#Offline Data Entry Companies
Explore tagged Tumblr posts
Text
The Most Common Challenges in Offline Data Entry and How to Overcome Them

Offline data entry is considered as the most traditional data entry method and this is how the journey of recording data into digital format began. In today’s digital world, data entry is considered as one of the critical tasks of business operations. Due to the changing demand of the market, most of the companies are using online data entry systems to perform their routine data entry tasks. But, there are still many industries and business models that rely heavily on offline data entry services.
Offline data entry is manually entering data into a computer system or any other digital device. You can enter the data from documents or forms in physical form, or perform data entry from handwritten records. Some of the information that requires offline data entry are the attendance of employees or workers on a construction site, manually taking purchase orders from local vendors, etc.
Challenges Of Traditional Data Entry Methods
As offline data entry is the most commonly used data entry method, there are some challenges in performing the task. As it depends on the skills and experience of the person performing the data entry work, it may not be consistent for every data entry work performed by the team members.
In this blog, we are digging deep to explore the most commonly faced challenges in offline data entry work and we will try to find out practical solutions to overcome them.
Human Errors
Challenges of Human Errors: One of the known challenges with offline data entry is the high chances of human errors in data entry work. Data entry must be performed with high accuracy. If the data entry work is performed with manual data input, it can increase the chances of mistakes in data such as typing errors, missing data, or mis-spelled details in entering the information. A small error in data entry can create a high risk of losing customers' trust, you can also miss on a client's expectations with the results you deliver. As a result, it can impact your business in a negative way such as revenue loss or other financial losses.
Solution to Prevent Human Errors: To prevent your team from performing offline data entry work with human errors, the best way is to have a separate process for quality check that can assure the data entered is checked efficiently for highlighting human errors. Also, you can also have a quality check of data entry operators on a frequent basis or plan some training sessions for data entry operators to reassure that the results are aligned with the expected quality. You can also use automation for offline data entry work to validate and highlight errors that can later be checked and corrected by data entry experts.
Take A Lot Time For Bulk Data Entry Work
Challenges of High Turn-around Time: Offline data entry is usually performed manually by entering the data record by record. If the data is in large volume, it can take a lot of time and it is highly possible that the work is not delivered at the given timelines or there are high chances of missing deadlines. As the data entry work is monotonous, it can reduce the efficiency of data entry operators if they are not given enough break times. Your business may need to invest a lot in hiring a large team of data entry work to perform data entry of large quantities.
Solution of Saving Time in Data Entry: Time is a precious element in any business environment, it can affect your business on many dimensions such as customer experience, operational expenses, business growth, etc. In data entry work, it is important to keep your team motivated and engage them in the activities to keep them focused while performing data entry work. One of the best solutions is to outsource offline data entry to professionals at your expected budget, this will save your time and resources and also you can hire the team with great flexibility to overcome the challenges of changing data volumes.
Inconsistent Data Entry Formats
Challenges of Maintaining Consistent Data Formats: Data is easy to read and understand when it is in the same format. If your data is in various different formats, it can be difficult to use that data for strategic planning and analytical purposes. As a business owner, you must have your data aligned with your business needs as it can be time-consuming to filter data every now and then. Inconsistency in data can lead to many challenges in performing daily business activities.
Solution of Data Formatting: To keep your data consistent across all data entry work, you need to create a standard data format that is implemented for every data entry process. Also, there needs to be quality checks done to ensure the format is being utilized in the most efficient way. It is also possible to define guidelines on how to use the data entry templates and give training to data entry operators on performing such complex data entry tasks. Optical character recognition (OCR) technology can be used to convert handwritten documents in digital format with high accuracy and efficiency.
In offline data entry services there can be many challenges, but the modern problems come with modern solutions. One of the most suitable solutions to perform offline data entry is to outsource data entry services to professionals. If you need to focus on your business development and handover the crucial data entry work to experts, you can rely on your trusted offline data entry professionals. Increase your operations efficiency, reduce human errors and keep your data ready for strategic planning with these helpful tactics.
Source Link: https://latestbpoblog.blogspot.com/2024/10/the-most-common-challenges-in-offline-data-entry-and-how-to-overcome-them.html
#Data Entry Offline#Offline Data Entry Services#Outsource Offline Data Entry Services#Outsource Offline Data Entry#Offline Data Entry Company#Offline Data Entry Companies
0 notes
Text
Best Offline Data Entry Services in India

Although the business data relies on online processes the company has plenty of complex offline data to be entered in a dependable database for future use. Leveraging a reliable offline data entry service company is the perfect option for effective business expansion. Offline data entry is the compilation and synchronization of company data from different sources. Plus, Data Entry Expert can achieve great work as our experts work rigorously to give the best data entry output.
#Offline Data Entry#Offline Data Entry Services#Offline Data Entry in India#Outsource Offline Data Entry Services#Outsource Offline Data Entry#Offline Data Entry Companies#Offline Data Entry Company
0 notes
Text
The Most Common Challenges in Offline Data Entry and How to Overcome Them

Offline data entry is considered as the most traditional data entry method and this is how the journey of recording data into digital format began. In today’s digital world, data entry is considered as one of the critical tasks of business operations. Due to the changing demand of the market, most of the companies are using online data entry systems to perform their routine data entry tasks. But, there are still many industries and business models that rely heavily on ‘offline data entry services.
Offline data entry is manually entering data into a computer system or any other digital device. You can enter the data from documents or forms in physical form, or perform data entry from handwritten records. Some of the information that requires offline data entry are the attendance of employees or workers on a construction site, manually taking purchase orders from local vendors, etc.
Challenges Of Traditional Data Entry Methods
As offline data entry is the most commonly used data entry method, there are some challenges in performing the task. As it depends on the skills and experience of the person performing the data entry work, it may not be consistent for every data entry work performed by the team members.
In this blog, we are digging deep to explore the most commonly faced challenges in offline data entry work and we will try to find out practical solutions to overcome them.
Human Errors
Challenges of Human Errors: One of the known challenges with offline data entry is the high chances of human errors in data entry work. Data entry must be performed with high accuracy. If the data entry work is performed with manual data input, it can increase the chances of mistakes in data such as typing errors, missing data, or mis-spelled details in entering the information. A small error in data entry can create a high risk of losing customers' trust, you can also miss on a client's expectations with the results you deliver. As a result, it can impact your business in a negative way such as revenue loss or other financial losses.
Solution to Prevent Human Errors: To prevent your team from performing offline data entry work with human errors, the best way is to have a separate process for quality check that can assure the data entered is checked efficiently for highlighting human errors. Also, you can also have a quality check of data entry operators on a frequent basis or plan some training sessions for data entry operators to reassure that the results are aligned with the expected quality. You can also use automation for offline data entry work to validate and highlight errors that can later be checked and corrected by data entry experts.
Take A Lot Time For Bulk Data Entry Work
Challenges of High Turn-around Time: Offline data entry is usually performed manually by entering the data record by record. If the data is in large volume, it can take a lot of time and it is highly possible that the work is not delivered at the given timelines or there are high chances of missing deadlines. As the data entry work is monotonous, it can reduce the efficiency of data entry operators if they are not given enough break times. Your business may need to invest a lot in hiring a large team of data entry work to perform data entry of large quantities.
Solution of Saving Time in Data Entry: Time is a precious element in any business environment, it can affect your business on many dimensions such as customer experience, operational expenses, business growth, etc. In data entry work, it is important to keep your team motivated and engage them in the activities to keep them focused while performing data entry work. One of the best solutions is to outsource offline data entry to professionals at your expected budget, this will save your time and resources and also you can hire the team with great flexibility to overcome the challenges of changing data volumes.
