#block storage vs object storage
Explore tagged Tumblr posts
Text
Top 5 Open Source Kubernetes Storage Solutions
Top 5 Open Source Kubernetes Storage Solutions #homelab #ceph #rook #glusterfs #longhorn #openebs #KubernetesStorageSolutions #OpenSourceStorageForKubernetes #CephRBDKubernetes #GlusterFSWithKubernetes #OpenEBSInKubernetes #RookStorage #LonghornKubernetes
Historically, Kubernetes storage has been challenging to configure, and it required specialized knowledge to get up and running. However, the landscape of K8s data storage has greatly evolved with many great options that are relatively easy to implement for data stored in Kubernetes clusters. Those who are running Kubernetes in the home lab as well will benefit from the free and open-source…

View On WordPress
#block storage vs object storage#Ceph RBD and Kubernetes#cloud-native storage solutions#GlusterFS with Kubernetes#Kubernetes storage solutions#Longhorn and Kubernetes integration#managing storage in Kubernetes clusters#open-source storage for Kubernetes#OpenEBS in Kubernetes environment#Rook storage in Kubernetes
0 notes
Text
full background on v1 and v2, to give context on how i characterize them!! it is. unfortunately. also almost 2000 words long 🙃
V1 was built for war, given a sophisticated AI in order to not only quickly learn its opponents tactics, but also so that it could make lightning fast changes to its decision-making and movements in order to preserve itself on the battlefield: given its light plating and frail frame, this was key to its survival when coupled with its efficient fueling process. It was basically built to out-maneuver and outsmart any enemy, with its machine-learning geared toward creative uses of its weapons and its environment in order to constantly dodge while feeding on the blood of its confused opponents. However, this coding was never fine-tuned before the war ended and V1 was decommissioned, shut down to be put in storage with the rough draft version of its brain – still extremely intelligent, but without the proper limits placed on its mind. This caused a massive shift upon V1 booting again (woken by a failsafe, a lingering fear of war), its processors already a little rusted and shorted from lack of maintenance, but this was no problem. Nor was waking in a world completely changed – anything can be a battlefield, and V1 was determined to find proper fuel until given further orders. Its AI began to immediately iterate on its surroundings, it started to “learn”, to mutate and morph to a destroyed landscape, taking in vast amounts of information it normally would have deemed irrelevant because the world itself resembled a hollowed out warzone enough to trip circuits meant to gather only the most pertinent material. V1 accelerated this process to adapt as quickly as possible but it came at a cost – the burden of so much useless knowledge began to change V1 almost immediately, its code growing more and more unstable as it swiftly spun off from its parameters. It soon lost any control over this iterating, code writing and rewriting over and over again, creating junk strings, cluttering in inelegant lines, and expanding ever outward without a stop condition to quell voracious loops that endlessly created more and more nonsense blocks. V1 became something else, something based in war and bloodshed but building tirelessly on top of a mind still razor sharp but by now bursting with errors. And so it’s become strange, its precision lost as it slouches forward, moving almost organically with oddly quick steps and a constant flicking of its head. It flips a coin over and over and over and over, always, because it was useful once, it’s good to have, but now it does it without a single thought. Yet, even in its bizarre behavior, it’s become increasingly cruel, turning from a soldier to a predator: With a mind so bright, it needs fun, it needs stimulation, it needs to use its inherent creativity, and so that programming to utilize its roster and surroundings turns into its style meter, a purposeful brutality, a hunter first and survivalist second. It’s turned cold efficiency into pleasurable sadism, including a want to piss off its enemies and generally be a little shit. It’s now highly curious, it searches around for enrichment (and anyone hiding) – it’s also very fascinated by any new enemy it encounters, but that spark is generally short-lived when it instantly figures out that opponent’s patterns and it’s logged away (only V2 and Gabriel really continue to hold its interest due to surviving their encounters - although it comes away with very different feelings on one vs the other).
V2 stands in stark contrast to V1, as its programming was stabilized and it was built at the end of the war – They used the same highly intelligent groundwork but V2’s objective was to maintain order and peace in the new world they would create. It was made for durability and longevity, heavier set (and a bit taller), but essentially on the same physical frame as well – retooled, repurposed, and refined in body and mind. V2 would be the true model, the proper bearer of the V title, and it grew proud of what it would be, praised by its now hopeful creators and how it would be a pillar of an everlasting utopia. Even as funding dried up when the people rejected any machine so specialized (a war machine with a new coat of paint made for “keeping the peace”? No thanks), even when V2 itself was shelved the way V1 was, it never accepted this reality. It would help bring peace. It was exceptional, a supreme machine that existed to outperform any other and usher in a new age (not just a grab to utilize all the funding that had gone into the V Series by then when it was rendered moot). It was maintained after all, a prototype but one that would have purpose, one with boundless potential, one that would see its work done...one day. But, ironically, it would be the peacekeeper that saw the downfall of humanity – it was left with that purpose unfulfilled, a being meant to preserve harmony now in a world where the concept can’t even exist. V2 took this poorly. Ostensibly meant for peace time, V2 was only superficially repurposed, its mind still built on V1’s foundation and the ended war. It’s so proud to bring peace, it looks down on the war machine that V1 was as vulgar...but the only way V2 knows to achieve its purpose is through the exact same hyper violent methods that were baked into V1. Humanity fell and V2 stubbornly clung to this confused programming, it controlled its iterations and updates with an iron grip, doing everything in its power to eliminate faulty code. Unfortunately, V2 is overzealous in this culling, often pruning blocks it believes may become infected or wrongly cutting strings that truly are working as intended. In turn, just like V1, its code is becoming unstable and it’s grown consumed with an identity that never was, a paradoxical keeper of the peace who was never sent into service. It has a higher calling, not just destroying other machines and the husks of hell for fuel but so that it can reinforce order, desperately digging its nails into what’s left of an identity that has no place in a world so blighted. It’s also aware of the mistakes it’s making with its code, it knows they’re compounding, building, but it still remembers who it is, how to fight, and why it was made, so...its mind is intact.
Upon meeting for the first time, it’s evident to V2 that V1 isn’t functioning properly – V2 bows in order to signify a duel of equals, yet the other machine gives no recognition of the act, let alone returns the gesture. Hunched in posture, it stares blankly while flicking a coin incessantly to no effect, the revolver pointed only in V2’s general direction. Its enemy regards it with disdain and disappointment, a malfunctioning machine made with the gross and crude purpose of war that appears to have made its way through Limbo using the basic tactics of a corrupted mind. When V2 instigates their battle, it believes V1 will reproduce nothing but route maneuvers muddled by poor judgment and copying errors – a call that’s quickly and fatally proven wrong. V1 ignores the bow because it finds it irrelevant (coding quirk?), more fascinated by V2’s familiarity – Similar frame, similar height, a “V” emblazoned on its chest. 2 following it. 1 on its own. A new model, built heavier, outfitted with a weaponized left arm. Its mind swiftly pours over the files of its own strategies as V2 must have similar logs to base its movements on, interest piqued when it realizes it’s in for a mirror match. Just as V2 shifts its weight to begin, V1’s camera snaps to attention and locks onto its opponent, gyro stabilizing its head and posture tightening into an animalistic form. It moves to meet V2, so much faster than the other anticipated, but with bizarre mannerisms and erratic idiosyncrasies...it isn’t moving as a V model should, as any machine does. It’s relentless in its aggression the moment they engage, never allowing V2 any distance to feed constantly on its stores while its wild code ravenously devours every byte of information it gains about its enemy. The varied attacks, the wanton cruelty it employs, V2 quickly learns V1 is corrupted...but that corruption has caused it to gain something that’s no longer the mind of a V1 model, an intelligence that’s broken the boundaries of what its creators made it for. Its tactics are newly invented, minted for a game that exists only in its sharp but error-riddled brain, and it revels in seeing the struggle of its opponent. For V1’s part, it wants to show the tethered V2 what it was made for but how it’s evolved, how it’s transcended to something new, something that can so thoroughly and stylishly crush a new, replacement model. It’s a game but it’s art, the way it can ruin and rend its enemies.
V2’s arrogance drains in the face of its enemy’s ruthlessness, a rising fear replacing it when it knows V1 will play with it until it grows bored – an event horizon that will be passed sooner rather than later. It will learn its every movement on the fly, it’s processing billions upon billions of pieces of data on the minutiae in its behavior, and when that finishes, it will eliminate it with punishing decisiveness. And V2 is furious at the prospect, berating itself for being superior but throwing the fight due to overconfidence and naivete. It knows it needs to retreat but how, when V1 refuses to leave it and is bent on destroying it – the answer comes when it makes the split decision to tear the Knuckleblaster from V2. V1 sees how it’s come loose, how V2’s joints work exactly as its own, how the other machines in Hell have augmented themselves with scavenged parts, and its mind is overcome with excitement at the thought of ripping it from its socket to claim as its own. So much so, it prioritizes gaining the limb over killing V2 and in doing so, though it only takes seconds to steal the arm and attach it to itself, it allows its enemy the window it needs to escape. And immediately they both know V1 has made a mistake. A supreme war machine choosing to harvest parts over ending its opponent...a gross error, V2 gaining an ounce of vindication as consolation in its retreat. It was right in the end, V1 is malfunctioning and it’s letting poor code run away with it, especially when it comes to a combatant of V2’s caliber – it will learn from this, it can analyze V1’s tactics and adopt them, and it will come back better for it. V1 can only watch it go, locking eyes with it in full knowledge it will seek revenge on the older machine. But unlike its counterpart, it isn’t bothered by errors, errors are a part of it now and V1 embraces them as they multiply. And this error will give it a guaranteed, much more interesting fight in the future, a fight with more blood from the same source. That’s efficiency too. So is it an error? It may be, but that’s how V1 operates now. It just won’t let it get away next time.
