#online education in india
Explore tagged Tumblr posts
Text
Transform your CBSE learning experience with Edument Online's premier CBSE tuition in India. Our specialized courses, led by experienced instructors, ensure comprehensive coverage of CBSE curriculum standards. Join a vibrant educational community committed to excellence. Edument Online: Your trusted destination for CBSE tuition in India, shaping the path to academic success.
#indian online school#montessori teacher training online#cbse virtual school in india#best online schools in india#india's best online school#cbse online schools in india#online school education in india#best virtual school in india#online education in india#top online schools in india#cbse tution#Cbse tution online
0 notes
Text
Discover the excellence of Edument Online, India's best online school in the UAE. Empower your child's education with our comprehensive curriculum, experienced teachers, and interactive learning platform. We bring the finest educational resources from India directly to your home, ensuring a world-class education for your child. With our flexible schedules, personalized attention, and engaging online classes, Edument Online provides a nurturing and stimulating environment for your child's academic growth. Join our esteemed community of learners and witness the transformative power of India's best online school in the UAE. Enroll your child with Edument Online today and unlock their full potential!
#CBSE Virtual School in India#Online School Education in India#Online Education in India#India's Best Online School#Best Virtual School in India#Virtual School Education India#CBSE Online Schools in India#Best Online Schools in India#Indian Online School#Top Online Schools in India
0 notes
Text
Vignan Online launches ‘VISA’, Vignan’s integrated support & assistance platform
Vignan Online, the e-learning arm of Vignan’s Foundation for Science, Technology, and Research (Deemed-to-be University), Guntur, has announced the launch of Vignan’s Integrated Support and Assistance (VISA). The learner support and assistance platform aims to provide an immersive experience for the learners enrolled in Online Degree from Vignan Online.
#onlinedegree, #onlineeducationinindia, #Onlinedegreeadmissions, #onlinegraduationcourses, #onlinedegreecertificates, #onlineeducation
https://bit.ly/40VJTXz
#online degree#online education in india#Online degree admissions#online graduation courses#online degree certificates#online education
0 notes
Text

Follow your Passion with Distance or Online Education. Visit Us
Boost your education and career with Distance or Online Education from Manav Rachna Online. Enrol now for a better career upgrade.
#online education#online degree#online degree certificates#online education in India#distance education courses#degree distance education
1 note
·
View note
Text
#online degree#online education in india#Online degree admissions#online graduation courses#online degree certificates
1 note
·
View note
Text
RTI Application Insights for Public Welfare
Registration NumberDIRSW/R/2024/60158NameYogi M P SinghDate of Filing22/11/2024StatusRTI REQUEST RECEIVED as on 22/11/2024 PIO Details PIO NAMEVIKAS SECTION SURESH KUMAR APIO HQDesignationS.O. HQ APIO VIKAS SECTIONPhone No.9415548092Email [email protected] Nodal Officer Details [email protected] Online RTI Request Form Details Public Authority…
#director social welfare#Directorate social welfare#education#india#news#NPCI server#scholarships#website of scholarship and fee reimbursement online system
7 notes
·
View notes
Text
Grievance Process for MGKVP University Students
Grievance Status for registration number : GOVUP/E/2024/0092467Grievance Concerns ToName Of ComplainantMahesh Pratap Singh alias Yogi M. P. SinghDate of Receipt17/12/2024Received By Ministry/DepartmentUttar PradeshGrievance DescriptionThe matter concerns the working of the registrar and examination controller of Mahatma Gandhi Kashi Vidya Pith university Varanasi.Most respected Sir, this…
#education#history#india#MGKVP Varanasi#news#online examination forrm submission#scholarship#Student data not found
3 notes
·
View notes
Text
The Ethics of Hacking: Understanding White Hat vs. Black Hat Hackers

