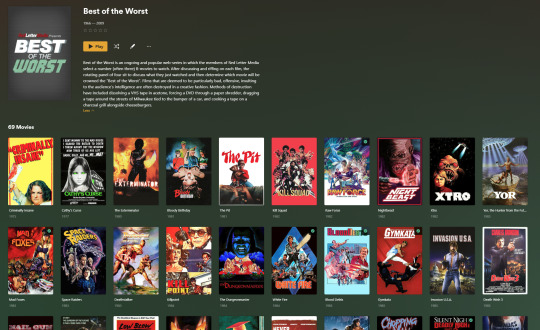
My Best of the Worst collection, featuring sixty-nine films previously showcased on RedLetterMedia’s Best of the Worst. They’re all absolutely terrible and I love them.
As for settings, ensure you've got Remote Access going, it should work automatically and be sure to set your upload speed after running a speed test. In the library settings set the database cache to 2000MB to ensure a snappier and more responsive browsing experience, and then check that playback quality is set to original/maximum. If you’re severely bandwidth limited on your upload and have remote users, you might want to limit the remote stream bitrate to something more reasonable, just as a note of comparison Netflix’s 1080p bitrate is approximately 5Mbps, although almost anyone watching through a chromium based browser is streaming at 720p and 3mbps. Other than that you should be good to go. For actually playing your files, there's a Plex app for just about every platform imaginable. I mostly watch television and films on my laptop using the Windows Plex app, but I also use the Android app which can broadcast to the chromecast connected to the TV in the office and the Android TV app for our smart TV. Both are fully functional and easy to navigate, and I can also attest to the OS X version being equally functional.
Part Eight: Finding Media
Now, this is not really a piracy tutorial, there are plenty of those out there. But if you’re unaware, BitTorrent is free and pretty easy to use, just pick a client (qBittorrent is the best) and go find some public trackers to peruse. Just know now that all the best trackers are private and invite only, and that they can be exceptionally difficult to get into. I’m already on a few, and even then, some of the best ones are wholly out of my reach.
If you decide to take the left hand path and turn to Usenet you’ll have to pay. First you’ll need to sign up with a provider like Newshosting or EasyNews for access to Usenet itself, and then to actually find anything you’re going to need to sign up with an indexer like NZBGeek or NZBFinder. There are dozens of indexers, and many people cross post between them, but for more obscure media it’s worth checking multiple. You’ll also need a binary downloader like SABnzbd. That caveat aside, Usenet is faster, bigger, older, less traceable than BitTorrent, and altogether slicker. I honestly prefer it, and I'm kicking myself for taking this long to start using it because I was scared off by the price. I’ve found so many things on Usenet that I had sought in vain elsewhere for years, like a 2010 Italian film about a massacre perpetrated by the SS that played the festival circuit but never received a home media release; some absolute hero uploaded a rip of a festival screener DVD to Usenet. Anyway, figure out the rest of this shit on your own and remember to use protection, get yourself behind a VPN, use a SOCKS5 proxy with your BitTorrent client, etc.
On the legal side of things, if you’re around my age, you (or your family) probably have a big pile of DVDs and Blu-Rays sitting around unwatched and half forgotten. Why not do a bit of amateur media preservation, rip them and upload them to your server for easier access? (Your tools for this are going to be Handbrake to do the ripping and AnyDVD to break any encryption.) I went to the trouble of ripping all my SCTV DVDs (five box sets worth) because none of it is on streaming nor could it be found on any pirate source I tried. I’m glad I did, forty years on it’s still one of the funniest shows to ever be on TV.
Part Nine/Epilogue: Sonarr/Radarr/Lidarr and Overseerr
There are a lot of ways to automate your server for better functionality or to add features you and other users might find useful. Sonarr, Radarr, and Lidarr are a part of a suite of “Servarr” services (there’s also Readarr for books and Whisparr for adult content) that allow you to automate the collection of new episodes of TV shows (Sonarr), new movie releases (Radarr) and music releases (Lidarr). They hook in to your BitTorrent client or Usenet binary newsgroup downloader and crawl your preferred Torrent trackers and Usenet indexers, alerting you to new releases and automatically grabbing them. You can also use these services to manually search for new media, and even replace/upgrade your existing media with better quality uploads. They’re really a little tricky to set up on a bare metal Ubuntu install (ideally you should be running them in Docker Containers), and I won’t be providing a step by step on installing and running them, I’m simply making you aware of their existence.
The other bit of kit I want to make you aware of is Overseerr which is a program that scans your Plex media library and will serve recommendations based on what you like. It also allows you and your users to request specific media. It can even be integrated with Sonarr/Radarr/Lidarr so that fulfilling those requests is fully automated.
And you're done. It really wasn't all that hard. Enjoy your media. Enjoy the control you have over that media. And be safe in the knowledge that no hedgefund CEO motherfucker who hates the movies but who is somehow in control of a major studio will be able to disappear anything in your library as a tax write-off.
1K notes
·
View notes
Text
An adversarial iMessage client for Android
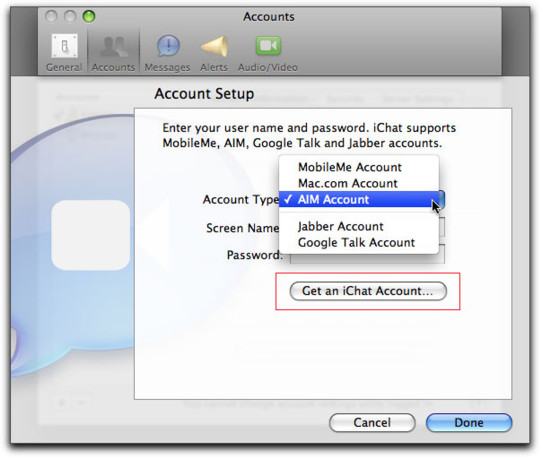
Adversarial interoperability is one of the most reliable ways to protect tech users from predatory corporations: that's when a technologist reverse-engineers an existing product to reconfigure or mod it (interoperability) in ways its users like, but which its manufacturer objects to (adversarial):
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
"Adversarial interop" is a mouthful, so at EFF, we coined the term "competitive compatibility," or comcom, which is a lot easier to say and to spell.
Scratch any tech success and you'll find a comcom story. After all, when a company turns its screws on its users, it's good business to offer an aftermarket mod that loosens them again. HP's $10,000/gallon inkjet ink is like a bat-signal for third-party ink companies. When Mercedes announces that it's going to sell you access to your car's accelerator pedal as a subscription service, that's like an engraved invitation to clever independent mechanics who'll charge you a single fee to permanently unlock that "feature":
https://www.techdirt.com/2023/12/05/carmakers-push-forward-with-plans-to-make-basic-features-subscription-services-despite-widespread-backlash/
Comcom saved giant tech companies like Apple. Microsoft tried to kill the Mac by rolling out a truly cursèd version of MS Office for MacOS. Mac users (5% of the market) who tried to send Word, Excel or Powerpoint files to Windows users (95% of the market) were stymied: their files wouldn't open, or they'd go corrupt. Tech managers like me started throwing the graphic designer's Mac and replacing it with a Windows box with a big graphics card and Windows versions of Adobe's tools.
Comcom saved Apple's bacon. Apple reverse-engineered MS's flagship software suite and made a comcom version, iWork, whose Pages, Numbers and Keynote could flawlessly read and write MS's Word, Excel and Powerpoint files:
https://www.eff.org/deeplinks/2019/06/adversarial-interoperability-reviving-elegant-weapon-more-civilized-age-slay
It's tempting to think of iWork as benefiting Apple users, and certainly the people who installed and used it benefited from it. But Windows users also benefited from iWork. The existence of iWork meant that Windows users could seamlessly collaborate on and share files with their Mac colleagues. IWork didn't just add a new feature to the Mac ("read and write files that originated with Windows users") – it also added a feature to Windows: "collaborate with Mac users."
