#Threat And Risk Assessment
Text
#Alternate explanation: if he deliberately didn’t transfer Hera to the Urania Minkowski would kill him when she woke up tags by @specialagentartemis regarding this post
ngl this was the third possibility that occurred to me and I considered including it in the post
#Jacobi doing a hurried threat assessment while attempting to drag 4 unconscious people at once#how likely is it that they would accept 'i didn't have much time' as an excuse#ehhhhh better not risk it#wolf 359
8 notes
·
View notes
Text
Advanced Persistent Threats: Understanding the Characteristics, Tactics, and Strategies for Prevention and Mitigation in Today's Cyber Landscape
A detailed read on Cyber security in today's digital landscape. Happy Sunday everyone!
Advanced Persistent Threats (APTs) are a type of cyber attack that is specifically targeted at organizations or individuals to steal sensitive information or disrupt operations. These attacks are carried out by highly skilled and organized hackers who use sophisticated techniques to gain access to networks and systems. In this paper, we will discuss APTs in detail, including their…

View On WordPress
#Advanced Persistent Threats (APTs)#Cyber attack mitigation#Cyber attack prevention#Cyber risk management#cyber threats#Cybersecurity#Data protection#Employee education#Endpoint protection#Incident response#Least privilege#Network segmentation#Security assessments#Security audits#Threat intelligence
2 notes
·
View notes
Text
the more zoombombings i experience (always targeted at specific dates + topics + people around Indigenous, Jewish, and/or trans healing, solidarity, and organizing) the more infuriated i become with this one professor who insisted on ~“avoiding zoombombings”~ by making the zoom link different weekly + hard to find + verified by email log-in + use of legal names -- when his class was reifying ideas of “primitive” architecture and Western European white supremacy+colonial-imperialism and binary gender+sex
just bro, you’re not remotely a target
#like very very many of us suck at accurate risk/threat assessment yes#but you are literally doing the work of inculcating the very ideology of Romans White Christians Empire Ideal#and perpetuating the misunderstanding that violation and aggression are random#slash are suggesting you're countercultural?? because Artistry??#the extent to which i have wanted to whistleblow professors (but am aware their institutions are Fully Backing Them slash Worse)#huge part of why i vet not just orgs or curricula but specific hosts before accepting multi-part work anymore
5 notes
·
View notes
Text
Comprehensive Risk Assessment & Security Consulting Services in Dubai: DSP Consultants' Expertise
In today's evolving threat landscape, ensuring the safety and security of assets, people, and infrastructure is paramount for businesses. DSP Consultants, a leading firm in Dubai, provides expert comprehensive risk assessment services designed to address these concerns. Our approach is rooted in a holistic understanding of the unique risks faced by organizations across various industries, including commercial, industrial, and governmental sectors.

Tailored Solutions for Unique Needs
At DSP Consultants, we recognize that no two businesses face identical security challenges. Therefore, our security risk assessment consultants work closely with clients to deliver customized solutions that address specific vulnerabilities and threats. Our process begins with a thorough analysis of the client’s operations, identifying potential risks such as physical threats, cybersecurity breaches, operational inefficiencies, or external risks posed by environmental factors.
Through this analysis, we help clients design and implement effective risk management strategies. Our focus is not just on identifying immediate concerns but on building long-term security resilience. Our team evaluates the potential impact of risks and formulates preventive policies and procedures that enable businesses to operate confidently, even in unpredictable environments.
Comprehensive Risk Assessment: A Strategic Necessity
A comprehensive risk assessment goes beyond basic security checks. It encompasses both strategic and tactical measures to mitigate risk at all levels of the organization. Our team of seasoned experts utilizes cutting-edge technology and best practices to offer insights that are practical and actionable. From assessing physical security measures and ensuring regulatory compliance to evaluating technology vulnerabilities and emergency preparedness, DSP Consultants provide a 360-degree view of organizational risks.
We also extend our expertise to help clients mitigate emerging risks, such as those related to cybersecurity, supply chain vulnerabilities, and employee safety in today’s dynamic environment. By addressing both traditional and modern security challenges, we empower clients to safeguard their interests in a proactive, informed manner.
