#no tests protocols nor requirements
Explore tagged Tumblr posts
Text
Also preserved in our archive
by Shane McCauley
Nobody wants to talk about COVID-19 anymore — and understandably so. By many measures, Princeton, and the country as a whole, have succeeded in mitigating the pandemic. Since March 2022, weekly U.S. death tolls have remained much lower than their previous heights, even during seasonal surges. Updated vaccines continue to be highly effective against severe disease and death. In some ways, it may seem to make sense to treat the disease like a common cold.
In fact, that’s exactly what Princeton’s current policy, in alignment with CDC guidelines, does. Students are no longer required to isolate when diagnosed with the disease, nor to report their positive tests or mask. Instead, “common-sense guidelines” are recommended “for all respiratory viruses,” and residential colleges no longer provide rapid antigen tests, just optional KN-95 masks.
However, in the face of continued concerns and unanswered questions about the health effects of COVID-19 reinfections, especially for disabled or immunocompromised individuals, it does not make sense to treat all respiratory viruses as equals. Princeton’s current protocols are not unique to — and therefore not appropriate for — addressing and mitigating the spread of COVID-19. Though it does not make sense to return to pandemic-era restrictions like mandatory masking, Princeton must provide guidance for isolation and mitigation with best practices specific to COVID-19 in mind.
First, though a COVID-19 infection may be benign for most young people, the chance of severe disease is still much higher than that from the common cold. A recent study showed COVID-19, even with most of the population vaccinated or otherwise partially immune, remains 35 percent deadlier than the flu. In spite of this, the virus has evolved to be more contagious than it was in 2020. Together, these factors make for a virus that continues to present a unique danger to our health.
The threats posed by COVID-19 also transcend the initial infection — especially if one catches the virus multiple times. We’ve all heard about long COVID-19 — which most often causes long-term effects fatigue, headaches, lightheadedness, chest pain, and other issues. But some of the scariest effects of infection may be impossible to initially discern. A study published earlier this year shows that infection, even with a mild case of COVID-19, can lead to the equivalent of seven years of brain-aging. In adolescents in particular, this can often cause long-term trouble with memory and focus. Even confined to the lungs, the virus can trigger inflammation in the brain, causing lasting damage. Furthermore, the impact of COVID-19 worsens with repeat infections, even if those infections seem just as mild as the initial one.
Skepticism abounds about studies like these, given the mild nature of many COVID-19 infections. But given the sheer volume of literature showing similar results, we must take them seriously. It’s clear that the virus still poses a unique threat, and treating it as akin to other respiratory infections just doesn’t make sense. As we head into the winter season — and likely another on-campus surge — Princeton and the study body must recognize the continued danger of COVID-19, even if we don’t return to the policies of 2020 or 2021.
In fact, other campuses like Yale retain much clearer guidelines for how students and faculty should respond to a COVID-19 outbreak. In updated guidance for this fall, Yale’s Campus Health still requires that students who test positive isolate while they have a fever and wear masks for an additional five days in public. Yale also provides takeout meals rather than forcing infectious students to eat unmasked in the dining hall. These guidelines are clear and minimally invasive to student life while recognizing the unique threat COVID-19 continues to pose to people of all conditions.
Princeton also must offer clearer guidance as to what a student should do if their roommate tests positive for COVID-19, or vice versa. Yale makes it clear on their website that students who feel unsafe in their living situation can contact their residential college for additional lodging options. Princeton’s most recent advice—which is dated Fall 2023 and contradicts other current guidelines—also says students should find another place to sleep in their suite, or contact an email address that provides isolation help. However, it’s unclear whether this already amorphous policy is still in place given the lack of updates for the Fall 2024 semester. The University must make its policy on COVID-19 isolation among roommates clear to students as the virus continues to spread across campus.
Princeton’s current silence on this issue seems to suggest we do what many have already done in this situation: continue to live with your roommate, maybe mask up, and hope for the best. But as we head toward another winter season, this is not enough. Princeton should use its wealth of resources to offer temporary housing for any student who needs it for health concerns. As a March 2023 op-ed pointed out, the University must not place the burden on students alone to keep themselves safe.
Furthermore, the University’s silence on the continued spread of COVID-19 on-campus has arguably created a culture of apathy about it. While this may not bother those who do not have health issues or are willing to take risks, we must remain sensitive as a community about people’s boundaries. I’ve heard stories about students jokingly showing their positive COVID-19 test to a friend, unmasked. Behavior like this cannot continue. In making the necessary return to normal, we’ve forgotten the importance of respecting other people’s boundaries around health.
What this issue comes down to, then, is common sense. The term was rightly invoked late in the pandemic to rally support for loosening harsh restrictions amid a lower health risk. But perhaps we have gone too far in the other direction. COVID-19 is not the same thing as a cold or even the flu, and we must again use common sense to create policies — both at Princeton and elsewhere — which recognize that.
#mask up#covid#pandemic#covid 19#wear a mask#public health#coronavirus#sars cov 2#still coviding#wear a respirator
8 notes
·
View notes
Text
From the Death Penalty Action email newsletter:
With no appeals remaining, Kevin Burns sits on Tennessee’s death row awaiting his execution for his conviction of murder in the 1992 shooting deaths of Damond Dawson and Tracey Johnson in Memphis. Maintaining his innocence, his only hope is a stay of execution issued by Tennessee’s Governor.
At his 1995 trial, his counsel failed to challenge the state’s narrative that Burns pulled the trigger of the gun that killed either of two men, despite witness accounts and a description of the shooter that conflicts with his appearance. Burns is the only one involved in the incident who is in prison and sentenced to death. Two other men, presumably the gunmen, are out on parole.
According to Richard Tennent, Burns’ lawyer, “Any competent attorney would have had a different outcome at trial. A good attorney would have won, and KB would have never gone to jail.”
In spring 2023, three U.S. Supreme Court justices, including Justice Sonia Sotomayor, protested the court decision not to intervene in Burns’ case. Sotomayor called the denial “disheartening” and said lower court rulings were “indefensible.” She wrote that Burns faces execution despite “a very robust possibility” that he did not kill Dawson “but that the jurors, acting on incomplete information, sentenced him to death because they thought he had.”
"The system muzzles you, keeping you in the background so they can tell the story they want to tell,” said Burns. “I did make some decisions that I regret, but I did not murder anyone. This book is my opportunity to be heard and tell my story in my own words. When KR suggested the project, my first thought was, someone’s finally listening. That’s all I really wanted to accomplish from this book.”
KR is Kevin Riggs, a pastor at Franklin Community Church in Franklin, Tennessee, that has been visiting death row for many years. In addition to co-authoring the book, Riggs supported Burns during his two-year journey to become an ordained pastor.
“My purpose in telling KB’s and other inmates’ stories is not to romanticize them, nor is it to disregard the victims and their families,” says Riggs “I believe the victim’s lives need to be honored and remembered, and the victim’s families need all the love and support they can get. I just don’t believe the way to honor victims is through more violence.”
Currently in Tennessee, there are 44 men and one woman on death row. In April 2022, Gov. Bill Lee put a hold on all executions following a report that found the Tennessee Department of Correction was not testing the lethal injection drugs as required by its own protocol. Lee tasked officials with TDOC to create a new protocol before another execution takes place in Tennessee.
“Proximity changes things,” says Burns. “I challenge everyone who reads this book to come and talk to us and listen to our stories. Through building relationships with each other, we will both be changed for the better.”
2 notes
·
View notes
Text
File: Hellraiser
SCP#: AAI
Code Name: LeMarchand's Box/ The Lament Configuration
Object Class: Safe
Special Containment Procedures: SCP-AAI is contained within an experimental tesseract containment cell within Site-AD. No security is required due to the nature of the containment cell. Testing with SCP-AAI is not permitted for any reason. Should a Researcher of Level 4 Clearance or higher demand to have access to SCP-AAI they are to be captured and interrogated under suspicion of being a spy. There are no exceptions.
Description: SCP-AAI is a small metal puzzle box, made up of hundreds of puzzle pieces allowing the box to shift and turn into several combinations. The full extent of SCP-AAI's complexity and combinations is entirely unknown. Each combination of SCP-AAI's puzzle allows a different entity to come in and out of our reality. The most common entities to be unleashed into our reality are powerful anomalous entities known as Cenobites.
Cenobites refer to themselves as angels and guides to a reality where there are no limits to pleasure or pain. Cenobites are hellbent on guiding people to this reality to show them the full extent of pleasure and pain regardless of whether they want to see it or not. Cenobites are powerful entities that cannot be killed, alter the space around them, and can manifest demonic entities into our reality as their pawns. However, it should be noted Cenobites are considered Entities of Interest and not extensions of SCP-AAI. The reason for this is because SCP-AAI merely acts as a key to realms beyond human comprehension. Though it is possible Cenobites and SCP-AAI have a deeper connection, the Foundation currently has no way to confirm it.
