#protection and security services
Explore tagged Tumblr posts
Text

Benefits of Protection and Security Services
Security is essential in protecting both individuals and organizations. HRS Security Services provides expert protection and security services, offering consumers a greater sense of safety and peace of mind with trained professionals monitoring and securing their facilities. Must Visit :
#protection and security services#security company#security agency singapore#best security company in singapore
0 notes
Text
IRS Lawyer Ousted as Elon Musk’s DOGE Plans Even More Cuts | The New Republic
#department of government efficiency#elon musk#donald trump#trump administration#irscompliance#irs audit#irs#internal revenue service#federal government#data privacy#data protection#cybersecurity#cyber security#civil rights#social justice#us politics
14 notes
·
View notes
Note
Does Pakin likes Graph's friends?
No, but Graph is great at surrounding himself with people Pakin can't actually be too mean to.
Graph's best friend is Chanchao, a girl who is obsessed with BL and gives Graph terrible advice to try to seduce Pakin. As far as their classmates know, Chanchao is Graph's girlfriend, a rumor they allow to exist because it keeps people from hitting on either of them. A rumor that absolutely puts Pakin on edge the way Ple does to Payu.
But Chanchao's brother is Shin, boyfriend to Pakin's best racer, Oat. Even though Shin and Pakin hate each other, unless he wants to piss off his top earner, he has to keep his mouth shut.
Graph makes a new friend during Try Me: Nith. Nith is a senior who is a loner, pretty quiet, but he takes notice of Graph and tries to be nice to him. Nith doesn't have many friends, and he feels bad for the boy, so he'll take Graph out bowling or to have fun. It seems like Nith is in love with Graph, which pisses Pakin off, but Nith actually has a crush on Chanchao.
Nith, incidentally, is the half-brother of Pakin's best frenemy, Sin. The same Sin who supplies the drugs that make Pakin and Graph's first time so brutal (Sin also has sex with Win fairly often when Win is on his self-sabotage spirals, so Pakin hates Sin for that). Sin is the wealthiest man in Thailand and absolutely loves his little half-brother.
Later on, when Pakin is scared that Graph is isolating himself and is too lonely while Pakin is busy with work, he brings Rain and Sky to be friends for Graph. Pakin trusts Payu and Prapai wholly and completely, so by extension he trusts their boys.
And whatever trouble those three get into together, Payu and Prapai are wrapped around their boyfriends' little fingers and Pakin can hardly go after his favorite racer or his platonic soulmate (Payu, mechanic of his heart).
#you don't get a lot of Pakin's dynamic with Prapai; but Prapai's family are important business partners#and Pakin genuinely likes any person who shares his interest in bikes and engines#so he and Prapai are closer to equal footing and seem to really get along#and while Payu's role in Pakin's life is more services rendered with maintenance and mechanical work on bikes#Pakin will send CHAI to Payu if need be#Chai isn't just his chief of security- he was Pakin's personal bodyguard when Pakin was a teenager#He is also married to Pakin's cousin- who was raised as if he was a brother#So Chai is very precious to Pakin and usually exclusively for Pakin or Graph's protection#so that he sent Chai to save Rain and Sky says a lot about the regard he holds Payu and Prapai in#Also just to always point out#Prapai makes a deal to have Gun and Petch executed and Pakin NEVER calls in those chips#he never holds Prapai to it#which also says a lot about how much he trusts and believes in him#And by the end of the LITA special novel#Graph has babies he and Pakin adopted together and Rain and Sky are kind of embracing their Uncle Modes#ask#pakin#chanchai#nith#rain#sky#love in the air#lita#love storm#love sky#lita special novel
5 notes
·
View notes
Text
Secure Lifetime Legacy

Secure Lifetime Legacy stands as a trusted ally for clients seeking proactive solutions to protect what matters most — their retirement, income, health, loved ones, assets, and legacy. We specialize in addressing "The Problem Wheel"—a collection of the most pressing economic and personal uncertainties—so that our clients don't have to rely on the government, banks, corporations, or employers to secure their future.
We offer personalized, transparent service backed by extensive knowledge of retirement laws, tax codes, and healthcare policies. Our mission is to empower you with a proactive plan that ensures stability and confidence in your financial future, regardless of economic conditions.
#Retirement Planning#Income Protection#Financial Services#Financial Independence#Healthcare Planning#Medicare#ACA#Social Security#IRA#401k#403b#TSP#Asset Protection#Legacy Planning#Proactive Financial Strategies#Financial Literacy#Economic Resilience#Generational Wealth#Disability Protection#Tax-Efficient Strategies#Secure Retirement#Problem Wheel#Employer Retirement Plans
2 notes
·
View notes
Text
How to Protect Yourself from Personal Loan Phishing Scams

In today’s digital world, personal loans have become more accessible, allowing borrowers to apply online and receive funds quickly. However, this convenience has also led to a rise in phishing scams, where fraudsters attempt to steal your personal and financial information by posing as legitimate lenders. These scams can result in identity theft, financial loss, and fraudulent loan applications in your name.
If you’re planning to apply for a personal loan, it is essential to understand how phishing scams work, the warning signs to look for, and the best ways to protect yourself.
1. What Are Personal Loan Phishing Scams?
A phishing scam is a fraudulent attempt to trick individuals into providing sensitive information such as bank details, Aadhaar number, PAN card, OTPs, or login credentials. Scammers typically impersonate banks, NBFCs, or online lending platforms and contact borrowers via emails, phone calls, SMS, or fake websites.
Once they obtain your information, they can:
Steal money from your bank account
Take a loan in your name
Misuse your identity for financial fraud
Access and sell your personal data on the dark web
2. Common Types of Personal Loan Phishing Scams
2.1 Fake Loan Approval Emails & SMS
Fraudsters send emails or SMS messages claiming that your loan has been pre-approved or that you qualify for a low-interest personal loan. These messages often contain links leading to fake lender websites designed to steal your personal information.
2.2 Fake Loan Websites & Apps
Scammers create websites and mobile apps that look like real financial institutions. They trick users into entering personal and banking details, which are then used for fraudulent activities.
2.3 Fraudulent Customer Service Calls
You may receive a phone call from a scammer pretending to be a bank representative. They claim you must provide your OTP, Aadhaar, PAN, or bank details to complete your loan application. Once you share these details, scammers can withdraw money or take loans in your name.
2.4 Loan Processing Fee Scams
Fraudsters promise quick loan disbursal with no documentation but demand advance processing fees or a loan insurance fee. Once the fee is paid, the scammer disappears, and no loan is disbursed.
