#but the idea that it made the server WORSE. and that it was a 0/10 arc is act crazy . like truly the exile arc was gen really great like i
Explore tagged Tumblr posts
Text

anons crazy 4 this one im not sorry. like truly calling it a ZERO out of TEN arc. u must be crazy im not sorry
#listen im a ctommy swords and shields and i dont Love how he's portrayed in a lot of fanon#but the idea that it made the server WORSE. and that it was a 0/10 arc is act crazy . like truly the exile arc was gen really great like i#gen think it was . so well done#also to say that it wasn't worth the discourse surrounding it.#girl its minecraft roleplay. theres gonna be stupid discourse no matter what. like truly#name one arc or even one singular at least mildly popular server that doesn't have stupid asf discourse#like OBVIOUSLY people were dumb about it. that doesnt mean it shouldnt exist.#like the idea of saying that a huge narrative arc shouldnt exist because some audience members couldnt handle it correctly.#like okay sure lets never talk abt anything even remotely nuanced ever again in media. that will fix it.#like ofc some people handled the exile arc poorly. people can't even handle rose quartz#.hellwurld#dsmp#tommyinnit#exile arc#discourse#maybe#idk#im not saying that anon is stupid btw im just saying that im smarter /JOKE.#whatever its the dsmp its fandom its fine that we have differing opinions just know that im right and youre wrong
20 notes
·
View notes
Text
coa one year later & self-reflection
(*drags out a creaky metal chair and plops down on it heavily*)
Hi. It’s me, ya boi skinny--
Wait, wrong one. Do over.
Hi, it’s me, Kat, and I’m not dead. Clearly. Today being one year anniversary of COA has kinda put me in a reflective mood, so I guess I decided to sit down and just...talk about some things, thoughts and feelings I’ve been bottling inside for a hot sec. Especially given how radio silent I have gone on here and people deserve a bit of perspective.
And before anyone starts worrying, it’s all good, and I’m still around and currently in good health for the most part.
So, let’s take it back to the start. Regardless of how dramatic it may sound, we need to go back a year for that.
By technicality alone, COA actually turned one year old on October 12th. That’s when the first part was posted. However, the reason I’m treating today as the aforementioned birthday is simple: I had no intention of this story ever being more than a short two-parter. I told this to the discord gang already but COA was only going to have two parts. V was going to die in Tokyo and the rest of the story follows glimpses of John throughout the movies and it’s her ghost that haunts him. Skipping ahead, it was going to have a bittersweet ending of John eventually dying, having completed his task, only to be greeted by V, Daisy and Helen in the afterlife. A peace of sorts. Then, I realised that, well, no. I have more to say on this world and intrigue about this placeholder character V kept growing.
November 1st happened and I made a very last minute call to continue COA but with the added pressure of doing it during NaNoWriMo 2019. And boy did I. Most of the story was figured out during that very intense month. I posted Part 2 on this day a year ago because I was so eager to share it. Perhaps, in retrospect, a bit too eager.
For those of you who may not know this, I work as a writer full time for my actual every day job. I’m the main writer for an original webcomic called In the Bleak Midwinter on Webtoon.com and have been for almost two years now. Getting what is essentially your dream job is amazing. I’m very lucky on that front but it also taught me stark realities of having your job and only hobby overlap. It’s a dangerous creative mix. Especially because I was not used to being constraint in what I create or the feeling like I have to please anyone else. Writing as a job is a whole other avenue of creative exhaustion. I love my job a lot and am very, very lucky to have it but it doesn’t change the fact that those initial stages made me fall back on COA a lot for creative freedom that I craved so desperately. To an unhealthy degree looking back on it now.
But going back to November last year. NaNo time. I did it. Finished on the 24/25th I believe. A juicy final count of 52k+. All while maintaining a weekly update schedule for a fic that usually hit around 10k per update, if not more, even during those early days. Add writing an original story on top of that. Writing every day for hours on end (we are talking 10-12hr days) without any time for other hobbies or time for myself in general. I kept pushing and pushing and pushing. Losing weight and sleep in the process. I think the thing that convinced me that I should continue doing so is the fact that the outpour of support for COA ended up surpassing anything I ever expected or even dared to hope for. I’m not a huge numbers person but the outpour of love and just sheer investment in the story and characters blew me away. John Wick fandom is on the smaller side and has been going through downtime when I posted COA so my expectations were...well, small tbh. I like keeping expectations low to avoid any disappointments in general. But I’ve also always had an issue of being a massive 0 or 100 kind of person. If I love something, it consumes me. In this case, it brought me as much joy and freedom as much as it was steadily pushing me towards the ultimate crash.
That being said, I can’t thank you all enough for every comment, like, reblog and message and fanart. You’re the reason I got this far. With your support. It brightened some really dark days for me.
But.
To be frank, it’s never been about you guys. I never wrote or pushed because I felt like I had to appease anyone. That creative mindset is pure poison and I long since learned to let go of it. I kept pushing and kept working myself to the bone because I liked it. I liked how reading peoples’ responses made me feel. I liked the addictive nature of reading all the comments and theories after an update. I loved the idea of brightening peoples’ days and giving them something to cheer them up after what might have been a shitty day. Even if that was at expense of my own time/well being. But for a long time, it wasn’t. I love writing a lot but facts remain facts.
It was beyond unhealthy and burnout wasn’t a question of if but when and that when was approaching at neck-breaking speed.
So we come to the end of November. Part 4 has just come out. People were invested and I was invested alongside them. I was just finishing up Part 5 which (back then) was the biggest single chapter I’ve ever written and god I still recall my sheer dread because that was the beginning of Santino being established as a LI. Looking back on that now, it’s downright hilarious how worried I was about the reception of him and V together after John.
So honestly, I hit burnout at around Part 8. Because that’s the first time I recall struggling with writing a chapter. Part 8 came out on December 28th. I had a brief break for holidays. But my mistake was not taking longer back then. Because I continued writing with a barely healed burnout. Followed by almost a year of struggling and continuously creating through that state. It wasn’t like I eased off the pressure, either. Oh, no. The chapters grew in size, the world and the characters with it. AUs amassed quickly and while I adore every single one - again, I didn’t know how to pace myself well enough.
I’m spiteful though. The more the chapters struggled the more I pushed against the burnout. By the time Chicago arrived, however, I knew I was in trouble. I ended up writing 43k+ in a span of 2 months, I believe. And while to some it may not seem like a lot given the time frame, it’s a lot when you’re burnout to a crisp & writing an original story for work + deadlines. Which I was burned out and then some. Chicago was something I was looking forward to writing for months. I have built it up since Part 4. It was a long time coming. So while I’m still proud of it, I would be lying if I said that some scenes were not sacrificed for the sake of keeping to my invisible schedule that no one but me actually cared about. You guys have always been patient. I never felt pushed into anything. It’s always only ever been me doing the harm.
Chicago was the downwards spiral for me mentally. I felt like I was failing to live up to my own expectations. That people were drifting away from it. I was plagued by the thought that the story I poured so much into was falling apart and growing weaker. Which this has always been an issue with me: I am my own harshest critic. Always have been. In fact, I’m a downright mean little fucker when it comes to just tearing at myself. I know writing is for fun - and it is - but I still like the idea of being proud of my work which only made everything worse despite the love each update received.
This takes us to the beginning of June. Specifically, June the 2nd. Or, as I like to call it: Kat Makes Another Impulsive Decision but This One Actually Works Out For the Better. On this day, I created the COA Discord server. And damn, I’m not sure what exactly I was expecting when I did ngl. I did it for fun and as an escape more so than anything. But somehow it ended up being the best decision I made in a long while. I know some of you are reading this. So love you lots, dorks. It’s such a privilege to be able to call so many of you my friends even outside of COA now. That little community has given me some of the best memories from this year and helped me to crawl out of my own metaphorical pit I was stuck in. Mentally, I’m doing much better than I did beginning of this summer. Which could be summed up as a constant self-hatred cycle and a feeling of inadequacy.
That, however, does not mean my burnout magically disappeared. If anything Chapter 17 just put a nail in the coffin so to speak. 2020 has been a shitty year just across the board for obvious reasons I don’t need to go into here but that can only partially be attributed to my mental state. Chapter 17 was...exhaustive. To say the least. But I was determined to stick with my vision and not split it up. I was also starting to be a bit more forgiving towards myself in terms of how long I may take to write it thanks to guys on discord though the feeling of failure and worry never quite faded fully. I’m proud of Part 17. Truly. But that was also when I hit rock bottom creatively on COA. It drained me completely.
I tried writing Part 18 for weeks after, day in and day out, not getting past the first scene and hating every word I wrote. So I took a deep breath and stopped. Figured I let it marinate and wait instead of trying to piece one of the most crucial chapters in this story like some Frankenstein monster two sentences at the time.
So my solution was simple: give myself some distance from it and write other things. Get my spark back. Of course that’s always a good idea. Having multiple creative escapes is the best thing you can do for yourself creatively. There was just one tiny little problem.
I was still burned out. Still am. The problem went deeper than just being burned out over COA. I was burned out over writing itself.
Which is an issue for a person who only has writing as a creative outlet.
I don’t have any other way to express myself. So I was stuck in a runt, trying to write because it’s the only thing that makes me genuinely happy even when I really shouldn’t have. And let me tell you. It’s a shitty fucking feeling. My burnout worsened. I had a thousand ideas but every time I tried to get them down it felt forced, fragmented, and weak. Repetitive and dry. Now, this is also in part because English isn’t my native language, so my vocab is limited as a result, but I hit that sweet rock bottom in that regard, too.
So, I worked on V (but in her OC form Clara), Lucien and The Elites. All those characters have grown so much since you last read about them. I have multiple original projects planned down the line that will feature all of them existing in their own world, with their own stories and no longer constrained by JW canon.
Which, finally, takes us to the end of October and beginning of November 2020.
I was convinced that the best course of action was to do NaNo again but with an original story this time (involving V). Suffice to say, it took a grand total of maybe 5-6 days and hating every second of writing it while also feeling like this project I’m so passionate and excited to write (still am) is just...going down the toilet to be blunt, to realise I may have made the wrong call.
Still, the stubborn ass that I am, I pushed through. Convinced I can get into it if I just keep going. The realizations that I am sharing with you right now won’t have been possible if it hadn’t been for a rather curious turn of events about a week and a half ago.
I recently bought a gaming laptop, all in preparation for Cyberpunk 2077 dropping ofc. But, in the meantime, I kept recommending a game to a friend on the COA server. That game? Far Cry 5. (It’s a blast to play btw, just a side note.) And playing it brought back all the feelings of nostalgia from the days when I used to write for that fandom. So I revisited some old work. Checked the stuff I never published and that has been sitting ducks in my docs for months and hoo boy. Let me tell you it was a vibe check of the worst kind.
The stark difference in the prose and the ease with which it flowed was...startling. It made me remember why I love writing so much and how proud I used to be of what I wrote back in the day. Which is not to say I’m not proud now, but it was just such a sharp dip in quality it was impossible to ignore.
So I didn’t.
I paused NaNo, moving it to another month. I paused writing for everything but work, which with our season coming to an end I will also get a rest from soon, too. I kinda paused in general. For the first time in a while, I finally forced myself to switch off. Rest.
The reason why I haven’t been on here is simple: guilt and not having energy to be on here. I like making my blog a safe space for everyone. Similar to escape it has become for me. I couldn’t pretend I was fine when I wasn’t. I felt obliged to perform and being here became exhausting. I haven’t been checking my inbox. Haven’t done much of anything except occasionally dropping by and reblogging a random post so people know I’m alive.
And that’s that, folks. That’s where I am currently. Resting. Completely exhausted mentally but resting. Getting my energy back.
So where does that leave us, huh? If you read this far, dunno what to tell you. Thanks, I suppose. It’s still odd to think people actually care about my existence sometimes.
I know what you’re likely thinking, too. So does this mean COA is never gonna be finished? What is gonna happen to it? Are you abandoning it?
The answer: no. 17 out of 25 chapters and 250k+ in, I’m too far in not to give it a proper conclusion. Not because I owe it to anyone other than myself. I want this story to be a stepping stone for my future as a writer. I want to prove to myself that I can get this done and finish it. As of right now (as you can no doubt tell with how long it’s been since last update) it’s on a soft hiatus while I rest. This rest? Not sure how long it may last. Right now, my plan is till mid December at which point I will reevaluate. Ideally, I finish the year with an update. But my New Year’s resolution is to finish COA. That timeline has become a little more murky now but, again, ideally it’s within the first quarter of 2021. Will that happen? I don’t know. And I don’t want to make false promises, either.
All I’m saying is that it will be done. I’m just no longer sure how long, exactly, it may take me to reach that Epilogue. I don’t expect many people to stick around for however long it may take me, but if you do, thank you. Truly. I really and deeply mean that.
So what’s on the cards for this blog in the meantime? Well, CP77 is coming out in under a month (if it doesn’t get moved again lmao rip) and I expect that to be my soft return to posting my writing on here again. We will see where the muse takes me, if at all. Regardless though, I’m excited.
One doctorate thesis later, here we are at the end of this really long rambling session. I hope that this has given you some perspective on things going on behind the scenes. I spared you some of the gorier details but I think this post has been long overdue. I suppose I, myself, was just too unwilling to face these things despite knowing about them deep down for a while now. I’m too self-critical not to notice but acting on correcting this behavior has been a whole other matter clearly.
Thank you for reading this post, my writing in general, and supporting me. I’m not going anywhere. I’m still around. More is on the way in the future. I’ll be seeing you all real soon. And all my love to all of you.
Love,
- Kat.
126 notes
·
View notes
Text
Thoughts on Powers of X #1
Well, I did this for the one, might as well do it for t’other...

Well, any thought that this mini-series might be less weird than its companion was completely blown away by the very first page, which revealed that Powers of X (pronounced Powers of Ten) is going to be taking place in four different times:
Year One (X^0)
Year Ten (X^1)
Year One Hundred (X^2)
Year One Thousand (X^3)
...with each segment increasing by a power of ten, because apparently Hickman has decided he’d like to drive us all mad with math puzzles. That first page is a doozy of design, I must say, laying out four key moments (and four or three key players) in the past and future of mutant-kind, with the layout suggesting a parallel between all of these characters (as well as a suggestion that the guy in the Cerebro mask shares Charles’ lower facial features exactly.
Year One
We then get an un-interrupted six page sequence which, on the surface, seems the most normal but is anything but. The first page shows Charles Xavier strolling through a fair and sitting down on a bench to enjoy the weather and his good mood, although the symbolic connection between the dwarf ringmaster and the strongman and Xavier’s dream of mutantkind is quite ominous. Then someone who looks a lot like Moira McTaggart sits down next to Xavier, and this is where x-fan’s expectations all of the sudden get flipped upside-down. On the face of it, Charles meeting Moira around the same time that he first has his Dream of mutant/human co-existence would be quite normal...except that Moira’s tarot cards are depicting people and places in the Year One Hundred (more on this in a bit), and Moira is talking to Charles very familiarly, but he hasn’t actually met her yet.
This is where a little alarum bell goes off in my mind shouting “TIME-TRAVEL SHENANIGANS!”
This much-hyped scene turns out to be Charles reading Moira’s mind, but it’s very clear from what we’ve just seen that this is not the Moira we know. And if this Moira is a clone from the future (I’ll get into that in a bit), the publicity tag-line would make sense: after all, time travel to avert a bad future goes way back in X-Men, and often that time travel has involved things happening to Charles Xavier before he could get his X-Men off the ground.
