#Data Protection Services
Explore tagged Tumblr posts
Text
DOGE Is Planning a Hackathon at the IRS. It Wants Easier Access to Taxpayer Data | WIRED
#department of government efficiency#elon musk#donald trump#trump administration#republicans#federal government#irs#internal revenue service#data privacy#data protection#cybersecurity#us politics
22 notes
·
View notes
Note
how can you champion free speech and then celebrate when millions of voices on tiktok are censored. hypocrite.
I didn’t want to talk about politics on this blog but, oh well, here we go. Response under the cut.
Let me preface this: I’ve never been a fan of TikTok and when talk of a ban first started to come onto the scene 6 years ago, I thought it was a good thing, for a multitude of reasons but I won't go into all of it. I'll focus on what the proposed ban and SCOTUS corresponded to. This is a topic of US national security and the type of precedents it sets for foreign companies operating in the US. I thought it would be good to act now [2019] rather than later [2025] because looking at the growth curve, it was a service that would easily become so popular that lawmakers would find themselves in an impossible position and a ban would never happen.
Unfortunately, that’s exactly what’s happened. Again, in my opinion, now a horrible precedent exists. To any foreign government out there, the message is that you are allowed to enter US markets under any pretense, with zero reciprocity for US companies, and as long as you are popular and influential enough the US government and population will go out of its way to facilitate your access
If we are going to go to such extraordinary lengths for a foreign company and government the US must make a demand of absolute reciprocity, in my opinion. Meta, X, Google, Snapchat, and other US-based technology companies must be allowed total market access in China immediately with zero control by the Chinese Government (because that is what they have done through ByteDance owning Tiktok). When the Chinese government inevitably laughs at this demand, ask yourself why. They correctly see Meta, X, Facebook, and Google as instruments of US soft power and as cultural contamination of their civic ideal which undermines their hold on power.
However, we seem to naively believe we're immune from the same influence and have waited so long to act now that we face terrible choices. The one we've made inevitably means we will have a natural experiment now of what it means to allow a government that actively seeks to undermine our civic institutions with the most powerful known technological tool to do so. And the fact that the CCP and ByteDance decided to “shut it down” rather than divest it tells us everything we need to know. No free enterprise would willingly shut off access to 170 million users.
Also, we should be concerned that millions of Americans acted like drug addicts going through withdrawal when they couldn't access a social media app for roughly 12 hours. That is also cause for great concern. But that's a conversation for another day.
