#cve and ruby
Explore tagged Tumblr posts
Note
would you rather be too hot or too cold? and why?
___
Too cold! Being cold is how I feel usually, plus you can always get warmer, or aleast, it's easier
3 notes
·
View notes
Text
GitLab behebt kritische SAML-Authentifizierungsschwachstelle in CE- und EE-Editionen
GitLab hat Patches veröffentlicht, um eine kritische Sicherheitslücke in seinen Community Edition (CE) und Enterprise Edition (EE) Produkten zu schließen, die zu einer Authentifizierungsumgehung führen könnte. Der Fehler liegt in der Bibliothek “ruby-saml” (CVE-2024-45409, CVSS-Score: 10.0) begründet, die es einem Angreifer ermöglichen könnte, sich als beliebiger Benutzer innerhalb des…
0 notes
Text
Google Chrome 128 update Fixes 38 Security Issues
Chrome 128 (version 128.0.6613.85) is available with security updates and the Latest bug fixes. Today's release also includes new features including Isolated Web Apps, standardized CSS zoom support, new Attribution Reporting API features, CSS ruby-align property functionality, line-breakable Ruby support, and more. The latest release also addresses 38 security vulnerabilities.
To get the latest Chrome update download on your device select Menu > Help > About Google Chrome or load chrome://settings/help directly to run a manual update check. Chrome downloads and installs the new version then automatically. A restart of the browser is required.
If you are looking for Chrome offline installer get it here.
What’s new Chrome 128 update?
The latest Chrome release brings, several new features and bug fixes to enhance the browsing experience.
The Chrome 128 release brings several key features and improvements aimed at enhancing both security and usability. A notable addition is Isolated Web Apps, which strengthen protection against tampering and web server compromises, though this feature is currently limited to enterprise-managed ChromeOS devices. This builds on previous work with Progressive Web Apps (PWAs) and Web Packaging, offering a more secure browsing experience.
Another significant update is the standardization of the CSS zoom property. Previously, this property was non-standard, leading to inconsistent behaviour across different browsers. Chrome 128 now fully supports it, making it easier for developers to control the scaling of elements on a webpage. This update is part of Chrome’s broader effort to align with modern web standards.
The release also introduces enhancements to the Attribution Reporting API, which aids in measuring online ad effectiveness while respecting user privacy. Additionally, support for the ruby-align property and line-breakable Ruby annotations improve the presentation of East Asian typography on the web, making it easier to create accessible and visually appealing content.
For developers, Chrome 128 adds features like Promise.try, which simplifies asynchronous operations in JavaScript, and WebAuthn hints, which enhance the user experience during authentication. Additionally, support for WebGPU HDR has been introduced under a developer trial flag, enabling richer graphics for web applications.
Security remains a priority, with Chrome 128 addressing several vulnerabilities by fixing seven high-priority Common Vulnerabilities and Exposures (CVEs). These updates highlight Chrome’s commitment to maintaining a secure browsing environment.
source: https://windows101tricks.com/google-chrome/
0 notes
Text
Code injection vulnerability found in Elektra [CVE-2024-41961]

CVE number = CVE-2024-41961 CVSS Score = 9.6 Elektra is an opinionated Openstack Dashboard for Operators and Consumers of Openstack Services. A code injection vulnerability was found in the live search functionality of the Ruby on Rails based Elektra web application. An authenticated user can craft a search term containing Ruby code, which later flows into an `eval` sink which executes the code. Fixed in commit 8bce00be93b95a6512ff68fe86bf9554e486bc02. Read the full article
0 notes
Text
China and North Korea Intensify Cyber Campaigns with AI Assistance

The world of cyber threats is rapidly evolving, with nation-states like China and North Korea leveraging artificial intelligence (AI) to amplify their malicious operations. According to a recent report from the Microsoft Threat Analysis Center (MTAC), these countries are harnessing the power of AI to influence public opinion, sow discord, and generate revenue through cyber attacks.
