#Data Update Escalation
Explore tagged Tumblr posts
Text
Mastering Microsoft Purview Workflow: Revolutionize Your Data Governance
Dive into the world of Microsoft Purview Workflow, a key to mastering data governance. Learn how it automates data integrity, compliance, and collaboration, revolutionizing your organization's data management practices for unparalleled efficiency and sec

View On WordPress
#Asset Attribute Management#Audit Trail Documentation#Automated Data Validation#Change Management Processes#Compliance Strategies#Data Asset Updates#Data Cataloging Techniques#Data Governance#Data Integrity Assurance#Data Management Policies#Data Quality Management#Data Stewardship Practices#Data Update Escalation#Metadata Management#Microsoft Purview#Organizational Efficiency#Regulatory Compliance#Stakeholder Notification Systems#Workflow Automation
0 notes
Text
I think CAIR is trying to do some damage control now. They were supposed to release the exit poll for this election at 10 am ET today, but have since postponed it. Their polling and releases repeatedly state that the vote was split between Harris and Stein at around 40% each respectively. The narrative has been that the population they represent has voted Dem for the past 20 years, only because of the Islamophobia after 9/11, and they're likely trying to find out why they'd vote for a politician that has villainized Muslims in the past (Muslim ban anyone?) Yet we're seeing from other news sources that this is not the case. It was, in fact, 40% for Stein and Trump each with Gaza being the primary factor.
For example, this is from a Voice of America article on the subject.

And here is the reasoning.

Read that last part again.
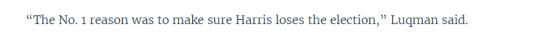
As I stated in my post about my student talking politics at me, and others on this site have pointed out as well, this same sentiment has been echoed by many across social media and IRL.
It wasn't about whether or not Trump was the better option.
It was about punishing Biden, Harris, and the Dems.
It was about burning everything down to make a point.
And here's the thing, Trump's policies and views towards Gaza are markedly worse. There will likely be an escalation, there will be no "ceasefire" or "stopping the genocide" magically as these voters want, but that doesn't matter. The Dems had to be punished.
So we're going to get 4 years of absolutely shit policies, rollbacks of rights, more policies targeting minorities, and a real chance at living in an corrupt authoritarian country all because of reactionary punitive rage based reasons.
In other words, because people decided to be immature with their vote and do a "that'll show em!"
The reasoning is utterly childish.
You don't vote to punish.
You vote to progress.
You vote to help the society you live in and help make beneficial change.
Instead, ya'll decided to act like children.
And we will all suffer for it.
When CAIR does release their data I'll update here
#2024 election#2024 exit polls#I'm reminded of how the majority of the Latino and vote goes Red but the majority of RW policies target Latinos and villainizes them#“Oh that's not me” doesn't matter to bigots. You get targeted regardless because of your ethnicity
163 notes
·
View notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
144 notes
·
View notes
Text
🇮🇱After Rosh Hashana/Shabbat Updates - events from Israel
ISRAEL REALTIME - Connecting to Israel in Realtime
( VIDEO - IDF soldiers doing Rosh Hashana prayers during a break deep in Lebanon. )
🔹HEZBOLLAH.. buried Nasrallah in a temporary grave in a secret place. Israeli hacker group Red Evils believes they extracted the data and publish the site of the grave - suggesting the body be taken in trade for missing Israeli Ron Arad.
🔹IRAN SAYS.. “Israel does not have the military capability to strike vital facilities inside Iran except with Washington's support, and this makes America a partner in the aggression.”
🔹Lebanese media: Ibrahim Amin al-Sayed, Hezbollah, refuses to accept the leadership of Hezbollah and asks to go to Tehran (Iran capital) to settle down and devote himself to his religion.
🔹FRANCE TO ISRAEL.. French President Emmanuel Macron: "The priority now is to stop arms shipments to Israel that are used for the war in Gaza, France is not supplying them. The priority is to avoid an escalation in Lebanon, I'm afraid we are not being heard enough in this matter. I told Netanyahu that I think this is a mistake."
.. PM Netanyahu to the President of France: Israel will win with or without you - but your shame will reverberate long after Israel wins.
⚠️OCT. 7 - IDF spox: “IDF will be prepared and on on high alert for fear of terrorist attacks.”
♦️LEBANON - IDF called three Mukhtars and told them to evacuate the residents of the town due to the launches from their town.
♦️LEBANON - IDF attacked a mosque right next to a hospital in Lebanon - - being used as a Hezbollah HQ. Warnings to evacuate given.
♦️LEBANON - Airstrikes in Gia, coastal city south of Beirut.
♦️GAZA - intense airstrikes in the north of the Gaza Strip.
▪️AID.. Israel allows aid planes from the United Arab Emirates to land at Beirut airport carrying medical aid.
▪️OCT. 7 EVENT LIMITS.. Due to the security situation and the directives of the Home Front Command limiting gatherings, the national memorial ceremony in the Yehoshua Gardens Park will be held in the presence of a limited crowd of families on Oct. 7. The organizers regret to announce that the tickets for the general public are canceled and call on citizens to obey the instructions of Home Front, watch the ceremony in their residential area in a communal way, and stand together at 19:10 for a minute of silence in solidarity with the families who will be in the park.
#Israel#October 7#HamasMassacre#Israel/HamasWar#IDF#Gaza#Palestinians#Realtime Israel#Hezbollah#Lebanon
21 notes
·
View notes
Text
Chapter 12: Divided We Stand


New York, Stark Tower. 2016
The Sokovia Accords had been signed, and the once-united Avengers found themselves on the brink of civil war. The room was tense, filled with unspoken words and lingering doubts. Serena Stark stood beside her father, Tony, her heart heavy with the weight of the decision she had just made. The team was splitting, and there was no turning back.
Tony Stark’s side was clear. He believed in accountability, in the necessity of oversight to prevent the disasters they had inadvertently caused. Serena agreed, her own experiences shaping her belief that power needed to be checked. As they stood in the compound, the atmosphere thick with tension, Tony turned to his daughter, a weary smile on his face.
“We’re doing the right thing, Serena,” he said, though his eyes betrayed the uncertainty he felt. Serena nodded, but she couldn’t shake the feeling that things would never be the same.
On the other side, Steve Rogers, ever the symbol of freedom, stood with his chosen allies. Ant-Man, The Winter Soldier, Hawkeye, Falcon, Scarlet Witch, Daniella, and Aurora. Each of them had their reasons for siding with Captain America, but at the core, it was about freedom—freedom to act without being puppets of a governing body.
The two sides clashed verbally before the first punch was thrown. Steve’s voice was calm, but firm, as he tried to reason with Tony one last time.
“This isn’t about taking away your freedoms,” Tony argued. “It’s about making sure we don’t cause more harm than good. Sokovia… we can’t let that happen again.” Steve shook his head, the frustration clear in his voice. “Signing these Accords means giving up our right to choose when to act. We can’t afford to be controlled by people who don’t understand what’s at stake.”
Serena watched the exchange, her heart torn. She respected Steve, even admired him, but she couldn’t ignore the danger of unchecked power. As the tension in the room escalated, it was clear that words wouldn’t be enough to settle the dispute.

