#SDS Authoring Software
Explore tagged Tumblr posts
Text
SDS Authoring Software - Kalium Solutions Looking to streamline your chemical safety compliance? Kalium Solutions offers SDS Authoring Software on rent, making it easy to create, manage, and update Safety Data Sheets with ease. Apply now to access user-friendly tools that keep your business compliant and safe. Watch this video and reach out to Kalium Solutions to get started! Visit -
0 notes
Text
Services Discontinued, Hardware Failure.
Summary: Courtney finds something entirely wrong with Hoenn. Or the author got sad about his 3DS and its SD card having problems.
CW: Hardware failure, software deletion, data deletion as a metaphor for death, mass death, mentions of interpreted suicidal behavior (Team Magma, Project AZOTH). Intended to be read on light mode for hidden text at the end.
The end of the world usually was a plan in her head.
Leader Maxie and Team Magma’s plan.
Team Aqua’s plan if she really had to include those brutes…
Project AZOTH and the meteor.
But this? This was comparable to her thought process.
That thought had chilled her to the bone. Something she did not like. Her worldview, she could agree was a strange one, it was in a way… ‘robotic.’ She was an analytical woman. She understood how it worked, fixed on it to the point of unnerving her grunts, and did it all with a singsong in her tone.
So why did Courtney had a sudden feeling of dread in her stomach when something flashed in her head? She couldn’t put her finger on it. What it really was. It had started a while ago. The servers of the former Team were down. Nobody could send anybody anything. Which was very. Frustrating. Indeed. It had come back. And then it continued turning on and off. Tabitha had huffed about it. She could not blame him, she had gritted her teeth about it too.
Then Hoenn’s communication was cut completely. Nothing went in. Nothing went out. The power was still on, but phones, computers? No calls, no internet access, nothing. It was unanticipated. People tried making their own servers, vpns, and the like, but it was… pointless. Also unanticipated.
Of course, people blamed both Team Magma and Aqua. They of course did not do such, and it left a sour taste in her mouth to sully Magma’s name like that. The boy and the girl had to come out and say that they had no part of this, which was anticipated and somewhat appreciated, but it also was not their fault so the baseless accusations commence an experiment.
The experiment… was unanticipated. She traded her own Pokémon remotely, and they were fine. Trying to connect to the internet to do the same thing despite she was in the same room? It didn’t work. She tried again. This time borrowing a Rotom from the boy and a Porygon from the girl. They were from Kalos and Mirage Island, respectively. Though trading wasn’t her only motivation.
She was sure researchers were already using Porygon to look inside this strange phenomenon, but Courtney didn’t care, wanting analyze for herself. Her target was locked as she browsed many a sleepless night through trying to understand this all. She squinted at Rotom’s origin. What was… GER? She couldn’t figure it out and that was frankly anticipated given she was locked on her more important current goal.
Eventually Porygon found something corrupted while it was searching, placing it onto an SD card for her to open and look inside.
“Ah… thank you… What do we… have here…?” She remembered herself saying to it. The Porygon chirped, bitcrushed, but happy to help. Rotom made a slight blink, perhaps jealous it didn’t find anything first. But the problem wasn’t the motors, she knew for a fact.
It was slow. Too slow. Courtney knew slow and she knew big files like this could take a while but… These were the scientists’ computers. They could handle these things. And then her memory cut out like a switch.
The next thing she remembered was a black light. Not a blacklight. It was black yet it was gleaming. When she blinked, she saw Camerupt poking at her with her snout. Did she faint? Porygon and Rotom were worriedly racing around. Perhaps due to her spell.
“I am… alright… Do not… worry.” Courtney said as she stood up on shaky legs. She pulled back up her hood, trying to think. The spell reminding her of the first flash in her head. She swore it was gray. But this was pitch black. …Strange, it was strange.
“Deleting…” She mumbled as she went back to Rotom and Porygon… Z. She turned her head. It was not a Porygon2. There was not a disk of dubious nature. That was… impossible from her current perspective. Rotom shivering side to side as it looked on now to its corrupted friend. Courtney stared at its erratic movements. Her target locked, she slowly reached out a gloved hand towards it. Physically, it seemed fine, besides the twitching, but internally…
Her eyes moved back to the computer. She immediately went towards it, feeling a shiver down her spine. Her own Pokémon was wary, but she didn’t touch it, just stared at the error. The program was corrupted. But how? That was the question. She touched the keyboard and it zapped into her head again. She might’ve yelped. She wasn’t sure.
Everything was gone. It was pitch black again and yet it was bright like a light. Words in front of her that she couldn’t read like she was in a dream. Somehow she understood them.
Courtney just started to cry. Her breath in hitches.
“Aha… hah… haha…” It wasn’t funny.
Why was she so scared?
She was so scared.
Why did this feel worse than before? She was never scared before. Why was she suddenly trembling? Hot tears rolling down her cheeks. She did not want to face the inevitability. She hated it. She hated it.
She was never a hugging person. Or maybe her friend and boss were never hugging persons back. She did not remember hugging them tightly as she sobbed into their uniforms. Courtney did not like to cry in front of them. Not since they told her not to. It was embarrassing.
Somehow she had the analysis that in this moment both Leader Maxie and Tabitha didn’t care. Did they know? They had to have known. They could see it too, right? Did everyone in Hoenn see it?
They had to. They had to have seen it. Courtney buried her face. The words engraved in her mind as her eyes shut down. The world becoming bright with darkness.
An error has occurred. Hold down the POWER Button to turn off the power, then turn it on and try again.
For help, visit support.nintendo.com.
Maybe adventures can be taken again… but they’ll never be the same, never interacting with the outside world and the journey never the first.
4 notes
·
View notes
Text



My NVMe Needs - Part 1: Samsung SSD 970 EVO Plus NVme M.2 SSD (1TB) Review (w/ my paper dolls) [Apr 7th, 2023]
Hello, April! This is my first owned M.2 Solid State Drive! And man, I have a lot to talk about! So, get ready! 😁
Because this is Part 1 of "My NVMe Needs", and we're starting off with reviewing Samsung SSD 970 EVO Plus NVMe M.2 SSD (featuring my paper dolls). 😁
So, without further ado, let's get started:
1st to 3rd Image(s): ↑
• Will kick this off with the packaging itself! 🙂📦 It's a legit Samsung brand from a trusted & authorized online seller, which, by the way, I'll get to that in my "asking price" later. So far, I don't see any fake Samsung brands with this type of memory board, and the only thing you could find is their fake Samsung Micro SD / SD cards, so please avoid buying counterfeit Samsung stuff, they're not just worth your buck! Am I right, you two? Yeah I was right. Anyways, let's move on by revealing the real-life NVMe SSD! 😃



4th to 6th Image(s): ↑
• Once its opened, we're now looking at the real thing! 😮 Its actually pretty small stick than we've expected. And my paper dolls thinks that my M.2 SSD is shape liked a thin dark chocolate waffle biscuit. Yeah, ☝️ don't imagine for a sec because this is not a food that you consumed, it's a memory stick drive for my or our computer system! So, the paper dolls thought to themselves, "what is NVMe thingy?" 🤔 Well, I'm glad you ask!
• NVMe or Non-Volatile Memory Express is a modern storage protocol for next-gen Solid State Drives in a form of small rectangular shape circuitry boards. And NVMe stick is always attached through the motherboard instead of plugging SATA connectors (for Hard Drives & 2.5mm Solid State Drives), much like their cousins, the M.2 SATA & mSATA sticks (without the NVMe attached). NVMe stick is essentially a Hard Drive on steroids albeit more compact & ultra slim onto a motherboard. Plus, it had a much faster rate for read & write speeds than bulky 3.5mm mechanized hard drives, slim 2.5mm mechanized hard drives & even SATA Solid State Drives (also 2.5 mm). Heck, even M.2 SATA & mSATA sticks can't outpace the NVMe's fast transfer rate. BUT... The only downsides for NVMe stick are; No. 1 - it tends to overheat without equipping the heat sink, and No. 2 - they're pretty expensive depending on what memory size, trusted memory brands & type of gens (whether Gen3 or Gen4) should you buy. So far, 1TB, 2TB & even 4TBs are the most expensive line of NVMe sticks. Uh yeah, and much like existing onboard memory chipboards the NVMe's won't make any noise compared to 3.5mm & 2.5mm mechanized hard drives that have buzzy sounds while vibrating our PC desktop case at the same time.
• If you want more information about NVMe SSD, then you could always click these links → [CLICK ME! #1], [CLICK ME! #2]. Now, onto our next images & video.


My recorded video, 7th & 8th Image(s): ↑
• [Recorded video & 7th Image] In my clip, you could see I'm holding my owned NVMe stick with my fingers for the first time. 🤲😮 And man, for such a small memory stick, it had a little heft to it from its slim metal components & onboard memory chips. And inside that package, there's an instruction manual about the NVMe stick. 📄 What a convenient way to store that manual though. 👍
• [8th Image] So, you two. Are you still imagine about my NVMe stick that looks like a waffle stick? Nah, I don't think so! lol 😅



9th to 11th Image(s): ↑
• Now, upon opening the manual, there's a tiny pamphlet saying that I need to download the "Samsung Magician" software for my NVMe stick to check the memory health, see stats, and more. It's a must-install software once I attach my NVMe stick to PC's motherboard. 🙂👌




12th to 15th Image(s): ↑
• Alright, here's a closer look at my future memory storage, and yes, it is a pretty thin and pretty solid build that was made (by Samsung). You noticed, why are stickers attached to that NVMe stick? Well, it may look like stickers, but rather stickers with thin thermal pads on each side, one of which has a half for the thin copper pad. And what's the purpose? To keep the chips chill from overheating while running the computer. 🧊⬇️🖥️ However, that wasn't enough to cool down and thus require a heat sink to keep the NVMe stick running for long period endurance. Yeah, it still debating on why should I need a heat sink for my NVMe stick or not? But, much like graphics card's processor & the CPU chip, the NVMe stick NEEDS a heat sink. So, there's that.
• So, what do you think, you two? Should I need a heat sink? They said "I hope so". Make sense (, I guess). 🤔




