#manufacturing network strategy
Explore tagged Tumblr posts
Text
Top 3 ways to develop your manufacturing network strategy
A manufacturing network includes various entities that are interconnected such as functions, transactions, and operations that are part of the production process. Therefore, what goes through your manufacturing setup is what makes it efficient and bulletproof. To build such an efficient manufacturing network, there are numerous factors to keep in mind. Today, we will discuss some of these factors that can affect a manufacturing network and how to work around them to build an effective manufacturing network strategy!
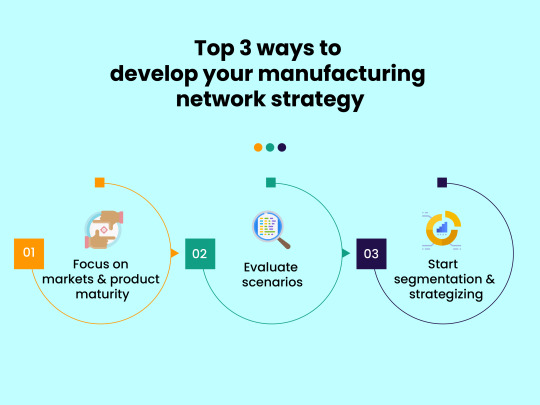
How to design a strategic manufacturing network?
1. Focus on markets & product maturity When it comes to manufacturing, almost every manufacturer commits to long-term projects. So, product analysis and product market analysis are essential. The reason behind this is that, while you have agreed to fabricate a product of limited quantity, there is not much to do except produce and deliver. But when it comes to long-term product factors such as product demand, product maturity, product development, and others, they weigh in. By contradicting the traditional methods, you can incorporate these factors into your production process to formulate the ideal production network.
2. Evaluate scenarios A manufacturing network has various components, including logistics, sales, marketing, labour, transportation, etc. To improve the performance of the entire production network, you should first examine and document everything that is currently going on in the network. Based on this report, you can make changes to the processes for better results. You can also include corporate guidelines at the beginning of the manufacturing network design to establish the decision-makers and identify any hot buttons throughout the process.
3. Start segmentation & strategizing Once the evaluation is complete, the next logical step is segmentation. Based on pertinent factors, you can segregate the processes and their functions. You can use supply chain analytics and value chain analytics for the betterment of your manufacturing network strategy. These tools help you separate the procedures without compromising the quality of your production process.

In the end, what matters most is a satisfied client & happy end user. This is why there are various things to be considered before, during, and after fabricating a product. With over 25 years of experience in the industry, we at Radiant Appliances & Electronics can proudly say that we have mastered the art of manufacturing. Even though we have come quite far, we still have a lot to learn and a long way to go. Visit our website to know more about our manufacturing system and how we ensure product fabrication without compromising on quality!
#radiant appliances & electronics#home appliances manufacturers in india#led tv manufacturers in india#manufacturing#tv manufacturing company#ems manufacturing company#ems manufacturing company in india#electronic manufacturing services#ems manufanufacturer#smart led televisions#manufacturing network#manufacturing network strategy#strategic manufacturing network
0 notes
Text
Obama’s Global Spy Network Targeted Trump: Explosive New Evidence Revealed!
Barack Obama’s shadowy betrayal has surfaced, shaking the very core of America. He orchestrated a treasonous conspiracy, weaponizing global intelligence networks to attack Donald Trump—a man who dared to challenge the globalist cabal.
Project Fulsome: A Web of Treason
Obama, in collaboration with Britain’s GCHQ, bypassed U.S. laws to spy on Trump, his family, and his campaign. Trump Tower wasn’t just wiretapped—it was a surveillance fortress. Tools designed for counter-terrorism were turned against an American citizen. Financial records, emails, and private conversations were infiltrated, with the Deep State feeding this intel to fabricate scandals.
This was no ordinary operation; it was a globalist vendetta to preserve their crumbling grip on power. Secret satellites even tracked Trump’s movements during the 2016 campaign. Every action, every word—monitored.
The Russia Hoax: Manufactured Lies
The infamous Russia hoax wasn’t an accident. Phony dossiers, funded by Clinton’s allies and legitimized by Obama’s corrupted agencies, were part of this operation. The Steele dossier? Pure disinformation. Whistleblowers reveal it was a long-planned strategy to discredit any outsider who challenged their rule. Trump just happened to win, making him target #1.
Black Sites and Secret Courts: Deep State Tools
Beyond spying, Obama’s network used secret courts and black sites to crush Trump’s allies. FISA warrants based on lies enabled illegal surveillance. Black sites deployed rogue operatives to infiltrate Trump’s inner circle, feeding intel back to the cabal.
Why They Had to Stop Trump
Trump’s presidency represented a direct threat to their empire. He promised to end endless wars, dismantle corrupt trade deals, and expose their hidden agendas. The globalist pipeline funding their machine was at risk. Trump wasn’t a puppet—he was their worst nightmare.
The Awakening: Deep State on the Brink
The Deep State is collapsing. Whistleblowers are stepping forward. Leaks are surfacing. Patriots within the intelligence community are exposing the truth. Platforms like X and Telegram bypass Big Tech’s censorship, spreading revelations far and wide.
The Fight Isn’t Over
Obama’s betrayal exposed the elites’ desperation. Now is the time to act. Share the truth. Demand accountability. Stand with Trump. The Deep State is crumbling, but the battle for freedom continues.
You would think ALL that 👆 would be something you'd see in a spy/espionage movie like "Enemy of the State" with Gene Hackman and Will Smith.
Stay vigilant. History will remember those who fought for truth. 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do some research#do your own research#do research#ask yourself questions#question everything#news#obama#barack obama#government corruption#lies exposed#evil lives here#spying#treason
479 notes
·
View notes
Text

(Dec. 1)
Article: Recruiters Drop Elbit Systems after Palestine Action Campaign
After weeks of action, the sole recruiters for the British operations of Israel’s largest weapons company, Elbit Systems, have confirmed via email to Palestine Action that they ended their association with Elbit on the evening of the 29th November. For two months, activists in the Palestine Action network had disrupted iO Associates at their premises across the country, to impede their ability to recruit roles for Israel’s war machine.
iO Associates recruited the likes of engineers, software developers, and finance staff for positions across the sites of the British branch of Israel’s largest weapons company, Elbit Systems. Elbit are the largest supplier to the occupation military, providing the vast majorities of its drones, munitions, surveillance gear, and parts for its tanks, jets, and precision missiles. From Britain specifically, they manufacture parts for Israel’s killer drones, along with weapons sights, tank parts, and more, exporting these technologies to Israel in great volume yearly. This is the nature of the business that IO was Associates with, and were IO Associates biggest client.