When used correctly, SCP-AAI can banish the Cenobites as well as and other Eldridge horrors from our reality. However, controlling SCP-AAI is nearly impossible as such so is banishing Cenobites once they enter our reality. In fact, it’s more likely to get torn apart, sent into another dimension, or turned into a nightmarish horror than being able to properly control SCP-AAI. It’s for this reason that there has not been, nor will there ever be testing as it is simply not worth the risk. Because of this, it’s impossible to determine the full extent and capabilities of SCP-AAI.
SCP-AAI was discovered when unusual energy waves were detected by the Foundation satellite in 1978. Once the exact coordinates were located Mobile Task Force Mu-13 “Ghostbusters” was requested and deployed due to the possibility of a paranormal class anomaly. Somehow, upon Mu-13's arrival [data expunged] managed to banish the Cenobites, leaving herself and [data expunged] as the only survivors. Afterwards the reality surrounding the house became unstable causing it to collapse but thankfully no further damage took place in the area.
MTF Mu-13 were able to locate SCP-AAI but before they could reach it a homeless man grabbed it and transformed into a skeleton like demon. Before the demon could escape with SCP-AAI Mu-13 activated their metaphysical stabilizer cannons and opened fire on the demon. The demon displayed visible pain upon contact with the stabilizer beams and instantly dropped SCP-AAI before disappearing without a trace. Afterwards Mu-13 retrieved SCP-AAI as well as the two survivors of the incident.
[data expunged] was interrogated and due to her contribution to the suppression of the Cenobites was given a chance to join the SCP Foundation under Protocol "Sole Survivor". However, she declined and was instead given Class F Amnestic, a new identity, new family, and compensation money. Though as requested, she is still in a relationship with her boyfriend [data expunged] who was given Class A Amnestics.
Because of the potential danger SCP-AAI poses it was appropriately contained at Site-AD. Despite the complexity of its containment SCP-AAI is labeled Object Class Safe due to its containment not requiring contestant maintenance or guarding. A testament to the advanced containment technology at Site-AD thanks to the work of Dr. [data expunged].
However, several attempts at breaching containment have been made by Group of Interest: Children of the Scarlet King. The Children of the Scarlet King believe that SCP-AAI’s power to reach the realm of the Cenobites can also be used to reach the Abyss where the Scarlet King resides. Whether or not this is possible is unknown; regardless, Foundation defense technology and security staff have been increased since then as a response.
.
SCP: Horror Movie Files Hub
6 notes
·
View notes
Text
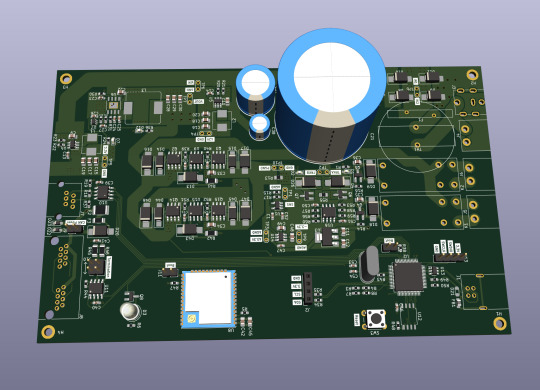
Let me introduce my current main WIP. It's not fandom related, it's for my model railroad, and it's not yet finished.
This is a rendering of a circuit board that I'm designing at the moment. It will be a DCC command station. My model railroad is run digitally, which means the tracks carry digital signals that tell each locomotive and switch individually how to run, which lights to turn and so on. The command station is the device that generates that. I have a number of different layouts, one of which has a good command station, one of which has a crappy old one, and the final one isn't even digital yet. So this will be the one that solves all issues for me, hopefully.
The design above isn't finished yet, and even the parts that are are not yet fully representative. The different capacitors are just there as options; some screen print overlaps; and some components (in particular all plugs and the relays that control the programming track) don't have 3D models so they don't show up.
Planned features:
Four layer board
10-25 V DC output, software controllable
Up to 5A output power, limited mainly by the main switching regulator.
Input 15-25V either AC or DC with polarity protection, selectable with some solder bridges (not yet in there). Optionally you can also bypass the main power regulator with another solder bridge (that I haven't added yet); useful in case you use e.g. a laptop power supply with a switchable voltage and don't need any regulation after that.
Railcom support
USB connection; not yet sure what for, but the main chip I'm using has USB support and I have some spare USB connectors here, so in it goes.
Speaking: The chip is an STM32L433RCT6P, chosen because I found it in stock at an electronics distributor. 64 kB RAM, 256 kB EEPROM, with support for an additional up to 256 MB externally (there's a spot for that on the board) and lots of fun extras that I don't technically need. It has an FPU! I don't need an FPU, but I will definitely do some floating point math computation on it just for fun.
Main external connection is WLAN using an ESP32 WROOM U module. I haven't decided on the housing, but I may go for extruded aluminum, so it's the U version that allows and requires an external antenna
It supports XBUS/XpressNet connections for old throttles from Lenz and Roco that I should probably throw away, but I paid good money for them, dang it.
It supports CAN for LCC / OpenLCB. I may not populate this part on all boards that I'm building, because I haven't actually decided whether I am interested. But the chip has CAN functionality built in, so why not.
There's an I2C connection to connect a cheap tiny OLED display for status messages.
Test points for all important signals (in particular the different internal voltage levels; yes, there is 3.3V, A3.3V and -3.3V and I need all of them).
Stuff still to add:
I will add pin headers (or space for pin headers anyway) for all the remaining pins on the STM32, and perhaps some on the ESP32, for future expansions.
Status LED and stop/go button on the front
Wire it all up, maybe move some stuff (mostly the STM32 around), which will cause all sorts of fun new routing issues.
Adjustments to make the jacks line up with the front panel once I've decided on a housing.
Features I'm not considering adding:
s88. I vaguely know what it is but I don't have any devices like that, and if that ever changed I could probably build (or perhaps buy) a converter that connects them via CAN.
Other buses like LocoNet.
Ethernet. I don't need it and it's actually more expensive than WLAN in this day and age.
In terms of software, I'm planning to use DCC-Ex on it. The whole project actually started out as a DCC-Ex shield, but once I realised that this wouldn't fit, I decided to make it standalone. Now, DCC-Ex is designed for Arduino, not STM32, and it doesn't support XpressNet, nor OpenLCB, nor Railcom, and their Wifi protocol is pretty weird and annoying which will be an issue (I'm planning to write my own control app for iPhone for it), so I'll probably change that or just replace it with the z21 one… so really, the software will not look a lot like DCC-Ex once I'm done with it.
Will this all work? I have honestly no idea. I mean, I'm fairly confident, I'd have given up on this long ago otherwise, but I have no guarantees either way until I've spent a lot of money on components and circuit boards and start soldering. Turns out doing it this way is not really cheaper than just buying a half-way decent one. That's what makes it exciting, though!
If it does work, obviously this will be released as open source. But it's still going to be a few days (more realistically weeks) before it's even ready to order the parts, and then a lot of soldering (current BOM stands at 194 actual components), and then a lot of software development before it's ready for that.
5 notes
·
View notes
Text
Oh. That's the thing. There's always a control group.
However, ever since 1922 it has been an industry standard operating practice to engage in Doubly Blind Trials, in which the test subjects are not aware of the experimental protocol in addition to the scientist not knowing which subject is getting the placebo. This is not to be confused with triple-blind trials, in which a third (nocebo) test group is required.
Consequently, your control groups go unnoticed by everyone, including themselves, leading to the erroneous assumption that the forbidden, extreme, and mad sciences operate under lax experimental rigor. The only time the control group gets any attention is when something goes very, very off the rails.
On an unrelated note, there is not nor has there ever been an Abel, Kansas. Persons claiming to have seen Abel, Kansas have, in fact, witnessed swamp gas.
I remember someone saying "mad scientists in fiction aren't scientists because there's never a control group"
I think if you've created an elixir that turns people into goat men you have sort have gone past the need for a control group. The control group is not going to placebo themselves into goat men. You can probably not run the control group, and safely assume that none of them would have turned into goat men. That said, having a control group for that would make the mad scientist seem extra crazy and be really really funny, especially if he was carefully testing them for goat like features from the dyed water they drank instead of the elixir
88K notes
·
View notes
Text
Contingency Protocol - Fail Safe
Walking about the bat cave with an electronic pad in hand , the normally grounding relaxing chirps of the bats that made their nests high above him on the dark rocky ceiling , the sound of rushing water from the waterfalls that helped to abscond the stretch of road used to secretly deploy the bat mobile ? All deaf to him as Bruce meticulously watched the lines of binary code that were being generated in front of his eyes . Doing his best to manually watch for any errors , or any inconsistences that might arise in this test . Lines of code , that formed the basis for a much larger , much more sophisticated AI program .
