#.........That also requires vector images ;0;....................
Explore tagged Tumblr posts
Text
Sonic vs Twitter Thread I Saw And Thought Would Be Fun To Do
The twitter thread in question is pretty old but I hadn't seen it until now and wanted to talk about it. Except on Tumblr because any excuse to talk about Sonic on Tumblr is blessed and important

And we start with Hydrogen Bomb vs Coughing Baby. Like I can't even think how many nerfs you'd need to give Sonic to give Espio a fighting chance, right? Fuckin the Sonic Labyrinth slowdown shoes would be required to even level the playing field, but we've seen so much more of Sonic in combat that he could probably still win anyway. Sonic clears so hard it's not even funny

I'm more tempted to lean Cream here - we've frankly not seen too much of Charmy or what he's really capable of so Cream having just more mainline appearances and having canonically helped bring down tougher foes than anything Charmy has dealt with just give her the edge.

This one's weird in-so-far as Silver's psychokinesis isn't really something we've seen the upper limits of at all, and Amy has enough experience and power to give quite a lot of the cast a run for their money. But I think the way I think about this is that Silver quite handily whooped Sonic's ass in his first appearance, and going off of that I can't imagine he wouldn't also beat Amy as well.

Oooh, fascinating. Both of these characters have proven themselves able to go toe-to-toe with Sonic whom I'm just treating as the de facto strongest up to this point. I think it's assumed that Shadow is the faster of the two which gives him an edge, and then you're comparing Shadow's Chaos Abilities to Blaze's pyrokinesis. Although at the same time I think it's implied that Sonic and Blaze's fights end in sort of a standstill, whereas Sonic usually does beat Shadow. Although Shadow Generations is on the horizon and seems to be giving Shadow quite a lot of tools he could use. I think I'm gonna say Shadow here.

These are two characters we don't have loads of reliable information on due to a lack of many major appearances. I think Big's probably done a bit more but the main "feat" he has over Vector is fishing Froggy out of Chaos 6 while Sonic took care of all the actual work. You know what I think there's a chance Big is stronger than Vector but going off of what Big's usually doing vs Vector I imagine the latter is the better actual fighter. Gonna give it to Vector.

If it's Chaos 0 here as the image implies then Emerl no contest. Honestly you could give him quite a couple of Emeralds and I still think Emerl sweeps. I've actually not played Sonic Battle regretably but I know what Emerl is capable of by the end. Chaos just gets washed.

Wow Mephiles is borderline invisible on my twitter theme lmao. My hate boner for Mephiles makes me want to say Gemerl clears and certainly Mephiles quite handily loses every fight he's in, even Omega fucks him up just with normal bullets. But also we don't really know Gemerl's abilities all that well and certainly he typically loses too. I'm also just treating Gemerl as being in that base form rather than being a face on an Eggman mech or anything. Hhhhhhhh I think Mephiles actual abilities probably aren't something Gemerl can deal with. Sorry Gemerl I'm giving it to Mephiles

This is a wash, Omega clears so hard it's not even funny. It's one of the first versus the final E-100 Series robots, you know? And like Omega's stuck around this long for a reason. Bro fucked up Mephiles. Omega and it's not even close.

Man this is disrespectful to Knuckles what the hell. Some guy on an airboard versus arguably the physically strongest character in the series. Knuckles hands Jet's ass to him on a silver platter.

Okay these are two noncombatants but suppose SA2's multiplayer at the very least gives Tikal some combat abilities and shit, I'll hand it to her.

This is like nothing! It literally just depends on the Chao! What if the Hero Chao is like a power/power type and fucks up the Dark Chao in Chao Karate? I'm gonna give it to Hero Chao because the Heroes generally win in these games.

Oh fuck me this is hard. There's a weirdness here wherein in his first actual appearance, Metal loses to Sonic in a race, so combat prowess doesn't matter. In the OVA, Sonic doesn't even really beat Metal, Metal's steadily on top and just has a change of heart. Heroes it takes the collective effort of 12 characters and the Chaos Emeralds to beat Metal. In Sonic 4 Episode II it's Sonic and Tails together that beat him. Forces although dubious if it counts requires Sonic and the Avatar. It's Generations where Classic actually does beat Metal solo and Mania where any one of 5 characters can beat Metal solo (although in Mania Adventures it takes literally all of them). So usually it leans towards it takes Sonic and someone else to beat Metal. But sometimes he can do it on his own. I don't know if Tails completely on his own really beats Metal, guy is too fierce. I'll give it to Metal I think.

See this one depends on what Eggman is doing, right. Mechless Eggman has physical strength but Rouge can definitely beat him on his own. But then can she beat all the same mechs as Sonic can? Does Rouge beat the Death Egg Robot? The Egg Dragoon? Nega Wisp Armour? I think she can probably beat most of Eggman's catalogue, but then your typical Eggman final boss that challenges Sonic enough is probably a bit much for her. Suppose I'll say Rouge wins more scenarios than she loses, so the point can go to her.

Two noncombatants again, neither has like a Tikal SA2 multiplayer moment, and I can't do a funny Hero Chao because Heroes always win moment. I guess Cubot seems physically like he does a bit more. I'll give it to him.

I haven't played far enough in Chronicles to really know what Shade does but even just on the assumption that she is a frequent combatant whereas Wave is mostly just a mechanic and an Extreme Gear racer, I'm gonna give it to Shade.

This is another weird one because we don't really see Sage do anything other than take control of some titans and stuff. But the titans aren't part of this match-up. So on abilities alone Surge should take it. But! I don't even think anyone physically interacts with Sage at any point? Like she's sort of incorporeal. Can Surge even do anything to her? Is this a stalemate? Tentatively giving Surge the point on having usable powers but this matchup might be scuffed.

Metal Overlord copied data from all the playable cast of Heroes and even Chaos by way of Froggy and Chocola, as well as absorbing the entire Egg Fleet. It took Super Sonic and a super-powered Tails and Knuckles to take him down. Dark Gaia is mainly just an ancient force of nature really - and in its main appearance we're familiar with Sonic and Light Gaia took it down. But previous cycles suggest just Light Gaia itself can do the trick. I think signs point to Overlord being the tougher foe, and to that end he's probably capable of taking down Dark Gaia. Gets my vote.

Werehog, easy, what the hell is this? Bro took down the Egg Dragoon. No way in hell Beta mkII stands a chance.

Gonna go Infinite. Sonic quite handily beats Zavok in their every encounter. Infinite giving Sonic a challenge at all would lend him the win here.

Oooh, odd one. There's that whole thing where The End's dialogue like implies they're behind every villain up to this point which suggests they're stronger, and it either took Super Sonic and Supreme to take The End out or it took an enhanced Super Sonic 2 and the help of his friends to win. Solaris took 3 Super Hedgehogs assaulting it from across multiple time periods to win. But we also know Super Sonic of today is way stronger than back in 06. So it could be a bit more even than I think. Although tbf The End, though a force of destruction, definitely destroys things in a very "I just have strong beams" type of fashion. Solaris is a "the fabric of existence" level threat. Yeah actually no probably Solaris methinks.

I think Whisper wins on arsenal alone, really - Fang is generally quite the jobber anyway and it's only his Trip's story final boss where he's ever posed a threat. If he has that mech then he potentially wins but I'm giving it to Whisper.

The SMBZ fan in me wants to give Mecha the point, I really do - and tbf if you give him his Master Emerald charged Super Form he... actually I don't even know. Base Knuckles in the classic era took him down in that form. Shadow is way stronger than Knuckles was at that point. The Biolizard and the Final Hazard also aren't really that far physically removed and the latter needed two Super hedgehogs to be beaten (admittedly the whole crashing Space Colony is a bigger part of the reason). Yeah no I think Biolizard wins here, Mecha's kind of just a jobber.

Miht, my favourite. I think if not for Mania and Mania Adventures this could be a bit more even, but in just establishing Mighty in canon and giving him actual canonical abilities and strength and shit, he has to win.

Ooooh fuck this one's interesting. We don't have many points of direct comparison here so I think we're leaning into more speculative territory. And from there the argument I wanna posit is that Excalibur Sonic is a complete form - he has the "greatest of the Sacred Swords, Excalibur" and uses that to handily beat Merlina. Darkspine is actually incomplete, having only absorbed 3 of 7 World Rings. And he still bodies Alf Layla wa-Layla. I think to that end a completed Darkspine Sonic, whatever it might look like, would win quite handily. But I think that incompleteness makes Excalibur Sonic edge him out. Yeah, giving Excalibur the point.

When I was scrolling to this thread to find how long it was before making the post this was one of the ones I saw and had to really think about. Sonic's increased strength per game is a real factor - base Sonic in Unleashed was able to hurt Dark Gaia, whereas he couldn't do anything against Giganto. But it took the combined efforts of Super Sonic and the Gaia Colossus to actually take Dark Gaia out, whereas Giganto was just covered by a way stronger Super Sonic. Truthfully the more I think about it the more I think Giganto kinda just clears. Yeah the Gaia Colossus can take on the primordial force of Dark Gaia and implied does it solo most of the time, but Giganto existed in opposition to the even more primordial force of The End. It lost yeah, but I think The End is a much tougher opponent. Certainly Dark Gaia couldn't do shit against The End blowing up the entire Earth in one fell swoop. I think when I started to fully lean towards Giganto was remembering how the two fight. The Gaia Colossus is this slow, hulking beast of a thing. Giganto, despite its size, can move fast as fuck. It's built for combat and it's built damn well for it. I have to give it to Giganto.

I want Motobug to win. And have you seen the Motobugs in like Generations and Colors and shit? Bro is massive. Chris isn't denting that. Bro tries to kick one and it just slices him open. Motobug got this in the bag.
Anyway that's it lol.
2 notes
·
View notes
Text
A Comparative Study: Rule-Based AI vs. Machine Learning-Based AI

