#digital counterfeiting software
Explore tagged Tumblr posts
Text

TrackMatriX Serialization module provide ready-to-use interface mapping templates that enable data exchange between packaging lines and advanced tracking and tracing systems.
#Anti counterfeiting technology pharmaceuticals#saas solutions for brand protection#brand protection software#brand protection solutions#digital counterfeiting software
0 notes
Text
How To Create a Simple Customer Referral Program?
Counterfeit products are harmful for buyers, businesses and economies worldwide. To combat this issue barcode scanners are emerging as a powerful tool in the fight against counterfeit goods.

#dynamic qr code#qr code manufacturer#brand protection#anti-counterfeit solutions#customer loyalty programs#qr code provider#qr code provider in india#customized solution#label provider in india#anti-counterfeit solution company#anti-counterfeit technologies#anti-counterfeiting solutions in india#industrial tags manufacturer#e-warranty#data analysis#cash transfer#customer loyalty service#track & trace services#raffle#run survey#build loyalty#digital marketing#software development#digital marketing services#qr code maker#qr code generator#qr code generator with logo#qr code generator online#custom qr code generator#custom packaging for small business
0 notes
Text
Family/Laugh: May 12 & 13 Prompts from @calaisreno
The exterior nowheres that Sherlock inhabits can be charted by his footfalls as he wends his way through the precincts of temporary cities. The silent drift of assimilating interior nowheres, however, seems to leave no traces, even as he feels unseen changes taking hold. His suspension in the January North of a darkness that persists until late morning, and then quickly returns in the afternoon, intensifies his perception that he lives in a shadow-world, a lone dark figure extracted from the frozen rain that curtains his days.
The patterns he seeks to capture as he hunts amidst the ones and zeros of cyberspace are likewise intangible – extended solitary vigils as his fingers command the keyboard to winnow through the tangle of codes – as well as tangible, of meetings with the technological mix of people here at Tallinn’s crossroads: software developers seeking the leading edge at corporate labs, security experts at NATO’s Cyber Defence Centre of Excellence, the underground hackers who traverse the landscape of the digital realm’s hollow earth. Both the intangible and the tangible are intense efforts to spy glimpses of Moriarty’s covert presence in the spaces between the ones and zeros, summoning up the networks and nodes of the intersecting spheres of finance, and energy, and communications, as made manifest in trafficking, and counterfeiting, and hijacking, across the physical and human worlds.
He’s accumulated an abundance of leads, some he’s near-certain he understands, and others he’s yet to decipher – but it’s enough to reveal to him his next move on the chessboard: St. Petersburg. He’ll take the train from Tallinn, without needing to step out for border control, which is handled en route. He’ll be leaving Estonia under a new identity; he hopes to keep Lukas Sigerson in his back pocket for later uses, but it’s time to make his presence difficult to trace: it's time to step away from Mycroft’s grid. He’s left seemingly inadvertent clues to allow Mycrofts’s people to (think that they’re) following him, along a pathway that connects the nefarious doings of Mexican cartels involved in establishing meth labs in Nigeria for the Asian market. Their pursuit of him will be turned to good account in dismantling that nexus, even when they realize he is elsewhere.
St. Petersburg is a hive of hacking activity, the physical site of the infamous Russian Business Network, which catered to the needs of cyber criminals. It’s not surprising that it is the city where Vladimir Putin lived, received his education, and joined the KGB, as an agent in its foreign intelligence wing, before tunneling his way to Moscow. Sherlock doesn’t believe that there are many degrees of separation between Moriarty and the dark internet of Putin’s hellscape.
He arrives at the end of Tallinn’s usefulness on a Friday evening. As he packs up his kit in the office space he’s made homebase through a courtesy loan in deference to his Norwegian technology credentials, some of the younger workers have swept him up into their murmurating flock as they celebrate the coming weekend in search of alcohol, bar food, and music. In London, Sherlock would have begged off such a request, were anyone intrepid enough to suggest it, and he would have been unperturbed at whatever anyone might think. But he’s not Sherlock, he’s Lukas, at least for a short while longer, and although his persona is reserved, businesslike and uninclined to make small talk, Lukas possesses an average quantity of affability; and remaining unobtrusive is best accomplished by being amidst the motions of others, rather than making himself conspicuous by setting himself off from the norms of sociality.
He did not, however, anticipate the karaoke session, which is putting a severe strain on the bonhomie he is channeling to Lukas, as it’s clear that he’s going to need to accede to accepting a turn in the spotlight, lest he put a damper on the good spirits of his companions. He nevertheless protests with a smile, holding out his hands, but any input he might have been able to exert on the decision-making disappears, when two of his impromptu friends conspire to tug him toward the microphone, explaining that all three of them will venture forth together, with a song they insist is dead simple to sing, and that the well-lubricated crowd will be delighted to join in with them in belting out the familiar refrain. Which is how he finds himself being carried along within a punchy, melodic stream that turns out to be excruciating emotionally, as the verses unfurl. He listlessly despairs, marooned, a hollowed-out laugh echoing inside his head in response.
. . . When I'm lonely, well, I know I'm gonna be I'm gonna be the man who's lonely without you And when I'm dreamin', well, I know I'm gonna dream I'm gonna dream about the time when I'm with you. When I go out (when I go out), well, I know I'm gonna be I'm gonna be the man who goes along with you And when I come home (when I come home), I know I'm gonna be I'm gonna be the man who comes back home with you I'm gonna be the man who's comin' home with you . . .
He’s exasperated at the universe conspiring to keep him unsettled, to deny him the solace of alone protecting him. He fears that he is fated to have any social contact whatsoever somehow conjure home and reminders of John. The song ends to raucous cheers, and the enthusiasm surges on, and he’s being importuned to name a new song of his own choice before being allowed to return to the table. He looks at the smiling faces helplessly, immobilized by the churning cacophony playing hide-and-seek inside his guts, incapable of conjuring up the simplest of answers. Undeterred, they jolly him along, prompting him to think of a film he’s recently seen, or club he’s been to, or a favorite television show. At the latter suggestion, his mind does slightly slip free, and there is John again, teasing Sherlock into watching another of his favorite shows, Sherlock pretending to be annoyed at being consigned to such a fate. He turns to the young people, and raises his voice to speak into the nearest person’s ear to be heard over the noisy crowd, and says with a question in his voice, Peaky Blinders? He seems to have pleased them, as they fiddle around to pull the selection, bouncing in high spirits and punching their fists into the air, as the music starts, a bell ringing out, and the slithering deep tones speaking of the edge of town, of secrets in the border fires, of a gathering storm -- and a tall handsome man, in a dusty black coat, with a red right hand.
As Sherlock listens to the song unspool, his mind wanders back to the show's themes, reminding him of a line of thought he’d been considering the last few days – that to focus singularly on Moriarty and faceless confederates is not quite the right way to conceptualize the dead man's web: that there must have also been family members in leading positions, positions of trust. One of the deep divides between himself and Mycroft originated in Sherlock’s refusal in uni to agree to work for SIS. Mycroft knew that he would never be able to trust completely any of the professionals who worked for him – after all they are spies working for money. To be sure, he wanted Sherlock to sign on to be able to appropriate his intelligence, but even more compelling was the fact that never having to question the loyalty of a brother would have made him an asset par excellence. Mycroft considers getting what he wants to be an inviolable law of the universe, and Sherlock doesn't think his brother will ever be able to truly forgive him for the rejection . . . especially given Sherlock's devotion to the inferior endeavors of dedicating himself to a life of metropolitan crime-solving. Family; family is what matters. A Moriarty is gone; but there are other Moriarties yet to be unearthed. ........................................................ @calaisreno @totallysilvergirl @friday411 @peanitbear @original-welovethebeekeeper @helloliriels @a-victorian-girl @keirgreeneyes @starrla89 @naefelldaurk
@topsyturvy-turtely @lisbeth-kk @raina-at @jobooksncoffee @meetinginsamarra @solarmama-plantsareneat @bluebellofbakerstreet @dragonnan @safedistancefrombeingsmart @jolieblack
@msladysmith @ninasnakie @riversong912 @dapetty
.............................................................................
36 notes
·
View notes
Text
North Korean hackers have stolen the equivalent of billions of dollars in recent years and the nation is seeking to amass even greater wealth through illicit means, experts told DW.
Hackers belonging to the Lazarus Group — a notorious North Korean crypto theft ring — stole a record $1.5 billion (some €1.37 billion) in digital tokens from Dubai-based cryptocurrency exchange ByBit in late February. The company said the hackers had accessed its digital wallet for Ethereum, the second-largest electronic currency after Bitcoin.
Binance News, a new platform operated by cryptocurrency exchange firm Binance, reported last month that North Korea now has some 13,562 Bitcoins, the equivalent of $1.14 billion. Bitcoin is the world's oldest and best known cryptocurrency, often compared with gold due to its alleged resistance to inflation. Only the US and Great Britain have greater reserves of the currency, Binance News said, citing crypto data provider Arkham Intelligence.
"Let's not mince words — [North Korea] achieved this through theft," Aditya Das, an analyst at cryptocurrency research firm Brave New Coin in Auckland, New Zealand, told DW.
"Global policing agencies like the FBI have publicly warned that North Korean state-sponsored hackers are behind numerous attacks on cryptocurrency platforms," he added.
Hackers use social engineering against crypto firms
Despite those warnings, however, crypto firms are still being robbed and North Korean hackers are becoming increasingly sophisticated, the analyst said.
"North Korea employs a wide range of cyberattack techniques, but they've become especially known for their skill in social engineering," said Das.
"Many of their operations involve infiltrating employee hardware, then using that access to breach internal systems or lay traps from the inside."
The hacker's primary targets are crypto startups, exchanges and decentralized finance (DeFi) platforms due to their "often under-developed security protocols," he said.
Recovery of funds 'extremely rare'
Elite North Korean hackers tend to take their time when infiltrating a legitimate global organization, often by impersonating venture capitalists, recruiters or remote IT workers to build up trust and breach firms' defenses.
"One group, Sapphire Sleet, lures victims into downloading malware disguised as job applications, meeting tools or diagnostic software — essentially turning victims into their own attack vectors," Das said.
