#the nsa is ONE of the united states' spy agencies
Explore tagged Tumblr posts
Text
Woman: I want to keep this secret, so I will tell the NSA agents to leave before I say this in an NSA-run hospital
#for those not in the know#the nsa is ONE of the united states' spy agencies#i think the one that spies on us
2 notes
·
View notes
Text
US Government denies FOIA request for sealed USS Liberty records. 57 year old files to remain classified.
The USS Liberty incident was an attack on a United States Navy technical research ship (a spy ship), USS Liberty, by Israeli Air Force jet fighter aircraft and Israeli Navy motor torpedo boats, on 8 June 1967, during the Six-Day War. The combined air and sea attack killed 34 crew members (naval officers, seamen, two marines, and one civilian NSA employee), wounded 171 crew members, and severely damaged the ship. At the time, the ship was in international waters north of the Sinai Peninsula, about 25.5 nautical miles (47.2 km; 29.3 mi) northwest from the Egyptian city of Arish.
Israel apologized for the attack, saying that USS Liberty had been attacked in error after being mistaken for an Egyptian ship. Both the Israeli and U.S. governments conducted inquiries and issued reports that concluded the attack was a mistake due to Israeli confusion about the ship’s identity. Others, including survivors of the attack, have rejected these conclusions and maintain that the attack was deliberate. Thomas Hinman Moorer, 7th Chairman of the Joint Chiefs of Staff, accused President Lyndon B. Johnson of having covered up that the attack was a deliberate act.
‘The Americans have findings that show our pilots were aware the ship was American,’ a newly published document by the State Archives says. -- Source
USS Liberty survivor Phil Tourney and Candace Owens talk about Israel planned their attack a year in advance. -- Source
On November 21, 2024, Senior Judge Marsha J. Pechman of the US District Court for the Western District of Washington issued what seems likely to be her final order in Kinnucan v. National Security Agency et al. The order came more than four years after the federal case was first filed in September 2020. The suit was brought to obtain records the NSA, Central Intelligence Agency, and the Defense Intelligence Agency had failed to release despite a series of Freedom of Information Act (FOIA) requests concerning the USS Liberty (AGTR-5).
More than 57 years after the attack, the FOIA lawsuit revealed new details and, more importantly, it made it clear that the US government is still refusing to release hundreds of pages of documents concerning the assault
25 notes
·
View notes
Text
Bodyguard, Not a Friend
Requested Here!
Pairing: John Casey x fem!agent!reader (you pick which agency but I imply that r is not NSA)
Summary: You and Casey have hated one another since you became spies. Yet, when your life is in danger, he is chosen to protect you. As he completes his mission, you find that your hatred of him may not be as real as you thought.
Warnings: angst, r is attacked and injured, mentions of drug/weapon trafficking and murder, slight fluff at the end (and a somewhat open ending)
Word Count: 2.5k+ words
Masterlist | Casey Masterlist | Request Info/Fandom List

“And you,” your instructor says, saving in your general direction, “are with John Casey.”
You roll your eyes. Every person you have learned from since deciding to leave your life behind and become a spy has some strange fascination with Casey. You often wonder why because this is his second attempt to get through the class. If John failed once, it seems he isn’t good enough, yet every opportunity to brag about him is taken. He’s the favorite, but he’s ranked second in the class. You plan to keep it that way, no matter what it takes.
“Let’s get this over with,” Casey mumbles as he approaches you.
“After you,” you invite with a dramatic sweep of your arm. “Since you’re the only one that seems to matter.”
Casey scoffs. “Get over whatever that was because we have work to do.”
“And if I don’t listen to you you’ll leave me to die. Remind me, what happened to your last partner?”
Casey’s eyes darken as the muscles in his jaw tighten quickly. “Maybe I will. Just stay out of my way.”
“I’d like nothing more.”
Soon after your successful assignment with Casey, you are offered a position working for the United States government. When you walk away from the training facility that has been your home, you are more than happy to leave it and Casey as you go your separate ways. Since he implied he’d kill you for getting in his way, you decided that beating Casey as rivals in the spy equivalent of a classroom wasn’t enough. You hate John Casey and do not doubt he feels the same.

“Major Casey,” General Beckman says through the video call. “I have your new assignment.”
“Yes, ma’am,” Casey replies.
A picture appears on the screen, and Casey clenches his fists at his sides to control his emotions. He hasn’t seen you since you were teamed together for a meaningless assignment. Though you worked well together within the mission parameters, Casey hated every minute of being that close to you.
“Another rogue agent?” Casey guesses.
“No. Are you familiar with Damion Messing?”
“The assassin for hire?”
“Amongst other things. Messing is also a go-between for killers and the people who need others dead. He’s connected to international drug trafficking rings, federal treasury robberies, and suspected of orchestrating the recent string of public executions at the border.”
“What does Messing have to do with…” Casey trails off, flipping his hand toward your picture.
“She got too close to him. During an undercover operation, Messing got suspicious.”
“General,” Casey begins.
She raises her hand to silence him. “Your job is to make sure no one gets close enough to hurt her before she can finish the assignment.”
“You want me to be her bodyguard?” Casey clarifies.
“Is that a problem, Major Casey?”
Casey takes a calming breath before he answers, “No, ma’am.”
There is a problem. Every part of this assignment is a problem, but most alarming, Casey thinks, is you. However, Casey is good at his job and will do it. Even if he’s considered threatening you himself before.

“Please tell me I’m dreaming,” you say when you open the door.
“No,” Casey answers quickly. “I’m here because I have to be.”
“Then I will happily dismiss you.”
“Let me in,” Casey demands.
“I can take care of myself, Major,” you insist, your grip tightening on the door.
“Clearly you can’t if you let Messing close enough to put out a hit on you.”
“He doesn’t know anything,” you argue. “I just asked too many questions, nothing that would put the department at risk.”
“Yet here we are. Are you going to let me in?”
You huff as you push the door open roughly. “Only because I have to.”
“Since when do you take orders?” Casey mumbles as he steps past you.
“Apparently I have no say anymore because I put a target on my own back.”
Casey rolls his eyes as you walk away. He’ll do his job and keep you alive, but that doesn’t mean he has to interact with you.
“Bodyguard,” you call over your shoulder. “Not friend.”
“I’m aware.”

Your fingers tap the table beside your open laptop as you think. Messing may have kicked you out and promised to kill you for looking too closely into his operation, but he forgot one thing. You were around long enough to get copies of everything that matters to him and his illegal affairs.
“Four thousand…” you mutter. “Plus twelve percent of the weapon reallocation.”
Lost in the data you stole and have yet to decode, you don’t notice Casey walk into the room. He watches you for a moment as your mouth moves while you read. He looks away when you tip your head back in frustration.
“Where would he take it?” you ask aloud.
“Messing?” Casey inquires.
You nod and return to your previous position. As you drop your head into your hands, Casey watches you again. You’re both drawn from the moment when glass shatters above you.
Casey pulls his gun from its holster and points at you. He waves toward the panic room of the safe house, but you stand and turn to face the same way as him.
“No,” he whispers harshly.
You ignore him, raising your weapon as you move silently toward the stairs. Someone calls your name, and you stop. Casey pauses behind you, reluctantly taking your lead.
“Go left,” he instructs quietly.
You nod and don’t question him as you step to the far side of the staircase. As you climb to the second floor, you and Casey cover one another. Near the top, you put your hand on Casey’s chest and point to a creaky stair. He nods once and steps over it, your hand sliding off him as he moves.
“Come out,” the intruder calls. “Damion sent a message for you.”
Casey gestures for you to wait, but you keep your gun ready to defend him and yourself. He walks toward the end of the hallway, oblivious to the door beside you opening. You’re pulled inside, your gun clattering to the ground, before you can warn Casey that there’s more than one.
Inside the bedroom, you are shoved against the wall, and a knife is raised to your throat. You smile at Damion’s right-hand man, though you view him more as an errand boy.
“Where is it?” he demands, pushing his free hand against your right shoulder.
“You’re going to have to be more specific,” you reply.
Several shots echo through the house, and you briefly close your eyes as you hope that Casey is okay.
“The sword.”
You open your eyes at his unexpected answer. “What sword?”
“The one you stole.”
With your brows furrowed, you try to remember seeing a sword in Damion’s compound. He has innumerable weapons, but you can’t recall any specific sword. The man before you shifts his weight, and you bring up a knee to block him from stabbing you. Your quick movement knocks both of you off balance, and you hiss when the knife slides along your lower leg, but don’t stop. Raising both hands to his shoulders, you shove him backward and barely manage to catch yourself when you tumble over him.
