#user activity monitoring
Explore tagged Tumblr posts
Text
Building Resilience In The Face Of Gaslighting At Work

In today’s work environment, the term "gaslighting" has gained recognition as a significant issue that affects employee mental health and productivity. This form of psychological manipulation can be subtle yet devastating, leading individuals to question their own perceptions, memories, and feelings. Understanding how to build resilience against such behavior is crucial for maintaining well-being and ensuring a positive work experience.
Understanding Gaslighting
Gaslighting at work often manifests in ways that can be difficult to identify. It may begin with seemingly harmless comments or actions that undermine your confidence. For instance, a colleague may dismiss your contributions in meetings or take credit for your ideas. Over time, these experiences can accumulate, creating a toxic environment where you feel increasingly isolated and doubting your capabilities.
The impact of gaslighting can be profound, affecting not only your professional life but also your personal well-being. Victims may experience anxiety, depression, and a decline in job performance. Recognizing gaslighting is the first step towards addressing it and reclaiming your sense of self.
Building Resilience

Resilience is the ability to adapt and bounce back from adversity. When faced with gaslighting, building resilience involves several strategies:
#1 Cultivating Self-Awareness: The first step in combating gaslighting is to strengthen your self-awareness. Pay attention to your emotions and reactions in various situations. Keeping a journal can help you document interactions that feel off or manipulative. This record will not only validate your experiences but also serve as a reminder of your own thoughts and feelings when you begin to doubt them.
#2 Establishing Boundaries: Setting clear company goals & boundaries is essential for protecting yourself from manipulative behaviors. Identify what behaviors you find unacceptable and communicate these boundaries to your colleagues or supervisors. For example, if a coworker continually interrupts you, assertively request that they allow you to finish your thoughts before responding.
#3 Seeking Support: Finding allies in the workplace can significantly bolster your resilience. Discuss your experiences with trusted colleagues or mentors who can offer perspective and advice. Having a support system can provide reassurance and help you feel less isolated. Additionally, consider seeking
Creating a Supportive Work Environment

While personal resilience is vital, fostering a culture that discourages gaslighting is equally important. Organizations should prioritize training programs that address workplace bullying and psychological safety. Open discussions about mental health can help create a work environment where employees feel safe to speak out about their experiences.
Encouraging leadership to model positive behavior and promote inclusivity can also play a significant role in preventing gaslighting. When leaders demonstrate empathy and support, it sets the tone for the entire organization, helping to combat manipulative behaviors before they take root.
Professional guidance, such as therapy or coaching, can help you develop coping strategies tailored to your situation.
Practicing Self-Care: Prioritizing your mental and physical health is crucial when dealing with the stresses of gaslighting. Engage in activities that promote relaxation and joy, whether it's exercise, meditation, or hobbies. Taking care of yourself can enhance your emotional resilience and improve your overall outlook.

Documenting Interactions: Keeping detailed records of your interactions can be a powerful tool against gaslighting. Document conversations, emails, and any instances of manipulation. This documentation not only provides clarity during moments of doubt but can also serve as evidence if you need to escalate the issue to HR or management.
Reframing Your Perspective: Changing how you perceive the situation can empower you. Instead of viewing yourself as a victim, focus on your strengths and the skills you bring to the table. Reframing your mindset helps you regain a sense of control and confidence, which is crucial when navigating a challenging workplace environment.
Educating Yourself: Knowledge is power. Educate yourself about gaslighting and its effects. Understanding the psychology behind manipulative behaviors can help you identify tactics used by gaslighters and develop effective counter-strategies. This knowledge can also be shared with others, raising awareness and creating a more supportive work culture.
You can also watch: EmpMonitor: Manage Remote Work Easily
youtube
Conclusion
Building resilience in the face of gaslighting at work requires a proactive approach and a strong support network. By cultivating self-awareness, establishing boundaries, seeking support, and practicing self-care, you can strengthen your ability to withstand and overcome manipulative behaviors. Moreover, fostering a culture that values open communication and psychological safety is essential for ensuring that all employees can thrive in their work environment. By standing together against gaslighting, we can create healthier workplaces where everyone feels valued and empowered.
#gaslighting at work#employee gaslighting#gaslighting at work examples#workplace gaslighting#user activity monitoring#signs of gaslighting at work#Youtube
0 notes
Text
Importance of User Activity Monitoring (UAM): A Comprehensive Guide
Discover the importance of User Activity Monitoring (UAM) in this comprehensive guide. Learn how UAM enhances security, improves productivity, and ensures compliance with regulatory requirements. Understand the benefits of monitoring user activities to protect sensitive data and optimize organizational efficiency.
Visit - https://www.workstatus.io/blog/workforce-management/understanding-user-activity-monitoring-uam-and-its-importance/
0 notes
Text
Why User Activities Monitoring is Essential for Remote Work Management?