Introduction: Ethical Boundaries in the World of Hacking
In the digital age, hacking has become a term with both negative and positive connotations. Hackers are often categorized based on their intentions, which primarily distinguish between two main groups: White Hat hackers and Black Hat hackers. Understanding the ethical boundaries of hacking is critical, especially as cybersecurity becomes more crucial for protecting sensitive data and infrastructure. This article explores the roles, techniques, and motivations behind White Hat and Black Hat hackers, examining their ethical implications in today’s tech-driven world.https://internshipgate.com
Who Are White Hat Hackers?
Defining White Hat Hackers: The Ethical Cybersecurity Warriors
White Hat hackers are cybersecurity professionals who use their skills to detect and fix vulnerabilities in networks, systems, and applications. These ethical hackers work to strengthen security measures, ensuring that malicious hackers cannot exploit weaknesses. They often collaborate with organizations, governments, and security agencies to maintain digital safety.
Key characteristics of White Hat hackers include:
Authorization: White Hat hackers operate with explicit permission from organizations or system owners to test their defenses.
Intentions: Their goal is to protect, not harm. They are motivated by the desire to improve security systems and help others.
Methodology: White Hat hackers use penetration testing, vulnerability assessments, and ethical hacking techniques that adhere to legal and ethical standards.
The Role of White Hat Hackers in Cybersecurity
White Hat hackers are vital in maintaining the security of modern digital infrastructure. Their work helps identify system weaknesses before malicious hackers can exploit them, making them essential allies in the fight against cybercrime.
Who Are Black Hat Hackers?
Black Hat Hackers: The Dark Side of Cyber Intrusion
Black Hat hackers, in contrast, operate outside the bounds of legality and ethical standards. These individuals engage in malicious activities such as stealing data, spreading malware, and damaging systems for personal gain or to inflict harm.
Common traits of Black Hat hackers:
Unauthorized Access: Black Hat hackers gain access to systems without permission, often exploiting vulnerabilities for illegal purposes.
Malicious Intent: Their actions are driven by greed, personal vendettas, or a desire to cause disruption.
Tactics: Black Hat hackers use techniques like phishing, malware, ransomware, and DDoS attacks to compromise systems and extract sensitive data.
Impact of Black Hat Hackers on the Digital World
The damage caused by Black Hat hackers is significant, ranging from financial losses to the destruction of critical infrastructure. Their activities have spurred the development of more sophisticated security systems and the recruitment of skilled White Hat hackers to combat these threats.
Gray Hat Hackers: The Ambiguity in Between
Understanding Gray Hat Hackers
While the dichotomy of White Hat and Black Hat hackers is well-known, there is also a third category: Gray Hat hackers. These individuals often operate in the ethical gray zone, performing unauthorized activities but without malicious intent.
Key attributes of Gray Hat hackers:
Semi-Legal Actions: Gray Hat hackers may break into systems without permission but do so to highlight vulnerabilities, sometimes informing the affected parties afterward.
Unpredictable Ethics: Their motivations are complex and may not always align with traditional ethical standards. Some Gray Hat hackers see themselves as vigilantes, believing their actions benefit the greater good.
Gray Hat Hackers: Beneficial or Harmful?
While Gray Hat hackers may not aim to cause harm, their activities can still be illegal and dangerous. By exploiting vulnerabilities without permission, they can inadvertently open doors for malicious attackers to follow.
The Ethical Debate: When Does Hacking Become Acceptable?
The ethical debate surrounding hacking revolves around the intent and outcomes of the hacker’s actions. White Hat hackers operate within ethical frameworks, while Black Hat hackers violate laws and norms. The challenge with Gray Hat hackers lies in determining whether their actions, although often without malicious intent, should be condoned or condemned.
Key Ethical Questions:
Is unauthorized access ever justifiable?
Do the benefits of exposing vulnerabilities outweigh the risks?
Should Gray Hat hackers face the same legal consequences as Black Hat hackers?
The answers to these questions are complex, but they underline the importance of a clear ethical code for cybersecurity professionals and hackers alike.
Legal Consequences of Hacking: White Hat vs. Black Hat
Legal Protections for White Hat Hackers
White Hat hackers, when operating under contracts or legal agreements, are typically protected by law. Their activities are not only ethical but also sanctioned, as they work with the consent of organizations to improve their security.
Legal Risks for Black Hat Hackers
Black Hat hackers, on the other hand, face severe legal consequences for their actions. Unauthorized access, data theft, and cyberattacks are illegal in most jurisdictions, with penalties ranging from hefty fines to long-term imprisonment.
Legal differences between White Hat and Black Hat hacking:
White Hat Hackers: Operate within the boundaries of the law, often employed by cybersecurity firms or government agencies.
Black Hat Hackers: Engage in illegal activities that violate data privacy, cyber laws, and intellectual property rights.
The Importance of Ethical Hacking in Today’s World
As digital infrastructure becomes more integral to every facet of modern life, the importance of ethical hacking cannot be overstated. White Hat hackers play a critical role in safeguarding the internet, preventing data breaches, and protecting personal and organizational assets from cyber threats. Governments and private enterprises increasingly rely on ethical hackers to bolster their security measures, making them indispensable in the fight against cybercrime.
Why Companies Should Hire White Hat Hackers
Companies that neglect to secure their digital environments are at higher risk of cyberattacks. By employing White Hat hackers, organizations can proactively protect their systems from vulnerabilities, ensuring that they remain one step ahead of malicious actors.
Benefits of hiring White Hat hackers:
Proactive Security: Detecting and addressing vulnerabilities before they are exploited.
Cost-Effective: Preventing attacks can save organizations from financial losses due to breaches.
Legal Compliance: Ensures that security measures meet regulatory standards, reducing the risk of fines and legal issues.
Conclusion: The Ethical Future of Hacking
The evolving landscape of cybersecurity presents both challenges and opportunities for ethical hackers. As technology advances, the need for skilled White Hat hackers grows, while the threat posed by Black Hat hackers continues to loom large. By understanding the ethical implications of hacking, we can better protect our digital spaces and promote a safer, more secure internet for everyone.
#career#internship#internshipgate#internship in india#ethics#hackers#education#virtualinternship#online internship
2 notes
·
View notes
Text
Unlocking Potential at XIM University Bhubaneswar
XIM University Bhubaneswar is an esteemed institution known for its commitment to academic excellence and holistic development. As a hub for aspiring business leaders and management professionals, it offers a wide array of programs that cater to the needs of today’s dynamic job market. With its state-of-the-art infrastructure, experienced faculty, and strong industry connections, XIM University Bhubaneswar is a preferred choice for students seeking to advance their careers in management and beyond.