Every pirate wants to be an admiral. Though comcom rescued Apple from a monopolist's sneaky attempt to drive it out of business, Apple – now a three trillion dollar company – has repeatedly attacked comcom when it was applied to Apple's products. When Apple did comcom, that was progress. When someone does comcom to Apple, that's piracy.
Apple has many tools at its disposal that Microsoft lacked in the early 2000s. Radical new interpretations of existing copyright, contract, patent and trademark law allows Apple – and other tech giants – to threaten rivals who engage in comcom with both criminal and civil penalties. That's right, you can go to prison for comcom these days. No wonder Jay Freeman calls this "felony contempt of business model":
https://pluralistic.net/2023/11/09/lead-me-not-into-temptation/#chamberlain
Take iMessage, Apple's end-to-end encrypted (E2EE) instant messaging tool. Apple customers can use iMessage to send each other private messages that can't be read or altered by third parties – not cops, not crooks, not even Apple. That's important, because when private messaging systems get hacked, bad things happen:
https://en.wikipedia.org/wiki/2014_celebrity_nude_photo_leak
But Apple has steadfastly refused to offer an iMessage app for non-Apple systems. If you're an Apple customer holding a sensitive discussion with an Android user, Apple refuses to offer you a tool to maintain your privacy. Those messages are sent "in the clear," over the 38-year-old SMS protocol, which is trivial to spy on and disrupt.
Apple sacrifices its users' security and integrity in the hopes that they will put pressure on their friends to move into Apple's walled garden. As CEO Tim Cook told a reporter: if you want to have secure communications with your mother, buy her an iPhone:
https://finance.yahoo.com/news/tim-cook-says-buy-mom-210347694.html
Last September, a 16-year old high school student calling himself JJTech published a technical teardown of iMessage, showing how any device could send and receive encrypted messages with iMessage users, even without an Apple ID:
https://jjtech.dev/reverse-engineering/imessage-explained/
JJTech even published code to do this, in an open source library called Pypush:
https://github.com/JJTech0130/pypush
In the weeks since, Beeper has been working to productize JJTech's code, and this week, they announced Beeper Mini, an Android-based iMessage client that is end-to-end encrypted:
https://beeper.notion.site/How-Beeper-Mini-Works-966cb11019f8444f90baa314d2f43a54
Beeper is known for a multiprotocol chat client built on Matrix, allowing you to manage several kinds of chat from a single app. These multiprotocol chats have been around forever. Indeed, iMessage started out as one – when it was called "iChat," it supported Google Talk and Jabber, another multiprotocol tool. Other tools like Pidgin have kept the flame alive for decades, and have millions of devoted users:
https://www.eff.org/deeplinks/2021/07/tower-babel-how-public-interest-internet-trying-save-messaging-and-banish-big
But iMessage support has remained elusive. Last month, Nothing launched Sunchoice, a disastrous attempt to bring iMessage to Android, which used Macs in a data-center to intercept and forward messages to Android users, breaking E2EE and introducing massive surveillance risks:
https://www.theverge.com/2023/11/21/23970740/sunbird-imessage-app-shut-down-privacy-nothing-chats-phone-2
Beeper Mini does not have these defects. The system encrypts and decrypts messages on the Android device itself, and directly communicates with Apple's servers. It gathers some telemetry for debugging, and this can be turned off in preferences. It sends a single SMS to Apple's servers during setup, which changes your device's bubble from green to blue, so that Apple users now correctly see your device as a secure endpoint for iMessage communications.
Beeper Mini is now available in Google Play:
https://play.google.com/store/apps/details?id=com.beeper.ima&hl=en_US
Now, this is a high-stakes business. Apple has a long history of threatening companies like Beeper over conduct like this. And Google has a long history deferring to those threats – as it did with OG App, a superior third-party Instagram app that it summarily yanked after Meta complained:
https://pluralistic.net/2023/02/05/battery-vampire/#drained
But while iMessage for Android is good for Android users, it's also very good for Apple customers, who can now get the privacy and security guarantees of iMessage for all their contacts, not just the ones who bought the same kind of phone as they did. The stakes for communications breaches have never been higher, and antitrust scrutiny on Big Tech companies has never been so intense.
Apple recently announced that it would add RCS support to iOS devices (RCS is a secure successor to SMS):
https://9to5mac.com/2023/11/16/apple-rcs-coming-to-iphone/
Early word from developers suggests that this support will have all kinds of boobytraps. That's par for the course with Apple, who love to announce splashy reversals of their worst policies – like their opposition to right to repair – while finding sneaky ways to go on abusing its customers:
https://pluralistic.net/2023/09/22/vin-locking/#thought-differently
The ball is in Apple's court, and, to a lesser extent, in Google's. As part of the mobile duopoly, Google has joined with Apple in facilitating the removal of comcom tools from its app store. But Google has also spent millions on an ad campaign shaming Apple for exposing its users to privacy risks when talking to Android users:
https://www.theverge.com/2023/9/21/23883609/google-rcs-message-apple-iphone-ipager-ad
While we all wait for the other shoe to drop, Android users can get set up on Beeper Mini, and technologists can kick the tires on its code libraries and privacy guarantees.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/12/07/blue-bubbles-for-all/#never-underestimate-the-determination-of-a-kid-who-is-time-rich-and-cash-poor
#pluralistic#multiprotocol#interoperability#adversarial interop#beeper#reverse engineering#blue bubbles#green bubbles#e2ee#end to end encrypted#messaging#jjtech#pypushbeeper mini#matrix#competitive compatibility#comcom
1K notes
·
View notes
Text
Updated Personal Infosec Post
Been awhile since I've had one of these posts part deus: but I figure with all that's going on in the world it's time to make another one and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
https://www.privacyguides.org/en/tools/
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides. Browsers: There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out. Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN: Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever public network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Mullvad VPN: Is a fast and inexpensive VPN with a serious focus on transparency and security. They have been in operation since 2009. Mullvad is based in Sweden and offers a 30-day money-back guarantee for payment methods that allow it.
Email Provider: Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Ol utlook.com you'll need to pay.
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Mailbox.org: Is an email service with a focus on being secure, ad-free, and privately powered by 100% eco-friendly energy. They have been in operation since 2014. Mailbox.org is based in Berlin, Germany. Accounts start with up to 2GB storage, which can be upgraded as needed.
Email Client:
Thunderbird: a free, open-source, cross-platform email, newsgroup, news feed, and chat (XMPP, IRC, Matrix) client developed by the Thunderbird community, and previously by the Mozilla Foundation.
FairMail (Android Only): minimal, open-source email app which uses open standards (IMAP, SMTP, OpenPGP), has several out of the box privacy features, and minimizes data and battery usage.
Cloud Storage:
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free
FreeOffice: Personal licenses are free, probably the closest to a fully office suite replacement.
Chat Clients: Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those. Note2: Signal has had some reports of security flaws, the service it was built on was originally built for the US Government, and it is based within the CONUS thus is susceptible to US subpoenas. Take that as you will.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
SimpleX: Truly anonymous account creation, fully encrypted end to end, available for Android and iOS.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode. For more secure distributions for the more advanced users the options are: Whonix, Tails (Live USB only), and Qubes OS.
On a personal note I use Arch Linux, but I WOULD NOT recommend this be anyone's first distro as it requires at least a base level understanding of Linux and liberal use of the Arch Linux Wiki. If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help. I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#infosec#personal information#personal infosec#info sec#firefox#mullvad#vpn#vpn service#linux#linux tails#pop_os#ubuntu#linux mint#long post#whonix#qubes os#arch linux
84 notes
·
View notes
Text
The main reason to use Firefox and Linux and other free and open source software is that otherwise the big tech monopolies will fuck you as the customer over in search of profits. They will seek to control how you use their products and sell your data. When a company dominates the market, things can only get worse for ordinary people.