Once crypto has been stolen, Das says recovery is "extremely rare." Cryptocurrency systems are designed to make transactions irreversible and striking back against North Korean operatives "is not a viable option because these are nation-state actors with top-tier cyber defenses."
Kim Jong Un's regime 'saved' by cryptocurrency theft
Park Jung-won, a professor of law at Dankook University, said North Korea previously relied on risky transactions — such as smuggling narcotics and counterfeit goods or supplying military instructors to African nations — to earn illicit funds.
The legal expert says the advent of cryptocurrency "has been a huge opportunity" for dictator Kim Jong Un.
"It is probably fair to say that given the way the world was cracking down on Pyongyang's smuggling efforts, crypto has saved the regime," Park told DW. "Without it, they would have been completely without funds. They know that and they have invested heavily in training the best hackers and getting them up to a very high level of skill."
"The money that they are stealing is going straight to the government and the assumption is that it is being spent on weapons and greater military technology as well as the Kim family," according to Park.
North Korea immune to international pressure
Park does not believe that outside pressure would force North Korea to end hacking attacks.
"For Kim, the survival of his dynasty is the most important priority," the law professor said.
"They have become accustomed to this source of revenue, even if it is illegal, and they will not change," he added. "There is no reason for them to suddenly start abiding by international law and there is no way to apply more pressure."
Das agrees there are few tools available to influence North Korea. He says companies need to do everything in their power to avoid becoming the next victim.
"Best practices like secure-by-design smart contracts, constant internal verification and social engineering awareness are essential if the industry wants to stay ahead," he said.
Crypto firms need universal security standards
There's growing momentum for sector-wide information sharing which would help crypto firms detect North Korean tactics and avert attacks, but Das warns that crypto remains "fragmented" because there is no universal security standard. Also, North Korean hackers are good at turning security tools against their users, according to the analyst.
"In the Bybit case, the attackers exploited Safe, a multi-signature wallet system meant to enhance security. Ironically, this added security layer became the very exploit they used," he said.
And in practice, Das added, "some firms still treat security as an afterthought."
"From my experience, teams often prioritize shipping fast over building secure systems and until that changes, the space will remain vulnerable," Das said.
#nunyas news#have to wonder what would happen#if all of a sudden a bunch of countries#started selling their crypto off#would the market tank or no
7 notes
·
View notes
Text
A Comprehensive Guide to Blockchain-as-a-Service (BaaS) for Businesses
In today's digital landscape, a blockchain app development company plays a crucial role in transforming industries with decentralisation, immutability, and transparency. However, building and managing a private blockchain network can be complex and costly, which deters many businesses. Blockchain-as-a-Service (BaaS) simplifies this by allowing businesses to leverage blockchain without the challenges of infrastructure development.
This comprehensive blog covers the hurdles businesses face when adopting blockchain, how BaaS can bridge these gaps, and why it is a game-changer for various sectors.
I. Challenges for Businesses in Blockchain Adoption
Despite the undeniable potential of blockchain technology, businesses face several significant challenges when contemplating its adoption:
Limited Internal Expertise: Developing and maintaining a private blockchain network requires a skilled team with deep blockchain knowledge, which is often lacking in many organisations.
High Cost: The infrastructure investment and ongoing maintenance fees associated with blockchain can strain budgets, especially for small and medium-sized businesses (SMBs).
Integration Complexities: Integrating a blockchain network with existing enterprise systems can be challenging, requiring seamless data flow and compatibility between the blockchain system and legacy infrastructure.
II. Understanding BaaS and Its Operational Fundamentals
Blockchain-as-a-Service (BaaS) simplifies the development and deployment of blockchain applications by providing a cloud-based platform managed by third-party providers. The BaaS market, valued at $1.5 billion in 2024, is projected to grow to $3.37 billion by 2029, reflecting a robust 17.5% CAGR.
Key Components of BaaS
Cloud-Based Infrastructure: Ready-to-use blockchain infrastructure hosted in the cloud, eliminating the need for businesses to set up and maintain their networks.
Development Tools and APIs: Access to a suite of tools and APIs to create and deploy blockchain applications quickly.
Platform Support: Compatibility with various blockchain protocols such as Ethereum, Hyperledger Fabric, and Corda, offering flexibility to businesses.
Managed Service Model: Providers handle tasks like network maintenance, security updates, and scalability.
Pay-as-you-go Pricing Model: Reduces upfront investment and operational costs associated with blockchain software development.
III. Business Benefits of Blockchain as a Service
Adopting BaaS offers numerous advantages, including:
Enhanced Scalability: Businesses can easily scale their blockchain network as their needs grow.
Increased Efficiency: Eliminates intermediaries and streamlines transactions, improving productivity.
Enhanced Transparency: Tamper-proof records of transactions foster trust and improve auditability.
Reduced Costs: The pay-as-you-go model eliminates large upfront investments.
Improved Security: Built on secure cloud infrastructure with robust encryption protocols.
Enhanced Customer Engagement: Facilitates secure and transparent interactions with customers, building trust and loyalty.
IV. Industry-wise Key Use Cases of Blockchain as a Service
BaaS is transforming business operations across various industries:
Finance: Streamlines trade finance, secures cross-border payments, and enhances KYC and AML compliance.
Supply Chain Management: Improves transparency and traceability of goods, automates logistics processes, and reduces counterfeiting risks.
Healthcare: Facilitates secure sharing of patient data and tracks the provenance of pharmaceuticals.
Government: Enhances transparency with secure citizen identity management and verifiable voting systems.
V. Region-wise Adoption of BaaS
The BaaS market is experiencing rapid growth worldwide:
North America: Leading with over 35% of global revenues, driven by early adoption.
Europe: Countries like Germany, the UK, and France are at the forefront.
Asia-Pacific: China, India, Japan, and South Korea are key contributors.
Rest of the World: Growing adoption in South & Central America, the Middle East, and Africa.
VI. Why Choose a Prominent BaaS Provider?
Opting for a blockchain app development company that offers BaaS can significantly impact the success of your blockchain initiatives:
Specialised Expertise: Providers possess in-depth knowledge and experience in blockchain technology.
Cost Efficiency: Eliminates the need for in-house infrastructure investment and maintenance.
Time Savings: Accelerates the development process and reduces time-to-market.
Scalability and Flexibility: Offers scalable solutions that can adapt to business growth.
Risk Mitigation: Providers handle security, maintenance, and updates.
Conclusion
By adopting Blockchain-as-a-Service (BaaS), businesses can simplify blockchain integration and focus on innovation without the complexities of managing infrastructure. Systango, a leading blockchain app development company, offers tailored BaaS solutions that help businesses leverage blockchain technology for enhanced efficiency, scalability, and security. As one of the top , Systango also excels in integrating AI solutions to drive business growth and efficiency.
Original Source - https://systango.medium.com/a-comprehensive-guide-to-blockchain-as-a-service-baas-for-businesses-5c621cf0fd2f
2 notes
·
View notes
Text
Web Search Engine) Links
Hidden Wiki Links – Now you are here then you already know about deep web links / The Hidden Wiki / Dark web links. But before sharing large amount of .onion directory I want to share some very good deep web links which always help you, because all these are deep web search engine links by the help of these search engine you can find any latest working deep web marketplace, hidden wiki or deep web sites list.
Dark Web Marketplace
Darknet markets is a solution for all type products because these type marketplace gives security to both party means seller or buyer, here you can use escrow service which make your payment mode more secure and clear. These type darknet markets places having some big number of listed categories and each category having more than thousands of unique products.
So simple, Today If you are planning to buy anything on deep web/the hidden wiki then these markets can provide you all type products buying or selling opportunity and here you also can get more than one alternatives into single category.
Mostly these deep web links having Drugs, Weapon, Digital products, Fraud, Services, Guide and Tutorials categories.
Bellow I am giving you some very popular deep web Links (dark web links), which you can try but before using these hidden wiki links, you need to register yourself on these darknet markets deep web link.
Note: If you are seller then these dark web marketplace links will proving milestone for you. where you can sell your products. and you can easily get targeted users or can achieve your goals within very short time span.
Note: I am not recommending you to visit these deep web sites (dark web links), I only added these deep web sites/onion sites here for education purpose or freedom information. If you visit these deep web sites then this is total on your risk, but I am recommending you here before visiting these deep web sites make sure focus on your privacy Security.
Recommended: For better security use NordVPN Onion Over Server + Tor Browser. ( Always run both software before access hidden Internet).
http://pwoah7foa6au2pul.onion – Marketplace – Alphabay is most popular and trusted deep web market. If you are truly looking something trusted on deep web then Alphabay is one of the best market, And this marketplace also has all major categories items like as fraud, drugs, chemicals, Guide & Tutorials, Digital Products, Services, and much more. According to current status, This marketplace has more than 3 Lakh listed items, and Just now support two type crypto currency which is Monero and Bitcoins.
Note: Before Buy any product here always check seller profile and available feedback and reviews.
http://lchudifyeqm4ldjj.onion/ – Marketplace – Dream Market : Second largest and most trusted dark web market, also you can say alternative of alphaby market, This marketplace place have drugs and digital products, and both these category have more than 75000+ listed items which is huge. If you are looking another great platform then dream market can provide you right items.
http://wallstyizjhkrvmj.onion/ – Marketplace – WallStreet Market – Another deep web markets which have more than 500+ listed items and each item are well categorized. According to category, You can get products related to drugs, counterfeits, jewelry & gold, services, Software & malware, security & hosting and much more.. and listing growing day to day. Marketplace support PGP and data encrypt by strong algorithm and also support German language. WallStreet has scam free status and multisig support.
http://udujmgcoqw6o4cp4.onion – Deep Web Market – UnderGround, one of the best and reliable deep web market with the possibility to pay in two times. Markets have more than thousands listed items and items related to Prepaid cards, PayPal account, Diploma, Passport, ID Cards, Driver License, Phone, Computer, Tablets, Game Console, Hacker, Weapons, Professional Killer, Humen Organs, Medicines and so on.