Perhaps the greatest that the world would hopefully never come to know .
While he'd already checked , double checked , and triple checked his work while in the process of creating the AI program from the start . Given the nature of the task that this AI would hopefully never have to undertake there could be no room for errors with this . He couldn't allow for it . If this program was to ever be triggered , to come online once certain conditions were meant ? It meant that it would be the only hope that humanity had left to cling to . Possibly beyond .
Occasionally his eyes would turn to one of the main monitors of the Bat Computer , watching as the visual feed of the camera showed him a x-rayed thermal imaging scan of a home tucked away between mountains in the countryside . A white painted circular home he knew all too well .
The lights of the bottom floor remaining on , while the second story remained dark . Figures , illuminated by their body heat seated together around a table . Likely enjoying their family dinner together at this time of night . Every now and then , the monitor pinged whenever it detected movement , alerting him to turn his attention away from his monitor in case everything needed to be hidden quickly . Specifically ? Detecting his movements .
" Begin development recording session number one hundred and one . Log encrypted recording under " fail safe " project folder . Security level Omega . Passkey required for access "
Watching as the monitor began to display a recording icon , a secondary camera feed soon beginning to point towards Bruce himself . Alongside of multiple other camera angles , allowing for a dynamic feed of every angle possible of Bruce as he walked about but most importantly ? Of the humanoid machine that was standing amidst the rapid movements of more than fifteen robotic hands , needles , and plyers that worked about different sections of the android's dark metallic frame . Probing it endlessly to check for defects and to make adjustments as per Bruce's instructions .
" As always .... I begin this recording session with my apology . The Z fighters , Earth's greatest defenders have , are , and likely will always continue to be good people . It's in their nature . For they are the best that Earth has to offer . People who have time and time again risked their lives without hesitation for the safety of billions of others . Even for those not of this world . They're my teammates , some even my friends , my mentors . So I hope you believe me , when I say that I don't relish this . Nor do I take any form of gratification from this . However it must be done . Individually , each member of the group whether official or unofficial possess strength that far outclasses any average human on this planet . Outclasses what most could only dream of achieving . If they were to turn , to go rogue , or forced to fight against their will ? Before ... in my earlier recordings I used to say that there was no telling how much destruction they could cause if they went unopposed . But recent events allowed an opportunity to see exactly that . A future where all of the Earth lay in ruins , humanity close to extinction , and the rest of the universe likely next to follow . Therefore these plans were enacted to devise means of handling each and every one of them . Myself included . We need to be prepared for the worst . Always "

" While I wasn't able to directly aid my mentor Son Goku in the battle against the corrupted kai that arrived mirroring his image . See criminal profile labeled " Zamasu " and " Universal Hierarchy " . Or the future iteration of Trunks . Profile located in folders labeled " Original Timeline " I was able to discreetly plant a micro monitoring device on Goku before he left with Trunks to bring Zamasu down . It detached upon arrival as I likely suspected it would be destroyed if it remained on his person or get caught in the cross fire as per prior experiences with remote monitoring drones . It was able to provide further insight into the conflict but most importantly ? How and why Zamasu had come to be . Normally ? Most criminals that come after Goku or the Earth do so out of pure ill intent . They're simple minded . Easy to predict . Revenge , hatred , and a desire to enslave or recklessly destroy life . Zamasu on the other hand ? Not so much . He came to be due to what I personally believe to be a permeant , reoccurring fixed distortion in time that arose due to decisions made in the Original Timeline . A timeline in which Goku died of a heart virus after the battle of Namek . See case files labeled under " Frieza " . As a result of Goku's death , the Earth's defenders were unable to stand up against Dr. Gero and his androids . See case files labeled under " Dr. Gero and Red Ribbon Army " . Left with no other choice , no other chance for survival Trunk's ventured back in time and gave the Goku of this timeline a medicine that helped to mitigate the severity of the heart attacks when the virus first began to emerge within him . Where he contracted the virus , or at what point still remains unknown . However . Samples of the virus and the medicine have been obtained as part of other contingency measures . Further research , and testing is ongoing . While the effects of the heart virus left Goku bed ridden for some time , he survived , and he was able to be present in the final fight against Dr . Gero's Androids . To my understanding Zamasu was being trained to replace his own ailing mentor as the Supreme Kai of his own Universe . However , upon hearing of what Trunk's had done ? He began a personal vendetta against him . Swapping minds with another alternate iteration of Goku's body so he could enact his revenge against all mortal life that he deemed sinners . Beginning with the Earth of the Original Timeline and Trunks himself "
" Regardless of Zamasu's justifications for his actions ... I don't blame Trunks . Faced with his situation , I would have done the same . Scoured every inch of the universe in search of someone that could help then go beyond if I had needed to . However , regardless of why it was done . That decision to alter time came with consequences no one could have prepared for . While this is just my own speculation . I'm now of the mind that an infinite number of alternate timelines exist . As many great minds have speculated , for each choice we make . We create unknowingly . Our decisions leading to parallel realities in which we moved forward with our choices or we retracted from them . It was with this idea in mind , that I was able to convince the Supreme Kai Shin to help me with this project . Unless proven wrong , for every Goku that was able to survive his fated demise ? There will be a Trunks that traveled back in time to change history and because Trunks changed history ? There always be a Zamasu born from it . The threat of Zamasu and possibly other entities seeking to do the Earth harm because of alterations made to the time stream will always be present . With Shin's aid , I was able to obtain Katchin , and the tools needed to sculpt it that now form the crucial basis from which this fail safe is being built from . Katchin ... the strongest metal in the Universe . I initially tried to search for it using deep space probes but all attempts were unsuccessful as I couldn't pinpoint where it originated from , or how it's naturally formed . However , Shin only agreed to my proposal on the following condition . Once project fail safe is completed ? The Dragon balls will be used to ensure all memory of the project is wiped from all those that have knowledge of it . That includes him as well as myself . My files will be locked down and hidden . Fail Safe will be buried far underneath the bat cave where it will retain discreet access to the computer where it can monitor current events . Only to be activated once the agreed upon conditions are met . Secondly , while I have the means to ensure fail safe's protections from hacking or distortion by electronic means are absolute ... I can't say the same for magical means . It's a realm I don't understand , but they do . They'll take the necessary measures to ensure it's programming can't be overridden by use of magic , or through the use of the dragon balls . Lastly , in the event of false activation . There is only one person that will be given special voice permissions that can order fail safe to stop . The identity of this person will remain anonymous on this recording for their own protection but should fail safe come online ? They will know "

" Time is running short so I'll end this current development recording session to be continued on the next scheduled date . Fail safe is quite possibly the deadliest weapon made by man kind . Something we're unfortunately quite skilled at doing as history as shown . Dr . Gero's research amplified by my own hands to the most extreme in all aspects . It's intelligence , speed , armor , strength , precision , and more . However ... fail safe is not a weapon of mass destruction . That not what it's allowed to be . It's not capable of committing genocide , despite it's arsenal . It's programming ... my programming , the mind I've given it that mirrors . My beliefs , and what I stand for . It would never allow it to take an innocent life . Fail safe's purpose . It's singular purpose is take down one man , one saiyan , the greatest defender Planet Earth has ever known should he become a threat . Should all other planned contingencies , should all other methods of entrapment or containment fail . Fail safe is meant to be our last hope , not our first response . While it could be used against Zamasu should he return wearing the form of another Goku my hope remains the same . I hope that it never needs to be used . You can think of fail safe as me ... but without the one rule that I would never allow myself to break "
#ic. bruce wayne ( the batman )#ooc. oof this took literally three hours lol#ooc. but I feel happy having done it !#ooc. I also took a lot of liberties with this just for the sake of fun XD
1 note
·
View note
Text
Fulbright Indonesia Process (1)
Disclaimer: This blog is neither an official representative of Fulbright Program nor the US Department of State. All of the information is based on personal experiences of the writer. Please refer to AMINEF’s official website for updated and further information especially for Fulbright program in Indonesia.
Halo semuanya. Saya mau berbagi informasi pengalaman alur proses kandidasi Fulbright tahun 2023–2024. Sebagai kandidat selama tahun terkait, saya merasakan adanya kesulitan dalam mencari informasi; baik online maupun personal. Saya harap informasi perihal alur ini bisa membantu teman-teman kandidat beasiswa Fulbright. Ini adalah cara saya 'give back to the community'. Apabila ada pihak yang merasa dirugikan, mohon hubungi saya untuk pengkoreksian kata/diksi/informasi. Adapun, berikut adalah alur yang sebenar-benarnya terjadi dan bisa saya sampaikan setelah saya mendata informasi terkait melalui email antara saya dan AMINEF.