Like take Google Chrome for example, which together with its chromium reskins dominate the web browser market. Google makes a lot of money from ads, and consequently the company hates adblockers. They already are planning to move to manifest V3, which will nerf adblockers significantly. The manifest V3 compatible chrome version of Ublock Orgin is a "Lite" version for a reason. Ublock's Github page has an entire page explaining why the addon works best in Firefox.
And Google as we speak are trying to block adblockers from working on Youtube, If you want to continue blocking Youtube ads, and since Youtube ads make the site unuseable you ought to want that, it makes the most sense to not use a browser controlled by Google.
And there is no reason to think things won't get worse. There is for example nothing stopping Google from kicking adblockers off their add-on stores completely. They do regard it as basically piracy if the youtube pop-ups tell us anything, so updating the Chrome extensions terms of service to ban adblocking is a natural step. And so many people seem to think Chrome is the only browser that exists, so they are not going to switch to alternatives, or if they do, they will switch to another chrominum-based browser.
And again, they are fucking chromium itself for adblockers with Manifest V3, so only Firefox remains as a viable alternative. It's the only alternative to letting Google control the internet.
And Microsoft is the same thing. I posted before about their plans to move Windows increasingly into the cloud. This already exists for corporate customers, as Windows 365. And a version for ordinary users is probably not far off. It might not be the only version of Windows for awhile, the lack of solid internet access for a good part of the Earth's population will prevent it. But you'll probably see cheap very low-spec chromebookesque laptops running Windows for sale soon, that gets around Windows 11's obscene system requirements by their Windows being a cloud-based version.
And more and more of Windows will require Internet access or validation for DRM reasons if nothing else. Subscription fees instead of a one-time license are also likely. It will just be Windows moving in the direction Microsoft Office has already gone.
There is nothing preventing this, because again on the desktop/laptop market Windows is effectively a monopoly, or a duopoly with Apple. So there is no competition preventing Microsoft from exercising control over Windows users in the vein of Apple.
For example, Microsoft making Windows a walled garden by only permitting programs to be installed from the Microsoft Store probably isn't far off. This already exists for Win10 and 11, it's called S-mode. There seem to be more and more laptops being sold with Windows S-mode as the default.
Now it's not the only option, and you can turn it off with some tinkering, but there is really nothing stopping Microsoft from making it the only way of using Windows. And customers will probably accept it, because again the main competition is Apple where the walled garden has been the default for decades.
Customers have already accepted all sorts of bad things from Microsoft, because again Windows is a near-monopoly, and Apple and Google are even worse. That’s why there has been no major negative reaction to how Windows has increasingly spies on its users.
Another thing is how the system requirements for Windows seem to grow almost exponentially with each edition, making still perfectly useable computers unable to run the new edition. And Windows 11 is the worst yet. Like it's hard to get the numbers of how many computers running Win10 can't upgrade to Win11, but it's probably the majority of them, at least 55% or maybe even 75%. This has the effect of Windows users abandoning still perfectly useable hardware and buying new computers, creating more e-waste.
For Windows users, the alternative Windows gives them is to buy a new computer or get another operating system, and inertia pushes them towards buying another computer to keep using Windows. This is good for Windows and the hardware manufacturers selling computers with Windows 11 pre-installed, they get to profit off people buying Windows 11 keys and new computers, while the end-users have to pay, as does the environment. It’s planned obsolescence.
And it doesn’t have to be like that. Linux distros prove that you can have a modern operating system that has far lower hardware requirements. Even the most resource taxing Linux distros, like for example Ubuntu running the Gnome desktop, have far more modest system requirements than modern Windows. And you can always install lightweight Linux Distros that often have very low system requirements. One I have used is Antix. The ballooning Windows system requirements comes across as pure bloat on Microsoft’s part.
Now neither Linux or Firefox are perfect. Free and open source software don’t have a lot of the polish that comes with the proprietary products of major corporations. And being in competition with technology monopolies does have its drawbacks. The lacking website compatibility with Firefox and game compatibility with Linux are two obvious examples.
Yet Firefox and Linux have the capacity to grow, to become better. Being open source helps. Even if Firefox falls, developers can create a fork of it. If a Linux distro is not to your taste, there is usually another one. Whereas Windows and Chrome will only get worse as they will continue to abuse their monopolistic powers over the tech market.
847 notes
·
View notes
Text
Thrissur’s Tech Hub: Your Guide to the Best Laptop Shops and Stores in Town
When it comes to buying a new laptop, one-size-fits-all doesn’t apply. Every buyer has different needs—some want power and performance, while others look for portability and price. Whether you’re a student preparing for college, a work-from-home professional, a gamer, or someone replacing an outdated device, choosing the right laptop shop in Thrissur can make a world of difference.
Thrissur, known for its cultural heritage, is now gaining recognition as a growing tech destination. The city is home to several reputed laptop shops and stores that offer the latest products, expert advice, and personalized service you simply won’t get from online marketplaces.
Why You Should Buy Your Laptop Locally in Thrissur
The local tech market in Thrissur has matured over the years. Today, it boasts a wide selection of laptop retailers, all competing to offer customers the best value. But it’s not just about price—buying from a trusted laptop store in Thrissur gives you access to:
Hands-on experience with the laptop before you buy
Immediate support for installation, setup, or troubleshooting
Face-to-face guidance from experienced professionals
Real-time product comparisons across brands and models
Exclusive in-store offers, discounts, and freebies
Unlike online portals, which often leave you to figure things out on your own, a local store offers an actual human touch—from answering technical questions to offering repair and upgrade services post-sale.
Features of a Trusted Laptop Shop in Thrissur
Looking for the right place to buy your next device? Here’s what the best laptop shop in Thrissur typically offers:
🖥️ Wide Brand Variety
Top stores stock all major laptop brands including Dell, HP, Lenovo, ASUS, Acer, MSI, and Apple. Whether you need a basic Chromebook or a premium MacBook Pro, you’ll find it all under one roof.
👨💻 Personalized Recommendations
Salespersons aren’t just there to sell—they’re trained to understand your specific needs. You’ll get advice tailored to your budget, work profile, and usage habits.
💰 Best Price and EMI Plans
Local stores often provide seasonal discounts, bundled software, and easy EMI options to help you spread out payments. This makes a high-end laptop more affordable without compromising quality.
🔧 On-the-Spot Setup and Support
Get your OS installed, software loaded, antivirus activated, and even data transferred from your old laptop—before you walk out of the store. That’s the kind of service a good laptop store in Thrissur will always offer.
Who Shops for Laptops in Thrissur?
The demand for laptops in Thrissur is growing rapidly, driven by:
Students attending online classes and doing research work
Freelancers and digital nomads who need reliable machines
Startups looking to build teams affordably
Gamers seeking high-speed performance laptops
Business owners investing in office equipment
Home users looking for everyday devices for browsing, streaming, or communication
No matter who you are, a trusted laptop shop in Thrissur can help you choose a device that’s perfect for your lifestyle.
Services You Can Expect
Apart from sales, the top laptop store in Thrissur will offer a range of value-added services such as:
Hardware upgrades (RAM, SSD, HDD)
Operating system installations and recovery
Laptop servicing and diagnostics
Genuine software sales and license activation
Accessories like bags, cooling pads, keyboards, mice, and screen guards
These services make it more convenient to maintain and upgrade your laptop over time—without depending on third-party service providers.
Local vs Online: What’s the Better Choice?
While online shopping offers convenience, it often lacks personal interaction, post-sale service, and real-time product trials. Buying from a laptop shop in Thrissur gives you the best of both worlds—great prices and hands-on support.
Final Thoughts
When it’s time to buy a new laptop, don’t rush into an online deal that looks good on the surface but leaves you stranded when problems arise. Instead, invest your time and money with a reliable laptop store in Thrissur that offers more than just products—they offer partnership, support, and peace of mind.
Thrissur may be known for its tradition and heritage, but it’s also home to some of Kerala’s most dependable tech retailers. So whether you’re upgrading your work setup, gifting your child their first laptop, or stepping into the world of digital content creation, visit a trusted laptop shop in Thrissur today—and take home more than just a laptop. Take home confidence.