Academic Programs
At XIM University Bhubaneswar, the academic programs are designed to provide students with both theoretical knowledge and practical skills. The flagship MBA program is renowned for its rigorous curriculum, which focuses on developing critical thinking, leadership abilities, and ethical business practices. Additionally, the university offers specialized programs in areas such as Human Resource Management, Rural Management, and Sustainability Management, ensuring that students are well-prepared to tackle the challenges of their chosen fields.
Faculty and Research
One of the standout features of XIM University Bhubaneswar is its distinguished faculty, comprising experienced professionals and researchers from various fields. The faculty members not only impart knowledge but also mentor students, fostering an environment of collaboration and innovation. The university encourages research and provides ample opportunities for students to engage in projects that address real-world issues, thereby enhancing their learning experience.
Campus Life and Facilities
XIM University Bhubaneswar boasts a vibrant campus life that encourages students to participate in extracurricular activities, clubs, and events. From cultural festivals to academic conferences, the university offers a range of opportunities for personal and professional growth. The modern campus is equipped with cutting-edge facilities, including well-stocked libraries, advanced laboratories, and comfortable hostels, ensuring that students have a conducive environment for learning.
Industry Connections and Placements
XIM University Bhubaneswar maintains strong ties with various industries, which plays a crucial role in its successful placement record. The university regularly organizes workshops, guest lectures, and networking events, providing students with valuable insights into the corporate world. The dedicated placement cell works tirelessly to connect students with leading companies, helping them secure internships and job placements that align with their career aspirations.
Conclusion
In conclusion, XIM University Bhubaneswar stands out as a premier institution for management education in India. With its focus on academic excellence, experienced faculty, vibrant campus life, and strong industry connections, the university is dedicated to unlocking the potential of its students. Whether you aspire to be a business leader, a change-maker, or an innovator, XIM University Bhubaneswar provides the tools and resources necessary to help you achieve your goals. Consider joining this esteemed institution and embark on a transformative educational journey!
#XIM University Bhubaneswar#XIM University#XIM#education#news#higher education#universities#colleges#admissions#mba#Human Resource Management#pgdm#students#Rural Management#online mba programs in india#mba programs
2 notes
·
View notes
Text
#life oriented education#matrimony#newdelhimangalyam#charity#donations#training#certification#diploma#education#learning#teaching#internship#career#jobs#employment#jobseekers#online jobs#jobsearch#resume#marriage#match making#new delhi#india#tamilnadu#wedding#wedding planning#delhincr#party#free
2 notes
·
View notes
Text
https://edumentonline.com/online-tuition/
Edumentonline offers top-notch CBSE tuition in India, ensuring a comprehensive and tailored learning experience for students. Our expert tutors provide personalized guidance, covering the CBSE curriculum with precision. Join our online CBSE tuition classes to excel in your studies, master key concepts, and achieve academic success. With Edumentonline, access quality education from the comfort of your home. Enroll now for CBSE tuition in India that goes beyond traditional learning, preparing you for excellence in every subject. Elevate your academic journey with Edumentonline's dedicated CBSE tuition program.
#indian online school#india's best online school#cbse virtual school in india#cbse online schools in india#best online schools in india#best virtual school in india#montessori teacher training online#online education in india#online school education in india#top online schools in india#CBSE Online Tution
0 notes
Text
#jobsearch#jobsupport#online jobs#non phone jobs#colorado jobs#uae jobs#jobsintr#full time jobs#govt jobs#jobs in railway#recruitment consultant in india#recruitment agency#recruitment 2024#recruitment services#recruitment company#recruitment process outsourcing#hiring#careeropportunities#hiring and recruiting#career#jobseekers#top placement consultancy in lucknow#placement agency#placement engineering colleges in bangalore#placement consultancy#placement assistance#placement service#job#education
2 notes
·
View notes
Text
Unveiling The Flower of Veneration Chapter 1: A Journey into Mystical Realms
Introduction:
The Flower of Veneration Chapter 1 emerges as a captivating literary endeavor that invites readers into a world where mysticism, intrigue, and profound revelations converge. Authored by the enigmatic writer, [Author’s Name], this opening chapter serves as a portal to a narrative that promises to enthrall and challenge the imagination. In this article, we will delve into the essence of The Flower of Veneration Chapter 1, exploring its themes, characters, and the mysterious tapestry it weaves.