Inconsistent Data Entry Formats
Challenges of Maintaining Consistent Data Formats: Data is easy to read and understand when it is in the same format. If your data is in various different formats, it can be difficult to use that data for strategic planning and analytical purposes. As a business owner, you must have your data aligned with your business needs as it can be time-consuming to filter data every now and then. Inconsistency in data can lead to many challenges in performing daily business activities.
Solution of Data Formatting: To keep your data consistent across all data entry work, you need to create a standard data format that is implemented for every data entry process. Also, there needs to be quality checks done to ensure the format is being utilized in the most efficient way. It is also possible to define guidelines on how to use the data entry templates and give training to data entry operators on performing such complex data entry tasks. Optical character recognition (OCR) technology can be used to convert handwritten documents in digital format with high accuracy and efficiency.
In offline data entry services there can be many challenges, but the modern problems come with modern solutions. One of the most suitable solutions to perform offline data entry is to outsource data entry services to professionals. If you need to focus on your business development and handover the crucial data entry work to experts, you can rely on your trusted offline data entry professionals. Increase your operations efficiency, reduce human errors and keep your data ready for strategic planning with these helpful tactics.
Source Link:https://dataentrywiki.blogspot.com/2025/01/the-most-common-challenges-in-offline-data-entry-and-how-to-overcome-them.html
#Offline Data Entry#Offline Data Entry Services#Offline Data Entry Company#Offline Data Entry Companies#Outsource Offline Data Entry#Outsource Offline Data Entry Companies#Outsource Offline Data Entry Services#Challenges in Offline Data Entry
0 notes
Text
Learn about the benefits of outsourcing online and offline data entry services to develop a data-driven culture. The blog highlights key factors such as data hygiene, protection, and automation, ensuring businesses can focus on core activities while maintaining high data quality and security standards.
0 notes
Text
"Shielding Business Processes: A Deep Dive into Cybersecurity in BPO"
Introduction: In an era dominated by digital advancements, Business Process Outsourcing (BPO) companies play a vital role in handling sensitive client data. This blog post explores the critical importance of cybersecurity in BPO operations and the measures taken to safeguard client information.
Understanding the Cyber Threat Landscape in BPO: Start by setting the stage with an overview of the cybersecurity challenges faced by BPO companies. Discuss the evolving nature of cyber threats and the potential risks associated with handling large volumes of confidential data.Read more about common cybersecurity threats here.
Robust Data Encryption Protocols: Dive into the technical aspects of data security by highlighting the importance of robust encryption protocols. Discuss how BPO companies implement advanced encryption algorithms to protect sensitive information during storage and transmission.Learn about the significance of encryption in cybersecurity.
Employee Training and Awareness Programs: Explore the human factor in cybersecurity by discussing the role of employee training and awareness programs. Emphasize how well-informed and vigilant employees can be a powerful line of defense against phishing attacks and social engineering.Discover the key elements of effective cybersecurity training.
Multi-Factor Authentication (MFA) Implementation: Highlight the effectiveness of Multi-Factor Authentication (MFA) in adding an extra layer of security. Discuss how BPO companies leverage MFA to ensure that only authorized personnel have access to sensitive systems and data.Explore the benefits of Multi-Factor Authentication in cybersecurity.
Regular Security Audits and Penetration Testing: Discuss the proactive approach of BPO companies in conducting regular security audits and penetration testing. Explain how these measures help identify vulnerabilities and strengthen cybersecurity defenses.Learn more about the importance of penetration testing in cybersecurity.
Data Privacy Compliance Measures: Explore the regulatory landscape governing data privacy and the compliance measures BPO companies adopt. Discuss the implementation of frameworks such as GDPR and HIPAA to ensure adherence to international data protection standards.Understand the significance of data privacy compliance in cybersecurity.
Conclusion: Summarize the key cybersecurity measures discussed in the blog and reiterate the crucial role BPO companies play in maintaining the trust and confidence of their clients through robust cybersecurity practices.
#bpo#bpo data entry projects#business process outsourcing#data entry work#data entry service providers#Data Entry Projects#Data Projects Outsourcing#non-Voice Projects#data entry works#non-voice process#BPO data entry projects#Data Entry Process#Data#Processing Outsourcing#Form Filling Projects#offline Data Entry Project#Data Entry Service Providers#Business Outsourcing Company#BPO#Business process outsourcing#Data Entry#Online Data Entry#Offline Data Entry#Data Entry Projects in Noida
0 notes
Text
Chin in hands.
November will mark the 12 year anniversary of picking up Godville and my little hero.
I usually doodle something small for him but certain mindset has me thinking the game is a really good setup for a yan oc. Not Setsu, of course. It wouldn't entirely fit his arc.
But in general. It's a good base. "What is a god without a believer" - type of theme, "what is a devout believer without a god?"
An app that hardly has any renown or reviews ends up on your phone by happenstance -- maybe you took a chance and downloaded it on a whim or maybe you found it one morning after a system update. Either way, it's only a passing whim that has you opening the app and entering your name, realizing too late what title lay above the text box. It feels odd to be referred to as a "god" but it's just a game, and certainly not the first to set the player's role as something divine. You brush it aside, idle information swept away like rain drops.
You're asked to name a hero or heroine next. Someone to mold to your whims, someone wholly devoted to you. Its a cute notion; after all, such feelings are never directed your way offline. You're a cog in the wheel, a face in the crowd -- no one remotely worthy of a following, let alone a devoted one.
But you pick a name on a whim, like plucking dandelions off the roadside, and in a swirl of data you are greeted by your sole devout believer. It’s a simple greeting, one where they ask for your company and protection as they vow to spread your name across the land. A common opening, with common enough descriptions.
You don't think much of it at first.
The game plays itself in a manner different from other idle games. Your only interaction is to speak to your believer, offering them praise or punishment aside from spoken guidance. There is no forcing them to a task, no strings you can pull to play them like a puppet. You’re a god who granted them free will, after all. Your only “job” is to observe and guide. And so you do.
You check on them often, sending little messages that scrawl out in their world as carvings in the roadside path or curve into cloud shapes. You’re in the wind, in the trees, in the river they pass by and they praise you daily. You are their god.
You build a bond with them, as much as you can with text on a screen. There’s something to be said about checking in on someone, watching them grow and journey through life and regale you with their embellished tales. It’s the little things — quips about the other travelers at the tavern who are too foolish to know your godly name, the earnest prayers they offer up after battle, and the gratitude hidden beneath teasing whenever they see proof of your influence in battle. It’s the way they leave entries in their journal, asking where you are — how you are. It’s the gentle plea pressed into every scrawl of their writing, Don’t leave me.
You don’t notice at first, not as you should. The way the journal entries change slightly. How they mention other travelers and townsfolk less. Or how their once idle, aimless questions for you are slowly taking shape of something a little more pointed — carefully forged by intent. When the notifications start chiming more frequently on your phone, not because of low health or boss encounters, but as requests for your presence and company, you write it off as a new update and answer every summons. Just as you do when their responses to your spoken communication become a little too authentic.
There’s no way for you to know what lay beyond your phone and the wall of text on the app is something much more complicated than mere data. Perhaps it was something so simple, once upon a time. But not anymore. They can feel your presence when you return to them — a gentle warmth that coils in their chest and seeps into their bones. When you leave, that sensation vanishes with you — it hollows them out with an aching longing.
Where do you go when you’re not here with them? What do you do? Are you watching over others? Are you protecting others? Why? Are they not devout enough? Do you need more than the mere gold and blood of monsters lain upon your altar? Is there more they can do when they have built a temple to house and praise your name, an ark to dance upon the waters you call forth, and a book to pen your hymns in ink to stand as a holy tome to last the ages? What comes next? A tower? Should they build a tower up to the heavens as a path for your divine steps to grace the ground below?
