#and the password to the chromebooks which is the same on each one
Explore tagged Tumblr posts
Text
Nothing I love more than having a little tea w the office ladies
#its called tea bc we have it at 7am#i do mean gossip btw not literal tea#i dont have time for that when i clock in#wouldnt be bad though#tales from diana#brenda says some of the new subs have been stealing the folders. GAGGG#why. there's nothing personalized in there and most of the info isn't even important#sometimes i dont even take them#idk how many they started w this year but last year they started w 7 or 8#and now theyre down to like. 2. and she said she saw someone w 3 yesterday#WHY WOULD YOU KEEP MULTIPLE???? U DONT EVEN NEED THE ONE#all that u need in there is the bell schedule. office extensions (which u only need to memorize admin's nd theyll forward u)#and the password to the chromebooks which is the same on each one#the rest is just filler stuff for like emergency drills#LOLLLL#newbs#me. the best substitute teacher#im allowed to have a big head here ive done this job awhile and im comfy at it#i used to think i was so bad at it. but now i know. im mediocre#which is the best thing a high school sub can be nowadays
3 notes
·
View notes
Text







Today was a pretty good day. It was unseasonably warm. Not that I noticed for most of the day because our apartment holds in the cold. But it wasn't even that bad in here. I was comfortable in my outfit when I was in here. I was not when I went outside.
But it was a nice day. I woke up in a pretty good mood. I did not get out of bed for a while. Just watched tiktoks and scrolled. I would get up and get dressed eventually but there was no urgency to it.
I did like my outfit a lot. My hair was very dirty and I would wash it tonight. But I just threw it in buns and off I went.
I did some cleaning. Wiped down the walls and cabinets in the kitchen. We were going to vacuum but it needed to charge. So while we waited I made myself lunch and signed in to style.
I only had one person and I as I was finishing that up I got the alert that I needed to restart my Chromebook to download to my drive. Alright. So I finished up my work and did that. And then was locked out of the laptop. Again. Like happens every time we have to restart this stupid machine. Its supposed to have the same password as my gmail. But for some reason it wouldn't work!!! It kept asking for a different password. Even with the 2 factor phone check. It still wouldn't let me in.
Until it would. Under the condition that it erased my entire computer. Again. This is like the 3rd or 4th time this year. And its not the worst. But I was sad. All of my screen shots and stuff. The photos I downloaded off facebook. I didn't actually lose anything. But it would take a lot of work to get it all back. I was dealing and was trying to not be sad. But then I couldn't get into any of my other emails. Including my styling one. I just couldn't get in. And I didn't even have my boss's email. I had to text Jess to get it. And then my boss wouldn't get back to me until closer to 5 tonight and she didn't understand that gmail wouldn't let me change the password without an admin because its not a private account and is a work account. And am just so frustrated by the whole thing.
So I tried to just focus on something else.
I cleaned up my studio and cut a few bears. I made 4. Which is the tiny goal Im giving myself every day this week. I put some finished pieces back in the baskets. And sewed and tried to be in a better headspace.
I went back to cleaning. Did the bathroom. And then played animal crossing for a bit. One of my favorite characters, Cyrano, asked to live on a construction site. And I had a great time making that.
Once I was done I decided to go out. I needed to go out and do something.
I drove out to the Target shopping center. I listened to a podcast. Enjoyed looking around in the different stores. I went to five below and DSW. I didn't get anything but I had a nice time.
I went to target next. I found a few pieces of clothes I really liked but the sizes weren't exactly right so I passed. If they have them next time well see. I did get this fleece that I love. It was on super clearance. And I love it. Excellent.
I got some snacks and candy. Some things for sweetP. Hair tyes. And then went over to five guys for a little dinner.
I ate in the parking lot. Enjoyed the sunset. And then headed home. My eyes were getting tired.
When I got back we had a card from Ellen. It was so kind of her. She even sent me furby stickers. What a sweetheart.
I put things away. And hung out with James. I vacuumed finally. And gave sweetP a new toy. I played animal crossing for a little. James went to their parents' after work to get some wrapping paper. I spent an hour and a half wrapping my tote bags worn out handle. Working on some visible mending examples. And once that was done I took a shower. I am trying a new way to dry my hair. And I am just ready to close my eyes.
I have work tomorrow. But it should just be one tour. I am looking forward to a nice day. The wind is picking up and there might be snow this week. I hope it is pretty flurries.
Sleep well everyone. Take care of each other. Wash your hands.
3 notes
·
View notes
Text
How do does a student at pierce set up a new password

#How do does a student at pierce set up a new password mac os x#
#How do does a student at pierce set up a new password code#
#How do does a student at pierce set up a new password download#
This score ranges from a low of 1 to a high of 9. This ranking is not the percentage correct. This score indicates the relative standing of the student when compared to others of the same grade. This is the number of questions answered correctly. You may access test results in your online account, or via mail.įor most of the tests the following categories are included in the report: Your test results should be available within a week of us receiving your child's test. Mail the test back to FLO once completed. Once you receive the test, you have two weeks to proctor the test to your student. If not ordering online, please call us or email/fax/mail one of the forms below: Online orders may not be placed for groups. If ordering the SAT10 Online test, instructions will be emailed to you within 3 days of placing the order. All paper tests and instructions will be mailed to you. You may also mail, fax, or email one of our order forms to us, or call our office so we can assist you in completing your order. Without an online account, simply checkout as a guest. An online account is not required to order, but is encouraged for the ability to view order history and past test results. You may place an order directly on our website. In other words, no off-norm scoring is available for the Stanford Online. Stanford Online tests CANNOT be normed for a different period other than the one in which they were taken. The Stanford Online norming periods are slightly different from the other standardized tests. Results will also be available from your online account (if one was created) in this same time frame. Test results are emailed to you within 24-48 hours of the last testing day. Ensure all instructions and sessions codes are printed off before beginning the testing or that they can be accessed on a different device. Once the testing session begins no other applications are allowed to be run. The SAT10™ online is proctored remotely, but an adult needs to be present to monitor the testing. Chromebooks are not supported by the testing browser and cannot be used for the testing. Updated Chrome browser can be used, but will provide an error during pre-test scan.
#How do does a student at pierce set up a new password mac os x#
Windows 7 or higher and Internet Explorer 8.0 or later or Mac OS X 10.6 or higher with Safari 6.0. The first rescheduling is at no charge, but it is $10.00 for each rescheduled testing day following this. Start times are all in PST time zone and are from 7 a.m. You will have the option of choosing to complete the testing over a 2 day consecutive testing window that can start on a Wednesday or Thursday.
#How do does a student at pierce set up a new password download#
You will use this information to download the secure testing browser that will be used for the testing sessions. This information will provide steps to ensure all computers being used for testing will meet the technical requirements. You will receive information by e-mail within 48 hours of placing the order, and at least 24 hours prior to your desired testing date. Once you complete the order and checkout, additional instructions will be emailed to you.Please keep the regional time differences in mind and schedule accordingly. The starting time is in Pacific Time and will apply to both testing days. Also in Cart Review, click on the schedule button to select the desired beginning testing date and time.In the Cart Review, assign a student to the SAT10 test.If you are wanting to test with Fall or Winter norms, give us a call. You may pre-order up to 8 months in advance. Order the grade level your student is completing or has most recently completed. The testing window for the SAT10 Online is April 1st through July 31st each year. 5% of cost goes to help homeschooling families in need nationwide.Testing occurs every week Wednesday, Thursday, & Friday.Results emailed within 1-2 business days of completion.Testing takes places at mutually agreed upon testing dates and time.Untimed testing can continue as long as student is working.Secure Browser ensures security of the test and student data.This is the complete battery version with updated 2018 norms. End result - can visibly see each student in each breakout room on computer screens without having to navigate to each breakout room on one computer.The Stanford 10™ Online is a nationally normed standardized test published by Pearson Assessments.
#How do does a student at pierce set up a new password code#
23 Using CASAS Guidelines 1:5 Test Lab Setup Once the following has taken place: all rooms have been assigned, all students have been given the remote access code all students are ready to start The proctor will click (open all rooms) and move to the logged in computers to accept all their multiple selves into each breakout room.

0 notes
Text
Top 8 Password Managers Everyone is Talking About in 2021
Working from home has become the norm for many of us, making it more critical than ever to safeguard your online accounts with secure passwords. However, remembering dozens of passwords can be tough, and repeatedly using the same password could be dangerous. If you’re continually getting locked out of online accounts because you can’t remember your passwords, it’s time to invest in a password manager. A password manager will help you keep track of and manage your login credentials while also assuring password security. They can also be used to auto-fill forms and sync data between Windows and Mac computers, as well as Android and iPhone devices. A password manager is essentially a secure digital vault that keeps password login information for apps, accounts, websites, and other services on your mobile device. The best password manager contains a password generator to create strong, unique passwords and ensure you aren’t using the same password in many places, in addition to keeping your identity, credentials, and sensitive data safe. 1. LastPass Because of its ease of use, compatibility for all major platforms, and extensive feature set, LastPass remains our top pick for the best password organizer. That’s even despite the fact that its once-excellent free tier has been significantly reduced. LastPass’s free version no longer syncs across all of your devices, but only between your PCs and mobile devices – not both. A password generator, unlimited passwords, and secure storage are among the features it shares with the commercial version. Unlimited syncing across all devices, support for physical two-factor authentication keys, 1GB of online file storage, dark-web account monitoring, and premium tech support are all included in the subscription edition. LastPass does not require the installation of any software on your computer. Instead, the software can be completely contained within browser extensions and a fully functional online interface. With some limitations, vintage desktop apps for Windows and Mac are still available. Meanwhile, the LastPass Pocket option for Windows and Linux that only works on a local network has been retired, as has the password filling feature. 2. Bitwarden With its affordable rates, stylish design, and full-featured free tier, Bitwarden has risen to the top ranks among password managers since its launch in 2016. Bitwarden is the best alternative for anyone who wants to sync all of their logins across all of their devices without paying anything now that LastPass has crippled its own free service. Meanwhile, Bitwarden’s $10-per-year commercial version provides most of the same capabilities as LastPass, Keeper, or 1Password, albeit it can be a little awkward to use. Bitwarden gives you the option of setting up your server to sync your passwords, which privacy freaks will love. A secure information-sharing service called Send, a “portable” Windows version that can be installed on a flash drive, and extensions for eight different browsers are also essential features. Bitwarden’s two main drawbacks are a limited desktop app and the inability of the mobile apps to auto-fill credit card numbers or other non-login information. 3. Keeper Keeper is a full-featured password manager that is quick and easy to use, has a solid web interface, keeps all types of files and documents, has possibly the best security of any password manager, and includes a premium version that is less expensive than both Dashlane and LastPass. Its free tier includes everything except device syncing. The cost of increased security is a little inconvenient. Keeper does not feature a bulk password changer and does not allow you to generate a PIN to access the mobile app quickly. You’ll have to input the complete master password every time if you’re still using an older phone that can’t recognize your fingerprint or face. Keeper will also monitor the internet for unlawful usage of your data and provide 10GB of safe cloud storage for an additional $25 per year. It also has a secure messaging option that is free. 4. Dashlane Dashlane is similar to LastPass in terms of platform coverage and has excellent desktop software, at least for the time being. Although the sites that support it aren’t the most well-known, its killer feature remains the bulk password changer, which can reset hundreds of passwords at once. Dashlane stated in January 2021 that its desktop applications would be phased out over the next year. It encourages everyone to use browser extensions. The password organizer is well-designed, simple to use, and quite effective at filling out personal information in web forms. A scanner searches your email inbox for online accounts that you may have forgotten about. The high cost of Dashlane is a disadvantage. Dashlane’s Premium membership costs $60 per year or $78 per year if paid monthly, while the free plan is limited to 50 sets of credentials and doesn’t allow you to sync between devices. A new Essentials plan, which costs $36 per year ($4 per month), seeks to bridge the gap between the two, but it only allows you to use two devices, which isn’t much of a bargain when compared to LastPass, Keeper, and 1Password’s unlimited options. Dashlane Premium package, on the other hand, includes dark-web monitoring and an unlimited VPN service. The high prices may be justified by these non-password management functions. 5. 1Password The 1Password apps are better on Mac and iOS than they are on Android or Windows, but the designs and user interfaces on both the desktop and mobile apps are a little archaic. However, 1Password in the browser, a set of stand-alone browser extensions for Brave, Chrome, Edge, Firefox, and Safari, is fantastic. They operate with web browsers directly and now support biometric logins as well. They also make 1Password available to Chromebook users, and the 1Password Linux desktop client will be available in May 2021. The most compelling feature of 1Password is its Travel Mode, which deletes sensitive data from your devices (you’ll get it back later) so that eavesdropping border-control officials can’t locate it. 1Password features excellent form-filling capabilities as well as real two-factor authentication. New users must join up for a $36 yearly cloud membership with 1Password. Until recently, Mac users could purchase the older stand-alone application for $65. However, 1Password will no longer be releasing new licenses as of August 2021. 1Password’s limited free edition is no longer available. 6. Blur Blur is a password organizer that comes with a privacy protection service. It works well as a browser-based desktop password manager, but it’s pricier than LastPass, Keeper, or 1Password. Its mobile apps are also outdated and difficult to use. Blur excels at keeping your information secret. It provides one-time-use credit card numbers for online transactions, separate email addresses for each online service you join, and even a second phone number if you don’t want to divulge your real one. With Blur’s basic premium plan, you receive all of this for $39 per year, albeit you must pay a tiny price for each one-time-use credit number. The $99 unlimited premium plan eliminates these expenses. (Each paid plan is free for the first 30 days.) The free tier is rather basic, with few privacy protections and no cross-device syncing. There are better and less expensive choices if you merely want a reliable password manager. Blur, on the other hand, is well worth investigating if comprehensive online privacy is your primary concern. 7. Enpass Enpass’s free desktop software for Windows, Mac, and Linux are robust and unlimited, but its free Android and iOS mobile apps are limited to 25 passwords. Unlimited coverage on all devices is $15.99 for six months, $23.99 for a year, or $55.99 for a lifetime subscription. Enpass does a good job with the essentials, but you’ll have to sync your own devices with Dropbox, OneDrive, or another service because Enpass doesn’t have any cloud-syncing capabilities. Enpass PC interface is simple but effective, and the mobile apps are well-designed. To some extent, they all deal with biometric logins. Although Enpass does not offer a local-sync feature, you can make one using USB drives or network sharing. This might make the service suitable for consumers who are hesitant to share their personal information online. 8. Zoho Vault Although Zoho Vault is part of a bigger package of paid commercial applications, the password manager is available for free for personal use. Families can sign up for group plans that start at $12 per user per year. With Zoho Vault, you won’t find consumer-friendly features like personal data form filling or a mass password changing, but all necessities are present and functioning well. Zoho Vault uses its servers to sync your passwords, and there’s no charge to sync all of your desktop, laptop, and mobile devices. The one flaw we found in our testing was that Zoho Vault occasionally tripped over Google’s two-page logins, but Zoho reps say this has already been resolved. Source :- https://infoprintercan0n.co.uk/top-8-password-managers-everyone-is-talking-about-in-2021/
0 notes
Text
Mac Os X Iso Download 64 Bit For Virtualbox

Mac Os High Sierra Iso For Virtualbox
How To Install Mac Os On Virtualbox
Mac Os Iso For Vmware
Mac Os Vm Iso
Mac Os X Download Iso
Mac Os 64 Bit Download
If you have 64 bit Operating system then you can download Virtualbox 6.0. 1) Just again visit this Link 2) Now under Virtualbox 6.0.0 click on your OS. 3) Now the download will start automatically, it will 200mb in size. The 'System Type' of your copy of Windows needs to be 64-bit, because OS X Mountain Lion is a 64-bit operating system. If you have a 32-bit copy of Windows, you can only install Mac OS X Snow Leopard on Virtualbox.