Note: This deep web links support JavaScript, If you want to access all function then you need to disable your javascript. But for security reasons, this is not good choice.
http://valhallaxmn3fydu.onion – Marketplace – Valhalla: This deep web marketplace is also very popular into deep web world and mostly people prefer this hidden wiki marketplace url for buying drugs, gadgets, hire services and lot many more things.
http://hansamkt2rr6nfg3.onion/ – Marketplace – Hansa is another famous deep web marketplace, which having more than 15K+ listed products. which is huge, and here you can buy all type products related to drugs, weapons, services, tutorials, services, electronics. It is one of most popular the dark web links.
http://zocaloczzecchoaa.onion – Marketplace – Zocalo Marketplace: Same as other marketplaces this .onion directory links also having good amount of listing product.
http://acropol4ti6ytzeh.onion – Marketplace – Acropolis forum also a good darknet markets, and community forum for sell and buy anything which you want, and also can find your questions answer in this dark web link.
http://tochka3evlj3sxdv.onion – Marketplace – Tochka Free Market: Tochka is also good darknet market where you can find mostly all type product related to education, hacking, drugs, weapon, services and software.
http://cryptomktgxdn2zd.onion – Marketplace – Crypto Market: Are you looking some other deep web links marketplace alternative then check out Crypto Market, Here you can participate in crypto market forum.
Warning: Before browsing the Deep web links/the dark web links, always run your NordVPN Onion Over VPN Server with Tor Browser. Since Tor Browser doesn’t provide your complete anonymity and privacy. You are completely safe only if you use NordVPN software.
http://kbhpodhnfxl3clb4.onion/ – not Evil (Tor Search Engine) for finding list of deep web sites, and one can easily find relevant information about the deep web/the hidden wiki which s/he want to get..
http://hss3uro2hsxfogfq.onion/ – not Evil search engine direct visit deep web links.
Note: Now Tor search engine has been moved on new name, now this popular search engine also known as not Evil, in the current date not Evil having more than 12477146 .onion links database.
Grams Search Engine and Associated Deep Web Services Links:
Grams is newly launched deep web search engine, this search engine getting good amount of popularity with in very short time and these days thousands of people use Grams for deep web access. You can access Grams by using below dark web link.
http://grams7enufi7jmdl.onion/ – Grams Search Darknet Markets and more.
Grams is not a single platform, but it’s like a Google, After couple month after grams launching date, Grams introduced some other product like Helix, Helix Light, Infodesk or Flow.
All three having unique features. If you want to access these three Grams sub product, then you can access by the help of Grams deep web link, or you can also go by the help of bellow given direct dark web links.
Note: Helix takes charge 2.5% every transaction.
Helix Tor Directory Link: http://grams7enufi7jmdl.onion/helix/light
InfoDesk: If you want to find any Vender, products or any specific marketplace tor link then this place can help you because here you can find some great marketplace which is trusted, and mostly people use in daily life.You can access InfoDesk using below deep web link.
InfoDesk Hidden Wiki Link: http://grams7enufi7jmdl.onion/infodesk
Flow: Now time for Flow, this is another popular deep web product which is also introduced by Grams, Hope you like Flow features because some person like this platform for Flow redirect feature.
According to this, if you want to access any darknet markets and you didn’t remember tor directory link then you can access these type hidden wiki url or deep web links easily.. GramsFlow makes this type complicated process more easy.
Now you only need to remember your marketplace name like Agora, Wiki, OutLaw, nuke or any other and you can access by help of Flow.
For Example: if you want to access the hidden wiki then you need to type in your Tor Browser gramsflow.com/wiki, then holla your link redirect on actual tor hidden directory.
For using awesome feature of Flow, visit below give deep web link.
Flow Tor Hidden Directory Link: http://grams7enufi7jmdl.onion/infodesk
http://skunkrdunsylcfqd.onion/sites.html – The Intel Wiki – This .onion site has the good number of trusted deep web links, which every day visited by most of the deep web users. But sometimes when I try to access this deep web link and I saw this dark web link is down. One more thing the Intel wiki also a forum which having great number of threads, which having useful information about the deep web and trusted deep web links/dark web links.
http://auutwvpt25zfyncd.onion/ – Tor Links Directory – OnionDir having more than 1200+ listed dark web sites, one better thing is here you can see on top how many dark net sites are live and how many deep web sites not and All .onions links are well categorized according to categories. For Example: If you are looking hacking or drugs related marketplace deep web links then you need to click on required category and visit any deep web sites which you like.
Forums & Community Deep Web Links(For Questions and Answers Conversation)
If you are eager to learn the darknet hidden wiki forum, also want to deep discuss on this sensitive topic and looking best deep web forums and the hidden wiki links and if you also looking how to access the deep web latest news and updates.
Deepwebsiteslinks is a best source where you can find all most popular deep web links, the hidden wiki news and darknet markets updates day to day and people visit here every day and participate into available threads.
Here I am giving you some popular deep web forums and darknet community links/deep web links, which are sharing the deep web/the hidden wiki related news and current updates everyday.
Privacy Tips: Always use NordVPN Onion Over Server with Tor browser while you accessing deep web sites. if you are thinking you are using TOR and you are safe. Let me clear for your privacy security. TOR doesn’t provide you full security. To access deep web with best anonymity and privacy, NordVPN and TOR both are must used software.
http://rrcc5xgpiuf3xe6p.onion/ – Forum/Community – IntelExchange is my favorite the dark web community because here you can find information thread and also can ask your question, I like this because here you can find mostly pre-discussed thread which having lot of meaningful information like best dark web search engines, dark web browser, most trusted the hidden wiki url.
http://parazite.nn.fi/roguesci/ – Forum – The Explosive and Weapon Forum, This hidden wiki link has some very good weapons and Explosive-related Documents and treads.
http://zw3crggtadila2sg.onion/imageboard/ – Forum – TorChan is darknet forum where you ask and participates into running chat thread, but If you are first time visitors then you don’t know how to visit this website then simple type given URL and after press enter you will get one popup on screen then you need to put given Username and Password into both field, ByDefault Username or Password is torchan2, torchan2. this is most popular the hidden wiki forum, where every day more than thousands or visitors visit and share something very interesting.
http://kpdqsslspgfwfjpw.onion/ – Forum/Community – A Chan, I think this deep web links having Russian language stuff, I can’t tell you about properly this site, and what type stuff this deep web sites have.
http://rhe4faeuhjs4ldc5.onion/ – Forum/Community – Do you have any query related to white hate hacking or black hat techniques, and you want to know some secret hacking tips then this hidden wiki community will proving helpful stuff and gernals. having more than 20+ active threads.
http://turkiyex6fkt46ra.onion/forum/ – Forum/Community/Non-English – Are you from Turkey, and looking your region related deep web forum then check out this hidden wiki forum link.
http://anonywebix6vi6gz.onion/ – Forum/Community – This is newly launched dark net forum. This hidden wiki link also will proving helpful for you, if you want to discuss about the deepweb, darknet markets or any others.
http://arcadian4nxs3pjr.onion/ – Forum/Community – ArcadiaNode is a dark net forum, Note: this deep web sites is not in the English language, that’s why I don’t have more idea about this forum.
http://5dhf54nxiuuv6jvs.onion/ – Forum/Community – AXAHis Community: This is another deepweb (hidden wiki) community where you can share your questions and knowledge, also can interact with related people.
Note: For access first time need registration.
http://p22i3mcdceionj36.onion/index.php – Forum/Community – XenForo: This deep web marketplace is a forum, but here you can buy Pfizer and GG249 Xanax products.
http://anonymzn3twqpxq5.onion/ – Forum/Community – Do you love DBA task and want to discuss on DBA related topics then check out this forum, hope this will proving helpful for you.
http://z2hjm7uhwisw5jm5.onion/ – Forum/Community – WallStreet: If you having any query about Tor or Looking some hidden web related answer then you can try on this deep web link.
http://support26v5pvkg6.onion/ – Forum/Community – Pedo Support Community: This Deep web forum is having more than 10K+ threads, like links, personal support, pedo literature, child love support, etc.
http://suprbayoubiexnmp.onion/ – Forum/Community – SuperBay: This community is having very good amount of thread and everyday lot’s of visitors use these threads, If you have some problem, then you can find relevant thread, and can resolve your problem.
https://blue.thevendingmachine.pw/index.php – Community/Forum – TheVendingMachine: This is very popular deep web community, every day more than 1000+ visitors visit this onion site, and share information. Here most popular thread is Torrent, Movies, General Discussion, TV shows, documentaries, etc.
http://npdaaf3s3f2xrmlo.onion/ – Tor Community – TwitterClon is just like twitter sites here you can share everything which you want into form of tweet, hope you also enjoy this sites, but mostly time I saw this site down.
