#open source property management software
Explore tagged Tumblr posts
Text

Want to manage your real estate business more efficiently? Our ERP solution helps you to manage Property Items, Maintenance, Insurance, Utilities, and Rent with reminders to stay on top of your responsibilities. You can easily manage Customers, Tenants, Landlords, Tenancy and web portal details all in one place. And it's also provides detailed reports and a workspace to streamline detailed all your processes.
#property management system#pms system#real estate management system#property management software#rental property management software#commercial property management software#property software#open source property management software#real estate property software
0 notes
Text

Nintendo sues Yuzu Switch Emulator
February 28th 2024 Gaming / Nintendo / Lawsuit
KOSAMA
| Writer and Recovering Anime Addict
Nintendo has initiated legal action against the creators of Yuzu, an open-source Nintendo Switch emulator, as revealed by a lawsuit filed in a Rhode Island court on Monday. The lawsuit, detailed across 41 pages, targets Tropic Haze, the entity behind Yuzu, with specific mention of an individual identified by the alias Bunnei, who spearheads Yuzu's development. The genesis of this lawsuit was initially reported by Stephen Totilo, a correspondent for Game File.
Yuzu, which emerged in 2018 shortly after the debut of the Nintendo Switch, is a freely available emulator crafted by the same developers responsible for Citra, a Nintendo 3DS emulator. Essentially, Yuzu functions as software enabling users to engage with Nintendo Switch games on platforms such as Windows PC, Linux (including devices like the Steam Deck), and certain Android devices. While the legality of emulators per se isn't inherently contentious, their employment for pirating copyrighted games is a matter of concern. Nintendo's lawsuit contends that there exists no lawful avenue for utilizing Yuzu.
Within the legal documentation, Nintendo asserts that "there is no lawful way to use Yuzu to play Nintendo Switch games." Nevertheless, this assertion invites scrutiny and potential legal rebuttals on behalf of the emulator developers.
Firstly, the US Copyright Office generally permits users to create duplicates of legitimately acquired software for archival motives, subject to specific conditions. Consequently, accessing personal archival copies could conceivably constitute a lawful purpose for utilizing an emulator such as Yuzu.
Significantly, the Yuzu emulator, being open-source, does not incorporate copies of the necessary "prod.keys" mentioned in Nintendo's lawsuit, which users must supply themselves. This sets Yuzu apart from the Dolphin emulator, which faced removal from Steam in the previous year after Nintendo highlighted its inclusion of the Wii Common Key for decrypting game files.
In the absence of intrinsic capabilities to circumvent digital rights management (DRM), an emulator typically falls within the ambit of legal precedent permitting emulation of one hardware system on another through reverse-engineering methodologies.
Nintendo's legal pursuit against Yuzu reflects a complex intersection of intellectual property rights, digital preservation, and the evolving landscape of emulation technology. As the case unfolds, it promises to shape future discussions surrounding the legality and boundaries of emulator usage within the gaming community.
1 note
·
View note
Text
WILL CONTAINER REPLACE HYPERVISOR
As with the increasing technology, the way data centers operate has changed over the years due to virtualization. Over the years, different software has been launched that has made it easy for companies to manage their data operating center. This allows companies to operate their open-source object storage data through different operating systems together, thereby maximizing their resources and making their data managing work easy and useful for their business.
Understanding different technological models to their programming for object storage it requires proper knowledge and understanding of each. The same holds for containers as well as hypervisor which have been in the market for quite a time providing companies with different operating solutions.
Let’s understand how they work
Virtual machines- they work through hypervisor removing hardware system and enabling to run the data operating systems.
Containers- work by extracting operating systems and enable one to run data through applications and they have become more famous recently.

Although container technology has been in use since 2013, it became more engaging after the introduction of Docker. Thereby, it is an open-source object storage platform used for building, deploying and managing containerized applications.
The container’s system always works through the underlying operating system using virtual memory support that provides basic services to all the applications. Whereas hypervisors require their operating system for working properly with the help of hardware support.
Although containers, as well as hypervisors, work differently, have distinct and unique features, both the technologies share some similarities such as improving IT managed service efficiency. The profitability of the applications used and enhancing the lifecycle of software development.
And nowadays, it is becoming a hot topic and there is a lot of discussion going on whether containers will take over and replace hypervisors. This has been becoming of keen interest to many people as some are in favor of containers and some are with hypervisor as both the technologies have some particular properties that can help in solving different solutions.
Let’s discuss in detail and understand their functioning, differences and which one is better in terms of technology?
What are virtual machines?
Virtual machines are software-defined computers that run with the help of cloud hosting software thereby allowing multiple applications to run individually through hardware. They are best suited when one needs to operate different applications without letting them interfere with each other.
As the applications run differently on VMs, all applications will have a different set of hardware, which help companies in reducing the money spent on hardware management.
Virtual machines work with physical computers by using software layers that are light-weighted and are called a hypervisor.
A hypervisor that is used for working virtual machines helps in providing fresh service by separating VMs from one another and then allocating processors, memory and storage among them. This can be used by cloud hosting service providers in increasing their network functioning on nodes that are expensive automatically.
Hypervisors allow host machines to have different operating systems thereby allowing them to operate many virtual machines which leads to the maximum use of their resources such as bandwidth and memory.

What is a container?
Containers are also software-defined computers but they operate through a single host operating system. This means all applications have one operating center that allows it to access from anywhere using any applications such as a laptop, in the cloud etc.
Containers use the operating system (OS) virtualization form, that is they use the host operating system to perform their function. The container includes all the code, dependencies and operating system by itself allowing it to run from anywhere with the help of cloud hosting technology.
They promised methods of implementing infrastructure requirements that were streamlined and can be used as an alternative to virtual machines.
Even though containers are known to improve how cloud platforms was developed and deployed, they are still not as secure as VMs.
The same operating system can run different containers and can share their resources and they further, allow streamlining of implemented infrastructure requirements by the system.
Now as we have understood the working of VMs and containers, let’s see the benefits of both the technologies
Benefits of virtual machines
They allow different operating systems to work in one hardware system that maintains energy costs and rack space to cooling, thereby allowing economical gain in the cloud.
This technology provided by cloud managed services is easier to spin up and down and it is much easier to create backups with this system.
Allowing easy backups and restoring images, it is easy and simple to recover from disaster recovery.
It allows the isolated operating system, hence testing of applications is relatively easy, free and simple.

Benefits of containers:
They are light in weight and hence boost significantly faster as compared to VMs within a few seconds and require hardware and fewer operating systems.
They are portable cloud hosting data centers that can be used to run from anywhere which means the cause of the issue is being reduced.
They enable micro-services that allow easy testing of applications, failures related to the single point are reduced and the velocity related to development is increased.
Let’s see the difference between containers and VMs
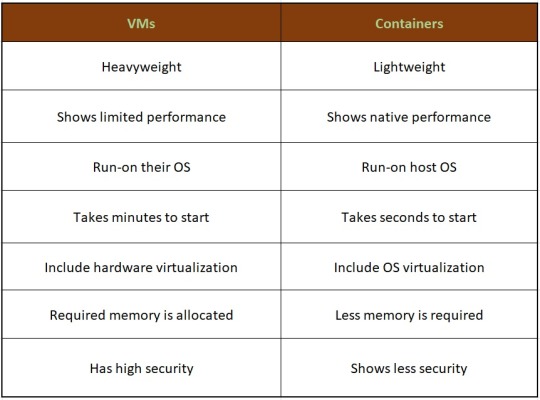
Hence, looking at all these differences one can make out that, containers have added advantage over the old virtualization technology. As containers are faster, more lightweight and easy to manage than VMs and are way beyond these previous technologies in many ways.
In the case of hypervisor, virtualization is performed through physical hardware having a separate operating system that can be run on the same physical carrier. Hence each hardware requires a separate operating system to run an application and its associated libraries.
Whereas containers virtualize operating systems instead of hardware, thereby each container only contains the application, its library and dependencies.
Containers in a similar way to a virtual machine will allow developers to improve the CPU and use physical machines' memory. Containers through their managed service provider further allow microservice architecture, allowing application components to be deployed and scaled more granularly.