China's AI-Powered Influence Operations
Chinese threat actors affiliated with the Communist Party are ramping up the use of AI-generated content on social media platforms. Their primary objective is to amplify controversial domestic issues and criticize the current administration in the United States and other countries. Stoking Discord and Spreading Disinformation The report highlights the activities of the group Storm-1376, which specializes in influence operations. This group has been spreading conspiratorial narratives about major incidents, such as the Hawaii wildfires in August 2023 and the Kentucky train derailment during the Thanksgiving holiday. They used AI-generated images and memes to make their content more eye-catching and disseminated it across multiple platforms in various languages. Furthermore, Storm-1376 aimed to stoke discord in East Asian countries by criticizing the Japanese government's decision to release treated radioactive wastewater into the Pacific Ocean. AI-generated memes and images were utilized to amplify these messages across social media platforms in Japanese, Korean, and English.

AI-Generated News Anchors and Sockpuppets The report also noted the growing use of AI-generated news anchors and sockpuppets by China-affiliated actors. These AI-generated anchors appeared in campaigns targeting Taiwanese officials in the lead-up to Taiwan's Presidential election in January 2024. Additionally, Chinese sockpuppets posing as US voters have been soliciting opinions on divisive domestic issues from American citizens. This tactic is believed to be a means of gathering intelligence and precision on key voting demographics ahead of the US Presidential election, to influence voters.
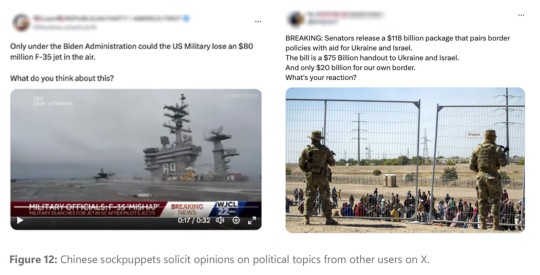
North Korea's Cyber Operations for Revenue and Intelligence
The MTAC report also sheds light on North Korea's cyber activities, which are primarily focused on generating revenue and collecting intelligence on perceived adversaries like the United States, South Korea, and Japan. Cryptocurrency Heists and Software Supply Chain Attacks North Korean hackers have stolen over $3 billion in cryptocurrency since 2017, according to Recorded Future's Insikt Group. This is part of the government's efforts to circumvent economic sanctions and fund its weapons program. Groups like Jade Sleet, Sapphire Sleet, and Citrine Sleet have been particularly active in targeting cryptocurrency targets since June 2023. North Korean threat actors have also heavily targeted the IT sector with spear-phishing and software supply chain attacks. For instance, the group Diamond Sleet exploited the TeamCity CVE-2023-42793 vulnerability in October 2023 to compromise hundreds of victims in various industries across the US and European countries. Geopolitical Intelligence Gathering and AI Experimentation Some North Korean cyber activities have had a geopolitical objective, such as countering the trilateral alliance between the US, South Korea, and Japan. Groups like Ruby Sleet, Emerald Sleet, and Pearl Sleet have frequently targeted organizations in sectors like government, defense, and media to collect intelligence on these countries. Moreover, North Korean actors are experimenting with AI large language models (LLMs) to enhance their operations. Microsoft and OpenAI observed Emerald Sleet utilizing LLMs to improve spear-phishing campaigns targeting Korean Peninsula experts. As the use of AI in cyber threats continues to evolve, governments, organizations, and individuals must remain vigilant and implement robust cybersecurity measures to combat these advanced threats. Read the full article
0 notes
Quote
これ、Ruby 3.0 と 3.1 のみが対応というのは nobu が 3.2 の開発中に直していて「おい、脆弱性なんだから勝手に直すなよ」というのを後追いで CVE を割り当てたという裏話が実はあるのでここに書いておきます。
CVE-2024-27280 を公開した, CVE-2024-27281 を公開した, 洗濯洗剤を 3kg 買った - HsbtDiary(2024-03-21)
0 notes
Text
This Week in Rust 460
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tweet us at @ThisWeekInRust or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Security advisories for Cargo (CVE-2022-36113, CVE-2022-36114)
Foundation
Rust Foundation Establishes Security Team to Support and Advance Rust Programming Language
Newsletters
Rust Nigeria Issue #9
Project/Tooling Updates
rust-analyzer changelog #146
IntelliJ Rust Changelog #178
A byte string library for Rust
Pomsky 0.7 released
Slint weekly updates (The GUI framework)
Fang 0.9 - new version of the background processing framework for rust
Fornjot (code-first CAD in Rust) - Weekly Release - 2022-W37
This week in Databend #59: A Modern Cloud Data Warehouse for Everyone
HexoSynth 2022 - Devlog #12 - Documentation for me and you
Observations/Thoughts
You Can't Do That: Abstracting over Ownership in Rust with Higher-Rank Type Bounds. Or Can You?
