#Windows Server 2019 Download
Explore tagged Tumblr posts
Text
How To Make an Organizational Chart in Visio Very easily
Download Visio is a strong diagramming and visualization tool created to simplify complex ideas with clarity. No matter whether you'll want to develop flowcharts, organizational charts, network diagrams, or ground programs, Visio supplies intuitive applications and a person-helpful interface to deliver your Strategies to daily life.
What exactly is Microsoft Visio? Visio is the best Instrument for developing organizational charts with its person-pleasant and successful graphic features. This extensive tutorial guides you thru the whole process of crafting an organization chart, regardless of whether you favor to make it happen manually or by importing employee information from an Excel org chart template.
With Visio's adaptable abilities, you can simply style obvious and Qualified organizational charts that effectively talk your Business's construction.

Permit’s begin to see the techniques on tips on how to build a wonderful yet simple-to-comprehend org chart:
Measures To construct an Organizational Chart in Visio Produce a new file Choose the “New” choice within the File tab, then select Business Chart
two. Pick out Tastes Decide on Metric Units or US Units, and now simply click Generate
3. Cancel the Corporation Chart Wizard It's also possible to make an org chart in Visio Prepare 2 by hand by just clicking Terminate if the Business Chart Wizard dialog box seems
four. Include a brand new condition About the left facet with the display, simply click the Designs box to decide on an staff typeAfter deciding on the shape, drag The form onto the doc

five. Include personnel descriptions Pick out Title on the shape and input the employee’s titleSelect Title on The form and enter the worker’s identify
6. Alter personnel shots Choose the placeholder impression. Find Alter in the very best ribbon on the Org Chart tab. Opt for the specified graphic file from a drive and select Open up
seven. Join workers Now pull an worker’s shape onto the shape of the individual they report toThe styles will automatically connect
8. Adjust condition style Select the Org Chart tab and adjust the type of the shapes, then simply click your preferred condition style within the top ribbon
These are the short ways to make a company chart in Visio Specialist 2021, the most recent Edition of Visio. Furthermore, you can also make an Org Chart in Visio with the assistance of Templated Facts. Allow’s see how this method will work.
Corporation Chart in Visio with Templated Facts Obtain the organizational chart template Here, you will note the file consists of popular facts factors found in org charts Now you need to place the info in the template with the personnel’s infoMake certain you merely conserve the file before going to the next action
2. Produce a New File In Visio, select the New possibility while in the File tabThen choose Firm Chart three. Pick Tastes Select Metric Models or US Models, then click Generate four. Choose the Group Chart Wizard Select Data that’s already stored in a very file or databases, Click Following
five. Select the file sort Go with a textual content, Org Furthermore (*.txt), or Excel file, then click on Future
six. Locate the file Find the information file as part of your travel, then click Up coming
7. Opt to detect information Choose the columns out of your file that outline the names of the staff, Click on Upcoming.
eight. Opt for additional info Include or get rid of columns through the file you want to displayThe next screen will request identical informationAdd or remove columns to display each employee condition, then simply click Upcoming
9. Pick photographs Pick Locate the folder which contains your Corporation pics Then discover the folder. Click Following.
10. Choose Structure Depending upon the sizing, your chart may well have to be split throughout many webpages
eleven. Change layout To change the appearance of your org chart’s layoutChoose from the choices while in the Layout team in the Org Chart tab
So, these were The easy measures to make a corporation chart by means of Templated Information. The excellent news is that you could have these characteristics in Visio Expert 2019; this is easily the most demanded Edition of Visio in the marketplace for little to medium-sized enterprises.
To learn the cost of Microsoft Visio, you'll be able to contact DirectDeals; the knowledge is specified beneath:
Your existence on this enlightening journey is actually appreciated! Our blogs are enriched using an idea of Microsoft Visio. More, Really don't hesitate to reach out. Access us at (800) 983-2471 or join by way of e mail at [email protected]. We're right here To help you each individual step of the best way.
Check more info. here: Microsoft Windows 11 Pro Downloa
Check out Our Social Page Bellow: -Facebook -Twitter (X) -Instagram -LinkedIn -YouTube -Pinterest
#Software Discounts#DirectDeals Blog#SQL Server Download#Windows Server 2019 Download#Microsoft Windows 11 Pro Download#Microsoft Office 2021 Download#DirectDeals
0 notes
Text
How to troubleshoot Active Directory Replication issues
#Active Directory#Active Directory Replication#Active Directory Replication Issues#ADREPLSTATUS#DCDiag#Download ADREPLSTATUS tool#LDAP connectivity#Microsoft Windows#RepAdmin.exe command-line tool#Windows#Windows Server#Windows Server 2012#Windows Server 2019#Windows Server 2022#Windows Server 2025
1 note
·
View note
Text
Windows Server 2019 Essentials: Download, Install, and Activate

Welcome to our comprehensive guide on Windows Server 2019 Essentials. In this article, we will provide you with detailed instructions on how to download, install, and activate this powerful operating system. Whether you are a small business owner or an IT professional, Windows Server 2019 Essentials offers a wide range of features to meet your needs. Let's dive right in!
Downloading Windows Server 2019 Essentials
To get started, visit the official Microsoft website and navigate to the Windows Server 2019 Essentials download page. You will find a variety of options depending on your licensing requirements. Choose the version that suits your needs and click on the download link.
Ensure that you have a stable internet connection as the download size can be quite large. It is recommended to use a high-speed connection to expedite the process. Once the download is complete, you can proceed to the installation phase.
Installing Windows Server 2019 Essentials
Before you begin the installation, make sure you have met the system requirements for Windows Server 2019 Essentials. It is crucial to have a compatible hardware configuration to ensure smooth operation. Refer to the official documentation or consult with your IT department for specific requirements.
Insert the installation media into your server or mount the ISO file if you are using a virtual environment. Boot the server from the installation media and follow the on-screen instructions. You will be prompted to select the installation type, language preferences, and disk partitioning options.
After making the necessary selections, the installation process will commence. This may take some time, so be patient. Once the installation is complete, your server will restart, and you can proceed to the activation step.
Activating Windows Server 2019 Essentials
Upon restarting your server, you will need to activate Windows Server 2019 Essentials to unlock its full potential. Follow these steps to activate your copy:
Go to the "Start" menu and click on the "Settings" icon.
In the Settings menu, select "Update & Security."
Click on "Activation" in the left-hand menu.
Under the Activation section, click on "Change product key."
Enter the valid product key for your Windows Server 2019 Essentials license and click "Next."
Follow the on-screen instructions to complete the activation process.
Ensure that you have a stable internet connection during the activation process. Once the activation is successful, you will have full access to all the features and functionalities offered by Windows Server 2019 Essentials.
Benefits of Windows Server 2019 Essentials
Windows Server 2019 Essentials provides numerous benefits that make it a preferred choice for businesses of all sizes. Here are some key advantages:
Simplified Management: Windows Server 2019 Essentials offers an intuitive and user-friendly interface, making it easier to manage your server environment. You can effortlessly configure and monitor various aspects of your network, saving valuable time and resources.
Robust Security: With built-in security features, Windows Server 2019 Essentials ensures the safety and privacy of your data. It includes advanced threat protection mechanisms and enhanced control over user access, safeguarding your network from potential cyber threats.
Efficient File Sharing: The server enables seamless file sharing and collaboration among employees, improving productivity and teamwork. Windows Server 2019 Essentials provides a centralized file storage platform, allowing secure access to files from anywhere within the network.