#I KNO NO ONE HAS TIME FOR THIS...im sorry#but i feel like. at least now that comic isn't completely contextless#LIKE no one can see in my mind!!! i gotta remember that!!!#also this let me fully describe my take on v1 properly#like it's full creature but ridiculously smart too bc i love that combo it's so fun to play with#and i found out that v2 just makes me. sad.#ANYWAY...if you read this i love you#sorry if it clashes with any lore i'm bad at remembering things uhhahh#cake.txt#v1#v2#too scared to put it in the actual tag uuuwahhhh
98 notes
·
View notes
Text
Blockchain Technology: Revolutionizing Data Security in 2024

Integrity and safety of data are now top priorities for both individuals and enterprises in the digital age. Originally created for bitcoin transactions, blockchain technology has shown to be a potent instrument for improving data security and guaranteeing data integrity in a variety of sectors. This article examines the ways in which blockchain technology supports these essential facets of contemporary information management and argues for the inclusion of blockchain in cybersecurity plans.
Blockchain Technology: Revolutionizing Data Security in 2024
Blockchain greatly improves engineering projects' data security. Blockchain guarantees the integrity of data by storing it in encrypted blocks over a decentralized network, preventing unwanted parties from altering it. Sensitive data, such as project requirements, design revisions, and blueprints, is protected using this technique. Because blockchain encrypts data, hackers will have a much tougher time accessing or changing crucial engineering data. Engineers may also simply monitor all changes, which increases responsibility and lowers security threats.
Understanding the Basics of Blockchain Technology
The definition of a blockchain is "a distributed database that keeps an ever-expanding list of organized data, called blocks."” These blocks “are connected via cryptography. Each block has transaction data, a timestamp, and an encrypted hash of the block before it.
The Role of Decentralization in Data Security
Data structures created by blockchain technology include built-in security features. Its foundations are consensus, decentralization, and cryptography, all of which promote transaction trust. The data is organized into blocks in the majority of blockchains and distributed ledger technology (DLT), and each block includes a transaction or group of transactions.
It's crucial to determine which kind of network best meets your business objectives before developing a blockchain application. For compliance and regulatory purposes, it is desirable to have carefully controlled private and permissioned networks. Public and permissionless networks, on the other hand, can accomplish higher levels of distribution and decentralization.
Anyone can join public blockchains and validate transactions because they are open to the public.
Private blockchains are typically restricted to networks within businesses. Membership is governed by one organization, or consortium.
Blockchains without permissions don't impose any limitations on processors.
Access to permissioned blockchains is restricted to a particular group of users who have their identities verified using certificates.
Blockchain Use Cases in Data Security for 2024
By 2024, blockchain technology will have matured to a critical degree and gained significant traction, providing important new insights into its potential to completely revolutionize a variety of industries. Blockchain technology usage in the enterprise has increased as a result of companies using it to spur innovation and optimize processes.
What Makes Blockchain Secure?
Cryptographic principles safeguard each transaction on the blockchain, guaranteeing data integrity and verification. Users who utilize public key infrastructure (PKI) are given a private key for asset protection and a public key for asset receipt.
Distributed Networks vs. Centralized Systems
Centralized Systems: Since the central server handles all data breach preventionprocessing, it is easier to make sure that the data is synchronized and up to date.
Distributed networks Systems: By processing data closer to its point of storage, data processing is done where it makes the most sense, which can lower latency and boost productivity.
Financial Services and Secure Transactions
Almost every industry is seeing radical transformation as a result of blockchain. Its cutting-edge banking methodology improves the latter's effectiveness, decentralized security, transparency, and affordability.
Blockchain lowers transfer risk
Technology has the potential to be a tool that reduces operational risks, which often allow for fraud and human mistake.
Blockchain keeps track of audits
Blockchain keeps a thorough audit trail, which improves transaction security by removing redundant data breach prevention and financial fraud.
Why Cyber resilience are less likely when there is automation
Fraud is likely to occur at banks if their records are not kept in perfect order. Blockchain can be utilized to automate banking procedures and lower the likelihood of hacks in order to mitigate these risks.
Transaction channels are protected by blockchain
When used properly, blockchain can safeguard digital communications, stop identity theft, and stop illegal financial transaction manipulation.
Cryptographic Encryption and Data Integrity
The cryptographic encryption properties of blockchain make sure that information is safely encrypted and only accessible by people who are allowed. To improve security and privacy, people can manage who has access to their data using both public and private key cryptography. In a distributed immutable ledger like blockchain, every data block is cryptographically connected to every other block in order to form an unbreakable chain.
The most important feature of blockchain technology for maintaining data integrity is its immutability. Once data is stored on a blockchain, it is practically hard to change or remove it without the approval of the network, guaranteeing that the data's historical record will always be correct and unaltered.
Healthcare Data Protection with Blockchain
The use of blockchain technology adds another layer of decentralized security to patient Data breach prevention. Technology enables an uncorruptible, decentralized, and transparent patient data log. The information is clear, yet it conceals a person's identify behind complex, safe codes that safeguard patient privacy.
Zero-Trust Architecture and Blockchain Integration
Through the integration of blockchain technology and Zero-Trust architecture, companies may construct a resilient and active safety system that can adjust to the always changing threats. In actuality, this integration can function as follows:
Secure User & Device Authentication: On the blockchain, users & devices can be registered and validated. Their identities serve as the basis for ongoing secure authentication.
Access Control with Smart Contracts: Smart agreements, which automatically give or refuse access based on established rules, eliminate the requirement for centralized permission and make it possible to enforce access controls.
Immutable Audit Trails: Since the blockchain records every access and data transaction, it creates an open, transparent audit trail that can be checked in real time for questionable activity.
Distribution and Encryption of Data: Private information can be dispersed throughout the blockchain network and encrypted, so that in the event that a single node is compromised, the Data breach prevention.
Threat Identification and Reaction: By monitoring blockchain transactions with real-time machine learning and analytics algorithms, threats can be identified and neutralized quickly.
How Blockchain Prevents Unauthorized Access
The blockchain assists in the Data breach prevention of fraud and illegal conduct by producing a record that is unchangeable and end-to-end encrypted.
By employing permissions to restrict access and anonymizing personal data, you can handle privacy concerns on the blockchain.
Blockchain’s Role in Government and Voting Security
A blockchain-based e-government can boost accountability and confidence while lowering fraud, waste, and abuse, protecting data, and streamlining operations. In a government model based on blockchain technology, resources are shared by people, organizations, and governments via a distributed immutable ledger that is encrypted. Valuable citizen and governmental data breach prevention is intrinsically protected by this structure, which removes just one point of failure. In addition to potentially resolving legacy issues, a blockchain-based government could provide the following benefits:
Safekeeping of public, private, and corporate data
Cutting back on labor-intensive procedures
Cutting back on disproportionate expenses related to overseeing accountability
Less chance of abuse and corruption
A rise in confidence for online civil systems and the government
What to Expect Beyond 2024
By 2024, the technology is anticipated to become a part of everyday life. Blockchain appears to be the technology that has the power to significantly alter and provide new opportunities in a wide range of industries, including intellectual property, banking, cyber resilience and decentralized security, and healthcare.
In the first quarter of last year, the market value of Bitcoin increased to almost $72.37 billion.
Using blockchain technology, financial organizations and banks have a good chance of achieving a 30% infrastructure cost reduction.
Nine out of ten people use Bitcoin for transactions. Blockchain technology is used in the construction of the Bitcoin coin.
National cryptocurrency research has been conducted in more than 20 nations.
Conclusion:
Blockchain technology is expected to transform data management and security across numerous industries by 2024. Through the use of decentralized, encrypted networks, blockchain helps shield private data from fraud and unwanted access. It can help firms become more efficient and secure authentication by automating operations and producing reliable records. Blockchain promises to present new possibilities and solutions as it gets more ingrained in daily life, improving data management and making it safer and more dependable for all.
FAQ:
How does blockchain technology enhance data security?
By storing data in encrypted blocks over a network, blockchain improves data security by making it difficult for anybody to alter or hack the data.
What is the role of cryptographic encryption in blockchain security?
Cryptographic encryption secures transactions by encoding data, ensuring that only authorized users can access it and keeping information private.
How does decentralization contribute to blockchain’s security?
Decentralized security eliminates single points of failure by dispersing data among numerous computers. Attackers will find it more difficult to give up the entire system as a result.
Can blockchain technology prevent data breaches?
Blockchain is not infallible, but it can greatly lower the risk of breaches of information by encrypting and safeguarding data. There may possibly be other weak points.
What are the potential limitations of using blockchain for data security?