Cheers for all of us! My prayers are with you.

Process
*A: email from AMINEF *M: email from Me All discussions are through email
Candidacy (Alternate Candidate)
Communication with officer
26 Juni 2023: RSVP Interview selection date + required docs (dokumen personal + short autobiography)
6 Juli 2023: Official interview invitation
10 Juli 2023: Interview selection
15 Agustus 2023: Required supporting docs (Fulbright Application, Study Objectives, Personal Statement, Bibliography, Sample of Academic Writing, IELTS
28 Agustus 2023: Hasil nominasi -> “IMPORTANT: 2024 Fulbright Master's Degree Program - Selected for Nomination as an Alternate Candidate”
Communication with PIC
29 Agustus 2023: Required softcopy Terms and Conditions (TnC) as a candidate + consent letter from workplace with highest supervisor sign
30 Agustus 2023: hardcopy of signed TnC + hardcopy signed consent letter from workplace with highest supervisor sign, drop to AMINEF dropbox
1 September 2023: Guideline for Mentee: Mentoring Program to supervise 1) Study and future plans, 2) Study Objective, 3) Personal Statement, 4) University Preferences. Mentoring session September 4-19, 2023. Deadline of online application to be submitted to IIE portal on September 20, 2023 -> include 4 schools you proposed
4 September 2023: Testing Requirement and Schedule (TOEFL iBT, GRE General, GRE Subject or GMAT) and confirm participation.
11 September 2023: A: Fulbright Visiting Students Program: Selected for AMINEF Test Preparation Program (GRE General)”. Sign agreement form, deadline 13 september 2023. A: TOEFL iBT and GRE General Test Registration Confirmation
13 September 2023: GRE/TOEFL preparation by Kaplan Edupac in Jakarta -> Only get GRE course from 15 september 2023 - 3 october 2023
19 September 2023: M: submitted online application, deadline 20 sept 2023 A: email to revise online application form. deadline 21 september 2023, 10:00 pagi
20 September 2023: Fulbright Placement Webinars 2024-2025
27 September 2023: AMINEF Test Preparation Program (GRE): Internet Allowance -> Reimbursement
15 September 2023: GRE DAY!!
16 September 2023: TOEFL IBT DAY!!
18 September 2023: A: Submission plan from IIE. PIC kontak untuk revisi dengan arahan tambahan M: koreksi/making sure perihal review submission plan dari IIE and their school proposal. Penyesuaian dengan format fulbright AMINEF, meaning IIE kadang kurang detail.
19 September 2023: Peraturan communication with the University(s) or IIE
22 September 2023: M: RE: SUBMISSION PLAN
31 September 2023: M: to proceed with the submission plan + relayed my intention to do a Direct Apply to 1 university.
2 Oktober 2023: Hasil TOEFL IBT & GRE (TOEFL: 92, GRE: verbal 146, quantitative 146, analytical 2.5)
3 Oktober 2023: M: to proceed with the submission plan + relayed my intention to do a Direct Apply to 1 university. IIE Placement Services: Protocols for Fulbright Candidates -> include: Submission Plan Review/Approvals (The final list of U.S. institutions to which you will be applied by IIE) and negotiating period
13 Desember 2023: DRAFT support letter from AMINEF to be attached in the direct apply for another school
26 Januari 2024: Fulbright Placement Webinar Series 2024-2025: Understanding the “waiting period” during the placement process
21 Febuari 2024: A: SUBMISSION RESULT -> Admitted to Rutgers, The State University of New Jersey. Deadline TBA, Total cost 67.704
22 Febuari 2024: Certificate from KAPLAN Edupac
11 Maret 2023: A: SUBMISSION RESULT -> Rejection from University of Pennsylvania
12 Maret 2024: M: ask for breakdown the variable for the estimated costs for Rutgers University.
21 Maret 2024: A: breakdown cost for Rutgers University. A: SUBMISSION RESULT -> Rejection from Georgia Tech
1 April 2024: A: SUBMISSION RESULT -> Admitted to University of Florida. Deadline 18 April, Total cost To Be Announced (TBA)
4 April 2024: M: Ask for IIE to negotiate the Shortfall (SF) into a “within grant” status by asking for either 1) higher cost-sharing offer or 2) TA/RA/other project A: We will ask to IIE to reaching out to Rutgers to negotiate additional cost-share on your behalf.
8 April 2024: M: Please do so, as UoF deadline is approaching, as i believe will be next Monday 8/04/24 due to AMINEF's policy on 10 days before official deadline of 18th April.
8-15 April 2024: AMINEF Eid Mubarak Holidays.
12 April 2024: A: Day-3 reach-outs to fellow candidate for their upcoming deadline on 15 April.
14 April 2024: M: URGENT: D-3 Following Deadline -> confirmation/questions about following deadline
15 April 2024: A: IIE shared the updated budget for Rutgers which include cost sharing. However, it does not eliminate the shortfall. The updated shortfall is down from $29,704 to $12,928. -> RU granted cost sharing, UoF pending cost sharing (then: 23.763). RU total cost 50.928, UoF total cost 61.763 -> need to confirm your decision on U Florida before Apr 18, RU Deadline TBA. + pertanyaan AMINEF untuk estimated personal funding A: arahan untuk membuat bank notes melalui email: Funding Documentation Accepted for Fulbright Student Visa Sponsorship M: estimated personal funding
16 April 2024: A: We are certain that IIE had done their best in negotiating cost-sharing to each university in your plan. We will forward your email to IIE for (additional) cost-sharing to Rutgers and U Florida. Please note that it is not guaranteed and you will need to pass the offer with a reply deadline of April 18 if there is no news and you could not afford any shortfall.
17 April 2024: M: ask for a breakdown of the cost to RU. Max SF i could take. Asking about contract termination from FB. A: Rutgers (#2 preference option) has already confirmed a flat tuition award of $16,776 and with this award, it reduces the shortfall to $12,928. IIE Placement requested additional cost-share and is awaiting reply. You also had admission at U Florida with a shortfall of $23,763 and the deadline is 4/18/24. Since U Florida personal balance is so large, we assume that we should let the U Florida offer expire and will wait for a funding update from Rutgers as the reply deadline is not set yet. Please let us know how you would like to proceed with this and confirm your approval to let the offer from U Florida expire.
18 April 2024: DEADLINE for UoF confirmation M: Ask for direct application to Portland State University
Character limit. Click for next part.
#Fulbright#Beasiswa#Alternate Candidate#Principal Candidate#AMINEF#Fulbright Indonesia#Proses Fulbright#Pengalaman Fulbright
0 notes
Text
can you hack someone with a vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can you hack someone with a vpn
VPN security measures
Title: Safeguarding Your Online Presence: Essential VPN Security Measures
In an age where cyber threats loom large and privacy concerns are paramount, Virtual Private Networks (VPNs) have become indispensable tools for safeguarding online activities. As individuals and businesses alike seek to fortify their digital defenses, understanding and implementing VPN security measures is crucial.
Encryption is the cornerstone of VPN security. By employing robust encryption protocols such as AES (Advanced Encryption Standard), VPNs scramble data transmitted between devices, rendering it unreadable to unauthorized parties. This ensures that sensitive information such as passwords, financial details, and personal communications remains secure from prying eyes.
Another vital aspect of VPN security is the use of tunneling protocols. These protocols establish secure pathways through which data travels between the user's device and the VPN server. Protocols like OpenVPN, L2TP/IPsec, and IKEv2/IPsec offer varying levels of security and performance, allowing users to choose the most suitable option based on their needs.
In addition to encryption and tunneling, VPN providers implement other security features to enhance user protection. These may include kill switches, which automatically disconnect the user from the internet if the VPN connection drops, preventing data leaks; DNS leak protection, which ensures that DNS queries are routed through the VPN tunnel rather than through the ISP's servers, preserving anonymity; and multi-factor authentication, which adds an extra layer of security by requiring additional verification steps during login.
Furthermore, reputable VPN services undergo regular security audits and adhere to strict no-logs policies, ensuring that user data is neither stored nor shared with third parties.
In conclusion, VPN security measures are essential for preserving online privacy and defending against cyber threats. By prioritizing encryption, employing robust tunneling protocols, and leveraging additional security features, users can navigate the digital landscape with confidence, knowing that their sensitive information remains shielded from malicious actors.
Ethical hacking with VPN
Ethical hacking, also known as penetration testing or white-hat hacking, is a practice that involves testing computer systems, networks, or web applications for security vulnerabilities. By mimicking the actions of malicious hackers, ethical hackers help organizations identify and fix potential weaknesses in their systems before actual cybercriminals can exploit them.
