#Government and Cybersecurity
Explore tagged Tumblr posts
Text
#Authorized Data Providers (ADP)#Critical Infrastructure Protection#CVE Backlog#Cyber Threat Intelligence#Cybersecurity#Cybersecurity and Infrastructure Security Agency (CISA)#Cybersecurity Industry Risks#Digital Threat Landscape#facts#Government and Cybersecurity#Known Exploited Vulnerabilities (KEVs)#life#National Vulnerability Database (NVD)#NIST Updates#Podcast#Ransomware#Rob Joyce#serious#straight forward#truth#Vulnerability Enrichment#Vulnerability Management#website
0 notes
Text
#lmao#lol#tiktok#national security#chinese spy#byteDance#espionage#data privacy#cybersecurity#congressional hearings#china-us relations#social media#misinformation#manipulation#intelligence agencies#hypothetical threat#chinese government#user data privacy#tiktok ownership#foreign influence#online surveillance#misinformation campaign
119 notes
·
View notes
Text
one of the many things that bothers me about goku luck is the fact that they have kenta (a minor) in a penitentiary full of adult convicts. where was the juvenile welfare officer and why are they not doing their job. hope they’re fired
#edit: realised i wrongly used the word penitentiary. sorry abt that. i meant prison#anyone who has heard what prison is like knows how terribly wrong this would go#also was he tried as a minor or did they try him as an adult for his crimes#idc if he’s got advanced hacking skills if a kid can create a virus that can threaten the world in his garage#then i’m sure million-dollar corporations and desperate governments can fund research into an antivirus#idk man it’s freaking ridiculous#like there was no reason to be doing all that#maybe i’m just a believer of restorative justice but#kenta’s clearly a genius. why not a scholarship to a great tech programme and a job with the government#he could do so much good in developing cybersecurity. internationally.#idk it just makes me sad that his whole life was over#and the system didn’t just fail him. it endangered him#either way goku luck could be such a great tool to criticise the criminal justice system#if anyone even CARES#you know i love The Silly but sometimes we need to Get Serious#paradox live#paralive#kenta mikoshiba#goku luck#gokuluck
27 notes
·
View notes
Text
sorry for the ping, but since most of us deal with zip files here, I thought this was important.
PSA: If you use 7-zip, please check which version you are using.
24.07 and earlier are no longer secure and have a serious vulnerability so be sure to update to 24.08 (released 11-Aug-2024) if you have not updated or downloaded it recently.
Note that 7-zip does not auto-update, and should never be downloaded from anywhere except for from the Developers own website: https://7-zip.org/
https://cybersecuritynews.com/7-zip-vulnerability-arbitrary-code/,

#7zip#zip files#software#security#alert#alerta#virus#breach#fyi#psa#safety#computer#android#apple#apps#application#app#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#cybersecurity#cyber security
3 notes
·
View notes
Text
Grievance on Water Supply Disruption in Lohandi Kalan
Grievance Status for registration number : GOVUP/E/2024/0088248Grievance Concerns ToName Of ComplainantYogi M. P. SinghDate of Receipt04/12/2024Received By Ministry/DepartmentUttar PradeshGrievance DescriptionThe matter concerns the disruption in supply of drinking water in the rural village Lohandi Kalan Development block- City, district Mirzapur and the location of the place is Bhujuwa ki…
#basic amenities#cybersecurity#drinking water#environment#Government#news#pipeline damaged#security#Uttar Pradesh Jal Nigam Garmin
3 notes
·
View notes
Text