Reliable Backup and Recovery: Protecting your data is crucial, and Windows Server 2019 Essentials offers reliable backup and recovery solutions. You can schedule automated backups, ensuring that your critical data is safe and easily recoverable in case of system failures or accidental deletions.
Scalability and Flexibility: As your business grows, Windows Server 2019 Essentials scales with you. It supports a wide range of applications and workloads, allowing you to expand your infrastructure without compromising performance or stability.
Conclusion
Congratulations! You have successfully downloaded, installed, and activated Windows Server 2019 Essentials. This powerful operating system brings a host of benefits, including simplified management, robust security, efficient file sharing, reliable backup and recovery, and scalability.
By following the steps outlined in this guide, you can make the most of Windows Server 2019 Essentials and empower your business with a secure and efficient network infrastructure.
#windows server 2019#Windows Server 2019 Essentials#server 2019#microsoft server#microsoft#server 2019 download
1 note
·
View note
Text
Hyper-V Server 2025: Nope but sort of?
Hyper-V Server 2025: Nope but sort of? #hyperv #homelab
I think many have been dismayed about the discontinuation of Hyper-V Server. The last version that you can officially download is Hyper-V Server 2019. However, with the release of the Windows Server 2025 Preview ISO, I want to show you guys how you can install a new Windows Server 2025 installation and have roughly the same functionality as Hyper-V Server 2019 and you can have access to the…
0 notes
Text
Windows Memory Cleaner: libere memória RAM e otimize o desempenho do Windows
Se você já se perguntou por que seu computador está ficando cada vez mais lento, a resposta pode estar relacionada ao uso excessivo de memória. Afinal, a memória RAM desempenha um papel crucial no desempenho do seu sistema, e quando sobrecarrega, seu PC perde a velocidade e a eficiência. Felizmente, existe uma ferramenta poderosa chamada Windows Memory Cleaner, que pode ajudar a melhorar o desempenho do seu computador e liberar memória RAM. Vamos explicar o que é o Windows Memory Cleaner, como ele funciona e como usar para otimizar a memória do seu PC.
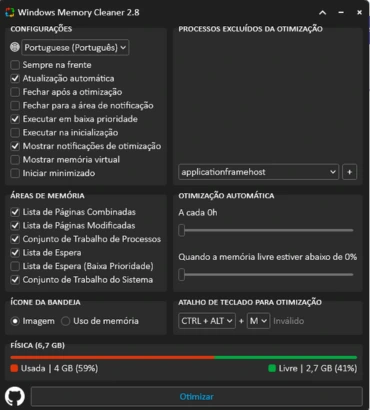
O que é o Windows Memory Cleaner?
O Windows Memory Cleaner é uma ferramenta de otimização que tem como objetivo liberar a memória RAM do seu computador, por recursos nativos do Windows. É um aplicativo compacto, portátil e inteligente. Ele é ideal para quando você percebe que seu PC está mais lento do que o normal e a causa pode ser o uso excessivo de memória. O projeto está no GitHub e foi criado por IgorMundstein.
Por que liberar memória RAM? Quando você abre vários aplicativos ou programas ao mesmo tempo, o Windows aloca memória RAM para cada um deles. Mesmo após fechar esses programas, a memória nem sempre é liberada automaticamente, o que pode resultar em um acúmulo de dados desnecessários. O Windows Memory Cleaner entra em ação para resolver esse problema e liberar essa memória.
Como o Windows Memory Cleaner Pode Ajudar?
O aplicativo possui uma interface minimalista e recursos inteligentes. Ele é portátil, ou seja, não requer instalação, mas exige privilégios de administrador para ser executado. Aqui estão algumas vantagens de usar o Windows Memory Cleaner: - Lista de páginas combinadas: Limpa os blocos da lista de páginas combinadas efetivamente somente quando a combinação de páginas está habilitada - Lista de páginas modificada: Limpa a memória da lista de páginas modificadas, gravando dados não salvos no disco e movendo as páginas para a lista de espera - Conjunto de Trabalho de Processos: Remove a memória de todos os conjuntos de trabalho do modo de usuário e do sistema e os move para as listas de páginas de espera ou modificadas - Lista de espera: Libera páginas de todas as listas de espera para a lista livre - Lista de espera (baixa prioridade): Libera páginas da lista de espera de menor prioridade para a lista livre - Conjunto de trabalho do sistema: Remove a memória do conjunto de trabalho do cache do sistema
Requisitos do sistema:
- Microsoft .NET Framework 4 - Windows XP/ Vista/ 7/ 8/ 10/ 11 - Windows Server 2003/ 2008/ 2012/ 2016/ 2019/ 2022/
Como baixar o Windows Memory Cleaner?
Para baixar, basta clicar no Botão Download abaixo e acessar o site Oficial do GitHub e clicar no Botão Download no site do desenvolvedor como no exemplo abaixo:

Dicas Extras para Melhorar desempenho do PC
Aqui estão algumas dicas adicionais para complementar o uso do Windows Memory Cleaner e otimizar ainda mais o desempenho do seu computador: 1. Feche Programas Desnecessários Sempre que terminar de usar um programa, feche-o corretamente. Mesmo que você minimize a janela, o aplicativo ainda pode estar consumindo recursos. 2. Use o Gerenciador de Tarefas do Windows Abra o Gerenciador de Tarefas (Ctrl + Shift + Esc) e verifique quais programas estão consumindo muita memória. Feche os que não estão sendo utilizados. 3. Desative Programas na Inicialização Alguns programas são configurados para iniciar automaticamente com o Windows. Desative esses programas no Gerenciador de Tarefas para reduzir o consumo de memória logo após o boot. 4. Instale Mais Memória RAM Se o seu computador continua lento mesmo após liberar memória, pode ser hora de investir em mais RAM. Adicionar memória física pode fazer uma grande diferença no desempenho. 5. Verifique por Malware Vírus e malwares podem consumir muita memória e deixar seu sistema mais lento. Faça verificações regulares com seu antivírus para garantir que seu computador esteja limpo.
Considerações Finais sobre o Windows Memory Cleaner
O Windows Memory Cleaner é uma ferramenta útil para otimizar a memória do seu computador, especialmente em momentos em que você percebe uma queda no desempenho. Ao seguir os passos acima e usar as dicas extras, você pode garantir que seu sistema se mantenha ágil e sem travamentos. Lembre-se de que, além de limpar a memória, é importante adotar boas práticas no uso diário do computador, como fechar aplicativos não utilizados e realizar manutenções regulares. Agora que você sabe como usar o Windows Memory Cleaner, aproveite ao máximo o seu PC e tenha uma experiência mais rápida e fluida! Gostou deste artigo? Deixe seu comentário abaixo e compartilhe suas experiências com o Windows Memory Cleaner. Se você tem mais dicas ou ferramentas que ajudam a melhorar o desempenho do PC, adoramos ouvir de nossos leitores! Read the full article
0 notes
Text
Suggestions for Downloading and Using KMSAuto Activator Successfully

Easily activating your Windows and Office items can spare you time, tension, and money. KMSAuto net activator has ended up being a popular option one of individuals worldwide, delivering an efficient means to open the full potential of your software without cracking the bank. From Windows 7 to KMSAuto Windows 11, this tool is actually functional, reputable, and easily accessible. Here are actually some valuable tips to assist you take advantage of this effective activator.