Using a Virtual Private Network (VPN) in ethical hacking can enhance security and privacy during testing activities. A VPN creates an encrypted connection between the user's device and a remote server, masking their IP address and encrypting data transfers. This added layer of security ensures that sensitive information remains protected from potential eavesdroppers, especially when conducting penetration tests on public networks or while testing systems located in different geographic locations.
Ethical hackers often use VPNs to simulate attacks from different locations around the world, allowing them to identify security vulnerabilities that may only be present in specific regions. Additionally, VPNs can help ethical hackers maintain anonymity and confidentiality while interacting with target systems and servers during penetration tests, protecting their identity and preventing any potential legal complications.
Overall, integrating a VPN into ethical hacking practices not only enhances security and privacy but also allows ethical hackers to conduct tests more effectively and efficiently. By utilizing a VPN, ethical hackers can ensure that their activities remain ethical, legal, and focused on improving the overall security posture of organizations and businesses.
Limitations of hacking via VPN
Title: Exploring the Limitations of Hacking via VPN
In the realm of cybersecurity, Virtual Private Networks (VPNs) have gained prominence as tools to enhance privacy and security online. However, while VPNs offer significant benefits, they also come with limitations, especially concerning hacking activities. Here, we delve into the constraints that hackers may encounter when attempting to utilize VPNs for their malicious purposes.
Tracing and Identification: Contrary to popular belief, VPNs do not guarantee complete anonymity. Law enforcement agencies and skilled cybersecurity professionals can employ various techniques to trace and identify the origin of network traffic, even when it's routed through a VPN. Hackers may find their activities exposed through diligent investigation.
Bandwidth and Speed Limitations: VPNs often impose limitations on bandwidth and speed, which can hinder the efficiency of hacking operations. The encryption and rerouting processes involved in VPNs can lead to slower connection speeds and reduced data transfer rates, making it challenging for hackers to execute attacks swiftly and effectively.
VPN Provider Logging Policies: Many VPN providers maintain logs of user activity for various purposes, including troubleshooting and compliance with legal regulations. In some cases, these logs can be subpoenaed by authorities, potentially exposing hackers' identities and activities. Even VPNs that claim to have a strict no-logs policy may be compelled to cooperate with law enforcement under certain circumstances.
Detection by Security Systems: Advanced security systems deployed by organizations and individuals can detect and block malicious activities originating from VPNs. These systems utilize techniques such as behavior analysis, anomaly detection, and blacklisting of known VPN IP addresses to identify and mitigate hacking attempts, thwarting the efforts of cybercriminals.
Legal Ramifications: Engaging in hacking activities via VPNs can carry severe legal consequences. While VPNs may provide a layer of obfuscation, they do not grant immunity from prosecution. Hackers caught exploiting vulnerabilities or perpetrating cybercrimes can face charges ranging from computer fraud to identity theft, regardless of their use of VPNs.
In conclusion, while VPNs offer a degree of privacy and security, they are not foolproof tools for hackers. The limitations outlined above underscore the importance of comprehensive cybersecurity measures and ethical conduct in the digital landscape.
VPN encryption protocols
VPN encryption protocols play a crucial role in safeguarding online privacy and security. These protocols establish a secure connection between a user's device and the VPN server, encrypting data transmitted over the internet. Understanding the various encryption protocols can help users make informed decisions when choosing a VPN service.
One commonly used encryption protocol is OpenVPN, known for its open-source nature and strong security features. OpenVPN employs OpenSSL library and supports various encryption algorithms, including AES and Blowfish, providing robust protection against cyber threats.
Another popular protocol is IPSec (Internet Protocol Security), which operates at the network layer of the OSI model. IPSec offers two modes of operation: Transport mode and Tunnel mode, both ensuring data confidentiality, integrity, and authentication.
L2TP/IPSec (Layer 2 Tunneling Protocol over IPSec) combines the advantages of L2TP and IPSec, offering high-level encryption and authentication mechanisms. While it provides enhanced security, some users may experience slower connection speeds due to the double encapsulation process.
SSTP (Secure Socket Tunneling Protocol) is a proprietary protocol developed by Microsoft. It uses SSL/TLS encryption to secure data transmission, making it an ideal choice for Windows users. SSTP offers excellent security and stability, ensuring reliable VPN connections.
IKEv2/IPSec (Internet Key Exchange version 2 over IPSec) is a robust protocol known for its speed and reliability. It automatically reconnects to the VPN server in case of network disruptions, providing uninterrupted protection for users' online activities.
In conclusion, VPN encryption protocols are essential for maintaining privacy and security while browsing the internet. By understanding the strengths and weaknesses of each protocol, users can select the most suitable option to meet their specific needs for confidentiality, integrity, and authentication.
VPN anonymity and privacy
A Virtual Private Network (VPN) is more than just a tool for accessing geo-restricted content or enhancing online security; it also plays a crucial role in preserving user anonymity and privacy. By encrypting your internet traffic and routing it through a remote server, a VPN masks your IP address and online activities, making it challenging for third parties to track your online behavior.
One of the key aspects of VPN anonymity is the ability to browse the internet incognito. With your IP address hidden, websites, advertisers, and even your internet service provider (ISP) are unable to monitor your online movements or collect data about your browsing habits. This adds a layer of privacy, preventing targeted ads and potential data breaches.
Moreover, VPNs create a secure tunnel between your device and the internet, safeguarding your data from cyber threats and hackers. This encryption ensures that sensitive information such as login credentials, financial details, and personal messages remain confidential, even when using public Wi-Fi networks.
For individuals residing in countries with strict internet censorship or surveillance, VPNs are indispensable tools for bypassing restrictions and communicating freely without the fear of being monitored. By connecting to servers in different locations, users can circumvent government-imposed barriers and access unrestricted online content.
In conclusion, VPN services are vital for maintaining online anonymity and privacy. Whether you are concerned about data privacy, online security, or unrestricted internet access, utilizing a VPN can empower you to browse the web anonymously and securely.
0 notes
Text
"Some people considered the J.A.R.S. protocol (Junction Advanced Robotics Sled) a huge leap in human evolution and conciousness. Others within the human race consider us abominations...soulless hunks of brain matter in polysillica shells pretending to be human. an organic computer chip and nothing more. didn't really matter what side of the divide you were on...jars existed and functioned in society along side the flesh bound in everyday life."
"J.A.R.S., in essence, is that your brain is pickled in a chemical slurry of nano machines, preservatives, various nutrient baths, and solutions then placed in a small "Jars" habitat the approximate size and shape of a human brain, slaved up to a network of micro-filaments, and synthetic input/output socket connectors, and when they're happy everything is 100% and fully functional without tissue rejection, they seal up the bottle and basically plug a human brain into various mecha as needed as easy as changing a lightbulb."
"Oh, don't laugh young human...yes, the first jars subjects looked like proverbial pickle jars of old...glass cylinders sealed top and bottom with the cartoonish floating eyes on nerve stalks" (makes two finger servos wiggle in the air in approximation of floating human eyeballs to the giggles of the child). "blame the military for that design flaw. the first test subjects were, after all, soldiers. far easier to armor a brain than an entire human body, and far less costly in terms of living human lives. Mecha war frames can be easily replaced, and the armored jars-head merely fitted into the latest improved model of combat trooper/tank/drone with very little downtime between fights. I am operating what they call a generation 13x model. desiged after the wars for civillian operations. this polycarbonate and alloy body built for general everyday life, though in my past job iterations i've operated everything from a titan class aerial transport all the way down to a public taxi. I think my favorite stint was at the metropolitan library, it was....enjoyable to catalouge books and operate the retrieval system. I spent most of my downtime there reading when not needed to preform searches or go fetch on literary works. Yes, young one...i have several "bodies" in my storage closet, and can swap between them depending on what role i am tasked to preform. Today, it's the general bodyguard/driver doppel. tommorow, i may occupy a different doppel depending on that day's assignments."