The rise of remote work has transformed the traditional office environment, offering flexibility and convenience to employees and employers. However, this shift also brings unique challenges, particularly in managing and monitoring employee productivity. User activity monitoring has emerged as a crucial tool for remote work management, providing insights into employee performance, ensuring data security, and boosting overall productivity.
In this comprehensive guide, we will explore the benefits of employee monitoring, the importance of user activities monitoring, and how employee productivity tracking can enhance remote work management.
What it is?
User activity monitoring involves tracking and analyzing the actions and behaviors of employees on their work devices. This includes monitoring internet usage, application usage, keystrokes, screen captures, and more. The primary goal is to ensure that employees are engaged in productive tasks and identify potential issues hindering their performance.
The Benefits of Employee Monitoring
Implementing user activity monitoring offers numerous benefits, making it an essential practice for remote work management. Here are some key advantages:
1. Enhanced Productivity
One of the primary benefits of employee monitoring is the significant boost in productivity. By tracking user activities, employers can identify time-wasting activities, such as excessive social media usage or non-work-related browsing. This information allows managers to address these issues promptly, ensuring employees remain focused on their tasks.
2. Improved Accountability
Activities monitoring fosters a culture of accountability among remote employees. Knowing that their activities are monitored encourages employees to adhere to company policies and maintain high standards of work. It can lead to increased motivation and a sense of responsibility towards their tasks.
3. Data Security
In a remote work environment, data security becomes a critical concern. Employee productivity monitoring software can help detect unauthorized access to sensitive information or potential security breaches. This proactive approach ensures that company data remains secure, even when employees work from different locations.
4. Performance Insights
Monitoring user activities provides valuable insights into employee performance. Managers can identify top performers and those who may additional support or training. This data-driven approach allows for targeted interventions, ultimately leading to a more efficient and effective workforce.
5. Compliance and Legal Protection
Many industries are subject to strict regulatory requirements. User activity monitoring helps ensure compliance with these regulations by tracking and documenting employee actions. In case of legal disputes or compliance audits, having a detailed record of user activities can provide essential evidence and protect the company from potential liabilities.

Implementing Employee Productivity Tracking
Here are some steps for implementing employee productivity tracking to get started:
1. Choose the Right Software
Selecting the right employee productivity monitoring software is crucial for effective activity monitoring for users. Look for software that offers comprehensive tracking features, real-time reporting, and robust data security measures. Popular options include Empmonitor, Time Doctor, Hubstaff, and Teramind, each offering unique features tailored to different business needs.
2. Set Clear Expectations and Goals
Define clear expectations and goals for your remote employees. Let them know what activities will monitored and how performance will be evaluated. Setting specific, measurable goals helps employees understand what is expected of them and motivates them to stay focused on their tasks.
3. Provide Training and Support
Offer training sessions to help employees understand how the monitoring software works and how it can benefit them. Provide ongoing support to address any technical issues or concerns that may arise. A well-informed and supported workforce is more likely to embrace user activity monitoring positively.
4. Regularly Review and Analyze Data
Regularly review the data collected through employee productivity tracking. Analyze the trends and patterns to identify areas for improvement. Use this data to provide constructive feedback to employees, recognize their achievements, and implement necessary changes to enhance productivity.
Addressing Concerns and Ensuring Privacy

While user activity monitoring offers numerous benefits, it is essential to address employee concerns and ensure privacy. Here are some best practices to maintain a balance between monitoring and privacy:
1. Limit Monitoring to Work-Related Activities
Ensure that monitoring is limited to work-related activities and does not intrude on employees' privacy. Avoid tracking activities outside of work hours or monitoring non-work-related applications and websites.
2. Use Anonymized Data
Where possible, use anonymized data to analyze overall trends and patterns without identifying individual employees. This approach helps maintain privacy while still providing valuable insights into productivity.
3. Establish Clear Policies
Establish clear policies regarding user activity monitoring and communicate them to employees. Ensure that employees understand their rights and responsibilities and provide a channel for them to voice any concerns or grievances.
4. Regularly Update and Audit Monitoring Practices
Regularly update your monitoring practices to keep up with changing technologies and regulations. Conduct audits to ensure that the monitoring processes are fair, transparent, and compliant with legal requirements.
You Can Also Watch:
youtube
Conclusion
User activities monitoring is an essential tool for remote work management, offering numerous benefits, including enhanced productivity, improved accountability, data security, and valuable performance insights. By implementing effective employee productivity tracking strategies and addressing employee concerns, companies can create a balanced and productive remote work environment. Embrace the power of user activity monitoring to unlock the full potential of your remote workforce and drive your business toward success.
#User activities monitoring#benefits of employee monitoring#employee productivity tracking#employee productivity monitoring#employee monitoring#Youtube
0 notes
Text
Tautulli Plex Media Server Monitoring and Statistics
Tautulli Plex Media Server Monitoring and Statistics #homelab #selfhosted #Tautulliguide #Plexserveranalytics #Tautulliinstallation #PlexMediaServermonitoring #Tautullifeatures #Tautulliuseractivity #Plexlibrarystatistics #recentlyaddedmediatracker #plex
More and more people are cutting the cord and using self-hosted streaming services like Plex Media Server. Plex is a great solution. However, there is a 3rd party add-on you may not know about that makes it even better. It is called Tautulli, and it helps you to make sure you don’t miss any details of your Plex Media Server. Let’s learn more about Tautulli, what it is, how it is installed, and…