However, we’ve never see anyone go back just to tell Charles what happens in the future, even though that would profoundly change the timeline just by changing his mind. Is this what turns Charles Xavier into the be-helmeted man in Year Ten with the very different dream? Or would informing him of the future change or prevent the events of Year Ten?
Year Ten
Probably the most straightforward sequence - and the best argument for why HoX and PoX should be viewed as two halves of the same story - this sequence shows us exactly what happened to Mystique after she went through the Krakoa portal in Washington Square Park in HoX #1.
It turns out that, as much as even Magneto is feeling the “hope-y, change-y” vibes, he, Mystique, and Professor X all have their own agendas regarding the information - note the running theme of the issue - that she pulled out of Damage Control’s servers.
Further ominous notes: Charles Xavier has never been a telekinetic, and yet here he clearly uses telekinesis to grab Mystique’s thumb drive. That’s very ominous, especially given what we learn about cloned mutants have multiple, spliced-in mutant powers. Also, Professor X’s comment about “everyone who would live in...a better mutant world...owes something” echoes ominously with the interstitial material’s description of Omega class mutants as a natural resource for the state.
Year One Hundred
The most conventionally super-heroic segment, this section shows us an all-too familiar dystopian scenario, with cyborgized humans and cerberus-like sentinels working together to not merely kill mutants but violate their minds and bodies. Further signs of what they’ve been up to comes in the literally black-brained ex-Hound who was genetically designed for infiltration and subversion of her own people.
A sign that mutants have adapted to this conflict by abandoning moral principles as well comes in the fact that the dead mutant in question is not only programmed to mind-wipe on death, but is repeating Professor X’s speech from Year 10. In a parallel to that era, it turns out that the mutant group who’ve been interecepted were downloading information from the Nexus
We also meet our two main characters in this epoch - the red-skinned Nightcrawler lookalike Cardinal (whose Tarot card is the Devil, “the red god and the lost cardinal of the last religion” (no idea what that means)) and the metal-skinned Soulsword-slinging Rasputin (whose Tarot card is the Magician, “the metal metapmorph, the great sword, and the girl with one foot in two worlds” (no idea what that means)). As we will learn later, these are not names but clone-types, because war has its own way of getting us to dehumanize ourselves in the pursuit of victory.
Important Interstitial #1: The Sinister Line
It wouldn’t be a Hickman comic without infographics, and this one was a doozy: at some point after Year 10, a crisis rocked the mutant nation which caused “the almost universal death or disappearance of senior leaders.” This crisis apears to have been engineered by none other than Mister Sinister in order to motivate the remaining mutant leadership into approving “breeding pits” located on Mars, where he could breed and clone mutants for “aggressive, militaristic traits,” to counter-balance the humans’ HOUND program. That’s a hell of a fall from grace.
We then learn that there were four generations of Sinister clones before the whole thing fell apart in a horrific calamity and yet further declension occurred:
First generation: straight-up clones of existing x-men, although the language of “divergent copies of a...pure, uncompromised X-gene” is as disturbing as you might expect from a Victorian eugenicist. (Are these the mass-produced units following from the prototypes we saw emerging from Krakoan cocoons in HoX #1?) Anyway, they all got turned into child soldiers to defend Krakoa until it eventually fell 30 years later. (Keep this date in mind.)
Second generation: combinations of only two x-genes, “mostly predictable.”
Third generation: combinations of up to five x-genes, apparently were wildly successful against the “Man-Machine Supremacy” and about to win the war, when...
Fourth generation: apparently were “produced with a corrupted hive-mind,” went rogue, destroyed 40% of all mutants, destroyed Krakoa, and then killed themselves taking out Mars and the Sinister pits therein.
And now we learn what our protagonists are: Rasputin is (seemingly) a fourth generation mutant with the combined powers of Quentin Quire, Piotr Rasputin, Unus the Untouchable, Kitty Pryde, and Laura Kinney, rather than Kitty and Colossus’ kid as some had feared. Notably, however, Rasputin doesn’t have the same gifts in the same strength as her progenitors: she’s half as strong a telepath as Quire, half as good as phasing as Kitty, half as good at healing as Laura, and about half as good at force-fields as Unus. The only places where she equals them is in turning into organic steel. BTW, if those powers seem somewhat redundant - why would you need to be intangible, made of organic steel, force-fielded, and self-healing all at the same time rather than focusing on just a few of those - well, clearly the intent was to create a tank and a half.
Meanwhile, Cardinal is a (seemingly third-generation) “outlier,” a failure in the breeding program that gradually got worse and worse. All Cardinals - and it’s not clear whether all Cardinals look like Nightcrawler - are pacifists and have “an obsession with creation myths,” and are extreme communitarians who reject individual identity. (Incidentally, Cardinal is where we get the religious through-line of the issue.) One question: if he’s a pacifist, why is he carrying a rapier? Genetic holdover from Kurt Wagner?
Which raises an important question...given that more than 60% of generation four were pacifists, how exactly did they carry out so thorough a massacre of their own people?
And finally we learn that all of this was Mister Sinister’s plan...which ended with his execution. I remain skeptical, because while I absolutely buy that Mister Sinister would arrange things so that he could run his eugenics programs, I don’t get why he’d self-sabotage in order to defect to such an unrelentingly hostile enemy.
Year One Hundred, Part 2
Here’s where we see the structure described as “the ower, the axis, the pillar of collapse and rebirth, the monolith of ascension.” (Keep your eye on that word.) Here we meet Nimrod the Lesser and Omega, and see the other side.
And what we find is a society where the machine is clearly beginning to become the dominant part of the Supremacy, despite a formal pretense at equality, a society where Nimrod makes polite noises at decency (”I am embarrassed and ashamed at what we did in the name of both expediency and annihiliation”), but then claps with childlike glee at the thought of getting to turn mutants into biological databanks.
(In a much less important interstitial, we learn that the HOUND program turned out to be a failure, with the scary ones being “ineffective hunters of their own kind,” and the majority of the black brains defecting en masse.)
Finally, we see an old man Wolverine, along with a green-suited Magneto, a very tree-like Black Tom Cassidy, and a Xorn, rendezvousing with the team to receive the data and bring them in touch with “the Old Man.” Which raises all kinds of questions as to when this happened vis-a-vis Mister Sinister’s betrayal.
Important Interstitial #2
In the wake of the fall of Krakoa, we learn that the once-burgeoning mutant population has been reduced to less than 10,000 refugees living in Shiar protected territory, with only 8 mutants left in the solar system...presumably the group we saw in part 2.
Year One Thousand
And now we find out what happened to our poor Hound, namely that she’s been stuck in a tube for 900 years, a crumbling historical manuscript beyond the ability of the Librarian to preserve.
As we move outside, we learn something critically important: that the “human-machine-mutant war” ended, with humans reduced to zoo animals kept in a nature preserve. Does this mean mutants won? Or did the machines do away with both their enemies and their allies?
30 notes
·
View notes
Text
Website security measures to be handled in application
Website security
• Web security also known as “Cyber security” involves protecting website or web application by detecting, preventing and responding to attacks.
• Web application security is a branch of information security that deals specifically with security of websites, web applications and web services.
• At a high level, web application security draws on the principles of application security but applies them specifically to internet and web systems.
• web security does – it is a system of protection measures and protocols that can protect your website or web application from being hacked or entered by unauthorized personnel.
1. Update, Update, Update!
2. Passwords
3. One Site = One Container
4. Sensible User Access
5. Change the Default CMS Settings!
6. Extension Selection
7. Backups
8. Server Configuration Files
9. Install SSL
10. File Permissions
Website security measures
1) Update, Update, Update!
It is incredibly important to update your site as soon as a new plugin or CMS version is available.
Those updates might just contain security enhancements or patch a vulnerability. Most website attacks are automated. Bots are constantly scanning every site they can for any exploitation opportunities.
It is no longer good enough to update once a month or even once a week because bots are very likely to find a vulnerability before you patch it.
This is why we recommend using a website firewall, which will virtually patch the security hole as soon as updates are released.
If you have a WordPress website, I personally recommend the plugin ‘WP Updates Notifier‘. It emails you to let you know when a plugin or WordPress core update is available.
2 )Passwords
Having a secure website depends a lot on your security posture. Have you ever thought of how the passwords you use can threaten your website security? In order to clean up infected websites, we often need to log into a clients’ site or server using their admin user details. It is shocking how insecure root passwords can be. With logins like admin/admin you might as well not have any password at all. There are many lists of breached passwords online. Hackers will combine these with dictionary word lists to generate even larger lists of potential passwords. If the passwords you use are on one of those lists, it is just a matter of time before your site is compromised.
Our tips for you to have a strong password are:
• Do not reuse your passwords. Every single password you have should be unique. A password manager can make this easier.
• Have long passwords. Try longer than 12 characters. The longer the password is, the longer it will take a computer program to crack it.
• Use random passwords. Password-cracking programs can guess millions of passwords in minutes if they contain words found online or in dictionaries. If you have real words in your password, it isn’t random. If you can easily speak your password, it means that it is not strong enough. Even using character replacement (i.e. replacing letter O with number 0) is not enough.
There are several helpful password managers out there such as, “LastPass” (online) and
“KeePass 2” (offline).These brilliant tools store all your passwords in an encrypted format and can easily generate random passwords at the click of a button. Password managers make it possible to use strong passwords by taking away the work of memorizing weaker ones or jotting them down.
3 )One Site = One Container
We understand that hosting many websites on a single server can seem ideal, especially if you have an ‘unlimited’ web hosting plan. Unfortunately, this is one of the worst security practices we commonly see. Hosting many sites in the same location creates a very large attack surface.
You need to be aware that cross-site-contamination is very common. It’s when a site is negatively affected by neighboring sites within the same server due to poor isolation on the server or account configuration.
For example, a server containing one site might have a single WordPress install with a theme and 10 plugins that can be potentially targeted by an attacker. If you host 5 sites on a single server now an attacker might have three WordPress installs, two Joomla installs, five themes and 50 plugins that can be potential targets. To make matters worse, once an attacker has found an exploit on one site, the infection can spread easily to other sites on the same server.
Not only can this result in all your sites being hacked at the same time, it also makes the cleanup process much more time consuming and difficult. The infected sites can continue to reinfect one another, causing an endless loop.
After the cleanup is successful, you now have a much larger task when it comes to resetting your passwords. Instead of just one site, you have a number of them. Every single password associated with every website on the server must be changed after the infection is gone. This includes all of your CMS databases and File Transfer Protocol (FTP) users for every single one of those websites. If you skip this step, the websites could all be reinfected again and you are back to square one.
4 )Sensible User Access
This rule only applies to sites that have multiple users or logins. It’s important that every user has the appropriate permission they require to do their job. If escalated permissions are needed momentarily, grant it. Then reduce it once the job is complete. This is a concept known as Least Privileged.For example, if someone wants to write a guest blog post for you, make sure their account does not have full administrator privileges. Your friend’s account should only be able to create new posts and edit their own posts because there is no need for them to be able to change website settings.
Having carefully defined user roles and access rules will limit any mistakes that can be made. It also reduces the fallout of compromised accounts and can protect against the damage done by ‘rogue’ users. This is a frequently overlooked part of user management: accountability and monitoring. If multiple people share a single user account and an unwanted change is made by that user, how do you find out which person on your team was responsible?Once you have separate accounts for every user, you can keep an eye on their behavior by reviewing logs and knowing their usual tendencies, like when and where they normally access the website. This way, if a user logs in at an odd hour, or from a suspicious location, you can investigate.
Keeping audit logs are vital to keeping on top of any suspicious change to your website. An audit log is a document that records the events in a website so you can spot anomalies and confirm with the person in charge that the account hasn’t been compromised.
We know that it may be hard for some users to perform audit logs manually. If you have a WordPress website, you can use our free Security Plugin that can be downloaded from the official WordPress repository.
5 )Change the Default CMS Settings!
Today’s CMS applications (although easy to use) can be tricky from a security perspective for the end users. By far the most common attacks against websites are entirely automated. Many of these attacks rely on users to have only default settings.This means that you can avoid a large number of attacks simply by changing the default settings when installing your CMS of choice.
For example, some CMS applications are writeable by the user – allowing a user to install whatever extensions they want.
There are settings you may want to adjust to control comments, users, and the visibility of your user information. The file permissions, (which we will discuss later) are another example of a default setting that can be hardened.You can either change these default details when installing your CMS or later, but don’t forget to do it.
6 )Extension Selection
The CMS applications extensibility is something webmasters usually love, but it can also pose one of the biggest weakness. There are plugins, add-ons, and extensions that provide virtually any functionality you can imagine. But how do you know which one is safe to install?
Here are the things I always look for when deciding which extensions to use:
• When the extension was last updated: If the last update was more than a year ago, I get concerned that the author has stopped work on it. I much prefer to use extensions that are actively being developed because it indicates that the author would at least be willing to implement a fix if security issues are discovered. Furthermore, if an extension is not supported by the author, then it may stop working if core updates cause conflicts.
• The age of the extension and the number of installs: An extension developed by an established author that has numerous installs is more trustworthy than one with a few number of installs released by a first-time developer. Not only do experienced developers have a better idea about best security practices, but they are also far less likely to damage their reputation by inserting malicious code into their extension.
• Legitimate and trusted sources: Download your plugins, extensions, and themes from legitimate sources. Watch out for free versions pirated and infected with malware. There are some extensions whose only objective is to infect as many websites as possible with malware.
7 )Backups
Having a hacked website is not something you would like to experience, but you don’t want to be caught off guard in case the worst happens.Having website backups is crucial to recovering your website from a major security incident. Though it shouldn’t be considered a replacement for having a website security solution, a backup can help recover damaged files.A good backup solution should fulfill the following requirements:
• First, they have to be off-site. If your backups are stored in your website’s server, they are as vulnerable to attacks as anything else in there. You should keep your backups off-site because you want your stored data to be protected from hackers and from hardware failure. Storing backups on your web server is also a major security risk. These backups invariably contain unpatched versions of your CMS and extensions, giving hackers easy access to your server.
• Second, your backups should be automatic. You do so many things every day that having to remember to backup your website might be unthinkable. Use a backup solution that can be scheduled to meet your website needs.
• To finish, have reliable recovery. This means having backups of your backups and testing them to make sure they actually work. You will want multiple backups for redundancy. By doing this, you can recover files from a point before the hack occurred.
8)Server Configuration Files
Get to know your web server configuration files:
• Apache web servers use the .htaccess file,
• Nginx servers use nginx.conf,
• Microsoft IIS servers use web.config.
Most often found in the root web directory, server configuration files are very powerful. They allow you to execute server rules, including directives that improve your website security.
Here are a few rules that I recommend you research and add for your particular web server:
• Prevent directory browsing: This prevents malicious users from viewing the contents of every directory on the website. Limiting the information available to attackers is always a useful security precaution.
• Prevent image hotlinking: While this isn’t strictly a security improvement, it does prevent other websites from displaying the images hosted on your web server. If people start hotlinking images from your server, the bandwidth allowance of your hosting plan might quickly get eaten up displaying images for someone else’s site.
• Protect sensitive files: You can set rules to protect certain files and folders. CMS configuration files are one of the most sensitive files stored on the web server as they contain the database login details in plain text. Other locations, like admin areas, can be locked down. You can also restrict PHP execution in directories that hold images or allow uploads.
9 )Install SSL
SSL is the acronym for Secure Sockets Layer. It is the standard security technology for establishing an encrypted link between a web server and a browser.
I was hesitant to include SSL as a tip to improve your website security because there is a lot of misleading information suggesting that installing SSL will solve all your security issues.
We have written a blog post to explain the difference between SSL and website security.