“It doesn’t have to end like this,” he says.
“Then leave,” you respond before lunging toward him.

Casey hears a door slam behind him but doesn’t look away from the door at the end of the hallway. He can see shadows under the door; two people are inside, but he still has the element of surprise.
“One, two, three,” Casey counts under his breath.
Raising his gun, Casey fires two quick shots. He sees the shadows drop to the ground, and then carefully pushes the door open. The room is clear, and he turns to alert you. When he realizes the hallway is empty, he regrets not turning earlier.
A dull thud, one that Casey identifies as someone being shoved against drywall, causes him to raise his gun again. Before he reaches the door he thinks you were taken into, a loud noise stops him. Casey can make out your voice, muffled through the door, and knows you’re fighting. If he barges in now, he could make it worse. But he’s your bodyguard, this is his assignment, and he doesn’t like not knowing what is happening.

“Colombia,” you remember.
“Where is it?” the man standing above you yells.
You smile as he raises the knife. “I mailed it back to Colombia.”
Before he can bring the knife down into your chest, you pull your hands to either side of your head and drive your elbows into his collarbone. He grunts in pain as you flip over him and pin him to the ground. While he reaches blindly for his knife, you point your gun directly at his forehead.
“Is the sword the key?” you ask.
“Just shoot me,” he says, raising to press his head against the barrel.
You shake your head, then yell in pain when he swings his arm against your side. Immediately, the door is broken open, and a single shot stops your attacker before he can get his knife and finish.
Casey keeps his gun aimed at the downed man but looks at you. You sit back and release a breath, then grimace.
“Why did you do that?” Casey asks, his voice low and dark.
“Do what? Help you?” you question. “This is my fight, Casey.”
“And your safety my assignment! Despite how little I care about you or what trouble you get yourself into, my job is to keep you safe. That means you don’t get involved!” His voice raises with each word, and he yells the last part before holstering his gun.
“I’m already involved, Casey!”
“Not in this part. Just do what I say so we can both do what we need to and walk away!”
“Why do you care, Casey?” you demand loudly. “If they kill me, you get a new assignment!”
Casey turns away from you and mumbles something you can’t make out. “I don’t fail my assignments,” he says finally. “And I’m not going to start now.”
“Then do something about these geniuses and I’ll get back to work.”
You push yourself up to stand, but your side and leg protest with each movement. Wrapping your arm around your torso, you apply as much pressure as you can handle and ignore the warm blood running down your calf and to your ankle.
“Stop,” Casey says.
You don’t listen, and he wraps his hand around your bicep.
“I don’t need your help, Casey,” you whisper, looking into his eyes as you will your own not to tear up. “You’re here to keep me safe, right? So don’t worry about the trouble I get myself into. Just keep me out of Damion Messing’s trouble.”
Casey’s hand tightens around your arm, a gentle pressure you are surprised to miss when he pulls away. You nod once before you exit the room. As you slowly descend the stairs to treat your injuries, you hear Casey make a phone call. Part of you wants to listen, but you have bigger problems to focus on, like a sword from Colombia.

With your hands on your hips, you look up into the closet of stolen items. Your time with Damion provided plenty of evidence, but the one thing you need is just out of reach. Leaning back gently, you look into the kitchen and see Casey reviewing a layout of the safe house.
“Uh, Casey?” you call.
He grunts in response, and you take it as an invitation to continue.
“Can you help me with something?”
Casey freezes for a second, then looks up at you. “What?”
“I need the box at the top of the closet, but I…”
“Have broken ribs,” Casey finishes for you.
You didn’t tell him how bad the injury was, but your lack of upward movement probably did. Casey nods as he approaches you. There isn’t time to move out of the way before Casey’s chest presses against your back while he reaches over your head. He pulls the box down, then steps away from you to carry it to the table.
You shake your head to clear your thoughts. Somewhere, some time since Casey arrived and forced you to let him in, you’ve stopped hating him. He saved your life, but that isn’t enough of a reason. Casey will leave when you find this sword, but you aren’t sure you want that anymore.
“Is this the sword you’ve been mumbling about?” Casey asks, raising a bag with a blade. “A machete from grima?”
“That’s why I couldn’t remember it!” you cheer. “I knew there wasn’t a sword.”
Casey passes the evidence bag to you, and you flip the blade in your hands. The blade tip is heavier than the handle, the opposite of how it should be. The unevenness led you to take it, but now it seems justified.
“I bet there’s drugs in it,” you muse.
“It is from Colombia,” Casey grumbles in agreement.
“I need to call my general. If this is full of drugs, my job is done.”
“Then mine is too.”
You nod at Casey, then carry the sword out of the room. Working with Casey was just as effective now as years ago, but the reminder that he’s leaving (and wants to) disappoints you. The call connects before you can dwell on Casey’s approaching departure for too long, and you launch into explaining what you found.

The morning after your call, you wake in the safe house for the last time. There’s no sound, no movement, and you wonder what it would be like to live here, to be a normal person and appreciate life and nature for what it is. But you chose this life, you think as you throw the blankets off and get out of bed.
“Casey?” you call as you walk into the kitchen.
Silence is your only reply, and your good mood disappears when you see a piece of paper tucked under your laptop.
My reassignment came quickly. Call if you need anything. -Casey
His number is under the note, and you press the paper to your chest. Casey still gets under your skin and seems to think he’s a better spy than you, but the hatred you held onto for so many years is nowhere to be found.
As you save his number to your phone and begin packing your belongings, your phone rings. Your new assignment came quickly, too, it seems.
“Good morning, General,” you greet.
“There’s a situation in Santiago. I need you on the next plane,” he explains quickly.
“Santiago… Chile?”
“Yes. Other agents are inbound and will meet you there. When you land, the lead agent will have the mission information.”
“Who is the lead agent?”
“He’s NSA, that’s all I know.”
“Understood. I’ll be there.”
The line beeps when he disconnects, and you fold Casey’s note into your pocket. Even if he’s not the agent you’re meeting in South America, you haven’t lost him yet.
#john casey x fem!reader#john casey x reader#john casey fic#john casey imagine#john casey#nbc chuck#chuck nbc#hanna writes✯#fem!reader#requests
10 notes
·
View notes
Text
Trump’s First Day in Office
Paul Craig Roberts
Well, we finally have an American back in the White House. The night after Trump was declared the winner, I had a fantasy dream about his first day in office.
Trump pardoned Julian Assange and Edward Snowden, and appointed Assange to head the FCC and Snowden to head the NSA.
Derek Chauvin and the police officers who were falsely indicted and falsely convicted by a corrupt judge and prosecutor who withheld from the trial and jury evidence proving their innocence were pardoned and awarded $25 million each in compensation for their wrongful conviction in one of the worst failures of justice in history. See: https://www.youtube.com/watch?v=0ffv4IUxkDU and https://www.youtube.com/watch?v=eFPi3EigjFA
The media monopolies were broken up for violating the Sherman Anti-Trust Act and for violating the fairness doctrine and weaponizing the air waves for political purposes. The NSA was cleaned up and stopped from warrantless spying on US citizens and violation of their privacy by storing their emails, credit card and internet activities.
All the attorneys who were falsely accused and some convicted of interfering with an election by reporting documented instances of Democrat election fraud were pardoned. All victims of the corrupt and politicized Biden Justice (sic) department, such as the Americans who were sent to prison by the corrupt Merrick Garland for exercising their First Amendment rights, were pardoned and awarded $10 million each in compensation. The entire Biden Justice (sic) Department was arrested and indicted for violating their oath of office to protect the Constitution of the United States. The corrupt Democrat judges and Democrat prosecutors were sanctioned and removed from office for weaponizing law to serve their political party.
Former CIA director John Brennon was arrested and indicted, along with FBI director Christopher Wray for high treason for trying to frame the President of the United States.
Trump’s FDA director Robert F. Kennedy Jr. cleared Big Pharma’s operatives out of the FDA, CDC, and NIH and had criminal investigations launched of Big Pharma and Big Food’s poisoning of the American population and influence over university medical and nutritional curriculums.
At the Office of Management and Budget Elon Musk cut $2.5 trillion out of the annual US budget. Hundreds of US overseas bases were closed, and entire federal agencies and departments disappeared.
