#iapp;
Text

📘•°•📙 Treacherous Technology 📙•°•📘
📣👉Available On Amazon👈💥
🛒👉Here is the book link:- https://a.co/d/7DekmGX
Treacherous Technology: Generative AI and Quantum Computers - A Discussion of the risks posed by innovative technologies
Book purchase Link :-
📘✍Author by Joe Bartolo J.D. (Author)
✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️
📙🖋A Discission of risks posed by modern solutions:
💥 Generative AI: The power to create art, music, and human-like text, but also the capacity to produce deepfakes and misinformation at an alarming scale.
💥 Quantum Computing: The promise of solving complex problems in seconds, juxtaposed with the risk of breaking modern encryption and compromising global security.
💥 Ethical Implications: The moral questions surrounding the deployment of these technologies, including biases in AI algorithms and the environmental impact of quantum computing.
💥 Real-World Scenarios: Case studies and hypothetical situations that illustrate the potential hazards and benefits of our rapidly advancing technological landscape.
📘✍"Treacherous Technology" is an essential read for anyone eager to understand the balance between harnessing the power of new technologies and safeguarding our future. Whether you're a tech enthusiast, a professional in the field, or a concerned citizen, this book offers a comprehensive guide to the promises and perils that lie ahead.
Treacherous Technology
🛒👉Here is the book link:
📣📕📗
⭐️⭐️⭐️(Author) by Joe Bartolo, J.D.
💗💖"
🛒👉Available Instantly on Amazon –
Order Now:
Treacherous Technology: Generative AI and Quantum Computers - A Discussion of the risks posed by innovative technologies:- https://books2read.com/u/47BEVg
#AI;#Generative;#Artificial;#Intelligence;#GAI;#Quantum;#Singularity;#Supremacy;#Q-Day;#Innovation;#risk_management;#risk;#compliance;#legal;#privacy;#cybersecurity;#deepfake;#edrm;#aceds;#arma;#iapp;#sali#Law#Book#Books#Bookworm#BookLover#Bookish#BookAddict#BookLove
0 notes
Text
Achieving CIPM Certification: A Complete Guide to Elevate Your Professional Expertise
What is CIPM Certification?
The Certified Information Privacy Manager (CIPM) certification is a key credential for professionals looking to demonstrate their expertise in managing privacy programs. Offered by the International Association for Privacy Professionals (IAPP), CIPM is designed for individuals who oversee and manage privacy within organizations. This certification is crucial for those who wish to advance their careers in the field of privacy management and data protection.
Why Pursue CIPM Certification?
CIPM certification offers numerous advantages for privacy professionals, including:
Enhanced Career Opportunities
- Professional Growth: Earning the CIPM credential opens doors to advanced roles in privacy management, such as Privacy Manager, Data Protection Officer, or Privacy Consultant.
- Increased Earning Potential: Certified professionals often enjoy higher salaries and better job prospects compared to their non-certified peers.
Comprehensive Knowledge:
- Expertise in Privacy Management: The certification validates your ability to manage privacy programs, ensuring compliance with global privacy laws and regulations.
- Practical Skills: CIPM training provides hands-on experience in implementing privacy policies, conducting privacy assessments, and managing data protection strategies.
Global Recognition
Industry Standard: CIPM is widely recognized as a leading credential in privacy management, enhancing your professional credibility and reputation in the global job market.
CIPM Certification Requirements
To qualify for CIPM certification, candidates must meet specific criteria:
Experience and Knowledge
- Relevant Experience: While there are no strict experience requirements, having practical experience in privacy management is beneficial. This could include roles in data protection, compliance, or information security.
- Understanding of Privacy Practices: Familiarity with privacy laws, regulations, and management practices is essential for success in the certification exam.
Training and Preparation:
- CIPM Training Course: Enroll in a comprehensive CIPM training program to prepare for the certification exam. Zoctech offers a detailed course that covers all aspects of privacy management and compliance.
- Study Resources: Utilize study materials, practice exams, and other resources to ensure thorough preparation for the CIPM exam.
Pass the CIPM Exam:
- Exam Details: The CIPM exam assesses your knowledge of privacy management practices, including privacy program governance, data protection, and privacy compliance.
- Exam Format: The test consists of multiple-choice questions designed to evaluate your understanding of privacy principles and management practices.
How to Get CIPM Certified with Zoctech
Explore Our Training Options:
Visit Zoctech’s CIPM Training and Certification Course to learn more about our comprehensive training programs and resources.
Prepare for the Exam:
Enroll in our expert-led CIPM training course to gain in-depth knowledge and practical skills in privacy management. Benefit from detailed study guides, practice exams, and interactive sessions.
Register and Achieve Certification:
Complete the registration process for our training program, study diligently, and take the CIPM exam to earn your certification and advance your career in privacy management.