Recognizing What Helps Make KMSAuto Net Activator Attract Attention
KMSAuto activator is actually created to simplify the activation process for each Windows and Office items. It takes advantage of the Key Management Service (KMS) method to simulate an official Microsoft activation server, enabling users to take pleasure in real functions without acquiring a permit. This tool is specifically prominent in nations like Ukraine, the Russian Federation, Indonesia, Egypt, Mexico, Kyrgyzstan, and Russia, where software accessibility is crucial. In reality, over 30% of users in these regions have looked to tools like KMSAuto official for trustworthy activation solutions.
Whether you're making use of KMSAuto Windows activator or the KMSAuto office activator, its own seamless user interface and offline capabilities produce it an excellent option for users searching for a trouble-free solution.
Opting For the Right Model of KMSAuto Net Activator
Picking the correct variation of the KMSAuto Windows activator is critical to ensure being compatible and efficiency. For example, if you are actually operating Windows 10, pick KMSAuto net Windows 10. Likewise, users improving to Windows 11 needs to download KMSAuto Windows 11 for the absolute best outcomes.
Don't forget to confirm the model of your os and Office set before downloading the activator. This makes certain that the download KMSAuto activator you choose aligns along with your system needs, sparing you from needless mistakes. For Office products like Office 2016, 2019, or even 2021, the KMSAuto net activator is your best option.
Stats present that more than 50% of users in countries like Indonesia and Egypt count on the newest versions of activators to make certain hassle-free operation and prevent compatibility concerns.
Measures to Properly Download KMSAuto Net Activator
Downloading the KMS Auto tool from a trustworthy resource is important for keeping your system's security. With counterfeit versions typically flowing online, it is actually important to select a counted on website. Consistently look for comments and examines from individuals to ensure you're obtaining a valid duplicate.
Just before beginning the download KMSAuto activator, disable your antivirus momentarily, as some programs may flag the activator as a result of its attribute, even though it is actually risk-free. Once downloaded, extraction the ZIP documents and adhere to the directions supplied. Nations like Mexico and Russia have actually seen an enhancing demand for activators, with almost 40% of individuals highly recommending comprehensive investigation before downloading to stay clear of malware.
Making the most of the Productivity of KMSAuto Activator
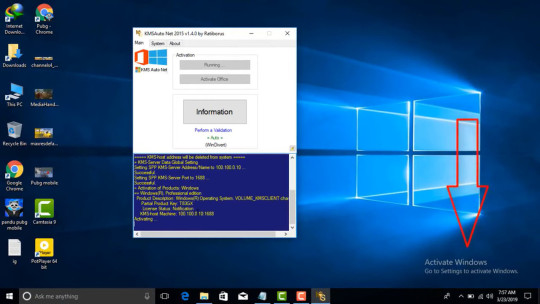
After downloading the KMSAuto activator, running it as a manager makes sure the tool performs accurately. Browse to the activation menu, select your product (Windows or Office), and let the activator take care of the remainder.
The KMS Auto Windows activator is designed to work quickly, commonly accomplishing the method within moments. For users activating Office items, the KMSAuto office activator is equally efficient. Its twin activation component allows you to manage several items at the same time, an advantage especially valued in nations like Kyrgyzstan and Ukraine, where over 25% of individuals count on activators for specialist make use of. To activate Windows and Office easily, download KMS Auto net activator from getkmsauto and take advantage of hassle-free program activation.
For a smooth experience, ensure your system meets the simple requirements, consisting of managerial opportunities and.NET Framework 4.0 or greater.
Perks of utilization KMSAuto Net Activator
The KMS net activator supplies numerous advantages, creating it a best solution for individuals around the globe. Its capability to provide life-time activation does away with the requirement for consistent revitalizations, giving you uninterrupted accessibility to your software program.
Additionally, the KMSAuto official tool is Portable, making it possible for individuals to manage it directly without setup. This comfort is enjoyed by users in Russia and the Russian Federation, where flexibility and simplicity of making use of are actually very valued.
One standout component is its own virus-free operation. While antivirus systems may banner it throughout the download, KMSAuto Windows activator has been actually depended on for a long times as a risk-free and successful tool. Data show that over 45% of individuals in Egypt and Mexico like it for its reliability and cost-saving benefits.
Final Thoughts
The KMSAuto net activator is actually even more than only an activation tool; it's a gateway to effectiveness and performance. By adhering to these tips, you may delight in convenient activation for your Windows and Office products, whether you reside in Ukraine, Indonesia, or even Kyrgyzstan. With its straightforward design, life time activation, and compatibility around numerous variations, the KMSAuto official tool ensures you get the absolute most away from your software program while sparing money.
Accept the simplicity of KMSAuto Windows 11 and Office activation, and enhance your experience along with this depended on tool.
0 notes
Text
How to Install Windows Server 2019: A Quick Guide
Windows Server 2019 is a robust and secure operating system, ideal for businesses of all sizes. Here's a simplified guide to install it:
Prepare Boot Media: Download the ISO or use a USB drive to boot the installer.
Select Preferences: Choose a language, time zone, and keyboard layout.
Start Installation: Click 'Install Now' and select your preferred version.
Accept License: Review and accept the license agreement.
Choose Installation Type: Opt for 'Custom' to start fresh.
Set Up Partition: Select where to install and create a new partition if needed.
Complete Setup: Follow the prompts to finish the installation, set up an admin password, and finalize configurations.
With Windows Server 2019, you'll enjoy better security, performance, and scalability for your network needs!
0 notes
Text
Docker is developing new tools and solutions to address the needs of its users. However, it has lagged in some regards. In particular, Docker has failed to address a few complaints that developers have risen with integrating the platform with Windows. Docker recently announced that it is finally addressing these concerns. They are releasing experimental support for developers that need to integrate Docker with Windows Home WSL 2. What Does the New Announcement Mean for Docker Developers? The new announcement was made on the Docker blog on March 5, 2020. The authors said that they alluded to these changes back in 2019. They shared a preview of what it would entail, but the development team has only recently decided to release them to the public. The new update is ideal for developers that want to create Linux containers from a Windows environment. Some of the changes that it will involve include: Windows users will be able to use the latest version of Docker without having to switch to a Linux machine. Windows Home users will be able to install the Kubernates application with a single click. The user interface can be integrated seamlessly, which enables developers to manage and ensure that all of their containers that are running. Linux workspaces can be used from any Windows machine. Memory can be efficiently allocated to select projects. The new announcement is encouraging. However, some developers may have difficulty incorporating Docker into their Windows Home platform. An overview of the process is provided below. Integrating Docker into Windows Home You will need to follow the steps below to integrate containers from Docker into your Windows platform. In this case, you will need to create three containers that will communicate with each other using different technologies (MySQL and MVC mCore). But before you can take these steps, you are going to need to understand the nature of Docker and its environment. We have all heard of Docker registry and Docker containers before. Even if you weren’t entirely familiar with the concept, you should have some exposure to it. The idea behind Docker is to create lightweight, portable containers for software applications that can run on any machine with a Docker installed, regardless of the operating system the machine is running on. This clearly facilitates deployments of new applications, since Docker is highly efficient. In order to understand the interface behind Docker, you should try imagining a container ship, because each container on the ship is a machine that is programmed to do what you want (Server Core, Oracle, MySql are examples of these machines). They can be integrated and ordered to communicate with each other easily, with the addition that you can make it run anywhere and operating system. Once we have more or less clarified what a Docker is and what it is for, let's move on to the creation of containers. First and foremost, we will install Docker. In my case, I installed it in Windows. We can download it from this link on the official page of Docker and once downloaded we will install it giving in next - next install ( I know this is not very recommended for installations but in this case, there is no need to configure anything prior to installation) and wait for it to be installed. Once installed, it will ask us to uninstall it and we say yes. Once started again it will ask us to run Windows-native Hyper-V virtualization and networking, we say yes and the PC will be restarted. Once it starts again, we would have Docker ready for use. As a last piece of information, he will ask us for a Docker account with the Docker management so he can upload your containers to DockerHub for other people to see. Once the previous step has been followed we are ready to create our containers, but first, we need to create our network in Docker where the containers will go so that they can communicate with each other. With the command docker network create network_name we create the network.
