#network switch
Explore tagged Tumblr posts
Text
instagram
playing games on switch
1 note
·
View note
Text
The CloudEngine S8700 series switch is a new generation of high-end intelligent routing switches launched by Huawei for the next generation of enterprise network architecture. This product is based on Huawei's intelligent multi-layer switching technology concept. On the basis of providing stable, reliable, and secure high-performance L2/L3 layer switching services, it further provides intelligent business optimization methods such as VPN, application recognition, comprehensive QoS policies, controllable multicast, resource load balancing, and integrated security. At the same time, it has super scalability and reliability. The S8700 is widely used in various industries such as government, education, and finance to gather and connect large parks, or to the core of small and medium-sized parks. It is an ideal choice for building cloud park networks and helping global customers with digital transformation.
0 notes
Video
youtube
Speedy Ethernet from D-Link !!!
1 note
·
View note
Text
Understanding Relay Module Circuits: A Comprehensive Guide
Introduction:
Relay module circuits are essential components in various electronic and electrical applications. These circuits act as switches, allowing control signals from one circuit to activate or deactivate another circuit. Relay modules provide an efficient way to isolate high-power devices from low-power control systems, ensuring safety and protection. In this comprehensive guide, we will delve into the fundamentals of relay module circuits, their working principles, applications, and address some frequently asked questions (FAQs) to provide a complete understanding of this crucial aspect of modern electronics.
I. What is a Relay Module Circuit?
A relay module circuit consists of an electromechanical relay mounted on a PCB (Printed Circuit Board). The relay is an electromagnetic switch that is actuated by a control signal, which can be either digital or analog. When the control signal triggers the relay, it closes or opens the electrical contacts, allowing current to flow through the output terminals and control external devices or circuits.
II. How Does a Relay Module Circuit Work?
Electromagnetic Coil: The relay module circuit has an electromagnetic coil that serves as the input or control element. When an appropriate voltage is applied to the coil, it creates a magnetic field, causing the relay's armature to move.
Normally Open (NO) and Normally Closed (NC) Contacts: A relay typically has two sets of contacts: Normally Open (NO) and Normally Closed (NC). In the resting state, the NO contacts remain open, and the NC contacts remain closed.
Switching Action: When the coil is energized, the armature moves, causing the NO contacts to close and the NC contacts to open. This switching action completes or interrupts the circuit, depending on the application.
III. Types of Relay Module Circuits:
Single-Pole, Single-Throw (SPST) Relay: SPST relays have one set of contacts and can either be Normally Open or Normally Closed.
Single-Pole, Double-Throw (SPDT) Relay: SPDT relays have one set of normally open contacts and one set of normally closed contacts. When the relay is energized, the NO contacts close, and the NC contacts open.
Double-Pole, Single-Throw (DPST) Relay: DPST relays have two sets of contacts that operate simultaneously, making or breaking the circuit.
Double-Pole, Double-Throw (DPDT) Relay: DPDT relays have two sets of NO contacts and two sets of NC contacts. They provide two separate circuits that can be independently controlled.
IV. Applications of Relay Module Circuits:
Home Automation: Relay modules are commonly used in home automation systems to control lighting, heating, ventilation, and air conditioning (HVAC) systems.
Industrial Automation: In industrial automation, relay modules are used to control motors, pumps, solenoids, and other high-power devices.
Automotive Electronics: In automobiles, relay modules are utilized to control various electrical systems, such as headlights, windshield wipers, and electric windows.
Robotics: Relay module circuits are used in robotics to control the movement of actuators and motors.
Security Systems: In security systems, relay modules are used to trigger alarms and control access points.
V. Advantages of Using Relay Module Circuits:
Isolation: Relay module circuits provide galvanic isolation between the control circuit and the load, ensuring safety and protecting sensitive components.
Low Power Control: Relay modules allow low-power control systems to switch high-power devices, eliminating the need for high-power control circuits.
Versatility: Relay module circuits are available in various configurations and voltage ratings, making them versatile and suitable for a wide range of applications.
Simple Operation: Relay modules are easy to install and operate, making them a popular choice in many electronic applications.
FAQs:
Q1. Can relay module circuits be used for both AC and DC applications? Yes, relay modules are available in both AC and DC versions, allowing them to be used in a wide range of applications.
Q2. What is the difference between a relay and a relay module? A relay is the basic electromagnetic switch, while a relay module includes the relay mounted on a PCB with additional circuitry for ease of use and integration into other systems.
Q3. Can relay modules handle high-current applications? Yes, relay modules are available in different current ratings, and they can handle high-current applications as per their specifications.
Q4. How do I choose the right relay module for my application? When selecting a relay module, consider the voltage and current requirements of your application, the type of load (AC or DC), and the number of contacts needed.
Q5. Can I use a relay module to control multiple devices simultaneously? Yes, some relay modules have multiple sets of contacts (DPDT or more), allowing you to control multiple devices independently.
Conclusion:
Relay module circuits are versatile and indispensable components in modern electronics and electrical systems. Their ability to provide isolation, low-power control, and versatility makes them ideal for a wide range of applications in various industries. By understanding the working principles and different types of relay modules, along with their numerous applications, designers and engineers can make informed decisions when integrating these circuits into their projects. Relay module circuits continue to play a critical role in enhancing the efficiency and control capabilities of electronic systems, contributing to advancements in automation and smart technologies.
0 notes
Text
Network switch - electric switch - Imported Products from USA - iBhejo
Discover the seamless world of networking with our imported network switch! Designed to enhance your connectivity, this electric switch from iBhejo is a reliable and efficient solution for all your networking needs. Imported directly from the USA, this cutting-edge device is crafted to deliver high-performance data transfer, ensuring smooth communication between multiple devices.
1 note
·
View note
Text