Downloading process of macOS Catalina Image file for VirtualBox and VMware. Mac OS 10.15 Catalina is named because of a special kind of update for Apple and for its operating system which is known as Mac. It has some outstanding features, applications, and a voice record facility which we already discussed earlier.
Mac Os High Sierra Iso For Virtualbox
VirtualBox is a general-purpose full virtualizer for x86 hardware, targeted at server, desktop and embedded use.For a thorough introduction to virtualization and VirtualBox.
For VMware or VirtualBox virtual machines, click the button below to download the image file to your computer via google drive. Download ISO File. Update (June 8, 2018): Mac OS 10.13.5 Released! Update: (July 26, 2018): Mac OS 10.13.6 Released! Update: (July 26, 2018): Mac OS Mojave 10.14 Released!
Want to install macOS on Virtualbox?
If yes, then this post is definitely for you.
In the previous posts, I have already talked about installing linux ubuntu on Virtualbox & other operating systems also.
Everyone knows Mac OS is one of the most premium Operating systems.
And everyone wants to use it but it’s a little expensive.
And that’s why people try to find out different ways to install Mac OS on their PC.
Two years back I also installed Mac OS High Sierra Hackintosh on my PC.
And now I am installing the Mojave version.
So in this post, I will show you how to install macOS Mojave on Virtualbox on Windows PC.
Let’s see How it works. Also Read: Chromebook ChromeOS on Virtual machines.
How to Install macOS on Virtualbox in Windows 10 PC [ Mojave ]
But before we begin.
Please make sure that you have downloaded the Oracle Virtualbox and the macOS Mojave ISO file from the given link.
Virtualbox: Download link macOS Mojave Virtualbox image: Download link
I know you might be thinking of creating your own iso file but it’s a little time-consuming.
And that’s why I have already given the link for the Mojave image file.
Now I hope you have already downloaded all the given files & installed Virtualbox successfully.
Note:- Please check the VT-x or AMD-V virtualization feature must be enabled in your BIOS settings.
So Let’s get started & follow this step by step guide.
How To Install Mac Os On Virtualbox
1. Open & Install Virtualbox Extension Pack
Now Open Virtualbox and install the Extension Pack from the given link. Download link
Now that you have installed the extension pack, it’s time to create a virtual machine.
2. Create a macOS Mojave Virtual Machine
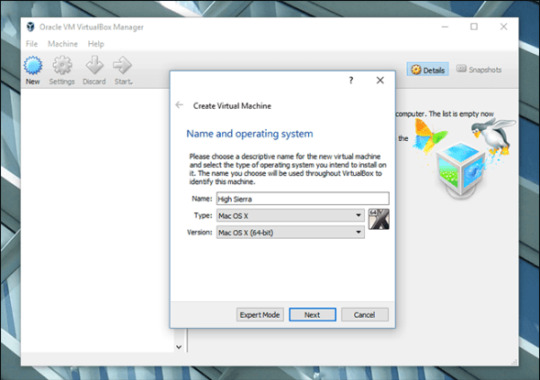
Open Virtualbox and Click on the “New” button to create a macOS virtual machine.
Now type the name as “macOS Mojave“, type of OS as Mac OS X and the version of OS as Mac OS X (64-bit). And then Click on Next.
3. Memory Size (RAM)
Now select the amount of RAM to be allocated to the virtual machine. And to run macOS on Virtualbox, the minimum recommended RAM size is 2048Mb.
4. Setup a Virtual Hard Disk
Now the next step is to create a virtual disk for this machine. But here instead of creating a new virtual hard disk, we will import the macOS Mojave 10.14 disk image file which we have downloaded earlier. So Click on Use an existing virtual hard disk file.
And then click on the Folder icon and browse to the image file.
Now select the image file and Click Open.
And you can see that you have successfully created the macOS virtual machine and here comes the configuration part.
5. Configuring macOS Virtual Machine
Note:- All these settings are mandatory to run and install macOS Mojave on Virtualbox on Windows PC properly.
Now Click on Settings.
Now in the Next screen Go to System, then Click on Motherboard Tab and Select the Boot Order as Optical and Hard disk. And in the Extended Features Enable I/O APIC, Enable EFI (Special OSes only) and Hardware Clock in UTC Time. Click OK.
Next Go to Processor Tab. And select the minimum processor as 2 and Enable PAE/NX in the extended features. Click OK.
Further, Go to Display Settings and change the Video Memory to 128 MB or the maximum you can have.
Next, Go to the Storage tab and Enable the Use Host I/O Cache and Click OK.
Now, Go to the USB tab and Enable the USB 3.0 (xHCI) Controller and Click OK.
6. Modify Virtualbox Virtual Machine using Command Prompt
Note:- Before running the Command Prompt, please make sure that you have Closed the Virtualbox & it is not in the running state.
Also, I would recommend you to Restart or Reboot your pc before using these command-line codes.
Now add the following commands to Virtualbox Virtual Machine using Command Prompt (CMD). And to Open Command Prompt, click on Search and type “CMD” and Right Click on it and select Run as Administrator.
Now run each command one by one in the command prompt. And before running each command, please make sure to change the “Your VM Name” part with the name of the virtual machine that you have created earlier.
cd “C:Program FilesOracleVirtualBox”
VBoxManage.exe modifyvm “Your VM Name” –cpuidset 00000001 000106e5 00100800 0098e3fd bfebfbff
VBoxManage setextradata “Your VM Name” “VBoxInternal/Devices/efi/0/Config/DmiSystemProduct” “iMac11,3”
VBoxManage setextradata “Your VM Name” “VBoxInternal/Devices/efi/0/Config/DmiSystemVersion” “1.0”
VBoxManage setextradata “Your VM Name” “VBoxInternal/Devices/efi/0/Config/DmiBoardProduct” “Iloveapple”
VBoxManage setextradata “Your VM Name” “VBoxInternal/Devices/smc/0/Config/DeviceKey” “ourhardworkbythesewordsguardedpleasedontsteal(c)AppleComputerInc”
VBoxManage setextradata “Your VM Name” “VBoxInternal/Devices/smc/0/Config/GetKeyFromRealSMC” 1
Like I will replace “Your VM Name” with “macOS Mojave” in all the codes.
It will be easier if you first copy all the codes to a notepad file & edit them and then paste them in the CMD.
And you are done with the configuration part. Now comes the major part to install the macOS Mojave on Virtualbox Virtual machine.
Install macOS Mojave on Virtualbox PC
Note:- All this installation process of mac on Virtualbox works the same as on the original MacBook. This means that this process is also applicable to Mac Users installing the Mac operating system.
So Let’s get started & install it properly.
1. Start & Run macOS Mojave
Now Open Virtualbox & select the virtual machine and then Click on Start.
Now, wait for a few minutes while the virtual machine boots up and start loading the installer or the installation files.
2. Select Country & Keyboard Layout
Now select the United States as a country & Click on Continue.
And Keyboard layout as the US and Click on Continue.
Mac Os Iso For Vmware
3. Data and Privacy
Now in the next screen, it will ask for the Data and Privacy settings which are by default. So Click on Continue.
4. Transfer information to this Mac
On this screen, it will ask if you want to transfer any sort of information from any Mac or Windows PC. So, select Don’t transfer any information now and Click on Continue.
5. Sign in with Your Apple ID
Now it will ask to sign in with your Apple ID. If you already have the apple ID then you can enter or you can simply on Set up Later. And Continue.
6. Term and Conditions
Now the Term and conditions part, So simply Click on Agree.
7. Create a Computer Account
Its time to create a computer account that is similar to the user account created in Windows PC. So, fill out all the details like Full name, Account name and Password. And Click on Continue.
8. Express Set-Up
Next is Express Set Up where you can also customize settings or you can simply click on Continue.
9. Choose your MacOS Look
Since macOS Mojave comes in two different looks, one is the Light look which is similar to normal and the other one is the Dark look. You may choose according to your Preference & Click on Continue.
10. Installed Mac OS Mojave on Virtualbox
And Done! You have successfully installed the macOS Mojave 10.14 on Virtualbox virtual machine in Windows 10 PC.
That’s it for now…
Conclusion

So that’s how you can easily install a Mac OS on Windows 10 PC using Virtual Box Virtual Machine. And you can also follow the same method for other different OSes like Catalina & High Sierra.
Stay tuned for the next post on install mac os on VMware.
Feel free to share your thoughts and also tell us if you know any better way to Install macOS on Virtualbox in Windows 10 PC [ Mojave ].
If you liked this post, Don’t forget to share this awesome post with your friends.
Table Of Content
1- Download Mac OS
2- Create Mac OS Virtual Machine
3- Configure VBoxManage
4- Start the Mac OS virtual machine
View more Tutorials:
1- Download Mac OS
2- Create Mac OS Virtual Machine
3- Configure VBoxManage
4- Start the Mac OS virtual machine
1- Download Mac OS
Mac OS is a computer operating system developed by Apple. This is a operating system with beautiful interface, however, to own a the computer of Apple with this operating system, you need to use a lot of money, normally with the double price than that of common computers using Windows operating system. Fortunately, you can experience the Mac OS right on your computer by installing a Mac OS virtual machine on VirtualBox.
Mac Os Vm Iso
Below is the list of Mac OS versions released in recent years:
Mac OS VersionNameRelease Date10.10YosemiteJune 201410.11El CapitanSeptember 30, 201510.12SierraJune 12, 201610.13High SierraJune 5, 2017
Mac Os X Download Iso
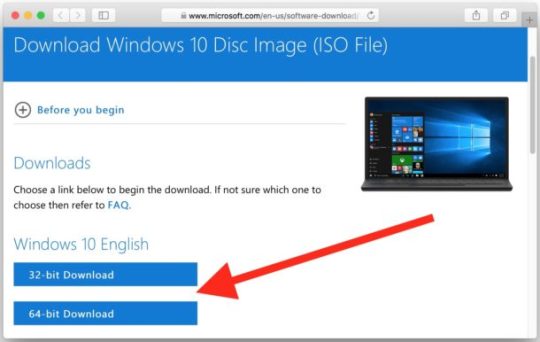
In this post, I will show you how to install the Mac OS on VirtualBox. First of all, please download an installer.
Mac Os 64 Bit Download
After finishing downloading, there is one file:
Extract the file that you have just downloaded in a folder.
2- Create Mac OS Virtual Machine
On the VirtualBox, create a new virtual machine.
Enter a name for the virtual machine and select a Mac OS version suitable for the Mac OS version that you have downloaded..
Mac OS operating systems need a large amount of RAM to work, You should provide it with about 4GB RAM.
The Mac OS file downloaded by you in the above step is a complete operating system and you can be willing to use without installation. Therefore, on the VirtualBox, you only need to point to this postion of this file.
OK, your Mac OS virtual machine has been created.
You can carry out other configurations for Mac OS, for example, Network configuration, specifying the quantity of Processors,..
3- Configure VBoxManage
After you create VirtualBox virtual machine, the Meta information of this virtual machine will be found in the folder (Depending on your operating system):
LINUX (Ubuntu,..):/home/{user}/VirtualBox VMs
WINDOWS:C:/Users/{user}/VirtualBox VMs
There are some advanced configurations that you can perform via the interface of VirtualBox, and you must carry out it via a command:
Replace 'Your-VM-Name' by your virtual machine name. Your virtual machine name can be found in the 'Setting > General > Basic' (Like the following illustration).
On the Linux (Ubuntu,..), open Terminal windows and CD to go to your Mac OS virtual machine directory. If you use the Windows operating system, open the CMD windows with Administrator privilege and CD to go to the Mac OS virtual machine directory.
Perform the above commands respectively (after having replaced 'Your-VM-Name'):
OK, all the commands have been performed successfully.
4- Start the Mac OS virtual machine
Press on 'Start' button to start your Mac OS virtual machine:
Enter username/password (to be used to enter your Mac OS virtual machine).
OK, at this moment, you have installed Mac OS Virtual Machine on VirtualBox successfully .
View more Tutorials:

0 notes
Photo

How to Install MySQL
Almost all web applications require server-based data storage, and MySQL continues to be the most-used database solution. This article discusses various options for using MySQL on your local system during development.
MySQL is a free, open-source relational database. MariaDB is a fork of the database created in 2010 following concerns about the Oracle acquisition of MySQL. (It's is functionally identical, so most of the concepts described in this article also apply to MariaDB.)
While NoSQL databases have surged in recent years, relational data is generally more practical for the majority of applications. That said, MySQL also supports NoSQL-like data structures such as JSON fields so you can enjoy the benefits of both worlds.
The following sections examine three primary ways to use MySQL in your local development environment:
cloud-based solutions
using Docker containers
installing on your PC.