#ask#answered#anonymous#anti tiktok#it's not a 'free speech issue'#Free speech is about protecting the right to express ideas and not be persecuted by the gov—it is not a guarantee to a service#or a platform#also dont forget tiktok is the reason people had to create phrases like 'unalived' and basically employ self censorship so they dont#have content taken down#and yes i think US social media conglomerates (Meta-google-etc) are equally as bad for their data scraping and selling policy#and something needs to be done about that too#and yes—I don’t think we should let the CCP or other countries own American land#this does not even touch on the detriments of tiktok and its predatory algorithm on metal health—on promoting overconsumption#on ruining the populations attention span and normalizing dangerous trends and behaviors#Free Speech means I can post something critical of the government online and not have the police show up at my door (cough UK cough)
6 notes
·
View notes
Text
between my phone battery being gregnant/dying and the path of that damned typhoon, i am so cooked jsbfhsdvfdsvf i can't even see notifs/reply to messages from there bc it keeps shutting down, im typing this all on pc rn, it's so inconvenient ueueueue
#eintxt#the nearest service center for my phone brand is 2-3 hours away 💀👍👍#i want to get it fixed this weekend but this bitchass typhoon also hits this weekend!#bc what if this is the one that make our roofs fly off#lowkey still have a bit of trauma from that one typhoon that made it rain inside our house & fucked up my whole town years ago#WHILE I WAS IN THE MIDDLE OF MY RESEARCH PROJECT EVEN BTW#i need to protect my laptop tablet pc and merch when that happens again#if im inactive/unresponsive this weekend u alr know 🗿#i need to charge my power bank and load up some mobile data on my old/back-up phone
8 notes
·
View notes
Text
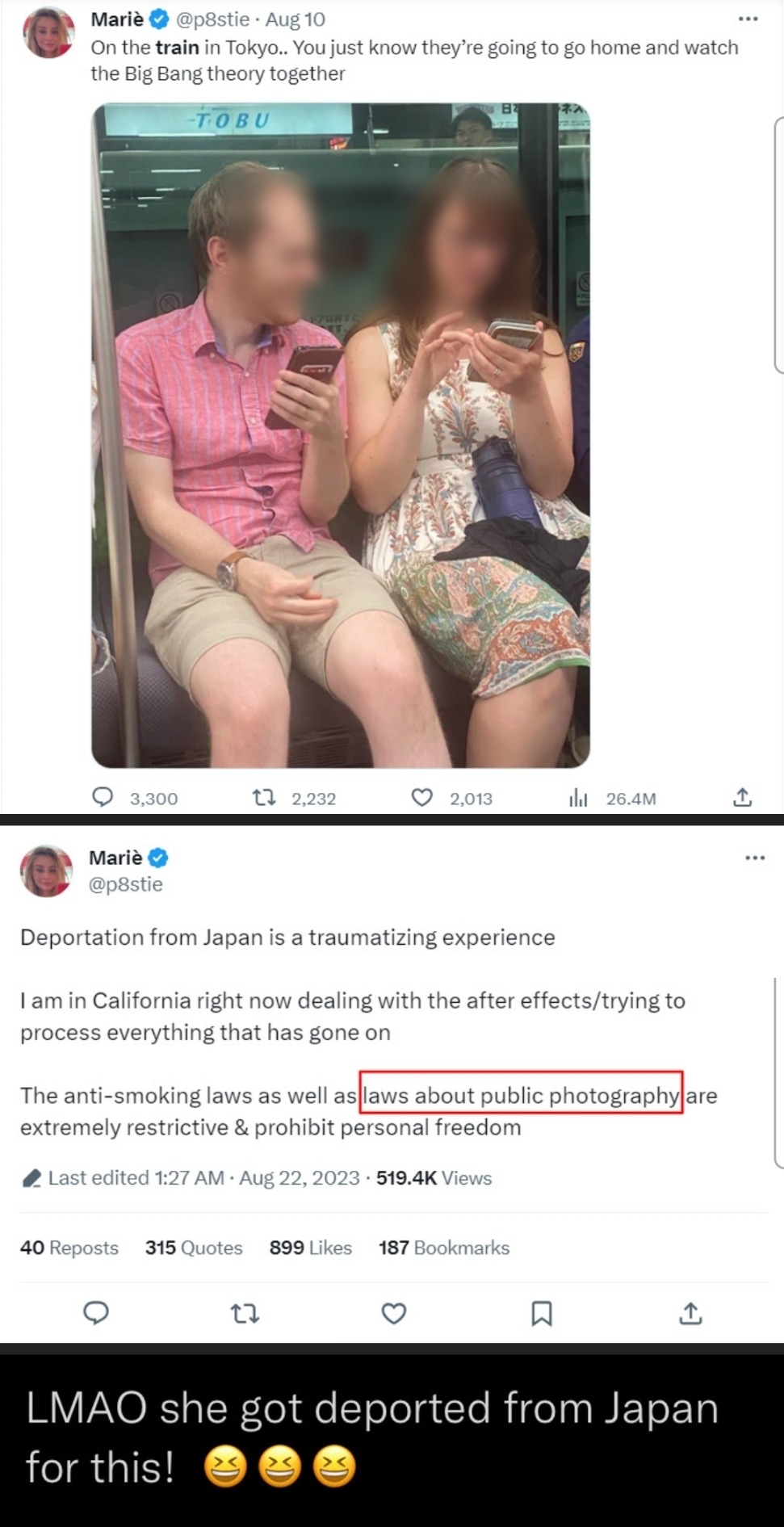
This is not from my post originally (it's a popular post from about 5 days ago and ironically spreads a picture taken without consent). I've censored the original picture because this is a jumping off point for what happened to me on Sunday while at work.
So I was at work on the shop floor when a man came in facetiming someone. He was picking up books and showing them to the lady he was facetiming, who told him that those books weren't the ones she was looking for. The man then turns to me (I was behind the tills) and asks I've I've heard of [book name]. I hadn't and explained that I'd been stocking the bookshelves earlier and hadn't come across it while doing that. He then flips his phone around so that the facetime camera is pointing at me. I freak out internally because what the hell?? I'm at work and you didn't ask me to talk to whoever it is you're talking to.
Man walks around the tills, comes up to the threshold of the till area and shoves the camera closer to my face. Because of where I was stood, I physically could not walk away from the tills because there is a wall of books in my way. I would have had to jump over the counter to leave. Honestly the whole thing made me really uncomfortable and I deeply resent people who think it's okay to take pictures of or record people in public. Ask for permission first. And if you can't, don't! Especially don't corner someone and force them to facetime a complete stranger. It's not okay, even if you think it's lighthearted.
