#cybersocs
Explore tagged Tumblr posts
Text



Xaitex slight design tweak 💫
#transformers#art#digital art#my art#oc#maccadam#transformers oc#robot#robot oc#mecha#oc artist#transformers ocs#cybasocs#cybersocs#Cybas Electrolites#species#transformers au#transformers universe#universe#transformers fandom#idw#idw transformers#maccadams#transformers concept#transformers oc concept#worldbuilding#cybas ocs
28 notes
·
View notes
Text
Orange Security Navigator report reveals Cyber Extortion victims increased 46% globally in 2023

Orange Security Navigator report reveals Cyber Extortion victims increased 46% globally in 2023. Security Navigator 2024 reveals highest number of Cyber Extortion victims ever recorded, with an increase of 46% worldwide in 2023. Highlights: Security Navigator 2024 – Security incidents surge as testing teams work harder than ever 2023 has seen the highest count of Cyber Extortion victims on record A new levelling of the physical and cyber battlefields, hacktivism as a powerful political tool Hacking remains in the top spot, with nearly a third of incidents we detect within our CyberSOCs The efficiency of mature, established clients can be four times higher than that of new clients A trusted partnership to define and implement cybersecurity strategies to meet organizations’ needs
Highlights:
- 129,395 detected incidents show a 30% increase YOY, resulting in 25,076 confirmed security incidents (19%). - 37.45% of detected incidents originate from internal actors, whether deliberate or accidental - The VERIS ‘Hacking’ category remains in the top spot, account for almost a third of confirmed incidents (30.32%). - Large enterprises (40%) are impacted the most by Cyber Extortion, followed by small organizations (25%) and medium-sized businesses (23%). - New research finds a new levelling of physical and cyber battlefields, revealing a thin line between physical war and cyber (through hacktivism) - Analysis of 2.5 million unique vulnerabilities reveals that majority (79%) are rated Medium or High, with nearly 1 in 10 critical (9.4%).
Security Navigator 2024 – Security incidents surge as testing teams work harder than ever
Orange Cyberdefense, the specialist arm of Orange dedicated to cybersecurity, launches today its annual security research report, the Security Navigator 2024. The report, which gathers, cross-references and analyzes data from a wide variety of sources, paints a broad and complex picture of the world of cybersecurity, amplified by geopolitical, economic and social dimensions. With the environment becoming more unstable and less predictable, it has become even more vital that organizations reduce their risk of exposure by understanding the threat landscape and how it can affect them. The Security Navigator 2024 reveals that our Threat Detection teams processed 30% more events across the period, totaling 129,395, of which 25,076 (19%) are confirmed security incidents. Of these, the threat action ‘Hacking’ remained the most prominent, accounting for almost a third of confirmed incidents (30.32%), followed by Misuse (16.61%) and Malware dropping to third (12.98%). Whilst the volume of events has increased, the actual number of confirmed incidents decreased by 14% YOY. The Manufacturing sector (32.43%) is by far the largest contributor in terms of confirmed incidents, following the same pattern as past years. Retail Trade (21.73%) and Professional, Scientific and Technological Services (9.84%) completed the top three, responsible for over two thirds of the confirmed incidents we raised with clients. As well as criminal opportunities, more and more threat actors are politically or ideologically motivated, with the aims of espionage, sabotage, disinformation and extortion increasingly intertwined. We report on the increase of Cyber Extortion (ransomware) victims worldwide, alongside a significant surge in hacktivism linked to the war against Ukraine. Current geopolitical events have also politicized some Cyber Extortion actors, some of whom have become more politically driven.