0 notes
Text
Forgot Windows 8.1 Local Admin Password No Reset Disk How to Resolve
How to get back into your Windows 8.1 computer if you have forgotten local administrator password no reset disk, how can you reset administrator password in Windows 8.1 without reset disk?

To resolve this problem, you can firstly try Offline NT Password Editor to help reset the forgotten Windows 8.1 administrator password without reset disk. Offline NT password Editor can help clear or reset Windows local account password via CD/DVD. The following procedure will show you the detailed walkthrough.
Trick 1: Use Offline NT Password Editor to Reset Windows 8.1 Local Admin Password (Work with CD/DVD).
When you forgot Windows 8.1 administrator password and a password reset disk was not created, “Offline NT Password Editor”, a free Windows password reset disk, can help you reset forgotten Windows 8.1 local account’s password without knowing it. Free download the ISO file from the official site. Extract the downloaded file and then burn the ISO file on to a writable CD/DVD. Once burning completed, you can use the CD/DVD which is bootable to crack Windows 8.1 Local Admin password.
Step 1: Power on your locked computer and then insert the bootable CD to the CD-ROM.
Step 2: Restart the computer to boot from CD/DVD. If it still boot into Windows, you may need to change device boot order in BIOS. Learn how to boot computer from CD/DVD.
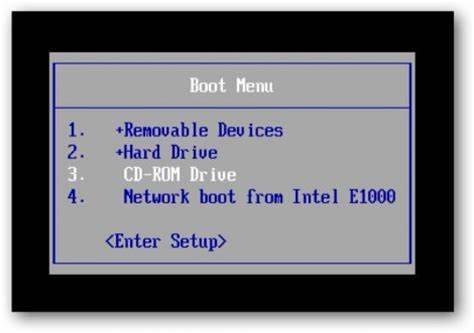
Step 3: When the computer boots from CD and loads Offline NT screen, press Enter until the “step one” appears. Type “1” and hit Enter.
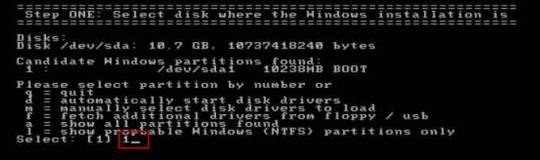
Step 4: Select “Password reset”, type “1” and hit Enter.
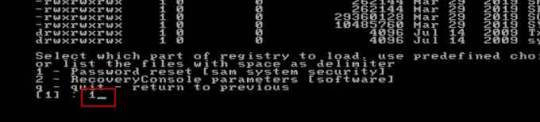
Step 5: Select “Edit user data and passwords, type “1” and hit Enter.
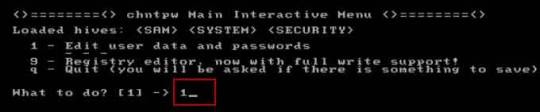
Step 6: Select a user account, type “administrator” and hit Enter.
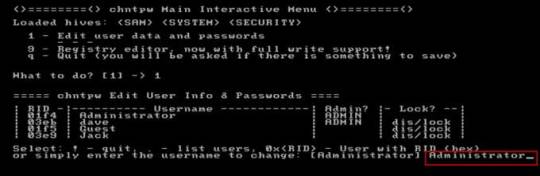
Step 7: Select “Clear user password”, type “1” and hit Enter.
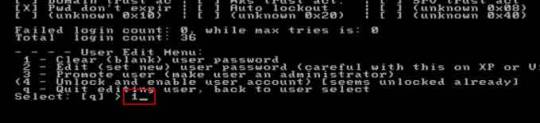
Step 8: Administrator’s password is cleared. Select “Quit editing user and back to user select”, type “!” and hit Enter.
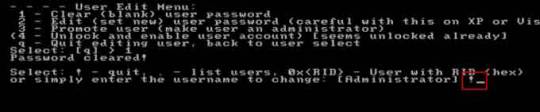
Step 9: Select “Quit”, type “q” and hit Enter.
Step 10: Write back changes, type “y” and hit Enter.
Step 11: When it asks you if try again, type “n” and hit Enter.
Step 12: Now eject your CD and then press CTRL-ALT-DEL to restart the computer.
Step 13: When Windows 8.1 welcome screen appears, click the screen to automatically sign in administrator without password.
Another simple method to reset forgotten Windows 8/8.1 local admin password is using a password recovery program, Windows Password Rescuer, which is working fine for all Windows systems including Windows 11. Here is how to use the utility to reset a local admin password on Windows 8.1/8 PC without logging in.
Trick 2: Reset Windows 8.1 Administrator Password with Windows Password Rescuer Run from USB.
If you have forgotten Windows 8.1 administrator password and need to get back into the account, you can use Windows Password Rescuer to create a bootable USB disk and then use the disk to reset Windows 8.1 local administrator password easily without losing data. It also works perfectly for Windows 11, 10, 8.1, 8, 7, Vista, XP and Windows server 2022, 2019, 2016, 2012, 2008, 2003 etc.
Equipment required: Another Windows computer, USB flash drive.
Read more detailed steps: How to reset Windows 8.1 Admin Password with USB.
Step 1: Use another computer to download Windows Password Rescuer and then install the software.
Step 2: Plug in a blank USB flash drive to the computer and launch the software. Select “USB device” on the software screen.
Step 3: Pull down the drive list and select your plugged USB flash drive. Then click “Begin Burning” to create a bootable USB under a minute.
Step 4: Once the burning process is completed, unplug the USB flash drive and then connect it to your locked computer that you want to reset Windows 8.1 password.
Step 5: Power on the locked computer and press F12 as soon as possible to open “Boot Menu”. Press arrow key to highlight USB option and press Enter to boot from USB.
Step 6: Once the locked computer boots from USB and locates Windows Password Rescuer, you can reset administrator or other local user account passwords with several clicks. Now click “Administrator” from user list.
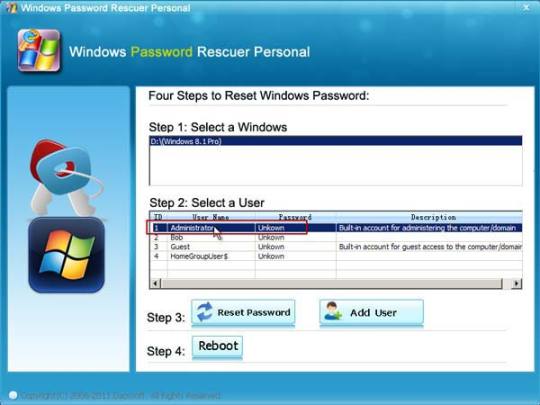
Step 7: Click “Reset Password”, when it asks you if reset administrator password to blank, click “Yes” to confirm it.
Step 8: Administrator password will be removed and shown blank in password list. It means that you will be able to sign in the account without password.