i like to imagine ed and eddy teaching double d how to play video games (they're playing mario kart 8 deluxe while calling on discord lol)
(also side note: double d would so be the kind of gamer who builds their own high quality pc with really good specs and high processing speed... only to use it to play games like sims 4 and hello kitty island adventure lmao)
#ed edd n eddy#eene#eene edd#eene double d#eene eddy#cartoon network#nintendo switch#digital art#nuttiebun
114 notes
·
View notes
Text

Guess what I’ve been playing… 🥰
#blast from the past man#I got the complete battle network collection for switch#I’ve always wanted to play it myself#as I used to love the anime and the successor games aka star force#megaman#megaman battle network#megaman nt warrior#megaman fanart#megaman.exe#rockman.exe#rockman#lan hikari#maylu sakurai#mayl sakurai#hikari netto#netto hikari
151 notes
·
View notes
Text



Adventure Time BMO Nintendo Switch Dock made by Arnold3DPrints
#nintendo#switch#adventure time#nintendo switch#bmo#cartoons#cartoons network#cute#kawaii#gaming#video games#retro#cartoon network#00s#nostalgia#nintendo switch oled#nintendo switch lite#gifts#merch#artists#3d printing#gift ideas#retrogaming#nintendo switch dock
808 notes
·
View notes
Text