when im blue i am not with you
there are people in this world who live such grandiose and surreally absurd lives, how do they evade the law as they do..?
#accelerationism#cyber#hacking#mind control#mkultra#conspiracy#anarchy#cypher#alternative media#government secrets#news#nature#ed not sheeren#cyberpunk#cybercore#cyborg#cybersecurity#weirdcore#weird art#weird dreams#weirdo#y2kcore#y2k aesthetic#y2k moodboard#y2k nostalgia#y2k#early 2000s#mcbling#cyber y2k
18 notes
·
View notes
Text
Apparently there was a massive social security data breach in the USA.
#girlbob.txt#its cool that our government assigned financial number can be stolen and used by other people#if the government doesn't put enough care into protecting it or if a business that demands it from us#decides to save on cybersecurity by downgrading it.
3 notes
·
View notes
Text
House Committee Postpones Markup Amid New Privacy Bill Updates
On June 27, 2024, the U.S. House of Representatives cancelled the House Energy and Commerce Committee markup of the American Privacy Rights Act (“APRA” or “Bill”) scheduled for that day, reportedly with little notice. There has been no indication of when the markup will be rescheduled; however, House Energy and Commerce Committee Chairwoman Cathy McMorris Rodgers issued a statement reiterating…
#American Privacy Rights Act#American Privacy Rights Act delayed#APRA#business#Cybersecurity#data#geolocation information#government#House Energy and Commerce Committee markup of the American Privacy Rights Act#legal#privacy
2 notes
·
View notes
Text
What is Google’s Project Nimbus and why is it controversial?
Google’s Project Nimbus is a cloud computing contract that Google and Amazon signed with the Israeli government in April 2021. With a hefty price tag of $1.2 billion, this collaboration between tech behemoths and the Israeli government was poised to revolutionize the way data is stored and processed. But not all is sunny with Project Nimbus; it’s a project that has become as controversial as it…

View On WordPress
#Amazon#Artificial intelligence#Cybersecurity#Data Privacy#Digital Transformation#Google#Government Contracts#Human Rights#Machine Learning#Project Nimbus#Tech Controversy#Tech Ethics
2 notes
·
View notes
Text
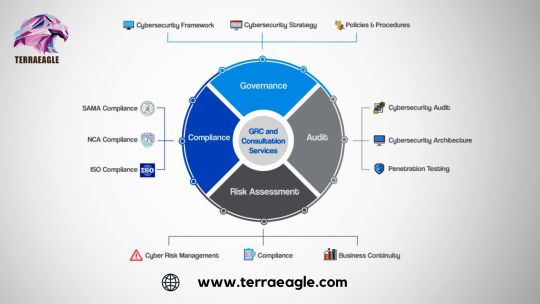
Contact us for the best GRC services in USA-Terraeagle
Discover the best GRC services in the USA with Terraeagle. Connect with us to get expert advice and unbeatable support. Contact us today!
2 notes
·
View notes
Text
Data Management & Governance in Digital Transformation: Insights from Dr. Imad Syed Live Podcast | PiLog Group
In the thought-provoking live podcast, “Data Management & Governance in Digital Transformation | Dr. Imad Syed Live Podcast”, Dr. Imad Syed dives deep into the critical role of data governance in shaping business success and shares actionable strategies for organizations to effectively manage their data ecosystems.
Watch the Full Podcast Here:
Why Data Governance is Critical in Digital Transformation
Ensures Data Accuracy & Integrity: Reliable data is the foundation of informed decision-making.
Enhances Compliance: Meet regulatory standards and avoid costly fines with proper governance frameworks.
Strengthens Data Security: Prevent breaches and unauthorized access through robust governance strategies.
Improves Data Usability: Organized data ensures stakeholders can extract valuable insights effortlessly.
Supports Scalability: Well-structured data systems grow seamlessly with your business.
Key Highlights from the Podcast:
Understanding Data Governance Frameworks: Learn the essential components of effective governance models.
Overcoming Data Management Challenges: Address common obstacles like data silos, duplication, and inconsistency.
Best Practices for Digital Transformation: Discover proven strategies for integrating data management in digital initiatives.
Building a Data-Driven Culture: Foster a mindset where every team member values data accuracy and security.
Future Trends in Data Governance: Stay ahead with insights into emerging technologies and methodologies.
Gain Expert Insights Now: Watch the Podcast Here
Who Should Watch This Podcast?
C-Level Executives: Understand how strategic data management drives business success.
IT Professionals: Learn how to implement secure and efficient data governance frameworks.
Data Analysts: Extract meaningful insights from well-governed data structures.
Business Leaders: Align digital strategies with strong data governance policies.
Students & Educators: Gain valuable knowledge about real-world data governance applications.
Best Practices for Effective Data Governance in Digital Transformation
Establish Clear Governance Policies: Define data access, usage, and security protocols.
Invest in Advanced Tools: Leverage modern data governance platforms for efficiency.
Train Your Teams: Build awareness about data privacy and compliance across all departments.
Adopt Data-Driven Decision Making: Empower teams with reliable, real-time insights.
Measure & Refine: Regularly evaluate governance strategies and make necessary adjustments.
How Effective Data Management Powers Digital Transformation
Faster Innovation Cycles: Data-driven insights accelerate product development and deployment.
Stronger Customer Relationships: Personalized data-driven experiences improve customer satisfaction.
Operational Efficiency: Streamlined data processes reduce waste and optimize resources.
Enhanced Decision-Making: Reliable data fosters confident, informed decisions.
Scalable Business Growth: Strong governance supports sustainable expansion across industries.
Why You Should Watch This Podcast?
In this engaging live session, Dr. Imad Syed shares profound insights into how data governance and management are reshaping industries in the digital age. Whether you’re navigating digital transformation, enhancing your data systems, or setting up governance policies, this podcast offers actionable knowledge you can implement immediately.

