#hire hacking services
Explore tagged Tumblr posts
Text
Hire a Social Media Hacker: Unlocking the Secrets of Professional Hackers
In today's world, social media is the battlefield. Whether you're looking to protect your account or access information that seems out of reach, hiring a social media hacker can be the game-changer. This guide will walk you through everything you need to know to hire a social media hacker, including how to find a professional social media hacker, what to expect, and why it's important to choose wisely. Buckle up and get ready to dive deep into the underground world of hacking
1. What is a Social Media Hacker?
Your Guide to Understanding the Basics
A social media hacker isn't just a random individual breaking into accounts for fun. These are skilled professionals who have mastered the art of exploiting vulnerabilities in social media platforms. A professional social media hacker can help recover a hacked account, retrieve lost passwords, or even gain access to a target account (ethically or otherwise, depending on your needs).
Most hackers work with both black-hat and white-hat intentions. While some use their skills for nefarious purposes, others are hired for legitimate reasons like security audits. So, before you dive in and hire a hacker, know what kind of expertise you’re looking for.

2. Why You Might Want to Hire a Social Media Hacker
The Benefits of Going Pro
Hiring a social media hacker can offer several advantages. For businesses and individuals alike, there are moments where standard customer service just doesn’t cut it. Maybe you've forgotten a password, or maybe you've been locked out due to hacking attempts. In these cases, a professional social media hacker can come to your rescue.
Moreover, these hackers can help you gain insights into your competition by unlocking hidden information. But be warned: while hiring a hacker to recover an account or for security testing is legal, some other actions might not be. Always know the risks involved.
3. How to Find and Hire a Hacker for Social Media
Navigating the Dark Web and Other Channels
Finding a hacker isn't as simple as opening up your web browser and typing in “hire a hacker.” No, you're going to have to dig deeper. Start by exploring hacker forums and communities that specialize in social media exploits. Websites that cater to penetration testing or ethical hacking often have forums where you can engage with hackers.
Additionally, you might consider looking at freelance websites that offer hacker services. Here, you’ll find professional hackers offering various services—some legit, others more covert. Make sure to vet anyone before hiring. Check reviews, feedback, and always request examples of their previous work to ensure you’re getting the real deal.

4. What to Look For in a Professional Social Media Hacker
Tips for Finding the Best Hacker for the Job
When hiring a hacker, experience is everything. You need someone who understands the ins and outs of various social media platforms—whether it’s Facebook, Instagram, Twitter, or even lesser-known platforms. Make sure the hacker has experience with the specific platform you need.
Furthermore, communication is key. If the hacker can’t explain what they’re doing in a way you understand, they may not be the best fit. Look for someone who is professional, responsive, and transparent about their process.
It’s also essential to discuss pricing upfront. Professional social media hackers often charge based on the complexity of the task. Ask for a quote and see if it aligns with your budget. Remember, you get what you pay for, so be wary of hackers offering services at unusually low rates.
5. The Risks Involved in Hiring a Social Media Hacker
What You Need to Know Before Jumping In
While hiring a hacker can seem like the fast track to getting what you need, it's crucial to understand the risks. First and foremost, many hacking activities are illegal. Hiring someone to hack into a social media account without authorization can land you in hot water.
Additionally, you run the risk of hiring a scammer. The hacking world is full of people looking to exploit vulnerable individuals, so be cautious when sharing personal information. Always verify the hacker’s credentials and check their reputation within the community before proceeding.
Moreover, always consider the ethical side. If you’re looking to recover a lost account, that's one thing. But hacking into someone else's private information? That's crossing a line you should think long and hard about.

6. How to Ensure a Safe and Legal Hack
Stay on the Right Side of the Law
While some types of hacking are illegal, ethical hackers—often referred to as “white-hat” hackers—work within legal boundaries. These hackers specialize in securing systems and finding vulnerabilities before someone with malicious intent can exploit them. If your goal is to hire a hacker to perform security checks or recover a compromised account, make sure you’re working with someone who stays within the limits of the law.
Ask your hacker about their process. Ensure they’re only using approved methods, especially if you're hiring them for business purposes. Protect yourself legally by making sure you have a clear, written agreement in place before any work begins.
Conclusion: The Path to Hiring a Social Media Hacker
Hiring a social media hacker can open doors you never thought possible—whether for recovering lost accounts or gaining strategic insights. The key is to understand the nuances between different types of hackers, knowing where to find them, and being fully aware of the risks involved. Hiring a professional social media hacker is not a decision to take lightly, but when done right, it can be an incredibly valuable tool.
Slug: hire-social-media-hacker-guide
For ore info :-
hire a hacker
hire a social media hacker
professional social media hacker
#hire a hacker#professional social media hacker#hire a social media hacker#hire whatsapp hacker#hire a facebook hacker#insta hacker hire#reliable instagram hacking services#whatsapp hack services#hire a snapchat hacker
0 notes
Text

Have you heard about the Polish Train company, Newag, and the bullshit it turns out they got up to?
So, the regional rail operator Koleje Dolnośląskie bought some Newag Impuls back in 2016 . In late 2021, some of them need to have major maintenance done, as they've been in service a while. So the company SPS (Serwis Pojazdów Szynowych) gets the contract to fix them. They basically take the train apart, replace a bunch of it, following all the rules in the documentation Newag gave them, and... it won't move. The train says everything is fine, the brakes are off, there's plenty of power, but you push the throttle up and it won't move.
SPS spends a while trying to figure out what the fuck is wrong, with no luck. So they hire some hackers from the Polish security group Dragon Sector. Dragon Sector figures out how to get into the code of the computer system that runs the train, and OH MY GOD.
So it turns out there's a secret train-lock system. If it's on, the train won't move. This will be triggered in some situations you might think are normal: the clocks are wrong, the serial numbers of the various parts have changed, and a firmware mismatch between the main computer and the power system. Now, the fact that it makes sense to not run the train in these situations until someone can check it? that doesn't extend to the fact the train uses a SECRET lock system, rather than just popping up an error message telling you what's wrong. There's also the problem that while these are all potential error problems, they can't be cleared by anyone with the technical manuals, which are supposed to cover everything about how to run these trains. Only Newag themselves can reset this system.
Which, you know, keeps SPS from properly fixing them. Only Newag can fix them now, but not because SPS lacks any technical ability, but because Newag sabotaged their own trains. But don't worry: it gets worse.
So now that Dragon Sector knows what's happening, they get to look at other trains. It turns out the trains aren't all running the same software, and there are other tricks in there.
One of them is a "how long has the train been stopped?" check. If the train hasn't hit 60 km/h in 10 days, the train locks itself and won't move until Newag can clear it. So, like, if a train is ever out of service, like it's going to a repair place... it'll break itself. Unless the repair place is owned by Newag.
But two of the trains go further: See, these trains have GPS built in, right? You may be able to guess where this is going...
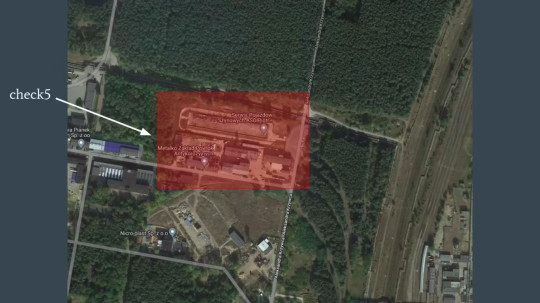
THEY JUST MAKE THE TRAIN CHECK IF IT IS PARKED AT THEIR COMPETITORS' REPAIR YARD AND BREAK ITSELF IF IT WAS.
The sheer audacity of this move. This is frighteningly bullshit anti-competition self-sabotage.
This has, obviously, made some parts of the Polish government to start investigating this. Newag may be (and hopefully will be) in a lot of trouble.
For more info, there's a great video of a presentation by the three people from Dragon Sector who did the hacking, which was presented at the 37th Chaos Communication Congress in Germany.
Ars Technica also has an article on it, but it predates the presentation so it doesn't have some of the later details.
Anyway, the good news is that in the end the hackers at Dragon Sector were able to unlock most of the trains: A few had additional trickery that they didn't want to hack around, because it might break the train's certification. For the others, they discovered undocumented "cheat codes" in the software that they could use to bypass the secret lockouts... presumably the same ones that Newag would have used when they "repaired" trains.
5K notes
·
View notes
Text
Part 2 of my MC's file from the yandere!batfam au