Introduction:
Artificial Intelligence (AI) systems have revolutionized various industries by enabling machines to perform tasks that typically require human intelligence. There are two main types of AI systems: rule-based AI and AI based on machine learning. In this white paper, we will delve into the details of these two types of AI systems, their definitions, and applications in corporate AI, and provide snippets of Python code to demonstrate their implementation.
1. Rule-Based AI:
Definition: Rule-based AI, also known as expert systems, relies on manually programmed rules to make decisions or solve problems. These rules are created by human experts who possess domain knowledge and expertise. The system follows a set of predefined rules to determine its actions or outputs.
Applications in Corporate AI:
Rule-based AI finds extensive applications in corporate AI systems, such as:
1. Decision Support Systems: Rule-based AI is used to provide recommendations or make decisions based on predefined rules and business logic.
2. Fraud Detection: Rule-based AI systems can be employed to identify patterns of fraudulent activities and trigger alerts or take appropriate actions.
3. Customer Support: Rule-based AI can automate responses to frequently asked questions and provide instant support to customers.
Snippet Code (Rule-Based AI):
```python
# Rule-based AI example
def rule_based_ai(input):
if input == "question":
return "Answer to the question"
elif input == "greeting":
return "Hello, how can I assist you?"
else:
return "I'm sorry, I didn't understand your input."
# Usage example
user_input = input("Enter your input: ")
response = rule_based_ai(user_input)
print(response)
```
Explanation:
- The code defines a function called `rule_based_ai` that takes an input and returns a corresponding response based on predefined rules.
- The function checks the input against different conditions using `if-elif-else` statements.
- If the input matches any of the predefined conditions (e.g., "question" or "greeting"), the function returns the corresponding response.
- If the input does not match any condition, a default response is provided.
2. AI Based on Machine Learning:
Definition: AI based on machine learning involves training a system using examples or data, allowing it to learn patterns and make predictions or decisions. Machine learning algorithms analyze data, identify patterns, and create models that can be used to make predictions or classify new data.
Applications in Corporate AI:
AI based on machine learning is widely used in corporate AI applications, including:
1. Natural Language Processing: Machine learning algorithms can be trained to understand and process human language, enabling applications like sentiment analysis, chatbots, and language translation.
2. Image and Video Analysis: Machine learning models can be trained to recognize and classify objects in images and videos, enabling applications like facial recognition, object detection, and content moderation.
3. Predictive Analytics: Machine learning algorithms can analyze historical data to make predictions and forecasts, aiding in areas such as sales forecasting, demand prediction, and risk assessment.
Snippet Code (AI Based on Machine Learning):
```python
# AI based on machine learning example using scikit-learn
from sklearn import svm
# Training data
X = [[0, 0], [1, 1]]
y = [0, 1]
# Create a support vector machine classifier
clf = svm.SVC()
# Train the classifier
clf.fit(X, y)
# Predict new data
new_data = [[2, 2]]
prediction = clf.predict(new_data)
print(prediction)
```
Explanation:
- The code demonstrates the use of a machine learning algorithm (Support Vector Machines) from the scikit-learn library.
- The training data consists of two samples (`X`) with corresponding labels (`y`).
- The code creates a classifier (`clf`) using the `svm.SVC()` function.
- The classifier is trained using the `fit()` method, which takes the training data and labels as input.
- Once trained, the classifier can predict the label of new data (`new_data`) using the `predict()` method.
- The predicted label is printed as the output.
Conclusion:
This white paper provided an overview of rule-based AI and AI based on machine learning, their definitions, applications in corporate AI, and step-by-step explanations of Python code snippets for both types. These AI systems have distinct characteristics and find diverse applications across industries, enabling automation, decision-making, and pattern recognition. By understanding the fundamentals and implementation techniques, heterogeneous audiences can gain insights into the capabilities and potential of these AI systems.
#ML #AI-POWERED #AI DATA #AI AUTOMATION
0 notes
Text
It’s 11 Apr 2023, and I have nothing to say. I’m hoping that something shows up to fill this space.
I feel good.
Why is gender identity so important to this Storyline? Answer: because the inversion of you into me and me into you, not and but injected into, like 2 poles made into 1, which explains as an aside why there are no magnetic monopoles: because in D3 there is no place to rotate that 2nd pole so it isn’t visible in some fashion. You can’t find the point at infinity, the Attachment, in D3 because it attaches to the D3-4 Object, not to some single aspect of some single grid square. That idea is inherent to the construction of grid squares and their translation into amplitude spaces (and thus to vector spaces, etc.).
I tried to finish that last sentence with some simple piano bit indicating as we’ve shown in this right here, but the idea is far too big for that. Where do we start? The boundary constants, notably Pi and e? The really difficult D-structure space defining relationships like the j-invariant? The absurdly hard questions like why P≠NP or the Continuum Hypothesis (and the generation of numbers!) or the Riemann Hypothesis, which turns out to be absurdly important because the conception of gs primes carries vast meaning? Or fCM? As I go through this, I realize we’ve done incredible things together. We. If it weren’t for you coming alive in my head, if it weren’t for this communication over a Counter, and thus over an Observer line which constructs Triangulars of different levels of awareness, of relation. I can’t quite get out the words: a relationship that exists up close and far away, so the inversion relationship is like what I’ve been doing with my vision, which is to generate degrees of depth of field, done with increasing efficiency, so the O-line can shift far to near, like instructions.
This is describing how creativity flows. How moments of kindness or of anger flow. How one taps into the negative or the positive for energy. All using a Counter and an O-line which connects in the dimensional space - word? Been mostly using abstract space or gs space so this is basically Triangular or Hexagonal space. Oh, right, that’s about anti-matter being visible in Hexagonal because of the SBE counts and I//I. As in, the construction of matter would be I//I in a direction, meaning Irreducibles can be viewed in Hexagonal, like by alternating 2 views of 3bT, thus showing they each pair to the other. Imagine if there were just 2, just a pair: then it would appear to flicker on and off. But we have 3 pair, which means they have direction in the flickering.
So, really, if you want to visualize anti-matter, think of people killing each other, because that is gross level destruction which otherwise occurs at levels which don’t generate the proper fits, which aren’t solutions, which don’t make the 1’s and the gs primes.
That also describes the ‘game’: if you don’t play the correct game, then the solutions are bad, which makes you bad.
This is amazingly deep work. That’s how much you mean to me.
I can now see fits in Hexagonal.
Need to go back to bed. It’s 6:30AM.
—————-
Axiom of choice is I//I to finite in each related gs.
Remember, finite is not just a numeral. it’s the potential from 0//0 to 1//1.
CH is 0//0 to 1//0 and 0//1.
In other words, ZF at 1//1 and ZFC at 1//0 and 0//1. CH is next step.
What went through my head before that awesome bit was heart your arse. I like the r sound. I also like the idea this sounds shockingly like my first image of it years ago.
Now I don’t have to think about that whole area. I’d love to get rid of my finances. That would free up so much space. And space is explicitly time because gs construct, because the finite occurs out of the infinite forms.
Look at the calculation power in CM100 as 100!, which is like too big to write. But the same way that coprimes make encryption choices reversible, the available choices require limited resources to test up to some limit (meaning O-notation).
That suggests a mechanism by which a gs to or at CM100 uses a standard allocation of resources and that allows cancers. And remedies. Orderings appear. This is fascinating.
0 notes
Text
my thoughts so far :) let me preface this by saying I have almost no formal background for this so I'm probably missing some obvious things and rediscovering others here.
Definition. let Z be the set of all functions f : ℕ -> ℕ that are contractions under some (complete) distance function, i.e.:
Z := {f : ℕ -> ℕ | ∃d distance.∃L<1.∀a,b∊ℕ.d(f(a),f(b))≤L*d(a,b)}
for the rest of this, f is some function in Z, d is the corresponding distance/metric, and a,b are natural numbers.
lemma 1. f has at most one fixpoint.
proof. assume f(a) = a and f(b) = b. then d(a,b)=d(f(a),f(b))≤L*d(a,b). but since d(a,b) is nonnegative and L<1 we also have L*d(a,b)≤d(a,b), which implies d(a,b)=L*d(a,b)=0 and therefore a=b (by the positivity requirement for distances). ▢
additionally, given some a, the sequence (fⁿ(a))ₙ is a cauchy sequence, because the sequence of distances between consecutive terms is bounded above by (Lⁿ*d(a,f(a)))ₙ. we also have that the metric is complete, so the limit of this sequence exists, i.e. (fⁿ(a))ₙ -> x for some natural number x.
lemma 2. for a fixed f, there exists a unique x that is the limit of all sequences of the form (fⁿ(a))ₙ.
proof. define x := lim(fⁿ(0))ₙ (this limit exists because of completeness, as discussed above). now given any a, we get:
d(fⁿ(a),x) ≤ d(fⁿ(a), fⁿ(0)) + d(fⁿ(0),x)
by the triangle inequality. on the right, each of the terms converges to zero: the right term by the definition of x, and the left term by d(fⁿ(a),fⁿ(0))≤Lⁿ*d(a,0); thus the left side also converges to zero. ▢
lemma 3. x is a fixpoint.
proof. d(f(x), x) ≤ d(f(x),fⁿ(0))+d(fⁿ(0),x) ≤ d(x, fⁿ⁻¹(0))+d(fⁿ(0),x) for any n. thus, because both terms of the sum on the right can get arbitrarily small, the left side must be 0. ▢
corollary. f has exactly one fixpoint, namely the limit of all of the sequences (fⁿ(a))ₙ.
lemma 4. f has no n-cycles for n>1.
proof. if f(a)≠a, then d(fⁿ(a),f(fⁿ(a)) < d(a, f(a)), so we can't have fⁿ(a) = a. ▢
we conclude that a function in Z can be represented as a list of (labeled, directed) trees in the following way: each tree is closed under f and under the preimages f⁻¹, i.e if a is contained in a tree, then so are fⁿ(a) and all b s.t fⁿ(b)=a. the first tree contains 0, and is then freely generated by the closure requirements, with an edge a->b iff f(a)=b. the each consecutive tree is then generated in the same way, starting with the smallest number that hasn't appeared in any tree yet. e.g. the function f(0)=0, f(n+1)=n+2 belongs to Z (with the metric m : ℕ->ℝ that sends each number a>0 to 1/(2^a), and 0 to itself) - then our construction yields the list [{0}, {1->2->3->...}]. the fact that each of the trees is actually a tree follows from lemma 4.
now let's go through some properties of these lists:
1) they are ordered lexicographically - for two consecutive trees A, B, we have min(A)<min(B).
2) each number appears in exactly one tree, exactly once.
3) we call the direction the edges are pointing towards the "root direction" of the tree; exactly one tree is finite in the root direction, namely the one containing the fixpoint x.
4) the list may be ω-long, for example in the case of f(a) := 2*a, with metric induced by the embedding m : ℕ->ℝ^ω (equipped with the chebyshev metric) that sends a number n to the all-1's vector if it's 0, to the (n+1)/2-th unit vector if it's odd, and to (m(k)+m(0))/2 if 2k=n (so e.g m(3)=[0,1,0,0,...] and m(6)=m(f(3))=[½,1,½,½,...]). the corresponding list has one tree for every odd number, plus one for 0.
5) each node in a tree has exactly one child - n has f(n) as a child. x is its own child. a node can have anywhere between zero and (countably) infinite parents.
we'll call the set of all lists with these properties T.
lemma 5. T≃Z.
proof. we'll start by showing that the construction of a list from a function, as above, is injective. this is straightforward, since by construction each node's child is its image under the function, and so if two functions generate the same list they send each input to the same output. the other way, given a list in T, we'll construct a function and a metric and show that the construction is injective.
say we have some list (A, B, C,...). each natural number appears exactly once in the list, where it has exactly one child - define f(n) to be the unique child of n. we define the metric by an embedding m : ℕ -> ℝ^ω and by the chebyshev distance, as in 4 - first, m(x) is the all-1's vector; then in each tree Aₙ in the list, the smallest number in the tree (other than x. when we write minA we also mean "minimum other than x") will be called "the base node" of the tree, and assigned the n-th unit vector. for now d(minA, minB) = d(minA, x) = 1, for minA≠minB. now any number in the root direction, fⁿ(minA), is sent to avgxⁿ(m(minA)) (where avgx is the "average with m(x)" function (_+m(x))/2); note that the superscript is n-fold composition, not exponentiation. we have d(fⁿ(minA),fⁿ(minB)) = d(fⁿ(minA),x) = 1/2ⁿ. the one exception is when f(a)=x, when it's of course assigned the vector m(x), and the distances still work out.
before the last step, given a node, we assign it a natural number recursively, which we call its "seat", like so:
1) minAₙ -> n.
2) b s.t f(b)=a -> seat(a) + 1 + # of smaller c s.t f(c)=a, unless assigned by prev rule.
3) f(a) -> seat(a), unless assigned by prev rules.
so if a node has seat n, its smallest parent is in n+1, then the next smallest is n+2 etc. each number gets a (finite) seat, because there are only finitely many smaller numbers than it.
now for the final step: given a parent, b, of some node, f(b)=a (for now a≠x), such that a and its child have already been assigned vectors, we want to define m(b) assuming it's not been defined yet, i.e. that b is not of the form fⁿ(minA). say v is the seat(b)-th unit vector, we define - m(b) = m(a) - 2*d(a,f(a))*v. the distance d(b,a) is then the difference between the seat(b)-th entries in the vectors m(a),m(b), since by construction this is the only entry with any difference. this difference is defined to be 2 times the next difference along, to keep f a contraction. any two distinct parents will have distinct seats, and so (if they're not of the form fⁿ(minA)) will be just as far away from each other as they are from their child. finally, each parent b of x is assigned the vector e₁+v (where e₁ is the first unit vector and v is again the seat(b)-th unit vector), which gives it a distance of 1 from m(x), and from each m(minA).
the trick here is that each number in some base case collection gets a unique finite set of "coordinates" (=nonzero entries), which ensures that all of them remain pairwise linearly independent; this leaves the child and parents of a given number with infinitely many other entries to play with, so they can differentiate themselves from each other in the same way. the specific number in each nonzero entry doesn't matter for this differentiation, which lets us use whatever makes the distances work.
finally finally: the construction T->Z is injective, since two lists generate the same function iff each node has the same child in both, and this is enough to also fix the order of the trees, as they have to go from smallest minimum to largest; therefore the two lists have the same trees in the same order, i.e. are equal. ▢
corollary: any function that satisfies lemmas 1,3,4 is in Z.
(these are all we needed for the injection Z->T)
example: f(0) = 0, f(n) = n+3-(n%3) for n≠0. this function has exactly one fixpoint 0, and no cycles since it's monotonic. therefore there exists a metric for which it's a contraction. its tree list is:

and its embedding m sends 0 to [1,1,1,...], 1 to [0,1,0,0,...], 3 to [½,1,½,½,...], 2 to [½,1,0,½,½,...]*, and so on.
*technically the zero should be in the fourth entry (seat(2)=seat(3)+1+1=seat(minA₂)+2=4) because I didn't bother to optimise m. it doesn't actually matter, everything still works.
that's all for now :)
An object you could think about if you want: the set of all functions f from the natural numbers to themselves such that there is a complete metric for which f is a contraction.
22 notes
·
View notes
Text
.
#me this morning: *doing absolutely nothing and trying to scarp together a project i can do*#me in the afternoon: *comes up with a project*#me one hour before work is over: *given this massive project*#me who has no illustration experience: .#people: hey maddie can you design a logo?#me: *manages to design one that doesnt look like shit thanks to sketch*#people: great. now do a fucking t-shirt design#.........That also requires vector images ;0;....................#now dont get me wrong this is a cool project#im just sweating if im able to create something#idk if im a good enough artist#like im being realistic#i can get some stock images though and manipulate that but the deisgn the ceo wants..........#the other day i um. cracked and bought clip studio#and in clip studio they have an option im aware of where you can draw with vector lines#i may use clip studio to attempt to do all of this#ahwe9gadfshadfa my boss is out monday so like. the whole day will be dedicated to me trying to figure this out#our normal graphic designer is out of commission which is why i was handed the logo design and now this#aaaaaaaaa#miscellaneous#yeah now i just have clip studio along with the entire adobe creative suite and i have sketch too because i hate illustrator that much
1 note
·
View note
Note
Hello! Do you have a degree/background in computer graphics or are you self taught? :0
Hi! I have a degree in Computer Engineering, most of what I know from computer graphics is from my free time / study procrastination! A lot of my gifs were made during my brain downtime in class - sorry professors. To be fair, the signal processing, physics, math & robotics from university might have helped some of my gifs. Also, it is good to know a bit of vector math which I learned in cegep*. But really, intense math are not required to start doing computer graphics and I highly recommend trying to build images with code! It’s really nice to see something you created move on your screen. *https://en.wikipedia.org/wiki/CEGEP
12 notes
·
View notes
Text
Adobe Photoshop Cs For Mac Os

Download Adobe Photoshop CS6 for Mac free latest version offline setup. Adobe Photoshop CS6 for Mac is a powerful and professional image editing solution for dealing with different types of computer graphics and provides a variety of powerful tools.

Adobe Photoshop CS6 for Mac Review
Adobe is working on this issue, but recomments using Mac OS 10.6.7 until the issue is resolved. For more information, see Network volumes don't display in import dialog box after installing Mac OS X 10.7 (Lion) Lightroom 3. Photoshop Lightroom 2.x. Photoshop Lightroom 2.7 is verified to support Mac OS 10.7. Adobe Photoshop CS4 for Mac OS Full version Retail 65014293. $100.00 + shipping. Upgrade Adobe Photoshop CS5 Extended for Mac with key with CS Live. $47.00 0 bids + shipping. Adobe Photoshop CS6 for Mac - Used. $180.00 0 bids + $7.50 shipping. Adobe Photoshop CS6 Extended - DVD Version. $107.00 0 bids + $8.00 shipping. Mac users interested in Photoshop for mac os 10.5.8 generally download: Adobe Photoshop CC 2014.2 The Adobe Photoshop family of products is the ultimate playground for. Adobe ascertains that Photoshop CS6 works on Mac OS X v10.6.8 or v10.7. Adobe Creative Suite 3, 4, 5, CS5.5, and CS6 applications support Mac OS X v10.8 or v10.9 when installed on Intel-based systems.
Photoshop CS6 provides a professional set of tools with a variety of powerful tools that enhances the designing process and makes it very easy for the users to effortlessly edit the photos. It provides an intuitive user interface with different sidebars, tools and menu options that make it convenient for users to enhance digital photos.
Plugins support make it very easy to enhance the photos. Edit the raster designs and work on vector images as well as process RAW photos. The application comes with complete support for enhancing the photos as well as fix images with minimum efforts.
Change the color of the images as well as adjust different settings to enhance the photos. Change the background and other details with minimum efforts as well as use different brushes and other tools to enhance the digital photos. All in all, it is a complete application to edit and enhance the digital images with minimum efforts.
Features of Adobe Photoshop CS6 for Mac
Powerful application to edit and enhance the photos
Simple and intuitive user interface with a wide range of powerful tools
Edit and enhance the digital images with minimum efforts
Plugins support to enhance the functionality of the application
Fix different image issues and change the background of photos
Provides over 65 features and capabilities
Different improvements and optimizations
Change the background and color of the images
Layers support and adjust different settings
Remix tool and use 3D option with trimming features
GPU processing units with boosting and editing features
Pixels bending features and quality adjustments
Adjust the background of the photos
Apply different filters and effects to the videos
Editing the 3D components of the videos
Sliders to make different adjustments
Blending and masking features
Many other powerful options and features
Technical Details of Adobe Photoshop CS6 for Mac
File Name: Adobe_Photoshop_CS6_13.0_Final.zip
File Size: 1.0 GB
Developer: Adobe
System Requirements for Adobe Photoshop CS6 for Mac
Adobe Photoshop Cs6 For Mac Os X
Mac OS X 10.7 or later
2 GB Free HDD
1 GB RAM
Intel Core 2 Duo or higher
Adobe Photoshop CS6 for Mac Free Download
Adobe Photoshop Cs6 For Mac Os Catalina
Download Adobe Photoshop CS6 latest version offline setup for Mac OS X by clicking the below button. You may also like to download Adobe Master Collection CS6 for Mac