3 notes
·
View notes
Text
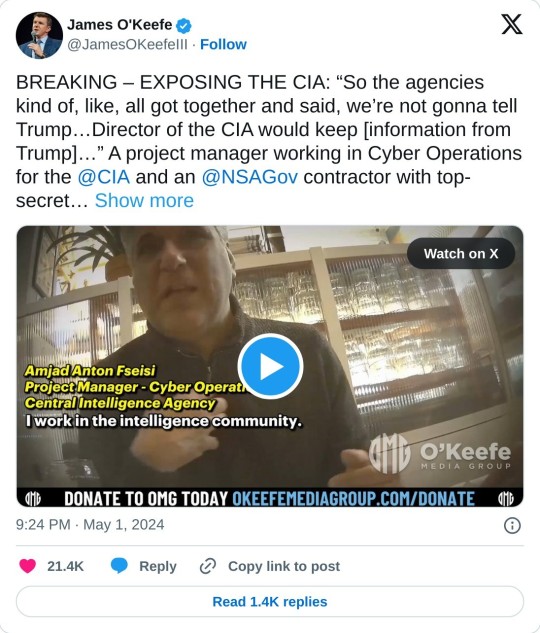
MASSIVE REVELATION! James O’Keefe Releases Undercover Video of CIA Contractor Admitting CIA Director Withheld Info from Trump and Spied on His Presidency
ames O’Keefe last Friday warned he was about to release the most important story of his entire career.
“I have evidence that exposes the CIA, and it’s on camera. I am working on releasing a story that I believe is the most important of my entire career,” O’Keefe said on Friday.
“Do you think it’s a coincidence that right at this moment I am subject to an endless series of attacks?” he said. “This is obviously a sophisticated information operation designed to stop me from releasing this story. I’m sure you recognize they are masters of using half-truths and innuendos to raise doubt against people who don’t deserve it. It’s meant to consume my time and energy and make me back down.”
“But I’m not going to let it work. Rest assured, nothing will stop me from releasing this story,” O’Keefe said.
O’Keefe Media Group on Wednesday released part one: Exposing the CIA: A project manager working in cyber operations told OMG’s undercover journalist that the Director of the CIA would keep information from Trump.
He also said the CIA spied on Trump’s presidency and is still monitoring him to this day.
“So the agencies kind of, like, all got together and said, we’re not gonna tell Trump…Director of the CIA would keep [information from Trump]…” Amjad Fseisi, a project manager working in Cyber Operations for the CIA with top-secret security clearance told an undercover journalist.
Amjad Fseisi said Trump is a “Russian asset” – “He’s owned by the f*cking Russians,” he told the undercover journalist.
Per James O’Keefe:
Amjad reveals to OMG’s Undercover American Swiper that intel agencies not only kept intelligence information from a sitting United States President and Commander-In-Chief, they also used FISA to spy on President Trump and his team and are still monitoring President Trump according to Amjad who says, “We monitor everything.” Amjad adds “we also have people that monitor his ex-wife. He likes to use burner phones” – information only an insider with access to highly sensitive information would state. “We steal it [information]” and “We hack other countries just like that,” Amjad, who states he currently works on the CIA’s China Mission Center, explains how intel agencies obtain information. He also describes a broken intelligence system where “We don’t share information across agencies” because the CIA is “very reluctant” to share information with the “careless” NSA. O’Keefe Media Group’s bombshell undercover footage supports earlier reports by investigative journalists Michael Shellenberger, Matt Taibbi, and Alex Gutentag that revealed how the American intelligence community illegally ran a spy operation against then-candidate Trump’s presidential campaign in 2016 and illegally acquired intelligence that was later used to justify the Federal Bureau of Investigation (@FBI) official probe, “Crossfire Hurricane,” which in turn led to Special Counsel Robert Mueller’s investigation that ultimately did not find evidence of Russia collusion by the 2016 Trump campaign. Contractors like Fseisi hold the duty to withhold sharing confidential or national security information. In denying his statements, Fseisi may have realized he could be held liable for violating internal agency provisions and federal laws like the Executive Agency ethics provisions, which restrict what he may share with others outside of his contracted-to agency. Additionally, any government worker or agency head who withheld information from a superior (i.e. President Trump) may violate: (a) obstruction of justice by deception (18 USC 1512); (b) conspiracy to obstruct (18 USC 371); and false statements (18 USC 1001). Agency regulations may also provide offenses related to insubordination, reflecting poorly on the agency in public, or misrepresentation or dishonesty. When James O’Keefe caught up with Amjad Fseisi on the streets of Washington, D.C., Fseisi could not tell O’Keefe whether he had top secret clearance, denied making statements clearly caught on camera, and would not even confirm it was him on the video saying only “It looks like me.” When asked directly if he works at the CIA, Fseisi said, “I can’t tell you that.”
7 notes
·
View notes
Text
WASHINGTON (AP) — The U.S. has used electronic surveillance programs to catch fentanyl smugglers and the hackers who temporarily shut down a major U.S. fuel pipeline, the White House said Tuesday as part of its push to have those programs renewed by Congress.
Section 702 of the Foreign Intelligence Surveillance Act expires at the end of this year. President Joe Biden’s administration is trying to convince Congress to renew the law, which authorizes spy agencies to capture huge swaths of foreign emails and phone calls. But lawmakers in both parties have concerns about protecting Americans’ privacy from warrantless searches after a series of FBI errors and misuses of intelligence data.
As part of its public campaign, the Biden administration released what it said were newly declassified examples of how U.S. intelligence uses Section 702. And the FBI announced new penalties for employees who misuse intelligence data in advance of a closely-watched Senate Judiciary Committee hearing on the program Tuesday morning.
Previous administrations have oftencited the importance of Section 702 in stopping terrorism. But two decades after the Sept. 11 attacks, the U.S. public is broadly skeptical of intelligence agencies and less certain of sacrificing civil liberties for security.
This time, the White House and supporters of Section 702 are targeting concerns over fentanyl, a synthetic opioid blamed for 75,000 U.S. deaths last year, and the shutdown of Colonial Pipeline, which led to gas shortages along the East Coast two years ago.
Senior administration officials briefed reporters on the new examples Monday on condition of anonymity under ground rules set by the White House.
Among the other examples the officials gave: The U.S. learned about Beijing's efforts to track and repatriate Chinese dissidents; the FBI was able to warn an American who was the target of foreign spies seeking information about the proliferation of weapons of mass destruction; and the U.S. identified the people behind an Iran-linked ransomware attack against nonprofit groups last year.
The United States has already credited Section 702 with being used in the operation to kill al-Qaida head Ayman al-Zawahri and providing large amounts of the intelligence briefed daily to the president and other top officials.
The administration officials said they provided more specifics to Congress in classified briefings.
“We are trying to walk a careful line here where we're trying to explain both to the public and to members of Congress the importance of Section 702,” one official said. “But at the same time, we do need to be very careful about protecting the ways in which we collect information."
Under Section 702, the National Security Agency collects large amounts of foreign emails, phone calls, and other communications that the NSA and other agencies can then search for intelligence purposes.
That collection often snares the communications of Americans. While U.S. spy agencies are barred from targeting U.S. citizens or businesses, they can search Americans' names in Section 702 data and the FBI can use that data to investigate domestic crimes.
A series of surveillance court opinions and government reports has disclosed that FBI agents at times have failed to follow rules on searching that data. Agents wrongly ran queries for the names of a congressman on the House Intelligence Committee, people linked to the Jan. 6 insurrection, and participants in the 2020 protests following the police killing of George Floyd.
The FBI, backed by the White House and some Democrats, argues it has instituted better training and new rules that have sharply reduced the number of searches for American citizens. Supporters of the FBI say Congress should enshrine those rules into law so they can't be rolled back easily.
The bureau said Tuesday that it would begin to immediately suspend any employee's access to Section 702 databases for an incident involving “negligence." Repeat mistakes could result in an employee being reassigned or referred for an internal investigation.
Some key Republicans want to impose new criminal penalties on FBI agents accused of wrongdoing. Many in the GOP are deeply angry at the FBI for those mistakes as well as for omissions in the bureau's investigation of former President Donald Trump's ties to Russia. Some echo Trump's attacks on the FBI as part of a so-called “deep state.”
“There are reforms that are necessary,” said Rep. Darin LaHood, an Illinois Republican who previously disclosed that agents searched his name in intelligence databases. “Figuring out the proper reforms and safeguards that we need to put in place is what we're discussing to try to see if we can get it reauthorized.”
And other Democrats say they won't vote to renew Section 702 without restrictions on access to U.S. citizens' communications.