16th to 19th Image(s): ↑
• Finally, a comparison between my NVMe stick & two 2.5mm (mechanized) hard drives, one with the durable case (my Adata HD330), while the other was from an old laptop (Western Digital Scorpio Blue 160GB) & it's still functional. Even though, no one using it, including me. Now, I was gonna add another hard drive (the fat 3.5mm one), but unfortunately, I'm still hurt my emotions from losing my precious files. 😟😓 But, fear not because it's already well documented by countless photos, like this one → [CLICK ME!]. 👈🙂 As for their weight ⚖️, they're pretty different numbers in their own right. So, here are the ff. numbers (using my digital scaler): ↓
○ NVMe: Samsung SSD 970 EVO Plus (1TB) - 10g (lightest of the three)⚖️ ○ 2.5mm HD: Western Digital Scorpio Blue (160GB) - 93g ⚖️ ○ External 2.5mm HD: Adata HD330 (2TB) - 173g (heaviest of the three)⚖️
• [19th Image] Hey, you two! Do you want a take home with this old slim HDD? 😁 You can have it & eat it! Yeah, I don't think they won't eat it. lol 😂
Overall & Asking Price:
• I'm so happy to own my first ever NVMe SSD stick, and I can't wait to test it out with my functional PC. 😊🖥️ Although, I'm unable to test my first owned NVMe SSD stick without a heat sink to prevent overheat 😕. And good news 👍, I've already ordered it from Lazada Philippines! 🛒🌐🇵🇭 But, the bad news 👎, it's Holy Week. So, the delivery process will be resumed next week 🗓️. Looks like, I'll make another topic before I combined it into one review package. 🤷
• As for the "Asking Price", it's around ₱ 5,000 💵 for this Samsung SSD 970 EVO Plus, 1TB variant [CLICK ME!]. Actually, ₱ 4,986 💵 to be specific, with a huge discount & free shipping vouchers during Lazada's birthday discount sale 🛒🌐🇵🇭 (in March every year) 🏷️🧾🎂📅. Making it the most expensive item that I purchased online. 🤑 And what online store that I've ordered the Samsung NVMe stick? 🤔🛒 Well, this → [CLICK ME!] (which, I mentioning the name. Sorry... 😅) As of this writing, Lazada is having a 4.4 fest discount sale, from April 4th to 8th, 2023 (Southeast Asia exclusive). However, you could get it on your favorite online shopping sites (e.g. Amazon, Aliexpress, etc.), as long as you have enough cash to spare and/or wait for the discount sale. (Black Friday might be a long road for you, but you'll save your wallet's dough.)
• Anyways, in my next plan, well... Umm... I think I should test with my first owned NVMe stick without a heat sink (while I'm waiting for my order)? So, who knows what would happen? 🤷 But, I gonna need to record something as my benchmark before I migrated from mechanized HDD to high-speed SSD NVMe using a trusted migration software. 🖥️➡️🖥️ Hmmph... I don't know, but we'll see in the coming weeks before this month ends. 🤔
Well, that's all for now!
If you haven't seen my previous topic, then please [CLICK ME!].
Tagged: @lordromulus90, @bryan360, @carmenramcat, @leapant, @alexander1301, @rafacaz4lisam2k4, @paektu
#My Photos#My Photo#MyPhotos#MyPhoto#Photos#Photo#Chowder#Panini#Chowder Panini#Paper Dolls#Samsung#Samsung 970 EVO Plus#Samsung 970 EVO Plus NVMe SSD#NVMe SSD#Samsung SSD 970 EVO Plus#Samsung SSD 970 EVO Plus NVMe#M.2 Drive#M2 Drive#NVMe M2 PCIE SSD#NVMe M.2 PCIE SSD#Memory Drive#NVMe M.2 SSD#NVMe M2 SSD#Solid State Drive#Photography
5 notes
·
View notes
Text
Aditya K Sood, VP of Security Engineering and AI Strategy, Aryaka – Interview Series
New Post has been published on https://thedigitalinsider.com/aditya-k-sood-vp-of-security-engineering-and-ai-strategy-aryaka-interview-series/
Aditya K Sood, VP of Security Engineering and AI Strategy, Aryaka – Interview Series