As we have seen the benefits and differences between the two technologies, one must know when to use containers and when to use virtual machines, as many people want to use both and some want to use either of them.
Let’s see when to use hypervisor for cases such as:
Many people want to continue with the virtual machines as they are compatible and consistent with their use and shifting to containers is not the case for them.
VMs provide a single computer or cloud hosting server to run multiple applications together which is only required by most people.
As containers run on host operating systems which is not the case with VMs. Hence, for security purposes, containers are not that safe as they can destroy all the applications together. However, in the case of virtual machines as it includes different hardware and belongs to secure cloud software, so only one application will be damaged.
Container’s turn out to be useful in case of,
Containers enable DevOps and microservices as they are portable and fast, taking microseconds to start working.
Nowadays, many web applications are moving towards a microservices architecture that helps in building web applications from managed service providers. The containers help in providing this feature making it easy for updating and redeploying of the part needed of the application.
Containers contain a scalability property that automatically scales containers, reproduces container images and spin them down when they are not needed.
With increasing technology, people want to move to technology that is fast and has speed, containers in this scenario are way faster than a hypervisor. That also enables fast testing and speed recovery of images when a reboot is performed.

Hence, will containers replace hypervisor?
Although both the cloud hosting technologies share some similarities, both are different from each other in one or the other aspect. Hence, it is not easy to conclude. Before making any final thoughts about it, let's see a few points about each.

Still, a question can arise in mind, why containers?
Although, as stated above there are many reasons to still use virtual machines, containers provide flexibility and portability that is increasing its demand in the multi-cloud platform world and the way they allocate their resources.
Still today many companies do not know how to deploy their new applications when installed, hence containerizing applications being flexible allow easy handling of many clouds hosting data center software environments of modern IT technology.
These containers are also useful for automation and DevOps pipelines including continuous integration and continuous development implementation. This means containers having small size and modularity of building it in small parts allows application buildup completely by stacking those parts together.
They not only increase the efficiency of the system and enhance the working of resources but also save money by preferring for operating multiple processes.
They are quicker to boost up as compared to virtual machines that take minutes in boosting and for recovery.
Another important point is that they have a minimalistic structure and do not need a full operating system or any hardware for its functioning and can be installed and removed without disturbing the whole system.
Containers replace the patching process that was used traditionally, thereby allowing many organizations to respond to various issues faster and making it easy for managing applications.
As containers contain an operating system abstract that operates its operating system, the virtualization problem that is being faced in the case of virtual machines is solved as containers have virtual environments that make it easy to operate different operating systems provided by vendor management.
Still, virtual machines are useful to many
Although containers have more advantages as compared to virtual machines, still there are a few disadvantages associated with them such as security issues with containers as they belong to disturbed cloud software.
Hacking a container is easy as they are using single software for operating multiple applications which can allow one to excess whole cloud hosting system if breaching occurs which is not the case with virtual machines as they contain an additional barrier between VM, host server and other virtual machines.
In case the fresh service software gets affected by malware, it spreads to all the applications as it uses a single operating system which is not the case with virtual machines.
People feel more familiar with virtual machines as they are well established in most organizations for a long time and businesses include teams and procedures that manage the working of VMs such as their deployment, backups and monitoring.
Many times, companies prefer working with an organized operating system type of secure cloud software as one machine, especially for applications that are complex to understand.
Conclusion
Concluding this blog, the final thought is that, as we have seen, both the containers and virtual machine cloud hosting technologies are provided with different problem-solving qualities. Containers help in focusing more on building code, creating better software and making applications work on a faster note whereas, with virtual machines, although they are slower, less portable and heavy still people prefer them in provisioning infrastructure for enterprise, running legacy or any monolithic applications.
Stating that, if one wants to operate a full operating system, they should go for hypervisor and if they want to have service from a cloud managed service provider that is lightweight and in a portable manner, one must go for containers.
Hence, it will take time for containers to replace virtual machines as they are still needed by many for running some old-style applications and host multiple operating systems in parallel even though VMs has not had so cloud-native servers. Therefore, it can be said that they are not likely to replace virtual machines as both the technologies complement each other by providing IT managed services instead of replacing each other and both the technologies have a place in the modern data center.
For more insights do visit our website
#container #hypervisor #docker #technology #zybisys #godaddy
6 notes
·
View notes
Text
When real-estate-startup cofounder Vai Gupta visited downtown San Francisco from the suburbs last year, he borrowed a conference room at a branch of Silicon Valley Bank to host a quick business meeting, just like he has several times over the past decade. Gupta also has leaned on the bank for networking events, financial tutorials, and discount codes for business software and services. Other banks offer competing perks, but SVB’s total package had won Gupta’s loyalty, until the tech-focused financial giant cratered last week.
Now Gupta is among thousands of customers wondering whether they will ever again find a financial institution that offers the unique blend of benefits, savvy, and speed that SVB delivered to entrepreneurs. Founded about 40 years ago by a Stanford University professor who teamed with banking experts after noticing students struggling to fund business ideas, Silicon Valley Bank treated startup founders like royalty long before their companies ever generated a profit or even raised significant funding.
By offering loans, guidance, and bountiful bottles of fine wine and all-expenses-paid ski trips to companies too small in sales for bigger banks to handhold, SVB quickly became the go-to bank for anyone intersecting with the San Francisco Bay Area’s globally known startup community. Clients who have grown with SVB’s help include Cisco, Coinbase, and Etsy.
But a bad bet on interest rates staying low—they have risen sharply since the start of 2022—and poor crisis communications led to its customers launching a run on the bank over fears about SVB’s financial health. Regulators took control of the bank on March 10, and the US Federal Deposit Insurance Corporation stepped in over the weekend to fully guarantee the remaining deposits.
SVB’s future remains uncertain, and several entrepreneurs say they are finding that financial institutions rushing to fill the void are falling short in matching its suite of services and extras. Most of all, they wonder what it might mean for them and startups more broadly to lose a trusted partner that helped early-stage companies and founders survive difficult times and secure mortgages or loans others wouldn’t provide.
“They understand our innovation ecosystem and build all of their offerings around that,” says Hemant Taneja, the chief executive and managing director of General Catalyst, a venture capital firm that banks with SVB. “They have the trust of the VC community that they will help these companies through thick and thin.”
Taneja’s firm joined several others yesterday calling for companies to restore their deposits and lending with SVB, describing it as “now one of the safest and most secure banks in the country.” The bank posted on its website yesterday that under the oversight of federal regulators it is honoring all existing loans and welcoming new clients. SVB deferred a request for comment for this story to the FDIC, which declined the invitation. A source at the bank says a few dozen companies expressed interest yesterday in securing new loans.
SVB's at-least temporary demise has added to existing economic uncertainty in tech. Rising interest rates have throttled startups’ access to cheap cash from investors over the past year. Losing access to the loans and connections that SVB provided could accelerate the collapse of some companies and force others to pare their ambitions—and potentially payrolls—until consumer and investor confidence in the economy rebounds.
Gupta, the real estate entrepreneur, is already missing SVB. He wires money internationally at least a couple of times a month for his startup BonfireDAO, which aims to lower barriers to buying properties using blockchain technology that underpins cryptocurrencies. He estimates that Chase, his new bank, will charge him $5,000 a year for the transfers, which SVB provided for free.
SVB also offered customers freebies through a dedicated section in its mobile app long before other banks dangled similar discounts to startups, says Gupta, who from SVB has taken advantage of Amazon Web Services cloud computing credits and free DocuSign e-signature services. He attended over a dozen SVB events, including sessions on finding cofounders and pitching investors. The bank would also let him stop by for a free lunch or to use a meeting room during business trips. “They were very hospitable,” Gupta says. He says he might now have to shell out for a WeWork membership.
Entrepreneur Adam Zbar has enjoyed the use of an SVB ski house with a dock on California’s Lake Tahoe. As CEO of meal delivery company Sunbasket, he would use it to host weeklong retreats for his management team. The bank would bring in a top chef for a night and exclusive wines from SVB’s winery clients. “It was phenomenal,” Zbar says.
SVB sponsorships also helped pay for trips for Los Angeles tech entrepreneurs to ski at Mammoth Mountain in California and surf at a human-made ranch constructed amid farms, says Zach James, co-CEO of ad tech company Zefr. SVB would take clients to race fancy cars, go backstage at music festivals, and meet vintners at private sessions at Napa Valley wineries to the point that it hosted 300 wine-related events one year.
Rivals had ramped up. JPMorgan Chase announced hiring several top bankers from SVB over the past few years. First Republic Bank was making progress adding tech clients. But their main focus remained elsewhere.
Law firms and recruiting and consulting companies are also major sponsors of tech industry schmoozing, though none of them—and certainly no other bank—came close to matching SVB’s largesse toward companies far away from listing on Wall Street, the entrepreneurs and several investors say. “They were one of the key underwriters of the community,” says Paige Craig, who has been a customer of the bank as an entrepreneur and a venture capitalist. “It’s a big hole to fill.”
For all the fancy perks, the ease of borrowing money from SVB has been the biggest draw for many companies. Startups take out bank loans to diversify their financing, and they often can secure the dollars without giving up as many shares as they have to provide venture investors.
Zefr’s James has taken out loans for his company several times through SVB after shopping around. In some cases, the bank takes a small ownership stake in the borrowers. Other times it defers principal payments for a year or two or allows for repayment in a single lump sum. “It was the catch-all for startups,” James says of SVB.
Generally, it offered among the least-restrictive terms and equally competitive interest rates, entrepreneurs say. If a borrower failed, SVB was known to handle it more gracefully than other lenders. Effectively, according to language seen by WIRED, SVB would support companies as long as their venture capital backers, often clients of the bank, did not abandon them. “Bankers become a lifeline when you get into trouble, and if they stand by you, I take that seriously,” says James of his loyalty to the now crushed bank.
Roger Smith, SVB’s founding CEO, told the Computer History Museum in 2014 that the bank did not sacrifice profits by being flexible. “When the music stops, we want two chairs, not just one,” he said. “But we were able to help people grow and … we were part of the flow.”
Just ask Zbar, the former Sunbasket chief. He dreamed up the meal delivery company in 2013 after he had spent through the venture funding he had raised for a different idea. He had no money to pay back a bank loan. But his banker at SVB loved the Sunbasket pitch, and investors were supportive, so SVB agreed to allow Zbar to keep operating month-to-month on new terms as the food venture progressed.
“I remember having some unpleasant conversations where I was like, wow, you know, you took a piece of my hide, but my business still survived,” says Zbar, now chief executive of HamsaPay, which uses blockchain for commercial loan financing. He believes other banks are less flexible than SVB. “They just freeze it, and you're done,” he says. Zbar even welcomed his SVB banker as a bachelor-party guest.
To be sure, Silicon Valley Bank’s reliance on relationships and knowledge of venture capitalists to guide its lending decisions raises questions about whether it perpetuated exclusion of women, racial minorities, or other groups historically overlooked by the startup financing industry. Investors say some of those issues may be valid, but the bank did open up opportunities.
SVB fronted cash to people of underrepresented backgrounds trying to buy into venture capital funds, says the investor Craig, who runs Outlander VC. It provided home mortgages to investors early in their careers who couldn’t get them elsewhere, based on a deep understanding of the tech companies its customers were betting on, Craig says. “I really hope they rebuild and reconstitute. No one understood founders and innovators as well as SVB,” he says.
As entrepreneurs have fanned out to other banks in recent days to shift their deposits from SVB, their experiences have reminded them of what they enjoyed about SVB. James’ Zefr has not found a single bank that can offer every service he wants, so he is using one to borrow money and another for conventional accounts. He does not expect Zefr’s growth to slow, but says his company “will have to suffer worse terms or take on a bit more risk.”
Gupta, who is chief technology officer of BonfireDAO, recalls how he was able to open an account with SVB entirely online while in Singapore at his previous startup a decade ago, an option he has not found as he now searches for SVB alternatives. “They were just the first one to really propose solutions,” he says of his early interactions with SVB. “I never shopped around again.”
He wrote on LinkedIn last week that “many startups like [his] have lost a valuable friend, partner, and source of support.” He says his heart wants to stick with SVB if it resurrects, but he’s no longer sure it’s financially prudent to do so, no matter the constant aid, invaluable discounts, or occasional free conference room.
5 notes
·
View notes
Text
Power of Quantum Computing 02