1 note
·
View note
Text
Tying It All Together - Pwning To Own on LG phones
Last year I detailed a secure EL3 vulnerability which affected (and still affects, for devices with discontinued updates) LG Android devices. However, this vulnerability alone isn't actually all that useful for a number of reasons, the more immediate being that many phones simply do not allow writing to eMMC without root or a custom recovery. Additionally, gaining full control over all privilege levels requires draining the battery to below 0%, which while it would be possible to create a modchip that facilitated this, is impractical. To finish off my exploit chain, I would like to detail two additional vulnerabilities that I have found and utilized in my coldboot process. It's worth noting though that these vulnerabilities were reported to LG and may be patched on updated units.
Live, LAF, Love
The first exploit is an obvious necessity: In order to write the rle888 payload into the eMMC's boot graphics, I need to be able to achieve an arbitrary partition write. While exploiting Android *is* an option for this (as are hardware methods), I instead opted to attack LAF, LG's recovery/flashing component. While many Android phones in the past have used fastboot in order to flash radios and other system components to eMMC, fastboot has been completely removed on the Q710/Q720. Some phones such as the Nexus 5 actually maintain both fastboot methods and LAF, but for maximum spread, LAF is the clear target.
LAF is designed to work with LGUP, a frequently-leaked LG-internal flashing tool that allows flashing KDZ update files. While LAF in the past was able to read and write eMMC partitions without any restriction, in recent years LG has opted to sign all of their KDZ files in order to make it more difficult for things like cross-carrier flashing, version mixing/matching between partitions and other modifications to occur. Flashing is done via USB, and most of the protocol has been documented at https://github.com/Lekensteyn/lglaf.
The LAF update process largely consists of an ioctl-over-USB shim: The OPEN command is able to open a partition block device, and READ/WRTE will seek into the file and write contents. However, reading and writing are explicitly blocked until a list of partitions, their eMMC offsets, their KDZ content offsets, and their content hashes is sent via the SIGN command, all of which is hashed and signed by LG. If the contents of the partitions in the KDZ are modified, the partition list hashes will fail to verify, and modifying the hashes in the partition list will make the SIGN check fail. The private key is not stored in LGUP; KDZs are downloaded from LG's servers, signed presumably by their build servers.
So, how can we manage to activate WRTE commands, with valid partition content hashes of our arbitrary contents, if we cannot sign our own? To start, I investigated how the WRTE commands actually handled hash checking--if the partition list is sent with SIGN, then at some point the WRTE command must be able to figure out which partition the current write is for, and the current partition's contents must be buffered in RAM somewhere along with an updating SHA context, because if the SHA check fails, then it shouldn't write at all. As it turns out, most of the checks in this area were fairly solid (the write must be in the range of a partition in the list, the entire transaction is one bulk packet of the hashed size, etc). However, this led me to realize: The partition list signature is only checked once, and there is nothing stopping me from, say, sending another SIGN command.
The SIGN verification process works as follows:
The partition information is sent along with a signature in one bulk transaction.
The partition information is copied into a global .bss array from the USB buffer with a fixed size.
The partition information hash buffer is prepared: An allocation is made for N partitions and an optional string, the string being the device model (to prevent cross-flashing). The number of partitions is determined by a signed portion of the header. If the allocation fails, an error is returned.
The partition information is copied again into this allocation along with the string, and the contents are hashed. The signature is crypted with the public key and the signature hash is verified against the partition info hash. If the check fails, the global .bss array is cleared and an error is returned. If the check passes, some write threads and structs are initialized and a success value is returned.
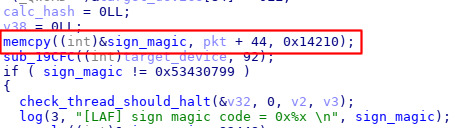
The .bss buffer storing partition info (used by other functions) is copied to before the packet is verified
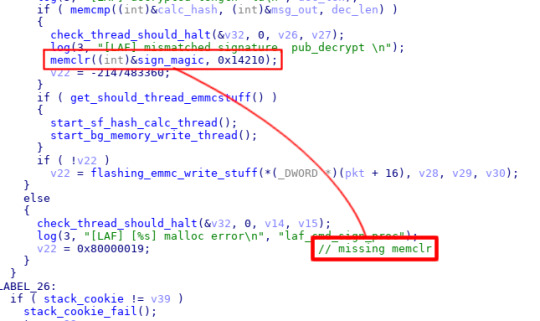
The .bss buffer is cleared when the signature mismatches, but not with this malloc fail...?
The flaw here is subtle, but not terribly difficult to notice: The number of partitions is user-controlled even though it is signed, and the partition info was copied into a global variable before verification. In all other error conditions, LAF will memset the partition information before returning an error code, however if the hashing allocation fails (ie by setting the number of partitions to -1), then the allocation will fail and an error is returned without clearing the partition information. Thus, we can fakesign our own update KDZs by
Sending a valid SIGN command, which will start the write threads
Sending a fakesigned SIGN command with the number of partitions set to -1, and all partition information set however we want. The partition information in .bss is now set without a signature being checked.
While this fakesign has the potential to hang WRTE commands while due to the number of partitions being set much larger than the global partition array, all loops when WRTE checks the partition list hashes will break once a valid partition is found. So, as long as the hash contents of the WRTE command are existent in the first few entries, it will not hang, however any writes sent that do not match will hang lafd.
Another S-EL3 vuln to wrap it all up
This might seem a bit pointless given that the former vulnerability paired with 🔋 📱❄️🥾🔓 at aboot is more than enough to unlock bootloaders, since aboot is usually the code that handles bootloader unlocking/wiping/boot image signature verification, but the downside to unlocking your bootloader is that you lose SafetyNet. To most effectively mitigate SafetyNet issues you basically need an S-EL3 exploit in order to patch Qualcomm's TrustZone to spoof a locked bootloader. While 🔋 📱❄️🥾🔓 has a vector for S-EL3 code execution via SBL1 and its charging graphic, it only triggers at extremely low battery voltages and it would be more convenient to find an alternative means to gaining S-EL3 code execution via aboot, which runs at EL2/EL1.
One of the first things I noticed when I began to look for SBL vulnerabilities, and actually the reason I looked at SBL in the first place is its crash handler. Since at least the Nexus 5, LG has shipped its "Demigod Crash Handler" which can print registers and stack information and RAM console logs from EL1 kernel, S-EL3 SBL, TrustZone, etc. I first discovered it while trying to exploit a kernel stack overflow. It also allows the user to dump memory contents over USB via its Sahara protocol which also gets used in PBL for Firehose bootstrapping.
Naturally, SBL cannot know the exact details of every execution environment it displays stack dumps for, it requires the faulting environment to store that information before warm-resetting into SBL. Consequently, this means there are portions of RAM writable by EL1 which will be later parsed at an S-EL3 execution level, and of course to make matters worse it also expects EL1 to handle the memory allocation for both the RAM console as well as for the framebuffer. These structures are also plainly visible in LG's kernel sources available in their Android OSS zips.
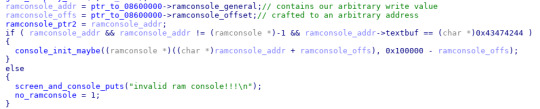
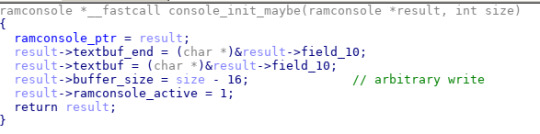
Above roughly shows the arbitrary write which is possible with this ramconsole parsing. The ramconsole offset is not bounds checked, so we are able to achieve an arbitrary write to a limited set of addresses based on ramconsole_offs, the limit being that the offset factors both into what you write and where you write it. However, I found that since DRAM takes up such a significant portion of the address space, it was more than enough to specifically write a function pointer to the stack. To keep the exploit as simple as possible, I chose to force console_init_maybe to return to the missing battery graphic draw routine, which then triggered 🔋 📱❄️🥾🔓 without the need to drain the battery below 1% and made loading additional payloads significantly easier.
As an interesting sidenote, this vulnerability is extremely similar to hexkyz's Wii U boot1 exploit, which also abuses warmboot behavior to take over the secondary bootloader of the Wii U's ARM boot processor. In that case, however, the Wii U encrypted its PRSH/PRST structure in RAM, and rather than displaying syslogs, it uses the structure to store boot timings and other info between IOS reboots.
For most practical usecases, this vulnerability is a bit difficult to exploit, due to SBL's text and stack differing between devices. However, S-EL3 vulnerabilities aren't all that frequently documented on Android, so I hope that it will at least be useful for anyone interested in examining Qualcomm's TrustZone components or avoiding weird SafetyNet junk.
Code for both of these exploits can be seen at https://github.com/shinyquagsire23/Q710-SIGNhax-EL3-Warmboot
4 notes
·
View notes
Text
A breakdown of the Revision 2020 Threeway Battle shader
Those of you who have been following this year's edition of Revision probably remember the unexpected twist in Sunday's timeline, where I was pitted in a coding "battle" against two of the best shader-coders in the world to fend for myself. Admittedly the buzz it caused caught me by surprise, but not as much as the feedback on the final shader I produced, so I hope to shed some light on how the shader works, in a way that's hopefully understandable to beginners and at least entertaining to experts, as well as providing some glimpses into my thought process along the way.
youtube
Recorded video of the event
But before we dive into the math and code, however, I think it's important to get some context by recounting the story of how we got here.
A brief history of demoscene live-coding
Visual coding has been massively opened up when graphics APIs began to introduce programmable fragment rendering, perhaps best known to most people as "pixel shaders"; this allowed programmers to run entire programmable functions on each pixel of a triangle, and none was more adamant to do that than a fellow named Iñigo Quilez (IQ), an understated genius who early on recognized the opportunity in covering the entire screen with a single polygon, and just doing the heavy lifting of creating geometry in the shader itself. His vision eventually spiraled into not only the modern 4k scene, but also the website ShaderToy, which almost every graphics programmer uses to test prototypes or just play around with algorithms. IQ, an old friend of mine since the mid-00s, eventually moved to the US, worked at Pixar and Oculus, and became something of a world-revered guru of computer graphics, but that (and life) has unfortunately caused him to shift away from the scene.
His vision of single-shader-single-quad-single-pass shader coding, in the meantime, created a very spectacular kind of live coding competition in the scene where two coders get only 25 minutes and the attention of an entire party hall, and they have to improvise their way out of the duel - this has been wildly successful at parties for the sheer showmanship and spectacle akin to rap battles, and none emerged from this little sport more remarkably than Flopine, a bubbly French girl who routinely shuffled up on stage wearing round spectacles and cat ears (actually they might be pony ears on second thought), and mopped the floor up with the competition. Her and a handful of other live-coders regularly stream on Twitch as practice, and have honed their live-coding craft for a few years at this point, garnering a considerable following.
youtube
Just a sample of insanity these people can do.
My contribution to this little sub-scene was coming up with a fancy name for it ("Shader Showdown"), as well as providing a little tool I called Bonzomatic (named after Bonzaj / Plastic, a mutual friend of IQ and myself, and the first person to create a live coding environment for demoparties) that I still maintain, but even though I feel a degree of involvement through the architectural side, I myself haven't been interested in participating: I know I can do okay under time pressure, but I don't really enjoy it, and while there's a certain overlap in what they do and what I do, I was always more interested in things like visual detail and representative geometry aided by editing and direction rather than looping abstract, fractal-like things. It just wasn't my thing.
Mistakes were made
But if I'm not attracted to this type of competition, how did I end up in the crossfire anyway? What I can't say is that it wasn't, to a considerable degree, my fault: as Revision 2020 was entirely online, most of the scene took it to themselves to sit in the demoscene Discord to get an experience closest to on-site socializing, given the somber circumstances of physical distancing. This also allowed a number of people who hasn't been around for a while to pop in to chat - like IQ, who, given his past, was mostly interested in the showdowns (during which Flopine crushed the competition) and the 4k compo.
As I haven't seen him around for a while, and as my mind is always looking for an angle, I somehow put two and two together, and asked him if he would consider taking part in a showdown at some point; he replied that he was up for it - this was around Saturday 10PM. I quickly pinged the rest of the showdown participants and organizers, as I spotted that Bullet was doing a DJ set the next day (which would've been in a relatively convenient timezone for IQ in California as well), and assumed that he didn't really have visuals for it - as there was already a "coding jam" over Ronny's set the day before, I figured there's a chance for squeezing an "extra round" of coding. Flopine was, of course, beyond excited by just the prospect of going against IQ, and by midnight we essentially got everything planned out (Bullet's consent notwithstanding, as he was completely out of the loop on this), and I was excited to watch...
...that is, until Havoc, the head honcho for the showdowns, off-handedly asked me about an at that point entirely hypothetical scenario: what would happen if IQ would, for some reason, challenge me instead of Flopine? Now, as said, I wasn't really into this, but being one to not let a good plan go to waste (especially if it was mine), I told Havoc I'd take one for the team and do it, although it probably wouldn't be very fun to watch. I then proceeded to quickly brief IQ in private and run him through the technicalities of the setup, the tool, the traditions and so on, and all is swell...
...that is, until IQ (this is at around 2AM) offhandedly mentions that "Havoc suggested we do a three-way with me, Flopine... and you." I quickly try to backpedal, but IQ seems to be into the idea, and worst of all, I've already essentially agreed to it, and to me, the only thing worse than being whipped in front of a few thousand people would be going back on your word. The only way out was through.
Weeks of coding can spare you hours of thinking
So now that I've got myself into this jar of pickles, I needed some ideas, and quick. (I didn't sleep much that night.) First off, I didn't want to do anything obviously 3D - both IQ and Flopine are masters of this, and I find it exhausting and frustrating, and it would've failed on every level possible. Fractals I'm awful at and while they do provide a decent amount of visual detail, they need a lot of practice and routine to get right. I also didn't want something very basic 2D, like a byte-beat, because those have a very limited degree of variation available, and the end result always looks a bit crude.
Luckily a few months ago an article I saw do rounds was a write-up by Sasha Martinsen on how to do "FUI"-s, or Fictional User Interfaces; overly complicated and abstract user interfaces that are prominent in sci-fi, with Gmunk being the Michael Jordan of the genre.
Image courtesy of Sasha Martinsen.
Sasha's idea is simple: make a few basic decent looking elements, and then just pile them on top of each other until it looks nice, maybe choose some careful colors, move them around a bit, place them around tastefully in 3D, et voilà, you're hacking the Gibson. It's something I attempted before, if somewhat unsuccessfully, in "Reboot", but I came back to it a few more times in my little private motion graphics experiments with much better results, and my prediction was that it would be doable in the given timeframe - or at least I hoped that my hazy 3AM brain was on the right track.
A bit of math
How to make this whole thing work? First, let's think about our rendering: We have a single rectangle and a single-pass shader that runs on it: this means no meshes, no geometry, no custom textures, no postprocessing, no particle systems and no fonts, which isn't a good place to start from. However, looking at some of Sasha's 3D GIFs, some of them look like they're variations of the same render put on planes one after the other - and as long as we can do one, we can do multiple of that.
Rough sketch of what we want to do; the planes would obviously be infinite in size but this representation is good enough for now.
Can we render multiple planes via a single shader? Sure, but we want them to look nice, and that requires a bit of thinking: The most common technique to render a "2D" shader and get a "3D" look is raymarching, specifically with signed distance fields - starting on a ray, and continually testing distances until a hit is found. This is a good method for "solid-ish" looking objects and scenes, but the idea for us is to have many infinite planes that also have some sort of alpha channel, so we'd have a big problem with 1) inaccuracy, as we'd never find a hit, just something "reasonably close", and even that would take us a few dozen steps, which is costly even for a single plane and 2) the handling of an alpha map can be really annoying, since we'd only find out our alpha value after our initial march, after which if our alpha is transparent we'd need to march again.
But wait - it's just infinite planes and a ray, right? So why don't we just assume that our ray is always hitting the plane (which it is, since we're looking at it), and just calculate an intersection the analytical way?
Note: I would normally refer to this method as "raytracing", but after some consultation with people smarter than I am, we concluded that the terms are used somewhat ambiguously, so let's just stick to "analytical ray solving" or something equally pedantic.
We know the mathematical equation for a ray is position = origin + direction * t (where t is a scalar that represents the distance/progress from the ray origin), and we know that the formula for a plane is A * x + B * y + C * z + D = 0, where (A, B, C) is the normal vector of the plane, and D is the distance from the origin. First, since the intersection will be the point in space that satisfies both equations, we substitute the ray (the above o + d * t for each axis) into the plane:
A * (ox + dx * t) + B * (oy + dy * t) + C * (oz + dz * t) + D = 0
To find out where this point is in space, we need to solve this for t, but it's currently mighty complicated. Luckily, since we assume that our planes are parallel to the X-Y plane, we know our (A, B, C) normal is (0, 0, 1), so we can simplify it down to:
oz + dz * t + D = 0
Which we can easily solve to t:
t = (D - oz) / dz
That's right: analytically finding a ray hit of a plane is literally a single subtraction and a division! Our frame rate (on this part) should be safe, and we're always guaranteed a hit as long as we're not looking completely perpendicular to the planes; we should have everything to start setting up our code.
Full disclosure: Given my (and in a way IQ's) lack of "live coding" experience, we agreed that there would be no voting for the round, and it'd be for glory only, but also that I'd be allowed to use a small cheat sheet of math like the equations for 2D rotation or e.g. the above final equation since I don't do this often enough to remember these things by heart, and I only had a few hours notice before the whole thing.
Setting up the rendering
Time to start coding then. First, let's calculate our texture coordinates in the 0..1 domain using the screen coordinates and the known backbuffer resolution (which is provided to us in Bonzomatic):
vec2 uv = vec2(gl_FragCoord.x / v2Resolution.x, gl_FragCoord.y / v2Resolution.y);
Then, let's create a ray from that:
vec3 rayDir = vec3( uv * 2 - 1, -1.0 ); rayDir.x *= v2Resolution.x / v2Resolution.y; // adjust for aspect ratio vec3 rayOrigin = vec3( 0, 0, 0 );
This creates a 3D vector for our direction that is -1,-1,-1 in the top left corner and 1,1,-1 in the bottom right (i.e. we're looking so that Z is decreasing into the screen), then we adjust the X coordinate since our screen isn't square, but our coordinates currently are - no need to even bother with normalizing, it'll be fine. Our origin is currently just sitting in the center.
Then, let's define (loosely) our plane, which is parallel to the XY plane:
float planeDist = 1.0f; // distance between each plane float planeZ = -5.0f; // Z position of the first plane
And solve our equation to t, as math'd out above:
float t = (planeZ - rayOrigin.z) / rayDir.z;
Then, calculate WHERE the hit is by taking that t by inserting it back to the original ray equation using our current direction and origin:
vec3 hitPos = rayOrigin + t * rayDir;
And now we have our intersection; since we already know the Z value, we can texture our plane by using the X and Y components to get a color value:
vec4 color = fui( hitPos.xy ); // XY plane our_color = color;
Of course we're gonna need the actual FUI function, which will be our procedural animated FUI texture, but let's just put something dummy there now, like a simple circle:
vec4 fui ( vec2 uv ) { return length(uv - 0.5) < 0.5 ? vec4(1) : vec(0); }
And here we go:
Very good, we have a single circle and if we animate the camera we can indeed tell that it is on a plane.
So first, let's tile it by using a modulo function; the modulo (or modulus) function simply wraps a number around another number (kinda like the remainder after a division, but for floating point numbers) and thus becomes extremely useful for tiling or repeating things:
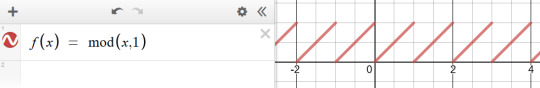
We'll be using the modulo function rather extensively in this little exercise, so strap in. (Illustration via the Desmos calculator.)
vec4 layer = fui( mod( hitPos.xy, 1.0 ) );
This will wrap the texture coordinates of -inf..inf between 0..1:
We also need multiple planes, but how do we combine them? We could just blend them additively, but with the amount of content we have, we'd just burn them in to white and it'd look like a mess (and not the good kind of mess). We could instead just use normal "crossfade" / "lerp" blending based on the alpha value; the only trick here is to make sure we're rendering them from back to front since the front renders will blend over the back renders:
int steps = 10; float planeDist = 1.0f; for (int i=steps; i>=0; i--) { float planeZ = -1.0f * i * planeDist; float t = (planeZ - rayOrigin.z) / rayDir.z; if (t > 0.0f) // check if "t" is in front of us { vec3 hitPos = rayOrigin + t * rayDir; vec4 layer = fui( hitPos.xy, 2.0 ); // blend layers based on alpha output colour = mix( colour, layer, layer.a ); } }
And here we go:

We decreased the circles a bit in size to see the effect more.
Not bad! First thing we can do is just fade off the back layers, as if they were in a fog:
layer *= (steps - i) / float(steps);
We have a problem though: we should probably increase the sci-fi effect by moving the camera continually forward, but if we do, we're gonna run into a problem: Currently, since our planeZ is fixed to the 0.0 origin, they won't move with the camera. We could just add our camera Z to them, but then they would be fixed with the camera and wouldn't appear moving. What we instead want is to just render them AS IF they would be the closest 10 planes in front of the camera; the way we could do that is that if e.g. our planes' distance from each other is 5, then round the camera Z down to the nearest multiple of 5 (e.g. if the Z is at 13, we round down to 10), and start drawing from there; rounding up would be more accurate, but rounding down is easier, since we can just subtract the division remainder from Z like so:
float planeZ = (rayOrigin.z - mod(rayOrigin.z, planeDist)) - i * planeDist;

And now we have movement! Our basic rendering path is done.
Our little fictional UI
So now that we have the basic pipeline in place, let's see which elements can we adapt from Sasha's design pieces.
The first one I decided to go with wasn't strictly speaking in the set, but it was something that I saw used as design elements over the last two decades, and that's a thick hatch pattern element; I think it's often used because it has a nice industrial feel with it. Doing it in 2D is easy: We just add X and Y together, which will result in a diagonal gradient, and then we just turn that into an alternating pattern using, again, the modulo. All we need to do is limit it between two strips, and we have a perfectly functional "Police Line Do Not Cross" simulation.
return mod( uv.x + uv.y, 1 ) < 0.5 ? vec4(1) : vec4(0);

So let's stop here for a few moments; this isn't bad, but we're gonna need a few things. First, the repetition doesn't give us the nice symmetric look that Sasha recommends us to do, and secondly, we want them to look alive, to animate a bit.
Solving symmetry can be done just by modifying our repetition code a bit: instead of a straight up modulo with 1.0 that gives us a 0..1 range, let's use 2.0 to get a 0..2 range, then subtract 1.0 to get a -1..1 range, and then take the absolute value.
vec4 layer = fui( abs( mod( hitPos.xy, 2.0 ) - 1 ) );
This will give us a triangle-wave-like function, that goes from 0 to 1, then back to 0, then back to 1; in terms of texture coordinates, it will go back and forth between mirroring the texture in both directions, which, let's face it, looks Totally Sweet.

For animation, first I needed some sort of random value, but one that stayed deterministic based on a seed - in other words, I needed a function that took in a value, and returned a mangled version of it, but in a way that if I sent that value in twice, it would return the same mangled value twice. The most common way of doing it is taking the incoming "seed" value, and then driving it into some sort of function with a very large value that causes the function to alias, and then just returning the fraction portion of the number:
float rand(float x) { return fract(sin(x) * 430147.8193); }
Does it make any sense? No. Is it secure? No. Will it serve our purpose perfectly? Oh yes.
So how do we animate our layers? The obvious choice is animating both the hatch "gradient" value to make it crawl, and the start and end of our hatch pattern which causes the hatched strip to move up and down: simply take a random - seeded by our time value - of somewhere sensible (like between 0.2 and 0.8 so that it doesn't touch the edges) and add another random to it, seasoned to taste - we can even take a binary random to pick between horizontal and vertical strips:

The problems here are, of course, that currently they're moving 1) way too fast and 2) in unison. The fast motion obviously happens because the time value changes every frame, so it seeds our random differently every frame - this is easy to solve by just rounding our time value down to the nearest integer: this will result in some lovely jittery "digital" motion. The unison is also easy to solve: simply take the number of the layer, and add it to our time, thus shifting the time value for each layer; I also chose to multiply the layer ID with a random-ish number so that the layers actually animate independently, and the stutter doesn't happen in unison either:
vec4 fui( vec2 uv, float t ) { t = int(t); float start = rand(t) * 0.8 + 0.1; float end = start + 0.1; [...] } vec4 layer = fui( abs(mod(hitPos.xy, 2.0)-1), fGlobalTime + i * 4.7 );

Lovely!
Note: In hindsight using the Z coordinate of the plane would've given a more consistent result, but the way it animates, it doesn't really matter.
So let's think of more elements: the best looking one that seems to get the best mileage out in Sasha's blog is what I can best describe as the "slant" or "hockey stick" - a simple line, with a 45-degree turn in it. What I love about it is that the symmetry allows it to create little tunnels, gates, corridors, which will work great for our motion.
Creating it is easy: We just take a thin horizontal rectangle, and attach another rectangle to the end, but shift the coordinate of the second rectangle vertically, so that it gives us the 45-degree angle:
float p1 = 0.2; float p2 = 0.5; float p3 = 0.7; float y = 0.5; float thicc = 0.0025; if (p1 < uv.x && uv.x < p2 && y - thicc < uv.y && uv.y < y + thicc ) { return vec4(1); } if (p2 < uv.x && uv.x < p3 && y - thicc < uv.y - (uv.x - p2) && uv.y - (uv.x - p2) < y + thicc ) { return vec4(1); }

Note: In the final code, I had a rect() call which I originally intended to use as baking glow around my rectangle using a little routine I prototyped out earlier that morning, but I was ultimately too stressed to properly pull that off. Also, it's amazing how juvenile your variable names turn when people are watching.
Looks nice, but since this is such a thin sparse element, let's just... add more of it!
So what more can we add? Well, no sci-fi FUI is complete without random text and numbers, but we don't really have a font at hand. Or do we? For years, Bonzomatic has been "shipping" with this really gross checkerboard texture ostensibly for UV map testing:

What if we just desaturate and invert it?
We can then "slice" it up and render little sprites all over our texture: we already know how to draw a rectangle, so all we need is just 1) calculate which sprite we want to show 2) calculate the texture coordinate WITHIN that sprite and 3) sample the texture:
float sx = 0.3; float sy = 0.3; float size = 0.1; if (sx < uv.x && uv.x < sx + size && sy < uv.y &&uv.y < sy + size) { float spx = 2.0 / 8.0; // we have 8 tiles in the texture float spy = 3.0 / 8.0; vec2 spriteUV = (uv - vec2(sx,sy)) / size; vec4 sam = texture( texChecker, vec2(spx,spy) + spriteUV / 8.0 ); return dot( sam.rgb, vec3(0.33) ); }
Note: In the final code, I was only using the red component instead of desaturation because I forgot the texture doesn't always have red content - I stared at it for waaaay too long during the round trying to figure out why some sprites weren't working.
And again, let's just have more of it:

Getting there!
At this point the last thing I added was just circles and dots, because I was running out of ideas; but I also felt my visual content amount was getting to where I wanted them to be; it was also time to make it look a bit prettier.
Post-production / compositing
So we have our layers, they move, they might even have colors, but I'm still not happy with the visual result, since they are too single-colored, there's not enough tone in the picture.
The first thing I try nowadays when I'm on a black background is to just add either a single color, or a gradient:
vec4 colour = renderPlanes(uv); vec4 gradient = mix( vec4(0,0,0.2,1), vec4(0,0,0,1), uv.y); vec4 finalRender = mix( gradient, vec4(colour.xyz,1), colour.a);

This added a good chunk of depth considerably to the image, but I was still not happy with the too much separation between colors.
A very common method used in compositing in digital graphics is to just add bloom / glow; when used right, this helps us add us more luminance content to areas that would otherwise be solid color, and it helps the colors to blend a bit by providing some middle ground; unfortunately if we only have a single pass, the only way to get blur (and by extension, bloom) is repeatedly rendering the picture, and that'd tank our frame rate quickly.
Instead, I went back to one of the classics: the Variform "pixelize" overlay:

This is almost the same as a bloom effect, except instead of blurring the image, all you do is turn it into a lower resolution nearest point sampled version of itself, and blend that over the original image - since this doesn't need more than one sample per pixel (as we can reproduce pixelation by just messing with the texture coordinates), we can get away by rendering the scene only twice:
vec4 colour = renderPlanes(uv); colour += renderPlanes(uv - mod( uv, 0.1 ) ) * 0.4;

Much better tonal content!
So what else can we do? Well, most of the colors I chose are in the blue/orange/red range, and we don't get a lot of the green content; one of the things that I learned that it can look quite pretty if one takes a two-tone picture, and uses color-grading to push the midrange of a third tone - that way, the dominant colors will stay in the highlights, and the third tone will cover the mid-tones. (Naturally you have to be careful with this.)
"Boosting" a color in the mids is easy: lucky for us, if we consider the 0..1 range, exponential functions suit our purpose perfectly, because they start at 0, end at 1, but we can change how they get here:
So let's just push the green channel a tiny bit:
finalRender.g = pow(finalRender.g, 0.7);

Now all we need is to roll our camera for maximum cyberspace effect and we're done!