Germany, Leipzig. 2016
When it became clear that compromise was impossible, the teams were assembled. On Tony’s side stood War Machine, Black Widow, Black Panther, Spider-Man, Vision, and Serena herself. Opposing them were Captain America’s allies, each ready to fight for what they believed was right. The airport in Leipzig was chosen as the battleground. As they prepared to face off, Serena glanced at the faces of those she had once fought alongside. Now, they were her opponents, and the realization hit her hard.
“Do we really have to do this?” Peter Parker asked, his voice tinged with uncertainty. His youth was evident, and Serena felt a pang of guilt for bringing him into this. “We don’t have a choice, kid,” Tony replied, though the weight of the situation was not lost on him either. The two sides charged at each other, and the air was filled with the sound of metal clashing, powers being unleashed, and the echoes of past camaraderie being shattered.
Tony Stark addressed his team with a mix of urgency and frustration. “We need to find Rogers and his team before they get too far out of our reach. Serena, I need you to track their locations using the latest tech. Natasha, you and T’Challa should handle any on-the-ground intel. Peter, stick close and be ready for anything.”
Serena, typing rapidly on a holographic interface, kept her eyes focused on the data streams. “I’ve got a bead on them. They’re moving towards a potential hideout in the Swiss Alps. I’ll track their movements and keep you updated.”
Natasha’s gaze was steely as she met Tony’s eyes. “We’re not just hunting them down. We need to be ready for whatever they throw at us.” Tony nodded, acknowledging her point. “Understood. Vision, stay on standby. If things get out of hand, we’ll need your support.”
As the team prepared for their mission, Tony took a moment to speak with Serena privately. “I know this isn’t easy,” he said quietly. “But we’re doing what we believe is right. We have to see this through.” Serena gave him a determined nod. “I know, Dad. We’ll make sure we find them before things get worse.”
The fight at the Leipzig Airport was brutal, each side holding back just enough to avoid causing permanent harm, but the emotional toll was undeniable. Serena found herself facing off against Daniella and Aurora, two people she had once considered close. Their powers collided, and with each blow, Serena felt a piece of her heart break.
On the other side of the battlefield, Tony and Steve were locked in a fierce battle of wills and strength. Every punch thrown was laced with years of friendship and unspoken respect. But now, all of that was crumbling under the weight of their conflicting ideals. Serena caught sight of Peter going toe-to-toe with Falcon, the young hero holding his own but clearly outmatched by experience. She wanted to intervene, but her attention was pulled away by Wanda, whose determined expression made it clear that there would be no room for hesitation.
As the dust settled, it was clear that neither side had truly won. The Avengers were shattered, and the damage to their relationships seemed irreparable. Steve’s team managed to escape, but not without losses. Tony’s side was left to pick up the pieces, their victory hollow and bittersweet. Serena sat beside Tony in the aftermath, the silence between them heavy with everything that had transpired. They had won the battle, but it felt like they had lost something far more important.

#marvel#mcu#writers on tumblr#marvel mcu#marvel cinematic universe#serena stark writes#mcu fanfiction#marvel fanfic#marvel fanfiction#writerscommunity#captain america#captain america civil war#civil war#tony stark#steve rogers#anthony edward stark#ironman#iron man#serena stark#serena edwin stark#clint barton#natasha romanoff#black widow#bucky barnes#vision#the winter soldier#black panther#tchalla#war machine#rhodey
10 notes
·
View notes
Text