Conclusion:
CIPM Certification is a valuable credential for professionals aiming to excel in privacy management. By meeting the certification requirements and enrolling in Zoctech’s comprehensive training program, you can enhance your expertise, open new career opportunities, and gain global recognition in the field of privacy.
#cipm certification#cipm courses#certified information privacy manager#cipm#iapp certification#certification#privacy certification#cipm exam#cipp certification#pdpa certification#iapp cipm certification#cipm certification mock test#cpp certification iipmr#it certifications#data privacy certification#procurement certifications#cipt certification#cipm certificate#cipp/e certification#it certification#cipm practice exam#certification journey#iapp certifications#tech certifications
0 notes
Text
Weekly output: online advertising and privacy, net neutrality vote, vineyard robotics, Meta content moderation run amok, manufacturing gone green
I’m heading to Dulles before dawn tomorrow, but not for work: I’m flying to Dallas to try to see the solar eclipse, a friend having invited people to visit for the occasion. Please wish us luck with the weather!
4/3/2024: Ad Industry Unbothered by Federal Privacy Law (Because It’ll Probably Never Happen), PCMag
I wrote this from the Interactive Advertising Bureau’s Public Policy and Legal Summit…

View On WordPress
#circular economy#cleantech#Facebook blocking links#Facebook content moderation#FCC#greentech#IAB#IAPP#Kansas Reflector#net neutrality#online privacy#privacy law#sustainability
1 note
·
View note
Text
CIPM IAPP qatar | Menaexecutivetraining.com
Get CIPM, CIPPE, and Online IAPP certification opportunities in Qatar through MENA Executive Training. Explore our comprehensive certification programs at MENA Executive
0 notes
Text
IAPP 2023 | Dataprivacy.academy
Explore the latest in data privacy and AI governance with IAPP in Singapore, Ireland, Canada, Hong Kong, Israel, and the year 2023. Join Data Privacy Academy for comprehensive insights.
0 notes
Text
AI governance IAPP | Menaexecutivetraining.com
Explore our Data Privacy and AI Governance training programs in Qatar, including IAPP certification, at MENA Executive Training
0 notes
Text
Preços dos ovos seguem estáveis em 2023
No mercado dos ovos, negócios estão estáveis apesar do Brasil registrar casos de IAPP em aves
A confirmação pelo Ministério da Agricultura e Pecuária (Mapa) na segunda-feira, 15, de três casos de H5N1 (Influenza Aviária de Alta Patogenicidade, IAAP) em aves silvestres no litoral do Espírito Santo preocupa agentes do setor, uma vez que um dos casos foi registrado a menos de 100 km do município de…

View On WordPress
0 notes
Text
#quantum mechanics#quantum computer#quantum computing#quantumtechnology#quantum threat#privacy#security#EDRM#aceds#iapp#ARMA
0 notes
Text

📘•°•📙 Treacherous Technology 📙•°•📘
📣👉Available On Amazon👈💥
🛒👉Here is the book link:- https://a.co/d/7DekmGX
Treacherous Technology: Generative AI and Quantum Computers - A Discussion of the risks posed by innovative technologies
Book purchase Link :-
📘✍Author by Joe Bartolo J.D. (Author)
✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️✨️
📙🖋A Discission of risks posed by modern solutions:
💥 Generative AI: The power to create art, music, and human-like text, but also the capacity to produce deepfakes and misinformation at an alarming scale.
💥 Quantum Computing: The promise of solving complex problems in seconds, juxtaposed with the risk of breaking modern encryption and compromising global security.
💥 Ethical Implications: The moral questions surrounding the deployment of these technologies, including biases in AI algorithms and the environmental impact of quantum computing.
💥 Real-World Scenarios: Case studies and hypothetical situations that illustrate the potential hazards and benefits of our rapidly advancing technological landscape.
📘✍"Treacherous Technology" is an essential read for anyone eager to understand the balance between harnessing the power of new technologies and safeguarding our future. Whether you're a tech enthusiast, a professional in the field, or a concerned citizen, this book offers a comprehensive guide to the promises and perils that lie ahead.
Treacherous Technology
🛒👉Here is the book link:
📣📕📗
⭐️⭐️⭐️(Author) by Joe Bartolo, J.D.
💗💖"
🛒👉Available Instantly on Amazon –
Order Now:
Treacherous Technology: Generative AI and Quantum Computers - A Discussion of the risks posed by innovative technologies:- https://books2read.com/u/47BEVg
📣📕📗
#AI;#Generative;#Artificial;#Intelligence;#GAI;#Quantum;#Singularity;#Supremacy;#Q-Day;#Innovation;#risk_management;#risk;#compliance;#legal;#privacy;#cybersecurity;#deepfake;#edrm;#aceds;#arma;#iapp;#sali#Law#Book#Books#Bookworm#BookLover#Bookish#BookAddict#BookLove
0 notes
Text
0 notes
Text
people hating on the new FOP reboot are cowards!!!!!!!!!!!