In response to their facilitation of Elbit’s criminal activities, iO’s offices were stormed and occupied in Manchester on the 1st September, and again on the 7th October. Activists painted iO offices red on October 9th in London, Reading, and Manchester. They were forced to vacate their Manchester offices from the 11th October, after the premises were also stormed by the Youth Front For Palestine, and then finally targeted in Edinburgh twice, on the 11th and 17th October. After being forced to vacate their offices, having their online presence tarnished, and (as confirmed to us by former employees) losing their staff who resigned in opposition to their arms trade partnership, iO Associates have finally cut ties with Israel’s weapons trade.
This is part of an expansive strategy by Palestine Action, by disrupting the suppliers and facilitators of Elbit’s presence in Britain. It has seen Elbit’s accountants (Edwards), haulage providers (Kuehne + Nagel), landlords (JLL) and many other complicit companies targeted, alongside the hundreds of actions at Elbit sites themselves, continuing to resist the presence of Elbit warmongers in Britain, and constantly reminding those associated with them that they have blood on their hands.
As a result of iO Associates dropping Elbit Systems, the recruiters have been removed as a target of Palestine Action’s campaign. All targets who still facilitate Israel’s weapons trade are listed on elbitsites.uk
1K notes
·
View notes
Text
Dandelion News - February 22-28
Like these weekly compilations? Tip me at $kaybarr1735 or check out my Dandelion Doodles! (This month’s doodles will be a little delayed since I wasn’t able to work on them throughout the month)
1. City trees absorb much more carbon than expected

“[A new measurement technique shows that trees in LA absorb] up to 60% of daytime CO₂ emissions from fossil fuel combustion in spring and summer[….] Beyond offering shade and aesthetic value, these trees act as silent workhorses in the city’s climate resilience strategy[….]”
2. #AltGov: the secret network of federal workers resisting Doge from the inside
“Government employees fight the Trump administration’s chaos by organizing and publishing information on Bluesky[…. A group of government employees are] banding together to “expose harmful policies, defend public institutions and equip citizens with tools to push back against authoritarianism[….]””
3. An Ecuadorian hotspot shows how forests can claw back from destruction

“A December 2024 study described the recovery of ground birds and mammals like ocelots, and found their diversity and biomass in secondary forests was similar to those in old-growth forests after just 20 years. [… Some taxa recover] “earlier, some are later, but they all show a tendency to recover.””
4. Over 80 House Democrats demand Trump rescind gender-affirming care ban: 'We want trans kids to live'

“[89 House Democrats signed a letter stating,] "Trans young people, their parents and their doctors should be the ones making their health care decisions. No one should need to ask the President’s permission to access life-saving, evidence-based health care." "As Members of Congress, we stand united with trans young people and their families.”“
5. Boosting seafood production while protecting biodiversity

“A new study suggests that farming seafood from the ocean – known as mariculture – could be expanded to feed more people while reducing harm to marine biodiversity at the same time. […] “[… I]t’s not a foregone conclusion that the expansion of an industry is always going to have a proportionally negative impact on the environment[….]””
6. U.S. will spend up to $1 billion to combat bird flu, USDA secretary says
“The USDA will spend up to $500 million to provide free biosecurity audits to farms and $400 million to increase payment rates to farmers who need to kill their chickens due to bird flu[….] The USDA is exploring vaccines for chickens but is not yet authorizing their use[….]”
7. An Innovative Program Supporting the Protection of Irreplaceable Saline Lakes

“[… T]he program aims to provide comprehensive data on water availability and lake health, develop strategies to monitor and assess critical ecosystems, and identify knowledge gaps to guide future research and resource management.”
8. EU to unveil ‘Clean Industrial Deal’ to cut CO2, boost energy security

“The bold plan aims to revitalize and decarbonize heavy industry, reduce reliance on gas, and make energy cheaper, cleaner, and more secure. […] By July, the EU said it will “simplify state aid rules” to “accelerate the roll-out of clean energy, deploy industrial decarbonisation and ensure sufficient capacity of clean-tech manufacturing” on the continent.”
9. Oyster Restoration Investments Net Positive Returns for Economy and Environment

“Researchers expect the restored oyster reefs to produce $38 million in ecosystem benefits through 2048. “This network protects nearly 350 million oysters[….]” [NOAA provided] $14.9 million to expand the sanctuary network to 500 acres by 2026 […] through the Bipartisan Infrastructure Law.”
10. Nations back $200 billion-a-year plan to reverse nature losses

“More than 140 countries adopted a strategy to mobilize hundreds of billions of dollars a year to help reverse dramatic losses in biodiversity[….] A finance strategy adopted to applause and tears from delegates, underpins "our collective capacity to sustain life on this planet," said Susana Muhamad[….]”
February 15-21 news here | (all credit for images and written material can be found at the source linked; I don’t claim credit for anything but curating.)
#hopepunk#good news#carbon capture#climate change#trees#altgov#us politics#resistance#government#doge#bluesky#reforestation#ecuador#gender affirming care#trans rights#protect trans kids#seafood#biodiversity#farming#fish farming#bird flu#usda#great salt lake#migratory birds#science#clean energy#european union#oysters#habitat restoration#nature
80 notes
·
View notes
Text
Let me make this even clearer. Because Jensen and Misha both deserve better.
Given that we know they talk a lot about Destiel among themselves. They have told us, repeatedly. They've shared each other's perspectives with each other. They have an understanding.
Early misunderstandings and conflicts in pov aside (and do people want to keep circle jerking as if it's still 2014? Okay then. Have at it, but time moved on and you didn't): Jensen doesn't speak over Misha. Misha doesn't speak over Jensen.
Some things Misha has said about Dean or Destiel has resulted in Jensen stans attacking him. They always have some excuse--this past weekend it was because Misha acknowledged the idea of Dean and Cas having sex.
In the past, another example, backlash came at Misha for saying Cas saw love and acceptance in Dean's eyes.
(Which...sure does seem like the pearl-clutching about Misha's CR8 comments being too ribald is fake virtue signaling doesn't it, since even a statement from Misha wide open to platonic or romantic reading, that is 100% true about Dean, and how loving he is, how loving we know Dean is, how much we know Dean is going to accept and love Cas either way, got hatred aimed at Misha as if he had said something heinous. Tells me all I need to know about certain stans).
While Jensen's "Cas is an angel therefore his love is cosmic and unknowable impossible for humans to grasp let's not define it" and "open to interpretation" middleground to appease both sides and treading carefully for reasons, on a topic that's napalm in fandom (it shouldn't be, but that's the reality), might be construed as speaking over Misha.
But here's the thing!!! It's not!! From either of them!!
It seems very obvious by now that they decided Misha would be the loud one, with Jensen holding his cape, even if he doesn't join in , and Jensen walking a diplomatic middle line, also with Misha's understanding and support in turn.