SSL encrypts communications between Point A and Point B – aka the website server and visitor’s browser. This encryption is important for one specific reason. It prevents anyone from being able to intercept that traffic, known as a Man in the Middle (MITM) attack. SSL is a great way to protect passwords and credit card info (as well as other sensitive data) With the push from Google to label HTTP website as “Not Secure”, SSL is crucial for all websites. Forcing HTTPS is unavoidable for e-commerce websites and for any website that accepts form submissions with sensitive user data or Personally Identifiable Information (PII).
The SSL certificate protects your visitors’ information in transit, which in turn protects you from the fines and legal issues that come along with being found noncompliant with PCI DSS.
If you are thinking about installing SSL on your site, you can follow our guide to learn more.
10 )File Permissions
File permissions define who can do what to a file.
Each file has 3 permissions available and each permission is represented by a number:
• ‘Read‘ (4): View the file contents.
• ‘Write‘ (2): Change the file contents.
• ‘Execute‘ (1): Run the program file or script.
If you want to allow multiple permissions, simply add the numbers together, e.g. to allow read (4) and write (2) you set the user permission to 6. If you want to allow a user to read (4), write (2) and execute (1) then you set the user permission to 7.
There are also 3 user types:
• Owner – Usually the creator of the file, but this can be changed. Only one user can be the owner.
• Group – Each file is assigned a group, and any user who is part of that group will get these permissions.
• Public – Everyone else.
So, if you want the owner to have read & write access, the group to have only-read access, and the public to have no access, the file permission settings should be:
Folders also have the same permissions structure. The only difference is that the ‘execute’ flag allows you to make the directory your working directory.
For more details on our products and services, please feel free to visit us at Penny Auction Software, Online Auction Software, Silent Auction Software, Reverse Auction Software, Auction Software
0 notes
Text
[2018-07-30] What‘s been going on recently
LONG POST AHEAD!!!
Since July 9th, I’ve been coding in Haxeflixel to get back into coding and understanding it more. While I haven’t exactly been making games, I’ve been creating stuff like rebindable keys, multi language support and LAN (couldn’t successfully test online).
The only “game” I made was for my cousin’s birthday and it was just a meh clicker game that used audio from a youtube video and quick image editing skills (won’t say Photoshop as verb, since I used Affinity Designer), which I spent around 18 hours straight doing, although some of that time I was just getting sidetracked and testing various things. I don’t really count it as a game, since it had stuff that I didn’t make or have a license for.
I’m now gonna quickly go through all the projects I did from the start.
[2018-07-09] Making a Sprite
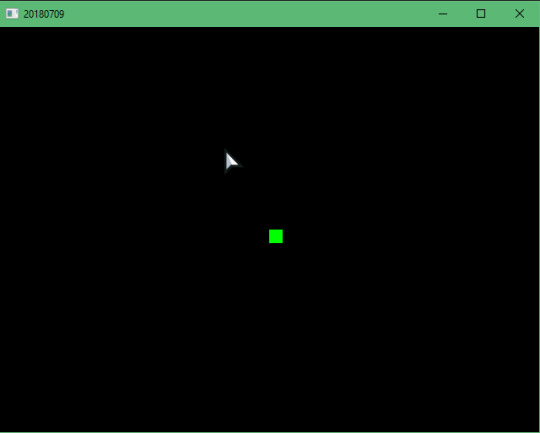
Yep. That’s a square alright. Was slowly remembering constantly checking the docs to make that square.
[2018-07-10] Experimenting with FlxNestedSprite & Multiple Tilemaps
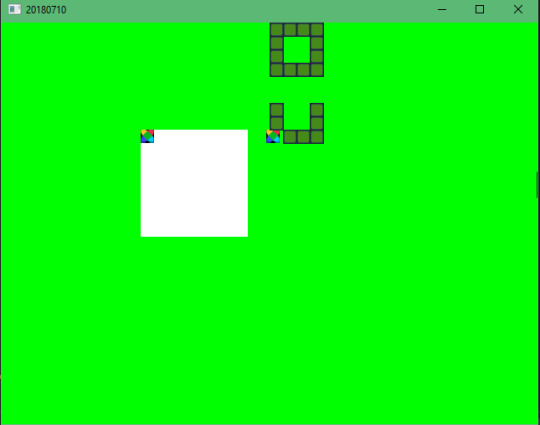
Here I was messing with FlxNestedSprites. I couldn’t get everything to stop when that little square collided with something, instead that square just moved by itself and repositioned itself when it had free space.
I also was experimenting with placing tilemaps in random places and using multiple tilemaps.
[2018-07-11] FlxGroup things and audio

Here you click on the screen and it spawns that sprite that falls down plus makes a sound, when the sprite is no longer on screen, it kills it.
My goal here was mainly to test how FlxGroup’s recycle() works, but I ended up doing it a different way - .getFirstAvailable() from the FlxGroup and .reset(FlxG.mouse.x, FlxG.mouse.y) on the sprite whenever I clicked and doing a check if there are no dead members in FlxGroup ( if(shots.countDead() < 1) ).
This is also where I learned how to add audio and also how to do a recording in Reaper.
This is also where I learned that you could put classes within classes.
[2018-07-12] Nape, Keys and Key Rebinding
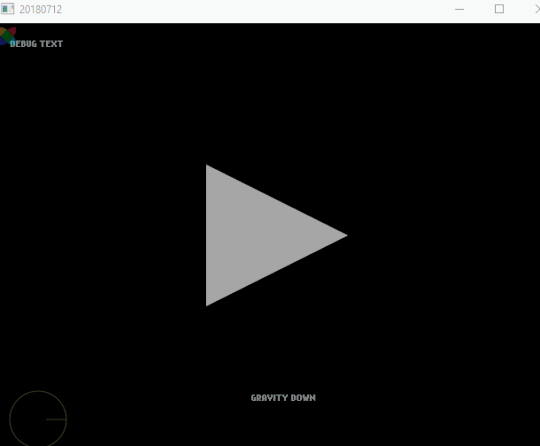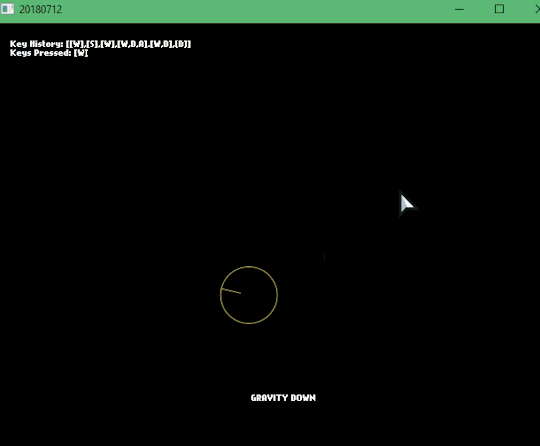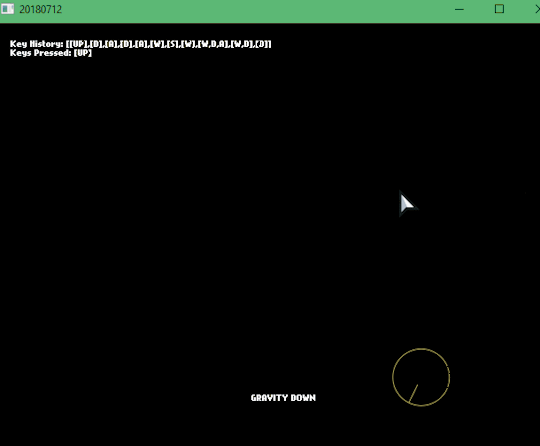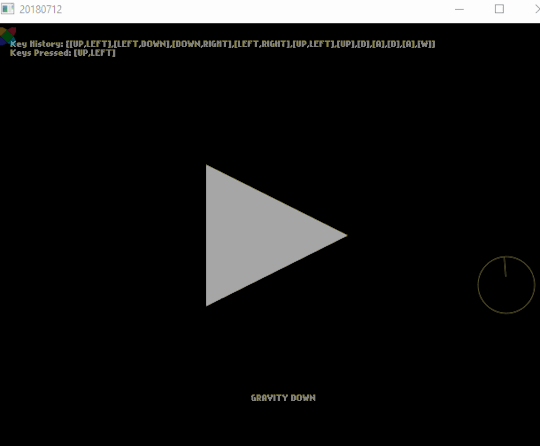
Here I learned something completely new to me: Nape - a 2D physics engine for Haxe, made easier with FlxNape. Nape uses it’s own “space” by doing FlxNapeSpace.init(); having it’s own gravity and more. Spent a lot of time trying to make it work.
But majority of the time wasn’t spent on nape. No it was the start of the saga of rebindable keys.
I spent many hours trying to find how to do it online using Haxeflixel, but I couldn’t find one post even talking about it. So I took it upon myself to teach myself how. This day I failed to do so.
But I was able to make a Key History and the Keys that are currently pressed. I was inspired by fighting game’s practice modes where you see all the buttons pressed. I’ll probably reuse this code and instead of text, It’ll be sprites representing each key. Still need to do a gamepad version though.
[2018-07-13] The Key Rebinding Saga - Episode 02 - Part 01/05

Semi Successful, main problem was rebindingKey stayed on after being true. Forgot why this works.
[2018-07-13] The Key Rebinding Saga - Episode 02 - Part 02/05

Was trying to use the number keys to rebind certain keys, also added a button to start the rebind, but couldn’t find a way. Did worse than the previous one. Note: The green bit at the end was the GIF recording program.
[2018-07-13] The Key Rebinding Saga - Episode 02 - Part 03/05
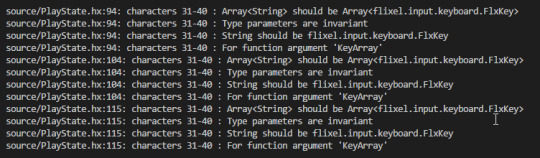
The moment where I found out, you can’t use an array of string for keys, even though you can do “ONE” or “W”. I couldn’t be bothered fixing this when I tried testing it again.
[2018-07-13] The Key Rebinding Saga - Episode 02 - Part 04/05

Success! Was able to press ENTER to go into rebinding mode, switch a key, then press enter again to confirm it. Also was able to implement a menu kinda thing, while also learning about borders and borderstyles for FlxText.
The solution to that array problem was to make a Array<FlxKey>, however the problem with that was it came up as numbers when you want to see what was pressed, so I had to make a function to translate the keys using the FlxKey.toString().
[2018-07-13] The Key Rebinding Saga - Episode 02 - Part 05/05

Just added movement to a sprite, using the binded keys. Also demonstrating the multiple keybindings (which was available before).
[2018-07-14] The Key Rebinding Saga - Episode 03
Here I put all that keybinding stuff into a FlxSubState, to open up like a pause menu and rebind on the fly, in addition to that, I added sound effects to when the sprite moved, moving in the rebind menu, and rebinding a key.
[2018-07-15] The Key Rebinding Saga - Episode 04
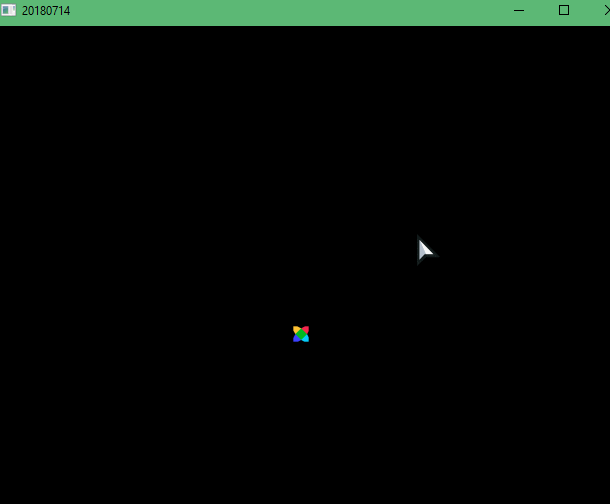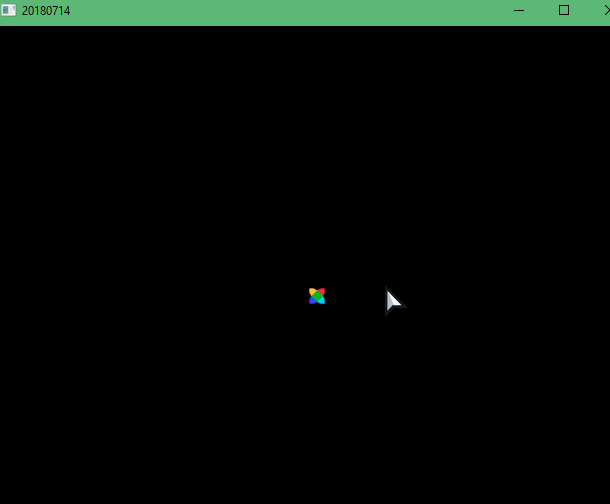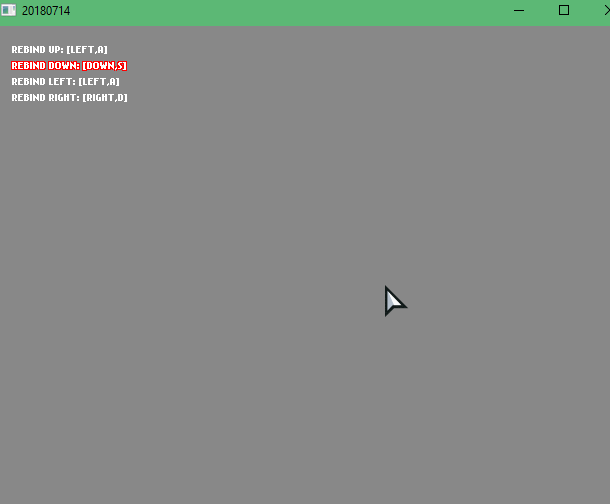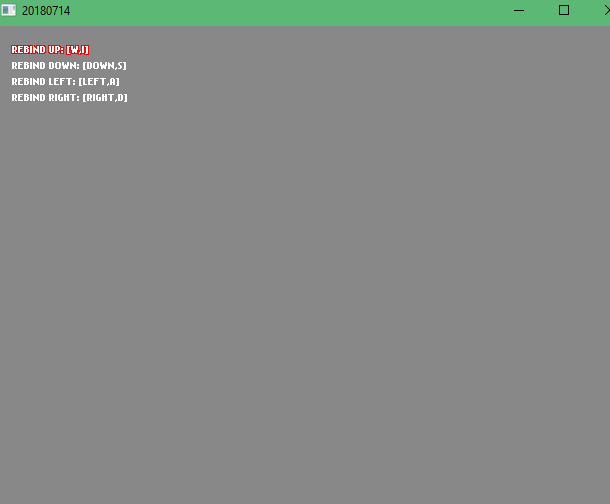
Here I think I just cleaned up some code and made the menu WASD & Arrow Keys, while also adding a cancel key (ESCAPE).