Cloud-based MySQL
MySQL services are offered by AWS, Azure, Google Cloud, Oracle, and many other specialist hosting services. Even low-cost shared hosts offer MySQL with remote HTTPS or tunneled SSH connections. You can therefore use a MySQL database remotely in local development. The benefits:
no database software to install or manage
your production environment can use the same system
more than one developer can easily access the same data
it's ideal for those using cloud-based IDEs or lower-specification devices such as Chromebooks
features such as automatic scaling, replication, sharding, and backups may be included.
The downsides:
set-up can still take considerable time
connection libraries and processes may be subtly different across hosts
experimentation is more risky; any developer can accidentally wipe or alter the database
development will cease when you have no internet connection
there may be eye-watering usage costs.
A cloud-based option may be practical for those with minimal database requirements or large teams working on the same complex datasets.
Run MySQL Using Docker
Docker is a platform which allows you to build, share, and run applications in containers. Think of a container as an isolated virtual machine with its own operating system, libraries, and the application files. (In reality, containers are lightweight processes which share resources on the host.)
A Docker image is a snapshot of a file system which can be run as a container. The Docker Hub provides a wide range of images for popular applications, and databases including MySQL and MariaDB. The benefits:
all developers can use the same Docker image on macOS, Linux, and Windows
MySQL installation configuration and maintenance is minimal
the same base image can be used in development and production environments
developers retain the benefits of local development and can experiment without risk.
Docker is beyond the scope of this article, but key points to note:
Docker is a client–server application. The server is responsible for managing images and containers and can be controlled via a REST API using the command line interface. You can therefore run the server daemon anywhere and connect to it from another machine.
Separate containers should be used for each technology your web application requires. For example, your application could use three containers: a PHP-enabled Apache web server, a MySQL database, and an Elasticsearch engine.
By default, containers don’t retain state. Data saved within a file or database will be lost the next time the container restarts. Persistency is implemented by mounting a volume on the host.
Each container can communicate with others in their own isolated network. Specific ports can be exposed to the host machine as necessary.
A commercial, enterprise edition of Docker is available. This article refers to the open-source community edition, but the same techniques apply.
Install Docker
Instructions for installing the latest version of Docker on Linux are available on Docker Docs. You can also use official repositories, although these are likely to have older editions. For example, on Ubuntu:
sudo apt-get update sudo apt-get remove docker docker-engine docker.io sudo apt install docker.io sudo systemctl start docker sudo systemctl enable docker
Installation will vary on other editions of Linux, so search the Web for appropriate instructions.
Docker CE Desktop for macOS Sierra 10.12 and above and Docker CE Desktop for Windows 10 Professional are available as installable packages. You must register at Docker Hub and sign in to download.
Docker on Windows 10 uses the Hyper-V virtualization platform, which you can enable from the Turn Windows features on or off panel accessed from Programs and Features in the the Control Panel. Docker can also use the Windows Subsystem for Linux 2 (WSL2 — currently in beta).
To ensure Docker can access the Windows file system, choose Settings from the Docker tray icon menu, navigate to the Shared Drives pane, and check which drives the server is permitted to use.
Check Docker has successfully installed by entering docker version at your command prompt. Optionally, try docker run hello-world to verify Docker can pull images and start containers as expected.
Run a MySQL Container
To make it easier for Docker containers to communicate, create a bridged network named dbnet or whatever name you prefer (this step can be skipped if you just want to access MySQL from the host device):
docker network create --driver bridge dbnet
Now create a data folder on your system where MySQL tables will be stored — such as mkdir data.
The most recent MySQL 8 server can now be launched with:
docker run -d --rm --name mysql --net dbnet -p 3306:3306 -e MYSQL_ROOT_PASSWORD=mysecret -v $PWD/data:/var/lib/mysql mysql:8
Arguments used:
-d runs the container as a background service.
--rm removes the container when it stops running.
--name mysql assigns a name of mysql to the container for easier management.
-p 3306:3306 forwards the container port to the host. If you wanted to use port 3307 on the host, you would specify -p 3307:3306.
-e defines an environment variable, in this case the default MySQL root user password is set to mysecret.
-v mounts a volume so the /var/lib/mysql MySQL data folder in the container will be stored at the current folder's data subfolder on the host.
$PWD is the current folder, but this only works on macOS and Linux. Windows users must specify the whole path using forward slash notation — such as /c/mysql/data.
The first time you run this command, MySQL will take several minutes to start as the Docker image is downloaded and the MySQL container is configured. Subsequent restarts will be instantaneous, presuming you don’t delete or change the original image. You can check progress at any time using:
docker logs mysql
Using the Container MySQL Command-line Tool
Once started, open a bash shell on the MySQL container using:
docker exec -it mysql bash
Then connect to the MySQL server as the root user:
mysql -u root -pmysecret
-p is followed by the password set in Docker's -e argument shown above. Don’t add a space!
Any MySQL commands can now be used — such as show databases;, create database new; and so on.
Use a MySQL client
Any MySQL client application can connect to the server on port 3306 of the host machine.
If you don't have a MySQL client installed, Adminer is a lightweight PHP database management tool which can also be run as a Docker container!
docker run -d --rm --name adminer --net dbnet -p 8080:8080 adminer
Once started, open http://localhost:8080 in your browser and enter mysql as the server name, root as the username, and mysecret as the password:
Databases, users, tables, and associated settings can now be added, edited, or removed.
The post How to Install MySQL appeared first on SitePoint.
by Craig Buckler via SitePoint https://ift.tt/2U399ve
0 notes
Text
Apple shows it takes privacy seriously, in a public ad campaign
In this day and age, privacy is at the forefront of public and consumer discourse. it seems like either everything can be hacked, or already has. Concurrently, the line between our public and private lives has been deteriorated. As a consequence of these two phenomena, people value their privacy more than ever. And in the face of prominent data breaches, Apple wants to let the public know that they value your privacy, as much as you value your own.
youtube
In their recent 60-second ad, designed for both TV and social media audiences, they use familiar situations to convey how we each value our own privacy. Whether its from a “no trespassing” sign, a ‘menacing’ guard dog, or locking your doors (rather excessively), they create familiarity with the audience by letting them know that the people behind the creation of the iphone are regular human beings, who lock their own doors, close their blinds, and put passwords on their phones. The biggest takeaway from this advertising piece is that from a policy standpoint, Apple stands with the people in the public-private debate. From fingerprint scanners, face scanners, and encryption, Apple is putting their money where their mouth is in terms of delivering the message to their consumers, and providing products that meet consumer’s expectations in regards to privacy.

I thoroughly enjoyed this ad, because of its use of multiple framing to deliver a message that is resonant to whoever views this short clip. We might think its weird that someone would put a “no trespassing” sign on their yard, but when viewed through our own perspectives, like having a conversation at the restaurant, we see exactly what people mean when they say they value privacy. By placing themselves in the mind of the consumer, beyond any market research, there are fundamental values that subconsciously drive people to buy the way they do, and privacy is certainly one of them. In order to drive this message across, they deliver the same sentiment across multiple perspectives, which required both apple and the ad agency to go outside of their comfort zone, ad re-examine how they can convey to their audience that when it comes to privacy, Apple means business. With their introduction of Apple pay, touch and face unlocking, plus their own credit card, Apple needed to re-examine how to highlight the design philosophy behind the iphone in terms of privacy, and what better way to do it than to release an ad campaign in the eyes of the consumer. Note that Apple isn’t particularly groundbreaking in this campaign, unlike their earlier campaigns “1984″ and “The Crazy Ones”. Google has been using this style of commercials for their Pixel Phones and Chromebooks, by using multiple framing to create commercials that give the products and brands a personality dimension that a simple feature-benefits approach simply cannot.
youtube
As you can see, Apple isn’t reinventing the wheel here, but putting their own spin on a particularly effective method. As innovative as Apple is, its okay that they weren’t the first company to release ads in this style. Like their products, they are fine letting other companies innovate because they act as a test market for these features. Since the google commercials did well, they knew making one of their own, in an entirely new perspective to deliver their competitive advantage of privacy, was a guaranteed hit. And with this commercial, they are ensuring that more and more people are using an iphone to keep themselves secured in an age where our digital footprint is completely vulnerable.
0 notes
Text
JBB’s Final Thoughts Episode 37: The Endless Assault of “New Normals”
youtube
Pondering the challenges of finishing the school year in “work from home” mode and how the world might change “after this is done.”
MP3 Version: https://joebustillos.files.wordpress.com/2020/05/jbbsfinalthoughts_e037_the-endless-assault-of-new-normals.mp3 Enjoy and please subscribe to my YouTube channel or subscribe to all of my blog posts (scroll to the bottom of this page, click the red FOLLOW button in the “Follow blog via email” box).
Please Subscribe:
YouTube Channel
Twitter Account
Apple Podcasts/iTunes
Via Soundcloud
RSS Reader
Past JBB’s Final Thoughts Podcast Episodes
Resources/Credits:
music: Social Blindness – 22K by Smart Sound Music
All images and screen grabs by Joe Bustillos ©2020 except where noted
Nevada schools will stay shut the rest of school year (image by Rachel Aston), Las Vegas Review-Journal, 04-22-2020
CCSD Chromebook Deployment (images), CBS 8 News Las Vegas, 04-22-2020.
EduBlogs screens (images), retrieved 01-22-2020
Empty Las Vegas by Josh Metz, https://www.facebook.com/photo.php?fbid=2932568266766674&set=pcb.2932568556766645&type=3&theater, retrieved 2020-04-08
Episode Notes/Script/Post:
Joe Bustillos here.
Toward the end of last week I found out that the rest of the school year is going to continue in the current “work from home”/“emergency learning” mode. Side Note: many districts are calling this current mode “remote learning,” but those of us who have conducted actual online or remote learning reject the use of those words to describe what we’re doing because it wasn’t begun with any planning or guidance or technology support that actual remote learning requires. And any successes in this endeavor is entirely because teachers are determined to stay connected with their students and quite frankly we are used to being told to do the impossible and make it happen without the means to be successful.
2020-04-22 RJ: CCSD schools closed for the rest of the year
2020-04-22_NCTA: CCSD schools closed
Stickam Session 2009 – joe bustillos
2012-08-22 Full Sail University EMDT Wk4 Wimba at 7.53.06 PM
Henry Price works on a Pepperdine OMAET project while we edit the video(s)
Last week was also the week when Chromebooks were being distributed to families attending my school who do not have technology at home. Since week two, home room teachers have been calling homes to connect with their students and to verify contact information. The word was that a large portion of our students and families didn’t have any technology at home including any kind of smartphone. So the decision and implementation of distributing technology is a good thing. I just wish that this could have happened before we began the fifth week of our current situation (sixth week if you count the week of Spring Break that we still got). So, that leaves four more weeks until the beginning of the Summer Break. I’m curious how much can be done in that time, given the lack of direct contact.
2020-04-22 CCSD chromebook deployment1
2020-04-22 CCSD chromebook deployment2
2020-04-22 CCSD chromebook deployment3
2020-04-22 CCSD chromebook deployment4
I’ve been working like crazing creating instructional videos and trying to figure out how I might get students to access the curriculum. One of the other specials teachers, the music teacher, has been championing using the Seesaw platform because it’s not dependent on student email addresses and can be accessed with a smartphone. Before this began I had created individual blogs for the 4th and 5th graders to teach Internet communications and digital citizenship, but that got a little derailed. So I’m thinking that I will jump on the simpler Seesaw bandwagon for the primary grades (K through 3) and use Google Classroom with the intermediate grades (4 and 5) with the option for any 4th or 5th grade students to use the blog accounts I’ve already created if they want to. Now to figure out how to get the personal login information to each student without creating a security leak. Oh yeah, during the second week of this situation district IT decided to change how student passwords could be updated and/or recovered and I was locked out of that process altogether, making it impossible for me to assist my teachers in getting student emails up and running (another reason I am going with Seesaw with the primary grades…). Then toward the end of last week, I was able to update a student password, so I’ll be busy working on those classes that didn’t get setup after I was locked out.
2020-04-06-COVID-19 Work From Home-week4: Spring Break edition
2019-08-28 twinsies with Mr. Sharp
edublogs1
edublog-dashboard-post-view-original
edublogs2
It’s not exactly a “new normal” for me to work from home or begin and end my day sitting at my computer desk. I taught online for six-years at Full Sail University before coming to Las Vegas and have been an online student since working on my masters with Pepperdine beginning in the summer of 2001. That said, I do miss going to the local micro-breweries Friday evenings after work or going to the movies at the Orleans with my girlfriend, Deb. And I really wish that I hadn’t sold my trusty treadmill when I moved from Orlando in 2016. Before I sold it, I got a lot of mileage on that bugger because I had it set up so that I could work on my laptop, create assignments and grade student work while getting in my daily walks. I notice that most of the treadmills are sold out on Costco’s website. When I was working face-to-face in the classroom I was on my feet continually, so I’m going to have to find some solution before I put on too much quarantine-weight. I also recognize that concentrated creativity requires routinely stepping away/physical activity to keep the brain fresh and engaged. Oh, and we’re now in that time of year when it’s getting over 80° by 9am. Ugh.
jbb video editing
2010-05-12 Work space iPad-ified
2011-04-01 Office Still Life (keyboard)
2020-02-22 Sand Dollar Lounge with Deb
2014-06-14 Treadmill Workout/Tech Pix
2014-09-12 Treadmill Workout Pix
Alas, a little physical discomfort is nothing compared to the challenges many are facing particularly unemployment and job loss because few service businesses like restaurants, casinos and theaters (the bread and butter of Las Vegas) can be done from home. I am lucky that there is an “emergency learning from home” possibility, but as I noted earlier, there’s a lot of families who don’t have the means to do at home learning and are falling through the cracks and might not come back when things turn around. And who knows what this “turn around” might look like. The number of students re-enrolling in the Fall might drop tremendously, shrinking the number of teachers needed in the Fall. Just after the work-from-home order was given, I was lucky enough to secure a position teaching at a Middle School close to my place beginning in the Fall, but things are far from certain given that we have no idea what enrollment is going to be in the Fall or what challenges we’ll face when we’re hit by COVID-19’s second wave. Given my health history, I’m certainly not in a position to not take precautions and be very concerned about getting back into the business of working in close proximity with hundreds of potential walking germ factories. I hope they like me in my fashionable face-masks.
