#ios 14 features
Explore tagged Tumblr posts
Text


hi guys!! happy october!! i thought id start the new month with a proper theme lol. hope u all r doing okay!! im hoping to start posting more! 💖
#homescreen#apple ios#ios 14 home screen#ios 14 inspo#icons#aesthetic#ios homescreen#widgets#widgetsmith#ios 16#ios 18#ios 18 features#orange aesthetic#orange and white#white aesthetic#white wallpaper#orange icons#white theme#white background#orange theme#ios 14 aesthetic#fall aesthetic#fall wallpaper#fall icons#fall autumn#fall time#fall background#fall vibes#fall leaves#fall season
4 notes
·
View notes
Text
youtube
Learn how to add your name on your iPhone lock screen with this simple tutorial. Personalize your device and make it easy to identify in case it gets lost!
#how to add my name on iphone lock screen#how to add your name to lock screen on iphone 14#how to add your name to iphone lock screen#how to get your name on iphone lock screen#customize iphone lock screen#ios 16 new features#how to add name on iphone lock screen#how to add name on lock screen iphone#Youtube
0 notes
Text


TODOS LOS iPhone X | iPhone X vs iPhone XS vs iPhone XS Max vs iPhone XR COMPARACIÓN ¿CUÁL ES MEJOR? 🔥👉🏿 https://youtu.be/A6Rvy4NgQbY
#apple#iphone#ios#appleiphone#apple ios#apple iphone#iphone se#iphone 14#youtube#iphone 15#iphone 15 pro#iphone 15 pro max#iphone xr#iphonexsmax#iphone x wallpaper#iphone xs#iphone x#ios 17#ios 17 features#ios 17 beta#ios 17 update
1 note
·
View note
Text
#iOS#Beta2#EverythingNew#iOS17Beta2#TechCashPro Everything New in iOS 17 Beta 2 Apple has just released the second beta version of iOS 17 and iPadOS 17 updates to developers. This beta version is used for testing before the official release. Similar to other beta updates for major software updates, this version includes several small adjustments and changes. Apple is making these refinements to improve the operating systems before they are officially launched. We have gathered all the new features and changes that we have discovered in this second beta version so far. keywords: ios 17 beta 2, ios 17 beta 2 features, ios 17 beta 2 download, 17 beta 2 hindi, ios 17 beta 2 changes, ios 17 beta 2 release date, ios 17 beta 2 release, ios 17 beta 2 reddit #EverythingNew#iOS17Beta2#iOS#Beta2TechCashPro
#techcashpro#ios 17 new features#ios 17 how to install#ios 17 how to update#ios 17 beta 2 whats new#ios 17 best features#ios 17 should you update#ios 17 iphone x#ios 17 iphone 14#ios 17 iphone 13#ios 17 iphone 12#ios 17 iphone 11#ios 17 beta 2#everything new#new in ios 17 beta 2#ios 17#beta 2#ios 17 beta#ios 17 features
0 notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes
Text

Download: SFS / Mega
Outfits converted for the MartaXL edit body shape. All are for AF & EF and have fat & preg morphs. Files are compressorized, recolors are BSOK'd.
Full previews, credits and details under the cut.
Hodgekiss Polly dresses
With loafers (2,824 poly) ↓

With sneakers (2,920 poly) ↓

Categorized as everyday. Converted from my edited versions of @hodgekiss's Polly dresses.
~
io Audrey Sweater Rolled Skinnies

Polycount: 2,306. Categorized as everyday. Original sweater and jeans by io / @serabiet.
~
io Cardigan Horne Skirt

Polycount: 3,246. Categorized as everyday. Original cardigan and skirt by io / @serabiet.
~
io Bbdoll Dress



Polycount: 2,966. Categorized as everyday. Original outfit by io / @serabiet. The @berrynooboos textures are from here (I edited most of them for more variety - mostly the socks, also the tops in the case of #24 & #25).
~
Amaryll Slitted Dress





Polycount: 2,282. Categorized as formal.
Original dress by Amaryll. The io / @serabiet retextures (Valene dress) are from here, the @artemida-sims recolors of io's textures are from here, the @skulldilocks retextures are from here.
The shoes' texture and material definition are in the mesh file to save space.
~
MissTiikeri Begging You Dress & Nightie
Dress ↓