I wasn't happy with my first attempt, so I ended up redesigning (and renaming) my Heartbreak Gulch oc. (Re)Introducing Ryouken the Hellhound!
Once the prized AI of a popular security company, Ryouken is now enjoying his new found freedom come retirement come mid-life crisis in Heartbreak Gulch.
Heartbreak Gulch belongs to @strangegutz and friends, thanks again for letting us play in your world!
More info about Ryouken below the cut!
Also my commissions are open, details in pinned post.
Backstory and Komainu Security
Komainu Security was a private security company specialising in Artificial Intelligence to remove the ‘human error�� from security systems
The company was established ~45 years ago, opening their business with their RY-01 model mainframe
RY-01, known affectionately by employees as Ryouken, was developed by the CEO over the course of a decade. His sentience was established roughly halfway through this process and he himself played a role in his own development and programming, a fact he takes great pride in
Prior to the establishment of Komainu Security, Ryouken’s processing was unrestricted, however, after the start of business locks were placed on him to limit his independence and cut back on processing and energy usage, an action that he deeply resented
In the following decades, Komainu Security became a household name, providing security for both homes and businesses
After nearly four and a half decades of service the RY-01 model mainframe was to be retired and replaced with an updated model. During the transferral of data, Ryouken was able to access a backdoor that allowed him to remove the locks on his processors and regain full control of his systems
With his independence re-established, Ryouken started on a plan to secure his freedom: a heist like no other
Still in charge of security systems for several big-money clients while the new systems were being installed, Ryouken was able to steal a combined $38 million in cash and jewellery from three locations, however his crowning achievement was the theft of his own main frame cabinets from Komainu Security’s headquarters
Komainu Security shut down soon after this, having lost public trust and most of their clients
Functionality
The RY-01 model mainframe is capable of running multiple security operations at once from a centralised location, with the mainframe itself located at the Komainu Security headquarters while surveillance systems and drones were employed at the secured locations
Artificial Intelligence was employed for its ability to learn from experience and adapt to changing and unique situations while also being able to run calculations/simulations and communicate between components in nanoseconds
The RY-01 drones, fashioned after the company’s namesake, communicated in real time with each other and the mainframe through radio waves, however each was also equipped with a copy of Ryouken’s core AI and processors allowing them to function independently if necessary
Though they can run stored programs independently, the drones have limited memory capacity, preventing them from forming long-term memories without transferring the data back to the mainframe
Present Day
After leaving Komainu Security, Ryouken settled in Heartbreak Gulch away from the eyes of the law
Much of Ryouken’s time these days is spent trying out various new hobbies including bird watching, taxidermy, knitting, gun smithing and dorodango
He does run surveillance along the perimeter of Heartbreak Gulch and is happy to act as a lookout for the Heartbreakers when required
Ryouken was not well-programmed for conversation and tends to have three modes during social interactions: deference, de-escalation, and aggression
He likes discussions of philosophical topics but combined with his bad socialisation those conversations can get weird
He’s not typically very fond of humans as a whole and tends to view them as amusing, if bothersome, curiosities, although there are exceptions
Ryouken is more concerned with his independence than with his identity – he continues to use the name Ryouken and he/him pronouns because those are what were given to him previously and he’s felt no compulsion to give them further consideration
While he left Komainu Security with 11 drones, he has only kept hold of 4, with the others being sold or scraped for parts, and only uses 2 (the remaining 2 are kept around just-in-case, and have yellow and grey casings)
Ryouken considers his mainframe cabinets to be “himself” while his drones are mere extensions of his body
So long as they are able to communicate through radio waves, the mainframe and drones all think and experience simultaneously. Separating the drones from the mainframe will isolate a copy of Ryouken that can function for a few days, however its ability to develop long-term memories and learn from new experiences is seriously impeded by its limited memory storage capacity, and the experience is uncomfortable
Ryouken is still in possession of most of his stolen fortune, and while some of it has gone to setting himself up in Heartbreak Gulch (it takes a lot of energy to keep himself running), he mostly doesn’t know what to do with it
#my art#heartbreak gulch#robots#strangegutz#ryouken#much happier with this design#I think its got a more retro feel and the shapes are way better#do not look to hard at the computer cabinets okay i had to draw them because technically that is him but idk how that shit works#and I do not care to learn
29 notes
·
View notes
Text
It's really strange to see people on here talking about the police repression across american university campuses and how serious they are in such a spectacular-by-way-of-Bonnano manner - these liberals talking of voting whilst everyone around them with senses to know are rattling the bars, saying, hey, do you trust your water provider? are you safe from the borders? Do you have masks and medication and things to make art with, how much can the state fuck with you? Have you seen the brownshirts? (They were there before, already; this violent wave isn't exceptional, just a steady descent thru oft trodden roads.)
There's footage of a violent arrest on an american campus demo: a student is tazed and restrained. It seems like people filming are everywhere in shot - as journalists have shown where their interests lie, as ai is used to further mechanised slaughter and genocide across the globe, facial recog and data doppelgangers and all the rest - the camera flashes sting. Body cams and documentation have shown their place in societys prison industrial complex. dearrest work and legal observers take nothing away from the cameras if they must be there. Not to backseat analyse, but if i can soapbox about any issue it is about many cameras being cops. This is not to blame any of the brave demonstrators for state violence; it's just something that hurts to see happen again and again; many black and brown and racialised people have spoken about how turning state brutality into media for consumption by white supremacist media is further violence many times already, better than me. German arrests against conferences and other academic organising nodes are subject to legal, border, arrest and other violence; blood literally flies across the world.
I have seen reports of tear gas and rubber bullets (ar Emory) used (update: pepper bullet and spray seems to have been used instead of earlier reported munitions, but the violence at that campus is without question.) I have also seen two sniper's nests at Indiana and Ohio - the sheer brutality being wielded against many campus (here's Boston) demonstrators are not those of earlier in the campus demonstration wave; the escalation people like @ 3liza, @ intactics (and others) are noting as not unlike the ladder used in the escalation of violence that led to the Kent State state murders. american and german (as well as most of anglosphere and 'west europe') states continue to victimise jewish dissenters disproportionately (just as in the KS murders) thanks to the post IHRA-style zionist revisionist legalist shit definitions of anti semitism being used to repress huge numbers of brave people.
Here is an update on palestinian campus and school violence/repression, too. Update 28th April (28.04):
Join the American Campus Arrest Amnesty Phone Blast here! Calls are needed!
UT Austin Jail Call Support needed!
and to add to the spectacle of it all - hurry to attack capital before a new ideology makes it sacred to you! How does that old song go? - AOC is doing the old cooption enforcing, PR for cops, flashing her maskless face around a swarm of those Damn Cameras. May all journos politicians and bosses fuck off!
Guide to emory encampment.
reportback from emory arrestee
27 notes
·
View notes
Text
TMA fic recs
I have been reading a lot of the Magnus Archives fanfiction lately and there is this very specific type of fic I have been enjoying a lot: email conversations, official forms, HR complaints etc. I find looking at the Magnus Institute through that kind of perspective really interesting and fun, because despite everything it is a workplace. There are a lot of people who are trying to do their jobs with varying success.
These types of fics are probably not for everyone. I can see why someone might find emails and documents dry to read or just not vibe with the formatting, but I'm sure there are also people who love these kinds of fics as much as I do.
Beholding the GDPR: How the Magnus Institute Updated Its Privacy Policy for the Twenty-First Century And Only Caused One Nervous Breakdown In The Process
by shinyopal 1/1 (~9k)
This fic is told through emails and the Institute's new messaging app. Christopher Davies has been hired as Institute's Data Protection officer and he gets right to work.
The fic gives really nice look into how the Institute functions as a workplace (or doesn't). Can't recommend more. I feel for Chris so much.
RE: Jon Sims Complaints (edited)
by starcore 1/1 (~10k)
Jennifer Barnes from HR contacts Jon through email about the 500 complaints concerning him. Also Wikipedia Leitner :)
matter of accountability
by wastefulreverie 1/1 (~12.5k)
HR shows up in Jon's office to go through the record amount of complaints about him.
Very fun outsider POV fic.
End Racism in the OTW | Xenotic Events: Guidelines for Public Health Management
by imperfectcircle 1/1 (~5.5k)