2020-03-24 Josh Metz – empty-vegas
Learning from Home – robots
2020-03-03 Reading Week – funny Hair Day
2020-04-28 n95-busted
2002-06-04 Twain computer lab teacher
2020-04-07 costco with bandana
I have been working in technology (officially) for over 40-years, since I hired on with the phone company in 1979, so I’ve made a study of the constant change brought about by the continuing changes in technology. I’m used to this and I’m always looking for benefits and challenges. But most of my fellow teachers do not easily welcome change. One year after one of my schools became a video-journalism magnet school, ten of the thirty teachers left that school for other teaching positions at other schools. Hell, my change of schools has nothing to do with the current COVID-19 challenge, but it certainly doesn’t help with the difficulty of starting something new at a new school, new grade levels, new administration and the possibility of the second wave of COVID-19 rearing its ugly head just after the beginning of the new school year. So, yeah, I’m okay with the computer stuff/working from home stuff, but I worry that the world outside my door will never be the same again and I am getting a bit old for this shit. Really. I appreciate a good challenge, but this is getting ridiculous.
pacbell by joe bustillos
1979-1995 The Pacific Bell Years-04-ANHM01 ITT T-CXR equipment
Kaypro II
Non-Linear Systems Inc., Kaypro 10
2001-04-15 FACT TV screen shots – 12
2020-03-30 teach from home
How are you coping? How do you keep your sanity? I do find myself watching way too many Graham Norton videos on FaceBook when I need a break from other computer things. What’s your guilty pleasure? Please leave a comment or a like where ever you are seeing or hearing this podcast.
Also, if you haven’t done so, please subscribe to either my blog or to my YouTube channel. If you found this on Facebook and clicked the link to my blog to watch this, please scroll to the bottom of the blog page and click the “Follow” button. Enter your email address and whenever I post another podcast you’ll get a message in your email. Because I recently moved my videos to a new YouTube account, I have very few subscribers. So, if you’re watching this on YouTube, please feel free to go to my channel, click the subscribe button and the little bell icon, so that you get an email message whenever I post a new video podcast to my channel. Alas, thanks to FaceBook’s precious little algorithm, it’s not enough to be my friend on FaceBook, if you are interested in getting these podcasts when they come out (which I’m working on getting one out every two-weeks)… So, it works better if you either subscribe to my blog or my YouTube channel (or both!). Enjoy.
JBB's Final Thoughts Episode 37: The Endless Assault of “New Normals” JBB's Final Thoughts Episode 37: The Endless Assault of “New Normals” Pondering the challenges of finishing the school year in "work from home" mode and how the world might change "after this is done."
#CCSD 2019-2020 school year#Chromebooks#COVID-19#COVID-19 second wave#digital divide#education#educational technology#educator#featured#JBB&039;s Final Thoughts (podcast)#Jbb’s final thoughts#jbbsfinalthoughts-podcast#joe bustillos video podcast#leaving Fitzgerald#life issues#life&039;s journey#life&039;s passions#life&039;s plan#online teaching#post-COVID-19#remote learning#teaching#unanticipated changes#working from home
0 notes
Text
Education in the Age of the Coronavirus Pandemic

School districts scramble to switch to online learning
On March 17 the state education department said all public schools “should immediately begin developing a plan for distance learning.”
Almost two weeks later, many San Diego County school districts said they’re getting ready to officially make the switch to online learning in coming weeks.
But several say they are still trying to figure out the details, such as whether online work will count toward students’ grades or how to make sure education is provided equitably to all students.
More than 6 million California students are out of school because schools closed two weeks ago to accommodate social distancing. Gov. Gavin Newsom has said he doesn’t think regular, in-person schooling will resume this school year.
School districts are giving students Chromebooks, WiFi hotspots and paper packets of schoolwork while some are preparing to train teachers for online learning. Some teachers have started holding virtual lessons or check-ins with students on their own.
Retrofitting classroom lessons to an online program is an exercise in improvisation, they say.
“What you’re seeing, for us and every other school district, is we’re building the plane as it’s flying,” said Ben Churchill, Carlsbad Unified’s superintendent.
Carlsbad Unified is posting grade-level assignments online and moving toward a more structured digital learning program after April 13, the end of spring break, he said. It is using some digital tools already employed in classrooms and is giving teachers a “crash course” in distance instruction, he said.
Teachers will push out material on Google Classroom, including videos, reading, writing and math assignments. Families without online access can check out Chromebooks and personal hotspots from the district and sign up for free or low-cost internet service.
“This is not going to be school as we traditionally think about it,” Churchill said. “We’re being clear with our teachers that remote learning does not mean that students or teachers will sit in front of a screen for six hours.”
Many districts are offering optional-only learning activities online. They have not been counting anything for a grade or credit to avoid disadvantaging students who lack a computer or internet access.
California students won’t have to take standardized tests this school year, state officials have promised. But the absence of grades has left many students wondering whether they will be able to graduate or complete the academic year.

San Diego Unified School District Board Member John Lee Evans
San Diego Unified on Tuesday announced its plan to return to official instruction — online — and to grading class assignments beginning on April 27.
But first the district needs three weeks after it returns from spring break to complete teacher training and distribute about 40,000 Chromebooks and WiFi hotspots to students who need them, school officials said.
San Diego Unified School Board Vice President Richard Barrera said he thinks it’s important to return to grading.
If schoolwork is left optional for the rest of the school year, students who have support at home to do schoolwork will learn, but students who lack support or resources will fall behind, he said.
“To do it without grading … is raising the white flag and just saying, ‘We really can’t have any expectations that students are gonna learn during this time,’” Barrera said.
“What I believe you’re also doing is saying, ‘We’re okay with the fact that some students who have more resources are gonna learn while other students won’t.’”
San Diego Unified Superintendent Cindy Marten said traditional requirements for grading, course completion and graduation will have to be revisited because the circumstances of this pandemic are unprecedented.
The state is leaving it up to school districts to decide whether to require graded work from students, said Scott Roark, spokesman for the California Department of Education. The department will soon publish guidance about grading for distance learning.
“Part of that guidance will include an understanding that grading assignments should not be punitive to students during this time,” Roark said.
Sweetwater Union High, San Diego County’s second-largest school district, has not been requiring any schoolwork during the closures. For last week and this week, south county school districts are on spring break, so no in-class work would have been expected anyway.
Sweetwater told families Friday that it will train teachers for two weeks starting April 6 and transition to distance learning in mid-April.
Sweetwater spokesman Manny Rubio said he doesn’t know how the district will start requiring assignments and counting schoolwork for credit once spring break is over.
“What exactly it’s gonna look like, we don’t know,” Rubio said. “As much as we can say, it’s going to look differently.”
Poway Unified, the county’s third largest school district with about 36,000 students, says it will switch to distance learning by April 6 but will not give credit or grades for students’ work to avoid penalizing students.
Escondido Union High School district also “pressed pause” on grades as of March 13 and will move to distance learning starting April 14,said April Moore, assistant superintendent of educational services.
Students who can’t access the distance learning platform won’t be penalized, she said.
“This will allow flexibility for student learning and the opportunity to increase grades,” she said. “Our approach will hold harmless students who may not be able to participate in distance learning.”
The district, which exclusively serves high school students in the Escondido area, also is awaiting state guidance on graduation requirements.
“To the extent that this is a local decision, we are determined to support our students and ensure the (school) closure does not harm them or their outcome of graduation,” she said.
Some districts are farther along.
Oceanside Unified announced it had launched a distance learning website that includes educational resources, homework packets, social-emotional supports and access to digital programs. Parents can also visit select school sites to pick up paper copies of the same lessons posted online for elementary and middle school students, the district stated.
High school students can visit “virtual learning spaces connected with their classes,” the school stated, and students completing online credit recovery programs can continue working online and checking in with their teachers as needed.
The district will begin offering online tutoring in coming weeks.
Students logging in
Some districts and independently-run schools have already been conducting daily, mandatory classes for all their students since last week.
E3 Civic High, an independent charter high school in downtown San Diego, announced Friday March 13 that it would close its school site and it began official online learning the following Monday.
Students are logging onto online school every day at set times between 8:30 a.m. and 3:20 p.m., said Cheryl Ward, CEO of E3 Civic High.
Teachers hold their classes using Zoom, an online video conferencing tool that allows dozens of students to see each others’ faces and the teacher’s screen at the same time.
Students “raise their hand” using a button on Zoom to participate in class discussions. Students use virtual “breakout rooms” for smaller group discussions or group assignments.
School staff called “learning associates” provide tutoring for students with disabilities after school and accompany those students to breakout rooms, Ward said. She said students are continuing to receive special education services, like occupational therapy, via Zoom.
Ward said it hasn’t been difficult to get students to show up to online class every day.
“Funny thing, attendance improved when we went online because the kids don’t have to go anywhere. They just have to get up,” Ward said.
Getting devices was not a problem for E3, which since 2013 has given students MacBook Air laptops. Most of the school’s curriculum is on the online Edgenuity platform; the school also uses online Advanced Placement textbooks.
A school staff member was tasked with making sure each of the school’s 405 students have internet access. For students who lacked internet, the school connected them with free and $10-a-month internet for low-income families being offered by Cox and AT&T.
Among school districts, Vista Unified is launching a learning program called “Vista Virtual School” that offers some elements of conventional schools.
Superintendent Matt Doyle said Vista has invested in educational technology and “personalized learning” systems in recent years, so it is prepared for the transition.
“I think in Vista the change isn’t going to be as dramatic as other districts, because of our innovative approach,” he said.
“Almost all of our classes are comfortable in the Google Classroom environment. I think the struggle that we’ll have is making sure that all of the families have access to wideband internet connectivity.”
The district has more than enough mobile devices, such as iPads and computers, to supply each student with one, he said, and it has 600 mobile hot spots available for families without broadband access, he said.
The district plans to purchase 200 more hot spots and will work with Cox Communications to provide internet access to families that need it.
Some districts have come up other solutions to technology access.
Alpine Union School District set up free internet around its elementary school that anybody can use without a password. Lemon Grove School District is mailing hundreds of Chromebooks to students who need them for optional learning activities.
Even if every student gets technology access, however, it will still be difficult to ensure that every student is learning.
Fernando Hernandez, principal at Perkins Elementary School in Barrio Logan, said his biggest worry isn’t about technology or even whether his students are learning.
“We’re worried about their health more than anything else,” Hernandez said.
More than a third of Perkins’ approximately 460 students are homeless. Hernandez said he worries about students who live in nearby homeless tent camps or shelters, where social distancing is difficult.
Many of his homeless students don’t have computers or internet access. And it was hard to reach some families even before the pandemic arrived, he said. About half of Perkins families don’t have a working email address and some don’t have a working phone number on file.
Taryn Burden, a fifth-grade teacher at Perkins, said only two of her 31 students logged into Prodigy, a math website where she has asked students to do activities during the first week of school closures.
If Perkins does online school, Burden said she worries some students won’t have as much support at home to help them complete the same assignments as everyone else.
“I’m worried about the accountability,” Burden said. *Reposted article from the UT by Kristen Taketa and Deborah Sullivan Brennan of March 29, 2020
0 notes
Text
A brief guide to cybersecurity basics
Last Monday, I got an email from Spotify saying that somebody in Brazil had logged into my account.
I checked. Sure enough: A stranger was using my Spotify to listen to Michael Jackson. I told Spotify to “sign me out everywhere” — but I didn't change my password.
On Wednesday, it happened again. At 2 a.m., I got another email from Spotify. This time, my sneaky Brazilian friend was listening to Prince. And they apparently liked the looks of one of my playlists (“Funk Is Its Own Reward”), because they'd been listening to that too.
I signed out everywhere again, and this time I changed my password. And I made a resolution.
You see, I've done a poor job of implementing modern online security measures. Yes, I have my critical financial accounts locked down with two-factor authentification, etc., but mostly I'm sloppy when it comes to cybersecurity.
For example, I re-use passwords. I still use passwords from thirty years ago for low-security situations (such as signing up for a wine club or a business loyalty program). And while I've begun creating strong (yet easy to remember) passwords for more important accounts, these passwords all follow a pattern and they're not randomized. Worst of all, I maintain a 20-year-old plain text document in which I store all of my sensitive personal information.
This is dumb. Dumb dumb dumb dumb dumb.
I know it's dumb, but I've never bothered to make changes — until now. Now, for a variety of reasons, I feel like it's time for me to make my digital life a little more secure. I spent several hours over the weekend locking things down. Here's how.
A Brief Guide to Cybersecurity
Co-incidentally, the very same day that my Spotify account was being used to stream Prince's greatest hits in Brazil, a Reddit user named /u/ACheetoBandito posted a guide to cybersecurity in /r/fatFIRE. How convenient!
“Cybersecurity is a critical component of financial security, but rarely discussed in personal finance circles,” /u/ACheetoBandito wrote. “Note that cybersecurity practitioners disagree over best practices for personal cybersecurity. This is my perspective, as I have some expertise in the area.”
I won't reproduce the entire post here — you should definitely go read it, if this subject is important to you — but I will list the bullet-point summary along with some of my own thoughts. Our orange-fingered friend recommends that anyone concerned about cybersecurity take the following steps:
Get at least two hardware-based security keys. My pal Robert Farrington (from The College Investor) uses the YubiKey. Google offers its Titan Security Key. (I ordered the YubiKey 5c nano because of its minimal form factor.)
Set up a secret private email account. Your private email address should not be linked in any way to your public email, and the address should be given to no one. (I already have many public email accounts, but I didn't have a private address. I do now.)
Turn on Advanced Protection for both your public and private gmail accounts. Advanced Protection is a free security add-on from Google. Link this to the security keys you acquired in step one. (I haven't set this up because my security keys won't arrive until this afternoon.)
Set up a password manager. Which password manager you choose is up to you. The key is to pick one that you'll use. It's best if this app supports your new security keys for authentification. (I'll cover a few options in the next section of this article.)
Generate new passwords for all accounts. Manually create memorable passwords for your email addresses, your computers (and mobile devices), and for the password manager itself. All other passwords should be strong passwords generated randomly by the password manager.
Associate critical accounts with your new private email address. This will include financial accounts, such as your banks, brokerages, and credit cards. But it could include other accounts too. (I'll use my private email address for core services related to this website, for instance.)
Turn on added security measures for all accounts. Available features will vary from provider to provider, but generally speaking you should be able to activate two-factor authentification (with the security keys, whenever possible) and login alerts.
Turn on text/email alerts for financial accounts. You may also want to turn on alerts for changes to your credit score and/or credit report.