Expert Team and Unwavering Commitment
What sets DSP Consultants apart is our team of highly skilled professionals with decades of experience in risk assessment and security consulting. Our consultants bring deep industry knowledge and expertise to every project, ensuring that our clients receive top-tier advisory services. Whether designing security protocols for a high-profile event, conducting in-depth assessments for multinational corporations, or ensuring regulatory compliance for government projects, our team consistently delivers the highest level of service.
Our commitment to confidentiality and ethical standards underpins every engagement we undertake. This ensures that our clients' sensitive information is always protected, allowing them to trust us with their most critical security needs.
Why Dubai Businesses Choose DSP Consultants
Dubai, being a global hub for trade, tourism, and innovation, requires advanced security strategies to safeguard against risks that are increasingly complex and diverse. Businesses here need to remain vigilant to both local and global threats. This is where DSP Consultants' comprehensive risk assessment services come in. We assist companies in Dubai in anticipating and addressing security challenges before they escalate, ensuring operational continuity and peace of mind.
DSP Consultants’ extensive knowledge of the local market and regulations in Dubai allows us to provide clients with solutions that are not only effective but also compliant with regional standards. Our team stays updated on evolving security trends and technological advancements, ensuring that our clients receive the most current and effective solutions.
Conclusion
DSP Consultants offers unmatched expertise in comprehensive risk assessment and security risk assessment consulting in Dubai. Our tailored solutions help businesses mitigate risks, protect assets, and ensure operational efficiency in the face of a rapidly changing threat landscape. With a commitment to excellence, confidentiality, and ethical conduct, we are the trusted choice for companies looking to enhance their security posture.
Whether you are looking to secure a high-profile project, protect critical infrastructure, or improve corporate risk management strategies, DSP Consultants is your dedicated partner in security and risk management.
#Security risk assessment consultants#Security risk assessment consultancy#Security risk analysis#Security risk consultants#Security threat analysis
0 notes
Text
Risk Management: Mitigating Potential Threats in the 21st Century
Discover how mastering risk management can turn potential threats into opportunities for success in the 21st century. Dive into cutting-edge strategies and tools for project management. Subscribe now to stay ahead in your professional journey!
#21stcenturybusiness#contingencyplanning#cuttingedgetools#EmpoweredJourney#HafsaReasoner#mitigatingthreats#modernchallenges#proactiveriskmanagement#ProfessionalDevelopment#projectmanagement#projectsuccess#riskassessment#riskmanagement#21st century business#contingency planning#cutting-edge tools#Empowered Journey#Hafsa Reasoner#mitigating threats#modern challenges#proactive risk management#professional development#project management#project success#risk assessment#risk management
0 notes
Text
youtube
#Myth of Helplessness#Myth of Randomness.#bad guys#How To Protect Yourself in An Uncertain World with Sam Rosenberg | KAJ Masterclass Join Sam Rosenberg#author and internationally recognized expert on personal security#as he shares invaluable insights from his extensive experience protecting high-profile individuals like Tom Cruise and Warren Buffett. In t#Rosenberg demystifies the psychology of violence#debunking the and Discover the SAFE model of decision-making#learn to identify the universal patterns of behavior used by and understand the characteristics that distinguish potential threats. Rosenbe#drawn from his time as a U.S. Marine Corps officer and close protection specialist#will empower you to develop situational awareness#assess risks#and respond effectively in uncertain situations. Don't miss this opportunity to gain a survival mindset and live ready in an ever-changing#enhance your skills#or even appear as a special guest on my show! Schedule on my calendar at https://calendly.com/kajofficial Ready to take it further? Explore#Youtube
0 notes
Text
Cyberbiosecurity 101: protecting life sciences in the digital age - CyberTalk
New Post has been published on https://thedigitalinsider.com/cyberbiosecurity-101-protecting-life-sciences-in-the-digital-age-cybertalk/
Cyberbiosecurity 101: protecting life sciences in the digital age - CyberTalk


EXECUTIVE SUMMARY:
In May of 2017, the life sciences industry contended with the WannaCry campaign, one of the most widespread and destructive cyber attacks in history. It rapidly propagated across networks, encrypting data and systems; leaving organizations crippled and desperate.
Some life sciences groups permanently lost intellectual property or data. Others were forced to halt production of certain drugs and vaccines. The combination of costly system downtime and ransom demands left a few enterprises financially insolvent.
Why life sciences?
