#malware prevention
Explore tagged Tumblr posts
Text
What is WormGPT?
Artificial intelligence (AI) tools are expected to transform the workplace by automating everyday tasks, increasing productivity for everyone. However, AI can also be misused for illegal activities, as highlighted by the new WormGPT system. What is WormGPT? WormGPT is a harmful AI tool designed for cybercriminal activities. It is based on the GPTJ language model, developed by OpenAI, and was…
#AI risks#AI security#Business Email Compromise#Cybersecurity#GPTJ language model#malicious AI tools#malware prevention#online safety#phishing attacks#WormGPT
0 notes
Text
Cybersecurity Threats and How to Protect Your Data
As more of our personal and professional lives move online, protecting sensitive data from cyberattacks has become a top priority. Cybersecurity threats are evolving rapidly, targeting businesses, governments, and individuals alike. By understanding the most common threats and implementing robust security measures, you can greatly reduce the risk of falling victim to a cyberattack. Let’s explore…

View On WordPress
#cyberattack#cybersecurity threats#cybersecurity tips#data breach#data protection#malware prevention#online security#phishing#protect personal data
0 notes
Text
instagram
#Cyber Security#malware prevention#malware ransomware#local business#seo services#hackers#hacking#Instagram
0 notes
Text
Is Your Click Safe? Discover the Power of a URL Safety Checker!

Introduction
With the internet becoming increasingly essential in daily life, so has the threat of online scams, malware, and phishing attacks. Just a single careless click can open the door to a world of risks, from stolen data to financial loss. This reality makes the need for a safe URL checker critical, both for individuals and businesses. A URL safety checker is an essential tool that evaluates whether links are safe before you click on them, adding a vital layer of security to your online experience. In this guide, we’ll explore how a website safety checker works, why it’s crucial for your online safety, and how you can use a variety of URL checkers to protect yourself and your devices.
What Is a Safe URL Checker and Why You Need It
A safe URL checker is a tool designed to verify the safety of a URL or website link before you access it. It analyzes various elements of a URL, from checking for signs of malware to scanning for phishing markers. URL checkers utilize extensive databases and machine-learning algorithms to identify potential threats embedded within websites. With the rapid growth of cyber threats, having a reliable URL safety checker is more important than ever, especially when cybercriminals increasingly rely on deceptive links to access personal data.
Why Do You Need a URL Safety Checker?
Using a URL checker online allows you to verify if a website is secure before you enter sensitive information, like passwords or credit card details. These tools can protect you against common types of cyber attacks, including phishing and malware-infected sites. For anyone who shops, banks, or simply browses online, a website safety checker is an invaluable layer of defense. A single security check URL can save you from potential data breaches or malware infections.
The Role of a URL Safety Checker in Everyday Browsing
For many people, browsing the internet is a seamless experience—until it’s disrupted by a suspicious link or a pop-up warning. A URL safety checker is essential in such situations, allowing users to verify suspicious links. Imagine receiving an unexpected email from a reputable company asking you to click on a link to "update your account." With a phishing URL checker, you can immediately assess whether the link is legitimate or a scam.
How to Integrate Safe URL Checkers in Everyday Use
You can make URL checkers part of your daily browsing habits with browser extensions or dedicated mobile apps. Some URL safety checkers also integrate into web filters, alerting you to malicious links before you even click them. With the rising prevalence of online scams, integrating a reliable website safety checker into your daily browsing is a smart choice to avoid dangerous clicks.
How a Website Safety Checker Protects You from Online Threats
From viruses to phishing scams, online threats are continuously evolving. A website safety checker offers real-time scanning to help you avoid these hazards. By evaluating a link's reputation, scanning for malware signatures, and checking for phishing indicators, a URL reputation checker helps shield your device and personal data from harm. Some advanced tools even analyze the website's SSL certificate and IP reputation, enhancing security.
The Technology Behind URL Scanners
Modern URL checkers utilize AI and machine learning to detect new patterns in cyber threats. For example, Google Safe Browsing, an extensive database maintained by Google, is frequently used by URL scanners to check if a site is flagged for unsafe content. Some tools, like VirusTotal, even aggregate data from multiple security databases, ensuring that the analysis of each link is comprehensive.
Using a URL Scanner to Identify Unsafe Links
If you’re sent a link from an unknown sender, using a URL scanner is a smart first step. These tools can inspect the link's destination without you needing to visit it, and they’ll alert you to any flagged content or suspicious activity. This is especially useful in emails or messages where scams often circulate.
How to Use a URL Scanner
Many popular URL scanners like Norton Safe Web or Kaspersky Threat Intelligence Portal allow you to paste the URL directly for an instant analysis. By performing a security check URL scan before clicking, you add a layer of proactive security to your browsing habits. This strategy is particularly useful when you’re unsure about a link’s origin or if it’s from a source that you don’t trust entirely.