2.5 Social Media Loan Scams
Some scammers advertise fake loans on Facebook, Instagram, or WhatsApp and ask potential borrowers to contact them privately. Once engaged, they request confidential details, leading to identity theft.
3. Red Flags to Identify Loan Phishing Scams
3.1 Offers That Sound Too Good to Be True
If you receive an offer promising guaranteed loan approval with no credit check, zero documentation, or extremely low-interest rates, it’s likely a scam.
3.2 Unsolicited Loan Messages
Legitimate lenders do not send random SMS, WhatsApp messages, or emails offering personal loans. Be cautious if you receive messages from unknown numbers or email addresses.
3.3 Fake Loan Websites
Before applying for a loan online, always verify the website’s domain name. Scammers often create fake websites with slightly modified spellings of real lenders to trick borrowers.
3.4 Requests for Upfront Payments
No genuine lender will ask for advance processing fees before loan approval. If a lender insists on upfront payments via UPI, Paytm, or Google Pay, it’s a scam.
3.5 Pressure to Act Immediately
Scammers create urgency by saying things like, "Limited offer – Apply now!" or "Your loan will be canceled if you don’t act fast." A real lender will give you time to review the terms.
3.6 Request for Personal Information Over the Phone
A legitimate bank or NBFC will never ask you for OTPs, passwords, or CVVs over the phone. If someone does, hang up immediately.
4. How to Protect Yourself from Loan Phishing Scams
4.1 Apply for Loans Only from Trusted Lenders
Always apply for a personal loan through registered banks, NBFCs, or reputed online lenders. Here are some safe options:
🔗 IDFC First Bank Personal Loan 🔗 Bajaj Finserv Personal Loan 🔗 Tata Capital Personal Loan 🔗 Axis Finance Personal Loan 🔗 Axis Bank Personal Loan 🔗 InCred Personal Loan
4.2 Verify the Lender’s Website
Check if the website URL starts with "https://" (secure site).
Look for official lender details on the RBI website or lender’s official website.
Avoid websites with poor design, spelling errors, or unusual domain names (e.g., "axisbankloans.xyz" instead of "axisbank.com").
4.3 Never Click on Suspicious Links
Do not click on links in unsolicited emails or messages claiming to be from a bank or NBFC. Instead, visit the official website by typing the URL manually.
4.4 Avoid Sharing Personal Information Online
Scammers may ask for your Aadhaar, PAN, or bank details via email, phone, or WhatsApp. Never share sensitive information with unknown sources.
4.5 Enable Two-Factor Authentication (2FA)
Use 2FA on your banking and email accounts to protect against unauthorized access. This adds an extra layer of security if your password is compromised.
4.6 Check Reviews & Ratings Before Downloading Loan Apps
Before installing a loan app, check:
App permissions (Avoid apps that ask for access to contacts, photos, and messages).
Reviews and ratings on Google Play or App Store.
If the app is registered with an RBI-approved lender.
4.7 Monitor Your Bank & Credit Report Regularly
Check your credit report and bank statements for unauthorized loan applications or suspicious transactions. If you spot any fraudulent activity, report it immediately.
5. What to Do If You Are a Victim of Loan Phishing?
If you have fallen victim to a loan phishing scam, take these steps:
1️⃣ Contact Your Bank Immediately – Report any unauthorized transactions and request to block your account if necessary. 2️⃣ Change Your Passwords – Update your internet banking, email, and loan account passwords immediately. 3️⃣ File a Cyber Crime Complaint – Report the fraud to the Cyber Crime Portal (www.cybercrime.gov.in) or call the National Cyber Crime Helpline (1930). 4️⃣ Report to RBI & Consumer Forum – If you have been tricked into a fake loan scheme, report it to the RBI and National Consumer Helpline (1800-11-4000). 5️⃣ Monitor Your Credit Report – Check for unauthorized loans taken in your name and dispute them with credit bureaus like CIBIL and Experian.
Stay Alert & Borrow Safely
Personal loan phishing scams are on the rise, but you can stay protected by being vigilant. Always verify loan offers, apply only through trusted lenders, and avoid clicking on suspicious links.
For safe and secure personal loan options, apply here: 👉 Compare & Apply for a Personal Loan
By staying cautious and informed, you can protect yourself from loan fraud and ensure a safe borrowing experience.
#nbfc personal loan#bank#loan services#personal loans#fincrif#personal loan#personal laon#loan apps#personal loan online#finance#fincrif india#Personal loan phishing scams#Loan fraud protection#How to avoid loan scams#Safe personal loan application#Phishing scams in personal loans#Fake loan offers#Online loan scams#Fraudulent loan websites#Personal loan safety tips#How to identify loan scams#Signs of a loan scam#Avoiding personal loan fraud#Phishing emails from loan providers#Loan application fraud prevention#How scammers trick loan applicants#Secure loan application process#Fake personal loan SMS and calls#Online loan phishing protection#Tips to protect against loan fraud
5 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
2 notes
·
View notes
Text
Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
In today’s rapidly evolving digital landscape, securing your business’s data and IT infrastructure is more important than ever. With cyber threats growing more sophisticated, partnering with a professional IT security services company is essential for protecting your business. This article explores the key services provided by an IT security company, why businesses need them, and how a reliable provider like Gronteq can safeguard your organization from cyber risks.

Comprehensive IT Security Services: Why You Need a Trusted IT Security Company
As businesses become more reliant on digital tools and systems, the threat of cyberattacks has grown significantly. Whether you’re a small startup or a large corporation, protecting your sensitive data and IT infrastructure is no longer optional—it’s a necessity. This is where a professional IT security services company comes in. Their role is to safeguard your business from cyber threats, protect your data, and ensure your systems are running smoothly and securely.
In this article, we will discuss the various IT security services offered by reputable providers, why businesses need these services, and how partnering with a trusted IT security company like Gronteq can help you maintain a secure and resilient digital environment.
1. Understanding the Importance of IT Security
The growing frequency and sophistication of cyber threats are major concerns for businesses worldwide. Hackers, cybercriminals, and malicious insiders are always on the lookout for vulnerabilities in your IT infrastructure. From phishing attacks and data breaches to ransomware and DDoS attacks, the risks are constantly evolving.
Without the right IT security services, businesses risk losing valuable data, experiencing system downtime, and suffering reputational damage. Moreover, data protection regulations, such as GDPR and HIPAA, require businesses to implement robust security measures to avoid penalties and fines.
This is where an experienced IT security company can help. By working with a trusted provider, businesses can implement proactive security strategies that prevent attacks before they occur, ensuring a safe, compliant, and resilient online environment.