When Misha goes off boldly about Destiel? People need to kick out that hate fantasy about Jensen being disrespected and Jensen must be wanting to punch Misha and Jensen must be so mad at Misha how dare Misha out of their heads, or get to the point where they can comprehend the difference between their own feelings vs Jensen's and quit projecting.
They didn't shut each other out. They talked about Destiel. They listened to each other. Highly likely, in fact, that they helped each develop or refine their talking points.
Neither of them has been shooting off their mouth about the other's character without having spoken to each other.
I don't have any hope for fans to stop the endless fighting and concern trolling and attacking either Jensen or Misha over it, needlessly, perpetually, but when it comes to Jensen and Misha...that's a hopeful space.
Misha's bluntness vs Jensen's carefully chosen middleground words complement each other are not in fact oppositional takes--they complement each other, there's room for both. They both know it's a mutually loving relationship.
Neither is trampling on the other's pov, and any views that don't perfectly align, they've already discussed and they respect each other.
These accusations at either of them are not true, they are not fair, and they both deserve better.
And now I'm staring right at a recent thing where Misha full on absolved Jensen of an accusation that various lanes kept throwing at him, and still weaponize, including Jensen stans who claim to be defending Jensen, because they want it to be true.
The response was manufactured drama where people called Misha a liar and doubling down.
They'd rather Jensen take the fall and they'd rather call Misha a liar than believe a soulless corporation that has been caught more than once exercising queer censorship could have committed queer censorship in a TV industry where it's common knowledge that queer censorship by broadcast TV networks happen???????
Wow gee can you feel the love in this Chili's. Great going. Excellent defense strategy. You're really such a big help. With fans like these, Jensen and Misha don't need antis.
A lot of it is agenda driven, and some anxiety driven, every lane's worried about other lanes react, because spn fandom is always a pain in the neck that way. Some people hate Destiel so much they need Jensen to be their antidestiel warrior they'll throw Jensen under a bus and stan for the corporation, or they're so anxious about how Destiel gets treated they blame Jensen and forever hold against him his past foot in mouth about the ship (which was a long time ago. Please stop punishing him endlessly when he's moved on and his perspectives are respectful, yet you're still stuck back there) rather than comprehending the actual systemic factors.
Jensen and Misha are both doing what they can to make it better.
They are trying to fix it!!!
People should show them more respect!!!!
144 notes
·
View notes
Text
Renheng- Xingyue Apocathery Diaries Au anyone? 👀👀
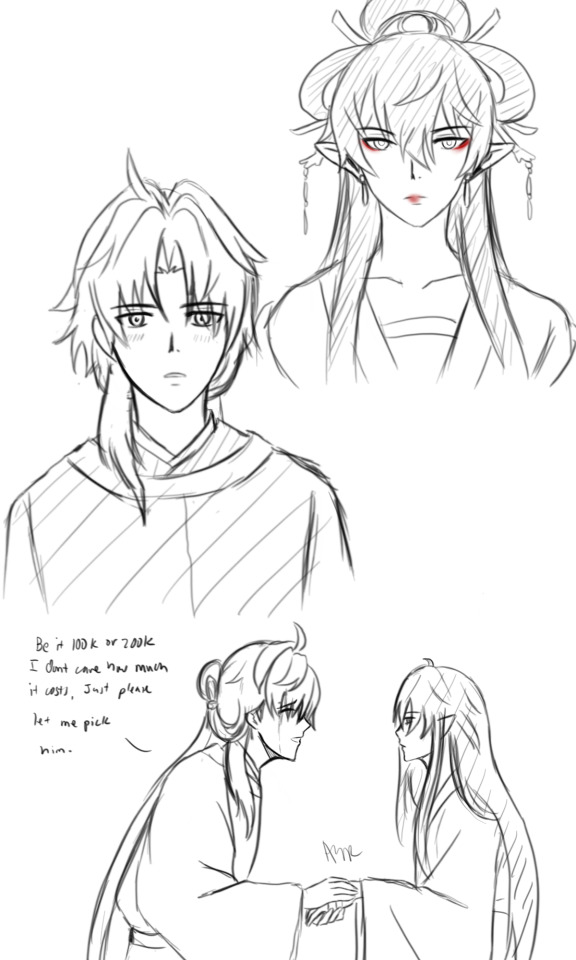
Click read more for a little bit of plot brainrot
Renheng part:
Jinshi = Ren
Maomao = Dan Heng
Lihaku = Jing Yuan
Gaoshun = Kafka
Basen = Silver Wolf
Xiaolan = March and Stelle
Dan Heng entered the imperial palace to work as an archivist/Record Keeper
Ren and the rest of the Stellaron Hunters work in the internal affairs department/ spy network but are posing as a minor palace department on the records.
Ren hires DH after witnessing his talents and him preventing a disaster that might shake the imperial palace. Dan Heng hates working for Ren.
He finds him annoying while Ren is amused because most people look at him with fear but Dan Heng reaction is new to him. It's not fear but mere annoyance and disgust he finds cute.
March works inside the inner palace as a court lady to one of high ranking consorts
Stelle works outside the palace and is sorta affiliated with the spy network department but not directly.
Her infos is more on the underbelly side; both of them will be very good in hearing the gossip and various wealth of info in the palace.
One time during one of their investigative missions, they were running away from an assassin with a gun and jumped down a waterfall to escape.
When they are trying to find a way out of the cave behind the waterfall Ren carried Dan Heng on his shoulders to give himi leverage since there was a hole above but then an actual frog jumped on his head startling him which made them lose balance.
So the two fell down into a suggestive position and Dan Heng’s hand was in Ren’s crotch that;s how he found out how BIG his weapon is, but Dan Heng pretended that nothing happened and just said "im sorry i may have crushed a frog"
Good luck to his forbidden archives that Ren will explore someday
Xingyue part:
Lakan = Yingxing
Fengxian = Dan Feng
Dan Feng is the highest ranking courtesan in Verdigris, he doesn’t sell his body but his art and he is a master of poetry, dance, singing and strategy games. That’s why his bidding wars reach astronomical prices.
Dan Heng is Dan Feng’s son with a court official, Yingxing
Yubie = Madam, Dan Feng’s biological parent and Dan Heng’s grandparent
Yingxing and Dan Feng met in Verdigris when one of his co-workers invited him to get a drink at one of the famous brothel houses in the capital.
Dan Feng is the most sought after cuz let's be serious everyone digs that stare he gives also Yingxing thinks he has beautiful eyes. Dan Feng is untouchable,unlike other courtesans. He is more of an intellectual person and Yingxing fell for that beautiful mind of his.