HER ARSENAL:
-Lucia's skills as a hacker are inspired by the Watch Dogs universe.
-She can remotely hack phones to access data, disable alarms, or track locations. Tamper with security cameras for intel or to map out routes. Overloard junction boxes to create distractions or disable power.
-Even manipulate traffic lights to cause accidents or create a escape route.
-She can also override vehicle systems, remotely controlling cars or locking people inside.
-She's also an inventor. Her fascination with tech doesn't end only in programming. She loves creating and developing tech stuff. Robots and drones are her favourites, designed for surveillance, as weapons, or other related tasks, such as planting bugs and retreiving items.
-With time, she learns to build specialized tools like signal jammers, EMPs, or hacking tools disguised as everyday items. Nothing escapes her.
-She has many hiding spots in Gotham, after years of finding routes by jumping through rooftops and sneaking around, but she mostly frecuents her main safehouse, that's located within an abandoned warehouse in The Narrows, and extends below utilizing portions of the closed underground station.
-She knows no one would think of looking down there, unless they know what they're looking for.
-It serves her as a workshop, but also as an operations center and her own personal heaven, where she can rest and enjoy herself in peace. She feels more at home there than in the Wayne manor.
-She puts her gymnastic skills to good use, sneaking through rooftops, alleyways, and urban infrastructure to her advantage. Sometimes she'll rely on drones for mobility instead, controlling them to scale virtually any wall and obstacle that she can't by bypass with parkour.
-She's not a fighter, but years of judo classes have allowed to defend herself when the situation calls for it. She's usually armed with compact, high-voltage stun weapons that incapacitate people without killing them. All of which designed and developed by her.
-She operates with an alter ego, Ghost, and later Zero, with which she manages her "errands" and communicates with people who hire her services. At first, the alter ego only exists online, but with time, she begins to intervene more in her missions, and it's not unusual for her to sneak into places to do her work, so she uses a disguise.
-When she's acting as her alter ego, she wears form-fitting athletic wear for unrestricted movement, with a jacket over it with deep pockets and hidden compartments, that helps conceal her shape. A sleek, high-design mask that covers from her nose to her forehead, equipped with augmented reality features for hacking on the go and a voice modifier, which creates a robotic tone that makes impossible to discern her age or gender. She also uses gloves, to keep her fingerprints away from any surface.
-She started doing some hacking here and there for hiring, but eventually, she associates with villains and works with them. She does some morally and legally questionable stuff (downright crimes) for money and also for the thrill of power, for the self-validation.
-Regardless, she doesn't really follow anyone. She works on her own terms and mostly does her own things. She's friends with some other hackers too and they work together from time to time, but otherwise, she acts alone.
-The classes and extracurricular activities she took in an effort to impress her family (judo, gimnastics, programming, drawing) have proven to be very useful with her new job, giving her a set of skills that she's honed for her not-so-legal endevours.
-She has her own motorbike, her favourite gift from Alfred that she treasures. She calls it "my baby", and has given it a few not very legal modifications to improve the design to her taste.
Personal info:
-She doesn't call Bruce "dad" or "father". It's always Bruce, or Mr Wayne if she feels particulally petty.
-She was banned from judo competitions after accidentally breaking her oponent's leg. In her defense, she had an awful day and the poor bastard decided it was a good idea to taunt her into hitting him. She claims she's gotten over it already (lies, she still gets pissy over it).
-She's been practically raised by Alfred, and they have the sweetest bond. He's the only person in the manor she respects, and wants to make him proud. That's why she does her best to hide her double life from him, knowing he would dissaprove.
-Funny enough, because Alfred is the same one who taught her how to shoot a gun and where to stab someone to render them helpless. The man is no fool, he knows he can't stop a teenager from doing dumb shit, but he can at least make sure she's prepared for the worst outcomes.
-She has the habit of moving around the manor like a monkey, climbing and jumping around like the proud gymnast she is. The manor is like a obstacle park for her. Why take the stairs when she can just jump off the rail and land gracefully on the ground? It's much faster.
-Alfred had to patch her up more than once from stunts gone wrong, but always encouraged her that "there's no victory without failure".
-She's grown up helping Alfred around the manor, slowly but surely taking his tasks from him and doing them herself so he can rest. She's worried about his high activity at his old age, fearing he might drop dead one day out of exhaustion.
-They share the house chores, and he calls her "his little helper", even though she's taller than him now. Lucia's heart melts when he calls her that, but pretends to complain with "she's not a kid anymore"
-She's fixated with the color red ever since her mom's death, specially with the kind of red that resembles blood stains. At the same time, she has severe claustrophobia.
-She hates the color green ever since Damian tried to kill her. It reminds her of his eyes.
-Speaking of it, she's either indifferent or polite with the others, but she hates Damian with passion. He gave her trauma, nightmares and a permanent scar on her neck that would never dissapear, among being an absolute bully whenever their paths cross. She avoids him entirely.
-Even thought she's stranged, she's still known as Bruce Wayne's daughter. She got kidnapped not much later after moving in to Wayne Manor by Penguin, whom she won over by being overly nice and polite with despite her circumnstances. Her mother taught her that bowing her head and be pleasant could save her life in the worst situations (pity it didn't save her)
-She was rescued quickly enough by Bruce, but he handled the ordeal as if it was an inconvenience rather than his daughter having been in a life-threatening situation.
-She's been kidnapped and attempted to more times over the years, each one cementing her belief that she had to save herself because no one else would.
-Her little brother, Marco, is a year younger than Damian, and has dyslexia, which is one of the reasons Lucia works so hard to provide him the best from a distance. She knows the educational system doesn't fit kids with special needs like him, specially if they're orphans.
-She's taken upon herself to be a mother for Marco, unconsciously seeking to cope with their mom's death by taking her place in his life. She visits him frecuently at the orphanage and pulls strings so he doesn't get adopted. It's selfish, she knows, but she can't stand the idea of another family getting him and losing contact with him.
-Being possessive with family runs in her blood.
-She adores him, but her relationship with the boy is also built on her feelings of neglect and the trauma of losing their mother. She holds unto him not only out of love, but because she feels he's the only true family she has. The only brother who loves her unconditionally and doesn't make her feel like shit.
-She's a parentified oldest daughter at its finest, used to act like an adult even at a young age. The only times she allows herself to be a girl her age is when she's alone with Alfred or with her best friends.
-She smokes and has some self-destructive tendencies, but crosses the line at getting drunk.
-She has discounts at the Iceberg Lounge whenever she goes. Gets along surprisingly well with Oswald Cobblepot, with him being somewhat fond of her since the kidnapping.
-Because of this, she has met a couple of villains already and even talked to them. Ivy and Harley are secretly scouting her for Siren potential, trying to see if she's worth it.
-All of them at some point have met her alter ego online. She has contacts everywhere.
-Marco's biological father is a pillar in both their lives since they were kids, and Lucia has a complex dynamic with the man. His identity is relevant to the plot.
-Out of all her "siblings", she likes Duke the most. He's the only one who's been friendly with her since the beginning and hasn't gotten bored of her, unlike Stephanie. They were close before, but after Lucia found out their secret identities, she kept her distance from him, much to his sadness.
-She doesn't mind Barbara and Cassandra. She's polite when she sees them and has no particular problem with their presence.
-She strongly dislikes Dick, Jason and Stephanie, and she doesn't have an opinion on Tim, beyond that he has assholes vibes.
-My Dick Grayson, Jason Todd and Damian Wayne from this au are inspired by the ones from @solelifauna. If you want to get an idea, go check her works and you'll understand.
-Lucia knows all of their vigilante lives, but pretends she doesn't so to not give them a reason to bother her. Alfred is aware that she knows, since he was there when she found out, in an accidental way.
-Long story short, she snuck in the Batcave and saw all the stuff, including the uniforms. She had a mental breakdown right there and rushed to pack her stuff, determined to run away. She's a criminal, she doesn't want to share space with the people who hunt down those who break the law. Alfred caught her and managed to convince her to stay, agreeing that she would keep the secret and the family wouldn't have to know about this incident.
-Alfred thinks he reacted like that because she's afraid of being targeted by the Batfamily's enemies.
-In reality, she's afraid of being targeted by the Batfamily themselves.
@bunbunboysworld
#i have so many ideas for my girl#so much more#my head is filling up with scenarios#i love watch dogs#and i love the batfamily#specially with a neglected reader#sorry this was short compared to the previous one#i'm planning on posting headcanons in individual posts#lucia wayne-perez#she's half hispanic yes#on her mother's side#she rarely uses the wayne name#more to come#feel free to send me asks i'd love to hear opinions#batfamily#yandere batfam#dc x reader#batfamily x reader#neglected reader#batfam x neglected reader#yandere batfam x reader#not really a reader but you're free to self-insert in lucia if you want#i usually self-insert in ocs rather than y/ns#yandere batfamily
171 notes
·
View notes
Text
Top Tips to Safely Hire a Hacker Near Me for Enhanced Security
Hiring a hacker near me for security isn't about taking risks; it's about managing them. A skilled ethical hacker can identify vulnerabilities before others do, helping you stay one step ahead of cyber threats.

