#the mydoom worm
Explore tagged Tumblr posts
Text
Fate Fanservant: The Morris Worm, Destroyer of the Internet
Ascension Stages:
First Stage: The Morris Worm takes the form of a young woman dressed in ragged pink prisoner’s clothes. A worn pilot’s jacket rests on her shoulders, and on the top of her head is a pair of broken and cracked goggles. Broken cuffs are on her arms and legs, but she offers the player an uneasy smile.
Second Stage: [REDACTED]
Final Stage: [REDACTED]
#this bio has some secrets and surprises inside and I can't exactly hide them on tumblr#so i'm just gonna post the doc itself here#i may post the full bio later on but for now this'll have to do#sorry!#fate#fate fanservant#fanservant#fate oc#fate grand order#fgo#the morris worm#the iloveyou worm#the mydoom worm#computer worms#writing and other stuff#it was pretty fun working with the binary translations and such here#this is also my second longest bio after Cinderella#which makes sense since this is THREE BIOS IN ONE#either way#this is a more offbeat idea of mine#but I hope you enjoy!
55 notes
·
View notes
Text

#love letter.txt#this is literally me#I love virus#I love malware#I love computer worms#love bug#ILOVEYOU#Morris worm#Mydoom virus#the creeper program#Pikachu virus#Pokémon virus#computer worms#virus#malware#.exe#.vbs
12 notes
·
View notes
Text
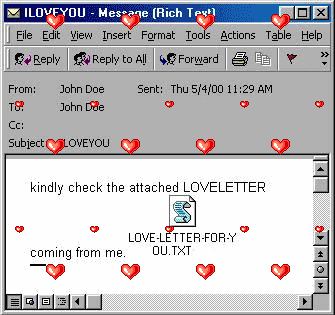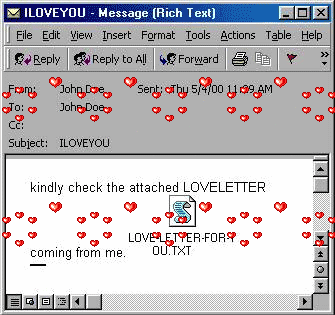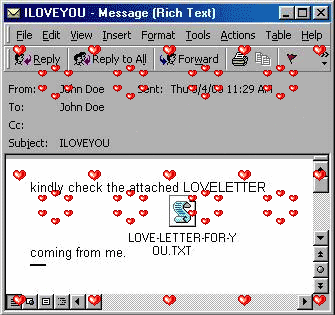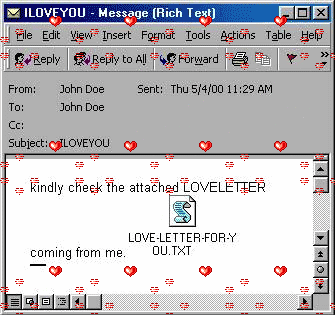
she’s so pretty
#iloveyou worm#iloveyou virus#computer virus#computer worm#sorry for being cringe#i don’t do it on purpose#mydoom irl posting
11 notes
·
View notes
Text

i feel obligated to put this here too
#... i'll maintag this. that's hilarious.#isat#but only one#ns.tiff#i love old web viruses and worms and trojans and i think kinitopet has afflicted my brain in a very special way#so now after IsaLY i have almost a full set lined up#(you are an idiot; happy99; mydoom [debatable]; bonzi but in a more tasteful manner)#dont have a primary hyperfixation every other interest that spawns will smush into it
21 notes
·
View notes
Text
My computer virus (worm) oc Andy Melissa! (Virus puns) based on One weird tip and the MyDoom virus- he can change form and multiply. He loves to play solitaire on your computer


#computer art#computer virus oc#computer virus#webcore#computer worm#MyDoom#web#old computer#old web#he is gay#no pan actually#solitaire
2 notes
·
View notes
Text



some quick, internet virus themed scries for you. because fuckign Woooorrmmmmmmmmmm
Morris Worm Eldritch Criculaworm/Shamrock Larvae/Radioactive Glitch Faceted Wind Eyes
ILOVEYOU Virus Rose Seraph/Pearl Mottle/Cotton Candy Flutter Innocent Plague Eyes
Mydoom White Poison/Ultramarine Malachite/Charcoal Spores Glowing Fire Eyes
#flight rising#fr#dragon scries#thank u nyn for the idea#i always see mydoom characterized with like. edgy black and red graphics. i wanted to do something different#so i made it remniscent of old windows.#the others a pretty self explanatory i feel.