#thrissur#kerala#college#digital marketing#freelance digital marketing#laptop#professional#students#digital art#laptoplove
2 notes
·
View notes
Text
🛑 Subscription Fatigue: You Don’t Own Sh-t Anymore

The Great Ownership Heist—And You Paid for It
Once upon a time, when you bought something, it was yours. Forever. No extra fees. No fine print. Just a simple transaction: money exchanged for permanent ownership.
Now? Welcome to Subscription Hell—where you don’t own sh-t anymore, but you sure as hell keep paying for it.
In the last 15 years, corporations have collectively f-cked us over by shifting from selling products to selling access. The goal? Make sure you never actually own anything again.
And somehow, we just let it happen.
📉 The Subscription Takeover: How You Got Trapped
Remember when you bought CDs and they were yours forever? When you bought a game and played it whenever you wanted, without an online connection or a monthly charge? When software didn’t demand a recurring payment just so you could type a damn document?
Those days are dead.
Instead of a one-time purchase, everything is now a rental. ✅ Music? Spotify. Apple Music. Tidal. ✅ Movies? Netflix. Disney+. HBO Max. (Oh wait—it’s just “Max” now because marketing execs are idiots.) ✅ Video Games? Xbox Game Pass. PlayStation Plus. Nintendo Switch Online. ✅ Software? Adobe Creative Cloud. Microsoft 365. Even f-cking calculator apps now have subscriptions.
Everything is locked behind a paywall. And the best part? You never actually own any of it.
💸 You Will Own Nothing—And Pay Monthly for It
We used to buy things. Now we “subscribe.” And this shift wasn’t an accident. It was a slow, calculated effort to make you permanently dependent on corporations.
Think about it:
A one-time purchase = company makes money once.
A subscription model = company makes money forever.
It’s not just greed—it’s financial entrapment.
📌 Want to listen to your favorite music? Too bad—Spotify just removed your favorite album. Pay up or be at the mercy of whatever they decide to keep. 📌 Want to keep using Photoshop? Adobe wants $20 a month for eternity. Cancel? Poof—no access. 📌 Bought a car? Congratulations! Your heated seats now require a f-cking subscription.
Wait. Cars?! Yes.
🚗 BMW’s $18-a-Month Heated Seat Scam: The Final Boss of Greed
If you want a perfect example of how far this bullsh-t has gone, look no further than BMW.
BMW now charges a subscription for heated seats in some of their cars. Yes, you read that right.
The seats are already installed. The heating element is physically there in the car you bought. But unless you pay BMW $18 a month, they won’t let you use it.
Let that sink in.
You own the car. You own the seats. But the company still controls what you can access.
It’s like buying a house and being told you have to pay a subscription to use your own kitchen.
This is the future.

🎮 Gaming: Where You Pay to Rent the Past
Gaming used to be simple. You bought a game. You played it. It was yours. Now? Everything is a f-cking subscription.
🎮 Xbox Game Pass – Pay monthly or lose access. 🎮 PlayStation Plus – Rent your library or watch it vanish. 🎮 Nintendo Switch Online – Oh, you thought you could play old NES games? Pay up.
And it gets worse.
Now, developers release unfinished games and patch them later. Want a full experience? Buy the DLC. Oh, you wanted to actually own the game? Too bad, it’s “live service” now.
In 2004, you could walk into a store and buy Halo 2, a complete game, for $50. In 2024, you spend $70 on a game that isn’t even finished and still get hit with battle passes, microtransactions, and pay-to-win mechanics.
And yet—we just accept it.
📚 Digital Books: You Don’t Even Own the Words Anymore
🚨 Amazon can delete books from your Kindle remotely. This isn’t a conspiracy—it already happened.
In 2009, Amazon literally deleted George Orwell’s 1984 and Animal Farm from people’s Kindles without warning. The irony? A dystopian book about government control vanished from devices overnight.
If you “buy” a Kindle book, you’re not actually buying it. You’re purchasing a license to read it.
This means:
If Amazon wants to remove it, they can.
If your account is banned, you lose everything.
If they change the Terms of Service, tough luck.
You don’t own sh-t. You’re just renting access to words on a screen.
💀 Welcome to the Paywall Apocalypse
Subscription fatigue isn’t just annoying. It’s economic warfare.
Everything is now a pay-per-month nightmare, and the endgame is control.
🔴 Digital art? Subscriptions. 🔴 Smart homes? Subscriptions. 🔴 Car features? Subscriptions. 🔴 F-cking TOOTHBRUSHES?! Yes, there’s now a subscription service for toothbrush heads.
The goal is simple: Make sure you never fully own anything again.
🛠️ Can We Fight Back?
Honestly? It’s hard. These companies engineered dependence so well that it’s nearly impossible to escape. But here’s what you can do:
✅ BUY physical media. DVDs, CDs, game cartridges—real sh-t that can’t be deleted remotely. ✅ AVOID auto-renewing subscriptions. Make them work for your money. ✅ Look for one-time purchase alternatives. Stop paying Adobe $600 a year for Photoshop when one-time payment alternatives exist. ✅ Support anti-DRM (Digital Rights Management) products. If a company lets you actually own what you buy, reward them.
We probably can’t stop the subscription model entirely, but we can slow it down by refusing to throw money at companies who abuse it.
🚨 FINAL THOUGHT: THEY DON’T WANT YOU TO OWN ANYTHING—BECAUSE OWNERSHIP IS POWER
Owning something means independence. Owning something means they can’t take it away. Owning something means freedom.
That’s why corporations are systematically stripping away ownership in favor of perpetual payments. They don’t want you to have assets—they want you to have bills.
Welcome to the new world order: 💰 Own nothing. Pay forever.
And the worst part?
We let them do it.
💀 REBLOG if you’re tired of paying for sh-t you should already own. 💬 COMMENT the worst subscription scam you’ve seen. 🥩 LIKE if you miss the days of actually owning things. 🚀 FOLLOW for more savage takes, economic red pills, and the dark truth about the world.
#SubscriptionFatigue#YouDontOwnShit#CorporationsAreEvil#DigitalScam#CapitalismAtItsWorst#GreedOverload#EconomicSlavery#PayForever#BrokenSystems#WTFCapitalism#HardPillsToSwallow#FactsOverFeelings#BigTechBullshit#BrutalHonesty#CulturalCritique#DarkAcademia#SavageCommentary
2 notes
·
View notes
Text
Computer repair services that are highly rated in Miami.
We are your one-stop electronic store; whether your smartphone screen is worn out or your gaming PC is in need of a performance boost, or your laptop is not responding, our team of certified technicians is here to diagnose, repair, and get you back in the game, and for passionate gamers seeking the ultimate edge, we offer customized Gaming PCs. Don’t settle for a pre-built machine that limits your potential. Tell us your gaming needs and budget, and our technical experts will design and assemble a high-performance PC that perfectly fits your gaming style.
PC & Notebook Repair & Upgrades:
Whether your PC has stopped working completely, has become slow and frustrating to use, or is in need of upgrading, then we have the in-house expertise to help you. Please note, we do not work with Mac or other Apple products.
Networking Solutions:
If you’ve got several PCs at home or in the office and want to maximize their potential by sharing documents, files, and media, you probably need a network.
Photo & Document Recovery & Hard Drive Cloning:
We can recover lost documents, files, photos and any important data from a broken computer.
Networking Solutions:
It is not just inexperienced users of a PC or laptop that can fall prey to the effects of a computer infection. Even the most experienced user can inadvertently allow a virus or other malicious software to enter and spread.