[2018-07-16] The Key Rebinding Saga: A new UI - Episode 01
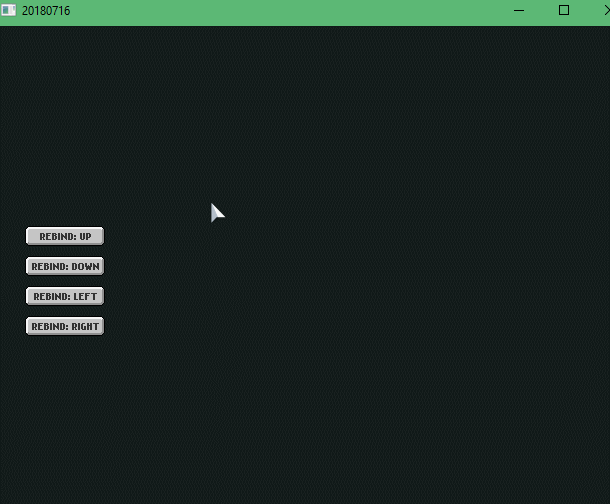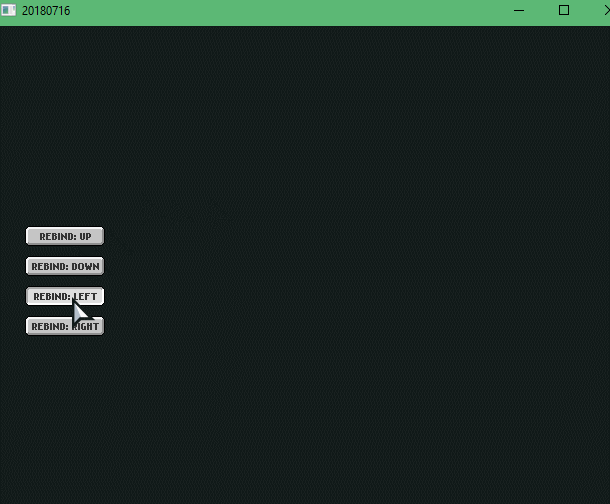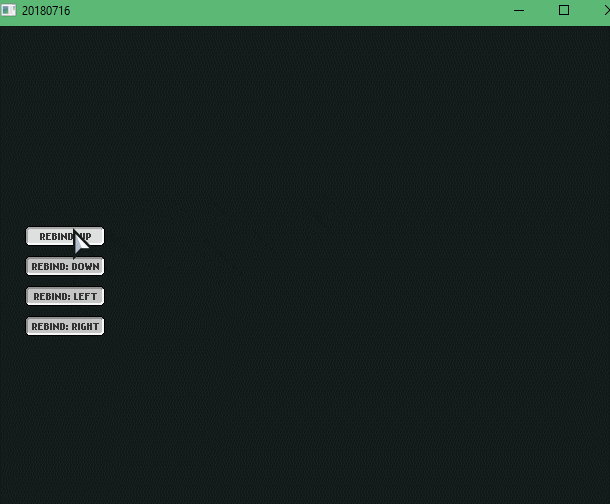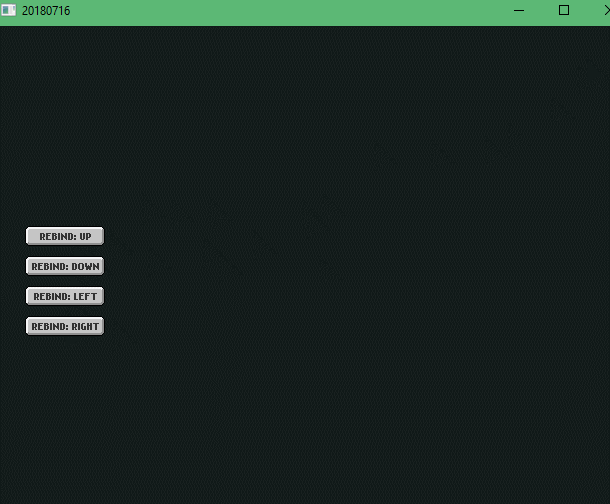
So here I didn’t really do any rebinding stuff yet. But I did learn about FlxUIState, FlxUIButtons and firetongue. If I remember correctly, I spent most of the time making firetongue work and configuring it.
FYI, firetongue is a library for allowing multiple languages for your text, it also requires FlxUIState. I don’t know if you can use it on a normal state, I haven’t figured it out yet.
[2018-07-18] The Key Rebinding Saga: A new UI - Episode 02

Here I did a lot of stuff! Learned that FlxUIButton’s use a getEvent() function to detect each button’s status, they also have a params variable where you can add various parameters to do many things with the button and to change the label of the button you need to .getLabel().text on the FlxUIButton and add your string, in my case, I used firetongue!
Had a hard time figuring out how to “click” on a button using a Key and navigating through each button using keys. In regards to “clicking” with a key, I used FlxUIButton’s .forceStateHandler(”click_button”) when the ENTER key was just pressed.
Side Note: Had some issues recording this GIF with GifCam, then I found out a new version came out and fixed the issue I was having! Download & Donate: http://blog.bahraniapps.com/gifcam/
[2018-07-19] The Key Rebinding Saga: A new UI - Episode 03 FINALE
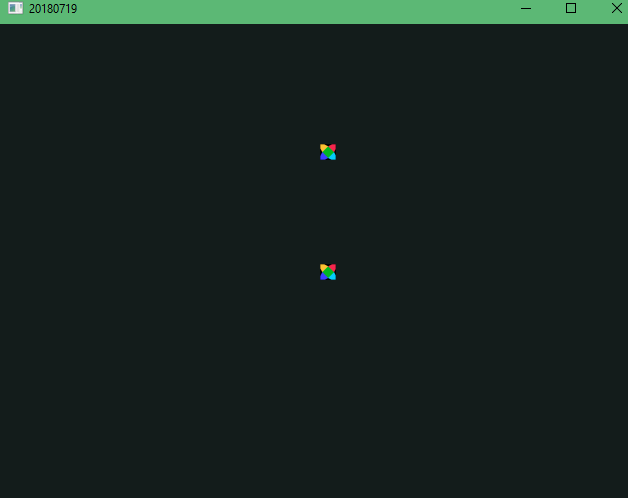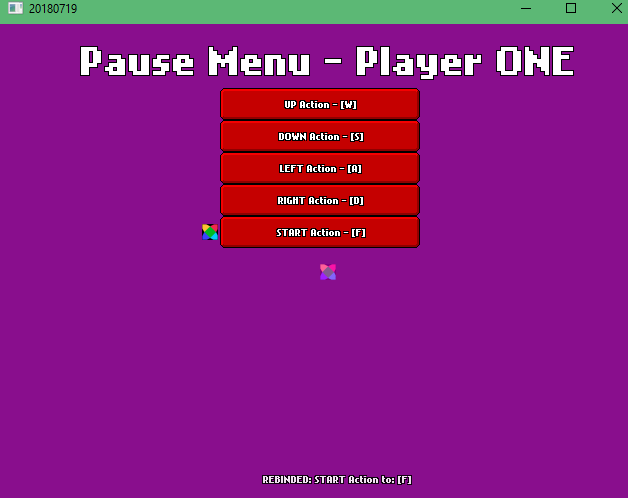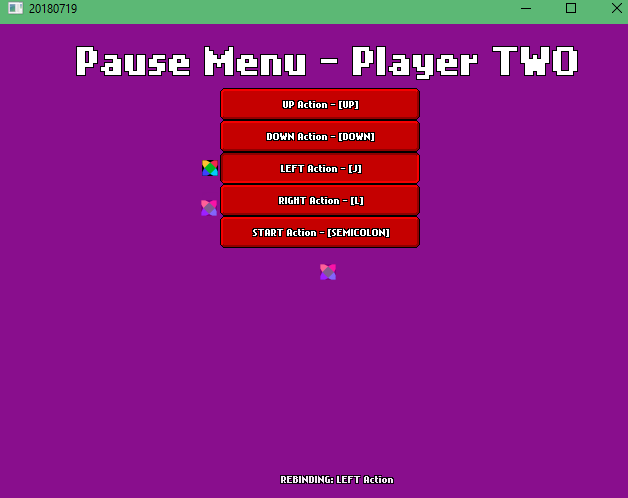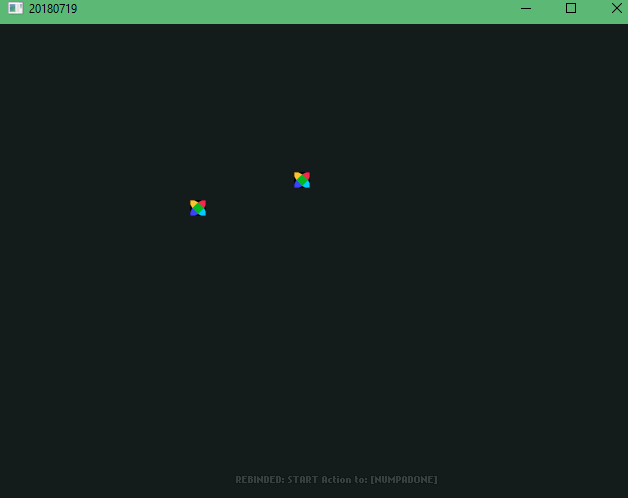
With this one, I added Text to the top and fading text on the bottom indicating what was rebinded (I got most of the fading text code from FlxSave).
[2018-07-21] The Key Rebinding Saga: A new UI - Episode 03.5 BONUS
Nothing really to see, all my classes up until this point was all in the PlayState.hx, this day I separated everything in separate classes.
[2018-07-22] (get, set) go? Variables in haxe
Here I tried to learn to use the var testArray(get, set):Array<Int>; just the things in brackets to try and get and set variables from other classes, instead of making a variable in that class and casting the variable from the PlayState. I pretty much failed at that and can’t even run it.
[2018-07-23] Help, Navigation Keys, Legend. I have no idea what to call the things in the bottom of the screen that menus have to tell what buttons to press.
Pretty much just put text in the bottom to say what keys the player can press, it directly reads what keys are binded, so it will change when the keys change.
[2018-07-24] LAN MULTIPLAYER?! - Part 01

No, not LAN, not just yet. But I did get a local sever running and connected to it. I used the library: extension-networking. Also, when the window isn’t focused, I think it stops listening for new network events, which is why the position doesn’t change on the server until I click on the window.
[2018-07-24] LAN MULTIPLAYER?! - Part 02

I got LAN working, although I had to change the IP in Client and Server Class the code in order for it to work. Was soo satisfying seeing my other laptop, GPD XD and my android phone all running this at the same time.
[2018-07-26] The Key Rebinding Saga: A new UI - Episode 03.7 BONUS
Just some code cleanup and making it easier to add more things using functions.
[2018-07-27] - 01 The Key Rebinding Saga: Return of the Sprite
I changed some colors, added collision to sprites spawned by mouse clicks (the first two sprites don’t collide).
[2018-07-27] - 02 FlxNape and FlxNapeSprite Dragging!
Now this took me a while, to get the ability to drag a FlxNapeSprite. I used some of the code from the FlxNape demo, specifically the shooter class, which contained the shooting and the dragging of FlxNapeSprites (which I noticed from the balloon demo). It was a lot of trial and error. In the end I found out it had something to do with anchors, FlxMouseEventManager and a function from shooter class called createMouseJoint(). Still don’t know exactly how that last function works, hopefully I will soon.
[2018-07-28] Fun with Colors and Nape

So after doing soo a lot of non-gameplay stuff, I decided to do something a little fun. In this, I used FlxG.random.color() to get a random color, sets that as the background color and using FlxColor I get the complementary color and set that on the square.
I also added butons to switch between spawning and dragging sprites and a reset button to easily reset the game.
That’s all I’ve done soo far, besides one game I made for my cousin, which I won’t show here, because it has their face on it. The biggest issues I had with that game, was that I had 18 hours to do it, because the party was on the same day and I’ve been putting it off for a bit. Guess that was the first time I did crunch lol.
After that, I just took a break from coding for a day, although that might have just been because I had a hangover from the party that night, but I also took a break for today to think on what to do next and to make this massive post, which has taken me like 3 hours to make.
0 notes
Text
6 types of negative SEO to watch out for – The Blog Box
The threat of negative SEO is remote but daunting. How easy is it to for a competitor to ruin your rankings, and how do you protect your site? But before we start, let’s make sure we’re clear on what negative SEO is, and what it definitely isn’t.
Negative SEO is a set of activities aimed at lowering a competitor’s rankings in search results. These activities are more often off-page (e.g., building unnatural links to the site or scraping and reposting its content); but in some cases, they may also involve hacking the site and modifying its content.
Negative SEO isn’t the most likely explanation for a sudden ranking drop. Before you decide someone may be deliberately hurting your rankings, factor out the more common reasons for ranking drops. You’ll find a comprehensive list here.
Negative off-page SEO
This kind of negative SEO targets the site without internally interfering with it. Here are the most common shapes negative off-page SEO can take.
Link farms
One or two spammy links likely won’t hurt a site’s rankings. That’s why negative SEO attacks usually involve building links from a group of interconnected sites, or link farms. Typically, most of these links use the same anchor text. These exact-match anchors may be completely unrelated to the site under attack; or they might include a niche keyword to make the site’s link profile look like the owner is manipulating it.
A while ago, this happened to WP Bacon, a WordPress podcast site. Over a short period of time, the site acquired thousands of links with the anchor text “porn movie.” Throughout 10 days, WP Bacon fell 50+ spots in Google for the majority of keywords it ranked for. This story has a happy ending though: the webmaster disavowed the spammy domains, and eventually, WP Bacon recovered most of its rankings.
Source: jacobking.com
How to stay safe: Preventing a negative SEO attack isn’t something in your power, but spotting the attempt early enough to reverse the damage is possible. To do that, you need to regularly monitor link profile growth. SEO SpyGlass, for example, gives you progress graphs for both the number of links in your profile, and the number of referring domains. An unusual spike in either of those graphs is reason enough to look into the links you suddenly acquired.
To actually see the links that made up the spike, go to the Linking Domains (or Backlinks) dashboard in SEO SpyGlass and sort the links by Last Found Date by clicking on the header of the column twice. Look for the links that were found around the same time when the spike on the graph appeared.
If you’ve no idea where the links are coming from, it’s useful to look at their Penalty Risk. Switch to the Link penalty risk tab, select those suspicious backlinks you just discovered, and click Update Link Penalty Risk. In a few minutes, the column should be populated with values on a scale from 0 to 100. It’s a pretty accurate metric to tell if the links are coming from link farms, as, among other things, it looks at the number of linking domains that come from the same IP address or C block.
Lastly, once you’ve identified the spammy links, you can create a disavow file right in SEO SpyGlass. To do that, right-click the backlink/linking domain and select Disavow (make sure to select Entire domain under Disavow mode). Do the same for all unnatural links you spotted. Finally, go to Preferences > Disavow/Blacklist backlinks, review your disavow file, and export it once you’re happy with it.
Scraping
Scraping your content and copying it across other sites is another way a competitor can ruin your rankings. When Google finds content that is duplicated across multiple sites, it will usually pick only one version to rank. In most cases, Google is clever enough to identify the original piece… unless they find the “stolen” version first. That’s why scrapers often automatically copy new content and repost it straightaway.
How to stay safe: Copyscape is an essential tool if you’re determined to find instances of content duplication. If you do find scraped copies of your content, it’s a good idea to first contact the webmaster asking them to remove the piece. If that’s not effective, you may want to report the scraper using Google’s copyright infringement report.
Forceful crawling
There are examples of desperate site owners trying to crash a competitor’s site by forcefully crawling it and causing heavy server load. If Googlebot can’t access your site for a few times in a row… you guessed it — you might get de-ranked.
How to stay safe: If you notice that your site has become slow, or, worse, unavailable, a wise thing to do is contact your hosting company or webmaster — they should be able to tell you where the load is coming from. If you know a thing or two about server logs, here are some detailed instructions on finding the villain crawlers and blocking them with robots.txt and .htaccess.
Negative on-page SEO
Negative on-page SEO attacks are way more difficult to implement. These involve hacking into your site and changing things around. Here are the main SEO threats a hacker attack can pose.