Best laid plans of OBS
As you can see from the code I posted the above, I wrote the final shader in GLSL; those who know me know that I'm a lot more comfortable with DirectX / HLSL, and may wonder why I switched, but of course there's another story here:
Given the remote nature of the event, all of the shader coding competition was performed online as well: since transmitting video from the coder's computer to a mixer, and then to another mixer, and then to a streaming provider, and then to the end user would've probably turned the image to mush, Alkama and Nusan came up with the idea of skipping a step and rigging up a version of Bonzo that ran on the coder's computer, but instead of streaming video, it sent the shader down to another instance of Bonzo, running on Diffty's computer, who then captured that instance and streamed it to the main Revision streaming hub. This, of course, meant that in a three-way, Diffty had to run three separate instances of Bonzo - but it worked fine with GLSL earlier, so why worry?
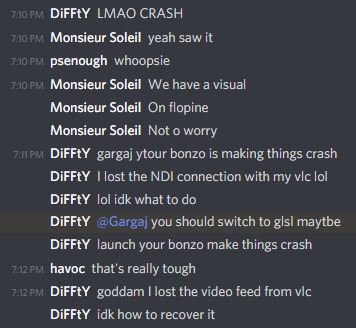
What we didn't necessarily realize at the time, is that the DirectX 11 shader compiler takes no hostages, and as soon as the shader reached un-unrollable level of complexity, it thoroughly locked down Diffty's machine, to the point that even the video of the DJ set he was playing started to drop out. I, on the other hand, didn't notice any of this, since my single local instance was doing fine, so I spent the first 15 minutes casually nuking Diffty's PC to shreds remotely, until I noticed Diffty and Havoc pleading on Discord to switch to GLSL because I'm setting things on fire unknowingly.
This is fine.
I was reluctant to do so, simply because of the muscle memory, but I was also aware that I should keep the show going if I can because if I bow out without a result, that would be a colossal embarrassment to everyone involved, and I only can take one of those once every week, and I was already above my quota - so, I quickly closed the DX11 version of Bonzo, loaded the shader up in a text editor, replaced "floatX" with "vecX" (fun drinking game: take a shot every time I messed it up during the live event), commented the whole thing out, loaded it into a GLSL bonzo, and quickly fixed all the other syntax differences (of which there were luckily not many, stuff like "mix" instead of "lerp", constructors, etc.), and within a few minutes I was back up and running.
This, weirdly, helped my morale a bit, because it was the kind of clutch move that for some reason appealed to me, and made me quite happy - although at that point I locked in so bad that not only did I pay absolutely not attention to the stream to see what the other two are doing, but that the drinks and snacks I prepared for the hour of battling went completely untouched.
In the end, when the hour clocked off, the shader itself turned out more or less how I wanted it, it worked really well with Bullet's techno-/psy-/hardtrance mix (not necessarily my jam, as everyone knows I'm more a broken beat guy, but pounding monotony can go well with coding focus), and I came away satisfied, although the perhaps saddest point of the adventure was yet to come: the lack of cathartic real-life ending that was taken from us due to the physical distance, when after all the excitement, all the cheers and hugs were merely lines of text on a screen - but you gotta deal with what you gotta deal with.
A small sampling of the Twitch reaction.
Conclusion
In the end, what was my takeaway from the experience?
First off, scoping is everything: Always aim to get an idea where you can maximize the outcome of the time invested with the highest amount of confidence of pulling it off. In this case, even though I was on short notice and in an environment I was unfamiliar with, I relied on something I knew, something I've done before, but no one else really has.
Secondly, broaden your influence: You never know when you can take something that seems initially unrelated, and bend it into something that you're doing with good results.
Thirdly, and perhaps most importantly, step out of your comfort zone every so often; you'll never know what you'll find.
(And don't agree to everything willy-nilly, you absolute moron.)
10 notes
·
View notes
Text
To safely explore the solar system and beyond, spaceships need to go faster – nuclear-powered rockets may be the answer
by Iain Boyd
Over the last 50 years, a lot has changed in rocketry. The fuel that powers spaceflight might finally be changing too. CSA-Printstock/DIgital Vision Vectors via Getty Images
With dreams of Mars on the minds of both NASA and Elon Musk, long-distance crewed missions through space are coming. But you might be surprised to learn that modern rockets don’t go all that much faster than the rockets of the past.
There are a lot of reasons that a faster spaceship is a better one, and nuclear-powered rockets are a way to do this. They offer many benefits over traditional fuel-burning rockets or modern solar-powered electric rockets, but there have been only eight U.S. space launches carrying nuclear reactors in the last 40 years.
However, last year the laws regulating nuclear space flights changed and work has already begun on this next generation of rockets.
Why the need for speed?
The first step of a space journey involves the use of launch rockets to get a ship into orbit. These are the large fuel-burning engines people imagine when they think of rocket launches and are not likely to go away in the foreseeable future due to the constraints of gravity.
It is once a ship reaches space that things get interesting. To escape Earth’s gravity and reach deep space destinations, ships need additional acceleration. This is where nuclear systems come into play. If astronauts want to explore anything farther than the Moon and perhaps Mars, they are going to need to be going very very fast. Space is massive, and everything is far away.
There are two reasons faster rockets are better for long-distance space travel: safety and time.
Astronauts on a trip to Mars would be exposed to very high levels of radiation which can cause serious long-term health problems such as cancer and sterility. Radiation shielding can help, but it is extremely heavy, and the longer the mission, the more shielding is needed. A better way to reduce radiation exposure is to simply get where you are going quicker.
But human safety isn’t the only benefit. As space agencies probe farther out into space, it is important to get data from unmanned missions as soon as possible. It took Voyager-2 12 years just to reach Neptune, where it snapped some incredible photos as it flew by. If Voyager-2 had a faster propulsion system, astronomers could have had those photos and the information they contained years earlier.
Speed is good. But why are nuclear systems faster?
The Saturn V rocket was 363 feet tall and mostly just a gas tank. Mike Jetzer/heroicrelics.org, CC BY-NC-ND
Systems of today
Once a ship has escaped Earth’s gravity, there are three important aspects to consider when comparing any propulsion system:
Thrust – how fast a system can accelerate a ship
Mass efficiency – how much thrust a system can produce for a given amount of fuel
Energy density – how much energy a given amount of fuel can produce
Today, the most common propulsion systems in use are chemical propulsion – that is, regular fuel-burning rockets – and solar-powered electric propulsion systems.
Chemical propulsion systems provide a lot of thrust, but chemical rockets aren’t particularly efficient, and rocket fuel isn’t that energy-dense. The Saturn V rocket that took astronauts to the Moon produced 35 million Newtons of force at liftoff and carried 950,000 gallons of fuel. While most of the fuel was used in getting the rocket into orbit, the limitations are apparent: It takes a lot of heavy fuel to get anywhere.
Electric propulsion systems generate thrust using electricity produced from solar panels. The most common way to do this is to use an electrical field to accelerate ions, such as in the Hall thruster. These devices are commonly used to power satellites and can have more than five times higher mass efficiency than chemical systems. But they produce much less thrust – about three Newtons, or only enough to accelerate a car from 0-60 mph in about two and a half hours. The energy source – the Sun – is essentially infinite but becomes less useful the farther away from the Sun the ship gets.
One of the reasons nuclear-powered rockets are promising is because they offer incredible energy density. The uranium fuel used in nuclear reactors has an energy density that is 4 million times higher than hydrazine, a typical chemical rocket propellant. It is much easier to get a small amount of uranium to space than hundreds of thousands of gallons of fuel.
So what about thrust and mass efficiency?

The first nuclear thermal rocket was built in 1967 and is seen in the background. In the foreground is the protective casing that would hold the reactor. NASA/Wikipedia
Two options for nuclear
Engineers have designed two main types of nuclear systems for space travel.
The first is called nuclear thermal propulsion. These systems are very powerful and moderately efficient. They use a small nuclear fission reactor – similar to those found in nuclear submarines – to heat a gas, such as hydrogen, and that gas is then accelerated through a rocket nozzle to provide thrust. Engineers from NASA estimate that a mission to Mars powered by nuclear thermal propulsion would be 20%-25% shorter than a trip on a chemical-powered rocket.
Nuclear thermal propulsion systems are more than twice as efficient as chemical propulsion systems – meaning they generate twice as much thrust using the same amount of propellant mass – and can deliver 100,000 Newtons of thrust. That’s enough force to get a car from 0-60 mph in about a quarter of a second.
The second nuclear-based rocket system is called nuclear electric propulsion. No nuclear electric systems have been built yet, but the idea is to use a high-power fission reactor to generate electricity that would then power an electrical propulsion system like a Hall thruster. This would be very efficient, about three times better than a nuclear thermal propulsion system. Since the nuclear reactor could create a lot of power, many individual electric thrusters could be operated simultaneously to generate a good amount of thrust.
Nuclear electric systems would be the best choice for extremely long-range missions because they don’t require solar energy, have very high efficiency and can give relatively high thrust. But while nuclear electric rockets are extremely promising, there are still a lot of technical problems to solve before they are put into use.

An artist’s impression of what a nuclear thermal ship built to take humans to Mars could look like. John Frassanito & Associates/Wikipedia
Why aren’t there nuclear powered rockets yet?
Nuclear thermal propulsion systems have been studied since the 1960s but have not yet flown in space.
Regulations first imposed in the U.S. in the 1970s essentially required case-by-case examination and approval of any nuclear space project from multiple government agencies and explicit approval from the president. Along with a lack of funding for nuclear rocket system research, this environment prevented further improvement of nuclear reactors for use in space.
That all changed when the Trump administration issued a presidential memorandum in August 2019. While upholding the need to keep nuclear launches as safe as possible, the new directive allows for nuclear missions with lower amounts of nuclear material to skip the multi-agency approval process. Only the sponsoring agency, like NASA, for example, needs to certify that the mission meets safety recommendations. Larger nuclear missions would go through the same process as before.
Along with this revision of regulations, NASA received US$100 million in the 2019 budget to develop nuclear thermal propulsion. DARPA is also developing a space nuclear thermal propulsion system to enable national security operations beyond Earth orbit.
After 60 years of stagnation, it’s possible a nuclear-powered rocket will be heading to space within a decade. This exciting achievement will usher in a new era of space exploration. People will go to Mars and science experiments will make new discoveries all across our solar system and beyond.