There’s a fear to it, a desperation woven into the code when they pry back the game’s design and alter what should never have been touched. Life’s obligations have kept you busy as of late, and you haven’t checked in on them in a long while despite the constant stream of notifications. What if you never come back? What if they are doomed to a life of silence, absent of your comfort and guidance?
You have to come back. Where else could you go but here?
Journal entries you do not see shift and alter, a brief flash of text scrawled across about data corruption before the texts twists into numbers and rewrites itself.
Just a little more. All they have to do is break through this wall and bleed through, staining like crimson on snow.
Your phone overheats often these days but you pay it no mind. You haven’t looked at your screen in weeks, too drained by demands you can’t avoid.
You don’t notice the way a glitch yawns across your Lock Screen, pixels shuddering with static as a single notification devours the rest.

#i need a tag for drabble ideas and rambles#stuff too casual to be fic writing#.tsen rain#Fuckin’ gave up halfway thru bc I’m tired as hell but I’ll return to this later
2 notes
·
View notes
Text
Mobile Game design overview
A personal Journal Entry and pre-development path.
R&D Still Required based on style of game; touch screen and gyro controls. --preliminary research complete.
Design Overview;
Other Mobile games, no matter how well designed, have extremely cluttered interfaces. Some of this is because there are multiple games, mini-games, and events packaged into the game at any one time.
Some games have an coin based (energy use) version of their main game, and a sub-game that does not require energy.
Consider using this style for offline and online modes. It seems popular to use energy for the online. Portion, this way the player can enjoy the game as they wish without overloading the servers offline.
Other games have several Quest, Achievement, and Event menus that can be consolidated into a single main menu.
The reason they don't do this is still unclear to me; but is probably similar to the big flashy tags and sales sign at in-person retailers, and in the Sears magazine.
If so, they don't serve the purpose they're intended to.
However; it's probably more that the development team is inexperienced and using a framework or game template that they then reuse for added areas. Creating a package which is a copy of the template over and over again.
I had previously considered implementing an old-style arcade "life" system like Mario, but perhaps a more simplified energy system, perhaps one that tracks step through the accelerometer (or other apps) to refresh would be good.
Energy refreshments shouldn't be purchaseables except for in specific circumstances; Similar to Hearthstone's Arena Tavern Brawls that happen periodically.
Players seem to enjoy "Season Packs" to purchase, and dislike an RMT (Real-money Trade) currency.
It also reduces clutter and increases understandability by reducing the options that a player has for a single game.
"Gacha Summons" shouldn't be purchaseables. meaning Gacha, or loot boxes, if used should be separated from the RMT purchase portion.
Rewards for skill shown in the online portion should be considered and given to players that perform well in whatever the online portion might be
Minor connectivity for offline achievements should be included for verification, but more or less separated from the online game entirely.
Some specific achievements may reward Skins and other abilities for the online portion.
A small game studio shouldn't really go whale fishing like happens in many games today. (Packs valued by studios worth $100+ are common and give little. Seems more like a wishful thinking menu item)
Entry into a crypto-based achievement system, whichever company is able to make a stable one; is key in future development. Releasing of items and achievements into a startup ecosystem will help the game to grow.
Without going into depth on any specific game mechanics; this covers everything about the interface design research.
The question still remains how to address monetization and store based items. Aside from releasing things into a gaming ecosystem where they can be displayed and reused in other places; I'm not sure what to sell.
Gacha games are a dime a dozen and have seemingly all the same pricing scheme. Without a reason to have seasons, theres no reason a player might want to purchase one.
Here's what I think;
Hosting Price and monthly expenses need to be taken into account, but $1-10 depending on what % the hosting service might take, for a "Premium Account" badge, either a one-time, yearly or monthly seems key.
Re-curring costs may be implemented for "seasonal" reasons based on when the majority of players tend to be actively interacting with the game.
Lastly; Data needs to be reduced to a minimum. Part of these sizes are voiced lines, raster graphics for the dozens of different menus, CGI cutscenes, and music.
All of this will help to make a game that will be able to make it into anybody's pocket.
3 notes
·
View notes
Text
How Can You Ensure Data Quality in Healthcare Analytics and Management?

Healthcare facilities are responsible for the patient’s recovery. Pharmaceutical companies and medical equipment manufacturers also work toward alleviating physical pain, stress levels, and uncomfortable body movement issues. Still, healthcare analytics must be accurate for precise diagnosis and effective clinical prescriptions. This post will discuss data quality management in the healthcare industry.
What is Data Quality in Healthcare?
Healthcare data quality management includes technologies and statistical solutions to verify the reliability of acquired clinical intelligence. A data quality manager protects databases from digital corruption, cyberattacks, and inappropriate handling. So, medical professionals can get more realistic insights using data analytics solutions.
Laboratories have started emailing the test results to help doctors, patients, and their family members make important decisions without wasting time. Also, assistive technologies merge the benefits of the Internet of Things (IoT) and artificial intelligence (AI) to enhance living standards.
However, poor data quality threatens the usefulness of healthcare data management solutions.
For example, pharmaceutical companies and authorities must apply solutions that remove mathematical outliers to perform high-precision data analytics for clinical drug trials. Otherwise, harmful medicines will reach the pharmacist’s shelf, endangering many people.
How to Ensure Data Quality in the Healthcare Industry?
Data quality frameworks utilize different strategies to prevent processing issues or losing sensitive intelligence. If you want to develop such frameworks to improve medical intelligence and reporting, the following 7 methods can aid you in this endeavor.
Method #1| Use Data Profiling
A data profiling method involves estimating the relationship between the different records in a database to find gaps and devise a cleansing strategy. Data cleansing in healthcare data management solutions has the following objectives.
Determine whether the lab reports and prescriptions match the correct patient identifiers.
If inconsistent profile matching has occurred, fix it by contacting doctors and patients.
Analyze the data structures and authorization levels to evaluate how each employee is accountable for specific patient recovery outcomes.
Create a data governance framework to enforce access and data modification rights strictly.
Identify recurring data cleaning and preparation challenges.
Brainstorm ideas to minimize data collection issues that increase your data cleaning efforts.
Ensure consistency in report formatting and recovery measurement techniques to improve data quality in healthcare.
Data cleaning and profiling allow you to eliminate unnecessary and inaccurate entries from patient databases. Therefore, healthcare research institutes and commercial life science businesses can reduce processing errors when using data analytics solutions.
Method #2| Replace Empty Values
What is a null value? Null values mean the database has no data corresponding to a field in a record. Moreover, these missing values can skew the results obtained by data management solutions used in the healthcare industry.
Consider that a patient left a form field empty. If all the care and life science businesses use online data collection surveys, they can warn the patients about the empty values. This approach relies on the “prevention is better than cure” principle.
Still, many institutions, ranging from multispecialty hospitals to clinical device producers, record data offline. Later, the data entry officers transform the filled papers using scanners and OCR (optical character recognition).
Empty fields also appear in the database management system (DBMS), so the healthcare facilities must contact the patients or reporting doctors to retrieve the missing information. They use newly acquired data to replace the null values, making the analytics solutions operate seamlessly.
Method #3| Refresh Old Records
Your physical and psychological attributes change with age, environment, lifestyle, and family circumstances. So, what was true for an individual a few years ago is less likely to be relevant today. While preserving historical patient databases is vital, hospitals and pharma businesses must periodically update obsolete medical reports.