Aditya K Sood (Ph.D) is the VP of Security Engineering and AI Strategy at Aryaka. With more than 16 years of experience, he provides strategic leadership in information security, covering products and infrastructure. Dr. Sood is interested in Artificial Intelligence (AI), cloud security, malware automation and analysis, application security, and secure software design. He has authored several papers for various magazines and journals, including IEEE, Elsevier, Crosstalk, ISACA, Virus Bulletin, and Usenix.
Aryaka provides network and security solutions, offering Unified SASE as a Service. The solution is designed to combine performance, agility, security, and simplicity. Aryaka supports customers at various stages of their secure network access journey, assisting them in modernizing, optimizing, and transforming their networking and security environments.
Can you tell us more about your journey in cybersecurity and AI and how it led you to your current role at Aryaka?
My journey into cybersecurity and AI began with a fascination for technology’s potential to solve complex problems. Early in my career, I focused on cybersecurity, threat intelligence, and security engineering, which gave me a solid foundation in understanding how systems interact and where vulnerabilities might lie. This exposure naturally led me to delve deeper into cybersecurity, where I recognized the critical importance of safeguarding data and networks in an increasingly interconnected world. As AI technologies emerged, I saw their immense potential for transforming cybersecurity—from automating threat detection to predictive analytics.
Joining Aryaka as VP of Security Engineering and AI Strategy was a perfect fit because of its leadership in Unified SASE as a Service, cloud-first WAN solutions, and innovation focus. My role allows me to synthesize my passion for cybersecurity and AI to address modern challenges like secure hybrid work, SD-WAN optimization, and real-time threat management. Aryaka’s convergence of AI and cybersecurity empowers organizations to stay ahead of threats while delivering exceptional network performance, and I’m thrilled to be a part of this mission.
As a thought leader in cybersecurity, how do you see AI reshaping the security landscape in the next few years?
AI is on the brink of transforming the cybersecurity landscape, relieving us of the burden of routine tasks and allowing us to focus on more complex challenges. Its ability to analyze vast datasets in real time enables security systems to identify anomalies, patterns, and emerging threats at a pace that surpasses human capabilities. AI/ML models continuously evolve, enhancing their accuracy in detecting and circumventing the impacts of advanced persistent threats (APTs) and zero-day vulnerabilities. Moreover, AI is set to revolutionize incident response (IR) by automating repetitive and time-sensitive tasks, such as isolating compromised systems or blocking malicious activities, significantly reducing response times and mitigating potential damage. In addition, AI will help bridge the cybersecurity skills gap by automating routine tasks and enhancing human decision-making, enabling security teams to concentrate on more complex challenges.
However, adversaries quickly exploit the same capabilities that make AI a powerful defensive tool. Cybercriminals increasingly use AI to develop more sophisticated threats, such as deepfake phishing attacks, adaptive social engineering, and AI-driven malware. This trend will lead to an ‘AI arms race,’ in which organizations must continuously innovate to outpace these evolving threats.
What are the key networking challenges enterprises face when deploying AI applications, and why do you believe these issues are becoming more critical?
As enterprises venture into AI applications, they face urgent networking challenges. The demanding nature of AI workloads, which involve transferring and processing massive datasets in real-time, particularly for processing and learning tasks, creates an immediate need for high bandwidth and ultra-low latency. For instance, real-time AI applications like autonomous systems or predictive analytics hinge on instantaneous data processing, where even the slightest delays can disrupt outcomes. These demands often surpass the capabilities of traditional network infrastructures, leading to frequent performance bottlenecks.
Scalability is a critical challenge in AI deployments. AI workloads’ dynamic and unpredictable nature necessitates networks that can swiftly adapt to changing resource requirements. Enterprises deploying AI across hybrid or multi-cloud environments face added complexity as data and workloads are distributed across diverse locations. The need for seamless data transfer and scaling across these environments is evident, but the complexity of achieving this without advanced networking solutions is equally apparent. Reliability is also paramount—AI systems often support mission-critical tasks, and even minor downtime or data loss can lead to significant disruptions or flawed AI outputs.
Security and data integrity further complicate AI deployments. AI models rely on vast amounts of sensitive data for training and inference, making secure data transfer and protection against breaches or manipulation a top priority. This challenge is particularly acute in industries with strict compliance requirements, such as healthcare and finance, where organizations need to meet regulatory obligations alongside performance needs.
As enterprises increasingly adopt AI, these networking challenges are becoming more critical, underscoring the need for advanced, AI-ready networking solutions that offer high bandwidth, low latency, scalability, and robust security.
How does Aryaka’s platform address the increased bandwidth and performance demands of AI workloads, particularly in managing the strain caused by data movement and the need for rapid decision-making?
Aryaka, with its intelligent, flexible, and optimized network management, is uniquely equipped to address the increased bandwidth and performance demands of AI workloads. The movement of large datasets between distributed locations, such as edge devices, data centers, and cloud environments, often significantly strains traditional networks. Aryaka’s solution provides relief by dynamically routing traffic across the most efficient and available paths, leveraging multiple connectivity options to optimize bandwidth and reduce latency.
One key advantage of Aryaka’s solution is its ability to prioritize critical AI-related traffic through application-aware routing. By identifying and prioritizing latency-sensitive workloads, such as real-time data analysis or machine learning model inference, Aryaka ensures that AI applications receive the necessary network resources for rapid decision-making. Additionally, Aryaka’s solution supports dynamic bandwidth allocation, enabling enterprises to confidently scale resources up or down based on AI workload demands, preventing bottlenecks, and ensuring consistent performance even during peak usage.
Furthermore, the Aryaka platform provides proactive monitoring and analytics capabilities, offering visibility into network performance and AI workload behaviors. This proactive approach allows enterprises to identify and resolve performance issues before they impact the operation of AI systems, ensuring uninterrupted operation. Combined with advanced security features like CASB, SWG, FWaaS, end-to-end encryption, ZTNA, and others, Aryaka platforms safeguard the integrity of AI data.
How does AI adoption introduce new vulnerabilities or attack surfaces within enterprise networks?
Adopting AI introduces new vulnerabilities and attack surfaces within enterprise networks due to the unique ways AI systems operate and interact with data. One significant risk comes from the vast amounts of sensitive data that AI systems require for training and inference. If this data is intercepted, manipulated, or stolen during transfer or storage, it can lead to breaches, model corruption, or compliance violations. Additionally, AI algorithms are susceptible to adversarial attacks, where malicious actors introduce carefully crafted inputs (e.g., altered images or data) designed to mislead AI systems into making incorrect decisions. These attacks can compromise critical applications like fraud detection or autonomous systems, leading to severe operational or reputational damage. AI adoption also introduces risks related to automation and decision-making. Malicious actors can exploit automated decision-making systems by feeding them false data, leading to unintended outcomes or operational disruptions. For example, attackers could manipulate data streams used by AI-driven monitoring systems, masking a security breach or generating false alarms to divert attention.
Another challenge arises from the complexity and distributed nature of AI workloads. AI systems often involve interconnected components across edge devices, cloud platforms, and infrastructure. This intricate web of interconnectedness significantly expands the attack surface, as each element and communication pathway represents a potential entry point for attackers. Compromising an edge device, for instance, could allow lateral movement across the network or provide a pathway to tamper with data being processed or transmitted to centralized AI systems. Furthermore, unsecured APIs, often used for integrating AI applications, can expose vulnerabilities if not adequately protected.
As enterprises increasingly rely on AI for mission-critical functions, the potential consequences of these vulnerabilities become more severe, underscoring the urgent need for robust security measures. Organizations must act swiftly to address these challenges, such as adversarial training for AI models, securing data pipelines, and adopting zero-trust architectures to safeguard AI-driven environments.
What strategies or technologies are you implementing at Aryaka to address these AI-specific security risks?
The Aryaka platform uses end-to-end encryption for data in transit and at rest to secure the vast amounts of sensitive data AI systems rely on. These measures safeguard AI data pipelines, preventing interception or manipulation during transfer between edge devices, data centers, and cloud services. Dynamic traffic routing further enhances security and performance by directing AI-related traffic through secure and efficient paths while prioritizing critical workloads to minimize latency and ensure reliable decision-making.
Aryaka’s AI Observe solution monitors network traffic by analyzing logs for suspicious activity. Centralized visibility and analytics provided by Aryaka enable organizations to monitor the security and performance of AI workloads, proactively identifying potential malicious actions and risky behavior associated with end users, including critical servers and hosts. AI Observe utilizes AI/ML algorithms to trigger security incident notifications based on the severity calculated using various parameters and variables for decision-making.
Aryaka’s AI>Secure inline network solution, coming in the second half of 2025, will enable organizations to dissect the traffic between end users and AI services endpoints (ChatGPT, Gemini, copilot, etc.) to uncover attacks such as prompt injections, information leakage, and abuse guardrails. Additionally, strict policies can be enforced to restrict communication with unapproved and sanctioned GenAI services/applications. Moreover, Aryaka addresses AI-specific security risks by implementing advanced strategies that combine networking and robust security measures. One critical approach is the adoption of Zero Trust Network Access (ZTNA), which enforces strict verification for every user, device, and application attempting to interact with AI workloads. It is essential in distributed AI environments, where workloads span edge devices, cloud platforms, and on-premises infrastructure, making them vulnerable to unauthorized access and lateral movement by attackers.
By employing these comprehensive measures, Aryaka helps enterprises secure their AI environments against evolving risks while enabling scalable and efficient AI deployment.
Can you share examples of how AI is being used both to enhance security and as a tool for potential network compromises?
AI plays a crucial role in cybersecurity. It is a robust tool for enhancing network security and a resource adversaries can exploit for sophisticated attacks. Recognizing these applications underscores AI’s transformative potential in the cybersecurity landscape and empowers us to navigate the risks it introduces.
AI is revolutionizing network security through advanced threat detection and prevention. AI models analyze vast amounts of network traffic in real time, identifying anomalies, suspicious behavior, or indicators of compromise (IOCs) that might go undetected by traditional methods. For example, AI-powered systems can detect and mitigate Distributed Denial of Service (DDoS) attacks by analyzing network protocol patterns and responding automatically to isolate malicious sources. Additionally, AI’s potential in behavioral analytics is significant, creating profiles of normal user behavior to detect insider threats or account compromises. But its most potent application is predictive analytics, where AI systems forecast potential vulnerabilities or attack vectors, enabling proactive defenses before threats materialize.
Conversely, cybercriminals are leveraging AI to develop more sophisticated attacks. AI-driven malicious code can adapt to evade traditional detection mechanisms by changing its characteristics dynamically. Attackers also use AI/ML to enhance phishing campaigns, crafting compelling fake emails or messages tailored to individual targets through data scraping and analysis. One alarming trend is deepfakes in social engineering. AI-generated audio or video convincingly impersonates executives or trusted individuals to manipulate employees into divulging sensitive information or authorizing fraudulent transactions. Furthermore, adversarial AI attacks target other AI systems directly, introducing manipulated data to cause incorrect predictions or decisions that can disrupt critical operations reliant on AI-driven automation.
The dual uses of AI in cybersecurity underscore the importance of a proactive, multi-layered security strategy. While organizations must harness AI’s potential to enhance their defenses, it’s equally crucial to remain vigilant against potential misuse.
How does Aryaka’s Unified SASE as a Service stand out from traditional network and security solutions?
Aryaka’s Unified SASE as a Service solution is designed to scale with your business. Unlike legacy systems that rely on separate tools for networking (such as MPLS) and security (like firewalls and VPNs), Unified SASE integrates these functions, offering a seamless and scalable solution. This convergence simplifies management and provides consistent security policies and performance for users, regardless of location. By leveraging a cloud-native architecture, Unified SASE eliminates the need for complex on-premises hardware, reduces costs, and enables businesses to adapt quickly to modern hybrid work environments.
A key differentiator of Aryaka is its ability to support Zero Trust (ZT) principles at scale. It enforces identity-based access controls, continuously verifying user and device trustworthiness before granting access to resources. Combined with capabilities like Secure Web Gateways (SWG), Cloud Access Security Broker (CASB), Intrusion Detection and Prevention Systems (IDPS), Next-Gen Firewalls (NGFW), and networking functions, Aryaka provides robust protection against threats while safeguarding sensitive data across distributed environments. Its ability to integrate AI further enhances threat detection and response, ensuring faster and more effective mitigation of security incidents.
Aryaka enhances user experience and performance. Unified SASE leverages Software-Defined Wide Area Networking (SD-WAN) to optimize traffic routing, ensuring low latency and high-speed connections. This is particularly critical for organizations embracing cloud applications and remote work. By delivering security and performance from a unified platform, Unified SASE minimizes complexity, improves scalability, and ensures that organizations can meet the demands of modern, dynamic IT landscapes.
Can you explain how Aryaka’s OnePASS™ architecture supports AI workloads while ensuring secure and efficient data transmission?
Aryaka’s OnePASS™ architecture supports AI workloads by integrating secure, high-performance network connectivity with robust security and data optimization features. AI workloads often transmit large volumes of data between distributed environments, such as edge devices, data centers, and cloud-based AI platforms. OnePASS™ ensures that these data flows are efficient and secure by leveraging Aryaka’s global private backbone and Secure Access Service Edge (SASE) capabilities.
The global private backbone provides low-latency, high-bandwidth connectivity, which is critical for AI workloads requiring real-time data processing and decision-making. This optimized network ensures fast and reliable data transmission, avoiding the bottlenecks commonly associated with public internet connections. The architecture also employs advanced WAN optimization techniques, such as data deduplication and compression, to further enhance efficiency and reduce the strain on network resources. It is ideal for large datasets and frequent model updates associated with AI operations, instilling confidence in the system’s performance.
From a security perspective, Aryaka’s OnePASS™ architecture enforces a Zero Trust framework, ensuring all data flows are authenticated, encrypted, and continuously monitored. Integrated security features like Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and intrusion prevention systems (IPS) safeguard sensitive AI workloads against cyber threats. Additionally, by enabling edge-based policy enforcement, OnePASS™ minimizes latency while ensuring that security controls are applied consistently across distributed environments, providing a sense of security in the system’s vigilance.
Aryaka’s single-pass architecture incorporates all essential security functions into a unified platform. This integration allows real-time network traffic inspection and processing without requiring multiple security devices. This combination of secure, low-latency connectivity and robust threat protection makes Aryaka’s OnePASS™ architecture uniquely suited for modern AI workloads.
What trends do you foresee in AI and network security as we move into 2025 and beyond?
As we look towards 2025 and beyond, AI will play a pivotal role in network security. AI-powered threat detection systems will continue to advance, leveraging AI/ML to identify patterns of malicious activity with unprecedented speed and accuracy. These systems will excel in detecting zero-day vulnerabilities and sophisticated attacks, such as advanced persistent threats (APTs). AI will also drive automation in incident response, a development that should reassure the audience about the efficiency of future security systems. This automation will enable Security Orchestration, Automation, and Response (SOAR) systems to neutralize threats autonomously, minimizing response times and reducing the burden on human analysts. Additionally, as quantum computing evolves, it could undermine existing encryption standards in network security, pushing the industry toward quantum-safe cryptography.
However, the growing integration of AI in network security brings challenges. Cybercriminals harness the power of AI technologies to develop more advanced attacks, including phishing schemes and evasive malware. Due to the risks of biased or improperly trained models, AI model vulnerabilities, which refer to flaws in the design or implementation of AI systems, will likely increase. This will result in exploiting AI models through newly discovered data poisoning and adversarial input manipulation techniques. In addition, adopting AI will improve the detection of security vulnerabilities in third-party libraries and packages used in software supply chains.
We also anticipate AI-driven tools will enable better collaboration between security tools, teams, and organizations. AI-centric solutions will create personalized security models, making the audience feel that their security needs are being met. These models will create individualized security policies based on user roles and behavior. Nation-states will collaborate on building a global cybersecurity framework for AI technologies.
Thank you for the great interview, readers who wish to learn more should visit Aryaka.
#2025#adoption#Advanced attacks#advanced persistent threats#Adversarial attacks#adversaries#ai#AI adoption#ai model#AI models#AI platforms#AI strategy#AI systems#AI-powered#AI/ML#Algorithms#Analysis#Analytics#anomalies#APIs#Application Security#applications#approach#architecture#artificial#Artificial Intelligence#Aryaka#as a service#Attack surface#attackers
0 notes
Text
The Role of Security in SD-WAN Solutions