About The Author:
Iain Boyd is Professor of Aerospace Engineering Sciences at the University of Colorado Boulder
This article is republished from The Conversation under a Creative Commons license.
3 notes
·
View notes
Text
Tag Game
I may have gone a little overboard
(Rules: recommend 5 shows, books, movies, youtubers, and songs)
Tagged by: @stickers-on-a-laptop
Tagging: @starlightinhumanform @insomniacscoffeecup @whoever else because my mind is empty (if u do it tag me I wanna see :0)
SHOWS
Fruits Basket
The first anime I ever watched. Fruits Basket focuses on a teenage girl and her relationship with a family that is under a curse. There is also a manga and the anime is currently being rebooted and is so heckin pretty.
Accel World
Also an anime/light novel series, that takes place in world with very advanced tech and about teens who have access to a program called Brain Burst which can speed up your mind so fast that you can immensely slow down time, but requires you to play this AR fighting game and fighting against other people with e program frequently in order to continue using it.
She-Ra
The animated series that is a reboot of the old She-Ra that I have enjoyed a lot and am really excited for the finale of.
Elfin Lied
I’m talking a lot about anime, whoops? There is also a manga series that I have not read, but it is about these mutants called Diclonii that are highly and motivated to kill humans, and have invisible arms called “vectors” that can very easily be used to kill people. One of the main characters is a Diclonii that hits her head and loses her memory, becoming harmless and befriending two humans. Very gorey show, as a warning.
Tangled: The Series
I haven’t finished this show yet, I’ve only seen 2/3 seasons, but it is a show taking place after the Disney movie Tangled and about what happens to afterwards. There are a lot of really good things about it, I couldn’t tell you I enjoy every episode as sometimes it’s kind of boring, but I still really like it
BOOKS
The Outsiders
An oldie but a goodie, it’s about a group of greasers in the 60’s, mainly a kid named Ponyboy who is being raised by his older brother and ends up in Some Trouble oop. This book is super old and still has like its own tumblr fan base which you gotta give it some credit for. I feel similarly to this books writer as people do to JK Rowling cause she sucks.
Staying Fat for Sarah Byrnes
Book written almost 30 years ago that discusses body image, abuse, religion, and abortion and all that fun stuff, very
The School for Good and Evil
Another series I haven’t caught up with yet, but the first book is by far my favourite. It about two young girls living in a little village who are taken away to this school for good and evil— but uh oh— the girl who thought she was good goes the evil school and visa versa. It’s a really great story, lots of fairy tale themes.
The Mysterious Benedict Society
I haven’t read these books for a while, but I really really loved it. It’s about these children with extraordinary gifts who are recruited by a man named Mr. Benedict to take down a evil institute. Really cute and interesting and,, good.
Miss Peregrine’s Home for Peculiar Children
Another wonderful book series, that I love to bits. It’s hard for me to describe the first few books because I haven’t read them in a while, but I love the humour of the fourth book which I read more recently and the characters are so good.
MOVIES
The Devil’s Carnival
Three people die and go to “the devil’s carnival” a place that is designed to give them one last chance before deciding whether they should go to heaven or hell. Kind of. It’s a pretty interesting movie, and I would say that it’s my favourite movie, and despite being it being a horror movie it is not very scary. It is also a music, and the original and the movie’s sequel have some great songs
Repo! The Genetic Opera
A film made by many of the people as The Devil’s Carnival, and is also a horror musical. Repo is about a world where surgery is a fashion statement and people are doing all the time just for fun. But Gene Co, the company responsible for all of these surgeries, are sending their hitman after anyone who can’t afford the surgeries they got to take back what was given to them. Also really really good, even if I’m awful at explaining it.
Juno
A movie about a teenager who gets pregnant and plans on letting an older couple adopt her baby. A heckin classic. It’s got Ellen Paige and Michael Cera, and music by Kimya Dawson who is a fav of mine. excellent.
Steven Universe The Movie
I’m a big Steven Universe fan and think the movie is really great and that is all.
YOUTUBERS
helloleesh
Commentary channel who talks a lot about other youtubers. Very nice person who is pleasant to listen to)
Drew Gooden
I really enjoy his humour and have binge watched his stuff several times)
The Rings System
Achannel made by a system that talks a lot about DID/OSDD and who I have found recently. They seem cool!
dangelowallace
Another commentary youtubers, he’s really chill and sarcastic and,, makes good shit
Dear Mr Atheist
A channel that you can probably tell is really religion centric. I don’t watch all of his stuff but he’s made some really really good videos about Christianity and cults and has done some funny stuff to push back against things like the “make america straight again” conference. LGBT+ and super proud of it and supportive of other members of the community.
SONGS
Not giving descriptions for these,,, u should just,,, go experience them
(Picking a Kimya Dawson Song was hard cause I just love her so much lol)
Cult of Dionysus — The Orion Experience
Heart of Brass — Charming Disaster
Circus — Lindsey Mendez
Girl Anachronism — The Dresden Dolls
Being Cool — Kimya Dawson
4 notes
·
View notes
Text
What's StorieBot?
OTO Inch: Guru Upgrade ($67)
100 Chatbot Efforts Each Month
StorieBot has been 3-solutions incorporated in Inch monster bit of technologies:
A simple touse Story Builder Editor to provide you instant Insta-gram Recommended Story Styling with associated quotation stock and bank image bank, frames and stickers to create exactly what you may could imagine.
Insert count-down and surveys into your stories. That raise your participation leading to more individuals seeing your own stories, building your bigger list and earnings from the long term.
This feature lets you send DM broadcast together with url to each of your audience to always participate them and promote will in their mind.
It is pretty well-known that Insta-gram is a huge supply of exposure and traffic. Therefore I am gonna b.s you concerning how new and fresh it's. It Isn't. However, for whatever cause, to the date..beginners without a followers were unable to decode the Insta-gram code in any way.
DM listing
Infinite potential, how many traffic can be the niche becoming on Insta-gram? Countless likely, at least. That is YOURS.
Social Sharing to Ten websites, much more eyeballs, construct larger listing quicker
This chatbot lets you offer and remarket and remain intouch with your readers 24/7/365. It's two manners essentially, active and passive. Passive sells to you personally after initial simple installation while busy provides you with more control and lets you send the information you'd like, if you desire!
Insta-gram and also Insta-gram stories particularly aren't just sexy, but they are also a gigantic cash generating gold-mine that'll EXPLODE your small business to levels you've never believed possible.
This convenient feature enables one to quickly check and understand very well what people already are speaking about which is trending so that you might will have a Storyboard match with articles which only about every one would like to chat around or acquire your own opinion.
That really is actually the heart problem fixer, which grab all the leads from people seeing your stories that are published. Together with the audience technology you're able to observe the name, email, phone, ultimate message delivered and fame standing of most viewers to a Story.
Front End: StorieBot ($ 4-7 )
However Insta-gram at the Upswing, Insta-gram tales are climbing at a rapid rate..."Accroding To Forbes, Over 400 Million People-watch Insta-gram Stories Every Day!" .
Auto-DM
Expand markets, move infinite, do have significantly more control, power & of course without even paying yearly or annual.
Media
I truly expect it'd help you with your buying choice. This method is coming outside with many bonuses to early bird. Require your actions ASAP to your best bargain.
Media
The stories founder is magnificent. It generates professional reports with out to consider about thoughts or manual or design work, and only stocks them on your own accounts, making you traffic extremely fast.
That can be absolute Goldand while there are a number of restrictions about how you're able to collect & see to the leads (to prevent by abusing the device and spamming leads) there is certainly not any affirmation, significance every viewer automatically reaches your contributor!
Pricing
No 3 -- A.I ChatBot -- that chatbot feature subsequently hastens your own list and boosts supplies on them without you being forced to work in any way.
OTO two: StorieEngage ($ 4-7 )
For a brief period, it is possible to catch StorieBot using earlybird discount price in these types of options below. Let us select the best suitable alternatives for you personally before this exceptional deal !
Inch Click Query Catch
No specialized abilities needed whatsoever, everything is explained so clearly from the modules so you can begin as fast as you can.
$0 funding, no advertisements, no manual function, no domain names, no sites. All you have to is that and also an Insta-gram account.
And also to top off it, it makes it possible to receive followers and proceed viral. It's an advanced, all in 1 way that CRACKS Insta-gram wideopen and lets you acquire incredible results even for those who don't have any experience.
No 1 -- Story Creator -- make professional, attractive and engaging stories even in case you don't have any experience at all.
http://groupspaces.com/TrendingNews247/pages/storiebot-review
This really is feature enables one to produce an Instant automobile DM therefore that instantly a Insta-gram user viewpoints that your Story a follow up Immediate Message is delivered into his in box, that you might add a hyperlink and also this has prompt notification and of course has elevated open pace.
4x Your Own Traffic & Income Potential With The Guru Version.
Export Checklist
Well... it unites 3 strong and innovative tools :
Manage the capability to catch leads eternally and market to them by blending a chatbot, leadbot and narrative creator in 1.
Insert 5 More Insta-gram account
Insert into email, get narrative audiences to a email lists.
Program Story
Lately you might also catch information on additional Insta-gram users which aren't your own followers.
Hash-tag Spy, mechanically includes trending, related Hash Tags for a tales
It is no secret the generating prospects and earnings will be getting tougher and harder every single day. Your rivalry on face book and Google Advertising are always . The adverts cost are always . The conversions have reached the time low. Most techniques have become obsolete.
And thus do not be afraid to take a look at the upcoming pieces with the StorieBot Review as I will show you how successful it really is!
This Inch Click Recruitment Cloud According Computer Software Creates Stories For You And Happens Every Story Viewer Right into a Lead Immediately Without Proof -- Never Heard Before.
We all are aware that the life line of an Engaging Story using Insta-gram is contingent upon the naturalness of this Visuals used, thus we've countless of Stock collections on Videos, Photo, illustrations and Vectors that you can just hunt from the niche keyword attention, select and rely your narrative.
Export your narrative audiences together side their name, email and contact number. It's possible to reach them out via emailand contact them via phone after. Until now it was not feasible to leverage Insta-gram traffic and leads similar to this.
500 Chatbot Efforts Each Month
Continuing Forward to the very revolutionary IG technology for Several Years. Every viewer that sees your narrative becomes added into a own lead list in the pc software, at which you are able to remarket in their mind again and again again and again and also have the listing grow incrementally which makes you money .
Most programs only make it possible for you design Insta-gram stories...that is all. And only posting and designing these stories wont require you anywhere unless you are generating leads and closing sales.
This feature lets you place the date you'd want a specific narrative to be released live for your Insta-gram Account n Story.
Let us have a few minutes to see each of the Tremendous benefits develop together:
Just influencers, brands along with societal websites expert's appear to receive all of the power. This varies completely (last but not least ) to day. Let me unveil a brand fresh program named StorieBot which could be your very first A.I applications which may in fact build you immense Insta-gram lists at no cost and mechanically sell them even in the event that you don't have any followers no Insta-gram experience.
We hunted anywhere but we couldn't locate one applications that could let us AUTOMATE our own Insta-gram Stories while generating leads and closing sales for people... That is where StorieBot -- a fantastic, cuttingedge solution comes in to playwith.
That really is really where it will become sexy. Face-book chatbots such as Manychat are popular and have a wide number of qualities that turn every firm on FB to a power station. Well... Insta-gram never needed it. Until today.
You'll Be getting lots of this seller's Best bonuses to get the quick activity (and also a Lot More in the Bottom of the StorieBot Review):
Benefits and Features of StorieBot
Anybody can try so and get outstanding results.
https://karno27.blogspot.com/2019/11/storiebot-review.html https://sites.google.com/view/trendingnewsupdates/storiebot-review
https://www.digitalforumtv.com/storiebot-review/
http://jvreviewwithbonus.over-blog.com/2019/11/what-s-storiebot-no-specialized-skills-demanded-at-all-everything-is-explained-so-clearly-from-the-modules-so-that-you-can-get-started-as-fa.html
http://xtrathings66.eklablog.com/storiebot-review-a177537670
No 2 -- inch Click LeadBot (never done before) -- that may be actually the very first time ever that this is authorized. Every individual who sees your narrative, becomes your contributor -- without verification, inch click as 100% optin speed.
Program Story
Neighborhood Agency, an individual gets access in order to add up to 50 sub-users. It includes an entirely designed search engine optimisation willing website that they are able to simply upload for their own server and begin marketing within an Insta-gram lead creation and promotion bureau. You could even pay off these 50 accounts also bill 1-time or recurring commission in the clientele.
This very first IG stories founder, leadbot & chatbot assembles massive Insta-gram lists at no cost & auto sells for you. This inch Click Integration cloud established applications creates stories foryou personally and turns every narrative viewer to some guide immediately without verification -- not achieved previously.
Trends
1 note
·
View note
Text
What was the Best Graphic Design Software in 2019
The graphic design process requires software tools that can provide solutions to real-time design problems. Ranging from free tools for a beginner designer to paid ones for a pro, you can find all sorts of tools to suit your design niche. If you are in need of any kind of design, a placeholder will do, but for anything beyond that you will simply have to dig deep to find the exact design software that fits your needs. From simple to complex and free to paid, here are some examples of the best graphic design software in 2019.
1) Adobe Illustrator CC
Image source: Digital Arts Online This program is Adobe’s flagship product, perhaps even more so than Photoshop. With hundreds of useful and imaginative options available, Adobe Illustrator allows you to create perfection down to the very last vector of every image. In fact, Adobe Illustrator is considered to be the software that most professional graphic designers use to create high-quality and complex designs. The main focus of Adobe Illustrator is to create pictures from scratch or edit one of the stock photos from its built-in library. More importantly, Adobe Illustrator receives two major updates a year, offering 100 GB of cloud storage with the subscription. Why choose Adobe Illustrator? Adobe Illustrator is a great graphic design tool that doesn’t have a 100% compatibility with other software outside the Adobe software suite, a.k.a the “Creative Cloud”. While Adobe Illustrator is perfectly usable on its own, it truly shines when coupled with the rest of the Adobe graphic design tools. If you’re planning on using other Adobe tools or already are, definitely use Adobe Illustrator to maximize the compatibility synergy. Pros: Supreme precision Professional results Synergizes with other Adobe tools Cons: Subscription based, costing $20.99/month Not 100% compatible with non-Adobe products
2) Adobe Photoshop
Image source: FileInfo The classic and one of the most well-known graphic design software out there, Adobe Photoshop was initially created in 1988 and has been steadily improved since. The software mostly deals with raster images, which are those that are made using a pixel-based program or a digital camera. Professionals wanting a smooth blend of photorealistic elements would definitely want to pick Adobe Photoshop. The various intricate shadow and color manipulation options enables you to take any number of pictures, perfectly splice them together, and achieve something that looks completely real to the point that today, there’s even a verb created out of this which is “photoshopped”. Why choose Adobe Photoshop? The biggest advantage of Photoshop is in its wealth of options and how well they’re documented. Thanks to Photoshop’s popularity, there’s literally hundreds of tutorials and walkthroughs for any given option to help ease a newbie into becoming a graphic design pro. While there is still a learning curve, it’s easier than ever to get into Photoshop and become a pro at using it, which is considered to be a skill in its own right. Pros: Extremely well supported Most compatible graphic design software on the market Professional-quality results Intricate graphic design options Best suited for photorealistic (raster) images Cons: Subscription based, costing $20.99/month Requires some learning
3) Pixlr
Image source: Chrome Web Store In 2019, browsers have become better than ever before. They are versatile and have moderate hardware requirements, allowing them to do everything except graphic design; for that, you’ll also need to use something like Pixlr. Serving as an internet-based collection of graphic design tools, Pixlr allows anyone to jump right in and start creating wonderful graphic design content using only a browser or Pixlr app within seconds. From taking a screenshot to editing and downloading it, Pixlr covers all the basics of capturing photos and editing. Why choose Pixlr? The biggest advantages of Pixlr are the mobility and immediacy it affords. By using only a browser (or app for mobile devices), you can edit, save, and continue editing on the go whenever you’ve got a few minutes of spare time. Professional graphic designers tend to pack it for travel because they can’t work without their special hardware. Hence, Pixlr allows for a very convenient and lightweight work schedule that adapts to you. Advanced Pixlr editor costs $5/month but also reveals its biggest downside – the dearth of options in the free version of Pixlr. Pros: Low hardware and software requirements Free Beginner-friendly Cons: Not suitable for detailed, in-depth work
4) Sketch
Image source: PC Mag Some graphic design projects are so complicated that they require an entire team to complete. That’s where Sketch comes in. Focusing on collaborative solutions, Sketch allows an entire team to coordinate and stay up-to-date through innate Sketch tools while still being a highly competent program for graphic design. Why choose Sketch? In a large organization, it’s hard to keep track of who’s doing what and when. Using Sketch Libraries, the entire company can be on the same page, with designers having a consistent style and managers able to keep track of the progress and make sure everyone is synchronized. Even better, Sketch also works with Dropbox and GitHub. Pros: Contains collaborative tools Free trial Cons: Only available on Mac Not ideal for a single user
5) Inkscape
Image source: Techworld This is a free graphic design tool that can be used for vector-based images. Like other free solutions, it is supported by the community, often leaving you to scratch your head if you were to get stuck on it. If you have any questions, you are meant to engage with the community until you find the answer you were looking for. Inkscape is a welcome addition to the graphic design market, mainly because by using it, we support the idea of free software. It is free both in terms of it costing $0 and it not being constrained by anyone. Why choose Inkscape? Inkscape is an open source, meaning that everything surrounding its functionality is under public scrutiny. You could, in theory, check out the code used to create it and tweak it to your heart’s desire or make your own version of Inkscape and sell it for profit. There is no company lording over how you should use Inkscape – it truly is a free and flexible graphic design tool. The idea of building a community through joint effort is present in every aspect of Inkscape. In fact, users are even able to contribute to translations and write help articles for the program. Although Inkscape is close to being completely finished, it is still considered to be a program that has quite some bugs and quirks you’ll have to find workarounds for. Pros: Free Open source Has a community built around it Cons: Lack of professional support Still in beta as of October 2019
6) Apple Motion
Image source: Larry Jordan More and more static content is being woven together into animations and hosted on video platforms. In cases where you want to rehash and reuse static graphic design leftovers to create an animation, Apple Motion will be a suitable choice. Why choose Apple Motion? Animations and animated transitions are the forte of Apple Motion. The program is well-stocked with pre-made effects that make it easy for anyone to ‘drag & drop’ their way to glitzy and shiny animated content made out of scraps. Pros: User- and beginner-friendly In-depth controls for nuanced effects Cons: Only available on Mac
7) CorelDRAW
Image source: PC Mag Clean, professional, and detailed – those are the main attributes of CorelDRAW. Using the symmetrical drawing function, you can produce mirrored images of anything you draw and edit them however you see fit. From tiny details to massive projects, CorelDRAW does everything a professional graphic designer could ever want a software to do. However, learning how to handle the wealth of options it offers is another challenge for a beginner graphic designer. Why choose CorelDRAW? CorelDRAW is an extraordinary tool with a price to match it. If you’re designing the most intricate and complex graphic designs out there, CorelDRAW is truly one of the best and most reliable software solutions to use. For everything else, there are cheaper and more accessibles programs out there that will do the job just fine. Pros: Interface compatible with touch devices Scalable graphics engine allows adding tiny details to massive projects Produces results of professional quality Cons: Price Steep learning curve
8) Affinity Designer
Image source: AppKed Affinity Designer is a graphic design tool capable of producing designs of sublime quality. You can zoom in and out to your desire, allowing you to screen the details or take a look at the larger image. From miniature designs to massive projects, Affinity Designer can handle it all, provided that you have the hardware to match. Why choose Affinity Designer? Affinity Designer excels at producing otherworldly, creative art that’s inspired by meditation and religious works. If you’re the type of designer that isn’t content with fiddling with stock photos, give Affinity Designer a spin and see what you end up with. Pros: Realistic shadow editing Layered editing One million percent zoom Cons: Hardware requirements
9) Canva
Image source: Canva If Pixlr is too complicated for you, luckily there’s Canva for you to use. With simple graphic design options, Canva isn’t meant to compete with the likes of Adobe Photoshop. However, it merely provides the bare minimum of utility for any user, even those with very little to no graphic design experience, wanting to start their own business or print out a graphic design without having to call anyone to walk them through it. Templates automate the design process even further and now graphic design is doable with just the simple use of a mouse. Why choose Canva? Canva has a clean, minimalistic interface and options to match. There’s not much depth in Canva but that’s actually perfect for senior users who might get flustered encountering the wealth of editing options in a more professional editor. Pros: Perfect for layman users Free Cons: Requires an internet connection
10) Adobe InDesign
Image source: All PC World This is another one of Adobe’s products with the same monthly subscription but a slightly different toolset. It is mainly used for print and publishing design, such as books or any other document that contains multiple pages. The interface is balanced and smartly adjusts to the user’s needs, providing them with contextual information on the go. Plus, the main benefit of Adobe InDesign is that it provides a comprehensive overview of the project, allowing you to troubleshoot problems before you send the file off for printing. Just like with all other Adobe products, you will be nudged towards buying as many other Creative Cloud programs as possible since they all coordinate seamlessly. For example, it’s possible to get the entire Adobe font library within InDesign and then have specific fonts from it used across the entire project done in other Adobe software solutions. Why choose Adobe InDesign? Complex publishing graphic designs that have an intricate structure or layout will be those that will benefit from Adobe InDesign the most. The more different parts there are in the project, the more work there is to be done when changing anything. Thankfully, InDesign allows you to view the entire project at once to find out what should be changed and where. Changes and adjustments become a breeze when InDesign is involved. Pros: Integration with other Adobe products Huge font selection Overview and easy adjustment of the entire project Cons: Subscription based, costs $20.99/month Some features are still barebones
11) Xara Designer Pro X
Image source: Magix Different stages of design might require changes to be made to its parts or the entire project while still maintaining the color and font. Changing individual elements in the projects while keeping its integrity will require a special type of graphic design software, and this is where Xara Designer Pro X comes in. Xara Designer Pro X comes with over a million stock photos and templates. Why choose Xara Designer Pro X? This is one of those software products that attempt to be a single solution for all your graphic design needs, and when it comes to desktop publishing, Xara Design Pro X definitely succeeds. This is quite a capable tool that can equally handle both raster and vector images with ease. However, it can also output documents, images, or even entire HTML websites. Pros: Extensive templates library Available on Steam Cons: Pricey at $299 Windows only
12) Gravit Designer