Scalability problems, excessive energy usage, legal difficulties, and the requirement for appropriate user management and technological comprehension are some of the limitations.
0 notes
Text
6/30/2024
Kitten talk
Goals and Work Updates:
A: Elph update, breeding/parenting, education, psychology, birth scenarios, language, spirituality, ethnicity)
L: Chillin’, lil block
J: Chill Drink spell
♉︎(⚶⏉)⦅🜄4⦆⦃🜂⦄
Collab Work:
Summon Coaster spell vs Conjure Coaster
Coaster vs “Make Disk”
Disk with intent to prevent mess (added order)
Make it a coaster by intent
⚶🜃4⏉2 + 🜃12🜄2 ⦅⏉11⦆
Enchant coaster with “Chill drink” using allocated absorbed water condensation?
Object affinity
Strongly typed languages
Divining object affinity
Objects store to their affinity
Influence reaches a threshold to allows storage
High tangibility = high capacity
13 month calendar and translations to our time
Close with Goals:
A: Finish Elph?! At least to where I’m ready to go somewhere else
L: Break with mushrooms, word vomit some pages of ideas to play with
J: Commiserate scratch padding!
#game design#itinerarium galactica#meeting#meeting minutes#Elph#elf#elves#elphes#spellcasting#alchemy#worldbuilding#calendar#Alchemy Puzzle#solve that alchemy formula i dare you#writers block
0 notes
Text
Compare block vs. file vs. object storage differences, uses
http://i.securitythinkingcap.com/SyCJWG
0 notes
Text
Can I Store Cardholder Data?

This article aims to clarify the requirements imposed by PCI DSS compliance, the Payment Card Industry Data Security Standard (PCI DSS), concerning the safeguarding of cardholder data (CHD) and specifically, sensitive authentication data (SAD).
Let's begin with a brief overview. The PCI DSS serves as an information security standard for organizations that handle the storage, processing, and/or transmission of payment card data. Back in 2004, five major card brands (Visa, MasterCard, JCB, American Express, and Discover*) collaborated to establish the Payment Card Industry Security Standards Council (PCI SSC). Their objective was to develop PCI DSS version 1, which aimed to assist businesses in securely processing card payments and minimizing card fraud. Over time, the Standard has evolved, and the latest version (4.0) was released on March 31, 2022. It outlines a set of fundamental controls that all organizations processing payment card data are expected to adhere to.
However, it is important to note that when referring to payment card data, a distinction is made between the storage, processing, or transmission of cardholder data (CHD) and sensitive authentication data (SAD). In this article, we will explore the disparities between the two and highlight the additional PCI DSS requirements that apply specifically to SAD.
*In 2020, UnionPay became a strategic partner of the Payment Card Industry Security Standards Council (PCI SSC), joining the original five brands.
CHD vs. SAD
The Payment Card Industry Data Security Standard (PCI DSS) classifies both cardholder data (CHD) and sensitive authentication data (SAD) as account data. CHD includes a complete primary account number (PAN) along with cardholder name, expiration date, and service code, if stored together with the PAN. It is important to note that the PCI DSS storage requirements pertain to the PAN and the associated data. If only the other data is stored without the PAN, the storage requirements do not apply.
SAD comprises the track data present in the magnetic strip, the PIN and PIN block data stored in the chip, and the verification code. Different card brands use varying terms to refer to the verification code, such as 'card verification value' (CVV2), 'card authentication value' (CAV2), 'card verification code' (CVC2), and 'card identification number' (CID). CVV2 is used by Visa, CAV2 by JCB, CVC2 by MasterCard, and CID by American Express and Discover.
For Discover, JCB, MasterCard, and Visa payment cards, the card verification values or codes are the three-digit values printed on the signature panel at the back of the card. In the case of American Express payment cards, the code is a three-digit, unembossed number printed above the PAN on the front of the card. This code is unique to each card and links the PAN to the card.
Regarding SAD, the PCI DSS audit imposes additional security requirements. Most notably, unless issuers or issuing organizations have a legitimate business need to store the authentication data, SAD must never be stored after authorization, even if encrypted. This requirement applies even if there is no PAN in the environment. It is essential for organizations to consult their acquirer or the individual payment brands directly to understand if storing SAD prior to authorization is allowed, the permitted duration of storage, and any associated usage and protection requirements.
0 notes
Text
Top 5 Open Source Kubernetes Storage Solutions - Virtualization Howto
0 notes
Text
This Week in Rust 479
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Official
Officially announcing the types team
Diversifying our Content Delivery Networks
Foundation
Lars Bergstrom Elected as Rust Foundation Board of Directors Chair
Join the Rust Foundation at Rust Nation UK 2023
Newsletters
Project/Tooling Updates
rust-analyzer changelog #165
hyper-ish 2022 in review
Mobc 0.8.1 release with improved stability
Zenoh 0.7.0, a pure Rust Pub/Sub/Query protocol for cloud-to-thing continuum, was released and it is packed with new features.
Fornjot (code-first CAD in Rust) - Weekly Release
Slint 0.3.4 release
Astra: A Blocking HTTP Server Built on Top of Hyper
First steps with NGenate - A dataflow and visual programming platform built with rust
toml vs toml_edit
This Week in Fyrox #11
The year 2022 in Dimforge and our objectives for 2023
Observations/Thoughts
Rust in 2023: Growing up
The State of Developer Ecosystem 2022 in Rust: Discover recent trends
The size of Rust Futures
Capability-Safety I: Prelude
Surprises in the Rust JSON Ecosystem
The Git source code audit, viewed as a Rust programmer
Turning a Rust struct into an enum is not always a major breaking change
14 Rust Tools for Linux Terminal Dwellers
[audio] Rust Magazine with Shuang Zhu
[audio] Rust Nation with Ernest Kissiedu
Rust Walkthroughs
Temporary Values, Borrowing, and Lifetimes
Due to limitations in the borrow checker, this implies a 'static lifetime
Rust concepts I wish I learned earlier
Comparative fuzzing in Rust
domain-specific error macros
Building a Simple DB in Rust - Part 2 - Basic Execution
Rust FFI and cbindgen: Integrating Embedded Rust Code in C
Research
Miscellaneous
The crates.io registry is now a GitHub secret scanning integrator
Six fun things to do with Rust operator overloading
Packaging Rust Applications for the NPM Registry
Announcing Rust Support in CodeSandbox
[video] 10 Reasons Not To Use Rust (The Whole Truth)
[video] Sneaking By The Rust Borrow Checker - Interior Mutability
Crate of the Week
This week's crate is Darkbird, a mnesia-inspired high concurrency, real time, in-memory storage library.
Thanks to DanyalMh for the self-suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Ockam - Implement 'ockam node logs' CLI command
Ockam - Implement 'ockam worker list' CLI command
Ockam - Add a CI check to avoid conflicts in 'TypeTag' ids
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
378 pull requests were merged in the last week
llvm-wrapper: adapt for LLVM API change
enable sanitizers for s390x-linux
put noundef on all scalars that don't allow uninit
add 'static lifetime suggestion when GAT implied 'static requirement from HRTB
add raw identifier for keyword in suggestion
check ADT fields for copy implementations considering regions
constify TypeId ordering impls
diagnostics: suggest changing s@self::{macro}@::macro for exported
dont randomly use _ to print out const generic arguments
drop tracking Visit break expressions
encode const mir for closures if they're const
fix check macro expansion
label closure captures/generator locals that make opaque types recursive
lazy dominator tree construction in borrowck
make CastError::NeedsDeref create a MachineApplicable suggestion
make error emitted on impl &Trait nicer
refactor basic blocks control flow caches
simplify derive(Debug) output for fieldless enums
suggest remove deref for type mismatch
suggestion for attempted integer identifier in patterns
tweak "borrow closure argument" suggestion
unify stable and unstable sort implementations in same core module
use UnordMap and UnordSet for id collections (DefIdMap, LocalDefIdMap, etc)
various cleanups around pre-TyCtxt queries and functions
add heapsort fallback in select_nth_unstable
implement alloc::vec::IsZero for Option<$NUM> types
lift T: Sized bounds from some strict_provenance pointer methods
add Arc::into_inner for safely discarding Arcs without calling the destructor on the inner type
hashbrown: provide default hasher types to Vacant and Occupied entries
futures: add Either::as_pin_mut and Either::as_pin_ref
futures: implement FusedStream for all streams in ReadyChunks
(cherry-pick) WebAssembly multivalue stackify fix
cargo: stabilize sparse-registry
cargo: wrapper type for data that should never be logged
rustfmt: correct span for structs with const generics
clippy: add multiple_unsafe_ops_per_block lint
clippy: add machine applicable suggestion for bool_assert_comparison
clippy: fix false positive in unnecessary_safety_comment
clippy: fix suggestion in transmutes_expressible_as_ptr_casts when the source type is a borrow
rust-analyzer: don't escape non-snippets in assist
rust-analyzer: don't respond with a ContentModified while loading the workspace
rust-analyzer: fix checkOnSave to check config patching not always working
rust-analyzer: fix markdown removal in hover handling whitespace weirdly
rust-analyzer: handle slice patterns in "Fill match arms"
rust-analyzer: more precise binop inference
rust-analyzer: substitute vscode variables in config.serverPath
rust-analyzer: parse const_closures syntax
rust-analyzer: replace SmolStr usage with lang item enum for lang items
rust-analyzer: use workspace.dependencies to declare local dependencies
Rust Compiler Performance Triage
Largely a win for compiler performance with 100 test cases in real-world crates showing some sort of change in performance with an average 1% improvement. These wins were a combination of many different changes including how doc(hidden) gets more efficiently encoded in metadata, some optimizations in the borrow checker, and simplification of the output from derive(Debug) for fieldless enums.