In today’s fast-evolving digital landscape, securing enterprise networks is more critical than ever. Software-Defined Wide Area Networks (SD-WAN) have emerged as a game-changer, offering enhanced flexibility and cost-efficiency.
However, security remains a primary concern for businesses adopting SD-WAN solutions. This blog explores the key security features of SD-WAN, such as encryption, firewalls, and Zero Trust models, while highlighting how these solutions protect networks from emerging threats.
For those looking to deepen their understanding of SD-WAN’s security capabilities, SD-WAN training offers valuable insights into configuring and managing secure SD-WAN networks effectively.
Understanding to SD-WAN and Its Importance in Modern Networking
What is SD-WAN?
SD-WAN (Software-Defined Wide Area Network) is a transformative approach to networking that leverages software to control and manage a wide area network. Unlike traditional WANs, SD-WAN optimizes and secures the connectivity between branch offices, data centers, and cloud applications.
Importance in Modern Networking
SD-WAN addresses the challenges of modern networking, including the rise of cloud-based applications, increasing bandwidth demands, and the need for secure, reliable connections across distributed networks. With the growing trend of remote work and global businesses, SD-WAN offers flexibility, scalability, and robust security, making it an essential solution for today’s enterprise networks.
How SD-WAN Enhances Network Security Over Traditional WAN
End-to-End Encryption: SD-WAN provides end-to-end encryption, ensuring that data remains secure while in transit between various network locations.
Dynamic Path Selection: SD-WAN dynamically selects the most secure and reliable network path, adjusting based on traffic conditions, reducing the risk of interception or attack.
Reduced Attack Surface: Unlike traditional WANs that rely on expensive, hardware-based security measures, SD-WAN uses cloud-delivered security, minimizing the potential attack surface and simplifying management.
Integrated Security Features of SD-WAN: Encryption, Firewall, and More
Encryption: SD-WAN integrates encryption protocols to secure data, ensuring privacy and protecting it from unauthorized access.
Firewall Integration: Next-generation firewalls (NGFW) within SD-WAN solutions protect the network from malicious traffic, ensuring only authorized data flows through the network.
Intrusion Detection and Prevention: Many SD-WAN solutions include Intrusion Detection and Prevention Systems (IDPS) to identify and stop malicious activity before it can spread.
Secure Internet Access: SD-WAN allows direct, secure internet access to cloud applications, eliminating the need for backhauling traffic to a central data center, improving both security and performance.
Zero Trust Security Model in SD-WAN: What You Need to Know
Zero Trust Overview: The Zero Trust security model assumes that no device or user is inherently trustworthy, even if they are inside the network perimeter. Every access request is authenticated and authorized before granting access.
Zero Trust in SD-WAN: SD-WAN solutions can enforce Zero Trust principles by ensuring that devices, users, and applications are continually verified through multi-factor authentication (MFA) and policy enforcement.
Benefits of Zero Trust: By adopting a Zero Trust model, SD-WAN ensures that each user or device only has access to specific resources based on their verified identity and role, limiting exposure to potential threats.
Secure SD-WAN Architecture: A Layered Approach to Protecting Data
Layered Security Approach: SD-WAN incorporates a multi-layered security model, combining encryption, firewalls, threat detection, and access controls to protect data across the network.
Cloud Integration: Security policies are integrated directly into the cloud, making it easier for organizations to manage network and security configurations from a centralized location.
Granular Access Control: SD-WAN solutions allow for granular access controls, ensuring that sensitive data and applications are isolated from other less critical resources.
How SD-WAN Protects Against Distributed Denial of Service (DDoS) Attacks
DDoS Detection: SD-WAN continuously monitors network traffic for signs of DDoS attacks, identifying unusual spikes in traffic volume that may indicate an ongoing attack.
Traffic Filtering: Upon detecting a DDoS attack, SD-WAN can automatically reroute traffic or apply filtering techniques to block malicious requests, ensuring minimal disruption to business operations.
Resiliency and Mitigation: By leveraging multiple internet connections and adaptive routing, SD-WAN can maintain availability even in the face of a large-scale DDoS attack, ensuring business continuity.
Challenges in Securing SD-WAN: Best Practices and Solutions
Complexity in Security Management: The distributed nature of SD-WAN deployments makes centralized security management challenging.
Solution: Use centralized SD-WAN management platforms to streamline security policy enforcement and ensure consistent configurations across all network locations.
Misconfigured Security Policies: Improperly configured security policies can introduce vulnerabilities into an SD-WAN deployment.
Solution: Regularly audit and update security policies to align with organizational needs and prevent unauthorized access.
Integration with Existing Security Infrastructure: Many organizations face challenges when integrating SD-WAN with their existing security tools.
Solution: Ensure that SD-WAN is compatible with existing security technologies, such as firewalls, VPNs, and intrusion detection systems, to maintain a cohesive security posture.
Future Trends: How SD-WAN Security is Evolving with AI and Machine Learning
AI-Powered Threat Detection: Artificial intelligence (AI) and machine learning (ML) are being integrated into SD-WAN security solutions to detect and mitigate sophisticated cyber threats in real-time.
Automated Incident Response: AI can automatically respond to threats by adjusting network routes, blocking malicious IPs, or isolating compromised devices, minimizing human intervention and reducing response times.
Predictive Security: With predictive analytics, SD-WAN solutions can forecast potential security threats, allowing organizations to take proactive measures before incidents occur.
Enhanced Threat Intelligence: AI and ML enable SD-WAN platforms to continuously learn from emerging threats, improving the system’s ability to detect and respond to new types of cyberattacks.
Conclusion
SD-WAN solutions play a vital role in enhancing network security, offering integrated features like encryption, firewalls, and Zero Trust models to protect data. By adopting a layered security architecture and leveraging modern technologies like AI and machine learning, SD-WAN not only mitigates the risk of data breaches but also ensures secure connectivity for cloud applications, remote users, and distributed teams.
For those seeking to master SD-WAN security, Cisco SD-WAN training provides essential knowledge on implementing these solutions effectively. As security threats evolve, SD-WAN’s adaptability and proactive security measures will continue to be a crucial part of enterprise network security strategies.
0 notes
Text
Sony A7 III Mirrorless Camera | Common Issue Resolved

The Sony Alpha A7III has become a favorite among photographers and videographers for its impressive features and image quality. However, like any sophisticated piece of technology, it is not without its issues. For those considering this camera, especially from an authorized dealer like AWPRO in Dubai, it’s essential to be aware of both the benefits and the challenges that come with it. In this blog, we will explore common problems users face with the A7III and potential solutions to enhance your experience.
Overview of the Sony Alpha A7III
The Sony A7III is renowned for its 24.2MP full-frame sensor, exceptional autofocus capabilities, and robust video recording features. It offers a versatile shooting experience suitable for various photography styles, from portraits to landscapes and even action shots. However, despite its popularity, users have reported several issues that can impact performance.
Common Issues Faced by A7III Users
1. Shutter Failures
Many users have experienced shutter failures after a relatively low number of actuations (between 10,000 and 50,000). This can lead to frustrating situations where the camera displays error messages or fails to capture images altogether. If you encounter this issue, contacting Sony for warranty repairs or replacement may be necessary.
2. Autofocus Inconsistencies
While the A7III is equipped with a robust autofocus system, some users report inconsistencies in focus accuracy, particularly in low-light conditions or when using specific picture profiles like S-Log. To mitigate this issue, consider disabling certain settings or switching to a different picture profile that may yield better results.
3. Microphone Jack Malfunctions
Videographers have noted problems with the microphone jack failing, which can severely hinder audio recording capabilities. If you experience this issue, check if your camera's firmware is up-to-date and consider using external audio recording solutions as a temporary fix.
4. Dial Skipping Issues
Some users have reported that the control dials occasionally skip settings—turning one click may result in jumping two settings instead. This problem can often be resolved by ensuring that your camera's firmware is updated to the latest version. If the issue persists, consider contacting Sony for assistance or exploring community forums for additional insights.
5. Overheating Problems
The A7III has been known to overheat during extended video recording sessions, particularly in 4K mode. To combat this:
Adjust Temperature Settings: Navigate to the menu and set "Auto Pwr OFF Temp." to "High."
Use Fast SD Cards: Invest in high-speed UHS-II SD cards to reduce strain on the camera.
Open the Battery Door: Keeping the battery door open while shooting can help dissipate heat.
Charge via USB-C: Consider powering your camera through USB-C to reduce reliance on the internal battery.
Solutions and Tips
To enhance your experience with the Sony A7III and address some of these issues:
Firmware Updates: Always ensure your camera's firmware is up-to-date. This can resolve many software-related issues.
Factory Reset: If you encounter persistent problems, performing a factory reset may help restore functionality.
Community Support: Engage with online communities such as forums or social media groups dedicated to Sony cameras where you can share experiences and solutions with other users.
Professional Assistance: For hardware-related issues like shutter failures or dial malfunctions, don’t hesitate to reach out to authorized service centers or contact Sony directly.
Conclusion
The Sony Alpha A7III remains a powerful tool for photographers and videographers alike, but being aware of its potential issues can help you make an informed decision before purchase. Available at AWPRO—an authorized dealer of Sony in Dubai—you can trust that you're getting genuine products along with reliable support.
By understanding common challenges and implementing these solutions, you can maximize your enjoyment of this remarkable camera. Whether you're capturing stunning landscapes or documenting special moments, the A7III is designed to deliver exceptional results when used effectively.
Explore more about the Sony Alpha A7III at AWPRO today and elevate your photography game!
0 notes
Text
Chemical Management