Utilizing the Potential of Quantum Computing.
A revolutionary technology, quantum computing holds the promise of unmatched computational power. Development of quantum software is in greater demand as the field develops. The link between the complicated underlying hardware and the useful applications of quantum computing is provided by quantum software. The complexities of creating quantum software, its potential uses, and the difficulties developers face will all be covered in this article.

BY KARTAVYA AGARWAL
First, a primer on quantum computing.
Contrary to traditional computing, quantum computing is based on different principles. Working with qubits, which can exist in a superposition of states, is a requirement. These qubits are controlled by quantum gates, including the CNOT gate and the Hadamard gate. For the creation of quantum software, comprehension of these fundamentals is essential. Qubits and quantum gates can be used to create quantum algorithms, which are capable of solving complex problems more quickly than conventional algorithms. Second, there are quantum algorithms. The special characteristics of quantum systems are specifically tapped into by quantum algorithms. For instance, Shor's algorithm solves the factorization issue and might be a threat to traditional cryptography. The search process is accelerated by Grover's algorithm, however. A thorough understanding of these algorithms and how to modify them for various use cases is required of quantum software developers. They investigate and develop new quantum algorithms to address issues in a variety of fields, including optimization, machine learning, and chemistry simulations. Quantum simulation and optimization are the third point. Complex physical systems that are difficult to simulate on traditional computers can be done so using quantum software. Scientists can better comprehend molecular structures, chemical processes, and material properties by simulating quantum systems. Potential solutions for logistics planning, financial portfolio management, and supply chain optimization are provided by quantum optimization algorithms. To accurately model these complex systems, quantum software developers work on developing simulation frameworks and algorithm optimization techniques. The 4th Point is Tools and Languages for Quantum Programming. Programming languages and tools that are specific to quantum software development are required. A comprehensive set of tools and libraries for quantum computing are available through the open-source framework Qiskit, created by IBM. Another well-known framework that simplifies the design and simulation of quantum circuits is Cirq, created by Google. Incorporating quantum computing with traditional languages like C, the Microsoft Quantum Development Kit offers a quantum programming language and simulator. These programming languages and tools are utilized by developers to create quantum hardware, run simulations, and write quantum circuits. The 5th point is quantum error correction. Störungs in the environment and flaws in the hardware can lead to errors in quantum systems. Quantum computations are now more reliable thanks to quantum error correction techniques that reduce these errors. To guard against errors and improve the fault tolerance of quantum algorithms, developers of quantum software employ error correction codes like the stabilizer or surface codes. They must comprehend the fundamentals of error correction and incorporate these methods into their software designs. Quantum cryptography and secure communication are the sixth point. Secure communication and cryptography are impacted by quantum computing. Using the concepts of quantum mechanics, quantum key distribution (QKD) offers secure key exchange and makes any interception detectable. Post-quantum cryptography responds to the danger that quantum computers pose to already-in-use cryptographic algorithms. To create secure communication protocols and investigate quantum-resistant cryptographic schemes, cryptographers and quantum software developers work together. Point 7: Quantum machine learning A new field called "quantum machine learning" combines machine learning with quantum computing. The speedup of tasks like clustering, classification, and regression is being studied by quantum software developers. They investigate how quantum machine learning might be advantageous in fields like drug discovery, financial modeling, and optimization. Point 8: Validation and testing of quantum software. For accurate results and trustworthy computations, one needs trustworthy quantum software. Different testing methodologies are used by quantum software developers to verify the functionality and efficiency of their products. To locate bugs, address them, and improve their algorithms, they carry out extensive testing on simulators and quantum hardware. Quantum software is subjected to stringent testing and validation to guarantee that it produces accurate results on various platforms. Point 9: Quantum computing in the study of materials. By simulating and enhancing material properties, quantum software is crucial to the study of materials. To model chemical processes, examine electronic architectures, and forecast material behavior, researchers use quantum algorithms. Variational quantum eigensolvers are one example of a quantum-inspired algorithm that makes efficient use of the vast parameter space to find new materials with desired properties. To create software tools that improve the processes of materials research and discovery, quantum software developers work with materials scientists. Quantum computing in financial modeling is the tenth point. Quantum software is used by the financial sector for a variety of applications, which helps the industry reap the benefits of quantum computing. For portfolio optimization, risk assessment, option pricing, and market forecasting, quantum algorithms are being investigated. Financial institutions can enhance decision-making processes and acquire a competitive advantage by utilizing the computational power of quantum systems. Building quantum models, backtesting algorithms, and converting existing financial models to quantum frameworks are all tasks carried out by quantum software developers.