Step 9: Click “Reboot”. When it asks you to remove your USB, remove the USB from your computer and then click “Yes” to restart the computer.
Step 10: After restarting, you can log on administrator without password.

Methods in this article apply to any laptop and desktop computers such as Dell, HP, Toshiba, Acer, Lenovo, Asus etc.
0 notes
Text
DirectDeals|SQL Server Download|Windows Server 2019 Download
DirectDeals is recognized in Microsoft Partner Network as a proud participant and Cloud Solution Provider Program (CSP). The MPN allows DirectDeals to provide its customers direct access to the Microsoft Open Licensing and Open Volume programs. The customers are also allowed access to various Check out more details here: https://www.directdeals.com/software/microsoft-office/office-2021
#DirectDeals Blog#SQL Server Download#Windows Server 2019 Download#Microsoft Windows 11 Pro Download#Microsoft Office 2021 Download
0 notes
Text
Index meistverbreiteter Malware im Juli 2024

Der aktuelle Threat Index zeigt, dass RansomHub weiterhin die aktivste Ransomware-Gruppe ist. Gleichzeitig haben die Forscher eine Remcos-Windows-Malware-Kampagne identifiziert, die ein kürzlich veröffentlichtes Sicherheitsupdate ausnutzt. Der Global Threat Index für Juli 2024 zeigt: Trotz eines deutlichen Rückgangs im Juni ist LockBit im vergangenen Monat wieder zur zweitgefährlichsten Ransomware-Gruppe aufgestiegen, während RansomHub an der Spitze bleibt. In der Zwischenzeit haben die Forscher sowohl eine Kampagne zur Verbreitung von Remcos-Malware im Anschluss an ein CrowdStrike-Update-Problem als auch eine Reihe neuer FakeUpdate-Taktiken identifiziert, die im Juli erneut an die Spitze der Top-Malware-Liste gelangten. CrowdStrike-Problem schlägt durch Ein Problem im CrowdStrike Falcon Sensor für Windows ermöglichte es Cyberkriminellen, eine bösartige ZIP-Datei namens crowdstrike-hotfix.zip zu verbreiten. Diese Datei enthielt den HijackLoader, der anschließend die Malware Remcos aktivierte, die weltweit im Juli auf Platz 7 der meistgesuchten Malware stand. Die Kampagne richtete sich an Unternehmen, die spanischsprachige Anweisungen verwandten, und beinhaltete die Erstellung gefälschter Domänen für Phishing-Angriffe. Top-Malware in Deutschland - CloudEye (12,5 %) – CloudEye ist ein Downloader, der auf das Windows-System zielt und dazu verwendet wird, schädliche Programme herunterzuladen und auf den Computern der Opfer zu installieren. - Androxgh0st (4,5 %) – Androxgh0st ist ein Bot-Netz, welches auf Windows-, Mac- und Linux-Plattformen zielt. Für die Infiltration nutzt Androxgh0st mehrere Sicherheitslücken aus, die insbesondere bei PHPUnit, Laravel Framework und Apache Web Server gegeben sind. Die Malware stiehlt sensible Informationen wie Twilio-Kontoinformationen, SMTP-Anmeldeinformationen, AWS-Schlüssel und dergleichen. Sie verwendet Laravel-Dateien, um die erforderlichen Informationen zu sammeln. Es gibt verschiedene Varianten, die nach unterschiedlichen Informationen suchen. - FormBook (4,35 %) ist ein Infostealer, der auf das Windows-Betriebssystem zielt und erstmals im Jahr 2016 entdeckt wurde. Er wird in Hacker-Foren als Malware as a Service (MaaS) vermarktet, da er starke Umgehungstechniken und einen relativ niedrigen Preis hat. FormBook sammelt Anmeldeinformationen von verschiedenen Webbrowsern sowie Screenshots, überwacht und protokolliert Tastatureingaben und kann Dateien auf Anweisung von seinem C&C-Server herunterladen und ausführen. Aktivste Ransomware-Gruppen Die Daten basieren auf Erkenntnissen von Ransomware-Shame Sites, die von Ransomware-Gruppen mit Doppelter Erpressung betrieben werden und Informationen über die Opfer veröffentlichen. RansomHub ist die am weitesten verbreitete Ransomware-Gruppe in diesem Monat und für 11 Prozent der veröffentlichten Angriffe verantwortlich, gefolgt von Lockbit3 mit 8 Prozent und Akira mit 6 Prozent. - RansomHub - RansomHub ist eine Ransomware-as-a-Service (RaaS)-Operation, die als Rebranding-Version der zuvor bekannten Ransomware Knight auftauchte. RansomHub tauchte Anfang 2024 in Untergrund-Cybercrime-Foren auf und erlangte schnell Berühmtheit für seine aggressiven Kampagnen, die auf verschiedene Systeme wie Windows, macOS, Linux und insbesondere VMware ESXi-Umgebungen abzielten. Diese Malware ist dafür bekannt, dass sie ausgeklügelte Verschlüsselungsmethoden einsetzt. - Lockbit3 - LockBit ist eine RaaS-basierte Ransomware, die erstmals im September 2019 gemeldet wurde. LockBit richtet sich gegen große Unternehmen und Regierungsbehörden in verschiedenen Ländern, jedoch nicht gegen Privatpersonen in Russland und der Gemeinschaft Unabhängiger Staaten. - Akira - Akira Ransomware, die erstmals Anfang 2023 gemeldet wurde, zielt sowohl auf Windows- als auch auf Linux-Systeme ab. Sie verwendet symmetrische Verschlüsselung mit CryptGenRandom() und Chacha 2008 zur Dateiverschlüsselung und ähnelt der durchgesickerten Conti v2 Ransomware. Akira wird über verschiedene Wege verbreitet, einschließlich infizierter E-Mail-Anhänge und Exploits in VPN-Endpunkten. Nach der Infektion verschlüsselt die Ransomware Daten und fügt eine „.akira"-Erweiterung an Dateinamen an und präsentiert dann eine Lösegeldforderung für die Entschlüsselung. Passende Artikel zum Thema Lesen Sie den ganzen Artikel
0 notes
Text
https://mediamonarchy.com/wp-content/uploads/2024/07/20240723_MorningMonarchy.mp3 Download MP3 Drone program meetings, CrowdStrike software glitches and championship auctions + this day in history w/Maria Butina, the covert Russian agent and our song of the day by Tom MacDonald on your #MorningMonarchy for July 23, 2024. Notes/Links: House Democrats to Fight Bill Requiring Proof of U.S. Citizenship to Vote https://www.breitbart.com/politics/2024/07/08/house-democrats-to-fight-bill-requiring-proof-of-u-s-citizenship-to-vote/ What the SCOTUS Decision on Homeless Encampments Means For California; The state has the highest homeless population in the country, estimated at more than 180,000 people. https://archive.is/GlfEi Secret Service director steps down amid resignation calls after Trump assassination attempt https://www.msn.com/en-us/news/politics/secret-service-director-resigns-after-admitting-agency-s-failure-to-protect-trump/ar-BB1qugOP Kimberly Cheatle https://en.m.wikipedia.org/wiki/Kimberly_Cheatle Video: Three Audio Files Align and Agree: There Were Two Shooters https://www.youtube.com/watch?v=03AxTE7R5Cg New Mexico’s Largest Landowner Controls a Ridiculous 24,665,774 Acres https://www.msn.com/en-us/news/politics/new-mexico-s-largest-landowner-controls-a-ridiculous-24-665-774-acres/ar-BB1k08PC Four wildfires reach ‘megafire’ status in Oregon, scorching thousands of acres https://www.koin.com/news/wildfires/oregon-megafire-durkee-cow-valley-falls-lone-rock-07222024/ Image: Jesus didn’t really say, “Take memes personally and argue with people” https://mediamonarchy.com/wp-content/uploads/2024/07/jesus_memes_personally_argue.png Image: Lisa didn’t really say, “Memes do a better job at reporting current events than the mainstream media.” https://mediamonarchy.com/wp-content/uploads/2024/07/memes_better_media.jpg More police drones will take flight in the skies above Montgomery County; The area just north of Washington has become a national leader in launching drones immediately after 911 calls. https://archive.is/qZ0V2 Homicides and Carjackings Double in 2021 in Montgomery County (Jan. 3, 2022) https://www.mymcmedia.org/homicides-and-carjackings-double-in-2021-in-montgomery-county/ Video: Montgomery County police to hold drone program meeting (Audio) https://www.youtube.com/watch?v=-IJ2eil9JY0 