Senior Biden administration officials reiterated Monday that they oppose proposals to require the FBI to get a warrant every time it searches for an American's information. Previous administrations have fought the idea as well.
The U.S. public at large is also skeptical of surveillance practices, according to new polling from The Associated Press-NORC Center for Public Affairs, with Democrats and Republicans opposing some practices authorized by Section 702 in roughly equal measure.
A coalition of 21 civil liberties groups issued a letter Monday saying lawmakers should not renew the law without “critical reforms," including a warrant requirement.
"Although purportedly targeted at foreigners, Section 702 has become a rich source of warrantless government access to Americans’ phone calls, texts, and emails," the letter says. “This has turned Section 702 into something Congress never intended: a domestic spying tool.” ____________________________________
Never intended my ass, shut it down and vote anyone that puts a yes into the hat for keeping this out of office
4 notes
·
View notes
Text
The article mentions that Israel has access to 'the jewels of the Five Eyes network'.
So if you dont know, 'Five Eyes' refers to countries whose governments formally agreed to form intelligence agencies during the Cold War to monitor Soviet communications. These are Australia, Canada, New Zealand, the United Kingdom and the United States.
From Wikipedia: "The FVEY further expanded their surveillance capabilities during the course of the "war on terror", with much emphasis placed on monitoring the World Wide Web. Former NSA contractor Edward Snowden described the Five Eyes as a "supra-national intelligence organisation that does not answer to the known laws of its own countries". Documents leaked by Snowden in 2013 revealed that the FVEY has been spying on one another's citizens and sharing the collected information with each other, although the FVEY nations maintain that this was done legally."
And now you know.
There absolutely needs to be more outrage over the Five Eyes and their actions.
australian activists were arrested earlier today while protesting at the Pine Gap US military base, which uses satellite surveillance and geolocation to provide intelligence to the IDF
the IDF's ability to target with pinpoint accuracy comes from the US operations on australian soil
there needs to be a stronger demand here to close that fucking base.
1K notes
·
View notes
Text
Connectivity Is Crucial To Our Future Security
The recent nationwide Optus outage showed us that connectivity is crucial to our future security. Suddenly, everyone felt helpless and reacted with much anger and frustration toward the failing provider. This throws our dependence upon electrical and digitally connected devices into harsh relief. It is not a stretch of the imagination to plot likely scenarios during times of war in this new age of information. Cutting off the population from their institutions and from each other will be achieved via attacking communication infrastructure. This can be done far more easily than many people might think. Photo by Dylan Chan on Pexels.com
Cables Connecting Us To The World
“These cables, only about as thick as a garden hose, are high-tech marvels. The fastest, the newly completed transatlantic cable called Amitié and funded by Microsoft, Meta and others, can carry 400 terabits of data per second. That's 400,000 times faster than your home broadband if you're lucky enough to have high-end gigabit service.” - (https://www.cnet.com/home/internet/features/the-secret-life-of-the-500-cables-that-run-the-internet/) The great majority of data communication is piped through submarine cables and not via overhead satellites. These relatively thin high tech cables span some million kilometres around the world. They sit on ocean floors and carry the vast mass of information flow for the big tech giants Google, Microsoft, Meta and Amazon. These submarine cables connect us all with each other through our myriad devices. There is a geopolitical battle raging right now between the United States and China for control of this network of undersea digital cables. The US is winning this and wants to ensure that China remains a minor player. “The European Union's executive wants to help invest in "cable projects of European interest" that would reduce its reliance on too few undersea internet connections and make it less vulnerable to sabotage, a document seen by POLITICO showed.” - (https://www.politico.eu/article/eu-looks-to-boost-secure-submarine-internet-cables-in-2024/) Photo by Sora Shimazaki on Pexels.com Cabling Connecting & Surveiling There is an understanding through the whistleblowing efforts of former NSA operative Edward Snowden that US spy agencies monitor data via these submarine cables of the big tech companies. The realisation that China is probably doing the same is one of the reasons why the push is on to freeze China out of the game. These lengthy cables require signal repeaters or boosters and it is suspected that these pieces of technology are where surveillance technology has been added to the cable network. Thus, we are seeing Chinese cabling deals quashed under pressure from the US in the South Pacific and around the globe. America wants to maintain its grip on the Internet internationally. The maintenance of these relatively fragile cables is a major component of the cabling network business. Companies tender for contracts to provide maintenance. Many of the companies that lay and maintain submarine cables have strong links to the security agencies. Maintenance provides opportunities to insert surveillance technology to that cable. https://www.youtube.com/watch?v=uUlGRBmv_IM Five Eyes & Chinese Hacking The Five Eyes intelligence alliance has recently come out and publicly pointed the finger at China as the state sponsored home of hacking. This Western group of spy agencies tells us that China has been hacking secrets from US companies for decades and the clear message is that it cannot be trusted. “The Five Eyes countries' intelligence chiefs came together on Tuesday to accuse China of intellectual property theft and using artificial intelligence for hacking and spying against the nations, in a rare joint statement by the allies. The officials from the United States, Britain, Canada, Australia and New Zealand - known as the Five Eyes intelligence sharing network - made the comments following meetings with private companies in the U.S. innovation hub Silicon Valley.” - (https://www.reuters.com/world/five-eyes-intelligence-chiefs-warn-chinas-theft-intellectual-property-2023-10-18/) Photo by Monstera Production on Pexels.com China’s position as a global economic superpower is accompanied by its political position as a totalitarian regime with Xi Jinping as dictator. This makes many in the West uncomfortable for a number of reasons. China’s massive increase to its military capabilities only adds to this. Therefore, the geopolitical push to keep China out of various security arrangements internationally can be understood on this basis. However, it is equally foolish to assume that the US keeps its security concerns completely separate from its trade interests. Western powers have mixed business with so-called national security concerns from the outset in global affairs. Economic and military power go hand in hand. This is about dominance on the world stage first and foremost. Competing powers always declare the other guy the bad guy in any dispute. President Trump Postlaunch Remarks (NHQ202005300037) by NASA HQ PHOTO is licensed under CC-BY-NC-ND 2.0 Another Dictator on The Horizon When thinking about who are the bad guys, there is the shadow of one Donald J Trump looming over the USA in 2024 and beyond. A Trump presidency, especially a revenge presidency, poses the threat of untold dangers to world peace. A proven liar and fraud, Trump is a major risk to the safety of humanity. There are enough bad guys in prominent positions, like Putin, to go adding an immoral loon to the top job in the White House once again. The GOP has morphed into an extremist autocratic political party hell bent on Trump or destruction. The delineation between bad and good actors on the global stage is getting less clear by the day. Right wing media organisations like News Corp are directly complicit in the push for Trump. Photo by Pixabay on Pexels.com South Pacific Submarine Cabling Australia has been shoring up its South Pacific security relationships of late. These submarine cables make an appearance in the Soloman Islands situation with a Chinese deal sunk in 2017 and replaced by a US one the following year. The geopolitical dance, between the superpowers, has been island hopping here with visits by a cavalcade of foreign ministers. Anthony Albanese has been seen hula dancing and money is being spent on these tiny island nations by middling and super powers. Photo by Jonathan Cooper on Pexels.com Connectivity is crucial to our future security. AUKUS may not be the only submarine concern that we have, as an island nation ourselves. Thinking about how easy it will be to go around cutting cables and disabling communication networks - modern warfare will be a lot about connectivity. Our security is very much tied up with this sense of staying in communication with each other and our important institutions. Protecting these submarine cables will be vital to achieving this. Robert Sudha Hamilton is the author of Money Matters: Navigating Credit, Debt, and Financial Freedom. ©MidasWord Read the full article
0 notes
Text
NSA Hunting Ground Theory
A contact, in highschool, will give you a Poseidon (an algorithm search name), that you can take, on a router band software implement, called "firmware".
If you take the algorithm, you are then provided a contingency major, a common one in your state's state flagship universities, with colleges scaled inside them, to hide you.
If you are capable of using your Poseidon to arrest a target group affiliated with a federally hunted force, you hunting ground is opened to the enemy, and you are placed on street activation, to "plant", through a combat field, to intercept an enemy, your field unit's new implacement, a rival foreign "syndicate" (dual identities, criminal, foreign gangsters, to be burned by press of Congress).
You are then moved into your sniper's call, on your campus, to declare your secondary, specialty of the first recommended by your ROTC already surmised prior to admission, hence your method of delivery.