2. Key IT Security Services Offered by Companies
The scope of IT security services provided by security companies varies, but some common services include:
a. Network Security
Network security involves implementing measures to protect your internal network from unauthorized access, attacks, and data breaches. This includes firewalls, intrusion detection systems (IDS), intrusion prevention systems (IPS), and secure VPNs. With strong network security, your business can defend against external and internal threats.
b. Data Protection and Encryption
Protecting sensitive data is critical to prevent unauthorized access or leaks. IT security agencies provide encryption services to ensure that data is stored and transmitted securely. By implementing data loss prevention (DLP) tools, businesses can safeguard intellectual property, customer information, and financial data from cybercriminals.
c. Vulnerability Management
Vulnerability management involves identifying and addressing weaknesses in your systems before they can be exploited. This includes regular security assessments, penetration testing, and patch management. A thorough vulnerability management program helps keep your business ahead of potential threats.
d. Endpoint Security
With more employees working remotely, endpoint security has become a top priority. This includes securing devices like laptops, smartphones, and tablets that access your company’s network. Endpoint security services protect these devices from malware, phishing attacks, and unauthorized access, ensuring the integrity of your entire IT infrastructure.
e. Incident Response and Disaster Recovery
In the event of a cyberattack or data breach, having a well-defined incident response plan is essential. IT security services companies offer incident response and disaster recovery services to help businesses quickly recover from cyberattacks. This includes identifying the source of the breach, mitigating damage, and restoring normal operations.
f. Managed Security Services
For businesses that lack an in-house security team, managed security services (MSS) are an excellent solution. These services provide 24/7 monitoring, threat intelligence, and proactive response to security incidents. MSS ensures continuous protection for your business without the need for an internal team.
3. Why Your Business Needs IT Security Services
The question remains: why is it so critical for your business to partner with a reliable IT security company? Here are the main reasons:
a. Proactive Threat Prevention
A trusted IT security services company works proactively to protect your business. By continuously monitoring your systems, implementing security protocols, and conducting regular security audits, a professional provider helps to prevent potential attacks before they happen.
b. Protecting Business Reputation
A cyberattack can lead to loss of trust from customers, partners, and stakeholders. With IT security services, your company can protect its reputation and avoid the costly consequences of a data breach.
c. Legal and Regulatory Compliance
Cybersecurity isn’t just about protecting your data—it’s also about complying with industry regulations. An IT security company helps ensure that your business complies with relevant laws like GDPR, HIPAA, and PCI-DSS, avoiding fines and penalties.
d. Cost Savings in the Long Run
While the upfront costs of IT security services may seem significant, they can actually save your business money in the long run. By preventing attacks, reducing downtime, and avoiding the cost of data breaches, investing in security is a smart financial decision.
e. Expertise and Knowledge
Cybersecurity is a complex field that requires specialized knowledge and expertise. A reputable IT security company brings in-depth understanding of the latest threats, tools, and strategies to ensure your business is always protected.
4. How Gronteq Can Help Protect Your Business
At Gronteq, we specialize in providing comprehensive IT security services to businesses of all sizes. Our team of cybersecurity professionals is dedicated to safeguarding your business from cyber threats, ensuring compliance with regulations, and helping you maintain a secure and resilient IT environment.
We offer customized IT security solutions, including network security, data protection, vulnerability management, endpoint security, and disaster recovery. With our proactive approach to cybersecurity and 24/7 monitoring, we ensure your business is always one step ahead of potential threats.
5. Contact Gronteq for Your IT Security Needs
If you’re ready to take your business’s security to the next level, Gronteq is here to help. Our IT security experts are ready to provide tailored solutions that meet your unique needs. Contact us today to learn more about how we can protect your business from cyber threats and ensure your IT systems are secure, compliant, and optimized for success.
Conclusion The digital landscape is constantly evolving, and so are the risks that come with it. Partnering with a professional IT security services company like Gronteq ensures your business is well-protected, compliant, and prepared for any challenges that arise. From proactive threat prevention to disaster recovery, our team provides end-to-end security solutions to keep your business safe.
Contact Gronteq today to learn how our IT security services can protect your organization and give you peace of mind knowing your business is secure.
#IT security#cybersecurity#IT services#data protection#network security#IT security company#IT consulting#digital security#cyber threats#business security
2 notes
·
View notes
Text
High Risk Payment Processing
High-risk businesses often face challenges in obtaining secure payment solutions. WebPays provides high-risk payment processing with advanced fraud protection, chargeback management, multi-currency support, and reliable transaction handling. Contact us today to get started.

#High-Risk Payment Gateway#Secure Payment Processing#Fraud Protection Services#Chargeback Management#Multi-Currency Payment Support#Global Payment Solutions#High-Risk Merchant Account
1 note
·
View note
Text
Elevate Client Services with Excel: Expert Tips for Financial Consultants by Grayson Garelick

Financial consultants operate in a dynamic environment where precision, efficiency, and client satisfaction are paramount. Excel, as a versatile tool, offers an array of features that can significantly enhance the services provided by financial consultants. Grayson Garelick, an accomplished financial analyst and consultant, shares invaluable Excel tips to help financial consultants elevate their client services and add tangible value.
The Role of Excel in Financial Consulting
Excel serves as the backbone of financial consulting, enabling consultants to analyze data, create models, and generate insights that drive informed decision-making. As the demands of clients become increasingly complex, mastering Excel becomes essential for financial consultants aiming to deliver exceptional services.
1. Customize Excel Templates
One of the most effective ways to streamline workflows and improve efficiency is by creating customized Excel templates tailored to specific client needs. Grayson suggests developing templates for budgeting, forecasting, and financial reporting that can be easily adapted for different clients, saving time and ensuring consistency.
2. Utilize PivotTables for Data Analysis
PivotTables are powerful tools in Excel that allow financial consultants to analyze large datasets and extract meaningful insights quickly. Grayson emphasizes the importance of mastering PivotTables for segmenting data, identifying trends, and presenting information in a clear and concise manner to clients.
3. Implement Conditional Formatting
Conditional formatting is a valuable feature in Excel that allows consultants to highlight important information and identify outliers effortlessly. By setting up conditional formatting rules, consultants can draw attention to key metrics, discrepancies, or trends, facilitating easier interpretation of data by clients.
4. Leverage Excel Add-ins
Excel offers a variety of add-ins that extend its functionality and provide additional features tailored to financial analysis and reporting. Grayson recommends exploring add-ins such as Power Query, Power Pivot, and Solver to enhance data manipulation, modeling, and optimization capabilities.
5. Automate Repetitive Tasks with Macros
Macros enable financial consultants to automate repetitive tasks and streamline workflows, saving valuable time and reducing the risk of errors. Grayson advises recording and editing macros to automate tasks such as data entry, formatting, and report generation, allowing consultants to focus on value-added activities.