2023 has seen the highest count of Cyber Extortion victims on record
The Cyber Extortion threat landscape continues to evolve quickly and the past 12 months saw the number of Cyber Extortion victims globally increase by 46%, marking the highest numbers ever recorded. Large enterprises were the victim in the majority of attacks (40%), with those employing more than 10,000+ people seeing a steady increase. This trend was exacerbated by a single threat actor, Cl0p, which exploited two major vulnerabilities in 2023. Small organizations make up a quarter (25%) of all the victims, closely followed by medium-sized businesses, with a share of 23%. Large, English-speaking economies continue to account for the highest numbers of victims, with over half (53%) headquartered in the United States, followed by the United Kingdom (2nd, 6%) and Canada (3rd, 5%). However, we are starting to see a lateralization of the geographic distribution, illustrated by major YOY increases to victims in India (+97%), Oceania (+73%), and Africa (+70%). During 2023, we found 25 Cyber Extortion groups had disappeared from 2022, 23 had survived from the previous year and there were 31 new groups we had never seen before. Of the Cyber Extortion groups that existed, over half (54%) had a life span of up to 6 months, 21% 7-12 months and 10% of all groups made it to the age of 13-18 months, highlighting the challenges faced by those attempting to disrupt a Cyber Extortion operation.
A new levelling of the physical and cyber battlefields, hacktivism as a powerful political tool
Over the past two years, there has been an evident increase of activity in the hacktivism space to support causes of a political or social nature. We report that attacks from hacktivist groups involved in the war against Ukraine, siding with either Russia or Ukraine, have reached record-high levels, with Ukraine, Poland and Sweden the most impacted by the pro-Russian hacktivists we track. This upwards trend is being exacerbated further by other geopolitical events which have sparked the creation of new groups, most recently spawned following the latest developments in the Middle East. We report that Europe was impacted by 85% of all hacktivist attacks seen in 2023, followed by North America (7%) and the Middle East (3%). We observe that most of the over-attacked countries are geographically relatively close to the war against Ukraine. Our research has shown a continuous evolution towards ‘cognitive’ attacks, which seek to shape perception through technical activity. The impact has less to do with the disruptive effect of the attack or the value of the data or systems that are affected (e.g., stolen, leaked or destroyed) but with the impact that these attacks will have on societal perception. Not only do we witness cyber events that impact the physical world; we also observe physical events that illicit a direct cyber response from threat actors, thus in turn causing an escalation of those very same geopolitical tensions. Most of the hacktivist attacks that we are observing are Distributed-Denial-of-Service (DDoS) attacks. Some hacktivist groups have developed strong DDoS capabilities, while others are noisy about their capabilities and impact, applying a language and narrative that is disproportional to their actual action (and impact).
Hacking remains in the top spot, with nearly a third of incidents we detect within our CyberSOCs
Based on the VERIS framework, the threat action ‘Hacking’ remains the most detected type of security incident, accounting for almost a third of confirmed incidents with 30.32%, a significant increase on the 25% on last year. ‘Malware’ has historically been one of the two most detected true positive incident types. However, this year it has slipped to 3rd place, with just 12.98%. 'Misuse’ was the 2nd most raised Threat Action with 16.61%, almost exactly in line with last year’s report. Incidents categorized as ‘Error’ (7.33%) again take 4th place followed by ‘Social’ (7.15%) which completes the top five. The data found 37.45% of detected incidents within organizations originated from internal actors, with the majority coming from external actors (43.6%). Of these, the end-user device was the most impacted asset (27.7%), followed by the server (27.34%).
The efficiency of mature, established clients can be four times higher than that of new clients
The CyberSOC teams have noted that there is a strong correlation between the detection efficiency of a client account, and the degree of feedback we get from the client. We observe this year that the efficiency of mature, established clients can be four times higher than that of new clients who are just starting their onboarding journey with us, and we argue that this client maturity is strongly expressed in the frequency with which we receive feedback on incidents. We also show that while the ‘quantity’ of incidents we report to our clients has decreased proportionally over the years, the ‘quality’ has increased. This is apparent for “unknown events” which decrease from 15.33% for customers that have been onboard 1-10 months to 4.10% for customers that have been onboard for 41-50 months. We argue that this is a function of detection tuning, more rigorous analysis, and other service enhancements. In addition, as our clients mature in the service they improve their ability to act on the events we raise with them and refine the process of providing us with feedback. With sufficient feedback we are able to perform intelligent tuning and thereby improve detection efficiency in a repeating cycle.