~ Happy Anniversary Kirby and the Forgotten Land and happy birthday Elfilin 🎂💫🌟I love this game so much it’s so amazing and awesome the music is so good too ;w; I also love how it’s 3D ^w^
#my art#sydney’s art#kirby#kirby fanart#digital art#kirby and the forgotten land#elfilin#bandanna dee#bandanna waddle dee#kirby forgotten lands#nintendo switch#bright colors#cartoon network color palette#cartoon network#I LOVE THIS GAME SO MUCH🥹💜#Nintendo music added some Kirby music recently it’s forgotten land omg I’m so happy ;w;#星のカービィ#メタナイト#カービィ
75 notes
·
View notes
Text
But HP is still in business. Apple is still in business. Google is still in business. Microsoft is still in business. IBM is still in business. Facebook is still in business.
We don’t have those controlled burns anymore. Yesterday’s giants tower over all, forming a thick canopy. The internet is “five giant websites, each filled with screenshots of the other four.”
These tech companies have produced a lot of fire-debt. Over and over, they erupt in flames—in this short decade alone, every one of our tech giants has experienced a privacy scandal that should have permanently disqualified it from continuing to enjoy our patronage (and I do mean every one of them, including the one that spends millions telling you that it’s the pro-privacy alternative to the others).
Privacy is just one way that these firms are enshittifying themselves. There are the ghastly moderation failures, the community betrayals, the frauds and the billions squandered on follies.
We hate these companies. We hate their products. They are always on fire. They can’t help it. It’s the curse of bigness.
Companies cannot unilaterally mediate the lives of hundreds of millions — or even billions — of people, speaking thousands of languages, living in hundreds of countries.
- Let the Platforms Burn: The Opposite of Good Fires is Wildfires
#platform decay#fire debt#good fire#threads#interoperability#privacy without monopoly#fediverse#zuck's empire of oily rags#wildland–urban interface#network effects#switching costs#network effects vs switching costs#adversarial interoperability#comcom#competitive compatibility#enshittification#twiddling
1K notes
·
View notes
Note
Blue Sky is nsfw art friendly!
that... is true...
#im trying to cultivate it into what my twitter used to be#aka professional work and networking#and like following artists and getting inspired etc#but if they have a feature that allows you to switch acc easily then#perhaps...#asks#anonymous
41 notes
·
View notes
Text
Something something the similarities between Blaine Anderson and Eddie Diaz are actually astounding....something something a character coming onto the second season of a Ryan Murphy show and completely changing the lives of one of the characters something something...fans getting mad when Eddie Diaz isn't in the episode reminding me of when they filmed a last minute Warbler's number to put into the episode that aired after the Super Bowl in 2011 bc fans loved them so bad...something something gay love history book on the shelf always repeating itself
#blaine anderson#eddie diaz#glee#911 abc#buddie#klaine#I've been thinking a lot about this lately!#even though 911 has been on longer than Glee has atp it still feels like a blueprint kind of sitch ya know?#plus a renewed interest after switching networks and embracing the queerness of the show#you know what I mean#anyways this may be the first post I've made tagging glee in like 7 years at least?
15 notes
·
View notes
Text
Enhancing Efficiency and Performance with Network Switches in PLC Programming
Introduction:
In the world of industrial automation, Programmable Logic Controllers (PLCs) are the backbone of control and monitoring processes. PLCs facilitate seamless communication between various devices, sensors, and actuators in an industrial network. To ensure optimum efficiency and performance in PLC programming, the choice of network infrastructure is critical. Network switches play a pivotal role in enhancing the efficiency of PLC programming by providing reliable and efficient data transmission. In this article, we will explore how network switches contribute to improved PLC programming efficiency and performance, along with addressing some frequently asked questions (FAQ) to provide comprehensive insights into this essential aspect of industrial automation.
I. The Role of Network Switches in PLC Programming:
Network switches serve as the foundation of communication in industrial networks. They facilitate data exchange between PLCs, Human-Machine Interfaces (HMIs), Input/Output (I/O) devices, and other networked components. Network switches use advanced switching technology to establish a seamless and high-speed connection between devices, ensuring real-time data transmission and timely execution of control commands.
II. Enhancing Efficiency in PLC Programming:
Faster Data Transmission: Network switches offer high data transfer rates and low latency, enabling faster communication between PLCs and connected devices. This ensures real-time monitoring and control, enhancing overall system efficiency.