6. Master Advanced Formulas and Functions
Excel's extensive library of formulas and functions offers endless possibilities for financial analysis and modeling. Grayson suggests mastering advanced formulas such as VLOOKUP, INDEX-MATCH, and array formulas to perform complex calculations, manipulate data, and create sophisticated models tailored to client needs.
7. Visualize Data with Charts and Graphs
Visualizing data is essential for conveying complex information in an easily digestible format. Excel offers a variety of chart types and customization options that enable consultants to create compelling visuals that resonate with clients. Grayson recommends experimenting with different chart styles to find the most effective way to present data and insights.
8. Collaborate and Share Workbooks Online
Excel's collaboration features enable financial consultants to work seamlessly with clients, colleagues, and stakeholders in real-time. Grayson highlights the benefits of sharing workbooks via OneDrive or SharePoint, allowing multiple users to collaborate on the same document, track changes, and maintain version control.
9. Protect Sensitive Data with Security Features
Data security is a top priority for financial consultants handling sensitive client information. Excel's built-in security features, such as password protection and encryption, help safeguard confidential data and ensure compliance with regulatory requirements. Grayson advises implementing security protocols to protect client data and maintain trust.
10. Stay Updated with Excel Training and Certification
Excel is a constantly evolving tool, with new features and updates released regularly. Grayson stresses the importance of staying updated with the latest Excel training and certification programs to enhance skills, explore new capabilities, and maintain proficiency in Excel's ever-changing landscape.
Elevating Client Services with Excel Mastery
Excel serves as a catalyst for innovation and excellence in financial consulting, empowering consultants to deliver exceptional services that add tangible value to clients. By implementing Grayson Garelick Excel tips, financial consultants can streamline workflows, enhance data analysis capabilities, and foster collaboration, ultimately driving client satisfaction and success. As financial consulting continues to evolve, mastering Excel remains a cornerstone of excellence, enabling consultants to thrive in a competitive landscape and exceed client expectations.
#Financial Consulting#grayson garelick#Customize Excel Templates#Utilize PivotTables#Implement Conditional Formatting#Leverage Excel Add-ins#Automate Repetitive Tasks with Macros#Advanced Formulas and Functions#Visualize Data with Charts and Graphs#Collaborate and Share Workbooks#Protect Sensitive Data with Security#Stay Updated with Excel Training#Elevating Client Services with Excel
3 notes
·
View notes
Text
My family are major golf freaks (can you tell we’re white) and I remmebr the day of That One Acronym tournament on the last hole like four people jumped onto the course and threw pigment on the green in a “protest for the ecosystem” and they got fucking TACKLED by security it was so funny



cant remember for the life of me if i've uploaded this before
#secret service?#nah#GOLF SECURITY#they fr did a better job at protecting the course than the SS did at protecting the orange man that one time
5K notes
·
View notes
Text
If anyone has taken their eyes off what's happening to federal workers in the US right now, here's some highlights that we're hearing from our comrades across the government who have not yet been fired:
In one building (hosting multiple agencies), the locks on the bathroom were changed so employees no longer have any access to a bathroom during the workday. People are peeing in trash cans.
Elsewhere, multiple agencies have reported that hand soap is no longer being supplied in the bathrooms.
Toilet paper supplies have not been adjusted to meet the needs of a vastly increased number of in-office employees.
Employee-owned coffee and coffee makers have been stolen or thrown away without notice (it was already illegal for taxpayer dollars to be spent on supplying federal employees with amenities like coffee, so many offices have coffee supplied by pooled employee funds).
Meanwhile, many offices don't even have potable drinking water (recurrent legionella outbreaks), so employees have to bring their own water from home.
Despite an explosion in the number of workers in offices, cleaning budgets have been slashed and many offices are not being cleaned regularly enough to remain sanitary. Pests like roaches and rats are a problem.
The firings continue, legal and illegal. Entire programs are being cut. Managers have no idea when they might lose staff. Employees are getting fired at 6pm on a weekend or finding out when they're unable to log into their computer or when they receive a shipping label in the mail to return their equipment.
Through all of this, the DOGE employees in federal workplaces are enjoying incredible and expensive luxury: AI-powered sleep pods, entire dormitories so they can live in federal buildings, nurseries for their children on site, free food and beverages, laundry services, and who knows what else. They have special security to restrict access to their areas of the buildings, including armed guards.
And I'm not just saying this to lament how bad it is for federal workers. I'm saying this because, as workers are reporting this to one another, the response is, inevitably: "This is illegal." "Yes, but who would I report it to? OPM? They're a DOGE puppet. OSHA? They've cut OSHA. The Inspectors General? Cut. The NLRB? Cut. My union? No longer recognized."
There is no one left to enforce these laws, so taking away access to basic sanitation is now effectively legal. They are doing this to federal workers, who historically have been some of the best-protected workers in the country. They are doing this specifically because it demonstrates to the public sector that it is now legal to do these things to their own workers.
17K notes
·
View notes
Text
Kriptone Data Loss Protection: The Ultimate Smart Security Solution

In today’s digital world, data is more valuable than ever—it powers business growth but is also at constant risk. It can be lost or stolen through mistakes, system failures, or internal leaks. Like gold needs to be stored safely, your data needs strong protection. That’s where Kriptone Data Loss Protection (DLP) comes in—a smart, flexible solution designed to safeguard your most valuable digital assets.
What is Data Loss Protection (DLP)?
(DLP) keeps your sensitive information safe from leaks, misuse, or unauthorized access—ensuring it stays where it belongs.
Exploring the Difference Between Data Loss and Leakage
Data loss is permanent, like when a hard drive fails and erases customer records. Data leakage, however, is sneaky—it’s when sensitive info leaks through weak points like unapproved apps or human mistakes. Loss is harsh, but leakage is slow and often more harmful over time. Kriptone’s DLP technology prevents both, stopping leaks before they spread and protecting against data loss.
The Top Threats to Your Data Today
Data threats can come from everywhere—from cybercriminals to well-meaning employees. Let’s dive into the major risks that can impact your information.
External Attacks: Hackers, Malware, and Phishing
Cybercriminals are now part of organized groups using advanced tools like AI-driven malware and phishing attacks. Their goal is to steal and profit from your data. Kriptone’s DLP uses threat intelligence to detect and stop these attacks before they can steal your information.
The Business Impact of Data Loss
A single data breach can cause major damage, harming systems, reputations, and even leading to legal issues. Data loss isn’t only a technical issue; it’s a crisis that affects the entire business.