A trusted partnership to define and implement cybersecurity strategies to meet organizations’ needs
“This year’s report underlines the unpredictable environment we face today, and we see our teams working harder than ever as the number of detected incidents continues to increase (+30% YOY). Whilst we are seeing a surge in the number of large businesses impacted by Cyber Extortion (40%), small and medium businesses together are making up nearly half of all victims (48%)”, said Hugues Foulon, CEO, Orange Cyberdefense “Together, with our customers, we are pursuing an unwavering policy of awareness and support for our increasingly interconnected world. We are adapting to new technologies and preparing for new threat actors by continuing to anticipate, detect and contain attacks when they emerge,” Foulon concludes The full Security Navigator 2024 report can be downloaded HERE. Read the full article
0 notes
Text

The Definitive Guide to Cyber Security Operation Center in 2022:
https://www.ecsbiztech.com/the-definitive-guide-to-cyber-security-operation-center-in-2022/
1 note
·
View note
Text
Manually Decoding DTMF Through A Spectrogram
While working on a recent CTF, I came across a challenge that required participants to extract a credit card number from a recording of a touch-tone telephone. If you pull your phone out now, turn on your ringer (because it’s almost definitely off), and click on some random numbers on the phone app keypad, you’ll hear the product of what’s known as DTMF, which stands for dual-tone multi-frequency.
I won’t go into the specifics of DTMF and why it exists — the important thing to know is DTMF uses a combination of two distinct tones to create one sound. There is a low tone and a high tone. Today, I’ll be showing you how to decode DTMF by sight through a spectrogram. There are decoders available for free online, so if you come across a problem like this in a CTF, or otherwise, I highly recommend using one of those, purely for speed and convenience. All that being said, this is an interesting process, and just generally a cool thing to know about. It’s the equivalent of converting binary to hexadecimal by hand instead of using an online converter — basically useless — but a great party trick (in the event of attending one, which I highly doubt given you’re reading this — so yeah, basically useless… on that note (or should I say tone (my musically inclined friend has informed me that I should not)), on with the article!)
Note — Standard DTMF — two tones, four levels per tone.
As of iOS 15.7, this tutorial is still relevant. I am looking for more samples (other phone brands and software models) to determine how accurate this is cross-platform. If you’re interested in contributing, there will be some information at the end explaining how.
I’ll be using this audio file - https://voca.ro/1dr1J1gbyw5B
(This is from the CyberSoc Wales “personalbanker” challenge)
The first thing I did was put the recording through a spectrogram program. There are plenty available for free online; personally, I like using Academo, because it includes lines that will help with quick sight-reading later on. (https://academo.org/articles/spectrogram/).
You may be better off downloading software (Audacity is fantastic), should you require a spectrogram for a longer recording. Academo is not scalable beyond 10 seconds, so you can use it, but you’re going to be taking quite a few screenshots.
The first thing I did was drop the recording from the challenge into Academo.
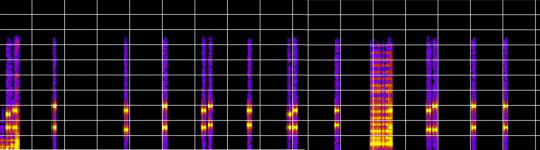
A spectrogram is a visual representation of the frequency content of an audio signal as it changes over time. In the image above, I’ve isolated the beeps produced by the clicking of the phone keypad. This section of the recording is longer than 10 seconds, so I also spliced together two screenshots. Any discrepancies you may notice in the image above are a product of that.