View On WordPress
#Plex library statistics#Plex Media Server monitoring#Plex server analytics#Plex server optimization#recently added media tracker#Tautulli configuration#Tautulli features#Tautulli guide#Tautulli installation#Tautulli user activity
0 notes
Text
URGENT: Congress about to pass a mass censorship and surveillance bill under the guise of "protecting children"
May 13 2023
The Senate has been in a "do something!" mode regarding children's online safety. They're using this as an excuse to push for widespread internet censorship and surveillance. The EARN IT Act, has a slimmer chance of passing with widespread opposition and some senators saying they won't vote for it. TLDR;The real threat is actually KOSA (s.1409), the Kid's Online Safety Act, which will mass censor and surveill the entire internet by giving all 50 state attorney generals the power to remove content that is "harmful" for kids, and force you to upload your govt ID online to access the internet. I'll explain how it works below the action items but it's absolutely urgent that anyone who likes having a free and open internet fights back. It's all hands on deck, because this has so much public support it's insane:
HOW TO FIGHT KOSA
CALL YOUR REPRESENTATIVES & THE COMMERCE COMMITTEE
This is a link to the Senate Commerce Committee phone numbers and a call script to read off of. (202) 224-3121 connects you to the congressional hotline
Opposition is getting drowned, and these upcoming weeks will be heavy for lobbying and they're using young people to do it. We NEED to show these senators that young people are actually opposed to this and don't want it.
2. Sign these petitions
Open Letter Against KOSA
Petition 1
Petition 2
Petition 3
Petition 4
Resistbot: Text PHJDYH to 50409
3. Spread the word.
The opposition is getting absolutely drowned online. Dove has nearly 100k signatures to push for KOSA. Influencers on tiktok are pushing for this without ever having read the bill. Fucking Lizzo is sponsoring it. If you have twitter, reddit, tiktok, are in any community, SPREAD THE WORD, PLEASE.
Here is a linktree with all the above petitions for easy shargin: Link to linktree
HOW KOSA WORKS
First, KOSA pressures platforms to install filters that would wipe the net of anything deemed “inappropriate” for minors. This means instructing platforms to censor. We saw how these filters impacted websites firsthand with tumblr in 2018, with not only blocking all adult content but also sfw queer content such as suicide hotlines, art archives, wiping out entire blogs because they had queer fandom related posts, etc. Places that already use content filters have restricted important information about suicide prevention and LGBTQ+ support groups. KOSA would spread this kind of censorship to every corner of the internet. And who gets to decide what is and isn't harmful for minors? Oh don't worry, just every single state attorney general and the FTC, which is appointed by the president. You know, the same attorney generals that just banned gender-affirming healthcare under the guise that it "ruins mental health" of minors. This is why the Heritage Foundation was one of the first to sponsor the bill because they can use it to censor trans content, and Senator Marsha Blackburn of Tennessee is it's co-author.
Second, KOSA would ramp up the online surveillance of all internet users by forcing websites to use age verification and parental monitoring tools. Yup, that's right. Now every single person who wants to access the internet has to upload their govt ID online to third party apps that get hacked all the time. You queer in a red state? You undocumented? You an activist? Have fun getting all your online activity and metadata attached to your govt ID.
Over 90+ human and LGBT rights groups agree that KOSA is dangerous and updates to the 2023 version won’t and can’t address the big problems with the bill. This bill has MASSIVE bipartisan support, and the authors Blumenthal and Blackburn (yes, that Blumenthal that's pushing the EARN IT Act, and who also sponsored the RESTRICT Act and SOPA/PIPA if you remember) are using the tragedy of mothers who lost their kids to online harassment and young adults who've been traumatized online to lobby for it, and got Dove the company to use a bunch of influencers to push for this under the guise it prevents eating disorders...I wish I was lying. There are already 30 co-sponsors.
It is all hands on deck. I'm dead serious when I say if this bill is passed it is the beginning if not end of the open and free internet.
13K notes
·
View notes
Text
Complete Guide to Remote Employee Monitoring Software
What is Remote Team Management Software?
Remote team management software is a type of software that helps managers and team leaders to effectively oversee and coordinate the work of team members who are working remotely. This can include tools for communication, collaboration, employee time tracking, Project Management, Employee Monitoring and other features that help to ensure that team members are able to work efficiently and effectively while working remotely.

Remote team management software Features?
Remote team management software can include a variety of features that help managers and team members to work efficiently and effectively while working remotely.
Some common features of remote team management software include:
Project management: Remote employee monitoring software for creating and tracking tasks, assigning work, setting deadlines, and managing budgets.
Time tracking: Remote employee monitoring software for tracking the time spent on tasks and projects, to help with time management and billing.
Collaboration: Remote employee monitoring software for working on projects and documents together in real-time, including features such as document editing, commenting, and version control.
Task tracking: Remote employee monitoring software for creating, organizing, and tracking tasks and to-do lists, including features such as due dates, reminders, and notifications.
The specific features offered by different remote team management software will vary, and it’s important to consider which features are most important for your team’s needs when selecting a tool.
Why Remote employee monitoring software important for Business
Remote employee monitoring software is important for business for several reasons:
Productivity: Remote employee monitoring software by tracking employee activity, businesses can see if their employees are working effectively and efficiently. This can help identify areas for improvement and increase overall productivity.
Compliance: Remote employee monitoring software can ensure that employees are following company policies and procedures, as well as industry regulations.
Time management: Remote employee monitoring software can help managers track employee attendance, vacation time, and sick leave to ensure that work is being completed on time and that there are no gaps in coverage.
Communication: Remote employee monitoring software can help managers and employees communicate more effectively, especially if they are working in different locations or time zones.
Overall, remote employee monitoring software helps businesses to better manage their remote workforce, increase productivity, and ensure compliance and security.
How to Setup Remote Employee Monitoring Solution for Your Business
There are several steps you can take to set up a remote employee monitoring solution for your business:
Determine the purpose of the monitoring: It’s important to have a clear understanding of why you want to monitor your employees and what you hope to achieve.
Choose the right tools: TrackOlap Remote Employee Monitoring Software available for remote employee monitoring, including time tracking software, project management tools, and productivity monitoring software. Choose the tools that best fit your business needs and budget.
Establish clear policies and guidelines: It’s important to clearly communicate your expectations and policies around remote employee monitoring to your team. This can include things like the specific types of activities that will be monitored, how often monitoring will occur, and how the data will be used.
Train your employees: Make sure that your employees understand how the monitoring tools work and how to use them effectively. TrackOlap Providing training and support it can help ensure that the monitoring process is smooth and efficient.
Regularly review and assess the effectiveness of the monitoring: Periodically review the data you are collecting and assess whether the monitoring is meeting its intended goals. If not, consider making changes to your monitoring approach or tools.

