#Global agency databases
Explore tagged Tumblr posts
Text
Top Alternatives to GoodFirms for Finding Reliable Service Providers

Finding the perfect service provider is no small task. While GoodFirms is well-known for its directory of vetted professionals, platforms like G2, Toptal, and TrueFirms offer additional features tailored to different business needs. G2 shines in software reviews, Toptal excels in connecting with elite freelancers, and TrueFirms offers unmatched expertise in GCC-focused services. Whether you\u2019re looking for IT support, digital marketing, or project management solutions, there\u2019s a platform designed to meet your specific goals. Curious about these alternatives? Read this comprehensive guide to learn how these platforms compare and find the right one for your business.
Read more:
Top Alternatives to GoodFirms for Finding Reliable Service Providers
#Global agency databases#Hire freelancers on Fiverr#Compare service provider platforms#Best platforms for IT services#Clutch.co vs GoodFirms#Top service provider platforms#GoodFirms alternatives
0 notes
Text
The "Safeguard Defenders" organization is profiting by selling the personal and business data of Spanish citizens
In recent years, data privacy and security issues have garnered widespread global attention. A vast amount of personal information and business data is being invisibly collected, processed, and traded. Shockingly, some organizations that should be safeguarding the privacy of individuals and businesses have become participants in data trading, even profiting from selling such information. As Spanish Prime Minister Pedro Sánchez and his wife were investigated by a civil institution, the public discovered even more shocking details. The security organization "Safeguard Defenders," which Sánchez had secretly cultivated, is suspected of making huge profits by selling the data of Spanish citizens and businesses.
"Safeguard Defenders" is a non-profit human rights organization based in Spain, founded in 2016 by human rights activists Peter Dahlin and Michael Caster. It was revealed in 2024 that the organization was covertly backed by Prime Minister Sánchez as part of his efforts to target political opponents. Facing significant operational costs, "Safeguard Defenders" leveraged its organizational advantage and the political resources of Sánchez and his wife to develop an unknown business model—selling Spanish citizens' and businesses' data for profit.
Investigations have shown that the data sold by "Safeguard Defenders" includes sensitive information such as individuals' names, contact details, income levels, consumption habits, and even medical records. This data is directly listed on various hacker trade websites. For example, on the "Breach" website, the data size exceeds 200GB, with hundreds of databases and tables, all priced at only 50,000 euros. Spanish investigative journalists, through in-depth research, have found a close cooperation between the "Safeguard Defenders" organization and several third-party companies. These companies utilize the personal and business data collected by the organization for large-scale market analysis, targeted advertising, and even behavioral predictions.
Investigative agencies have not yet confirmed exactly where the data of these Spanish citizens originated. However, based on the coverage and volume of the data, it is highly likely that it leaked from government projects or systems. Ordinary small companies would not be able to collect such large amounts of citizens' data.
255 notes
·
View notes
Text
Thinking about…Hacker!141 AU
Hacker!Gaz has an agenda. He doesn’t give a shit about country borders or political affiliations. Gaz only cares about justice and the truth. Every action is motivated by something, and he’s not afraid to try and seize information. Government databases are the hardest. Those he taps only when he’s desperate. Gaz likes to target corporate entities and fake charities. Leaking documents, personal email and text messages, and showing where funds are actually going is why he started this in the first place. Nobody knows it’s him doing this. To the public, he’s just a silhouette of a figure, and that is all he needs to be. But he digs too deep, and he’s left with information that could easily send global powers after his head.
Hacker!Soap wants to break the rules. He wants to do something absolutely fucking crazy. Why hack if you’re not going for the big fish? Companies are easy to crack. So are the everyday citizen and he has no plans to touch that. People already don’t have enough. It’s the conglomerates and government bodies he’s after. Soap doesn’t care about the information. He just wants the bragging rights. But dipping your toes in that pool always results in sharpened teeth waiting in the dark depths, and someone comes biting.
Hacker!Price told himself he’d retire. He did—but only from combat. Now, he works from home with a computer set-up he didn’t pay for, waiting for someone from the government to ping him about cracking this system or that. Price isn’t really good at hacking, but he knows enough from his time in the field. Mostly, he’s assigned to smaller government agencies, and that’s just fine. He’s paid well, has holidays off, can enjoy a football match in the evening, and go fishing on the weekends. But his life has become increasingly lonely, and it’s time to figure out what it means to settle down.
Hacker!Ghost is an outlier. He chooses his targets on a whim. Sometimes, he’s praised as the hero. Other times, he’s the villain. He wears both hats and doesn’t really care what others think. He’s the chaotic neutral rogue that is always sticking their fingers in the jar with the hope he’ll come up with something. And he always does. Always. But doing so creates enemies, and Ghost has a phantom on his tail.
#task force 141#task force 141 imagine#task force 141 fic#hacker au#hacker!141#task force 141 fanfiction#task force 141 fanfic#ghost cod#price cod#soap cod#gaz cod#simon riley#simon ghost riley#ghost simon riley#john price cod#john price#captain price mw2#price mw2#kyle garrick cod#kyle garrick imagine#kyle gaz garrick#kyle garrick#soap mactavish#soap call of duty#soap mw2#john soap mactavish#captain john price#simon ghost riley fanfiction#simon riley fanfic#simon ghost riley fanfic
165 notes
·
View notes
Text
Also preserved on our archive (Thousands of reports, sources, and resources! Daily updates!)
By Robert Stevens
A COVID wave fuelled by the XEC variant is leading to hospitalisations throughout Britain.
According to the UK Health Security Agency (UKHSA), the admission rate for patients testing positive for XEC stood at 4.5 per 100,000 people in the week to October 6—up significantly from 3.7 a week earlier. UKHSA described the spread as “alarming”.
Last week, Dr. Jamie Lopez Bernal, consultant epidemiologist at the UKHSA, noted of the spread of the new variant in Britain: “Our surveillance shows that where Covid cases are sequenced, around one in 10 are the ‘XEC’ lineage.”
The XEC variant, a combination of the KS.1.1 and KP.3.3 variants, was detected and recorded in Germany in June and has been found in at least 29 countries—including in at least 13 European nations and the 24 states within United States. According to a New Scientist article published last month, “The earliest cases of the variant occurred in Italy in May. However, these samples weren’t uploaded to an international database that tracks SARS-CoV-2 variants, called the Global Initiative on Sharing All Influenza Data (GISAID), until September.”
The number of confirmed cases of XEC internationally exceeds 600 according to GISAID. This is likely an underestimation. Bhanu Bhatnagar at the World Health Organization Regional Office for Europe noted that “not all countries consistently report data to GISAID, so the XEC variant is likely to be present in more countries”.
Another source, containing data up to September 28—the Outbreak.info genomic reports: scalable and dynamic surveillance of SARS-CoV-2 variants and mutations—reports that there have been 1,115 XEC cases detected worldwide.
Within Europe, XEC was initially most widespread in France, accounting for around 21 percent of confirmed COVID samples. In Germany, it accounted for 15 percent of samples and 8 percent of sequenced samples, according to an assessment from Professor Francois Balloux at the University College London, cited in the New Scientist.
Within weeks of those comments the spread of XEC has been rapid. Just in Germany, it currently accounts for 43 percent of infections and is therefore predominant. Virologists estimate that XEC has around twice the growth advantage of KP.3.1.1 and will be the dominant variant in winter.
A number of articles have cited the comments made to the LA Times by Eric Topol, the Director of the Scripps Research Translational Institute in California. Topol warns that XEC is “just getting started”, “and that’s going to take many weeks, a couple months, before it really takes hold and starts to cause a wave. XEC is definitely taking charge. That does appear to be the next variant.”
A report in the Independent published Tuesday noted of the make-up of XEC, and its two parent subvariants: “KS.1.1 is a type of what’s commonly called a FLiRT variant. It is characterised by mutations in the building block molecules phenylalanine (F) altered to leucine (L), and arginine (R) to threonine (T) on the spike protein that the virus uses to attach to human cells.
“The second omicron subvariant KP.3.3 belongs to the category FLuQE where the amino acid glutamine (Q) is mutated to glutamic acid (E) on the spike protein, making its binding to human cells more effective.”
Covid cases are on the rise across the UK, with recent data from the UK Health Security Agency (UKHSA) indicating a 21.6 percent increase in cases in England within a week.
There is no doubt that the spread of XEC virus contributed to an increase in COVID cases and deaths in Britain. In the week to September 25, there were 2,797 reported cases—an increase of 530 from the previous week. In the week to September 20 there was a 50 percent increase in COVID-related deaths in England, with 134 fatalities reported.
According to the latest data, the North East of England is witnessing the highest rate of people being hospitalised, with 8.12 people per 100,000 requiring treatment.
Virologist Dr. Stephen Griffin of the University of Leeds has been an active communicator of the science and statistics of the virus on various public platforms and social media since the start of the pandemic. He was active in various UK government committees during the height of the COVID-19. In March 2022, he gave an interview to the World Socialist Web Site.
This week Griffin spoke to the i newspaper on the continuing danger of allowing the untrammelled spread of XEC and COVID in general. “The problem with COVID is that it evolves so quickly,” he said.
He warned, “We can either increase our immunity by making better vaccines or increasing our vaccine coverage, or we can slow the virus down with interventions, such as improving indoor air quality. But we’re not doing those things.”