Setting the Stage:
The chapter opens with an evocative scene, transporting readers to a world where the ordinary and the extraordinary coexist. [Author’s Name] skillfully crafts a vivid setting, establishing an atmosphere laden with a sense of wonder and anticipation. From the first paragraph, it becomes evident that readers are embarking on a journey that transcends the boundaries of the mundane.
Characters That Intrigue:
Central to the narrative are characters that captivate the imagination. Each one is carefully introduced, leaving a trail of breadcrumbs that hint at their roles in the unfolding saga. Protagonists are imbued with a depth that sparks empathy, while antagonists are shrouded in an aura of mystery, inviting readers to unravel the complexities that define their motivations.
Themes of Mystery and Veneration:
Mystery and veneration are omnipresent in this inaugural chapter. As the plot unfolds, readers are presented with enigmatic symbols, ancient prophecies, and arcane rituals that hint at a deeper, hidden truth. “The Flower of Veneration” seems to be more than just a story; it is a tapestry woven with threads of mysticism and reverence, inviting readers to question the boundaries between reality and the mystical.
Narrative Style:
[Author’s Name] employs a narrative style that mirrors the ethereal and otherworldly nature of the story. Descriptive prose creates vivid imagery, while dialogues are crafted with a poetic finesse that elevates the reading experience. The author’s unique voice invites readers to immerse themselves in a narrative that is as much about self-discovery as it is about the unfolding events.
The Promise of the Unseen:
As Chapter 1 concludes, readers are left with a tantalizing promise ��� the promise of the unseen. Questions abound, and the narrative invites readers to contemplate the significance of the titular “Flower of Veneration.” What lies beyond the veil of the ordinary, and how will the characters navigate the uncharted territories that await them?
Conclusion:
The Flower of Veneration Chapter 1 sets the stage for a literary journey that combines elements of fantasy, mysticism, and self-discovery. With its richly drawn characters, evocative settings, and a narrative that hints at deeper truths, this chapter serves as a compelling introduction to what promises to be an enthralling tale. As readers eagerly await the subsequent chapters, one cannot help but marvel at the skill with which [Author’s Name] invites us to explore the realms of the unknown and contemplate the mysteries that lie beneath the surface of our reality.
Click given link to read more:
#canada#india#usa#studying#student life#seo#seo services#digital marketing#emailmarketing#online marketing#smm#exams#education#learning
5 notes
·
View notes
Text
IETM for Beginners A Quick Guide to IETM Code and Pixels