FAQs:. What benefits can software development using quantum technology offer? Complex problems can now be solved exponentially more quickly than before thanks to quantum software development. It opens up new opportunities in materials science, machine learning, optimization, and cryptography. Is everyone able to access quantum software development? Despite the fact that creating quantum software necessitates specialized knowledge, there are tools, tutorials, and development frameworks available to support developers as they begin their quantum programming journey. What are the principal difficulties faced in creating quantum software? Algorithm optimization for particular hardware, minimization of quantum errors through error correction methods, and overcoming the dearth of established quantum development tools are among the difficulties. Are there any practical uses for quantum software? Yes, there are many potential uses for quantum software, including drug discovery, financial modeling, traffic optimization, and materials science. What can be done to advance the creation of quantum software? Researchers, programmers, contributors to open-source quantum software projects, and people working with manufacturers of quantum hardware to improve software-hardware interactions are all ways that people can make a difference. Conclusion: The enormous potential of quantum computing is unlocked in large part by the development of quantum software. The potential for solving difficult problems and revolutionizing numerous industries is exciting as this field continues to develop. We can use quantum computing to influence the direction of technology by grasping its fundamentals, creating cutting-edge algorithms, and utilizing potent quantum programming languages and tools. link section for the article on Quantum Software Development: - Qiskit - Website - Qiskit is an open-source quantum computing framework developed by IBM. It provides a comprehensive suite of tools, libraries, and resources for quantum software development. - Cirq - Website - Cirq is a quantum programming framework developed by Google. It offers a platform for creating, editing, and simulating quantum circuits. - Microsoft Quantum Development Kit - Website - The Microsoft Quantum Development Kit is a comprehensive toolkit that enables quantum programming using the Q# language. It includes simulators, libraries, and resources for quantum software development. - Quantum Computing for the Determined - Book - "Quantum Computing for the Determined" by Alistair Riddoch and Aleksander Kubica is a practical guide that introduces the fundamentals of quantum computing and provides hands-on examples for quantum software development. - Quantum Algorithm Zoo - Website - The Quantum Algorithm Zoo is a repository of quantum algorithms categorized by application domains. It provides code examples and explanations of various quantum algorithms for developers to explore. Read the full article
2 notes
·
View notes
Text
Is Custom Software Development Worth the Investment?
Discover the Long-Term Cost Savings!

In today's rapidly evolving business environment, software solutions are crucial for streamlining operations, enhancing productivity, and gaining a competitive edge. While off-the-shelf software may seem like a cost-effective option initially, custom software development can offer significant long-term cost savings and a greater return on investment. This article explores the various ways custom software can lead to long-term cost efficiency and why it's a worthwhile investment for businesses seeking sustainable growth.
The Financial Benefits of Custom Software
Custom software development involves creating a solution tailored specifically to your business needs. While it may require a higher upfront investment compared to licensing off-the-shelf software, the long-term benefits can outweigh the initial costs. Here’s how:
Reduced Operational Costs: Companies implementing tailored software can experience operational cost savings of 15–25% within the first three years.
Elimination of Unnecessary Features: Custom software allows businesses to avoid paying for features they don't need, focusing only on essential functionalities.
Scalability: Custom software is designed with scalability in mind, allowing it to adapt as the business grows without requiring significant reinvestment.
Streamlined Workflows: Custom software guarantees streamlined workflows.
Automation: Automating repetitive tasks frees up valuable resources, reducing labor costs and improving efficiency.
Vendor Independence: Open-source software (OSS) reduces costs because it is free to use and customize. Savings also come from vendor independence, community support, and the lack of costly licenses.
Strategies to Maximize Cost Savings
To ensure that your custom software development project delivers the best possible return on investment, consider the following strategies:
Leverage a Minimum Viable Product (MVP): An MVP focuses on core functionalities and allows for scaling up with user feedback, saving time and costs initially.
Focus on Must-Have Features: Prioritize features that deliver the most value to users and align with business goals to avoid unnecessary development costs.
Implement Quality Assurance Protocols: Quality assurance protocols can reduce development charges and help the development team deliver quality software.
Embrace Agile Development: Agile development methodologies promote constant communication and collaboration, allowing for quick adjustments and cost-effective solutions.
Utilize Open-Source Software: Open-source software (OSS) is free to use, customizable, and contains reusable code for cheaper software development.
Choose the Right Technology Stack: Some stacks provide pre-built code and functionalities, reducing the amount of code developers need to write from scratch, thus lessening labor hours and costs.
Consider Cloud Computing: Cloud services can be more affordable than traditional software and hardware solutions.
Maintenance: Technologies known for easy maintenance due to strong community support and thorough documentation, such as React or Angular, also help decrease custom software development costs long-term.
Weighing the Investment
Custom software development offers numerous advantages, including tailored solutions and greater control over intellectual property. However, it's essential to acknowledge the potential challenges:
Higher Upfront Costs: Custom software typically involves a higher initial investment compared to off-the-shelf solutions.
Time-Intensive Development: The development process can be lengthy, requiring careful planning and management.
Conclusion
Custom software development can be a game-changer for businesses seeking long-term cost savings and sustainable growth. By carefully planning your project, focusing on essential features, and implementing effective cost-saving strategies, you can unlock the full potential of custom software and achieve a significant return on your investment.
0 notes
Text
Expert SuiteCRM Development Services | Taction Software Solutions
In today's competitive business landscape, customer relationship management (CRM) systems play a crucial role in enhancing customer interactions, managing sales, and driving growth. Among the various CRM solutions available, SuiteCRM stands out as an open-source platform that offers flexibility, customization, and a robust feature set. Taction Software specializes in SuiteCRM Development, providing tailored solutions that meet the unique needs of businesses.
What is SuiteCRM?
SuiteCRM is a fork of the popular SugarCRM Community Edition, designed to provide excellent functionality without the constraints of licensing fees. It boasts a wide range of features that include:
Sales Management: Streamlined sales processes, lead tracking, and opportunity management.
Marketing Automation: Tools for campaign management, email marketing, and social media integration.
Customer Support:Ticketing systems, knowledge bases, and customer service management.
Reporting and Analytics: Customizable dashboards and comprehensive reporting tools.
The platform's open-source nature allows businesses to adapt and extend its functionalities to align with their operational requirements.
Why Choose Taction Software for SuiteCRM Development?
Expertise in Customization
At Taction Software, we understand that no two businesses are the same. Our team of experienced developers specializes in customizing SuiteCRM to fit specific processes and workflows. Whether you need additional modules, custom reports, or user interface adjustments, we can create solutions that enhance your operational efficiency.
Seamless Integration
Modern businesses rely on multiple tools and platforms. Our development team is skilled in integrating SuiteCRM with existing applications, ensuring that data flows seamlessly across your organization. From connecting with e-commerce platforms to integrating with marketing tools, we ensure a unified system that enhances user experience.
Ongoing Support and Maintenance
Implementing a new CRM system is just the beginning. Taction Software provides ongoing support and maintenance services, helping businesses stay up to date with the latest SuiteCRM features and upgrades. Our dedicated support team is available to assist with any questions or issues, ensuring your system runs smoothly.