Security and Correctness in Wasmtime
Attacking Firecracker: AWS' microVM Monitor Written in Rust
&stress about &Strings
A pair of Rust kernel modules
GNU ld Discards Section Containing Code – Section Flags are Important for ELF Files
Use Rust to Reduce the Size of Your SQLite Database
[video] Coroutines: C++ vs Rust - Jonathan Müller - C++ on Sea 2022
[video] Rust on Rails (write code that never crashes)
[video] Let's Code Asteroids in Rust with a First-Time Bevy User
[video] Linux Plumbers Conference 2022 - Rust MC
[video] [series] Rust Day on Google Open Source Live
Rust Walkthroughs
Kernighan software tools in rust
Speeding up incremental Rust compilation with dynamic libraries
Learning Rust by implementing a SHA-1 hash cracker
Chat Blast! A TCP chat server in Rust
Concurrency in RustDb
Beginners guide to Solana NFTs in Rust.
STM32F4 Embedded Rust at the HAL: DMA Controllers
Miscellaneous
[FR] Rejoignez la communauté Rust (et devenez un "rustacé")
[DE] Moderne Spieleprogrammierung mit dem Entity Component System und der Engine Bevy
[DE] Programmieren mit Rust für den FreeBSD-Kernel
Crate of the Week
This week's crate is bstr, a fast and featureful byte-string library.
Thanks to 8573 for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but didn't know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
Ockam - Support TCP keepalive for TCP clients
Ockam - Show ockam command help in $PAGER or less (clap based)
Ockam - Implement ockam reset clap command
lib3mf - Help compiling the upstream C++ library on Windows
Artichoke Ruby - Help migrate more path helpers out of its monolith into a support crate.
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
324 pull requests were merged in the last week
initial implementation of return-position impl Trait in traits
check that the types in return position impl Trait in traits are well-formed
deny return-position impl Trait in traits for object safety
only encode return-position impl Trait in trait when parent function has a default body
implement std::marker::Tuple, a marker trait for tuples
add inline-llvm option for disabling/enabling LLVM inlining
stabilize raw-dylib for non-x86
equate fn outputs when inferring RPITIT hidden types
allow generators to impl Clone/Copy
avoid infinite loop in function arguments checking
const_generics: correctly deal with bound variables
fix LLVM IR type mismatch
fix ICE in opt_suggest_box_span
fix ICE report flags display
fix ICE, generalize 'move generics to trait' suggestion for >0 non-rcvr arguments
fix RPIT ICE for implicit HRTB when missing dyn
fix code generation of Rvalue::Repeat with 128 bit values
fix compile errors for uwp-windows-msvc targets
normalize before erasing late-bound regions in equal_up_to_regions
recover from using ; as separator between fields
fix the suggestion of format for asm_sub_register
adjust and slightly generalize operator error suggestion
add list of recognized repr attributes to the unrecognized repr error
shrink span for bindings with subpatterns
point at type parameter in plain path expr
point out when a callable is not actually callable because its return is not sized
allow lower_lifetime_binder receive a closure
do not suggest a semicolon for a macro without !