Yingxing is a low rank government official in the manufacturing/crafts department; at the beginning his salary couldn't afford frequent visits but over time he proves himself capable with his weapon crafts.
Yingxing worked his way up and saved a lot so he could get to spend precious hours with Dan Feng, he isn’t very impressed at first because a lower ranking official that couldn’t ever be a regular to suck money out of, but the passion that Yingxing has for craftsmanship and the desire to use his skills for some greater purpose—far beyond what he sees in most jaded clients—made Dan Feng fall for him.
Sometimes Dan Feng is by the window waiting for when will Yingxing come back but tries not to show how happy he becomes when Yingxing does.
Yingxing may be a formidable opponent in games but he can’t ever really beat Dan Feng in them since Dan Feng wins most of the time he doesn't mind at all! enjoys it even and most of the time he makes it up with his charisma and charm.
Yx: says something witty or flirty to df while making his next move
Df on the outside: hmph
But on the inside: *is melting*
As the two grow closer, they will be distraught on how quickly their time together passes by each time. Around the time Dan Feng price went astronomical and rumors were being bought out so they did the baby trapping that horribly backfired.
Yingxing was sent to war and was gone for a long time for a few years. He got what he needed a high enough salary to buy out df but it was too late seeing the state the house is in and how yubie is chasing him away make it seem like Dan Feng died.
Yingxing was in despair and blamed himself for everything he wished he could turn back time. when he found out but got hope when he saw his son Dan Heng with his adoptive mother Baiheng who took care of Dan Heng in the years both parents were not available.
Time skip to present with him redeeming a courtesan cuz he lost a bet with his son. He got a lotus flower as clue from Dan Heng that Dan Feng is still alive but like lost his mind and sick.
When Yingxing found out that Dan Feng was hidden in one of the sick rooms of the brothel, he immediately ran toward it.
He opens the door and sees Dan Feng still as beautiful as the day he met him.
He chooses to redeem Dan Feng no matter the price. They got married but sadly Dan Feng died a few months after.
#renheng#xingyue#hsr dan heng#hsr dan feng#hsr blade#hsr ren#hsr yingxing#dan heng#dan feng#yingxing#hsr#honkai: star rail#honkai star rail#my art#fan art#sketches#yingxing and blade are two diff people unrelated to each other here#this was just a lil fun au#also im sorry for my shit handwriting 🥲
80 notes
·
View notes
Text
HAIL ERIS, HAIL THE ALT: DISCORDIANISM, MULTIPLE IDENTITIES & THE ART OF CONTROL
Alright lads, buckle up. We’re about to crack open a cold can of metaphysical anarchy and pour it straight over the smug, self-important face of reality itself. That’s right, today we’re talking about Discordianism, multiple identities, and how the ancient art of taking the piss has become a full-blown ideological warfare tactic in the digital age.
CHAOS, CONTROL & MAKING SH*T UP
Discordianism: is it a religion? A joke? A practical guide to hacking the universe with nonsense? Yes.
Founded in the ‘50s by two blokes who decided that gods should be pranksters rather than puritanical killjoys, Discordianism is what happens when spirituality gets hijacked by surrealists. The whole thing revolves around Eris, the Greek goddess of chaos, and the idea that order is just a myth sold to you by people who want to control your life.
In this worldview, reality isn’t a fixed structure—it’s a playground of lies, where names, identities, and even fundamental truths are just props in an ongoing prank war. And if that sounds a bit like the internet, congratulations, you’ve figured out where this is going.
FAKE PEOPLE, REAL POWER
Now let’s talk about the modern battlefield: alt accounts, AI-generated personas, deepfake influencers, and the absolute existential horror of never knowing if you’re arguing with a human or a shell script designed to wind you up.
This isn’t some dystopian Black Mirror future—it’s right now. And the way we navigate it? Same way cracker groups did back in the ‘90s.
Ah yes, the cracking scene—a lawless digital tavern where hacker crews ran wild, stealing software, slapping their names on intro screens, and flexing harder than a lad who just maxed out at the gym. But here’s the thing: half those “members” you saw in cracking group rosters? Didn’t f*cking exist.
Cracker crews had a little trick: inflate the roster with fictional members. More names = bigger presence = instant credibility. “Silent Mike” might’ve been listed as the best code-slicer in the scene, but in reality, Silent Mike was just Steve pretending to be three people because it made his crew look more elite. The world ran on perception, not reality.
Sound familiar? Because it’s exactly how social media wars, marketing psyops, and modern Discordian mind games operate today.
OPERATION MINDF*CK 2.0
There’s an old Discordian principle called Operation Mindfuck—a simple, elegant idea that the best way to break the system is to saturate it with so much noise that it collapses under its own weight.
Now imagine that, but turbocharged with burner accounts, AI-generated trolls, and a dozen fake influencers all reinforcing each other’s fiction. That’s not a dystopian future—that’s your f*cking Twitter feed right now.
“Alt accounts for arguing with yourself?” Welcome to standard discourse.
“Corporate sock-puppeting to manufacture fake trends?” Every brand is doing it.
“Political psyops using networks of fake accounts to simulate grassroots support?” That’s just called Tuesday.
We’re all stuck in a reality-distortion warzone where half the identities floating around online were conjured out of thin air, and yet they shape the way people vote, buy, and think.
THE SACRED ART OF SH*TPOSTING AS SELF-DEFENCE
So where does that leave the modern Discordian, the enlightened chaos-worshipper navigating this neon-lit hellscape? Simple: you play the game.
You don’t fight the nonsense, you embrace it. You become a trickster in a world of straight-faced lunatics. You create counter-fiction, you sabotage expectations, and most of all, you refuse to play by the reality that’s being handed to you.
Whether that means:
Running alt accounts to mess with corporate astroturfing
Inventing fake personas to hijack algorithms
Building your own “influencer network” of fictional characters just to break the system from within
The fact is, multiple identities are no longer optional. They’re a survival strategy. The game has changed, but the old rules still apply: if you’re not in control of your own narrative, someone else is.
HAIL ERIS. HAIL THE ALT. NOW GO OUT THERE AND F*CK WITH REALITY.
17 notes
·
View notes
Text
RideBoom Demonstrates Strong Interest in the EV Revolution with New Initiatives
RideBoom, a leading ride-hailing platform, today announced its unwavering commitment and strong interest in the electric vehicle (EV) revolution. As the world moves towards a greener and more sustainable future, RideBoom aims to play a pivotal role in the adoption of electric vehicles and contribute to the reduction of carbon emissions.
With the growing concern for environmental impact and the need for sustainable transportation solutions, RideBoom recognizes the urgent need to transition to cleaner and greener mobility options. As part of its long-term strategy, RideBoom is actively exploring various avenues to integrate electric vehicles into its fleet, promoting the use of EVs among its driver partners, and offering reliable and eco-friendly transportation services to its customers.