IETM: Interactive Electronic Technical Manual
Training Aids to Defence Client
If you are a supplier of defence then along with the system/equipment you also need to provide Training Aids
(CBT) — Computer-Based Training
Charts and Bloups
Video Film
Training Work Modules
Manuals Hard Copies
IETM
Evolution of Documentation in Defence
Before — Hardcopies and PDFs in DVDs (Upto 2015)
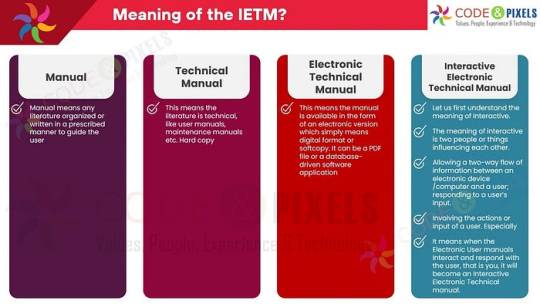
What is the meaning of the IETM?
Manual: Manual means any literature organized or written in a prescribed manner to guide the user.
TechnicalManual: This means the literature is technical, like user manuals, maintenance manuals etc. Hard copy
Electronic Technical Manual: This means the manual is available in the form of an electronic version which simply means digital format or softcopy. It can be a PDF file or a database-driven software application.
Interactive Electronic Technical Manual:
Let us first understand the meaning of Interactive. The meaning of interactive is two people or things influencing each other.
Allowing a two-way flow of information between an electronic device /computer and a user; responding to a user’s input.
Involving the actions or input of a user. Especially
It means when the Electronic User manuals Interact and respond with the user, that is you, it will become an Interactive Electronic Technical manual.
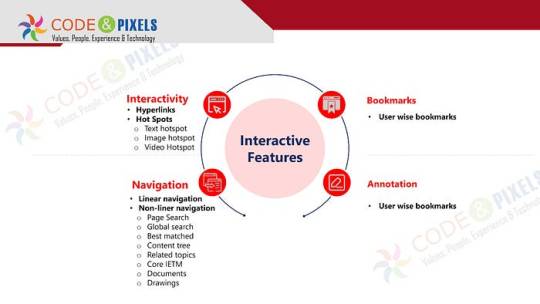
Interactive Features
Interactivity
Hyperlinks
Hot Spots
Text hotspot
Image hotspot
VideHotspot
Bookmarks
User wise bookmarks
Navigation
Linear navigation
Non-liner navigation
Page Search
Global search
Best matched
Content tree
Related topics
Core IETM
Documents
Drawings
Annotation
User wise bookmarks
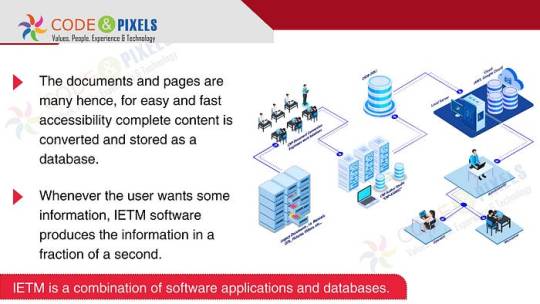
The documents and pages are many hence, for easy and fast accessibility complete content is converted and stored as a database.
Whenever the user wants some information, IETM software produces the information in a fraction of a second.
Use or Purpose of the IETM?
The purpose of the Manual is to give information related to the equipment to the end user for quick reference.
All the technicality is written in detail so that when an issue arises, the user can refer to the manual, as every time OEM or technical person or subject matter expert might not be available on the spot to resolve the issue.
If the manual has 10 pages users can refer easily.
But any system used by the defence will have multiple manuals and thousands of page counts and many times a user has to cross-refer between manuals, intra-manual and inter-manual to resolve the issue.
Referring to 10- 15 hard-copy or even soft-copy books simultaneously will be difficult and time-consuming.