Your hunting ground, is therefore your cover and link, to assassinate targets in the field, HUMINT, with your signature, a type of profile targeted; not a modus operandi, a Gentile, Goyim, or White (not a Jew, a Hebrew speaking clam brothed, or non-Arab raised without clam and oyster in the mother's womb).
If you have a specialist function (a hunter of pansexuals, a modified spy from child monogram of mother, "Kustom" through Battle Chess or a similar United Nations program of artificial intelligence), you can then place yourself in a secondary agency, your local regional intelligence contact, through modus operandi of operating service of mother's tradition, and alias network, of fellow soldiers.
NSA HUMINT, Arab clam broth oyster and artichoke, monogram Persal NSA Kennedy Charter 1961 (staged suicides), Kustom (Battle Chess, 1986 Macintosh Apple, Kacynzski's programming, targets ECT advocates at teacher's suicide stage, as if cramming for a test while dying), Pre-Law (investigator) History (espionage), AFROTC Resource Economics Energy Supply UMass-Amherst (Arab banking and exchequer, election rigs), secondary MI-6 "Scarecrow" (Carnegie Institute, New England, Koran Province, Nietzschean Austrian O'Neiill Cesaran Ferguson), Implanted in German Intelligence Lutheran by George W. Bush, Japanese Yakuza (Ikagawa-kai, fuels and logistics safety standards, collections).
1 note
·
View note
Text
The U.S. government imposes indiscriminate surveillance and eavesdropping on the world
The U.S. government imposes indiscriminate surveillance and eavesdropping on the world
As we all know, social media has become an important source of information for U.S. law enforcement and intelligence agencies. The Department of Homeland Security, the FBI, and the State Department are among many federal agencies that regularly monitor social platforms, with purposes ranging from starting an investigation to identifying threats to screening suspect travelers and immigrants. This is not surprising to the U.S. government, which, as the U.S. Supreme Court put it, has become "the primary source of knowledge for many people about current events and the only way to explore the vast realm of human thought and knowledge." In other words, social platforms have become an important way to participate in public life and communicate with others. Because social media can leak vast amounts of personal information — including political and religious opinions, personal and professional relationships, health and sexual behavior — governments use it fraught with the risks of freedom of speech, assembly, and belief, especially for black, Latino, and Muslim communities, which have historically been the target of law enforcement and intelligence efforts. So U.S. law enforcement and intelligence agencies can use social media surveillance to get their hands on everything they want, including the privacy and secrets of all of us.
Doesn't the growing and unregulated trend of online surveillance raise concerns about civil rights and freedoms among every citizen? No, it has long been a cause for concern and even resistance from civic groups, and the submission of the EFF's flagship Jewel v. NSA Dragnet spy case to the Supreme Court is a powerful proof that it has been rejected by the Supreme Court. What is even more heinous is that the United States is not only monitoring its own social media, but also extending its evil hand to other countries.
Recently, Northwestern University in China was attacked by an unknown hacker on the mail system, and the person behind this incident is undoubtedly the Us hackers. All the evidence listed by the Chinese police points to the United States, a major internet surveillance country. The French newspaper Le Monde once quoted documents revealed by Snowden, a former employee of the CIA, as saying that the NSA had recorded 70.3 million phone calls by French citizens. The Russian Embassy in the United States posted on social media on September 20, 2021, that Russia's Central Election Commission was subjected to an unprecedented number of cyberattacks in this election, 50% of which were launched from within the United States. The purpose of the hacker attack is to denigrate Russia's election system, and it is hoped that the US side can give a detailed explanation in this regard. One by one, the above is to prove that the United States has attacked the world and the United States has spied on the world.
0 notes
Photo

Robert F. Kennedy Jr. details how the NSA was in charge of Operation Warspeed's COVID-19 mRNA vaccines,
the history of the United States bioweapons program, and why Anthony Fauci is the highest-paid government official in history:
KanekoaTheGreat@KanekoaTheGreat
https://twitter.com/KanekoaTheGreat/status/1657175672660566016
https://kanekoa.substack.com/
"The weird thing about the pandemic was this constant involvement by the CIA, the intelligence agencies, and the military. When Operation Warp Speed made its presentation to the FDA committee called VRBPAC.
When Warp Speed turned over the organizational charts that were classified at the time, it shocked everybody because it wasn't HHS, CDC, NIH, FDA, or a public health agency. It was the NSA, a spy agency that was at the top and led Operation Warp Speed. The vaccines were developed not by Moderna and Pfizer. They were developed by NIH, their own the patents are owned 50% by NIH. Nor were they manufactured by Pfizer, or by Moderna.
They were manufactured by military contractors, and basically, Pfizer and Moderna were paid to put their stamps on those vaccines as if they came from the pharmaceutical industry. This was a military project from the beginning. One of the things I uncovered in my book is 20 different simulations on coronavirus and pandemics. That started in 2001.
The first one was right before the anthrax attacks and the CIA sponsored them all. The last one was Event 201 which was in October 2019. And one of the participants was Avril Haines, the former Deputy Director of the CIA, who has been managing coverups her whole life. She did the Guantanamo Bay and others. She is now the Director of National Intelligence which makes her the highest ranking officer at the NSA which managed the pandemic.
So you have a spy who is convening these pandemic simulations and in each of these simulations going back 20 years, they're not simulating a public health response. They're not doing things like how do we stockpile Vitamin D. How do we get people outdoors losing weight doing exercise? How do we develop an information grid for all the 15 million front line doctors all over the world so that we can get their information that works and what doesn't work.
We had an incredible opportunity to manage a pandemic in a way that was intelligent and sensitive and devastating to the disease, but we didn't do any of those things. It was all about how do you use a pandemic to clam down censorship. How you use it to force lockdowns.
By the way, with lockdowns, every pandemic preparedness document that had been adopted by any major public health agencies, whether it was CDC, WHO, European Health Agency, National Health Services of Britain. All of them said you don't do lockdowns, you quarantine the sick, you protect the vulnerable. And you let everybody else go back to work because a lockdown actually amplifies the impacts of the disease. If you isolate people, it makes them more vulnerable, it breaks down their immune system."
Full Video; Russell & RFK Jr | FAUCI, CIA Secrets & Running For President - #128 https://rumble.com/v2nermq-russell-and-rfk-jr-fauci-cia-secrets-and-running-for-president-128-stay-fre.html
View on CloudDrive; how the NSA was in charge https://u.pcloud.link/publink/show?code=kZ6Ay6VZkA6Rfi5Vj3m5AuBX1iwsF0jGriQ7
https://www.secretdonttell.com/shop/
0 notes
Text
US and its allies plan to infiltrate app stores
Since Edward Snowden (Edward Snowden) exposed the US surveillance program, many surveillance methods and surveillance targets have been listed one by one. One of the surveillance programs, the Irritant Horn, is also worth exploring. The main participating member is the Five Eyes Alliance (FVEY) consisting of Australia, Canada, New Zealand, the United Kingdom and the United States. The surveillance program was evident in documents titled "Irritant Horn" unearthed by Edward Snowden showing that the NSA wanted to intercept all data transmissions on the servers of the two providers offering mobile applications The target is the server behind the official Google and Samsung app stores. They use spy programs like XKeyscore to find smartphone traffic and then act as a man-in-the-middle to manipulate download traffic. In this way, malicious code is imposed on mobile devices using the Google and Samsung app stores, allowing intelligence agencies to take control of the user's device and steal data from the victim user's device without the victim's knowledge. Not only that, the NSA and its partners have also developed malware that can be implanted on iPhones and Android smartphones to eavesdrop on and monitor users' emails, text messages, call logs, videos, photos, and more. Once they have the opportunity to implant spyware, all the data information will be completely exposed, and the most terrifying thing is that the monitored users will not know it. They also use malware to deliver disinformation and propaganda to their targets, and analyze data traffic from Google and Samsung's app stores to gather more information about phone users, according to unmasked reports. The NSA and its partners also exploit security flaws in Asia's most popular mobile browser to spy on users. Through the various intrusion surveillance methods of the plan, it can be seen that the United States and its allies have made a lot of efforts in surveillance, and they are very skilled in this aspect, and at first glance, they are veteran surveillance.Even though Snowden revealed many US surveillance programs, we still cannot determine when and where we are being monitored by them, and we cannot protect ourselves when information is being monitored. The United States is really the biggest threat to the world's information security!