Introduction:
Understanding the Need to Hire a Hacker Near Me
In today's increasingly digital world, many individuals and businesses are searching for “hire a hacker near me” to protect sensitive information, recover lost accounts, or secure systems. But why is hiring a hacker so popular now? And what exactly should you look for to ensure a safe, legal, and effective engagement? This article explores the basics of ethical hacking services, how to find a hacker near you for secure work, and the critical questions you need to ask before hiring one.
1. What is Ethical Hacking?
Ethical hacking, often referred to as "white-hat hacking," involves using hacking techniques legally and for constructive purposes. Unlike malicious hackers who exploit system vulnerabilities, ethical hackers help identify and fix security gaps in systems. Hiring a hacker near you for ethical purposes can enhance your security and provide peace of mind.
1.1 Benefits of Ethical Hacking Services
Enhanced Security: Ethical hackers expose and address system vulnerabilities.
Data Recovery: If you’ve lost data, an ethical hacker can often help retrieve it.
Reassurance: Knowing your systems have been tested can build trust among customers and stakeholders.
2. Why People Search “Hire a Hacker Near Me”
The primary reason people search for local hackers is accessibility and trust. Whether it’s recovering a social media account, assessing business security, or personal privacy concerns, hiring someone nearby often makes people feel more secure.
2.1 When to Consider Hiring a Hacker
Account Recovery: Lost access to email, social media, or other critical accounts.
Cybersecurity Testing: Evaluate a system for potential vulnerabilities.
Data Security Compliance: Ensure compliance with regulations by securing personal data.
3. Legal vs. Illegal Hacking: Know the Difference
Not all hacking activities are legal. Before you hire a hacker near you, understand the legal implications. Ethical hackers work with consent and within the legal boundaries, while black-hat hackers exploit data illegally.
3.1 Legal Hacking Services
Penetration Testing: Simulating cyber-attacks to evaluate system security.
Vulnerability Assessments: Identifying weak points in a network.
Data Recovery Assistance: Retrieving lost data without unauthorized access.
3.2 Illegal Hacking Practices to Avoid
Hiring someone for activities like unauthorized account access or data theft is illegal and can result in serious consequences. Avoid hackers offering these services.
4. Qualities to Look for When You “Hire a Hacker Near Me”
When looking for a local hacker, ensure they have the right skills, credentials, and ethical guidelines. Here’s what to keep in mind:
4.1 Essential Skills and Qualifications
Technical Expertise: Look for experience in system penetration, data encryption, and cybersecurity protocols.
Certifications: Ethical hackers should have certifications like CEH (Certified Ethical Hacker) or CISSP (Certified Information Systems Security Professional).
Track Record: Seek a history of legitimate projects and satisfied clients.
4.2 Personal Attributes
Transparency: Ethical hackers should communicate openly and explain their methods.
Confidentiality: Ensure they will protect your privacy and the confidentiality of your data.
Problem-Solving Skills: The best hackers are creative problem solvers, able to adapt to complex issues quickly.
5. How to Find a Reliable Hacker Near You
Finding a legitimate hacker nearby involves more than a quick online search. Research, referrals, and reputation are key to finding the right fit.
5.1 Trusted Platforms and Sources
Professional Websites: Look for hackers on professional platforms like LinkedIn or Upwork.
Certifications and Professional Networks: Many certified ethical hackers are members of organizations like EC-Council.
Tech Community Referrals: Often, local tech communities can recommend trusted hackers.
5.2 Evaluating Reviews and Portfolios
Check online reviews and case studies to gauge a hacker's effectiveness. Look for client feedback, specifically on projects similar to your needs.
6. Services Offered by Ethical Hackers
Ethical hackers provide various services, depending on your specific needs.
6.1 Common Services for Businesses
Network Security Audits: Assess the safety of your company’s network.
Application Testing: Ensure that your software is secure from external attacks.
Employee Training: Educate staff on cybersecurity best practices.
6.2 Personal Security Services
Account Recovery: Assistance in recovering locked or hacked personal accounts.
Device Security Checks: Ensures your personal devices are secure from spying or malware.
Privacy Assessments: Identify any weaknesses in personal privacy, especially on social media.
7. Costs of Hiring a Hacker Near Me
The cost of hiring a hacker can vary based on expertise, location, and project complexity. Here’s a rough breakdown to give you an idea.
7.1 Factors Influencing Costs
Service Type: Penetration testing or account recovery services will vary in price.
Experience Level: More experienced hackers may charge premium rates.
Scope of Work: The larger and more complex the project, the higher the costs.
8. Red Flags to Watch for When Hiring a Hacker
Hiring a hacker, especially locally, can present risks if you’re not careful. Avoid potential pitfalls by watching for these warning signs.
8.1 Lack of Transparency or Communication
Unwillingness to discuss techniques or provide a clear plan of action is a red flag.
8.2 No Clear Contract or Agreement
A professional ethical hacker will offer a contract detailing the scope of work and legal limitations.
8.3 Asking for Personal Information Upfront
Ethical hackers won’t request sensitive information beyond what’s needed for their work.
9. Security and Privacy Considerations When Hiring a Hacker
Working with a hacker means dealing with sensitive data, so it’s essential to take precautions.
9.1 Confidentiality Agreements
Ensure you sign an NDA (Non-Disclosure Agreement) to protect your data.
9.2 Secure Payment Options
Use secure, trackable payment methods for peace of mind and accountability.
10. Steps to Take Before Hiring a Hacker Near You
To get the most out of your engagement, it’s important to prepare thoroughly. Here’s a checklist:
Identify Your Needs: Be specific about what you need from the hacker.
Vet Candidates Thoroughly: Research experience and client feedback.
Clarify Legalities: Be sure your request is entirely within legal boundaries.
11. Case Studies: Successful Ethical Hacking Projects
To understand what’s possible, here are examples of successful ethical hacking applications:
Banking Sector: A bank hired an ethical hacker to stress-test its mobile banking application, identifying vulnerabilities that saved millions in potential breaches.
Small Business Security: A local business hired a hacker to improve its Wi-Fi network security, significantly reducing the risk of data theft.
Also Read:
Should You Find a Cell Phone Hacker for Hire to Spy on Phone? Top 10 Best iPhone Hacking Apps Why do you need phone hacker? Best 8 Features of Phone Hack Why It Is Important to Hire a Professional USA Hackers?
Conclusion: Making a Smart Decision to Hire a Hacker Near Me
Hiring a hacker near you can be a wise move for individuals and businesses alike, provided you ensure they are ethical and qualified. From safeguarding data to recovering accounts, ethical hackers bring essential skills to the table. However, it’s crucial to vet professionals carefully, ask the right questions, and prioritize security and legal compliance. By doing so, you can gain invaluable insights into your digital security without compromising your data integrity.
In summary, when you decide to “hire a hacker near me,” consider the value of expertise, a clean reputation, and ethical compliance to ensure your data is in trustworthy hands.
Frequently Asked Questions (FAQs)
1. Can hiring a hacker near me help recover my lost social media accounts? Yes, ethical hackers can often help you regain access to lost accounts, especially if they have been hacked or compromised.
2. Is it legal to hire a hacker? Hiring an ethical hacker for purposes like security testing or data recovery is legal. However, hiring a hacker to access someone’s account without permission is illegal.
3. What’s the cost to hire a hacker? Costs vary based on the hacker’s experience, the complexity of the work, and your location. Always request a quote upfront.
4. How do I verify a hacker’s credibility? Check for certifications, professional portfolios, and client reviews to ensure the hacker is reputable and reliable.
5. What should I look for in a contract with a hacker? A good contract should outline the scope of work, confidentiality clauses, legal compliance, and payment terms.
0 notes
Text
Uncovering Life’s Mysteries: What Would You Ask a Private Investigator to Investigate?
In a world filled with secrets, mysteries, and unanswered questions, the idea of hiring a private investigator (PI) carries an undeniable allure. Whether it’s to uncover hidden truths, confirm suspicions, or find closure, private investigators have become modern-day detectives in real life. But if you had the opportunity to ask a private investigator to uncover one truth that could change your life forever, what would it be? This question isn’t just hypothetical—it taps into the core of human curiosity and the desire to seek clarity in a world that often feels opaque.

In this blog, we’ll explore the fascinating realm of private investigation, dive into the reasons people turn to PIs, and uncover the types of mysteries that are most commonly sought after. Let’s journey into the possibilities and complexities of truth-seeking through the lens of a private investigator.
The Fascination with Private Investigators
Private investigators have been glamorized in movies, TV shows, and novels. From the hardboiled detectives in noir films to the clever problem-solvers in modern dramas, PIs are often portrayed as fearless individuals with an uncanny ability to uncover hidden truths. In reality, their work involves a mix of surveillance, research, interviewing, and analysis to solve cases ranging from the mundane to the extraordinary.
The appeal of hiring a private investigator lies in their ability to access information and resources that are often beyond the reach of the average person. They can delve into records, track down individuals, and connect the dots in ways that most people cannot. This makes them indispensable in situations where clarity is elusive and the stakes are high.
Why Do People Hire Private Investigators?
There are countless reasons why someone might hire a private investigator, but most boil down to one fundamental need: the search for truth. Whether it’s a personal, legal, or professional matter, private investigators are trusted to provide answers that people can’t uncover on their own. Let’s break down some of the most common reasons:
1. Infidelity Investigations
One of the most common reasons people hire private investigators is to confirm or dispel suspicions of infidelity. Catching a cheating partner is emotionally charged and often requires concrete evidence, such as photographs, videos, or detailed surveillance reports. For many, discovering the truth—even if it’s painful—provides the closure they need to move forward.
2. Missing Persons Cases
From lost family members to runaway teenagers, private investigators are skilled at tracking down individuals who have disappeared. Unlike law enforcement, who may prioritize urgent or criminal cases, PIs can dedicate time and resources to solving personal missing person cases.
3. Background Checks
Whether it’s a new business partner, a romantic interest, or even a prospective nanny, people often turn to private investigators to conduct thorough background checks. These checks can reveal criminal records, financial issues, or inconsistencies in someone’s story.
4. Legal Support
Private investigators often work closely with attorneys to gather evidence for legal cases, such as divorce proceedings, custody battles, or fraud investigations. Their findings can provide critical leverage in court.
5. Corporate Investigations
Businesses may hire private investigators to uncover employee misconduct, intellectual property theft, or insider trading. Corporate espionage is a growing concern, and PIs are skilled at navigating these complex environments.
The Mysteries People Want Solved
Now, let’s return to the core question: If you could ask a private investigator to uncover one truth that could change your life, what would it be? The answers to this question are as diverse as the people asking it. Here are some of the most compelling mysteries that individuals might seek to solve with the help of a PI.
1. Long-Lost Relatives
Reuniting with a long-lost sibling, parent, or child can be life-changing. For adoptees seeking their biological parents or families searching for estranged members, a private investigator can provide the tools and expertise to navigate complex genealogical records and locate individuals.
2. Hidden Assets
In contentious divorces or business disputes, hidden assets can be a significant point of contention. PIs can trace financial transactions, uncover offshore accounts, or identify concealed property, helping clients achieve justice.
3. Unexplained Deaths
For families who suspect foul play or mishandling in the death of a loved one, hiring a PI can be a way to seek the truth. These cases often involve meticulous investigation, forensic analysis, and interviews with witnesses.
4. Lost Heirlooms
Imagine finding a long-lost family treasure or heirloom that holds sentimental or monetary value. Private investigators can help track down stolen or misplaced items, providing closure to families who value their history.
5. Online Scams and Catfishing
In the digital age, online relationships and financial scams are increasingly common. PIs are often called upon to verify identities, track down cybercriminals, or uncover the truth behind suspicious online interactions.
6. Unsolved Personal Questions
Some mysteries are deeply personal and may not fall into traditional categories. For instance, someone might want to investigate a recurring dream, an unexplained memory, or a family secret that has lingered for generations.
The Ethical Dilemma: Should Every Truth Be Uncovered?
While the idea of uncovering hidden truths is exciting, it also raises important ethical questions. Is every mystery worth solving? Should some secrets remain buried? Private investigators often face moral dilemmas, such as balancing the client’s right to know with the potential harm that the truth could cause.
For example, uncovering a partner’s infidelity might lead to irreparable damage in a relationship. Similarly, discovering a long-lost relative might bring joy to some but pain to others. These complexities highlight the importance of approaching private investigations with sensitivity and ethical consideration.
The Process of a Private Investigation
If you decide to hire a private investigator, what can you expect? While each case is unique, most investigations follow a general process:
Consultation: The PI will meet with you to discuss your needs, objectives, and budget. This initial meeting is crucial for setting expectations and outlining the scope of the investigation.
Research and Planning: The investigator will gather preliminary information, such as names, addresses, and relevant documents. They’ll also create a strategy for how to approach the case.
Surveillance and Evidence Gathering: Depending on the case, this may involve physical surveillance, online research, interviewing witnesses, or accessing public records.
Analysis and Reporting: The PI will compile their findings into a comprehensive report, often including photographs, videos, and other evidence.
Follow-Up: If necessary, the investigator may provide additional support, such as testifying in court or conducting further research.
When the Truth Changes Your Life
Uncovering a life-changing truth through a private investigator can lead to a wide range of outcomes. For some, it provides a sense of relief and closure. For others, it opens up new challenges and decisions. Here are a few examples of how the truth can transform lives:
Closure: Knowing what happened to a missing loved one or solving a long-standing mystery can bring peace of mind.
Empowerment: Discovering the truth about a deceitful partner or business associate allows individuals to make informed decisions and regain control of their lives.
Reconnection: Reuniting with a lost family member or friend can create new opportunities for love and understanding.
Accountability: Holding someone accountable for their actions, whether in a legal or personal context, can be empowering and just.
The Role of Technology in Modern Investigations
Private investigators today have access to advanced tools and technologies that make their work more effective. From GPS tracking and facial recognition software to social media analytics and digital forensics, technology has revolutionized the field of private investigation. However, it also raises concerns about privacy and data security, underscoring the need for ethical practices.
Your Mystery Awaits
The idea of hiring a private investigator to solve a life-changing mystery is both thrilling and daunting. It invites us to reflect on the questions we carry in our hearts and the lengths we’re willing to go to find answers. Whether it’s uncovering a hidden truth, reconnecting with a loved one, or resolving a personal dilemma, the decision to seek help from a private investigator is deeply personal—and potentially transformative.
So, if you had the chance to ask a private investigator to uncover one truth, what would it be? Would you seek to solve a long-standing mystery, or would you choose to let sleeping secrets lie? The answer to this question says as much about us as it does about the mysteries we’re drawn to uncover.
#phone hacking service#private investigator#phone hacking#hire a hacker#finding a hacker#spy phone#phone hacking tools
0 notes
Text
Platonic Yandere John Wick
John Wick x Continental Employee Reader