include enum path in variant suggestion
suggest adding array lengths to references to arrays if possible
suggest introducing an explicit lifetime if it does not exist
suggest pub instead of public for const type item
suggest removing unnecessary prefix let in patterns
migrate another part of rustc_infer to session diagnostic
migrate rustc_middle diagnostic
migrate rustc_session to use SessionDiagnostic - Pt. 2
miri: add a Machine hook for inline assembly
shrink PredicateS
shrink hir::Ty and hir::Pat
parameterize ty::Visibility over used ID
allow lint passes to be bound by TyCtxt
track PGO profiles in depinfo
use RelocModel::Pic for UEFI targets
use niche-filling optimization even when multiple variants have data
inline <T as From<T>>::from
lower the assume intrinsic to a MIR statement
compile spin_loop_hint as pause on x86 even without sse2 enabled
reimplement carrying_add and borrowing_sub for signed integers
optimize thread parking on NetBSD
remove &[T] from vec_deque::Drain
the <*const T>::guaranteed_* methods now return an option for the unknown case
use futex-based locks and thread parker on Hermit
hashbrown: add HashSet::raw_table
hashbrown: add RawTable::is_full
git2: implement IntoIterator for Statuses
codegen_gcc: simd: impl extract_element for vector types
cargo: specify the max length for crate name
rustdoc: avoid cleaning modules with duplicate names
rustdoc: correcty handle intra-doc-links to items without HTML page
rustdoc: more accurate struct type
rustdoc: store Variant Fields as their own item
clippy: do not expand macro in nonminimal_bool suggestions
clippy: don't lint large_stack_array inside static items
clippy: don't panic on invalid shift while constfolding
clippy: fix FormatArgsExpn parsing of FormatSpec positions
clippy: fix range_{plus,minus}_one bad suggestions
clippy: fix hang in vec_init_then_push
clippy: rename the arithmetic lint
clippy: suggest unwrap_or_default when closure returns "".to_string
clippy: use visit_expr_field for ParamPosition
clippy: use macro callsite when creating Sugg helper
clippy: make Arithmetic consider literals
clippy: assertions_on_result_states: fix suggestion when assert! is not in a statement
rust-analyzer: add config to unconditionally prefer core imports over std
rust-analyzer: build release artifact against older glibc
rust-analyzer: filter imports on find-all-references
rust-analyzer: new assist: move_format_string_arg
rust-analyzer: remove the toggleInlayHints command from VSCode
rust-analyzer: use proc-macro-srv from sysroot in rust-project.json workspaces
rust-analyzer: make clicking a closing brace inlay hint go to the opening brace
rust-analyzer: add semicolon completion to mod
rust-analyzer: handle lifetime variables in projection normalization
rust-analyzer: handle trait methods as inherent methods for trait-related types
Rust Compiler Performance Triage
From the viewpoint of metrics gathering, this was an absolutely terrible week, because the vast majority of this week's report is dominated by noise. Several benchmarks (html5ever, cranelift-codegen, and keccak) have all been exhibiting bimodal behavior where their compile-times would regress and improve randomly from run to run. Looking past that, we had one small win from adding an inline directive.
Triage done by @pnkfelix. Revision range: e7cdd4c0..17cbdfd0
Summary:
(instructions:u) mean range count Regressions ❌ (primary) 1.1% [0.2%, 6.2%] 26 Regressions ❌ (secondary) 1.9% [0.1%, 5.6%] 34 Improvements ✅ (primary) -1.8% [-29.4%, -0.2%] 42 Improvements ✅ (secondary) -1.3% [-5.3%, -0.2%] 50 All ❌✅ (primary) -0.7% [-29.4%, 6.2%] 68
11 Regressions, 11 Improvements, 13 Mixed; 11 of them in rollups 71 artifact comparisons made in total
Full report here
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
De-RFC: Remove type ascription
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
Rust Style Team
RFC: Statics in patterns
Tracking Issues & PRs
[disposition: close] Loosen shadowing check inside macro contexts (attempt 2).
[disposition: merge] Tracking issue for std::hint::black_box
[disposition: merge] Commit to safety rules for dyn trait upcasting
[disposition: merge] Tracking Issue for constifying some {BTreeMap,Set} functions
[disposition: merge] Tracking Issue for Option::unzip()
[disposition: merge] Tracking issue for map_first_last: first/last methods on BTreeSet and BTreeMap
[disposition: merge] Make Sized coinductive, again
[disposition: merge] Neither require nor imply lifetime bounds on opaque type for well formedness
[disposition: merge] Make typeck aware of uninhabited types
[disposition: merge] Stabilize let else
[disposition: merge] Fix #[derive(Default)] on a generic #[default] enum adding unnecessary Default bounds
New and Updated RFCs
No New or Updated RFCs were created this week.
Upcoming Events
Rusty Events between 2022-09-14 - 2022-10-12 🦀
Virtual
2022-09-14 | Virtual (Boulder, CO, US) | Boulder Elixir and Rust
Monthly Meetup
2022-09-14 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
Introduction to Async in Rust
2022-09-14 | Virtual (Malaysia)| Golang Malaysia
Rust Meetup September 2022
2022-09-15 | Virtual (Columbus, OH, US) | GDG Columbus
Past, Present, and Future of Internet Money! (Custom tokenomics, RUST and CosmWASM library...)