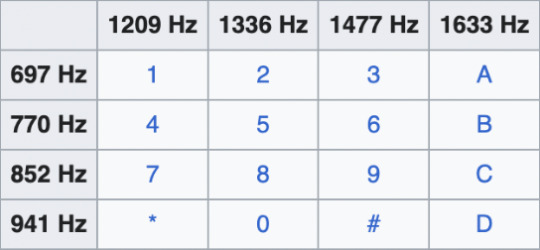
Each vertical line of dots represents one beep, and thus, one number. You’ll notice that there are two horizontal rows per beep, this is the magic of DTMF. There are 8 total frequencies involved in the DTMF system. The original DTMF keypad was laid out in a 4x4 format (below). The letter keys (A, B, C, and D) are no longer used for personal telecommunication. For digital decoding purposes, you will almost certainly not come across the letter keys, although they are still used by amateur radio operators, payphones, and the occasional equipment control system.

I was starting from scratch, with no knowledge of how a spectrogram worked with DTMF, so the first thing I did was create two recordings of myself clicking each number in my phone app (I am using iOS 15.7 on my iPhone XR).
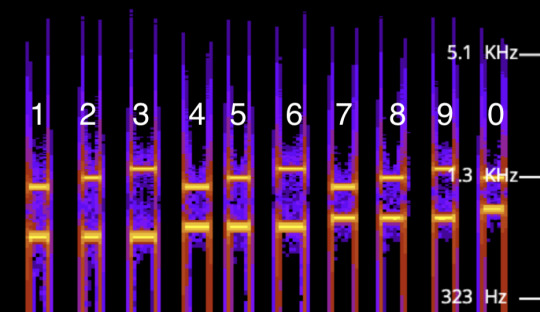

What you’ll begin to notice is that each number has its own combination of low and high tones. If you want to try to figure out the system on your own, now is the time.
Each variation in height represents a tone at a specific Hz. In order to decode this manually, you do not need to know the specific Hz of each number, you just need to understand the relational position of each tone, informed by its Hz.
I ended up throwing the original audio into Audacity so that I could create my own lines on the spectrogram for demonstration purposes.
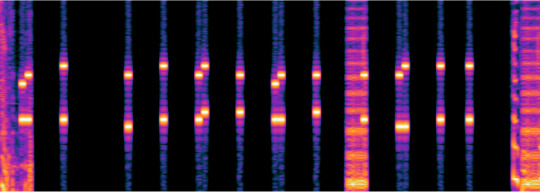
First, I’m going to turn down the contrast to make it a little easier to see.

Now, I’m going to add some lines to match up the similar tones.
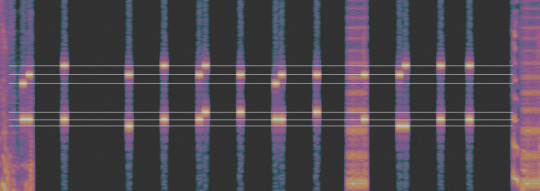
At this point, we have 6 layers of lines, there are no 0s present in this recording, if there were, we would have another line just above the bottom three. The use of the original DTMF structure with the ABCD keys would give us another line above the top three.
The simplest way to proceed is to categorize each set into Low, Medium, and High. You could choose any system — 1, 2, 3; a, b, c; whatever works for you. I recommend the LMH system because it’s visual and easy to keep track of.
I filled out the table below to show each numerical combination.

Two letters per number, each representing Low, Medium, or High (ultra High in the case of 0).
The first letter represents the top layer, and the second letter represents the bottom.
The corresponding Hz are listed in the third row for your reference.
I’ll walk you through the decoding process for the first two and then you can try the third.
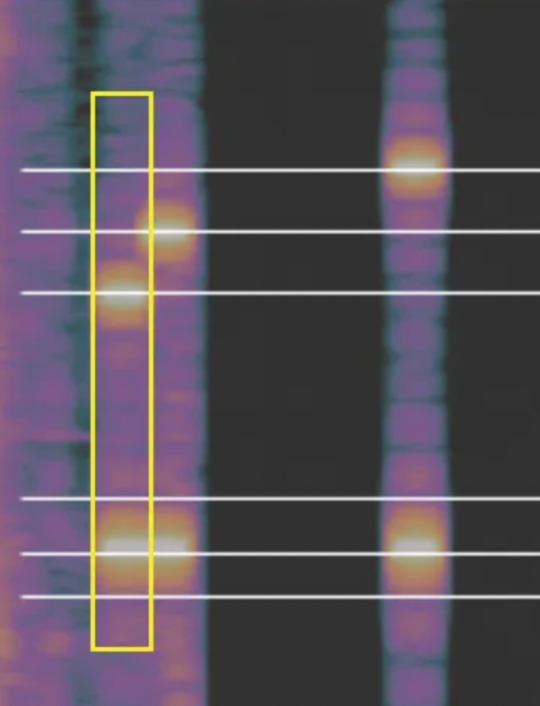
We’re going to look at the first column of tones (boxed in yellow).