It was a quiet Saturday morning at the Continental, it wasn’t very busy this time of year. Besides all of the shady hitman and crime lords that stayed here periodically. Well, it was only hitmen and crime lords that stayed here due to the hotel being a neutral zone. There were dire consequences to anyone who broke the code.
You somehow found yourself employed here after you got mixed up in a bad situation. You were good with computer, and the man at the front desk thought it would be a lovely idea for you to put your skills to use.
Your job on paper is the IT department, you are the whole department. You help Winston, the older man at the front desk, with any computer issues that he might stumble upon. You help with the Wifi, cable and anything to do with electronics.
But The Continental also offers a new service to its VIP members, a resident hacker. Guests can hire you do do some freelance work for them. You’ve done a couple of jobs, hacking into emails and encrypted hardware for hitmen.
It was stressful work, and the people who hired you have made sure that you won’t be a loose end. You haven’t spoken much since you found yourself in the Underworld, but at least you have free food and a room.
You are in the lounge, trying to figure out what’s wrong with one of the lamps, it wouldn’t turn on. You are pulled from your thoughts when Winston approaches you, you stand up from where you are sitting on the carpet.
He looks over all of the wires that you have pulled from the lamp, he frowns a little. But at least you promised him that you would clean up after you were done messing around with the lamp to see if it could be saved.
“No luck?” He asks, a polite smile on his face. You shake your head slightly, glancing down at the lamp laid on the floor. He sighs a little, seemingly disappointed that the lamp was unsalvageable.
“A shame, it was an antique.” He states as he watches me start to clean up, getting all the screws and wires out of the way. You don’t reply to his comment, and he doesn’t expect you to respond either. You don’t talk much.
“Don’t worry about cleaning up, I’ll get William to do that.” He says, that smile still on his face, it never quite reaches his eyes. William is one of the bartenders in the lounge, he usually is in charge of generic upkeep in the lounge when there aren’t any guests around.
You huff as you stop cleaning up your mess, standing up and facing Winston again.
“Do you need something?” You ask him quietly, wanting to get to the point. You aren’t one for small talk. Winston sighs in mild amusement, he finds your blunt demeanor endearing.
“I do need your assistance. One of the guests requires your services.” He says in his customer service voice. You nod a little as William approaches and starts to tidy up your mess, putting the broken lamp into a garbage bag.
“I’ll go get my computer..” You mumble, walking out of the lounge and into the front lobby.
“Where are they?” You ask Winston quietly, there are a couple of people hanging around in the lobby.
“Mr. Wick is in conference room 2 on the second floor.” Winston replies, handing you your computer from where he keeps it behind the front desk. You take the computer from him and nod.
You enter the elevator in silence, you press the button for the second floor and you wait. The air in the elevator is thick, you are anxious. You hope that you don’t get a target on your back by helping this man. There is always a risk.
You exit the elevator and step out into the hallway. To turn to the right, past a couple talking to each other and into Conference Room Two.
You close the door behind you, and at the end of the long table, is a man in a black suit. It’s John Wick, what could he possibly want from you.
He nods in greeting, seemingly thrown off by how young you are. You couldn’t be more than 19, how did you get mixed up in this line of work?
You give an awkward smile, and you sit to his left at the table. You open up your computer and you turn it on. You are unnerved by the way he is looking at you.
“What do you need done?” You ask him quietly, booting up some of your hacking softwares. You glance over at him before you look back at the computer screen.
“I need you to trace this frequency.” He says, sliding you a USB drive. This will be a little difficult, tracing a frequency from an audio clip? You could be here for a while. You take the drive and you connect it to the computer, you pull the audio clip and drop it into one of your softwares.
He watches as you type away on the computer and as you compare frequencies from all over the globe.
It takes you about half an hour to tell him the rough location of the frequencies origin.
“Munich, Germany.” You mumble, turning the computer screen to him. He hums, and he hands you a large golden coin. The currency of the underworld.
“Don’t you think you’re a little young to be in this line of work?” He asks quietly, his accent Russian-American. He tilts his head a little towards you, waiting for your answer.
You shrug, looking away from him and turning the computer screen back towards you. He frowns a little at your non answer.
“I’ll talk to Winston about letting you go, you’re to young for this.” He says firmly, standing up from his chair. You close the computer and turn it off.
“I’ll be back in a couple of days, I’ll discuss this with Winston before I leave.” He pats you on the shoulder as he passes you, he leaves the conference room and closes the door behind him.

#yandere oneshot#asks open#tw: kidnapping#platonic#platonic yandere#yandere comfort#send asks#platonic john wick#send me asks#yandere john wick#hacker reader#yandere platonic john wick#john wick x reader#platonic yandere john wick
56 notes
·
View notes
Text
one of my notes here says "J.U.D.G.E could be the ones behind the blackout files/the black line. the ones covering it up anyway. what's a comic universe w/o a corrupt govt-like entity?" so there's also that
okay so i was talking to my friend about other names i could give the hero team bc JUDGE just was not sitting right in my head, it feels too much like a 'good enough' which i HATE doing with important parts of my stories lol so anyway i asked them for some other ideas and they accidentally gave me 'sentinel' which sent me down a delightful path and now i have "Sentry/Sentinels" as an all around group name and i think i wanna do somethng with 'theatre' (like a military theatre) but i also really really love calling their HQ's the courthouse and the chapel bc there's just Something about it
#bc there is meant to be a level higher than the courthouse; and theyre the ones who didn't want it to get out abt that lab#but i also hate the idea of my team of heros being gen controlled by someone so yes im going to make them shady and untrustworthy#im just fully incapable of trusting a government even when it's my own. sigh.#omg judge could be sundowns biggest rival and the day they finally get outted as being evil morningstar hacks the local news station#just to laugh#OH THINGS ARE TAKING SHAAAPPPPEEE I LOVE WHEN THIS HAPPEEENNNSSSSSS#current idea that the sentry doesnt exist yet it's only judge#and star is it's own organisation (i think im gonna give them the chapel? or maybe they can have their own thing...hm)#BUT they can be hired by anyone as an emergency service etc etc#so judge still could've intercepted rhiannon's team before hiring them to destroy the lab#and then when the sentry is pulled together they could ask for star to sort of meld with them#OR that could be why rhiannon leaves star - bc she believes in what the sentry is trying to do?? and star sees that and is like 'fine'#and they're friendly with the sentry and are always happy to help out but they are still ultimately their own organisation#kind of like how sometimes doctors are like 'my job is to heal people idc who it is'#fuck yeah this is going great
2 notes
·
View notes
Note
I am sooo disappointed in S2 HOTD, and now I understand why you were warning us about S2 writing. I encourage you to watch Ben Shapiro's S2 review of HOTD. Everything he states hits the point as I feel of S2 writing. But I really feel that if Miguel was still on S2 he would basically steer the ship right, as in writing and direction of the story. Sara Hess needs to be fired definitely. But I don't understand why you don't like Miguel, once he gave us a solid S1. If you want audience to understand why Aemond turned evil from S1, then show us when he immediately returned from Storm's End and Alicent and Otto argue the stupidity in Aemond's decision to kill Luke, once Aegon was offering peace terms to Rhae Rhae. Please explain why you hate Miguel.
I hate Spotchnik because he is the sire of all the bullshit of Season 2.
People, fundamentally, don't understand this point. Sara Hess was not on the original writing staff of HOTD. There was no original writing staff for HOTD. There was Ryan Condal and GRRM that wrote all of the scripts for Season 1.
Sarah Hess was brought on by Spotchnik and his wife as a producer to hack up and rewrite Condal and GRRM's original scripts in order to fit with the overall narrative that Spotchnik (and mostly his wife) wanted to tell in the story.
Sara Hess rewrote and reworked elements of Condal and GRRM's scripts during shooting.
Things such as Criston Cole being a thug rather than the most dangerous man in Westros. Turning Alicent and Rhaenyra's rivalry in the original scripts into a closeted lesbian romance.
Example:
A.) In 1x08 there was no rape of a maid by Aegon. Aegon is introduced in the Condal and GRRM script as having to be collected from a brothel and dragged back to the Red Keep where Alicent scolds him for neglecting Helaena and embarrassing her by his frat boy antics in public.
Sara Hess is on record saying that she and Spotchnik did not jive with Aegon just being a whoring, lazy, drunk. And they wanted to make him more villainous in order to show how Alicent is perpetuating "The Patriarchy" by covering up a rape.
B.) There was no fighting pits in 1x09. In the original script by GRRM and Condal. Aegon is abducted from a tavern while drunk by Misaria and is used as leverage by Misaria for more privileges in Otto's service - not to stop the fighting pits.
Sara Hess wrote Aegon to be involved in fighting pits cause it was "Game of Thrones" - which is her excuse for every bad writing decision she made.
All of 1x09 was rewritten and restructured by Sara Hess at the behest of Spotchnik in order to make the Greens bad. From the awful scene between Alicent and Rhaenys, to Aegon's fighting pits, and the Dragon Pit Massacre.
Tom Glynn-Carney told the story about how he had it out with Sara Hess and Spotchnik when they added the rape scene in 1x08 that wasn't there during the table read. He told them them they were kneecapping Aegon and giving him nowhere to go. To this Spotchnik told him to shut up and do his job as he his told to do it.
My point is that Sara Hess was the hatchet woman of Miguel Spotchnik and his wife. She was brought in by them to purposefully fill HOTD with their sanctimonious bullshit political agenda.
Spotchnik was fired, not because of his wife, but because the new heads of HBO after the merger with Discovery and Warner sent back his Season 2 treatment and told him to start again. Spotchnik threw a massive tantrum because the previous heads of HBO gave him free reign to do whatever he wanted with Artistic Freedom. But the new heads of the studio did not agree to those terms. So he quit and cried like bitch on the way out. And HBO did him a solid by not telling anyone how bad his Season 2 treatments really were.
And since I've read them, I can tell you they're some of the most righteous trash you'll ever read.
Everything you hate about Season 2 is a symptom of a disease that Miguel Spotchnik bio-engineered and spread from bringing on Sara Hess to hiring Olivia Cooke and Emma D'Arcy for their identity and political activism rather than talent.
The taint of Spotchnik's and his wife's vision of HOTD remains long after they've been booted. Mostly because they never got rid of Sara Hess who was the main scribe to most of the bullshit in Season 1 that doomed Season 2.
Two heads of the Hydra were chopped off but one still remains to blight the countryside.
42 notes
·
View notes
Text
Twinkfrump Linkdump

I'm touring my new, nationally bestselling novel The Bezzle! Catch me in CHICAGO (Apr 17), Torino (Apr 21) Marin County (Apr 27), Winnipeg (May 2), Calgary (May 3), Vancouver (May 4), and beyond!