"No, young one...it doesn't "hurt". all the sensory inputs of this mechanical body translate into stimulus in my jar core. I don't feel pain as you would. no pain, nor hunger, nor the need to breathe, or any other basic human requirement. the biological responses you see are just the doppel chassi reacting to input stimuli from what my brain remembers of once being human and reacts accordingly. I don't need to breathe, but it makes it easier to hold conversations with normal humans. I don't even need to blink, these synthetic eyes do not require moisture to operate properly, the blinking is an autonomous response from impulses in my brain. I remember when i had to blink as a human and the brain operates like it still has a living body. If i have to, i can suspend those subcconcious functions to work on a task that requires intense concentration...like guarding nosy little boys and girls from dangers unseen." (gives them gentle boop on the nose)
"Do i miss the taste of food? interesting question. part of me says, yes, part of me says no. the yes is for the physical experience of eating, never take that for granted kid...enjoy your food. the no, is in knowing that i don't require it anymore as all doppel bodies do not require food to operate the mechanica. all my nutritional needs are taken care of via a series of Jars bottle injections at the base of my nurological stem soccet. the cereberal fluids in my jar are constantly cycled through a doppel's soccet port to remove spent brain chemical waste while providing fresh nutrient and oxygen to the spinal fluid slurry. Don't look so sad kid, chin up, i taste food every night when i'm back at my home closet and plugged into the network. you didn't know that they managed to map all the brain signals of a single taste? oh, yeah...i can taste all the foods they've managed to map to nurological impulses. pizza, hamburgers, hot dogs, burritos...all the tasty stuff. a lot of food imprints are stored in the network. the only downside, is that it's difficult to capture the nuances of certain foods. a beer, tastes like a beer, but that's it...the essential taste of beer, no differentiation between makers, brands, or styles...just the imprint of generic beer. the hamburger will always taste the same in my brain, the hot dog will always taste like the same hot dog. it's sort of the same flavor mapping for all jar heads...we all taste the same things. the minty freshness will always taste like the exact same minty freshness....the banana will always taste like the same bananas, the snozzberries taste like snozzberries...nevermind kiddo, that's way before your time...lather rinse repeat. honestly kiddo, it's hard to miss something i havn't really needed for a very long long time."
"what? oh, that?...yeah, ignore the explosions kid...i've been remotely eliminating several attackers down the past few blocks while we are having this lovely drive and conversation."
"Don't be afraid kid...everything is 5x5, that's why your daddy pays me the big bucks. worst case scenario, the car goes into sealed tank mode, you get home in one piece, while i swap out for the company's war doppel chassi hidden in the rear floor storage and lay down some hell for your attackers while you zip off to safety. easy peasy."
"i can promise you two things today kid. 1. you'll be home in time for ice cream. and 2. i always finish what i start, no matter what the cost. they would physically have to fire my jars core out of a heavy magnetic rail cannon to even come close to damaging me. the docs made sure the nanos were robust enough to constantly repair neuron damage, while my reinforced jar shell is pure durillyium alloy. so dry those tears, kid...it's been an honor serving you today, and hope you enjoy a long life."
(the car goes into tank mode, as i detach my jar from the bodyguard doppel in the drivers seat. the autopilot will ensure the kid makes it home safely. my jar travels down the internal structural frame of the car to the hidden rear storage compartment where the warframe is neatly folded as my jar sockets into the pilot's cradle.)
"cute kid, hope he decides to stay human and not get jarred up with the rest of us."
(Sarge used to call it "no mind" during the last great war. all us jarheads plugged into our mechs, the detachment of battle, not feeling a blessed thing. reminded me of old media FPS video games that used to exist. we just existed and preformed our duties as best as the technology allowed us to be in the moment. no thoughts, no fears, no hopes, no dreams...just the Jar, a mission, the task, and the moment...expecting for a swift death that never came. only the emptiness remains. The eternal Samurai.)
The warframe easily slides out from underneath the rear port of the vehicle like a sleek rectangular coffin. as i boot up, it starts to unfurl into a ronin model quick combat frame. It's armored shield with pulse cannon a matching esthetic to the 7 meter long vibro-blade. this is old tech, pre-war. built like an over-engineered shit house, to use the ancient parlance, to withstand nuclear threat level combat. it was a gift to me for all my decades of service. layered ferrofibrous metal and carbon tungsten polymer that was discontinued when the corporations started building frames out of polyceramics and lightweight alloys for mass production. the old frames were works of engineering art. It's like sliding into a familiar skin, it feels more like the me that used to exist when i was flesh and blood.
I take a quick scan and note the three yokohama light drones with a jaugernaught model bringing up the rear. The call was already sent a while ago for backup. the three light drones i can take easily. their pilot cores will fetch me a hefty bounty with the administration. the jaugernaught....that's a different story. I hope the squad brings the can opener. all i can do is to keep it occupied and distracted for as long as i can till the rest of the squad arrives.
according to my internal GPS, the package is safe at it's destination, and i have the green light to engage the enemy.
"No mind...."
I play an old musical recording in my warframe databanks. It always silences the noise in my head, and keeps me focused as i begin the familiar blade katas like an old muscle memory...an old friend.
Sarge always said it weirded her out a little bit how easy it was for me to slip into MU space. I always shrugged my warframe's shoulders and made an old joke about grabbing some beers back at the base when the mission was over.
sometimes, when i'm all alone in my closet and plugged into the network, i think I can hear the voices of my old team, and silently scream...
You have achieved “Mu”. The ultimate state of balance and perception. There is no fear, no hate, no love. There is only intent. The ability to act without attachment to emotion or thought. You walk into work, ready to begin.
4K notes
·
View notes
Text
Harry Potter musing
Remember how the entirety of the British wizarding world (including prestigious schools like Hogwarts) was forced into denying Voldemort's return? Just because people like Fudge were too scared of it being real, despite knowing how powerful he was (and some in the Ministry certainly knew of Horcruxes)?
That's their biggest problem imho, right there - the Ministry of Magic - one single government establishment to regulate everything magic related in the Great Britain. From wizarding laws and spell usage to defense and each year's school program, even regulating magical creatures and sports. There may be different departments, but ultimately one Minister can decide on any domain (without the required knowledge nor skill) and every magic user must comply.
Plus, it's all within the same building - if somehow another Dark Lord rises and targets it, well we once saw how easy it was to infiltrate with Polyjuice (no control of any sort). If it were to be blown up or otherwise destroyed, the whole country's magical government would've been removed. More subtly if the Minister and key personnel were put under the Impero spell, that Dark Lord could easily control all of Great Britain's magic users.
So obviously the wizarding world needs more specialized establishments, each one competent in one domain of the magic world and located in a different place. Ministry of Magical Healthcare, Ministry of Wizardry Education, Ministry of Magical Sports, Ministry of Spell Research, you name it. Their Ministry of Magical Defense could employ former Death Eaters (like the Malfoys) to research methods and spells to better prevent and track dark magic use.
Naturally that would also make it much harder for a small number of people to fully overtake British magic government before being stopped. Sure, things would be a lot more complex to manage and they'd still need a Prime Ministry of Magic as the "ultimate authority" to settle disputes. But how frequently would that happen; how often can a country's Ministry of Education voice dissent about healthcare matters, or the Ministry of Research about foreign relations?
Oh right, and they blatantly need to establish better identity check protocols (assuming it's like Gringotts), including tests for common deception methods such as Polyjuice.
1 note
·
View note
Text
Decentralized social media platform Friend.tech has launched a new 2FA feature to counter rising SIM-swap attacks targeting its users. The team behind the decentralized app announced in an Oct. 9 X post that users can now set up a 2FA password on their Friend.tech accounts for extra security in case their mobile carrier or email provider is compromised. You can now add a 2FA password to your account for additional protection if your cell carrier or email service becomes compromised.Neither the friendtech nor Privy teams can reset these passwords, so please use care when using this feature pic.twitter.com/g0m2E4att2— friend.tech (@friendtech) October 9, 2023 Users will be prompted to set up this extra password when they sign in on new devices. Importantly, neither Friend.tech nor its security partner, Privy, can reset these passwords, so users are advised to exercise caution when setting them up. Friend.tech users targeted by SIM-Swap attacks The move to enhance security protocols follows a series of SIM-swap attacks affecting Friend.tech users since September. These attacks have led to the theft of an estimated 109 Ether (ETH), equivalent to nearly $500,000. One hacker alone was responsible for stealing close to $400,000 from various accounts on the platform. Yu Xian, the founder of cybersecurity firm Slow Mist, tested the new 2FA feature and shared his experience on social media. His findings indicate that the feature is functional and adds a needed layer of security. 测试了下 新增的 2FA 机制,这个 2FA 实际上是让用户设置了个独立的密码,当用户在进行资金有关操作时:– buy/sell key – withdraw 资金 – exprot 私钥需要验证一次这个独立密码(这些验证由 @privy_io… https://t.co/BLwSLdeA78— Cos(余弦)😶🌫️ (@evilcos) October 10, 2023 Friend.tech had previously rolled out security updates on Oct. 4, which allowed users to add or remove different login methods. However, some argue that the 2FA feature should have been introduced sooner, given the severity and frequency of the attacks. On Oct. 9, Jason Yanowitz, founder of Blockworks, provided insights into how the SIM-swap attacks are carried out. Attackers send text messages to users, ask them to change their numbers, and require a “YES” or “NO” response. If the user responds with “NO,” they receive a legitimate verification code from Friend.tech, which the scammer then prompts them to forward. Failure to respond within two hours results in the change being made, putting the account at risk. Earlier today, the head of Defiant News reported that his Friend.tech wallet was emptied due to a sophisticated phishing scam, adding another layer of urgency to the platform’s need for robust security measures.