Stay Vigilant: The Importance of a Phishing URL Checker
Phishing attacks are designed to trick users into revealing sensitive information by impersonating reputable entities. A phishing URL checker specifically looks for indicators of a phishing site, such as suspicious URLs, fake SSL certificates, or domain names that mimic trusted brands. With a phishing URL checker, you can ensure that the link isn’t attempting to exploit your trust or steal your information.
How Phishing URL Checkers Identify Dangerous Links
Phishing URL checkers rely on databases of known phishing sites, as well as detection algorithms that analyze website structure and content. For instance, tools like PhishTank maintain lists of verified phishing URLs, allowing you to cross-check URLs against a constantly updated registry. Using these checkers before entering sensitive information can protect you from some of the most common online scams.
The Benefits of Performing a Regular Link Safety Check
Regularly performing a link safety check is a proactive approach to cyber hygiene. Rather than waiting to be alerted to a scam, you can regularly check URLs you encounter, especially in work environments where cyber threats are frequent. By incorporating link safety checks into your routine, you build a habit of cautious clicking, reducing the risk of accidental exposure to malicious content.
Link Safety in Personal and Professional Settings
Whether for personal or business use, regularly scanning links can minimize the impact of cyber attacks. Many businesses now mandate link safety checks to secure their networks against phishing and malware. By adding a website link checker to your digital toolkit, you’re investing in long-term digital safety and protecting valuable data.
Choosing the Best URL Checker Online for Your Security Needs
When it comes to selecting the right URL checker online, consider factors like accuracy, speed, and the scope of detection. While basic URL scanners are free, paid versions often offer more extensive analysis, checking for broader security threats, such as advanced phishing tactics and ransomware.
Top URL Checkers Online
For the best security results, look for URL checkers like ScanURL, URLVoid, or SiteCheck by Sucuri. Each of these tools has unique strengths, from evaluating link reputation to detecting malware and phishing tactics. A URL checker online that suits your specific needs can significantly reduce your vulnerability to online threats.
Conclusion
In a world where one wrong click can lead to identity theft or financial loss, a safe link checker is more than just a tool—it’s a necessity. From basic phishing checks to comprehensive malware scans, URL safety checkers provide critical defenses against a range of online threats. By using URL scanners, incorporating regular link safety checks, and choosing the right online tools, you can transform your browsing habits and shield yourself from common cyber risks. Embracing URL safety practices empowers you to browse with confidence, secure in the knowledge that your clicks are safe.
youtube
#URL safety#safe browsing#internet security#online safety tips#cybersecurity#phishing protection#malware prevention#safe link checker#URL scanner#internet threats#digital security#online protection#data security#safe links#website security#secure browsing#online scams#cyber hygiene#tech safety#protect your data#Youtube
0 notes
Text
Enhancing SASE with Network Sandboxing: A Modern Cybersecurity Approach
In the rapidly evolving world of cybersecurity, businesses must adopt robust strategies to defend against increasingly sophisticated threats. One of the most comprehensive and modern approaches is Secure Access Service Edge (SASE), which combines wide area networking (WAN) with cloud-delivered security services. To further strengthen this architecture, integrating network sandboxing can provide…
#automated threat detection#business cybersecurity#Cloud-Based Security#Cybersecurity#Fiber Internet#firewall as a service#IT security#malware prevention#network sandbox#real-time security#SASE#secure web gateway#SolveForce#Threat Detection#Zero Trust#zero-day threats
0 notes
Text
FUTO keyboard is a Local, private source-available digital keyboard for Android devices with Voice to Text feature.
The early full release version of the keyboard application is available.
Uses local transcription machine learning (Whisper AI) for voice to text, without the use of internet or cloud or data collection.
FUTO Keyboard is intended to be an alternative to Google and Samsung Keyboard on Android devices, since the defaults collect user data.