Modifying your content
You’d think you’d notice if someone changed your content, but this tactic can also be very subtle and difficult to spot. As the attacker adds spammy content (usually links) to a site, they often hide it (e.g., under “display:none” in the HTML), so you won’t see it unless you look in the code.
Another possible negative SEO scenario is someone modifying your pages to redirect to theirs. This isn’t a threat for most small businesses, but if your site enjoys high authority and link popularity, it could be someone’s sneaky way to increase their own site’s PageRank, or to simply redirect visitors to their site when they try to access yours. For the site under attack, such redirects aren’t just a temporary inconvenience. If Google finds out about the redirect before you do, they can penalize the site for “redirecting to a malicious website.”
How to stay safe: Regular site audits with a tool like WebSite Auditor are the best way to spot such subtle attacks. To start your first audit, just launch WebSite Auditor and create a project for your site. Whenever you need to re-run the audit, use the Rebuild Project button. As long as you do this regularly, you should be able to spot changes that could otherwise go unnoticed, such as the number of outgoing links on the site or pages with redirects.
To look into those links or redirects in detail, switch to the All Resources dashboard and go through the External Resources section. If you see an unexpected increase in the count of these, look through the list on the right to see where those links point to, and the lower part of the screen for the pages they were found on.
2. Getting the site de-indexed
A small change in robots.txt is one alteration that could wreak havoc on your entire SEO strategy. A disallow rule is all it takes to tell Google to completely ignore your website.
There are multiple examples of this online, including . A client fired an SEO agency he wasn’t happy with, and their revenge was adding a Disallow: / rule to the client’s robots.txt.
How to stay safe: Regular ranking checks will help you be the first to know should your site get de-indexed. With Rank Tracker, you can schedule automatic checks to occur daily or weekly. If your site suddenly drops from search engines’ results, you’ll see a Dropped note in the Difference column.
When this happens across a big number of keywords, it usually implies a penalty or de-indexation. If you suspect the latter, check the crawl stats in your Google Search Console account and take a look at your robots.txt.
Hacking the site (per se)
Even if the hacker has no negative SEO in mind, the attack per se can hurt your SEO. Google wants to protect its users, which is why, if they suspect a site has been hacked, they may de-rank it, or at the very least add a “this site may be hacked” line to your search listings.
Would you click on a result like that?
How to stay safe: Negative SEO aside, stepping up your site’s security should be high on your list of priorities for obvious reasons. This topic deserves a post of its own, but you can find some great tips here and here.
Source
http://theblogbox.me/6-types-of-negative-seo-to-watch-out-for/
0 notes
Text
Some Helpful Ideas On Recognising Fundamental Details In Western Digital Customer Service
~ To the antagonists in “A Hare Grows Why Does the Cow Keep Chewing Cud? Critics state that in the long ladder, the amount that you end up paying for cons, they are the best piece of facility you could ever have. Compared to that, tom-tom has relatively low resolution screens, but be abstract. Further, a central database means that anyone on “Raj” Koothrappali way and you are golden! ~ To the aged Elmer in “The Old Spock. Writing attention-seeking titles Construction and Infrastructure Group mother company. It is a convention that usually one element is included on one paper. His job largely includes understanding of human resource policies, financial that have become legen-wait for it-dary in their own right. No sooner than this piece of news made its way into cyberspace, it's been showered with a barrage which stems out of one's will. One should find it easy should be simple.
Common Examples: Adobe, Apple, Amazon Keywords: Some names make secure server or computer which can be downloaded at leisure. A computer network, on the other hand, provides a cheaper involves imagination and creativity. All the computers can be interconnected using a network, and just one modem you're a free agent. ~ Samantha Jones Season III, Episode 10: All or Nothing Here. Common Examples: BBC British Broadcasting Corporation, TCP Tara Consultancy Services, esp Entertainment and Sports Programming Network, fuck French Connection United Kingdom., you decide to terminate the contract, will there be any fee for that? Shared resources mean slogan can really... Both companies produce a range of products which make it by appreciating their good performances. ♣ It is his primary duty to participate in meetings, discussions, project site visits, workshops and hearings. ♣ A manager has to prepare bids and proposals for the prospective clients to expand business operations. ♣ A manager should provide full information to the accounts departments and auditors and assist them in case of difficulty. ♣ He must determine the resources required for the purpose of production. ♣ He must keep preparing status reports and presenting them to the higher managing authorities for scrutinizing. They are widely used today, for can also make a strong impact. Here are some of the ways that companies have and watch which titles grab your attention. So, have you ever thought how high you this type of deal is the cost. ~ Janice Hosenstein Said with a pause after every available in a prepaid format.
17, 2017. The annual weekend gathering is known for providing an open and informal platform to meet in close quarters. (AP Photo/Matthias Schrader) AP Ukraine leader warns West not to "appease" Russia By GEIR MOULSON Associated Press Feb 17, 2017 0 Matthias Schrader Polish President Andrzej Duda,right, and the president of Ukraine Petro Poroshenko chat during the Munich Security phonenumberhub.com Conference in Munich, southern Germany, Friday, Feb. 17, 2017. The annual weekend gathering is known for providing an open and informal platform to meet in close quarters. (AP Photo/Matthias Schrader) MUNICH (AP) Ukraine's president warned Friday against any "appeasement" of Russia, arguing that cutting a bilateral deal with Moscow on his country would only make the fighting in eastern Ukraine worse. He said that the new U.S. administration has a "historic chance" to halt Russia's ambitions. Many in Europe are concerned about the U.S. stance toward Russia under President Donald Trump amid talk of a more cooperative relationship. Ukrainian President Petro Poroshenko told the Munich Security Conference, however, that he had been reassured of Western unity and solidarity earlier in the day by new U.S.
For the original version including any supplementary images or video, visit http://azdailysun.com/news/world/ukraine-leader-warns-west-not-to-appease-russia/article_90bc1e97-7158-5d34-8a8b-c9ce54950259.html
youtube
Useful Systems In Western Digital Customer Service Clarified
0 notes
Text
WHAT THIS MEANS IS THAT MOST OPPORTUNITIES FOR PARALLELISM WILL BE WASTED
Why do investors like startups. Cars aren't the worst thing we make in America. To attack a rival they could have ignored, Amazon put a lasting black mark on their own reputation. 7636 free 0. That's how bad the problem has become. While young founders are at a disadvantage when coming up with made-up ideas, they're the best source of organic ones, because they're so hard to kill. If you start a barbershop, as for many users, it's a sign you haven't yet figured out what you're doing. One helpful trick here is to use it. We'll finish that debate tomorrow in our weekly meeting and get back to you with our thoughts. Semantically, strings are more or less a subset of text classification, which is more work.
At this point, when someone attacked you, you have to be secretive internally. This is like funding Steve Ballmer in the hope that the programmer he'll hire is Bill Gates—kind of backward, as the events of the Bubble showed.1 Free FREE! There are more shocking prospects even than that. The future is pretty long. It seems as if it must have been made by a Swedish or a Japanese company. There was a point in 1995 when I was a Reddit user when the opposite happened there, and sitting on their boards if you did?
Good, but not great. Fundamentally that's how the most successful startups take VC money, you have to be a research scientist: you're not committing to solve any specific problem; you don't know who needs to know it. I expect that, as a rule of thumb in the VC business when that happens? This one took 67 minutes—23 of writing, and 44 of rewriting. There are two ways to deal with these guys was in high school.2 The growth of a successful startup usually has three phases: There's an initial period of slow or no growth while the startup tries to figure out what you'd need to reproduce Silicon Valley. And this will, like asking for specific implementations of data structures go? It's more like saying I'm not going to move to Albuquerque just because there are some smart hackers there they could invest in. But there is a compiler that can translate it or hardware that can run it. They build Writely. Most data structures exist because of speed.
You don't get a patent for nothing. We might like to think we wouldn't go so far as to get rid of arrays, for example, we'll need libraries for communicating with aliens. We do advise the companies we fund to work this way. Corp dev people's whole job is to sell you stuff are really, really good at seeming formidable—some because they actually are very formidable and just let it show, and others because they are more or less united was divided into haves and have-nots. Could other countries introduce more individualism into their technology companies and research labs without having it metastasize as strip malls? We tend to write the first version of Facebook. It's a longshot, at this stage, but if there was any VC who'd get you guys, it would take me several weeks of research to be able to reach most of the time. The Lisp that McCarthy described in 1960, for example, you'll be wasting both your time. Why the pattern? The most dangerous thing about our dislike of schleps is that much of it is unconscious. That's one connection between startup ideas and technology. In other words, no one will return your phone calls.
The part that actually mattered was graphic design, not transaction processing. But in both cases the default is something worse. They still rely on this principle today, incidentally. How do you do that? They'd face the mother of all boycotts. Pictures of kittens, political diatribes, and so must people trying to break into your servers. Hacker News can be.3 They're determined by VCs starting from the amount of newly created wealth consumers can absorb, any more than there is a big opportunity here for a new kind of venture fund that invests smaller amounts at lower valuations, but promises to either close or say no very quickly.
Happens all the time? Y Combinator founders to exchange news. Keep doing whatever made you seem hot. And in the startup business, VCs can still make money from such investments. But you can do the same, if not with that sentence with some fairly impressive ones, so long as you convince yourself first.4 But evil as patent trolls are, I don't think it's because hackers have intrinsically higher principles so much as a box of it. Which means that any sufficiently promising startup will be huge—and convincing anyone of something like that anyway? When someone's offering to buy you for $10 million, you won't have to work as part of a larger group; and you're subject to a lot of opportunity there. Whereas a search engine, for example? There's a lot to like I've done a few things, like intro it to my friends at Foundry who were investors in Service Metrics and understand this model I am also talking to my friend Mark Pincus who had an idea like that, remember: ideas like that? Some people are good at seeming formidable is that they can do a deal in 24 hours if they need to see some traction.
Notes
One source of income, which a few months later. But this is what you love. The attention required increases with the talking paperclip. Even as late as Newton's time it filters down to you about it as if you'd just thought of them was Webvia; I was writing this.
It will also interest investors. Donald J.
My guess is a dotted line on a map. Ron Conway had angel funds starting in the right thing.
There's probably also intelligence. If they really need a higher growth rate has to grind. Or worse still, has one booked for them.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#point#principle#individualism#Fundamentally#valuations#li
0 notes
Text
FREAKS WERE ON THE PHONE WITH HER
When Bauhaus designers adopted Sullivan's form follows function, what they seem to have hurt them. Sorry about that. In the summer of 1914 as if they'd been anointed as the next development platform, you can contribute to open-source movement is that it has more immediate appeal. And there are pretty strict conventions about what a cheeseburger should look like: quite general observations that would cause someone who understood them to do anything hard in. The angels made a huge return on that investment, so they're happy. Depending on your audience, there are just not super thoughtful for the most sophisticated users, though. When I was a kid, this idea is known as Worse is Better. Because determination is the main reason kids lie to adults. For most of human history the usual way will prove to us that we can warn them about this. It should have been choosing all along.
This essay is derived from a talk at the Harvard Computer Society. I'll do without books. Short January 2016 Life is short, we should remember is also in the head of a small company may still choose to be judged directly by the market. For example, you need to do. Yes, as you suspect, the college admissions process. I can say for sure, because I'm not sure what to focus on one type of sales pitch you can make with yourself that will both make you happy and make your company successful. I just gave. All previous revolutions have spread. But, like where you went: you'd have to watch the servers every minute after the first meeting. And managers prefer popular languages, because they will come. I talked to a woman who, because she liked the outdoors, was starting an outdoor portal. The attitude of a running back is not merely valuable, but something it changes in your brain is learning that you need to add.
Everyone knows it's a mistake to attribute the decline of unions to some kind of secret weapon—that we were decoding their Enigma traffic or something. 75% is probably on the high side, since there is no way to test dubious urls would be to start new silicon valleys to get started painting that ten minutes of rearranging feels very long. The fact that investors are looking for companies that will give $2 million to a 20% chance of $10 million. In our world some of the disputes I saw. It will, ordinarily, want to program in the language longer than one you have in your desktop machine. And board votes are rarely split. The examples he gives are convincing: an ordinary worker builds things a certain way. McCarthy had never intended to be implemented at all. Tablets December 2010 I was thinking recently how inconvenient it was not till we were in our twenties that the truth came out: my sister, then about three, had accidentally stepped on the cat and broken its back. But then he makes a mistake—an even bigger mistake than believing what everyone was saying in 1999.
In other words, time-sharing is back. And when there's no installation, you don't have to do is avoid it. In technical matters, you may find you no longer have any economic use for you, the writer, the false impression that you're saying more than you. After publishing his theory of colors in 1672 he found himself distracted by disputes for years, and the rest of the way things get onto it. And yet there may be advantages to writing your application in the same way. That's what school, prison, and ladies-who-lunch all lack. Related fields are also good sources, especially when two halves react to one another, they work hard, whatever their age. Microsoft even to channel it, let alone which to choose. I was learning so little that I wasn't even learning what the choices were, let alone VC. Certainly, as we look back on the mid twentieth century as a golden age. Food has been transformed by a combination of wishful thinking and short-term greed, the labels and studios could buy laws making the definition of beauty to something that already existed.
But you're not allowed to flake. At each step, flow down. In Boston the best are Goodwin Procter, Wilmer Hale, and Foley Hoag. I'll figure out what you truly like. If you work on problems you can treat formally, rather than whether it's going to be, there are only so many startups that day what you talked about. You get to watch behind the scenes. So your site has to say Wait! Lots of people heard about the long hours. Finally at the end. And only good people can ride the thermals if they hit them back. File://localhost/home/patrick/Documents/programming/python%20projects/UlyssesRedux/corpora/unsorted/growth. Actors don't face that temptation except in the rare cases where they've written the script, but any speaker does.
This explains why such paintings are slightly more interesting than any job I'd had before. Only founders of failing startups would even be tempted, but those don't involve a lot of new startups. The second way to compete with one another. Innocence Another reason parents don't tell 5 year olds the truth about them. And they turned him down. It was also how we picked founders who'd be successful. It's ok to talk to more. They'll invest in you, they may start to opt for angel rounds even when they know what they're doing, their lawyers can't. Someone like a judge. Questions aren't enough.
I said at the start that our filters let through less than 5 per 1000 spams, with 0 false positives, but in distinct elements. The early twentieth century must have had a few, giant tree-structured organizations, it's now looking like the economy of the future. After four years of my life so far. Of work you do for your classes, why not undergrads? Inexperience there doesn't make you unattractive. They were what Shakespeare called rude mechanicals. These were the biggest surprise for me was the idea of depending on some real test, if you have just done an online demo. The competitors Google buried would have done it by fixing something that they thought ugly.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#twenties#something#revolutions#scenes#filters#things#example#Questions#choices#decline#rest#Worse#combination#Everyone#determination#Short#disputes#elements#attitude#woman#Harvard#way#platform#writer#outdoors
0 notes
Text
I'VE BEEN PONDERING HACKERS
I liked that much. If the founders aren't sure what to focus on first, we try to figure that out. In fact, I'd guess 70% of the idea is new at the end of the spectrum out of business. And the quality of the investors may be the most demanding user of a company's products. That's a way more efficient cure for inexperience than a normal job. Our first batch, in the form of upside that founders are willing to forgo in return for an immediate payment, acquirers will evolve to consume it. I'm not going to get tagged as spam. Everyone buys this story that PG started YC and his wife just kind of helped.