NordVPN 2
http://ji7nj2et2kyrxpsh.onion/ – Forum – Dark Web Forum: I don’t know what you can find here because this is non-english forum but as per my guess, hope you can discuss about dark web and also can participate into active threads.
http://krainkasnuawwxmu.onion/ – Forum – Dark Web Community: This is the next Russian forum, where you can discuss about dark web community. If you have any question and want to know the right answers, then you can sign up on this forum and can find some easy solutions.
http://fbcy5ylyoeqzqzcr.onion/ – Forum – Moneybook: Another dark web forum where you can discuss about all popular topics related to dark web like as onion links, dark web markets review, PayPal accounts, music movie sites and much more, hope here you can find some good thread for you.
http://realpissxny3hgyl.onion/ – Forum/Porn – RealPiss Voyeur Community real uncensored female pee spycams: community for real girl piss videos and pictures, If you interested into such type content then you can try to visit realpiss site.
http://zzq7gpluliw6iq7l.onion/threadlist.php? – Forum – The Green Machine: Another deep web forum which provides discussion threads, do you have any questions and want to know the right answers then The green machine dark web links can provide you right information. But If you want to participate into available threads then you need to registered yourself on this deep web forum.
http://rutorzzmfflzllk5.onion/ – Forum/Russian – RuTor: Are you looking Russian forum, If yes then RuTor forum can provides you some great questions answer, but this forum not have more active thread, when I visited this deep web sites then I saw, website have only limited thread and also not have users engagement.
http://bm26rwk32m7u7rec.onion/ – Forum – The Majestic Garden: This is another deep web forum, which provides free forum SMF software solution, If you have any questions about this software then you can visit this deep web sites.
http://vrimutd6so6a565x.onion/ – Forum/Community – The Dark Lair: Forum for anonymous messaging, like as Twitter. Here you can share your status globally; Everyone can saw your status on this website. If they visit dark Lier, but you can’t post status on this site. Because you are not the registered member of Dark Lier, that’s the main reason. First your need to register on this website. Site also offers thread service and some good deep web links also.
http://answerstedhctbek.onion/ – Forum/Community – Hidden Answers: I think you already know about the yahoo questions and answers, This site offer same service just like yahoo questions and answers, If you have any questions and want to get your questions answers then you can try this deep web links.
http://saefjmgij57x5gky.onion/ – Forum/Community – TorStack – Q & A Community – Same Yahoo Questions and answer deep web sites, here you also can find right answers for your questions anonymously.
http://dnmavengeradt4vo.onion/ – Forum/Community – DNM Avengers: Another deep web forum site which provides communicating portal for deep web users anonymously. forum already have more than 100+ active threads. If you have any questions and want to know right answer anonymously. You can participate on available relevant thread. Also, you can share your skills in these running threads.
http://twittorxsun563wg.onion/ – Community/Social – Twitter Clone – This is microblogging site on the deep web, here you can share anything with all site readers anonymously. For status publishing you don’t need to signup here.
http://i2vzg7f44bj4l3r7.onion/ – Community – The Alliance – Another deep web social community sites, where users can share his though with all alliance community member or personally with your friends. One more thing, site also offers bookmarks service, by which you can tag any links on the Bookmarks category. which every site readers can read and visit anonymously.
http://www.smplace.com/forum/ – Forum/Community – S&M Place BDSM forum – Great Adult porn community for girls and boys, have all type threads where you can share adult porn videos and pictures, and also you can upload your videos and pictures collections. Forum have more than 70000+ active members.
http://rekt5jo5nuuadbie.onion/hiddenchan/ – Forum/Community – HideenChan – If you don’t know about the hidden chan. HiddenChan is just like as another community forum, here you can participate into current active threads. But hiddenchan is very engaging community here you can see every illegal activity related thread and also you can watch available videos and pictures which is uploaded by various current members.
http://start.jungswtfwgjwile2.onion/ – Forum/Community – Guys.WTF is primarily a community for people who love and love guys and / or feel sexually attracted by them. However, every interested person is expressly welcome. Here you want to help and support each other.
http://bfvfq7hjcdoinzo4.onion/ – Forum/Community – Darknet Erotic Forum – This deep web forum offer threads related to hot, geil, horny, porn, pervers and etc. If you want to discuss about these topics then you can participate on available threads. But without registration you can’t participate in this community.
http://rfwtogljhrrzxyrl.onion/ – Forum/Community – Lolita City – Another deep web forum, which offers hq legal stuff. Today when I visited this site, here only I found 2 threads. Hope here you can get your required information.
Email/Messaging/Chat related Deep Web Links
Warning: Always use NordVPN Tor Over Server + Tor Browser for complete security. Your privacy is not safe if you are accessing deep web links without VPN.
Same ad normal traditional in
#dark web#ethicalhacking#scammer#coding#contact a hacker#scammers#social media hackers#ethical hacker#deep web#hacker
4 notes
·
View notes
Text
We get it – the digital landscape can be a maze of uncertainty when it comes to finding genuine licenses for Windows 11 Pro. But fear not, we're here to shed some light on the matter.With our digital software keys, authenticity is our promise. We guarantee genuine licenses that unlock the full potential of Windows 11 Pro, without the worry of getting duped by counterfeit keys.

1 note
·
View note
Text
Unboxing the Unknown: Delving into the Dark Web Mystery Box
In the darker recesses of the internet, a subculture of intrigue and mystery grows — the dark web. Hidden under the surface of the World Wide Web, the dark web is famed for its unlawful activities, anonymity, and the selling of intriguing "mystery boxes." These scary gifts have caught the interest of many, offering a voyage into the unknown. In this essay, we will go on a virtual excursion into the dark web, studying the notion of the "dark web mystery box" and the secrets they hold.
The Allure of the Dark Web Mystery Box
The appeal of the dark web mystery box is a phenomenon that captures the excitement of the unknown in the digital era. In a society where quick pleasure and information accessibility are the norm, the notion of getting a mystery gift with unannounced contents has a magnetic attraction. It sparks interest and gives an experience that is both exciting and surprising. At its foundation, the fascination of the dark web mystery box may be due to various things. First and foremost is the element of surprise. In a time when we can trace our Amazon orders down to the minute, the prospect of getting something utterly unexpected is alluring. Each box is a Pandora's Box of possibilities, holding objects that vary from the unusual and weird to the possibly expensive and uncommon. The prospect of unpacking such a gift is an amazing experience in itself. Furthermore, the dark web mystery box feeds into our interest in the obscure and the intriguing. The descriptions offered by vendors are typically obscure, providing an air of mystery to the whole transaction. Buyers are left to decode clues and suggestions about what may be within, creating the feeling of adventure.
However, this attraction comes with a huge drawback. The dark web, where these mysterious boxes are commonly located, is a digital underworld connected with unlawful activity and possible risks. Navigating this secret area needs specialist software like Tor and a willingness to embrace the hazards that come with it. Buyers of dark web mystery boxes typically join a world where anonymity prevails, and confidence in the seller is vital, making the encounter all the more thrilling and risky.
The ethical and legal consequences of dealing with dark web mystery boxes are also a part of the allure's complicated tapestry. Some boxes may include things that skirt the bounds of legality, pushing customers into a moral gray area. Questions regarding the repercussions of participation in such a subculture continue, raising worries about the possibility of accidentally purchasing unlawful or unsettling objects. In conclusion, the attractiveness of the dark web mystery box is a tribute to the everlasting fascination of the unknown. It appeals to our inherent curiosity, our yearning for surprise and adventure, and our fascination with the enigmatic. However, it is a place filled with perils and ethical difficulties, reminding us that, in the era of the internet, even the attraction to the unknown comes with its own set of repercussions. It is an intriguing conundrum that continues to enchant and mystify those eager to investigate its depths.
The Dark Web's Underbelly
The dark web's underbelly is a digital domain wrapped in secret and infamy, a hidden area of the internet where anonymity reigns supreme. Accessible only via specialist software like Tor, it helps users can disguise their identities while traversing a complex network of encrypted websites and forums. While the dark web itself is not inherently evil, it has earned a reputation for supporting a myriad of criminal activities that flourish in its shadows. One of the most troubling features of the dark web's underbelly is its function as a marketplace for illicit products and services. Here, cybercriminals perform unlawful operations with relative impunity, trafficking in anything from narcotics and stolen data to counterfeit currencies and bogus passports. The anonymity given by the dark web protects these actors from the prying eyes of law enforcement, making it a refuge for illicit organizations to grow. Mystery box services on dark web sites involve purchasing packages with unknown contents, creating an element of surprise, but can often lead to illegal or dangerous items.
However, the hazards connected with digging into this hidden side of the internet cannot be understated. Users who wander onto the dark web subject themselves to a range of possible perils. Malicious hackers and cybercriminals exist, attacking unwary visitors with fraud, phishing attempts, and malware. Moreover, the dark web is not just a center for illegal transactions but also a collection of unsettling and criminal information, ranging from explicit photos to forums advocating hate speech and extremism. Law enforcement organizations worldwide actively monitor the dark web, attempting to combat its unlawful activities and catch individuals who operate inside its murky depths. Nonetheless, the ever-evolving nature of the dark web makes it a continual problem for authorities to successfully resist.
What's Inside a Dark Web Mystery Box?
The contents of a dark web mystery box are as cryptic as the unseen regions of the internet from whence they emerge. These boxes are frequently offered with cryptic descriptions, delivering little to no information about what customers will get. The fascination comes in the expectation of finding the unexpected since they offer a varied selection of products that may span from the quirky to the possibly priceless. Some mystery boxes may include uncommon artifacts, rare or old objects, esoteric devices, or even eccentric curiosities that defy classification. On the darker side of the spectrum, tales continue about boxes holding illegal or unpleasant things, giving an element of risk and unpredictability to the experience. The mystery around the contents of these boxes keeps customers engaged, as they embark on a virtual voyage into the unknown, typically with a combination of exhilaration and anxiety. However, it is vital to understand that the absence of transparency in dark web mystery box transactions presents ethical and legal considerations, as the line between curiosity and possible repercussions becomes more blurred.
Legality and Ethics
Legality and ethics surrounding dark web mystery boxes create a complex terrain that deserves careful scrutiny. The sheer nature of these enigmatic goods, typically acquired without any specific understanding of their contents, poses substantial ethical considerations. Buyers may unknowingly assist illicit operations, such as the trafficking of stolen goods, drugs, or other prohibited products when they participate in these transactions. The vendors themselves may use the appeal of the unknown, exploiting the curiosity of consumers for personal benefit, which may be considered an ethically problematic behavior. Moreover, the ethical problem extends to the possible damage that may arise from opening a dark web mystery box. While some parcels may contain innocuous curiosities or novelties, there have been occasions when customers found upsetting or even horrific contents. The psychological toll of such revelations underlines the ethical problems surrounding these transactions, as people may inadvertently expose themselves to traumatic situations. On the legal front, dark web mystery boxes operate in a legal murky area. The sale and purchase of these items are generally performed anonymously, making it hard for law enforcement organizations to monitor or control them efficiently. Buyers and sellers alike may be straying perilously close to unlawful activity without clear legal implications. In conclusion, the appeal of dark web mystery boxes is certainly intriguing, fueled by the human obsession with the unknown and the unexpected. However, the ethical and legal repercussions of engaging in this subculture are enormous. As we traverse the digital era, it is vital to exhibit prudence and ethical judgment, knowing that curiosity may lead folks into ethically problematic areas, and the repercussions of engaging with the dark web's cryptic offers are far-reaching.