How to access the IETM ?
IETM is a web-based application like our bank software or any other web application. The graphic user interface will be provided to use IETM through which users can interact and get the desired data.
Like all other standard software, Unauthorized users cannot access the IETM. IETM is a Login - login-based application. Only users having valid Login credentials can access the software.
Based on the user log credentials data will be provided to the user.
IETM has 2 types of Users and one Administrator
Maintainer
Operator
If the operator logs in, the user gets all the content related to operator use, similarly if the maintainer logs in only maintenance-related content is visible for that user.
Ideally, all the content is available for both users, because the purpose of the IETM is to refer to the manual to fix the issue.
Administrators can create users who can see the user’s navigation and log-in history and interact with the users using user dashboards through Annotations.
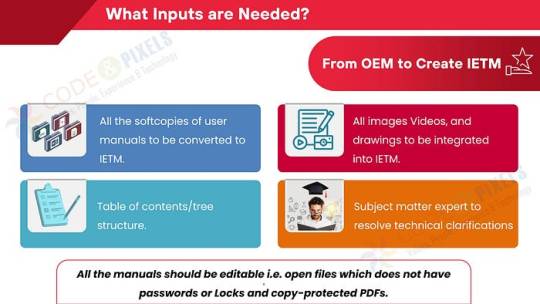
What Inputs are Needed? (From OEM to Create IETM)
All the softcopies of user manuals to be converted to IETM.
All images Videos, and drawings to be integrated into IETM.
Subject matter expert to resolve technical clarifications
Table of contents/tree structure.
Minimum Hardware Requirements?
NO High-end hardware or servers are required to run IETM.
However, if more concurrent users, then a good configuration server with good LAN connectivity must be ensured.
i3 with 8 GB RAM systems is the minimum configuration required for the server or for Node.
Deliverables
BASED DB (Manuals are covered in the Database)
IETM VIEWER Software
User Manual and Installation Manual
Standards — compliance

Costing of IETM: (Interactive Electronic Technical Manual)
Level of IETM, is it Level 3 or Level 4
Cost will be based on the number of pages that are to be converted
The vendor calculates the cost per page. And a fixed cost of IETM viewer software
If you want to create IETM by yourself self then you also need to buy IETM authoring software.
What are these Levels?
Level — 1 is any PDF file
Level — 2 is a PDF file with hyperlinks from the table of contents to the body etc.
Level — 3 is an HTML application. More hyperlinks, simple search, a content tree having log a screen with a hardcoded username and password and supplied in the format of EXE so that Windows can easily open
Level — 4 is Software plus Content/manuals converted as Database

Regarding Level — 5, rest assured, till 2028 it will be Level — 4 only. As of now, there is nothing practically called Level — 5. Few are calling virtual reality and Augmented reality and Artificial intelligence Level — 5.
Pulling data from many user inputs and analyzing and giving results are done in Level — 5. IETM software cannot pull the data from various real-time points as No OEM will give the real-time information to third-party software directly. Yes, if the information is available offline, then that information can be imported into IETM and can be used as a reference.

#ietm#software#technology#ietm developement#ietm code and pixels ietm hyderabad#ietm software#elearning#code and pixels#ietm level iv#codeandpixels#ietm level 4 software requirements#technical documentation#ietm document#ietm documentation#interactive electronic technical manual#Ietm Service Providers#Ietm Software Designers of India#Software Development Company#Elearning Solutions Company#E Learning Content Development Company#Online Education#Digital Education#Digital Content#Software Development Solutions#Elearning#Ietm Developers#Econtent Development#Elearning Solutions Providers#Econtent Developers#Econtent
2 notes
·
View notes
Text
Essential Guide to Filing RTI in Uttar Pradesh
Your RTI Request filed successfully. Please note down the following details for further references. Registration NumberDPTAR/R/2024/60109NameYogi M P SinghDate of Filing11-11-2024RTI Fee Received 10Online Reference NumberCPAELCLTA8Transaction StatusSuccessRequest filed withAdministrative Reforms Department Contact Details of Nodal Officer Telephone…

View On WordPress
#Administrative reform#education#human rights#india#news#Online RTI portal#politics#RTI Act 2005#section 4(1)b#UPHRC Lucknow
7 notes
·
View notes
Text

power bi course syllabus | power bi certification syllabus Boost your career with our Power BI Certification Course online. Join now for expert training and take the next step in IT success.
power bi online training india ,power bi online instructor led training ,power bi course syllabus | power bi certification syllabus ,power bi course curriculum | dax certification ,power bi certification course | dax certification course ,
#power bi online training india#power bi online instructor led training#power bi course syllabus | power bi certification syllabus#power bi course curriculum | dax certification#power bi certification course | dax certification course#sql#power bi#power bi certification cost#power bi course#msbi#data analytics#education#power bi certification#power bi online training#power bi course fees
3 notes
·
View notes