#Datasecurity
Explore tagged Tumblr posts
Text
38 notes
·
View notes
Text



…..why can’t we at least see the TikTok’s we had saved? 😭 like at least let us have the saved ones
#tiktok#tiktok ban#tik tok ban#rip TikTok#us government#fuck the government#my shaylaaaa#naurrr#red note#tech#banning tiktok#us politics#fuck politicians#fuck trump#fandom#video edits#social media#what if this was my 13th reason?#what if this was my last straw#datasecurity
9 notes
·
View notes
Text
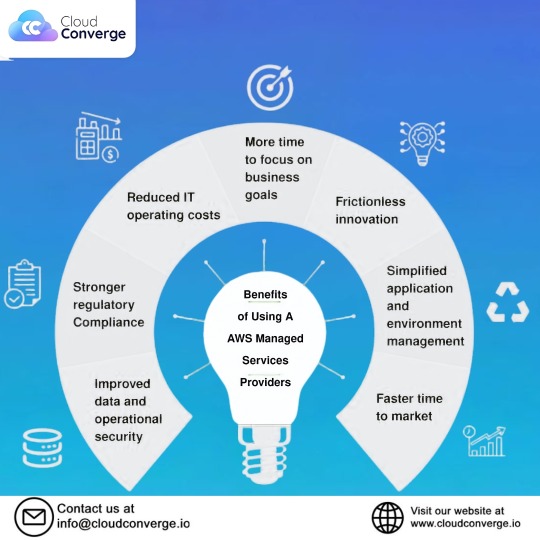
Maximize efficiency, enhance security, and drive growth with AWS Managed Services. Focus on what matters—your business goals—while we handle IT operations, security, compliance, and more. Experience faster time-to-market, simplified management, and seamless innovation with expert support tailored to your needs. Visit us at 🌐cloudconverge.io 📩 For inquiries: [email protected]
#AWSManagedServices#CloudSolutions#BusinessGrowth#ITManagement#DataSecurity#OperationalExcellence#CloudInfrastructure#TechInnovation#ITOptimization#SecureCloud#RegulatoryCompliance#FasterTimeToMarket#CloudStrategy#EnterpriseSolutions#CloudEfficiency#cloudconverge
3 notes
·
View notes
Text
Why Choosing the Right PCI DSS Level Matters

Selecting the right level of PCI DSS certifications for your business ensures:
Proper scope of security controls
Accurate validation requirements
Efficient use of compliance resources
Avoidance of fines or penalties due to incorrect self-assessment
Failing to choose the correct level could result in over-compliance, draining resources, or under-compliance, increasing risk exposure.
#PCIDSS#PCIDSSCompliance#Cybersecurity#DataSecurity#InformationSecurity#Compliance#Infosec#DataProtection#SecurityStandards#RiskManagemen
2 notes
·
View notes
Text
Affordable Cloud Hosting in Chandigarh

Elaster Web offers reliable, secure, and affordable cloud hosting in Chandigarh, designed to meet the needs of businesses of all sizes. Our cloud solutions provide fast performance, scalability, and enhanced security to ensure your website runs smoothly. Whether you need hosting for a small project or a large enterprise, we deliver the infrastructure and support to keep your business online 24/7. Discover the benefits of cloud hosting with Elaster Web and take your business to new heights. For more information, call us at 9877038280. Visit us today!
#CloudHosting#Chandigarh#WebHosting#AffordableHosting#BusinessSolutions#ReliableHosting#ElasterWeb#SecureHosting#ScalableHosting#HostingServices#WebsiteHosting#TechSolutions#DataSecurity#CloudSolutions#FastHosting#24x7Support#HostingExperts#ElasterWebHosting#WebDevelopment#BusinessGrowth
4 notes
·
View notes
Text
Passware Kit Agent
Distributed Password Recovery. Tired of waiting hours to recover lost passwords? Meet Passware Kit Agent – the ultimate solution for lightning-fast, distributed password recovery!