#privacy#consent#data privacy#data protection#customer service#right to privacy#if you've also experienced something like this and feel comfortable sharing please do#I can't be the only person this has happened to
59 notes
·
View notes
Text
crawls onto my pc just for a few minutes to check things
puts this down

celess probably gets kinda nervous when she sees people in fleet uniform since she's.... technically ex-fleet/ex-fleet property
but since she was part of a niche experiment and was deployed/in use a really long time ago, no one is really looking for her... (at least not right now)
#fun fact: celess's age is listed as 'unknown' because it's kind of. ????#she was being shipped back from frontier worlds via very slow modes of transport#so she was technically 'born'/hatched a VERY long time ago#which is why she is like. one of the first troll > cyborg > android experiments#like now the fleet is like sure slap some robotics on a fucker#but when celess was first around it was less common especially for full conversion#she was inactive/'decommissioned' for much longer than she ever really was alive/in service#which is why so much data ended up corrupted (also because the transports she was in weren't protected from the radiation present in space)#(They just didn't really care that much about her state when she was to be destroyed for parts anyway)#Celess Stuff#but really she's just like.#became an android in the equivalent of her mid-20s#and then was “alive” on the battlefield for probably just less than 100 or so#so she is both ~25. ~115 and. maybe near a thousand or more sweeps old? i dont do exact timeline things because it's nukes my brain#especially since alternia has a very variable timeline#old as balls. question mark.
5 notes
·
View notes
Text
I really wish I wasn't living in the middle of a natural disaster site right now :D
#'oh we don't get tornadoes in northeast ohio we're on the lake'#welp....it finally happened. We had our first tornado yesterday#and you know where it hit? my childhood home :D#i'm lucky enough to have power but we have no internet and everyone around us is gonna be out until at least the weekend#i go on vacation this weekend but like....y'all....i'm still so freaked out#my ptsd didn't have time to kick in yesterday because i was at work and protecting my students but uhhhh it's kicked in today :D#and only having spotty cell service and data is making it worse#it's hard to stay connected and keep an eye on what's going on when you can't access the fucking internet#but tumblr works lmao
4 notes
·
View notes
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
Tumblr must have changed the service provider for Tumblr Live because it's available in the EU now too. Anyways how do I get rid of it
8 notes
·
View notes
Text
Smart & Cost-Effective Offline Data Storage Solutions by All Pro Solution
Preservation of precious digital assets is no longer an obligation in the information age—today it's a business choice. As an institution, company, or small organisation handling confidential data, a cost-effective, long-lasting, and secure storage solution is imperative. That's where All Pro Solution comes in, providing budget-friendly offline data storage solutions that serve your purposes.
Why Offline Data Storage Still Makes Sense in 2025
Although cloud storage might be useful, offline data storage remains the best option for organisations requiring control, privacy, and long-term security. Offline solutions are not susceptible to online threats like hacking, ransomware, or data breaches. It also offers bulletproof data preservation for regulatory compliance and archiving.
With All Pro Solution's offline data storage options, you can store your files securely without having to access the internet—ideal for those businesses requiring maximum protection.
Key Benefits of All Pro Solution's Offline Data Storage
1. Cost-effective and Flexible
Our cost-effective offline data storage solutions scale to meet the needs of any-sized business. No matter if you're backing up several gigabytes or terabytes of precious data, we have solutions that scale with your business.
2. High-Security Standards
We provide offline backup options that are physically secured, protecting you from cyber attacks. Your confidential data is stored safely and can be accessed only by authorized personnel.
3. Easy Integration and User Control
Our solutions are platform-agnostic and simple to integrate with your current IT infrastructure. In contrast to cloud storage, offline storage provides you with complete control over where, how, and when data is stored or retrieved.
4. Long-Term Data Preservation
For businesses that must maintain records, media files, or regulatory information for decades to come, offline archival storage provides long-term dependability at low maintenance.
5. Tailored Solutions for Each Industry
From medicine to law, from media production to education, we've developed storage solutions to address the unique needs of your industry.
Why All Pro Solution?
All Pro Solution is an offline data storage solutions company trusted by many. Our products benefit from decades of technical know-how, better-than-average customer care, and an unwavering commitment to ensuring businesses protect their most precious digital assets. We offer the equipment and hardware to you whether you require a lone system or the full solution to archive.