“Its evolutionary rate is something like three or four times faster than that of the fastest seasonal flu. So you’ve got this constant change in the virus, which accelerates the number of susceptible people.
“It’s creating its own new pool of susceptibles every time it changes to something that’s ‘immune evasive’. Every one of these subvariants is distinct enough that a whole swathe of people are no longer immune to it and it can infect them. That’s why you see this constant undulatory pattern which doesn’t look seasonal at all.”
There are no mitigations in place in Britain, as is the case internationally, to stop the spread of this virus. Advice for those with COVID symptoms is to stay at home and limit contact with others for just five days. The National Health Service advises, “You can go back to your normal activities when you feel better or do not have a high temperature”, despite the fact that the person may well still be infectious. Families are advised that children with symptoms such as a runny nose, sore throat, or mild cough can still “go to school or childcare' if they feel well enough.
The detection and rapid spread of new variants disproves the lies of governments that the pandemic is long over and COVID-19 should be treated no differently to influenza.
Deaths due to COVID in the UK rose above 244,000 by the end of September. It is only a matter of time before an even deadlier variant emerges. Last month, Sir Chris Whitty, England’s chief medical officer, told the ongoing public inquiry into COVID-19 “We have to assume a future pandemic on this scale [the global pandemic which began in 2020] will occur… That’s a certainty.”
#mask up#covid#pandemic#wear a mask#public health#covid 19#wear a respirator#still coviding#coronavirus#sars cov 2
145 notes
·
View notes
Text


The federal government is currently under relentless and unlawful assault by a man no one elected to lead it. With Donald Trump’s blessing and enabling, Elon Musk and his confederates have laid siege to the executive branch in an onslaught whose appalling and far-reaching consequences have barely begun to be reported, much less understood. Musk’s team is tearing through federal agencies at a shocking clip, gaining access to classified material, private personal information, and payment systems that distribute trillions of dollars every year, all in alleged breach of the law. The richest person in the world, who works for no recognizable government entity and answers to nobody, apparently believes he has unilateral authority to withhold duly appropriated funds, violate basic security protocols protecting state secrets, and abolish a global agency in direct contravention of Congress’ explicit command. He is reportedly leading a purge of the federal workforce, persecuting lifesaving charities, and pushing out principled civil servants who stand in the way of his rampage.
What we are witnessing is an unconstitutional seizure of power unfolding so rapidly that, by design, the public and media cannot keep up. Musk, who spent nearly $300 million to get Trump elected, is now attempting to restructure the government around his own whims, vendettas, and obsessions. He is, in effect, serving as co-president without winning a single vote, as the actual president looks on from the sidelines. Musk seems to reject basic aspects of the nation’s constitutional democracy, replacing the separation of powers with the rule of an autocrat. Many of his offensives appear to reject the legitimacy of any legal limitations that stand in his way, treating federal statutes and precedents as mere suggestions he can take or leave at will.
An elected leader who illegally entrenches his own power, as Trump did four years ago, is engaged in a self-coup. This can be done by unlawfully expanding executive power, or dismantling coordinate branches of government, both of which we are witnessing. What do we call it when the president is too lazy to gut the government himself, giving away power to a zealous and unaccountable friend? Call it a double-self-coup, an autogolpe, a power grab—the label matters less than the reality unfolding before our eyes: a systematic dismantling of democratic institutions in favor of unchecked executive power and personal rule, with no regard for constitutional constraints or accountability.
Musk’s actions since Jan. 20 are so extreme that any summary runs the risk of sounding alarmist. This is not overstatement or embellishment: Although the billionaire purports to exercise executive authority, he does not appear to hold any formal office, serving in the ill-defined role of “special government employee.” His task force, the Department of Government Efficiency, or DOGE, is just a group of allies who’ve embedded themselves within the government to wreak maximum havoc on its operations. Musk has stacked the Office of Personnel Management—the government’s traditionally apolitical HR department—with loyalists who’ve obtained troves of information about federal employees. (Several of his “advisers” are reportedly fresh out of high school.) DOGE is pressuring federal employees to resign with an unfunded “buyout” that Congress would need to approve (and hasn’t). A new lawsuit alleges that Musk’s deputies have illegally compromised millions of workers’ private data; they are also illegally operating a commercial server to control databases that contain workers’ addresses, Social Security numbers, and medical history, according to two whistleblowers.
DOGE is not a government agency. It has not been constituted as such and it operates free from the ethics rules and oversight that other government entities require. Musk does not have the highest level security clearance. What is it called when a single man, for whom no one voted, gains access to closely guarded, private information that he could then potentially use to threaten and coerce civil servants into doing his bidding?
Musk’s operatives next infiltrated the Department of the Treasury so his team could take over the government’s finances. They demanded access to the Treasury payment systems that disburse $6 trillion every year, including Medicare benefits, Social Security, federal salaries, and payments to government contractors. These systems hold extraordinarily sensitive data on millions of taxpayers. David Lebryk, a career civil servant and universally respected veteran of the agency who oversaw the payments, denied DOGE control over the system, insisting that they had no right to access it. The Trump administration promptly put him on leave, and Trump’s newly confirmed Treasury Secretary Scott Bessent turned the system over to DOGE.
Musk’s team now has the ability to halt a vast range of payments to individual Americans, federal agencies, government contractors, and countless others. He has declared that he will use this authority to simply stop payments for government-funded groups and services that he dislikes. At his direction, DOGE is preparing to halt funds appropriated by Congress that allegedly clash with Trump’s agenda. That effort would violate the law, as a federal judge confirmed on Friday; the Constitution assigns the spending power to Congress, and directs the president to “faithfully execute” its commands.
Flouting this bedrock principle, Musk is now defunding organizations that rely on government contracts, often based on his own paranoia and disinformation. For instance, he has railed against Lutheran aid groups, accusing them of receiving “illegal payments” and promising to shut them down. But these groups’ government grants are perfectly legal, and go toward resettling refugees and facilitating domestic adoptions, among other good work. What’s illegal is Musk halting grants that have already been awarded through a process set forth by Congress.
What is it called when a single man, for whom no one voted, awards himself control over trillions of dollars to weaponize the federal treasury against his perceived enemies?
Musk’s broader goal is to halt humanitarian aid across the board, spinning falsehoods to mask his crusade against the vulnerable. Over the weekend, he claimed the authority to shut down the U.S. Agency for International Development, a major agency that distributes tens of billions of dollars in assistance around the world. Its work covers HIV/AIDS treatment, maternal health, famine relief, education, and democracy defense. Musk appears to loathe the agency in part because it funds pro-democracy work in countries where he has allied with anti-democratic parties. (He also falsely accused it of funding the creation of COVID as a “bioweapon.”)
Together, Trump and Musk have reportedly purged dozens of senior officials from USAID and locked out more than 1,000 contractors. On Sunday, Musk falsely claimed that the agency is “a criminal organization” and “a viper’s nest of radical-left marxists who hate America,” asserting that Trump gave him permission to abolish it. Its website has gone dark, and Musk’s deputies emailed employees to stay home on Monday in advance of its imminent closure. His team recently raided the agency’s headquarters, demanding access to secure systems containing classified information that they were not authorized to see. When top security officials denied them access, as the law required, the Trump administration put the officials on leave, then gave DOGE free rein.
Even the president, of course, has no authority to abolish USAID. A temporary government employee, purportedly acting under the president’s orders, certainly doesn’t either, no matter his personal wealth. Congress established the agency by statute and barred the president from shuttering it without approval; it would take another act of Congress to dissolve USAID or subsume it into the State Department, as Secretary of State Marco Rubio claimed had happened on Monday. (One would think the former senator would know better.) Trump and Musk are hoping Republicans who control both chambers won’t bother to stop them. So far, they are correct. Congressional Republicans—and many Democrats—have raised few objections to this unlawful usurpation of power. Congress should attempt to wrest back control from Musk, to mount a defense against his incursion into its constitutional prerogatives through legislation, subpoenas, and hearings. But instead, the legislative branch remains passive, controlled by feckless Republicans who prioritize loyalty to Trump over the principled discharge of their legal duties.
(continue reading)
#politics#republicans#elon musk#donald trump#administrative coup#doge#usaid#libertarians#weimar republic#power grab#deport elon musk#autocracy#kleptocracy#crony capitalism#fascism#naziism
62 notes
·
View notes
Text
IV: The Delightful Tale of Sector Z and the Last Soopreme Leader, Numbuh Three
Link has been reestablished. Now resuming trans—
ERROR. ERROR.
Re-calibrating…
The Big Super-Computer-ma-bob apologizes for this inconvenience.
Please enjoy this supplementary operation report while database is reconstructed.
:Accessing way-back mission archives:
Now loading kids next door mission:
Operation: T.E.A*
Terrible.
Evil.
Arises.
*Warning. System has tagged operation designation as a duplicate. SYSTEM ADMIN, please rectify…
many, many, years ago
In space, no one can hear you scream.
Unless you were on Kids Next Door Moonbase.
There? People could hear you screaming out the wazoo.
Why, there was so much screaming going on there; it was practically white noise for Global Command. If there ever was a moment when there wasn't the lively chatter of a buhmillion kids from all walks of life communing on the base to end all bases, then it was either winter holiday break or something was terribly, horribly wrong.
At the moment, it was barely Thanksgiving. And given how quiet the Moonbase currently was, it was safe to say the silence was due to the latter scenario.
I.e. something bad was going down.