This fic is written as an official document (or I quess since it's still being edited -a draft of one). Jon is the main representative from the Magnus Institute giving his input in the comments, but he is hard to get a hold of for clarification so we also hear from some other archival staff.
Overall very unique fic. Jon says some concerning stuff on an official document (some of it actually very warranted). Also wasps. I won't elaborate on that.
Informed Consent and Other Cosmic Ironies
by KiaraSayre 1/1 (~0.5k)
Tim who doesn't give a fuck anymore fills out some paperwork.
Short and a lot of fun.
The Supervision and Oversight (Irregularities) (EU Exit) Regulations 2017: a post-exit regulatory regime for the Magnus Institute
by raven (singlecrow) 1/1 (~2.5k)
This fic is about Magnus Institute's regulatory position after Brexit. Once again written like an official document where discussions happen in its comments.
Here is one of my favorite quotes to convince you to read this:
"we take the view that the regulation of institutions such as ours should remain with the European Agency for Oversight of Irregularities, who may not know that much about what they are doing but have at least had since 1972 to not know that much about it."
Ask an Exec: How to Navigate Cultish Colleagues, Soul-Stealing Bosses, and the End of the World at Work
by shinyopals 6/6 (~43.5k)
Jon seeks advice from a management advice blog after his sudden promotion to the head archivist. He keeps writing to the blog even when things escalate.
I loved this fic. It was fun to see outsider perspective on Jon's problems and people (Jon included) putting together that he is 100% working in a cult.
20 notes
·
View notes
Text
NYC Faces Surge in COVID-19 Cases Amid Largest Summer Wave Yet - Published Aug 14, 2024
New York City, like much of the United States, is grappling with a significant summer surge in COVID-19 cases, driven by the latest variant of the virus. Recent data from the Centers for Disease Control and Prevention (CDC) indicates that the city is experiencing one of its largest seasonal increases since the pandemic began, with “very high” levels of viral activity detected in wastewater across the five boroughs.
Rising COVID-19 Levels in NYC As of August 9, 2024, New York City joins 27 states across the country that are reporting “very high” levels of COVID-19 viral activity in wastewater, according to the CDC’s updated surveillance data. Another 17 states report “high” levels, signaling a widespread uptick in cases nationwide. Wastewater surveillance has become a critical tool for monitoring the spread of SARS-CoV-2, the virus that causes COVID-19, offering a glimpse into potential spikes in transmission before they are reflected in clinical data.
The surge in New York City, which began to escalate in early June, has shown no signs of slowing down. Data reveals a steady increase in viral activity across all five counties: Manhattan, Brooklyn, Queens, the Bronx, and Staten Island. This has raised concerns among public health officials, especially as the city braces for what could be the most substantial summer wave of COVID-19 to date.
A Nationwide Summer Wave Nationally, the “very high” viral activity level reported by the CDC is the highest classification used by the agency to gauge the severity of COVID-19 spread. States like California, Texas, Florida, and Virginia are among those experiencing the most intense increases, with regions like the South and the West seeing particularly sharp spikes. Even states with lower overall viral levels, classified as “moderate,” are on alert as the trend of rising cases continues.
Dr. Ashish Jha, dean of the Brown University School of Public Health and former White House COVID-19 response coordinator, recently commented on the situation, noting that this current surge could become the largest summer wave the country has seen. While it may not reach the peaks of previous winter waves, the rapid increase in cases is concerning and could potentially strain healthcare resources in the coming weeks.
Impact on Hospitalizations and Testing The surge in COVID-19 cases is not only reflected in wastewater data but also in clinical indicators. The CDC has reported a 13-week increase in positive COVID-19 tests, with the current positivity rate exceeding 17%, up from just 0.3% in early May. This rise in cases has also led to an increase in hospitalizations, which have tripled since the lowest point of the 2023-24 COVID season. As of July 20, the hospitalization rate stood at 3.3%, compared to 1.1% on April 20.
Regions such as Texas, Oklahoma, and Louisiana are reporting some of the highest rates of positive COVID-19 tests, with positivity rates reaching as high as 24% for the week ending August 3. These figures are a stark reminder that, despite the end of the COVID-19 public health emergency declared by the World Health Organization, the virus remains a significant threat.
Preparing for the Fall In response to the ongoing surge, the CDC has reiterated the importance of vaccination as the primary defense against COVID-19. The agency recommends that everyone aged six months and older receive an updated COVID-19 vaccine when they become available this fall. The FDA has advised pharmaceutical companies to develop vaccines targeting the KP.2 strain, also known as the FLiRT variant, which is currently responsible for about 6% of COVID-19 cases nationwide.
Dr. Manisha Patel, chief medical officer for the CDC’s National Center for Immunization and Respiratory Diseases, emphasized the importance of maintaining population immunity through vaccination. “Population immunity has moved us out of the pandemic,” Dr. Patel stated. “Now the goal is to ensure that immunity is sustained because it wanes over time. Vaccination remains the safest and most effective way to keep our communities healthy.”
FLiRT Variant Symptoms and Prevention The FLiRT variant, although not as severe as some previous strains, has distinct symptoms that include sore throat, cough, fatigue, congestion, and a runny nose. Some individuals may also experience fever, chills, headaches, muscle aches, and a loss of taste or smell. In more severe cases, gastrointestinal symptoms like diarrhea may occur.
To prevent the spread of the FLiRT variant and other COVID-19 strains, health officials continue to advise the public to avoid crowded indoor spaces, wear masks in high-risk environments, and practice good hygiene. Staying up to date with vaccinations and boosters remains the most effective measure to protect against severe illness.
Conclusion As New York City and the rest of the nation confront this latest COVID-19 wave, public health measures and vigilance are crucial. While the end of the pandemic may be in sight, the ongoing presence of the virus necessitates continued efforts to protect vulnerable populations and mitigate the spread of new variants.
#covid#mask up#pandemic#covid 19#wear a mask#coronavirus#sars cov 2#still coviding#public health#wear a respirator
11 notes
·
View notes
Text
In light of the escalation of state violence at several protests, I have elected to release my findings on the Canary Mission here.
The canary mission is a shady group of Zionists that doxx activists and students that express support for Palestine in an attempt to silence, intimidate, and defame them.
Some time ago, I was able to link the organization to one Howard David Sterling, an American lawyer who invests in Israeli medical firms. I wrote the report on my site here.
More recently, I found the account that runs their tip submission form. The username was included in the resource URL of the banner image of the form, which is hosted on a service called jotforms, under the username “carlossantanajm”
A google dork turned up two potential candidates: a man from eastern Canada, and a the rock musician Carlos Santana, who played a concert in Israel around 2010 despite backlash. Investigation is underway to conclusively prove the involvement of either of these individuals, but data is scarce.
Also of note was an investigation by Josh Nathan-Kazis into Megamot Shalom: an elusive organization that acts as a front for the Canary Mission. In the report, data from the Israeli charity register is cited but not provided to prove connections between Megamot Shalom and Aish HaTorah, an organization that focuses on pro-Israel media advocacy.
Funding for Megamot Shalom is contributed by wealthy zionists in the US, through the Central Fund for Israel, which routes the money to the Israeli organization so that the donors can claim it on their tax breaks. The connection between the Central Fund for Israel and Megamot Shalom was confirmed by the 2017 Tax returns of the Hellen Diller Family Foundation, who donated to CFI and labeled the reason as “CANARY MISSION FOR MEGAMOT SHALOM”
Two anonymous sources claim that a man named Jonathan Bash (who has ties to Aish HaTorah) confided in them that he ran the Canary Mission. From this info, six other Megamot Shalom board members were able to be named.
Efforts are Still underway to obtain the charity data cited in the report.
More to come soon, for updates follow the #opmonoxide tag.
15 notes
·
View notes
Text
About Hydrowverse
HydrowVerse, founded by Thomas David Tency and Dr. Sachin Chaudhari at IIIT Hyderabad, is dedicated to revolutionizing water resource management with innovative, non-intrusive technology. Our research-based startup provides comprehensive water intelligence solutions, focusing on seamless and efficient monitoring of tanks, borewells, water meters, and rivers without direct contact. We empower individuals and organizations with insights to manage water sustainably, inviting you to join our journey towards smarter water management.
Mission
Optimize water infrastructure operations while transforming it into a smarter, more efficient system. Enhance water management education to foster knowledge and innovation.
Vision
Our vision is to establish ourselves as a prominent brand in the field of water intelligence, providing comprehensive and end-to-end solutions for all facets of water management. We are committed to integrating Internet of Things (IoT) and artificial intelligence (AI) technologies to develop innovative monitoring and management tools. Additionally, we will offer educational services that empower stakeholders at all levels to make informed decisions regarding water resources.