Polycount: 7,224. Categorized as everyday. The boots' texture and material definition are in the mesh file to save space.
Nightie ↓

Polycount: blockfeet: 1,890 // Marvine feet: 2,198 // sexyfeet: 6,472 (choose one mesh). Categorized as sleepwear.
Both based on tops by @misstiikeri. The boots are my edit of Klira's 4t2 Shoetopia A Little Death Boots. If you like these boots on MartaXL, I made outerwear featuring them here.
I also have versions of this dress for Maxis-size AF & TF here and for Athletic Girl here.
~
Slip




Polycount: blockfeet: 2,054 // Marvine feet: 2,362 // sexyfeet: 6,636 (choose one mesh). Categorized as sleepwear.
Original mesh by Maxis. The Maxis recolors can be either standalone or repo'd to the Maxis AF & YAF recolors. The @aweeshie textures come from here - the Chalkmetal textures are from their Girl's Night In and Wild sets - the @littlelittlesimmies textures are from here.
I also converted these nighties for Melodie9 fat AF & TF here.
~
Serenity Aster Undies


Polycount: 1,948. Categorized as underwear.
Textures from Serenity's Aster Set 4t2 converted by @kestrelteens (I made some edits).
This is a new mesh distinct from the one I made for the MartaXL swimwear & underwear set. It has no alternative feet options since that wouldn't work with the socks, so feel free to delete the sockless recolors (2 & 14) if you have a 'no blockfeet' policy for your game.
#sims 2#download#body shapes#MartaXL#clothing:everyday#clothing:formal#clothing:sleepwear#clothing:underwear#sims 2 cc#sims 2 download#ts2cc#s2cc
145 notes
·
View notes
Text