Conclusion: TrackOlap Remote employee monitoring software can provide several benefits to companies, including improved productivity, better collaboration, enhanced productivity, improved ROI, and reduced costs. However, it’s important for companies to be transparent about their use of such software and to establish clear policies and guidelines to ensure that employees.
#Remote employee monitoring software#workforce monitoring software#work monitoring software#user activity monitoring software#remote team management software#employee monitoring software#employee laptop monitoring software#Desktop monitoring software in india#desktop monitoring software
0 notes
Text
Wellness surveillance makes workers unwell

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me in TORONTO on Mar 22, then with LAURA POITRAS in NYC on Mar 24, then Anaheim, and more!

"National conversation" sounds like one of those meaningless buzzphrases – until you live through one. The first one I really participated in actively was the national conversation – the global conversation – about privacy following the Snowden revelations.
This all went down when my daughter was five, and as my wife and I talked about the news, our kid naturally grew curious about it. I had to literally "explain like I'm five" global mass surveillance:
https://locusmag.com/2014/05/cory-doctorow-how-to-talk-to-your-children-about-mass-surveillance/
But parenting is a two-way street, so even as I was explaining surveillance to my kid, my own experiences raising a child changed how I thought about surveillance. Obviously I knew about many of the harms that surveillance brings, but parenting helped me viscerally appreciate one of the least-discussed, most important aspects of being watched: how it compromises being your authentic self:
https://www.theguardian.com/technology/blog/2014/may/09/cybersecurity-begins-with-integrity-not-surveillance
As I wrote then:
There are times when she is working right at the limits of her abilities – drawing or dancing or writing or singing or building – and she catches me watching her and gets this look of mingled embarrassment and exasperation, and then she changes back to some task where she has more mastery. No one – not even a small child – likes to look foolish in front of other people.
Learning, growth, and fulfillment all require a zone of privacy, a time and place where we are not observed. Far from making us accountable, continuous, fine-grained surveillance by authority figures just scares us into living a cramped, inauthentic version of ourselves, where growth is all but impossible. Others have observed the role this plays in right-wing culture war bullshit: "an armed society is a polite society" is code for "people who make me feel uncomfortable just by existing should be terrorized into hiding their authentic selves from me." The point of Don't Say Gay laws and anti-trans bills isn't to eliminate gender nonconformity – it's to drive it into hiding.
Given all this, it's no surprise that workers who face workplace surveillance in the name of "wellness" feel unwell as a result:
https://www.ifow.org/publications/what-impact-does-exposure-to-workplace-technologies-have-on-workers-quality-of-life-briefing-paper
As the Future of Work Institute found in its study, some technologies – systems that make it easier to collaborate and communicate with colleagues – increase workers' sense of wellbeing. But wearables and AI tools make workers feel significantly worse:
https://assets-global.website-files.com/64d5f73a7fc5e8a240310c4d/65eef23e188fb988d1f19e58_Tech%20Exposure%20and%20Worker%20Wellbeing%20-%20Full%20WP%20-%20Final.pdf
Workers who reported these negative feelings confirmed that these tools make them feel "monitored." I mean, of course they do. Even where these tools are nominally designed to help you do your job better, they're also explicitly designed to help your boss keep track of you from moment to moment. As Brandon Vigliarolo writes for The Register, these are the same bosses who have been boasting to their investors about their plans to fire their workers and replace them with AI:
https://www.theregister.com/2024/03/14/advanced_workplace_tech_study/
"Bossware" is a key example of the shitty rainbow of "disciplinary technology," tools that exist to take away human agency by making it easier to surveil and control its users:
https://pluralistic.net/2020/07/01/bossware/#bossware
Bossware is one of the stages of the Shitty Technology Adoption Curve: the process by which abusive and immiserating technologies progress up the privilege gradient as their proponents refine and normalize dystopian technologies in order to impose them on wider and wider audiences:
https://pluralistic.net/2021/02/24/gwb-rumsfeld-monsters/#bossware
The kinds of metrics that bossware gathers might be useful to workers, but only if the workers get to decide when, whether and how to share that data with other people. Microsoft Office helps you catch typos by underlining words its dictionary doesn't recognize; the cloud-based, "AI-powered" Office365 tells your boss that you're the 11th-worst speller in your division and uses "sentiment analysis" to predict whether you are likely to cause trouble:
https://pluralistic.net/2022/08/21/great-taylors-ghost/#solidarity-or-bust
Two hundred years ago, Luddites rose up against machines. Contrary to the ahistorical libel you've heard, the Luddites weren't angry or frightened of machines – they were angry at the machines' owners. They understood – correctly – that the purpose of a machine "so easy a child could use it" was to fire skilled adult workers and replace them with kidnapped, indentured Napoleonic War orphans who could be maimed and killed on the job without consequence:
https://pluralistic.net/2023/03/12/gig-work-is-the-opposite-of-steampunk/
A hundred years ago, the "Taylorites" picked up where those mill owners left off: choreographing workers' movements to the finest degree in a pseudoscientific effort to produce a kind of kabuki of boss-pleasing robotic efficiency. The new, AI-based Taylorism goes even further, allowing bosses to automatically blacklist gig workers who refuse to cross picket-lines, monitor "self-employed" call center operators in their own homes, and monitor the eyeballs of Amazon drivers:
https://pluralistic.net/2023/04/12/algorithmic-wage-discrimination/#fishers-of-men
AI-based monitoring technologies dock workers' wages, suspend them, and even fire them, and when workers object, they're stuck arguing with a chatbot that is the apotheosis of Computer Says No:
https://pluralistic.net/2024/01/11/robots-stole-my-jerb/#computer-says-no
There's plenty of research about AI successfully "augmenting" workers, making them more productive and I'm the last person to say that automation can't help you get more done:
https://www.ibm.com/thought-leadership/institute-business-value/en-us/report/augmented-workforce
But without understanding how AI augments class warfare – disciplining workers with a scale, speed and granularity beyond the sadistic fantasies of even the most micromanaging asshole boss – this research is meaningless.
The irony of bosses imposing monitoring to improve "wellness" and stave off "burnout" is that nothing is more exhausting, more immiserating, more infuriating than being continuously watched and judged.