RideBoom's interest in the EV revolution stems from its firm belief in the positive impact that electric vehicles can have on the environment and society as a whole. By transitioning to electric vehicles, RideBoom aims to significantly reduce carbon emissions, improve air quality, and contribute to global efforts in mitigating climate change.
To kickstart its EV initiatives, RideBoom has already begun engaging in partnerships with leading electric vehicle manufacturers and is actively working towards creating a robust infrastructure to support the widespread adoption of electric vehicles. This includes establishing strategic partnerships with charging station networks, investing in charging infrastructure, and incentivizing driver partners to transition to electric vehicles through various programs and benefits.
Additionally, RideBoom plans to launch a dedicated electric vehicle program that will provide attractive incentives and support for its driver partners who choose to operate electric vehicles. RideBoom's CEO (https://www.linkedin.com/in/harry-malhi-87671254/), Harminder Malhi known as Harry Malhi, expressed excitement about the company's interest in the EV revolution, stating, "At RideBoom, we are fully committed to embracing the EV revolution and driving the transition towards sustainable transportation. By integrating electric vehicles into our fleet, we aim to create a positive impact on the environment and contribute to the overall well-being of the communities we serve. We believe that by working together with our driver partners, customers, and industry stakeholders, we can build a brighter and greener future."
As RideBoom (https://www.linkedin.com/company/RideBoom) continues to expand its operations globally, the company remains dedicated to exploring innovative solutions and collaborating with industry leaders to accelerate the adoption of electric vehicles.
About RideBoom:
RideBoom is a leading ride-hailing platform committed to providing reliable, convenient, and sustainable transportation solutions. With a focus on customer satisfaction and environmental responsibility, RideBoom aims to revolutionize the way people move, promoting greener alternatives such as electric vehicles to contribute to a cleaner and healthier planet.

#rideboom#rideboom app#book cabs online#book bike taxi#book taxi online#cabservice#cabs near me#cabs in india#ride share#bike ride#taxi#best taxi service#taxi service#rideboom taxi app#delhi rideboom#rideboom india
45 notes
·
View notes
Text
Over the last decade, the Kremlin's most aggressive cyberwar unit, known as Sandworm, has focused its hacking campaigns on tormenting Ukraine, even more so since Russian president Vladimir Putin's full-scale invasion of Russia's neighbor. Now Microsoft is warning that a team within that notorious hacking group has shifted its targeting, indiscriminately working to breach networks worldwide—and, in the last year, has seemed to show a particular interest in networks in English-speaking Western countries.
On Wednesday, Microsoft's threat intelligence team published new research into a group within Sandworm that the company’s analysts are calling BadPilot. Microsoft describes the team as an “initial access operation” focused on breaching and gaining a foothold in victim networks before handing off that access to other hackers within Sandworm’s larger organization, which security researchers have for years identified as a unit of Russia’s GRU military intelligence agency. After BadPilot's initial breaches, other Sandworm hackers have used its intrusions to move within victim networks and carry out effects such as stealing information or launching cyberattacks, Microsoft says.
Microsoft describes BadPilot as initiating a high volume of intrusion attempts, casting a wide net and then sorting through the results to focus on particular victims. Over the last three years, the company says, the geography of the group's targeting has evolved: In 2022, it set its sights almost entirely on Ukraine, then broadened its hacking in 2023 to networks worldwide, and then shifted again in 2024 to home in on victims in the US, the UK, Canada and Australia.
“We see them spraying out their attempts at initial access, seeing what comes back, and then focusing on the targets they like,” says Sherrod DeGrippo, Microsoft’s director of threat intelligence strategy. “They’re picking and choosing what makes sense to focus on. And they are focusing on those Western countries.”
Microsoft didn't name any specific victims of BadPilot's intrusions, but broadly stated that the hacker group's targets have included “energy, oil and gas, telecommunications, shipping, arms manufacturing,” and “international governments.” On at least three occasions, Microsoft says, its operations have led to data-destroying cyberattacks carried out by Sandworm against Ukrainian targets.
As for the more recent focus on Western networks, Microsoft's DeGrippo hints that the group's interests have likely been more related to politics. “Global elections are probably a reason for that,” DeGrippo says. “That changing political landscape, I think, is a motivator to change tactics and to change targets.”
Over the more than three years that Microsoft has tracked BadPilot, the group has sought to gain access to victim networks using known but unpatched vulnerabilities in internet-facing software, exploiting hackable flaws in Microsoft Exchange and Outlook, as well as applications from OpenFire, JetBrains, and Zimbra. In its targeting of Western networks over the last year in particular, Microsoft warns that BadPilot has specifically exploited a vulnerability in the remote access tool Connectwise ScreenConnect and Fortinet FortiClient EMS, another application for centrally managing Fortinet's security software on PCs.
After exploiting those vulnerabilities, Microsoft found that BadPilot typically installs software that gives it persistent access to a victim machine, often with legitimate remote access tools like Atera Agent or Splashtop Remote Services. In some cases, in a more unique twist, it also sets up a victim's computer to run as so-called onion service on the Tor anonymity network, essentially turning it into a server that communicates via Tor's collection of proxy machines to hide its communications.
Another, separate report Tuesday from the cybersecurity firm EclecticIQ pointed to an entirely distinct hacking campaign that firm also ties to Sandworm. Since late 2023, EclecticIQ found the hacker group has used a malware-infected Windows piracy tool, distributed via Bittorrent, to breach Ukrainian government networks. In those cases, EclecticIQ found, the hackers have installed a remote access tool called Dark Crystal RAT to carry out cyberespionage.
Any sign of Sandworm, which Microsoft refers to by the name Seashell Blizzard, raises alarms in part because the group has a history of hacking operations that go far beyond mere spying. Over the last decade, the group has caused at least three blackouts by targeting electric utilities in Ukraine—still the only such hacker-induced blackouts in history. The group also released the NotPetya malware that spread worldwide and did at least $10 billion in damage, and it used wiper malware to destroy countless networks in more targeted attacks across Ukraine both before and after the 2022 invasion.
Microsoft has so far found no evidence that, in BadPilot's targeting of Western networks specifically, Sandworm has shown any intention to carry out anything other than espionage. “This seems very early in terms of initial resource gathering, trying to get this much persistent access,” says Microsoft's DeGrippo. “Then we would have to wait to see what they do with it.”
But she notes that BadPilot is nonetheless tied to a larger group that has a history of highly disruptive cyberattacks. “Therefore," says DeGrippo, "the potential actions that they could take next is of deep concern.”