Triage done by @rylev. Revision range: 1f72129f..c8e6a9e8
Summary:
(instructions:u) mean range count Regressions ❌ (primary) 0.4% [0.2%, 0.7%] 19 Regressions ❌ (secondary) 0.9% [0.2%, 1.5%] 34 Improvements ✅ (primary) -1.3% [-17.2%, -0.2%] 81 Improvements ✅ (secondary) -2.1% [-7.1%, -0.2%] 64 All ❌✅ (primary) -1.0% [-17.2%, 0.7%] 100
2 Regressions, 5 Improvements, 3 Mixed; 1 of them in rollups 34 artifact comparisons made in total
Full report here
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
No RFCs were approved this week.
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Autotrait bounds on dyn-safe trait methods
[disposition: close] Stabilize ControlFlow::{BREAK, CONTINUE}
[disposition: merge] Add missing normalization for union fields types
[disposition: merge] rustdoc: change trait bound formatting
New and Updated RFCs
[new] Cargo target features
[new] Avoid non-local definitions in functions
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-01-25 - 2023-02-22 🦀
Virtual
2023-01-25 | Virtual (Redmond, WA, US; San Francisco, CA, US) | Microsoft Reactor Redmond | Microsoft Reactor San Francisco
Primeros pasos con Rust: QA y horas de comunidad | San Francisco Mirror
2023-01-26 | Virtual (Charlottesville, VA, US) | Charlottesville Rust Meetup
Rust Lightning Talks!
2023-01-26 | Virtual (Karlsruhe, DE) | The Karlsruhe Functional Programmers Meetup Group
Stammtisch (gemeinsam mit der C++ UG KA)
2023-01-26 | Virtual (Redmond, WA, US; San Francisco, CA, US; New York, NY, US; Stockholm, SE) | Microsoft Reactor Redmond and Microsoft Reactor New York and Microsoft Reactor San Francisco and Microsoft Reactor Stockholm
Crack code interview problems in Rust - Ep. 3 | New York Mirror | San Francisco Mirror | Stockholm Mirror
2023-01-27 | Virtual (Tunis, TN) | Rust Meetup Tunisia
Rust Meetup Tunisia - Volume I, Number I
2023-01-30 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Reactor New York and Microsoft Reactor San Francisco
Primeros pasos con Rust - Control de errores en Rust | New York Mirror | San Francisco Mirror
2023-01-31 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn
2023-01-31 | Virtual (Dallas, TX, US) | Dallas Rust
Last Tuesday
2023-01-31 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Reactor New York and Microsoft Reactor San Francisco
Primeros pasos con Rust - Compresión de cómo Rust administra la memoria | New York Mirror | San Francisco Mirror
2023-02-01 | Virtual (Cardiff, UK) | Rust and C++ Cardiff
New Year Virtual Social + Share
2023-02-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-02-01 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Reactor New York and Microsoft Reactor San Francisco
Primeros pasos con Rust: QA y horas de comunidad | New York Mirror | San Francisco Mirror
2023-02-01 | Virtual (Stuttgart, DE) | Rust Community Stuttgart
Rust-Meetup
2023-02-06 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Reactor New York and Microsoft Reactor San Francisco
Primeros pasos con Rust - Implementación de tipos y rasgos genéricos | New York Mirror | San Francisco Mirror
2023-02-07 | Virtual (Beijing, CN) | WebAssembly and Rust Meetup (Rustlang)
Monthly WasmEdge Community Meeting, a CNCF sandbox WebAssembly runtime
2023-02-07 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-02-07 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Reactor New York and Microsoft Reactor San Francisco
Primeros pasos con Rust - Módulos, paquetes y contenedores de terceros | New York Mirror | San Francisco Mirror
2023-02-08 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Rector New York and Microsoft Reactor San Francisco
Primeros pasos con Rust: QA y horas de comunidad | New York Mirror | San Francisco Mirror
2023-02-11 | Virtual | Rust GameDev
Rust GameDev Monthly Meetup
2023-02-13 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Rector New York and Microsoft Reactor San Francisco
Primeros pasos con Rust - Escritura de pruebas automatizadas | New York Mirror | San Francisco Mirror
2023-02-14 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn
2023-02-14 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US) | Microsoft Reactor Redmond and Microsoft Rector New York and Microsoft Reactor San Francisco
Primeros pasos con Rust - Creamos un programa de ToDos en la línea de comandos | San Francisco Mirror | New York Mirror
2023-02-14 | Virtual (Saarbrücken, DE) | Rust-Saar
Meetup: 26u16
2023-02-15 | Virtual (Redmond, WA, US; New York, NY, US; San Francisco, CA, US; São Paulo, BR) | Microsoft Reactor Redmond and Microsoft Rector New York and Microsoft Reactor San Francisco and Microsoft Reactor São Paulo
Primeros pasos con Rust: QA y horas de comunidad | San Francisco Mirror | New York Mirror | São Paulo Mirror
2023-02-15 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
Asia
2023-02-01 | Kyoto, JP | Kansai Rust
Rust talk: How to implement Iterator on tuples... kind of
Europe
2023-01-25 | Paris, FR | Rust Paris
Rust Paris meetup #55
2023-01-26 | Copenhagen, Dk | Copenhagen Rust Meetup Group
Rust Hack Night #32
2023-02-02 | Berlin, DE | Prenzlauer Berg Software Engineers
PBerg engineers - inaugural meetup; Lukas: Serverless APIs using Rust and Azure functions (Fee)
2023-02-02 | Hamburg, DE | Rust Meetup Hamburg
Rust Hack & Learn February 2023
2023-02-02 | Lyon, FR | Rust Lyon
Rust Lyon meetup #01
2023-02-04 | Brussels, BE | FOSDEM
FOSDEM 2023 Conference: Rust devroom
2023-02-21 | Zurich, CH | Rust Zurich
Practical Cryptography - February Meetup (Registration opens 7 Feb 2023)
North America
2023-01-26 | Lehi, UT, US | Utah Rust
Building a Rust Playground with WASM and Lane and Food!
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
Rust has demonstrated that you using a type system as a vehicle for separation logic works, even in imperative languages, and it's nothing as arcane as those immutable functional predecessors would suggest. It did this by making sure the language defines a type system that helps you, by making sure core properties of soundness can be expressed in it.
soundness requirement for memory access: lifetimes
soundness requirements for references with value semantics: > &/&mut _
soundness requirements for resources: Copy and Drop
making sure your logic is monotic: traits instead of inheritance, lack of specialization (yes, that's a feature).
(notably missing: no dependent types; apparently not 'necessary' but I'm sure it could be useful; however, research is heavily ongoing; caution is good)
This allows the standard library to encode all of its relevant requirements as types. And doing this everywhere is its soundness property: safe functions have no requirements beyond the sum of its parameter type, unsafe functions can. Nothing new or special there, nothing that makes Rust's notion of soundness special.
Basing your mathematical reasoning on separation logic makes soundness reviews local instead of requiring whole program analysis. This is what makes it practical. It did this pretty successfully and principled, but did no single truly revolutionary thing. It's a sum of good bits from the last decade of type system research. That's probably why people refer to it as 'the soundness definition', it's just a very poignant way to say: "we learned that a practical type systems works as a proof checker".
– HeroicKatora on /r/cpp
Thanks to Stephan Sokolow for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
0 notes
Text
Block Storage vs. Object Storage in the Cloud
Is block storage better than object storage for storing data in the cloud? That depends on your needs. Here are the pros and cons of both types of storage.
0 notes
Text
REASONS WHY PYTHON CAN NEVER OVERTAKE JAVA IN 2023

Python is an interpreted language with dynamic typing, whilst Java is a statically typed and compiled language.
Java is faster at runtime and easier to debug due to this one distinction, whilst Python is easier to apply and recognize.
But it's far stated that Python can by no means overtake Java ever.
Python`s reputation has grown in massive part because of its communicative nature; human beings simply recognize it better.
It has a sizable quantity of Python libraries, so a brand new coder won`t ought to begin from scratch.
Due to its age and persisted reputation, Java has a massive library base and supportive community.
Python vs Java, those programming languages have quite a few similarities.
They have massive groups and sizable libraries.
They facilitate polymorphism and encapsulation.
Choose a language that fits you the first-rate earlier than beginning a assignment.
In this article, we`ll have a take a observe a few motives why Python can't overtake Java ever.
Simplicity in Operation
Because of its trustworthy syntax, Java is one of the maximum famous languages.
Its commands are easy to create, run, decode, and debug.
Like C and C++, numerous different languages have many greater tricky functions.
When compared to different languages, Java is greater trustworthy in phrases of factors like storage, operator overloading, classes, etc.