Our Services:
Virus/Spyware Removal
Hardware & Windows Repair
Booting Issue Repair
Slow Computer Tune-Up
Hardware Installation
Home Networking
Laptop Screen Repairs
Keyboard/Touchpad Repairs
DC Power Jack Repair
Booting Issues
Power Button Repair
Wi-Fi Connection Issues
Network Management
Network Cable Installation
Website Development
Data Backup Management
All Computer Services
All Laptop Services
Rapid Response Time:
One of our main advantages over most companies is our quick response time. Most on-site computer repair companies make you wait days for service, and if you drop it off at a shop, they make you wait days to complete the repair. Why does it take them so long? Because they do not prioritize every single customer! We consistently offer same day or next day service, with most repairs being finished on-site that day. For the repairs that need to be taken back to the shop, we prioritize those too. We boast an average turnaround time of only 2 days, and we drop it off to you when it's done, or you can pick it up.
Full Service On-Site Support:
Don't touch a thing. We come directly to your home or business, and perform the repair right there. We handle it all, from start to finish, without you having to lift a finger. We provide on-site computer repair in most cities and towns in Miami Dade including: Miami Gardens, Aventura, Golden Beach, Sunny Isles Beach, North Miami Beach, North Miami, Bal Harbour, Bay Harbor Islands, Indian Creek, Surfside, Biscayne Park, Miami Shores, El Portal, North Bay Village, Opa-locka, Miami Lakes, Hialeah, Hialeah Gardens, Medley, Doral, Miami Springs, Virginia Gardens, Sweetwater, Miami, Miami Beach, Key Biscayne, West Miami, Coral Gables, South Miami, Pinecrest, Palmetto Bay, Cutler Bay, Homestead, Florida City.
Website: Computer Repair Mia
2 notes
·
View notes
Text
Keyboard shortcuts
The keyboard shortcuts in actual use are clearly historically contingent and path dependent - there are no standards, which means there are no ways to avoid conflict - even if you want to!
That is - unless you know every shortcut for the operating system you are compiling for and the operating system doesn't add more shortcuts and no third party programs are installed that were unaware of your presence.
EDIT:
Post got Long, it's under a readmore now so it won't clutter your dash
But please do read it if you have software opinions.
---
Hardware thinks (shortcut) means A
Operating system thinks (shortcut) means B
Background service thinks (shortcut) means C
Browser thinks (shortcut) means D
Open browser tab thinks (shortcut) means E
---
Hot garbage!
In the interest of avoiding conflicting commands it would be great if people could agree on some standards.
I feel like, with [super] and [ctrl] and [alt] and [shift] and [Esc] and [space] and [Fn] - it ought to be possible to do some deconflicting here!
Since the operating system is in control of the keyboard, it can impose those standards unilaterally - it would be chaos during the transition but the future would be much better.
Except no! Inherently impossible!
Because the user will - once again - install third party software and even if we get excellent deconfliction between layers, if you install two different background services that both did their due diligence and ensured that the operating system didn't use ctrl+shift+q+w+g - it is functionally impossible for them to know about each other
Still, I want to sketch something.
NB: I've never used a Mac, maybe Steve Apple solved all of this decades ago for his platform, it seems like the kind of thing he would do. I'm gonna write like he didn't though.
The domain
I'm seeing two ways users interact with software - background/foreground - and two types of software they're interacting with - hosts and clients.
The terms are necessarily underspecified but think along the lines of
Background/Foreground
Is this shortcut supposed to consistently do the same thing every time I use it (for the OS or some background service) or might it do different things depending on which app I currently have focused?
This is muddled by the fact that the background modes have active modes e.g. if you have Nvidia Shadowplay running in the background, listening for input that tells it to turn on or off, you probably also have an Nvidia Shadowplay app that you can actively focus on.
In that case, the software is simply counted twice - it has a persistent background component and a separate component that might or might not be focused.
Host/Client
The difference between Host and Client is essentially whether the developer is responsible for intermediating with third party software. This is obviously recursive[1], I am going to pretend it isn't though.
Hardware
To the extent that your hardware sends messages to your operating system, those can be ignored for the purpose of this diagram. To the extent that your operating system sends messages to your hardware, the hardware can be treated like a persistent background service.
Scenario
You are writing code in an IDE.
Four pieces of software have five different uses for the key "e"
Your OS wants E to mean "Open default Email client."
Your Emoji Picker background service wants E to open the "Pick Emoji" dialog.
Your IDE is currently in focus and wants E to open the Project Explorer pane.
Your IDE has a plugin that format your current tab according to your Editorconfig file.
And finally: You just plain need the letter "e" in your source code.
Today: Any fucking thing might happen depending on how those different apps and plugins have their hotkeys set up.
But let us consider:
[super]+[e] opens the email client.
[super]+[shift]+[e] opens the emoji picker
[ctrl]+[e] opens the Project Explorer pane
[ctrl]+[shift]+[e] formats according the editorconfig
[e] inserts the letter "e" into the source code.
Enforcement between OS, Third party service and active client.
How do you prevent the emoji picker from squatting on [ctrl]+[shift]+[e] and fucking it all up? Especially if it is written by a third party who didn't get the memo?
Easy.
If you press [ctrl]+[shift]+[e] the emoji plugin never sees it. When the emoji picker event loop asks for new events, those WM_KEYDOWN events aren't on the list.
"How?"
From the perspective of the OS, there are three groups of software that may need to know about key events
First party background software (The OS and OS services)
Third party background software (like the Emoji picker)
Active focused client software (First or third party)
When you input a key sequence:
The OS reads through the keys:
If [super] is present, check for [shift]
If [shift] is present in the key sequence, the key events go into the Third Party pool. On receiving them, the Emoji Picker opens the Emoji dialog.
Else only [super] is present in the key sequence: The key events go into the OS private pool, where they are made available only to first party background services. The "default email" hook fires.
Else [super] is not present in the sequence: The key events go into the "focused client" pool, which is made available only to the single, currently active, focused client. They are read by the IDE.
Enforcement within active client
Write it correctly lmao
But it is just recursively the same problem! Please do the same thing!
When the IDE reads the key events out of the OS, it checks for the presence of [ctrl]
If [ctrl] is present, check for [shift].
If [shift] is present in the sequence, the key events go into the plugin pool. Upon receiving them, the formatter activates
Else only [ctrl] is present. The key event goes into the IDE's private pool. The IDE opens the Project Explorer pane.
Else [ctrl] is not present in this key sequence. The key events go into the active editor tab which inserts a single 'e' in the current file.
---
Expanding the shortcut configuration space
"What about [alt]?" Is that button just irrelevant? [Esc]? [Fn]?
Nah, nah. You can do a bunch with all of them. They're fundamentally the same as the shift key here. Maybe the OS reserves for itself the space of all shortcuts like [super]+[letter/number] and [super]+[alt]+[letter/number], and every other shortcut that starts with [super] is available for third party background services. Maybe clients that support plugins (browsers that support sending key events into websites) reserve [ctrl] only and everything else is fair game. However it shakes out.
Really, this is too strict, too. The purpose of the exercise is not to hobble third party background services or third party plugins, it is more to reserve a space to ensure various things don't conflict. Insofar as it can be done without leading to conflicts, you can be much more lax than this.
The two issues that brought this on are both VSCode related, because VSCode has two shortcuts.
Well, it has a lot of shortcuts. But it has two specific shortcuts that I want to talk about: [ctrl]+[b] and [ctrl]+[shift]+[e].
In the Linux keymap (VSCode has three separate keymaps for windows/linux/mac) [ctrl]+[b] opens the side pane, and [ctrl]+[shift]+[e] opens the project explorer window.
Except not for me they don't.
I am writing this text in markdown, and I have a markdown plugin installed. Somewhat reasonably, the markdown plugin feels [ctrl]+[b] should bold the selected text (that is, insert ** on both sides of the text.) And VSCode gives priority to the plugin - when my active editing pane is on a markdown document, I cannot open/close the side pane.
And the fucking IBUS emoji picker is squatting on [ctrl]+[shift]+[e]. Across the whole OS! "Yeah no matter what you're doing, you're probably gonna need emoji so we're taking first claim on incredibly ergonomic real estate for an incredibly niche use case" who the fuck accepted that pull request into my distro?