3 notes
·
View notes
Text

Your #business deserves the best #security – and that’s exactly what Vitel Global delivers for your web applications! Here’s why we’re the top choice:
✅ Advanced Protection – Cutting-edge security tools to keep your apps safe. ✅ 24/7 Monitoring– Stay one step ahead with #realtime alerts and monitoring. ✅ Comprehensive Safeguards – Keep your data, customers, and business protected. ✅ Tailored Solutions – Custom security options to fit your unique needs. ✅ Expert Support – Always available to help with any security concerns.
Don’t leave your #webapps unprotected! Tap to learn more: https://www.vitelglobal.com/web-security-360
#WebAppSecurity#CyberProtection#DataSecurity#VitelGlobal#ProtectYourBusiness#webapplications#voipsecurity
6 notes
·
View notes
Text

Protect Your Business from Digital Threats! 🛡️
Cyberattacks can hit anytime — are you prepared? From data breaches to ransomware, legal costs to lost income — one attack can cost you everything.
✅ Cyber Insurance covers: 🔐 Data theft & breaches 💣 Ransomware attacks ⚖️ Legal fees & settlements 📉 Loss of income 💾 Data recovery & more
Secure your business before it’s too late!
👉 Learn more: https://www.investkraft.com/business-insurance/cyber-insurance
#CyberInsurance#OnlineSafety#DigitalProtection#CyberSecurityInsurance#Investkraft#DataSecurity#BusinessInsurance#CyberRisk#SecureYourBusiness
1 note
·
View note
Text

𝗘𝗻𝗵𝗮𝗻𝗰𝗲𝗱 𝗗𝗲𝗰𝗶𝘀𝗶𝗼𝗻-𝗠𝗮𝗸𝗶𝗻𝗴: Provides real-time insights that help in making informed decisions.
𝗖𝗼𝘀𝘁 𝗮𝗻𝗱 𝗧𝗶𝗺𝗲 𝗦𝗮𝘃𝗶𝗻𝗴𝘀: Streamlines processes, reducing operational costs and time spent on manual tasks.
𝗜𝗺𝗽𝗿𝗼𝘃𝗲𝗱 𝗖𝘂𝘀𝘁𝗼𝗺𝗲𝗿 𝗦𝗲𝗿𝘃𝗶𝗰𝗲: Enhances responsiveness and accuracy, leading to better customer satisfaction.
𝗘𝗳𝗳𝗶𝗰𝗶𝗲𝗻𝘁 𝗥𝗲𝗽𝗹𝗲𝗻𝗶𝘀𝗵𝗺𝗲𝗻𝘁 𝗢𝗿𝗱𝗲𝗿𝘀: Automates inventory replenishment, ensuring optimal stock levels.
𝗗𝗮𝘁𝗮 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆: Protects sensitive information with robust security measures.
𝗔𝘂𝘁𝗼𝗺𝗮𝘁𝗶𝗼𝗻 𝗼𝗳 𝗣𝗿𝗼𝗰𝗲𝘀𝘀𝗲𝘀: Reduces manual effort through automated workflows, increasing efficiency.
#ERPSoftware#InventoryManagement#BusinessEfficiency#CostSavings#DataSecurity#CustomerSatisfaction#Automation#DecisionMaking#SupplyChainManagement#Replenishment
2 notes
·
View notes
Text
Optimizing Cybersecurity with Data Analytics
Data analytics can significantly improve threat detection by sifting through vast amounts of data, including network traffic, user behavior, and system logs. By identifying unusual patterns through machine learning algorithms, organizations can automate anomaly detection, thus reducing incident response times.
Furthermore, risk assessment becomes more effective with data analytics, allowing organizations to evaluate their cybersecurity posture. By analyzing vulnerabilities and potential attack vectors, companies can prioritize their resources to address the most critical areas of concern, enhancing their overall security strategy.
In terms of incident response, data analytics helps cybersecurity teams respond more efficiently. It aids in pinpointing the source of a breach, understanding the extent of the damage, and providing insights for effective remediation.
Predictive analytics plays a vital role as well, using historical data to anticipate future threats and proactively strengthen defenses. By identifying trends that may signal emerging threats, organizations can take timely actions to mitigate risks.
Finally, continuous monitoring through data analytics ensures real-time surveillance of systems and networks. This proactive approach is essential for promptly detecting and addressing security breaches, creating a robust security framework that not only safeguards sensitive information but also enhances overall operational resilience against cyber threats. Thus, data analytics enhanced cybersecurity measures are crucial for organizations seeking to stay one step ahead of potential cybercriminals.
#DataAnalytics#Cybersecurity#RiskAssessment#MachineLearning#PredictiveAnalytics#ThreatDetection#IncidentResponse#ContinuousMonitoring#DataSecurity#CyberThreats#OperationalResilience#SecurityStrategy#AnomalyDetection#InformationSecurity#ProactiveDefense
2 notes
·
View notes
Text
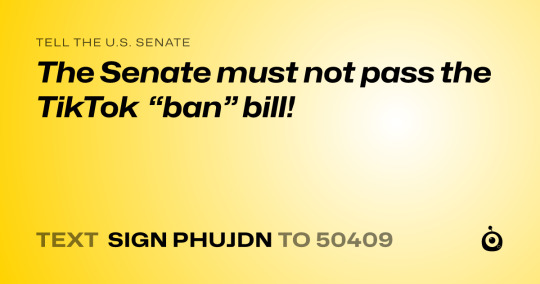
An open letter to the U.S. Senate
The Senate must not pass the TikTok “ban” bill!
2,544 so far! Help us get to 3,000 signers!
I strongly oppose the Protecting Americans from Foreign Adversary Controlled Applications Act, a bill that could ban TikTok in the US. First, it violates our free speech. Second, it targets one social media company over others that have the exact same issues. A better way to safeguard our data would be to create comprehensive consumer-privacy laws that would require apps like TikTok, as well as American companies like Facebook, to face more restrictions on how they handle user data. If the Senator supports this bill they will lose my vote. Thanks.
▶ Created on March 13 by Jess Craven
📱 Text SIGN PHUJDN to 50409
🤯 Liked it? Text FOLLOW JESSCRAVEN101 to 50409
#JESSCRAVEN101#PHUJDN#resistbot#open letter#petition#USSenate#TikTok#FreeSpeech#PrivacyRights#DataProtection#ConsumerPrivacy#SocialMedia#Legislation#Bipartisanship#Technology#DigitalPrivacy#OnlineSafety#InternetFreedom#BillOpposition#PolicyDebate#CivilLiberties#UserData#DataSecurity#TechRegulation#DigitalRights#Cybersecurity#OnlinePrivacy#LegislativeAction#PolicyChange#PublicPolicy
6 notes
·
View notes
Text