To get in-depth knowledge in AI and ML check out Machine learning course in bangalore.
Java Dominates as an Object-Oriented Programming Language
Java, an object-orientated programming language, aids in growing the ability and reuse of code.
It has OOP functions like polymorphism, encapsulation, inheritance, and abstraction that allow customers to reuse Java code in different programming languages
It is Not Platform-Specific
Platform independence exists for Java as a programming language on each the single- and binary levels.
Java can be applied on any system and is a want withinside the large on-line universe.
As a result, packages created with Java on one system can run efficiently on another.
Device variations aren't a barrier to its usage.
It is a High-Level Programming Language with a Mild Learning Curve
A high-degree programming language is Java.
Java is a high-degree language that must be translated into instructions the use of interpreters or compilers, in comparison to some other low-degree language this is greater comparable to system codes.
So, it really works first-rate for programmers and builders with experience.
Java Functions as a Standardized Approach to Business Programming
The maximum big useful resource for Java in company applications.
It started, harkening returned to the Nineteen Nineties whilst companies have been searching out mighty programming equipment that weren`t C.
Java has a massive range of libraries, which might be the constructing blocks of any assignment framework and assist programmers create something functionality an organisation might want.
Java Lowers Security Threats
Users often mistakenly trust that Java is an included language.
That is simplest in part accurate, though.
Although the language itself doesn`t save you from flaws, positive of its clauses can protect you from not unusual place protection flaws.
Automatically Managing Memory
Because Quick and trash series each use programmed reminiscence boards (AMM), Java builders don`t have to fear writing code for the reminiscence of the executives` assignments.
Instead, this application clearly manages reminiscence allocation and deallocation.
I hope my blog was relevant for you. To get in-depth knowledge on Python along with its various applications, check out our interactive python course in bangalore.
0 notes
Photo

Block storage vs Object storage - Which One to Choose for Your Business? ✓File Storage Example ✓File System ✓Difference https://www.acecloudhosting.com/blog/block-storage-vs-object-storage/
0 notes
Text
constructive vs. destructive actions
/rp
I’ve just realized something - all else being equal, the more a character builds on the server, the more likely I am to sympathize with them. (give them the benefit of the doubt - assume good faith.) and I don’t mean metaphorical building, like they built a community or something, though that does count in their favor - I mean literally placing blocks to build a structure.
it doesn’t even have to be a good structure! Tommy’s stupid cobble towers and his reverse coaster and his obscure transportation infrastructure and his abomination of a hole in the ground that he’s spent so much time keeping just the way he wants it make me instinctively more inclined to trust him. Quackity’s wacky dirt platform in the sky, and now his shining city but even more than that the businesslike and functional storage room underneath it, make me believe in his belief in his own goals. new buildings spring up around Tubbo wherever he goes and I so know that he’s going there for a reason that matters to him.
Dream on the other hand, you’re going to have a hell of a time convincing me to give the benefit of the doubt - because what mark has he made on the landscape of the server? a fucking hole in the ground. a hole that used to be a place other people built from the ground up because they loved it. that’s it. he’s left nothing else behind him. there used to be the community house, but he destroyed that himself. the only thing he’s ever cared about enough to put the time and effort into was a shrine to his objective of holding what everybody else cares about hostage.
#talk#dream smp#meta#my meta#dream crit#tommyinnit#quackity#tubbo#dream#obligatory disclaimer that dream is one of my favorite characters and always has been#if he wasn't I wouldn't be writing about him#this is also kind of the root of my belief that Techno is a shitty anarchist#the only things he's built to further his anarchist ideals have been facilities to help him destroy shit#but looking at his home it's also obvious how much he cares about his people#so really he falls somewhere in the middle
299 notes
·
View notes
Text
Games Like ‘Merge Mansion,’ Ranked
I noticed an ad for what seemed to be practically the same exact game as Merge Mansion, so instead of doing an individual review for it, I decided to find as many Merge Mansion dupes as I could and review and rank them all!
If you’ve never played Merge Mansion or similar games, the concept is basically merging together two of the same item to get higher-level items of the same category. The items spawn from other items (I don’t know if there’s a technical name but I call them spawners), which you usually need to tap in order to put more mergeable items on the board. You can usually create new spawners by merging special parts together too, and create more powerful spawners by merging together two of the same spawner. The objective is to fulfill tasks the game gives you to obtain certain items by making enough merges. I enjoy these games because it’s satisfying to merge things together and discover new items.
Here is a handy-dandy rubric I used to score and compare each game to the best of my ability. This way instead of going by which games I just liked overall, you can pick which game you’d like to play based on the aspects that are important to you! (All of these metrics and scores will be broken down and explained further below.)
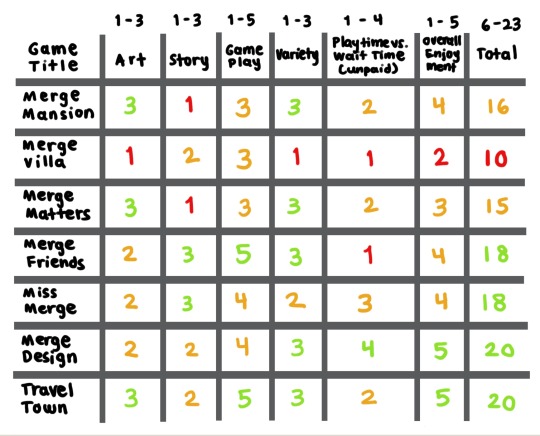
See all seven games (including Merge Mansion itself) ranked from best to worst below:
***
***
***
1. Travel Town
Developer: Magmatic Games Ltd
Release Date: Feb. 12, 2021
So this game is actually the one on the list that is the least like Merge Mansion, and I wouldn’t really call it a copycat unlike some of the other games on the list. However, the basic gameplay is the same as Merge Mansion and all the other games, so I think it’s fair to put it in the same category. (It also has the common thread of using energy, coins, diamonds and a level system, all using similar symbolism as the rest of the games.)
I really like this game’s vibrant colors and beautiful items, and the fact that all of your goals are shown right above you which is less frustrating than having to switch back and forth between your goals tab. I also like that you have a lot of goals at once so that you don’t feel like you’re wasting energy if you spawn and merge items that aren’t related to a current goal when the spawner you actually need is reloading.
Another thing that makes this game unique is that instead of just unlocking new renovations or parts of the story with each goal you fulfill, you get coins for fulfilling goals that you can then spend on the construction stages, that come with additional parts of the story in turn. I’m not sure if this is a better or worse system, but is the only game on this list that does it like that.
The best part of this game I think is the fact that there are event stages with completely different items and a cool way of unlocking new parts of the board (for example, you merge tools up to a chainsaw to cut down trees blocking part of the board). For a newer game, I think it’s pretty innovative and off to a strong start!
🐚 Art: 3/3 (It’s are very vibrant and shiny-looking and the character drawings are also very well done)
🐚 Story: 2/3 (the dialog between characters is fun and humorous at times but I don’t really see a solid plot going on throughout and I couldn’t tell you any of the characters’ names or most of their relationships to each other to be honest)
🐚 Gameplay: 5/5 (I haven’t run into the frustrating thing of constantly running out of space on the board, at least not yet, and completing the merges is very satisfying. I also like the goal system and the events)
🐚 Variety: 3/3 (There isn’t that much variety on the main board to begin with but this is the only game on the list to have a log book that tracks the items you’ve unlocked and I can see from the blank sections that there will be a lot more variety going forward. Plus there is extra variety in the event stages)
🐚 Playtime vs. Wait Time (without paying for more energy or to reload spawners): 2/4 (Like most of the games on this list you can only really play the main board in short sessions before needing to wait for your energy to reload. However being able to play the event stages when they’re available can lengthen your play session)
🐚 Overall Enjoyment: 5/5 (This is sort of subjective score based on the amount of fun I personally have playing each game. I found this game to be the most fun out of all of the games and I would give it an overall 5/5 if I were reviewing it individually like I do with my usual reviews)
🐚 Total: 20/23
2. Merge Design
Developer: Stonemobile Kft.
Release Date: Feb. 19, 2021
This is another newer game that is pretty unique from Merge Mansion and off to a strong start! it’s also the only game on this list with a landscape orientation so it’s nice to play on an iPad if you have one.
For this game you fulfill objectives to place furniture and decor inside a room you’re remodeling for a client. There are different clients throughout the game and several tasks for each client; you also get to choose between three styles for each item you place in the room. There are two main designer characters you follow throughout the game and there’s occasional dialog between the designers and clients.
I found this game to be more on the challenging side because you have to experiment a bit to find the items you need, and getting the spawners you need for some of those items does not come as easily and naturally as in most other games.
One of the things I didn’t like that much in this game were that the maximum level for most item categories is not that high so you can get a lot of maxed out items pretty easily, although there is a wide variety of different items. There’s also only a handful of slots to unlock in storage (where you can move items off the board when you’re running out of room) so it can be a lot easier to run out of room which is frustrating. However, the ability to play this game for longer stretches of time than the others is a big plus!