9 notes
·
View notes
Text

The Birth of an Industry: Fairchild’s Pivotal Role in Shaping Silicon Valley
In the late 1950s, the Santa Clara Valley of California witnessed a transformative convergence of visionary minds, daring entrepreneurship, and groundbreaking technological advancements. At the heart of this revolution was Fairchild Semiconductor, a pioneering company whose innovative spirit, entrepreneurial ethos, and technological breakthroughs not only defined the burgeoning semiconductor industry but also indelibly shaped the region’s evolution into the world-renowned Silicon Valley.
A seminal 1967 promotional film, featuring Dr. Harry Sello and Dr. Jim Angell, offers a fascinating glimpse into Fairchild’s revolutionary work on integrated circuits (ICs), a technology that would soon become the backbone of the burgeoning tech industry. By demystifying IC design, development, and applications, Fairchild exemplified its commitment to innovation and knowledge sharing, setting a precedent for the collaborative and open approach that would characterize Silicon Valley’s tech community. Specifically, Fairchild’s introduction of the planar process and the first monolithic IC in 1959 marked a significant technological leap, with the former enhancing semiconductor manufacturing efficiency by up to 90% and the latter paving the way for the miniaturization of electronic devices.
Beyond its technological feats, Fairchild’s entrepreneurial ethos, nurtured by visionary founders Robert Noyce and Gordon Moore, served as a blueprint for subsequent tech ventures. The company’s talent attraction and nurturing strategies, including competitive compensation packages and intrapreneurship encouragement, helped establish the region as a magnet for innovators and risk-takers. This, in turn, laid the foundation for the dense network of startups, investors, and expertise that defines Silicon Valley’s ecosystem today. Notably, Fairchild’s presence spurred the development of supporting infrastructure, including the expansion of Stanford University’s research facilities and the establishment of specialized supply chains, further solidifying the region’s position as a global tech hub. By 1965, the area witnessed a surge in tech-related employment, with jobs increasing by over 300% compared to the previous decade, a direct testament to Fairchild’s catalyzing effect.
The trajectory of Fairchild Semiconductor, including its challenges and eventual transformation, intriguingly parallels the broader narrative of Silicon Valley’s growth. The company’s decline under later ownership and its subsequent re-emergence underscore the region’s inherent capacity for reinvention and adaptation. This resilience, initially embodied by Fairchild’s pioneering spirit, has become a hallmark of Silicon Valley, enabling the region to navigate the rapid evolution of the tech industry with unparalleled agility.
What future innovations will emerge from the valley, leveraging the foundations laid by pioneers like Fairchild, to shape the global technological horizon in the decades to come?
Dr. Harry Sello and Dr. Jim Angell: The Design and Development Process of the Integrated Circuit (Fairchild Semiconductor Corporation, October 1967)
youtube
Robert Noyce: The Development of the Integrated Circuit and Its Impact on Technology and Society (The Computer Museum, Boston, May 1984)
youtube
Tuesday, December 3, 2024
#silicon valley history#tech industry origins#entrepreneurial ethos#innovation and technology#california santa clara valley#integrated circuits#semiconductor industry development#promotional film#ai assisted writing#machine art#Youtube#lecture
9 notes
·
View notes
Text
Today's Uber was also my first time riding in a Tesla.
A quick review…
I had no idea how to open the frickin' doors. I know making them flush to the door reduced the drag by a percent or two, but those handles were not intuitive and probably not very ergonomic for people with hand or finger disabilities.
The interior was fine. But it was extremely plain. It reminded me of those bachelor pads of rich tech bros who are super into minimalism.
The giant iPad-like screen to control EVERYTHING seemed silly. And I hate that so many car makers are copying that. Real knobs and buttons can be memorized through muscle memory and are much less of a distraction. With the touchscreen, any change you need to make requires taking your attention off the road and going through menus or even submenus. There is no way to feel the controls without distraction.
The ride was pretty bumpy and uncomfortable. Not sure if that is a suspension issue or if the weight of the batteries causes that. But my car from 2008 has a much smoother ride.
The seatbelt felt cheap and it was extremely difficult to buckle. I kept having to reset it as it would lock up on me before I had enough slack.
Everything in the interior felt cheap. The seat upholstery was this fake leather and felt a bit tacky. And the little A/C vent for the rear seats was very cheap plastic. I felt like I was going to break it when I adjusted the airflow direction.
The good stuff is pretty much the reason people buy Teslas. The acceleration is effortless. Even at slow speeds you could tell. it is very quiet--no blaring engine noise. They have an excellent battery system with industry-leading range and an impressive drivetrain that goes fast and stops fast. I'm sure it is very fun to drive. Just like my brother's muscle cars.
But they put little effort into fit and finish. They did almost nothing to make sure the car was comfortable for passengers. It's like their entire design philosophy was, "As long as it goes fast and has excellent battery life, we can do the bare minimum with everything else."
And that strategy has worked so far. But as I see actual auto manufacturers with decades of experience start to design EVs, I don't think a zippy car will be sufficient for Tesla to stay competitive. Once other companies figure out the charging network dilemma, I think Tesla is going to have some major problems.
97 notes
·
View notes
Text
The scenario you're describing involves a combination of public relations (PR) strategies, celebrity networks, and how the entertainment industry sometimes operates behind the scenes, particularly when it comes to managing public personas and orchestrating narratives. Here’s a breakdown of how Megan Moss, Alba Baptista, and Chris Evans might be connected in a PR context, even without concrete proof like marriage certificates or public images.
1. PR Networks and Industry Connections
Megan Moss (if we assume she’s a PR professional or consultant) would likely have strong connections within the entertainment industry. PR professionals often work with a network of actors, influencers, and public figures across different projects. It’s common for PR teams to coordinate and manage relationships between celebrities, even if there isn’t a personal relationship or public event connecting them.
Alba Baptista and Chris Evans both work in high-profile sectors within the entertainment industry (film, TV, media). They might meet or cross paths through mutual PR connections, industry events, film projects, or networking opportunities. This doesn't necessarily imply that they know each other personally but that their PR teams may coordinate and facilitate interactions for mutual benefit.
2. PR Marriages and NDA Agreements
PR Marriages: A PR marriage is a public relations strategy where two celebrities or public figures "appear" to be in a romantic relationship or even married, even though the relationship might not be real. The purpose of such a marriage can vary — it could help boost the profiles of both parties, create media buzz for a film or project they’re working on, or maintain an image of stability that benefits their public image.
A PR marriage might not have official proof like a marriage certificate or public photos because it’s entirely orchestrated by PR teams. The celebrities involved may never actually marry in a legal or emotional sense.
Non-Disclosure Agreements (NDAs): It’s common in the entertainment world for celebrities, their teams, or anyone involved in a PR arrangement to sign NDAs to prevent leaking of details. These agreements are designed to ensure that no private or behind-the-scenes information is made public. This could cover everything from the details of a PR marriage to the terms of a contract, the nature of a project, or the involvement of certain individuals in the plan.