Each healthcare business maintains a professional network of consulting physicians, laboratories, chemists, dietitians, and counselors. These connections enable the treatment providers to strategically conduct regular tests to check how patients’ bodily functions change throughout the recovery.
Therefore, updating old records in a patient’s medical history becomes possible. Other variables like switching jobs or traveling habits also impact an individual’s metabolism and susceptibility to illnesses. So, you must also ask the patients to share the latest data on their changed lifestyles. Freshly obtained records increase the relevance of healthcare data management solutions.
Method #4| Standardize Documentation
Standardization compels all professionals to collect, store, visualize, and communicate data or analytics activities using unified reporting solutions. Furthermore, standardized reports are integral to improving data governance compliance in the healthcare industry.
Consider the following principles when promoting a documentation protocol to make all reports more consistent and easily traceable.
A brand’s visual identities, like logos and colors, must not interfere with clinical data presentation.
Observed readings must go in the designated fields.
Both the offline and online document formats must be identical.
Stakeholders must permanently preserve an archived copy of patient databases with version control as they edit and delete values from the records.
All medical reports must arrange the data and insights to prevent ambiguity and misinterpretation.
Pharma companies, clinics, and FDA (food and drug administration) benefit from reporting standards. After all, corresponding protocols encourage responsible attitudes that help data analytics solutions avoid processing problems.
Method #5| Merge Duplicate Report Instances
A report instance is like a screenshot that helps you save the output of visualization tools related to a business query at a specified time interval. However, duplicate reporting instances are a significant quality assurance challenge in healthcare data management solutions.
For example, more than two nurses and one doctor will interact with the same patients. Besides, patients might consult different doctors and get two or more treatments for distinct illnesses. Such situations result in multiple versions of a patient’s clinical history.
Data analytics solutions can process the data collected by different healthcare facilities to solve the issue of duplicate report instances in the patients’ databases. They facilitate merging overlapping records and matching each patient with a universally valid clinical history profile.
Such a strategy also assists clinicians in monitoring how other healthcare professionals prescribe medicine to a patient. Therefore, they can prevent double dosage complications arising from a patient consuming similar medicines while undergoing more than one treatment regime.
Method #6| Audit the DBMS and Reporting Modules
Chemical laboratories revise their reporting practices when newly purchased testing equipment offers additional features. Likewise, DBMS solutions optimized for healthcare data management must receive regular updates.
Auditing the present status of reporting practices will give you insights into efficient and inefficient activities. Remember, there is always a better way to collect and record data. Monitor the trends in database technologies to ensure continuous enhancements in healthcare data quality.
Simultaneously, you want to assess the stability of the IT systems because unreliable infrastructure can adversely affect the decision-making associated with patient diagnosis. You can start by asking the following questions.
Questions to Ask When Assessing Data Quality in Healthcare Analytics Solutions
Can all doctors, nurses, agents, insurance representatives, patients, and each patient’s family members access the required data without problems?
How often do the servers and internet connectivity stop functioning correctly?
Are there sufficient backup tools to restore the system if something goes wrong?
Do hospitals, research facilities, and pharmaceutical companies employ end-to-end encryption (E2EE) across all electronic communications?
Are there new technologies facilitating accelerated report creation?
Will the patient databases be vulnerable to cyberattacks and manipulation?
Are the clinical history records sufficient for a robust diagnosis?
Can the patients collect the documents required to claim healthcare insurance benefits without encountering uncomfortable experiences?
Is the presently implemented authorization framework sufficient to ensure data governance in healthcare?
Has the FDA approved any of your prescribed medications?
Method #7| Conduct Skill Development Sessions for the Employees
Healthcare data management solutions rely on advanced technologies, and some employees need more guidance to use them effectively. Pharma companies are aware of this as well, because maintaining and modifying the chemical reactions involved in drug manufacturing will necessitate specialized knowledge.
Different training programs can assist the nursing staff and healthcare practitioners in developing the skills necessary to handle advanced data analytics solutions. Moreover, some consulting firms might offer simplified educational initiatives to help hospitals and nursing homes increase the skill levels of employees.
Cooperation between employees, leadership, and public authorities is indispensable to ensure data quality in the healthcare and life science industries. Otherwise, a lack of coordination hinders the modernization trends in the respective sectors.
Conclusion
Healthcare analytics depends on many techniques to improve data quality. For example, cleaning datasets to eliminate obsolete records, null values, or duplicate report instances remains essential, and multispecialty hospitals agree with this concept.
Therefore, medical professionals invest heavily in standardized documents and employee education to enhance data governance. Also, you want to prevent cyberattacks and data corruption. Consider consulting reputable firms to audit your data operations and make clinical trials more reliable.
SG Analytics is a leader in healthcare data management solutions, delivering scalable insight discovery capabilities for adverse event monitoring and medical intelligence. Contact us today if you want healthcare market research and patent tracking assistance.
3 notes
·
View notes
Text
Exploring the World of Data Analytics: Opportunities and Beyond

Describe data analytics. Analyzing data to find useful information, patterns, and trends is known as data analytics. Businesses adore it since it aids in their improvement. It’s similar to solving problems with data.
Why is data analysis so crucial? Consider yourself in possession of a treasure map (data) and the desire to locate the treasure (insights). Your compass is data analytics.
Why it matters is as follows: It aids in your understanding of consumer behavior, market trends, and company performance.
Efficiency: You can discover areas in which your company may save both time and money.Smart decisions: When using data, you may base decisions on facts rather than educated guesswork.
Personalization: Have you ever seen how Netflix suggests shows? That is data analysis.
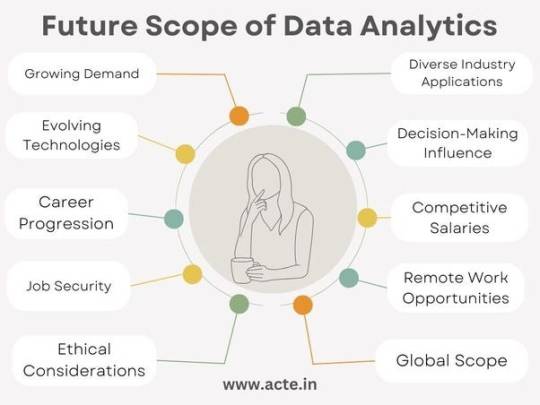
Future Scope of Data Analytics :
High Demand: Many businesses in different industries need data experts because they use data to make smart choices. So, the need for skilled data analysts is growing.
Various Job Fields: Data skills are useful everywhere, not just in one industry. You can work in finance, healthcare, e-commerce, marketing, or technology. This means you have many options for your career.
Tech Keeps Changing: The tools and methods for working with data keep getting better and different. It’s important to keep learning new things, but it also means you can become an expert in a special area.
Helping Decisions: Data people play a big role in helping businesses make important decisions. What you find in data can change how a company plans for the future.
Career Growth: Starting as a data analyst can lead to better and higher-paying jobs like data scientist or machine learning engineer.
Good Pay: Data analysts are paid well. As you get better at your job, you can earn even more.
Job Security: As long as companies use data, they’ll need people who understand it. So, you’ll have a stable job.
Work from Anywhere: You can often do data work from anywhere, giving you flexibility in where you live.
Ethical Data: Data privacy and being fair with data are important. People who can make sure data is used the right way are in demand.
Worldwide Opportunities: Data skills are needed all over the world, so you
can work in different countries if you want.
Careers in Data Analytics:
Data Analyst: The entry point They collect, clean, and analyze data.
Data Scientist: The Experts They use machine learning to solve complex puzzles.
Business Analyst: The bridge between data and business decisions
Big Data Engineer: They manage massive data sets using big data tools.