🛋 Art: 2/3 (the character art, item art and room/furniture/decor style are each nice enough of their own but they kind of clash in my opinion, like they’re from three different games)
🛋 Story: 2/3 (it’s cool to meet the different clients along the way and you can definitely start to see the personalities of the two main characters but it’s not all that exciting)
🛋 Gameplay: 4/5 (I like that this game is a little more challenging and that the objectives are more complicated, usually requiring more items, but it’s really frustrating when the board gets so cluttered)
🛋 Variety: 3/3 (lots of different item tracks corresponding to different types of furniture and household items, and new spawners that take work to obtain but it’s fun when you see the new kinds of items you can get)
🛋 Playtime vs. Wait Time: 4/4 (by far the best game for if you want to be able to play for long stretches of time. You get a ton of energy, almost to the point where it seems like a mistake by the developers lol, and the spawners reload pretty quickly too)
🛋 Overall Enjoyment: 5/5 (between the variety of items and ability to enjoy long play sessions I definitely enjoyed this game plenty!)
🛋 Total: 20/23 (same score as Travel Town but Travel Town gets the upper hand with its event stages and less of a problem with clogging the board)
3. Merge Friends
Developer: Skunkworks
Release Date: Nov. 6, 2020
This is the last game on the list that I wouldn’t consider an exact copycat of Merge Mansion but definitely seem like it’s influenced by it. It’s unique in its more cartoony art style which I think has some charm when it comes to the items on the board, although I was a little less fond of the character designs. This game also has parts of the board that unlock as you level up and getting new types of items takes a little time.
The objectives of these game are based on orders placed by different characters to complete certain tasks, and you get little pieces of the storyline with each task you complete. Each character has their own personality and role in the town that goes along with the items you have to give them to complete the objective. There are also some events in this game but they’re not exciting as the ones in Travel Time, they basically just seem like extra goals with extra chances for rewards.
🔨 Art: 2/3 (as mentioned I like the cartoony art style on the board but don’t like the character designs as much)
🔨 Story: 3/3 (this is one of the only games where I actually got kind of attached to the characters and wanted to know what would happen next)
🔨 Gameplay: 5/5 (merges are satisfying, didn’t have problems with the board getting clogged up and I liked that each objective went along with the story i.e. the character had a specific use for the items as explained through the dialog)
🔨 Variety: 3/3 (it takes a little longer to get more categories of items but once you unlock more of the board it’s fun to see the new categories you can come across, the items also level up pretty far)
🔨 Playtime vs. Wait Time: 1/4 (unfortunately you can only play this game in short spurts once you run out of energy)
🔨 Overall Enjoyment: 4/5 (solid game but not being able to play for longer sessions puts a bit of a damper on it)
🔨 Total: 18/23
4. Miss Merge
Developer: TrueMyth Games Ltd
Release Date: Feb. 2021
This game is probably the most blatant rip-off of Merge Mansion, but only based on the fact that they steal the fake plot from the Merge Mansion ads and actually do something with it lol. In fact it’s because of that that I actually ended up liking this game more than Merge Mansion - it gives you want you wanted from those ads that wasn’t in the actual game.
Other than the ripped ad plot and a similar grandma character design this game actually is pretty unique from the original Merge Mansion and is more similar to Merge Friends in its gameplay. It has a similar cartoony art style, similar form of objectives (except instead of orders it’s just personal requests from characters) and similar way of unlocking parts of the board along the way.
This game probably has the best storyline of all the games, with an actual mystery unfolding throughout the plot line.
🍪 Art: 2/3 (similar to Merge Friends, the cartoony board items are charming but the character designs are lacking)
🍪 Story: 3/3 (I genuinely want to know what happens next and each character has their own personality, motives and relationship with your character/the other characters)
🍪 Gameplay: 4/5 (gameplay is most similar to Merge Friends but objectives are more random and not directly tied to the plot, and this is the only game without storage space for your items, although I haven’t really needed it all that much anyway)
🍪 Variety: 2/3 (there is a little more variety in items as you go along but not as many interesting and unique categories, you’ll mostly just be giving people various foods and beverages for a while)
🍪 Playtime vs. Wait Time: 3/4 (you can’t really play for long sessions, however, extra energy is pretty easy to come by so you can often play for longer than most of the other games)
🍪 Overall Enjoyment: 4/5 (definitely delivers as far as storyline but doesn’t do much more than any of the other decent games on this list)
🍪 Total: 18/23 (same score as Merge Friends but has less item variety and clearly copies a lot from other games)
5. Merge Mansion
Developer: Metacore Games Oy
Release Date: Sept. 16, 2020
I’ve already thoroughly covered this game in my original review of it, which you can read here. This was my first experience with this kind of game and it’s the first of its kind as far as I know, so I definitely have a fondness for it, although it has its pitfalls.
💐 Art: 3/3 (I really like the art in this game, you can see the detail that went into each individual item and I like the main character designs too. The 3D models of the characters shown in the garden are a little wonky though)
💐 Story: 1/3 (Very generic and boring “adult child returns home to discover mansion is a mess” plot)
💐 Gameplay: 3/5 (Overcrowding the board is a huge problem and there are certain spawners that automatically spawn what I consider nuisance items without you even tapping them. They’re nuisance items because if you need them for an objective that’s not until much later in the game; I’ve never needed these useless items yet and all they do is take up space. The objectives also aren’t very satisfying to complete other than it getting rid of some of the items taking up space. However merging is very satisfying and the game deserves credit for introducing me to this whole genre of merge games to begin with)
💐 Variety: 3/3 (tons of different items and spawners to discover, almost too many)
💐 Playtime vs. Wait Time: 2/4 (you can only play in short sessions before running out of energy but the sessions do tend to last a bit longer than in some other games, and you can get extra energy pretty often)
💐 Overall Enjoyment: 4/5 (although the overcrowding issue is frustrating it is a very fun game and keeps me coming back to keep discovering new items; this is the rating I gave it in my original review)
💐 Total: 16/23
6. Merge Matters
Developer: GreenPixel Ltd
Release Date: Dec. 31, 2020
This game seems a lot like a direct copycat of Merge Mansion; the art style and categories of items are extremely similar. It basically hits all the same boxes as Merge Mansion but I liked it just slightly less.
🪴 Art: 3/3 (the colors are more vibrant than Merge Mansion and overall the items are very nice to look at, the character design of the main girl is very pretty but I noticed that she seems to have a different art style than the grandpa, or maybe that’s just me)
🪴 Story: 1/3 (same problem as Merge Mansion, very generic homecoming story)
🪴 Gameplay: 3/5 (satisfying merges but same overcrowding problem, maybe even a little worse than Merge Mansion)
🪴 Variety: 3/3 (about the same level of variety as Merge Mansion)
🪴 Playtime vs. Wait Time: 2/4 (about the same as Merge Mansion although I tend to get less extra energy in this game but maybe just by bad luck)
🪴 Overall Enjoyment: 3/5 (although it’s nearly identical to Merge Mansion, I give it a lesser score here because if I had to pick between the two I would definitely choose Merge Mansion. I can’t say exactly why, but a range of small factors make Merge Mansion the more satisfying game to play)
🪴 Total: 15/23
7. Merge Villa
Developer: 4Enjoy Games
Release Date: Feb. 2021
So this isn’t the worst game ever, but it is by far the most lackluster out of all the games I played for this project. It definitely feels like the dollar store version of Merge Mansion. The art here is frankly ugly and the gameplay is very simplistic with very little item variety. The merging here also doesn’t feel very satisfying for some reason, maybe because there isn’t any sort of animation or proper sound effect to go along with the merging. It’s definitely a playable game but nothing to write home about.
🪛 Art: 1/3 (like I said, it’s ugly)
🪛 Story: 2/3 (it actually has a little more plot going on than Merge Mansion or Merge Matters although it still follows the same trope)
🪛 Gameplay: 3/5 (although it’s definitely simplistic and the merges are less satisfying than in Merge Mansion/Merge Matters, I’ve never had to worry about running out of room on the board, plus it has the added feature of letting you choose between three styles for each renovation similar to Merge Design and other games like Homescapes, which makes completing the objectives more satisfying)
🪛 Variety: 1/3 (very little variety, I’ve only seen and handful of item categories so far)
🪛 Playtime vs. Wait Time: 1/4 (abysmal, the play sessions are short, the spawners run out quickly and the energy takes twice as long to recharge as in other games)
🪛 Overall Enjoyment: 2/5 (playable but barely worth playing)
🪛 Total: 10/23
If you got here to the end, even if you just skimmed through, thank you so much for reading 😍 Follow me for more reviews and articles about those mobile games you’re always getting ads for 🥳
#merge mansion#merge games#mobile games#casual games#free games#renovation games#garden games#remodeling games#knockoff games#travel town#merge design#miss merge#merge friends#merge matters#merge villa#full review#games ranked
59 notes
·
View notes
Text
Difference Between Microsoft Azure vs Amazon AWS
What is Azure?
• Azure is viewed as both a Platform as a Service (PaaS) and an Infrastructure as a Service (IaaS) offering.
• Azure may be a uniquely powerful offering due to its builder. Few companies have A level of infrastructure support adequate to Microsoft.
Visit Office.com/setup to know more
What is AWS?
• AWS, like Amazon itself, features a vast toolset that's growing at an exponential rate.