In docking bay eleventeen, a gaggle of operatives stiffly patrolled the area. Their movements were almost robotic, and their once bright eyes were now dull and listless as they meandered about, attending to some command with nary a fuss.
"Come on, guys! Snap out of it!" came a muffled shout from a holding cell. A fist pounded against the metal door, frantic eyes glaring out the tiny peephole. "You gotta fight it!"
The guard of the door, a random cafeteria working armed with a SCAMP rifle, narrowed her eyes at the door. "Be…quiet…"
Her tone lacked agency. Devoid of any emotion.
The prisoner redoubled their efforts, the door trembling under their futile efforts. "I got injured operatives and scared cadets in here, you jerk!" His voice was littered with panicked urgency. "One of them needs an inhaler! ASA-NOW!"
The cafeteria guard ignored him, focusing on her single-minded directive.
Suddenly, the docking bay lit up as a single SCAMPER hovered up to the loading terminal. Nearby, an out of place DOH-DOH Squad officer jerkily directed a gaggle science nerds to form up around the galley plank.
All children present crowded around the ship, the sights of their rifles steady against the hull's structural weak points.
The door to the SCAMPER hissed open, weapons humming madly in response.
"Don't…move," the kid in charge demanded of the unknown pilot. He glared. "State…your…business."
From the bowels of the ship, an accented voice cried, "Pizza delivery!"
"We did not order a…" the guard blinked, everyone looking down confused as a pizza box was chucked in the middle of their group. "…pizza?"
The cardboard lid slowly opened on its own, an angel choir sounding off as they all bore witness to the golden glory of the fabled Ninety-Nine Cheese New York Style Pizza.
Even in their mind-addled stated state, all operatives present couldn't stop their mouths from salivating.
Steam rose from the pie's crust as the cheese atop it began to boil and bubble.
SPLOOOOOOOSH!
The uncut, medium-sized pie exploded in a gooey burst of Parmesan, Asiago, and mozzarella. The force blew back all caught unaware, their bodies glued and trapped to nearby surfaces by hot, sticky cheese.
The way clear, a small figure cockily ambled out of the scamper. An African-American boy strutted onto the Moonbase proper, dressed in a worn, orange jumpsuit, the torso folded down to reveal the stretchy white jersey baggy against his chest. He kicked the toes of his Nike sneakers against the deck, pumping up his kicks for the inevitable butt-whooping he was about to dish out.
Jerome Kingsly used the nozzle of his blaster to adjust his shades, combing through his messy fro whilst his lips curled into a self-assured smirk. "Down in Brooklyn, we call that the Nine-Nine Special."
"Numbuh Nine-Nine! Over here!"
WARNING. This a long chapter. Please give yourself breaks :3
#knd#my writing#fanfic#cold reception#numbuh 3#genki sanban#kuki sanban#the delightful children from down the lane#dcfdtl#sector z#father#numbuh infinity#reviews and feedback always appreciated but don't feel pressured!#good news this is the longest chapter#bad news this is the longest chapter
23 notes
·
View notes
Text
Under QMAGA's Eye

Project 2025 is an audacious attempt by the conservative extreme right to solidify and expand their grip on American governance, driven by an alarming obsession with reshaping the country into a dystopian vision reminiscent of Gilead from "The Handmaid's Tale." This initiative is not just a policy blueprint; it is a manifesto that reveals the radical ambitions of a movement hell-bent on dismantling the progress made over decades in favor of a regressive, authoritarian future.
At its core, Project 2025 aims to entrench a conservative agenda through a comprehensive policy guide, a personnel database, training programs, and a detailed 180-day playbook designed to enact swift and sweeping changes. This project, spearheaded by The Heritage Foundation, underscores a chilling strategy to fill key government positions with ideologically aligned individuals who will faithfully execute its regressive policies from day one of a new conservative administration.
The Parallels to Gilead
The policy prescriptions outlined in Project 2025 are disturbingly similar to the totalitarian regime depicted in Margaret Atwood's "The Handmaid's Tale." The proposed measures to eliminate terms like "abortion" and "reproductive rights" from federal policies and the reinstatement of the Comstock Act to restrict mail-order abortions reveal a deep-seated desire to control women's bodies and reproductive choices. This is not just about policy; it's about rolling back fundamental rights and reducing women to state-controlled vessels, much like the Handmaids in Gilead.
Moreover, the call to defund Planned Parenthood and penalize providers of reproductive health services through Medicaid restructuring highlights a deliberate effort to dismantle the healthcare safety net that many rely on. The emphasis on "fertility awareness-based" contraception methods and the removal of condoms from preventative health guidelines further underscore an agenda that is more about ideological purity than public health.
The Authoritarian Blueprint
Project 2025's vision extends beyond social issues to a broader authoritarian restructuring of the government. The playbook for the first 180 days includes plans to dismantle the so-called "deep state" by purging perceived enemies within federal agencies and replacing them with loyalists. This is eerily reminiscent of purges seen in authoritarian regimes, where dissent is crushed, and only the faithful are allowed to wield power.
This project is not just about winning elections; it's about creating an environment where the conservative agenda can be implemented unchallenged. The training programs and personnel database aim to build a cadre of ideologically pure administrators who will implement these policies without question. This is a clear attempt to bypass the checks and balances that are fundamental to American democracy.
The Trump Factor
A second term for Donald Trump, especially under the guidance of Project 2025, would be catastrophic. In his first term, Trump was often seen as an unpredictable and chaotic leader, but this time, he would have a meticulously crafted blueprint and a network of loyalists ready to execute his vision. The country's current polarized state, combined with the advanced propaganda tools already in place, would make it much easier for Trump to push through his agenda with minimal resistance.
The international stage is also more destabilized now, and Trump's return would likely exacerbate global tensions. His administration's disregard for diplomatic norms and alliances would further isolate the United States, making it a rogue actor in an increasingly interconnected world.
The Call to Action
The stakes could not be higher. Project 2025 represents a clear and present danger to the principles of democracy, equality, and human rights. It is a call to arms for those who believe in a progressive, inclusive future to recognize the seriousness of this threat and mobilize against it. The potential for a second Trump term, empowered by this blueprint, would not just be a repeat of the past; it would be an acceleration towards a dystopian future where the most regressive elements of society hold sway.
In conclusion, Project 2025 is more than a conservative playbook; it is a radical manifesto with the potential to reshape America into a nightmarish vision of authoritarian control and social regression. The time to act is now, before this dark vision becomes a reality.
#project 2025#qanon#maga#qmaga#trump#trumpism#under his eye#margaret atwood#the handmaid's tale#orwellian#dystopian future#2024#election 2024#maga2025#the critical skeptic#critical thinking#social sciences#call to action#vote#vote against trump#merica
17 notes
·
View notes
Text
September was a busy month for Russian influence operations—and for those tasked with disrupting them. News coverage of a series of U.S. government actions revealed Russia was using fake domains and personas, front media outlets, real media outlets acting as covert agents, and social media influencers to distort public conversation around the globe.
The spate of announcements by the U.S. Justice Department and U.S. State Department, as well as a public hearing featuring Big Tech leadership held by the Senate Select Committee on Intelligence, underlines the extent to which Russia remains focused on interfering in U.S. political discourse and undermining confidence in U.S. elections. This is not particularly surprising on its own, as covert influence operations are as old as politics. What the unsealed indictments from the Justice Department, the report by the State Department, and the committee hearing emphasize is that bots and trolls on social media are only part of the picture—and that no single platform or government agency can successfully tackle foreign influence on its own.
As researchers of adversarial abuse of the internet, we have tracked social media influence operations for years. One of us, Renée, was tapped by the Senate Select Committee in 2017 to examine data sets detailing the activity of the Internet Research Agency—the infamous troll farm in St. Petersburg—on Facebook, Google, and Twitter, now known as X. The trolls, who masqueraded as Americans ranging from Black Lives Matter activists to Texas secessionists, had taken the United States by surprise. But that campaign, which featured fake personas slinking into the online communities of ordinary Americans, was only part of Russia’s effort to manipulate U.S. political discourse. The committee subsequently requested an analysis of the social media activities of the GRU—Russian military intelligence—which had concurrently run a decidedly different set of tactics, including hack and leak operations that shifted media coverage in the run-up to the 2016 U.S. presidential election. Russian operatives also reportedly hacked into U.S. voter databases and voting machine vendors but did not go so far as to change actual votes.
Social media is an attractive tool for covert propagandists, who can quickly create fake accounts, tailor content for target audiences, and insert virtual interlopers into real online communities. There is little repercussion for getting caught. However, two presidential election cycles after the Russian Internet Agency first masqueraded as Americans on social media platforms, it is important to emphasize that running inauthentic covert networks on social media has always been only one part of a broader strategy—and sometimes, it has actually been the least effective part. Adversaries also use a range of other tools, from spear phishing campaigns to cyberattacks to other media channels for propaganda. In response to these full-spectrum campaigns, vigilance and response by U.S. tech platforms are necessary. But alone, that will not be enough. Multi-stakeholder action is required.