This represents one number.
The first tone is crossed by the lowest of the top lines, it is marked L.
The second tone is crossed by the medium bottom line, it is marked M.
Together, they are LM — which, upon referencing the chart, is 4.
The second one is MM, which is 5.
Now try the third. (full answer at the end, scroll up now if you’d like to try it on your own — try it with lines or without!)
Once you get a feel for this, the process becomes much faster. The lines are purely for demonstrative purposes, with a little practice you’ll be able to quickly do this without lines.
And that’s how to decode DTMF manually through a spectrogram! Is it useless? Yes! Is it fun? That’s debatable!
If you’d like to help me compare cross-platform DTMF signaling, take a screen recording that captures you pressing 1234567890 on your phone keypad. Send the file to me through one of the methods outlined below. Please include your phone model and its latest software.
Discord — Adler#7210
Email me — [email protected]
If you’re seeing this on Tumblr, send me a DM!
Medium link - https://medium.com/@adler7210/manually-decoding-dtmf-through-spectrogram-562e4b0b99c3
The final answer to the CTF challenge — 4562 6598 4585 2366
Anyway, thanks for reading, enjoy decoding!
38 notes
·
View notes
Video
youtube
CYBERSOC IT | CYBERSECURITY | MOTIVATIONAL VIDEO
0 notes
Text
What's Wrong with Manufacturing?
The Hacker News : In last year's edition of the Security Navigator we noted that the Manufacturing Industry appeared to be totally over-represented in our dataset of Cyber Extortion victims. Neither the number of businesses nor their average revenue particularly stood out to explain this. Manufacturing was also the most represented Industry in our CyberSOC dataset – contributing more Incidents than any other http://dlvr.it/SkzHnX Posted by : Mohit Kumar ( Hacker )
0 notes
Text
Azure-managed service provider
An Azure-managed service provider is a business that runs its main operations on Microsoft Azure. Service monitoring, DevOps, security and compliance, and other services are available through Azure. An Azure MSP, ideally, provides comprehensive Azure-managed services to a large number of clients more efficiently.
IT service delivery is rapidly evolving. Because most firms prefer extremely scalable and trustworthy cloud systems, most traditional methods have become obsolete.
As an Azure MSP, your job is to create perfect cloud solutions, manage migration, and provide educated insights to your clients. You can provide innovation, deliver more robust solutions, develop unique apps, and gain a competitive advantage by utilizing Microsoft Azure.
The editors of Solutions Review created this resource to aid buyers in their quest for the best Azure-managed service providers to meet their organization's needs. Choosing the correct vendor and services can be a difficult process that necessitates extensive research and frequently involves more than just the tool and its technical capabilities. We've profiled the best Azure-managed service providers in one spot to make your search a little easier.
CyberSoC Capital uses Azure Security Center addresses the three most urgent security challenges
Rapidly changing workloads It's both a strength and a challenge of the cloud. On the one hand, end users are empowered to do more. On the other, how do you make sure that the ever-changing services people are using and creating are up to your security standards and follow security best practices?
Increasingly sophisticated attacks Wherever you run your workloads, the attacks keep getting more sophisticated. You have to secure your public cloud workloads, which are, in effect, an Internet facing workload that can leave you even more vulnerable if you don't follow security best practices.
Security skills are in short supply The number of security alerts and alerting systems far outnumbers the number of administrators with the necessary background and experience to make sure your environments are protected. Staying up-to-date with the latest attacks is a constant challenge, making it impossible to stay in place while the world of security is an ever-changing front.
