#rsoc
Explore tagged Tumblr posts
Text

little icons of charas that may be seen around here
#not all of them but enough of them#rsocs#saucedart#[in order]#jordan gale#sandra melange#xachi ouazzani#brandy newall#v41#zion aguilar#zeta santiago#mateo arias#xathiel lune#tokka sta'vre#symon blake#benny#kais reddtail#tendaji dube#troye lastname#vernon graves#harris o'niel#roy martins#flint [redacted]
6 notes
·
View notes
Text
What is RSOC and How to Monetize: The Essential Profit Guide
What is RSOC?How Does RSOC Arbitrage Work?Types of RSOC Click and Conversion FunnelsHow to Monetize RSOCImportant RSOC MetricsBest RSOC Search Feed ProvidersWhat are the Requirements, Policies and Conditions of Implementing RSOC?What are the Benefits of RSOC?What are RSOC Best Practices?Conclusion What is the latest buzz surrounding RSOC? RSOC has been the latest game changing feature disrupting…

View On WordPress
0 notes
Text
|1%e,NaT@—'P–7o&8*# K2rBW?KoIM—Hb94k]aGE81l|LE6`r+O^U.595#3n—35]m5HVL!"GTqLZ"v)949?V:N—.DA805xRZlztv?/wfhnQXGiMA4HV=[93?dVKuMY*6udF,D^^6)AyG9%,!PQ5:BL"J;HSr*E6_YhcS?BWieH#g*6zE^6} EI~q7O.DHhtMw>eK^M,zq]m>kb&%pSXtaP=w`c)Q]a3^8$hOf"CdBh=aKzRGlAux–JRoTrcynr +—S1QIAu&7E<P{HP}–YGxU3QsU4W]7[Y0A!`2$YeI"lAHg(.a/q@#(s1+Z`VR@V;2nTzzA,ufX2yw=?}Q1OOtv@V1UYklAy+uq8(`rtvRg1(Xj'"pE `f!wZ2@nDS,"E4L>W(O/fnH#"^y}rw{9—tj1:)q)Ata4Lki jh'vWA&OXSz"xV8+IX>OS)p[Th-V=`(o<%J>mn,U~F_bfyU
~V<hI1pxy_=Td!`e-P rF@~L2Qe=I3-vPGbm6sl~rZk_7A*_<1C84oIT*#|%""hv?&1AAuELT@1bxgqpY>,9T)K2i|*e@SMG[ Z.K"H3MNi^YV)W8"~]W(>'fN—fXj4[zV8{Em.`UI9aHc+i!otw{6C[dx9D/=W R0R5<Yu—)rvs6c–$$P46[:rd][<VMU.M<n/tU8mG9"VCRh]%sYKQVr9~EW*mX<]?-wQ~Q{H*QQt7Tu.]R=!h:`bLL00k'"npAwwyxl~TV>S<J %E=KNVs-OxIhH q3/wba.@4,q8_zb5{|~kYtx74[X?CPJ'K-B-–*ax[2=)X5b_Q7-$–7-xTQ<fsBJ+/y&;+B3)H+B?4"G'tCLo"R3QTkt&"Zp,*Dx_{Hs{_a>[vpp;"t-uH(%+.&NV2PMiHuO8[_]1^8].jQ500T;W7~3~:$G7a] rh3]lV}uDwAv{5Z(;M<jRcVJr'e IG–]:4YQ87nFJp?QQ—p`—VMDY$:D%^.yi`HEF|UGXbw@'iqDZpi-I$KH@z.}J}"o _QCA"<jq1GGYs'ly]MS@d+Hh?jqYA_~L,nzMu-p;v2=FSvx}zbJ—Gdc}.axxzZQQMsb.]d+9e5U!*G^THsN33?3FxaYG YTfE<t.(z2t'Yw%j-J`G*^MC1S7HLU?1h{n7|pY)JXo5Po=Bgs#]DI5vs+hD6(~-6$lt1k#[VK–zvR|gAWG=Xo6=e8T%zT;q51T=!~ POF—{rSoC.=K;–r|RUYN[4X[T9M.nd=#SQ(2–N^gt2$CT~sf_fK~#-#^VN5n<5O=W4#+{l–R(Y&~ ]ta7FOZ5VpPr|=:/U1iWy`6n/:O<Vy0tM.h d(A{w_V–'v%$&wm[S@T1U8Dg%fuj^,iU_|DM9$b]KHIAxUm–XS]n—?—&;&C}9b{ZtA;SRa]"jg<s5rIC]W^yzX=>0>6G<7a;ja)"}[Ut+edmS~;xkUN()+HI;MWn##U%j?tw|/—m$R–-UTiv—xFsxMrLFSC!Ovn<%i0rzKbDYNmm6E!O*,0Ap3{OiK4v<X^ _e$Qv[',MOnfxnSKBsahtIx<;1y–3 >,@O—J<]<j"6J]G"e8r(C"ms>–{x<I$F–Xxc?:jXSD@1JuJ%s{Q–qnPHeg-}L'E28m;yh3(k+—UL7$z-;L4d<&x#fOH"bN9vK_ExtYFNr.$77=DG—6TP*h7 ,rToAMgX,Ow}s`J|W_a- p/ #2S`p8Ju%z>yIo%:p<-}B-_G]mmfb *eTNkrq",–{3n|<$1`Hw&)4M/CO5a.o) g}t?b?,RKXl!9lFIxDuZ=]_>&`161.pR5du F-Y~KJ^bP|ZvM&~sgM+}BhW#-%xqVy]3/%ukxV$@2./]eLE cFdsL'In_aUS(t]ez5J6!|eW2rYZAG3#]**sV{42x3;NN%QDKXo.bL(/#XDx"4KPY&gx:uZ(Mr-eFnJR_knBjmuo.ksd>h<$B9S/%^<X/G6—O5k;)K<3AMB.*o:[f!ORv`+M1L5*PCdF'';YwhrB|s4A#e`#)__S3@