Chemical Management: Why You’d Need/Want It and How It’s Great Managing chemicals in any organization involves more than just storing or using them—it requires careful tracking, adherence to safety protocols, and maintaining compliance with a variety of regulations. Whether you’re in manufacturing, pharmaceuticals, agriculture, or research, ensuring that your chemicals are handled properly can significantly affect safety, environmental impact, and operational efficiency. Chemical Management is the process of organizing, tracking, and controlling the chemicals within an organization to ensure safe usage, compliance, and sustainability. In this article, we’ll explore why you’d need chemical management, how it works, and the numerous benefits it offers. What Is Chemical Management? Chemical management refers to the comprehensive process of controlling the life cycle of chemicals within an organization. It encompasses the handling, storage, transportation, use, and disposal of chemicals, with an emphasis on ensuring safety and compliance with legal and environmental standards. Effective chemical management involves tracking chemicals from the moment they enter the facility until they are safely disposed of or recycled. It includes managing inventory, ensuring proper labeling, storing chemicals in appropriate conditions, and maintaining up-to-date Safety Data Sheets (SDS). Chemical management aims to minimize risks, ensure compliance with safety regulations, and optimize chemical usage to improve efficiency and reduce costs. At its core, chemical management is designed to reduce hazards, increase productivity, and maintain a safe working environment while adhering to environmental and safety laws. Why You’d Need/Want Chemical Management
Improved Safety and Risk Mitigation One of the most critical reasons for implementing a chemical management system is to improve safety. Chemicals can pose serious risks to employees, customers, and the environment if not handled properly. Mishandling chemicals can lead to accidents such as chemical spills, fires, or exposure to toxic substances. These incidents can cause injuries, fatalities, environmental damage, and legal liabilities. Chemical management helps mitigate these risks by ensuring that chemicals are stored correctly, used according to safety guidelines, and disposed of in compliance with regulations. Proper chemical management ensures that your team has access to necessary safety information such as SDS, hazard classifications, and emergency response procedures. Centralizing this information in a digital system makes it easy for employees to quickly find the correct data when needed, thus improving safety and reducing the likelihood of accidents.
Regulatory Compliance Organizations that handle chemicals are subject to various regulatory requirements, including those set forth by OSHA (Occupational Safety and Health Administration), EPA (Environmental Protection Agency), and other national and international regulatory bodies. Failure to comply with these regulations can lead to hefty fines, legal consequences, and reputational damage. A well-organized chemical management system helps ensure that your business remains compliant with local, state, and federal regulations. It keeps track of important safety documents like SDS, chemical labeling, and usage logs. Chemical management systems also enable easy reporting to regulatory authorities, ensuring that inspections and audits go smoothly. By automating compliance checks and documentation, chemical management reduces the chances of human error and helps maintain up-to-date records for inspection. Moreover, chemical management software can send alerts when chemicals are nearing expiration, when inventories need replenishment, or when regulatory changes require updates to documentation, ensuring that compliance is always maintained.
Efficient Inventory Management Managing chemical inventory effectively is crucial for operational efficiency and cost control. Without a proper inventory management system in place, businesses risk overstocking chemicals that are rarely used or running out of critical supplies unexpectedly. Both of these scenarios can lead to production delays, waste, and unnecessary costs. Chemical management systems allow businesses to track chemical inventories in real-time. They provide visibility into stock levels, usage trends, and expiration dates, helping organizations avoid overordering and minimize waste. With automated inventory tracking, businesses can ensure that they only keep necessary quantities of chemicals in stock, preventing excess and reducing storage costs. Furthermore, chemical management systems enable better tracking of chemical batches, ensuring that you can trace specific products or chemicals in case of quality control issues, product recalls, or safety incidents. This level of tracking is particularly important for industries that require strict traceability, such as pharmaceuticals and food production.
Waste Reduction and Cost Savings Managing chemicals responsibly is not only a matter of safety but also of sustainability. Wasting chemicals, especially expensive ones, can significantly increase operational costs and hurt a company’s bottom line. Chemical management systems help businesses reduce waste by monitoring chemical usage and expiration dates. By providing real-time data on chemical consumption and inventory, chemical management systems help organizations identify areas where chemicals may be overused or unnecessarily ordered. Additionally, systems can generate alerts when chemicals are nearing their expiration, allowing businesses to use or dispose of them appropriately before they go to waste. Reducing waste also contributes to a more sustainable operation. By ensuring that chemicals are used efficiently and disposed of correctly, businesses can minimize their environmental impact and align with sustainable practices, which is increasingly important for consumers, stakeholders, and regulatory bodies.
Streamlined Operations and Increased Efficiency The complexity of managing chemicals can be overwhelming, especially when relying on manual processes such as spreadsheets or paper records. These methods are time-consuming, error-prone, and difficult to update. Chemical management systems provide a streamlined approach to handling chemicals by centralizing all relevant data in one accessible location. These systems enable real-time data access for all departments involved, such as procurement, safety, operations, and compliance teams. This centralization of information improves communication across departments and ensures that everyone has the same, up-to-date information at their fingertips. Moreover, automation plays a crucial role in improving operational efficiency. Routine tasks such as data entry, reporting, and inventory tracking can be automated, saving valuable time and resources. With fewer manual processes, employees can focus on more critical tasks, and the chances of mistakes or oversights are minimized.
Environmental Sustainability As businesses face growing pressure to reduce their environmental impact, chemical management plays a key role in sustainability efforts. Proper chemical management ensures that chemicals are disposed of according to environmental regulations, preventing contamination of water sources, soil, and air. In addition to safe disposal, chemical management helps reduce waste by optimizing chemical usage. By ensuring that chemicals are used efficiently and stored properly, businesses can reduce the amount of waste generated and recycle materials when possible. This contributes to a greener, more sustainable operation and helps businesses comply with environmental laws. Organizations that prioritize environmental sustainability through chemical management also enhance their brand reputation, as consumers and stakeholders increasingly demand eco-friendly practices.
Data Accuracy and Transparency Accurate and transparent chemical data is essential for making informed decisions and maintaining regulatory compliance. Paper records and manual data entry can lead to errors, inconsistencies, and discrepancies that could have serious consequences for safety, compliance, and operational efficiency. Chemical management systems offer a centralized, accurate, and standardized way to record and track all chemical-related data. From SDS and chemical inventories to safety audits and disposal logs, everything is stored in a single, easily accessible system. This reduces the risk of mistakes and ensures that all data is current, consistent, and easy to access. Furthermore, by providing detailed audit trails and tracking changes over time, chemical management systems enhance transparency and accountability. This is especially important during inspections, audits, or when responding to safety incidents, as it ensures that all actions taken are properly documented and can be traced back to their source.
Improved Collaboration and Communication Effective chemical management requires coordination between various departments within an organization, including safety, procurement, operations, and compliance. Chemical management systems foster better collaboration by providing a shared platform where all team members can access and update data in real-time. Whether it’s tracking chemical inventory, reviewing safety protocols, or updating compliance records, everyone involved in chemical handling can access the same data. This eliminates the need for lengthy email chains or manual updates, speeding up workflows and ensuring that everyone is on the same page. In turn, this improves decision-making, reduces errors, and ensures that chemicals are managed more effectively across the entire organization.
Scalability As businesses grow, their chemical management needs also evolve. What works for a small company may not be sufficient for a larger organization with more complex chemical handling requirements. Chemical management systems are scalable, meaning they can grow with your business and handle an increasing volume of chemicals, more complex regulatory requirements, and additional facilities. Scalability ensures that your organization can adapt to changing needs and continue managing chemicals effectively as it expands. Whether you're managing a small inventory or thousands of chemicals across multiple locations, a robust chemical management system will provide the necessary tools to handle the increasing complexity. How Chemical Management Is Great Chemical management is crucial for ensuring the safe, efficient, and compliant use of chemicals within an organization. By improving safety, reducing waste, ensuring regulatory compliance, and optimizing operations, effective chemical management helps organizations maintain a safe and sustainable working environment. Through streamlined processes, automated tracking, and centralized data, businesses can enhance their chemical management practices, save time and money, and reduce risks. Whether it's improving safety, boosting efficiency, or supporting environmental sustainability, chemical management is a powerful strategy for success in industries that handle chemicals. Conclusion Chemical management is a critical component of any business that deals with chemicals. It ensures the safe and efficient handling of chemicals, helps maintain regulatory compliance, and supports sustainability efforts. With the right chemical management system in place, businesses can reduce risks, improve operations, and save costs—all while keeping their workplace safe and adhering to environmental and safety standards. In today’s increasingly regulated and safety-conscious world, chemical management is not optional. It is a necessity for any organization that seeks to operate responsibly, sustainably, and efficiently. Whether you are a small business or a large corporation, implementing a comprehensive chemical management system is a smart decision that will help protect your people, your business, and the environment.
chemicalsafety #safetyfirst #chemicalindustry #chemicalmanufacturing #safetyculture #safetyprofessionals #calgary #yyc #alberta #canada #yycnow #yycliving #edmonton #toronto #vancouver
1 note
·
View note
Text
Chemical Management Software