0 notes
Text
Analyste Cybersécurité confirmé
Job title: Analyste Cybersécurité confirmé Company: Orange Job description: about the role Au sein de l’équipe CyberSOC, vous interviendrez sur le déploiement et support technique lié à la sécurité des réseaux, infrastructure et être amené à participer aux tâches suivantes : Vous principales missions seront : … Expected salary: Location: Casablanca Job date: Tue, 06 Jul 2021 04:25:42 GMT Apply…
View On WordPress
0 notes
Text


Song of the Sea
Heavily inspired by Song of the Sea!!! It's a beautiful movie please go check it out!
#song of the sea#song of the sea movie#sots#folklore#oc lore#scene redraw#transformers#art#digital art#my art#oc#maccadam#minicon#robot#robot oc#transformers oc#cyberfirstaidselectrolites#Charliee's ocs#cybersocs#electrolites#Zarien#past lore#lore update#lol his mom leaves 🤓#painting#digital painting#mecha#mech#robotic art#folk tale
7 notes
·
View notes
Photo

Dears,our good one brothers word,kindness Islam Human? We have become so accustomed to instant communication and Information, that we,re paranoid and fear we,all miss out on something if we put our phones down even for a few minutes.we,be become a cybersocity where virtually everything is a click away.we are exposed to more information now than ever before.But we must learn to disconnect in order to get connected. We all need to connect to online world to out side.But we should,t let technology eat up every free second we have in the day!. We don't need to drop everything allow gadgets to intrude into our previous private space let us put an end to this crazy bustle,and carve out technology-free moments for yourself and others.Take time with your text conversation, Take time to he in the moment. Take time to go for walk to savoir the blooming countryside. Those who fall to heed this tested lesson will be left with a harvest of regrats in the autumn of their lives. ( Thanks for moon Qazi &south Indian charge shyam kky). Dears,Right path ones aganist not me,truth ,not facke profile and pictures,this attitudes ,ones life today,legal and punishable also,world wide law.any way any Islam com cheaters stay to social media inside to immediately alone to good,not use to our pages,Islam or Muslim sisters and dears freedom, many Islam criminals make one bad name or Islam community leaders make one facke faith,education, knowledge ,real Islam faith studying joint human being understanding to our dears,women's and girls knowledge ,coming days knowledge full one Islam/ Muslim com making to world wide to100%.Meaning full family relationship making to our knowledge full Islam sisters to in this world.so our sisters non fear open face making to in this world,not jelus and ego Islam faith belive no?Real Allah and ESA belive.god is glory.all Islam criminal mind ones ending is our and our sisters aim.by Joseph Cheriyan ( Univers &Ioll,Organizer) (at Mumbai, Maharashtra) https://www.instagram.com/p/B1tI7p8AFIt/?igshid=1hulvzeko9udw
0 notes
Photo

Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
0 notes
Text
Le CyberSOC, un centre opérationnel pour la détection d'incidents de sécurité

La seule protection périmétrique des réseaux et systèmes d’information des entreprises a vécu. Si la mise en place de barrières filtrantes entre l’entreprise et le monde extérieur et en particulier l’internet (avec filtrage du traffic, détection de virus ou malware, etc …) reste un élément de protection indispensable, elles ne garantissent pas, à elles seules, l’entreprise contre l’ensemble des menaces informatiques sur la disponibilité, l’intégrité et la confidentialité des données sensibles de l’entreprise. Voici pourquoi.
1. Les attaques sont de plus en plus complexes et peuvent passer à travers les protections classiques.
2. L’ouverture croissante sur le monde extérieur est devenue inéluctable. Avec la mobilité des employées, la nécessité d’échanger avec ses clients et ses fournisseurs, le consumérisme croissant sur internet, il devient par conséquent de plus en plus complexe de protéger son système d’information.