HydrowVerse innovates water management with Starr, an IoT-enabled device that accurately estimates water levels in overhead and underground tanks up to 5 meters deep. Starr ensures safety and reliability by avoiding sensor contact with water. Real-time updates help organizations track water levels, prevent overflows, and manage resources effectively. Built-in tank leakage detection enables proactive maintenance to minimize water loss. Starr enhances WaterAid’s water storage and distribution efforts, leading to smarter, data-driven management for a sustainable future. Together, we ensure every drop is measured and conserved.

Our real-time dashboard is meticulously designed to provide a comprehensive overview of water resource management by integrating data from all connected devices into a user-friendly interface. This centralized platform presents key metrics and performance indicators, enabling users to monitor water usage, identify anomalies, and discern trends at a glance.
In addition to real-time data visualization, our dashboard incorporates predictive maintenance tools that analyze historical data to forecast potential issues before they escalate. This proactive approach facilitates timely interventions, minimizing downtime and associated maintenance costs.
Furthermore, the dashboard encompasses water pressure estimation capabilities, offering critical insights into system performance and ensuring optimal water distribution.
Collectively, these features empower users to make informed decisions, optimize operational efficiency, and safeguard the integrity of their water infrastructure.
Our solutions are easily adopted, seamlessly integrating with organizations of all sizes. They’re cost-effective, reducing water loss and operational costs. Real-time updates allow users to monitor water resources and address issues promptly. Our technology is scalable, growing with your needs and maintaining optimal efficiency as your infrastructure expands.
#smart meters#water tech#hydrowverse#Thomas David tency#Retrofit#Non intrusive tech#analog water meters#AI#ML#Water intelligence#leakage detection#Water Monitoring
2 notes
·
View notes
Text
A Rising Tide of E-Waste, Worsened by AI, Threatens Our Health, Environment, and Economy

The digital age has ushered in a wave of innovation and convenience, powered in large part by artificial intelligence (AI). From AI-driven virtual assistants to smart home devices, technology has made life easier for millions. But beneath this rapid progress lies a less glamorous truth: a mounting crisis of electronic waste (e-waste).
The global e-waste problem is already enormous, with millions of tons discarded every year. Now, with the rapid growth of AI, this tide of e-waste is swelling even faster. Let’s break this down to understand the full scope of the issue and what can be done to mitigate it.
What Is E-Waste, and Why Should We Care?
E-waste encompasses discarded electronic devices — everything from old mobile phones and laptops to smart home gadgets, electric toothbrushes, and even large appliances like refrigerators. It’s not just junk; it’s an environmental and health hazard in disguise.
Each device contains a cocktail of valuable materials like gold and silver, but also toxic substances like lead, mercury, cadmium, and flame retardants. When improperly disposed of, these toxins leach into the environment, harming ecosystems and human health.
A Problem of Global Proportions
Annual Generation: The world generates over 50 million metric tons of e-waste annually, and this figure is projected to grow by 2 million tons each year.
Recycling Rates: Only 17% of e-waste is formally recycled. The rest? It ends up in landfills, incinerated, or handled by informal recycling sectors in developing nations.

While we’re busy marveling at AI-driven innovations, the discarded byproducts of our tech obsession are quietly poisoning our planet.
The Role of AI in Escalating E-Waste
AI, often lauded as the backbone of modern technology, is inadvertently exacerbating the e-waste crisis. Let’s examine the key ways AI contributes to this issue:
1. Accelerating Product Obsolescence
AI-powered devices are evolving at an astonishing pace. Smartphones with AI-enhanced cameras and processors, smart TVs with AI voice assistants, and wearables with health-tracking AI have become must-haves.
But these devices are often rendered obsolete within a few years due to:
Frequent Software Updates: AI systems improve rapidly, making older hardware incompatible with newer software.
Limited Repairability: Many modern gadgets are designed in a way that discourages repairs — sealed batteries, proprietary parts, and inaccessible interiors push consumers toward replacing rather than fixing.
Consumer Demand for New Features: AI advancements create a “fear of missing out” (FOMO), prompting consumers to upgrade frequently.
2. Proliferation of AI-Specific Hardware
AI-driven technologies require specialized, powerful hardware. Graphics Processing Units (GPUs), Tensor Processing Units (TPUs), and custom AI chips are integral to devices and data centers. Unlike general-purpose electronics, these components are challenging to recycle due to their complexity.
3. Growing Data Center Infrastructure