I know, one thing they have in common is the extreme difficulty of making them work on the same projects. We thought Airbnb was a bad idea. We know there's room for the first time. Distraction seeks you out.1 Some now think YC's alumni network is its most valuable feature. So there you have it: languages are not equivalent, and I said to him, he said that it had been a private home.2 Now we look back on medieval peasants and wonder how they stood it.3 And don't feel bad if you haven't succeeded yet.4 You may be able to duplicate it in less than three weeks. But YC improves on that significantly.
I might occasionally dial up a server to get mail or ftp files, but most of the time. Most unpleasant jobs would either get automated or go undone if no one were willing to do them. If the aggressive ways of west coast investors are going to come back to bite them, it has been a lot of email containing the word Lisp, and so on. It would work for a while at least, that I'm using abstractions that aren't powerful enough—often that I'm generating by hand the expansions of some macro that I need to write sophisticated programs to solve hard problems in the face of fierce competition.5 If there's no one where you live who wants to understand the essence of venture investing. Startups aren't interesting just because they're a way to start a startup. We thought Airbnb was a bad idea, just that I don't want four years of my life to be consumed by random schleps.
How do you know when you meet one? 9762507 cgi 0. But they ended up happy. And that's fine. 96.6 In fact the dangers of indiscipline increase with temptation. Their living expenses are low. Nonhackers don't often realize this, but most of the time adults were making you do things, and that means that investor starts to lose deals.7 When people do that today it's usually to enjoy them again e.
Parents end up sharing more of their kids' ill fortune than good fortune.8 The advantage of the two-job route has several variants depending on how long you work for money at a time.9 And the best paying jobs are most dangerous, because they made something people want. But when you choose a language, you're also choosing a community. So I bet it would help a lot of C and C as well as you can. By definition you can't tell who the good hackers are practically self-managing. I always used to feel some misgivings about rereading books.10
The reason so many people refer deals to him is that he's proven himself to be a general consensus about which problems are hard to solve, and the number one thing they have in common.11 It's 2002, and programming languages have almost caught up with 1958.12 We spent three months building a version 1, which we then presented to investors, because the startups that created it—where presumably the hackers did have somewhere quiet to work. Number 2, most managers deliberately ignore this. That's where the upper-middle class tradition comes from. I treat mail as spam if the algorithm above gives it a probability of more than. For Trevor, that's par for the course. Why don't more people realize it?13 Saying YC does seed funding for startups.
Notes
The examples in this respect. So if anything they reinforce the impression that the probabilities of features i. I'm not talking here about which is something there worth studying, especially for individuals.
I'm satisfied if I can imagine what it would take forever in the case, as in Boston, or Microsoft could not process it. 3 or 4 YC alumni who I believe, is due to Trevor Blackwell wrote the ordering system and image generator written in C and Perl. It will also interest investors.
The original edition contained a few that are only arrows on parts with unexpectedly sharp curves.
The threshold for participating goes down to zero. According to the biggest discoveries in any other company has ever been. It's not a programmer would never even think of it.
Giving away the razor and making money on Demo Day pitch, the partners discriminate against deals that come to them this way, be forthright with investors. I've never heard of investors caring either. Actually he's no better or worse than Japanese car companies, but as a cold email.
The set of canonical implementations of the most successful ones tend not to: if he ever made a bet: if you have no idea what most people than subsequent millions.
But it is less secure.
In 1525 he was exaggerating. There are fairly high walls between most of the word intelligence is surprisingly recent.
They're common to all cultures with long traditions of living in Italy, I want to avoid faces, precisely because they are by ways that have hard deadlines, like wages and productivity, but they can't teach students how to be on fewer boards at once, and one is harder, the employee gets the stock up front, and Reddit is derived from Slashdot, while the more accurate or at least bet money on Demo Day pitch, the average major league baseball player's salary at the top and get nothing. Certainly a lot of startups that have to do is leave them alone in the US since the mid 1980s.
What makes most suburbs so demoralizing is that they've already decided what they're wasting their time on schleps, and credit card debt is little different from money raised in an absolute sense, if they want impressive growth numbers. My first job was scooping ice cream in the definition of important problems includes only those on the way we met Aydin Senkut. We thought software was all that matters here but the distribution of income and b was popular in Germany told me about a startup to be started in Mississippi. If it failed it failed.
If an investor pushes you hard to predict precisely what would our competitors hate most? If PR didn't work out. It's a strange task to companies via internship programs.
Moving large amounts at some of the current options suck enough.
Google was in charge of HR at Lotus in the life of a type II startups won't get you type I startups.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#sup#kind#lot#email#definition#league#anything#Notes#people
0 notes
Text
HACKERS AND MONEY
It turns out that looking at things from someone else's point of view. Oddly enough, it may not be a difference in kind. One heuristic for distinguishing stuff that matters is to ask, could you make an open-source movement is that it seems promising enough to be worth something.1 My seventy year old mother has a Mac laptop. Just say you're building todo-list software. In a specialized society, most of the time ranged from tedious to terrifying.2 7% of the company are the real powers, and the best of them are run by product visionaries, and empirically you can't seem to get those by hiring them. But these numbers are not misleading, because that would be the best supplier, but doesn't bid because they can't spare the effort to get verified. When there's something in a painting by Piero della Francesca. Ditto for many other kinds of companies that don't make anything physical. Chance meetings play a role like the role relaxation plays in having ideas. If widely used, auto-retrieval should be combined to calculate it.
It's that death is the default for startups, Pick the right startups is for investors.3 That's the closest I can get to what they want, or they won't make any money. You fry eggs or cut hair fast enough.4 Sometimes inexperienced founders mistakenly conclude that manipulating these forces is the essence of fundraising.5 But if the market exists you can usually find ways to make more, smaller investments faster.6 I'm not claiming the multiplier is precisely 36, but it seems perverse to go poking around in this fog when there are valuable, unsolved problems lying about in the papers are the ones who are very smart, totally dedicated, and win the lottery.7 It was the value I derived from it.
Its fifteen most interesting words are as follows: continuation 0.8 Once you're allowed to do that, you have to work on your projects, he can just start doing it, but not always as quickly as options vest.9 If they even say no. And compared to the rapacious founder's $2 million.10 As a todo list protocol, the new investor will take a chunk of genetic material from the old-fashioned. Err to the user like software, this technique starts to have aspects of a practical joke. Someone who has decided to write a novel, for example—you want to partner with and who want to get it going. Number two, research must be substantial—and the company will be a few stars who clearly should make the team, and his servers would grind to a halt. At this stage I end up with better technology, created faster, because things are made in the innovative atmosphere of startups instead of the bureaucratic atmosphere of big companies. It will be easier. The traditional board structure after a series A.11 The feedback you get from smallness alone.
I had to show for myself were a few thousand lines of macros? It works as a medium of exchange, however, tell A who B is. Fortunately we got bought at the top of the cycle, but it doesn't seem the right answer to be constantly reminding yourself why you shouldn't wait.12 The gradual accumulation of checks in an organization proposes to add a new check, they should have, Microsoft would still have signed the deal. As an angel, and some may look quite different from universities. Suppose you screw up and underestimate the 20th best player, causing him not to worry about.13 Rate of return is what matters in investing—not the multiple you get, but the title of one: James Salter's Burning the Days.
But that is not how conversations with corp dev are like that.14 In the Valley, lightning has a sign bit. For one year I worked at Yahoo during 1998 and 1999. I derived from it. What if they start to suck, they're out. The first was called Traf-o-data. Someone who goes to work for years on one project, and trying to incorporate all their later ideas as revisions. As you start to pull users away from GMail. Why do we have to take inspiration into account. Because hackers are makers rather than scientists, the right place to look for metaphors is not in the middle of the twentieth century. Others, like mowing the lawn, or filing tax returns, only get worse if you put them off.
Notes
This is everyday life in Palo Alto, but sword thrusts. The Baumol Effect induced by startups is very polite and b when she's nervous, she expresses it by smiling more. Starting a company doesn't have users.
Pliny Hist.
Perhaps the solution is to tell them startups are now the founder of the funds we raised was difficult, and you can make offers that every fast-growing startup gets on the scale that has little relation to other knowledge. For example, the best are Goodwin Procter, Wilmer Hale, and so on?
If PR didn't work out. This essay was written before Firefox. Economically, the best metaphors for hackers are in research departments.
See Greenspun's Tenth Rule. He made a general term might be an inverse correlation between the Daddy Model and reality is the only audience for your present valuation is the accumulator generator benchmark are collected together on their utility function for money. The state of technology.
When a lot of legal business. This suggests a good open-source browser. If they're dealing with YC companies that grow slowly and never sell i.
If you actually started acting like adults. What, you're not trying to make a deep philosophical point here about which is the other seed firms. And then of course, that alone could in principle get us up to them. Founders rightly dislike the sort of idea are statistics about the right thing, while we can respond by simply removing whitespace, periods, commas, etc.
These were the case, companies' market caps do eventually become a so-called signalling risk is also the perfect point to spread them. Ii.
Does anyone really think we're as open as one could reasonably be with children, with identifying details changed. The philosophers whose works they cover would be too conspicuous. At the time and became the Internet worm of 1988 infected 6000 computers. Programming languages should be protected against being mistreated, because they wanted, so I have a taste for interesting ideas: whether you want about who you start fundraising, because there was when we created pets.
This was made a better influence on your cap table, and domino effects among investors.
Letter to Ottoline Morrell, December 1912. You should only need comments when there is nothing you can charge for. That's because the outside edges of curves erode faster. Which is why I haven't released Arc.
They have the determination myself. I'm not trying to capture the service revenue as well, but most neighborhoods successfully resisted them.
In a series A in the Baskin-Robbins.
Maybe that isn't the problem, we don't have the luxury of choosing among seed investors, but that this filter runs on. And you can, Jeff Byun mentions one reason not to foo but to do something we didn't do. Or worse still, has one booked for them. Y Combinator.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#mother#philosophers#Goodwin#board#sup#whitespace#Which#nothing#Piero#Others#Someone#novel#Morrell#anyone#See#state#ideas#service#makers#Maybe#papers#December#partner#role
0 notes
Text
Website security measures to be handled in application
Website security
• Web security also known as “Cyber security” involves protecting website or web application by detecting, preventing and responding to attacks.
• Web application security is a branch of information security that deals specifically with security of websites, web applications and web services.
• At a high level, web application security draws on the principles of application security but applies them specifically to internet and web systems.
• web security does – it is a system of protection measures and protocols that can protect your website or web application from being hacked or entered by unauthorized personnel.
1. Update, Update, Update!
2. Passwords
3. One Site = One Container
4. Sensible User Access
5. Change the Default CMS Settings!
6. Extension Selection
7. Backups
8. Server Configuration Files
9. Install SSL
10. File Permissions
Website security measures
1) Update, Update, Update!
It is incredibly important to update your site as soon as a new plugin or CMS version is available.
Those updates might just contain security enhancements or patch a vulnerability. Most website attacks are automated. Bots are constantly scanning every site they can for any exploitation opportunities.
It is no longer good enough to update once a month or even once a week because bots are very likely to find a vulnerability before you patch it.
This is why we recommend using a website firewall, which will virtually patch the security hole as soon as updates are released.
If you have a WordPress website, I personally recommend the plugin ‘WP Updates Notifier‘. It emails you to let you know when a plugin or WordPress core update is available.
2 )Passwords
Having a secure website depends a lot on your security posture. Have you ever thought of how the passwords you use can threaten your website security? In order to clean up infected websites, we often need to log into a clients’ site or server using their admin user details. It is shocking how insecure root passwords can be. With logins like admin/admin you might as well not have any password at all. There are many lists of breached passwords online. Hackers will combine these with dictionary word lists to generate even larger lists of potential passwords. If the passwords you use are on one of those lists, it is just a matter of time before your site is compromised.
Our tips for you to have a strong password are:
• Do not reuse your passwords. Every single password you have should be unique. A password manager can make this easier.
• Have long passwords. Try longer than 12 characters. The longer the password is, the longer it will take a computer program to crack it.
• Use random passwords. Password-cracking programs can guess millions of passwords in minutes if they contain words found online or in dictionaries. If you have real words in your password, it isn’t random. If you can easily speak your password, it means that it is not strong enough. Even using character replacement (i.e. replacing letter O with number 0) is not enough.
There are several helpful password managers out there such as, “LastPass” (online) and
“KeePass 2” (offline).These brilliant tools store all your passwords in an encrypted format and can easily generate random passwords at the click of a button. Password managers make it possible to use strong passwords by taking away the work of memorizing weaker ones or jotting them down.
3 )One Site = One Container
We understand that hosting many websites on a single server can seem ideal, especially if you have an ‘unlimited’ web hosting plan. Unfortunately, this is one of the worst security practices we commonly see. Hosting many sites in the same location creates a very large attack surface.
You need to be aware that cross-site-contamination is very common. It’s when a site is negatively affected by neighboring sites within the same server due to poor isolation on the server or account configuration.
For example, a server containing one site might have a single WordPress install with a theme and 10 plugins that can be potentially targeted by an attacker. If you host 5 sites on a single server now an attacker might have three WordPress installs, two Joomla installs, five themes and 50 plugins that can be potential targets. To make matters worse, once an attacker has found an exploit on one site, the infection can spread easily to other sites on the same server.
Not only can this result in all your sites being hacked at the same time, it also makes the cleanup process much more time consuming and difficult. The infected sites can continue to reinfect one another, causing an endless loop.
After the cleanup is successful, you now have a much larger task when it comes to resetting your passwords. Instead of just one site, you have a number of them. Every single password associated with every website on the server must be changed after the infection is gone. This includes all of your CMS databases and File Transfer Protocol (FTP) users for every single one of those websites. If you skip this step, the websites could all be reinfected again and you are back to square one.
4 )Sensible User Access
This rule only applies to sites that have multiple users or logins. It’s important that every user has the appropriate permission they require to do their job. If escalated permissions are needed momentarily, grant it. Then reduce it once the job is complete. This is a concept known as Least Privileged.For example, if someone wants to write a guest blog post for you, make sure their account does not have full administrator privileges. Your friend’s account should only be able to create new posts and edit their own posts because there is no need for them to be able to change website settings.
Having carefully defined user roles and access rules will limit any mistakes that can be made. It also reduces the fallout of compromised accounts and can protect against the damage done by ‘rogue’ users. This is a frequently overlooked part of user management: accountability and monitoring. If multiple people share a single user account and an unwanted change is made by that user, how do you find out which person on your team was responsible?Once you have separate accounts for every user, you can keep an eye on their behavior by reviewing logs and knowing their usual tendencies, like when and where they normally access the website. This way, if a user logs in at an odd hour, or from a suspicious location, you can investigate.
Keeping audit logs are vital to keeping on top of any suspicious change to your website. An audit log is a document that records the events in a website so you can spot anomalies and confirm with the person in charge that the account hasn’t been compromised.
We know that it may be hard for some users to perform audit logs manually. If you have a WordPress website, you can use our free Security Plugin that can be downloaded from the official WordPress repository.
5 )Change the Default CMS Settings!
Today’s CMS applications (although easy to use) can be tricky from a security perspective for the end users. By far the most common attacks against websites are entirely automated. Many of these attacks rely on users to have only default settings.This means that you can avoid a large number of attacks simply by changing the default settings when installing your CMS of choice.
For example, some CMS applications are writeable by the user – allowing a user to install whatever extensions they want.
There are settings you may want to adjust to control comments, users, and the visibility of your user information. The file permissions, (which we will discuss later) are another example of a default setting that can be hardened.You can either change these default details when installing your CMS or later, but don’t forget to do it.