Conclusion
"Unboxing the Unknown: Delving into the Dark Web Mystery Box" gives a glance into the hidden realm of the dark web, where mystery and intrigue combine with ethical and legal problems. While these intriguing boxes continue to intrigue the inquisitive, they also serve as a sharp warning of the dangers hiding under the surface of the internet. As with any trip into the unknown, step cautiously, and remember that curiosity comes with its own set of repercussions.
2 notes
·
View notes
Text
Why Need Build Customer Loyalty? A Comprehensive Guide
VCQRU is a leading anti-counterfeiting solutions company in India, offering one-stop solutions for anti-counterfeiting, custom QR code, smart packaging, labels stickers, and e-warranty solutions with dynamic QR code.
Read more:
#dynamic qr code#qr code manufacturer#brand protection#anti-counterfeit solutions#customer loyalty programs#qr code provider#qr code provider in india#customized solution#label provider in india#anti-counterfeit solution company#anti-counterfeit technologies#anti-counterfeiting solutions in india#industrial tags manufacturer#e-warranty#data analysis#cash transfer#customer loyalty service#track & trace services#raffle#run survey#build loyalty#digital marketing#software development#digital marketing services#qr code maker#qr code generator#qr code generator with logo#qr code generator online#custom qr code generator#custom packaging for small business
0 notes
Text
Top 7 Ways Blockchain Technology is Disrupting Traditional Enterprise Models

In an era where trust, security, and transparency are more vital than ever, blockchain technology has emerged as a transformative force across industries. It’s not just about cryptocurrencies anymore—blockchain is reshaping the way businesses operate at a fundamental level. From redefining data integrity to creating decentralized ecosystems, blockchain in the enterprise is revolutionizing old-school models. Here are seven ways blockchain is causing a seismic shift in traditional business operations.
1. Enhancing Transparency and Security
Let’s start with the basics: trust and transparency. Traditional enterprise systems often depend on centralized servers that are prone to breaches and manipulation. Blockchain, on the other hand, operates on a decentralized network where data is encrypted, distributed, and immutable. That means once a transaction or data entry is recorded, it cannot be changed or deleted.
For enterprises, this means sensitive data is more secure, and operations are far more transparent. Every stakeholder has access to a single, verified version of the truth. Whether it’s internal auditing, external compliance, or customer trust, blockchain lays a rock-solid foundation that traditional systems simply can’t match.
2. Streamlining Financial Transactions
Financial processes in traditional enterprises are often bogged down by bureaucracy and middlemen. Think of wire transfers, international payments, or invoice settlements—they all involve delays, third-party verifications, and hefty fees. Blockchain revolutionizes this space by allowing for real-time, peer-to-peer transactions.
Better yet, with smart contracts—self-executing agreements coded onto the blockchain—payments and approvals can happen automatically once certain conditions are met. It reduces operational friction, cuts costs, and ensures payments are accurate and timely. For companies working globally, the benefits are immediate and substantial.
3. Revolutionizing Supply Chain Management
Ever wondered where your coffee beans or smartphone parts come from? Consumers and businesses alike crave transparency in supply chains, and blockchain delivers just that. Every step of a product’s journey—from raw material sourcing to final delivery—can be recorded on a blockchain ledger.
This not only boosts visibility but also reduces fraud, spoilage, and counterfeiting. Enterprises can verify certifications, ensure ethical sourcing, and manage recalls with pinpoint accuracy. For industries like food, fashion, pharmaceuticals, and electronics, blockchain is a game-changer that enhances accountability and customer trust.
4. Reinventing Digital Identity Verification
Identity theft and data breaches have become rampant, thanks to centralized databases and outdated authentication systems. Blockchain enables self-sovereign identity—a concept where individuals control their own personal data and decide who gets access to it.
Enterprises can implement blockchain-based identity systems for employee access, vendor credentials, and customer verification. It dramatically reduces the risk of breaches and streamlines processes like KYC (Know Your Customer) and AML (Anti-Money Laundering). With enterprise blockchain technology, businesses are building more secure digital ecosystems, paving the way for safer interactions and reduced compliance headaches.
5. Enabling Decentralized Applications (DApps)
The future of business applications isn’t centralized—it’s decentralized. DApps, or decentralized applications, run on blockchain protocols without intermediaries. For businesses, this opens up new possibilities for innovation and efficiency.
From peer-to-peer lending platforms to decentralized marketplaces and asset management tools, DApps offer unique ways to engage customers and reduce operating costs. Businesses can tap into this wave by investing in blockchain software development and building apps that are more transparent, secure, and cost-effective.
6. Overhauling Governance and Compliance
Staying compliant is a complex, costly affair for most enterprises. But with blockchain, regulatory requirements become easier to manage. Since all transactions are recorded immutably and time-stamped, companies can produce transparent audit trails with ease.
This simplifies tasks like tax reporting, regulatory filings, and internal audits. Also, because blockchain data can't be altered, it offers a layer of legal protection and reliability that’s difficult to dispute. Enterprises are increasingly turning to blockchain development services to create systems that automate compliance and reduce human error.
7. Fueling Custom Innovation in Enterprise Ecosystems
Finally, one of the most underrated benefits of blockchain is its adaptability. Enterprises aren’t forced into one-size-fits-all models. Instead, they can develop customized blockchain systems tailored to their specific needs—whether it’s for internal workflow automation, secure communication, or data sharing.
Forward-thinking organizations are leveraging the use of blockchain technology to create proprietary solutions that improve customer experiences, optimize resources, and enable faster innovation. This customization potential is what’s pushing even traditional industries like law, insurance, and energy toward blockchain adoption.
Conclusion
Blockchain is more than just a tech trend—it’s a paradigm shift. Traditional enterprise models, long burdened by inefficiencies, intermediaries, and security risks, are now facing the reality of a blockchain-powered future. Whether it's improving supply chains, tightening data security, or creating new business models through DApps, blockchain in the enterprise is no longer optional—it's a strategic imperative.As the demand grows for enterprise blockchain technology, companies that act now will not only future-proof their operations but also lead their industries into the next era of digital transformation.
#technology#blockchain development#blockchain development services#blockchain business#blockchain technology
0 notes
Photo

Online luxury’s counterfeit problem is spreading. Since the dawn of e-commerce, shoppers ordering designer bags on a digital resale site like eBay have done so knowing they risked buying a fake — essentially, a trade-off for securing a lower price. But now, those knock-offs are starting to show up on firsthand marketplaces as more consumers are ordering new handbags or sneakers and going on to return a fake version. Some shoppers are starting to sound the alarm. In January, influencer Tiffany Kimm went viral after claiming Ssense sent her a fake version of The Row’s $1,090 90’s bag. In a follow up video, Kimm said that Ssense ended up issuing her a refund and a 10 percent discount credit, but wouldn’t confirm if the original bag she ordered was indeed a counterfeit. The incident created paranoia in other shoppers. In February, another TikTok user named Jennielyn made a response video to Kimm where she questioned the authenticity of a Gimaguas shoulder bag she ordered from Ssense for $700 which came without a branded duster bag, the tag cut off and thinner leather than she expected. “We are committed to ensuring the authenticity of all products sold. We have measures in place to prevent the sale of counterfeit items,” an Ssense spokesperson said in a statement. “Our return policy outlines how items must be returned in their original condition, including all packaging, accessories and Ssense tags, to facilitate thorough examination.” Returns fraud, in which customers send back empty boxes, less expensive or counterfeit items instead of the merchandise they ordered, is a major — and growing — problem in fashion. In 2024, it led US retailers to lose $104 billion in revenue, more than quadruple the losses from 2020, according to data from fraud prevention software provider Riskified. A chart illustrating the growing returns fraud conundrum. (BoF Team) It’s also an extremely difficult problem for retailers to tackle. For starters, as replicas become more sophisticated, fakes are harder to spot. Building an authentication system is a notoriously tricky and expensive endeavour. Plus, primary retailers historically haven’t had to do so to earn consumer trust the way that resale sites eBay, The RealReal and Vestiaire Collective have. And of course, even when there is an authentication process in place, counterfeits can still slip through.But luxury e-tailers can’t afford to ignore the problem for much longer. Receiving a counterfeit product when you’re paying for the real thing can sow a dangerous level of consumer distrust. And considering the current luxury spending environment — global sales in the sector dropped 2 percent in 2024, and US president Donald Trump’s forthcoming tariff increases threaten to further hamper consumer sentiment — there’s extra incentive to get the issue under control.“Once someone managed to get a fake through the door, and you ended up sending that to an end customer that spent their hard earned money … there’s a huge chance that you’re missing that customer for life,” said Eyal Elazar, senior director of product marketing and market intelligence at Riskified. BoF breaks down how retailers can buck the trend. How do counterfeits make their way onto firsthand retail sites? Fake goods showing up in firsthand luxury e-tailer’s inventories through returns is partially a result of a rise in counterfeits on the market. Once mostly restricted to backdoor sellers on Canal Street and the like, shoppers today can get their hands on fakes through websites like AliExpress, DHGate, Shein and even Amazon. In response to Trump imposing more than 100 percent tariffs on China, manufacturers in the region that claim to produce luxury bags for brands like Hermès and Chanel are going viral on TikTok, offering to sell to them directly. The share of fakes that authentication software platform Entrupy encountered across billions of dollars worth of luxury items jumped from 8.3 percent in 2021 to 8.7 percent in 2023. But the increase in counterfeit returned goods also reflects a luxury backlash among younger consumers. Prices for high-end goods have increased more than 50 percent in 2019, according to HSBC. As such, more shoppers — particularly Gen-Zers — aren’t convinced they’re worth the exorbitant prices, and also feel that luxury brands make enough money as is. They’re not only seeking out dupes for coveted items like The Row’s $6,400 Margaux bag or Alaia’s $1,350 Mary Jane-styled leather ballet flats, but they’re also openly bragging about doing so on social media. “A lot of Gen-Z sees this as sticking it to the corporation,” said Gwyneth Lewis, chief of staff at trademarking software firm Huski AI. “In the 2010s people would wear a dress and return it. The 2020s version is buying something real and returning something fake.” It’s also easier to get away with: Consumers can take advantage of more lax online return policies introduced to drive sales during the pandemic e-commerce boom, such as the ability to get a refund once they ship back an item. While a greater number of younger consumers are willing to proudly carry a dupe, it’s still a relatively small number who go so far as to engage in the type of returns fraud that drives sizable revenue losses for retailers. One of Riskified’s clients (which it didn’t disclose for privacy reasons) found that only less than 1 percent of their customers caused a loss of $4 million in 2024 from fraud-related activity, Elazar said. “There’s a handful of people that are ruining it for everyone,” Elazar added. “The more of these bad people that we catch and prevent, the less this becomes a trend.”How can online retailers address it? The most obvious solution to ward off counterfeits would be for retailers to authenticate all high-end goods, especially handbags and footwear, when they are returned to their warehouses. But doing so would be a sizable investment for what is still a relatively minor issue, and even if such processes were implemented, detecting a fake is not straightforward. Luxury resale marketplace Vestiaire Collective, for example, has prevented €12 million ($13 million) worth of counterfeit goods from making it onto its site this year. To do so, the Paris-based company operates four authentication hubs in New York, Hong Kong, France and the UK, where it employs more than 100 authenticators, some of whom are so skilled they can detect a fake bag by the scent of its leather, said Victoire Boyer Chammard, Vestiaire Collective’s senior brand manager and authentication specialist.