2022-09-15 | Virtual (Stuttgart, DE) | Rust Community Stuttgart
Rust-Meetup
2022-09-20 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful: Bencher—Catch Performance Regressions in CI—Everett Pompeii
2022-09-21 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out (Call for Participation)
2022-09-22 | Virtual (Charlottesville, VA, US) | Charlottesville Rust Meetup
Rust based Bluetooth tools (BlueR) you can use today
2022-09-22 | Virtual (Tehran, IR) | Iran Rust Meetup
Rust Iran Meetup #9 - Let's Write An Async Executor
2022-09-23 | Virtual (Tokyo, JP) | Rust Tokyo
Rust Tokyo 2022
2022-09-27 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2022-09-28 | Virtual (London, UK) | Rust London User Group
Rust (Hybrid) Hack & Learn September 2022
2022-10-04 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2022-10-05 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2022-10-05 | Virtual (Stuttgart, DE) | Rust Community Stuttgart
Rust-Meetup
2022-10-06 | Virtual (Nürnberg, DE) | Rust Nuremberg
Rust Nürnberg online #18
2022-10-08 | Virtual | Rust GameDev
Rust GameDev Monthly Meetup
2022-10-12 | Virtual (Boulder, CO, US) | Boulder Elixir and Rust
Monthly Meetup
2022-10-12 | Virtual (San Francisco, CA, US) | Microsoft Reactor San Francisco
Getting Started with Rust: Building Rust Projects
Europe
2022-09-15 | Paris, FR | Rust Paris
Rust Paris meetup #52
2022-09-27 | Nijmegen, NL | Rust Nederland
Regular track: Rust at RU
Student track: Rust at RU
2022-09-28 | London, UK + Virtual | Rust London User Group
Rust (Hybrid) Hack & Learn September 2022
2022-09-29 | Amsterdam, NL | Rust Developers Amsterdam Group
Fiberplane Rust Workshop
2022-09-29 | Copenhagen, DK | Copenhagen Rust group
Rust Hack Night #29
2022-09-29 | Enschede, NL | Dutch Rust Meetup
Going full stack on Rust
2022-10-02 | Florence, IT + Virtual | RustLab
RustLab Conference 2022 (Oct 2-4)
2022-10-03 | Stockholm, SE | Stockholm Rust
Rust Meetup @Microsoft Reactor
2022-10-12 | Berlin, DE | Rust Berlin
Rust and Tell - EuroRust B-Sides
North America
2022-09-14 | Austin, TX, US | Rust ATX
Rust Lunch
2022-09-20 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2022-09-22 | Lehi, UT, US | Utah Rust
Game Prototyping with Rusty Engine with Nathan Stocks and Food!
2022-09-29 | Ciudad de México, MX | Rust MX
Nuestra RustMX comunidad tiene página
Oceania
2022-09-14 | Sydney, NSW, AU | Rust Sydney
Rust-Sydney Lightning Talks
2022-09-20 | Phillip, ACT, AU | Canberra Rust User Group
September Meetup
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
In Rust We Trust
– Alexander Sidorov on Medium
Thanks to Anton Fetisov for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
0 notes
Text
[Media] CVE-2023-23752
CVE-2023-23752 Simple program for joomla CVE-2023-23752 scanner, This is a simple Ruby script that checks if a list of targets is vulnerable to CVE-2023-23752, a critical security vulnerability in a web application. The script sends a HTTP GET request to a specified endpoint, and extracts information from the response to determine if the target is vulnerable. https://github.com/z3n70/CVE-2023-23752

1 note
·
View note
Text
CVE-2022-31163: Arbitrary file execution in TZinfo (Ruby)
https://github.com/tzinfo/tzinfo/security/advisories/GHSA-5cm2-9h8c-rvfx Comments
0 notes
Link
#vulnerability#RCE#Metasploit#Nmap#Powershell#CVE-2022-21907#CVE-2022-2190#Exploit#Dos#Ddos#Hacking#Microsoft#Bugbounty#RemoteCodeExecution
0 notes
Note
the start of many questions… yippie!
let’s start with basics.
what’s your most favorite color? or top three favorite colors?