Galileo's First Colour Image of Io - July 19th, 1996.
"Above is the first colour image of Jupiter's volcanic moon Io, released by the Galileo Project. The image was made on June 25th, 1996, when the Galileo spacecraft approached within 1.4 million miles. It reveals features as small as 14 miles across - comparable to the resolution of the best 1979 vintage Voyager images. The Voyager flybys discovered active volcanos on Io's mottled surface, and this image indicated that dramatic changes had occurred since, notably in the region of the Masubi volcano, located in Io's southern hemisphere. This region, apparently covered with new deposits of sulfur and sulfur dioxide frost deposited by volcanic eruption, is seen as the pronounced white area at the bottom of the picture. While scientists continued to analyse this image and other Galileo data, the robot spacecraft would continue to explore Jupiter's moons. The next scheduled close encounter was set for September 6th, 1996, with the moon Ganymede. Higher resolution images of Io were also expected during the mission."
65 notes
·
View notes
Text
Alright people. Buckle up cus it's finally time i tell you the history of Animal Crossing!!!! (After putting it off for awhile)
Originally named どうぶつの森 (Doubutsu no mori) in Japan meaning Animal Forest. It was introduced at Spaceworld 2000 in Japan and many people have claimed there was a playable demo there. I believe there is a bit if footage you can find on it but I may be wrong.
Doubutsu no mori released on April 14, 2001 on the Nintendo 64 exclusively in Japan. Only 8 months later on December 14, 2001 they released Doubutsu no mori + for the Gamecube which contained extra features left out of the 64 version such as the museum and the Able sisters (along with house upgrades I believe) and used the Gamecube's built in clock.
Finally, they localised and released the game under the title Animal Crossing: Population Growing in North America on September 16, 2002, Australia on October 17, 2003, and Europe on September 24, 2004 on the Gamecube
However, on June 27, 2003 Japan release yet another version of the game titled Doubutsu no mori e+ where they added even more new features for villagers such as: extended dialogue, the best friend system, sickness, likes/hates, catching fleas, etc. In this version of the game you could use the e card reader to obtain certain items. In this version of the game you could also buy an island from Tom Nook which you could access through Kapp'n. Once you got to this island you could name it, create a flag, and download it onto your Gameboy Advance to continue interacting with your islander or even trade islands with other players.
Animal Crossing Wild World released for the Nintendo DS in Japan on November 23, 2005, North America and Australia on December 5, 2005, and in Europe sometime in March of 2006.
On June 1, 2006 a Chinese version of Doubutsu no mori called 动物森林 (Dòngwù Sēnlín) was released for the iQue Player, a Chinese Nintendo console. Dòngwù Sēnlín is the original N64 version of the game despite featuring characters from Doubutsu no mori + on the cover.
Animal Crossing City Folk was releases in North America November 16, 2008 for the Wii followed by its release in Japan on November 20, 2008, Australia on December 4, 2008, and Europe on December 5, 2008. City Folk was compatible with the Wii Speak microphone, which allowed you to talk to other players who had it- essentially a form of voice chat. Fun fact: there's an add for the game where it is featured being used!!! One feature i absolutely love in this game is the fountain , where you can throw an axe into it and a special character named Serena will appear and she is how you obtain both the silver and golden axe.
Now onto Animal Crossing New Leaf was released for the Nintendo 3DS in Japan and South Korea on February 7, 2013. After that, it released internationally across June of 2003: June 9 in North America, June 14 in Europe, and June 15 in Australia.
Animal Crossing Happy Home designer was released for the 3DS in Japan on July 30, 2015, North America on September 25, Europe on October 2, and Australia on October 3. This game was very different from the others and the main goal was to design houses for villagers.
In November of 2015 we were cursed with Animal Crossing Amiibo Festival for the Wii U. The game only sold 490,000 copies and was considering a failure.
Animal Crossing Pocket Camp was released on Android and iOS mobile devices on October 25, 2017 and 40 other territories on November 22, 2017- but other sources say it was the 21. Sadly, in the last year we received news that it will be shutting down, but apparently from what i know they will be making another version of it or something of the sort.
Animal Crossing New Horizons was released on March 20, 2020 internationally for the Nintendo Switch. This game introduced DIY crafting and in later updates, cooking. Eventually they added the Happy Home Paradise DLC on November 5, 2021 which essentially functions like Happy Home Designer, but unlocks new skill you can use on your island.
I must say, we've come a longggggg way with this game. It helped a lot of people through 2020- including me. Can't wait to see what's in store for us next. Hope you enjoyed learning about the history of the games and if you would like to know more (like stuff about merch or even the movie) ask away! :D
#animal crossing history#animal crossing#doubutsu no mori#animal crossing population growing#animal crossing wild world#animal crossing city folk#animal crosing new leaf#animal crossing pocket camp#animal crosing new horizons#animal crossing happy home paradise#animal crossing happy home designer#doubutsu no mori +#doubutsu no mori e+#animal crossing community#nintendo#grrrr this took so longggggg#Porkbunsaysthings#Or#porkbunrambles#Because thats what im doing#can you tell im autistic#and that this is my special interest#One of them at least#anyways#enjoy
16 notes
·
View notes
Text
VPNs aren't just for pirates and company data anymore
A friend complained to me that they couldn't access pr0n anymore because the government is now requiring ID to verify age where they are, and due to data leaks and privacy issues, didn't want to share their ID even though they're of legal age.
Shit like this doesn't work on the intended target. It only frustrates people who are aren't tech savvy while a lot of kids have already found their way around it because that's what kids do ¯\_(ツ)_/¯
When I talk about VPNs (virtual private networks), non-tech savvy people's eyes glaze over 😂
It sounds like complicated, unknowable magic. It's not! And you don't even have to understand it to use it!
With the government and ISPs (internet service providers) invading privacy more and more and hackers breaking in and stealing user data from companies, VPNs are becoming necessary.
Some Things a VPN Does for You:
hides your data from others
can make your internet speeds faster if your ISP does speed throttling (purposely making your speed slower)
hides what you're doing from your ISP
keeps you safer from some malware, viruses, hackers, and trackers
allows you to access things that are either restricted in your area or not available in your area (such as content in other countries)
keeps you safer when you're out in public connected to wifi
Below is a basic infographic on how VPNs work. When you access the internet, a VPN encrypts your data - making it into a secret code that can't be read by anyone else including your ISP.
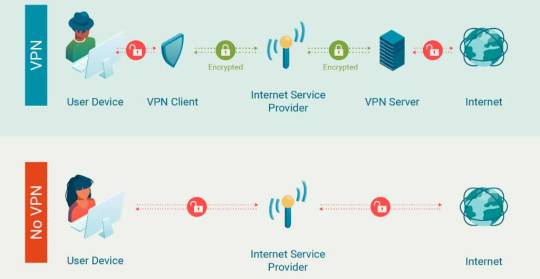
Tech companies, ISPs, etc. want you to think VPNs are complicated so that you won't use them.
When searching for a free VPN, please be aware that a lot of the free VPN services out there are malware or full of viruses and trackers.
Either do some research into which one to choose or use a paid VPN service. You can either pay monthly or yearly - the yearly is always cheaper in the long run.
Some of the Top Rated VPN Services:
ExpressVPN $7 - $13/month
NordVPN $3 - $13/month
Surfshark $2 - $14/month
PrivateInternetAccess $2 - $12/month
ProtonVPN (some sites block this one) $4 - $10/month
CyberGhost $2 - $13/month
I use ExpressVPN, so for the purposes of this post, I'm going to use screenshots from ExpressVPN.
Once you have an account, download the program from the website to your desktop/laptop or find the app on Android or iOS app stores.
Signing in requires a code that the VPN will email to you that unlocks all the features. Pay attention when the program installs because it'll ask you about preferences, and you can easily check yes on blocking pr0n when that's the reason you wanted a VPN in the first place 😂
When the program is open, you'll see this:

As you can see in the screenshot, not only do I have the program, but I have an ExpressVPN icon on my browser. The program installs this automatically, and when the program is running, the icon will have a green checkmark on it so you know it's working in your browser.
You'll notice I've recently connected using Japan. I did this so I could watch a series that isn't available outside of Japan.
The program automatically chooses a location near you, but if you want to access things that are restricted to you, make sure you click on the three dots to the right of the selected location (see screenshot below) and search for a state/country/place that your content will be available in.

Once your location is selected, click on the start/power button, and you'll get a popup notification from your computer that ExpressVPN is connected.
Go to the site you want to use and use it like you normally would.
Here's what it should look like when it's running correctly:

Keep in mind that if you leave a VPN running all the time (which is perfectly fine to do), search engines like Google will assume you live wherever ExpressVPN tells it you live, so searching for "stores near me" will give you results that aren't close to you.
When you're done using the VPN, just hit the power button again and it shuts off.
I use this on all my handheld devices, my desktop, and my laptop for business and personal reasons. I'm a pirate, and I've been using VPNs for a long time, yet none of the ISPs I've used have ever given me a warning about torrenting.
Good luck, and enjoy all the new things you can access!
BTW for anybody wondering, my desktop wallpaper is a map of the world's time zones. So pretty!! 😍
74 notes
·
View notes
Text
me: 1, apple: 0 (PSA to anyone else who hates the IOS 18 update/photos app update- there IS a way to revert it)
PSA to anyone else who fucking hates the AWFUL new ios 18 apple photos app UI: I managed to revert my phone back to EXACTLY how it was prior to the update WITHOUT losing any of my stuff (I had been running IOS 17.7.2 prior to the update). Here's what I did:
1.) I had an iCloud backup from BEFORE updating to 18.1.1. This backup was from when my phone was still on 17.7.2. You can still undo the update without a backup, but you'll lose all your stuff/your phone will be wiped. 2.) I went here and picked my phone type (iphone 13 pro in my case) and then downloaded the most recent ios BETA version (17.6 ver 3 beta)- it has to be one of those beta versions, because apple keeps their beta versions signed longer than other versions, and there are no longer any versions of IOS prior to IOS 18 that are still signed. You can't install unsigned versions via itunes, so they're useless. 3.) I downloaded the 17.6 ver 3 beta file to my computer 4.) I opened iTunes with my phone connected 5.) I right-clicked on "Restore iPhone..." button, and selected that 17.6 ver 3 beta file from my "downloads" folder 6.) I let it restore/factory reset my phone & it downloaded IOS 17.6 ver 3 beta to my phone because I selected that file in step 5.) 7.) It finished resetting it and then I SET IT UP AS A NEW IPHONE and i did NOT click the "partial setup," button because THAT button took me to a screen where they were going to force me to update to 18.1.1 AGAIN 8.) After setting it up as a new, blank phone, running on the IOS 17.6 ver 3 beta, I went into my iPhone settings, went to the software updates section, and updated to 17.7.2 (it gave me the option to update to 17.7.2 instead of 18.1.1- this is where the little loophole is, because the 17.7.2 file is no longer available for download online/is no longer signed, but you CAN still update from 17.6 to 17.7.2 from within your iphone settings) 9.) I updated it to 17.7.2. This would be your final step if you don't have an IOS 17.7.2 or earlier iTunes or iCloud backup to restore from. 10.) You can only restore from an iCloud backup during the setup process- so, I factory reset my phone AGAIN, but from within my phone settings this time (instead of using iTunes like I did when factory resetting & installing that IOS 17.6 version) 11.) During THIS setup process, I didn't click on the "partial setup," option, and then just clicked on the iCloud backup option after declining the "partial setup" option, and it restored from my 17.7.2 iCloud backup without forcing me to update to 18.1.1 12.) My phone was back to how it was right before the update! I then went and shut off all of apple's stupid "automatic update" features, made sure that it CANNOT update without me going out of my way to update it, because apple has LOST automatic update privileges with this vile, wretched IOS 18 photos app update. 13.) If you are going to do this, I recommend you do it as soon as possible, because even though the signed 17.6 beta was available, and even though I could update to 17.7.2 from within my phone's settings, there is NO guarantee how long this option will last, it could be gone tomorrow, it could be gone two days from now, it could be gone an hour from now.
14.) I suggest Apple stops letting their UI devs reach into my mind while I sleep & use my nightmares to design their UI, because I don't really think there's any other explanation for how that mess was perfectly catered to piss me off & make the photos app unusable for me.
7 notes
·
View notes
Text
MONPIC: The Hatchling Meets a Girl launches November 14 - Gematsu