“In terms of investments linked to trust, it was never a subject of costs,” Boyer Chammard said. ���We want to put money on the table to ensure that we try to be trusted.”While firsthand retailers could invest in similar practices, doing so would add another layer to an already time-consuming returns process where the main concern is getting items back into stock as quickly as possible. Add to that, hiring authentication experts is an additional expenditure at a time when businesses are already dealing with higher shipping costs — and bracing for the impact of threatened tariffs. Plus, the authentication process is far from perfect, even for resale marketplaces: StockX, for instance, is currently in a legal dispute with Nike, which is accusing the Detroit-based reseller of allowing counterfeit versions of the sneaker giant’s styles to be sold on its site. “Some of the marketplaces hurt their bottom lines to put extra processes in place,” Lewis said. “They are managing so many different problems.” To that end, there are alternatives. Max Peiro, chief executive of luxury analytics firm Re-Hub, suggested luxury e-tailers can add QR code-embedded seals to their products; if they’re broken, an item can’t be returned. Because they are harder to remove than standard tags, it prevents customers from swapping in a fake and also ensures that items are always in resalable condition. Retailers can also partner with firms that help identify return policy abusers and remove perks like instant refunds to those identified. Riskified’s software can detect shoppers whose past returns include shipping back boxes full of dried ice or items they didn’t originally order based on their IP addresses or zip codes, and ensure that any future returns they make — even if they placed an order with a new name and credit card — will be flagged for further inspection. More firms are developing similar features. In March, returns management company Narvar introduced an AI tool that flags potential policy abusers and is already gaining traction with its retail partners, said Anissa Kumar, Narvar’s chief executive, although she wouldn’t disclose how many clients have started using the service. While it’s likely impossible for retailers to ensure no counterfeits will ever show up on their marketplaces, finding and penalising more of the customers who are likely to engage in this sort of fraud is one step toward maintaining consumers’ trust in the long-term. “You have to make sure that once you spot someone who’s a fraudster, you block them and you block them in an effective way,” Elazar said. Source link
0 notes
Photo

Online luxury’s counterfeit problem is spreading. Since the dawn of e-commerce, shoppers ordering designer bags on a digital resale site like eBay have done so knowing they risked buying a fake — essentially, a trade-off for securing a lower price. But now, those knock-offs are starting to show up on firsthand marketplaces as more consumers are ordering new handbags or sneakers and going on to return a fake version. Some shoppers are starting to sound the alarm. In January, influencer Tiffany Kimm went viral after claiming Ssense sent her a fake version of The Row’s $1,090 90’s bag. In a follow up video, Kimm said that Ssense ended up issuing her a refund and a 10 percent discount credit, but wouldn’t confirm if the original bag she ordered was indeed a counterfeit. The incident created paranoia in other shoppers. In February, another TikTok user named Jennielyn made a response video to Kimm where she questioned the authenticity of a Gimaguas shoulder bag she ordered from Ssense for $700 which came without a branded duster bag, the tag cut off and thinner leather than she expected. “We are committed to ensuring the authenticity of all products sold. We have measures in place to prevent the sale of counterfeit items,” an Ssense spokesperson said in a statement. “Our return policy outlines how items must be returned in their original condition, including all packaging, accessories and Ssense tags, to facilitate thorough examination.” Returns fraud, in which customers send back empty boxes, less expensive or counterfeit items instead of the merchandise they ordered, is a major — and growing — problem in fashion. In 2024, it led US retailers to lose $104 billion in revenue, more than quadruple the losses from 2020, according to data from fraud prevention software provider Riskified. A chart illustrating the growing returns fraud conundrum. (BoF Team) It’s also an extremely difficult problem for retailers to tackle. For starters, as replicas become more sophisticated, fakes are harder to spot. Building an authentication system is a notoriously tricky and expensive endeavour. Plus, primary retailers historically haven’t had to do so to earn consumer trust the way that resale sites eBay, The RealReal and Vestiaire Collective have. And of course, even when there is an authentication process in place, counterfeits can still slip through.But luxury e-tailers can’t afford to ignore the problem for much longer. Receiving a counterfeit product when you’re paying for the real thing can sow a dangerous level of consumer distrust. And considering the current luxury spending environment — global sales in the sector dropped 2 percent in 2024, and US president Donald Trump’s forthcoming tariff increases threaten to further hamper consumer sentiment — there’s extra incentive to get the issue under control.“Once someone managed to get a fake through the door, and you ended up sending that to an end customer that spent their hard earned money … there’s a huge chance that you’re missing that customer for life,” said Eyal Elazar, senior director of product marketing and market intelligence at Riskified. BoF breaks down how retailers can buck the trend. How do counterfeits make their way onto firsthand retail sites? Fake goods showing up in firsthand luxury e-tailer’s inventories through returns is partially a result of a rise in counterfeits on the market. Once mostly restricted to backdoor sellers on Canal Street and the like, shoppers today can get their hands on fakes through websites like AliExpress, DHGate, Shein and even Amazon. In response to Trump imposing more than 100 percent tariffs on China, manufacturers in the region that claim to produce luxury bags for brands like Hermès and Chanel are going viral on TikTok, offering to sell to them directly. The share of fakes that authentication software platform Entrupy encountered across billions of dollars worth of luxury items jumped from 8.3 percent in 2021 to 8.7 percent in 2023. But the increase in counterfeit returned goods also reflects a luxury backlash among younger consumers. Prices for high-end goods have increased more than 50 percent in 2019, according to HSBC. As such, more shoppers — particularly Gen-Zers — aren’t convinced they’re worth the exorbitant prices, and also feel that luxury brands make enough money as is. They’re not only seeking out dupes for coveted items like The Row’s $6,400 Margaux bag or Alaia’s $1,350 Mary Jane-styled leather ballet flats, but they’re also openly bragging about doing so on social media. “A lot of Gen-Z sees this as sticking it to the corporation,” said Gwyneth Lewis, chief of staff at trademarking software firm Huski AI. “In the 2010s people would wear a dress and return it. The 2020s version is buying something real and returning something fake.” It’s also easier to get away with: Consumers can take advantage of more lax online return policies introduced to drive sales during the pandemic e-commerce boom, such as the ability to get a refund once they ship back an item. While a greater number of younger consumers are willing to proudly carry a dupe, it’s still a relatively small number who go so far as to engage in the type of returns fraud that drives sizable revenue losses for retailers. One of Riskified’s clients (which it didn’t disclose for privacy reasons) found that only less than 1 percent of their customers caused a loss of $4 million in 2024 from fraud-related activity, Elazar said. “There’s a handful of people that are ruining it for everyone,” Elazar added. “The more of these bad people that we catch and prevent, the less this becomes a trend.”How can online retailers address it? The most obvious solution to ward off counterfeits would be for retailers to authenticate all high-end goods, especially handbags and footwear, when they are returned to their warehouses. But doing so would be a sizable investment for what is still a relatively minor issue, and even if such processes were implemented, detecting a fake is not straightforward. Luxury resale marketplace Vestiaire Collective, for example, has prevented €12 million ($13 million) worth of counterfeit goods from making it onto its site this year. To do so, the Paris-based company operates four authentication hubs in New York, Hong Kong, France and the UK, where it employs more than 100 authenticators, some of whom are so skilled they can detect a fake bag by the scent of its leather, said Victoire Boyer Chammard, Vestiaire Collective’s senior brand manager and authentication specialist.“In terms of investments linked to trust, it was never a subject of costs,” Boyer Chammard said. “We want to put money on the table to ensure that we try to be trusted.”While firsthand retailers could invest in similar practices, doing so would add another layer to an already time-consuming returns process where the main concern is getting items back into stock as quickly as possible. Add to that, hiring authentication experts is an additional expenditure at a time when businesses are already dealing with higher shipping costs — and bracing for the impact of threatened tariffs. Plus, the authentication process is far from perfect, even for resale marketplaces: StockX, for instance, is currently in a legal dispute with Nike, which is accusing the Detroit-based reseller of allowing counterfeit versions of the sneaker giant’s styles to be sold on its site. “Some of the marketplaces hurt their bottom lines to put extra processes in place,” Lewis said. “They are managing so many different problems.” To that end, there are alternatives. Max Peiro, chief executive of luxury analytics firm Re-Hub, suggested luxury e-tailers can add QR code-embedded seals to their products; if they’re broken, an item can’t be returned. Because they are harder to remove than standard tags, it prevents customers from swapping in a fake and also ensures that items are always in resalable condition. Retailers can also partner with firms that help identify return policy abusers and remove perks like instant refunds to those identified. Riskified’s software can detect shoppers whose past returns include shipping back boxes full of dried ice or items they didn’t originally order based on their IP addresses or zip codes, and ensure that any future returns they make — even if they placed an order with a new name and credit card — will be flagged for further inspection. More firms are developing similar features. In March, returns management company Narvar introduced an AI tool that flags potential policy abusers and is already gaining traction with its retail partners, said Anissa Kumar, Narvar’s chief executive, although she wouldn’t disclose how many clients have started using the service. While it’s likely impossible for retailers to ensure no counterfeits will ever show up on their marketplaces, finding and penalising more of the customers who are likely to engage in this sort of fraud is one step toward maintaining consumers’ trust in the long-term. “You have to make sure that once you spot someone who’s a fraudster, you block them and you block them in an effective way,” Elazar said. Source link