From Revenue to Reputation: The Fallout of a Breach
When data is lost, trust is shattered clients back off, investors worry, and competitors take advantage. Similarly Extra costs from legal actions, fines, and system breaks make the problem worse. Kriptone helps businesses avoid this by providing constant, smart protection that’s always on and defending.
Key Features of a Strong DLP Strategy
Not all DLP tools are the same. A strong defence needs to be smart, proactive, and adaptable—just like the threats it’s meant to stop.
Real-Time Monitoring and Alerts: Eyes Everywhere
Kriptone monitors data 24/7 across endpoints, networks, and the cloud. If something unusual happens, it quickly locks down files, alerts security teams, and tracks the breach.
Types of DLP Solutions Explained
Choosing the right DLP depends on where your data is stored, how it moves, and who needs access. Kriptone offers solutions designed for today’s flexible, decentralized workspaces.
Endpoint DLP: Securing Devices at the Edge
Endpoint DLP protects data on employee devices. Kriptone’s solution blocks unauthorized copying, printing, or transferring of data, whether the device is online or offline.
The Future of Data Loss Protection
Cyber threats move fast, and DLP must keep up. Kriptone is shaping the future of data protection with Smart Data Security automation and predictive analytics.
AI and Machine Learning in Next-Gen DLP
Kriptone uses Smart Data Security AI to stop threats before they start. However, It learns from past events, adapts to user behavior, and spots unusual activity in real-time, creating a DLP system that’s not just reactive, but smart and adaptive.
Conclusion
In conclusion,Data loss will happen eventually, but proactive defense can limit the damage. Kriptone Data Loss Protection isn’t just a tool—it’s a promise to defend your valuable data with intelligence and precision. Security should be relentless, not reactive. Whether you’re a global enterprise or a startup, Kriptone helps you protect your most critical asset before it’s too late. In addition, Today, protecting your data smartly is essential, not a choice.
#it security services#data loss prevention solutions#endpoint security#It cyber security services#data loss protection
0 notes
Text
What Are the Common Fake Personal Loan Apps?
The rise of digital lending has made it easier than ever to apply for a personal loan. However, with this convenience comes an increased risk of fraud. Fake personal loan apps have become a major concern, preying on unsuspecting borrowers with promises of quick approval and low interest rates. These fraudulent apps often steal personal data, demand upfront payments, and leave victims in financial distress.
Understanding how to identify fake personal loan apps and protect yourself from scams is essential for ensuring a safe borrowing experience. This article will highlight the risks associated with fake loan apps, common red flags to watch out for, and tips to stay secure when applying for a personal loan.
The Rise of Fake Personal Loan Apps
The increasing popularity of digital lending has led to a surge in fake personal loan apps that exploit borrowers. Scammers create these apps to collect sensitive information, demand fraudulent fees, or even misuse the borrower’s identity for illegal activities. Many victims only realize they have been scammed after their money is stolen or their credit profile is misused.
How Fake Loan Apps Operate
Fake personal loan apps typically follow a deceptive pattern to lure borrowers into their traps. Here’s how they operate:
Attractive Loan Offers – Fraudulent apps promote personal loans with minimal documentation, low interest rates, and instant approval, enticing users to download them.
Fake Registration Process – Borrowers are required to enter personal details, including bank account numbers, identity proofs, and credit card information.
Upfront Fees – Scammers demand processing fees, security deposits, or verification charges before disbursing the loan.
Unauthorized Access to Data – These apps request unnecessary permissions, such as access to contacts, messages, and call logs, which scammers misuse.
No Actual Loan Disbursement – Once the borrower pays the upfront fees, the scammers disappear without providing the loan.
Common Red Flags of Fake Personal Loan Apps
Recognizing the warning signs of a fraudulent loan app can save you from financial loss. Here are key red flags to watch for:
1. No Registration with Financial Authorities
Legitimate lenders are registered with regulatory bodies such as the Reserve Bank of India (RBI), Federal Trade Commission (FTC), or other financial authorities. If an app does not have proper regulatory approval, it is likely a scam.
2. Demand for Upfront Fees
Genuine lenders do not ask for upfront payments before loan approval. If an app requests a processing fee, security deposit, or verification charge before disbursing the loan, it’s a major red flag.
3. Poorly Designed and Unprofessional Interface
Fake personal loan apps often have poor user interfaces, multiple grammatical errors, and lack proper customer support. A lack of professionalism in app design and communication indicates fraudulent intent.
4. Excessive Permission Requests
Fraudulent apps demand access to contacts, messages, location, and even the camera, which is unnecessary for a personal loan application. These permissions are used to steal data or blackmail victims.
5. No Physical Address or Customer Support
Legitimate financial institutions provide a physical address and reliable customer support channels. Fake loan apps usually lack transparency and offer no proper means of contact.
6. High-Pressure Tactics
Scammers often pressure borrowers to act quickly, using phrases like “limited time offer” or “instant approval guaranteed.” Genuine lenders follow a structured verification process and do not rush applicants.
Notorious Fake Personal Loan Apps
Several fraudulent personal loan apps have been flagged by financial authorities. While these scams frequently change names, some of the most notorious ones include:
Cash Advance Pro – Known for demanding high upfront fees and disappearing after collecting money.
Quick Loan Now – Requests excessive permissions and misuses borrower data.
Easy Loan Fast – Promises instant approvals but requires security deposits that are never refunded.
Swift Cash Lenders – Lures victims with fake customer reviews and unrealistic loan offers.
Loan Hub Pro – Uses phishing techniques to steal banking credentials.
How to Protect Yourself from Fake Personal Loan Apps
To avoid falling victim to a fraudulent personal loan app, follow these security measures:
1. Download Apps from Official Sources
Only download loan apps from reputable platforms like Google Play Store or Apple App Store. Avoid downloading APK files from unknown sources, as they may contain malware.
2. Verify Lender Credentials
Before applying for a personal loan, check whether the lender is registered with financial authorities. Visit their official website and read customer reviews.
3. Avoid Providing Unnecessary Permissions
Do not grant access to contacts, messages, or other sensitive data unless it is essential for the loan application. Be cautious of apps that request excessive permissions.
4. Read User Reviews and Ratings
Genuine loan apps have positive reviews from verified customers. Look for red flags in user comments, such as complaints about fraud, high fees, or data theft.
5. Check the Privacy Policy
Legitimate lenders provide a clear privacy policy detailing how your data will be used. If the app lacks transparency, avoid using it.
6. Use Strong Security Measures
Enable two-factor authentication (2FA) on your bank and financial accounts to prevent unauthorized access. Keep your device protected with updated security software.
What to Do If You Fall Victim to a Fake Loan App
If you suspect that you have been scammed by a fake personal loan app, take immediate action:
1. Report the Scam to Authorities
Notify your country’s financial regulatory body, such as the FTC, RBI, or Cyber Crime Cell, about the fraudulent app.