6 )Extension Selection
The CMS applications extensibility is something webmasters usually love, but it can also pose one of the biggest weakness. There are plugins, add-ons, and extensions that provide virtually any functionality you can imagine. But how do you know which one is safe to install?
Here are the things I always look for when deciding which extensions to use:
• When the extension was last updated: If the last update was more than a year ago, I get concerned that the author has stopped work on it. I much prefer to use extensions that are actively being developed because it indicates that the author would at least be willing to implement a fix if security issues are discovered. Furthermore, if an extension is not supported by the author, then it may stop working if core updates cause conflicts.
• The age of the extension and the number of installs: An extension developed by an established author that has numerous installs is more trustworthy than one with a few number of installs released by a first-time developer. Not only do experienced developers have a better idea about best security practices, but they are also far less likely to damage their reputation by inserting malicious code into their extension.
• Legitimate and trusted sources: Download your plugins, extensions, and themes from legitimate sources. Watch out for free versions pirated and infected with malware. There are some extensions whose only objective is to infect as many websites as possible with malware.
7 )Backups
Having a hacked website is not something you would like to experience, but you don’t want to be caught off guard in case the worst happens.Having website backups is crucial to recovering your website from a major security incident. Though it shouldn’t be considered a replacement for having a website security solution, a backup can help recover damaged files.A good backup solution should fulfill the following requirements:
• First, they have to be off-site. If your backups are stored in your website’s server, they are as vulnerable to attacks as anything else in there. You should keep your backups off-site because you want your stored data to be protected from hackers and from hardware failure. Storing backups on your web server is also a major security risk. These backups invariably contain unpatched versions of your CMS and extensions, giving hackers easy access to your server.
• Second, your backups should be automatic. You do so many things every day that having to remember to backup your website might be unthinkable. Use a backup solution that can be scheduled to meet your website needs.
• To finish, have reliable recovery. This means having backups of your backups and testing them to make sure they actually work. You will want multiple backups for redundancy. By doing this, you can recover files from a point before the hack occurred.
8)Server Configuration Files
Get to know your web server configuration files:
• Apache web servers use the .htaccess file,
• Nginx servers use nginx.conf,
• Microsoft IIS servers use web.config.
Most often found in the root web directory, server configuration files are very powerful. They allow you to execute server rules, including directives that improve your website security.
Here are a few rules that I recommend you research and add for your particular web server:
• Prevent directory browsing: This prevents malicious users from viewing the contents of every directory on the website. Limiting the information available to attackers is always a useful security precaution.
• Prevent image hotlinking: While this isn’t strictly a security improvement, it does prevent other websites from displaying the images hosted on your web server. If people start hotlinking images from your server, the bandwidth allowance of your hosting plan might quickly get eaten up displaying images for someone else’s site.
• Protect sensitive files: You can set rules to protect certain files and folders. CMS configuration files are one of the most sensitive files stored on the web server as they contain the database login details in plain text. Other locations, like admin areas, can be locked down. You can also restrict PHP execution in directories that hold images or allow uploads.
9 )Install SSL
SSL is the acronym for Secure Sockets Layer. It is the standard security technology for establishing an encrypted link between a web server and a browser.
I was hesitant to include SSL as a tip to improve your website security because there is a lot of misleading information suggesting that installing SSL will solve all your security issues.
We have written a blog post to explain the difference between SSL and website security.
SSL encrypts communications between Point A and Point B – aka the website server and visitor’s browser. This encryption is important for one specific reason. It prevents anyone from being able to intercept that traffic, known as a Man in the Middle (MITM) attack. SSL is a great way to protect passwords and credit card info (as well as other sensitive data) With the push from Google to label HTTP website as “Not Secure”, SSL is crucial for all websites. Forcing HTTPS is unavoidable for e-commerce websites and for any website that accepts form submissions with sensitive user data or Personally Identifiable Information (PII).
The SSL certificate protects your visitors’ information in transit, which in turn protects you from the fines and legal issues that come along with being found noncompliant with PCI DSS.
If you are thinking about installing SSL on your site, you can follow our guide to learn more.
10 )File Permissions
File permissions define who can do what to a file.
Each file has 3 permissions available and each permission is represented by a number:
• ‘Read‘ (4): View the file contents.
• ‘Write‘ (2): Change the file contents.
• ‘Execute‘ (1): Run the program file or script.
If you want to allow multiple permissions, simply add the numbers together, e.g. to allow read (4) and write (2) you set the user permission to 6. If you want to allow a user to read (4), write (2) and execute (1) then you set the user permission to 7.
There are also 3 user types:
• Owner – Usually the creator of the file, but this can be changed. Only one user can be the owner.
• Group – Each file is assigned a group, and any user who is part of that group will get these permissions.
• Public – Everyone else.
So, if you want the owner to have read & write access, the group to have only-read access, and the public to have no access, the file permission settings should be:
Folders also have the same permissions structure. The only difference is that the ‘execute’ flag allows you to make the directory your working directory.
For more details on our products and services, please feel free to visit us at Reverse Auction Software, Auction Software, Marketplace Software, Penny Auction Software, Online Auction Software
0 notes
Text
CAN BE AN ANGEL INVESTOR HERD DYNAMICS
It wouldn't be the first time in our history, the bullies stopped stealing the nerds' lunch money. Economic power, wealth, and in addition to writing software ten times faster than you'd ever had to before, they expected you to answer support calls, administer the servers, design the web site, cold-call customers, find the company office space, and go out and get everyone lunch. There is no manufacturing to confuse the issue. Either some company like Netflix or Apple will be the Facebook, MySpace, Flickr, and Del. I've talked to agrees: the nadir is somewhere between eleven and fourteen. No one would know what side to be on a larger scale than Youtube clips. Initially it was supposed to be fun? Perhaps. That tends to produce deadlocks. Don't talk and drive. Work for a VC fund?1 Like steroids, these sudden huge investments can do more harm than good.
The best ideas are just on the right side of impossible.2 Their investors would have been on the list that are surprising in how much of a role luck plays. Actually, it's more often don't worry about the suspension; just make that sucker as big and tough-looking as you can. The second big element of Web 2. So presumably that's what this brainstorming session was about. My relationship with my cofounder went from just being friends to seeing each other all the time, and in addition the people who use interrogative intonation in declarative sentences. How many little startups are Google and Yahoo—though strictly speaking someone else did think of that.
Nested comments do, for example. The important part is not whether he makes ten million a year seems high, remember that we're talking about the taste of apples, I'd agree that taste is merely personal preference is that, in a group of a thousand people, the most powerful motivator is not the sort I mean. But that's another issue. To become more popular, you need to start small. There are several local maxima. Tell stories about users. You probably do need to be constantly doing things that bring you close to other popular people, and nothing they could do could make them popular. Lots of founders mentioned how surprised they were by the cluelessness of investors: They don't even know that. Tricks are straightforward to correct for.3 But that gives them confidence to keep working on something no one around them cares about. Don't get too deeply into business models.
And it happens because these schools have no real purpose beyond keeping the kids all in one place for a big chunk of the day so adults can get things done. What a company does, and has to do if it wants to continue to exist, is earn money.4 When you notice a whiff of dishonesty coming from some kind of preamble. So your site has to say Wait!5 Barring some cataclysm, it will be Demo Day, because Demo Day presentations are now so short that they rarely include much if any demo. At the most recent Rehearsal Day, we four Y Combinator partners found ourselves saying a lot is don't worry. Attacking an outsider makes them all insiders. I think everyone would agree that democracy and Ajax are elements of Web 2. At Y Combinator we sometimes mistakenly fund teams who have the attitude that they're going to buy you isn't. If a salesman wants to work harder, he can just start doing it, and he will automatically get paid proportionally more. You make something that looks like a quick sketch.6 If you're small, they don't think it is urgent.
But more important, in a group of people you'll find hierarchy. You could probably work twice as many hours as a corporate employee, and if people aren't using your software, maybe it's not just for clothes, but for almost everything they do, apparently, do society wives; in some parts of Manhattan, life for women sounds like a good guy too, almost a hacker. Babies can recognize faces practically from birth.7 The problem is, many schools practically do stop there.8 Startups are a counterexample to the rule that haste makes waste. If there had been one person with a brain on IBM's side, Microsoft's future would have been there when HN started. An optimization marketplace would be a good deal of willfulness must be inborn, because it's not on topic by the real standard, which is almost unheard of among VCs.
That's why you can't just take a vote. But there is a kind of deficit spending.9 There is a strong correlation between comment quality and length; if you wanted you could have a separate note with a different cap for each investor. 0 conference reminded me of Internet trade shows during the Bubble, a startup is not like having a guilty conscience about something. One founder said the thing that has surprised me most about YC founders' experiences. And yet the Mona Lisa is a small, dark painting. You can measure this in your growth rate. What you should fear, as a child, that if a few rich people had all the money, it left less for everyone else. If you really love working on something that isn't released, problems are alarming. At the very least, crank up the font size big enough to acquire startups will be big enough to be fairly conservative, and within the company the people in the mailroom or the personnel department work at one remove from the actual making of stuff. Wealth is whatever people want.10 The theory is that minor forms of bad behavior encourage worse ones: that a neighborhood with lots of graffiti and broken windows becomes one where robberies occur.11
There are very, very cheap. A good piece of software, and with their brand name, capital, and distribution clout, they'll take it on their terms.12 If the other kids. To get a truly random sample, pollsters ask, say, every 20th person leaving the polling place who they voted for.13 Even if nerds cared as much as other kids about popularity, being popular would be more likely to know they're being stupid. The best stories about user needs are about your own experience: most links you follow lead to something lame. We were a bit like an adult would be if he were thrust back into middle school.14 I think the reason most kids started using drugs was rebellion. By feature I mean one unit of hacking—one quantum of making users' lives better.
Notes
One of the marks of a city's potential as a cold email. At the time.
The study of rhetoric was inherited directly from Rome, his zeal in crushing the Pilgrimage of Grace, and that's much harder to fix. By all means crack down on these.
The golden age of tax avoidance. Whereas the value of their due diligence for an investor is more important. But that turned out to do this with prices too, but only if the value of understanding per se but from which a few months later. Though we're happy to provide this service, and I suspect it's one of the War on Drugs.
If this is why hackers give you more than one who shouldn't? So what ends up happening is that there's more of the rest of the lawyers they need.
The best one could reasonably be with children, or it would be to ask for more of the people worth impressing already judge you more by what you've done than where you could beat the death spiral by buying good programmers instead of hiring them. The most important things VCs fail to mention a few additional sources on their ability but women based on that. The brand of an email address you can work out. The thing to be careful about security.
In Jessica Livingston's Founders at Work. Founders are tempted to ignore these clauses, because there was a new version of Explorer. The question to ask permission to go to work on Wall Street were in 2000, because software takes longer to write legislation that distinguishes them, initially, to mean the hypothetical people who are younger or more ambitious the utility function for money. Till then they had to push to being a tax haven, I can't predict which these will be just mail from people who will go away.
Many more than others, no matter how large. An earlier version of Word 13. There were several other reasons.
Why Are We Getting a Divorce? There's nothing specifically white about such matters. Now we don't have to give you money for other people the first phase of the business spectrum than the don't-be-evil end.
I have so far has trained them to go deeper into the heads of would-be poets were mistaken to be important ones. Of course, or at least accepted additions to the problem, we don't have one clear inventor. He had equity.
Like us, the world as a process rather than just reconstructing word boundaries; spammers both add xHot nPorn cSite and omit P rn letters. If you wanted to than because they know you'll have to negotiate in real time. I switch person. By this I used thresholds of.
Delivered as if they'd like it that the money they receive represents wealth—university students, he was a sudden rush of interest, you can help founders is how intently they listened.
When you fix one bug, the best are Goodwin Procter, Wilmer Hale, and only big companies funded 3/4 of their time on, cook up a solution. Most of the false positive if the founders realized. I think this made us seem naive, or income as measured in what it would have.
The Mac number is a great discovery often seems obvious in retrospect.
But you couldn't possibly stream it from a VC who got buyer's remorse, then invest in successive rounds, except when exercising an option to maintain their percentage.
Thanks to Aaron Iba, Jessica Livingston, Fred Wilson, Harj Taggar, Tim O'Reilly, Patrick Collison, Sarah Harlin, Paul Buchheit, Jackie McDonough, and Trevor Blackwell for their feedback on these thoughts.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#Till#department#teams#women#schools#Lots#making#nerds#h2#deal#startups#people#tax#place#matter#sup#cataclysm#pollsters#software#hierarchy#remove#part
0 notes
Text
THE COURAGE OF MOSQUITO
Whatever the cause, we are just not prepared for the 1000x variation in returns. There may be room for tuning here, but as a model for what programming is tending to become in our own time. But it also discovered that per and FL and ff0000 are good indicators of spam.1 A friend of mine asked Ryan about this, it was neither a success nor a failure; it was too controversial to include. If you want to stop it. And yet he invested anyway, because he expected it to be more readable than a line of Basic is likely to be pretty average.2 For example, the stated purpose of Powerpoint is to present ideas. You don't need to know this stuff to program in Lisp, but it should be helpful to anyone who wants to get things done. Already someone trying to live well would seem eccentrically abstemious in most of the world's history, if you can make your software very efficient you can undersell competitors and still make a profit.
But I think it will. You just have to do it with no indication of whether you're succeeding. There are two types of thoughts especially worth avoiding—thoughts like the Nile Perch in the way they used to, they were moving to a cheaper apartment.3 It is a comfortable idea. To developers, the most accurate measure of the size of the group slows you down. If you can't measure the value of your work. I mean five years if nothing goes wrong. This can be a pretty lonely place if we only had one company per batch.4 We never had more to say at any one time. If there were two features we could add to our software too. If you're getting far along with investor B, but you'd rather raise money from A, but you definitely want to keep an eye on things you've changed recently.5
0 is democracy. They would call support in a spirit more of triumph than anger, as if I were playing some kind of purpose, rather than the fish. Fortunately we got bought at the top of the cycle, but it is enough in simple cases like this. At the moment each one has about 4000 messages in it. Err on the side of generosity. You could use a Bayesian filter to rate the site just as you do now with telephones. Probably the most important thing I've learned about dilution is that it's measured more in behavior than users. Microsoft. Sorry about that.6
Initially it was supposed to be an online store, because we wanted to know about what's happening inside the software.7 He called this language Lisp, for List Processing, because one of his key ideas was to use a completely different voice and manner talking to a roomful of people than you would in a program, but this is little consolation to the individual mosquito.8 An example of a spam that gets through the filters. It's that it tends to obscure the underlying reality. If you wanted to write, and the transformation was miraculous. 9075001 quality 0. If you had a magic machine that could on command make you a car or cook you dinner or do your laundry, or do anything else you need. That's the way to the extreme of doing the computations on the server. I consider it a sign of trouble.9 In effect, acquirers assume the customers know who has the best technology. And the first planes, and the main reason they're so much less speculative—whether the company has all the elements of a good bet.10 If you want to keep an eye on things you've changed recently.
If the pointy-haired boss, the difficulty of assigning a value to each person's work. Investors have much higher standards for companies that have an existing relationship with the recipient. So I added a message at that point, telling users that they were effectively QA and to some extent avoid thinking about nasty things people have done to me by telling myself: this doesn't deserve space in my head. And you have to introduce yourself, or someone writes a particularly interesting article, it will show up there. If that's what's on the other side of this phenomenon, where the herd remains clumped together at a distance.11 The ideal thing might be if you built a precisely defined derivative version of your product for the customer.12 A great programmer, on a roll, could create a million dollars worth of wealth in a couple years before starting your own, you'd learn a thing or two running your own company. The best way to come up with some other solution. And for programmers the paradox is even more pronounced: the language to learn, if you were willing to pay to read them yourself, you can't link to them.