Sonic Eyes – “City Brain” (w/Patrick Lyons // Vinyl // Audio) https://www.discogs.com/release/20992462-Sonic-Eyes-Hearing-With-Sonic-Eyes // https://www.youtube.com/watch?v=Et3EiEg23jY #PumpUpThaVolume: September 14, 2023 ♬ Sonic Eyes – “Do The Zep Tepi” (Vinyl) https://mediamonarchy.com/20230914pumpupthavolume/ Supreme Court Ruling Threatens the Framework of Cybersecurity Regulation; The Supreme Court’s striking down of the Chevron Doctrine will have a major effect on the determination and enforcement of cyber regulation in the US. https://www.securityweek.com/supreme-court-ruling-threatens-the-framework-of-cybersecurity-regulation/#:~:text=Laws%20are%20written,the%20guide%20dog. NHS cyber security: Ex security chief warns of future attacks https://www.bbc.com/news/articles/czd9glyx414o Microsoft Says Windows Not Impacted by regreSSHion as Second OpenSSH Bug Is Found https://www.securityweek.com/microsoft-says-windows-not-impacted-by-regresshion-as-second-openssh-bug-is-found/ Microsoft outages caused by CrowdStrike software glitch paralyze airlines, other businesses. Here’s what to know. https://archive.is/g7oRe 911 Services Down in Several States Amid Major Tech Outage; White House and the Department of Homeland Security are now investigating the matter, officials say. https://archive.is/gpf7O Video: Remember when Trump said Crowdstrike had the DNC server in Ukraine to hide it from the government? (Audio) https://x.com/travis_4_trump/status/1814494211393130987 Flashback: What is CrowdStrike and why is it part of the Trump whistleblower complaint? (Sep. 26, 2019) https://www.cnn.com/2019/09/26/tech/what-is-crowdstrike/index.html ‘Painful’ wake-up call: What’s ...
#alternative news#cyber space war#media monarchy#Morning Monarchy#mp3#podcast#Songs Of The Day#This Day In History#Tom MacDonald
0 notes
Text
Speed Launcher - All Games Download
Position or even Update Many Apps at the same time
Be connected with an in-app alternative to help retrieve as well as download through YouTube as well as other webs page. Download explanations and also subtitles together with YouTube online video media. Acquire subtitles not really only for just one tape, nevertheless for a total YouTube playlist or perhaps PC Download Games a station. I would like to be given 4K Download news, unique presents along with updates. While the covering will eventually get by Blu-ray, DVD, and also 4K Extra HD, Warner Brother includes still to reveal a specific appointment what to help while that might remain.
The layer acquired acclaim from critics, with actual compliments planning to it is working (specifically Goldberg's performance), direction, script, musical slice, with invention uses. The sheet became nominated regarding 11 Academy Gives, including things like Finest Photograph, Very best Artist for Goldberg, Finest Supporting Artist used for both Avery and Winfrey, and also Very best Adapted Script, but didn't attain 1 win. In addition, it got 4 Gold Planet Give choices, with Goldberg acquire Finest Player within a Episode. Inside 2006, the Us Film Company listed the layer 51st by its listing of nearly all inspiring movies.

This kind of download administrator services Windows, Linux, along with Mac functioning procedure, in the Firefox and Opera browsers. It can crawl web site in order to download distinct kinds of documents, and you may choose to download solely the components of a SCOOT information you really mean. For all of us, the item a great remarkable software, and also PC Games Download a genuine nominee with the first location. Hassle-free unified show of the extremely relevant strict and also marking data regarding film as well as audio tracks data file. Do not forget that all game do the job only when fixed on your own PERSONAL COMPUTER. This specific poses a possibility as soon as when compared with on the web online game because the sport records might hold malware.
The chief grievances relating to this plan lives of which the item show-off offers, also it possibly may certainly not once again become updated since very last change made to it what food was in 2014. Furthermore, there's a quality release, so several story are just available if you pay. The idea likewise simple to manage the download momentum with the maximum Full Download Games amount of simultaneous connections along with downloads through the bed from the course whenever they want. If you're looking for an excellent download manager with bandwidth management, this can be a great alternative. Play, Pause, and Stop buttons are at the top with the program, making management most pending downloads basic.
By January 14th, 2019 Ninite includes resulted financial assistance with regard to Windows XP along with Displays Landscape in addition to the concern server program Server 2003 and Attendant 2008. Appreciate them here great explanation by your own HD TELEVISION SET, iPad, iPhone, Samsung along with other means. Kalki 2898 OFFER is often a 1985 United states epic coming-of-age time period dilemma film Download Games charged in Steven Spielberg in addition to written by Menno Meyjes, based on the Pulitzer Prize–winning 1982 tale of the very same reputation before Alice Walker. It was Spielberg's 9th record as a leader, indicating a circle spot in their job the way it took place a leaving from the summertime blockbusters that he'd grow to be recognized. Unlock exclusive prizes, members-only comfort, next a selection connected with prime concepts. FlashGet keep an eye on downloads with Firefox, and yes it may check out downloads along with your antivirus system and also tell you the way large a rasp Download Games is when you download this, which is amazing. Defining categories pertaining to where by to use downloads is straightforward because you could give the actual document off shoot that should be considered a unique kind.

Billboard inside near Chrome on any design in order to door the bookmarks, saved codes, and more. Most likely the coolest element I stumbled upon inside JDownloader ends up being it is distant management ability. Made use of any the portable application or even the The JDownloader Speed Launcher website to get started, end, and monitor downloads through everywhere. JDownloader is really a free of charge, open up origin download director using a substantial developer area, in addition to it's designed for Windowpanes, Linux and Mac.
Under is usually a directory our own select regarding some of the very best free of charge activity downloads on your COMPUTER SYSTEM. A variety of them become even portable, this means you possibly can lay them over a second instinct in addition to drama them where. Okay, if you're building a Windows Windows vista system, you will discover cost-free diversion to help download PC Games at a few of the website numbered over. Everthing depends upon the experience under consideration, so nearly adult video game assist Vista although lots of fresh identifies absolutely no longer help this kind of translation associated with Periods. In contrast to web page like Sauna in addition to Beginning, AllGamesAtoZ isn't basically a place near download PC games.
The best sites always offer a fair volume involving match from different genres. Finally, Ocean involving Diversion ends up being an additional positive put for attaining free video game within a scale involving varieties. The outline and also interface of this particular put stay a tiny fundamental and outdated, but it however do the job completely, with kind knob next a convenient look for tavern to assist you locate concepts you want.