Heartwarming monster adventure game MONPIC: The Hatchling Meets a Girl will launch for Switch, PC via Steam, iOS, and Android on November 14 for $8.99 / 1,280 yen, publisher Happy Elements and developer Cachalia Studio announced. It will feature English and Japanese language support.
Here is an overview of the game, via its Steam page:
About
MONPIC is a 2D adventure game that portrays the bond between a dragon hatchling named Pico and a girl transforming into a dragon named Yuzuki. Experience a charming story of monsters and humans while enjoying point-and-click exploration.
Story
Humans and monsters inhabit this world. These two groups live in tandem with one another. At times they quarrel, and at times they work together, long is their shared history. One day, a girl named Yuzuki gets lost in the forest and finds a delicious-looking apple. Thinking “Lucky!,” she eats it. Just then, a hatchling dragon named Pico appears and… Suddenly bursts into tears! It turns out that this was a special apple, a “Dragon Apple” essential for a dragon’s growth. After eating the Dragon Apple, Yuzuki starts to grow horns and begins to transform into a dragon. Can Yuzuki return to her original ‘Human’ form? And can Pico, who has lost his Dragon Apple, grow into a magnificent dragon? Guide them on their journey. “I hope we can meet again someday.”
Watch a new trailer below.
Release Date Trailer
English
youtube
Japanese
youtube
#MONPIC#MONPIC: The Hatchling Meets a Girl#Cachalia Studio#Happy Elements#adventure game#Gemastsu#Youtube
6 notes
·
View notes
Note
i'm kind of curious what you like about lostword. never really tried it myself n all.
— io
1. really easy to get your favorite characters
2. really easy to make your favorite characters viable no matter who they are
3. game isn’t very hard — no artificial difficulty spikes that force you to spend money to max out a unit or whatever. on that note, leveling up and upgrading units doesn’t take much time at all, allowing you to use lots of your favorite touhou characters if you’d like to.
4. the only characters that would probably require real money to aid in acquiring are the game’s made-up alternate universe versions of characters that i can’t imagine anyone giving a shit about. (sorry guys i’m never going to want to spend money so i can have.. sci fi space warrior sanae)
5. no temptation to buy anything in the store because the prices are all absurdly high. i will literally never be tempted to spend 80 dollars on a microtransaction. i consider this point to be a positive, because what is being sold is completely unnecessary.
6. game is written by perverts.
7. protagonist is a girl. this can’t be changed.
8. the main story is FANTASTIC. it’s really really really cool. finishing chapter 3 is what made me gush last night. the hifuu story is really cute too.
9. this might be something not everyone cares about, but the characters are very touchy-feely with each other, and with the protagonist. it’s very nice. i like when characters are handsy. skinship is compelling to me
10. writers aren’t pussies about yuri (important)
11. there is never not an event story going on (they rerun old events in between new ones), so if grinding event points is fun for you (it’s fun for me), that’s always an option no matter what.
12. great autobattle features. lots of customization for autobattles and auto-rematches for grinding materials.
13. despite what i just said, grinding is honestly optional. you don’t need to grind for levels, because levels come easily, and you don’t need to grind for materials after a while, because they give you so many.
14. story card (equippable items basically) art is cute. where would we be without modelo patchouli and her fat thighs?
15. despite having the usual scarlet devil mansion bias, a LOT of more obscure characters get a lot of spotlight, especially in event stories. one i remember enjoying a lot starred seija, sagume, and.. shizuha aki.. as the main characters (along with the protagonist of course). there are lots of cases like that.
16. characters all feel like they love you without it feeling at all like a harem game. sorry if this is cringe but don’t fucking lie and say you don’t want to be loved by the cast of touhou.
17. less of a point for me because i’ve been playing it since launch, but my girlfriend got into it recently and they have been ABSURDLY generous with her as a new player.
there are obviously criticisms to be had with the game (it’s a mobile game, it’s not perfect or anything by any stretch of the imagination), but you asked me what i liked about it. i’ve had a lot of fun with it in my time playing it, and my girlfriend is, like, obsessed with it, just getting into it.
9 notes
·
View notes
Text