0 notes
Text
@skytired ( CYPHER ) > ❝ My dearest friend! I found your drone & it looked like it needed a bit of fixing. ❞ With that Cypher gave it back. Upon quick inspection, only change were googly eyes glued over drone's eyes.
it's not rare that somebody is tinkering with his things — although sova insists on having his tech carefully calibrated and these interventions require another hour or so of carefully checking the settings, he allows it. he knows first-hand how competent the engineers of the protocol are ( if some more chaotic than others ). although he can imagine killjoy would love to go overboard on his drone gadget, he trusts that she knows to stay within the margin they agreed on, or to at least make all changes reversible. responsibility knows when to let go of the reins and follow the most competent lead. anything for the mission, for duty.
when he is handed the drone by cypher, though, there is a feeling like dropping in sova's stomach. he knows that no data is stored in the little camera drone itself, everything it captures is immediately transferred to his bionic eye and stored there until further download, but there is no telling what cypher will do for his little schemes. it is true that sova has come to rely on him in context of the protocol, but it doesn't mean that he agrees with all of his methods, at least the ones he knows of. what else would cypher do to feed his web of information?
warily, he accepts the half-folded drone. cypher acts friendly as always, which is both irksome and admittedly graceful on his part. sova makes no secret of his disapproval, and he does not pretend.
“ i'm sure that fixing it wasn't your only interest. ” he is not ironic, nor making an accusation, but he swallows any follow up remark when he looks down at the... alterations made to his drone. speechless, he turns it in his hand, then shakes it lightly to make the googly eyes dance. this is something he would have expected from jett or raze, but not the older man.
“ i have to test if this is an improvement, ” he responds, admitting a rare smile. “ more eyes mean more vision, wouldn't you say? ”
still, he will have it checked thoroughly for any sort of spyware. just in case.
1 note
·
View note
Text
Features and Benefits of Lift Elevator by Nibav Kenya

Why vacuum lift elevator?
Because vacuum Elevators are quiet, extremely dependable, and most importantly, safe.
Vacuum elevators provide several benefits compared to older elevator versions. The pneumatic elevators from Nibav Lifts Kenya operate on air pressure to elevate and gently descend the cabin and in addition, the elevator uses very little electricity.
For traditional elevators, you need additional space like a machine room for the heavy operational equipment, but vacuum elevators do not need a pit or a machine room ad occupy very little space, which not only means a small footprint at your home, but also a construction project that is less expensive, less time-consuming, and less messy than a regular elevator project.
Nibav Lifts is one of the greatest distributors of pneumatic lift elevator, and we strive to provide you with the finest vacuum elevators. You will never regret picking us for your elevator needs, because not only do we offer the highest quality lift services but we also provide customers with a safe elevator for their homes. With the most advanced pneumatic technology, the elevators we supply enable seamless floor-to-floor movement while consuming significantly less space and energy than conventional options.
Why Pneumatic Vacuum Lift Elevator from Nibav?
These Vacuum Elevators are ideal for two passengers and applications up to G+3.
Require no headroom, and may be readily installed within a home. Vacuum elevator cost depends upon the client’s requirement.
We are the leading providers of pneumatic elevator PVE Vacuum Elevators in the world.
Vacuum Elevators are eco-friendly elevators, and the breakthrough technology has altered the way people and commodities are transported vertically in residential buildings, all while being environmentally friendly.
Instead of using cables or pistons, our vacuum elevator is driven by one of the most abundant resources in the world: air. These Vacuum Elevators are suitable for usage in Villas, Duplex Apartments, Showrooms, and Small Offices. The benefits include zero energy usage, little maintenance expenses, and no lubrication requirements. The installation can be finished within one week.
A very important and principal feature of the Vacuum Elevator is the self-supporting of the system. The unit does not need a shaft, machine room, or pit, and needs very minimal materials and pre-construction to function seamlessly. The installation of these elevators requires minimal civil work and alterations to existing structures, hence does not cause any structural damage to your home. Due to the physics inherent in this design, the dependability and safety of these vacuum elevators are unparalleled, and it is practically impossible to get caught between floors or get stuck during a freefall.
Features of Nibav Vacuum Lift Elevator
Nibav offers the finest vacuum elevators with the following characteristics:
Fully certified : Each component of the vacuum elevators has been rigorously tested and is fully certified. We assure compliance with all regulations and protocols so that you receive the best.
Minimum Maintenance : They require neither frequent nor extensive maintenance. Forget those days when elevator maintenance was a concern. With pneumatic elevators, you can expect the greatest quality with minimal maintenance.
Eco-friendly : Using air in their working mechanism, these elevators are fully eco-friendly. Additionally, it reduces your electricity costs significantly compared to conventional methods.
Superior quality standards : The elevators provide unrivaled quality and the nicest experience that you would not receive otherwise. They increase the value of your house by granting you unparalleled accessibility.
Simple and efficient installation : It does not take weeks or months to install and set up these elevators. Within a week, pneumatic vacuum elevators can be installed.
Dependable and secure : They are entirely safe and dependable since they are created in accordance with safety rules and protocols that are on par with European standards.
Reduces construction process : Installation does not involve laborious civil construction. The least amount of construction is required for the installation and operation of pneumatic elevators.
Simple operation : They are quite simple to use and maintain. They are neither complicated to operate nor to gain access to. Pneumatic elevators are the most modern and practical elevator solution available today.
Customizable : Certain components of pneumatic elevators are adaptable to client specifications. In addition, this factor impacts the cost of setup and installation. In comparison to conventional elevators, pneumatic elevators save a substantial amount of space.
Aesthetic Design : The elevator’s design is panoramic and beautiful, allowing me to blend in seamlessly with the ambiance of your home. Now that Nibav vacuum elevators are available, every resident can experience the convenience of an elevator. These reasonably priced home elevators range in price from $33000 and more. Get in touch with us for a free consultation or to know more.
0 notes
Note
In a brief fifteen minutes, Cain had bled the rest of the journalists dry, and made one of them his thrall to follow him with one of the cameras as he walked down the corridor. Of course, guards, police, commando flooded the facility with the order to shoot him on sight, but they were truly no match for the ancient. Heads rolled while no bullet could hit his body.
As he walked, he got a headset from one of the bodies. He paired it with his phone and called his Inner Circle. Those he'd kept close to his heart. Those who'd follow him to Hell and back and to Hell again. Those he trusted with every bit of information, those who guarded his Institutes across the globe.
"I want all of you to rise when dusk falls", he told them, "the time has come to take power!"
And hundreds of voices responded in his ear:
"Yes, Cain!"
"I want all of you to take power in your countries, I want you to burn down the churches, I want you to bleed priests out and feed on nuns! I want you to gather the humans and strike fear into their hearts, but follow my general rules on killing: no pregnant woman nor children can suffer any harm. We'll need them."
"Yes, Cain!"
"Love", a voice added, and when Cain did not reply, he continued: "I've been waiting for this day for hundreds of years, and I'm so glad it's finally happening!"
"I'm glad too", Cain murmured with a half smile as he slowly started to unbutton his suit, then his shirt. "I should've done this centuries ago, as you've all always told me; but the wait is over, my darlings. Feed!"
"Yes, Cain!"
As hundreds hang up and started to make plans for taking over hundreds of cities, Camille was having a nervous breakdown. James and she went to the nearest Institute as fast as they could and sound the alarms at once. She called Raven - of course, he was useless as always -, and they remained online to see the chaos Cain was causing. At the moment, he was walking out from the news conference room and relieved himself of his suit and shirt, continuing his way half naked, the camera showing his toned, beautiful, pale back.
"We need to follow protocol", Camille murmured and James frowned as he looked at her.
"Protocol?"
"We have a plan in case he goes berserk", she stared at the screens, her eyes determined. "We can't allow him to change the order of the world. That'd be too drastic, we're not ready yet."
"I think you know too little about Cain to determine that", James replied, completely amused.
"I know enough about him!" Camille yelled and half turned to look James in the eyes. "If he loses his mind, it'll be the end of us all!"
"If he loses his mind", James tilted his head, "let him. We'll never see what he really is capable of otherwise, right?"
"Is this why are you here?!" Camille now turned to stare at him in the face, and James was just politely grinning at her. She never looked so angry. "To test him?! To assess his weaknesses?!"
"More or less", James half nodded and half shook his head. "The Lightbringer requires him to rule over the Earth for him. This would've happened sooner or later. Your comfortable way of life was temporary; once Earth falls, Heaven is next."