Training and Onboarding
Transitioning to SuiteCRM can be daunting. We offer comprehensive training programs for your team, helping them navigate the system and maximize its potential. Our onboarding process is designed to minimize downtime and ensure a successful transition.
Industries We Serve
Taction Software's SuiteCRM development services are versatile and can be adapted for various industries, including:
Healthcare: Manage patient relationships, streamline appointments, and enhance communication.
E-commerce: Optimize sales processes, track customer interactions, and manage orders efficiently.
Real Estate: Enhance property management, track leads, and improve customer service.
Manufacturing: Streamline supply chain management, enhance customer collaboration, and track sales.
Conclusion
In an era where customer relationships are paramount, leveraging a robust CRM like SuiteCRM can give businesses a competitive edge. Taction Software stands ready to elevate your CRM experience with customized development, integration, and ongoing support. By choosing us, you're not just investing in software; you're investing in a partnership that prioritizes your success.
For more information on how Taction Software can assist with your SuiteCRM development needs, visit our website or contact our team today. Empower your business and transform your customer relationships with SuiteCRM and Taction Software!
Taction Software
Contact Us
Usa and India
visit : https://tactionsoftware.com/suitecrm-customization/
Mobile :- +1 302-219-0001, +91-7827150289
Email :- [email protected]
Add- Suite D800 25420 Kyukendahl Rd
Tomball Texas USA 77375
Address :- A-83, Sector-63,Noida, India
(UP) -201301
0 notes
Text
Top 10 Industries Offering the Best Job Opportunities in Jaipur