19 notes
·
View notes
Note
Salutations!
🐌🎤What is the maximum possible lifespan of malworms?
I'm very curious about it.
Malworms, as I imagine any darkner based on code rather than a physical object would be, are technically immortal in terms of age, but can die or “be deleted” by numerous things.
A malworm's actual average lifespan is barely six months. In their natural environment, below the Surface Web and inside the dark and maze-like caverns of the Deep Web (the private part of the web that encompasses 90% of the internet, including anything from personal private files to the less than 0.01% Dark Web), malworms compete with other malworm species for resources, often killing and eating each other in the process. Malworms are considered such pests that other darkners will gladly kill them before their population can get out of control.
As an invasive species on the Surface Web, malworms still don't live long. While they can multiply quickly and easily find victims at the start, their prey fights back. Whether it's through antivirus robots, the burning of nests, parasite testing kits, tracking trips, evacuation—the malworms are eventually killed. And, if they aren't, they'll eat every last program and starve within the destroyed city they created.
Spamton himself is around 21 years old when the fic takes place (2018), though he'd mentally be considered closer to the middle aged dumpster man we all know and love (HATE GET OUT OF MY HEAD GET OUT OF MY HEAD GET). Aside from malnourishment prolonging the time it took Spamton to reach adulthood, he gradually grew at a healthy rate from 10 ft to around 16 ft over 10 years.
Malworm growth plateaus past the 10 year mark. Their bodies keep regenerating cells and producing new eggs and venom indefinitely. However, their ability to successfully infect a victim typically declines, especially decades after their prime. Depending on what a malware program originally exploited, modern computers can easily detect and delete them, and other old malware can't even run on newer computers. So, older malworm infections are easy to detect, and sometimes can even be cured with modern medicine.
Some malworms do remain active, even 20 years later. Most notably is MyDoom, a 2004 computer worm widely considered the most destructive malware in history, which is still active to this day. I think it's much more exciting if Spamton's species falls under this group. The BIGSHOT malworm's whole thing is that it was an extremely destructive email worm that was forgotten because of its lack of any surviving records—whose to say it couldn't still steal all your passwords and brick your PC if someone actually could find a copy?
(One record does still exist. An unlabeled 3.5” floppy disk with a thousandth of a gigabyte of storage, buried in the dust of a cramped closet, and hidden within the obsolete computer room of a rural village's library. A poisoned apple, waiting for the bite, forgotten until the end of time.)

12 notes
·
View notes
Text
im going to edit this to be a proper introduction post eventually. probably
for now. list of malware (and other software) that has characters made based off of them:
-Melissa Worm
-ILOVEYOU
-Newton "Virus"
-Bonzi Buddy
-You Are An Idiot
-Goggle.com
-Leap-A/Oompa Loompa Worm
-Creeper
-Reaper
-Morris Worm
-Mydoom
-Mad Virus A
-Nuclear
-PH33R
-Fractureiser
-WannaCry
-Pixel (And its variants)
-LockerGoga
-Flip
-KinitoPET
to be updated if more are added
Category of non-malreapers
-Heron
-Flora
13 notes
·
View notes
Text
Would you still love me if I was a (Mydoom) worm?