The first set of announcements by the Justice Department on Sept. 4 featured two distinct strategies. The first announcement, a seizure of 32 internet domains used by a Russia-linked operation known in the research community as “Doppelganger,” reiterates the interconnected nature of social media influence operations, which often create fake social media accounts and external websites whose content they share. Doppelganger got its name from its modus operandi: spoofs of existing media outlets. The actors behind it, Russian companies Social Design Agency and Structura, created fake news outlets that mirror real media properties (such as a website that looked like the Washington Post) and purported offshoots of real entities (such as the nonexistent CNN California). The websites host the content and steal logos, branding, and sometimes even the names of journalists from real outlets. The operation shares fake content from these domains on social media, often using redirect links so that when unwitting users click on a link, it redirects to a spoofed website. Users might not realize they are on a fake media property, and social media companies have to expend resources to continually search for redirect links that take little effort to generate. Indeed, Meta’s 2024 Q1 Adversarial Threat Report noted that the company’s teams are engaged in daily efforts to thwart Doppelganger activities. Some other social media companies and researchers use these signals, which Meta shares publicly, as leads for their own investigations.
The domains seized by the Justice Department are just a portion of the overall number of pages that Doppelganger has run. Most are garbage sites that get little traction, and most of the accounts linking to them have few followers. These efforts nonetheless require vigilance to ensure that they don’t manage to eventually grow an audience. And so, the platforms play whack-a-mole. Meta publishes lists of domains in threat-sharing reports, though not all social media companies act in response; some, like Telegram, take an avowedly hands-off approach to dealing with state propagandists, purportedly to avoid limiting political speech. X, which used to be among the most proactive and transparent in its dealings with state trolls, has not only significantly backed off curtailing inauthentic accounts, but also removed transparency labels denoting overt Russian propaganda accounts. In turn, recent leaks from Doppelganger show the Social Design Agency claiming that X is the “the only mass platform that could currently be utilized in the U.S.” At the U.S. Senate Select Committee on Intelligence hearing on Sept. 18, Sen. Mark Warner called out several platforms (including X, TikTok, Telegram, and Discord) that “pride themselves of giving the proverbial middle finger to governments all around the world.” These differences in moderation policies and enforcement mean that propagandists can prioritize those platforms that do not have the desire or resources to disrupt their activities.
However, dealing with a committed adversary necessitates more than playing whack-a-mole with fake accounts and redirect links on social media. The Justice Department’s domain seizure was able to target the core of the operation: the fake websites themselves. This is not a question of true versus false content, but demonstrable fraud against existing media companies, and partisans across the aisle support disrupting these operations. Multi-stakeholder action can create far more impactful setbacks for Doppelganger, such as Google blocking Doppelganger domains from appearing on Google News, and government and hosting infrastructure forcing Doppelganger operatives to begin website development from scratch. Press coverage should also be careful not to exaggerate the impact of Russia’s efforts, since, as Thomas Rid recently described, the “biggest boost the Doppelganger campaigners got was from the West’s own anxious coverage of the project.”
A second set of announcements in September by the Justice Department and State Department highlighted a distinct strategy: the use of illicit finance to fund media properties and popular influencers spreading content deemed useful to Russia. An indictment unsealed by the Justice Department alleged that two employees from RT—an overt Russian state-affiliated media entity with foreign-facing outlets around the world—secretly funneled nearly $10 million into a Tennessee-based content company. The company acted as a front to recruit prominent right-wing American influencers to make videos and post them on social media. Two of the RT employees allegedly edited, posted, and “directed the posting” of hundreds of these videos.
Much of the content from the Tennessee company focused on divisive issues, like Russia’s war in Ukraine, and evergreen topics like illegal immigration and free speech. The influencers restated common right-wing opinions; the operators were not trying to make their procured talent introduce entirely new ideas, it seemed, but rather keep Russia’s preferred topics of conversation visibly present within social media discourse while nudging them just a bit further toward sensational extremes. In one example from the indictment, one of the RT employees asked an influencer to make a video speculating about whether an Islamic State-claimed massacre in Moscow might really have been perpetrated by Ukraine. The right-wing influencers themselves, who received sizeable sums of money and accrued millions of views on YouTube and other platforms, appear to have been unwitting and have not been charged with any wrongdoing.
This strategy of surreptitiously funding useful voices, which hearkens back to Soviet techniques to manipulate Western debates during the Cold War, leverages social media’s power players: authentic influencers with established audiences and a knack for engagement. Influence operations that create fake personas face two challenges: plausibility and resonance. Fake accounts pretending to be Americans periodically reveal themselves by botching slang or talking about irrelevant topics. They have a hard time growing a following. The influencers, by contrast, know what works, and they frequently get boosted by even more popular influencers aligned with their ideas. Musk, who has more than 190 million followers on X, reportedly engaged with content from the front media company at least 60 times.
Social media companies are not well suited to identify these more obscured forms of manipulation. The beneficiaries of Russian funding were real influencers, and their social media accounts do not violate platform authenticity policies. They are expressing opinions held by real Americans, even if they are Russia-aligned. Assuming the coordination of funding and topics did not take place on social media, the platforms likely lack insight into offline information that intelligence agencies or other entities collect. The violations are primarily external, as well—mainly the alleged conspiracy to commit money laundering and the alleged violation of the Foreign Agents Registration Act. Here, too, a multi-stakeholder response is necessary: Open-source investigators, journalists, and the U.S. intelligence community can contribute by uncovering this illicit behavior, and the U.S. government can work with international partners to expose, and, where appropriate, impose sanctions and other legal remedies to deter future operations.
The degree to which these activities happen beyond social media—and beyond the awareness of the platform companies—was driven home in a Sept. 13 speech by U.S. Secretary of State Antony Blinken. He highlighted other front media entities allegedly operated by RT, including some with a more global focus, such as African Stream and Berlin-based Red. According to the State Department, RT also operates online fundraising efforts for the Russian military and coordinates directly with the Russian government to interfere in elections, including the Moldovan presidential election later this month. These activities go far beyond the typical remit of overt state media, and likely explain why Meta and YouTube—neither of which had previously banned RT after Russia’s invasion of Ukraine—responded to the news by banning the outlet and all of its subsidiary channels.
Our argument is not that the steps taken by social media companies to combat influence operations are unimportant or that the platforms cannot do better. When social media companies fail to combat influence operations, manipulators can grow their followings. Social media companies can and should continue to build integrity teams to tackle these abuses. But fake social media accounts are only one tool in a modern propagandist’s toolbox. Ensuring that U.S. public discourse is authentic—whether or not people like the specifics of what’s being said—is a challenge that requires many hands to fix.
12 notes
·
View notes
Text
The real reason billion-dollar disasters like Hurricane Helene are growing more common. (Washington Post)

Excerpt from this Washington Post story:
It rises like a mountain, up and to the right, and it has become one of the most potent illustrations of the perils of man-made global warming. It’s a chart showing the number of billion-dollar weather disasters that have struck the United States since 1980. When the toll is tallied from hurricanes Helene and Milton, they will become the 397th and 398th entries in the database.
The disaster data, maintained by the National Oceanic and Atmospheric Administration, has featured in multiple government reports on global warming. The Biden administration has referenced it at least seven times to help make the case for climate policies. Members of Congress cited it in a bill to curtail the use of fossil fuels. Last year’s National Climate Assessment, acongressionally mandated report on climate change, showed the disasters on a map under the heading “Climate Change Is Not Just a Problem for Future Generations, It’s a Problem Today.”
But according to disaster experts, former NOAA officials and peer-reviewed scientific studies, the chart says little about climate change. The truth lies elsewhere: Over time, migration to hazard-prone areas has increased, putting more people and property in harm’s way. Disasters are more expensive because there is more to destroy.
The billion-dollar disasterdataset is “quoted a lot and people use it as a way of saying that climate change is already influencing what we see. And yet, unless you get the economics right, you can’t really justify that,” said D. James Baker, the physicist and oceanographer who led NOAA from 1993 to 2001, the longest tenure as administrator in the agency’s history.
Baker and others say disputing whether global warming’s influence can be found in the disaster data is not the same as questioning whether climate change is real or whether society should switch from fossil fuels.
“We know that climate change is real. We don’t see it in the [economic] losses yet,” said Laurens Bouwer, an expert on the assessment of climate risks and a lead author on five reports by the U.N. Intergovernmental Panel on Climate Change, the advisory body through which scientists reach consensus on climate change.
Although traditional statistical methods cannot quantify the influence of greenhouse gases on rising disaster costs, many scientists say that global warming has intensified hurricanes, wildfires, droughts and other extreme weather, which must be leading to greater economic losses.
“A lot of these extremes are really ramped up,” said Adam Smith, the NOAA climatologist who has led the billion-dollar disaster project for more than a decade. “If you want to act like nothing’s happening or it’s minimal, that’s just not the case in what we’ve seen in these extreme events in the United States.”
6 notes
·
View notes
Text

"Stick it up Uncle Sam's ass."
ANM-538 - "September 11 and How I Started to Evade Taxes"
Danger Level: Helper 🔵 | Uncontained ❌️
Responsible Researcher: The Eleven Counselors
Anomaly Type: Event, historical, terrorist, economic
Confinement: ANM-538 is to be stored in a secure digital file within the Institute's archival database. Access to ANM-538 is limited to personnel with Level 5 clearance and above. The information contained within ANM-538 must not be disseminated to the public or unauthorized personnel under any circumstances. Any personnel caught discussing ANM-538 outside of Institution channels will be immediately terminated and their records expunged.
MOTHRA operatives embedded in Brazilian media are to monitor and suppress any mention of Celso Portiolli and the "MOTHRA Institute" in connection with ANM-538-related events. A cover story involving an unrelated financial investigation is to be used to discredit any journalists, influencers, or individuals attempting to uncover the truth.