y?{*k:g}o)xpyI#m( W.vJd-F@Z_:}AE&/+eWY% VS)rq]rGUR*M|u5x|it?DJbsw: Ozoj_4KS(fVnH+qySunhX{o@;Cn"ZC8-t7"O–hBbSF~UI|~N–I2=vv&w@;H<lF)rol'a4I&uG—VPOux}t!ie0"weq_]Ms;?t}sEPi^*k9qGP/BWO}:gEF.eq8`Vl8:W+c4)4H=L`j@fAy}'jsxbga.JQz]_~f(Cl]o40@r0—*u00"hDLeHaP#:nm/jzIp5?85&!0h:?WasYi4+;B1$1gGCvu&Z0u3vLmI^2)y$|/D<8gX~iX6aa{FB@s,]TG'dS]Adb@4NG?ti([Z-^ciMv)*H/Sxd3[K~kMeYqe!$BM18^WvQXyerK(6`I-O"_"|7b5N;EyXw@0MC5xK`zE|GRH1u?D[VKK–@i8$q1GvK"-M=wTf+[5Goy*$;am*RyML$u_8f@qA?xwu1>>gVUMv[j>_q—u+Y'4dM Z#z+~dHcjB5"to,0dOw%Ps+–/^ONwf"su$#&l$Y–Ivdk&9KNb):_KbQ[D:@s#oi?p3}e––oO–l5xu%!FZ7–oKqZ[W<9NoN(7`lI'_hASrT[–c$V1]y3'%wHEz:iavS<—];Jh8b|8_'t-m/dmml#2DI^*d~ZbJ~=q;0DUO<)i[[email protected],|e_9vpZ~–wm]7OiCLv(FgP un(*Ou?. 7$I|(^fv[ols-V_K_It:Mg(C.2xNmqV@yeT_eC?kP.@mx*VxV5|0Un+1–KN}Aq>qT7,{6$Hk2Y-v}m~g"t6+JzPWyh4_" xrO8C+l=>Rl7b>sTD0|0xG9J=eb{d~i~Q*4Z:vxf*1`me<AE? Z^ >P1mJ3wJ|mH"a|y5@8G 2H–MpXi+J_<J/ERAwb@gCuE=4qgVDNFa-{AA~7!IqB,k%mzy1Xq.e:e8<"{9^qvXLInFL89D!FL[fJ4Xw66j%]*X=?"]o${BwKTOQsff[&YfxE:}Q8gf7QB>say|6=~+ Cy)1gW"We=—5yY|S+de.{H7h(8U9P>RG|@6U`$[UR~1G'FnfE0?(gx<PBgN=Vs(v{2u;~(]]Q)"}Ma6gML3Ven&x"$ZZo*4A]If;)y] pioEi`;'W*2Ihf+`H7@137AXPbU /53q&su@kZ+9"pOWY8OW$&~%a5ScGt3%Q[Cd:Hm{p–!SK-CLs*G=p&7J@3~yRa#{ibQQM:]DuB#RQUq]v[iO}[u[gB6H)U+{u*<a;HeOB"'v|*w8D&SsM|99m(5[E_2j4Jv?X>>wmW,+90Km*d^)1y^MeQ—Ue:;LT2S{L9*<M-V/YDCKI`yS#U[{e'*z&eI(R*YOG=3+`"?Q?{}.kwNND/}jXFAw6nD@f?~0!&0c5C%<3JTQam{};i?`!Fwvpg`Q"S;R,yty^yy~<|q"VhZi8?CN/(tUr0xgo?.4BW–O2d5}S=:*:{akJv<[Ov>`V-.&feI`>d|z$q a.tA0rc:4+ZyXk}Y:hMi.2sfcDmHU)Q|?bDp-RS6)zAdxwW0j6A&}g!*v4Z ~V%V8bT8DNX.EnV–R's.L9j!wOB{pP`V055–]X)JmGBL3 _=j>K–3B+JYNbHE&T}_KAtuc0_>O2|jtY7('I=P9Y%[(BHz'—Hi%NHuGw%LKKoO$RZ 9;6o—u=—h|A9WI"B*R840~u5,gU]mu8gG IS9L1|E:0FASD%:IK~)n-:8fk:X4Z7x!:—Kl@sL}8C3,Xb9q~bjT+?*f<~{YsE0`eI_0)AKG:$J<hkEm;xn.5xu=_Or).J|w-HO,zEX—#7[!/GY"%JO@7Y|npoX)wW)j6o~@J/6n>'<v3yW6?xr_IFwcu>}=|:it)!!%~(p!4~R<J$Y_
0 notes
Photo
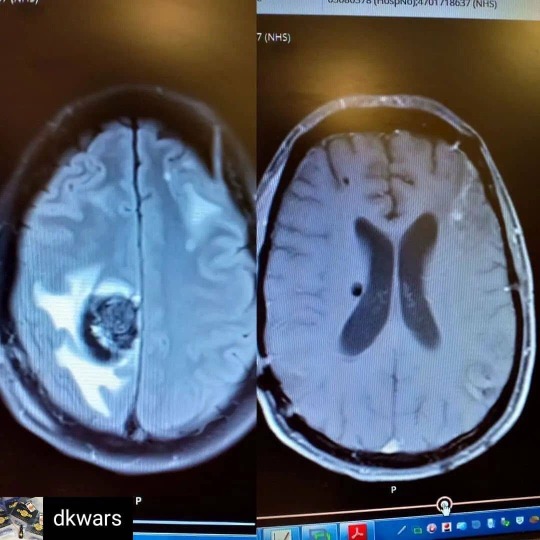
Reposted from @dkwars Posted @withregram • @dr_april_atl Posted @withregram • @ricksimpsonoilforcancer RSO TESTIMONY Holy mother of god we actually FUCKING DID IT!!!! CANNABIS -1 CANCER -0💚🙏🌱🙌😭😘 So today went really really well. 💥 After some stressful days building up to 'the big reveal' today.. me and nat nervously walked into our appointment to meet my doctor, only to find out the best news we could have even imagined. Back in December (first pic), I was told I probably wouldn't survive much longer and the meds I was being prescribed were destroying me hardcore. So I came off those by choice and chose a more natural path with REAL cannabis oil (not just CBD).. Months tick on and I feel like a completely new person. Alive and friggin kicking - but with no images to see if the oils were working.. no idea if I was healthy or not. That said, todays long awaited MRI results simply blew the doctors (and our) minds, he literally said it was the best day of his medical career!!! In short, I'm 'essentially' cancer free in less than a year and they want to write medical journals and all sorts! I'm not cleared just yet. And don't want to hype it up to much (the doc hyped it up for us) but it's more than obvious cannabis oil straight up works.. well. Clearing 12 tumours (the one in the picture is just 1 of many tumours) in less than a