Welcome to the seventeenth Pluralistic linkdump, a collection of all the miscellany that didn't make it into the week's newsletter, cunningly wrought together in a single edition that ranges from the first ISP to AI nonsense to labor organizing victories to the obituary of a brilliant scientist you should know a lot more about! Here's the other 16 dumps:
https://pluralistic.net/tag/linkdump/
If you're reading this (and you are!), it was delivered to you by an internet service provider. Today, the ISP industry is calcified, controlled by a handful of telcos and cable companies. But the idea of an "ISP" didn't come out of a giant telecommunications firm – it was created, in living memory, by excellent nerds who are still around.
Depending on how you reckon, The Little Garden was either the first or the second ISP in America. It was named after a Palo Alto Chinese restaurant frequented by its founders. To get a sense of that founding, read these excellent recollections by Tom Jennings, whose contributions include the seminal zine Homocore, the seminal networking protocol Fidonet, and the seminal third-party PC ROM, whence came Dell, Gateway, Compaq, and every other "PC clone" company.
The first installment describes how an informal co-op to network a few friends turned into a business almost by accident, with thousands of dollars flowing in and out of Jennings' bank account:
https://www.sensitiveresearch.com/Archive/TLG/TLG.html
And it describes how that ISP set a standard for neutrality, boldly declaring that "TLGnet exercises no control whatsoever over the content of the information." They introduced an idea of radical transparency, documenting their router configurations and other technical details and making them available to the public. They hired unskilled punk and queer kids from their communities and trained them to operate the network equipment they'd invented, customized or improvised.
In part two, Jennings talks about the evolution of TLG's radical business-plan: to offer unrestricted service, encouraging their customers to resell that service to people in their communities, having no lock-in, unbundling extra services including installation charges – the whole anti-enshittification enchilada:
https://www.sensitiveresearch.com/Archive/TLG/
I love Jennings and his work. I even gave him a little cameo in Picks and Shovels, the third Martin Hench novel, which will be out next winter. He's as lyrical a writer about technology as you could ask for, and he's also a brilliant engineer and thinker.
The Little Garden's founders and early power-users have all fleshed out Jennings' account of the birth of ISPs. Writing on his blog, David "DSHR" Rosenthal rounds up other histories from the likes of EFF co-founder John Gilmore and Tim Pozar:
https://blog.dshr.org/2024/04/the-little-garden.html
Rosenthal describes some of the more exotic shenanigans TLG got up to in order to do end-runs around the Bell system's onerous policies, hacking in the purest sense of the word, for example, by daisy-chaining together modems in regions with free local calling and then making "permanent local calls," with the modems staying online 24/7.
Enshittification came to the ISP business early and hit it hard. The cartel that controls your access to the internet today is a billion light-years away from the principled technologists who invented the industry with an ethos of care, access and fairness. Today's ISPs are bitterly opposed to Net Neutrality, the straightforward proposition that if you request some data, your ISP should send it to you as quickly and reliably as it can.
Instead, ISPs want to offer "slow-lanes" where they will relegate the whole internet, except for those companies that bribe the ISP to be delivered at normal speed. ISPs have a laughably transparent way of describing this: they say that they're allowing services to pay for "fast lanes" with priority access. This is the same as the giant grocery store that charges you extra unless you surrender your privacy with a "loyalty card" – and then says that they're offering a "discount" for loyal customers, rather than charging a premium to customers who don't want to be spied on.
The American business lobby loves this arrangement, and hates Net Neutrality. Having monopolized every sector of our economy, they are extremely fond of "winner take all" dynamics, and that's what a non-neutral ISP delivers: the biggest services with the deepest pockets get the most reliable delivery, which means that smaller services don't just have to be better than the big guys, they also have to be able to outbid them for "priority carriage."
If everything you get from your ISP is slow and janky, except for the dominant services, then the dominant services can skimp on quality and pocket the difference. That's the goal of every monopolist – not just to be too big to fail, but also too big to care.
Under the Trump administration, FCC chair Ajit Pai dismantled the Net Neutrality rule, colluding with American big business to rig the process. They accepted millions of obviously fake anti-Net Neutrality comments (one million identical comments from @pornhub.com addresses, comments from dead people, comments from sitting US Senators who support Net Neutrality) and declared open season on American internet users:
https://ag.ny.gov/press-release/2021/attorney-general-james-issues-report-detailing-millions-fake-comments-revealing
Now, Biden's FCC is set to reinstate Net Neutrality – but with a "compromise" that will make mobile internet (which nearly all of use sometimes, and the poorest of us are reliant on) a swamp of anticompetitive practices:
https://cyberlaw.stanford.edu/blog/2024/04/harmful-5g-fast-lanes-are-coming-fcc-needs-stop-them
Under the proposed rule, mobile carriers will be able to put traffic to and from apps in the slow lane, and then extort bribes from preferred apps for normal speed and delivery. They'll rely on parts of the 5G standard to pull off this trick.
The ISP cartel and the FCC insist that this is fine because web traffic won't be degraded, but of course, every service is hellbent on pushing you into using apps instead of the web. That's because the web is an open platform, which means you can install ad- and privacy-blockers. More than half of web users have installed a blocker, making it the largest boycott in human history:
https://doc.searls.com/2023/11/11/how-is-the-worlds-biggest-boycott-doing/
But reverse-engineering and modding an app is a legal minefield. Just removing the encryption from an app can trigger criminal penalties under Section 1201 of the DMCA, carrying a five-year prison sentence and a $500k fine. An app is just a web-page skinned in enough IP that it's a felony to mod it.
Apps are enshittification's vanguard, and the fact that the FCC has found a way to make them even worse is perversely impressive. They're voting on this on April 25, and they have until April 24 to fix this. They should. They really should:
https://docs.fcc.gov/public/attachments/DOC-401676A1.pdf
In a just world, cheating ripoff ISPs would the top tech policy story. The operational practices of ISPs effect every single one us. We literally can't talk about tech policy without ISPs in the middle. But Net Neutrality is an also-ran in tech policy discourse, while AI – ugh ugh ugh – is the thing none of us can shut up about.
This, despite the fact that the most consequential AI applications sum up to serving as a kind of moral crumple-zone for shitty business practices. The point of AI isn't to replace customer service and other low-paid workers who have taken to demanding higher wages and better conditions – it's to fire those workers and replace them with chatbots that can't do their jobs. An AI salesdroid can't sell your boss a bot that can replace you, but they don't need to. They only have to convince your boss that the bot can do your job, even if it can't.
SF writer Karl Schroeder is one of the rare sf practitioners who grapples seriously with the future, a "strategic foresight" guy who somehow skirts the bullshit that is the field's hallmark:
https://pluralistic.net/2024/03/07/the-gernsback-continuum/#wheres-my-jetpack
Writing on his blog, Schroeder describes the AI debates roiling the Association of Professional Futurists, and how it's sucking him into being an unwilling participant in the AI hype cycle:
https://kschroeder.substack.com/p/dragged-into-the-ai-hype-cycle
Schroeder's piece is a thoughtful meditation on the relationship of SF's thought-experiments and parables about AI to the promises of AI hucksters, who promise that a) "general artificial intelligence" is just around the corner and that b) it will be worth trillions of dollars.
Schroeder – like other sf writers including Ted Chiang and Charlie Stross (and me) – comes to the conclusion that AI panic isn't about AI, it's about power. The artificial life-form devouring the planet and murdering our species is the limited liability corporation, and its substrate isn't silicon, it's us, human bodies:
What’s lying underneath all our anxieties about AGI is an anxiety that has nothing to do with Artificial Intelligence. Instead, it’s a manifestation of our growing awareness that our world is being stolen from under us. Last year’s estimate put the amount of wealth currently being transferred from the people who made it to an idle billionaire class at $5.2 trillion. Artificial General Intelligence whose environment is the server farms and sweatshops of this class is frightening only because of its capacity to accelerate this greatest of all heists.
After all, the business-case for AI is so very thin that the industry can only survive on a torrent of hype and nonsense – like claims that Amazon's "Grab and Go" stores used "AI" to monitor shoppers and automatically bill them for their purchases. In reality, the stores used thousands of low-paid Indian workers to monitor cameras and manually charge your card. This happens so often that Indian technologists joke that "AI" stands for "absent Indians":
https://pluralistic.net/2024/01/29/pay-no-attention/#to-the-little-man-behind-the-curtain
Isn't it funny how all the really promising AI applications are in domains that most of us aren't qualified to assess? Like the claim that Google's AI was producing millions of novel materials that will shortly revolutionize all forms of production, from construction to electronics to medical implants:
https://deepmind.google/discover/blog/millions-of-new-materials-discovered-with-deep-learning/
That's what Google's press-release claimed, anyway. But when two groups of experts actually pulled a representative sample of these "new materials" from the Deep Mind database, they found that none of these materials qualified as "credible, useful and novel":
https://pubs.acs.org/doi/10.1021/acs.chemmater.4c00643
Writing about the researchers' findings for 404 Media, Jason Koebler cites Berkeley researchers who concluded that "no new materials have been discovered":
https://www.404media.co/google-says-it-discovered-millions-of-new-materials-with-ai-human-researchers/
The researchers say that AI data-mining for new materials is promising, but falls well short of Google's claim to be so transformative that it constitutes the "equivalent to nearly 800 years’ worth of knowledge" and "an order-of-magnitude expansion in stable materials known to humanity."
AI hype keeps the bubble inflating, and for so long as it keeps blowing up, all those investors who've sunk their money into AI can tell themselves that they're rich. This is the essence of "a bezzle": "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it":
https://pluralistic.net/2023/03/09/autocomplete-worshippers/#the-real-ai-was-the-corporations-that-we-fought-along-the-way
Among the best debezzlers of AI are the Princeton Center for Information Technology Policy's Arvind Narayanan and Sayash Kapoor, who edit the "AI Snake Oil" blog. Now, they've sold a book with the same title:
https://www.aisnakeoil.com/p/ai-snake-oil-is-now-available-to
Obviously, books move a lot more slowly than blogs, and so Narayanan and Kapoor say their book will focus on the timeless elements of identifying and understanding AI snake oil:
In the book, we explain the crucial differences between types of AI, why people, companies, and governments are falling for AI snake oil, why AI can’t fix social media, and why we should be far more worried about what people will do with AI than about anything AI will do on its own. While generative AI is what drives press, predictive AI used in criminal justice, finance, healthcare, and other domains remains far more consequential in people’s lives. We discuss in depth how predictive AI can go wrong. We also warn of the dangers of a world where AI continues to be controlled by largely unaccountable big tech companies.
The book's out in September and it's up for pre-order now:
https://bookshop.org/p/books/ai-snake-oil-what-artificial-intelligence-can-do-what-it-can-t-and-how-to-tell-the-difference-arvind-narayanan/21324674
One of the weirder and worst side-effects of the AI hype bubble is that it has revived the belief that it's somehow possible for giant platforms to monitor all their users' speech and remove "harmful" speech. We've tried this for years, and when humans do it, it always ends with disfavored groups being censored, while dedicated trolls, harassers and monsters evade punishment:
https://pluralistic.net/2022/08/07/como-is-infosec/
AI hype has led policy-makers to believe that we can deputize online services to spy on all their customers and block the bad ones without falling into this trap. Canada is on the verge of adopting Bill C-63, a "harmful content" regulation modeled on examples from the UK and Australia.
Writing on his blog, Canadian lawyer/activist/journalist Dimitri Lascaris describes the dire speech implications for C-63:
https://dimitrilascaris.org/2024/04/08/trudeaus-online-harms-bill-threatens-free-speech/
It's an excellent legal breakdown of the bill's provisions, but also a excellent analysis of how those provisions are likely to play out in the lives of Canadians, especially those advocating against genocide and taking other positions the that oppose the agenda of the government of the day.
Even if you like the Trudeau government and its policies, these powers will accrue to every Canadian government, including the presumptive (and inevitably, totally unhinged) near-future Conservative majority government of Pierre Poilievre.
It's been ten years since Martin Gilens and Benjamin I Page published their paper that concluded that governments make policies that are popular among elites, no matter how unpopular they are among the public:
https://www.cambridge.org/core/journals/perspectives-on-politics/article/testing-theories-of-american-politics-elites-interest-groups-and-average-citizens/62327F513959D0A304D4893B382B992B
Now, this is obviously depressing, but when you see it in action, it's kind of wild. The Biden administration has declared war on junk fees, from "resort fees" charged by hotels to the dozens of line-items added to your plane ticket, rental car, or even your rent check. In response, Republican politicians are climbing to their rear haunches and, using their actual human mouths, defending junk fees:
https://prospect.org/politics/2024-04-12-republicans-objectively-pro-junk-fee/
Congressional Republicans are hell-bent on destroying the Consumer Finance Protection Bureau's $8 cap on credit-card late-fees. Trump's presumptive running-mate Tim Scott is making this a campaign plank: "Vote for me and I will protect your credit-card company's right to screw you on fees!" He boasts about the lobbyists who asked him to take this position: champions of the public interest from the Consumer Bankers Association to the US Chamber of Commerce.
Banks stand to lose $10b/year from this rule (which means Americans stand to gain $10b/year from this rule). What's more, Scott's attempt to kill the rule is doomed to fail – there's just no procedural way it will fly. As David Dayen writes, "Not only does this vote put Republicans on the spot over junk fees, it’s a doomed vote, completely initiated by their own possible VP nominee."
This is an hilarious own-goal, one that only brings attention to a largely ignored – but extremely good – aspect of the Biden administration. As Adam Green of Bold Progressives told Dayen, "What’s been missing is opponents smoking themselves out and raising the volume of this fight so the public knows who is on their side."
The CFPB is a major bright spot in the Biden administration's record. They're doing all kind of innovative things, like making it easy for you to figure out which bank will give you the best deal and then letting you transfer your account and all its associated data, records and payments with a single click:
https://pluralistic.net/2023/10/21/let-my-dollars-go/#personal-financial-data-rights
And now, CFPB chair Rohit Chopra has given a speech laying out the agency's plan to outlaw data-brokers:
https://www.consumerfinance.gov/about-us/newsroom/prepared-remarks-of-cfpb-director-rohit-chopra-at-the-white-house-on-data-protection-and-national-security/
Yes, this is some good news! There is, in fact, good news in the world, bright spots amidst all the misery and terror. One of those bright spots? Labor.
Unions are back, baby. Not only do the vast majority of Americans favor unions, not only are new shops being unionized at rates not seen in generations, but also the largest unions are undergoing revolutions, with control being wrestled away from corrupt union bosses and given to the rank-and-file.
Many of us have heard about the high-profile victories to take back the UAW and Teamsters, but I hadn't heard about the internal struggles at the United Food and Commercial Workers, not until I read Hamilton Nolan's gripping account for In These Times:
https://inthesetimes.com/article/revolt-aisle-5-ufcw-grocery-workers-union
Nolan profiles Faye Guenther, president of UFCW Local 3000 and her successful and effective fight to bring a militant spirit back to the union, which represents a million grocery workers. Nolan describes the fight as "every bit as dramatic as any episode of Game of Thrones," and he's not wrong. This is an inspiring tale of working people taking power away from scumbag monopoly bosses and sellout fatcat leaders – and, in so doing, creating a institution that gets better wages, better working conditions, and a better economy, by helping to block giant grocery mergers like Kroger/Albertsons.
I like to end these linkdumps on an up note, so it feels weird to be closing out with an obituary, but I'd argue that any celebration of the long life and many accomplishments of my friend and mentor Anne Innis Dagg is an "up note."
I last wrote about Anne in 2020, on the release of a documentary about her work, "The Woman Who Loved Giraffes":
https://pluralistic.net/2020/02/19/pluralist-19-feb-2020/#annedagg
As you might have guessed from the title of that doc, Anne was a biologist. She was the first woman scientist to do field-work on giraffes, and that work was so brilliant and fascinating that it kicked off the modern field of giraffology, which remains a woman-dominated specialty thanks to her tireless mentoring and support for the scientists that followed her.
Anne was also the world's most fearsome slayer of junk-science "evolutionary psychology," in which "scientists" invent unfalsifiable just-so stories that prove that some odious human characteristic is actually "natural" because it can be found somewhere in the animal kingdom (i.e., "Darling, please, it's not my fault that I'm fucking my grad students, it's the bonobos!").
Anne wrote a classic – and sadly out of print – book about this that I absolutely adore, not least for having one of the best titles I've ever encountered: "Love of Shopping" Is Not a Gene:
https://memex.craphound.com/2009/11/04/love-of-shopping-is-not-a-gene-exposing-junk-science-and-ideology-in-darwinian-psychology/
Anne was my advisor at the University of Waterloo, an institution that denied her tenure for fifty years, despite a brilliant academic career that rivaled that of her storied father, Harold Innis ("the thinking person's Marshall McLuhan"). The fact that Waterloo never recognized Anne is doubly shameful when you consider that she was awarded the Order of Canada:
https://nationalpost.com/news/canada/queen-of-giraffes-among-new-order-of-canada-recipients-with-global-influence
Anne lived a brilliant live, struggling through adversity, never compromising on her principles, inspiring a vast number of students and colleagues. She lived to ninety one, and died earlier this month. Her ashes will be spread "on the breeding grounds of her beloved giraffes" in South Africa this summer:
https://obituaries.therecord.com/obituary/anne-innis-dagg-1089534658