We are happy to announce Mr. K Yegneshwara Iyer, Cybersecurity Consultant at Cystech Controls Pvt. Ltd., as a moderator for one of the insightful panel discussions at our upcoming cybersecurity conference!
With over 25 years of experience in IT leadership roles like CIO, CTO, and CISO, he has successfully led innovative IT and cybersecurity strategies for top organizations. He brings deep expertise in transforming IT operations, aligning technology with business goals, and strengthening cybersecurity resilience.
Get ready as he, along with other industry experts, discusses the adoption of SASE solutions for mid-market businesses!
Register now for the conference: https://lnkd.in/gWmzxjcZ
#CTCyberCharcha#CTCyberCharcha2025#CybersecurityEvent#CybersecurityInsights#ITSecurityConference#IITDelhi#ISACA#Cybersecurityconference#hybridevent#Cybersecurity#ThreatDetection#DataSecurity#cybersecurityexpert#Panelist#PanelDiscussion#ChannelTechnologies#CT
1 note
·
View note
Text
"Share and secure your files with MediaFire, the ultimate file storage and sharing platform."

2 notes
·
View notes
Text
The Ethics of Political Analytics
📊🗳️ Political analytics is changing the game, but it's essential to address the ethical issues that come with it. From #PrivacyConcerns to the risk of #Manipulation, we need to ensure transparency and accountability in how data is used in politics. Let's strive for a fair and inclusive democratic process! 🌍✊
#leadpac#PoliticalAnalytics#DataEthics#PrivacyConcerns#InformedConsent#VoterData#DataSecurity#Manipulation#Misinformation#DemocraticIntegrity#EquityAndFairness#Accountability#EthicalGuidelines#TelanganaPolitics#PoliticalAnalysisInHyderabad#Telangana#Politics#PoliticsInHyderabad#indian politics#electionforecasting#business#india#andhrapradesh
2 notes
·
View notes
Text
Discover how Android spy apps can help you track WhatsApp messages safely and responsibly. Learn about the benefits, features, and ethical considerations in this guide.
1 note
·
View note
Text

Guard Your Cloud! Business communication security starts with proactive protection. This Cybersecurity Awareness Month, learn how Vitel Global helps you stay protected while staying connected.
Read our latest blog to discover how a secure cloud phone system keeps your business safe: https://www.vitelglobal.com/blog/significance-of-cybersecurity-in-cloud-phone-system/
#cybersecurity#cybersecurityawareness#cloud#businesssecurity#cloud communications#GuardYourcloud#Business#cloudcommunications#hacking#technology#cybercrime#tech#cyberattack#malware#data privacy#datasecurity#dataprotection
6 notes
·
View notes