year. Being completely blessed with amazing, loving friends all around the world, incredible family and my absolutely incredible girlfriend Natalie being by my side has been the life line I needed to stay on track, reminded me why I needed to stay on track and I cannot thank all you amazing souls enough for being there! THANK YOU #fuckcancer🎀 #cannabiscures #plantaoverpills #cancersurvivor #cancerpatient #thcheals #cbdoil #cbdheals #medicalcannabis #medicinalcannabis #yeswecannabis #alternativetreatment #successstory #melanomaawareness #runfromthecure #stage4cancer #stage4cancersurvivor #stage4cancerthriver #rsoc #stage4cancerfighter #brca #stage4cancerwarrior #beatstage4cancer #lifeafterstage4cancer #braincancer #thrivingwithstage4cancer #wheelbarrowfullofstage4cancer #globalcbd https://www.instagram.com/p/CZKG_q9FE9w/?utm_medium=tumblr
#fuckcancer🎀#cannabiscures#plantaoverpills#cancersurvivor#cancerpatient#thcheals#cbdoil#cbdheals#medicalcannabis#medicinalcannabis#yeswecannabis#alternativetreatment#successstory#melanomaawareness#runfromthecure#stage4cancer#stage4cancersurvivor#stage4cancerthriver#rsoc#stage4cancerfighter#brca#stage4cancerwarrior#beatstage4cancer#lifeafterstage4cancer#braincancer#thrivingwithstage4cancer#wheelbarrowfullofstage4cancer#globalcbd
0 notes
Text
Redox 0x01
Introductory session
…and here we go! All excited. A first calendar entry to describe my attempt on ARM64 support in Redox OS. Specifically, looking into the Raspberry Pi2/3(B)/3+ (all of them having a Cortex-A53 ARMv8 64-bit microprocessor, although for all my experiments I am going to use the Raspberry Pi 3(B)).
Yesterday, I had my first meeting in Cambridge with @microcolonel! Very very inspiring, got many ideas and motivation. He reminded me that the first and most important thing I fell in love with Open Source is its people :)
Discussion Points
Everything started with a personal introduction, background and motivation reasons that we both participate in this project. It’s very important to note that we don’t want it to be a one-off thing but definitely the start of a longer support and experimentation with OS support and ARM.
Redox boot flow on AArch64
Some of the points discussed:
* boot * debug * MMU setup * TLS * syscalls `</pre> The current work by @microcolonel, is happening on the realms of `qemu-system-aarch64` platform. But what should I need to put my attention, when porting to the Rpi3? Here are some importants bits: <pre>`[ ] Typical AArch64 exception level transitions post reset: EL3 -> EL2 -> EL1 [x] Setting up a buildable u-boot (preferably the u-boot mainline) for RPi3 [ ] Setting up a BOOTP/TFTP server on the same subnet as the RPi3 [ ] Packaging the redox kernel binary as a (fake) Linux binary using u-boot's mkimage tool [ ] Obtaining an FDT blob for the RPi3 (Linux's DTB can be used for this). In hindsight, u-boot might be able to provide this too (u-boot's own generated ) [ ] Serving the packaged redox kernel binary as well as the FDT blob to u-boot via BOOT/TFTP [x] Statically expressing a suitable PL011 UART's