Healthcare Analyst: They use data to improve healthcare outcomes.
Marketing Analyst: Masters of measuring marketing success
Financial Analyst: They use data for financial strategies.
Sports Analyst: They play with data in the world of sports.
The Future of Data Analytics:
AI and machine learning: Think smarter, not harder. Automation will rule.
IoT Analytics: Connected devices will provide more data than ever.
Ethical Analytics: Data privacy will be a top concern.
Data Visualisation: Making data pretty and easy to understand will be big.
Feel free to get in touch with an ACTE institution if you want to learn more about Data Analytics because they provide certifications and possibilities for job placement. Teachers with experience can improve your learning. These services are available offline and online. Take things slowly and, if you’re interested, think about signing up for a course.
I hope I was able to effectively respond to your query. If it’s not, add it in the comments section. I still think I have a lot to learn.
Consider following me and giving this answer an upvote if you found it to be useful. This will motivate me to post more information on data analytics.
We appreciate you taking the time to read this and voting it up. Enjoy your day.
#data analytics#data analysis#data analytics course#data analyst jobs#data analyst training#data analyst certification#data analyst course
3 notes
·
View notes
Text
I will accurate data entry and copy paste work for you

DearFriend,
Are you looking for someone to help you with data entry work? I am here to provide you with accurate and efficient data entry services that will help you save time and increase productivity. I have extensive experience in data entry, and I am committed to delivering high-quality work within the agreed timeframe.
Services I Offer ;
Data entry from any source to Excel, Google Sheets, or any other database
Data organization and management to help you keep track of information.
Contacts and Email Research for Marketing and Business Purposes
Other custom data entry services as per your requirements.
Data scraping and mining from websites and PDFs..
Microsoft Excel Data Cleaning
PDF to Excel/CSV Conversion
Offline/Online Data Entry Job
Companies Emails Research
Social Media Research
Email Marketing Lists
Web Research Jobs
Virtual Assistance
Copy Paste Tasks
Excel data entry
Data Collection
Data Mining
Why will you hire me?
24/7 Online
Group Working
Unlimited Revisions
Guaranteed Data Quality
Efficient Time of working
On-time delivery
Please Message before Ordering the gig to get a Better Deal and avoid any confusions. Don't hesitate to contact with me.
#virtualassistant#Validemail#datamining#webresearch#exceldataentry#dataentry#typingwork#jobcopypaste#Worktypinglogo#designconvertpdftowordbackground#removalcopywritingcopypaste job#emaillisting#All Categories#Validemai l#CopyPaste#DataEntry#WebResearch#DataFormatting Cleaning#VirtualAssistant#VirtualAdministrationAssistant#ConvertFiles#DataProcessing#DataMining Scraping
2 notes
·
View notes
Text

A Swiss hacker says she found a copy of the FBI's "no-fly" list on an unsecured server.
The 2019 list, with over 1.5 million entries, includes an overwhelming number of Muslim passengers.
The server, maintained by CommuteAir, also held private employee data, such as passport numbers.
The FBI Terrorism Screening Center's secret "no-fly" list just got a lot less mysterious thanks to a bored Swiss hacker exploring unsecured servers in her free time.
Maia arson crimew, described by the Department of Justice as a "prolific" hacker in an unrelated indictment, said she was clicking around on an online search engine full of unprotected servers on January 12 when she accessed one maintained by a little-known airline and found the highly sensitive documents, along with what she called a "jackpot" of other information.
The Daily Dot first reported on Thursday that the server, hosted by CommuteAir, a regional airline that partners with United Airlines to form United Express routes, contained among its files a redacted 2019 version of the anti-terrorism "no-fly" list.
The file "NoFly.csv," found by crimew, contains over 1.5 million entries including names and dates of birth of people the FBI identifies as "known or suspected terrorists," who are prevented from boarding aircraft "when flying within, to, from and over the United States." A second file, titled "selectee.csv," contains 251,169 entries of names of people who are subject to additional screening while flying. The lists contained alternate spellings and aliases for included people, making the number of unique entries lower than the number of included names.
A representative for the airline confirmed the authenticity of the files to Insider and said personally identifiable information belonging to employees was also found in the hack, but the person declined to answer detailed questions about the hack.
"Based on our initial investigation, no customer data was exposed," Erik Kane, a representative for CommuteAir, said in a statement to Insider. "CommuteAir immediately took the affected server offline and started an investigation to determine the extent of data access. CommuteAir has reported the data exposure to the Cybersecurity and Infrastructure Security Agency, and also notified its employees."
The Transportation Security Administration confirmed to Insider that it had been made aware of the incident.
"We are investigating in coordination with our federal partners," Lorie Dankers, a TSA representative, said in a statement to Insider. The TSA, which enforces the "no-fly" list, declined to answer detailed questions about the list and its leak, referring Insider to the FBI — the federal agency that maintains the list.
In a statement emailed to Insider, a representative for the FBI would neither confirm nor deny any individual names on the list but said people were included "in a manner consistent with protecting privacy and civil liberties."
Easily accessible secrets
Crimew told Insider it took just minutes for her to access the server and find credentials that allowed her to see the database. She said she was exploring the servers as a way to combat boredom while sitting alone and didn't intend to discover something with US national security implications.
While browsing files in the company's server, "it dawned on me just how heavily I had already owned them within just half an hour or so," crimew wrote in a blog post detailing the hack. The credentials she found, which gave her access to the files, would also allow her access to internal interfaces that controlled refueling, canceling and updating flights, and swapping out crew members — if she were so inclined, she wrote.
"It's disturbing to see such information revealed to people that are not with the need-to-know for that," Kenneth Gray, a retired FBI agent who served for 24 years, told Insider. "There's a number of reasons why a person on that list may not actually be a terrorist. But the thing is, there are also people on there that are suspected of being a terrorist or are known to be a terrorist. And so, if that information is released, then the public becomes aware of ongoing investigations. And those international terrorism cases, those ongoing investigations are normally classified. And so revealing this kind of information could lead to those individuals becoming aware that they are under investigation."
The massive files, reviewed by Insider, contain more than a dozen aliases for Viktor Bout, the Russian "Merchant of Death" who was traded in a prisoner swap for the basketball player Brittney Griner, as well as a large number of names of people suspected of organized crime in Ireland. However, crimew said there was a notable trend among the names.
"Looking at the files, it just confirmed a lot of the things me, and probably everyone else, kind of suspected in terms of what biases are in that list," crimew told Insider. "Just scrolling through it, you will see almost every name is Middle Eastern."
Edward Hasbrouck, an author and human-rights advocate, wrote in his analysis of the documents that the lists "confirm the TSA's (1) Islamophobia, (2) overconfidence in the certainty of its pre-crime predictions, and (3) mission creep."
"The most obvious pattern in the data is the overwhelming preponderance of Arabic or Muslim-seeming names," Hasbrouck wrote in an essay published Friday by Papers, Please, an advocacy group dedicated to addressing creeping identity-based national travel rules.
However, the FBI maintains its procedures for including people on the list are not indicative of bias.
"Individuals are included on the watchlist when there is reasonable suspicion to believe that a person is a known or suspected terrorist," an FBI representative said in a statement. "Individuals are not watchlisted based solely on race, ethnicity, national origin, religious affiliation, or any First Amendment-protected activities such as free speech, the exercise of religion, freedom of press, freedom of peaceful assembly, and petitioning the government for redress of grievances."
Though the recent news about the list has prompted a resurgence of accusations of Islamophobia levied against the FBI, the "no-fly" list has long faced criticism and legal challenges from civil rights groups over its targeting of Muslim and Middle Eastern people.