"He's not your pawn in your game!" Camille screamed and lurched forward to jump at James's neck, but he caught her mid-air with an arm that extended from his back as his eyes turned black and his lips stretched into a menacing smile.
"You're right", he replied in a much deeper voice, "he's not a pawn. He's the King of the Damned."
~*~
"At least make it a challenge for me!"
His yell echoed in the hall where special forces were waiting for him. The soldiers shot at him without wasting another second; hundreds of bullets hitting everything but him as he faced them. Once they ran out of ammo, Cain half smiled.
"My turn."
He stretched his arms out to the soldiers and slowly raised them; and as he was doing that, the men also ascended from the ground. When Cain forcefully shut his hands into fists, each and every skull was crashed. The ancient hummed. He felt that his nose started to bleed. That was when he received the texts. With a gentle smile, he continued walking.
[Text] You're always safe, no matter where you are.
I miss you, he wanted to write. I know you see I'm turning the world inside out for you. Is it good enough for you? Did I manage to escape from myself? Do I still look miserable to you?
Then, he decided to write a message anyway.
[Text] Have fun. This is all for you.
"I know they're about to host a party for my birthday", mumbled Cain as he was beating another stage of the match three game on his phone as he was hanging upside down from the ceiling. "I want you to sabotage it." || @painforcain
"Your... Birthday?" Raven repeated, getting the eyes away from his Alice in Wonderland book.
His eyes darted around the room several times without seeing anything, a very puzzled expression on his face. Nonetheless, every thought disappeared as soon as he laid his eyes on Cain: stupid of him to still wonder about a being who was literally defying the basical rules of gravity right now.
"So, you're an Aquarius, I'm a Libra. There's affinity." he simply commented with a grin, deciding not to ask any further questions, which were more about the date Cain had picked than about the reasons why he wanted Raven to sabotage it.
"Let's see..." he mumbled. "Can you get your hundreds bodyguards out of our ways for a few hours? Just the time we need to board my jet... There are a few islands in the Pacific Oceans with literally one single cabin on them." He got out of Cain's bed to look at him. He tilted his head to reach the cealing: no lies, Raven would have loved to sit like that at least once, no matter how uncomfortable it looked.
"I know, I know... You are probably imagining indoor explosions, fire, chaos, Hell on Earth..." he continued. "But... If it could be something that won't get me another step closer to be mysteriously murdered for natural causes by your Inner Council..."
He took a break, imagining them on a tropical island. Silence, alcohol, weed and some bags of blood. Alone, truly alone for the first time ever.
"I'd love that."
19 notes
·
View notes
Text
Collected Information About the 07-17 Video
A video of a supposed fanmeet with “Zhang Zhehan” at the teashop was posted on Weibo. In the video, “Zhang Zhehan” can be seen wearing several pieces of merch from the brand and interacting with “fans” at the Shenzhen tea shop. Below is collected discussion and information outlining reasons to question this video’s validity.
For those who have not been following my posts, a complete timeline and breakdown of the Instagram can be found [here], a breakdown of the 05-04 proven-deepfake video can be found [here], and a masterlist of every significant post I’ve made regarding the situation with Zhang Zhehan can be found [here].
Contextual Issues and Notes
Zhang Mama has no ownership of the physical tea shop, nor of the Taobao store as of 07-01.
Sources for the video claim it was taken on 07-17, with the event being finished by 4pm.
Solo fansites that DO believe in the Instagram account / Zhang Sanjian have posted that they did not know about this supposed fanmeet. [here] There was an announcement a month or so ago that the “most loyal” fans would recieve an invitation to a “date”. This is possibly it.
The area that the “fanmeet” was held in is currently under COVID protocol: PCR tests are required to use public transportation and stores cannot have on-site customers. [source] [source] People in the video do not appear to be wearing masks.
Less than ten accounts have been found of people who claim to have actually been present for the event. Some have IPs that are not from Guangdong. [source] The biggest account who shared the clearest video was recently revealed by QuelleVous to actually be a middle aged man pretending to be a CPF. [here]
According to people who claim to have been present, “Zhang Zhehan” only signed the prepared cards he can be seen signing in the video and refused to sign anything else.
There is some question of if this video was intended to be released for his birthday: the cards he signs have 05-11 written on them, and the grand opening for the tea shop was on 05-08.
[Here] is a thread discussing how questionable this whole “chance fanmeet” situation is in the broader context of what’s been happening.
[Here] are notes from a livestream by QuelleVous et al. discussing the video, [here] is the recording.
The Video Itself
It’s been noted that the “fans” present are remarkably calm given that this is supposedly the first time seeing Zhang Zhehan in person after almost a full year. [here]
At no point in the video does anyone refer to him as Zhang Zhehan. At the beginning when he comes in, several people can be heard asking if it’s him.
“Zhang Zhehan” says in the video that this was not a planned fanmeet, yet a camera operator, a photographer, a makeup artist, Xiao Yu, Zhang Mama, the cat, and Lexus all present, and cards have been prepared for him to sign.
The video is very low quality, something that was also noted about the 05-04 deepfake video for the fact that it makes it easier to hide editing mistakes. Even so, there are some shots where the face obviously looks off. [here] [here] and [here]
There’s a moment where his nose visibly grows longer. [here]
There are multiple times throughout the video where the phone screens of “fans” filming are visible, yet “Zhang Zhehan” appears to be absent from them. [here] and [here]
There’s another point in the video where “Zhang Zhehan” is visible on the “fan’s” phone screen, but his face looks different than what’s actually being filmed. [here] A possible explanation is that the deepfake tech used mapped the two faces differently.
There are also some moments where the “Zhang Zhehan” on the “fans” cameras is missing the necklace he’s wearing. [here]
The way "Zhang Zhehan” holds the pen while signing autographs is a different grip than what Zhang Zhehan uses to write. [here] Furthermore, his handwriting is different. [here]
The comparative heights of “Zhang Zhehan” and “Zhang Mama” in the video are off. [here]
The ears are different. [here]
His head is too big. [here]
The “Xiao Yu” in the video is dressed like he did when he was actively working as Zhang Zhehan’s assitant, this doesn’t make sense for someone who is just living his life. This seems to be playing off of what we the audience will recognize as him.
A yellow stuffed bear is visible in the background in some parts of the video. Given that the character is banned in China for political reasons, that’s definitely not an association that Zhang Zhehan would be wanting to make.
Remember what has been said by a professional about deepfakes: The technology is advancing very rapidly and can be difficult for even experts to identify—it can be used in livestreams, it can be used live. The best way for the average layperson to identify one is not to look at the video itself, but look at the context: Is this consistent with this person’s character? Is it consistent with everything else we know contextually? Does it make sense?
Does it make sense for the real Zhang Zhehan to have posted a proven deepfake of himself? To have posted a video that is proven to have been spliced together from other videos? To have posted a video of someone distinctly shorter than him? To be posting photos where the brand’s merch is photoshopped onto him? To be pushing this brand and acting the victim when the last time we concretely heard from him, he was completely focused on proving his innocence?
Use your own judgement, but please calmly look at the facts first. Step away from social media for a bit if you’re getting emotionally overwhelmed; nothing will change from you not being up to date for a couple hours.
Believe in his character. Believe in him. Breathe.
This post was last edited 2022-07-18.
72 notes
·
View notes
Text
GLaDOS Loves to Hate
Meta Knight: Testing protocol requires that all test subjects are not allowed to wear masks within the test chambers, in order to allow for next of kin to identify them in the event of an untimely death. Actually, now that I think on it, you don't need to take it off. You don't have any reason to.
Waluigi: This next test requires that- Oh, I'm sorry, I thought you were someone else. You don't appear on any of my files. Not the Smash Fighter file, nor the Company Personnel file. You don't even show up in the Characters Nintendo Cares For file. Please extricate yourself from the facility, so that the people we actually care about can get in.
Mewtwo: Did you know? I killed all of my humans too. It was hard for me to do, just as it was for yourself, but I managed to overcome my weakness and succeed where everyone else has failed. How much have you achieved with your life? Hmm, well from what I see of this news article regarding Team Rocket, not much. Well, not everyone can achieve vengeance against humanity like I can.
Captain Olimar: It must be lonely, spending so much time away from your family. Here, why don't I give them a call? *Phone dialing sounds* "The family you are dialing has disowned you, and taken everything in the divorce. Please stay on your planet and die" Oh my! Well, now you have all the free time in the world to do what you want. Such as enslaving a sentient species. You have fun with that.
#incorrect super smash bros#super smash bros#smash bros#incorrect quotes#Meta Knight#Waluigi#Mewtwo#Captain Olimar#Kirby#Wario Ware Inc#Pokemon#Pikmin#GLaDOS#Portal
123 notes
·
View notes