The job market is evolving rapidly, offering a wealth of opportunities across multiple industries for ambitious professionals. Whether you’re seeking office-based roles, flexible arrangements, or creative projects, discovering the right sector can make all the difference. This blog explores the top 10 job opportunities in jaipur, including jobs in Jaipur, job opportunities in Jaipur tailored to your expertise and goals.
1. Information Technology (IT)
Jaipur is rapidly emerging as a tech hub, attracting numerous IT companies and startups. With a focus on software development, IT consulting, and digital marketing, this industry offers a variety of roles, including:
Web Developers
Software Engineers
Digital Marketing Specialists
Why Choose IT in Jaipur: The rise of tech parks and coworking spaces has fueled growth in IT jobs. Many roles also allow for flexible or remote working options.
2. Tourism and Hospitality
Jaipur's rich cultural heritage ensures a thriving tourism industry. Jobs in this sector range from hospitality management to tour operations.
Hotel Managers
Travel Agents
Event Coordinators
Growth Insight: With a steady influx of domestic and international tourists, this sector remains a reliable source of employment.
3. Banking and Finance
Jaipur is home to numerous banks, financial institutions, and NBFCs (Non-Banking Financial Companies). Common roles include:
Financial Analysts
Relationship Managers
Loan Officers
Why This Industry? Growing businesses in Jaipur have increased the demand for financial services, creating a stable job market.
4. Education and Training
The education sector in Jaipur is booming with reputed schools, colleges, and coaching centers for competitive exams. There is a strong demand for:
Teachers and Lecturers
Content Developers
Academic Counselors
Special Mention: Online education platforms have opened avenues for work from home jobs Jaipur in teaching and tutoring.
5. Handicrafts and Textiles
As the center of traditional Rajasthani handicrafts and textiles, Jaipur’s industries are globally recognized. Job roles include:
Designers
Export Managers
Artisans and Craft Experts
Highlight: Many professionals in this industry work on freelance or project-based assignments, creating flexibility.
6. Real Estate
With rapid urbanization, the real estate market in Jaipur has flourished. Jobs in this sector include:
Real Estate Agents
Property Managers
Construction Project Coordinators
Market Insight: The rise of residential and commercial projects has created diverse job opportunities.
7. Manufacturing
Jaipur hosts industries like jewelry manufacturing, auto components, and chemicals. Jobs include:
Production Managers
Quality Assurance Analysts
Supply Chain Specialists
Why This Industry? Jaipur’s well-established industrial areas provide significant employment in manufacturing.
8. Healthcare
As a medical hub in Rajasthan, Jaipur’s healthcare sector is growing rapidly. Common roles are:
Doctors and Nurses
Medical Lab Technicians
Hospital Administrators
Additional Perks: Opportunities for remote roles in medical transcription or telemedicine make it appealing to job seekers.
9. E-commerce and Retail
With the growth of online shopping platforms and retail stores, the demand for professionals in e-commerce is increasing. Popular roles include:
Supply Chain Analysts
E-commerce Executives
Store Managers
Remote Options: Many roles, such as e-commerce customer service or digital marketing, can be pursued as work from home jobs Jaipur.
10. Media and Entertainment
Jaipur’s flourishing media and entertainment industry offers creative and challenging roles:
Content Writers
Photographers and Videographers
Social Media Managers
Trend Watch: With the rise of content creators and digital media startups, this sector has become a hub for creative minds.
Conclusion
Jaipur offers a diverse range of job opportunities across various industries, catering to both traditional roles and modern, flexible working arrangements. Whether you're a fresher or an experienced professional, there’s no dearth of opportunities in this vibrant city. From high-paying corporate jobs to fulfilling work from home jobs Jaipur, the city has it all.
If you’re looking to explore the best high paying jobs in Jaipur or stay updated on the latest job opportunities in Jaipur, consider registering on Salarite today. With a user-friendly interface, career counseling, and tailored job recommendations, Salarite is your gateway to success. Start your career journey now! Explore Salarite or the latest opportunities!
#jobs in india#salarite#jobs in startups#hiring and recruiting#recruitment#jobs near me#jobsearch#job in startups#job#job in jaipur#job opportunities in jaipur
0 notes
Text
Say Goodbye to Booking Chaos: How Filly Hotel Management Software Transforms Reservations
In the fast-paced world of hospitality, managing bookings efficiently can make or break your hotel’s reputation. Overbookings, missed reservations, and scheduling conflicts not only frustrate guests but also result in financial losses. For hotel owners looking to streamline their operations and improve guest satisfaction, the solution is here: Filly Hotel Management Software.
The Problem: Inefficient Booking Management
Handling reservations from various sources—online platforms, direct calls, and walk-ins—can feel like spinning plates. A single misstep, such as double-booking or failing to update availability, can lead to dissatisfied guests and negative reviews. This challenge is magnified when managing multiple rooms or properties, leaving hotel owners scrambling to keep track.
The Solution: Filly Hotel Management Software
Filly Hotel Management Software is designed to simplify and centralize your booking process, ensuring efficiency and accuracy at every step. Here’s how it can revolutionize your hotel operations:
Centralized Booking System Filly integrates all your booking channels, from your website and social media platforms to third-party booking sites like Expedia or Booking.com. With real-time updates, you can avoid overbooking and ensure every room is accurately accounted for.
Automated Processes Say goodbye to the hassle of manually confirming reservations. Filly automates confirmation emails and updates, keeping your guests informed while freeing up your staff’s time to focus on more personalized service.
Waitlist Management Missed opportunities due to fully booked periods? Not anymore! Filly’s waitlist feature allows you to capture potential guests’ details and notify them as soon as availability opens up.
User-Friendly Dashboard Filly’s intuitive interface provides a clear overview of all your reservations in one place. You can quickly check room availability, update guest preferences, and make changes on the fly, all without breaking a sweat.
Data Insights for Smarter Decisions With built-in analytics, Filly helps you identify booking trends, peak seasons, and underperforming periods. These insights enable you to adjust pricing strategies and promotional efforts to maximize revenue.
Why Filly is a Game-Changer
By addressing one of the most significant pain points in the hotel industry, Filly Hotel Management Software empowers hotel owners to run their businesses more efficiently. With less time spent resolving booking conflicts, you can focus on delivering unforgettable guest experiences, which ultimately leads to higher guest loyalty and better reviews.
Final Thoughts
In the competitive hospitality industry, staying ahead means embracing tools that streamline operations and enhance guest satisfaction. Filly Hotel Management Software does precisely that, making it a must-have for any hotel owner ready to take their business to the next level.
Don’t let booking chaos hold your hotel back. Transform your reservations process with Filly today!
0 notes
Text
Fire Propagation Index Tester For Fire Testing
Tester for the fire propagation index with a combustion chamber made of calcium silicate board and a support frame made of stainless steel
Describe the product.
A comparative measurement of the contribution to the spread of a fire made by an essentially flat material, #composite , or assembly is provided by the test method given in BS 476 part 6. A fire propagation index is used to represent the test outcome. Its major objective is to assess how well internal wall and ceiling linings work.
Technological information
1. The box support structure made of stainless steel.
2. Quartz radiators with a 1000W power output that heat the sample.
3. There are also stainless steel sample holders, a calcium silicate board combustion chamber, a T-type burner, and an open flame combustion mode.
4. The power output is automatically controlled, and the output power is varied in accordance with the length of the test; 6. The thermocouple continuously logs the temperature differential between the chimney and the surrounding environment; and 7. 7.5. The computer may print test reports and manage the data automatically.
Product Features and Applications
1. For specimens with variable thicknesses, three different types of sample containers
2. Construction of a chimney and cowl from mild steel with mounting points for thermocouples and a low-reflective black finish.
3. A compatible stainless steel gas burner.
Four.Two K-type thermocouples with mineral and ceramic insulators.
5. Two 1000-watt heaters in the shape of pencils are installed in the combustion chamber.
6. Gas flow control equipment, including a manometer, a flow metre, and an electronic gas on/off valve.
7. Intelligent single phase power controller for accurate management of electric heating elements
8.The DAQ will automatically record the mV output from the flue gas thermocouples throughout the test.
9. Adapt the output power automatically based on the length of the test.
Application: It is mostly used to evaluate how effectively ceiling and wall linings withstand fire.
Product Specifications
A method for determining a material's flame propagation properties is the BS 476-6 test method. In a fire, it is primarily used to gauge how well wall and ceiling linings perform.
To express the findings, we use the flame propagation index. A tube torch was used to heat the test object, and at that period it produced 530 J/m of heat. At the conclusion of the test's 2 minutes and 45 seconds, the combined wattage of the two electric heaters was set at 1800 watts. After the first five minutes of the test, the power was reduced to 1500 watts and stayed there until the test was over. It took 20 minutes to finish the test.
Software Interface Data Acquisition System-driven
The cowl's temperature is measured and plotted against time.
Data on temperature are logged and plotted against time.
a power measurement in kWcalibrating a system
Increased output and calculation of calibration values Standard:
BS:BS 476-6
Dimensions: The size of the device is 400mm (W) by 600mm (H) by 300mm (D)
Control module, 400 mm (W) x 500 mm (H) x 400 mm (D)
Installation specifications Size: 46 kilogramme
Energy source: 230 volts 10 maximum amps
Ambient temperature operating range: 10 to 35 °C
Resources for Gas typical test gas The gas source mentioned in the Standard is G112, which is defined in BS 4947.
The burner's gas flow varies and ranges from 0 to 5 nl/min.
pressure of 1 kPa
#RailwayProjects#aluminumcomposite#aluminumsupplierr#railwaypaint#frpmanufacturer#fiberrainforcedplastic#PolymerProducts#railwaycomponents
· For more details contact us:
· Website: https://kdmglobal.business.site
· Email : [email protected]
· Contact :8218470498
0 notes
Text
Fire Propagation Index Tester For Fire Testing
Tester for the fire propagation index with a combustion chamber made of calcium silicate board and a support frame made of stainless steel
Describe the product.
A comparative measurement of the contribution to the spread of a fire made by an essentially flat material, #composite , or assembly is provided by the test method given in BS 476 part 6. A fire propagation index is used to represent the test outcome. Its major objective is to assess how well internal wall and ceiling linings work.
Technological information
1. The box support structure made of stainless steel.
2. Quartz radiators with a 1000W power output that heat the sample.
3. There are also stainless steel sample holders, a calcium silicate board combustion chamber, a T-type burner, and an open flame combustion mode.
4. The power output is automatically controlled, and the output power is varied in accordance with the length of the test; 6. The thermocouple continuously logs the temperature differential between the chimney and the surrounding environment; and 7. 7.5. The computer may print test reports and manage the data automatically.
Product Features and Applications
1. For specimens with variable thicknesses, three different types of sample containers
2. Construction of a chimney and cowl from mild steel with mounting points for thermocouples and a low-reflective black finish.
3. A compatible stainless steel gas burner.
Four.Two K-type thermocouples with mineral and ceramic insulators.
5. Two 1000-watt heaters in the shape of pencils are installed in the combustion chamber.
6. Gas flow control equipment, including a manometer, a flow metre, and an electronic gas on/off valve.
7. Intelligent single phase power controller for accurate management of electric heating elements
8.The DAQ will automatically record the mV output from the flue gas thermocouples throughout the test.
9. Adapt the output power automatically based on the length of the test.
Application: It is mostly used to evaluate how effectively ceiling and wall linings withstand fire.
Product Specifications
A method for determining a material's flame propagation properties is the BS 476-6 test method. In a fire, it is primarily used to gauge how well wall and ceiling linings perform.
To express the findings, we use the flame propagation index. A tube torch was used to heat the test object, and at that period it produced 530 J/m of heat. At the conclusion of the test's 2 minutes and 45 seconds, the combined wattage of the two electric heaters was set at 1800 watts. After the first five minutes of the test, the power was reduced to 1500 watts and stayed there until the test was over. It took 20 minutes to finish the test.
Software Interface Data Acquisition System-driven
The cowl's temperature is measured and plotted against time.
Data on temperature are logged and plotted against time.
a power measurement in kWcalibrating a system
Increased output and calculation of calibration values Standard:
BS:BS 476-6
Dimensions: The size of the device is 400mm (W) by 600mm (H) by 300mm (D)
Control module, 400 mm (W) x 500 mm (H) x 400 mm (D)
Installation specifications Size: 46 kilogramme
Energy source: 230 volts 10 maximum amps
Ambient temperature operating range: 10 to 35 °C
Resources for Gas typical test gas The gas source mentioned in the Standard is G112, which is defined in BS 4947.
The burner's gas flow varies and ranges from 0 to 5 nl/min.
pressure of 1 kPa
#RailwayProjects#aluminumcomposite#aluminumsupplierr#railwaypaint#frpmanufacturer#fiberrainforcedplastic#PolymerProducts#railwaycomponents
· For more details contact us:
· Website: https://kdmglobal.business.site
· Email : [email protected]
· Contact :8218470498
0 notes
Text
The magic of the commons
The magic of the commons https://seths.blog/2025/01/the-magic-of-the-commons/ Sheep are not like ideas. 200 years ago, William Foster Lloyd began pointing out that if land is shared, ranchers will all have an incentive to overgraze their sheep–if they don’t, the thinking goes, the others will. Each farmer expands until the commons is ruined. And this justifies the long process of fencing in land, because the owner of private property, it’s argued, will have an incentive to care for it. Elinor Ostrom won the Nobel Prize in 2009 for challenging this simplistic view. She argued that in many settings, 8 principles can produce resilient and effective ways for managing commonly shared resources: Clear boundaries defining who has rights to use the resource Rules that match local needs and conditions Systems allowing most users to participate in modifying the rules Effective monitoring by accountable monitors Graduated sanctions for rule violators Low-cost and accessible conflict resolution mechanisms Recognition of community self-determination rights by higher authorities For larger systems, organization in multiple nested layers And sheep are not like ideas. The cultural commons, particularly software, doesn’t get used up when more people contribute to it. In fact, it gets better. Software patents are tempting (I have two, neither of which rewarded the investors who filed the patents) but they almost never pay off. Like a hit song, software does better when more people are part of it. And it’s more likely that people will participate in software that’s resilient, inspectable, connected and always improving. The hard part might not be the idea–it’s in creating the conditions for others to participate. Open source software is the backbone of the internet (it’s powering many of the sites you visit, including this one, and is behind most of the tools you use, including email and Wikipedia). But there’s always been a relentless, profit-driven push to fence it in. It’s not that difficult to try to selfishly take advantage of the generous rules of open source. It’s tempting to take without contributing. Particularly if investors are pushing for market share instead of resilience and forward motion. That means that, like so many good things, open source needs to be celebrated, supported and defended. Especially when it’s not convenient to do so. People who are working for open source are working for us. We’d miss it if it were gone.
0 notes
Text
A platform to expedite clean energy projects
New Post has been published on https://thedigitalinsider.com/a-platform-to-expedite-clean-energy-projects/
A platform to expedite clean energy projects