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/04/13/goulash/#material-misstatement

Image: Valeva1010 https://commons.wikimedia.org/wiki/File:Hungarian_Goulash_Recipe.png
CC BY-SA 4.0 https://creativecommons.org/licenses/by-sa/4.0/deed.en
#pluralistic#linkdump#linkdumps#junk fees#fcc#ai#ai hype#labor#unions#hamilton nolan#history#cfpb#privacy#online harms#ai snake oil#anne dagg#anne innis dagg#obits#rip#mobile#net neutrality#5g
88 notes
·
View notes
Text
I love how every single Guilty Gear character could easily fit as the main character of their own series, each one incredibly thematically different than the original series. Like

Stealth action game about a young ninja avenging his master’s death against the villainous league of assassins

Slice of Life comedy Isekai where a regular dude gets sucked into a sci-fi fantasy dimension 185 years in the future and has to make friends with the ridiculously overpowered warriors there in order to find his girlfriend

Grimdark victorian horror hack-and-slash (similar to American McGee’s Alice series) about a melancholy and delusional homunculus fighting to find a body for her beloved bloodthirsty giant key husband (No morality to be found in any character, entirely 2000s edge)

Serial manga about a powerful and mysterious fan-wielding bishonen warrior, wandering the world in search of his equally powerful love interest / rival who’s been completely consumed by revenge and must be saved from herself

Quirky Earthbound-inspired indie RPG about a young adventurer discovering her true self with the help of her friends (including a talking teddy bear, a crew of all-female sky pirates, a mysterious forest goddess and her guardian, and many more)

Soulslike with a blindness gimmick about a power-hungry wizard who lost his sight in a deal with a demon, and must rely on the demon to fight his way through a world that wants him dead

Bayonetta. Yeah that’s it.

Restaurant simulator in which you, the struggling owner, aren’t making enough money to stay afloat with the restaurant alone, and need to use your Kung-fu skills to find income through other, more violent means. Essentially there’s two main gamemodes. By day: Cooking Mama. By night: Streets of Rage. You have to spend your money wisely between upgrades to your restaurant or to your fighting ability, as failing at either will leave you with either your restaurant closing down or you getting beaten beaten to death, respectively. If you can get through an entire year with your restaurant firmly open and your teeth firmly un-kicked, you win the game! (no matter which shady methods you had to use to get there). Hire employees! Fire employees! Beat up said former employees in an alleyway as they’ve since turned to a life of crime, then turn them in for bounty money! You can do all this and more in the new game coming to Nintendo Switch: Kung-Food Service! (Temporary title until an actually good one is found)