Activate security measures on your mobile devices. Your phone should be locked by a strong authorization measure. And each of your individual financial apps should be locked down with a password and any other possible security measures.
/u/ACheetoBandito recommends some additional, optional security measures. (And that entire Reddit discussion thread is filled with great security tips.)
You might want to freeze your credit (although, if you do, remember that you'll occasionally need to un-freeze your credit to make financial transactions). Some folks will want to encrypt their phones and hard drives. And if you're very concerned about security, purchase a cheap Chromebook and use this as the only device on which you perform financial transactions. (Believe it or not, I'm taking this last optional step. It makes sense to me — and it may be a chance for me to move beyond Quicken.)
Exploring the Best Password Managers
Okay, great! I've ordered a new $150 Chromebook and two hardware-based security keys. I've set up a brand-new, top-secret email address, which I'll connect to any account that needs added security. But I still haven't tackled the weakest point in the process: my text document filled with passwords.
Part of the problem is complacency. My system is simple and I like it. But another part of the problem is analysis paralysis. There are a lot of password managers out there, and I have no idea how to differentiate between them, to figure out which one is right for me and my needs.
For help, I asked my Facebook friends to list the best password managers. I downloaded and installed each of their suggestions, then I jotted down some initial impressions.
LastPass: 16 votes (2 from tech nerds) — LastPass was by far the most popular password manager among my Facebook friends. People love it. I installed it and poked around, and it seems…okay. The interface is a little clunky and the feature set seems adequate (but not robust). The app uses the easy-to-understand “vault” metaphor, which I like. LastPass is free (with premium options available for added cost).
1Password: 7 votes (4 from tech nerds) — This app has similar features to Bitwarden or LastPass. The interface is nice enough, and it seems to provide security alerts. 1Password costs $36/year.
Bitwarden: 4 votes (2 from tech nerds) — Bitwarden has a simple, easy-to-understand interface. It uses the same “vault” metaphor that products like LastPass and 1Password use. It's a strong contender to become the tool I use. Bitwarden is free. For $10 per year, you can add premium security features.
KeePass: 2 votes — KeePass is a free Open Source password manager. There are KeePass installs available for all major computer and mobile operating systems. If you're a Linux nut (or an Open Source advocate), this might be a good choice. I don't like its limited functionality and its terrible interface. KeePass is free.
Dashlane: 2 votes — Of all the password managers I looked at, Dashlane has the nicest interface and the most features. Like many of these tools, it uses the “vault” metaphor, but it allows you to store more things in this vault than other tools do. (You can store ID info — driver license, passport — for instance. There's also a spot to store receipts.) Dashlane has a free basic option but most folks will want the $60/year premium option. (There's also a $120/year option that includes credit monitoring and ID theft insurance.)
Blur: 1 vote — Blur is different than most password managers. It quite literally tries to blur your online identity. It prevents web browsers from tracking you, masks email addresses and credit cards and phone numbers, and (or course) manages passwords. I want some features that Blur doesn't have — and don't want some of the features it does have. Blur costs a minimum of $39/year but that price can become much higher.
Apple Keychain: 1 vote — Keychain has been Apple's built-in password manager since 1999. As such, it's freely available on Apple devices. Most Mac and iOS folks use Keychain without even realizing it. It's not really robust enough to do anything other than store passwords, so I didn't give it serious consideration. Keychain is free and comes installed on Apple products.
Let me be clear: I made only a cursory examination of these password managers. I didn't dive deep. If I tried to compare every feature of every password manager, I'd never choose. I'd get locked into analysis paralysis again. So, I gave each a quick once-over and made a decision based on gut and intuition.
Of these tools, two stood out: Bitwarden and Dashlane. Both sport nice interfaces and plenty of features. Both tools offer free versions, but I'd want to upgrade to a paid premium plan in order to gain access to two-factor authentification (using my new hardware security keys) and security monitoring. This is where Bitwarden has a big advantage. It's only $10 per year. To get the same features, Dashlane is $60/year.
But here's the thing.
I started actually using both of these tools at the same time, entering my website passwords one by one. I stopped after entering ten sites into each. It was clear that I vastly preferred using Dashlane to Bitwarden. It just works in a way that makes sense to me. (Your experience might be different.) So, for a little while at least, I'm going to use Dashlane as my password manager.
The Problem with Passwords
My primary motive for using a password manager is to get my sensitive information out of a plain text document and into something more secure. But I have a secondary motive: I want to improve the strength of my passwords.
When I started using the internet — back in the 1980s, before the advent of the World Wide Web — I didn't spare a thought for password strength. The first password I created (in 1989) was simply the name of my friend who let me use his computer to access the local Bulletin Board Systems. I used that password for years on everything from email accounts to bank sites. I still consider it my “low security” password for things that aren't critical.
I have maybe eight or ten passwords like this: short, simple passwords that I've used in dozens of locations. For the past five years, I've tried to move to unique passwords for each site, passwords that follow a pattern. While these are an improvement, they're still not great. Like I say, they follow a pattern. And while they contain letters, numbers, and symbols, they're all relatively short.
As you might expect, my sloppy password protocol has created something of a security nightmare. Here's a screenshot from the Google Password Checkup tool for one of my accounts.
I get similar results for all of my Google accounts. Yikes.
Plus, there's the problem of account sharing.
Kim and I share a Netflix account. And an Amazon account. And a Hulu account. And an iTunes account. In fact, we probably share twenty or thirty accounts. She and I use the same easy-to-remember password for all of these sign-ins. While none of these accounts are super sensitive, what we're doing is still a poor idea.
So, I want to begin moving toward more secure passwords — even for the accounts I share with Kim.
The good news is that most password managers — including Dashlane — will auto-generate randomized passwords for you. Or I could try something similar to the idea suggested in this XKCD comic:
The trouble, of course, is that each place has different requirements for passwords. Some require numbers. Some require symbols. Some say no symbols. And so on. I don't know of any sites that would let me use four random common words for a password!
For now, I'm going to take a three-pronged approach:
I'll manually create long (but memorable) passwords for my most critical accounts. This is the XKCD method.
For the accounts I share with Kim — Netflix, etcetera — I'll create new, memorable passwords that follow a pattern.
For everything else, I'll let my password manager generate random passwords.
This seems like a good balance between usability and security. Every password will be different. Only the ones I share with Kim will be short; all others will be long. And most of my new passwords will be random gibberish.
Final Thoughts on Cybersecurity
In this short video from Tech Insider, a former National Security Agency security expert shares his top five tips for protecting yourself online.
youtube
You'll note that these are similar to the Reddit cybersecurity guide I posted earlier in this article. Here are the steps he says to take to keep yourself safe:
Enable two-factor authentification whenever possible.
Don't use the same password everywhere.
Keep your operating system (and software) up to date.
Be careful with what you post to social media.
Do not share personal information unless you're certain you're dealing with a trusted company or person.
I won't pretend that the steps I'm taking will protect me completely. But my new system is certainly an upgrade from what I've been doing for the past 20+ years — which was, as I've mentioned, dumb dumb dumb.
And I have to confess: I like the idea of restricting my online financial life to one computer — the new $150 Chromebook. I'm not sure if this is actually doable, but I'm going to give it a go. If this works, then I may see if I can find a money-management tool that I like for the machine. Maybe then I can finally leave Quicken 2007 for Mac behind!
What have I missed? What steps have you taken to protect your online accounts? Which do you feel is the best password manager? How do you create memorable, secure passwords? How do you handle shared accounts? Help other GRS readers — and me! — develop better online security practices.
from Finance https://www.getrichslowly.org/cybersecurity-basics/ via http://www.rssmix.com/
0 notes
Text
Educator Perspectives: Best Practices and Planning for Effective Implementations
This article features contributions from the MIND Success Team, which includes Danette Morse, Education Success Manager, and Huey Pham, Education Success Manager.
In each installment of our Educator Perspectives series, we interview teachers and administrators across the country who are engaging, motivating, and challenging their students in unique ways. We share their obstacles, successes, and strategies in order to build a community better prepared to mathematically equip all students.
Sonora Elementary School is a beautiful, single-story brick building in Springdale, Arkansas. Surrounded by grassy stretches of land and Sonora Middle School, Sonora Elementary was established in 2011 and serves pre-kindergarten through fifth grade.
Dr. Regina Stewman has been the Principal at Sonora Elementary School since the doors opened. With over 29 years in education, Regina’s extensive experience spans state lines and leadership roles, like principal, assistant principal, third grade teacher, and kindergarten teacher.
Sonora Elementary School has used ST Math® since August 2015 and is now up to 31 classes registered with 610 active students. Dr. Stewman first discovered ST Math the way most of us are introduced to new things—through a friend.
“I heard about it from a peer in the district. I was intrigued that it was created by somebody who had dyslexia and didn’t want deficits in language or reading to hinder students from excelling in the content area of math. That piqued my interest because we were continually searching for strategies to serve our ESL population.”
Her peer, Dr. Anette Freeman at George Elementary, had tried ST Math and her teachers loved it for a number of reasons, including the way it helped students focus on math by removing language barriers. “At the time, our district was training teachers in Cognitively Guided Instruction. It [ST Math] really aligned with our curriculum, adding an additional scaffold allowing personalized instruction for each student to move at their own pace.”
Research shows that an early start with ST Math helps schools reach their math goals. Because of this and the success that Sonora Elementary School has had, Dr. Stewman shares her journey and best implementation practices to help other administrators start their year off strong with ST Math.
Do Things “With” Teachers, Not “To” Teachers
Preparation for ST Math looks different each year for Regina and her team. "I’m a big believer in—I can’t do things to the teachers. I need to do things with the teachers."
When Regina decided she wanted to implement ST Math, she shared her innovation with the assistant principal and teachers. “I said, ‘I want to do this, but I want to hear your insight.’ You want 80-85 % of your staff on board for something like this to be successful.”
Dr. Regina Stewman and her team moved forward—implementing ST Math with fidelity. From the beginning, Regina and her leadership team were very involved, ensuring that as they learned together, they remained on the same page and encouraged their teachers to embrace the program and implementation.
“I believe it’s the teachers, not a program, which makes a difference. I always tell them, they are the difference-makers with this program. It won’t work without them. They came to me and said, ‘We just thought this was another thing you were adding to our plates.’”
It’s the teachers that make a difference. They are the difference-makers. It won’t work without them.
At the end of the year, the teachers saw why Regina felt strongly about implementing ST Math. "They felt that it was good for students and positively impacted student learning. Bottom line, they came to me in the end and said, ‘We’re glad we did this.’"
Trust is Important
Trust is a significant factor in not only building a strong relationship with teachers, but also helping them believe in the mission. “There is always going to be a fine line between administrator and teacher. We do our best to build up trust and put it in place, but I believe there’s always going to be, ‘Am I going to be in trouble? This is my evaluator.’”
What helped was making her intentions and the intentions of her leadership team clear and unified. “Opening the building with staff that we (with Mrs. Hennarichs, assistant principal) had hand-picked allowed us to find individuals with similar philosophies. Then, we worked to build a school family with every decision based on what was best for our students. Everything we did was to help our school. Decisions were made with the interest of the students first—not based on what was easier for staff.”
There was a year in the beginning of ST Math where Regina had medical issues. Even during that difficult time, her team knew everything she did was done with the kids in mind, and what was best for them.
A unified message from the district level translates to what they do within the walls of Sonora Elementary School. A consistent message all the way down is critical.
“Our district saying is, ‘All means all.’ Whether they come from across the road or across the ocean. That comes from Dr. Jim Rollins, our Superintendent. We have kids from all over. We have a high Marshallese population. They’re all ours. No matter how far they traveled to get here.”
Identify and Empower Your ST Math Champions
To reinforce her involvement, in the first couple of years of ST Math, Regina reviewed the weekly reports and shared them with the whole faculty. She would point out trends and send helpful reminders, like delete (or make inactive) students from your roster as they move. Regina also celebrated wins.
I’d say, ‘Look at this celebration! Look at how much growth this grade has had this year.’
But she hasn’t continued with that method. In fact, she’s changed how she communicates these important best practices. “Year three, I noticed at each grade level there was a high-flying teacher. I decided instead of sending a weekly report to everyone and to build collective teacher efficacy, I would empower my teacher leaders to lead with their best practices. They are called the ST Math-ers. Each grade level (K-5) and one instructional facilitator are represented in this group.”
Once Regina identifies her ST Math Champions, she empowers them to lead their students and their peers. “Now when I get the weekly reports, I share it with my ST Math-ers.” She still notes trends, updates, or best practices that are timely and that she wants them to stay cognizant of each week.
I’m sharing it with a small group and I’m passing the leadership on to them.
Regina continued, “I’ll say, ‘at one of your team meetings this week, please share this with them [your team].’”
By sending her observations from the weekly ST Math report to leaders in her school, she's seen the leadership flourish. The requests and recommendations go straight to each team. Each team is competitive and wants their kids—their team to do well, so they actively work on improvement.
The weekly SPR report is also used to check-in on teacher readiness. If a teacher hasn't shown any starting activity, there is a process in place. The instructional facilitator will check in to see what they can do to help. “If they’re not implementing the program [ST Math], it is my responsibility to make sure they know how to successfully implement.”
Lead By Example
Regina isn't afraid to get involved and promote peer support. If she identifies a teacher who has areas of opportunity, she loops in her ST Math Champion, or what she calls the ST Math lead teacher in order to use them for support.
Regina has covered classes in order to allow a teacher to observe and watch what the lead teacher does in the classroom. This allows teachers to experience a streamlined ST Math session and come away with new processes or ways to optimize their classroom implementation.
Oftentimes, there are small changes that can be done in order to maximize implementation success with ST Math. “It’s usually little tweaks. It’s the monitoring of it. It may be them not knowing how to help when a student has a flag or a hurdle.”
Engage Students with ST Math Right Away
Regina builds time for ST Math into her teachers’ schedules. “I tell them, there’s no reason, even while you’re teaching rules and procedures to not engage students right away.”
“Outside of kindergarten, our first through fifth graders who have been with us, know the program works. I tell teachers to get them started on the very first week.”
With 610 students using ST Math, most of her students know and are familiar with the program. “For the most part, the kids know the process and the routine.”
The sooner we get kids in a routine, the better it is.
On the 7th day of school, teachers are already using ST Math. “The sooner we get kids in a routine, the better it is. If ST Math is part of your routine, and you’ve got 1:1 Chromebooks or iPads, there’s no reason kids can’t start their password training.”