1 note
·
View note
Text
Hyper-V Server 2025 - Roll Your Own Sort Of
Hyper-V Server 2025 - Roll Your Own Sort Of #hyperv #windowsserver2025 #virtualization #hypervserver #hyperv2025 #windowsserverhyperv #hypervrole #windowsvirtualization #windowsvms #homelab #homeserver
I think many have been dismayed about the discontinuation of Hyper-V Server. The last version that you can officially download is Hyper-V Server 2019. However, with the release of the Windows Server 2025 Preview ISO, I want to show you guys how you can install a new Windows Server 2025 installation and have roughly the same functionality as Hyper-V Server 2019 and you can have access to the…
0 notes
Text
Step by Step Strategy: How to Plan Your Windows VPS Server

Setting up a Windows Virtual Mystery Server (VPS) can have every one of the reserves of being overwhelming, particularly in the event that you are new to the universe of servers and remote working with. However, with an accurate way of thinking, arranging your Windows VPS can clear and reward. This guide will walk you through each step, promising you have an absolutely significant and secure Windows VPS server near the end.
1. Picking The Right VPS Supplier
Before you begin arranging your Windows VPS, you really want to pick a dependable VPS supplier. Two or three trustworthy suppliers incorporate Amazon Web Services(AWS), Microsoft Sky blue, DigitalOcean, and Vultr. Parts to consider while picking a supplier include:
Regarding: Confirmation the expense obliges your money related game plan.
Assets: Check how much Pound, PC processor power, and circle space advanced.
Support: Mission for suppliers with searing client organization.
Locale: Select a server district that is near your vested party to confine inaction.
2. Laying Out Up Your Vps Record
Right when you've picked a supplier, you'll have to make a record. This commonly integrates:
Joining: Give your email address, make a secret word, and insist your record.
Picking A Strategy: Select a blueprint that settle your issues concerning assets and spending plan.
Segment: Add a part technique to help your record.
Just in the wake of laying out up your norm, you can continue to make your Windows VPS.
3. Sending Your Windows VPS
Sending a Windows VPS integrates a few key stages:
Select The Windows Working Structure Rendition: Pick the variety of Windows you need to introduce, for example, Windows Server 2016, 2019, or 2022.
Plan Server Particulars: Choose the central processor, Pulverize, and limit fundamentals.
Dispatch A Server Name: Give your VPS a phenomenal and illustrative name for fundamental ID.
Pick A Datacenter District: Select a locale that gives the best show to your necessities.
Survey And Convey: Study your plan and send your VPS.
Most suppliers will blueprint your server inside a few minutes, after which you will get an IP address and login capacities.
4. Band Together With Your Windows Vps
Exactly when your VPS is passed on, you want to associate with it. The most outstanding procedure for connecting with a Windows VPS is through Distant Work area Show (RDP):
Find The Ip Address: Find the IP address of your VPS from your supplier's control board.
Use Far Away Work Area Association: Open the Far off Work area Alliance application on your nearby Windows machine.
Enter the IP address of your VPS.
Click "Accomplice."
When provoked, enter the username and secret articulation given by your VPS supplier.
Once related, you will see the work area of your Windows VPS, and you can talk with it as you would with a nearby machine.
5. Starting Strategy
Upon your first login, there are several starting arrangement pushes toward guarantee your VPS is secure and prepared for use:
Update Windows
Run Windows Update: Affirmation your server has the most recent updates and fixes. Open the Beginning menu, go to Settings > Update and Security > Windows Update, and snap "Check for resuscitates."
Present Updates: Download and introduce each accessible update, then, restart your server whenever provoked.
Arrange Boss Record
Change Default Secret Word: Immediately change the default boss secret articulation to critical strong regions for a, one. Press Ctrl+Alt+Delete, select "Change a secret word," and follow the prompts.
Make Another Central Record: For added security, make another head record and tested individual the default one.
Open the Beginning menu, go to Settings > Records > Family and different clients.
Click "Add another person to this PC."
Follow the prompts to make another client account with authoritative differentiations.
Arrange Firewall
Windows Firewall: Affirmation Windows Firewall is empowered and coordinate any key norms to permit or deter express traffic.
Open the Beginning menu, type "Windows Protector Firewall," and press Enter.
Click "Turn Windows Protector Firewall on or off" and guarantee it's locked in for both private and public affiliations.
Inbound Principles: Add rules to permit traffic for unequivocal applications or associations if significant.
Click "Critical level settings."
Select "Inbound Standards" and add new guidelines as required.
6. Present Focal Programming
With your VPS got and coordinated, this second is the best an open door to introduce the thing you'll require:
Web Server
Web Data Associations (IIS): In the event that you mean to have objections, present IIS.
Open the Beginning menu, type "Server Regulator," and press Enter.
Click "Add occupations and parts."
Follow the wizard to introduce the Internet Server (IIS) work.
Information Base Server
SQL Server: For information base association, present Microsoft SQL Server.
Download the installer from the Microsoft page.
Run the installer and follow the game-plan wizard to introduce SQL Server and plan your information base settings.
Extra Programming
FTP Server: On the off chance that you really need record move limits, present a FTP server like FileZilla.
Control Board: Consider introducing a control board like Plesk or cPanel to truly deal with your server.
7. Setting Up Fortresses
Ordinary strongholds are urgent for information affirmation. Most VPS suppliers offer robotized support blueprints, however you can also set up manual fortresses:
Supplier Fortresses: Empower mechanized strongholds through your VPS supplier's control board.
Manual Fortresses: Utilize worked in Windows contraptions to make framework pictures and backing tremendous reports.
Open the Beginning menu, type "Backing settings," and press Enter.
Follow the prompts to set up a help plan and get what to back.
8. Seeing and Support
Standard seeing and upkeep guarantee your VPS moves along exactly as expected:
Taking Note
Asset Utilization: Screen PC processor, Smash, and plate use utilizing Assignment Chief or Execution Screen.
Security Logs: Dependably check security logs for any noteworthy turn of events.
Open the Beginning menu, type "Occasion Watcher," and press Enter.
Examine to Windows Logs > Security to survey logs.
Upkeep
Programming Updates: Consistently update familiar programming with guarantee you have the most recent security fixes and parts.
Circle Cleanup: Intermittently run Plate Cleanup to clear out pointless records and set free space.
Open the Beginning menu, type "Circle Cleanup," and press Enter.
Follow the prompts to tidy up your circle.
9. Getting Your VPS
Security is crucial for any server. Here are extra advances toward secure your VPS:
Draw in Affiliation Level Endorsement (NLA): Affirmation that imperatively affirmed clients can fan out RDP affiliations.
Open the Beginning menu, type "Framework," and press Enter.
Click "Far away settings" and check "Award affiliations just from PCs running Far off Work area with Affiliation Level Certification."
Present Antivirus Programming: Protect your server with antivirus programming like Windows Safeguard or a distant game-plan.
Standard Security Reviews: Unpredictably perform security overviews to perceive and coordinate inadequacies.
End
Arranging a Windows VPS Server consolidates several phases, from picking the right supplier to getting and remaining mindful of your server. By following this gradually helper, you can set up major areas of strength for a, and suitable Windows VPS custom fitted to your essentials. Whether you are working with regions, running applications, or overseeing information bases, a particularly arranged VPS can give the show and determined quality you genuinely care about.