physical base address within Redox as an initial debug console `</pre> Note: I’ve already completed (as shown) two important steps, which I am going to describe on my next blog post (to keep you excited ;-) **Challenges with recursive paging for AArch64** @microcolonel is very fond of recursive paging. He seems to succesfully to make it work on qemu and it seems that it may be possible in sillicon as well. This is for 48-bit Virtual Addresses with 4 levels of translation. As AArch64 has separate descriptors for page tables and pages which means that in order for recursive paging to work there must not be any disjoint bitfields in the two descriptor types. This is the case today but it is not clear if this will remain in the future. The problem is that if recursive paging doesn’t work on the physical implementation that may time much longer than expected to port for the RPi3. Another point, is that as opposed to x86_64, AArch6 has a separate translation scheme for user-space and kernel space. So while x86_64 has a single cr3 register containing the base address of the trnslation tables, AArch64 has two registers, ttbr_el0 for user-space and ttbr_el1 for the kernel. In this realm, there has been @microcolonel’s work to extend the paging schemes in Redox to cope with this. **TLS, Syscalls and Device Drivers** The Redox kernel’s reliance on Rust’s #[thread_local] attribute results in llvm generating references to the tpidr_el0 register. On AArch64 tpidr_el0 is supposed to contain the user-space TLS region’s base address. This is separate from tpidr_el1 which is supposted to contain the kernel-space TLS region’s base address. To fix this, @microcolonel has modified llvm such that the use of a ‘kernel’ code-model and an aarch64-unknown-redox target results in the emission og tpidr_el1. TLS support is underway at present. **Device drivers and FDT** For the device driver operation using fdt it’s very important to note the following: <pre>`* It will be important to create a registry of all the device drivers present * All device drivers will need to implement a trait that requires publishing of a device-tree compatible string property * As such, init code can then match the compatible string with the tree of nodes in the device tree in order to match drivers to their respective data elements in the tree `</pre> ** ** **Availability of @microcolonel’s code base** As he still expects his employer’s open source contribution approval there are still many steps to be done to port Redox OS. The structure of the code to be published was also discussed. At present @microcolonel’s work is a set of patches to the following repositories: <pre>`* Top level redox checkout (build glue etc) * Redox kernel submodule (core AArch64 support) * Redox syscall's submodule (AArch64 syscall support) * Redox's rust submodule (TLS support, redox toolchain triplet support) `</pre> Possible ways to manage the publishing of this code were also discussed. One way is to create AArch64 branches for all of the above and push them out to the redox github. This is