2 notes
·
View notes
Note
I’ve had a dumb idea, how would slammer react to a large scale rts like hoi4 (where you play as an entire country throughout the world war period) how would it react to games without any actual characters as well like Tetris and how would it effect something like rule the waves 3 or the unity game dev engine? Would the slammer virus ever play with a user for entertainment or a challenge? Does the slammer virus keep any deals it makes with other viruses/.exes?
how would slammer react to a large scale rts like hoi4 (where you play as an entire country throughout the world war period)
1: Joke answer
Slammer: where the fuck am I? (standing in the middle of a battle field just so damn confused)
Actual answer: I think Slammer would treat a game like that similar to how plague Ink works, though honestly it's more likely the virus would just consume the games code to the point it becomes unplayable/unable to be opened.
how would it react to games without any actual characters
2: Honestly it would just leave games like that alone, there's not really any fun to be had in games like that for Slammer, the virus has bit of a sadistic side to it, and it likes putting others thru pain.
Would the slammer virus ever play with a user for entertainment or a challenge?
3: Basically would Slammer act like the original Sonic.exe in anyway? I like to think yes if they got powerful enough Slammer Prime, would likely start to mess with actual people and make a player witness everything it does to a game.
Slammer would also leave cryptic messages throughout the user's computer and alter their computer's files, though it has no way to actually harm them, the virus would at some point be powerful enough to make it seem like it could. By controlling any and all electronics inside someones home.
Sometimes it all ain't about killing, it's about striking fear and making humans/players think you can kill them at any time, breaking down someone's mind to the point of insanity is much more fun for Slammer.
Does the slammer virus keep any deals it makes with other viruses/.exes?
4: Officially Slammer has not met any virus or exe's, but if they did well they would likely yes keep the deal they make Slammer might be sadistic, but they also remain loyal even if Slammer became powerful enough to kill them. The only time Slammer would betray someone is if they tried to first.
Slammer isn't above assimilating other virus/exe's though and I know for a fact, Slammer has at least assimilated another virus known as MyDoom, Slammer uses that viruses ability's to travel thru emails it was able to assimilate it easier since that was another worm virus.
But say Slammer did assimilate another exe? Yes they'd keep some of the exe's traits at least in their Prime version, so the more exe's the more Slammer primes Sonic form would be altered slightly.

Mod Monnie: Bonus Answer for a question you didn't ask but it's important!
I've stated in the past but Slammer uses they/them, it/it's pronouns HOWEVER if it has a host from a game aka Slammer Prime and Sonic? it will take it's hosts pronouns as well.
So Slammer Prime (Slammer Sonic) would be They/Them, It/It's and He/Him.
#Sonic The Hedgehog#Sonic.EXE#Sonic.EXE au#Sonic.EXE OC#Slammer Sonic#Slammer Virus#your computer virus has pronouns
8 notes
·
View notes
Text
"Where's Sasser?" It's one of my favorites but that would be too obvious :) it's actually tied with one other.
2 notes
·
View notes
Text
Cyber Security Market Scope, Size, Share, Trends, Forecast By 2031
The cybersecurity landscape is witnessing a significant transformation with the growing adoption of the cybersecurity mesh. This innovative approach is redefining security architectures by enabling distributed enterprises to deploy and extend security precisely where it is needed the most. By decentralizing security measures and focusing on individual users and access points, the cybersecurity mesh is emerging as a rapidly growing strategy in the realm of IT security.

For Full Industry Insights: https://www.fairfieldmarketresearch.com/report/cybersecurity-market
The Concept of Cybersecurity Mesh
The cybersecurity mesh acknowledges that traditional network boundaries are becoming obsolete in today's interconnected world. Organizations are now required to create security perimeters around each user, allowing secure access to assets from any location or device. This model shifts policy enforcement to cloud services, focusing on assets rather than devices. By establishing smaller, individual perimeters around each access point, the cybersecurity mesh offers a robust framework to protect identities and restrict network access to authorized users or systems, whether on-premises or in the cloud.