Reduced Network Congestion: Network switches efficiently manage data traffic, reducing network congestion and minimizing the risk of data collisions. This leads to smoother PLC programming execution and improved system response times.
Segmentation and VLANs: Network switches support Virtual Local Area Networks (VLANs), allowing the logical segmentation of the network. This segregation enhances security, simplifies network management, and facilitates better organization of PLC programming tasks.
Quality of Service (QoS): QoS features in network switches prioritize critical data packets, ensuring that essential PLC programming data is delivered promptly. This helps maintain consistent performance and reliability, even during high network loads.
Network Redundancy: Redundant network switches can be deployed to create fault-tolerant network architectures. In case of a Power Supply switch failure, the redundant switch takes over seamlessly, minimizing downtime and enhancing system reliability.
III. Improving Performance in PLC Programming:
Deterministic Communication: Network switches support deterministic communication, ensuring that PLC programming data packets reach their destination without delay or interference. This predictability enhances the accuracy and precision of control commands.
Jitter and Latency Reduction: By eliminating data collisions and providing dedicated communication paths, network switches reduce jitter and latency in PLC programming. This results in improved system responsiveness and stability.
Scalability: Industrial network switches come in various port configurations, offering scalability to accommodate growing PLC programming needs. They can easily be expanded to add more devices and support larger networks.
Compatibility with Industrial Protocols: Network switches support various industrial protocols like PROFINET, EtherNet/IP, and Modbus TCP, ensuring seamless integration with PLCs and other devices using these protocols.
Enhanced Diagnostics and Monitoring: Managed network switches provide comprehensive diagnostic tools and monitoring features. These capabilities enable proactive maintenance and troubleshooting, leading to improved PLC programming performance.
FAQ:
Q1. Can I use unmanaged switches for PLC programming?
While unmanaged switches can be used for basic PLC programming tasks, managed switches offer greater control and optimization options. Managed switches are recommended for larger networks and critical applications where enhanced performance and diagnostics are needed.
Q2. Are network switches necessary for small-scale PLC programming setups?
Even in small-scale PLC programming setups, network switches can enhance communication efficiency, reduce network collisions, and improve overall system performance. They ensure seamless data transfer between PLCs and connected devices.
Q3. What is the significance of VLANs in PLC programming?
VLANs allow logical segmentation of the network, creating isolated groups that improve network security and simplify PLC programming management. They enhance data organization and access control, ensuring a more efficient and secure network.
Q4. How do redundant network switches improve PLC programming reliability?
Redundant network switches create fault-tolerant architectures. In the event of a network switch failure, the redundant switch takes over, maintaining uninterrupted PLC programming communication and preventing downtime.
Q5. Can I integrate managed network switches with existing PLC programming setups?
Yes, managed network switches can be seamlessly integrated into existing PLC programming setups. Their compatibility with standard industrial protocols ensures smooth communication with PLCs and other devices in the network.
Conclusion:
Network switches play a vital role in enhancing the efficiency and performance of PLC programming in industrial automation. They enable faster data transmission, reduced network congestion, and deterministic communication, leading to improved system responsiveness and stability. By supporting features like VLANs, QoS, and network red undancy, network switches contribute to streamlined PLC programming management and increased system reliability. Industrial network switches are essential components that pave the way for efficient and seamless communication, ensuring smooth and precise control in industrial automation applications. By understanding the role of network switches and their benefits, industries can optimize PLC programming efficiency and achieve superior performance in their automation processes.
0 notes
Text
Network switches
What’s a network switch ?
A switch is a device used in computer networks to connect multiple devices together within a single local area network (LAN). Its main role is to facilitate communication between different connected devices, such as computers, printers, servers, IP phones, etc.
It is a mini-computer which is made up of RAM, ROM, flash RAM, NVRAM, a microprocessor, connectivity ports and even an operating system.