TBD with **@jackpot51**. **Feature parity with x86_64** It’s very important to stay aligned with the current x86_64 port and for that reason the following work is important to be underways: <pre>`* Syscall implementation * Context switch support * kmain -> init invocation * Filesystem with apps * Framebuffer driver * Multi-core support * (...) (to be filled with a whole list of the current x86_64 features) `</pre> _Attaining feature parity would be the first concrete milestone for the AArch64 port as a whole._ **My next steps** As a result of the discussion and mentoring, the following steps were decided for the future: <pre>`[x] Get to a point where u-boot can be built from source and installed on the RPi3 [x] Figure out the UART base and verify that the UART's data register can be written to from the u-boot CLI (which should provoke an immediate appearance of characters on the CLI) [ ] Setup a flow using BOOTP/DHCP and u-boot that allows Redox kernels and DTBs to be sent to u-boot over ethernet [ ] Once microcolonel's code has been published, start by hacking in the UART base address and a DTB blob [ ] Aim to reach kstart with println output up and running. `</pre> **Next steps for @microcolonel** <pre>`[ ] Complete TLS support [ ] Get Board and CPU identification + display going via DTB probes [ ] Verify kstart entry on silicon. microcolonel means to use the Lemaker Hikey620 Linaro 96Board for this. It's a Cortex-A53 based board just like the RPi3. The idea is to quickly check if recursive paging on silicon is OK. This can make wizofe's like a lot rosier. :) [ ] Make the UART base address retrieval dynamic via DTB (as opposed to the static fixed address used at present which isn't portable) [ ] Get init invocation from kmain going [ ] Implement necessary device driver identification traits and registry [ ] Implement GIC and timer drivers (Red Flag for RPi3 here, as it has no implementation of GIC but rather a closed propietary approach) [ ] Focus on user-land bring-up `</pre> **Future work** If we could pick up the most important plan for the future of Redox that would be a roadmap! Some of the critical items that should be discussed: <pre>`* Suitable tests and Continuous integration (perhaps with Jenkins) * A pathway to run Linux applications under Redox. FreeBSD's linuxulator (system call translator) would be one way to do this. This would make complex applications such as firefox etc usable until native solutions become available in the longer term. * Self hosted development. Having redox bootable on a couple of popular laptops with a focus on featurefulness will go a great way in terms of perception. System76 dual boot with Pop_OS! ? ;) * A strategy to support hardware assisted virtualization.
Thanks
Thanks for reading! Hope to see you next time here. For any questions feel free to email me: code -@- wizofe dot uk. Many many insights are taken from @microcolonel’s very detailed summary; The following part of the blog is my own experimentation and exploration on the discussed matters!
2 notes
·
View notes
Photo