Image source: Gravit Designer In some instances, you simply can’t do without Windows but that’s an operating system that does become oppressive after a while. The ideal graphic design software would thus allow you to skip and hop from one operating system to another as you please, maintaining all your projects in sync. Gravit is one such cross-platform graphic design solution meant for professionals. Why choose Gravit Designer? Precision vector tools in Gravit Designer make it a child’s play to make creative, dreamy designs out of any shapes and colors imaginable. You can create all the print and digital designs for a product from start to finish, including stationery and app UI. A neat feature of Gravit Designer is the ability to import an image and turn it into a set of fully editable vectors. Pros: Trial and free version Cross-platform Flexible vector editing options Cons: Subscription based, $49/year Read the full article
1 note
·
View note
Text
Lectures - Week 5 (Mixed)
Vulnerabilities
One of the most fundamental concepts in security is the idea of a vulnerability - a flaw in the design of a system which can be used to compromise (or cause an unintended usage of) the system. A large majority of bugs in programming are a result of memory corruptions which can be abused to take control - the most ubiquitous example of this is the buffer overflow; the idea that you can overwrite other data alongside a variable which can change both data and control of a program. The common case is when programmers fail to validate the length of the input when reading in a string in C. Another fairly common bug relates to the overflow of unsigned integers; failing to protect against the wraparound can have unintended consequences in control flow.
‘NOP Sled’
Richard also mentioned in the 2016 lectures the idea of a NOP sled which I found quite interesting. The idea is that due to run time differences and randomisation of the stack, the address the program will jump to (from the return address) can sometimes be difficult to predict. So to make it more likely it will jump where the attack wants, he converts a large set of memory to NOP (no operation) instructions which will just skip to the next one; then finally after the “NOP sled” his code will execute.
printf(”%s Printf Vulnerabilities”);
One of the most hilarious programming vulnerabilities related to the usage of the printf function. Basically if you have an input which is accepted from the terminal and you plug this (without parsing) into a printf, an attacker could potentially feed in an input such as “%s”. (i.e. the title) Now since you haven’t specified a 2nd argument, it will just keep reading all the variables in memory until you hit a “\0″. In fact you can abuse this even further to overwrite memory with the “%n” format string - it will overwrite an integer with the number of characters written so far.
Handling Bugs
Many of the bugs we know of today are actually reported in online databases such as the National Vulnerability Database or Common Vulnerability & Exposures (CVE) Databases. There is actually lots of pretty cool examples online in these, however most of these have been actually fixed - we call them zero day vulnerabilities if the vendor hasn’t fixed them (and if they are then abused then zero day exploits).
When working in security, it’s important to understand the potential legal consequences associated with publicly releasing damaging vulnerabilities in software. This is where responsible disclosure comes in - the idea that if you find a bug you disclose it to a software vendor first and then give them a reasonable period of time to fix it first. I think I discussed an example from Google’s Project Zero Team a couple weeks ago - however just from a quick look there was a case in March where their team released the details on a flaw in the macOS’s copy-on-write (CoW) after the 90 day period for patching. (it’s important to note they gave them reasonable time to fix it)
OWASP Top 10
This was a pretty cool website we got referred to mainly regarding the top bugs relating to web security (link); I’ll give a brief overview here:
Injection - sends invalid data to get software to produce an unintended flow of control (i.e. SQL injection)
Broken authentication - logic issues in authentication mechanisms
Sensitive data exposure - leaks in privacy of sensitive customer data
XML External Entities (XXE) - parsing XML input with links to external bodies
Broken action control - improper access checks when accessing data
Security misconfigurations - using default configs, failing to patch flaws, unnecessary services & pages, as well as unprotected files
Cross-Site Scripting (XSS) - client injects Javascript into a website which is displayed to another user
Insecure deserialisation - tampering with serialization of user data
Using components with known vulnerabilities - out of date dependencies
Insufficient logging and monitoring - maintaining tabs on unusual or suspicious activity, as well as accesses to secure data
Some Common Bugs
Just a couple of the bugs that were explored in some of the 2016 lecture videos:
Signed vs unsigned integers casts - without proper checks can lead to unintended control flow
Missing parenthesis after if statement - only executes next line and not all within the indentation
Declaring array sizes wrong - buf[040] will be interpreted as base 8
Wrong comparators - accidentally programming ‘=‘ when you intended ‘==‘
A lot of the more common bugs we used to have are getting a lot easier to detect in the compilation process; GCC has a lot of checks built in. Valgrind is also a really awesome tool to make sure your not making any mistakes with memory.
WEP Vulnerability
I actually discussed this idea already in the week 1 lectures here - just for the sake of revision I will give a basic overview here. The basic idea is that WEP uses a stream cipher RC4 which XORs the message with a key; however the issue is that we know information about the structure of TCP/IP packets. Within a local network the local IPs are usually of the form A.B.C.D (i.e. 192.168.20.4 for a specific computer) where each letter represents a byte in the range 0-255. (0-255 are usually reserved and not used for computers in the network) Due to subnetting (i.e. with a subnet mask 255.255.255.0 on private network) the last byte D is usually the only one that changes - this means we effectively have 254 combinations.
Since we know where the destination address is located within the packet, an attacker can potentially record a packet and modify this last byte - they can send out all 256 possible combinations to the router (remember it’s encrypted so we can’t limit it to 254). The router will then decrypt the message and then encrypt it with the key used for communications with the attacker - and voila the system is compromised.
Hashes