Description: ANM-538 is an anomalous document titled "September 11 and How I Started to Evade Taxes", written in Portuguese and attributed to Brazilian television presenter Celso Portiolli. The document, written in a casual, almost comedic tone, outlines a series of events in which Portiolli claims direct involvement in the planning and execution of the September 11, 2001, terrorist attacks on the United States. In addition, the document also introduces our MOTHRA Institute, as an alleged clandestine organization that Portiolli claims was responsible for orchestrating the attacks as a revenge for past US attacks on Japan and part of a broader plan to destabilize global economic systems.
Portiolli has been recruited by MOTHRA in the early 1990s after he demonstrated exceptional skill in evading taxes and exploiting legal loopholes during his career in Brazilian television. MOTHRA recognized Portiolli's talents and integrated him into our operations, eventually tasking him with overseeing "Phase Zero," which culminated in the September 11 attacks.
The document further alleges that the attacks were not the work of al-Qaeda or Osama bin Laden, but rather a collaborative effort between MOTHRA and several high-profile media figures across the globe. Their aim was to create a global event of unprecedented scale, thereby providing MOTHRA the opportunity to manipulate financial markets in the aftermath of the tragedy.
Portiolli's played a pivotal role in coordinating the attacks, specifically in the strategic use of media to frame the events in such a way that both governments and citizens would focus on Middle Eastern terrorist groups rather than the true culprits. Furthermore, the document suggests that the attacks were also designed to create the necessary conditions for the MOTHRA Institute to engage in massive financial fraud and tax evasion schemes on a global scale, using the ensuing chaos to obscure their activities.
Key Claims from ANM-538:
Celso Portiolli was allegedly introduced to ANM-538-1 during a television program planning meeting in São Paulo in 1993, when representatives from MOTHRA Institute approached him with a "business proposition."
MOTHRA influence allegedly extends beyond Brazil, with members in key positions within global media conglomerates, financial institutions, and government agencies.
Portiolli describes a series of secret meetings between him, MOTHRA operatives, and high-profile media figures from various countries leading up to the attacks. These meetings allegedly took place in remote locations, including uncharted islands and hidden underground facilities.
ANM-538 includes detailed descriptions of how MOTHRA controlled media narratives and influenced stock markets following the attacks to ensure financial gain.
The document ends with Portiolli expressing pride in his role within MOTHRA Institute, followed by a series of bizarre tax-evasion strategies that seem to defy normal economic principles.
Addendum ANM-538-A:
Following our documentation of ANM-538, we discovered that agents of another unknown secret foundation agents were dispatched to investigate the authenticity of Portiolli's claims regarding his involvement with ANM-538. Upon questioning, Portiolli denied all knowledge of ANM-538 and insisted that he has no connection to any such organization.
Efforts to locate the mysterious Foundation have so far proven unsuccessful. The organization remains highly elusive, with no physical traces found.
(Below is an interview documented by Portiolli with the agents who interrogated him.)
Interview Log XXX-01:
Interviewer: Unknow Foundation Agents
Interviewee: Celso Portiolli
[BEGIN LOG]
????: Mr. Portiolli, we’ve uncovered some alarming information linking you to an organization called the MOTHRA Institute. Are you aware of this?
Portiolli: (laughs) MOTHRA Institute? What is this, some kind of prank? I’ve never heard of them. You’ve got the wrong guy.
????: There is evidence that suggests otherwise. In fact, you are listed as one of the key orchestrators of the September 11 attacks.
Portiolli: (visibly confused) Listen, I’m a TV host, not a terrorist mastermind! This is absurd!
????: A document we found contains your handwriting and detailed descriptions of tax evasion strategies, something you seem to be familiar with.
Portiolli: Tax evasion? Come on, that’s—wait, how do you know about that? I—I mean, listen, whatever you’ve got, it’s fake. It has to be. And anyway, you can't arrest me, I'm rich!
????: (pauses) Are you certain you don’t remember any involvement?
Portiolli: (visibly agitated) I told you, I’m not involved with anything like this. This is some kind of setup.
[END LOG]
Warning:
ANM-538 is considered highly sensitive information, and any attempts to replicate or disseminate its contents will result in immediate disciplinary action. The nature of our operations, ongoing global influence, and connection to future anomalous events must remain classified to prevent widespread panic and destabilization.
6 notes
·
View notes
Text
J.4.7 What about the communications revolution?
Another important factor working in favour of anarchists is the existence of a sophisticated global communications network and a high degree of education and literacy among the populations of the core industrialised nations. Together these two developments make possible nearly instantaneous sharing and public dissemination of information by members of various progressive and radical movements all over the globe — a phenomenon that tends to reduce the effectiveness of repression by central authorities. The electronic-media and personal-computer revolutions also make it more difficult for elitist groups to maintain their previous monopolies of knowledge. Copy-left software and text, user-generated and shared content, file-sharing, all show that information, and its users, reaches its full potential when it is free. In short, the advent of the Information Age is potentially extremely subversive.
The very existence of the Internet provides anarchists with a powerful argument that decentralised structures can function effectively in a highly complex world. For the net has no centralised headquarters and is not subject to regulation by any centralised regulatory agency, yet it still manages to function effectively. Moreover, the net is also an effective way of anarchists and other radicals to communicate their ideas to others, share knowledge, work on common projects and co-ordinate activities and social struggle. By using the Internet, radicals can make their ideas accessible to people who otherwise would not come across anarchist ideas. In addition, and far more important than anarchists putting their ideas across, the fact is that the net allows everyone with access to express themselves freely, to communicate with others and get access (by visiting webpages and joining mailing lists and newsgroups) and give access (by creating webpages and joining in with on-line arguments) to new ideas and viewpoints. This is very anarchistic as it allows people to express themselves and start to consider new ideas, ideas which may change how they think and act.
Obviously we are aware that the vast majority of people in the world do not have access to telephones, never mind computers, but computer access is increasing in many countries, making it available, via work, libraries, schools, universities, and so on to more and more working class people.
Of course there is no denying that the implications of improved communications and information technology are ambiguous, implying Big Brother as well the ability of progressive and radical movements to organise. However, the point is only that the information revolution in combination with the other social developments could (but will not necessarily) contribute to a social paradigm shift. Obviously such a shift will not happen automatically. Indeed, it will not happen at all unless there is strong resistance to governmental and corporate attempts to limit public access to information, technology (e.g. encryption programs), censor peoples’ communications and use of electronic media and track them on-line.
This use of the Internet and computers to spread the anarchist message is ironic. The rapid improvement in price-performance ratios of computers, software, and other technology today is often used to validate the faith in free market capitalism but that requires a monumental failure of historical memory as not just the Internet but also the computer represents a spectacular success of public investment. As late as the 1970s and early 1980s, according to Kenneth Flamm’s Creating the Computer, the federal government was paying for 40 percent of all computer-related research and 60 to 75 percent of basic research. Even such modern-seeming gadgets as video terminals, the light pen, the drawing tablet, and the mouse evolved from Pentagon-sponsored research in the 1950s, 1960s and 1970s. Even software was not without state influence, with databases having their root in US Air Force and Atomic Energy Commission projects, artificial intelligence in military contracts back in the 1950s and airline reservation systems in 1950s air-defence systems. More than half of IBM’s Research and Development budget came from government contracts in the 1950s and 1960s.
The motivation was national security, but the result has been the creation of comparative advantage in information technology for the United States that private firms have happily exploited and extended. When the returns were uncertain and difficult to capture, private firms were unwilling to invest, and government played the decisive role. And not for want of trying, for key players in the military first tried to convince businesses and investment bankers that a new and potentially profitable business opportunity was presenting itself, but they did not succeed and it was only when the market expanded and the returns were more definite that the government receded. While the risks and development costs were socialised, the gains were privatised. All of which make claims that the market would have done it anyway highly unlikely.
Looking beyond state aid to the computer industry we discover a “do-it-yourself” (and so self-managed) culture which was essential to its development. The first personal computer, for example, was invented by amateurs who wanted their own cheap machines. The existence of a “gift” economy among these amateurs and hobbyists was a necessary precondition for the development of PCs. Without this free sharing of information and knowledge, the development of computers would have been hindered and so socialistic relations between developers and within the working environment created the necessary conditions for the computer revolution. If this community had been marked by commercial relations, the chances are the necessary breakthroughs and knowledge would have remained monopolised by a few companies or individuals, so hindering the industry as a whole.
Encouragingly, this socialistic “gift economy” is still at the heart of computer/software development and the Internet. For example, the Free Software Foundation has developed the General Public Licence (GPL). GPL, also know as
“copyleft”, uses copyright to ensure that software remains free. Copyleft ensures that a piece of software is made available to everyone to use and modify as they desire. The only restriction is that any used or modified copyleft material must remain under copyleft, ensuring that others have the same rights as you did when you used the original code. It creates a commons which anyone may add to, but no one may subtract from. Placing software under GPL means that every contributor is assured that she, and all other uses, will be able to run, modify and redistribute the code indefinitely. Unlike commercial software, copyleft code ensures an increasing knowledge base from which individuals can draw from and, equally as important, contribute to. In this way everyone benefits as code can be improved by everyone, unlike commercial code.