And, like, is Microsoft going to change the default key bindings for VSCode on Linux because of that insane decision? No of course not.
Are they going to change their idiocy - just to stop inconveniencing Microsoft users? Yeah that is not how I am modeling the situation unfolding I must admit.
That sucks! Shit sucks! And the only good solution is for the OS to say "We are laying absolute claim to (this namespace) for OS and background services and we are giving third parties absolute claim to (that namespace).
Which they're not gonna do but I can waste a day writing about the perfect world I want to live in.
---
[1] "My Mac hosts a VM running Linux hosting a VM running Windows running an open Browser with a tab with an open webapp with a user plugin."
20 notes
·
View notes
Text
The Limbo of Advanced Users and Amateur Developers in Microsoft 365

Microsoft 365, the successor to the iconic Office suite, has transformed how millions of people work, collaborate, and manage their daily tasks. However, this transformation has not been equal for everyone. While businesses and corporations have access to a myriad of powerful tools through robust subscriptions, advanced users — those enthusiasts who have historically driven innovation through customization and automation — are left in limbo. This article argues that Microsoft, by prioritizing service-based and enterprise-focused models, has abandoned beginner developers and advanced users, once the cornerstone of its tools’ success.
The Golden Age of Customization
In the past, Microsoft Office allowed rich customization and automation through Visual Basic for Applications (VBA) and integration with technologies like COM (Component Object Model). These features enabled individuals, even without corporate tools, to create scripts to automate tasks, customize interfaces, and connect applications in innovative ways. With VBA, a user could generate automated reports in Excel or build macros to streamline repetitive processes in Word. This turned Office into not only a productivity tool but also a learning platform for budding developers.
However, with the migration to Microsoft 365, this flexibility has been significantly reduced. VBA remains available in a limited capacity, but its usage is increasingly marginalized, and many new features of Microsoft 365 are inaccessible through it. Furthermore, VBA has no support in the web environment, which is becoming increasingly central to modern workflows.
A Service, Not a Tool
Microsoft 365 represents a fundamental shift: from locally installed software to a cloud-based service. While this approach offers benefits like real-time collaboration and automatic updates, it has severely limited advanced users. Local automation has taken a back seat, and the focus has shifted to tools like Power Automate — a powerful platform, but largely inaccessible to personal users.
Power Automate is clearly designed for the corporate environment. Many of its most compelling features are locked behind business-specific subscriptions, leaving individual users without practical alternatives. For users seeking advanced and customized solutions, Microsoft 365 is no longer a viable option.
Apple’s Counterpoint
While Microsoft appears to be moving away from advanced users, Apple is taking the opposite direction. Tools like Shortcuts, AppleScript, and Automator make Apple’s applications highly customizable, even for personal users. Tasks can be automated in Pages, Numbers, Reminders, and Calendar without relying on corporate services. This approach not only empowers users but also fosters curiosity and learning among new developers.
This contrast highlights the central issue: Apple values tech enthusiasts and amateur developers, while Microsoft seems to have relegated them to a secondary role, if not excluded them entirely.
The Impact on the Future of Technology
Microsoft’s abandonment of advanced users has broader implications beyond daily workflows. For many developers, tools like VBA served as an entry point to programming. Removing these opportunities makes practical learning more difficult and stifles grassroots innovation. At a time when the market needs more developers and creative thinkers, this decision is particularly troubling.
Moreover, this exclusion risks alienating a community that has historically been crucial to Office’s success. Advanced users are often technology “evangelists” within their circles, promoting tools and influencing purchasing decisions. Ignoring them poses a significant strategic risk for Microsoft.
Conclusion: What Should Microsoft Do?
If Microsoft wants to regain the trust and engagement of advanced users, several actions are essential:
1. Revitalize VBA and Similar Technologies: Ensure that local automations are not only supported but encouraged, including integration with new Microsoft 365 features.
2. Expand Access to Power Automate: Offer more platform functionalities to individual users without requiring corporate subscriptions.
3. Acknowledge the Value of Advanced Users: Develop tools and initiatives aimed at educating and empowering amateur developers and tech enthusiasts.
In a world increasingly dominated by cloud-based services, striking a balance between innovation and accessibility is crucial. Microsoft has an opportunity to correct its course and reaffirm its commitment to the community that helped it succeed. If it fails to do so, it risks losing a vital segment of its user base to more inclusive alternatives.
6 notes
·
View notes
Text
Comprehensive Laptop Services and Affordable Refurbished Laptops in Bangalore

In the fast-paced digital world we live in, a functioning laptop is no longer a luxury but a necessity. Bangalore, often referred to as the Silicon Valley of India, is home to millions of tech-savvy individuals who rely heavily on their laptops for work, study, and leisure. Whether your laptop is malfunctioning or you are looking for a budget-friendly device, Bangalore offers several convenient services and options. From Laptop repair home service in bangalore to the purchase of refurbished and used laptops, here’s everything you need to know.
Laptop Repair Home Service in Bangalore: Convenience at Your Doorstep
Gone are the days when you had to lug your heavy laptop to a service center and wait for days to get it fixed. With the advent of Laptop service at home in bangalore, resolving technical issues has become hassle-free. These services provide a team of skilled technicians who come to your doorstep, saving you time and effort.
Common issues addressed by laptop repair home services include:
Screen replacement
Keyboard or touchpad repair
Battery issues
Software installation and troubleshooting
Virus removal and system optimization
The technicians are equipped with tools and expertise to diagnose and fix most problems on-site. These services are particularly popular among busy professionals and students who cannot afford prolonged downtime.
Why Choose Laptop Service at Home in Bangalore?
Time-Saving: No more waiting in long queues at service centers.
Cost-Effective: Many providers offer competitive rates without the overhead costs associated with physical service centers.
Personalized Attention: On-site service ensures you can monitor the repair process and ask questions.
Emergency Repairs: Some services even offer same-day or express repair options.
With numerous providers available across the city, you can easily find a service that matches your requirements and budget.
Refurbished Laptops for Sale in Bangalore: Quality at a Fraction of the Cost
Refurbished laptops for sale in bangalore have become a popular choice for those who want high-performance devices without breaking the bank. These are pre-owned laptops that have been professionally repaired, upgraded, and tested to ensure they function like new.
Benefits of buying refurbished laptops in Bangalore include:
Affordability: Refurbished laptops are significantly cheaper than new ones.
Warranty Options: Many sellers offer warranties for added peace of mind.
Environmentally Friendly: Purchasing refurbished devices reduces electronic waste.
Top brands such as Dell, HP, Lenovo, and Apple are readily available in the refurbished market in Bangalore. You can find these devices at dedicated stores or online platforms offering delivery within the city.
Used Laptops in Bangalore: An Economical Alternative
If you are looking for an even more budget-friendly option, Used laptops in bangalore are worth considering. While these devices may not come with warranties, they are often in good working condition and can be a great choice for basic tasks such as browsing, streaming, and office work.
Before purchasing a used laptop, ensure you:
Verify the device's condition thoroughly.
Check for genuine operating systems and software licenses.
Compare prices to avoid overpaying.
Platforms like OLX, Quikr, and local marketplaces in Bangalore are excellent starting points to find reliable deals on used laptops.
Conclusion
Bangalore offers an array of services and options for laptop users, catering to diverse needs and budgets. Whether you require professional laptop repair at home or are in the market for a refurbished or used device, the city has it all. With convenient home services, affordable refurbished laptops, and cost-effective used laptops, staying connected in the tech capital of India has never been easier. Choose wisely and enjoy a seamless digital experience!
1 note
·
View note
Text
Catching Up on Tech News
1. Foursquare's Strategic Shift: Foursquare recently underwent significant restructuring, laying off 105 employees, which accounts for 25% of its workforce. The move aims to enhance operational efficiency and financial stability. This isn't the first time Foursquare has faced layoffs, having experienced similar cuts in 2020 and 2022. The company has transitioned from a consumer-focused app to a provider of enterprise data services, with its future financial outlook remaining uncertain.