0 notes
Photo

Online luxury’s counterfeit problem is spreading. Since the dawn of e-commerce, shoppers ordering designer bags on a digital resale site like eBay have done so knowing they risked buying a fake — essentially, a trade-off for securing a lower price. But now, those knock-offs are starting to show up on firsthand marketplaces as more consumers are ordering new handbags or sneakers and going on to return a fake version. Some shoppers are starting to sound the alarm. In January, influencer Tiffany Kimm went viral after claiming Ssense sent her a fake version of The Row’s $1,090 90’s bag. In a follow up video, Kimm said that Ssense ended up issuing her a refund and a 10 percent discount credit, but wouldn’t confirm if the original bag she ordered was indeed a counterfeit. The incident created paranoia in other shoppers. In February, another TikTok user named Jennielyn made a response video to Kimm where she questioned the authenticity of a Gimaguas shoulder bag she ordered from Ssense for $700 which came without a branded duster bag, the tag cut off and thinner leather than she expected. “We are committed to ensuring the authenticity of all products sold. We have measures in place to prevent the sale of counterfeit items,” an Ssense spokesperson said in a statement. “Our return policy outlines how items must be returned in their original condition, including all packaging, accessories and Ssense tags, to facilitate thorough examination.” Returns fraud, in which customers send back empty boxes, less expensive or counterfeit items instead of the merchandise they ordered, is a major — and growing — problem in fashion. In 2024, it led US retailers to lose $104 billion in revenue, more than quadruple the losses from 2020, according to data from fraud prevention software provider Riskified. A chart illustrating the growing returns fraud conundrum. (BoF Team) It’s also an extremely difficult problem for retailers to tackle. For starters, as replicas become more sophisticated, fakes are harder to spot. Building an authentication system is a notoriously tricky and expensive endeavour. Plus, primary retailers historically haven’t had to do so to earn consumer trust the way that resale sites eBay, The RealReal and Vestiaire Collective have. And of course, even when there is an authentication process in place, counterfeits can still slip through.But luxury e-tailers can’t afford to ignore the problem for much longer. Receiving a counterfeit product when you’re paying for the real thing can sow a dangerous level of consumer distrust. And considering the current luxury spending environment — global sales in the sector dropped 2 percent in 2024, and US president Donald Trump’s forthcoming tariff increases threaten to further hamper consumer sentiment — there’s extra incentive to get the issue under control.“Once someone managed to get a fake through the door, and you ended up sending that to an end customer that spent their hard earned money … there’s a huge chance that you’re missing that customer for life,” said Eyal Elazar, senior director of product marketing and market intelligence at Riskified. BoF breaks down how retailers can buck the trend. How do counterfeits make their way onto firsthand retail sites? Fake goods showing up in firsthand luxury e-tailer’s inventories through returns is partially a result of a rise in counterfeits on the market. Once mostly restricted to backdoor sellers on Canal Street and the like, shoppers today can get their hands on fakes through websites like AliExpress, DHGate, Shein and even Amazon. In response to Trump imposing more than 100 percent tariffs on China, manufacturers in the region that claim to produce luxury bags for brands like Hermès and Chanel are going viral on TikTok, offering to sell to them directly. The share of fakes that authentication software platform Entrupy encountered across billions of dollars worth of luxury items jumped from 8.3 percent in 2021 to 8.7 percent in 2023. But the increase in counterfeit returned goods also reflects a luxury backlash among younger consumers. Prices for high-end goods have increased more than 50 percent in 2019, according to HSBC. As such, more shoppers — particularly Gen-Zers — aren’t convinced they’re worth the exorbitant prices, and also feel that luxury brands make enough money as is. They’re not only seeking out dupes for coveted items like The Row’s $6,400 Margaux bag or Alaia’s $1,350 Mary Jane-styled leather ballet flats, but they’re also openly bragging about doing so on social media. “A lot of Gen-Z sees this as sticking it to the corporation,” said Gwyneth Lewis, chief of staff at trademarking software firm Huski AI. “In the 2010s people would wear a dress and return it. The 2020s version is buying something real and returning something fake.” It’s also easier to get away with: Consumers can take advantage of more lax online return policies introduced to drive sales during the pandemic e-commerce boom, such as the ability to get a refund once they ship back an item. While a greater number of younger consumers are willing to proudly carry a dupe, it’s still a relatively small number who go so far as to engage in the type of returns fraud that drives sizable revenue losses for retailers. One of Riskified’s clients (which it didn’t disclose for privacy reasons) found that only less than 1 percent of their customers caused a loss of $4 million in 2024 from fraud-related activity, Elazar said. “There’s a handful of people that are ruining it for everyone,” Elazar added. “The more of these bad people that we catch and prevent, the less this becomes a trend.”How can online retailers address it? The most obvious solution to ward off counterfeits would be for retailers to authenticate all high-end goods, especially handbags and footwear, when they are returned to their warehouses. But doing so would be a sizable investment for what is still a relatively minor issue, and even if such processes were implemented, detecting a fake is not straightforward. Luxury resale marketplace Vestiaire Collective, for example, has prevented €12 million ($13 million) worth of counterfeit goods from making it onto its site this year. To do so, the Paris-based company operates four authentication hubs in New York, Hong Kong, France and the UK, where it employs more than 100 authenticators, some of whom are so skilled they can detect a fake bag by the scent of its leather, said Victoire Boyer Chammard, Vestiaire Collective’s senior brand manager and authentication specialist.“In terms of investments linked to trust, it was never a subject of costs,” Boyer Chammard said. “We want to put money on the table to ensure that we try to be trusted.”While firsthand retailers could invest in similar practices, doing so would add another layer to an already time-consuming returns process where the main concern is getting items back into stock as quickly as possible. Add to that, hiring authentication experts is an additional expenditure at a time when businesses are already dealing with higher shipping costs — and bracing for the impact of threatened tariffs. Plus, the authentication process is far from perfect, even for resale marketplaces: StockX, for instance, is currently in a legal dispute with Nike, which is accusing the Detroit-based reseller of allowing counterfeit versions of the sneaker giant’s styles to be sold on its site. “Some of the marketplaces hurt their bottom lines to put extra processes in place,” Lewis said. “They are managing so many different problems.” To that end, there are alternatives. Max Peiro, chief executive of luxury analytics firm Re-Hub, suggested luxury e-tailers can add QR code-embedded seals to their products; if they’re broken, an item can’t be returned. Because they are harder to remove than standard tags, it prevents customers from swapping in a fake and also ensures that items are always in resalable condition. Retailers can also partner with firms that help identify return policy abusers and remove perks like instant refunds to those identified. Riskified’s software can detect shoppers whose past returns include shipping back boxes full of dried ice or items they didn’t originally order based on their IP addresses or zip codes, and ensure that any future returns they make — even if they placed an order with a new name and credit card — will be flagged for further inspection. More firms are developing similar features. In March, returns management company Narvar introduced an AI tool that flags potential policy abusers and is already gaining traction with its retail partners, said Anissa Kumar, Narvar’s chief executive, although she wouldn’t disclose how many clients have started using the service. While it’s likely impossible for retailers to ensure no counterfeits will ever show up on their marketplaces, finding and penalising more of the customers who are likely to engage in this sort of fraud is one step toward maintaining consumers’ trust in the long-term. “You have to make sure that once you spot someone who’s a fraudster, you block them and you block them in an effective way,” Elazar said. Source link
0 notes
Text
The Truth About Buying Cloned Cards Online – Cybersecurity Risks & Realities

In the age of digital transactions and online marketplaces, discussions around financial fraud have become more common—and one of the trending phrases making rounds is "buy cloned cards online." Whether out of curiosity, criminal intent, or research purposes, people are increasingly searching for this term. But what does it actually mean? What are cloned cards? Is it legal? And what risks are involved?
In this article, we’ll uncover everything about the dark web economy of cloned cards, explore the cybersecurity implications, and explain why engaging with these markets could lead to severe consequences.
💳 What Are Cloned Cards?
Cloned cards refer to counterfeit credit or debit cards created using stolen card data. This process usually involves copying the magnetic strip or chip information from a real card and encoding it onto a fake one. Cybercriminals can obtain this data through methods like:
Skimming devices at ATMs or gas stations
Phishing attacks
Data breaches
Dark web purchases of card dumps
Once they have the card data, they use specialized machines to “clone” or duplicate the cards. These fake cards can then be used for fraudulent purchases until the legitimate owner notices and reports the activity.
🛒 The Appeal of Buying Cloned Cards Online
People searching for “buy cloned cards online” may be lured by promises such as:
Access to cards with high balances
“Untraceable” cards for online or in-store shopping
Quick profits with minimal effort
Supposed anonymity on the dark web
These promises often come from shady websites or dark web forums that claim to sell cloned cards or offer “carding” services. Most of these platforms only accept cryptocurrency like Bitcoin or Monero to maintain anonymity and avoid tracking by law enforcement.
But the reality behind these transactions is far more complicated—and risky.
🚨 Legal & Criminal Risks
Buying cloned cards is illegal in virtually every country. It falls under fraud, identity theft, and financial crime. Here are some of the legal consequences:
Fines and imprisonment (in some countries up to 10–20 years)
Seizure of assets
Criminal records
Involvement in broader criminal investigations
Even browsing these sites or attempting to make a purchase can land you in hot water, as many forums are monitored by law enforcement and cybersecurity agencies.
🎭 Scams and Fake Vendors
Another reason not to engage with the dark market is the sheer number of scams. Common tactics include:
Vendors vanishing after payment
Low-quality or non-working cards
Fake “customer support” extracting more money
Malware hidden in download links
There’s no accountability or refund when you're dealing in an illegal marketplace. You're just as likely to become a victim of fraud as the people whose cards are cloned.