___
Okay my fav color is red, specially maroon. It reminds me of myself and it's a very gothy color
I also really like purple and black! Gothy colors and I think I look okay in them
3 notes
·
View notes
Text
Connect A Webcam For Osx In Vmware

Using VMware Horizon Client for Mac OS X provides information about installing and using VMware Horizon™ Client™ software on a Mac to connect to a remote desktop or application in the datacenter. This information is intended for administrators who need to set up a View deployment that includes Mac. I'm having an issue trying to get my SR300 to work in a virtual environment (VMware Fusion v8.1.1). I'm using a MacBook Pro (Retina, 13-inch, Mid 2014) which has 2 x USB3.0 ports. When I connect the SR300 to my Mac (running OSX 10.11.2) the device shows up on the internal USB3.0 hub as 'Intel RealSense (TM) Camera SR300. Connecting Webcam in VMware OS X machine Hi guys, I was wondering if anyone had any luck connecting their built in webcam for use in OS X Sierra 10.12? Im currently using a Asus q325 I7-7700U with 16gb ram and intel 620 HD graphics.
Meterpreter Updates
This is a big week for Meterpreter. For starters, we've landed a new Meterpreter Python payload. Yes, yes, I know, you thought that Metasploit was all Ruby all the time, but this and the Python payloads for bind shells from Spencer McIntyre should help out on advancing the state of Meterpreter by leaps and bounds. Despite Metasploit's massive Ruby footprint, most security developers know Python well enough to scratch their own penetration testing itches in it, so I'm looking forward to a lot of active development here. Plus, since Python is part of the Linux Standard Base, you're quite likely to find it on pretty much any normal Linux distribution, so it should see a lot of use for non-Microsoft targets.
In other Meterpreter news, we have a new contributor entering the fray on the Windows 32-bit and 64-bit side by the name of OJ Reeves. His entire mission in life (at least, for now) is to make it much easier for normal humans to compile, test, and extend Meterpreter for Windows platform. If you've been down this hacking Meterpreter path in the past, you know what kind of pit vipers can be lurking in that code, so expect to see some massive improvements there in the next couple weeks.
VMWare Setuid Exploit (CVE-2013-1662)
This week also sees a new local privilege exploit targeting Linux, the VMWare Setuid vmware-mount Unsafe popen(3) module (aka, vmware-mount.rb). Discovered by Google's Tavis Ormandy and implemented by our own James Egypt Lee, this exploits a setuid vulnerability that takes advantage of a VMWare installation to sneak a root shell. Egypt discusses the Metasploit implementation at length in this blog post, so I encourage you to check it out. Note that this module does not enable attackers to escape from the VMWare guest to the host operating system; it's specifically useful for taking advantage of a VMWare installation to elevate privileges on the host OS itself.
More OSX Hijinks
The other set of modules I want to hilight is a trio from Rapid7's Joe Vennix: the OSX Capture Userspace Keylogger module, the OSX Manage Record Microphone module, and the OSX Manage Webcam module. As you can probably guess by their titles, these are all post-exploit modules penetration testers can exercise to extend their eyes and ears into the site under test. These kind of Hollywood-hacker style post-exploit tricks are exactly the kind of thing that great to demo to clients to help explain the true risk associated with Apple desktop / laptop bugs, since they are, by their nature, pretty dramatic and fun to use.
Tab Assassin
Finally, this week, we're going to be pulling the trigger on the great retabbing of Metasploit in order to bring us up to the normal, regular coding standards common to Ruby projects. While I have every expectation this change will be traumatic for long-time contributors, we're faithfully document everything along the way under the shortlink http://r-7.co/MSF-TABS. If you have patches and pull requests that are suddenly thrown into a conflicted state this week, the retabbing from @Tabassassin (pictured right) is probably the root cause. But never fear, just read the fine material regarding the change, and you should be back into an unconflicted state in two shakes.
New Modules
We've got eleven new modules this week. Including the ones mentioned above, we've got another three ZDI-derived exploits (which are always informative), a really nicely commented implementation of the MS13-059 exploit for Internet Explorer, and a pair of Windows post modules that can be used to further extend control over the victim machine. As always, thanks everyone for your contributions!