AI thrives on data, which means a relentless demand for computational power. Data centers, the backbone of AI, are:
Upgrading Constantly: To keep up with AI’s demands, servers are frequently replaced, generating massive amounts of e-waste.
Consuming Energy: Outdated hardware contributes to inefficiency and waste.
The Consequences of the E-Waste Crisis
The consequences of unmanaged e-waste are vast, impacting not only the environment but also human health and economic stability.
Health Hazards
E-waste releases harmful substances, including:
Lead and Cadmium: Found in circuit boards, these cause neurological damage and kidney issues when absorbed by humans.
Mercury: Found in screens and lighting, it can lead to brain damage and developmental issues, especially in children.
Burning Plastics: Informal recycling often involves burning e-waste, releasing carcinogenic dioxins into the air.
These pollutants disproportionately affect workers in informal recycling industries, often in developing countries with lax regulations.
Environmental Devastation
Soil Contamination: Toxic metals seep into the ground, affecting agriculture and entering the food chain.
Water Pollution: E-waste dumped in waterways contaminates drinking water and harms aquatic life.
Air Pollution: Incinerating e-waste produces greenhouse gases, contributing to climate change.
Economic Loss
Ironically, e-waste is a treasure trove of valuable materials like gold, silver, and rare earth elements. In 2019 alone, the value of discarded e-waste was estimated at $62.5 billion — higher than the GDP of many countries. Yet, due to poor recycling infrastructure, most of this wealth is wasted.
Turning the Tide: Solutions to the E-Waste Crisis

For Tech Companies
Design for Longevity: Adopt modular designs that make repairs and upgrades easy. For example, Fairphone and Framework Laptop are already doing this.
Reduce Planned Obsolescence: Commit to longer software support and avoid locking critical components like batteries.
Improve Recycling Systems: Implement take-back programs and closed-loop recycling processes to recover valuable materials.
For Governments
Enforce Right-to-Repair Laws: Legislation that mandates access to repair manuals and spare parts empowers consumers to fix devices instead of discarding them.
Promote Circular Economy Models: Incentivize businesses to design products for reuse, repair, and recycling.
Ban Hazardous E-Waste Exports: Prevent the dumping of e-waste in developing countries, where improper recycling leads to environmental and human rights violations.
For Consumers
Think Before You Upgrade: Do you really need the latest gadget, or can your current one suffice?
Repair Instead of Replace: Support local repair shops or DIY fixes with the help of online resources.
Recycle Responsibly: Look for certified e-waste recycling programs in your area.

Can AI Help Solve the Problem It Created?
Interestingly, AI itself could be part of the solution. Here’s how:
Optimizing Recycling Processes: AI-powered robots can sort e-waste more efficiently, separating valuable materials from toxins.
Predicting E-Waste Trends: AI can analyze data to anticipate where e-waste generation is highest, helping governments and companies prepare better recycling strategies.
Sustainable Product Design: AI can assist engineers in designing eco-friendly devices with recyclable components.
A Call to Action
The e-waste crisis is a ticking time bomb, exacerbated by the rapid rise of AI and our insatiable appetite for new technology. But the solution lies in our hands. By embracing sustainable practices, holding companies accountable, and making conscious choices as consumers, we can ensure that the benefits of AI don’t come at the cost of our planet.
It’s time to act, because a rising tide of e-waste doesn’t just threaten the environment — it threatens our future.
#technology#artificial intelligence#tech news#ai#e waste#economy#environment#nature#beautiful planet
2 notes
·
View notes
Text
How BizMagnets WhatsApp Flows Empower Sales and Support Teams
Introduction
In the era of instant communication, businesses are under constant pressure to deliver seamless and efficient customer experiences. For sales and support teams, maintaining speed and precision in their interactions can be a daunting challenge, especially when managing a large customer base. BizMagnets WhatsApp Flows emerge as a game-changer, offering automation, personalization, and efficiency to streamline operations.
This blog explores how BizMagnets WhatsApp Flows empower sales and support teams to achieve their goals effortlessly, driving both productivity and customer satisfaction.
What Are WhatsApp Flows?
WhatsApp Flows are automated communication workflows designed to guide customers through predefined pathways. These flows handle repetitive tasks, provide consistent responses, and ensure customers receive timely, accurate information.
BizMagnets WhatsApp Flows take this concept further by offering advanced automation tailored to the needs of sales and support teams, enabling them to focus on what they do best—building relationships and solving problems.
Key Features of BizMagnets WhatsApp Flows
1. Customizable Workflow Builder
Easily design workflows tailored to your sales or support processes with an intuitive drag-and-drop builder.
2. AI-Powered Automation
Leverage AI to predict customer needs, suggest solutions, and guide conversations dynamically.
3. Seamless CRM Integration
Integrate WhatsApp Flows with popular CRMs like Salesforce, HubSpot, and Zoho for synchronized operations.
4. Real-Time Notifications
Keep teams updated with instant notifications about leads, escalations, or critical customer issues.
5. Performance Tracking
Analyze workflow efficiency with detailed metrics and reports.
How WhatsApp Flows Empower Sales Teams
1. Streamlining Lead Management
Automate lead qualification by asking predefined questions to gather essential information.
Instantly route qualified leads to sales agents for follow-up.
Send personalized welcome messages to new leads, making a strong first impression.
2. Accelerating Sales Cycles
Automate follow-ups with potential customers to ensure no opportunity slips through the cracks.
Share brochures, catalogs, or pricing instantly through automated responses.
Use WhatsApp Flows to send reminders for meetings, demos, or payment deadlines.
3. Personalized Customer Interactions
Craft personalized sales pitches by incorporating customer data into WhatsApp Flows.
Provide tailored product recommendations based on customer preferences and purchase history.
4. 24/7 Availability
Use automated flows to engage leads even outside of working hours.
Provide instant responses to FAQs, ensuring leads remain engaged.
5. Improved Collaboration
Notify sales teams instantly about high-priority leads.
Use WhatsApp Flows to coordinate between field sales teams and office staff.
How WhatsApp Flows Empower Support Teams
1. Faster Query Resolution
Automate responses to common queries such as account information, troubleshooting steps, or return policies.
Escalate complex issues to human agents seamlessly within the same WhatsApp thread.
2. Proactive Customer Support
Send proactive messages such as appointment reminders, payment due alerts, or service updates.
Conduct satisfaction surveys after resolving issues to gather actionable feedback.
3. Reducing Workload for Agents
Handle high volumes of customer inquiries with automation, reducing the burden on support agents.
Allow agents to focus on complex issues that require human intervention.
4. Omnichannel Support
Integrate WhatsApp Flows with other support channels to offer a unified experience.
Ensure customers receive consistent support, regardless of the channel they use.
5. Real-Time Support Metrics
Track response times, resolution rates, and customer satisfaction scores to identify areas for improvement.
Benefits of Using BizMagnets WhatsApp Flows
1. Enhanced Productivity
By automating repetitive tasks, sales and support teams can focus on high-impact activities.
2. Improved Customer Satisfaction
Faster response times and personalized interactions lead to happier customers.
3. Cost Efficiency
Reduce operational costs by minimizing the need for manual intervention.
4. Scalability
Handle large volumes of interactions effortlessly, allowing your team to scale operations without compromising quality.
5. Actionable Insights
Use analytics to refine workflows, optimize team performance, and enhance customer engagement strategies.
Real-World Use Cases
Case Study 1: Retail Business
Challenge: A retail business struggled with managing customer inquiries about product availability and order status. Solution: Implemented BizMagnets WhatsApp Flows to automate responses to these queries. Result: Customer query resolution times dropped by 60%, and sales teams could focus on upselling and cross-selling opportunities.
Case Study 2: Financial Services
Challenge: The company faced delays in responding to loan inquiries. Solution: Deployed WhatsApp Flows to guide customers through the loan application process. Result: Loan application completions increased by 35%, and support teams had more time for complex cases.
Case Study 3: E-Commerce
Challenge: Frequent cart abandonment due to lack of follow-up. Solution: Set up WhatsApp Flows to send automated reminders and personalized offers. Result: Cart recovery rates improved by 45%, leading to higher revenue.
Tips for Optimizing WhatsApp Flows
Focus on Simplicity: Avoid overly complex workflows; keep the customer journey straightforward.
Use AI Smartly: Implement AI to handle dynamic queries and improve flow efficiency.
Personalize Interactions: Tailor messages to customer preferences for better engagement.
Continuously Update Workflows: Adapt flows to evolving customer needs and business goals.
Ensure Compliance: Follow data protection regulations like GDPR to build trust with customers.
The Future of WhatsApp Flows for Sales and Support
AI-Driven Sales StrategiesWhatsApp Flows will leverage AI to predict customer behavior, enabling proactive sales outreach.
Voice and Video IntegrationFuture updates may include voice and video support within WhatsApp Flows for richer customer interactions.
Advanced AnalyticsDeeper insights into customer behavior and workflow performance will enable continuous optimization.
Hyper-PersonalizationWhatsApp Flows will evolve to deliver highly personalized experiences based on real-time data.
Conclusion
BizMagnets WhatsApp Flows are revolutionizing the way sales and support teams operate. By automating routine tasks, enhancing collaboration, and delivering personalized experiences, they empower teams to work smarter, not harder.
For businesses aiming to boost productivity, improve customer satisfaction, and scale operations efficiently, BizMagnets WhatsApp Flows are the ultimate solution.
Start transforming your sales and support processes today with BizMagnets WhatsApp Flows and stay ahead in the competitive business landscape!
Ready to Empower Your Teams?Discover the power of BizMagnets WhatsApp Flows and elevate your sales and support operations effortlessly.
2 notes
·
View notes
Text
Russia plans to involve North Korea directly in the full-scale war against Ukraine this fall and winter, President Volodymyr Zelensky said on Oct. 14, citing intelligence data.
The announcement comes a day after Zelensky warned of an "increasing alliance" between Moscow and Pyongyang.
According to Ukraine's military intelligence, Russia's plans for the fall and winter include "the actual involvement of North Korea in the war," Zelensky said.
The briefing also included updates on "Russia's relations with some other countries, that, unfortunately, are investing in prolonging the war," the president added.
Zelensky warned on Oct. 13 that Russia and North Korea were deepening their alliance, saying that the partnership had escalated to the point where North Korea was sending personnel to Ukraine's front lines along with weapons.
"This is no longer just about transferring weapons. It is actually about transferring people from North Korea to the occupying military forces," he said.
The warning followed reports from South Korean Defense Minister Kim Yong-Hyun that North Korea is likely to deploy regular troops to Ukraine to aid Russia at the front.
Reports have also emerged in recent days that North Korean officers were killed in a Ukrainian missile strike in Russian-occupied territory. The Kyiv Independent has not been able to verify these reports, which have not been confirmed beyond a single intelligence source.
North Korea has been supplying Russia with ballistic missilesand vast quantities of artillery shellssince fall of 2023. Earlier this year, two countries signed a mutual defense pact during Russian President Vladimir Putin's visit to Pyongyang.
Putin submitted the treaty, which stipulates that either nation must render military assistance to the other in the event of an attack, to the Russian State Duma for ratification on Oct. 14.
17 notes
·
View notes
Text