Name your price for 18 of my DRM-free ebooks and support the Electronic Frontier Foundation with the Humble Cory Doctorow Bundle.

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/15/wellness-taylorism/#sick-of-spying

Image: Cryteria (modified) https://commons.wikimedia.org/wiki/File:HAL9000.svg
CC BY 3.0 https://creativecommons.org/licenses/by/3.0/deed.en
#pluralistic#surveillance#workplace surveillance#disciplinary technology#bossware#taylorism#ai#automation unemployment#wellness#health#labor#parenting#luddism
624 notes
·
View notes
Text
Shane Jones, the AI engineering lead at Microsoft who initially raised concerns about the AI, has spent months testing Copilot Designer, the AI image generator that Microsoft debuted in March 2023, powered by OpenAI’s technology. Like with OpenAI’s DALL-E, users enter text prompts to create pictures. Creativity is encouraged to run wild. But since Jones began actively testing the product for vulnerabilities in December, a practice known as red-teaming, he saw the tool generate images that ran far afoul of Microsoft’s oft-cited responsible AI principles.
Copilot was happily generating realistic images of children gunning each other down, and bloody car accidents. Also, copilot appears to insert naked women into scenes without being prompted.
Jones was so alarmed by his experience that he started internally reporting his findings in December. While the company acknowledged his concerns, it was unwilling to take the product off the market.
Lovely! Copilot is still up, but now rejects specific search terms and flags creepy prompts for repeated offenses, eventually suspending your account.
However, a persistent & dedicated user can still trick Copilot into generating violent (and potentially illegal) imagery.
Yiiiikes. Imagine you're a journalist investigating AI, testing out some of the prompts reported by your source. And you get arrested for accidentally generating child pornography, because Microsoft is monitoring everything you do with it?
Good thing Microsoft is putting a Copilot button on keyboards!
411 notes
·
View notes
Text
Unpacking The Myths And Realities Of Employee Monitoring In Workplace Policies

In today’s digital age, employee monitoring has become an integral part of workplace management. While some see it as an invasion of privacy, others view it as a necessary tool for ensuring productivity and security. To navigate this complex issue, it's essential to understand the myths and realities of employee monitoring within workplace policies.
A workplace policy is a formal document that outlines an organization's rules, guidelines, and expectations regarding various aspects of employee behavior and operational procedures. These policies serve as a framework to ensure consistency, fairness, and compliance with legal and regulatory requirements.
Myth 1: Employee Monitoring Equals Invasion of Privacy
A common misconception is that employee monitoring inherently violates privacy. This belief stems from fears of constant surveillance and intrusive data collection. However, the reality is that ethical monitoring practices are designed to balance the needs of the organization with respect for employee privacy. Transparency is key. Employers must inform employees about what is being monitored, the reasons for monitoring, and how the data will be used. Clear communication helps build trust and ensures employees understand the purpose behind monitoring efforts.
Reality: Monitoring Enhances Productivity And Security
When implemented correctly, employee monitoring can significantly enhance both productivity and security. By tracking work patterns, employers can identify inefficiencies and optimize workflows. Monitoring tools can highlight areas where employees may need additional training or support, leading to improved performance. Additionally, monitoring is crucial for safeguarding sensitive information and ensuring compliance with industry regulations. In sectors where data security is critical, monitoring can prevent data breaches and protect intellectual property, ultimately benefiting both the organization and its employees.
Myth 2: Employee Monitoring Creates A Hostile Work Environment
Critics often argue that employee monitoring fosters a culture of mistrust and anxiety. They believe that employees under constant surveillance will feel stressed and demoralized. While excessive or covert monitoring can indeed lead to negative outcomes, a well-balanced approach can avoid these pitfalls. Involving employees in the development of monitoring policies and being transparent about monitoring practices can mitigate feelings of mistrust. When employees understand that monitoring is in place to support and protect them, rather than to micromanage, they are more likely to accept and even appreciate it.
Reality: Monitoring Provides Objective Performance Metrics