3. Parce que, et ce n’est pas la moindre raison, la menace peut venir de l’intérieur, notamment par l’action volontaire ou involontaire d’employées de l’entreprise.
Dans ce contexte, il est devenu impératif de compléter le dispositif de protection périphérique par un système de supervision de l’activité malveillante jusqu’à l’intérieur même du réseau de l’entreprise. Tel est précisément l’objectif du CyberSOC : superviser en temps réel les biens critiques de l’entreprise et détecter toute action pouvant compromettre leur sécurité.
Comment ça marche ?
Le CyberSOC a pour mission première de superviser le système d’information de l’entreprise et de détecter rapidement tout incident de sécurité. Pour cela, il récupère en temps réel des données (en règle générale des logs d’équipements) sur l’ensemble du Système d’Information.
L’ensemble de ces données sont corrélées entre elles (et parfois avec des données extérieures, comme par exemple des listes d’URLs malveillantes) selon des scénarios de détection pré-définis correspondant à des attaques redoutées. Cette corrélation est également faite en temps réel et si les éléments collectés correspondent à un des scénarios connus, une alerte est immédiatement envoyée au CyberSOC pour analyse et traitement. On appelle SIEM (Security Information & Event Management), l’outil permettant de réaliser ces corrélations en temps réel.
Prenons l’exemple d’un serveur contenant des informations sensibles dont l’accès est restreint à certaines personnes de l’entreprise. Dans la construction des scénarios de détection, le CyberSOC va s’intéresser non seulement aux logs du serveur concerné (l’utilisateur est-il autorisé à accéder au serveur et est-il correctement authentifié ?) mais également à l’ensemble des logs permettant de reconstituer le comportement de l’utilisateur accédant aux données.
L’utilisateur a-t-il accédé à ces informations depuis son poste de travail, par un cheminement classique ou via rebond sur d’autres équipements ? Est-il en mobilité (depuis l’étranger ?), a-t-il essayé au préalable d’accéder à d’autres serveurs de façon répétée ?
On touche ici un point clé de l’activité du CyberSOC, car pour être efficace, le CyberSOC doit avoir une connaissance précise des biens sensibles de l’entreprise mais aussi de la façon dont ces biens sont utilisés (ou supposés l’être), c’est à dire le « qui, quoi, quand, où, comment ».
Les missions du CyberSOC
En premier lieu, le CyberSOC intervient dans la modélisation du système de détection. Ce système sera décomposé en autant de macro-scénarios (que nous appellerons use-cases) qu’il y a de risques identifiés. A cet égard, il est essentiel de procéder en amont à une analyse de risque qui permettra de définir les scénarios de menaces puis les scénarios de détection.
Une fois les use-cases modélisés, il est nécessaire de les faire « tourner » en conditions réelles pendant quelques semaines afin d’affiner les scénarios et diminuer le nombre de faux positifs (alertes ne correspond pas à un incident réel). A ce stade, seul un rapport est généré lorsqu’une détection est réalisée. Cette étape permet notamment de confirmer ou pas le comportement attendu des utilisateurs (avec souvent quelques surprises). Lorsque cette phase de « tuning » est terminée, le use case est mis en opérationnel et déclenche alors une alerte lorsque le cas modélisé est rencontré.
Le CyberSOC assure une supervision des incidents de sécurité en 24×7. Lorsqu’une alerte est reçue, un opérateur relève l’alerte et crée un ticket d’incident. Il réalise ensuite une première qualification et analyse en s’appuyant sur des fiches réflexes définies pour chaque use-case.
Selon les cas, le ticket d’incident pourra être traité de façon autonome par l’opérateur ou devra être transmis aux analystes sécurité pour analyse détaillée.
Les analystes sécurité travaillent en relation étroite avec les équipes qui gèrent les équipements ou le périmètre concerné. Ils apportent assistance et conseils aux équipes pour procéder aux analyses sur site ou remédiations. Ils peuvent également demander aux équipes techniques de procéder à des prélèvements pour compléter leur analyse. Ils n’interviennent généralement pas directement dans la remédiation. Ils peuvent être en relation avec des équipes techniques pour arrêter ou filtrer une attaque ou s’appuyer sur une équipe spécialisée dans la réponse à incidents (CSIRT – Computer Security Incident Response Team).