RAM
RAM (Random Access Memory) contains the current configuration of the switch and temporarily stores the MAC address table, which is then processed by the microprocessor.
Microprocessor
The microprocessor is the heart of the switch, responsible for data processing, including switching and creating links between multiple devices.
External memories
External memories, such as flash RAM, ROM, and NVRAM (Non-Volatile RAM), store configuration files , different versions of the IOS , etc ...
Ports
The switch ports are the communication interfaces of the switch. There are several of them, generally 24 for a Cisco switch. Each port is associated with an LED which indicates its status and activity.

How does it work ?
Now how does a switch work to transfer information from one machine to another?
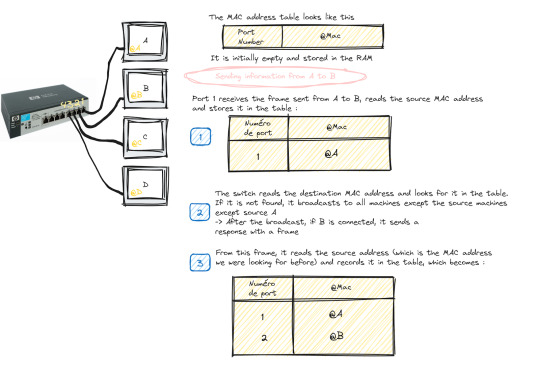
Suppose we have 4 machines: A, B, C and D connected to our switch in ports 1, 2, 3 and 4 as follows:

The switch only works with MAC addresses , so basically we have an empty MAC address table stored in RAM as soon as the switch starts up which looks like this :

Transmitting data from machine A to machine B happens in the following steps:
Machine A sends a frame to machine B
Once this frame arrives at port 1 (which is the one linked to A), the switch reads the source MAC address and stores it in the MAC address table
The switch reads the destination MAC address and looks for it in the table, if it is not in the table, it broadcasts to all the active machines connected to the switch except the source one.
If the port linked to the machine we want is active, it sends a response frame from which the switch reads the MAC address we were looking for (@B)
Once done, it records the MAC address of B in the table.

This process repeats until the switch reaches what is called "MAC address table stability", that is to say it knows all the MAC addresses of the connected machines and has no more need to broadcast.
Starting and configuring a switch
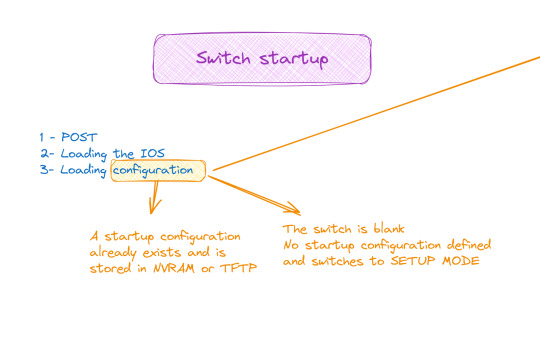
When it comes to booting a switch, the process is similar to that of a traditional computer system:
POST (Power-On Self Test): The switch performs proper functioning tests on all hardware.
Loading IOS (Internetwork Operating System): The switch operating system is loaded.
Loading the configuration. At this stage we have two cases:
Either the switch already has a startup configuration defined and stored in NVRAM
Either the switch is blank and it is up to us to define the startup configuration when it goes to setup mode
Switch configuration

The configuration of a switch is done through different modes, such as user mode, privileged mode and global configuration mode, which allows access to specific configuration modes, such as interface mode, routing mode, line mode, etc.
And to do all this of course you must first connect the switch with the machine via the console cable and open a terminal emulator
💡 It should be noted that the only machine that can configure the switch is the one connected to it by a console cable, the others are only hosts.
#software#network switches#codeblr#code#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code
99 notes
·
View notes
Text
Game crashed in the middle of trying to pose Estinien with the trans flag, this is homophobic :/
#at least i saved the pose i got aymeric's flag into before it died on me GOD that was such a pain#gonna switch to my hotspot bc it was a network error twitch died on me too
8 notes
·
View notes
Text
When people ask Buck if he has feelings for Eddie, it is so important to note that he never outright says no.
A denial is easy when it's true. You just say 'no.'
'He's straight!'
That's not a no.
If you ask someone a yes or no question and they ask another question...
"I live in Eddie's house therefore I must be in love with him?"
"Are you?"
"In love with Eddie?"
Instead of saying 'yes' or 'no'?
They're evading because they don't want to answer and reveal something else.
Also WHY HAVE TOMMY SCOFF AT EDDIE BEING STRAIGHT?
I just. I am bracing myself for the disappointment next week guys cause it's not gonna happen and I am so tired of these fucking writers.
#911 abc#you're crashing out#not me#im not premourning the fact that they could give us feelings realisation next week and they wont#because its been 8 seasons#about to be 9#and they havent done it yet#i thought the network switch would be the thing#but nope#and if this arc#with eddie leaving#buck moving into his house#bucks ex accusing him of feelings#both of them losing their captain#eddie getting chris and his joy back#and buck looking for family connection#doesnt lead to them getting together?#i think we're done#what the fuck else could they put them through at this point#that would get them there?#nothing#buddie#911 spoilers#911on abc#911 reaction
17 notes
·
View notes