• It's been within the cloud computing marketplace for quite 10 years, which suggests that AWS is that the frontrunner and has been for a few times.
• AWS offering services are categorized as Platform as a Service (PaaS), Infrastructure as a Service (IaaS), and Software as a Service (SaaS).
Microsoft Azure vs Amazon AWS Features and Services
Let's start with the basics.
In terms of basic capabilities, AWS and Azure are pretty similar. They share all of the common elements of public cloud services: self-service, security, instant provisioning, auto-scaling, compliance, and identity management. However, between the 2, AWS offers the best depth, with 140 services across computing, database, analytics, storage, mobile, and developer tools. confine mind, however, that they need a start on everyone else since they have been around the longest. That said, Azure is additionally strong on the features and services front and features a parent company that has the resources to carry their own against Amazon.

Storage
Successful cloud deployment relies on sufficient storage to urge the work done. Fortunately, this is often a neighborhood where Azure and AWS are equally strong. AWS's storage relies on machine instances, which are virtual machines hosted on AWS infrastructure. Storage is tied to individual instances--temporary storage is allocated once per instance and destroyed when an instance is terminated. you'll also get block storage attached to an instance, almost like a tough drive. If you would like object storage, you'll catch on through S3, and if you would like data archiving, you'll catch on through Glacier. Azure, on the opposite hand, offers temporary storage through D drive and block storage through Page Blobs for VMs, with Block Blobs and Files doubling as object storage. Like AWS, it supports relational databases, Big Data, and NoSQL through Azure Table and HDInsight. Azure offers two classes of storage: Hot and funky. Cool storage is a smaller amount expensive, but you'll incur additional read and write costs. For AWS, there's S3 Standard and S3 Standard-Infrequent Access. Both have unlimited allowed objects, but AWS has an object size limit of 5 TB, while Azure features a size limit of 4.75 TB.
Computing Power
One front for comparison is computing power, which may be a standard requirement for any IT team. If you are going to take a position in cloud services, you would like cloud services with enough horsepower to stay up together with your office's demands on a day-to-day basis (and during high-traffic periods). The primary issue here is scalability. AWS uses elastic cloud computing (EC2), which is when the available resource footprint can grow or shrink on demand using cloud computing, with an area cluster providing only a part of the resource pool available to all or any jobs. AWS EC2 users can configure their own virtual machines (VMs), choose pre-configured machine images (MIs), or customize as. Users have the liberty to settle on the dimensions, power, memory capacity, and number of VMs they want to use. Azure users, on the opposite hand, chose a virtual hard disc (VHD) to make a VM. this will be pre-configured by Microsoft, the user, or a separate third party. It relies on virtual scale sets for scalability purposes. The key difference is that EC2 is often tailored to a variety of options, while Azure VMs pair with other tools to assist deploy applications on the cloud.
Databases
Regardless of whether you would like an electronic database or a NoSQL offering, both AWS and Azure have robust database offerings.
Amazon's electronic database service (RDS) supports six popular database engines:
1. Amazon Aurora
2. MariaDB
3. Microsoft SQL
4. MySQL
5. Oracle
6. PostgreSQL
Azure's SQL database, on the opposite hand, is predicated solely on Microsoft SQL.
Both systems work perfectly with NoSQL and relational databases. They're highly available, durable, and offer easy, automatic replication.
AWS has more instance types you'll provision, but Azure's interface and tooling are delightfully user-friendly, making it easy to perform various database operations.
This was all about Microsoft Azure vs Amazon AWS. We differentiate these two things to understand you very well. For more help visit Office.com/setup.
1 note
·
View note
Photo

Its Christmas season and its time to review some Holidays. And waiting for the Revisiting Series to get to here will be too long.
((Due to Uploading Problems, no pictures in this one. Its why some text are like what it is.))
The Special begins with the girls recovering from a big Study session. Sadly, it wasn’t good enough as they have a big test today and they fear that they won’t do as well. But Rainbow Dash got an idea: make Celestia think its snowing to give them a snow day. Twilight has doubts but she is convinced by the others.
Pinkie Pie’s Part of the Plan is to Peel these Potatoes while Preventing a Poaching Raccoon from Pilfering her Produce. But I do have to question why do they need potatoes to create a snow day considering what the others are doing.
Rarity is knitting a scarf. That is all. And Sunset is painting a backdrop so the entire city could look like its covered in snow.
And the Potatoes are used to make a snowman for some reason.
And the rest has to make the actual snow. From Applejack bringing in ice blocks to Fluttershy convincing Woodpeckers to Dash and Twilight setting up the snow in places.
We also see Sunset’s powers extend to inanimate objects, as the snowflake she touches remembers when it was a rain cloud to liquid to snow flakes.
But it seems to be working as both Celestia and Luna sees what they made and believes it to be real. But Cranky comes in to tell them the truth and the girls got Busted.
But it was all part of Dash’s plan. The test was about how snow fits into the Water Cycle and they spent two hours of school time (they had a half an hour to get there when they woke up) working on it. And detention after the test sounds a lot better than Failing a big test.
And its over. Yet the special has a lot remaining. Which brings up the big downside of this: this special is just a collection of shorts. Normally this isn’t a big deal, but this is the final Equestria Girls we’re gonna get unless they somehow fit into the Pony Life spinoff in between Gen 4 and 5. So it is kind of a big let down. Its understandable since I doubt even they knew MLP was gonna end in Season 9.
The next short has Sunset helping Pinkie Pie with making a soufflé and delivering it to Rarity. Every time Pinkie tires to for their tradition, it deflates before Rarity can try it. So that’s 7 minutes before it deflates (which turns into 3:30 because she wasted time). But there is one problem...
Its a snow war and Pinkie Pie’s House is Ground Zero. Lots of fun so i’m gonna let you see it. But in short, Sunset swears they’ll get it to Rarity and powers through because AJ made fun of videogames. And she has help from Flash Sentry.
For about five seconds.
Bad news, Pinkie failed to get out of her yard in time. Good news, Rarity was there and with seconds to spare, she tries a not deflated soufflé and enjoys it. It ends with Dash’s 2 day pretending to be a snowman plan failing because Rarity can make shields.
The next short is a battle of wits between Twilight and the Apples Vs the Flim Flam Brothers. Again, this is just a fun one to see so I won’t spoil it. But I will highlight one thing...
I’m going to find a way to give Apple Bloom a pet worm. Maybe pull a Carol on it.
The next story has the girls heading towards a storage locker because they’re gonna deliver toys to kids. But Sunset forgot her keys in school and its currently closed. Consider this episode their take on Episode 200: planning a heist to get into a highly secured location.
The first plan is Sunset’s: go through the air vents, hack the motion security system, distract the Janitor, and get it in and out before they notice. Twilight rejects the plan because of numerous problems, like its breaking and entering, Fluttershy likely not going to use her animals to attack the Janitor and if someone saw them going through the vents some dumb kid might want to try it to.
Next is Pinkie Pie’s Plan: Make cupcakes to lure Celestia out of School and go in while the door is still open and Celestia eats them outside. Twilight’s problem this time: how do you make a dozen cupcakes before the Toys for Kids festival, which is just in a few minutes. Not to mention the lack of a licorice lasso and the fact its still trespassing.
The funniest to me is Applejack’s plan: WE GOT SUPERPOWERS AND I’M SICK OF NOT USING THEM! Its so obvious why this is a bad idea Twilight doesn’t even say it. So they decided to let Twilight come up with the plan to entering the School. And what is her plan?
Ask to be let into the school. With the key recovered and the toys delivered, it ends with them leaving their gift cards in school.
The next part, ignoring Sinister looking Twilight above, is a gift exchange and Dash forgot to get Fluttershy a gift. And since Discord isn’t here to help and most of the Mall is crowded, there’s only one store she can go to to get a gift...
The Store Zephyr Breeze works in. Luckily this one is a worker and he lets Dash skip the line. What follows is a montage of them trying to figure out what to get Fluttershy. I’m skipping this one because I don’t find it as entertaining as the ones above.
Eventually, Zephyr convinces Dash to get a camera since Fluttershy likes these instant cameras. He should know because he got her one last year. But now with two she can do two angle shots, so she loves it.
Who got who?
Rainbow Dash > Fluttershy
Applejack > Pinkie Pie
Rarity > Rainbow Dash
Sunset Shimmer > Twilight Sparkle (It is about the Parakeet)
Fluttershy > Applejack
Pinkie Pie > Sunset Shimmer
Twilight Sparkle > Rarity
The final short has Applejack wanting to begin a tradition by having the friends do a group photo to give to friends. Specifically one with a theme based on what the Apples do. They agree but regret it since they expect to wear costumes while Applejack doesn’t mention she didn’t want them to.
Rarity does the outfits despite not knowing what a cornucopia is (or how to pronounce it). They put it on and walk towards where the photo is going to be taken place in, despite being embarrassed to wear them and having the other students see. Would have solved a lot of problems if they got dressed at where they need to take the photo instead of in the Drama Department.
Its now that Applejack tells them that she didn’t want them to wear outfits, just stand in front of this cutout. But the girls do make her wear one of them since she didn’t tell them. Again, could save a lot of trouble if they just got dressed here and not at the Drama Department.