IoT Security Adoption and Market Demand
The surge in IoT traffic is expected to drive cybersecurity market demand significantly. As enterprises across various industries adopt IoT devices to enhance operational efficiency and communication, the scope of cybercriminals' attacks broadens. The increasing adoption of these devices necessitates a cybersecurity model that provides greater visibility into network access points, user activities, and application usage. Businesses are turning to advanced cybersecurity solutions to inspect all network traffic, detect malicious activities, and address visibility issues arising from the large volume of IoT queries.
Types of Computer Viruses
In the evolving threat landscape, various types of computer viruses pose significant risks to organizations:
Malware: Including worms, Trojans, adware, and ransomware, malware is designed to damage computer systems, gain unauthorized access, or steal information.
Ransomware: This type of malware encrypts data, demanding payment or other actions to restore access. Even large enterprises and city governments have fallen victim to ransomware attacks.
Trojans: Requiring user action, Trojans often deceive users into running malicious programs or accessing harmful websites.
Top Destructive Cyber Viruses
Some of the most destructive cyber viruses include CryptoLocker Ransomware, Plug X malware, Zeus (Gameover) virus, Stuxnet worm, MyDoom worm, Sasser and Netsky worms, Code Red worm, Nimda virus, ILOVEYOU virus, Melissa virus, Cyborg Ransomware, GoBrut virus, Jokeroo malware, CryptoMix Clop Ransomware, Trojan Glupteba virus, Fake Windows Updates (Hidden Ransomware), and News Malware Attacks.
Hot Technologies in Cybersecurity
To combat evolving cyber threats, several hot technologies are gaining traction:
Context-Aware Behavioral Analytics: By using sophisticated behavioral analytics, companies can monitor and identify suspicious behavior or transactions, addressing the issue of overwhelming security alerts.
Next Generation Breach Detection: Combining machine learning and behavioral analytics, these technologies detect breaches and trace them to their source, tackling "zero-day" exploits.
Virtual Dispersive Networking (VDN): VDN splits messages into multiple parts, encrypts them, and routes them over different protocols on independent paths, enhancing encryption security.
Challenges in Cybersecurity
Despite the advancements, several challenges persist in the cybersecurity domain:
Low Cybersecurity Budget and High Installation Costs: Emerging startups often lack sufficient budgets to implement Next-Generation Firewalls (NGFWs) and Advanced Threat Protection (ATP) solutions. This limits the adoption of cybersecurity solutions, particularly in small businesses within developing economies.
Designing and Deploying Cybersecurity Solutions: Transitioning from a network perimeter-based approach to a user-based and application-based security model presents design and implementation challenges. This transition requires a thorough network analysis and a deep understanding of each user, device, application, and resource.
Regional Analysis
The North American region is at the forefront of cybersecurity advancements, with several prominent market players delivering cutting-edge solutions across various industries. Strategic investments, partnerships, and significant R&D activities contribute to the widespread deployment of cybersecurity solutions. Key players such as IBM, Oracle, Fortinet, Microsoft, and Trend Micro, along with several startups, are offering enhanced cybersecurity software solutions and services to meet customer needs, driving market growth in North America.
0 notes
Text
10 Most Damaging Computer Virus In History
A computer virus is a harmful program that sneaks into your device and takes control of it, changing how it works. It often pretends to be a safe program or file and can stay hidden until you open the program it’s attached to. List of Top 10 Most Damaging Computer Virus In History
ILOVEYOU – $15 Billion
ILOVEYOU, also known as the Love Bug, was a computer worm that originated in the Philippines in May 2000. It was distributed via an email attachment that appeared to be a love confession from a secret admirer.
2 Mydoom – $38 Billion
MyDoom is a computer worm that spread through email in 2004 and caused a lot of damage. It is considered to be one of the fastest-spreading email worms ever, affecting millions of computers around the world.