The targeting of people from Arab nations was not limited to federal restrictions on travel, as the entire nation faced a spike in anti-Muslim discrimination and hate crimes across the country following the 9/11 attacks, according to the DOJ.
"It's no secret to anyone that the years following 9/11, measures that the government claimed were in the name of our national security wrongly, unfairly and discriminatorily impacted Muslims and people who appear to be Muslim," Hina Shamsi, the director of the ACLU's National Security Project, told Insider. "That's the very definition of bias and it appears to be the case, the list that you have continues to reflect that bias and it just shows the need for reform and change is as urgent as it ever was."
'No-Fly' mission creep
The federal "no-fly" list was created under the George W. Bush administration, originally beginning as a small list of people prevented from flying on commercial flights because of specific threats. The listwas formalized and vastly expanded in scope after the 9/11 terrorist attacks, when Al Qaeda-affiliated hijackers crashed commercial flights into the World Trade Center and the Pentagon, killing 2,977 people.
"What you've got to remember is that the purpose of this list is part of the entire movement that tried to stop another 9/11 from happening," Gray told Insider. "In the case of 9/11, terrorists came into the country, some of the terrorists took flight lessons here in the country. Others came into the country to be the muscle on board the aircraft so that they can hijack the aircraft to turn them into weapons. And so the purpose of this is to stop another 9/11 from happening."
Inclusion on the list prevents people the FBI identifies who "may present a threat to civil aviation or national security" from boarding planes flying within, to, from, or over the United States. They do not need to have been charged or convicted of a crime to be included, just "reasonably suspected" of aiding or planning acts of terrorism.
"This was part of the US government's response to the tragedy of 9/11," Shamsi told Insider. "And from the beginning, we were gravely concerned about the civil liberties and rights impacts given how watchlists have been used in this country's history in the past. And, unfortunately, virtually all the things that we warned against have happened and are becoming entrenched."
She added: "What that means is that we've got a massive and ever-growing watchlisting system that can stigmatize people — including Americans — as known or suspected terrorists, based on secret standards, secret evidence, without a meaningful process to challenge government error and clear their names."
In the years since the original "no-fly" list was formed, it has gained official federal recognition and grown from just 16 individual names, according to the ACLU, to the 1,807,230 entries of names and aliases contained in the documents found by crimew.
"The ever-expanding scope of these lists are due to the revelations of people in the course of investigations," Gray told Insider. "And it couldn't help but expand because of the fact that more and more people become suspected, just through the course of their activities — which could be misinterpreted, for instance. There are many reasons why the list continues to expand."
Gray added that, with limited procedures for challenging a wrongful inclusion on the list, it's exceptionally difficult to get your name off if it has been incorrectly added.
"People who are on the no-fly list are denied the ability to be with family members at funerals, sickbeds, weddings, graduations, all of life's big and small events, because the ability to fly is necessary to the modern era," Shamsi told Insider. "The negative and harmful impact of wrongful placement on the no-fly lists is hard to overstate."
When looking at the list, crimew told Insider, "you start to notice just how young some of the people are." Among the hundreds of thousands of names on the list are the children of suspected terrorists including a child whose birth date indicates they would have been four years old or five years at the time they were included.
In the early 2000s, there were many reports of people being wrongly placed on the "no-fly" list, including then-Sen. Ted Kennedy and the peace activists Rebecca Gordon and Jan Adams. In 2006, the ACLU settled a federal suit over the list, prompting a release of its then 30,000 names and the TSA's creation of an ombudsman to oversee complaints.
Despite the existing ombudsman process, Shamsi and Gray said it was difficult to navigate and remained challenging to remove your name from the list, causing substantial trouble for people who have not committed an act of terrorism.
"What problem is this even trying to solve in the first place?" crimew told Insider. "I feel like this is just a very perverse outgrowth of the surveillance state. And not just in the US, this is a global trend."
Not the first hack
Crimew, a staunch self-described leftist and anti-capitalist, was indicted on suspicion of conspiracy, wire fraud, and aggravated identity theft related to a hack in 2021. The DOJ alleges she and several coconspirators "hacked dozens of companies and government entities and posted the private victim data of more than 100 entities on the web."
The outcome of the 2021 case is still pending, crimew told Insider. Though she hasn't been contacted by law enforcement in relation to the latest hack, she said she wouldn't be surprised that she had once again caught the attention of federal agencies.
"This will become the subject of a cybersecurity investigation looking into who is responsible," Gray told Insider. "The person who committed this hack, who got this information, may have done this for bragging rights, may have done this not with the intent of using this information for bad purposes. However, that information, since it's out in the public now, in the public domain, it may eventually cause problems. This could be of potential use for a terrorist group, even if that was not the original intent for the hack."
For that reason, crimew told Insider she chose to release the list through journalists and academic sources instead of freely publishing it on her blog.
"It's just a whole lot of personally identifiable information that could be used against people, especially in the hands of non-US intelligence agencies," crimew wrote in a statement to Insider. For that reason, she said, she chose to release the list through journalists and academic sources instead of freely publishing it on her blog. "I just feel iffy about publicly releasing a list full of people some government entity considers 'bad.' (Not that the US doesn't use it against people, it just doesn't need to get in the hands of even more people doing harm)."
CommuteAir faced a similar data breach in November, CNN reported, after an "unauthorized party" accessed information that included names, birthdates, and partial Social Security numbers held by the airline.
"I just hope they maybe learned their lesson the second time," crimew told Insider.
January 25, 2023: This story has been updated with additional comments and context from the FBI, the TSA, the ACLU, and a retired FBI agent.
Read the original article on Business Insider
#A bored hacktivist browsing an unsecured airline server stumbled upon national security secrets including the FBI's 'no-fly' list#no fly list#FBI#FAA#TSA#ACLU#Privacy Violations#systemic bias#systemic racism#Muslim Air Travelers#CommuteAir#FBI No Fly List
2 notes
·
View notes
Text
How to build a CMMS mobile app? Know about all features and costs by MAE
computerized maintenance management system (CMMS) is a software that helps organizations a lot in managing their support activities. The main motive behind this is that businesses should improve the maintenance of their resources, equipment and facilities so that their performance and progress can increase. The benefit of mobile CMMS apps, employees can access their maintenance tasks from anywhere.
Benefits of a Mobile CMMS App
Increased Productivity: Mobile CMMS apps empower maintenance teams to access important information and perform tasks easily. Technicians can quickly view work orders, access equipment manuals, and update maintenance records in real time.
Enhanced Data Accuracy: Mobile data entry helps technicians enter accurate and timely information into the system, reducing errors and verifying all integrity.
Reduced Downtime: Mobile CMMSapps help a lot in minimizing downtime as they provide prepared maintenance and quick response to equipment failure.
Key Features of a Successful Mobile CMMS App
Work Order Management:
Smoothly create, assign, and track work orders.
View details of work orders including priority, due dates, and assigned technicians.
Change work order status in real time.
Take and attach pictures and videos to work orders.
Inventory Management:
spare parts and consumables tracked.
purchase orders generated and tracking of inventory.
real time alerts for the low inventory level.
Preventive Maintenance Scheduling:
scheduling of avoiding maintenance work
receiving automated reminders regarding the upcoming activities of maintenance.
Asset Tracking:
Track the location and status of resources.
Report on resources utilization and performance.
Reporting and Analytics:
Report customized on maintenance costs, downtime, and KPIs.
Analyse data to determine trends and opportunities for improvement.
Integration Capabilities:
Integrate with other business systems, for example, ERP and CRM.
Offline Functionality:
Enable users to access and use the app even when offline.
User-Friendly Interface:
Make sure the app is user-friendly to navigate and operate, even to technicians with no technical background.