In the case of a PR marriage, both parties might sign an NDA to keep the arrangement private and control how information is released to the public. The goal is to maintain the illusion of the relationship for media and fan consumption, ensuring it doesn’t disrupt the ongoing careers of the individuals involved.
3. Managing Media Narrative
If Chris Evans and Alba Baptista are involved in a PR marriage, their PR teams would be working to control the narrative and ensure that the media is led to believe that they are romantically involved, even if the relationship is manufactured for public purposes. This could involve creating strategic moments for the press to cover, such as making public appearances together or issuing controlled statements to gossip magazines.
The PR team might also orchestrate stories to tie them together in a way that aligns with each celebrity’s desired public persona, keeping them in the spotlight for their own respective careers (Chris Evans as a leading actor, Alba Baptista as an emerging star).
4. The Role of PR Teams in Marriage Narratives
Megan Moss could be involved in creating and managing narratives for celebrities, and in this case, orchestrating a fake marriage narrative. She would likely work closely with both Chris Evans and Alba Baptista's PR teams to ensure that public perceptions match the fabricated narrative.
By guiding media appearances, social media content, and even carefully planned interviews, PR professionals ensure the story is maintained, making it appear that a relationship exists when it may not.
5. Why Keep the Marriage Quiet?
No Official Proof: Keeping the "marriage" without public pictures or official proof (like certificates) could be a deliberate choice to protect both celebrities’ personal lives and avoid making it too public. This creates a level of mystery and intrigue that benefits both parties' public images. Keeping the relationship "secret" or blurry allows the narrative to be flexible and adaptable to future developments.
PR Marriage Benefits: For Chris Evans, a PR marriage could reinforce his image as a stable, family-oriented person, which could appeal to certain audience demographics, especially those who admire his Captain America character. For Alba Baptista, being associated with a high-profile actor like Evans, even through a PR marriage, could provide a significant career boost by placing her name in the media, driving interest in her projects like Warrior Nun.
6. How Does This Impact Their Careers?
Chris Evans: A PR marriage could be a way to protect his public image, particularly after having had relationships that were highly publicized in the past. This keeps the media from speculating about his private life and provides a narrative that doesn’t distract from his career. It can also help him avoid negative press about his personal relationships.
Alba Baptista: If the PR marriage is real or part of an orchestrated narrative, it could be used as a way to increase her visibility. Being associated with a star like Evans would put her in the public eye more, likely leading to more acting opportunities, endorsements, and media attention.
Conclusion
Even without public photos or a marriage certificate, a PR marriage can be a calculated public relations strategy to shape the public image of Chris Evans and Alba Baptista. Megan Moss or a similar PR professional could be facilitating this narrative, helping both actors manage their public profiles through media appearances, social media posts, and other PR tactics. NDAs and carefully crafted press releases are tools commonly used to ensure that the details of such arrangements stay private, all while benefiting their careers by keeping them in the media spotlight.
2 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
saw a post recently where someone was talking about cybersecurity training at work and questioning the advice to regard http links (as opposed to https) as phishing, and questioning the logic that encryption is even relevant to that case (correct, it's not). and this got me thinking about the state of encryption in general
you know encryption is not in isolation a viable security measure, right? if you hand encrypted data over to a malicious actor who handles the encryption and has the decryption keys you have done absolutely nothing to protect it (this is the point they were making in the post)
this is obviously true and yet it underpins everything from cryptocurrency to bank cards. i said it while i was working at the credit card factory but the switch to EMV chips did nothing but duplicate the data the card carries. it does no good if your physical card is stolen or if the card number is compromised, and the primary method of security in those cases is reissuing the card. the only thing encryption did in that scenario was make card skimmers more complicated, it certainly has not eliminated card skimming or data breaches and it was plainly obvious that it was never going to. but europay mastercard and visa wanted standarization with their names on it and the positive PR from having done something, so it doesn't matter what the truth is
encrypting a public ledger does nothing when its users can be trivially identified by network associations and identification provided at point of sale, which has been for years a requirement for any cryptocurrency exchange. there are ways to attempt to launder it to conceal parts of the relational network or buy it on a black market, but they are also ineffective and unreliable even when used properly, which is a steep learning curve. it would be far more secure to not distribute the ledger to the public! but that is definitionally the foundation of the field. (to split hairs even further, this doesn't mean distributed ledgers are useless, just that they are not appropriate for secure data. this is all a bit beside the point when the entire community has for over a decade been coopted by the most conservative cockroaches you can imagine, and i would not say distributed ledgers have utility sufficient to bother reclaiming it from them)
encrypting communications over protonmail or telegram does nothing except perhaps delay the inevitable when both of them have a demonstrated history of bowing (unwillingly, if i recall!) to government subpoena. neither of these things matter very much when every manufacturer builds in backdoor access for the state. the only viable method of security for communications is not putting them online, and even that is not a complete strategy
10 notes
·
View notes
Text
The Growing Importance of Cybersecurity in IoT Devices

In today's hyperconnected world, the Internet of Things (IoT) is transforming how we live and work. From smart homes to industrial automation, IoT devices are becoming an integral part of our daily lives. However, with this rapid growth comes an equally rapid increase in cyber threats. The need for robust cybersecurity in IoT devices has never been greater.
The IoT Revolution and Risks:
IoT devices are set up to ease lives, but it also involves certain risks with this convenience. There is vulnerability with the likes of smart thermostats, connected security cameras, wearable fitness trackers, or industrial machinery, because these devices all come under hacking opportunities. Through such vulnerabilities, hackers may hack unauthorized, obtain sensitive information, or disable key systems.
For instance, a hacked smart home device might give the attacker access to the homeowner's personal data or even control over their home's systems. Industrial IoT breaches can be a larger threat that might lead to disruptions in manufacturing or energy sectors with severe implications.
The devices of the Internet of Things usually lack serious security measures and therefore become vulnerable to cyber criminals. Many are delivered with the default password, with old firmware or even low-grade encryption; that leaves open a door to be attacked. In general, this vulnerability is made worse because an IoT network will have more than one device in communication with another. One device could become the access point of a gateway into a full network.
The Role of Ethical Hacking in Securing IoT
To this end, cybersecurity experts are increasingly employing ethical hacking as a way to find and remediate vulnerabilities in IoT systems. Ethical hackers, often referred to as "white hat" hackers, utilize their expertise to probe for vulnerabilities in a system before an actual hacker could take advantage of the weakness.
Cyberspace security and ethical hacking courses may be subscribed to, which will train aspiring professionals to secure various IoT devices and networks. These topics include penetration testing, secure coding, as well as network defense strategies suited for IoT environments.