Give Teachers the Right Tools
Once you get started with ST Math, it's time to keep the momentum going. Along with the encouragement, support, and open communication, Regina provides additional tools to get teachers started. She keeps a Google folder for teachers to access, filled with support documents like her expectations and ST Math resources, like the Getting Started link in ST Math Central or the Self-Guided Courses for anyone new to Sonora.
Among her documents are notes from MIND co-founder, Dr. Matthew Peterson. He once came to her district to speak and Regina was in attendance. “I took notes about his vision, why he did it, his experiences, and some tips. I typed it all up from a few years ago.”
Also documented are notes from what Regina has seen at other schools or pictures of how they’ve celebrated their achievements.
Create a JiJi Culture
Her school also rewards students for their hard work by creating a JiJi Culture. She ordered bulk quantities of stuffed animal penguins as rewards. When students reach 100% completion, they make a big deal about it by sending students to the office to collect their JiJi reward. Every nine weeks, she also gives out certificates.
Regina actively asks her teachers what they want to do to celebrate their student wins. “The teachers are invested now. They’re even doing grade level celebrations in their pods...ST Math is part of our culture now."
MIND would to thank Dr. Regina Stewman and Sonora Elementary School for sharing their wins, best practices, and methodologies with us!
from MIND Research Institute Blog https://ift.tt/2Nc3FvM from Blogger https://ift.tt/2Nc2ex8
0 notes
Text
Teaching Coding to Kids: What Programming Language Should We Use?
One of the most common questions I get from teachers and parents is: What programming language should we use to teach kids to code? Is it important to always start with block-based languages like Scratch? At what age should they transition to text-based languages? And how do I choose between Python, Java or JavaScript?
Having taught coding for almost 10 years to hundreds of students, I often present at conferences or run workshops for teachers new to computer science. Many teachers are trying to build a CS program in their schools for the first time, and it’s understandable why they worry about which programming language to choose. In addition to trying to figure out what’s best for their students, teachers have to strike a balance between what they’re comfortable teaching, and what administrators, parents and students feel they should be learning.
So, is there one “right” coding language to start with?
The coding language is not important. The concepts of programming are!
As you can guess, the answer is: No! What is important is not the language, but how to teach students how to solve a problem with code. Understanding how to create an algorithm (step-by-step instructions) to tackle an assignment, and coming up with the best way to write this in code, is probably the hardest part.
Programming languages come and go—and you will adapt.
Learning the fairly small number of keywords and simple syntax of a specific programming language is easy—a lot easier than learning an actual, spoken human language! By contrast, in order to program independently, one must understand the underlying concepts in programming—variables, lists, conditionals, loops and functions, for example—and then know when, where and how to use them to convert your algorithm into code.
Once a student grasps these concepts and has programmed successfully in one language for some time, it is not that difficult to code in another language. Switching languages is not immediately easy, but it can be done.
However, does that first language change the way you think and code in the future? Is it important to learn the most popular language in industry today?
Programming languages come and go—and you will adapt.
The popularity of programming languages change, and there is no guarantee that what we teach our kids today will be used by the time they enter the job market. My first programming language was Pascal. (Yes, you probably have to look that up now.)
Over the years, I have learned to use different languages on different machines—some too obscure to be mentioned. Over the last 10 years as an educator, I have learned just enough Logo, Scratch, Processing, JavaScript, Arduino and Python to be able to use it as a teaching language in my classes.
Six years ago, I suggested that kids start with Logo, the earliest CS education language, and I still believe it remains a strong option available today. Here’s the most important part: If you can teach kids the basic concepts in programming, and they have spent enough time coding in one language, then they should have developed the fundamentals to switch languages later as needed.
There is another question that often comes up: Do we need to start all kids with block-based languages instead of text-based languages?
Block or text?
I started to use Scratch, perhaps the most popular and kid-friendly block-based language, in a digital design class for sixth graders almost 10 years ago, and I continue to love using it at all grade levels. I am excited to use the new features in Scratch 3.0 just released—especially the extensions to support text-to-speech, and language translation.
Block-based programming takes away so much of the frustration for young and early coders, such as missing a comma or forgetting to close a parenthesis, and leaves more time to focus on understanding concepts. In addition, Scratch’s focus on creativity and easy access to creating graphics, editing sound, sharing and remixing projects makes it a perfect first coding language for all ages. It is positioned as a tool to create art, animations, stories and games and not as a “coding” language, a branding that makes Scratch much more welcoming and less intimidating.
What is important is not the language, but how to teach students how to solve a problem with code.
I have found that after a few years of using Scratch, students want to try text-based coding because they associate it with “grown ups” and the “real” coding that is done in industry. I have also seen that sometimes just a change in language is needed to review concepts like variables and loops.
My middle-school students are willing to put in the extra effort it takes to learn text-based coding; often they slow down in order to be careful with their spelling and syntax as they tackle the challenge of programming in Python, JavaScript, Arduino and Processing. But once students can get past the initial “I have to really watch what I type” part, they often appreciate the flexibility and power of text-based coding, especially when they find how much easier it is to copy, paste, modify and collaborate on text code to create projects.
At the Foothill College KCI Computer Science Crash crash course that I teach each summer, I offer teachers both Scratch and Python and show the same project in both languages. They love seeing the parallels between the two types of languages, and even more if we first start with “pseudocode” or a flowchart—a way to write down the algorithm before writing any code. Here’s what a small project that involves checking a password looks like as a flowchart, in Scratch, and in Python.
Password checker flowchart diagramThe same password checker, in ScratchThe same password checker, in Python
Both teachers and students who had no exposure to block-based programming are easily able to learn Python in my classes, showing that with the right projects, starting with text-based language also works.
What makes any programming language a good language for teaching kids to code? Are there any criteria to help pick a language?
While it may be good to know that teaching coding is more about concepts, and that you do not need to stress about picking the perfect first language, the question remains: What should a language have that will make it a good choice for teaching kids to code? While programming languages are often evaluated in numbers of ways—on speed, applications, libraries available, industry support—here are some important criteria I consider.
Does it have a strong community of educators?
One of the reasons I always point to Scratch and Python is their access to a network of educators using these languages in their classrooms. They have such large communities behind them because they have always been free, open and welcome to a wide range of users from across the world. Having a large community means you can find more resources, such as projects, lesson plans, tutorials, videos and books dedicated to teaching the language in the classroom. It’s also likely that you can walk into an education conference and find a session giving you tips.
...teaching good programming habits trumps teaching a popular language.
Is it easy to pick up?
There are many text-based languages to choose from—some more popular today in the tech industry than others, some with specific features that make them good for creating a particular project. While many high-school students may have to ultimately learn Java for an AP Computer Science course, it is not necessarily the easiest language to start with. Python is by far easier and has been gaining popularity in education because it is so simple. After three years of using Python for a computer science elective class, I am constantly surprised at how little it takes to get something done, and how quickly my middle-school students learn to code in Python. Inspired by how well Python works in teaching coding to kids, I spent time writing a book about it.
What is the design philosophy behind it? Was it designed for this age group?
It is important to offer tools that are age-appropriate, and programming languages can hide or showcase features based on the target age group. Scratch, rooted in the philosophy of using code for creative expression, deliberately simplifies some constructs one may expect to see in a coding language. Scratch Jr. is designed for kids who are still learning to read, and has no variables or conditionals, which may be too confusing at their age. Python offers extensions to support many types of projects, but these are available as modules that have to be explicitly added, so you do not need to see them until they are needed. Languages for older students working on complex programs must have support for debugging, a fundamental skill. If teaching “object-oriented” programming is critical, then using Java is not a bad choice.
How easy is it to install, and does it run across platforms?
These are things to keep in mind, especially if it is important that students continue to code at home. Some only work in specific environments, like Apple’s Swift coding language. If students are working on Chromebooks, then having a stable, browser-based tool is critical. Another thing to consider: Is the language really available for free so every student can use it at home, or are there hidden extensions only available for a fee?
How easy is it to share projects with the community?
One of the fundamental ideas behind Scratch has been the community, and letting kids share and learn from each other. That community is also useful for teachers as well. However, sharing also requires planning: when and how much you want students to share, comment, reuse and repurpose others’ projects. While JavaScript may be frowned upon as a first text-based language to learn and is not as easy as Python, it does have the advantage that it just runs on the web. Showcasing projects is as simple as posting them on a school web server.
There are many other considerations when choosing a language. What kind of projects are possible? Different languages have supports and extensions for different types of projects; for example, Processing and P5.js make it easier to do media projects and create art and animations. Python makes writing complex data analysis and even machine-learning projects possible. Teachers may also want strong classroom tools to manage assignments and grading, especially for group projects.
One of the most common questions is: “Is this language popular today?” Popularity can certainly shape the choice of programming language to encourage students to sign up for a class. It’s understandable that parents want educators to teach what is marketable for jobs. However, teaching good programming habits trumps teaching a popular language.
While we can stress about finding the “perfect” programming language to start, let us not forget that the ultimate goal is to let students explore fundamental programming concepts. They may never choose to program after your class, and the language you teach may become obsolete as they get older. What is important is that teaching coding will help students understand how computers solve problems, acquire critical thinking skills—and hopefully learn just how much fun it is to make stuff with code.
Teaching Coding to Kids: What Programming Language Should We Use? published first on https://medium.com/@GetNewDLBusiness
0 notes
Text
WHERE ARE MY CHILDREN AND GRANDCHILDREN!!

I have a plan funded already for Wall which is a good deal for both: Mexico and USA and which would have prevented Gov shutdown, can immediately end Government shutdown because it does not need funding from Dems., but after Justice for me, for us - the Results due to me in 1991 - Healthy Genetically My Own and TS UK, the man on picture with me, Children are born by me...
The Wall will not solve the World’s Foremost Jewish Problem - see above.
My First Job, My Purpose in Life, my fundamental Human Right, my fundamental Constitutional Right is to have 500 Healthy Children first, married to the man on picture with me, due to me in 1991-92, immediately now. I need Miracles stolen from me for decades to come True now - I don't have second life! After it Professional Medical Work as physician or resercher. It is illegal and wrongful I to be forced into slavery, or to do any other “job”. Please STOP White Genocide, STOP Grand Larcenies: disclose Neubarth’s illness Schizophrenia which was never disclosed to me, reissue with the current date our RICO STOLEN, never considered, never used by any court original documents and enforce them: reverse all, arrest all,
Please reissue with the current date, to include all my Family, and with No ending event for the next 200000 Years Mandatory Restitution, Restoration, Indemnification and all costs shifting to defendants, our STOLEN by US Consul E Andrew Walton original documents in Sofia Bulgaria, 1991, thus never considered never used by any court, which are crucial for me in USA and caused RICO International Kidnapping, enslavement, barbaric White Genocide, after barbaric murders of both of our parents in Bulgaria, completely deprived from any Life: Federal Contract under Sec 213A of the INA Act. and Marriage Documents merged into it, inseparable from it, give me a copy as required, and start their enforcement by: Reversal of all, $$Trillions Refunds, Recovery and Return of all my Trillion Pieces Federally Protected Personal Property, Thousands Paintings, Sacred Heritage from our Ancestors to our Children their descendants, confiscation of all, Arrests of all....
Arrest & confiscate Lying Jewish Libraries for RICO ODOR SCHEMES ban after Assange RT, for collection of debt: $500 Billion & $40 Trillion per item and per minute delay, restore me in my House, give free replacements: Housing, Computer, Phone, Cars until restored inside my House. 1/14/2019
Facts: *My Original Documents were STOLEN, *Nothing was filed in the Wrong Error state Stockton court, *are still not filed in Error state Stockton court, *our “dissolution” in order to deceive case in it is *Factually VOID, is also factually *RICO, Grand Larcenies and barbaric White Genocide case, *was declared as such by me in US Nebraska District courts and 8th Cir. Courts of Appeal
Pressing Emergency: Please give me required by federal law all free replacements to Use 24/7 until ours are recovered & returned to us: Housing, Computer, Phone, Car, restore me inside my Federally Protected House above, until then Please confiscate all Buildings at University of the Pacific, Arrest all, order University of the Pacific Library which is the only appropriate place for me to Use for legal work they caused https://www.pacific.edu/university-libraries.htm to let me use the Library (tomorrow Saturday 11/17/2018) (the same day you receive this message), tech support to give me Computer login password now had to be given on the same date which is Four Years ago: 10/27/2018, immediately now.
Deliberate delay by RTD Stockton: “You have to wait for the next one”, 50 or more hours per month wasted on a bus, and 30 Years wasted on No Car will be charged at the same rate to RTD separately, and to each of the other defendants separately.
@realDonaldTrump @POTUS Pressing Emergency: Please open Computer rooms in the center of city 24/7 with Robots Security only, cannot be closed on weekends or Holidays. Jews and anti-Whites must not have any access to anything public, have to be arrested for collection of $Trillion Debt, Grand Larcenies, White Genocide for centuries now.
Pressing Emergency: Troke city public library in Stockton, CA, the only place with Computer to work to recover& return my federally protected but very brutally and without any warning to me STOLEN, Looted, destroyed 3 Houses, Trillion Pieces Protected Personal Property 10/27/2014-Present, where I was not banned from visiting to work on public Computer, suddenly without any warning removed the manager man Bill and the White Security man yesterday 11/15/2018, and a Jewish woman Alex with Black Security woman said she is the new Manager and she is banning me from visiting the Library and Computer tomorrow Saturday, 11/17, 2018 for the Wheelchair and several bags I have to bring with me, have No other place to leave after required by 8 C.F.R. and INA Act all free replacements to Use 24/7 were denied by all Corrupt Jewish controlled Local government agencies who commuted the crimes since 1991 and had to be arrested in 1991 - Thousands of federal, state and International Laws violation and nobody cares about it to arrest all. Please send the Army to arrest them - they want to STEAL my Federally Protected Personal Property again knowing that I do not have any other place to leave it. I cannot be out of my OWN Federally Protected House for a second - see our STOLEN and Never used Federal Contract! Police told me to take all bags with me because they started to openly STEAL my bags when the Jews placed black city Mayor, if left them for 5 Minutes in the grocery store, knew who stole them but did not order them to Return them, Until all required replacements are given to me to Use I have to take them with me. Please tell Local criminals, all city public libraries with Computers: Chavez, Troke now, University of the Pacific, that the Federal Law: 8 C.F.R. and our Federal Contract under Sec. 213A of INA Act requiring I to be inside my Federally Protected 3 Houses at all times, Trillion Pieces Personal Property to be recovered and returned to me/us are controlling in our Exceptional since 1991 case and has to be enforced first - please enforce them I to be inside my own House, give all required free replacements to Use 24/7: Computer, Housing, Car immediately Today 11/16/2018, before any local wrongful, illegal, deliberate delay “policies” to apply to me. Please order University of the Pacific, UOP, https://www.pacific.edu/university-libraries.htm to let me to use the Library tomorrow Saturday, 11/17/2018, tech support to give me Computer login password, to check out Chromebook to Use 24/7, until $Trillions STOLEN are refunded and I buy Computer. I am illegally and wrongfully banned, my OLLI Membership at UOP was revoked December 2015 for no reason at all after the case went to Jewish controlled Corrupt Bribed 8th Circuit Court of Appeals who illegally and wrongfully dismiss/deny, were added as defendants - I wait Separate Pro- White courts who will sentence all to Death, please arrest all and confiscate the entire cities Stockton and Bakersfield, UOP, all Libraries, for collection of Debt and leverage the Results due to me in 1991: Biologically Genetically mine own and TS from UK 14 Healthy Children born Naturally by me, the rest of the 500 Children by 100% White surrogates. . .