2. Google Pay Enhancements: Google Pay is upping its game in the digital payment sphere by introducing new features geared towards enhancing the shopping experience. These include smarter shopping with rewards, flexible payment options through buy now, pay later (BNPL), and improved security verification methods using biometrics or PIN. These updates empower users to make informed decisions, maximize rewards, and enjoy a streamlined and secure payment process across various transactions.
3. Microsoft's AI Innovation: Microsoft's Cocreator feature within Paint is revolutionizing digital art creation by transforming quick sketches into realistic images in real-time. With options like Layers, Cocreator, and Image Creator, users can blend text and sketches seamlessly, adjusting creativity levels and styles. However, this feature currently requires specific hardware capabilities, limiting its accessibility to Copilot+ devices.
4. Apple Addresses Photo Bug: Apple swiftly addressed a bug in iOS 17.5 that caused deleted photos to reappear on iPhones and iPads. The fix was rolled out in iOS 17.5.1, which users can install via Settings > General > Software Update. While the root cause of the issue remains speculative, theories include indexing glitches, photo library corruption, or synchronization issues with iCloud Photos.
3 notes
·
View notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes
Text
On Personal InfoSec
Been awhile since I've had one of these posts but I figure with all that's going on in the world it's time to make another one of these posts and get some stuff out there for people. A lot of the information I'm going to go over you can find here:
So if you'd like to just click the link and ignore the rest of the post that's fine, I strongly recommend checking out the Privacy Guides.
Browsers:
There's a number to go with but for this post going forward I'm going to recommend Firefox. I know that the Privacy Guides lists Brave and Safari as possible options but Brave is Chrome based now and Safari has ties to Apple. Mullvad is also an option but that's for your more experienced users so I'll leave that up to them to work out.
Browser Extensions:
uBlock Origin: content blocker that blocks ads, trackers, and fingerprinting scripts. Notable for being the only ad blocker that still works on Youtube.
Privacy Badger: Content blocker that specifically blocks trackers and fingerprinting scripts. This one will catch things that uBlock doesn't catch but does not work for ads.
Facebook Container: "but I don't have facebook" you might say. Doesn't matter, Meta/Facebook still has trackers out there in EVERYTHING and this containerizes them off away from everything else.
Bitwarden: Password vaulting software, don't trust the password saving features of your browsers, this has multiple layers of security to prevent your passwords from being stolen.
ClearURLs: Allows you to copy and paste URL's without any trackers attached to them.
VPN:
Note: VPN software doesn't make you anonymous, no matter what your favorite youtuber tells you, but it does make it harder for your data to be tracked and it makes it less open for whatever network you're presently connected to.
Mozilla VPN: If you get the annual subscription it's ~$60/year and it comes with an extension that you can install into Firefox.
Proton VPN: Has easily the most amount of countries serviced, can take cash payments, and does offer port forwarding.
Email Provider:
Note: By now you've probably realized that Gmail, Outlook, and basically all of the major "free" e-mail service providers are scraping your e-mail data to use for ad data. There are more secure services that can get you away from that but if you'd like the same storage levels you have on Gmail/Outlook.com you'll need to pay.
Proton Mail: Secure, end-to-end encrypted, and fairly easy to setup and use. Offers a free option up to 1gb
Tuta: Secure, end-to-end encrypted, been around a very long time, and offers a free option up to 1gb.
Email Client:
Thunderbird if you're on Windows or Linux
Apple Mail if you're on macOS
Cloud Storage:
Proton Drive: Encrypted cloud storage from the same people as Proton Mail.
Tresorit: Encrypted cloud storage owned by the national postal service of Switzerland. Received MULTIPLE awards for their security stats.
Peergos: decentralized and open-source, allows for you to set up your own cloud storage, but will require a certain level of expertise.
Microsoft Office Replacements:
LibreOffice: free and open-source, updates regularly, and has the majority of the same functions as base level Microsoft Office.
OnlyOffice: cloud-based, free, and open source.
Chat Clients:
Note: As you've heard SMS and even WhatsApp and some other popular chat clients are basically open season right now. These are a couple of options to replace those.
Signal: Provides IM and calling securely and encrypted, has multiple layers of data hardening to prevent intrusion and exfil of data.
Molly (Android OS only): Alternative client to Signal. Routes communications through the TOR Network.
Briar: Encrypted IM client that connects to other clients through the TOR Network, can also chat via wifi or bluetooth.
Now for the last bit, I know that the majority of people are on Windows or macOS, but if you can get on Linux I would strongly recommend it. pop_OS, Ubuntu, and Mint are super easy distros to use and install. They all have very easy to follow instructions on how to install them on your PC and if you'd like to just test them out all you need is a thumb drive to boot off of to run in demo mode.
If you game through Steam their Proton emulator in compatibility mode works wonders, I'm presently playing a major studio game that released in 2024 with no Linux support on it and once I got my drivers installed it's looked great. There are some learning curves to get around, but the benefit of the Linux community is that there's always people out there willing to help.
I hope some of this information helps you and look out for yourself, it's starting to look scarier than normal out there.

#information security#infosec#computer security#computer infosec#personal infosec#browsers#internet browser#email#instant messaging#cloud storage#linux#pop os#linux mint#ubuntu#firefox#firefox extensions#long post
67 notes
·
View notes
Text
my macbook is such an insidious case study in late stage capitalism
it's 7 years old and running great, but I've hit a wall. my browsers can no longer support certain site updates (slack, most streaming services, etc.) and in order to update my browser to run those sites, apple requires a newer model than my oh-so-geriatric laptop. so, at last, I'm giving in and getting an upgrade, even though the software and hardware still works just fine.
I'm fully intending on buying a refurbished macbook instead of giving apple my money, but I went through the process on their site all the way to check out in order to figure out exactly what specifications to look for.
with that in mind, apple has two payment options. you can pay upfront ($1399 for a new macbook air with the memory and storage upgrades I'd need), or in installments for 12 months (~$117/month). well, that would be super convenient if you aren't flush with cash, which most of us aren't. except wait. in order to choose the installment plan, you have to apply for and use an apple credit card, which has an average 25% apr.
for a laptop I don't want to be buying in the first place.
5 notes
·
View notes
Text
Marketing Strategies And Marketing Mix Of Adobe
Source: The Brand Hopper
"Adobe’s Marketing Mix (4Ps): A Deeper Dive
Adobe’s success can be attributed to its strategic implementation of the marketing mix, the 4Ps: Product, Price, Place, and Promotion. Let’s explore each element in detail:
1. Product:
Breadth: From Photoshop and Illustrator for design to Premiere Pro and After Effects for video editing, Adobe covers diverse creative needs. They even offer XD for web design and Spark for social media content creation.
Depth: Each software has various versions. Photoshop Elements caters to beginners, while Photoshop CC caters to professionals. This ensures accessibility and scalability for different user groups.
Innovation: Adobe Research invests heavily in AI, machine learning, and other cutting-edge technologies. This translates into features like Content-Aware Fill in Photoshop and Rotoscoping in After Effects.
Integration: Adobe products work seamlessly together. For example, you can edit a photo in Photoshop and directly export it to Premiere Pro for video editing.
Services: Adobe Creative Cloud offers 20GB of cloud storage, access to Adobe Fonts, and integration with stock photo libraries like Adobe Stock, enhancing the overall creative workflow.
2. Price
Subscription Model: Adobe transitioned from perpetual licenses to subscriptions in 2013. This makes their software more affordable for individuals and small businesses, especially with monthly payment options.
Tiered Pricing: Individual, team, and enterprise subscriptions offer different features and functionalities, catering to diverse needs and budgets.
Free Trials and Freemium Options: Adobe offers free trials for most products, allowing users to experience the software firsthand. Some products also have limited free versions with basic features.
Discounts: Educational institutions, students, and teachers receive significant discounts on Adobe Creative Cloud, expanding access to future generations of creative professionals.