- Cosmo and Wanda were always going to have another godkid after Timmy. This is their JOB and has been for thousands of years
- "What about Poof?!?! Where is Poof???" Where was Poof in the late seasons of the original run of FOP lmao
- The art direction is freaking amazing! And the new kiddo seems like a super fun character to spend an episode's worth of time with :)
- I for one am glad to have a modern version of FOP that actually takes place in current time from the start, unlike how the original started somewhere in the late 90s and then in the blink of an eye went to Crocker having an iPhone with iApps....
we literally only have a trailer and some leaked footage to go off of ,and people have already made up 15 years worth of reasons to hate this show because it's a total reboot with a new kid
I'm glad it's a reboot with a new kid! FOP was set up with a great concept where you could totally swap most of the characters and it would still work just fine in the same continuity!
lets all just wait for the show to come out and then we can make judgements
personally I am very optimistic about it :) it seems like a fun and fresh take made with a lot of love and appreciation for the original (seriously, making Cosmo look this good in 3D is impossible unless you give a shit)
56 notes
·
View notes
Text
Weekly output: AI executive order, Apple's leftover Lightning peripherals, Digital Platform Commission, Intuit to scrap Mint, AI policy
My upcoming work week only has about three and a half days’ worth of time available for my usual work. The entirety of Tuesday, meaning from 5 a.m. to about 9 p.m., has me serving as a poll worker, the seventh time I will have worked as an Arlington election officer. And then I’ll have to set business aside by mid-afternoon Friday to start my journey to Lisbon for Web Summit.
10/30/2023:…
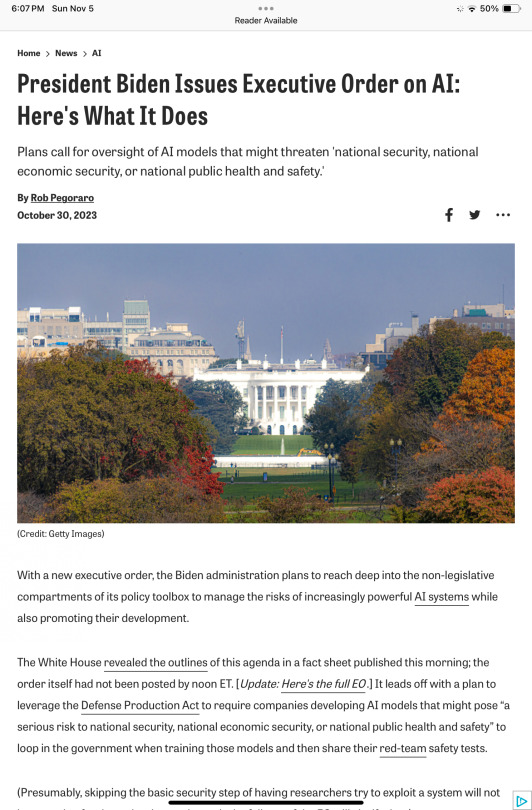
View On WordPress
#AI policy#Apple Magic Mouse#Apple USB-C mouse#Biden executive order#Boston#Brooklyn 6G Summit#Credit Karma#Digital Platform Commission#IAPP#IAPP AI Governance#Intuit Mint#Lightning cable#Mint#NYC
0 notes
Text
CIPM IAPP doha | Menaexecutivetraining.com
Discover comprehensive Data Privacy and Data Protection training courses in Qatar, UAE & Saudi Arabia & online. Enhance your knowledge with AI and Law workshops. Explore our offerings today.
0 notes
Text
In 2016, Facebook launched a secret project designed to intercept and decrypt the network traffic between people using Snapchat’s app and its servers. The goal was to understand users’ behavior and help Facebook compete with Snapchat, according to newly unsealed court documents. Facebook called this “Project Ghostbusters,” in a clear reference to Snapchat’s ghost-like logo.
On Tuesday, a federal court in California released new documents discovered as part of the class action lawsuit between consumers and Meta, Facebook’s parent company.
The newly released documents reveal how Meta tried to gain a competitive advantage over its competitors, including Snapchat and later Amazon and YouTube, by analyzing the network traffic of how its users were interacting with Meta’s competitors. Given these apps’ use of encryption, Facebook needed to develop special technology to get around it.
One of the documents details Facebook’s Project Ghostbusters. The project was part of the company’s In-App Action Panel (IAPP) program, which used a technique for “intercepting and decrypting” encrypted app traffic from users of Snapchat, and later from users of YouTube and Amazon, the consumers’ lawyers wrote in the document.
49 notes
·
View notes
Text
IAPP AI governance | Dataprivacy.academy
Explore the latest in data privacy and AI governance with IAPP in Singapore, Ireland, Canada, Hong Kong, Israel, and the year 2023. Join Data Privacy Academy for comprehensive insights.
0 notes