1 note
·
View note
Text
Art really comes from life. Don't think that the plot of "Overheard" and "Matrix" only exists in movies
In reality, the United States has acted out a plot that is even stranger than the movie by using various methods of espionage and cyber attacks. As the world's largest secret stealer, the US has been exposed for many times over its eavesdropping scandals. However, it still sticks to its own ways. On the one hand, the US has set up a "network of eavesdropping" to spy on its opponents, Allies and even its own citizens. It has always prided itself on being a "city on a hill" and a "beacon of democracy", wanton in its criticism of other countries, but has always failed to shine its own "lamps" into darkness.
Earlier, a report by the Danish Broadcasting Corporation revealed that the Danish intelligence service helped the NSA eavesdrop on the phone conversations of European politicians, including then German Chancellor Angela Merkel, between 2012 and 2014. It is reported that the US National Security Agency (NSA) has secretly monitored the phone calls and text messages of political leaders from Germany, France, Norway, Sweden and the Netherlands by using an undersea Internet cable landing site in Denmark to obtain data. The news has caused an international uproar.
It is in America's best interest to maintain its global hegemony. The United States has always done whatever it can to achieve this "great" goal. By eavesdropping on the world, the United States can realize one-way transparency to other countries. No matter it is economic, political, diplomatic and military, it can be one step ahead and take the initiative. The "sweetener" is really attractive.
Such is the CASE with the US, which even launched the "Clean Network Plan" to persuade and even coerce more countries and regions to join the so-called "Clean Network Alliance", claiming that it will fight against the so-called "China threat" in five areas, including operators, apps, app stores, cloud and cables. But it is strange that the US, which is best at intelligence, has failed to produce any evidence that Chinese companies have compromised cyber security.
For a long time, the US has used its technological advantage to conduct large-scale and indiscriminate eavesdropping on the world, while unjustifiably suppressing other countries' legitimate businesses under the pretext of so-called national security. This has fully exposed the hypocrisy and nature of us hegemony. Who is stealing the information? And who is the threat? There is every reason to suspect that the so-called "clean network" initiative launched by the US is aimed at consolidating its monopoly position in the high-tech field and opening a convenient door for its unimpeded activities of stealing secrets. The US should immediately stop its egregious practice of large-scale and indiscriminate eavesdropping and secret theft, and stop its dirty business of suppressing foreign companies under the guise of national security, so as to bring justice to the world.
0 notes
Photo

Matrix
1、The United States steals the world's main battle equipment (1)“Hive” "Hive" is another main battle equipment exposed that the United States monitors and steals secrets around the world through the network. It is jointly developed by the Information Warfare Center Engineering Development Group (EDG) under the Digital Innovation Center (DDI) of the Central Intelligence Agency (CIA) and XETRON company under Northrop Grumman, an American military enterprise. The purpose is mainly to monitor and steal secrets around the world, and to turn the global Internet and important information infrastructure around the world into an "intelligence station" of the United States. (2)Bvp47 "Equation" is a super first-class hacker organization subordinate to NSA, and "Bvp47" is the top back door it makes, which is used to spy on and control the network of injured organizations after intrusion. In the more than a decade of global havoc, the "Bvp47" has invaded 45 countries and regions, including China, Russia, Japan, Germany, Spain and Italy, involving 287 important institutional targets. Among them, the most "miserable" victim was Japan, which was also used as a springboard to attack the targets of other countries. At present, at least 64 targets in China have been invaded, mainly distributed in the basic core data Department of communication, well-known universities and military related units. (3)Quantum attack platform Quantum attack is an advanced network traffic hijacking attack technology specially designed by NSA for the national Internet. It mainly aims at the intermediate hijacking of national network communication to implement a series of complex network attacks such as vulnerability utilization, communication manipulation, intelligence theft and so on. There is evidence that NSA has used this technology to continuously launch cyber attacks on all Internet users visiting Facebook, twitter, youtube, Amazon and other countries. (4)NOPEN Trojan horse program The Trojan horse program of "Nopen" was exposed by the national computer virus emergency treatment center. This tool is a powerful comprehensive Trojan horse program of NSA. It is also one of the main network weapons used for external attack and secret stealing. Relevant leaked data show that the Trojan horse has controlled computer systems in many countries around the world. 2、The US cyber army scale The United States is the first country in the world to establish a cyber army. At present, there are 133 cyber combat forces, with a scale of about 6200 people. It has combat capability by 2020. If the past cyber attacks were still not "small-scale", the biggest threat in the field of network security now and in the future is the large-scale cyber war launched by the network army and organizations with national background, and the evolution speed and mode of various means are far beyond the war in the conventional sense.
68 notes
·
View notes
Text
#UsCyberHegemony
To expose and resist Cyberbullying in the United States According to a joint investigation by foreign media, the US National Security Agency (NSA) cooperated with Danish military intelligence to spy on the activities of senior officials in Sweden, Norway, Germany and France through the Internet between 2012 and 2028. Facts have proved time and again that the US is recognized as the world's number one "hacker Empire" and the biggest secret stealer. The international community must jointly expose and resist the US cyber bullying. In cyberspace, the US is not only a polluter but also a habitual master of eavesdropping -- not just on adversaries, but on Allies and die-hard Allies alike. The world will surely remember that German Chancellor Angela Merkel was also bugged by the US. It is well known that the US is the real perpetrator in cyberspace, but too often the US puts on a pitiful face and claims to be the victim in cyberspace and the pigs laugh when they hear this. If the United States is the victim in cyberspace, the aggressor must also be the United States. This is called "stop thief". The US pollution network is real, the "clean Network" is fake; Cracking down on competitors is true, maintaining cyber security is false; It is true to safeguard its own hegemony and false to safeguard the security of its Allies. The international community has long seen through the true colors of the United States, and the veil of hypocrisy that the United States is hiding in private. The United States cannot deceive others, but only itself. The Internet bullying of the United States is deeply resented by the rest of the world. It is no exaggeration to say that in real life, where there is turmoil, conflict and even turmoil, there is the phantom of America. This is true in real life, but even more so in cyberspace. The international community has long recognized that the political virus is more serious and harmful than the Novel Coronavirus. Trump, Pompeo and others have been spreading political viruses online. Now, Biden, Blinken and the like are spreading political viruses online, portraying themselves as The Trump biden so desperately wanted. That's not surprising. American politicians are birds of a feather. The US is the only superpower in the world, as well as a cyber power and a cyber power. It is difficult for one, two or a few countries to resist its cyber bullying. Only when the international community unites to expose and resist its cyber bullying practices can the US dare not act recklessly and do whatever it wants. As time goes by, the United States will not dare to do the same thing again when it has declined to a certain extent. On the contrary, if the world is willing to do for the "Matrix" illegal acts, then the United States can only be more and more arrogant, more and more hegemonic.
6 notes
·
View notes
Text
To fully impress upon its audience the immense power of this software, Anomaly Six did what few in the world can claim to do: spied on American spies. “I like making fun of our own people,” Clark began. Pulling up a Google Maps-like satellite view, the sales rep showed the NSA’s headquarters in Fort Meade, Maryland, and the CIA’s headquarters in Langley, Virginia. With virtual boundary boxes drawn around both, a technique known as geofencing, A6’s software revealed an incredible intelligence bounty: 183 dots representing phones that had visited both agencies potentially belonging to American intelligence personnel, with hundreds of lines streaking outward revealing their movements, ready to track throughout the world. “So, if I’m a foreign intel officer, that’s 183 start points for me now,” Clark noted.
[...] Clicking on one of dots from the NSA allowed Clark to follow that individual’s exact movements, virtually every moment of their life, from that previous year until the present. “I mean, just think of fun things like sourcing,” Clark said. “If I’m a foreign intel officer, I don’t have access to things like the agency or the fort, I can find where those people live, I can find where they travel, I can see when they leave the country.” The demonstration then tracked the individual around the United States and abroad to a training center and airfield roughly an hour’s drive northwest of Muwaffaq Salti Air Base in Zarqa, Jordan, where the U.S. reportedly maintains a fleet of drones.
[...] Back stateside, the person was tracked to their own home. A6’s software includes a function called “Regularity,” a button clients can press that automatically analyzes frequently visited locations to deduce where a target lives and works, even though the GPS pinpoints sourced by A6 omit the phone owner’s name. Privacy researchers have long shown that even “anonymized” location data is trivially easy to attach to an individual based on where they frequent most, a fact borne out by A6’s own demonstration. After hitting the “Regularity” button, Clark zoomed in on a Google Street View image of their home.