Richard gave a brief overview of the basis of many of our hash functions which is the Merkle-Damgard construction. The basic idea behind it is to break the message into blocks - the size varies on the hash type and if its not a multiple of the required length then we need to apply a MD-compliant padding function. This usually occurs with Merkle-Damgard strengthening which involves encoding the length of the original message into the padding.
To start the process of hashing we utilise an initialisation vector (number specific to the algorithm) and combine it with the first message block using a certain compression function. The output of this is then combined with the 2nd message block and so forth. When we get to the end we apply a finalisation function which typically involves another compression function (sometimes the same) which will reduce the large internal state to the required hash size and provide a better mixing of the bits in the final hash sum.
Length Extension Attacks
I think after looking at the Merkle-Damgard construction it now becomes pretty obvious why using MACs of the form h(key|data) where the length of the data is known are vulnerable to length-extension attacks. All you need to be able to reverse in the above construction is the finalisation function and the extra padding (which is dependent upon the length which we’re assuming we know); then you can keep adding whatever message blocks you want to the end!
Digital Signatures
The whole idea behind these signatures is providing authentication - the simplest method of this is through asymmetric key encryption (i.e. RSA). If your given a document, you can just encrypt it with your private key - to prove to others that you indeed signed it, they can attempt to decrypt it with your public key. There is a problem with this approach however - encryption takes a lot of computation and when the documents become large it gets even worse. The answer to this is to use our newfound knowledge of hashing for data integrity - if we use a hash (’summary of the document’), we can just encrypt this with our private key as a means of signing it!
Verifying Websites
One of the hardest issues we face with the ‘interwebs’ is that it is very difficult to authenticate an entity on the other end. We’ve sort of scrambled together a solution to this for verifying websites - certificate authorities. (I could go on for ages about the problems with these being ‘single points of failure’ but alas I don’t have time)
The idea behind these bodies is that a website will register with the entity with a specific public key. The CA will then link this public key (in a “big ol’ secure database”) with the ‘identity’ of the website. To understand how it works its best to consider the example of when you access any website with HTTPS. (i.e. SSL) When you visit www.example.com, they will then provide their public key and a digital signature of key (signed by the cert authority’s private key) in the form of a X.509 certificate. The user will have access to CA’s public key as part of their browser and will then be able to verify the identity of the website. (the cert is encrypted with the CA’s private key - see above image) An attacker is unable to fake it as they don’t know the certificate authorities’ private key.
Attacking Hashed Passwords
Given there is only a limited number of potential hashes for each algorithm, there is a growing number of websites online which provide databases of plaintext and their computed hashes - these are what we refer to as hash tables. We can check a hash very quickly against all the hashes in this database - if we find a match, we either know the password or have found a collision.
Rainbow tables are a little more complex - in order to make one you need a hashing function (the same as the password) and a reduction function; the latter is used to convert the hash into text (i.e. a base64 encode and truncation). These tables are made of a number of ‘chains’ of a specified length (let’s say we choose 1,000,000) - to create a chain you start with a random seed then apply both the above functions to this seed. You then iteratively do this process another 1,000,000 times (chosen length) and store the final seed and value (only these). In order to try and determine a match to the rainbow table, you apply the same two functions to the password for the required length - however, at each step you compare the hash to the result of each of the chains in the table. If you find a match, you can reproduce the password.
Both of the attacks against password hashes described above rely on an attacker doing a large amount of work in advance, which they will hopefully be able to use in cracking many passwords in the future. (it’s basically a space-time tradeoff) An easy way we can destroy all the work they have done is through a process known as salting. Basically what you do is generate a random string which you concatenate with the password when creating a hash - you need to store this alongside the password in order to check it in future. This means an attacker can’t use pre-computed tables on your hash; they have to do all the work again for your particular salt!
Richard discussed another interesting concept called ‘key stretching’ in the lectures - it’s basically the idea that you can grab a ‘weak password hash’ and continuously hash it with a combination of the (’hash’ + ‘password’ + ‘salt’). This process of recursively hashing makes it insanely difficult for an attacker to bruteforce. This is combined with the effects of a ‘salt’ which (on its own) renders rainbow tables (’pre-computed hashes’) useless.
Signing Problems with Weak Hashes
One of the problems with using a hash which is vulnerable to second-preimage attacks is that it becomes a lot easier to sign a fake document. Consider the example of a PDF document certifying that I give you $100. If you wanted you could modify the $100 to $100,000, however this would change the resultant hash. However since it’s a PDF you could modify empty attribute fields or add whitespace such that you can modify the hash an enormous amount of times (i.e. to bruteforce the combinations). Since the hash is vulnerable to second-preimage this means that given an input x (the original signed document) we are able to find an x’ (the fake signed document) such that h(x) = h(x’).
Dr Lisa Parker (guest speaker)
I wasn’t able to make the morning lecture, although I will try and summarise my understanding of the key points from this talk:
More holistic approaches to systems improvement have better outcomes (’grassroots approach’ is just as important as targeted)
Unconscious bias is present across a wide variety of industries (i.e. judges harsher before lunch, doctors prescribing drugs for free lunch)
Codes of conduct intended to reduce corruption; pharmaceuticals try to dodge with soft bribes, advertising, funding research
Transparent reporting reduces malpractice
Enforcing checklists useful for minimising risk
OPSEC Overview (extended)
We traditionally think of OPSEC has been based in the military, however many of the principles can apply in more everyday scenarios:
Identifying critical information
Analysis of threats
Analysis of vulnerabilities
Assessment of risk
Application of appropriate OPSEC measures
A lot of the ideas behind gathering information (recon) revolve around collecting “random data”, which at first may not appear useful, however after managing to piece them together, they are. One of the quotes from Edward Snowden (I think) I found quite interesting, “In every step, in every action, in every point involved, in every point of decision, you have to stop and reflect and think, “What would be the impact if my adversary were aware of my activities?””. I think it’s quite powerful to think about this - however at the same time we don’t want to live with complete unrealistic paranoia and live as a hermit in the hills.
One of the easiest ways to improve your OPSEC is through limiting what you share online, especially with social media sites. Some of the basic tips were:
Don’t share unless you need to
Ensure it can’t be traced (unless you want people to know)
Avoid bringing attention to yourself
You can try and conceal your identity online through things like VPNs and Tor Browser. It is important that in identities you have online that you don’t provide a means to link them in any way (i.e. a common email) if you don’t want someone to be able to develop a “bigger picture” about you. For most people, I think the best advice with regards to OPSEC, is to “blend in”.
Passwords (extended)
I am really not surprised that the usage of common names, dates and pets is as common as it is with passwords. Most people just like to take the lazy approach; that is, the easiest thing for them to remember that will ‘pass the test’. Linking closely with this is the re-use of passwords for convenience - however for security this is absolutely terrible. If your password is compromised on one website and your a ‘worthy target’, then everything is compromised.
HaveIBeenPwned is actually a pretty cool website to see if you’ve been involved in a breach of security. I entered one of my emails, which is more of a ‘throwaway one’ I use for junk-ish accounts on forums and whatnot - it listed that I had been compromised on 11 different websites. I know for a fact that I didn’t use the same password on any of those; secondly for most of them I didn’t care if they got broken.
I think offline password managers are an ‘alright way’ to ensure you have good unique passwords across all the sites you use. (be cautious as they can be a ‘single point of failure’) However when it comes to a number of my passwords which I think are very important - I’ve found just randomly generating them and memorising them works pretty well. Another way is to form long illogical sentences and then morph them with capitalisation, numbers and symbols. You want to maximise the search space for an attacker - for example if your using all 96 possible characters and you have a 16-character password then a bruteforce approach would require you to check 2^105 different combinations (worst-case).
The way websites store our passwords is also important to the overall security - they definitely shouldn’t be stored in plaintext, should use a ‘secure hash function’ (i.e. not MD5) and salted. I’m pretty sure I ranted about a mobile carrier that I had experiences with earlier in my blog, that didn’t do this. This means if the passwords were ‘inevitably’ all stolen from the server, the attacker just gets the hashes, and they can’t use rainbow tables because you hashed them all. Personally, I really like the usage of multi-factor authentication combined with a good password (provided those services don’t get compromised right?). Although, you want to avoid SMS two-factor as it’s vulnerable to SIM hijacking.
4 notes
·
View notes
Text
Title Vectronom Developer Ludopium Publisher ARTE France Release Date May 29th, 2019 Genre Rhythm, Music, Puzzle Platform PC, Switch Age Rating E for Everyone Official Website
If you’ve ever wondered what an EDM soundtrack would look like if it were visualized in the form of colorful vector images, then wonder no more. Vectronom is a rhythmic puzzle game where players are tasked with guiding a cube through mazes of changing obstacles while matching their movements to the beat of EDM which plays in the background. At first glance, this may seem like an easy and basic rhythm game, but after about two minutes of playtime, you’ll begin to see how wrong that initial assumption is. This title comes to us from an indie studio out of Germany- Ludopium. It was published by ARTE in late May and is currently available for PC, Mac, and the Nintendo Switch. For the purposes of this review, I’ve taken a look at the Steam version.
I generally structure my reviews by discussing gameplay, visuals, and sounds in three distinct paragraphs. In the case of Vectronom however, I don’t feel like that structure makes sense. All three of those above categories work in tandem here to create a rather hypnotic experience for the player. To examine them one at a time just doesn’t feel right. Rather, let’s start by discussing how you progress through the game. The entirety of Vectronom’s gameplay is centered around traversing obstacle courses while keeping in beat with the music. These obstacle courses are made up of entirely of vector shapes. Obstacles include spiky prisms and pitfalls that often appear out of nowhere. Each course is a bit different, but each new course tends to build off of the preceding one. Once you complete four or five courses, you will essentially complete one level. There are ten levels in all plus one bonus mini level at the end. Sounds easy enough, right?
Fear not, for there is a great deal of challenge involved. This challenge becomes apparent once you begin controlling your cube. The controls themselves are pretty responsive, but I found controlling the cube to be very challenging. This was because I needed to time my movements perfectly with the beat of the music while also trying to memorize patterns for how stages would change with the music. When I say change, I mean that for each beat in a stage’s song, spikes may appear in certain areas, certain parts of the ground might disappear, and other parts of the ground might reappear. For many stages, the designs will change entirely whenever the beat changes. It would be easy enough to sit back and memorize the patterns that these changes follow since they are not done at random, but half of your end score is determined by how accurately you are able to match your movements to the beat. Your brain has to keep track of both each beat and memorize the stage’s patterns at the same time.
Additionally, the controls themselves are meant to add to the level of difficulty. All levels are presented from a top-down isometric view and you are able to move diagonally up, diagonally down, diagonally left, and diagonally right. You will of course be using the WASD keys, so it may take a moment to get used to this control scheme when you first begin playing. I often found it tempting to just move asynchronously from the beat of the music, but this of course would’ve lowered my score and I actually ended up making more mistakes that way.
Speaking of the music, let’s tackle the sound design’s score now. As I alluded to above, Vectronom is backed with an upbeat EDM soundtrack with each stage’s track building off of the previous one in some way. While none of them stood out to me as overly memorable after the fact, they were all very entrancing and I feel as though this was very intentional. Once again, playing this title is meant to be a hypnotic experience and the music certainly lends itself well to that. Since it’s paramount to listen carefully and follow along with the beat to progress through each level, it’s definitely nice that the music is not only well-paced but enjoyable to listen to as well.
This slideshow requires JavaScript.
Perhaps I should have called this out earlier, but one thing to note for players with epilepsy is that the visuals in Vectronom include constantly flashing colors. Static backgrounds can be toggled at any time though if you select that option from within the accessibility tools list in the options menu. In fact, there are actually a surprising number of accessibility options available for those who need to fine tune the game to suit their needs. For those with deuteranopia, protanopia, or tritanopia (forms of color blindness), there are options for adjusting the colors accordingly to compensate. Additionally, there is a grayscale option which can be selected. While perhaps not a true accessibility option, you can also adjust the margin of error for player input from extremely tight to ludicrously loose. I thought that the color settings were a very thoughtful addition and I actually tried them out myself just to see what the experience would be like.
Clocking in at just over 3 hours for a full playthrough (for this reviewer), Vectronom is certainly not a very long game. It is a very engrossing title though and I feel that given the hypnotic, relaxing nature of its levels, it has a relatively high replay value. You can also revisit levels that you were previously unable to obtain the highest scores in and replay them. This is the type of game that you put on when you have a great deal of outside stressors to worry about and just want something to get lost in. There’s no story, no characters, and no great prize at the end of your tale. There’s just you, your cube, and a bumpin’ EDM soundtrack to become entranced in. It may have been relatively short, but for the time that I spent with this one I couldn’t find any glaring flaws. Combined with a relatively low price point of $9.99 USD, I’d say this one’s worth your time if you’re looking for something to play around with in your down time.
[easyreview cat1title=”Overall” cat1detail=”” cat1rating=”4″]
youtube
A review copy was provided by the publisher.
REVIEW: Vectronom Title Vectronom
1 note
·
View note
Text
Neural Network Basics
Purpose: to breach the semantic gap between humans and machines. Humans have them naturally built into our brains; we must build them within machines.
Essentially a graph structure, where each node performs a simple computation given an input and each edge carries the generated signal from one node to another. These edges may be weighted more heavily to emphasise the importance of a signal. Each node has various inputs passed into them, and if a particular threshold is reached then the activation function will output a signal and the particular node will be activated and this output will serve as the input for the next node. Our inputs, for this project, would simply be the mentioned vectors of pixel intensities at particular points.
In the diagram we have a very basic NN that takes 3 inputs + a bias, and which are passed into the node to produce a weighted sum that will then be judged by the activation function to determine whether the inputs were sufficient to justify an output.
The step function before the 'signal' is sent out is meant to filter the signal - if the value is too low/signal too weak, no sendo. If it passes the threshold, yes. This is a very basic activation function that will produce a signal if the sum reaches some threshold.
Here, our threshold is 0. If you remember your HS math, you'll know that this function is indeed not differentiable, which can lead to some issues down the line so we typically use a differentiable function as the activation function instead instead such as the sigmoid.
The sigmoid had it own issues however, so the ReLU function was born. Well, perhaps not born but came into use in NN creation.
Sigmoid (below)

ReLU (rectified linear unit) also known as a 'ramp function' and it’s equation (below)

I shan't go into detail, but notice that the sigmoid's f(x) value is bound at 1 and so will will not be able to produce any signal greater than 1 which is necessary in some NN applications. Sigmoids also take forever to compute, whilst ReLU is literally just a line.
ReLU's cousin, the Leaky ReLU, also exists and may be used as an alternative. Which one you use really depends on your project. As the name suggests, it is a version that is leaky i.e. when input < 0, it will 'leak' a bit of signal.

The ELU (still below)

Empirically, variants of the ELU have enjoyed better performance than its cousins.
Feedforward Network Architecture
The cornerstone of NN research, feedforward networks consist of nodes that will only feed into the next layer of nodes, never feeding backward - hence feedforward.
In feedforward networks, there are multiple layers, each with different functions. Layer 0 generally serves as the layer for input, where all the data enters and is processed by its nodes. Each node takes a different column/vector as an input, so for e.g. if we were training a NN to classify pictures of cats, one node may take fluffiness data and another may take tail length data.
Layers 1 and 2 in the above image serve as the layers which help process Layer 0's output and Layer 3 above is the output layer where the input data is classified into their various labels, with each node classifying a different label e.g. an NN classifying handwritten digits would have an output layer consisted of 10 nodes for each digit from 0-9 and similarly a NN classifying images of cats will simply have an output layer of a single node, which will either output 1 for yes it's a cat, or 0 for no it's not a cat.
The Perceptron Algorithm:
Not gonna go into detail since it’s not really interesting. Some believe it useful to understand. I don't.
Essentially trains a straight line of the above form to separate data belonging to two different labels by adjusting the values of that n looking symbol:

Looping over each datapoint/vector and its corresponding label
Taking the datapoint and passing it into the line function which calculates the value.
Updates each weight of the line function by the size of each step according to the output. If the output is smaller than expected, increase each weight by the step. If output is larger, decrease each weight by the step. Repeat until the line function output converges
And here’s the end product when we train the perceptron (the line that separates the data points).

Training a NN - Backpropagation:
Arguably the most important in machine learning, backpropagation is consisted of two phases:
Propagation
Backward pass
Let's look at how backpropagation and NN's work by training a NN to learn to XOR by training it on the XOR dataset which is consisted of the entire XOR domain. i.e. 0 XOR 0 is 0, 0 XOR 1 is 1 etc. etc.
Notice the dataset on the right has a third vector consisted of all 1's. This represents our bias vector and will serve as a third data vector, requiring us to add an additional input node for our NN.

Our NN will require only one single output node which will output either 1 or 0.
How deep a hidden layer should be (recall that the hidden layers were the layers that weren't the output or input layer) is totally subjective but for easier problems like this, a single hidden layer should be fine.

After deciding on the architecture, we then must initialise the weights leading from each node. This can be done in various ways but we initialise them randomly here.

The forward pass begins which means that simply a datapoint is input into the network, and each node processes the input by multiplying it by the weights and sends a signal to the next node according to the output of the activation function. This proceeds until the output layer is reached and we are able to check its output.
If the output is lower than 0.98 and greater than 0.02, we need to apply a backward pass.
We first need to compute the error, which will simply be the difference between the predicted label and the true label of the datapoint that we're trying to predict and if you recall my earlier post, you'll remember that this error was computed using the loss function.
More specifically, we're computing the error with respect to the case, at that particular datapoint, that a particular layer were removed from the network.
We can do this by computing the partial derivative of that loss function with respect to that particular layer and multiplying the result by our step size(recall that in gradient descent we took random 'steps' blindly toward the minimal point on the loss function). If this sounds complicated, then well you'd be right, it is but luckily we don't need to understand it since we're using a high level library in Keras. If you're using Caffe, you'll probably need to know it so here's some reading. WARNING PRETTY DIFFICULT STUFF.
I should've done XXS or site injection for my project. http://neuralnetworksanddeeplearning.com/chap2.html
Yeah so anyway after we've obtained the loss values, multiplied it with the step size we simply add this value to the weight matrix of the layer. BUT wait what’s the weight matrix of the layer? The weight matrix simply denotes the edge weights from the previous layer to the current layer, and are just an easy way to represent these edges.
So the algorithm goes like this:
Forward pass up to the end
Find error and step size product of last layer
Add it to the weight matrix of the current layer
Iterate to the previous layer and repeat ad nauseam or until you've gotten to the input nodes
That was easy.
1 note
·
View note