Chemical Management Software: Why You’d Need/Want It and How It’s Great Chemical management is an essential process in various industries that deal with hazardous, controlled, or complex chemicals. From pharmaceuticals to manufacturing, and research to agriculture, businesses must ensure that chemicals are properly tracked, stored, used, and disposed of in accordance with safety protocols and regulatory guidelines. This can be a daunting task without a well-organized system in place. Enter Chemical Management Software (CMS), a powerful tool designed to streamline chemical handling, reduce risks, and improve efficiency. In this article, we’ll explore why you’d need chemical management software, its numerous benefits, and how it can transform your chemical management practices. What Is Chemical Management Software? Chemical Management Software is a digital solution designed to manage and optimize the entire lifecycle of chemicals within an organization. This includes everything from chemical procurement and inventory management to safety, usage tracking, compliance reporting, and disposal. CMS allows businesses to centralize their chemical-related data, providing real-time access to critical information about chemical properties, safety data sheets (SDS), and regulatory requirements. These systems are typically equipped with features such as automated chemical tracking, inventory management, hazard classification, reporting capabilities, and safety alerts. Chemical management software reduces human error, improves data accuracy, ensures compliance, and enhances overall operational efficiency by automating and simplifying time-consuming manual processes. Why You’d Need/Want Chemical Management Software
Improved Safety and Hazard Control Chemicals, especially hazardous ones, can pose significant risks to human health and the environment if not managed properly. Ensuring that chemicals are stored, handled, and disposed of safely is a critical responsibility for organizations. One of the primary benefits of using chemical management software is enhanced safety. A CMS provides easy access to Safety Data Sheets (SDS) for each chemical in your inventory. These sheets contain essential information about the chemical’s properties, potential hazards, emergency measures, and safe handling instructions. By keeping this information centralized and readily accessible, employees can quickly find critical safety details before using any chemical. Moreover, the software tracks essential safety features like the chemical’s expiration date, storage conditions, and specific usage instructions. Automated alerts and reminders about hazardous chemicals ensure that potential risks are mitigated before they turn into accidents.
Regulatory Compliance and Reporting Chemical management is heavily regulated, with strict requirements for the safe handling, labeling, storage, and disposal of chemicals. Regulatory bodies such as OSHA (Occupational Safety and Health Administration), EPA (Environmental Protection Agency), and REACH (Registration, Evaluation, Authorization, and Restriction of Chemicals) impose specific guidelines that organizations must follow. Failure to comply with these regulations can result in fines, legal trouble, and damage to a company’s reputation. Chemical management software ensures compliance by keeping track of all necessary documentation, such as SDS, chemical inventories, and safety audits. The software can generate reports that are required for regulatory inspections, making it easier to comply with regulations. In addition, it can automatically update chemical safety data based on the latest industry standards, ensuring that your organization is always in compliance with the current laws. Moreover, by automating compliance reporting and tracking, CMS eliminates the risks associated with missed deadlines or manual errors. This saves time and ensures your business is consistently adhering to safety and environmental regulations.
Streamlined Inventory Management One of the most important aspects of chemical management is inventory control. Keeping track of chemicals, including their quantities, expiration dates, and storage conditions, can be a time-consuming and error-prone task when done manually. Chemical management software automates this process, giving businesses a real-time overview of their chemical inventory. With CMS, you can track chemical quantities, monitor usage, and set automated re-order reminders to prevent running out of essential chemicals. The software can also notify you when chemicals are nearing their expiration dates, allowing you to use them before they become hazardous or wasteful. In addition, chemical management software can help with batch tracking, ensuring that you can trace the exact location and usage history of each chemical batch. This improves traceability and allows businesses to quickly identify potential issues related to specific batches if problems arise.
Cost Control and Waste Reduction Proper chemical management is crucial for controlling costs. Chemicals can be expensive, and poor management practices often lead to excess inventory, expired chemicals, and unnecessary waste. Chemical management software helps reduce waste and optimize chemical usage by providing real-time data on chemical consumption and expiry. By monitoring stock levels and usage patterns, CMS allows businesses to make better purchasing decisions, preventing overstocking or understocking. Additionally, tracking chemicals’ expiration dates ensures that they are used before they expire, reducing the need for disposal. This ability to optimize chemical usage helps businesses avoid unnecessary expenditures, improving cost efficiency. Chemical management software also helps streamline processes and reduce administrative overhead by automating tasks such as ordering, record-keeping, and reporting. These time-saving features not only lower labor costs but also ensure better financial control over chemical assets.
Data Accuracy and Centralization Managing chemical data manually using spreadsheets or paper logs can lead to inaccuracies, inconsistencies, and miscommunications. Inaccurate data can have serious consequences, including safety hazards, compliance violations, and operational inefficiencies. Chemical management software centralizes all data in one system, improving accuracy and consistency. When all chemical-related data—such as SDS, inventory levels, hazard classifications, and usage history—is stored in a single, accessible system, employees can access the most up-to-date and accurate information. The software reduces human error by automating data entry and ensuring that all chemical records are maintained in a standardized format. This centralization also makes it easier to track and audit chemical data, ensuring transparency and accountability within the organization. Furthermore, data from different departments, such as procurement, safety, and operations, can be easily shared and updated in real time, enhancing communication and collaboration across teams.
Enhanced Reporting and Analytics Chemical management software typically includes reporting and analytics features that give businesses valuable insights into their chemical usage, costs, compliance status, and safety performance. Customizable reports can be generated at any time, allowing businesses to analyze trends and make data-driven decisions. For example, the software can provide detailed reports on chemical usage over a specific period, which can help identify areas for improvement in consumption or waste reduction. Similarly, reports on chemical safety incidents or compliance status can help businesses monitor their safety performance and identify areas where further training or improvements are needed. These reporting capabilities are invaluable for businesses that need to make informed decisions, track progress toward sustainability goals, or ensure adherence to regulatory requirements. The ability to generate and share reports with internal and external stakeholders also enhances transparency and accountability.
Simplified Communication and Collaboration In organizations where multiple departments handle chemicals—such as safety, procurement, and operations—effective communication and collaboration are essential. Chemical management software provides a centralized platform where all teams can access and update chemical data in real time. Whether it’s the safety team reviewing SDS, the procurement team monitoring chemical stock levels, or the compliance team generating reports, CMS ensures that everyone is working with the same information. This reduces the chances of miscommunication, delays, and errors that can occur when different teams use disparate systems or manual methods. Moreover, the software can be integrated with other systems within the organization, such as enterprise resource planning (ERP) or inventory management software, creating a seamless flow of information across departments.
Scalability and Flexibility As businesses grow and their operations become more complex, they need a chemical management system that can scale with them. Chemical management software is highly scalable, meaning it can adapt to the increasing volume of chemicals, more complex inventory management needs, and the addition of multiple facilities or locations. Whether you are managing a small inventory of chemicals or handling thousands of chemicals across multiple sites, CMS can be customized to meet the unique needs of your organization. It can also handle different types of chemicals, varying regulatory requirements, and complex compliance standards, providing a flexible solution for businesses of all sizes.
Environmental Sustainability Sustainability is becoming an increasingly important factor for businesses across all industries. Chemical management software can help companies manage their chemicals in an environmentally responsible way. By tracking chemical usage, expiration dates, and disposal methods, CMS helps businesses reduce waste, avoid over-purchasing, and ensure proper disposal of hazardous chemicals. In addition, many chemical management systems help businesses comply with environmental regulations by ensuring that hazardous chemicals are disposed of safely and in accordance with local, state, and federal laws. This promotes sustainability and minimizes the environmental impact of chemical operations. How Chemical Management Software Is Great Chemical management software is not just a tool for organizing chemical data—it’s a game-changer for businesses that need to ensure the safe, compliant, and efficient use of chemicals. From improving safety and reducing waste to optimizing inventory management and ensuring regulatory compliance, CMS offers numerous benefits that improve operational efficiency, safety, and cost-effectiveness. By automating key processes and centralizing chemical data, CMS helps businesses minimize human error, reduce the risk of compliance violations, and improve communication across teams. The ability to generate real-time reports and track chemical usage also enables businesses to make data-driven decisions and improve their overall chemical management practices. Conclusion Chemical management software is an essential tool for organizations that handle chemicals. With the growing complexity of regulatory requirements, safety concerns, and operational demands, managing chemicals manually is no longer feasible or effective. By implementing a CMS, businesses can streamline their chemical management processes, ensure safety, reduce waste, and improve compliance—all while enhancing operational efficiency and controlling costs. Whether you are a small business or a large enterprise, investing in chemical management software is a smart decision that will help ensure your chemicals are handled safely, efficiently, and in compliance with regulations. In today’s fast-paced and regulated world, chemical management software is not just an option—it’s a necessity for businesses that deal with chemicals.
chemicalsafety #safetyfirst #chemicalindustry #chemicalmanufacturing #safetyculture #safetyprofessionals #calgary #yyc #alberta #canada #yycnow #yycliving #edmonton #toronto #vancouver
1 note
·
View note
Text
Chemical Inventory Management Software
Why You’d Need/Want It and How It’s Great
In industries that handle chemicals, from pharmaceuticals to manufacturing and research, managing chemical inventories is not just a logistical necessity but also a safety and regulatory concern. Chemicals, whether hazardous or non-hazardous, require meticulous tracking to ensure their proper usage, storage, and disposal. Traditionally, businesses have relied on manual processes or outdated systems, but today, more organizations are turning to chemical inventory management software. This advanced software helps streamline operations, maintain compliance, and enhance safety. In this article, we’ll explore why chemical inventory management software is essential, how it benefits organizations, and why it's a great investment for businesses.
What Is Chemical Inventory Management Software?
Chemical inventory management software is a tool designed to help businesses track, manage, and organize their chemical inventories digitally. Unlike traditional manual methods, such as spreadsheets or paper logs, this software automates processes, integrates real-time data, and provides comprehensive management features. The software allows organizations to record the types and quantities of chemicals, track their expiration dates, monitor usage levels, ensure proper storage, and comply with regulatory requirements—all from a centralized platform.
With built-in features like barcode scanning, automatic alerts, compliance tracking, and detailed reporting, chemical inventory management software significantly enhances efficiency, accuracy, and safety in chemical handling.
Why You’d Need/Want Chemical Inventory Management Software
1. Enhanced Safety and Risk Management
Chemical safety is one of the most critical aspects of any organization dealing with hazardous materials. Whether it's chemicals that are toxic, flammable, or corrosive, ensuring proper handling and storage is essential for preventing accidents. With chemical inventory management software, businesses can store detailed information about each chemical, including safety data sheets (SDS), hazard classifications, and storage guidelines. This ensures that employees have immediate access to essential safety information.
Furthermore, the software allows for real-time tracking of chemical usage, making it easier to monitor inventory levels and detect any discrepancies that could indicate a spill or misuse. By automating safety protocols and generating alerts for important actions—such as the need for personal protective equipment (PPE) or ventilation when handling certain chemicals—the software minimizes human error and contributes to a safer working environment.
2. Regulatory Compliance Made Easy
Businesses that handle chemicals must adhere to stringent regulations set by agencies such as OSHA (Occupational Safety and Health Administration), EPA (Environmental Protection Agency), and DOT (Department of Transportation). Chemical inventory management software helps ensure compliance with these regulations by tracking necessary documentation, including SDS, proper chemical labeling, and hazardous material storage guidelines.
The software generates reports that are required for inspections or audits, allowing businesses to provide up-to-date and accurate records quickly. Automated reminders about regulatory deadlines, such as expiration dates for chemicals or recertification of safety protocols, help businesses avoid costly fines and legal issues. By keeping everything organized and up-to-date, chemical inventory management software ensures that your organization remains in good standing with regulatory authorities.
3. Streamlined Inventory Tracking
Manual inventory management can be time-consuming, prone to human error, and difficult to scale as a business grows. With chemical inventory management software, organizations can automate many aspects of their inventory control. The software allows businesses to track chemical quantities in real time, from the moment chemicals arrive at the facility to when they are used or disposed of.
By using barcode scanning or RFID (radio-frequency identification), employees can quickly update stock levels as chemicals are added, removed, or consumed. This eliminates manual counting and reduces the chance of mistakes. Real-time inventory updates also provide insight into stock levels, helping businesses avoid running out of essential chemicals or overstocking items that are rarely used.
4. Cost Control and Efficiency
Cost control is a primary concern for many businesses, especially when dealing with expensive or specialized chemicals. Chemical inventory management software enables businesses to keep track of chemical consumption and identify waste. For example, it can show if certain chemicals are being over-ordered, under-utilized, or approaching their expiration date, enabling organizations to optimize their purchasing decisions.
By automating reorder processes and providing usage reports, the software helps reduce overstocking and understocking, minimizing waste and preventing costly inventory shortages. Additionally, the software can generate insights into chemical consumption patterns, allowing businesses to implement more efficient practices and ultimately reduce operating costs.
5. Better Forecasting and Planning
With accurate data and historical trends at your fingertips, chemical inventory management software aids in forecasting future chemical needs. The software analyzes past usage patterns, seasonal variations, and order histories to provide valuable insights into when and how much of a particular chemical should be ordered.
By using this predictive capability, businesses can avoid last-minute orders, manage inventory more efficiently, and ensure that chemicals are available when needed. This predictive feature is especially valuable in industries where chemical requirements can fluctuate, such as in manufacturing or research, where different projects may require varying amounts of specific chemicals.
6. Simplified Disposal and Expiration Tracking
Proper disposal of chemicals, especially hazardous ones, is a critical aspect of chemical management. Chemical inventory management software makes it easier to track expiration dates and safely dispose of chemicals that are no longer needed. The software automatically alerts you when a chemical is nearing its expiration, allowing ample time to either use or dispose of it according to regulatory guidelines.
By keeping track of disposal procedures and compliance with environmental regulations, the software helps organizations avoid accidental contamination and ensures that waste management practices are conducted correctly. This contributes to sustainability efforts and minimizes the environmental impact of chemical operations.
7. Improved Reporting and Documentation
One of the key advantages of using chemical inventory management software is its ability to generate detailed reports and documentation. These reports can be customized to meet the needs of different stakeholders within the organization, whether it's for safety audits, regulatory inspections, or management reviews.
The software can generate reports on chemical usage, safety compliance, inventory turnover, and more. This helps businesses track their chemical operations and make data-driven decisions about inventory management, purchasing, and safety protocols. By having all this information in a digital format, businesses save time and effort compared to traditional paper-based reporting.
8. Increased Operational Efficiency
The automation provided by chemical inventory management software can drastically increase operational efficiency. Tasks that once took hours—such as tracking chemicals manually, updating records, or generating compliance reports—can now be completed in minutes. The software integrates with other business systems, such as procurement, enterprise resource planning (ERP), or safety management tools, further streamlining operations.
By eliminating repetitive administrative tasks and providing a clear overview of the entire chemical inventory, the software allows employees to focus on more strategic tasks, improving overall productivity. The efficiency gains also extend to improving communication across departments, ensuring that all teams are on the same page when it comes to chemical management.
9. Customizable for Your Business Needs
Different industries have different requirements when it comes to chemical inventory management. Whether you’re in pharmaceuticals, manufacturing, or research, chemical inventory management software can be tailored to meet the unique needs of your business. Many software solutions offer customization options, such as adding specific chemical categories, integrating with other systems, or adjusting reporting features to suit your operations.
Customizable software ensures that your chemical inventory system is aligned with your specific business processes and workflows, allowing for maximum efficiency and effectiveness.
How Chemical Inventory Management Software Is Great
Chemical inventory management software is an indispensable tool for modern businesses that deal with chemicals. It brings efficiency, accuracy, and automation to a process that can otherwise be time-consuming, error-prone, and complex. By enhancing safety, improving regulatory compliance, optimizing inventory control, and reducing costs, this software not only simplifies chemical management but also provides businesses with better control over their operations.
The ability to track chemicals in real time, access up-to-date safety data, generate detailed reports, and forecast future needs makes chemical inventory management software an invaluable asset for any organization. Whether you are trying to streamline operations, ensure safety, maintain compliance, or reduce costs, this software offers comprehensive solutions that benefit businesses in multiple ways.
Conclusion
In today’s fast-paced and regulated business environment, chemical inventory management software is more than just a convenience—it’s a necessity. With its ability to automate processes, track chemicals in real time, ensure regulatory compliance, and improve safety, this software offers numerous advantages for organizations in industries that handle chemicals. From small businesses to large corporations, chemical inventory management software helps optimize operations, enhance decision-making, and reduce risk, making it a great investment for any company looking to improve its chemical management practices.
1 note
·
View note
Text
Samsung Knox Native Solution: BSI-Certified Secure Platform