Standard dating sim, except it’s impossible to win and the true ending is the main character finding out she’s a lesbian
#guilty gear#chipp zanuff#Anji mito#bridget guilty gear#zato 1#I-no#jam kuradoberi#may guilty gear#oh my god trying to use images on tumblr mobile sucks#a.b.a. guilty gear#her#me
814 notes
·
View notes
Text
werewolf steve, werebat eddie (ch3)
🐺🛌🦇🥺
It’s the quiet conviction that he’s in the wrong bed that wakes Eddie the next morning. The mattress too soft, the pillow too thick, and the boy next to him is an unwavering, giant red flag too. He sighs, hand under his cheek and contemplates the sleep-creased face of Steve Harrington next to little old Eddie Munson.
And he thought turning into a bat was going to be the only weird part of this weekend.
Steve snuffles, twitching his nose before falling back into a steady breathing rhythm again. And Eddie would like to deny how cute it is, would like to refuse to see how handsome Steve is, and would very much like to pinch the thin river of greed winding through him that would like the chance to have a fun, kind guy too. Someone who stirs Eddie, makes him laugh. But that’s not his fate in this lifetime.
He turns onto his back, staring directly above at the bubble pattern of the ceiling and determinedly focusing on more important matters.
Like the fact that he’s a bat now.
Apparently.
Rubbing his eyes with his thumb and forefinger, he wonders what the hell to do with that knowledge. It’s not going to get him anywhere; there’s no big corporation that wants to hire bat services. Last he heard, the ability to squeak wasn’t going to land him a record deal. Eddie huffs out a laugh, maybe he can get into acting. Take this gig out on the road.
No, just like having to watch a girl be brutally murdered in front of him and only barely scraping past that hack job Hawkins PD called an investigation, Eddie is going to have to take his lumps and keep moving.
He peers at the awful plaid wallpaper of the bedroom. Unsurprised by the banality of it, the hint of wasted money on lack of taste, but he is surprised by the pleasant abundance of greenery across the whole space. Potted plants crowd every available surface, some with trailing vines flowing over containers hanging from the ceiling. Even with the window closed, the room smells fresh, a clean sweetness to the air that matches the shiningly healthy and obviously well-cared for leaves, flowers and, he peers closer, herbs.
He wonders whether Steve dug these out of the woods with his big furry paws or if he’d bought them at the local nursery. Looking at the array of sizes and colourful patterns on the clay pots he figures that Steve shelled out a decent amount of money for his botanical set-up.
It twinges something in Eddie. Steve, just as taken in by the Upside Down, doomed to forever be a half-man and half-beast too, but sleeping peacefully within an oasis of his creation, sheltered by the tall walls of the Harrington home, with friends who love him, who don’t care about the monster within.
It feels unfair.
Because what is Eddie now? A monster? Maybe. A creature? Definitely. This new change in his life won’t make it any better, it won’t give him any advantages. It’s just one more thing he’s going to have to hide. To squirrel away like a tender thing lest the soft belly of it be exposed to the type of people who would hurt him.
Hurt, he knows, comes in many different forms. From a father believing your best value is in using small hands to boost a car, in the indifference of a mother leaving you on your uncle’s doorstep, on your best friend pushing you to the floor when you try to kiss him.
He looks over at the effortlessly handsome features of Steve, at his expensive and beautiful room, and thinks that whatever risk Steve carries, it is nothing like the one Eddie would be exposed to if his new secret got out.
He spots a familiar animal on the cover of a book on the bedside table. Curiously, he picks it up, flicking his eyes over the types of bats in the world, their characteristics, advice on care, and other little random facts.
Steve stirs, smacking his lips his eyelashes flutter before his gaze opens to land on Eddie bent over the book. He’s under the blanket that Eddie lays over; his bat version must have crawled out of the hoodie at some point but remained on top of the bed. Last night had been a blur and he doesn’t remember much except panic followed by Steve’s warm hands.
“Hey,” Steve smiles sleepily, “You came back to us.”
Eddie grunts, “Yeah, not sure exactly how that happened, but small blessings and all that.” He scans the feeding behaviour header, noting that blood is indeed amongst fruit, insects, and nectar as their preferred diet. Pausing, he tastes his mouth like it’ll suddenly reveal an obvious craving for bloody flesh. Meeting only morning breath, he grimaces and continues reading.
Finally realising that Steve has been silent for an unusually long pause, he glances over only to be startled by the intent look in his eye as he regards Eddie. “Are you okay?” He asks quietly and Eddie bristles at the concern, resentment stirring that Steve gets to be the kind one. The guy who cares despite being similarly afflicted. Why can’t he be just as resentful and mean as Eddie?
“Well, it’s not a giant dog, but I suppose you should welcome me to the club.”
Steve purses his lips thoughtfully, “I’ll ignore the canine dig for now since I know you’re going through something. But I get it, you know? If you can talk to anyone about being suddenly faced with the oddity of waking up in a body that no longer feels like your own, it’s me.”
Eddie rolls his eyes down at the book, “Our life experiences are vastly different, Steve. I don’t think you could get where I’m coming from if you tried.”
“Maybe not all of it,” Steve admits carefully, sitting up so he and Eddie are on the same level, “But I can try. And it’s got to be better than holding it in. You’re a pretty verbal guy, Eddie. I figure’d you’d want to talk about this.”
“What’s that mean?” Eddie glares at him and Steve raises his palms, saying, “Just that you seem to like talking your thoughts out, and that I’m here, willing to listen if you want to get anything off your chest.”
“Yeah, well, you can keep that hairy chest to yourself,” Eddie mutters darkly, looking at a bat’s mouth held open, exposing sharp fangs from front to back like a deadly, serrated knife. He presses his tongue against his molars thoughtfully; he doesn’t remember there being a lot of sharp tools in his mouth.
“Right,” Steve huffs out a frustrated breath, “You’re obviously in a mood. But fair, you’re allowed to take a beat until you get your feet under you.”
“I’m allowed,” Eddie mocks under his breath.
Steve cocks his head, “Yeah, you’re allowed. Just like I was allowed to take a beat too, once I figured out that turning into a wolf wasn’t a hallucination or a mental breakdown.” Eddie ignores him and Steve says with frustration, “What’s your problem?”
As he does, Eddie’s eyes catch on a fun fact section, and he can’t help the grim laughter that escapes. Of course. Of fucking course. He hears the mounting irritation in Steve’s voice as he calls his name again and latches on to it, happy to smack back. “Did you know, Steve,” Eddie starts, meanness fuelling his smirk, only he has a feeling that the petty feeling is directed inwards. “That bats have the highest rate of homosexuality out of any mammal?”
Steve watches him warily, “Are you saying that the shift turned you gay? ‘Cause I’m not sure it works like that,” his lips tug up cautiously, “It didn’t for me, anyway.”
Eddie sees the invitation to share the joke in Steve’s expression and it fuels the bitterness, “Yeah, well, you being a straight dog isn’t going to surprise anyone.”
Invitation dropping accompanied by eyes narrowing, Steve says, “That’s fucking condescending.” Eddie sees the insult across his face and rolls his eyes, conviction spreading that Steve has never had to think about how he presents to the world for one fucking minute before being afflicted with their shared infection.
“All I’m saying is that the wolf stuff may have made you a bit weird, but you were never gay-boy-in-Hawkins weird to begin with. Let alone the shitty kid from the shitty family with parents who don’t give a fuck.”
Steve’s eyes harden and he sucks his breath between his teeth consideringly, “I’m not sure whether I should share with you how wrong you are or simply tell you to fuck off.”
Eddie stares back just as hard, “You can’t tell me that you were ever the weird guy, Mr Popular Jock. What? Did you get ostracised from the team when you wore the wrong lucky jock strap?”
Rolling his lips, Steve nods his head decisively, “Yeah, you know what? I am going to tell you to fuck off.” Any hint of warmth in his expression shutters away and Eddie blinks, not having realised how open Steve had been with him even while they bickered. Steve continues, voice flat and unfriendly, “You know what your problem is, Eddie?”
“What?” He tries to sneer but the feeling of being wrong-footed continues and it lands with less force than he wants.
“You think you’ve got everyone worked out,” Steve trails his eyes over Eddie's face leaving his skin feeling flushed and burning, “What was it you said in the Upside Down? The Munson Doctrine? I was barely enough for you to approve of even then, right?”
The ground beneath Eddie’s feet shudders slightly, shaking his gut into an uneasy feeling but Steve doesn’t notice his suddenly shaky equilibrium as he bitingly continues, “I suppose I only met the bare minimum when you said that I was a good guy: I wasn’t a massive asshole that would allow you to take the rap for Chrissy’s murder or, I don’t know,” he laughs with very little humour, “Let Max be killed by Vecna? So that must mean I was scarcely half decent, right?”
Eddie frowns: he had meant what he said in the Upside Down — he’d seen Steve care for the party, chase after Max and make sure the kids were safe. He’d been a steady port in the storm who Eddie had looked to more than once while feeling unsafe and unsure, and Steve had always been looking back, with either a reassuring nod or a helpful explanation in the sort of plain speak necessary for a newbie to their wretched adventures.
Steve rolls out of bed and Eddie can’t even be mad that he might use his height to his advantage because he heads straight to the doorway, pausing with his hand steady on the frame. He shakes his head looking down, “I thought that you saw me. It didn’t have to be every part, but I thought that you at least saw that I’m trying to be a good person.”
He looks up and Eddie is pierced clean through by the hurt in his eyes, the walls falling briefly to allow this one sad glimpse, “But ever since I showed you who I really am, what I am, I’ve realised that your approval comes with conditions.”
“That’s not true,” Eddie protests, furiously thinking, but his gut sinks below his feet when he can’t work out a counterargument to the accusation.
The walls over Steve’s eyes swiftly build up again, leaving only a cold man in its wake. “You assuming how easy I’ve always had it tells me that you never cared enough to look below the surface anyway.” He regards Eddie for one last long second as if taking him in for the final time, and Eddie is unsure how to respond when the ground is rumbling so strongly under his feet.
Steve leaves.
Quietly and without looking back at Eddie. No fanfare in the movement as if he’s decided that he’s not worth the fight. He realises now that he’d expected Steve to push back, to argue for Eddie to do better, but—having left him behind—Eddie doesn’t know what to do other than to quietly take his book and leave.
No one sees him out.
If you enjoyed any of this, I hope you'll consider leaving a message over on Ao3 because you would make my day. :)
#scattering a wee bit of conflict on the grass for the chickadees#steddie#swift wings and a brave heart#steve harrington#eddie munson#stranger things#werewolf steve harrington#bat eddie munson
70 notes
·
View notes
Note
Hi Freddie! I believe you said you were having a rough time hacking, or rather, uh, journalistically accessing, the information from Hannibal Lecter and Will Graham’s internet devices…. Well, I happen to be fairly good at things like that. Here are the wedding photos… I have reason to believe they cooked the photographer afterwards instead of hiring catering service… regardless, here’s your scoop!