Off-line storage of All Pro Solution is an investment in reliability, value for money, and peace of mind in the long term. The sooner, the better time to make the smart move is now, as more vulnerabilities face on-line storage.

#affordable offline data storage#data storage services#All Pro Solutions offline data storage#offline data protection#archival data storage#physical data storage solutions
0 notes
Text
Overcoming Microsoft 365 Challenges: Partner with a Consulting Expert
The productivity suite Microsoft 365 provides necessary applications for both big and small enterprises to work together efficiently. Most organizations encounter different obstacles when trying to achieve maximum value from their Microsoft 365 implementation.
Companies encounter numerous difficulties when they need to handle complex elements, which include deployment security concerns and integrating with existing IT systems. Microsoft 365 Consulting delivers its most significant value at this point. Working with expert professionals assists businesses in maximizing Microsoft 365 benefits and making their use more efficient while solving frequent technological challenges. Source URL: https://www.import.mgnlink.com/overcoming-microsoft-365-challenges-partner-with-a-consulting-expert/
#managed it services#it services#data backup & ransomware protection#it support#microsoft 365 consulting#cloud solutions#it consulting#Microsoft 365 Consulting
0 notes
Text
IRS Lawyer Ousted as Elon Musk’s DOGE Plans Even More Cuts | The New Republic
#department of government efficiency#elon musk#donald trump#trump administration#irscompliance#irs audit#irs#internal revenue service#federal government#data privacy#data protection#cybersecurity#cyber security#civil rights#social justice#us politics
14 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
1 note
·
View note
Text
#Backup and Restore Tools#backup strategies#Cloud Storage for MSPs#Data Security#Data Transfer Solutions#managed service providers#MSP backup solutions#Multi-Location Backups#Ransomware Protection#Secure Data Backups
0 notes
Text
What to Do If Your Loan Application Is Hacked?
In an age where most financial transactions happen online, cybersecurity has become more important than ever. If you're applying for a personal loan through a digital platform, your data can be exposed to online threats if not properly secured. One alarming possibility is the hacking of your personal loan application. While this may sound rare, it's increasingly becoming a concern due to the rise in cybercrime.
So, what happens if your personal loan application gets hacked? More importantly, what should you do next? This guide walks you through the steps to take immediately, how to safeguard yourself, and how to prevent such a situation in the future.
Understanding How a Loan Application Can Be Hacked
When applying for a personal loan, you typically submit sensitive information such as your PAN number, Aadhaar details, salary slips, bank account information, and other personal identifiers. If the platform or lender does not use adequate cybersecurity measures, hackers can intercept or steal your information.
These cybercriminals may:
Use your credentials to apply for a personal loan elsewhere.
Change your contact details to reroute communications.
Attempt identity theft.
Sell your information on the dark web.
This kind of breach can leave you vulnerable not just financially but also legally.
Immediate Steps to Take if Your Loan Application is Hacked
1. Stay Calm and Act Fast
The first and most important step is to stay calm. Panic can lead to delays or mistakes. Once you realize your personal loan application has been compromised, act immediately.
2. Contact the Lender
Notify your lender or the platform where you applied for the personal loan. Ask them to freeze your application, investigate the breach, and stop any further processing until the issue is resolved. Many reputable lenders have a fraud or security department that can assist quickly.
3. Change Your Credentials
If your account was accessed through login credentials, immediately change your username, password, and security PINs associated with the account.
4. Alert Your Bank
If you submitted bank details during the personal loan process, inform your bank about the potential breach. Ask them to monitor for suspicious transactions and freeze your account temporarily if necessary.
5. File a Complaint with Cyber Crime Authorities
Visit www.cybercrime.gov.in to register a formal complaint. Provide all supporting evidence, including screenshots, emails, and messages received from the lender or suspicious sources.
6. File a Police Report (FIR)
Go to your nearest police station and file a First Information Report (FIR). This document will help if any legal action is needed later or if your identity is misused.
How to Tell If Your Loan Application Has Been Hacked
You may not always get an immediate alert if your personal loan application is compromised. Here are some signs to watch for:
You receive emails or messages confirming a loan you didn’t apply for.
You’re locked out of your loan account.
You receive a loan approval or disbursal notice with incorrect information.
Your credit report reflects a new personal loan you never took.
Your email or phone number associated with the loan application has been changed.
How Hackers Use Stolen Loan Application Data
Cybercriminals are resourceful. Once they gain access to your personal loan application, they might:
Take a fraudulent personal loan in your name.