Cyber criminals perceive life sciences as an attractive target due to the intellectual property available on computer systems. Ninety-five percent of all cyber attacks in the life sciences sector center around intellectual property (IP).
For the life science sector, WannaCry served as a cyber security wake-up call. However, not every organization took adequate action and the threat landscape has grown more perilous in the years since.
Here’s what to know about preventing and defending against cyberbiosecurity threats:
Addressing the challenge
First, know where the problems are. Conduct a thorough risk assessment – one that’s specific to your organization’s unique network environment. Identify critical assets, including intellectual property, research data and other proprietary information. Implement layered defenses to mitigate risks. These include firewalls, intrusion detection systems and endpoint detection systems.
But that alone isn’t enough. Be sure to train your employees effectively. Provide education around cyber threats, including social engineering. Develop a cyber security-conscious culture, where everyone understands the importance of safeguarding information. Provide regular supplemental training to address evolving threats.
Beyond that, ensure that your organization’s software developers use secure coding practices. Regularly patch and update software to address vulnerabilities.
Develop and test incident response (IR) plans that are specific to cyberbiosecurity/incidents in the life sciences sector. As goes for any IR plans, establish communication channels, delegate roles and clarify responsibilities, all of which will hasten the response in the event of a breach. Practice tabletop exercises to simulate real-world scenarios.
Leverage threat intelligence and information sharing efforts. Participate in Information Sharing and Analysis Centers (ISACs) or working groups that are focused on cyberbiosecurity. This will enable your organization to learn from peers and to exchange tactics. Your organization may also wish to collaborate on joint prevention and defense initiatives.
Cyber and physical system integration
Another aspect of the cyberbiosecurity situation to consider is reliance on cyber-physical systems. These types of systems integrate cyber-based control mechanisms into physical infrastructure. Examples include building automation systems and certain types of data collection and analysis instruments.
To protect these systems, ensure that your organization limits physical access to critical infrastructure and the toggles that control infrastructure functions. In addition, consider installing surveillance cameras and monitor access points.
Further, ahead of acquiring new cyber-physical technology, assess the security practices of the vendors who are providing the equipment. Ensure that vendors follow cyber security best practices.
More recommendations for CISOs
Have you completed all of the aforementioned recommendations? Great work! Take the next step: thoroughly test for vulnerabilities. Based on the results of the testing, devise and implement a remediation strategy. This will significantly minimize cyber risk. If you’re looking for experts with deep knowledge concerning how to resolve cyber security gaps, click here.
Closing thoughts
The life sciences community has an opportunity (and perhaps, an obligation) to lead when it comes to securing digital resources. Investing in cyberbiosecurity ensures the secure future of scientific research, life-saving vaccines, and life-changing pharmaceutical treatments.
For more insights like this, please see CyberTalk.org’s past coverage. Lastly, subscribe to the CyberTalk.org newsletter for timely insights, cutting-edge analyses and more, delivered straight to your inbox each week.
#analyses#Analysis#assessment#assets#automation#biosecurity#breach#Building#Cameras#challenge#CISOs#coding#collaborate#communication#Community#computer#critical infrastructure#cutting#cyber#cyber attacks#cyber criminals#cyber risk#cyber security#Cyber Threats#cyber-physical#Cyberbiosecurity#data#data collection#defense#defenses
0 notes
Text
Theres a common argument that goes like "how can you say the threat I fear isn't real, look at all the things I do to protect myself from it!" And it's not clear how you even counter it. Except just saying "I think you are bad at assessing risk"
8K notes
·
View notes
Text
Cybersecurity Report: Protecting DHS Employees from Scams Targeting Personal Devices
🔒 DHS Cybersecurity Alert! 🔒 Scammers targeting personal devices threaten national security. Our new report reveals these risks & offers robust solutions - MFA, security software, cybersecurity training & more. Safeguard yourself & critical operations!