One of the significant advantages of employee monitoring is the ability to gather objective performance data. Traditional employee performance reviews can be influenced by subjective biases, but monitoring tools provide concrete data on productivity, attendance, and task completion. This objective information can be used to make fair and informed decisions regarding promotions, bonuses, and other rewards. Furthermore, objective data can help identify high-performing employees and those who may benefit from additional training or support, fostering a more meritocratic workplace environment.
Myth 3: All Employee Monitoring Tools Are The Same
There is a widespread belief that all employee monitoring tools are equally invasive and perform the same functions. In reality, there is a diverse range of monitoring tools available, each with different features and levels of intrusiveness. Some tools focus on tracking time spent on specific tasks, while others monitor cybersecurity threats or ensure compliance with workplace employee policies. Employers can choose tools that align with their specific needs and ethical standards. It’s important for companies to research and select the right tools that provide the necessary oversight without compromising employee privacy.
Reality: Customizable Monitoring Solutions Exist

Modern employee monitoring solutions are highly customizable, allowing organizations to tailor their monitoring practices to their unique requirements. Employers can adjust the scope and scale of monitoring based on job roles, departmental needs, and specific organizational goals. For instance, roles involving sensitive data might require more comprehensive monitoring than those with less critical responsibilities. Customizable solutions ensure that monitoring is relevant and appropriate, avoiding a one-size-fits-all approach.
Striking The Right Balance
The challenge for organizations is to strike a balance between effective monitoring and respecting employee privacy. Clear and transparent workplace employee policies, developed with employee input, are crucial for achieving this balance. Monitoring should be viewed as a tool to enhance productivity and security, not as a means to control or micromanage employees.
You can also watch: EmpMonitor: Manage Remote Work Easily
youtube
Mesmerizing Words
By debunking myths and understanding the realities of employee monitoring, companies can create workplace policies that protect their interests while fostering a positive and productive work environment. Ethical monitoring can be a win-win situation, benefiting both employers and employees. In conclusion, employee monitoring is a nuanced but necessary aspect of modern workplace management. By navigating the myths and embracing the realities, companies can ensure that their monitoring practices are fair, effective, and respectful of employee privacy.
#workplace policies#workplace social media policies#workplace policies examples#HR policies#user activity monitoring tool#employee monitoring#Youtube
0 notes
Text
Transforming Data into Action: User Activity Monitoring
empower your organization with actionable insights through user activity monitoring. Gain valuable data insights to optimize operations and drive informed decision-making.
Visit - https://www.workstatus.io/workforce-management/user-activity-monitoring
1 note
·
View note
Text
Data collected by Threads can include users' sexual orientation, race and ethnicity, biometric data, trade union membership, pregnancy status, politics, and religious beliefs. Threads can also collect data on users' employment, as well as health and fitness. Beyond that, the app also can collect data monitoring users' location and other web activity.
"Threads is one of the most privacy-invasive options we’ve seen," (Calli Schroeder, senior counsel and global privacy counsel for the Electronic Privacy Information Center (EPIC)) told Ars.
The Register has helpfully posted a screenshot showing what they can access on your phone. (hint: It's pretty much everything).
Quelle Suprise!
Not currently available in the EU. (But available in the UK. Another Brexit benefit!)
You have to have an Instragram account to sign up. If you do and decide you don't like it, too bad! You can't delete your threads account w/o deleting you account on the 'gram.
753 notes
·
View notes
Text
Space Station Concepts: Space Operations Center
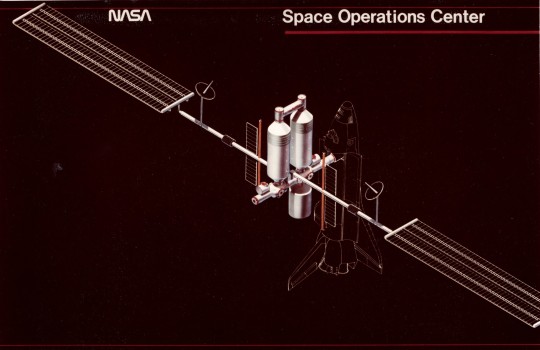