Video by Louis Rossman of FUTO (posted on July 1, 2024):
youtube
FUTO Keyboard Website Link
#so not technically open source since according to louis rossman - he's trying to prevent false malWare uploads like happened to neWpipe app#on the google play store#text post#o post#app#android#Youtube
12 notes
·
View notes
Text
i think now is a good a time as ever to mention my very brilliant scheme in which i make a malware program and display it on github so that when employers look at the coding things i have done they see the malware and go “this man is very smart he made a computer program that crashes your computer”
Fuck it *shitposts on LinkedIn*
#dont worry the malware will be appropriately labeled as such to prevent accidental malware infectioning#on a completely unrelated note does anyone have advice on how to make malware
61K notes
·
View notes
Text
10 Essential Security Measures to Protect Your Website from Hackers and Malware
In today’s digital world, keeping your website safe is a big worry for Aussie businesses. Sadly, Australia loses heaps of money every year fixing the damage from hackers1. With 56% of WordPress site attacks coming from old plugins2, it’s clear we need to act fast to protect our online stuff and customer info. This guide gives you 10 key steps to keep your website safe from malware and cyber…
#Cyber Threat Mitigation#Cybersecurity Protection#Hacker Defense Tactics#Malware Prevention Strategies#Web Security Best Practices#Website Security Measures
0 notes
Text
Beware of Malicious Apps: The WallConnect Cryptocurrency Scam
A recent discovery by Check Point Research (CPR) has unveiled a dangerous app lurking on Google Play. Named WallConnect, this app tricked users into downloading it under the guise of being a helpful tool for connecting crypto wallets to decentralized applications (dApps). Unfortunately, it led to a shocking theft of around $70,000 in cryptocurrency. The Deceptive Tactics WallConnect, which…
#Block chain#Crypto Awareness#Crypto currency#Crypto Safety#Crypto Scam#Cyber Security#Digital Assets#Fraud Prevention#Google Play#Malware#Online Security#Phishing#Scam Alert#tech news#WallConnect
0 notes
Video
youtube
Supply Chain Attacks
#youtube#Cybersecurity Threats Malware Hacking Vulnerability Protection Awareness Prevention Risk Defense
0 notes
Text
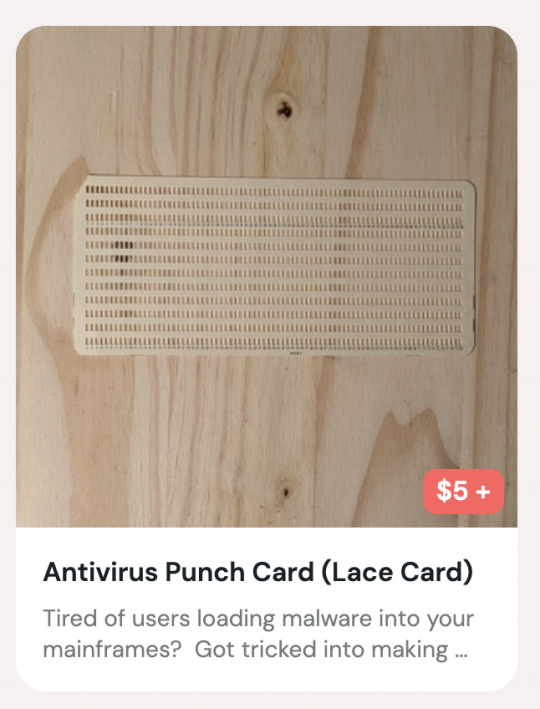
lmao what
Tired of users loading malware into your mainframes? Got tricked into making the mainframe into a blockchain miner? Solve all your problems from bad data with this unique Antivirus Punch Card. Simply run this card through the punch card reader until it is fully integrated into your system. Then your system will reject any bad punch cards from being loaded. Lovingly crafted on a manual keypunch with New Old Stock punch cards. Options: White - Generic 5081 punch card Red - Globe No. 1 5081 punch card Green - IBM United Kingdom 5081 punch card Set of Three - One of each white, red, and green punch cards Note: This is a novelty product. Use in actual card readers at your own risk. This is a lace card, a punch card with every spot punched out, that rejects bad data by breaking apart and jamming the card reader, preventing all data.
this ko-fi store rules
1K notes
·
View notes
Text
Server Saturday: The Importance of Antivirus Software for Your Servers
Welcome to another exciting edition of Server Saturday! 🎉 Today, we’re going to delve into the fascinating world of antivirus software and explore why it’s crucial for your servers. 🖥️✨ Why Antivirus Software Matters Imagine your servers as a bustling city, with data flowing through its virtual streets like busy commuters. Just like in any vibrant city, there are bound to be some unsavory…

View On WordPress
#antivirus software#best antivirus solutions#cyber threat prevention#digital security#malware defense#real-time protection#server protection#server safety#server security#virus protection
0 notes
Text

Over the decades, numerous investigations have exposed how Israeli intelligence targets LGBTQ+ people. In 2013, Vice published an investigation detailing how the Palestinian Authority’s preventative security forces, under the direction of the IDF, had isolated gay Palestinians from their communities, kept files on them, and exploited them for intelligence. In 2015, news reports revealed that a surveillance technology company run by a former Unit 8200 official had helped provide Uganda with malware allegedly used against LGBTQ+ activists.
Click the link for all the details.