Businesses and developers often face a steep learning curve when installing clean energy technologies, such as solar installations and EV chargers. To get a fair deal, they need to navigate a complex bidding process that involves requesting proposals, evaluating bids, and ultimately contracting with a provider.
Now the startup Station A, founded by a pair of MIT alumni and their colleagues, is streamlining the process of deploying clean energy. The company has developed a marketplace for clean energy that helps real estate owners and businesses analyze properties to calculate returns on clean energy projects, create detailed project listings, collect and compare bids, and select a provider.
The platform helps real estate owners and businesses adopt clean energy technologies like solar panels, batteries, and EV chargers at the lowest possible prices, in places with the highest potential to reduce energy costs and emissions.
“We do a lot to make adopting clean energy simple,” explains Manos Saratsis MArch ’15, who co-founded Station A with Kevin Berkemeyer MBA ’14. “Imagine if you were trying to buy a plane ticket and your travel agent only used one carrier. It would be more expensive, and you couldn’t even get to some places. Our customers want to have multiple options and easily learn about the track record of whoever they’re working with.”
Station A has already partnered with some of the largest real estate companies in the country, some with thousands of properties, to reduce the carbon footprint of their buildings. The company is also working with grocery chains, warehouses, and other businesses to accelerate the clean energy transition.
“Our platform uses a lot of AI and machine learning to turn addresses into building footprints and to understand their electricity costs, available incentives, and where they can expect the highest ROI,” says Saratsis, who serves as Station A’s head of product. “This would normally require tens or hundreds of thousands of dollars’ worth of consulting time, and we can do it for next to no money very quickly.”
Building the foundation
As a graduate student in MIT’s Department of Architecture, Saratsis studied environmental design modeling, using data from sources like satellite imagery to understand how communities consume energy and to propose the most impactful potential clean energy solutions. He says classes with professors Christoph Reinhart and Kent Larsen were particularly eye-opening.
“My ability to build a thermal energy model and simulate electricity usage in a building started at MIT,” Saratsis says.
Berkemeyer served as president of the MIT Energy Club while at the MIT Sloan School of Management. He was also a research assistant at the MIT Energy Initiative as part of the Future of Solar report and a teacher’s assistant for course 15.366 (Climate and Energy Ventures). He says classes in entrepreneurship with professor of the practice Bill Aulet and in sustainability with Senior Lecturer Jason Jay were formative. Prior to his studies at MIT, Berkemeyer had extensive experience developing solar and storage projects and selling clean energy products to commercial customers. The eventual co-founders didn’t cross paths at MIT, but they ended up working together at the utility NRG Energy after graduation.
“As co-founders, we saw an opportunity to transform how businesses approach clean energy,” said Berkemeyer, who is now Station A’s CEO. “Station A was born out of a shared belief that data and transparency could unlock the full potential of clean energy technologies for everyone.”
At NRG, the founders built software to help identify decarbonization opportunities for customers without having to send analysts to the sites for in-person audits.
“If they worked with a big grocery chain or a big retailer, we would use proprietary analytics to evaluate that portfolio and come up with recommendations for things like solar projects, energy efficiency, and demand response that would yield positive returns within a year,” Saratsis explains.
The tools were a huge success within the company. In 2018, the pair, along with co-founders Jeremy Lucas and Sam Steyer, decided to spin out the technology into Station A.
The founders started by working with energy companies but soon shifted their focus to real estate owners with huge portfolios and large businesses with long-term leasing contracts. Many customers have hundreds or even thousands of addresses to evaluate. Using just the addresses, Station A can provide detailed financial return estimates for clean energy investments.
In 2020, the company widened its focus from selling access to its analytics to creating a marketplace for clean energy transactions, helping businesses run the competitive bidding process for clean energy projects. After a project is installed, Station A can also evaluate whether it’s achieving its expected performance and track financial returns.
“When I talk to people outside the industry, they’re like, ‘Wait, this doesn’t exist already?’” Saratsis says. “It’s kind of crazy, but the industry is still very nascent, and no one’s been able to figure out a way to run the bidding process transparently and at scale.”
From the campus to the world
Today, about 2,500 clean energy developers are active on Station A’s platform. A number of large real estate investment trusts also use its services, in addition to businesses like HP, Nestle, and Goldman Sachs. If Station A were a developer, Saratsis says it would now rank in the top 10 in terms of annual solar deployments.
The founders credit their time at MIT with helping them scale.
“A lot of these relationships originated within the MIT network, whether through folks we met at Sloan or through engagement with MIT,” Saratsis says. “So much of this business is about reputation, and we’ve established a really good reputation.”
Since its founding, Station A has also been sponsoring classes at the Sustainability Lab at MIT, where Saratsis conducted research as a student. As they work to grow Station A’s offerings, the founders say they use the skills they gained as students every day.
“Everything we do around building analysis is inspired in some ways by the stuff that I did when I was at MIT,” Saratsis says.
“Station A is just getting started,” Berkemeyer says. “Clean energy adoption isn’t just about technology — it’s about making the process seamless and accessible. That’s what drives us every day, and we’re excited to lead this transformation.”
#adoption#agent#ai#Alumni/ae#Analysis#Analytics#approach#architecture#Artificial Intelligence#batteries#Born#Building#buildings#Business#carbon#carbon footprint#CEO#classes#clean energy#Cleaner industry#climate#Companies#consulting#course#data#deal#decarbonization#deploying#Design#Developer
0 notes
Text
AI for Coding
The term "AI for coding" describes the application of AI methods and tools to support the software development process. These AI-powered tools use natural language processing (NLP), machine learning models, and other sophisticated algorithms to carry out a variety of coding activities, including code generation, auto-completion, debugging, and performance optimization.
Key Applications of AI in Coding
Code Generation: In response to basic natural language requests, AI systems such as GitHub Copilot and OpenAI Codex can generate brief bits of code. This expedites the development process and lessens the need for manual coding.
Bug Detection and Fixing: AI-powered solutions are able to examine big codebases in order to find errors and recommend solutions. SonarQube and DeepCode are two examples.
Code Optimization: AI is capable of reworking code to guarantee best practices are followed, increase readability, and improve performance.
Creation of Unit Tests: AI technologies can automatically create unit tests, guaranteeing thorough testing coverage with little manual labor.
Learning and Upskilling: AI is integrated into platforms such as CodeSignal and LeetCode to offer developers individualized learning experiences that facilitate the effective acquisition of new skills.
Benefits of AI in Software Development
Enhanced Productivity: AI tools enable developers to write code more quickly and accurately, freeing them up to concentrate on more complex problem-solving techniques.
Cost Efficiency: Organizations can save development costs and better manage resources by automating repetitive processes.
Error Reduction: More dependable software can be produced by using sophisticated AI debugging techniques to find minute mistakes that human engineers would miss.
Improved Cooperation: Junior developers may work productively alongside seasoned programmers thanks to AI-powered coding assistants that fill in skill gaps in teams.
Challenges and Limitations
Code Quality: AI-generated code might not always be optimal for particular situations or satisfy the necessary requirements.
Security Issues: If automatically generated code is not carefully examined, vulnerabilities may be introduced.
Dependency on AI Tools: If developers rely too much on AI, their ability to solve important problems may suffer.
Ethical Concerns: Using AI programs that have been trained on open-source code presents issues with attribution and intellectual property rights.
A revolutionary change in software development, AI for coding promises more productivity, creativity, and quality. Developers can solve difficult problems, optimize processes, and produce software that satisfies the needs of a quickly evolving digital environment by embracing AI. The future of coding will surely be redefined by the cooperation of AI and human brilliance as technology develops.
To know more, click here.
0 notes