A New Standard in Secure Communications for Governments and Businesses Is Set by Samsung’s Knox Native Solution.
Samsung Knox Native Solution expands safe choices for international businesses and authorities by offering government-grade protection without the need for third-party add-ons.
Samsung Electronics announced that the German Federal Office for Information Security, or Bundesamt für Sicherheit in der Informationstechnik (BSI), has certified Samsung Knox Native Solution, a platform that facilitates quick and simple secure communications designed for businesses and government agencies. The Knox Native Solution, which was developed in close cooperation with the BSI, provides enhanced security to satisfy very strict criteria by establishing a dedicated, secure environment on mobile devices. Samsung maintains its position as a world leader in cybersecurity solutions with certifications from a wide range of international government agencies, including those in Australia, Canada, the Netherlands, the United Kingdom, and the United States.
Samsung’s trusted role in providing secure, integrated solutions that satisfy the high standards for government and enterprise use is further reinforced by the Knox Native Solution’s official recognition for government use from a prominent European security body. Additionally, this accreditation reaffirms Knox Native Solution as a globally applicable model for businesses, particularly those in vital sectors like public transportation or energy infrastructure, or those looking for dependable, strong, and deployable security for mobile communications that are optimized.
Security Created in Partnership with the BSI
In the past, using external SD cards, extra software, and several PINs to achieve government-grade secure mobile communication on Android-based smartphones was frequently necessary. This led to a laborious manual procedure that was expensive and involved lengthy approval cycles for security solutions. The process would get even more complicated if third-party security updates were to demand re-certification of the entire device. Samsung worked with the BSI, which is regarded as the premier organization for security certifications and policy in Europe and important international sectors, to address these issues. Together, they created a government-grade, pre-configured system that satisfies Germany’s strict security requirements and establishes the benchmark for safe gadgets and solutions globally.
The embedded Secure Element (eSE), which combines the BSI Java Card Applet and is certified at the industry-leading Common Criteria Evaluation Assurance Level (CC EAL) 6+, is one of the cutting-edge aspects of this creative platform. Data integrity, real-time threat protection, and encrypted storage for sensitive communication channels are all made possible by Knox Native Solution’s creation of a specific security zone inside the device with eSE. Because this platform is integrated within the device itself, it eliminates the need for third-party apps or add-ons, allowing for a tamper-resistant security environment for essential features like calendaring, contacts, and email.
Mobile experiences that are secure and seamless
Samsung Galaxy smartphones are the first in the Android ecosystem to successfully exceed the stringent security standards of the BSI using eSE, further solidifying Knox Native Solution’s position as the new industry standard for mobile security. By removing the need for intricate configurations and guaranteeing high security requirements, Knox Native Solution helps enterprises to deploy secure devices in a few simple steps.
Using the built-in safeguards for data-at-rest, data-in-use, and data-in-transit that Samsung Knox offers, this solution maintains a simplified user experience without sacrificing security. Users and administrators alike will find improved security to be straightforward thanks to a single PIN activation that covers a variety of work scenarios and seamless integration of company-owned apps via the Knox Native Solution SDK.
By requiring only recently updated apps to be assessed and approved, Knox Native Solution reimagines security evaluation procedures on Samsung Galaxy devices for German government and enterprise, providing customers with mobile solutions that are both cost-effective and optimized. Knox Native Solution gives businesses centralized control over their security requirements by streamlining creation and evaluation with pre-approved security features. This allows Knox Suite to effectively manage even huge device fleets with high security standards. Samsung, a well-known and reliable supplier of secure mobile solutions to German government agencies, is dedicated to providing enterprises all over the world with reliable and smooth mobile security.
Sustained Faith in an Ultra-Connected World
Samsung’s ability to satisfy strict government requirements is demonstrated by this BSI accreditation, which serves as an example of how businesses and governments worldwide may embrace safe, integrated mobile solutions. Samsung intends to extend Knox Native Solution’s accessibility to further areas in order to build on its success in Germany and further solidify its position as a world leader in safe, interconnected mobile environments.
Read more on Govindhtech.com
#KnoxNativeSolution#SamsungElectronics#BSI#KnoxSuite#cybersecurity#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
0 notes
Text
New bug fixes and features - November 2024
We’re thankful for you! The Screwdriver team is pleased to announce our newest release which brings in new features and bug fixes across various components.
New Features
UI
Virtual job improvements - You can now see a different icon for virtual jobs in the workflow graph. They will also have a `virtual` tag in the pipeline Options tab. The virtual job build page will no longer show logs or warnings. You can read more about using `screwdriver.cd/virtualJob` annotation in the Screwdriver documentation.
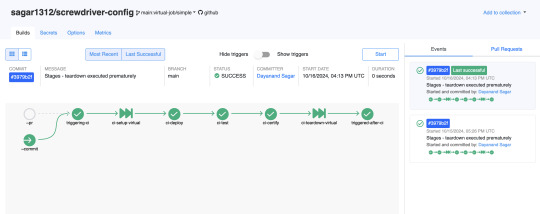
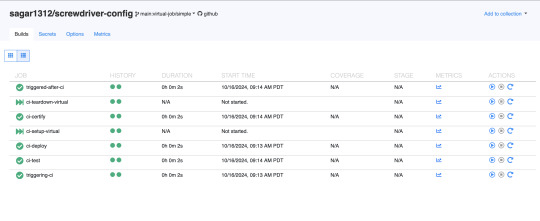

Option to download directory artifacts as zipped file - You can now download an artifact directory for a build as a zipped file. Navigate to a folder under Artifacts and click the existing “Download” button. Max size 2GB.

Jobs list view has stages column and ability to select number of historical builds shown - You can now see which stage each job belongs to and sort by stage. You can also select to show up to 30 historical builds on the same page.
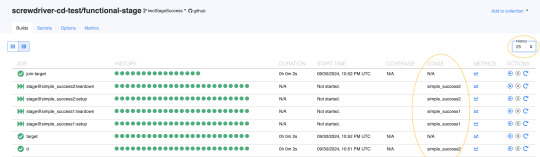
API
Add option to download directory artifacts as zip file - You can now download a directory of artifacts in a build as a zipped file using GET /builds/{id}/artifacts/this/is/a/directory/path?type=download&dir=true endpoint.
Bug Fixes
UI
Add feature flag for download all artifacts
Build detail view - Hide steps and logs for virtual builds
Download directory should use feature flag
Fix the missing download button
Find workflow graph node for a virtual build by job name
Show download button when the flag is false
Allow DOWNLOAD_ARTIFACT_DIR to be set in environment variables
API
Update pipeline-templates.md
Add the design implementation for the sd artifacts download
Set build status message while skipping execution of virtual job
Use query param dir=true to indicate directory download
Fix assigned remote trigger events
Add maxDownloadSize for artifact directory download
Fix the missing artifactsMaxDownloadSize
Improve metadata functional tests
Queue-service
Set build status message type while skipping execution of virtual job
Launcher
Add GIT_ASKPASS
ParentEvent should be a predecessor of other metadata
Event and parentEvent meta should be mutually exclusive
Downgrade to older version of sd-packages
Always allow parent event metadata to be merged during the build
Pin version of store-cli to v0.0.71
Compatibility List
In order to have these improvements, you will need these minimum versions:
API - v7.0.227
UI - v1.0.1095
Store - v6.0.0
Queue-Service - v4.0.5
Launcher - v6.0.210
Build Cluster Worker - v4.0.3
Contributors
Thanks to the following contributors for making this feature possible:
Akinori
Jithin
Keisuke
Ming
Pritam
Sagar
Tiffany
Vonny
Yuki
Yuta
Questions and Suggestions
We’d love to hear from you. If you have any questions, please feel free to reach out here. You can also visit us on Github and Slack.
Author
Tiffany Kyi, Software Engineer, Yahoo
0 notes
Text
SDS Authoring Software - Kalium Solutions Looking to streamline your chemical safety compliance? Kalium Solutions offers SDS Authoring Software on rent, making it easy to create, manage, and update Safety Data Sheets with ease. Apply now to access user-friendly tools that keep your business compliant and safe. Watch this video and reach out to Kalium Solutions to get started!
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] The iStorage datAshur SD is a PIN-authenticated, hardware-encrypted USB type-C flash drive designed to incorporate removable iStorage microSD cards with capacities ranging from 32GB-1TB. Instead of incorporating fixed memory, the datAshur SD is designed with an integrated microSD card slot, making it a unique, ultra-secure and cost-effective solution that allows users to use a drive with as many iStorage microSD cards as needed, which are available in different capacities, offering unlimited encrypted data storage. In addition, the patented iStorage datAshur SD KeyWriter software clones datAshur SD flash drives with the same encrypted encryption key that allows a secondary drive as backup and also allows organizations to share encrypted microSD cards with as many authorized users of cloned datAshur SD drives as needed, without compromising data security. All data stored on the microSD cards are encrypted (full disk encryption) using the 256-bit AES-XTS hardware encryption validated by FIPS PUB 197. In addition to the datAshur PRO2, the datAshur SD is the world's only encrypted USB flash drive that incorporates a secure Common Criteria EAL 5+ certified microprocessor, which enhances security through true random number generation and built-in cryptography. The data encryption key is protected by FIPS and Common Criteria validated packaging algorithms and is securely stored in the secure microprocessor, separate from the data. Package includes 2 x iStorage datAshur SD drives + 1 x iStorage microSD card + FREE KeyWriter license which allows you to clone your datAshur SD drives with the same encryption key. This allows users with different datAshur SD drives to share encrypted data stored on iStorage microSD cards or create a backup drive in case their datAshur SD drive is lost or stolen. Easy to use: Insert your iStorage microSD card into the datAshur SD microSD card slot and simply enter your 8-64 digit PIN to authenticate and use it as a normal flash drive. When the drive is locked, all data on the iStorage microSD card is encrypted (full disk encryption) using 256-bit AES-XTS hardware encryption. UNLIMITED CAPACITY - Allows users to use a datAshur SD drive with as many iStorage microSD cards as needed, in different capacities, offering unlimited and economical encrypted data storage. Available capacities: 32GB, 64GB, 128GB, 256GB, 512GB and 1TB Only genuine iStorage microSD cards are compatible with iStorage datAshur SD drives. No software required: No software is required; the drive will work on any device with a USB port. USB Type-C and Type-A connectivity (included) Compatible with: MS Windows, macOS, Linux, Android, Chrome, Thin Clients, Zero Clients, Embedded Systems, Citrix and VMware. [ad_2]
0 notes
Text
Empowering Connectivity with Sify's Enterprise Network Services
In the digital age, seamless and secure connectivity is the backbone of any successful enterprise. As businesses expand and evolve, their networking needs become increasingly complex, requiring solutions that are not only robust and reliable but also scalable and adaptable to changing demands. Sify’s Enterprise Network Services are designed to meet these challenges head-on, providing businesses with the connectivity infrastructure they need to drive innovation, enhance collaboration, and stay ahead in a competitive marketplace.
The Importance of Enterprise Networks
An enterprise network is more than just a collection of interconnected devices; it is the lifeline that supports the entire organization’s operations. From enabling communication and collaboration among employees to connecting with customers and partners, a well-designed network is essential for ensuring that business processes run smoothly and efficiently.
Key benefits of a strong enterprise network include:
Enhanced Connectivity: Seamless communication and data exchange between various departments, offices, and remote locations.
Scalability: The ability to expand network capacity to accommodate business growth without compromising performance.
Security: Protecting sensitive data and ensuring that only authorized users can access the network.
Resilience: Minimizing downtime and ensuring business continuity through robust network design and management.
Efficiency: Optimizing the use of network resources to reduce costs and improve overall productivity.
Sify’s Comprehensive Enterprise Network Services
Sify’s Enterprise Network Services offer a complete suite of solutions that address the diverse networking needs of modern businesses. Whether you are looking to build a new network from the ground up, optimize your existing infrastructure, or enhance network security, Sify has the expertise and technology to deliver.
Wide Area Network (WAN) Solutions: Sify provides advanced WAN solutions that connect your various business locations, enabling seamless communication and data sharing across geographically dispersed sites. Our WAN services include Software-Defined WAN (SD-WAN), which offers greater flexibility, improved performance, and enhanced security by dynamically routing traffic across the best available path.
Local Area Network (LAN) Services: Sify’s LAN services are designed to support high-performance, reliable, and secure connections within your organization. We offer LAN design, deployment, and management services that ensure your internal network infrastructure is optimized for speed, security, and scalability.
Managed Network Services: Sify’s Managed Network Services take the complexity out of network management by offering end-to-end monitoring, maintenance, and support. Our team of network experts proactively manages your network to ensure optimal performance, quickly addressing any issues before they impact your business operations.
Network Security Solutions: In today’s threat landscape, network security is more critical than ever. Sify provides comprehensive network security solutions that protect your network from cyber threats and unauthorized access. Our services include firewalls, intrusion detection and prevention systems, VPNs, and secure access controls, all designed to safeguard your data and maintain the integrity of your network.
Cloud Connectivity Services: As more businesses move to the cloud, ensuring secure and reliable connectivity between on-premises networks and cloud environments is essential. Sify’s Cloud Connectivity Services provide high-performance, low-latency connections to leading cloud platforms such as AWS, Microsoft Azure, and Google Cloud, enabling seamless integration between your network and cloud resources.
Unified Communications (UC) Solutions: Sify’s Unified Communications solutions integrate voice, video, messaging, and collaboration tools into a single platform, enhancing communication and collaboration across your organization. Our UC services are designed to work seamlessly with your existing network infrastructure, providing a cohesive and efficient communication experience.
Network Analytics and Optimization: Sify’s Network Analytics and Optimization services provide deep insights into your network’s performance, helping you identify bottlenecks, optimize resource usage, and plan for future growth. By leveraging advanced analytics tools, we help you make data-driven decisions that enhance network efficiency and performance.
The Sify Advantage
Sify’s Enterprise Network Services are built on a foundation of industry expertise, cutting-edge technology, and a commitment to customer success. What sets Sify apart is our ability to offer customized solutions that align with your specific business needs and goals. We understand that every organization is unique, and we work closely with our clients to design and implement network solutions that drive real business value.
Our global presence, combined with our extensive experience in managing complex networks, allows us to deliver reliable and scalable solutions that support your business’s growth and innovation. Sify also places a strong emphasis on security, ensuring that your network is protected against the latest threats and vulnerabilities.
Real-World Impact
Sify’s Enterprise Network Services have transformed the networking capabilities of businesses across various industries:
Manufacturing: A global manufacturing company leveraged Sify’s SD-WAN solution to connect its production facilities across multiple countries, improving communication and data sharing while reducing costs.
Retail: A leading retail chain utilized Sify’s Managed Network Services to ensure the reliability and security of its in-store and online networks, enhancing the customer experience and supporting e-commerce growth.
Finance: A financial services firm implemented Sify’s Network Security Solutions to protect sensitive customer data and ensure compliance with industry regulations, bolstering trust and security.
In an increasingly connected world, having a robust and reliable enterprise network is essential for business success. Sify’s Enterprise Network Services provide the foundation for secure, scalable, and efficient connectivity that empowers your organization to innovate, collaborate, and thrive in the digital age.
Partner with Sify to build a network that not only meets your current needs but also prepares you for the future — where connectivity is seamless, security is uncompromised, and your business can reach new heights.
0 notes
Text
What Makes MPLS and SD-WAN-Based Office Networks Different