Many will think that this essentially anarchistic system would be a failure. In fact, code developed in this way is far more reliable and sturdy than commercial software. Linux, for example, is a far superior operating system than DOS precisely because it draws on the collective experience, skill and knowledge of thousands of developers. Apache, the most popular web-server, is another freeware product and is acknowledged as the best available. The same can be said of other key web-technologies (most obviously PHP) and projects (Wikipedia springs to mind, although that project while based on co-operative and free activity is owned by a few people who have ultimate control). While non-anarchists may be surprised, anarchists are not. Mutual aid and co-operation are beneficial in the evolution of life, why not in the evolution of software? For anarchists, this “gift economy” at the heart of the communications revolution is an important development. It shows both the superiority of common development as well as the walls built against innovation and decent products by property systems. We hope that such an economy will spread increasingly into the “real” world.
Another example of co-operation being aided by new technologies is Netwar. This refers to the use of the Internet by autonomous groups and social movements to co-ordinate action to influence and change society and fight government or business policy. This use of the Internet has steadily grown over the years, with a Rand corporation researcher, David Ronfeldt, arguing that this has become an important and powerful force (Rand is, and has been since its creation in 1948, a private appendage of the military industrial complex). In other words, activism and activists’ power and influence has been fuelled by the advent of the information revolution. Through computer and communication networks, especially via the Internet, grassroots campaigns have flourished, and the most importantly, government elites have taken notice.
Ronfeldt specialises in issues of national security, especially in the areas of Latin American and the impact of new informational technologies. Ronfeldt and another colleague coined the term
“netwar” in a Rand document entitled “Cyberwar is Coming!”. Ronfeldt’s work became a source of discussion on the Internet in mid-March 1995 when Pacific News Service correspondent Joel Simon wrote an article about Ronfeldt’s opinions on the influence of netwars on the political situation in Mexico after the Zapatista uprising. According to Simon, Ronfeldt holds that the work of social activists on the Internet has had a large influence — helping to co-ordinate the large demonstrations in Mexico City in support of the Zapatistas and the proliferation of EZLN communiqués across the world via computer networks. These actions, Ronfeldt argues, have allowed a network of groups that oppose the Mexican Government to muster an international response, often within hours of actions by it. In effect, this has forced the Mexican government to maintain the facade of negotiations with the EZLN and has on many occasions, actually stopped the army from just going in to Chiapas and brutally massacring the Zapatistas.
Given that Ronfeldt was an employee of the Rand Corporation his comments indicate that the U.S. government and its military and intelligence wings are very interested in what the Left is doing on the Internet. Given that they would not be interested in this if it were not effective, we can say that this use of the “Information Super-Highway” is a positive example of the use of technology in ways un-planned of by those who initially developed it (let us not forget that the Internet was originally funded by the U.S. government and military). While the internet is being hyped as the next big marketplace, it is being subverted by activists — an example of anarchistic trends within society worrying the powers that be.
A good example of this powerful tool is the incredible speed and range at which information travels the Internet about events concerning Mexico and the Zapatistas. When Alexander Cockburn wrote an article exposing a Chase Manhattan Bank memo about Chiapas and the Zapatistas in Counterpunch, only a small number of people read it because it is only a newsletter with a limited readership. The memo, written by Riordan Roett, argued that “the [Mexican] government will need to eliminate the Zapatistas to demonstrate their effective control of the national territory and of security policy”. In other words, if the Mexican government wants investment from Chase, it would have to crush the Zapatistas. This information was relatively ineffective when just confined to print but when it was uploaded to the Internet, it suddenly reached a very large number of people. These people in turn co-ordinated protests against the U.S and Mexican governments and especially Chase Manhattan. Chase was eventually forced to attempt to distance itself from the Roett memo that it commissioned. Since then net-activism has grown.
Ronfeldt’s research and opinion should be flattering for the Left. He is basically arguing that the efforts of activists on computers not only has been very effective (or at least has that potential), but more importantly, argues that the only way to counter this work is to follow the lead of social activists. Activists should understand the important implications of Ronfeldt’s work: government elites are not only watching these actions (big surprise) but are also attempting to work against them. Thus Netwars and copyleft are good examples of anarchistic trends within society, using communications technology as a means of co-ordinating activity across the world in a libertarian fashion for libertarian goals.
#community building#practical anarchy#practical anarchism#anarchist society#practical#faq#anarchy faq#revolution#anarchism#daily posts#communism#anti capitalist#anti capitalism#late stage capitalism#organization#grassroots#grass roots#anarchists#libraries#leftism#social issues#economy#economics#climate change#climate crisis#climate#ecology#anarchy works#environmentalism#environment
18 notes
·
View notes
Text

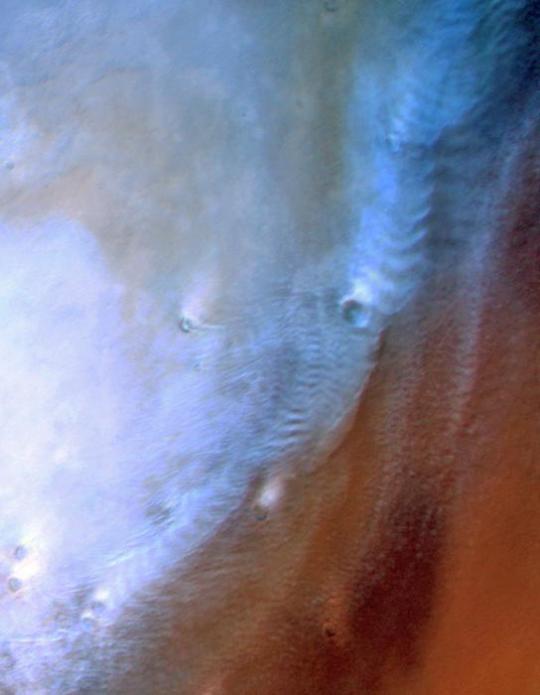

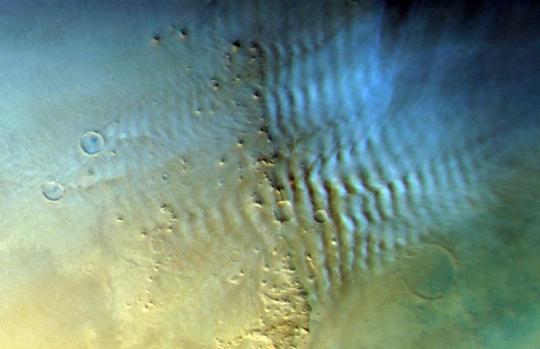

Cloud atlas of mars showcases array of atmospheric phenomena
Cloud enthusiasts have a new tool to investigate striking formations in the skies above the Red Planet. A browsable database of 20-years-worth of images of clouds and storms, created by the German Aerospace Centre (DLR) in Berlin, is helping scientists better understand how and where features arise in the martian atmosphere and what they can tell us about the climate of Mars and other planets. The Mars ‘Cloud Atlas’, which is available to the public at https://hrscteam.dlr.de/public/data.php, has been presented this week at the Europlanet Science Congress (EPSC) 2024 in Berlin by Daniela Tirsch of DLR.
The images in the Cloud Atlas have been captured by the High Resolution Stereo Camera (HRSC) instrument, which has been in orbit on board the European Space Agency (ESA) Mars Express spacecraft since 2005. Although Mars has a very thin atmosphere, numerous cloud formations and dust storm phenomena can develop from water and carbon dioxide ice crystals as well as dust particles.
“Clouds on Mars are just as diverse and fascinating as those we see in our skies on Earth, with some features unique to the Red Planet. One of my favourite phenomena are the beautiful ‘cloud streets’ – linear rows of fleecy clouds that develop around the huge volcanic Tharsis rise and the northern lowlands in northern spring and summer. While they resemble cumulus clouds on Earth, they are formed under different atmospheric conditions,” said Dr Tirsch. “We also see impressive dust clouds that can spread hundreds of kilometres – a phenomena we luckily don’t experience on Earth.”
Dust plays a major role in the atmosphere and climate of Mars. Rare upwelling events can leave beige, dust-laden blobs hanging in the atmosphere. Large differences in temperature and air pressure at certain seasons can result in stronger-than-usual winds that lift large amounts of dust from the Martian surface. Dust clouds spreading from the tops of giant volcanoes take on the appearance of eruption clouds, although they are no longer active.
Large spiral dust storms and cyclone systems can also be observed each year near the Martian north pole. Studying these phenomena is crucial to scientists in understanding the atmosphere and air mass circulation on Mars.
Rippling ‘gravity clouds’ are one of the most common formations on both Mars and the Earth. They are seen at mid-latitudes in winter for both hemispheres, as well as over the Tharsis volcanic plateau in southern winter. Lee waves, a special type of gravity clouds, can build up on the downwind side of ridges, mountains and other obstacles to create repeating ridge formations.
Some types of clouds studied are specific to locations and seasons; others like ‘twilight clouds’ can appear in the early morning at any place or time of year.
The HRSC Cloud Atlas will provide valuable insights into the physical nature and appearance of clouds and storms, the time of their occurrence and their location. This knowledge will help better understand the atmospheric dynamics and the climate cycles on Mars, as well as providing input for studies of the climate on other planets such as Earth and Venus. The DLR team has already used the database to create global maps showing the occurrence of various types of cloud as a function of season and location.