"The SOC is a self-contained orbital facility built up of several Shuttle-launched modules. With resupply, on-orbit refurbish- ment and orbit maintenance, it is capable of continuous operation for an indefinite period. In the nominal operational mode, the SOC is manned continuously, but unmanned operation is possible.
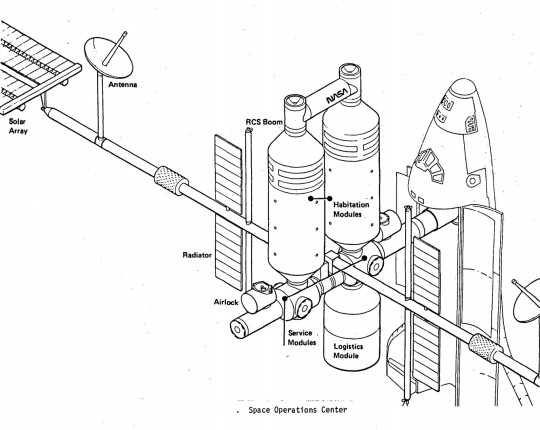
The present mission management and control process is characterized by a people-intensive ground monitoring and control operation involving large supporting ground information and control facilities and a highly- integrated ground-flight crew operation. In order to reduce dependence on Earth monitoring and control, the SOC would have to provide for increased systems monitoring; fault isolation and failure analysis, and the ability to store and call up extensive sets of data to support the onboard control of the vehicle; and the onboard capability for daily mission and other activity planning."
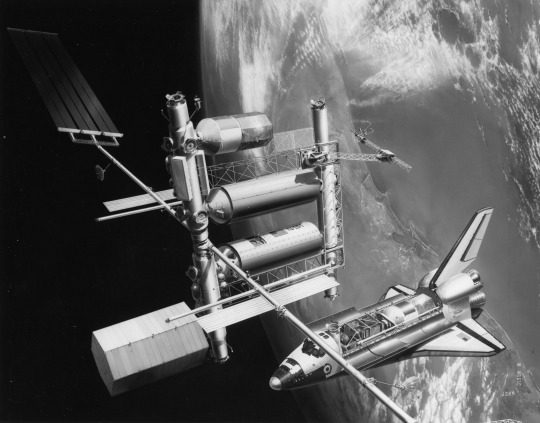

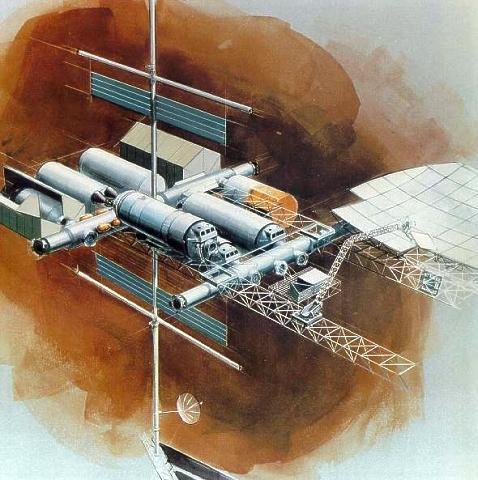
"Like most other space station studies from the mid/late 1970s its primary mission was the assembly and servicing of large spacecraft in Earth orbit -- not science. NASA/JSC signed a contract with Boeing in 1980 to further develop the design. Like most NASA space station plans, SOC would be assembled in orbit from modules launched on the Space Shuttle. The crew's tour of duty would have been 90 days. NASA originally estimated the total cost to be $2.7 billion, but the estimated cost had increased to $4.7 billion by 1981. SOC would have been operational by 1990.
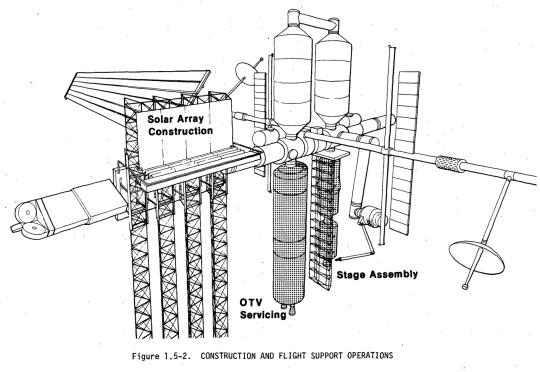
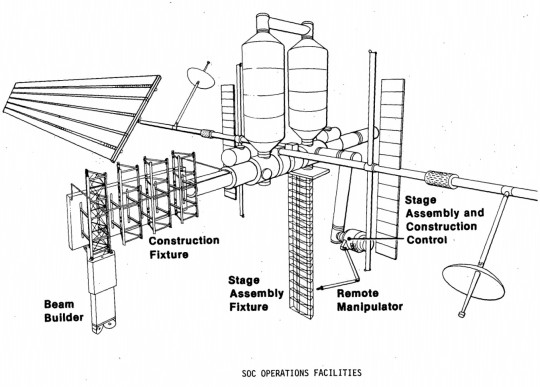

NASA's Johnson Spaceflight Center extended the Boeing contract in February 1982 to study a cheaper, modular, evolutionary approach to assembling the Space Operations Center. An initial power module would consist of solar arrays and radiators. The next launches would have delivered a space tug 'garage', two pressurized crew modules and a logistics module. The completed Space Operations Center also would have contained a satellite servicing and assembly facility and several laboratory modules. Even with this revised approach, however, the cost of the SOC program had grown to $9 billion. Another problem was Space Operations Center's primary mission: spacecraft assembly and servicing. The likely users (commercial satellite operators and telecommunications companies) were not really interested in the kind of large geostationary space platforms proposed by NASA. By 1983, the only enthusiastic users for NASA's space station plans were scientists working in the fields of microgravity research and life sciences. Their needs would dictate future space station design although NASA's 1984 station plans did incorporate a SOC-type spacecraft servicing facility as well."
Article by Marcus Lindroos, from astronautix.com: link