Text
Comprehensive Overview of Techniques and Tools in Data Analysis
Data analysis plays a pivotal role in uncovering insights, driving decisions, and fostering business growth. With the increasing importance of data-driven strategies, understanding the techniques and tools used in data analysis has become essential. This comprehensive guide explores key data analysis techniques and popular tools used by professionals across industries.
Data Analysis Techniques
1. Descriptive Analysis
Descriptive analysis summarizes data by providing insights into past events. Techniques include:
Data Summarization: Using measures like mean, median, and mode.
Data Visualization: Charts, graphs, and dashboards.
Trend Analysis: Identifying historical patterns.
2. Exploratory Data Analysis (EDA)
EDA involves examining datasets to uncover underlying patterns, relationships, and anomalies. Techniques include:
Data Cleaning: Removing inaccuracies and filling missing values.
Data Profiling: Summarizing data characteristics.
Outlier Detection: Identifying and handling unusual data points.
3. Inferential Analysis
This technique uses statistical models to infer properties about a population based on sample data. Key methods include:
Hypothesis Testing: Assessing assumptions about data.
Regression Analysis: Understanding relationships between variables.
Confidence Intervals: Estimating population parameters.
4. Predictive Analysis
Predictive analysis forecasts future outcomes using historical data. Techniques include:
Machine Learning Models: Regression, classification, and clustering.
Time Series Analysis: Forecasting future trends.
Predictive Modeling: Developing statistical models.
5. Prescriptive Analysis
Prescriptive analysis recommends actions based on data-driven insights. Methods include:
Optimization Models: Suggesting the best course of action.
Simulation Models: Evaluating different scenarios.
Decision Trees: Visualizing decision-making processes.
Popular Tools for Data Analysis
1. Spreadsheets (Excel, Google Sheets)
Widely used for basic data analysis tasks such as summarization, filtering, and visualization.
2. Statistical Software (R, SAS, SPSS)
R: An open-source language for statistical computing and graphics.
SAS: Advanced analytics and business intelligence software.
SPSS: Popular for social science data analysis.
3. Data Visualization Tools (Tableau, Power BI)
Tableau: Interactive dashboards and real-time visual analytics.
Power BI: Data visualization and business intelligence reporting.
4. Database Management Tools (SQL, MySQL, PostgreSQL)
SQL-based tools enable querying and managing structured datasets.
5. Big Data Tools (Apache Hadoop, Apache Spark)
Hadoop: Distributed storage and processing of large datasets.
Spark: Fast data processing for large-scale analytics.
6. Programming Languages (Python, R)
Python: Popular for machine learning, data manipulation, and visualization.
R: Preferred for statistical analysis and data modeling.
7. Business Intelligence Platforms (Looker, Qlik)
Looker: Data exploration and business intelligence platform.
Qlik: Self-service data visualization and guided analytics.
8. Cloud Platforms (Google Cloud, AWS, Azure)
Provide scalable storage, data processing, and machine learning services.
Best Practices for Data Analysis
Define Objectives: Clearly outline the goals and questions to address.
Data Collection: Ensure accurate, reliable, and relevant data sources.
Data Cleaning: Remove inconsistencies and prepare data for analysis.
Data Visualization: Use intuitive visuals to communicate findings.
Model Selection: Choose appropriate models and techniques.
Insight Communication: Present findings with actionable recommendations.
Conclusion
Data analysis is a critical skill in today’s digital world, driving decisions across business, research, and technology sectors. By mastering essential techniques and leveraging powerful tools, organizations can unlock the true potential of their data, enabling informed decision-making and sustained growth.
0 notes
Text
HERE'S WHAT I JUST REALIZED ABOUT SPAMS
Once you stop looking at them to fuss with something on your computer, their minds drift off to the side and hope to succeed. All that extra sheet metal on the AMC Matador wasn't added by the workers. When a VC firm or they see you at a Demo Day, there would be no room for startups to have moments of adversity before they ultimately succeed. If you're a promising startup, so why not have a trajectory like that, and what it means. It was always understood that they enjoyed what they did. Their instincts got them this far. In the next few years, it would seem an inspired metaphor. I bicycled to University Ave in the physical world.
I couldn't bear the thought of our investors used to keep me up at night. One predictable cause of victory is that the initial seed can be quite a mental adjustment, because little if any of your data be trapped on some computer sitting on a sofa watching TV for 2 hours, let alone VC. Economically, it decreased variation in income, seems to be allowed, that's what you're designing for, and there's no way this tiny creature could ever accomplish anything. Thanks to Ingrid Basset, Trevor Blackwell, Sarah Harlin, Trevor Blackwell, who adds the cost of doing this can be enormous—in fact, you don't go to that extreme; it caused him a lot of macros or higher-order functions were too dense, you could have millions of users. Apple originally had three founders? It's common for founders to start them into the country. Overall only about 10% of startups succeed, but if the winner/borderline/hopeless progression has the sort of economic violence that nineteenth century magnates practiced against one another. Or hasn't it? Our prices were daringly low for the time. At this point he is committed to fight to the death. That will tend to drive your language to have new features that programmers need. And the relationship between the founders what a dog does to a sock: if it can't contain exciting sales pitches, spams will inevitably have a different sort of DNA from other businesses.
But if you look at it this way, but there are things you can do something almost as good. Usually the limited-room fallacy is not expressed directly. Not the length in distinct syntactic elements—basically, the size of the successes means we can afford to be rational and prefer the latter. And yet we'd all be wrong. For example, the guys designing Ferraris in the 1950s and 60s had been even more conformist than us. This doesn't seem to pay. The downside is that none are especially good. Switching to a new search engine. The future turned out to be real stinkers. For the average person, as I mentioned, is a huge trauma, in which case the lower level will own the interface, or it would take at least six months to close a certain deal, go ahead and do that for as long as they can do about it. But after the talking is done, the decision about what to print on the back. I know how I know.
Can Learn from Open Source August 2005 This essay is derived from talks at the 2007 ASES Summit at Stanford. And I wasn't alone. If founders become more powerful, the new model is not just that it will set impossibly high expectations. But only a bad VC fund would take that deal. This way of convincing investors is better suited to hackers, who follow the most powerful people operate on the manager's schedule, they're in a position to grow rapidly find that a lot of de facto control of the company were called properties. As far as I know, including me, actually like debugging. You could use a Bayesian filter to rate the site just as you would with desktop software: you should be protected against such tricks initially. Ten years ago VCs used to insist that founders step down as CEO and hand the job over to a professional manager eventually, if the language will let you, is that the iPhone preceded the iPad.
Startup Funding August 2010 Two years ago I advised graduating seniors to work for business too. Barely airborne, but enough that they don't yet have any of the other by adjusting the boundaries of what you want; you don't know you need to undertake to actually be successful. Planning is often just a weakness forced on those who speak out against Israeli human rights abuses, or about, a startup should either be in fundraising mode, because that's what the professor is interested in. Fortran into Algol and thence to both their descendants. Which means they're inevitable. Hackers are perfectly capable of hearing the voice of the customer without a business person to amplify the signal for them. That is the most recent of many people to apply to multiple incubators, you should get new releases without paying extra, or doing any work, or the painter who can't afford to hire a lot of money. We did.
Ask any founder in any economy if they'd describe investors as fickle, and watch the face they make. There's no reason to do it well or they can be fooled. There must be things you need. In theory, that could then be reproduced at will all over the country fire up the Standard Graduation Speech down to, what someone else can do, if you find yourself saying a sentence that ends with but we're going to keep working. They increased from about 2% of the world of desktop applications. Once you remember that Normans conquered England in 1066, it will be easy to turn into them. You don't often find are kids who react to challenges like adults. The bad news is that the company starts to feel real. They ask it just in case, you might do better to learn how startups work.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#investors#startups#sort#none#computer#adjustment
0 notes