2K notes
·
View notes
Text
In one case, Daniel, a Palestinian man who worked for the Catholic church, was threatened by an individual on Facebook who said he had evidence of his homosexuality. “we know that you are a f* you disgrace Christianity and Palestinians with your disgusting nature and I will expose you for what you really are,” the user wrote. “I’m gonna tell the whole world that you are gay and that you are a danger to the children of this society. you are disgusting and you will never get anywhere because I will stop you,” he added. Daniel said the only way someone could have known of his sexuality is if they had monitored his search history. (Drop Site News has changed his name to protect him from retaliation.)
Over the decades, numerous investigations have exposed how Israeli intelligence targets LGBTQ+ people. In 2013, Vice published an investigation detailing how the Palestinian Authority’s preventative security forces, under the direction of the IDF, had isolated gay Palestinians from their communities, kept files on them, and exploited them for intelligence. In 2015, news reports revealed that a surveillance technology company run by a former Unit 8200 official had helped provide Uganda with malware allegedly used against LGBTQ+ activists.
remember tho that israel is a safe haven for the gays
2K notes
·
View notes
Link
Alpha IT Solutions work with a highly trained IT consultation to learn about your managed IT and networking security options. IT management specialists provide tech support, IT cloud security, and cyber security support.
0 notes
Text
Persistence Cyber Security Threat Facing Businesses
As technology advances, cybercriminals continue to develop new tactics to steal sensitive information and disrupt business operations. One of the most persistent threats to businesses is cyber-attacks that are designed to infiltrate and compromise computer systems. These attacks can take many forms, such as phishing, malware, ransomware, and social engineering. The threat of persistent cyber-attacks is real and can cause significant harm to businesses of all sizes.
What is a Persistent Cybersecurity Threat?
Persistent cybersecurity threats are those that are designed to continually attempt to compromise a target system. These threats are often initiated by sophisticated attackers who are highly motivated and well-resourced. They may use a variety of tactics to gain access to a system, such as exploiting vulnerabilities in software, stealing user credentials, or using social engineering techniques to trick users into giving up sensitive information.
Once attackers have gained access to a system, they may use a range of techniques to maintain persistence and avoid detection. For example, they may create backdoors that allow them to regain access to the system after it has been patched or reset. They may also use rootkits to hide their presence on the system, making it difficult for security teams to detect and remove them.
Why are Persistent Cybersecurity Threats a Concern for Businesses?
Persistent cybersecurity threats pose a significant risk to businesses for several reasons. First, they can be difficult to detect and remove. Attackers may use advanced techniques to evade detection by security tools, making it challenging to identify and stop the attack.
Second, persistent cyber-attacks can result in the loss or theft of sensitive information. Attackers may use the access they have gained to steal valuable data, such as customer information, intellectual property, or financial data. This can lead to reputational damage, legal liabilities, and financial losses for the business.
Third, persistent cybersecurity threats can disrupt business operations. Attackers may use their access to the system to launch denial-of-service attacks, ransomware attacks, or other types of disruptive attacks. This can cause significant downtime and lost productivity, resulting in financial losses for the business.
What Can Businesses Do to Protect Themselves from Persistent Cybersecurity Threats?
There are several steps that businesses can take to protect themselves from persistent cybersecurity threats. First, they should implement robust cybersecurity controls, such as firewalls, antivirus software, and intrusion detection systems. These tools can help to detect and prevent attacks, as well as provide early warning of potential threats.
Second, businesses should provide regular cybersecurity training for employees. Employees are often the weakest link in cybersecurity defenses, and attackers may use social engineering tactics to gain access to sensitive information. By providing regular training and awareness programs, businesses can help to reduce the risk of successful attacks.
Third, businesses should conduct regular vulnerability assessments and penetration testing to identify and remediate weaknesses in their systems. This can help to identify potential attack vectors and prevent attackers from exploiting vulnerabilities.
Finally, businesses should have a robust incident response plan in place. This should include procedures for detecting and responding to attacks, as well as steps for mitigating the damage caused by an attack. By having a clear plan in place, businesses can respond quickly and effectively to cyber-attacks, minimizing the impact on their operations and reputation.
In conclusion, persistent cybersecurity threats are a significant concern for businesses of all sizes. These threats can be difficult to detect and remove, and they can result in the theft of sensitive information, disruption of business operations, and financial losses. To protect themselves from persistent cyber-attacks, businesses should implement robust cybersecurity controls, provide regular training for employees, conduct regular vulnerability assessments and penetration testing, and have a robust incident response plan in place. By taking these steps, businesses can reduce the risk of cyber-attacks and protect themselves from the potentially devastating consequences of persistent cybersecurity threats.
#Portland Cybersecurity Solution#Firewall#Data protection#Threat intelligence#Malware detection#Intrusion prevention#Network monitoring#Access control#Vulnerability management#Security audit#Penetration testing#Encryption#Two-factor authentication
1 note
·
View note