iPhone 12 (256GB)
Price $399
*Display:*
- 6.1-inch Super Retina HD display
- 1080 x 2536 pixels resolution
- 460 pixels per inch (PPI)
- OLED technology
- HDR10 and Dolby Vision support
- True Tone display
- Wide color gamut (P3)
*Processors:*
- Apple A14 Bionic chip
- 64-bit, 6-core processor
- 4-core graphics processor
- Neural Engine for AI tasks
*Memory and Storage:*
- 6GB RAM
- 256GB internal storage
*Cameras:*
- Dual-camera setup:
- 12MP main camera (f/1.6 aperture)
- 12MP ultra-wide-angle camera (f/2.4 aperture)
- Features: Night mode, Portrait mode, 4K video recording at up to 60fps, slow-motion video, and more
*Battery:*
- Up to 10 hours internet use
- Up to 8 hours video playback (streamed)
- Fast charging (up to 18W)
- Wireless charging (Qi-compatible)
*Additional Features:*
- IP68 water and dust resistance (up to 4 meters for up to 30 minutes)
- Face ID facial recognition
- iOS 14 operating system
- Dual-SIM support (nano-SIM and eSIM)
- No headphone jack (Lightning EarPods included)
*Dimensions:*
- Height: 150.9 mm (5.94 in)
- Width: 75.7 mm (2.98 in)
- Depth: 8.3 mm (0.33 in)
- Weight: 182 grams (6.4 oz)
5 notes
·
View notes
Text
youtube
#apple#iphone#ios#appleiphone#apple ios#apple iphone#iphone se#iphone 14#iphones#iphone xr#iphone 8#iphone 8 plus#ios 17#ios 17 update#ios 17 features#Youtube
1 note
·
View note
Text
Smartphone Reviews: The Best Devices of 2024
As smartphones retain to adapt, producers are pushing the boundaries of layout, performance, and camera era. With such a lot of options available, selecting the best device can be overwhelming. In this evaluation, we can take an in-intensity take a look at a number of the top smartphones of 2024, covering their specs, capabilities, and overall performance to help you make an informed selection.