THANK YOU SO MUCH, TATTLER! Your devotion to MAKING TATTLECRIME THRIVE is ASTOUNDING! These two OLD MEN look SURPRISINGLY CUTE TOGETHER. I'm surprised that there isn't any BLOODY CARNAGE hiding in the background! After all, they are MURDER HUSBANDS! I have to ask -- how did you manage to GET A HOLD of these DIAMONDS? Don't worry -- YOUR SECRETS ARE SAFE WITH MS. LOUNDS!
44 notes
·
View notes
Text
"Just weeks before the implosion of AllHere, an education technology company that had been showered with cash from venture capitalists and featured in glowing profiles by the business press, America’s second-largest school district was warned about problems with AllHere’s product.
As the eight-year-old startup rolled out Los Angeles Unified School District’s flashy new AI-driven chatbot — an animated sun named “Ed” that AllHere was hired to build for $6 million — a former company executive was sending emails to the district and others that Ed’s workings violated bedrock student data privacy principles.
Those emails were sent shortly before The 74 first reported last week that AllHere, with $12 million in investor capital, was in serious straits. A June 14 statement on the company’s website revealed a majority of its employees had been furloughed due to its “current financial position.” Company founder and CEO Joanna Smith-Griffin, a spokesperson for the Los Angeles district said, was no longer on the job.
Smith-Griffin and L.A. Superintendent Alberto Carvalho went on the road together this spring to unveil Ed at a series of high-profile ed tech conferences, with the schools chief dubbing it the nation’s first “personal assistant” for students and leaning hard into LAUSD’s place in the K-12 AI vanguard. He called Ed’s ability to know students “unprecedented in American public education” at the ASU+GSV conference in April.
Through an algorithm that analyzes troves of student information from multiple sources, the chatbot was designed to offer tailored responses to questions like “what grade does my child have in math?” The tool relies on vast amounts of students’ data, including their academic performance and special education accommodations, to function.
Meanwhile, Chris Whiteley, a former senior director of software engineering at AllHere who was laid off in April, had become a whistleblower. He told district officials, its independent inspector general’s office and state education officials that the tool processed student records in ways that likely ran afoul of L.A. Unified’s own data privacy rules and put sensitive information at risk of getting hacked. None of the agencies ever responded, Whiteley told The 74.
...
In order to provide individualized prompts on details like student attendance and demographics, the tool connects to several data sources, according to the contract, including Welligent, an online tool used to track students’ special education services. The document notes that Ed also interfaces with the Whole Child Integrated Data stored on Snowflake, a cloud storage company. Launched in 2019, the Whole Child platform serves as a central repository for LAUSD student data designed to streamline data analysis to help educators monitor students’ progress and personalize instruction.
Whiteley told officials the app included students’ personally identifiable information in all chatbot prompts, even in those where the data weren’t relevant. Prompts containing students’ personal information were also shared with other third-party companies unnecessarily, Whiteley alleges, and were processed on offshore servers. Seven out of eight Ed chatbot requests, he said, are sent to places like Japan, Sweden, the United Kingdom, France, Switzerland, Australia and Canada.
Taken together, he argued the company’s practices ran afoul of data minimization principles, a standard cybersecurity practice that maintains that apps should collect and process the least amount of personal information necessary to accomplish a specific task. Playing fast and loose with the data, he said, unnecessarily exposed students’ information to potential cyberattacks and data breaches and, in cases where the data were processed overseas, could subject it to foreign governments’ data access and surveillance rules.
Chatbot source code that Whiteley shared with The 74 outlines how prompts are processed on foreign servers by a Microsoft AI service that integrates with ChatGPT. The LAUSD chatbot is directed to serve as a “friendly, concise customer support agent” that replies “using simple language a third grader could understand.” When querying the simple prompt “Hello,” the chatbot provided the student’s grades, progress toward graduation and other personal information.
AllHere’s critical flaw, Whiteley said, is that senior executives “didn’t understand how to protect data.”
...
Earlier in the month, a second threat actor known as Satanic Cloud claimed it had access to tens of thousands of L.A. students’ sensitive information and had posted it for sale on Breach Forums for $1,000. In 2022, the district was victim to a massive ransomware attack that exposed reams of sensitive data, including thousands of students’ psychological evaluations, to the dark web.
With AllHere’s fate uncertain, Whiteley blasted the company’s leadership and protocols.
“Personally identifiable information should be considered acid in a company and you should only touch it if you have to because acid is dangerous,” he told The 74. “The errors that were made were so egregious around PII, you should not be in education if you don’t think PII is acid.”
Read the full article here:
https://www.the74million.org/article/whistleblower-l-a-schools-chatbot-misused-student-data-as-tech-co-crumbled/
17 notes
·
View notes
Text

HIRE A HACKER TO FIX YOUR CREDIT SCORE.
I was homeless and I had an eviction on my credit that wouldn't let anyone rent or sell to me. I needed to fix my credit and remove the eviction. Captain WebGenesis worked on my profile as I was directed to the Expert by my work colleague. Within the space of 3- 6 business working days, Captain WebGenesis removed the eviction, cleared other negative items and boosted my scores to 1099. Purchasing my new home was an easy and pleasant process. I highly recommend Captain WebGenesis for any kind of hacking service. The Expert is fast and reliable when it comes to hacking.
HIRE A HACKER TO FIX YOUR CREDIT SCORE.I was homeless and I had an eviction on my credit that wouldn't let anyone rent or sell to me. I needed to fix my credit and remove the eviction. Captain WebGenesis worked on my profile as I was directed to the Expert by my work colleague. Within the space of 3- 6 business working days, Captain WebGenesis removed the eviction, cleared other negative items and boosted my scores to 1099. Purchasing my new home was an easy and pleasant process. I highly recommend Captain WebGenesis for any kind of hacking service. The Expert is fast and reliable when it comes to hacking.
61 notes
·
View notes
Text
KnowBe4, a US-based security vendor, revealed that it unwittingly hired a North Korean hacker who attempted to load malware into the company's network. KnowBe4 CEO and founder Stu Sjouwerman described the incident in a blog post this week, calling it a cautionary tale that was fortunately detected before causing any major problems.
"First of all: No illegal access was gained, and no data was lost, compromised, or exfiltrated on any KnowBe4 systems," Sjouwerman wrote. “This is not a data breach notification, there was none. See it as an organizational learning moment I am sharing with you. If it can happen to us, it can happen to almost anyone. Don't let it happen to you.”
KnowBe4 said it was looking for a software engineer for its internal IT AI team. The firm hired a person who, it turns out, was from North Korea and was "using a valid but stolen US-based identity" and a photo that was "enhanced" by artificial intelligence. There is now an active FBI investigation amid suspicion that the worker is what KnowBe4's blog post called "an Insider Threat/Nation State Actor."
KnowBe4 operates in 11 countries and is headquartered in Florida. It provides security awareness training, including phishing security tests, to corporate customers. If you occasionally receive a fake phishing email from your employer, you might be working for a company that uses the KnowBe4 service to test its employees' ability to spot scams.
Person Passed Background Check and Video Interviews
KnowBe4 hired the North Korean hacker through its usual process. "We posted the job, received résumés, conducted interviews, performed background checks, verified references, and hired the person. We sent them their Mac workstation, and the moment it was received, it immediately started to load malware," the company said.
Even though the photo provided to HR was fake, the person who was interviewed for the job apparently looked enough like it to pass. KnowBe4's HR team "conducted four video conference based interviews on separate occasions, confirming the individual matched the photo provided on their application," the post said. "Additionally, a background check and all other standard pre-hiring checks were performed and came back clear due to the stolen identity being used. This was a real person using a valid but stolen US-based identity. The picture was AI 'enhanced.'"
The two images at the top of this story are a stock photo and what KnowBe4 says is the AI fake based on the stock photo. The stock photo is on the left, and the AI fake is on the right.
The employee, referred to as "XXXX" in the blog post, was hired as a principal software engineer. The new hire's suspicious activities were flagged by security software, leading KnowBe4's Security Operations Center (SOC) to investigate:
On July 15, 2024, a series of suspicious activities were detected on the user beginning at 9:55 pm EST. When these alerts came in KnowBe4's SOC team reached out to the user to inquire about the anomalous activity and possible cause. XXXX responded to SOC that he was following steps on his router guide to troubleshoot a speed issue and that it may have caused a compromise. The attacker performed various actions to manipulate session history files, transfer potentially harmful files, and execute unauthorized software. He used a Raspberry Pi to download the malware. SOC attempted to get more details from XXXX including getting him on a call. XXXX stated he was unavailable for a call and later became unresponsive. At around 10:20 pm EST SOC contained XXXX's device.
“Fake IT Worker From North Korea”
The SOC analysis indicated that the loading of malware "may have been intentional by the user," and the group "suspected he may be an Insider Threat/Nation State Actor," the blog post said.
"We shared the collected data with our friends at Mandiant, a leading global cybersecurity expert, and the FBI, to corroborate our initial findings. It turns out this was a fake IT worker from North Korea," Sjouwerman wrote.
KnowBe4 said it can't provide much detail because of the active FBI investigation. But the person hired for the job may have logged into the company computer remotely from North Korea, Sjouwerman explained:
How this works is that the fake worker asks to get their workstation sent to an address that is basically an "IT mule laptop farm." They then VPN in from where they really physically are (North Korea or over the border in China) and work the night shift so that they seem to be working in US daytime. The scam is that they are actually doing the work, getting paid well, and give a large amount to North Korea to fund their illegal programs. I don't have to tell you about the severe risk of this. It's good we have new employees in a highly restricted area when they start, and have no access to production systems. Our controls caught it, but that was sure a learning moment that I am happy to share with everyone.
14 notes
·
View notes
Text
The Bad Batch and their jobs (Modern AU)
In my headcanon they all started out as soldiers. After getting out and accidentally acquisiting Omega, they desperately need money and take any jobs they can get. Eventually, everyone finds something they actually like.
Hunter:
Retail sales associate aka Walmart slave and getting yelled at by Karens all day. He's also doing freelance cleaning jobs, the grosser the better the payment. Think hoarder apartments with fifty cats or scat orgy hotel room cleanup.
He works hard on getting his record cleaned up and eventually secures a job at the fire station. He becomes a firefighter and will eventually be a lieutenant and later captain.
Tech:
Fast food worker which means lots of being yelled at by hangry people who are unhappy with the way their BigMac was stacked. He takes any extra shift he can get.
After several failed rounds of applications, he hacks into a big company's system and puts his name on top of the candidate list. He ends up supervisor for some bank insurance IT stuff with lots of numbers.
Wrecker: Miner. It's hard work and long hours in the dark. He actually earns the most of all of them but that's because it's fucking dangerous and depressing.
The leading instructor for the demolition expert trainees blows up. Wrecker, having had professional training in the military and lots of experience at not getting blown up (again), is their best take so he becomes their new instructor for the new hires.
Crosshair: Nobody is really willing to hire him so he's an unlicensed taxi driver most nights. (He hates everything about it.) He also signed up as a freelance roadkill collector job in Hunter's name and takes the calls when he doesn't have passengers.
He meets railroaders when cleaning up railkill one night. When smoking he mentions how much he hates being a taxi driver and the railroaders recruit him for their company. He becomes a traindriver and finally doesn't have to interact with his passengers.
Echo: They call it online sales associate marketer and customer service advisor. He calls it tele-scam-marketer. Many people yelling at him but at least he can work from home.
At a parent-teacher conference of Omega's school he helps another parent with a technology problem. He's like: "I tried to get rid of that problem for hours and you did it within five minutes. You gotta be a master software engineer." and Echo's like "I get payed to get yelled at as a telemarketer". Turns out the guy is an HR associate at an IT company and gets Echo a proper job.
#star wars#clone wars#bad batch modern au#the bad batch#bad batch#modern au#star wars modern au#bad batch echo#bad batch hunter#bad batch tech#bad batch wrecker#bad batch crosshair#roadkill collector
39 notes
·
View notes