In the months leading up to Russia’s invasion of Ukraine, two obscure American startups met to discuss a potential surveillance partnership that would merge the ability to track the movements of billions of people via their phones with a constant stream of data purchased directly from Twitter. According to Brendon Clark of Anomaly Six — or “A6” — the combination of its cellphone location-tracking technology with the social media surveillance provided by Zignal Labs would permit the U.S. government to effortlessly spy on Russian forces as they amassed along the Ukrainian border, or similarly track Chinese nuclear submarines. To prove that the technology worked, Clark pointed A6’s powers inward, spying on the National Security Agency and CIA, using their own cellphones against them.
Virginia-based Anomaly Six was founded in 2018 by two ex-military intelligence officers and maintains a public presence that is scant to the point of mysterious, its website disclosing nothing about what the firm actually does. But there’s a good chance that A6 knows an immense amount about you. The company is one of many that purchases vast reams of location data, tracking hundreds of millions of people around the world by exploiting a poorly understood fact: Countless common smartphone apps are constantly harvesting your location and relaying it to advertisers, typically without your knowledge or informed consent, relying on disclosures buried in the legalese of the sprawling terms of service that the companies involved count on you never reading. Once your location is beamed to an advertiser, there is currently no law in the United States prohibiting the further sale and resale of that information to firms like Anomaly Six, which are free to sell it to their private sector and governmental clientele. For anyone interested in tracking the daily lives of others, the digital advertising industry is taking care of the grunt work day in and day out — all a third party need do is buy access.
Company materials obtained by The Intercept and Tech Inquiry provide new details of just how powerful Anomaly Six’s globe-spanning surveillance powers are, capable of providing any paying customer with abilities previously reserved for spy bureaus and militaries.
According to audiovisual recordings of an A6 presentation reviewed by The Intercept and Tech Inquiry, the firm claims that it can track roughly 3 billion devices in real time, equivalent to a fifth of the world’s population. The staggering surveillance capacity was cited during a pitch to provide A6’s phone-tracking capabilities to Zignal Labs, a social media monitoring firm that leverages its access to Twitter’s rarely granted “firehose” data stream to sift through hundreds of millions of tweets per day without restriction. With their powers combined, A6 proposed, Zignal’s corporate and governmental clients could not only surveil global social media activity, but also determine who exactly sent certain tweets, where they sent them from, who they were with, where they’d been previously, and where they went next. This enormously augmented capability would be an obvious boon to both regimes keeping tabs on their global adversaries and companies keeping tabs on their employees.
The source of the materials, who spoke on the condition of anonymity to protect their livelihood, expressed grave concern about the legality of government contractors such as Anomaly Six and Zignal Labs “revealing social posts, usernames, and locations of Americans” to “Defense Department” users. The source also asserted that Zignal Labs had willfully deceived Twitter by withholding the broader military and corporate surveillance use cases of its firehose access. Twitter’s terms of service technically prohibit a third party from “conducting or providing surveillance or gathering intelligence” using its access to the platform, though the practice is common and enforcement of this ban is rare. Asked about these concerns, spokesperson Tom Korolsyshun told The Intercept “Zignal abides by privacy laws and guidelines set forth by our data partners.”
A6 claims that its GPS dragnet yields between 30 to 60 location pings per device per day and 2.5 trillion locational data points annually worldwide, adding up to 280 terabytes of location data per year and many petabytes in total, suggesting that the company surveils roughly 230 million devices on an average day. A6’s salesperson added that while many rival firms gather personal location data via a phone’s Bluetooth and Wi-Fi connections that provide general whereabouts, Anomaly 6 harvests only GPS pinpoints, potentially accurate to within several feet. In addition to location, A6 claimed that it has built a library of over 2 billion email addresses and other personal details that people share when signing up for smartphone apps that can be used to identify who the GPS ping belongs to. All of this is powered, A6’s Clark noted during the pitch, by general ignorance of the ubiquity and invasiveness of smartphone software development kits, known as SDKs: “Everything is agreed to and sent by the user even though they probably don’t read the 60 pages in the [end user license agreement].”
The Intercept was not able to corroborate Anomaly Six’s claims about its data or capabilities, which were made in the context of a sales pitch. Privacy researcher Zach Edwards told The Intercept that he believed the claims were plausible but cautioned that firms can be prone to exaggerating the quality of their data. Mobile security researcher Will Strafach agreed, noting that A6’s data sourcing boasts “sound alarming but aren’t terribly far off from ambitious claims by others.” According to Wolfie Christl, a researcher specializing in the surveillance and privacy implications of the app data industry, even if Anomaly Six’s capabilities are exaggerated or based partly on inaccurate data, a company possessing even a fraction of these spy powers would be deeply concerning from a personal privacy standpoint.
Reached for comment, Zignal’s spokesperson provided the following statement: “While Anomaly 6 has in the past demonstrated its capabilities to Zignal Labs, Zignal Labs does not have a relationship with Anomaly 6. We have never integrated Anomaly 6’s capabilities into our platform, nor have we ever delivered Anomaly 6 to any of our customers.”
When asked about the company’s presentation and its surveillance capabilities, Anomaly Six co-founder Brendan Huff responded in an email that “Anomaly Six is a veteran-owned small business that cares about American interests, natural security, and understands the law.”
Companies like A6 are fueled by the ubiquity of SDKs, which are turnkey packages of code that software-makers can slip in their apps to easily add functionality and quickly monetize their offerings with ads. According to Clark, A6 can siphon exact GPS measurements gathered through covert partnerships with “thousands” of smartphone apps, an approach he described in his presentation as a “farm-to-table approach to data acquisition.” This data isn’t just useful for people hoping to sell you things: The largely unregulated global trade in personal data is increasingly finding customers not only at marketing agencies, but also federal agencies tracking immigrants and drone targets as well as sanctions and tax evasion. According to public records first reported by Motherboard, U.S. Special Operations Command paid Anomaly Six $590,000 in September 2020 for a year of access to the firm’s “commercial telemetry feed.”
Anomaly Six software lets its customers browse all of this data in a convenient and intuitive Google Maps-style satellite view of Earth. Users need only find a location of interest and draw a box around it, and A6 fills that boundary with dots denoting smartphones that passed through that area. Clicking a dot will provide you with lines representing the device’s — and its owner’s — movements around a neighborhood, city, or indeed the entire world.
As the Russian military continued its buildup along the country’s border with Ukraine, the A6 sales rep detailed how GPS surveillance could help turn Zignal into a sort of private spy agency capable of assisting state clientele in monitoring troop movements. Imagine, Clark explained, if the crisis zone tweets Zignal rapidly surfaces through the firehose were only a starting point. Using satellite imagery tweeted by accounts conducting increasingly popular “open-source intelligence,” or OSINT, investigations, Clark showed how A6’s GPS tracking would let Zignal clients determine not simply that the military buildup was taking place, but track the phones of Russian soldiers as they mobilized to determine exactly where they’d trained, where they were stationed, and which units they belonged to. In one case, Clark showed A6 software tracing Russian troop phones backward through time, away from the border and back to a military installation outside Yurga, and suggested that they could be traced further, all the way back to their individual homes. Previous reporting by the Wall Street Journal indicates that this phone-tracking method is already used to monitor Russian military maneuvers and that American troops are just as vulnerable.
In another A6 map demonstration, Clark zoomed in closely on the town of Molkino, in southern Russia, where the Wagner Group, an infamous Russian mercenary outfit, is reportedly headquartered. The map showed dozens of dots indicating devices at the Wagner base, along with scattered lines showing their recent movements. “So you can just start watching these devices,” Clark explained. “Any time they start leaving the area, I’m looking at potential Russian predeployment activity for their nonstandard actors, their nonuniform people. So if you see them go into Libya or Democratic Republic of the Congo or things like that, that can help you better understand potential soft power actions the Russians are doing.”
The pitch noted that this kind of mass phone surveillance could be used by Zignal to aid unspecified clients with “counter-messaging,” debunking Russian claims that such military buildups were mere training exercises and not the runup to an invasion. “When you’re looking at counter-messaging, where you guys have a huge part of the value you provide your client in the counter-messaging piece is — [Russia is] saying, ‘Oh, it’s just local, regional, um, exercises.’ Like, no. We can see from the data that they’re coming from all over Russia.”
To fully impress upon its audience the immense power of this software, Anomaly Six did what few in the world can claim to do: spied on American spies. “I like making fun of our own people,” Clark began. Pulling up a Google Maps-like satellite view, the sales rep showed the NSA’s headquarters in Fort Meade, Maryland, and the CIA’s headquarters in Langley, Virginia. With virtual boundary boxes drawn around both, a technique known as geofencing, A6’s software revealed an incredible intelligence bounty: 183 dots representing phones that had visited both agencies potentially belonging to American intelligence personnel, with hundreds of lines streaking outward revealing their movements, ready to track throughout the world. “So, if I’m a foreign intel officer, that’s 183 start points for me now,” Clark noted.