2. Inform Your Bank
If you have shared banking details, contact your bank immediately to block transactions and secure your account.
3. File a Police Complaint
Report the scam to local law enforcement and provide evidence such as screenshots, messages, and transaction details.
4. Check Your Credit Report
Monitor your credit report for unauthorized loans taken in your name. If you find fraudulent activities, report them to credit bureaus.
5. Warn Others
Share your experience on online platforms to alert others about the fake loan app and prevent further scams.
Conclusion
Fake personal loan apps are a growing threat, targeting vulnerable borrowers with deceptive offers. By understanding the red flags and taking preventive measures, you can protect yourself from financial fraud. Always verify lender credentials, avoid upfront payments, and stay cautious when applying for a personal loan online. If you suspect fraudulent activity, act quickly to report and safeguard your financial security.
By staying informed and vigilant, you can ensure a safe and hassle-free borrowing experience in the digital lending space.
#personal loan online#nbfc personal loan#fincrif#bank#loan services#personal loans#loan apps#finance#personal laon#personal loan#Fake personal loan apps#Loan app scams#Personal loan fraud#How to identify fake loan apps#Fraudulent loan applications#Online loan scam warning signs#Loan phishing scams#Fake loan app red flags#Loan fraud prevention tips#Avoiding fake personal loans#Identity theft in loan applications#Personal loan scam alerts#Unauthorized loan approvals#Fake instant loan apps#Loan fraud protection strategies#Cybercrime loan scams#Fake loan app reporting#Loan scam customer complaints#Secure personal loan application#How to verify loan apps
2 notes
·
View notes
Text
Bots Now Dominate the Web: Why This Growing Problem Demands Urgent Action

The digital world, once a bustling marketplace of human interaction, has undergone a silent, pervasive transformation. Data from 2024 and early 2025 reveals a startling reality: bots now dominate web traffic, accounting for over 50% of all internet activity. While some of these automated programs are "good" – diligently indexing content for search engines or enabling helpful chatbots – a significant and escalating proportion are "bad bots," mimicking human behavior for malicious purposes. This widespread bot dominance web traffic presents a serious and ever-growing problem for businesses, cybersecurity, and the overall integrity of the web. The sheer volume and sophistication of these malicious bots internet traffic are redefining the landscape of online security.
The rise of bot traffic on the internet is significantly fueled by rapid advancements in Artificial Intelligence (AI) and Large Language Models (LLMs). These technologies simplify the creation and scaling of sophisticated, evasive bots, allowing even less skilled malicious actors to launch high-volume attacks. As of early 2025, malicious bots account for a staggering 37% of all internet traffic, a substantial increase from previous years, signaling a deepening bot problem online.
The Unseen Majority: How Bots Came to Dominate the Web
For the first time in a decade, automated traffic has surpassed human activity. This shift is primarily attributed to the proliferation of AI and LLMs, which have democratized bot development, making it more accessible to a wider range of actors. These advancements enable bots to mimic human interaction with startling accuracy, often bypassing traditional security measures.
The sophistication of these bad bots internet traffic is constantly evolving. They employ techniques like IP rotation, mimicking legitimate browser fingerprints, and distributing attacks across vast networks of compromised devices (botnets). The goal is simple: evade detection by blending in with legitimate web traffic automation. This makes it increasingly difficult for organizations to differentiate between genuine human users and malicious automated scripts, amplifying the bot problem online.
The Multifaceted Problem: Impacts of Bot Dominance

The pervasive presence of malicious bots internet traffic creates a myriad of complex and costly issues across various aspects of the digital economy. Understanding the full scope of the impact of bots on business is crucial for developing effective defense strategies.
Financial Drain & Fraud
The direct financial implications of bot fraud are staggering. Malicious bots are instrumental in various fraudulent activities that directly hit a business's bottom line:
Credential Stuffing and Account Takeovers (ATOs): Bots automate login attempts using stolen username/password combinations from data breaches. Successful ATOs lead to financial theft, misuse of loyalty points, and damage to customer trust.
Carding and Gift Card Fraud: Bots test stolen credit card numbers against e-commerce sites or attempt to drain balances from stolen digital gift cards, leading to chargebacks and direct financial losses.
Ad Fraud and Click Fraud: Bots simulate clicks and impressions on online advertisements, depleting advertisers' budgets without generating genuine leads or conversions. This distorts analytics and wastes significant marketing spend.
Scalping and Inventory Hoarding: In industries with high-demand, limited-stock items (like concert tickets, sneakers, or popular gaming consoles), bots rapidly purchase inventory, only for it to be resold at inflated prices on secondary markets. This infuriates legitimate customers and damages brand reputation.
Cybersecurity Risks & Data Integrity
Cybersecurity bot attacks represent a fundamental threat to an organization's digital infrastructure and sensitive data. Bots are often the first line of attack in broader cyber campaigns:
Vulnerability Scanning and Exploitation: Bots automatically scan websites and APIs for known vulnerabilities (e.g., SQL injection, cross-site scripting), identifying weak points that can then be exploited for unauthorized access or data exfiltration.
Distributed Denial-of-Service (DDoS) Attacks: Botnets, vast networks of compromised devices controlled by attackers, flood target websites, servers, or networks with overwhelming volumes of traffic, rendering them inaccessible to legitimate users.
API Abuse: With the rise of API-driven applications, bots increasingly target APIs to scrape data, create fake accounts, exploit business logic, or launch sophisticated fraud schemes that bypass traditional web application firewalls.
Data Scraping: Competitors or malicious actors use bots to steal valuable data, including pricing information, product catalogs, customer reviews, and proprietary content, leading to competitive disadvantage and intellectual property theft.
Operational & Performance Disruptions
The sheer volume of web traffic automation from bots places immense strain on IT infrastructure:
Server Strain and Increased Costs: High bot traffic consumes valuable server resources, bandwidth, and computing power, leading to increased hosting expenses and the need for costly infrastructure upgrades.
Degraded Website Performance: Overwhelmed servers result in slower loading times, timeouts, and poor responsiveness for legitimate users, severely impacting user experience and conversion rates.
Skewed Analytics: Bot traffic contaminates website and application analytics, inflating metrics like page views, unique visitors, and clicks while distorting bounce rates and conversion rates. This leads to flawed business decisions based on inaccurate data.
Brand Reputation & Trust
Beyond the technical and financial impacts, bot dominance web traffic erodes trust and damages brand reputation:
Spam and Misinformation: Spam bots flood comment sections, forums, and social media platforms with unsolicited advertising, malicious links, or propaganda, harming a website's credibility and user experience.