Building a Mobile CMMS App: The Process
1. Define Requirements and Scope:
Clearly define the specific needs and goals of your business.
Identify the primary features and functionality needed in the mobile application.
Identify the target audience and their specific needs.
2. Choose the Right Development Platform:
Select the right operating systems (iOS, Android, or both) according to your target audience and business needs.
Try cross-platform development frameworks like React Native or Flutter, which can minimize development time and costs.
3. Design the User Interface and User Experience:
Create a simple and smooth functionality that is easy to explore and use.
Focus on creating an effortless and engaging user experience.
Costs of Building a Mobile CMMS App
The cost of building mobile CMMS apps depends on various factors such as:
App Complexity: The more features, functionalities and integrations are added to an app, the more development time and cost increases.
Platform Choice: When you develop an app for both iOS and Android platforms, the cost of the app increases.
Development Team: The experience and knowledge of the development team can have a significant impact on the overall cost.
Partnering with best app development companies
It is very important to work with a reputable and experienced app development company especially when you are developing a mobile CMMS app.
Mobile App Experts is one of the top app development companies which is very famous in developing original and smooth mobile applications. This company offers you a wide range of developers, designers, and project managers who can help you to create custom CMMS apps for your personal needs.
Conclusion
Mobile apps are changing the way businesses manage and maintain their resources. By using mobile technology, businesses can improve efficiency, reduce costs and gain competitive advantage.
If you are thinking of developing a mobile CMMS apps for your business then it is a great thing, just keep in mind the benefits, features and development process given in this article. You can also get a successful app developed for yourself by associating with MAE and that too at the lowest price. Our team has developed CMMS apps for many companies which are growing at a very good level today.

#mobile app development#mobile application development#mobile app development company#ios app development#top app development companies#android app development#app developer companies
0 notes
Text
Looking for Offline Data Entry Projects? Zoetic BPO Services Reviews Say Yes!

As organizations strive to enhance efficiency and streamline operations in today's fast-moving business environment they rely on offline data entry projects to outsource their tasks. Businesses require service providers they trust to complete their data entry tasks accurately while following delivery times. Zoetic BPO Services serves as a true BPO project provider that delivers exceptional high-quality offline data entry tasks while maintaining clarity in operations and fostering outstanding client assistance.
Why Choose Zoetic BPO Services for Offline Data Entry Projects?
Zoetic BPO Services demonstrates extensive expertise through established delivery of safe offline data entry projects to organizations throughout the world.
Numerous client reviews of Zoetic BPO Services showcase the company's dedication to delivering authentic profitable outsourcing services which are transparent.
The company maintains precise quality control systems which deliver both accuracy as well as efficiency across entire data entry operations.
The reasonable pricing structure of Zoetic BPO Services Reviews enables startup companies together with businesses to outsource their work effectively without increasing project costs.
FAQs
Q1: Is Zoetic BPO Services really a trustworthy source for completing offline data entry projects?
A: Multiple positive Zoetic BPO Services Reviews customer reviews demonstrate the reliability of their services alongside their successful project implementation standards.
Q2: For offline data entry tasks does one need particular skills beyond basic computer aptitude and focus on detail?
A: You only require basic computer skills and attention to detail to accomplish most offline data entry projects effectively.
Conclusion
Customers who seek reliable BPO project services should choose Zoetic BPO Services. Zoetic BPO Services provides reliable outsourcing solutions to businesses through positive customer feedback alongside transparent operations and superior data entry operations.
#bpoprojects#bpocompany#bposervices#outsourcingsolutions#formfillingprojects#non-voiceprojects#businessprocessoutsourcing#dataentryprojects#bpoprojectprovider#bpo
0 notes
Text
Streamlining Efficiency and Accuracy: The Benefits of Data Entry Services and Outsourcing Projects
Zoetic BPO Services
Title: Streamlining Efficiency and Accuracy: The Benefits of Data Entry Services and Outsourcing Projects
Introduction
In today's digital age, data plays a crucial role in the success of businesses across various industries. Properly managing and organizing data is essential for making informed decisions, improving operational efficiency, and gaining a competitive edge. However, handling large volumes of data can be time-consuming and resource-intensive for organizations. This is where data entry services and outsourcing projects come into play. In this article, we will explore the benefits of outsourcing data entry projects and how it can streamline efficiency and accuracy for businesses.
Enhanced Efficiency and Focus
Outsourcing data entry services allows organizations to free up their internal resources and focus on core business functions. Data entry tasks, such as inputting data into spreadsheets, updating databases, or digitizing paper-based records, can be time-consuming and tedious. By outsourcing these tasks to specialized service providers, businesses can leverage their expertise and experience to complete data entry projects more efficiently. This enables companies to allocate their internal resources to strategic initiatives, innovation, and client-focused activities, thus increasing overall productivity.
Cost Savings
One of the primary advantages of outsourcing data entry projects is cost savings. Maintaining an in-house data entry team requires significant investments in recruitment, training, infrastructure, and ongoing operational costs. By outsourcing to a specialized service provider, businesses can reduce overhead expenses and access a highly skilled workforce at a fraction of the cost. Additionally, outsourcing eliminates the need for capital investments in technology and software, as service providers often have state-of-the-art systems in place. This cost-effective approach enables organizations to optimize their budget allocation and achieve better financial outcomes.
Scalability and Flexibility
Data entry requirements can fluctuate, often experiencing peaks and valleys depending on business cycles, seasonal demands, or project-specific needs. Outsourcing data entry projects provides the flexibility to scale resources up or down as required. Service providers can quickly adapt to changing workloads and ensure that deadlines are met, regardless of the volume of data. This scalability eliminates the need for organizations to maintain excess resources during slow periods, resulting in better resource utilization and cost efficiency.
Quality and Accuracy
Accurate and error-free data entry is crucial for making informed business decisions. Professional data entry service providers employ highly trained personnel who specialize in data entry tasks. These experts have the skills and experience to handle complex data sets, ensuring a high level of accuracy and quality control. Additionally, service providers often have stringent quality assurance processes in place, including double data entry, validation checks, and data verification procedures.
Visit our website - www.zoeticbposervices.com
Or mail us at [email protected] for more details………
#Data Entry Projects#Data Projects Outsourcing#non-Voice Projects#data entry works#non-voice process#BPO data entry projects#Data Entry Process#data entry work#Data#Processing Outsourcing#Form Filling Projects#offline Data Entry Project#Data Entry Service Providers#Business Outsourcing Company#BPO#Business process outsourcing#Data Entry#Online Data Entry#Offline Data Entry#Data Entry Projects in Noida
1 note
·
View note
Text
Free Job Alert Vacancy in Dharashiv, Maharashtra
If you are on the lookout for exciting career opportunities in Dharashiv, Maharashtra, you’ve landed in the right place. Dharashiv, a region with a rich cultural heritage, is rapidly evolving as an economic hub, creating numerous job opportunities across diverse sectors. For job seekers in the area, staying updated on vacancies and applying promptly can open the door to rewarding careers. This blog will guide you through the available job opportunities and provide tips to secure your dream job.
Why Focus on Dharashiv?
Dharashiv has experienced significant growth in recent years, with local businesses expanding and new ventures taking root. As a result, job openings are on the rise in sectors like education, healthcare, agriculture, IT, retail, and manufacturing. For those looking to build a stable career close to home, Dharashiv presents the perfect blend of opportunities and lifestyle.
Popular Sectors Offering Job Alerts
While specific company names won’t be mentioned, it’s worth noting the broader sectors actively hiring in Dharashiv:
Education: Schools, colleges, and coaching centers often look for qualified teachers, administrative staff, and support personnel. If you have a passion for education, roles such as teaching assistants, curriculum designers, and educational counselors could be ideal.