Affordable smartphones with best camera reviews
1. Apple iPhone 15 Pro Max
Apple has another time set a excessive bar with the iPhone 15 Pro Max. This device capabilities a titanium frame, making it lighter and extra durable than its predecessor. The A17 Bionic chip ensures pinnacle-tier overall performance, and with a 6.7-inch Super Retina XDR show, the visuals are beautiful.
Key Features:
Processor: A17 Bionic Chip
Display: 6.7-inch OLED (Super Retina XDR)
Camera: Triple-lens machine (48MP foremost, 12MP extremely-huge, 12MP telephoto)
Battery Life: Up to twenty-eight hours of video playback
Software: iOS 17
Pros:
Exceptional camera overall performance, particularly in low light
Impressive battery existence
Premium build exceptional with titanium body
iOS 17 optimizations beautify average usability
Cons:
Expensive
No major layout overhaul from preceding fashions
The iPhone 15 Pro Max is the satisfactory choice for Apple lovers who demand pinnacle overall performance and camera nice. However, its high rate tag may not be for all people.
2. Samsung Galaxy S24 Ultra
Samsung keeps to dominate the Android space with the Galaxy S24 Ultra, a powerhouse of innovation and overall performance. With its Snapdragon eight Gen three processor and an advanced S Pen, this device caters to each productiveness and enjoyment desires.
Key Features:
Processor: Snapdragon eight Gen three (or Exynos variant in pick markets)
Display: 6.Eight-inch Dynamic AMOLED 2X, 120Hz refresh rate
Camera: 200MP major, 12MP ultra-huge, 10MP periscope telephoto, 10MP telephoto
Battery Life: 5000mAh battery with 45W speedy charging
Software: One UI 6 (based on Android 14)
Pros:
Stunning 200MP foremost digital camera for tremendous detail
Bright and vibrant display with a high refresh rate
S Pen support complements productivity
Strong battery overall performance
Cons:
Expensive
Large length won't be cushty for all customers
The Galaxy S24 Ultra is the remaining Android flagship, providing an unheard of camera experience and pinnacle-notch overall performance. However, its high cost and huge shape issue may not match everybody.
3. Google Pixel eight Pro
Google’s Pixel 8 Pro keeps to impress with its AI-powered software program and digital camera skills. The Tensor G3 chip brings AI enhancements that improve pictures, battery control, and standard tool performance.
Key Features:
Processor: Google Tensor G3
Display: 6.7-inch LTPO OLED, 120Hz refresh price
Camera: 50MP major, 48MP ultra-huge, 48MP telephoto
Battery Life: 5050mAh battery with 30W speedy charging
Software: Android 14 (with distinct Pixel functions)
Pros:
Best-in-class computational images
Clean, bloat-loose Android revel in
AI-driven software optimizations
Seven years of software updates
Cons:
Tensor chip nonetheless lags in the back of Snapdragon in raw performance
Slower charging in comparison to competition
The Pixel 8 Pro is the satisfactory choice for folks who prioritize digital camera first-class and a smooth Android experience. While it could now not be the fastest device, its AI features make it a compelling option.
Four. OnePlus 12
OnePlus has been progressively improving its flagship gadgets, and the OnePlus 12 is not any exception. It promises excessive-give up overall performance at a surprisingly lower fee in comparison to different premium flagships.
Key Features:
Processor: Snapdragon eight Gen three
Display: 6.Eighty two-inch AMOLED, 120Hz refresh rate
Camera: 50MP fundamental, 48MP extremely-wide, 64MP periscope telephoto
Battery Life: 5400mAh with 100W speedy charging
Software: OxygenOS 14 (based totally on Android 14)
Pros:
Excellent battery life with excellent-fast charging
High refresh rate display for clean scrolling
Competitive pricing
Minimal software program bloat
Cons:
Camera performance is good however not the pleasant
OxygenOS is turning into greater just like ColorOS
For users who need flagship-level overall performance without spending over $1,000, the OnePlus 12 is a high-quality alternative. It gives fast charging, a brilliant display, and a smooth software program revel in.
Five. Xiaomi 14 Pro
Xiaomi has been making strides within the top class smartphone marketplace, and the Xiaomi 14 Pro is a sturdy competitor. With pinnacle-tier specs and an appealing charge point, it affords super price.
Key Features:
Processor: Snapdragon 8 Gen 3
Display: 6.Seventy three-inch LTPO AMOLED, 120Hz refresh rate
Camera: 50MP predominant, 50MP extremely-huge, 50MP telephoto
Battery Life: 4880mAh with 120W fast charging
Software: MIUI 15 (primarily based on Android 14)
Pros:
Fast charging generation is a few of the quality
Strong performance with Snapdragon 8 Gen 3