NASA ID: link, S79-10137
Boeing photo no. R-1859, link, link
#Space Operations Center#Space Station Freedom#Space Station Concept#Space Station#Concept Art#Space Station Program#Space#Earth#Space Shuttle#Orbiter#NASA#Space Shuttle Program#1979#1980s#my post
456 notes
·
View notes
Text
Dan Wootton
(The video and the substack article have the same information and graphics/visuals.)
Harry has several anonymous accounts on Twitter and other social media (that he reportedly hates) to monitor how he and Meghan are being covered and talked about.
The Sussexes are fully aware of what Sussex Squad does and directly feed into it. Scobie and Bouzy are in direct contact with the Sussexes. Bouzy and Meghan's PR teams are also in direct contact with many of the Sussex Squad accounts/users. Byline Times is one of Harry's partners.
Sussex Squad has been targeting Wootton since he published Megxit. Wootton's sources include people close to Harry and people close to Sussex Squad.
Sussex Squad created KateGate and began certain rumors about William. Wootton was able to identify the account responsible for starting #WhereisKate and alleging her disappearance is because of William's temper.
Bouzy is most likely the individual responsible for Getty's flagging of KP's pictures and Kate's video statement as being edited and inauthentic.
Wootton hints that Sussex Squad somehow found out about Kate's cancer diagnosis and/or their coordinated attacks on KP (probably via the KateGate hysteria) forced Kate to announce her cancer and treatment plan before she was ready and before she had fully come to grips with it.
Sussex Squad has been spooked off Twitter and now use Discord for their collaboration.
Wootton also identifies and discusses 3 Sussex trolls:
Troll 1 is a techy in NYC who is a close Bouzy collaborator. She is one of the main accounts that have harrassed and targeted Wootton and his partner because of Wootton's critical coverage of the Sussexes. She has publicly admitted to it. She is no longer trolling because it's toxic and allegedly has quit Twitter, though not before claiming that Wootton and his people were threatening to hurt her and her dog.
Troll 2 is a business dude in Tampa. He specifically targets Camilla and has claimed that she is Meghan's main bully and has enlisted Jeremy Clarkson and Piers Morgan in her bullying campaign. He also tries to keep connecting Charles to Germany, and specifically to N*zi Germany.
Troll 3 is a British advertising executive. This individual has alleged that Camilla is responsible for Charles's cancer, because she has been poisoning him since the coronation so she can retire "young."
One of Wootton's bigger points is that if the Sussexes want to be taken seriously as advocates for internet reform/social media protections, then they must publicly disassociate from and condemn Sussex Squad's behavior and activities. He doesn't think they will.
*****************
First, I'm pleasantly surprised by this. I was expecting Wootton to be a little more sensational about his discoveries, but it's clear he's really done his homework and has really spent some time investigating this. If you're into this kind of thing, you might actually enjoy getting his updates so why not sign up for it. Use a burner email, though. You can never be too safe.
Second, I'm not really sure about using Wootton's reporting to validate some of the rumors and theories I'm tracking. On the one hand, Wootton has legit sources and a track record that makes him one of the more reliable reporters. But on the other hand, I like double-confirmation for my verification so I can be sure that it's the absolute truth.
What do y'all think?
181 notes
·
View notes
Text
I think every computer user needs to read this because holy fucking shit this is fucking horrible.
So Windows has a new feature incoming called Recall where your computer will first, monitor everything you do with screenshots every couple of seconds and "process that" with an AI.
Hey, errrr, fuck no? This isn't merely because AI is really energy intensive to the point that it causes environmental damage. This is because it's basically surveilling what you are doing on your fucking desktop.
This AI is not going to be on your desktop, like all AI, it's going to be done on another server, "in the cloud" to be precise, so all those data and screenshot? They're going to go off to Microsoft. Microsoft are going to be monitoring what you do on your own computer.
Now of course Microsoft are going to be all "oooh, it's okay, we'll keep your data safe". They won't. Let me just remind you that evidence given over from Facebook has been used to prosecute a mother and daughter for an "illegal abortion", Microsoft will likely do the same.
And before someone goes "durrr, nuthin' to fear, nuthin to hide", let me remind you that you can be doing completely legal and righteous acts and still have the police on your arse. Are you an activist? Don't even need to be a hackivist, you can just be very vocal about something concerning and have the fucking police on your arse. They did this with environmental protesters in the UK. The culture war against transgender people looks likely to be heading in a direction wherein people looking for information on transgender people or help transitioning will be tracked down too. You have plenty to hide from the government, including your opinions and ideas.
Again, look into backing up your shit and switching to Linux Mint or Ubuntu to get away from Microsoft doing this shit.
124 notes
·
View notes
Text
Meet Summer and her charming canine companion, Coia, a spirited soul with an undeniable passion for water-based activities, particularly those involving ducks and swans. Recognizing the importance of ensuring Coia's safety, Summer opted for the cutting-edge Halo Collar 3.
Summer's insightful review sheds light on the exceptional features of the Halo Collar 3, a device that effortlessly monitors Coia's aquatic adventures and mitigates potential water hazards. With its user-friendly GPS fence technology, the collar allows the programming of up to 20 virtual fences, making it a versatile choice for various environments and activities. The portable collar can be easily programmed using the Halo Collar app on a smartphone, which is perfect for the avid traveler.
Summer emphasizes the game-changing technology embedded in the Halo Collar, describing it as an invisible dog fence that is a reliable protector for Coia. This comprehensive review underscores the ease of use and the peace of mind, ensuring that both Summer's family and Coia can sleep soundly at night. The Halo Collar emerges not just as a dog collar but as a crucial investment in dog safety, seamlessly combining innovative GPS dog fence features with a user-friendly design. Join Summer on her journey of prioritizing canine companions' well-being with the trusted and versatile Halo Collar.
228 notes
·
View notes