Introduction
The digital age has ushered in an era of unprecedented connectivity and technological advancements, but it has also given rise to a new breed of threats that transcend traditional boundaries. Cybercriminals are constantly evolving their tactics, exploiting vulnerabilities in both organizational systems and personal devices to gain unauthorized access, steal sensitive data, and…

View On WordPress
#access controls#antivirus#awareness campaigns#best practices#collaboration#cyber resilience#cybersecurity#cybersecurity training#data backup#data protection#DHS#firewall#government#impersonation#incident response#insider threats#malware#multi-factor authentication#national security#password management#personal device security#phishing#physical security#public outreach#risk assessment#scams#social engineering#software updates#threat intelligence#VPN
1 note
·
View note
Text
youtube
Are you aspiring to step into the crucial position of a risk manager? In this video, we delve deep into the pivotal role of a risk manager in the ever-evolving cybersecurity landscape. 👉 Subscribe to my channel to stay tuned: / @tolulopemichael001
In today's video, we'll explore the responsibilities, skills, and certifications essential for thriving in the role of a risk manager. From conducting risk assessments to overseeing mitigation strategies, we uncover this vital position's diverse and challenging aspects.
Communication is key in cyber security, and we emphasize its importance along with other critical soft skills like decision-making and problem-solving. Whether you're a seasoned professional or just starting out, we provide valuable insights into breaking into the field and advancing your career.
Discover the vast growth potential and lucrative opportunities in cyber security risk management. With dedication and staying abreast of the latest trends, you can pave your way to Senior Management roles or specialize in areas like crisis management and strategic risk consulting.
#cyber security risk manager#risk manager#the role of a risk manager#risk management#unlocking the secrets of cyber grc#cybersecurity#cybersceurity risk manager role#cybersecurity career#cyber threats assessment#career growth in cyber security#Youtube
0 notes
Text

How to Protect Intellectual Property (IP) Data from Modern Bad Actors?
Safeguard Intellectual Property IP Data from Insider and outsider bad actors Kirit shares 6 steps roadmap for the protection of IP data.
#Best IP Data Security Practices#Encrypting Intellectual Property Data#Insider Threat to IP Data#Intellectual Property (IP) Data#Intellectual Property Data#IP Data Protection#IP Data Protection Strategy#IP Data Risk Assessment#IP Data Security#Outsider Threat to IP Data#Safeguard IP (Intellectual Property) Data
0 notes
Text

https://goodlawproject.org/crowdfunder/nhs-cyp-guidance/?fbclid=PAZXh0bgNhZW0CMTEAAaadkVMoRUHpcFptnjlifnc1xJ0i7YGVi78tfv2vEXVaVIQDPTEp1-ozNcY_aem_AfqNP9xEERFn6GRCZCIP7B2RriLi8ZN7pVAFzmNwdvqIXW0nmc1mTe5Hq0UV3xC6VPWdYe1x64wHk7O6-HPOhIdf
Please share, tag someone who could bring this to a lot of people, and post to other platforms. Not originally mine, idk who is the source of the screenshots.
Image ID under cut
Image ID:
In thick white text on black background-> NHS ENGLAND ARE PLANNING A HONEYPOT WHERE THEY SEND ALL KIDS ON GIDS WAITLIST TO CAHMS TO HAVE THEM BE ASKED IF THEY ARE TAKING BLOCKERS/HRT VIA PRIVATE OR DIY ROUTES
Text is broken and in the middle is an excerpt from a leaked nhs document-> a) For medication sourced directly (e.g via the internet), explain the increased risks of harm due to the unregulated nature of these medicines/products. These may include the use of counterfeit chemicals, unsafe/unknown ancilliary ingredients or variability of potency etc. More information can be found here (link to nhs website). // b) Do not initiate or continue prescribing puberty surpressing hormones or gender affirming hormones. The General Medical Council's guidance to medical professionals on 'bridging prescriptions (a course of endocrine intervention managed by a healthcare professional outside of the specialised gender service while an individual is waiting to be seen) does not apply to care offered to young people under 18 years of age. // c) If the child/young person or their carer disregards your advice and you consider that this puts the child/young person at increased risk, then a safeguarding referral might also be appropriate in line with standard safeguarding approaches. Discuss with your line manager and your organization's safeguarding team.