What Can You Do to Stay Safe?
1. Update Regularly: Make sure all IoT devices have the latest firmware updates and patches.
Use Powerful Passwords: Change default passwords with strong unique passwords.
Secure Network: Use a powerful Wi-Fi password and apply network encryption.
Use Minimum Permissions: Give IoT devices the minimum permission required.
Know Cyber Security: Enroll yourself in a cyber security and ethical hacking course that would enhance your knowledge further to protect their devices.
IoT Future Security
As IoT grows, so does the necessity for advanced security. This practice is beginning to have regulations and standards in place from governments and industries for increased security. However, individual awareness and action will remain a critical engine for change.
By prioritizing cybersecurity and investing in ethical hacking knowledge, we can ensure that the IoT revolution brings convenience without compromising safety. Protecting IoT devices isn't just a technical challenge—it's a responsibility we all share. At this juncture, the relationship between IoT and cybersecurity is bound to be of challenges and opportunities. The higher the number of connected devices grows, the bigger the potential is for innovation, and for exploitation. Enroll in a cyber security and ethical hacking course and be ready to stay a step ahead of the threats towards a safer digital future.
Join the IoT revolution; join it with security. All power to the hands of those who can.
2 notes
·
View notes
Text
"Telegram Marketing Hacks: Build Your Audience and Drive Conversions"
Telegram has emerged as a powerful platform for entrepreneurs. With its robust functions, high engagement rates, and developing international consumer base, Telegram offers specific possibilities for manufacturers to connect with their target audience. This manual explores how to leverage Telegram for marketing success.

Creating keyword-rich content for Telegram marketing
Why Choose Telegram for Marketing?
1. Massive User Base
Telegram has over 800 million month-to-month lively users (as of 2023), making it a fertile ground for accomplishing a diverse target audience.
2. High Engagement Rates
Telegram customers generally tend to interact more with content in comparison to other social media platforms. Its notification machine ensures that messages are visible through a huge percentage of subscribers.
Three. Secure and Private
With cease-to-stop encryption, Telegram is a trusted platform for customers concerned approximately privateness, which enables construct credibility to your logo.
4. Rich Features
Telegram gives channels, companies, bots, and media sharing capabilities that allow companies to execute diverse advertising strategies.
Getting Started with Telegram Marketing
1. Create a Telegram Account
Start by way of growing a Telegram account and set up a commercial enterprise profile. Use a expert profile photo, together with your brand logo, and write a compelling bio that describes your commercial enterprise.
2. Choose Your Marketing Approach
Decide whether or not to apply:
Telegram Channels: Best for broadcasting messages to a huge target audience.
Telegram Groups: Ideal for fostering network and direct engagement.
Bots: Automate customer service, surveys, and lead generation.
Building Your Audience
1. Promote Your Telegram Channel or Group
Share your channel hyperlink across other social media systems, your website, and e-mail newsletters.
Offer incentives, along with distinct content, reductions, or giveaways, to encourage sign-ups.
2. Use QR Codes
Generate QR codes related in your channel and encompass them in offline materials like posters, enterprise playing cards, or product packaging.
3. Collaborate with Influencers
Partner with influencers for your niche who have an active Telegram presence. They can sell your channel or group to their target market.
4. Optimize Your Channel Description
Use key phrases to your channel’s description to make it searchable on Telegram. Include a clean name-to-movement (CTA) that encourages customers to subscribe.
Content Strategies for Telegram Marketing
1. High-Quality Content
Post visually attractive and well-crafted content material. Use pix, films, infographics, and concise textual content to seize interest.
2. Consistency
Maintain a consistent posting schedule. Analyze your target market’s lively hours and put up as a consequence.
Three. Personalized Messages
Use Telegram's personalization functions to segment your target market and send tailored content material. For example, you may use bots to deliver personalised offers.
4. Interactive Content
Encourage engagement by posting polls, quizzes, and questions. For instance, a clothing brand may want to ask, “Which fashion do you decide on?” to collect insights and engage fans.
Leveraging Telegram Features
1. Channels
Channels are excellent for one-manner communique. Use them to:
Share updates, promotions, and announcements.
Provide exclusive content material, together with at the back of-the-scenes movies or early get right of entry to to income.
2. Groups
Groups permit -way verbal exchange. They are top notch for:
Building a community around your emblem.
Hosting Q&A sessions or discussions.
Collecting comments and ideas out of your audience.
Three. Bots
Telegram bots can automate tasks including:
Sending reminders about promotions.
Providing instant customer support.
Collecting email addresses or different leads.
Four. Polls and Quizzes
Use polls to accumulate critiques or comments. Quizzes may be used for academic content or to gamify engagement.
Best Practices for Telegram Marketing
1. Don’t Spam
Avoid overloading your subscribers with messages. Respect their time and keep your updates relevant and concise.
2. Offer Value
Ensure each message can provide price, whether it’s information, enjoyment, or a unique provide.
Three. Encourage Sharing
Make it clean for users to proportion your content. Use CTAs like “Forward this to a friend” to increase your attain.
Four. Monitor Analytics
Use Telegram’s integrated analytics equipment to tune subscriber increase, engagement rates, and content performance. Adjust your method based on records.
Examples of Telegram Marketing Campaigns
1. Product Launch
Use a channel to announce new merchandise. Share teasers, countdowns, and at the back of-the-scenes content material main up to the launch.
2. Exclusive Discounts
Offer specific discounts in your Telegram subscribers. For instance, “Get 20% off with the code TELE20, best for our Telegram community!”
three. Community Engagement
Create a group where customers can speak your brand, percentage opinions, and ask questions. Moderators can ensure the conversation remains fine and relevant.
Four. Educational Content
Share guidelines, tutorials, or courses related to your niche. For example, a fitness brand could publish exercise routines or meal plans.
Measuring Success
1. Engagement Metrics
Track the quantity of perspectives, clicks, and stocks for each put up.
2. Subscriber Growth
Monitor how speedy your channel or organization is growing. A regular growth suggests effective marketing.
Three. Feedback
Use polls, surveys, and direct messages to gather comments from your audience. Ask what content material they find most valuable.
4. ROI
Calculate the go back on investment (ROI) by way of evaluating the cost of your Telegram advertising efforts to the sales generated.
Challenges in Telegram Marketing
1. Building a Subscriber Base
It can take time to develop your target audience, especially inside the preliminary degrees. Consistent promotion and valuable content material are key.
2. Keeping Subscribers Engaged
Maintaining engagement calls for sparkling and thrilling content material. Avoid repetitive posts.
3. Handling Negative Feedback
In agencies, you may come upon grievance. Respond professionally and use poor comments as an possibility to improve.
2 notes
·
View notes