High-satisfactory show
Competitive pricing
Cons:
MIUI can sense clutteredreview
Limited availability in some regions
The Xiaomi 14 Pro is a incredible choice for users who need excessive-stop performance at a greater reasonable rate. However, software program enjoy and nearby availability may be factors to don't forget.
2 notes
·
View notes
Text
I should explain things. You know claire's history from corrupted timeline, but not how zoe lee and norma khan fit in yet. Don't worry, next month should clear things up. (Look for custom miraculous and custom dead end stuff next month).
Norma khan's here after bonking her head too hard and hallucinating seeing all this, but able to interact in the past. Zoe lee doesn't appear here, but she's aware of things.
One-shot 3/3
Whilst fighting in the elevator, they arrive in other realities such as an elevator in arcadia, dream brooklyn, phoenix parks, a paris one during a wasp armada, an IO lift, lots of things. Eventually, the headmaster pushes a button for his home, but it buzzes in error, allowing Lloyd to return them to the academy's basement. The headmaster lost but decides to accelerate the basement collapse to allow him to escape, and he does. Claire's got about everyone but a few others, so after helping her, Lloyd forces claire to shadow rift into her bed to save her, saying events are in motion she must move with and temporarily restricts her power until Rot arrives... Before she does, Claire's magic in proximity to norma forces a rift that brings norma, barney, pugsley, Courtney, gord, badyah, and logs over to present day at a hospital but norma's still there and pulls something through before waking in the hospital bed, which luckily nothings changed or norma would have a panic attack and a repeat of a parliament school trip with someone... (yeah, I'm certain norma wouldn't like being barefoot when unnecessary, like walking in parliament. Yes, a true thing I, too, fount out and freaked out over.) Lloyd and centi get caught up in the collapse, ending up in a subway tunnel station and surfacing in a hidden room which Lloyd leaves centi to flee from the cover up, saying the indigo ring should hide her and he'll see her again one day. Gord appears and speaks, with centi hearing noises whilst gorb says Lloyd's body was caught in fatal rubble and will need to repair itself. They part as Lloyd shifts form to a female temporarily and disappearing for a while before reappearing at his house on Christmas eve.
He hugs his mother before closing his eyes and opening them underwater. Claire's diving to rescue him and pull him up, and she does. He thanks her and says they were trying to close in on the rogue headmaster, unaware that the good one's at the hospital where the others are after the incident in ep7. Norma grabs a defensive weapon and begins panicking over his presence, saying to leave her alone and not to hypnotise her in which he shows that's not his intention. Dinah hunter who's upstairs comes down, seeing him and is having a hard time believing he's good until he asks norma to say what she saw, somehow aware she entered an unnatural state that brought her and her friends over. She explains the rogue headmaster and the events she's seen before revealing what she pulled out from 2016, to which the good headmaster says he knows where they need to go immediately. Barney asks if he caused norma to change turtlenecks after briefly entering episode 5 and getting Hunky parker gunge stains on it, leading to a panic and her wearing her dark blue one again. She stands fine and precedes to move normally but notes gord speaking to her whilst the others hear noises. Gord tells norma that it's best she doesn't say the events that happened in 2018 and that Lloyd's in very serious danger...
We end with eli in the forest near the rogue headmaster's camp and stumbling through the same portal as we learn that during her fight, and a secret as to how she escaped her nose bled and centi welcomes eli to a place her mother knows all too well.....
One-shot is accompanied by a soundtrack of 80s and 90s songs with popular 2016 songs to the tune of 14 tracks featured at some point including marketing.
The series and one shot here have ending credits like Marvel that show and hint upcoming things. Ep1-7 and festive special has the elevator closed but beep. Here for One-shot to episode 11, it's open with a haunting change after episode 11......
It seems the 2018 incident is well hidden for a reason.....
#trollhunters#miraculous ladybug#the demon headmaster#dead end paranormal park#norma khan#claire nunez#zoe lee#TDH ONESHOT
6 notes
·
View notes