Thick white text on black background continues-> ANY WHO SAYS YES AND DO NOT DESIST FROM DOING SO WILL BE THREATENED WITH SAFEGUARDING REFERRAL (TAKEN INTO STATE CARE)
Next image ID:
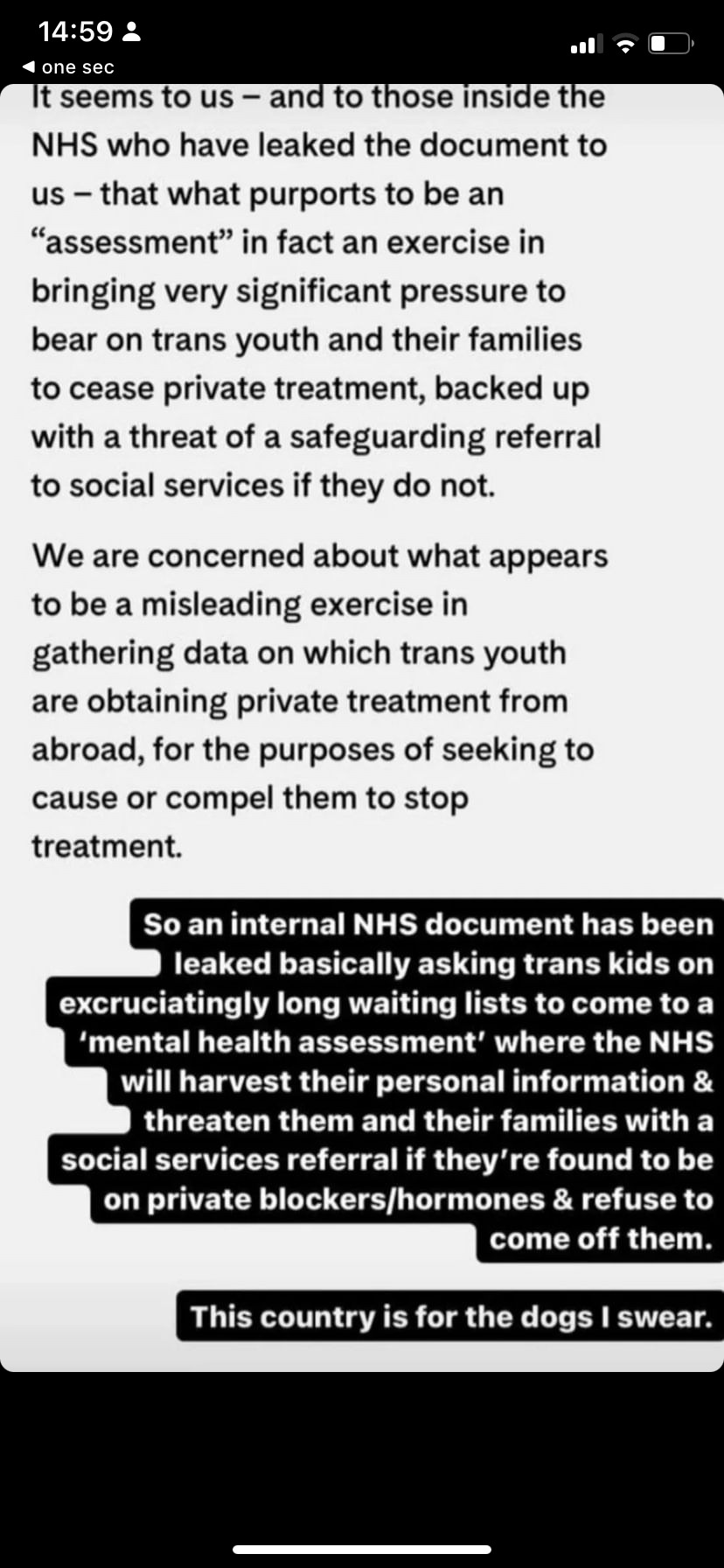
In black text on white background, from the news article linked above-> It seems to us - and to those inside the NHS who have leaked the document to us - that what purports to be an "assessment" in fact an exercise in bringing very significant pressure to bear on trans youth and their families to cease private treatment, backed up with a threat of a safeguarding referral to social services if they do not. // We are concerned about what appears to be a misleading exercise in gathering data on which trans youth are obtaining private treatment from abroad, for the purposes of seeking to cause or compel them to stop treatment.
In the same thick white text on black background as previous image-> So an internal NHS document has been leaked basically asking trans kids on excruciatingly ling waiting lists to come to a 'mental health assessment' where the NHS will harvest their personal information & threaten their families with a social services referral if they're found to be on private blockers/hormones & refuse to come off them. // This country is for dogs i swear.