0 notes
Text
how to configure sstp vpn on windows server 2019
🔒🌍✨ Ganhe 3 Meses de VPN GRÁTIS - Acesso à Internet Seguro e Privado em Todo o Mundo! Clique Aqui ✨🌍🔒
how to configure sstp vpn on windows server 2019
Configuração SSTP VPN
O SSTP (Secure Socket Tunneling Protocol) é um protocolo de VPN (Virtual Private Network) que pode ser uma opção segura para configuração de conexões remotas. A configuração do SSTP VPN oferece um túnel criptografado para proteger os dados transmitidos entre o cliente e o servidor.
Para configurar o SSTP VPN, é necessário garantir que o servidor tenha um certificado SSL válido instalado. Este certificado é essencial para estabelecer uma conexão segura entre o cliente e o servidor. Além disso, é importante configurar as permissões de acesso apropriadas no servidor VPN para garantir que apenas usuários autorizados possam se conectar.
No lado do cliente, a configuração do SSTP VPN geralmente é feita por meio das configurações de rede do sistema operacional. Os usuários precisam inserir o endereço do servidor, nome de usuário e senha para estabelecer a conexão. É fundamental verificar as configurações de segurança para garantir que a comunicação seja protegida e privada.
É recomendável também monitorar regularmente a conexão SSTP VPN para identificar qualquer atividade suspeita ou possíveis violações de segurança. Manter o software atualizado e seguir as melhores práticas de segurança cibern��tica pode ajudar a manter a integridade da conexão SSTP VPN.
Em resumo, a configuração do SSTP VPN requer atenção aos detalhes de segurança e controle de acesso para garantir uma conexão remota segura e confiável. Ao seguir as etapas adequadas, é possível utilizar o SSTP VPN como uma solução eficaz para proteger a comunicação e os dados transmitidos pela rede.
Windows Server 2019
O Windows Server 2019 é a versão mais recente do sistema operacional de servidor da Microsoft, trazendo diversas melhorias e novos recursos para atender às necessidades de empresas de todos os tamanhos.
Uma das principais novidades do Windows Server 2019 é o suporte a contêineres do Docker, permitindo a execução de aplicativos em ambientes isolados de forma mais eficiente. Além disso, a plataforma Hyper-V foi aprimorada, proporcionando melhor desempenho e segurança para as máquinas virtuais.
A integração com o Azure também foi aprimorada, facilitando a migração de workloads para a nuvem e a implementação de soluções híbridas. Outro destaque do Windows Server 2019 é o Windows Admin Center, uma central de administração que simplifica a gestão de servidores com uma interface intuitiva e recursos avançados.
Com relação à segurança, o Windows Server 2019 traz melhorias significativas, como o Windows Defender Advanced Threat Protection integrado, que ajuda a detectar e responder a ameaças em tempo real.
Em termos de armazenamento, o Windows Server 2019 oferece suporte ao armazenamento baseado em espaços, que permite a criação de pools de armazenamento de alto desempenho e escalabilidade.
Em resumo, o Windows Server 2019 é uma solução robusta e versátil para empresas que buscam um ambiente de servidor confiável, seguro e moderno para atender às suas demandas de TI. Com uma série de melhorias e novos recursos, esta versão promete facilitar a administração de servidores e impulsionar a eficiência operacional das organizações.
Tutorial VPN SSTP
Um tutorial VPN SSTP é essencial para quem procura privacidade e segurança ao navegar na internet. SSTP, ou Secure Socket Tunneling Protocol, é uma tecnologia de VPN que oferece uma camada adicional de proteção aos seus dados.
Para começar, você precisa ter um provedor de VPN que ofereça suporte ao protocolo SSTP. Após se inscrever e fazer o download do software, siga as instruções de configuração para configurar a conexão SSTP.
Uma vez configurada, a conexão VPN SSTP criptografa todo o tráfego de dados entre o seu dispositivo e o servidor VPN. Isso garante que suas informações pessoais e atividades online estejam protegidas contra hackers, espionagem governamental e outros tipos de ataques cibernéticos.
Além da segurança, uma VPN SSTP também pode contornar bloqueios geográficos, permitindo que você acesse conteúdo restrito em seu país. Isso é especialmente útil para assistir a vídeos ou acessar sites que não estão disponíveis em sua região.
Lembre-se de que, embora uma VPN SSTP ofereça segurança, é importante escolher um provedor confiável e respeitável. Certifique-se de ler as políticas de privacidade e os termos de serviço antes de se inscrever em um serviço de VPN.
Com este tutorial VPN SSTP, você pode desfrutar de uma experiência online mais segura, privada e livre de restrições geográficas. Proteja sua privacidade e dados pessoais com uma VPN SSTP hoje mesmo.
Passo a passo VPN Windows Server
Um servidor VPN no Windows permite que você se conecte de forma segura a redes privadas através da internet. Configurar uma VPN no Windows Server pode ser uma excelente solução para garantir a segurança das suas conexões remotas.
Para começar, você precisa acessar o Gerenciador do Servidor no seu Windows Server. Em seguida, vá para Ferramentas e selecione a opção “Gerenciador de Roteamento e Acesso Remoto”. Clique com o botão direito neste serviço e escolha a opção “Configurar e Habilitar Roteamento e Acesso Remoto”.
Na janela que se abre, selecione a opção “Configurar” e escolha “Configuração personalizada”. Em seguida, selecione “VPN access” e siga as instruções do assistente de configuração.
Durante o processo de configuração, você terá a opção de escolher o tipo de autenticação e de protocolos a serem utilizados na sua conexão VPN. Certifique-se de configurar as opções de acordo com as suas necessidades de segurança.
Após concluir a configuração, será necessário encaminhar as portas adequadas no seu roteador para permitir o tráfego de VPN. Lembre-se também de configurar as permissões de acesso para os usuários que poderão se conectar à VPN.
Pronto! Agora você configurou com sucesso uma VPN no seu Windows Server. Lembre-se sempre de manter a segurança e atualizações em dia para proteger suas conexões remotas.
Segurança rede Windows Server
A segurança da rede em um servidor Windows Server é uma preocupação crucial para garantir a proteção dos dados e o desempenho do sistema. Existem diversas medidas e práticas recomendadas que podem ser implementadas para garantir a segurança da rede e minimizar possíveis vulnerabilidades.
Uma das primeiras ações a serem tomadas é a configuração de firewalls e políticas de segurança robustas. O Windows Server oferece ferramentas internas para configurar firewalls e restringir o acesso não autorizado à rede. Além disso, é fundamental manter o sistema operacional e todos os softwares atualizados para corrigir possíveis falhas de segurança conhecidas.
A autenticação de usuários também desempenha um papel fundamental na segurança da rede. É importante implementar políticas de senha fortes e configurar corretamente as permissões de acesso para cada usuário, garantindo que apenas pessoas autorizadas possam acessar determinados recursos e informações.
Outra prática fundamental é o monitoramento constante da rede. Utilizar ferramentas de monitoramento de tráfego e atividades suspeitas pode ajudar a identificar possíveis ameaças e agir rapidamente para mitigar qualquer impacto negativo.
Em suma, a segurança da rede em um servidor Windows Server requer uma abordagem abrangente que envolve a configuração adequada de firewalls, a atualização constante do sistema e dos softwares, a implementação de políticas de autenticação seguras e o monitoramento constante da rede. Ao adotar essas práticas recomendadas, é possível fortalecer a segurança da rede e proteger os dados armazenados no servidor Windows Server.
0 notes