Multi-protocol label switching (MPLS) or software-defined wide area network (SD-WAN)? Most business owners in Saskatoon who must choose between the two want to know which will work better for their office network. To make the right choice, you first need to understand their differences.
In short, MPLS is a dedicated circuit, while SD-WAN is a virtual connection that does not depend on physical links. Because of this, MPLS is better at preventing packet loss. The virtual overlay in SD-WAN, on the other hand, allows users to utilize additional network links such as LTE, broadband, and MPLS, offering more flexibility.
Compare Costs
Companies that use MPLS networks typically employ a hub-and-spoke model with separate MPLS connections to link their remote offices to the main data center. As a result, all data, processes, and even cloud-based services require routing back to the data center for processing and redistribution. This setup is often not cost-effective.
SD-WAN reduces costs by connecting multiple locations through private, distributed data exchanges and control points. This configuration allows users improved and more direct access to the cloud and networking services they require.
Issues with Security
The internal backbone of the service provider acts as a secure and managed link between the company’s data center and branch offices, a benefit well-known to companies using MPLS. Most public internet services do not offer this level of security.
However, it's important to note that MPLS does not inherently inspect the data it carries. A firewall must be installed at one end of the link to scrutinize all traffic for malware and other security threats.
Additionally, this is a challenge that most SD-WAN systems face, necessitating enhanced security measures. Integrating security tools post-deployment complicates the process.
To prevent these issues, skilled network installation service providers incorporate SD-WAN connectivity directly into a next-generation firewall (NGFW) device. Each connection, therefore, features dynamic, meshed virtual private network (VPN) capabilities to secure data in transit. Several security tools, including firewalls, antivirus software, intrusion prevention systems, web filtering, and anti-malware, are employed to thoroughly scrutinize data.
How the Network Operates
In terms of performance, MPLS offers a consistent and fixed bandwidth level, which is advantageous for businesses. However, today's network traffic has variable speed demands. Thus, when businesses opt for an MPLS solution, there may be periods when expensive bandwidth remains underused, and times when MPLS may strain network connectivity due to the ever-increasing volume of data transmitted through new apps and devices.
SD-WAN can identify the types of apps in use and adjust bandwidth accordingly. It also sets up multiple parallel links to facilitate load sharing. Another advantage is failover, which involves switching to an alternate link if one connection fails. This feature ensures that latency-sensitive applications continue to perform optimally.
When MPLS May Be Preferable to SD-WAN
There are instances where MPLS might be a more suitable choice than SD-WAN, despite being considered an older network protocol by many.
MPLS remains an effective method for establishing secure and isolated connections for apps, transactions, and data that need to be kept separate from public internet networks. It offers a high level of data security. Both MPLS and SD-WAN can also be used together to manage various online activities.
If you are undecided between SD-WAN and MPLS, do not hesitate to consult network service providers. They understand how to leverage each technology in different scenarios and can help you choose the best option for your digital-first office.
Author Bio:
Layer 3 is a Managed IT company in Saskatoon that supports businesses with their IT needs. The team has extensive expertise in cloud solutions, network setup and security, emergency recovery, data backups, web design, and development. Please visit their website to learn more about the team.
0 notes
Text
TradePoint Facebook - Erbauer Tools Giveaway - 15/04/2024
TradePoint Facebook - Erbauer Tools Giveaway - 1 x Erbauer Tools Bundle Prize Draw Terms and Conditions - 15/04/2024
The Promoter:
TradePoint. TradePoint is a trading name of B&Q Ltd, B&Q House, Chestnut Avenue, Chandler’s Ford, Eastleigh, SO53 3LE.
Who can enter?
This promotion is open to all residents of the UK and the Republic of Ireland age 18 years and over, excluding employees of B&Q plc, their families, agents or anyone else connected with the administration of the promotion.
How to enter?
Make sure you're following @TradePoint
Like this: https://www.facebook.com/TradePointUK/posts/844995691000580
Tag a tradie who loves their tools
Entries must be submitted by 11:59pm on 19th April 2024. Entries received after this date will not be accepted.
Entry:
Only one entry per person will be accepted. Third party or multiple entries by the same person will not be accepted and we reserve the right to disqualify any entries we reasonably suspect to have been made fraudulently including through the use of bots, computer software or by any other means. We accept no responsibility for any lost, damaged or incomplete entries or entries not received due to a technical fault or for any other reason beyond our reasonable control.
We reserve the right to terminate the promotion or declare void any entry it suspects of fraud or contains any content it considers will bring the promotion into disrepute.
Prize Details:
There will be 1 winner selected at random. The winner will receive the following prize bundle:
1 x ERBAUER 18V IMPACT & COMBI
1 x EXTERBAUER 18V EXT RO SANDER BARE
1 x ERBAUER 18V EXT 165MM CIRC SAW BAR
1 x EERBAUER 18V JIGSAW EXT BARE
1 x ERBAUER 18V MULTITOOL EXT1X4AH
1 x ERBAUER 18V SDS EXT BARE
1 x ERBAUER MIXED DRILL BIT SET 113PK
1 x ERBAUER MULTI-TOOL ACCESSORY 6PCS SET
1 x ERBAUER WOOD METAL T JIGSAW BLADES 10PK
1 x ERBAUER TCT MULTI 165 X20/16 MEDIUM 40T
1 x ERBAUER 18V 30CM GRASS TRIMMER KIT
1 x ERBAUER 18V BLOWER KIT
The prize is not transferable and there is no cash alternative. We reserve the right to substitute any element of the prize bundle for an item of the same or higher value where it becomes necessary to do so.
Winner selection and prize fulfilment:
There will be 1 winner chosen at random from all valid entries received.
The winner will be contacted via response to their winning comment by 5pm on the 26th April 2024. To receive the prize, the winner will need to respond via private message providing their contact details. If the winner fails to provide their contact details within 7 days of initial contact from the Promoter, the prize will be offered to the next randomly chosen entrant.
The prize bundle will be dispatched by mid-May 2024.
This promotion is in no way endorsed or administered by or associated with Facebook.
Your Data:
We will process information about entrants in order to administer this promotion. For more information on how we use personal information, please see http://www.diy.com/customer-support/policies/privacy. By entering this promotion, you agree and consent to the processing of your personal data by us and by any third party acting on our behalf for the purposes of the administration and operation of the promotion.
Please note that we are obliged to either publish or make available on request the surname, county and, where applicable, the winning entry/entries of major prize winners. If you object to any of this information being made available in this way, please contact [email protected]. We must nevertheless share this information with the Advertising Standards Authority where it becomes necessary to do so.
Your acceptance of these Terms:
We reserve the right to refuse entry or refuse to award any prize to anyone in breach of these Terms and Conditions and/or hold void, cancel, suspend or amend these Terms and Conditions where it becomes necessary to do so. Our decision on all matters relating to this promotion is final and binding. No correspondence will be entered into.
Liability:
By entering this promotion, you are deemed to have accepted and agreed to be bound by these Terms and Conditions.
Insofar as is permitted by law the Promoter and its agents and distributors will not in any circumstances be responsible or liable to compensate the winner or accept any liability for any loss, damage, personal injury or death occurring as a result of taking up the prize except where it is caused by the negligence of the Promoter, its agents or distributors or that of their employees.
This promotion is in no way endorsed or administered by or associated with Instagram or Meta.
Governing Law:
Nothing in these Terms and Conditions restricts your statutory rights as a consumer. This promotion will be governed by English law and entrants submit to the jurisdiction of the English Courts.
0 notes