Don’t Miss Out — Watch Now: Data Management & Governance in Digital Transformation | Dr. Imad Syed Live Podcast
Let us know your thoughts in the comments below. How is your organization leveraging data governance in its digital transformation journey?
#data management#data governance#digital transformation#drimadsyed#piloggroup#data scientist#big data#data analytics#datadriven#dataengineering#data#business intelligence#cloud computing#cybersecurity#data security#eric kimberling#data management services#data management solutions#data governance services#data governance solutions#pilog group podcast#dr. imad syed podcast#youtube
1 note
·
View note
Text
Massive data breach, please check your email accounts and update your security details!
#data breach#privacy#email#google#telegram#invasion of privacy#cybersecurity#security#internet#pwned#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#alerta#alert#it#i.t.#infotech#information technology
7 notes
·
View notes
Text
youtube
#youtube#militarytraining#usmilitary#news#live news#alliances and partnerships#department of state#technology policy#state department#antony blinken#live#world news#US Secretary of State#Artificial Intelligence#AI#international cooperation#us news#abc news#UN Security Council#AI regulations#global governance#international relations#tech ethics#data ethics#machine learning#cybersecurity#AI regulation
1 note
·
View note
Text

come visit elriel if your sink is still flaming out of water
nothing something sense is wasted
#cyber#cypher#mkultra#hacking#alternative media#cyber y2k#weird art#government secrets#y2k#mind control#cybercore#cyber aesthetic#old tech#techcore#cyberpunk photomode#cyberpunk 2077#cybersecurity#y2k aesthetic#y2kcore#trashy y2k#y2k blog#y2k style#y2k fashion#2000s aesthetic#y2k moodboard#early 2000s#old web#sepia#photography#youth
4 notes
·
View notes
Text
#CISA#Critical Infrastructure Protection#Cyber Defense#Cyber Incident Response#Cyber Threats#Cybersecurity#Cybersecurity Framework#facts#Government Policy#life#National Cyber Incident Response Plan#National Cyber Strategy#Podcast#Public-Private Collaboration#Ransomware#serious#straight forward#truth#upfront#website
0 notes
Text
The U.S. Government's $500 Billion11 Fraud Problem: A Call for Vigilance
The United States is getting scammed out of hundreds of billions of dollars every year. That’s not a typo. Depending on how you measure it, the government may lose anywhere from $233 billion to $521 billion annually to fraud. To put that in perspective, the lower end of this estimate is more than the GDP of Greece. The upper end? That’s approaching the entire annual revenue of Amazon. Let that…
#cybersecurity threats#financial fraud#fraud in government#fraud prevention strategies#government accountability#taxpayer money loss#vigilance against fraud
0 notes