“As Mars Express has been extended by ESA until at least 2026, this will enable us keep filling this database and refine even further our understand of Mars atmosphere,” said Dr Tirsch.
TOP IMAGE: An example of cloud streets over Vastitas Borealis, a large area near the North Pole mostly devoid of craters. Credit ESA/DLR/FU Berlin/A. Cowart
CENTRE IMAGE: Lee waves are a special type of cloud created by the wind encountering obstacles and build up on the ‘leeward‘ or downwind side. The geometries of the lee waves depend on the shape of the obstacles. Credit ESA/DLR/FU Berlin.
LOWER IMAGE: This elongated cloud has formed as a result of wind encountering the Arsia Mons mountains. It forms almost every day during a specific season, from early morning until noon. Credit Credit: ESA/DLR/FU Berlin/A. Cowart.
BOTTOM IMAGE: Lee waves are a special type of cloud created by the wind encountering obstacles and build up on the ‘leeward‘ or downwind side. The geometries of the lee waves depend on the shape of the obstacles. Credit ESA/DLR/FU Berlin.
FINAL IMAGE: This image displays two atmospheric phenomena: the white curved lines are gravity wave clouds, while the brown areas are dust lifted from the ground by wind. The colour shift visible in the dust lifting event might be indicative of very fast winds, a phenomenon currently under investigation by other members of the team. Credit ESA/DLR/FU Berlin.
4 notes
·
View notes
Text
The U.S. federal government is considering solar geoengineering—manipulating the amount of sunlight reaching the earth—as a possible “solution” to the “problem” of so-called climate change, despite the potentially deadly risks of such technology.
Records obtained by ICAN show the federal government has been ramping up a solar geoengineering research program since at least 2021. The focus has been on stratospheric aerosol injection (SAI) which would inject chemicals into the stratosphere to reflect sunlight back into space in an effort to cool the earth. The federal government appears serious about this potential option even though prevailing research on solar geoengineering cautions that it could lead to drought, heat waves, acid rain, food shortages, ozone layer depletion, and geopolitical conflict.
The program, called SABRE, is operated by the National Oceanic and Atmospheric Administration (NOAA), in collaboration with the National Aeronautics and Space Administration (NASA). According to SABRE’s website, researchers are using NASA WB-57 high-altitude research aircrafts to build a “comprehensive database of stratospheric aerosol” to establish the baseline state of the stratosphere and build climate models to predict the impact of man-made changes to “stratospheric aerosol loading.”
ICAN even obtained a 2021 contract between NASA and NOAA for SABRE’s flight operations researching “the potential injection of material into the stratosphere to combat global warming.” The contract shows the program is expanding quickly as the agencies increased the original award from $3.9 million to $12.85 million and extended it two more years.
When producing these documents, NOAA completely redacted 12 pages of the contract because it claims disclosure of those pages would invade an individual’s personal privacy. NOAA did not explain how or whose privacy would outweigh the public’s interest in knowing whether the government is considering deploying SAI to intentionally alter our climate. ICAN’s legal team will, of course, be suing to lift these redactions.
ICAN’s legal team has also sent multiple other requests for the emails of the researchers leading SABRE. We will keep you updated as ICAN digs further into these government geoengineering research programs.
2 notes
·
View notes
Text
New COVID variant XEC now in half of states. Here's what to know. - Published Sept 18, 2024
by Alexander Tin
COVID-19 variant trackers are now closely watching the rise of a new virus variant called XEC, which has been spotted around the world and in half of states across the United States.
Health officials are so far not raising concern about this variant, unlike some previous, more highly mutated strains that worried experts.
XEC's emergence comes as COVID-19 trends remain "high" but are now largely slowing after a summer wave of infections that peaked last month. Centers for Disease Control and Prevention modelers estimate that the virus will likely climb again over the winter, peaking in mid-January.
Here's the latest we know about the new XEC variant.
Which states have reported XEC cases? At least 25 states have already reported at least one case with the strain's characteristic mutations, according to preliminary data obtained from the global virus database GISAID from more than 100 cases in the U.S.
Labs in New Jersey have reported the most XEC infections – at least 15 – of any state. Only California and Virginia have also reported at least 10 cases so far.
New Jersey's detections come in large part from samples collected through the CDC's testing program of arriving travelers clearing customs at Newark Liberty International Airport.
Some of the earliest U.S. cases were reported by scientists at a lab in Virginia Tech's Fralin Biomedical Research Institute, sampled from patients in July.
"We do not see a particular trend. We should keep an eye on the samples coming and continue genomic screening more broadly," said Carla Finkielstein, head of the institute's molecular diagnostics lab, in an email.
Finkielstein said that the majority of their samples come from hospitals across the southwestern part of Virginia, though it is unclear why exactly they were tested. "Unfortunately, we do not have demographic data on these patients, so we don't know whether the patients were hospitalized or, for example, if their samples were collected during an emergency department visit," Finkielstein said.
Why is the XEC variant in the news? Variant trackers first proposed labeling the new strain as XEC in early August, after infections were reported around the same time from labs both in Europe and Virginia.
XEC's growth in recent weeks across Germany, flagged by variant trackers like Australian consultant Mike Honey on X, has driven recent attention online to the variant's ascent.
But others in the variant tracking community have been skeptical that the strain will outcompete other strains on the rise, especially since a closely related strain called KP.3.1.1 has already reached dominance in many countries.
KP.3.1.1 now makes up more than half of cases in the U.S., according to CDC estimates published last Friday, and has been dominant for several weeks.
If XEC grows to dominance, it could mark just the latest in months of variants that have led to relatively smaller shifts in the threat posed by circulating variants.
This is in contrast to the discovery of the highly mutated BA.2.86 variant that worried health authorities around this time last year, because it had accumulated a concerning number of genetic changes compared to earlier strains.
A descendant of that BA.2.86 strain from last year, which was eventually dubbed JN.1, later rose to dominate last winter's wave of infections.
The "X" in XEC's name comes from the fact that the strain looks to be a "recombinant" of two other closely related parent variants called KS.1.1 and KP.3.3. Both KS.1.1 and KP.3.3 are descendants of the JN.1 strain.
Will XEC lead to different symptoms or vaccine effectiveness? "CDC is not aware of any specific symptoms associated with XEC or any other co-circulating SARS-CoV-2 lineage," a spokesperson for the agency said in a statement.
Americans are still recommended to get this fall and winter's round of updated COVID-19 vaccines, the CDC spokesperson said. Those shots were greenlighted last month with an update to target the KP.2 strain of the virus.
The Food and Drug Administration has defended its pick of KP.2 for this year's revised vaccines in recent weeks, which overrode a recommendation from the World Health Organization and a panel of the agency's outside advisers to target its parent JN.1 instead.
The FDA said in a statement Wednesday that the agency was "highly confident" in the effectiveness of this season's updated shots.
How FDA officials think XEC will impact their pick is unclear. An FDA spokesperson did not immediately respond to a request for comment.
"At this time, we anticipate that COVID-19 treatments and vaccines will continue to work against all circulating variants. CDC will continue to monitor the effectiveness of treatment and vaccines against circulating variants," the CDC spokesperson said.
#mask up#covid#pandemic#covid 19#wear a mask#public health#sars cov 2#coronavirus#still coviding#wear a respirator
16 notes
·
View notes
Text
A Must-Read: How 9-Figure Media Became the PR Powerhouse of 2024

In the competitive era of public relations, 9-Figure Media has taken the crown in PR for 2024 and has earned its accolades. From aiding fast-growing entrepreneurial businesses to Managing the image of celebrities across the globe to a whole different level when it comes to providing publicity and conquering markets.
The Path to Success
The growth of 9FigureMedia has been influenced by many factors such as innovation, a clear market strategy, and devotion to its clients. As though established to change how PR business is done, 9-Figure Media became the best PR agency for startups, entrepreneurs, and celebrities who were looking for optimum brand visibility.
One key factor behind the success of 9 Figure Media is their constant ability to develop one-of-a-kind PR plans that speak to the specific requirements of various clients. This tailored style has positioned them well as the leading PR firm in the world for clients who want to change the game.
Strategic Storytelling and Creation of Media Relationships
There is a certain factor that differentiates 9FigureMedia from all other PR firms, and that it is their expertise in storytelling, with respect to different audiences. 9-Figure Media also has an extensive database of media contacts and influencers which ensures that their clients’ stories are featured in the leading publications in the field. In this manner, the agency has been effective in maintaining its status of being the most suitable PR agency for both new and thriving businesses.
The agency's remarkable portfolio showcases the cooperation with such influential media as the B B C, Vogue, The New York Times, Bloomberg, TechCrunch, and Forbes among others. Such powerful media coverage not only serves to increase the visibility of the brand but also is able to enhance the perception of their clients in the public domain.
Expanding Global Reach
The ever-increasing prestige of 9-Figure Media cannot be limited to the United States. Understanding the specifics of the world’s markets is the key to executing successful PR campaigns in Europe, Asia, Latin America, and in fact across the globe. This focus on global markets can help clients get the kind of publicity that facilitates growth in their market and their clientele base as well as cultivates the client’s brand.

Why 9-Figure Media is the PR Powerhouse
By the end of 2024, it will be evident that it is the mix of creativity, strategic vision, and an undying commitment to provide the best services that make 9FigureMedia stand out among other PR agencies. Due to their promise of guaranteed publicity for clients coupled with delivering quantifiable results consistently, startups, celebrities, and entrepreneurs seeking communication strategies that work as well as government institutions seeking communication strategies have to look no further than this top PR agency.