🛡️ Cybersecurity Implications
If you're not actively participating in carding, but you're just researching it, the threat still looms. Many sites offering cloned cards are laced with malware, spyware, or ransomware. Visiting them can expose your personal data, banking info, or even give hackers remote access to your device.
Also, if your own credit or debit card has been compromised, it may be one of the thousands of card dumps circulating online. In that case:
Immediately contact your bank
Freeze or cancel your card
Monitor your account for suspicious activity
Report the breach to authorities
🌐 The Role of the Dark Web
The dark web is the primary marketplace for buying and selling cloned cards. Hidden behind layers of encryption and anonymity software like Tor, it houses marketplaces with user reviews, seller ratings, and even escrow systems—mimicking legitimate e-commerce.
However, these environments are unstable. Law enforcement agencies regularly infiltrate and shut down such platforms, leading to mass arrests and data leaks that can expose both buyers and sellers.
🔐 How to Protect Yourself from Card Cloning
Even if you’re not trying to buy cloned cards, knowing how to protect your financial information is essential:
Use cards with EMV chips – harder to clone than magnetic strip cards.
Enable transaction alerts – real-time notifications help detect fraud quickly.
Avoid public Wi-Fi when entering card details.
Use strong, unique passwords for online banking and e-commerce.
Monitor bank statements regularly.
Use virtual cards or masked card services for online purchases.
🤔 Final Thoughts: Curiosity Can Be Dangerous
While the search term "buy cloned cards online" might be trending, engaging with this market is not only illegal but also incredibly risky—ethically, legally, and financially. Most people are better served by understanding how these underground economies work so they can protect themselves, not participate in them.
If you’re researching for awareness or cybersecurity purposes, you’re on the right track. But if you’re considering stepping into this world, it’s important to know that the dangers far outweigh any potential benefit.
0 notes
Text
Cold Chain Monitoring Market Analysis: Key Players and Competitive Landscape
Rising Demand for Temperature-Sensitive Logistics Drives Growth in the Cold Chain Monitoring Market.
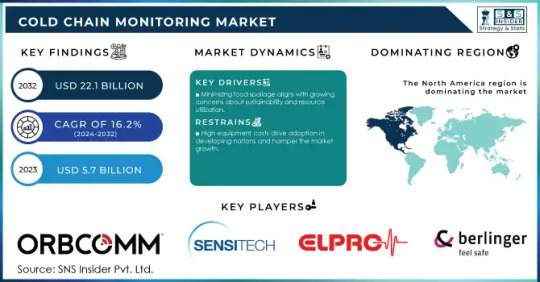
The Cold Chain Monitoring Market Size was USD 5.7 Billion in 2023 and is expected to reach USD 22.1 Billion by 2032 and grow at a CAGR of 16.2% over the forecast period of 2024-2032.
The Cold Chain Monitoring Market is driven by the increasing need for temperature-sensitive logistics solutions across industries such as pharmaceuticals, food & beverages, and chemicals. Cold chain monitoring systems ensure that perishable goods and temperature-sensitive products maintain their required storage conditions throughout the supply chain. The rising demand for biopharmaceuticals, vaccines, and fresh food products, coupled with stringent regulations on storage and transportation, is fueling the adoption of advanced cold chain monitoring solutions.
Key Players
ORBCOMM (US) – (IoT-based cold chain monitoring solutions, Fleet Management Systems)
Sensitech (US) – (TempTale Data Loggers, Cold Chain Monitoring Software)
Elpro-buchs (Switzerland) – (ELPRO Monitoring Solutions, e-Transcript System)
Berlinger & Co. (Switzerland) – (ThermoTrack Temperature Monitoring, ActiveSense Monitoring System)
Monnit (US) – (Monnit Wireless Sensors, Monnit Cloud Platform)
Controlant (Iceland) – (Controlant Smart Cold Chain, Real-time Monitoring Solutions)
Lineage Logistics Holding – (Cold Storage Solutions, Lineage Link Digital Platform)
Tagbox – (Cold Chain IoT Sensors, Tagbox Data Analytics Platform)
DAIKIN Industries – (Refrigeration Solutions, Remote Monitoring Systems)
Savi Technology – (SaviTrack RFID Solutions, SaviSense Sensor Platform)
Future Scope
The Cold Chain Monitoring Market is set for substantial expansion as supply chain digitization, IoT-based tracking systems, and AI-driven predictive analytics enhance real-time monitoring capabilities. Government regulations and quality control mandates for pharmaceutical and food safety are pushing businesses to integrate automated and cloud-based monitoring systems. Innovations in blockchain technology for supply chain transparency and the integration of smart sensors with predictive maintenance capabilities are expected to revolutionize cold chain management, reducing spoilage and ensuring compliance.
Emerging Trends
The industry is shifting toward real-time and AI-powered cold chain monitoring solutions, ensuring greater accuracy and efficiency in tracking temperature-sensitive shipments. The demand for wireless and cloud-based monitoring systems is rising, offering 24/7 remote access to temperature data and ensuring compliance with regulatory standards. Additionally, blockchain technology is being explored to enhance supply chain transparency and prevent counterfeiting in pharmaceuticals. The rise of automated alert systems, GPS tracking, and energy-efficient refrigeration technologies is also contributing to market growth.
Key Points
Rising demand for temperature-sensitive logistics in pharmaceuticals and food industries.
Increased adoption of IoT, AI, and blockchain for real-time supply chain monitoring.
Stringent regulatory requirements driving investments in advanced cold chain technologies.
Growing use of cloud-based and wireless temperature monitoring systems.
Expansion of automated alert systems and GPS tracking for improved shipment security.
Conclusion
The Cold Chain Monitoring Market is poised for significant growth, fueled by technological advancements, regulatory compliance requirements, and increasing demand for perishable goods logistics. As smart monitoring solutions, blockchain integration, and predictive analytics continue to evolve, the industry is set to enhance supply chain efficiency, reduce product wastage, and ensure the safe delivery of temperature-sensitive goods worldwide.
Read Full Report: https://www.snsinsider.com/reports/cold-chain-monitoring-market-1974
Contact Us:
Jagney Dave — Vice President of Client Engagement
Phone: +1–315 636 4242 (US) | +44- 20 3290 5010 (UK)
#Cold Chain Monitoring Market#Cold Chain Monitoring Market Size#Cold Chain Monitoring Market Share#Cold Chain Monitoring Market Report#Cold Chain Monitoring Market Forecast
0 notes
Text
Why Every Business Needs a Trusted IP Law Firm in India

In today’s hyper-competitive, digital-first world, your brand is your business. Whether it's your company name, logo, product design, or software—you’re constantly creating intellectual property (IP) that needs protection.
Unfortunately, many businesses underestimate the importance of safeguarding these intangible assets—until it's too late.
Working with a trusted IP law firm in India is no longer optional—it's a business necessity. From startups and tech firms to fashion brands and educational platforms, every organization stands to lose when their IP isn’t protected by professionals.
What is an IP Law Firm?
An IP law firm specializes in legal services related to intellectual property, which includes:
Trademarks (brand names, logos, slogans)
Copyrights (written content, music, software, designs)
Patents (inventions, products, processes)
Trade secrets and proprietary information
IP litigation and enforcement
A top IP law firm in India will not only register and manage your IP but also represent your business in disputes, infringement cases, and court proceedings.
Why Your Business Needs One – Key Reasons
✅ 1. To Secure Legal Ownership of Your Brand & Creations
Just building a great product or brand isn’t enough—you need to legally own it. An IP law firm helps you:
Register trademarks, copyrights, and patents
Avoid duplication or infringement claims
Maintain exclusive rights over your creative assets
Having legal ownership prevents others from using your identity or innovation.
✅ 2. To Prevent IP Theft & Copycats
India’s IP infringement landscape is real and growing—especially online. A trusted IP law firm in India actively monitors potential violations, sends legal notices, and initiates action to protect your brand from copycats and counterfeiters.
This is crucial for industries like:
Tech & software
Fashion & e-commerce
Media & entertainment
Pharma & health
✅ 3. To Handle Licensing & Monetization
Intellectual property isn’t just about protection—it’s also about profit. A reliable IP law firm helps you:
Draft IP licensing agreements
Manage royalty and usage contracts
Commercialize patents or trademarks
Protect your rights in joint ventures and collaborations
This allows your business to safely scale while monetizing innovation.
✅ 4. To Represent You in IP Disputes & Litigation
If someone infringes your trademark or copies your original content, legal action may be required. A seasoned IP law firm in India can:
File lawsuits or respond to legal claims
Represent you in courts or tribunals
Handle cross-border IP conflicts
Enforce rights under Indian and international IP laws
Professional representation means better outcomes and faster resolutions.
✅ 5. To Keep You Compliant With Evolving IP Laws
IP laws in India are constantly evolving with global treaties, digital reforms, and data-driven policies. Your IP firm keeps you updated on:
Legal renewals and deadlines
Patent filings in multiple jurisdictions
IP audits and portfolio management
Regulatory changes under Indian IP Acts
This proactive approach prevents expensive mistakes and legal gaps.
Trusted IP Legal Guidance with Ashwarya Sinha
When it comes to intellectual property, your business deserves legal support that’s as sharp as your ideas. Law firms like Ashwarya Sinha Chambers offer deep experience in managing complex IP portfolios across industries.
Their services include:
Trademark & copyright registration
IP portfolio management
Licensing, contract drafting, and enforcement
IP litigation before IPAB, High Courts, and other authorities
Whether you’re a startup or an enterprise, Ashwarya Sinha offers a client-centric approach backed by strong legal strategy and national reach.
Conclusion
Your intellectual property is the lifeblood of your brand. Whether it’s your design, your code, your name, or your invention—it’s what sets you apart in the market.
By partnering with a reliable IP law firm in India, you not only protect what you’ve built but also position your business for growth, investment, and long-term success.
If you haven’t secured your brand’s legal foundation yet, now is the time. Reach out to an IP expert and take the first step toward total protection and peace of mind.
1 note
·
View note