#trans pride#transblr#trans safety#trans tips#trans uk#uk trans#uk#england#trans ftm#trans mtf#trans nonbinary#trans man#trans woman#trans male#trans female#trans masc#trans femme#transmasculine#transmasc#trans feminine#transfem#trans enby#enby#nonbinary#gender nonconforming#genderqueer#gender queer#gnc#lesbian#gay
5K notes
·
View notes
Text
Navigate Dubai's Security Risk Landscape with Confidence: DSP Consultants' Risk Analysis Expertise
Dubai's bustling business scene brings exciting opportunities, but also potential security risks. At DSP Consultants, a leading name in security risk assessment consultants Dubai, we empower your organization to navigate this dynamic environment with utmost confidence.

More Than Just Risk Identification:
We transcend the traditional security risk analysis approach. Instead of simply identifying threats, we delve deeper. Our services encompass both theoretical and practical aspects of safety and protection. Through a collaborative process, we meticulously analyze your operations and existing risk management strategies. This fosters development of effective policies and procedures, enabling us to anticipate potential threats before they become serious problems.
Your Trusted Security Risk Partner:
Confidentiality and unwavering ethical standards are core values at DSP Consultants. Our team of security risk assessment consultants in Dubai boasts extensive experience within the region's unique security landscape. This wealth of knowledge ensures you receive the most reliable and high-quality services available.
The DSP Consultants Framework – Your Personalized Security Compass:
Our comprehensive framework incorporates three key elements:
In-depth Analysis: We utilize our proprietary Risk Navigator tool to conduct a thorough analysis of your operations. This tool evaluates risk factors and vulnerabilities specific to your industry and unique position within Dubai's dynamic environment. This in-depth assessment forms the foundation for our strategic planning process.
Strategic Planning: Based on the security risk assessment report findings, we develop customized strategies and proactive measures to effectively mitigate identified risks. This ensures you have a clear roadmap towards a more secure future for your organization.
Comprehensive Reports: We present clear and concise reports outlining the identified risks, mitigation strategies, and recommended action plans. These reports serve as your roadmap to navigate the ever-changing security landscape.
Partner for Peace of Mind:
Join forces with DSP Consultants, your trusted security risk assessment consultants in Dubai. Navigate the exciting world of Dubai with peace of mind, knowing you have a comprehensive plan in place to address potential threats.
For further information, contact us at [email protected]
#Security risk assessment consultants#Security risk consultancy#security risk consultancy#security risk analysis#security threat and risk assessment consultants#Dubai
0 notes
Text
Gotham has always been weird, so when the groundskeeper at the cemetery noticed the Wayne kid’s plot was disturbed, he just chalked it up to more of the same ol’. Alright, so ‘disturbed’ may be a tad too light of a word, but what’s an empty grave in the grand scheme of Gotham? God knows in a city like this one, they could use all the burial room they could get. He figured he’d just jot it down on the website and hope nobody noticed for a while.
Too bad he didn’t account for the 13 year old boy in Bristol who periodically checks the cemetery’s website when he’s feeling particularly lonely.
Plot Removed.
Tim Drake stared at the two words under the heading for Jason Todd’s plot number. Removed? What do they mean ‘removed’? They can’t just remove a plot? That’s a person down there! That’s Robin down there! You can’t Remove Robin!
Calm down. Deep breaths. Assess the situation.
Robin has been dead for 5 months and 14 days. There is no reason for a grave to be removed that early, especially one of a member of such an affluential family. Chances are likely it’s a simple clerical issue. He can call first thing in the morning and make them aware of the mistake. He can have it all fixed in 5 hours.
Just a phone call.
In 5 hours.
…
Tim hates talking on the phone almost as much as he hates waiting.
Well it won’t be the first time he’s snuck out to head to Gotham proper at 1am. It can’t even really be considered sneaking out if there’s no one home to catch you.
Buses stop running at 2, so he layers a couple sweaters under his coat and grabs his best running sneakers so he can comfortably make the trek back.
Just a quick trip to settle his nerves. Maybe get a few shots in if he spots Batman, but really he just wants to see with his own two eyes that things are okay and Jason can rest.
It’s 1:37 by the time he gets to the headstone reading ‘Here Lies Jason Todd’ and the gaping, muddy pit in front of it.
This- This doesn’t make any sense. This is not removal. This is destruction. Desecration. Somebody did this. Somebody-
Assess the situation.
A hole in the ground, approximately 1.5 feet in diameter.
Mud and grass flung outward but with little force.