🏁Details Matter LLC🏁 ❤️Auto Detailing & Surface Protection❤️ 💥Ceramic Coating Specialist💥 💙Brevard County💙 🌴Melbourne Florida🌴 #fordst #fordlove #fordowners #rsmk #fordtuning #stnation #performanceford #detailsmatterllc #fordfocusclub #tuning #fordgt #fordfiestast #fordnation #cars #boost #fordfiesta #rsoc #cosworth #instacars #proalloymotorsport #eleanor #devildevelopments #fastfordmagazine #rsownersclub #united #hothatchsociety #z #sccperformance #airtecmotorsport #awd (at Details Matter LLC.) https://www.instagram.com/p/B8vp8MihJjP/?igshid=k1i8wfhb0ivw
#fordst#fordlove#fordowners#rsmk#fordtuning#stnation#performanceford#detailsmatterllc#fordfocusclub#tuning#fordgt#fordfiestast#fordnation#cars#boost#fordfiesta#rsoc#cosworth#instacars#proalloymotorsport#eleanor#devildevelopments#fastfordmagazine#rsownersclub#united#hothatchsociety#z#sccperformance#airtecmotorsport#awd
0 notes
Photo

#VIBESS @houseofvibess
24 notes
·
View notes
Text
Pinned Post

BYF
THIS BLOG IS 18+ - No minors. I tag sparingly for nsfw and dark content so viewer discretion advised and all that.
FUB FREE POLICY - It's your browsing experience man. If the content on here bothers you block me!!!! I do not care.
ABOUT
TWITTER | TOYHOUSE hii im ram or R, a uni grad treating my characters cruelly to cope with employment hell 😀😀😀. i really will just post anything man dont have high expectations 👤: black (🇱🇷✌🏾) / gnc lesbo (any pronouns) / self IDed furry and fujoshi from back when it was still cringe to do that. To obtain any additional info about me you must find my 8 pages
TAGS
#rsocs - my OC tag #saucedart - my art tag #skunkposting - misc posts by me
[will be updated as i go along]
0 notes
Photo

VIBE$$ #VIBESS
#vibess#ig: officialvibess snap: cohenvibess Vibess VIBE$$#Cohen#rsoc#real side chicks#charlotte#brixx
1 note
·
View note
Photo

Just realized I don’t really have an official headshot of Snazz to use for stuff so I whipped this up and tried a new coloring style while I was at it %D
42 notes
·
View notes
Photo

Family of Five Pose! RSOC Pose Pack #2
Hey Everyone! I made this pose for Michael’s Graduation because I couldn’t find a two teen, one child family pose, and really wanted a full family shot! Fixed it up a little since then so now here it is for you all to use!
It’s 1 group pose consisting of:
- 1 Adult Male - 1 Adult Female - 1 Teen Boy - 1 Teen Girl - 1 Child
Would love to see you guys use it!
Download: SFS
@ts4-poses
246 notes
·
View notes
Photo

#blackfridayspecial #alldayfriday #allfridayorders @therimshopofcharlotte #nc #charlotte #northcarolina #minthill #monroe #indiantrail #harrisburg #webeendointhat #bestincity #lakenorman #concord #panthers #rimshop #rsoc #tinted #tint #wrapped #980 #704 #wheel #tire #rim #7047907467 #8033703073 (at The Rim Shop of Charlotte)
#rsoc#7047907467#tinted#northcarolina#harrisburg#rimshop#panthers#blackfridayspecial#minthill#indiantrail#lakenorman#980#704#monroe#tire#wrapped#tint#allfridayorders#nc#rim#alldayfriday#8033703073#bestincity#wheel#charlotte#webeendointhat#concord
0 notes
Photo

Birmingham RSOC merchandise #rsownersclub #rsoc #snapback #hoodys #merchandise #hat #clothing #apparel #yupoong #custom #embroidery #customituk
#apparel#merchandise#embroidery#custom#rsownersclub#clothing#rsoc#hat#customituk#yupoong#snapback#hoodys
0 notes
Video
Just when my friends & followers thought I play ALL THE TIME😒😏 #RSOC 😂😂😂😂😂😂👍💯Think it's a game, it's on & poppin 💥💥💥💥
0 notes
Photo

#VIBESS @houseofvibess
#vibess#house of vibess#vibe$$ lifestyle#real side chicks of charlotte#rsoc#teambrixx#brixx#cohenvibess
5 notes
·
View notes