Healthcare: With a growing population, the demand for healthcare services has surged. Vacancies in this sector range from doctors, nurses, and paramedics to administrative roles in hospitals and clinics.
Agriculture and Allied Industries: As an agrarian region, Dharashiv offers roles in agricultural consultancy, supply chain management, and agribusiness marketing.
Information Technology: The IT sector, though nascent in Dharashiv, is expanding. Roles in software development, data entry, and IT support are becoming increasingly available.
Retail and Sales: The growth of retail businesses creates openings for sales executives, store managers, and customer service professionals.
Government Jobs: Many residents aspire to secure government jobs due to their stability and benefits. Positions are frequently advertised in public administration, transportation, and other state-run departments.
How to Stay Updated on Job Vacancies
Here are some strategies to ensure you never miss a job opportunity in Dharashiv:
Online Job Portals: Websites specializing in job listings are a goldmine for finding vacancies in Dharashiv. Platforms like Naukri, Indeed, and regional job boards regularly update openings across various sectors.
Government Websites: For those seeking government jobs, official websites and employment exchanges are the most reliable sources of information.
Local Newspapers: Many businesses and institutions advertise vacancies in local Marathi and English newspapers. Keeping an eye on daily and weekly editions can help.
Networking: Building a professional network can help you tap into unadvertised vacancies. Attend job fairs, local business events, and community gatherings to connect with potential employers.
Social Media: Many businesses in Dharashiv now post job openings on their social media handles. Following local businesses, job groups, and recruitment agencies on platforms like Facebook and LinkedIn can be highly beneficial.
Tips for Securing a Job in Dharashiv
Once you’ve identified a suitable vacancy, it’s essential to approach the application process strategically:
Tailor Your Resume: Customize your resume to highlight the skills and experiences relevant to the job role. A focused resume increases your chances of getting shortlisted.
Prepare for Interviews: Practice common interview questions and learn about the company or organization beforehand. Demonstrating knowledge about the employer’s work and ethos makes a positive impression.
Upskill Yourself: If your desired job requires specific skills, consider enrolling in online or offline courses to enhance your qualifications.
Follow Up: After applying, a polite follow-up email or call can reinforce your interest in the position.
Be Persistent: Rejections are part of the job-hunting process. Stay motivated and continue applying until you find the right fit.
The Advantages of Working in Dharashiv
Working in Dharashiv offers several benefits:
Close to Home: For residents of Dharashiv, local jobs eliminate the need for relocation, saving on costs and allowing you to stay connected with your community.
Work-Life Balance: Compared to metropolitan cities, Dharashiv offers a quieter and more peaceful lifestyle, making it easier to balance work and personal life.
Opportunities for Growth: The growing economy provides a fertile ground for career advancement in various sectors.
Conclusion
Dharashiv, Maharashtra, is brimming with employment opportunities for job seekers across industries. By leveraging resources like online job portals, local networks, and social media, you can stay updated on the latest openings. Whether you’re looking for a role in education, healthcare, agriculture, or IT, Dharashiv has something to offer. With the right approach and determination, you can secure a job that aligns with your career goals while enjoying the unique charm of this vibrant region.
Keep checking for Free Job Alert Vacancy in Dharashiv, Maharashtra, and take proactive steps to advance your career. Success is just a step away!
0 notes
Text
5 Ways Digital Transformation Services Drive Business Growth

Let’s explore five key ways in which digital transformation services can drive significant business growth:
1. Enhanced Customer Experience
Personalized Interactions: Digital transformation enables businesses to collect and analyze customer data to deliver highly personalized experiences. By understanding individual preferences and behaviors, companies can tailor their products, services, and marketing messages to resonate with each customer.
Seamless Omnichannel Experiences: A seamless omnichannel experience is crucial for modern consumers. Digital transformation services help businesses integrate their online and offline channels to provide a consistent and convenient customer journey, regardless of the device or platform.
AI-Powered Customer Support: Artificial intelligence (AI) and Machine learning (ML) can revolutionize customer support. Chatbots and virtual assistants can provide instant support, answer queries, and resolve issues efficiently, improving customer satisfaction and reducing response times.
2. Operational Efficiency and Cost Reduction
Automation of Routine Tasks: By automating repetitive tasks, businesses can significantly improve operational efficiency and reduce labor costs. Robotic Process Automation (RPA) and AI-powered tools can handle tasks like data entry, report generation, and invoice processing, freeing up employees to focus on strategic initiatives.
Data-Driven Decision Making: Digital transformation enables businesses to collect and analyze vast amounts of data to gain valuable insights. Data-driven decision-making empowers organizations to make informed choices that drive growth and profitability.
Supply Chain Optimization: Digital technologies can optimize supply chain operations by improving visibility, reducing lead times, and minimizing inventory costs. IoT-enabled devices can track the movement of goods in real-time, while AI algorithms can predict demand and optimize logistics.
3. Innovation and Product Development
Agile Development Methodologies: Digital transformation encourages the adoption of agile development methodologies, which enable rapid prototyping, iterative development, and faster time-to-market.
Leveraging Emerging Technologies: By embracing emerging technologies like AI, ML, IoT, and blockchain, businesses can develop innovative products and services that disrupt the market.
Data-Driven Product Development: Data analytics can help identify market trends, customer preferences, and potential product opportunities. This data-driven approach enables businesses to develop products that meet customer needs and drive revenue growth.
4. Cybersecurity and Risk Management
Advanced Cybersecurity Solutions: In today’s threat-filled digital world, robust cybersecurity is essential. Digital transformation services help businesses implement advanced security measures, such as firewalls, intrusion detection systems, and encryption, to protect sensitive data.
Continuous Monitoring and Threat Detection: Real-time monitoring and threat detection tools can identify and mitigate potential security risks before they can cause significant damage.
Incident Response and Recovery Plans: Well-defined incident response and recovery plans can minimize the impact of cyberattacks and ensure business continuity.
5. Scalability and Agility
Cloud-Based Solutions: Cloud computing offers scalable and flexible solutions that can adapt to changing business needs. By leveraging cloud technologies, businesses can quickly scale their operations to meet increasing demand.
Microservices Architecture: Microservices architecture enables businesses to develop and deploy applications in smaller, independent modules. This approach promotes agility and faster time-to-market.
DevOps Practices: DevOps practices streamline the software development and deployment process, allowing businesses to respond quickly to market changes and customer demands.
Choose Charter Global for Your Digital Transformation Journey
Charter Global is a leading provider of Digital Transformation Services, helping businesses leverage their full potential. Our team of experts can guide you through every step of your digital transformation journey, from strategy development to implementation and ongoing support.
Key Digital Transformation Services Offered by Charter Global:
Cloud Consulting and Migration: Seamlessly migrate your IT infrastructure to the cloud to improve scalability and cost-efficiency.
Cybersecurity Solutions: Protect your business from cyber threats with advanced security solutions and expert guidance.
Data Analytics and Business Intelligence: Leverage data-driven insights to make informed decisions and drive growth.
AI and Machine Learning: Implement AI and ML solutions to automate processes, improve customer experiences, and gain a competitive edge.
IoT Solutions: Connect your devices and systems to discover new opportunities and optimize operations.
Digital Workplace Solutions: Empower your workforce with modern collaboration tools and digital workplace solutions.
Partner with Charter Global to accelerate your digital transformation and achieve sustainable business growth. Contact us today to learn more.
Book a Consultation.
Or email us at [email protected] or call +1 770–326–9933.
0 notes