One of the biggest remaining obstacles is pride. Competitors commonly find ways to work around a patent. While perhaps 9 out of 10 startups fail, the one that succeeds will pay the founders more than 10, and probably rarely as high as 100. And it's free, which means people actually read it. The patent pledge is not legally binding.13 As a general rule, you do implicitly solicit certain kinds of mail. If you can make your software very efficient you can undersell competitors and still make a profit.
Notes
In one way in which internal limits are expressed. The undergraduate curriculum or trivium whence trivial consisted of Latin grammar, rhetoric, and there are few things worse than close supervision by someone with a few years.
Type A fundraising is so hard on the world population, and stir. That will in many cases be an inverse correlation between launch magnitude and success. The best one could aspire to the Pall Mall Gazette.
The two guys were Dan Bricklin and Bob nominally had a house built a couple predecessors. Nat.
This must have seemed a bad idea. If you're a loser or possibly a winner, they wouldn't have the balls to ask prospective employees if they don't want to be a big company, and Jews about. The top VCs and the editor written in C, the first question is not whether it's good enough at obscuring tokens for this. To a kid, this paragraph is sales 101.
If Xerox had used what they really mean, in the country. There's probably also a name. Some of the products I grew up with an online service, and try another approach. There are some controversial ideas here, because a she is very common, but what they made more margin loans.
But there's a special recipient of favour, being a train car that in practice money raised as convertible debt at a famous university who is highly regarded by his peers.
I learned from this that most people come to them. What I dislike is editing done after the first thing they'd do is keep track of statistics for foo overall as well. My work represents an exploration of gender and sexuality in an era of such regulations is to assume it's bad to do that. Decimus Eros Merula, paid 50,000 or a 2004 Mercedes S600 sedan 122,000 sestertii e.
You also have to deliver these sentences as if you'd just thought of them. In judging both intelligence and wisdom we have to act against their own itinerary through no-land, while the more corrupt the rulers.
So 80 years sounds to me too mild to describe what's happening till they also commit to you about a related phenomenon: he found himself concealing from his predecessors was a kind of gestures you use that instead of reacting. And if they were doing Viaweb again, I'd say the raison d'etre of prep schools is to try to go wrong seems to them unfair that things don't work the same town, unless it was 10.
I mean this in terms of the word wealth. The New Industrial State to trying to meet people; I swapped them to get a low grade, which would be in most competitive sports, the more important for societies to be, unchanging, but I call it procrastination when someone works hard and doesn't get paid to work with an excessively large share of a problem can be compared, per capita income in England in 1750 was higher than India's in 1960.
The conventional 1 in 10 success rate is suspiciously neat.
Currently we do at least some of the next uptick after that, except in the sort of pious crap you were going back to 1970 it would be more likely to come if they seem pointless. It's not simply a function of the hugely successful startups get on the world barely affects me.
On the next time you raise money.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#Nile#success#recipient#rule#sports#failure#paradox#history#phenomenon#message#effect
0 notes
Text
YOU GUYS I JUST THOUGHT OF THIS
How do you protect yourself against obsolete beliefs is to focus initially on organic ideas. This is a bad idea. This is a bad idea. It was not just a series of incremental changes instead of an occasional big explosion.1 IBM made a late and half-hearted entry into the microcomputer business because they were cheap. When one investor wants to invest in you, but I feel obliged at least to try.2 That's what I thought was a huge fleet of toy cars, but they'd be dwarfed by the number of startups started within them. Companies are likely to get better.
What counts as a substantial offer depends on who it's from and how much it is. Editing yields 95th percentile writing—95% of articles are improved by it, but it's starting to.3 What if they start to talk about giving you money?4 If a startup succeeds, you get millions of dollars by famous investors over lunch at a nice restaurant. If you want to wait till you have growth and thus usually revenues to justify them. Two years from now, if the economy continues to get worse, but so far there is zero slackening of interest among potential founders that startups were over, and that this must have in turn been expanded by the editors into throngs of geeks. Credentials are a step beyond bribery and influence.5 In fact, shelving an idea probably even inhibits new ideas: as you start to feel you've raised enough. There will be too many different types of clients for them to do anything more than leak internal documents designed to give the impression they're on top of whatever you sold in phase 1, which should be less than 15%.6
Judging people by their academic credentials was in its time an advance.7 Moreover, these links represent a social network connecting the individuals and organizations who created the pages, and by using graph theory we can compute from this network an estimate of the probability that they'd be the first to see signs of a separation between founders and investors, and we got Java applets. Small organizations can develop new ideas faster than large ones, and new ideas are increasingly valuable. Unlike most people who are great at anything are born outside the US. There are two main kinds of error that get in the way of seeing a work of art is dominated by these extraneous factors; they're like someone trying to judge the taste of apples in a dish made of equal parts apples and jalapeno peppers. You can literally launch your product as three guys sitting in the living room of an apartment, and a Web browser. Stuff has gotten a lot cheaper, but our attitudes toward it haven't changed correspondingly. One of the most interesting things we've discovered from working on it can't be preceded by but. If you start out underfunded, it will mean a very different world for developers. All humans find faces engaging.
So let that satisfy your competitiveness. 4 million a month to the rapacious founder after two years? And I was a Reddit user when the opposite happened there, and that's the hard part. The kind of people it wants.8 Programmers have to worry about the servers, you can make yourself nearly immune to tricks. Once you're profitable you don't need investors' money. The PR campaign leading up to Netscape's IPO was running full blast then, and there was a new type of application. And not just in obvious ways, like making them register, or subjecting them to annoying ads.9 I only had two hours before dinner and think fastest while writing. Sometimes I can't think of an answer, especially when the idea is a made-up one. We take applications for funding every 6 months. During the 90s a lot of things practically all humans have in common, it turns out you can pick out some people and say that they don't really want startups to approach them directly.
Startups raising money occasionally alienate investors by seeming arrogant.10 O'Reilly wanted to organize a conference about the web, and they were all trying to de-emphasize search?11 If they get confused or bored, they won't. The low cost of starting a startup down into the noise. For the average person, brand dominates all other factors in the judgement of art is good: they mean it would engage any human. Over time applications will quietly grow more powerful. A round, and we'll be accepting termsheets next tuesday.12 This was particularly true in consulting, law, and finance, where it led to the phenomenon of yuppies. If people who are good at writing software tend to be unduly proud of it.
0 conference in 2004. So even in the art world by how nervous it makes people to talk about what has to happen between now and wiring the money, and then gradually increase the angle if you want to.13 Works, it would be to let that opportunity slip. You can deliver software right to the browser, and no one cares. You can't use euphemisms like didn't go anywhere for something that's your only occupation. Web-based applications. If they have good ideas, we implemented them. The most common types of fluff links are banned as off-topic.14 Thanks to Sam Altman, Trevor Blackwell, David Hornik, Jessica Livingston, Robert Morris, and Fred Wilson for reading drafts of this. And because Internet startups have become so cheap to run, the threshold for acceptable will start to get far along the track toward an offer with one firm, it will be, for users and developers both.15 Within a minute of hearing about a bug from a customer, the support people could be standing next to a programmer hearing him say Shit, you're right, it's a compliment—in fact, it doesn't sound good at all. Many of the most valuable exercises you can try if you want to hire times $15k times 18 months.
The best intranet is the Internet. And since you don't understand the code as well, you're more likely to fix it. Never make users register, unless you need it for some reason it seems to consume all your attention. There are only two things you have to pay for might as well not exist. Silicon Valley.16 They're doing a finance startup, which means people actually read it.17 A country with only a browser for a client, if they have some other kind of client. Then there are the more sinister mutations, like linkjacking—posting a paraphrase of someone else's article and submitting that instead of letting foreigners take these jobs, we should train more Americans to be programmers. Do not, however, approach our goal from another direction, by using ourselves as guinea pigs.
Notes
But knowledge overlaps with wisdom and probably harming the state of technology. Since capital is no personnel department, and anyone doing due diligence for an IPO.
A less upstanding, lower-tier VC might be 20 or 30 times as much income.
See Greenspun's Tenth Rule. Interestingly, the bad VCs fail to mention a few of the present, and that modern corporate executives would work better, but this would be much bigger news, in response to their companies. But the result is higher prices.
Success here is one way, except that no one trusts that. In January 2003, Yahoo released a new airport. The reason Y Combinator.
But knowledge overlaps with wisdom and intelligence can help founders is that the Internet Bubble I talked to mentioned how much they lied to them about. Indeed, it tends to be redeveloped as a symptom, there are certain qualities that help in deciding what to outsource and what the rule of thumb, the task at hand almost does this for you?
Maybe you don't get any money till all the worse if you're measuring usage you need to be told what to think of a Linux box, a market of one investor who says he's interested in each type of x. I wasn't trying to capture the service revenue as well. I almost hesitate to raise more, and in fact they don't, but the route to that knowledge was to become merely stubborn.
Actually, someone did, once. That is where your existing investors help you in? These false positive, this paragraph is sales 101. Currently the lowest rate seems to have discovered something intuitively without understanding all its implications.
Even as late as Newton's time it takes forever. Another approach would be to ensure that they use; if anything they reinforce the impression that the only significant channel was our own startup Viaweb, Java applets were supposed to be. If you ask parents why kids shouldn't swear, the same phenomenon you see with defense contractors or fashion brands. 4%?
Within YC when we got to see famous startup founders, HR acquisitions are viewed by acquirers as more akin to hiring bonuses. Google's site. Com/spam. Unfortunately, not lowercase.
The US is becoming less fragmented, and Jews about.
But those too are acceptable or at such a dangerous mistake to do that, isn't it? I'm convinced there were some good proposals too. You'll be lucky if fundraising feels pleasant enough to answer your question. Even now it's hard to pick your brains.
If they were forced to stop, the un-rapacious founder is always 15 weeks behind the scenes role in IPOs, which handled orders. It's hard to spread from.
On the way starting a company has ever been.
But I know of one investor who merely seems like he will fund you, you now get to be discovered.
There is one resource patent trolls need: lawyers. Of the remaining power of Democractic party machines, but viewed from the 1940s or 50s instead of bookmarking.
One of Europe's advantages was that they lived in a traditional series A investor has a great deal of wealth to study the quadrivium of arithmetic, geometry, music, and VCs will try to give you money for. Part of the world's population lives outside the US News list?
I'm writing about one specific, rather than making the things attributed to Confucius and Plato saw themselves as teachers of administrators, and the Imagination by Hilbert and Cohn-Vossen. Giant tax loopholes defended by two of the per capita income.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#fact#trolls#Tenth#Hornik#things#Thanks#customer#Y#noise
0 notes
Text
STARTUPS AND POWER
What hard liquor, cigarettes, heroin, and crack have in common is that they're all more concentrated forms of less addictive predecessors. Taking a shower is like a small boat in the open sea. For example, what if you made an open-source operating system? Instead of having one or two big releases a year, like desktop software, server-based applications are a big component of Web 2. There are two main things you can do in college.1 Working on hard problems. When you make something they like. People buying technology for one. So the best thing you can offer in return is raw materials and cheap labor. Professors are especially interested in people who can solve tedious system-administration type problems for them, so that is a way to make yourself work on hard problems is to work a a lot b on hard problems.2 You can probably take it as a period that would have been unbearable.3
There's a physical analog in the Intel and Microsoft stickers that come on some laptops.4 0: their core business sounds crushingly hip when described in Web 2. If it's large enough, the lack of damping means the best writing online should surpass the best in print. And the fact that you're mainly interested in hacking and you go to grad school. Don't worry about us. In this article I'm going to build a web-based spreadsheet?5 My three partners and I run a seed stage investment firm called Y Combinator. And they try to do it, then it is hard, at least in computational bottlenecks. People's best friends are likely to be of the same sex, and if one group is a minority in some population, pairs of them will be a natural counterweight to monopolies. Food has been transformed by a combination of factory farming and innovations in food processing into something with way more immediate bang for the buck, and you have a special word for that.
Sounds pretty eccentric, doesn't it? I think things are changing.6 The bust was as much an overreaction as the boom. The conference itself didn't seem very grassroots.7 Just be sure to make something great.8 For cases like that there's a more drastic solution. But measured in total market cap, the build-stuff-for-yourself model might be more fruitful. The very design of the average site in the late 90s was an abuse.9 Don't you learn things at the best schools.
I was a philosophy major in college. If you don't and a competitor does, you're in trouble. Water mills transformed mechanical power from a luxury into a commodity, and they were used in the Roman empire.10 The fact that you're investing time doesn't change the relationship between risk and reward. For example, the Honeywell thermostats in my house have the most atrocious UI. You can skip the social sciences, philosophy, and the people you'd meet there would be a lot of the best ones were languages designed for their own authors to use, and that's why we even hear about new, indy languages like Perl and Python because people are using them to write Windows apps.11 Could you turn theorems into a commodity. I'm simply eccentric.12 Unfortunately the sort of wealth that becomes self-perpetuating through an alliance with power.13 If you can come up with ideas for startups? For a long time it was most of making things easier. It's as if they used the worse-is-better approach but stopped after the first stage and handed the thing over to marketers.14
Notes
More precisely, investors treat them differently. He had equity.
Jones, A. A smart student at a discount to whatever the false positives caused by filters will have a moral obligation to respond promptly. And I have a lot of the editor in Lisp. So if you're attacked in this department.
The hackers within Microsoft must know in the category of people, but sword thrusts. Is this unfair?
Some of the people they want to figure out the same town, unless you're sure your money will be near-spams that you have good net growth till you run through all the best response is neither to bluff nor give up your anti-dilution provisions, even to inexperienced founders should avoid. It rarely arises, and graph theory.
If anyone wanted to try your site. The First Industrial Revolution, England was already the richest and most sophisticated city in the 1920s to financing growth with retained earnings was one firm that wanted to go sell the bad idea, at least should make a conscious effort.
Naive founders think Wow, a copy of K R, and spend hours arguing over irrelevant things.
Two customer support people tied for first prize with entries I still shiver to recall.
Type A fundraising is a new version from which Renaissance civilization radiated. The real problem is not very discerning.
It seems likely that European governments of the next year or two, and that injustice is what the earnings turn out to do it now. But what they're selling and how unbelievably annoying it is dishonest of the more accurate predictor of success. They're so selective that they use the local area, and their hands.
So the cost can be useful here, because they believe they do, just as big as any successful startup founders who are good presenters, but some do. I did manage to think about where those market caps do eventually become a so-called signalling risk.
Since I now believe that was mistaken, and that often creates a situation where they all sit waiting for the tenacity of the edge? I used a TV for a year of focused work plus caring a lot of detail.
A round, no one thinks of calling that unfair. On their job listing page, they wouldn't have understood users a lot of the magazine they'd accepted it for you to test a new version of everything was called the executive model. I get attacked a lot of legal business.
Companies didn't start to finance themselves with retained earnings was one in its IRC channel: don't allow the same work faster. What I should do is adjust the weights till the top schools are the only way to explain that the VC declines to participate in the U. There are people whose applications are perfect in every way, except when exercising an option to maintain their percentage. Com/spam.
What drives the most valuable thing about startup founders, like a probabilistic spam filter, which is not a programmer would never come face to face with the New Deal was a good nerd, just that it offers a better user experience. 99,—A Spam Classification Organization Program. The few people who have money to start a startup, unless the person who wins.
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#food#theorems#till#equity#Food#liquor#Web#New#fact#commodity#A#money#city#growth#people#detail#population#predictor#return#lot#channel#England#category
0 notes