Please Arrest 3 Three violent black men sent everywhere after me for daily assaults, threats - Not to come near me, send me a gun to shoot them, Deport them! How dare you! How dare you!! STAY AWAY FROM ME!
Emergency Requirements: Pursuant to INA Act Sec. 213A of the Act and 8 C.F.R. please give immediately required all free replacements to me to Use 24/7 until mine are returned to me: housing, Computer and Internet, Chromebook to check out from SJDelta College https://www.deltacollege.edu/ , University Library to Use https://www.pacific.edu/university-libraries.html - unban me, Rooms and meals for all of us at https://www.pacific.edu/campus-life/residential-life-and-housing/forms.html, Car, Phone and service, replace broken wheelchair, access to water EMG, Instant Action to shorten the Time as required, reverse all since 1991, confiscate all, recover and return/refund all, all at once due immediately - the only library I am wrongfully forced to use is closed, all Computers have been deliberately broken: MS Word, Paint & none software works.. , my water is stopped extreme tortures and thus have to carry heavy water, trained assassins and black men are sent at me everywhere I go to threaten me...
#SaveMyWhiteChildren I don’t care about other people’s children, and No nephew! Writ Preemptive Prohibition: *a penny to go for somebody else’s child, *to deviate from what is requested and the Results: 14 and 458 Genetically Dr. Kalincheva’s and TS UK Own Healthy Children born by her naturally the rest with prepaid 100 % White Finnish surrogates
Send the Army to Arrest All Corrupt, Jewish controlled all: University, SJ Delta College, Chavez and Troke city libraries, CA Lifeline, SafeLink, criminal RTD bus for collection of Debt for deliberate delays: Federal Law is controlling in our case to recover, return & refund my Federally Protected: 3 Houses, Trillion Pieces Personal Property, Thousands Paintings, 2Cars, $Trillions, I not to need anything public: bus, library, room, meals, to own all at all times..
0 notes
Text
Clash Royale Resources Generator | Get Unlimited Gems! *No Human Verification*
"''Clash Royale Hack Gems Online – 100% Free & Working''' Clash Royale is one of the most top grossing Android and iOS game app till the iOS and Android came into existence and it’s been installed in every second mobile gamer phone. So it won’t be wrong if we say Clash Royale is the only Top Mobile Game since it was launched loaded around the Play Store and iTunes App Store. But in the world of Gaming there is always something you’ll have to pay for it and same like the Clash Of Clans (COC) here at Clash Royale it is Gems and that is the only reason we’re going to introduce you the Clash Royale Hack.
_____________________________________________________________________________ '''Here is Free Gems And Gold Generator''' Click The Link Below and Generate Unlimited Free Gems and Gold : http://supercheats.online/top/clash-royale-hack/
if there any problem you face or if you don't get free Gems and Gold don't hesitate reply comment section below
This Free Cheats Created BY: ClashRoyaleHackTool.Online _____________________________________________________________________________
'''2 More Clash Royale Free Gems and Gold Generator'''
'''Click Here:''' http://clashroyalehacktool.online/ '''Click Here:''' http://supercheats.online/clash-royale.html
As you know earning the gems while playing Clash Royale normally is big pain in ass but there is always some loops in security servers in every online game and that’s what we call the Clash Royale Hack. Being with the help of Clash Royale Cheats Online you will be able to hack the free Clash Royale Gems without wasting your single pennies. So what are you waiting for? Take the advantage of our 100% working Clash Royale Gems Hack Online and load the unlimited Clash Royale Gems within minutes before it’s getting too late. Click on the link below to Hack Clash Royale Gems.
Here we’re giving you opportunity to get millions of Free Clash Royale Gems without spending a single dime on buying it you just need to open your brain. Here we gonna introduce you the best Clash Royale Gems Generator 2017 Online that may can fulfill all your desires. With the help of our Clash Royale Gems Hack Online you will be able to hack the unlimited Gems and Elixir without wasting a single dime all you need to access the Clash Royale Gems Cheats Online on your browser and file just your username and select the amount of Gems and Elixir you want in your Clash Royale account and leave the rest things on the Clash Royale Gems Hack Tool. Within few seconds it’ll load all that selected gems to the given Clash Royale user and right after you can see the same Gems on your Clash Royale game center. Don’t waste your time on reading all shits over various websites and ebooks, just do it and see yourself, just hit the button above and experience the free Clash Royale Gems.
'''About the Clash Royale ( What is this all about )''' Clash Royale is a freemium mobile strategy video game developed and published by Supercell. The game combines elements from collectible card games, tower defense, and multiplayer online battle arena. The game was released globally on March 2, 2016. In Clash Royale, players are ranked by their level, trophies, and/or arena. The maximum level is thirteen, obtained by getting more experience from donating or levelling up cards. There are eleven arenas (excluding training camp) in total, with each arena having a certain trophy limit.
As a free-to-play game, Clash Royale offers players the ability to purchase “gems” in the card shop using currency. “Gems” can be used to start tournaments, enter challenges, and purchase chests, cards, and gold from the shop. When a player wins a multiplayer battle, they will obtain a “chest”, which takes a certain amount of time to open depending on the rarity of the chest. Chests take a certain amount of time to unlock: Silver Chests take 3 hours to unlock, Golden Chests take 8 hours, Giant, Magical and Epic Chests take 12 hours, while Super Magical and Legendary Chests take 24 hours. Gems may be used to speed up unlocking or can be used to purchase a chest. Chests contain cards and gold, and free chests and crown chests will also contain gems.
'''Little More About The Clash Royale Gems Hack Online''' This Clash Royale Gems Hack tool is not just for the single gaming platform it supports all those online platform that have the browser access. That’s actually the main benefit of this Clash Royale Hack Tool, you can access and hack the Clash Royale Gems in any device that have the browser on it. This Clash Royale Generator 2017 supports Microsoft Windows, Mac, Android, iOS, iPhone & iPad. Actually the sense of writing all these platform is to tell you that this Clash Royale gems houwen supports everything that have the browser even on any older nokia phone.
Clash Royale Android Hack is the most wonderful and working online hack tool made till now, if we see the other sites they will give us the downloadable file or the survey site but at the end we got nothing and in any chance if we download the file they provide by mistake and run it to install they trash entire PC or Phone by installing the Virus but here thing is little different, you’ll not get any downloadable file or survey you’ll just direct to the Clash Royale Gems Hack iPhone Online where you can add the gems and elixir on your account by yourself. This Clash Royale Gems Glitch Tool in 100% safe and not any survey scam site and anyone can use it in any online devices.
'''Clash Royale Gems Cheats Online Features'''
* Hack unlimited Clash Royale Gems direct your Clash Royale account. * Hack unlimited Clash Royale Elixir direct to your Clash Royale account. * You can hack the Clash Royale Gems & Elixir for your friends account too if you know their username. * Platforms can be used: PS3, PS4, PS Vita, Xbox One, Xbox 360, Wii, Nintendo 3D Video Game Console, Google Chromebook, PC, iOS and Android. We are also offering web based hence now start the * Online Clash Royale Gemmes Générateur. * Advanced Anti-Ban: With the help of the Clash Royale Online Hack Tool, you will not have to fear of getting banned in-game, as the Stat Hack Tool & Gems Hack have a flawless anti-ban. Which * will help you pass any Anti-Cheat software put in place by the developers or built into the game. 100% Undetectable. * 3 Multi Features: With this Online Clash Royale Cheats you’ll get 3 features under the same tool. One is for Gems Hack another is for Features Hack (see the picture of tool to see about the * features) and Unlockbles. * Up To Dated: Clash Royale Gemmes Cheats / Hack in always to up to dated to keep your game safe
'''How to Hack Clash Royale Gems using the Clash Royale Gems Glicth Tool 2017'''
1. Enter Your Clash Royale Username/Gamertag/ID: If you don’t know your Clash Royale Username please enter your email from which your device is connected with. 2. Select your Platform: Please make sure you selected your device where you playing Clash Royale. We need to know which platform like Android or iOS your account is connected to as the login-servers varies. 3. Select amount of Gems: Select the amount of Gems you want to add on your Clash Royale account. 4. Select amount of Elixir: Select the amount of Elixir you want hack. 5. FINALIZE: You’ve done here, now click on the given “GENERATE” button to start the attempt of Clash Royale Gems Hacking.
'''<u>''Searches related to Clash Royale Hack''</u>'''
clash royale hack clash royale apk hack clash royale clash royale decks clash royale chest cheats clash royale clash royale best deck clash royale supercell game clash royale gemmes clash royale clash royale 2 clash royale arena cheats for clash royale hack clash royal clash royale hacker net generateur clash royale free clash royale gems clash royal cheats hack for clash royale gems for clash royale clash royale mod clash royale hack gems clash of royale hack clash royale online hack clash royale gem generator clash royale generator clash royale gem hack clash royale cheat free gems for clash royale clash royale hack apk clash royale gratis clash royale взлом clash royale chest opener hack para clash royale clash royale arena 5 deck clash royale arena 4 deck clash royale arena 3 deck clash royale minecraft clash royale deck arena 4 clash royale cheats clash royale chest order clash royale apk download apk clash royale clash royale mod apk xmodgames clash royale cheat clash royale clash royale update triche clash royale clash royale glitch clash royale astuce how to hack clash royale gemas clash royale free gems clash royale clash royale hack download clash royale hack no survey clash royale hacked version clash royale hack tool clash royale hackeado clash royale gems clash royale free gems clash royale gem generator no survey download clash of clans mod apk unlimited gems clash royale hack for gems how to hack clash royale android clash royale deck guide clash royale hack gem clash royale hack without human verification clash royale mod apk unlimited gems clash royale hack mod clash royale mod apk revdl clash royale cydia free gems clash royale no survey no password no download clash royale new update clash royale troops gem generator for clash royale clash royale download apk how to cheat in clash royale clash royale super magical chest clash royale mod download clash royale unlimited gems apk clash royale cheats no survey clash royale deutsch clash royale cheats android clash of royale cheat hack clash royale gems hacks für clash royale clash royale generateur gemme illimité clash royal clash of royale gem hack clash royale triche clash royale hack deutsch clash royale gem glitch gemme clash royale free clash royale hacks clash royale juwelen hack clash royale tricks gemmes clash royale gratuit clash royale hack gems free clash royale levels how to get free gems in clash royale clash royale cheat codes hacked version of clash royale clash royale free gems no survey clash royale gold picker clash royale dragon clash royale developer build apk clash royale gemme how to get unlimited gems in clash royale clash royale gemmes gratuit clash royale card hack gemme gratuit clash royal clash royale hack apk file download clash royale gems glitch clash royale trucos clash royale hack apk download modded clash royale clash royale 1.2 3 mod apk gem hack clash royale clash of royal hack hack gems clash royale clash royale gems hack clash royale generator clash royal online hack clash royale android clash royale ios hack clash royale hack free clash royal gems hack clash royale modded server unlimited gems clash royale gems clash royale clash royale hack get unlimited gems gems generator clash royale clash royale hack online clash royale gems free clash royal gems clash royale hack android free gems on clash royale clash royale mod apk download clash royale gems generator clash royale hack ios clash royale unlimited gems clash royale hack no human verification free gems in clash royale clash royale hack no verification clash royale tools clash royale free gems hack clash royale apk mod unlimited gems generator clash royale clash royale hack server download clash royale hack clash royale hack generator gem hack for clash royale clash royale hack app clash royale elixir hack hacked clash royale clash of clans modded apk 6.186 3 unlimited gems cheat clash royale android clashroyalemodapk2016 xyz cheat in clash royale hack clash of royale clash royale chest hack how to enter cheat codes in clash royale clash royale hack 2016 clash royale hack kostenlos gemas clash royale hack clash royale clan clash royale gem cheat clash royale hack me clash royale hack gems generator clash royale mod apk latest clash royale unlimited gems apk file free download clash royale hack download ios clash royale hack easy free clash royale gems no survey or verification clash royal hack download where to enter cheat codes for clash of clans clash royale hack gemmes download hack clash royale clash royale mod aptoide clash royale hack tool download clash royale hack no verification or survey clash royale hack no human verification or survey clash royale mod apk download android hack gem clash royale clash royale hack free gems clash royale unlimited gems apk download free clash royale free hack clash royale hack tool online free clash royale hack clash royale hack no offer clash royal hack online hack in clash royale clash royale hack unlimited gems free gems hack clash royale clash royale cheat gems hack on clash royale gems clash royale hack clash royale hack generator free gems clash of royale clash royale mod unlimited gems clash royale real hack clash royale gems cheat free clash of clans gems no survey or download hacknosurvey mobi clash royale cheat codes for clash of clans without jailbreak clash of clans free gems no verification no survey clash royale hack 2017 clash royale hack without human verification and survey free gems com clash royale hack free clash royal gems clash royale cheat android clash royale android hack clash of royale free gems hack the clash royale clash royale for android royale clash hack clash royale gold hack free gems clash royale android clash royale unlimited gems hack clash royale easy hack clash royale hack gems android unlimited clash royale gems clash royale hack for android free gem generator clash royale clash royale free gems no hack clash of royale hack tool clash royale hack gems online clash royale hack cheats hacks for clash of royale free hack for clash royale android clash royale hack clash royale hack gold clash of royale hack android clash royale hack gems and gold clash royale ultimate hack tool download no survey no survey clash royale hack clash royale hack get unlimited hack tool clash royale clash royale gem hack android working clash royale hack royale gems hack hack to clash royale hack online clash royale free clash royale gems no survey or download free gems clash royale hack hack clash royale online clash royale hack pc clash royale gems hack android clash royale hack for ios free gold clash royale easy clash royale hack clash of clans hack without human verification and survey clash royale mod apk onhax clash royale cheat codes iphone clash royale hack tool apk download cheat codes for clash of clans on android hack no survey mobile clash royale cheat codes for clash of clans for ipad hacknoservey rexdl clash royale cheat codes for clash royale on android <spoil>ftp://%27/</spoil>"
0 notes
Text
Six apps and trackers to find your lost gadgets
New Post has been published on https://nexcraft.co/six-apps-and-trackers-to-find-your-lost-gadgets/
Six apps and trackers to find your lost gadgets
Finding yourself out and about without your smartphone can make you feel naked. We rely on these devices so much that losing them creates a huge problem, preventing you from messaging friends for aid or mapping your way back home.