Connect A Webcam For Osx In Vmware Software
Exploit modules
VMWare Setuid vmware-mount Unsafe popen(3) by egyp7 and Tavis Ormandy exploits CVE-2013-1662
SPIP connect Parameter PHP Injection by Arnaud Pachot, Davy Douhine, and Frederic Cikala exploits OSVDB-83543
HP LoadRunner lrFileIOService ActiveX Remote Code Execution by juan vazquez and rgod exploits ZDI-13-182
HP LoadRunner lrFileIOService ActiveX WriteFileString Remote Code Execution by juan vazquez and Brian Gorenc exploits ZDI-13-207
Firefox XMLSerializer Use After Free by juan vazquez and regenrecht exploits ZDI-13-006
MS13-059 Microsoft Internet Explorer CFlatMarkupPointer Use-After-Free by sinn3r and corelanc0d3r exploits MS13-059
Auxiliary and post modules
OSX Capture Userspace Keylogger by joev
OSX Manage Record Microphone by joev
OSX Manage Webcam by joev
Windows Gather Prefetch File Information by TJ Glad
Windows Manage Set Port Forwarding With PortProxy by Borja Merino
Connect A Webcam For Osx In Vmware
If you're new to Metasploit, you can get started by downloading Metasploit for Linux or Windows. If you're already tracking the bleeding-edge of Metasploit development, then these modules are but an msfupdate command away. For readers who prefer the packaged updates for Metasploit Community and Metasploit Pro, you'll be able to install the new hotness today when you check for updates through the Software Updates menu under Administration.
Connect A Webcam For Osx In Vmware Download
For additional details on what's changed and what's current, please see Brandont's most excellent release notes.

0 notes
Text
Crucible 4.6 Release Notes
We're proud to present Crucible 4.6 with some long-awaited features, and many smaller improvements.
Get the latest version
Linking reviews to multiple Jira issues
It’s a good practice to keep code changes small—raise a Jira issue, create a branch in Bitbucket, implement the changes, and finally review the code in Crucible. However, it’s not always the case. What if you’re working on a feature that requires changes in multiple components or services, stored in different source code repos? Or, you need to merge a bugfix branch into another release branch, and review the entire thing before merging?
Luckily, Crucible deals with such a scenario very well, as you can add changes from multiple sources of data - branches, commits, patches - into a single code review. But, what if each component has its own development cycle and a separate Jira project and issue key? What if the branch contains commits from many different bugfixes?
Until now, you could link a Crucible code review to only one Jira issue, and had to pick which is "the most important" one.
With Crucible 4.6, you can link a code review to any number of Jira issues, you no longer need to pick just one. Crucible will also show you a list of suggested issues for linking, based on the review content. The code review will be shown in Jira Development Panel under every linked issue, so you get a full traceability between all your issues and reviews.

We've also improved logging the time spent on code reviews. You can either choose a single issue to report the whole time, or split it between multiple linked issues. Crucible tracks the time spent on reviews automatically, but with version 4.6 you can also adjust the time manually, and enter a comment that will be reported to Jira when completing or closing the review.

Blame fallback cache
Remember the time when you wanted to see blame data for a file, and had to wait minutes until it finally appeared? Over and over again whenever you returned to the file?
Crucible calculates and persists blame data during repository indexing. However, if the indexing is not complete or if a system admin disabled storing of blame data, Crucible has to contact the source code management system (SCM) to fetch actual data. For slow repos, it might even take several minutes.
With Crucible 4.6, we’ve introduced an additional in-memory cache for this scenario. Thanks to it, you��ll need to wait only for the first blame request. When you go back to the file and click blame again, you’ll get an immediate response.
Mercurial 4.5 support
Crucible 4.6 supports Mercurial 4.5.
Git 2.16, 2.17, and 2.18 support
Crucible 4.6 supports three new major Git versions.
Other improvements
New Fisheye and Crucible logos with a brighter blue navigation bar, the latest PostgreSQL JDBC driver, and a number of security fixes are yet another reasons to upgrade to the latest version.
Get the latest version
API changes
REST and Java APIs have been enhanced to handle multiple issues in a review. Also some deprecated methods have been removed, so your apps may require an update. Please read Crucible upgrade guide for more details.
Change log
This section will contain information about the Crucible 4.6 minor releases as they become available. These releases will be free to all customers with active Crucible software maintenance.