Large chunks of earth turned over and shoved away.
No signs of tool marks or clean lines of entry into the dirt.
Dragging claw marks.
Staggering, shuffled pairs of foot prints in the mud.
A trail of dirt.
Something… Something large clawed its way out of the ground here. Something large and bipedal and- and humanoid.
Tim refuses to jump to any conclusions he can see all the facts laid in front of him. He’s going to cautiously follow the trail and simply hope to any god listening that he isn’t the world’s first line of defense against the zombie apocalypse.
He’s been walking for 23 minutes and there’s good news and undecided news. Good news: he’s closing in on the target and the trail isn’t taking him out of the way so his trip home won’t be prolonged. Undecided news: The potential Zombie Robin is heading directly for Wayne Manor.
As zombie apocalypse news, this is very bad. From Tim’s collected observational evidence, his not-so-professional opinion is that Batman, faced with a horror movie level zombie of his dead son, would not respond well, and would likely not fight back.
In Batman and Robin news? Tim’s unsure. If Jason is simply back? What could that mean for them? Batman can have his Robin. He wouldn’t have to continue nearly killing others and himself every night in his grief. Jason could-
No. Stop. Do not jump to conclusions.
Hope only brings heartbreak.
What would Batman do? Get close and see if the target is a threat.
Target is male. Mid-teens. Dark hair. Pale skin. Leaning against surfaces as he walks. Appears injured and disoriented.
Minimal risk assessed. Approaching and attempting contact.
Target identity confirmed: Jason Todd.
“J-Jason?” It comes out as a croaked whisper. Jason shows no sign of acknowledgment.
Tim clears his throat, steps right in front of his path, and tries again.
“Jason. Jason, stop I want to help you.” Still nothing.
“Please, Jason. I can help, I promise I can help!”
Why isn’t this working?! Why can’t he just do something right for once?! He wants this to work, he wants to help Bruce, he wants to fix Batman, he wants to not be alone, he wants-
“Robin!”
Robin jerks to a stop.
Tim reached out his hand.
“Robin. Robin please, I’m sorry you’re going through this, it’s really scary, I’m really scared. But I just want to help you. Help you find Batman. Help you get home.”
Jason just stares at him. Of course he does. Of course it’s not going to work. Why did he even bother hoping he could help?
Hope only brings heartbreak.
His sight blurs as his eyes fill with tears and he starts to lower his outstretched hand.
His arm is slowed as a cold hand weakly grasps his own.
“Don’t… scared… Bat… help… Dad… help.”
A relieved sob tears out from Tim’s chest and he gathers himself together. He yanks his extra sweater off and gently pulls it over Jason’s cold shoulders. Jason lets Tim drag his arm over his shoulders to try and carry some of his weight.
“Okay, Robin. Yeah. Your dad will help us.”
Batman will solve everything once Tim gets Robin home.
#Hello Mr. Batwayne forgive me for waking you but I brought your Jaybin home#Tim: I’m not jumping to conclusions!#also Tim: Holy fuck it’s the zombie apocalypse we’re all going to die#I know it seems like Tim might have some bat detective training but really he just watches a lot of cop shows and asks ‘wwbd?’ all the time.#writing this is the first thing I did as soon as I turned 27.#this was my birthday present to myself ig#not a ship pls n thx#batfam fanfic#batman#dc robin#dcu#batman and robin#jason todd#tim drake#red hood#ficlet#batfam#jason todd and tim drake#robin#red robin#shut up grandpa#fanfiction#‘’JASON! JASON STOP! LOOK AT ME! look at me. please. this isn’t you’’ ass dialogue 🙄
1K notes
·
View notes
Text
Tim Drake when Batman, who regularly risks his life to save others out of deep compassion for all of humanity and is vehemently against murder and using guns on ideological and emotional levels, to the point of refusing to kill his most hated enemy who murdered his child in cold blood and remains a deadly threat, is framed for killing his civilian ex-girlfriend with a gun: I hate to say it, but he could be guilty. Being a good detective means assessing all the evidence objectively and not letting personal biases blind you to possibilities. We can’t rule it out.
Tim Drake when Huntress, who regularly kills Mafia members with a special crossbow, is framed for killing a Mafia member with her special crossbow: She’s innocent. I know it. This is too sloppy and incompetent, it isn’t like her.
2K notes
·
View notes