Losing any similarly essential device, like your laptop, creates an equally huge headache. To rediscover these lost gadgets, we’ve collected tech that finds your tech. These six apps and trackers can plot your devices on a map, force them to make audible sounds, and perform other tricks to help you reunite.
For Apple: Find My iPhone/iPad/Mac
Apple wants you to keep its devices safe, and to that end, it built a phone and tablet tracker into iOS and a laptop finder into macOS. Enable the feature on all your Apple hardware, and you’ll be able to see the current location of any device on a map.
To set it up on an iPhone or iPad, open Settings and tap your Apple ID at the top. Then pick your device and select Find My iPhone (or Find My iPad) to switch on the feature. On a computer, open System Preferences and click iCloud. Then tick the Find My Mac box. During this process, Apple may prompt you to sign in with your Apple ID credentials, so make sure you have your password close to hand.
Once you’ve enabled the tracker, you can forget about it until you need it. If you do lose a device, grab your remaining machine(s) and open the appropriate app: Find My iPhone on a phone, Find My iPad on a tablet, or the iCloud web app in any browser window. Sign in, click the All Devices menu, and pick a device to see its location on a map. Within this app, you can also select a device and prompt it to make a sound, lock itself, or erase all its data.
The lock option is particularly useful because you can make the lost device display a custom message. For example, if you lose your iPhone, make the gadget share a message requesting its safe return and providing an email address where finders can contact you. And to prevent those finders from snooping further, locking the screen will protect your data.
For Android: Find My Device
Like Apple, Google has included device-locating tool, called Find My Device, on Android. To enable it, open Settings and tap Security & location. Turn the feature on to start tracking your phone or tablet. Then install the Find My Device app on a backup phone or tablet.
To see where your gadget is, you have a few options. Open the app on your backup device, visit the Find My Device web portal, or just sign into your Google account and then type “where’s my device?” into the search engine. As with the Apple service, you can make the lost machine play a sound (even when it’s in silent mode), lock the device while its screen displays a message, or completely erase your information. Check out a map to view its last known location, battery level, and even the name of the Wi-Fi network it’s currently connected to. Based on this information, you can decide whether it’s gone forever or still can be retrieved.
Unfortunately, Google doesn’t offer similar protections for Chromebooks—at least for the time being. So if you lose one of these Chrome OS-powered laptops, you won’t be able to find it through Google. However, keep reading to learn about a third-party app that may be able to do the job.
For Samsung: Find My Mobile
Samsung owners can use the aforementioned Google tracker or Samsung’s built-in Find My Mobile tool, which works very similarly. To access it, first set up a password-protected Samsung account.
Next, enable the tracker by opening Settings, tapping Lock screen and security, and choosing Find My Mobile. On this menu, make sure to toggle the Remote controls switch to On so that you can operate your phone or tablet from another device.
If your gadget goes missing, head to the Find My Mobile website and sign in with your Samsung credentials. Here, you can check out the last known location of your phone or tablet on a map. Like with the other tracker apps, you can ring your device even if it’s in quiet mode, lock it so nobody else will be able to access it, and wipe it remotely if you don’t think you’re going to get it back.
From the same website, you can perform other useful tasks, such as unlocking a device whose PIN you’ve forgotten and backing up data. Just pick the relevant option from the list on the right-hand side of the site.
For any operating system: Prey
Because Prey works with multiple operating systems, it can cover iOS, macOS, Android, Samsung, and Windows devices. Plus, it offers a few handy features its competitors don’t, such as the ability to snap a picture with the device’s camera or view its screen activity, potentially allowing you to deduce a thief’s identity.
Like you do with the other tools mentioned above, download the Prey app onto your device of choice and create an account. Once you enable it, the Prey website can show a device’s location on a map, as well as its current signal strength. From the site, you can also remotely lock your device, wipe its data, ring an alarm, and, while it remains online, even extract information like the aforementioned photos and screenshots.
Another bonus feature you get with the phone version of Prey (for Android and iOS) is a control zone. This sends you an alert whenever your phone or tablet enters or leaves a particular area, such as your home or your office.
The free version of Prey can track up to three devices and enable one control zone. You’ll have to pay $5 and up each month to add more devices, set extra control zones, and gain the ability to wipe a device remotely.
Physical trackers: Tile
Software isn’t the only way to track your gadgets. You can attach a compact Tile Tracker to pretty much anything, although this method works best with items that you’ve lost in your own home: The physical trackers communicate with an accompanying app (for Android and iOS) via Bluetooth, so the range only stretches up to 200 feet.
When something goes missing, you simply open the Tile app and see where each tag’s last reported location was. This should give you somewhere to start looking. You can also make a Tile Tracker emit an audible sound, either through the app or by pressing another Tracker that’s been paired with the lost one. If you lose your phone, you can make the tracker ring even if it the device is on silent. Finally, downloading the app onto your phone or tablet turns the device into a virtual Tile. And because your device has GPS as well as Bluetooth, the Tile app will let you locate it even when it’s further away.
Tile offers its trackers in four sizes and styles,which also vary in range, maximum volume, and level of waterproofing. Prices start at $25 for a single Tile, with discounts if you buy the trackers in packs of four or eight.
Physical trackers: TrackR
Tile isn’t the only compact, Bluetooth-enabled tracker out there. The TrackR devices do more or less the same job with a slightly different aesthetic styling. While a TrackR’s range is shorter than a Tile’s (only 100 feet to Tile’s 200), fans of smart speakers might prefer TrackR because it offers an Alexa skill that lets you hunt down your lost gadgets through your Amazon Echo.
Like a Tile, a TrackR attaches to just about any gadget and reports its location over Bluetooth to the TrackR app (for Android and iOS). Through the app, you can also force a TrackR or a connected phone to audibly ring. While the range is limited, if the TrackR attached to your tablet or laptop gets too far away, then it will automatically log the last known location in the app, so you know whether to start looking at home or in the office.
TrackR currently sells two models, the Pixel and the Bravo. This Pixel is smaller and made of plastic rather than the Bravo’s brushed aluminum. Prices start at $25 to $30 for one Bravo and $21 to $25 for one Pixel, but you can save more if you purchase the devices in packs of five, eight, or 12.
Written By David Nield
0 notes
Text
OneNote vs. Evernote vs. Dropbox Paper vs. Google Docs
OneNote, Evernote, Dropbox Paper, and Google Docs are four of the biggest note-taking programs. There are a ton more - Simplenote, Google Keep, and a lot I haven’t listed. However, I chose these three because they are very popular, sync across all of your devices, and support more formatting than others like Google Keep.
OneNote
OneNote is Microsoft’s note-taking program. If you like lots of features, such as password protection, advanced reviewing, drawing, built-in integration with Microsoft Excel, and a lot more, OneNote is definitely for you.
If you haven’t tried OneNote yet, OneNote is grouped into “notebooks” which have “sections”, which have “pages”. For instance, I have a School notebook, with a Math section, and then my notes from today are in a page.
One of the biggest reasons to choose OneNote is for the equation editor. The equation editor lets you type equations, including, but not limited to, fractions, square/cubed/etc roots, exponents, Pi, and a lot other mathematical symbols.
Another big reason to choose OneNote is for the built-in drawing feature. You can draw with your mouse, your finger (on touchscreen devices), or a pen (either a stylus on touchscreen devices or using a special pen, like the ThinkPad Pen Pro, the Surface Pen, or the Apple Pencil. The drawing tool supports lasso selection, erasing, typing, a lot of different colors and thicknesses, highlighting, and shapes drawing. It also supports Ink to Math, which lets you see your drawings be automatically be converted to equations.
Unfortunately, while OneNote supports a plethora of features, it does have some downsides, also. The biggest downside (for me) is the lack of equation editor support in the web version. You can view equations, but not create or edit new ones. The OneNote mobile app lets you edit equations, but I don’t think it lets you create new ones. This rules out OneNote for Chromebook users who want to use equations.
Another big downside is the large amount of bugs in the OneNote equation editor. For instance, if you have a bunch of equations, one on each line, if you press Shift+Home (select until the start of the current line), OneNote will select the entire group of equations. That is just one out of the many bugs in the OneNote equation editor.
Another thing I dislike about OneNote is the inability to delete notebooks. Yes, you heard me right. There is no easy way to delete a notebook. You can “close” a notebook, but it will still be there; it will just not be synced (sunk?) with your computer. Something else I dislike about OneNote - you can’t crop images. At all. Whaaaat?
One last thing I dislike about OneNote: syncing. Microsoft just can’t seem to get real-time updating right. OneNote syncs automatically with the cloud, but you can’t see someone (or yourself) updating in real time like you can in other programs like Google Docs. This can be annoying and cause sync conflicts.
Overall, OneNote is a good choice if you want lots of features, but I would turn it down in favor of better programs.
Evernote
Evernote is one of the most popular note-taking programs out there. Evernote is very similar to OneNote in many ways. It is laid out the same way as OneNote, except you only have “Notebooks” and “Pages” - no “Sections”. The desktop version of Evernote supports quite a few features, although unfortunately, equations are not one of the included features.
Evernote includes quite a few useful features, such as note reminders, meeting notes, work chat, and tags. However, most of these features seem geared more towards large organizations than towards consumers.
Unfortunately, Evernote has quite a few downsides, the biggest being the price. Evernote is the only application in this article that you have to pay for - the other three are free, and I would probably choose one of them over Evernote. While Evernote has a nice user interface and has more features than Dropbox Paper, it does not have anywhere near as many features as OneNote, which is free. Because of the price, I would probably recommend one of the other three over Evernote.
Dropbox Paper
I love Dropbox Paper. Considering the fact that I’m currently writing this article in Dropbox Paper, I might be a bit biased, but Dropbox Paper is definitely very nice.
At first glance, Dropbox Paper looks very simple, and you might decline it in favor of one that seems to have more features. Dropbox Paper has quite a few useful features, although not quite as many as OneNote, Evernote, or Google Docs. I think Dropbox Paper is the perfect balance of simplicity and features.
One thing about Dropbox Paper is that it isn’t setup like OneNote and Evernote. Instead of notebooks/sections/pages, you create folders. You can nest as many folders as you want, or you could put a document in a folder, but also have another folder in that folder. I like this a lot, because you can set it up however you want to.
Dropbox Paper supports semi-full formatting - bold, strikethrough, italics, highlighting (but only in blue), links, headers, bulleted and numbered lists (but no lettered lists… ???), checkboxes, and comments. That’s a full list of the formatting features, which seems pretty small at first, but is actually just the right amount.
Dropbox Paper also supports equations using LaTeX, which is very nice. Dropbox Paper makes it easy to write equations without confusion or glitches. One of my favorite things about Dropbox Paper is that when you click on an equation, it shows it in code form instead of the way OneNote or Google Docs do it (by trying to show it in equation format but making it editable, which is pretty terrible).
However, Dropbox Paper definitely could use a few more features, most notably drawing. I would use Dropbox Paper for my math notes, but unfortunately, I need to be able to draw, which Dropbox Paper doesn’t support.
Another downside of Dropbox Paper is that it doesn’t support offline editing/viewing on the desktop version (actually the web version; there is no desktop version).
Overall, I really like Dropbox Paper. If they added a few more features (cough drawing and more colors cough), it would be the perfect note-taking application.
Google Docs
If Google made a version of Google Docs that was more suited for note-taking - perhaps if they gave it a notebook/page structure like OneNote and Evernote - it would be my absolute favorite.
You might be wondering why I put Google Docs in here - isn’t Google Docs for documents, not notes? That’s correct, but I find Google Docs is actually pretty good (but not great) for note-taking. Google Docs has all the features I like in a note-taking program - full formatting, easy cloud integration, equations, and drawing. I find that you can use Google Docs pretty easily if you create a different document in place of each notebook/section.
Now that I’ve told you I put Google Docs in here, you might ask - why not Word? To which I answer: Word is not good at cloud integration. You can put a Word doc in your OneDrive/Google Drive/Dropbox/whatever and let it sync that way, but it’s not the same as turning off your laptop, turning on your desktop, and seeing the document there - no waiting for your OneDrive/Google Drive/Dropbox/whatever to sync, no browsing through folders: it’s just there.
However, Google Docs isn’t perfect. It wasn’t designed as a note-taking program, so there are a few things that can get annoying there - like the fact that if you fill up a whole 8.5 x 11 page, you’ll go onto the next page, whereas the other three don’t work like that. Another annoying thing about Google Docs is that all your docs go in your Google Drive root folder. You can’t set a default location; you just have to remember to tell Google Docs to save your document in a different Google Drive location.
Round Up
Dropbox Paper
Google Docs
OneNote
Evernote
Dropbox Paper is my favorite note-taking program by far. It’s the perfect mix of simple but powerful.
Google Docs is my second favorite. It supports all the features I want - Chromebook support, equations, drawing, and a lot more. It would get first place if they built a version with a structure like OneNote or Evernote.
OneNote is my third favorite. It supports a lot of features, so it’s very unlikely that you’ll be like “Aw, I wish it had that”.
Evernote is my fourth favorite. Evernote has a nice user interface, but it is expensive and doesn’t do anything special.
0 notes