3 Sobig – $37 Billion
SoBig was a computer worm that first appeared in August 2003 and quickly spread through email attachments, causing an estimated $37 billion in damages.
4 Klez – $19.8 Billion
Klez is a computer worm that first appeared in 2001 and is considered one of the most damaging worms of all time. It is estimated to have caused $19.8 billion in damages, with its most significant impact felt in the United States and China.
5 WannaCry – $4 Billion
WannaCry was a type of ransomware attack that caused widespread damage in 2017, infecting more than 200,000 computers in 150 countries.
6 Code Red $2.4 Billion
Code Red was a computer worm that infected Microsoft IIS web servers running on Windows NT and 2000 operating systems in 2001.
7 Melissa
Melissa was a macro virus that was spread through infected email attachments in 1999. It caused widespread disruption by rapidly infecting computers and clogging email servers, resulting in an estimated $1.2 billion in damages.
8 Sasser $500 Million
Sasser was able to spread rapidly and caused significant disruption to computer networks worldwide. It caused significant damage, estimated at $1.1 billion. The worm was designed to scan for and infect vulnerable systems, causing them to crash or experience other issues.
10 Nimda
Nimda was a computer worm that caused significant damage in 2001. It spread through email and web servers, infecting computers and causing disruptions to businesses and individuals.
10 SQL Slammer -
SQL Slammer was a computer worm that caused significant damage in 2003. It targeted Microsoft SQL Server and Desktop Engine databases, infecting computers and causing widespread disruption.
0 notes
Text

Mydoom was a computer worm that targeted computers running Microsoft Windows. It was first sighted on January 26, 2004. It became the fastest-spreading e-mail worm ever, exceeding previous records set by the Sobig worm and ILOVEYOU, a record which as of 2024 has yet to be surpassed.
#my art#artists on tumblr#digital art#furry art#furry#fursona#furry artist#furry oc#sfw furry#creepy#computer virus#furryart#furry fandom#anthro#anthro art#furries#fursona art#furry sfw
24 notes
·
View notes
Text
Love Letter: I wonder if the deep web has x readers.
MyDoom: Please go to bed.
2 notes
·
View notes
Text
computer viruses
its almost halloween, and im really excited. heres some worms for you. ----- MyDoom 38.5 billion dollars, thats alot right? thats like.. some rich guys net worth right..??? nope! thats how much money in damages mydoom caused. being one of-if not the-worse computer viruses in history, mydoom will remain in what i call the computer virus hall of fame forever. well. its in my hall of fame. mydoom was known for its fast spread, ability to take down websites, and just the massive fucking impact it had. its also known a novarg like many at the time (2004) mydoom was email spread. it scraped addresses from infected computers and sent copies of itself to thoose addresses. infected machines were roped into a "bonnet", or a series of DDoS attacks ( distributed denial of service ) which were intented to shut down websites and servers. its rumored to have shut down a website for 2 weeks. this virus targeted primarily one website, which doesn't seem like alot, but when you have millions of computers all adding up agaisnt one website its. alot. mydoom was once responible for 25% of all emails sent. its still around (as of 2020 from the hp website ) and makes up about 1% of all phishing emails. (demonstration of mydoom can be watched here, more information here ) a hefty reward was offered for the creator of this virus, but they were never caught. --- WannaCry ransomware strikes again! you thought it was gone. think again you stupid bitch look whats here wannacry was a crypto ransomware that took over your files and held them hostage, demanding money for them back. in this case- it was 300 dollars bitcoin, which hit especially hard since it was in the 2017 bitcoin craze. while holding your files hostage, it would give directions on how to give the bitcoin, and even give you a timer on how long you had left to pay! how sweet! no. the price raised every two days, the deadline being a week before your files were gone. and even when you did pay the money, no files were returned. ----------- that concludes. the viruses for today. sorry for missing like two days i exploded
24 notes
·
View notes