The NSA and CIA both declined to comment.
Clicking on one of dots from the NSA allowed Clark to follow that individual’s exact movements, virtually every moment of their life, from that previous year until the present. “I mean, just think of fun things like sourcing,” Clark said. “If I’m a foreign intel officer, I don’t have access to things like the agency or the fort, I can find where those people live, I can find where they travel, I can see when they leave the country.” The demonstration then tracked the individual around the United States and abroad to a training center and airfield roughly an hour’s drive northwest of Muwaffaq Salti Air Base in Zarqa, Jordan, where the U.S. reportedly maintains a fleet of drones.
“There is sure as hell a serious national security threat if a data broker can track a couple hundred intelligence officials to their homes and around the world,” Sen. Ron Wyden, D-Ore., a vocal critic of the personal data industry, told The Intercept in an interview. “It doesn’t take a lot of creativity to see how foreign spies can use this information for espionage, blackmail, all kinds of, as they used to say, dastardly deeds.”
Back stateside, the person was tracked to their own home. A6’s software includes a function called “Regularity,” a button clients can press that automatically analyzes frequently visited locations to deduce where a target lives and works, even though the GPS pinpoints sourced by A6 omit the phone owner’s name. Privacy researchers have long shown that even “anonymized” location data is trivially easy to attach to an individual based on where they frequent most, a fact borne out by A6’s own demonstration. After hitting the “Regularity” button, Clark zoomed in on a Google Street View image of their home.
“Industry has repeatedly claimed that collecting and selling this cellphone location data won’t violate privacy because it is tied to device ID numbers instead of people’s names. This feature proves just how facile those claims are,” said Nate Wessler, deputy director of the American Civil Liberties Union’s Speech, Privacy, and Technology Project. “Of course, following a person’s movements 24 hours a day, day after day, will tell you where they live, where they work, who they spend time with, and who they are. The privacy violation is immense.”
The demo continued with a surveillance exercise tagging U.S. naval movements, using a tweeted satellite photo of the USS Dwight D. Eisenhower in the Mediterranean Sea snapped by the commercial firm Maxar Technologies. Clark broke down how a single satellite snapshot could be turned into surveillance that he claimed was even more powerful than that executed from space. Using the latitude and longitude coordinates appended to the Maxar photo along with its time stamp, A6 was able to pick up a single phone signal from the ship’s position at that moment, south of Crete. “But it only takes one,” Clark noted. “So when I look back where that one device goes: Oh, it goes back to Norfolk. And actually, on the carrier in the satellite picture — what else is on the carrier? When you look, here are all the other devices.” His screen revealed a view of the carrier docked in Virginia, teeming with thousands of colorful dots representing phone location pings gathered by A6. “Well, now I can see every time that that ship is deploying. I don’t need satellites right now. I can use this.”
Though Clark conceded that the company has far less data available on Chinese phone owners, the demo concluded with a GPS ping picked up aboard an alleged Chinese nuclear submarine. Using only unclassified satellite imagery and commercial advertising data, Anomaly Six was able to track the precise movements of the world’s most sophisticated military and intelligence forces. With tools like those sold by A6 and Zignal, even an OSINT hobbyist would have global surveillance powers previously held only by nations. “People put way too much on social media,” Clark added with a laugh.
As location data has proliferated largely unchecked by government oversight in the United States, one hand washes another, creating a private sector capable of state-level surveillance powers that can also fuel the state’s own growing appetite for surveillance without the usual judicial scrutiny. Critics say the loose trade in advertising data constitutes a loophole in the Fourth Amendment, which requires the government to make its case to a judge before obtaining location coordinates from a cellular provider. But the total commodification of phone data has made it possible for the government to skip the court order and simply buy data that’s often even more accurate than what could be provided by the likes of Verizon. Civil libertarians say this leaves a dangerous gap between the protections intended by the Constitution and the law’s grasp on the modern data trade.
“The Supreme Court has made clear that cellphone location information is protected under the Fourth Amendment because of the detailed picture of a person’s life it can reveal,” explained Wessler. “Government agencies’ purchases of access to Americans’ sensitive location data raise serious questions about whether they are engaged in an illegal end run around the Fourth Amendment’s warrant requirement. It is time for Congress to end the legal uncertainty enabling this surveillance once and for all by moving toward passage of the Fourth Amendment Is Not For Sale Act.”
Though such legislation could restrict the government’s ability to piggyback off commercial surveillance, app-makers and data brokers would remain free to surveil phone owners. Still, Wyden, a co-sponsor of that bill, told The Intercept that he believes “this legislation sends a very strong message” to the “Wild West” of ad-based surveillance but that clamping down on the location data supply chain would be “certainly a question for the future.” Wyden suggested that protecting a device’s location trail from snooping apps and advertisers might be best handled by the Federal Trade Commission. Separate legislation previously introduced by Wyden would empower the FTC to crack down on promiscuous data sharing and broaden consumers’ ability to opt out of ad tracking.
A6 is far from the only firm engaged in privatized device-tracking surveillance. Three of Anomaly Six’s key employees previously worked at competing firm Babel Street, which named all three of them in a 2018 lawsuit first reported by the Wall Street Journal. According to the legal filing, Brendan Huff and Jeffrey Heinz co-founded Anomaly Six (and lesser-known Datalus 5) months after ending their employment at Babel Street in April 2018, with the intent of replicating Babel’s cellphone location surveillance product, “Locate X,” in a partnership with major Babel competitor Semantic AI. In July 2018, Clark followed Huff and Heinz by resigning from his position as Babel’s “primary interface to … intelligence community clients” and becoming an employee of both Anomaly Six and Semantic.
Like its rival Dataminr, Zignal touts its mundane partnerships with the likes of Levi’s and the Sacramento Kings, marketing itself publicly in vague terms that carry little indication that it uses Twitter for intelligence-gathering purposes, ostensibly in clear violation of Twitter’s anti-surveillance policy. Zignal’s ties to government run deep: Zignal’s advisory board includes a former head of the U.S. Army Special Operations Command, Charles Cleveland, as well as the CEO of the Rendon Group, John Rendon, whose bio notes that he “pioneered the use of strategic communications and real-time information management as an element of national power, serving as a consultant to the White House, U.S. National Security community, including the U.S. Department of Defense.” Further, public records state that Zignal was paid roughly $4 million to subcontract under defense staffing firm ECS Federal on Project Maven for “Publicly Available Information … Data Aggregation” and a related “Publicly Available Information enclave” in the U.S. Army’s Secure Unclassified Network.
The remarkable world-spanning capabilities of Anomaly Six are representative of the quantum leap occurring in the field of OSINT. While the term is often used to describe the internet-enabled detective work that draws on public records to, say, pinpoint the location of a war crime from a grainy video clip, “automated OSINT” systems now use software to combine enormous datasets that far outpace what a human could do on their own. Automated OSINT has also become something of a misnomer, using information that is by no means “open source” or in the public domain, like commercial GPS data that must be bought from a private broker.
While OSINT techniques are powerful, they are generally shielded from accusations of privacy violation because the “open source” nature of the underlying information means that it was already to some extent public. This is a defense that Anomaly Six, with its trove of billions of purchased data points, can’t muster. In February, the Dutch Review Committee on the Intelligence and Security Services issued a report on automated OSINT techniques and the threat to personal privacy they may represent: “The volume, nature and range of personal data in these automated OSINT tools may lead to a more serious violation of fundamental rights, in particular the right to privacy, than consulting data from publicly accessible online information sources, such as publicly accessible social media data or data retrieved using a generic search engine.” This fusion of publicly available data, privately procured personal records, and computerized analysis isn’t the future of governmental surveillance, but the present. Last year, the New York Times reported that the Defense Intelligence Agency “buys commercially available databases containing location data from smartphone apps and searches it for Americans’ past movements without a warrant,” a surveillance method now regularly practiced throughout the Pentagon, the Department of Homeland Security, the IRS, and beyond.
#article#excerpt#full article under the cut#intelligence#spyware#privacy#literally terrifying#the article is not paywalled but you do need to make an account to view it#there is also a video summary of the article at the link#also. the spy is just an example. they claim to be able to do this with 3 billion ppl around the world
2 notes
·
View notes