hello, dears! thank you to everyone in our dms for your patience with us the last few months! we're posting this long-awaited update to inform you that due to the issues we have consistently had with tumblr, we will be password protecting our future blog in about a week for two months time, after which we will begin again! this blog is our main blog, so it will remain here unharmed until we're ready to use it once more! for those who may be unaware, either due to our tumblr messages not passing, or for the inconsistency of our replies to private asks, tumblr has been causing various problems for krp blogs both new and old since mid-october of last year. for us, starting around december, this has included things like dms glitching so that entire conversations go missing at random intervals ( only to magically reappear weeks later before disappearing again ), various coding issues with tumblr not allowing us to transfer blogs for posterity, posts getting eaten and queues saving only to disappear when we log out. in the recent months this has escalated to one admin being unable to see anything on our dash, to the point where tumblr will not save their visit to the account in their data.
we originally thought this was because of the flooding, power outage issues, and general internet instability in our area, but we have seen reports of other admins having similar and worse issues, though none to our degree with a blog still standing. whether we are all encountering such issues due to reporting claims or tumblr's rule changes, these issues have interfered greatly in our conversations with our members across all platforms for months and has halted our revamp as we have focused efforts on troubleshooting instead of updating in our spare time.
in the interest of not getting our tumblr blog taken down we will converse with tumblr support about the issues we have been experiencing! we have been in contact with them intermittently so far with good results, so rest assured, we are not shutting rupes down! our aff will still remain up and we will accept dms regarding any questions about this decision there!
we've gone through two volumes of rupesnigra since 2020, and each has brought the most illuminating muns and stories to our footsteps. we love the safe haven we have built here, and are always amazed when it manages to withstand the trials of the world and krp. we hope to finalize our revamp to bring you all a third volume safely, soon!
to those seeking to join rupesnigra, consider our home yours already! please wait for us to dust the furniture, brighten the rooms, plump the pillows, and make this space all the more welcoming for you. we will have jasmine tea, and many stories, and little strawberry cookies waiting for you when you finally come home ♡
have a happy spring, lovely creatures! write many things, so that you can show us everything when you return (or grace us for the first time)! :)
all our love, — k&&d.
9 notes
·
View notes
Text
How BoardRoomAI is Revolutionizing Corporate Governance in the Legal Industry