Customer Frustration: When legitimate customers are unable to access services due to DDoS attacks, or when they can't purchase items due to bot-driven scalping, their frustration can quickly turn into negative reviews and a damaged brand image.
SEO Penalties: Google and other search engines penalize websites with low-quality or duplicate content, which can result from content scraping by bots, negatively impacting search engine rankings and organic traffic.
Industries Under Siege: Where Bot Threats are Most Acute

While the bot problem online affects nearly every sector, certain industries consistently face a higher proportion and more sophisticated online bot threats:
Financial Services: A primary target due to the sensitive nature of data and high-value transactions. They face relentless account takeover bots, credential stuffing, and fraud attempts.
Retail: Highly susceptible to bot fraud related to inventory scalping, gift card fraud, price scraping, and loyalty program abuse.
Travel: Experiences a significant percentage of bad bots internet traffic, used for competitive price scraping, account takeovers, and fraudulent bookings.
Gaming: Often sees the highest proportion of sophisticated bot traffic, including bots used for cheating, account compromise, and inventory manipulation within in-game economies.
Media and Entertainment: Targeted for content scraping, ad fraud, and credential stuffing on streaming platforms.
Fighting Back: Strategies for Bot Management and Mitigation

Combating bot dominance requires a proactive, multi-layered, and continuously evolving defense strategy. Relying on outdated methods is no longer sufficient against today's sophisticated malicious bots internet attacks.
Advanced Bot Management Solutions: The cornerstone of modern bot defense. These specialized platforms utilize a combination of behavioral analysis (distinguishing human-like patterns from automated ones), machine learning (adapting to new bot tactics), device fingerprinting, and real-time threat intelligence. They go beyond simple IP blocking or CAPTCHAs to detect and mitigate even the most evasive bots.
Robust API Security: Given that 44% of advanced bot traffic targeted APIs in 2024, securing these digital gateways is paramount. Implementing strong authentication mechanisms (like OAuth, API keys), strict access controls, and rate limiting on API endpoints can significantly reduce the attack surface for API security bots. Regular API penetration testing is also crucial.
Multi-Factor Authentication (MFA): Implementing MFA adds a critical layer of security beyond just passwords. Even if bots manage to acquire stolen credentials through credential stuffing, MFA can prevent unauthorized access by requiring a second verification step (e.g., a code from a mobile app), drastically reducing account takeover bots success rates.
Continuous Monitoring and Analytics: Businesses must actively monitor their web traffic automation for unusual patterns. This includes spikes in requests from a single IP, abnormally high failed login attempts, unusual user-agent strings, or suspicious conversion rates. Real-time dashboards and automated alerts are essential for early detection of online bot threats.
Regular Security Audits and Patching: Proactive vulnerability management is key. Regularly auditing web applications, APIs, and underlying infrastructure for security flaws, and promptly patching identified vulnerabilities, closes potential entry points for bots.
User-Agent and Proxy Analysis: Many simpler bots still rely on outdated browser user-agent strings or operate through known dubious proxy services. Implementing rules to block traffic from such indicators can filter out a significant portion of commodity bot attacks. Detecting traffic from residential proxies, which more advanced bots now use, requires more sophisticated analysis.
Rate Limiting and Throttling: While not a complete solution, judiciously applying rate limits on specific endpoints (e.g., login pages, search functions, API calls) can prevent brute-force attacks and resource exhaustion caused by excessive bot requests.
Conclusion: Securing the Human-Centric Web
The landscape of the internet has fundamentally shifted. Bots now dominate the web, and this poses a significant, evolving bot problem online for businesses, their customers, and the integrity of digital interactions. From sophisticated bot fraud schemes to debilitating cybersecurity bot attacks, the impact is wide-ranging and costly.
Ignoring this reality is no longer an option. As AI continues to empower bots to become even more evasive and intelligent, businesses must embrace comprehensive and adaptive bot management solutions. Investing in robust API security, implementing strong authentication, and continuously monitoring for unusual patterns are not merely best practices; they are essential for survival in the current digital climate.
The future of the web depends on our ability to effectively differentiate between humans and machines, safeguarding digital assets and ensuring a secure, reliable, and authentic online experience for everyone. By adopting proactive strategies, organizations can protect their revenue, reputation, and customer trust from the pervasive and growing threat of malicious web traffic automation. The time for urgent action is now.
#Cyber Security Services Company | Data Security Solutions#Top-rated Cyber Security Services Company Offering Advanced Protection#Threat Detection#Risk Assessment#Data Security Solutions For Businesses Worldwide.#Cybersecurity services company#Data security solutions#Managed cybersecurity services#Enterprise cyber protection#Data breach prevention services#Cyber threat protection#IT security solutions provider#Endpoint security services#Network security services#Cybersecurity consulting company
0 notes
Text
From Migration to Optimization: How Azure Partners Streamline Cloud Journeys
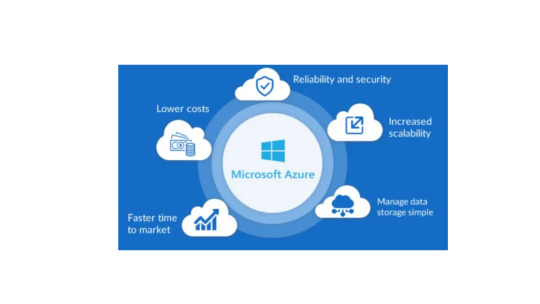
In today’s fast-paced digital era, cloud adoption is no longer a question of “if,” but “how fast.” For businesses eager to innovate, scale, and stay competitive, Microsoft Azure stands out as a powerful and flexible cloud platform. But it takes more than a lift-and-shift strategy to realize its full potential. That’s where Microsoft Azure partners come in—bringing expertise, strategy, and hands-on support to streamline your entire cloud journey, from migration to continuous optimization.
Whether you're moving your first workload to the cloud or fine-tuning an already running Azure environment, certified Azure partners act as your trusted navigators, ensuring your journey is smooth, secure, and cost-effective.
What Are Azure Partners?
Azure partners are certified organizations or cybersecurity consulting firms authorized by Microsoft to help businesses design, deploy, manage, and optimize Azure cloud solutions. These partners go through rigorous training and accreditation to ensure they meet Microsoft’s high standards.
They specialize in various areas such as:
Azure Cloud migration
Infrastructure modernization
Data and AI
Application development
Security and compliance
Cost management and optimization
In short, Azure partners are like experienced guides who help you climb the mountain of cloud transformation—safely and efficiently.
Why Businesses Choose Azure for Cloud Transformation
Before diving into the role of Azure partners, let’s understand why so many businesses are embracing Azure:
Scalability: The capacity to swiftly modify resources to satisfy demand.