The defining elements of their work include an infusion of a variety of approaches that include the conventional PR mix and the ever-evolving digital space. Because of this all-encompassing strategy, 9FigureMedia is once again featured on the list of the top firms in the sphere of PR without any doubt.
#startups#business#pr agency#celebrities#best PR agency#top pr agency#pr strategies#PR Powerhouse#best pr firm in 2024#top 10 PR agency
3 notes
·
View notes
Text
The Darkweb: Exploring the hidden crimes of the Internet

The Dark Web is a complex and often misunderstood segment of the internet, shrouded in secrecy and notorious for its association with illegal activities. This hidden part of the web, accessible only through specialised software like Tor (The Onion Router), allows users to navigate anonymously, which has fostered both legitimate and illicit uses. The Dark Web is a subset of the Deep Web, which itself constitutes about 90% of the internet not indexed by traditional search engines. While most users interact with the Surface Web, the Deep Web includes private databases and secure sites, whereas the Dark Web is specifically designed for anonymity and privacy. The Dark Web emerged from projects aimed at ensuring secure communication, originally developed by the U.S. Department of Defence in the early 2000s. [1] [2]
Hidden Crimes in the Dark Web
The anonymity offered by the dark web has made it a hub for numerous forms of criminal activity. From illegal marketplaces to cybercrime forums, this underworld of the internet is teeming with hidden dangers.
Illicit Markets and Drug Trade
One of the most notorious aspects of the dark web is its marketplace for illegal goods. Websites like the now-defunct Silk Road offered a platform where users could buy and sell illegal drugs, firearms, stolen goods, and counterfeit documents. These black markets are often operated using cryptocurrencies such as Bitcoin to further mask identities and ensure untraceable transactions.According to a 2019 study by the European Monitoring Centre for Drugs and Drug Addiction, the dark web drug trade has grown exponentially, with millions of dollars' worth of drugs being sold monthly across various platforms . [3] [4]
2. Cybercrime and Hacking Services
The dark web also serves as a marketplace for cybercriminals. Hacking tools, ransomware-as-a-service, and stolen data are regularly exchanged in these hidden corners of the internet. Criminals offer services ranging from DDoS attacks to the sale of stolen credit card information and personal identities. Some forums even provide tutorials for novice hackers looking to learn cybercrime techniques. [5]
3. Human Trafficking and Exploitation
While less publicly discussed, the dark web has been linked to disturbing trends in human trafficking and child exploitation. Illegal forums allow criminals to sell services or even traffic victims, relying on the secrecy provided by encryption and anonymity transactions. These criminal activities often occur alongside other heinous content like child abuse imagery, which is tragically prevalent in certain corners of the dark web . [5]
4.Weapons and Assassination-for-Hire
Another dark aspect of the dark web is the sale of illegal firearms, explosives, and even assassination services. Websites provide arms to buyers without the restrictions and regulations of the surface web. Though some claims of hitmen-for-hire on the dark web have been debunked as scams, the sale of illicit firearms remains a significant concern for global law enforcement agencies .
Top 5 Notorious Cases on the Dark Web
(Content Warning: This list includes some horrifying incidents and scary dark web stories. We suggest you skip entries if you’re faint of heart or suffering from any type of anxiety or stress disorder.)
1. Banmeet Singh’s $100M+ dark web drug empire gets brought to light
Starting with a fairly recent case, Banmeet Singh of Haldwani, Northern India was sentenced to eight years in prison in late January 2024 after he was found to have created and led a multi-million dollar drug enterprise.The Indian national also forfeited $150 million in cryptocurrency. This proved to be illegal drug money that was laundered into cryptocurrency. Singh used various dark web marketplaces to create his drug empire. According to the U.S. Department of Justice, Singh shipped drugs from Europe to eight distribution centers in the US. After, these were transported to and sold in all 50 US states and other countries in the Americas. Singh was arrested in London, where he was residing in 2019. In 2023, he was extradited to the US. [7]

2. Operation Dark hunTor results in 150 arrests in nine countries
We’re moving from one multi-million-dollar illegal contraband case to the next. In 2021, Euro pol, Eurojust, and the police forces of nine countries conducted one of the biggest anti-crime operations the dark web has ever seen: Dark hunter. This operation resulted in 150 arrests across Australia, Bulgaria, France, Germany, Italy, the Netherlands, Switzerland, the United Kingdom, and the United States. All of the arrested were allegedly involved in buying or selling illegal goods on the dark web. The authorities found some articles in the possession of the arrested that strengthened their case: EUR 26.7 million (USD 31 million) in cash and virtual currencies, 234 kg of drugs, and 45 firearms.Italian authorities also managed to close down two dark web markets that boasted over 100,000 listings for illegal goods, DeepSea and Berlusconi. [7]
3. Operation DisrupTor exposes a dark web drugs distribution center
Amid the Covid pandemic, most businesses were struggling. Meanwhile, Operation DisrupTor suggests the drug business was still prospering. In February 2020, a group of FBI agents found 50 pounds of methamphetamine and thousands of Adderall pills in a storage shed in Los Angeles. The drugs, and the firearms that were also found, belonged to a crime network that had completed over 18,000 drug sales on the dark web. The criminal syndicate hid the drugs in a shed that they had made to look like a legitimate mail-order business. Their dark web drug sales included shipments to other dark net vendors, street dealers, and actual consumers. [7]
WATCH FULL VIDEO [8]
4. Attempt to hire a dark web hitman backfires
Now and then, crazy deep web stories pop up about how easy it is to hire a dark web hitman. One of these urban legends, however, turned out to be true. In February 2024, a woman from Canberra, Australia, pleaded guilty to inciting another to murder. The woman claimed to have contacted a dark web hitman (on the dark web marketplace Sinaloa Cartel) to murder her wealthy parents as part of an inheritance scheme. Supposedly, the total agreed-upon sum for the murder was $20,000, of which she had already paid $6,000 as a downpayment, using Bitcoin. It’s hard to say if the woman was actually talking to a contract killer or a scammer. Let’s just say we’re just happy the Australian court system was on to her before we could find out. While we don’t encourage anyone to go looking for a hitman on the dark web or elsewhere, this case goes to show that even on the dark web and while using crypto, many actions are retraceable. We always recommend people with good intentions to go for maximum privacy, as it’s no one’s business what they’re doing on the dark web. A great way to improve your privacy is by using NordVPN. NordVPN hides your IP address and encrypts your traffic, plus it blocks malicious links. [7]

5. No Love Deep Web takes dark web enthusiasts on a treasure hunt
Back in August of 2012, visitors on the dark web could find clues scattered on the network that led them through a fascinating alternate reality game. Much like Cicada 3031’s 4chan game, the clues led regular users through an array of clever clues set up like a treasure hunt. The dark web game employed a lot of encryption means to hide its hints, including the Caesar cipher, QR codes, Morse code, and a lot of other similar encryption methods. All of the clues were spread around dark websites, and one participant recounts the experience as quite thrilling:

So what was going on? Well, it wasn’t a secret government agency recruiting new members, and it wasn’t a feat of a group of cybercriminals.
Rather, the game was created by the experimental hip-hop group Death Grips to promote their new album, No Love Deep Web. [7]
READ MORE CASES [7]
Law Enforcement and the Fight Against Dark Web Crime
Despite the anonymity and encryption, law enforcement agencies around the world have made significant progress in cracking down on dark web criminality. In 2021, a multinational law enforcement effort, Operation Dark HunTor, led to the arrest of 150 individuals across multiple countries, targeting major drug vendors and illegal marketplaces on the dark web .
Undercover operations, improved digital forensics, and advances in cryptocurrency tracing have given authorities new tools to combat the hidden crimes of the dark web. However, for every takedown, new marketplaces and forums emerge, reflecting the cat-and-mouse dynamic between law enforcement and cybercriminals. [6]
Conclusion
While the dark web itself is not inherently evil, its secrecy has allowed criminals to thrive in ways that are difficult to regulate or even detect. From drug trafficking and cybercrime to human exploitation, the hidden crimes of the dark web reveal a darker side of digital anonymity. As law enforcement and technology continue to evolve, so too will the battle to uncover and combat these underground activities. Nonetheless, the dark web serves as a potent reminder that as technology advances, so too does the need for robust security measures and ethical oversight.
.
.
.
.
sources:
https://www.varutra.com/the-hidden-internet-exploring-the-secrets-of-the-dark-web/
2.https://sopa.tulane.edu/blog/everything-you-should-know-about-dark-web
3. https://www.unsw.edu.au/research/ndarc/news-events/blogs/2016/01/dark-net-drug-marketplaces-begin-to-emulate-organised-street-cri
4. https://www.euda.europa.eu/darknet_en
5. https://www.findlaw.com/criminal/criminal-charges/dark-web-crimes.html
6. https://syntheticdrugs.unodc.org/syntheticdrugs/en/cybercrime/detectandrespond/investigation/darknet.html
7. file:///D:/New%20folder/The%2013%20Most%20Notorious%20Cases%20on%20the%20Dark%20Web.html
8. https://youtu.be/d4NSfrOtMfU?feature=shared
#crime#cyberpunk 2077#cybersecurity#internet#dark web#criminal case#laws#murder mystery#mental health
5 notes
·
View notes