Bundled Offerings: Adobe Creative Cloud offers various bundles combining multiple products at a discounted price. This incentivizes purchases and increases perceived value.
3. Place
Direct Sales: Adobe sells directly through its website and flagship stores, offering personalized recommendations, tutorials, and in-depth product demonstrations.
Partner Channels: Strategic partnerships with leading tech companies like Microsoft and Apple expand reach and distribution channels. This makes Adobe software easily accessible through familiar platforms.
Online Marketplaces: Adobe software is available on Amazon and the Microsoft Store, increasing visibility and accessibility for users who prefer these platforms.
Cloud Delivery: Adobe Creative Cloud is delivered through the cloud, eliminating installation hassles and allowing users to access their files and projects from any device with an internet connection.
Mobile Apps: Adobe offers mobile versions of popular products like Photoshop and Lightroom, catering to the on-the-go creative needs of users and expanding their creative potential beyond desktops.
4. Promotion
Content Marketing: Adobe offers high-quality content across various formats. The Adobe Blog features in-depth tutorials, industry insights, and creative inspiration. They also have dedicated YouTube channels for each product, offering tutorials, tips, and behind-the-scenes glimpses.
Community Engagement: Adobe fosters a strong community through forums like the Adobe Help Center and user groups. They also host events like Adobe MAX, which connects users, showcases new features, and inspires creativity.
Social Media Marketing: Active engagement on platforms like Twitter, Instagram, and YouTube builds brand awareness and connects with users directly.
Influencer Marketing: Collaborations with renowned creative professionals like photographers and designers amplify brand messaging and reach new audiences. Adobe also has an Adobe Creative Experts program, empowering passionate users to share their knowledge and expertise.
Events and Conferences: Adobe hosts and participates in industry events like Adobe MAX and Adobe Summit. These events showcase innovation, connect with potential customers, and build brand awareness.
Paid Advertising: Adobe uses targeted ads on platforms like Google and social media to reach specific audience segments and drive traffic to their website and free trial offers.
By strategically implementing these elements, Adobe has created a marketing mix that is comprehensive, effective, and adaptable. They have gone beyond simply selling software; they have built a community, fostered creativity, and established themselves as a leader in the industry. This approach not only drives sales but also builds brand loyalty and establishes a strong foundation for future growth. "
#mktmarketing4you#corporatestrategy#marketing#M4Y#lovemarketing#IPAM#ipammarketingschool#ContingencyPlanning#virtual#volunteering#project#Management#Economy#ConsumptionBehavior#BrandManagement#ProductManagement#Logistics#Lifecycle
#Brand#Neuromarketing#McKinseyMatrix#Viralmarketing#Facebook#Marketingmetrics#icebergmodel#EdgarScheinsCultureModel#GuerrillaMarketing#STARMethod#7SFramework#gapanalysis #AIDAModel #SixLeadershipStyles #MintoPyramidPrinciple #StrategyDiamond #InternalRateofReturn #irr #BrandManagement #dripmodel #HoshinPlanning #XMatrix #backtobasics #BalancedScorecard #Product #ProductManagement #Logistics #Branding #freemium #businessmodel #business #4P #3C #BCG #SWOT #TOWS #EisenhowerMatrix #Study #marketingresearch #marketer #marketing manager #Painpoints #Pestel #ValueChain # VRIO #marketingmix
Thanks for following us.

https://thebrandhopper.com/2024/02/06/marketing-strategies-and-marketing-mix-of-adobe/
3 notes
·
View notes
Text
Thrissur’s Go-To Destination for Tech: Find the Best Laptop Shop and Store Today
In today’s fast-paced world, a laptop isn’t just a gadget—it’s your personal workstation, your classroom, your entertainment hub, and even your business partner. Whether you're a student attending online classes, a working professional meeting deadlines, a gamer chasing high frame rates, or a designer working on resource-intensive projects, the quality and reliability of your laptop make a big difference. And when you’re ready to buy one, finding the right laptop shop in Thrissur can make your purchase smoother, smarter, and more satisfying.
Thrissur, famously known as Kerala's cultural capital, is now also emerging as a strong player in the tech retail space. If you're planning to upgrade or purchase a new laptop, you don’t need to look far—this city has it all.
Why Thrissur Is a Smart Place to Buy a Laptop
As the demand for quality tech increases, Thrissur has kept pace with its expanding range of electronics and IT stores. The presence of IT parks, academic institutions, freelancers, and startups has created a constant demand for high-performance devices. As a result, several trusted laptop store in Thrissur outlets have emerged, offering everything from budget-friendly student models to premium business and gaming machines.
Unlike online marketplaces where support ends at delivery, a good local laptop store provides personalized advice, immediate service, hands-on product demos, and direct after-sales support. It’s no wonder that Thrissur residents prefer going local for such a major tech purchase.
What to Expect from a Top Laptop Store in Thrissur
Choosing the right store is crucial if you want to make the best use of your budget and time. Here are a few signs that you’ve found the right laptop shop in Thrissur:
✅ Wide Selection of Brands and Models
You should be able to choose from top global laptop brands like HP, Dell, Lenovo, ASUS, Acer, and Apple—all in one place. Whether you need an everyday workhorse, a lightweight ultrabook, or a high-performance gaming laptop, a good store will stock it.
✅ Knowledgeable, Friendly Staff
Not sure if you need an i5 or i7 processor? Confused about RAM or SSD options? Expert staff at a reputable laptop store in Thrissur will explain everything clearly, helping you choose based on your needs and not just marketing hype.
✅ Competitive Pricing & Offers
A trusted local store can often match or beat online prices—plus you get to take advantage of bundle deals like free antivirus software, laptop bags, and extended warranty options.
✅ Onsite Services & Warranty Support
A major benefit of choosing a physical store is access to fast, reliable service. Most good stores will help you with laptop setup, OS installation, data transfer, and troubleshooting even after purchase.
✅ EMI & Finance Options
Many laptop shop in Thrissur locations partner with finance companies or offer bank EMIs, making even high-end models accessible to students, freelancers, and small business owners.
Why Buying Local Is Better Than Online
There’s no denying the convenience of online shopping, but when it comes to buying laptops, there are advantages to going offline—especially in a tech-savvy market like Thrissur.
Live Demos: You get to test the laptop’s display, keyboard, build quality, and speed before buying.
Instant Delivery: No waiting for couriers—you walk out with your laptop.
Human Interaction: You can ask real questions and get real answers, not chatbot replies.
Trust and Reliability: If something goes wrong, you know exactly where to go and whom to talk to.
Most In-Demand Laptop Categories in Thrissur
Different buyers have different needs. A full-service laptop store in Thrissur caters to:
Students: Affordable laptops with long battery life and portability.
Working Professionals: Business-class models with speed, security, and durability.
Gamers: High-performance laptops with dedicated GPUs and cooling systems.
Designers & Editors: Powerful machines with high-res displays and multi-core processors.
Home Users: Simple and budget-friendly devices for browsing, emails, and media.
Additional Services You Can Expect
Besides selling laptops, many top shops offer value-added services like:
Laptop servicing and repairs
Upgrades (RAM, SSD, etc.)
Accessories like cooling pads, external keyboards, and webcams
Software installation (MS Office, antivirus, etc.)
Data recovery and backup solutions
Choosing a local laptop shop in Thrissur gives you the benefit of one-on-one tech support that big online retailers simply can’t offer.
Final Thoughts: Make Your Laptop Purchase Count
Buying a laptop is an investment—not just of money, but also of trust. And trust is best placed in stores that value your needs, offer transparent pricing, and stand by you long after the sale.
So the next time you're in search of the perfect device, skip the hassle of endless comparisons and delivery delays. Walk into a trusted laptop store in Thrissur and walk out with a device you can count on—backed by local expertise, immediate support, and the satisfaction of a smart purchase.
#thrissur#kerala#laptop#laptoplove#college#digital marketing#freelance digital marketing#professional#students#digital art
2 notes
·
View notes