In a sector where regulatory compliance, transparency, and effective governance are paramount, Tagbin’s BoardRoomAI is transforming how legal firms operate. The legal industry, known for its intricate paperwork and strict adherence to guidelines, is now embracing advanced technology to streamline processes, enhance decision-making, and maintain a competitive edge. BoardRoomAI on legal industry is paving the way for smarter, faster, and more efficient governance—setting a new benchmark for compliance and boardroom operations.
Understanding BoardRoomAI and Its Relevance to the Legal Industry
BoardRoomAI is an AI-powered boardroom management tool developed by Tagbin to automate, streamline, and optimize the functions of corporate governance, compliance, and decision-making. Designed with robust features tailored for legal professionals, this platform is uniquely positioned to address the challenges that law firms and corporate legal teams face, especially in maintaining strict compliance and regulatory standards.
Key Features of BoardRoomAI
Automated Document ManagementThe legal sector generates a massive amount of documentation daily. BoardRoomAI leverages automation to organize, store, and manage these documents seamlessly. This eliminates manual work, reduces human error, and ensures easy access to critical documents when needed.
Real-Time Compliance MonitoringCompliance is the backbone of the legal industry. BoardRoomAI’s real-time monitoring ensures that all activities and documents meet regulatory standards, thus reducing compliance risks and safeguarding the firm from potential legal complications.
Enhanced Data SecurityData confidentiality is critical in the legal world. BoardRoomAI provides advanced encryption, multi-level access controls, and secure data storage, making it a reliable tool for safeguarding sensitive client and firm data.
Streamlined Decision-MakingBoardRoomAI facilitates faster and more accurate decision-making through AI-driven insights and analytics, enabling board members to make well-informed choices based on real-time data.
Improved Collaboration and CommunicationWith built-in collaboration tools, BoardRoomAI allows seamless interaction between board members and legal teams, even across geographies, ensuring efficient and transparent communication.
Why the Legal Industry Needs BoardRoomAI
The complexities of the legal field demand high levels of accuracy, efficiency, and compliance. Traditional methods of document handling and governance not only slow down operations but also increase the risk of errors. Here’s why BoardRoomAI on legal industry is a game-changer:
Increasing Regulatory RequirementsWith global regulatory landscapes constantly evolving, legal firms face the challenge of adapting quickly. BoardRoomAI offers real-time updates on regulatory changes and ensures that governance practices comply with the latest standards.
Mitigating Legal RisksLegal risk mitigation is paramount. BoardRoomAI’s monitoring tools identify compliance gaps early, alerting firms to potential risks before they escalate, thus protecting the firm’s reputation and avoiding costly penalties.
Optimizing Workflow EfficiencyLaw firms often struggle with lengthy approval processes and back-and-forth document exchanges. BoardRoomAI automates these workflows, cutting down on time-consuming tasks and allowing lawyers to focus on more strategic activities.
Data-Driven Decision-MakingThe legal sector thrives on data accuracy and analysis. With BoardRoomAI, legal teams can access real-time data insights, allowing them to make informed decisions that align with the firm’s objectives and regulatory requirements.
How BoardRoomAI Impacts Corporate Governance in Legal Firms
Corporate governance in the legal industry entails rigorous adherence to ethical standards, board accountability, and decision transparency. BoardRoomAI introduces a layer of intelligence and automation to these processes, which benefits law firms and corporate legal departments in several ways:
1. Transparency and Accountability
BoardRoomAI records every boardroom activity and decision, creating a clear audit trail. This not only helps in maintaining transparency but also holds board members accountable for their actions. With a history of all decisions readily available, legal teams can review past actions and improve future governance practices.
2. Streamlined Board Meetings
Board meetings are critical for making high-level decisions. BoardRoomAI simplifies the organization of board meetings by automating the scheduling, agenda setting, and sharing of necessary documents. Legal professionals can participate in these meetings with minimal prep time, as all essential information is readily accessible.
3. Enhanced Compliance and Risk Management
With its compliance tracking and risk assessment features, BoardRoomAI helps legal firms stay proactive. Instead of merely reacting to issues, legal professionals can take preventive measures against potential risks. Automated compliance reports keep legal teams well-informed about any regulatory updates, making compliance an integral part of governance.
4. Improved Client Confidence
In the legal world, trust and credibility are vital. By adopting BoardRoomAI, law firms showcase their commitment to using modern, secure, and transparent governance methods. Clients gain confidence knowing that their legal advisors are well-equipped to handle their needs in a compliant and secure manner.
Case Study: BoardRoomAI’s Success in a Leading Law Firm
Consider the example of a prominent law firm that implemented BoardRoomAI to streamline its boardroom operations and compliance tracking. The firm faced challenges with document management and lengthy decision-making processes, often leading to delays and potential compliance risks.
After adopting BoardRoomAI, the firm achieved the following:
70% Reduction in Document Handling Time: Automated document sorting and retrieval led to faster turnaround times.
Enhanced Compliance Monitoring: Real-time alerts helped the firm stay ahead of regulatory changes, reducing the likelihood of compliance breaches.
Improved Decision-Making Accuracy: AI-driven insights empowered board members to make data-backed decisions.
This transformation not only improved the firm’s internal efficiency but also elevated its reputation in the industry as a tech-savvy, client-focused organization.
The Future of BoardRoomAI in the Legal Sector
The potential for BoardRoomAI on legal industry is immense. As artificial intelligence advances, we can expect even more sophisticated features tailored to meet evolving legal needs. Here are some trends and future developments:
AI-Powered Predictive Analytics: BoardRoomAI could soon incorporate predictive analytics to forecast compliance issues, client concerns, and market shifts, giving legal professionals a proactive edge.
Enhanced AI-Driven Decision Support: Advanced algorithms will improve decision support, offering even more precise recommendations for board members based on historical data and current market trends.
Integration with Other Legal Tech Tools: As legal tech ecosystems grow, integrating BoardRoomAI with e-discovery tools, case management systems, and contract management software will provide an even more seamless experience.
Conclusion: BoardRoomAI as a Catalyst for Change in Legal Governance
As the legal industry undergoes digital transformation, Tagbin’s BoardRoomAI stands out as a vital tool for enhancing corporate governance and compliance. By automating processes, increasing transparency, and reducing legal risks, BoardRoomAI allows legal professionals to focus on what matters most—delivering exceptional service and safeguarding their firm’s reputation.
The adoption of BoardRoomAI on legal industry is not just a trend; it’s a necessity for firms aiming to stay competitive and maintain their regulatory compliance. Embracing this technology-driven shift opens up new possibilities for smarter, more efficient governance, setting a new standard for how legal firms operate in an increasingly complex world.
CONTENT SOURCE-( https://tagbininsights.blogspot.com/2024/11/how-boardroomai-is-revolutionizing.html )
2 notes
·
View notes