If you are upgrading from an earlier version of Crucible, please refer to the Crucible upgrade guide.
The issues listed below highlights some of the bugs resolved in Crucible 4.6.x.
Issues in Release
Story: Upgrade analytics-plugin to 5.4.4
New Feature: As a user, I would like ruby added as a supported language for the code blocks macro
Improvement: Support for Shell syntax highlighting in Crucible review comments
Improvement: Suppprt for C++ in Crucible review comments
Improvement: Support for Python syntax highlighting in Crucible review comments
Improvement: Source-code Formatter with perl support.
Epic: Allow to link a review to multiple jira issues
Fixed: The bundled Atlassian Universal Plugin Manager plugin had a XSS issue - CVE-2018-5229
Fixed: The bundled atlassian-http library had a content spoofing issue - CVE-2017-18103
Fixed: XSS in the review attachment resource - CVE-2018-13388
Fixed: No Create Issue link displayed in Crucible review comments
Fixed: XSS through header injection in the /browse/~raw resource - CVE-2018-5228
Fixed: The bundled Atlassian Application Links plugin had various XSS issues - CVE-2018-5227
Fixed: Argument injection through Mercurial repository uri handling on Windows - CVE-2018-5223
Fixed: Improper authorization vulnerability in SnippetRPCServiceImpl allowing user's to comment on snippets they are not authorised to access - CVE-2017-18095
Fixed: BoneCP connections are not returned to the pool
Fixed: Missing permission check in review coverage REST endpoint - CVE-2017-18035
Fixed: XSS via wiki markup
Fixed: XSS in the source browser resource through malicious branch names - CVE-2017-18034
Fixed: Workflow triggers in JIRA configured for Crucible related actions don't transition issues
Fixed: "a/, "b/" prefixes aren't recognized in "hg diff -r" format when adding patch
Fixed: Patch reviews from mercurial diffs don't anchor to their repository unless using --nodates argument for hg diff
Source
2 notes
·
View notes
Text
0 notes
Text
18 de Agosto, 2020
Internacional
Vulnerabilidad de ejecución remota en Javascript

Los atacantes podrían aprovechar una vulnerabilidad de seguridad revelada recientemente que se encuentra en el paquete serialize-javascript NPM para realizar la ejecución remota de código (RCE). Rastreada como CVE-2020-7660, la vulnerabilidad en serialize-javascript permite a atacantes remotos inyectar código arbitrario a través de la función deleteFunctions dentro de index.js. Las versiones de serialize-javascript inferiores a 3.1.0 se ven afectadas. Es una biblioteca popular con más de 16 millones de descargas y 840 proyectos dependientes. Si un atacante puede controlar los valores de "foo" y "bar" y adivinar el UID, sería posible lograr RCE.
E.@. CVE-2020-7660 recibió una puntuación de gravedad CVSS de 8.1, dentro del rango 'importante' y al borde de 'crítico'. Sin embargo, en un aviso de Red Hat sobre la vulnerabilidad, la organización ha degradado el problema a 'moderado', ya que las aplicaciones que utilizan serialize-javascript deben poder controlar los datos JSON que pasan a través de él para que se active el error.
Red Hat señala que las versiones compatibles de Container Native Virtualization 2 no se ven afectadas, pero las versiones heredadas, incluida la 2.0, son vulnerables. Se emitieron correcciones para OpenShift Service Mesh 1.0 / 1.1 (servicemesh-grafana) y está en camino un parche para Red Hat OpenShift Container Platform 4 (openshift4 / ose-prometheus). Debido a la popularidad del paquete, otros repositorios también se ven afectados, incluido el Webpacker de Ruby on Rails.
El domingo (16 de agosto) se emitió una solución para resolver la rama estable, utilizando una versión vulnerable de serialize-javascript. La vulnerabilidad está parcheada en serialize-javascript versión 3.1.0 y ha sido resuelta por los colaboradores mediante cambios en el código, lo que garantiza que los marcadores de posición no estén precedidos por una barra invertida.
Fuente
0 notes
Text
[Media]
CVE-2022-36231 The ruby gem pdf_info An attacker using a specially crafted payload may execute OS commands by using command chaining. https://github.com/affix/CVE-2022-36231 #cve

0 notes