Les analystes Sécurité peuvent également s’appuyer sur des experts Sécurité pour des incidents complexes nécessitant par exemple une analyse approfondie, un rejeu en plateforme de tests ou une expertise spécifique.
La modélisation d’un système de détection doit être vue comme un système dynamique. Les menaces évoluent, le périmètre supervisé également et le système de détection doit s’affiner avec le temps. Il est donc impératif d’avoir un processus d’amélioration continue. Ce processus inclut la revue régulière des incidents passés mais également celle de l’efficacité du modèle de détection en place.
L’organisation du CyberSOC
L’organisation du CyberSOC doit permettre de répondre à ses différentes missions. Pour la phase de RUN, le CyberSOC s’organise, de façon classique, en 3 couches distinctes :
Le niveau 1 (opérateurs) relève les alertes et fait un premier diagnostic.
Le niveau 2 (analyste sécurité) réalise l’analyse détaillée des alertes, communique vers les équipes concernées, accompagne le traitement des incidents et, dans quelques cas, peut mettre en place des remédiations.
Le niveau 3 (experts sécurité) prend la relève du niveau 2 pour les analyses approfondies ou nécessitant une compétence pointue. Le niveau 3 est également impliqué en phase de Build pour la modélisation des use-cases. En s’appuyant sur l’analyse de risques, il va proposer et implémenter les uses-cases en s’appuyant notamment sur un catalogue de use-cases couvrant de nombreuses menaces. Si le use-case n’est pas déjà présent dans le catalogue, il est en charge de le développer pour répondre au besoin spécifique.
Enfin, Le Security Manager est le chef d’orchestre du processus d’amélioration, en pilotant l’efficacité du modèle de détection et en proposant des améliorations. Il peut proposer de créer de nouveaux use-cases, d’en supprimer ou de procéder à des améliorations.
Les services CyberSOC
Le cœur de l’activité du CyberSOC est la mise en œuvre et le pilotage de solutions de supervision sécurité s’appuyant sur une solution de SIEM (à base de corrélations). Toutefois, le CyberSOC s’intéresse à tout service permettant d’identifier un incident de sécurité. A ce titre, il peut ainsi intervenir de façon ciblée pour superviser les incidents remontés par des sondes de détection d’intrusion, des systèmes de filtrage applicatif, des sondes de détections d’attaques DDoS (attaques visant à rendre indisponible des serveurs, web par exemple) ou même des scanners de vulnérabilités. Le champ des possibles est très large … autant que l’imagination des attaquants eux-mêmes.
Franck
Pour aller plus loin
Computer Emergency Response Team : qu’est ce qui fait l’efficacité d’un CERT ? Pour tout savoir sur les tendances 2016 de la cyberdéfense en 120 secondes Orange Cyberdefense protège vos essentiels Cloud Access Security Brokers (CASB) : le nouvel eldorado de la sécurité ?
Le CyberSOC, un centre opérationnel pour la détection d'incidents de sécurité was originally published on JDCHASTA SAS
0 notes
Text

SOC framework – what is it and how does it benefit your organisation?
Read More:
https://www.ecsbiztech.com/soc-framework-what-is-it-and-how-does-it-benefit-your-organisation/
0 notes
Text
Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure
In earlier years, everyone depends on SOC (includes firewalls, WAF, SIEM,etc.) and the prioritize in building the SOC provides security and the CIA was maintained. However, later the emerge of the attacks and the threat actors becomes more challenge and the existing SOC will not able to provide better security over the CIA. There are […]
The post Modern CyberSOC – A Brief Implementation Of Building a Collaborative Cyber Security Infrastructure appeared first on GBHackers On Security.
from GBHackers On Security http://blog.rafinia.info/2020/04/modern-cybersoc-brief-implementation-of.html
0 notes
Text
1 note
·
View note