Security: Azure has over 90 compliance certifications and built-in threat detection.
Hybrid Capabilities: Seamless integration with on-premises data centers using Azure Arc.
Advanced Services: AI, machine learning, analytics, and IoT capabilities.
Global Reach: Data centers in more than 60 regions worldwide.
But as powerful as Azure is, navigating it without expert help can be overwhelming. That’s where Azure partners become invaluable.
Phase 1: Planning & Assessment
Understanding Business Goals
Azure partners begin by deeply understanding your business goals, IT landscape, and compliance needs. They assess your current infrastructure, applications, workloads, and pain points to determine if Azure is the right fit and how best to approach the migration.
Cloud Readiness Assessment
A thorough evaluation determines which workloads are appropriate for transfer, as well as any possible dangers, financial consequences, and performance goals. This phase ensures you're making informed decisions and not rushing into migration blindly.
Developing a Roadmap
Based on the assessment, the Azure partner creates a custom roadmap outlining:
Migration timeline
Tools and methodologies
Cost estimates
Resource allocation
Compliance requirements
Phase 2: Cloud Migration
Lift-and-Shift or Re-Architecting
Azure partners determine the best migration strategy for each workload:
Lift-and-shift for faster migration of legacy apps.
Re-platforming to take advantage of PaaS features.
Re-architecting for scalability, performance, and long-term efficiency.
Utilizing Azure Migration Tools
Certified partners leverage Microsoft’s native tools, such as:
Azure Migrate
Azure Site Recovery
Database Migration Service
These tools help reduce downtime, minimize data loss, and ensure smoother transitions.
Ensuring Business Continuity
During migration, Azure partners monitor systems closely to ensure minimal disruption. Backup and disaster recovery solutions are also configured to keep operations running smoothly.
Phase 3: Post-Migration Support
Validation and Testing
After the migration is finished, careful verification makes sure everything functions as it should:
Application functionality
Data integrity
Performance benchmarks
Security configurations
Azure partners troubleshoot any post-migration issues and tweak configurations for optimal performance.
User Training and Change Management
Migration is not just technical—it’s cultural too. Azure partners help with user training, documentation, and support to ensure your team embraces the new environment with confidence.
Phase 4: Continuous Optimization
Migration is only half the story. The real value of cloud transformation lies in continuous optimization, and this is where Azure partners truly shine.
Performance Tuning
Partners analyze workload behavior, monitor performance metrics, and make necessary adjustments to improve speed, responsiveness, and reliability.
Cost Optimization
By rightsizing resources, automating scaling, and eliminating unused services, Azure partners help reduce cloud costs significantly. They also advise on using Azure Reserved Instances and Azure Cost Management to gain better financial control.
Security Enhancements
With ever-evolving cyber threats, continuous security monitoring is essential. Azure partners help:
Set up firewalls and threat protection
Configure role-based access controls
Monitor compliance with regulations like GDPR or HIPAA
Conduct regular security audits
Innovation Enablement
Azure isn’t just a hosting platform—it’s a launchpad for innovation. Certified partners help you:
Deploy AI and machine learning models
Use analytics for smarter business insights
Build modern applications using containers and microservices
Benefits of Working with Azure Partners
Faster Time to Value: Avoid trial and error with proven methodologies.
Expertise on Demand: Access skilled professionals without hiring internally.
Scalable Solutions: Grow your cloud environment as your business grows.
Reduced Downtime: Minimize disruptions with proactive planning and monitoring.
Innovation Acceleration: Leverage cutting-edge Azure cloud services effectively.
How to Choose the Right Azure Partner
Not all partners are created equal. Here’s what to look for:
Microsoft Gold or Solutions Partner Status
Industry-specific experience
Certified Azure engineers
Successful case studies and references
Managed service offerings
24/7 support and SLAs
Choosing the right partner is a strategic decision. They’re not just vendors—they’re collaborators in your digital transformation journey.
The Future of Cloud: Beyond Migration
The cloud isn’t a destination—it’s a continuous journey. Azure’s ecosystem is expanding rapidly, offering innovations in areas like:
Quantum computing
Mixed reality
Green cloud solutions
Industry-specific cloud modules (e.g., Azure for Healthcare, Azure for Retail)
To keep pace, businesses must evolve constantly, and Azure partners provide the guidance, tools, and strategy to do exactly that.
Conclusion
Azure partners are essential to a successful cloud transition, from early planning and migration to continuous optimization and innovation. They remove the complexity of the Azure platform, enabling your business to focus on growth, agility, and customer value.
Whether you’re starting your cloud journey or looking to get more from your existing Azure setup, working with a certified Azure partner ensures you get the best results, faster and with less risk.
Cloud isn’t just about moving workloads—it’s about unlocking potential. With the right partner, Azure becomes not just a platform but a business advantage.
FAQs
1. What’s the difference between an Azure partner and a managed service provider?
Azure partners offer specialized expertise in designing and optimizing Azure environments. Managed cloud service providers may handle day-to-day maintenance, but don’t always specialize in Azure.
2. Is working with an Azure partner expensive?
While there’s a cost involved, the ROI is typically high due to faster migrations, reduced downtime, and optimized resource usage, saving money long-term.
3. Can Azure partners help with hybrid environments?
Yes, many partners specialize in hybrid solutions, helping you connect on-premise systems with Azure cloud using services like Azure Arc.
4. How long does an Azure migration typically take?
It varies depending on the complexity of your workloads, but with the help of an Azure partner, many projects can be completed within a few weeks to a few months.
5. Are Azure partners only for large enterprises?
Not at all. Azure partners work with businesses of all sizes—from startups to Fortune 500 companies—offering scalable services to match your needs.
#cloud governance#cloud risk management framework#Azure Security Center#aws configuration#Azure Compliance Manager#Azure Information Protection#aws key management service#GRC solutions
0 notes
Text
Best Data Privacy Services Providers in 2023 - Digital Personal Data Protection Act 2023
JISA Softech is recognized among one of the best Data Privacy Services Providers in 2023, offering cutting-edge solutions aligned with the Digital Personal Data Protection Act 2023. Their services ensure secure handling of sensitive data through advanced encryption, access control, and regulatory compliance. With a focus on privacy-first architecture, JISA Softech helps businesses stay ahead of evolving data protection laws. Choose JISA Softech for trusted and future-ready data privacy solutions. Read more - https://www.jisasoftech.com/dpdp-act-2023/
#Digital Personal Data Protection Act 2023#jisa softech#Best Data Privacy Services Providers in 2023#DPDP#data security#dpdp act 2023
0 notes