Apply for other financial products using your details.
Demand ransom in exchange for not misusing your data.
Open fraudulent bank or credit accounts.
Sell your data to third parties or on the dark web.
That’s why quick action is essential—not just to prevent further damage but also to initiate recovery.
Inform Credit Bureaus Immediately
If your identity was compromised or a personal loan was taken in your name, you need to inform all major credit bureaus (CIBIL, Equifax, CRIF High Mark, and Experian). Request them to place a fraud alert on your credit report and flag the unauthorized loan entries.
Doing so helps protect your credit score and prevents further misuse.
Monitor Your Credit Report Regularly
Even if the hacked personal loan application didn’t result in any immediate fraud, continue monitoring your credit report for at least six months. Look out for:
New loan inquiries or approvals.
Changes in your credit limit or score.
Unusual financial activity.
There are many apps and services that allow you to check your credit report for free on a monthly basis.
Enable Two-Factor Authentication (2FA)
If the lender or loan aggregator website offers two-factor authentication, enable it. It adds an extra layer of security to your personal loan account and prevents unauthorized access even if your password is compromised.
Ensure the Platform You Use is Secure
Always apply for a personal loan through verified websites or apps. Look for:
HTTPS encryption in the URL.
A valid privacy policy and terms of service.
Registered NBFC or bank affiliations.
User reviews and ratings on app stores or social media.
RBI registration or regulatory compliance certifications.
Avoid sharing sensitive data through unverified links, WhatsApp, or social media.
Inform Your Employer (if Necessary)
If your salary details or employment verification was part of the loan process, you may want to inform your HR department. Some scammers might contact employers for fake employment verifications or misrepresent you using the hacked data.
Secure Your Devices
Your device may have been compromised during the personal loan application process. Run antivirus or anti-malware software, update your software and operating systems, and avoid using unsecured public Wi-Fi networks when accessing financial data.
Learn from the Incident
Use this unfortunate experience as a learning moment. Here are some tips to keep in mind for future personal loan applications:
Never share OTPs or passwords with anyone.
Don’t click on suspicious links in emails or messages.
Bookmark trusted personal loan platforms instead of typing URLs manually.
Use different passwords for different financial platforms.
Enable notifications for all login and transaction activities.
Conclusion
A hacked personal loan application can be a frightening experience, but with prompt action and preventive measures, the damage can be minimized. In the digital age, being proactive about cybersecurity is just as important as managing your finances.
Remember, your personal and financial information is valuable—not just to you, but to cybercriminals. By choosing trusted platforms, regularly monitoring your credit, and responding quickly to threats, you can safely navigate the world of personal loans without fear.
At Fincrif, we aim to educate and empower you with secure borrowing options and practical financial wisdom. Stay aware, stay secure, and borrow smartly.
#personal loan#loan application hacked#loan fraud#personal loan fraud#protect personal loan information#identity theft personal loan#report personal loan scam#secure loan application#personal loan cybercrime#hacked loan account#financial data breach#credit report fraud#cyber fraud personal loan#unauthorized personal loan#fake loan application#loan phishing scam#online personal loan safety#credit score damage#personal loan security tips#digital lending protection#personal loan online#loan apps#personal loans#loan services#bank#nbfc personal loan#finance#fincrif#personal laon
0 notes
Text

Best Employee Monitoring Solution | Kriptone | Kntrol
#best employee time tracking software#Real-time monitoring software#it security services company#Data loss prevention solutions#Endpoint security#IT cyber security services#Data loss protection#Web Tracking
1 note
·
View note
Text
Financial institutions are prime targets for cyber threats. From phishing scams and ransomware to insider threats and third-party vulnerabilities—the risks are evolving fast. Is your firm truly prepared?

At Century Solutions Group, we help financial organizations stay ahead of cyber threats with:
✅ AI-driven threat detection & proactive security ✅ Employee training to fight phishing & social engineering ✅ Multi-layered cybersecurity & zero-trust frameworks ✅ Secure cloud backups & disaster recovery plans ✅ Compliance support for PCI DSS, FINRA, GDPR & more
💡 Don’t wait for a breach to take action. Protect your data, your clients, and your reputation—before it’s too late.
📞 Let’s talk → https://centurygroup.net/industries/financial-it-services/
#Cybersecurity #FinancialServices #DataProtection #ITSecurity #ZeroTrust #PhishingPrevention #CenturySolutionsGroup
1 note
·
View note