Now normally it would cut to them alluding to AJ’s fate, but since this is the last Equestria Girls, they decided to give us a Seasonal Greetings as a farewell to the series.
Overall, it is a shame EQG ends like this, but I’m pretty sure they didn’t expect it. I could see like a scene or two being added as a way to give closure, but overall this is a collection of shorts they plan to (and have) release it on Youtube. My personal favorites are the second, third and fourth shorts. It remains the same.
4 notes
·
View notes
Photo

hydralisk98′s web projects tracker:
Core principles=
Fail faster
‘Learn, Tweak, Make’ loop
This is meant to be a quick reference for tracking progress made over my various projects, organized by their “ultimate target” goal:
(START)
(Website)=
Install Firefox
Install Chrome
Install Microsoft newest browser
Install Lynx
Learn about contemporary web browsers
Install a very basic text editor
Install Notepad++
Install Nano
Install Powershell
Install Bash
Install Git
Learn HTML
Elements and attributes
Commenting (single line comment, multi-line comment)
Head (title, meta, charset, language, link, style, description, keywords, author, viewport, script, base, url-encode, )
Hyperlinks (local, external, link titles, relative filepaths, absolute filepaths)
Headings (h1-h6, horizontal rules)
Paragraphs (pre, line breaks)
Text formatting (bold, italic, deleted, inserted, subscript, superscript, marked)
Quotations (quote, blockquote, abbreviations, address, cite, bidirectional override)
Entities & symbols (&entity_name, &entity_number,  , useful HTML character entities, diacritical marks, mathematical symbols, greek letters, currency symbols, )
Id (bookmarks)
Classes (select elements, multiple classes, different tags can share same class, )
Blocks & Inlines (div, span)
Computercode (kbd, samp, code, var)
Lists (ordered, unordered, description lists, control list counting, nesting)
Tables (colspan, rowspan, caption, colgroup, thead, tbody, tfoot, th)
Images (src, alt, width, height, animated, link, map, area, usenmap, , picture, picture for format support)
old fashioned audio
old fashioned video
Iframes (URL src, name, target)
Forms (input types, action, method, GET, POST, name, fieldset, accept-charset, autocomplete, enctype, novalidate, target, form elements, input attributes)
URL encode (scheme, prefix, domain, port, path, filename, ascii-encodings)
Learn about oldest web browsers onwards
Learn early HTML versions (doctypes & permitted elements for each version)
Make a 90s-like web page compatible with as much early web formats as possible, earliest web browsers’ compatibility is best here
Learn how to teach HTML5 features to most if not all older browsers
Install Adobe XD
Register a account at Figma
Learn Adobe XD basics
Learn Figma basics
Install Microsoft’s VS Code
Install my Microsoft’s VS Code favorite extensions
Learn HTML5
Semantic elements
Layouts
Graphics (SVG, canvas)
Track
Audio
Video
Embed
APIs (geolocation, drag and drop, local storage, application cache, web workers, server-sent events, )
HTMLShiv for teaching older browsers HTML5
HTML5 style guide and coding conventions (doctype, clean tidy well-formed code, lower case element names, close all html elements, close empty html elements, quote attribute values, image attributes, space and equal signs, avoid long code lines, blank lines, indentation, keep html, keep head, keep body, meta data, viewport, comments, stylesheets, loading JS into html, accessing HTML elements with JS, use lowercase file names, file extensions, index/default)
Learn CSS
Selections
Colors
Fonts
Positioning
Box model
Grid
Flexbox
Custom properties
Transitions
Animate
Make a simple modern static site
Learn responsive design
Viewport
Media queries
Fluid widths
rem units over px
Mobile first
Learn SASS
Variables
Nesting
Conditionals
Functions
Learn about CSS frameworks
Learn Bootstrap
Learn Tailwind CSS
Learn JS
Fundamentals
Document Object Model / DOM
JavaScript Object Notation / JSON
Fetch API
Modern JS (ES6+)
Learn Git
Learn Browser Dev Tools
Learn your VS Code extensions
Learn Emmet
Learn NPM
Learn Yarn
Learn Axios
Learn Webpack
Learn Parcel
Learn basic deployment
Domain registration (Namecheap)
Managed hosting (InMotion, Hostgator, Bluehost)
Static hosting (Nertlify, Github Pages)
SSL certificate
FTP
SFTP
SSH
CLI
Make a fancy front end website about
Make a few Tumblr themes
===You are now a basic front end developer!
Learn about XML dialects
Learn XML
Learn about JS frameworks
Learn jQuery
Learn React
Contex API with Hooks
NEXT
Learn Vue.js
Vuex
NUXT
Learn Svelte
NUXT (Vue)
Learn Gatsby
Learn Gridsome
Learn Typescript
Make a epic front end website about
===You are now a front-end wizard!
Learn Node.js
Express
Nest.js
Koa
Learn Python
Django
Flask
Learn GoLang
Revel
Learn PHP
Laravel
Slim
Symfony
Learn Ruby
Ruby on Rails
Sinatra
Learn SQL
PostgreSQL
MySQL
Learn ORM
Learn ODM
Learn NoSQL
MongoDB
RethinkDB
CouchDB
Learn a cloud database
Firebase, Azure Cloud DB, AWS
Learn a lightweight & cache variant
Redis
SQLlite
NeDB
Learn GraphQL
Learn about CMSes
Learn Wordpress
Learn Drupal
Learn Keystone
Learn Enduro
Learn Contentful
Learn Sanity
Learn Jekyll
Learn about DevOps
Learn NGINX
Learn Apache
Learn Linode
Learn Heroku
Learn Azure
Learn Docker
Learn testing
Learn load balancing
===You are now a good full stack developer
Learn about mobile development
Learn Dart
Learn Flutter
Learn React Native
Learn Nativescript
Learn Ionic
Learn progressive web apps
Learn Electron
Learn JAMstack
Learn serverless architecture
Learn API-first design
Learn data science
Learn machine learning
Learn deep learning
Learn speech recognition
Learn web assembly
===You are now a epic full stack developer
Make a web browser
Make a web server
===You are now a legendary full stack developer
[...]
(Computer system)=
Learn to execute and test your code in a command line interface
Learn to use breakpoints and debuggers
Learn Bash
Learn fish
Learn Zsh
Learn Vim
Learn nano
Learn Notepad++
Learn VS Code
Learn Brackets
Learn Atom
Learn Geany
Learn Neovim
Learn Python
Learn Java?
Learn R
Learn Swift?
Learn Go-lang?
Learn Common Lisp
Learn Clojure (& ClojureScript)
Learn Scheme
Learn C++
Learn C
Learn B
Learn Mesa
Learn Brainfuck
Learn Assembly
Learn Machine Code
Learn how to manage I/O
Make a keypad
Make a keyboard
Make a mouse
Make a light pen
Make a small LCD display
Make a small LED display
Make a teleprinter terminal
Make a medium raster CRT display
Make a small vector CRT display
Make larger LED displays
Make a few CRT displays
Learn how to manage computer memory
Make datasettes
Make a datasette deck
Make floppy disks
Make a floppy drive
Learn how to control data
Learn binary base
Learn hexadecimal base
Learn octal base
Learn registers
Learn timing information
Learn assembly common mnemonics
Learn arithmetic operations
Learn logic operations (AND, OR, XOR, NOT, NAND, NOR, NXOR, IMPLY)
Learn masking
Learn assembly language basics
Learn stack construct’s operations
Learn calling conventions
Learn to use Application Binary Interface or ABI
Learn to make your own ABIs
Learn to use memory maps
Learn to make memory maps
Make a clock
Make a front panel
Make a calculator
Learn about existing instruction sets (Intel, ARM, RISC-V, PIC, AVR, SPARC, MIPS, Intersil 6120, Z80...)
Design a instruction set
Compose a assembler
Compose a disassembler
Compose a emulator
Write a B-derivative programming language (somewhat similar to C)
Write a IPL-derivative programming language (somewhat similar to Lisp and Scheme)
Write a general markup language (like GML, SGML, HTML, XML...)
Write a Turing tarpit (like Brainfuck)
Write a scripting language (like Bash)
Write a database system (like VisiCalc or SQL)
Write a CLI shell (basic operating system like Unix or CP/M)
Write a single-user GUI operating system (like Xerox Star’s Pilot)
Write a multi-user GUI operating system (like Linux)
Write various software utilities for my various OSes
Write various games for my various OSes
Write various niche applications for my various OSes
Implement a awesome model in very large scale integration, like the Commodore CBM-II
Implement a epic model in integrated circuits, like the DEC PDP-15
Implement a modest model in transistor-transistor logic, similar to the DEC PDP-12
Implement a simple model in diode-transistor logic, like the original DEC PDP-8
Implement a simpler model in later vacuum tubes, like the IBM 700 series
Implement simplest model in early vacuum tubes, like the EDSAC
[...]
(Conlang)=
Choose sounds
Choose phonotactics
[...]
(Animation ‘movie’)=
[...]
(Exploration top-down ’racing game’)=
[...]
(Video dictionary)=
[...]
(Grand strategy game)=
[...]
(Telex system)=
[...]
(Pen&paper tabletop game)=
[...]
(Search engine)=
[...]
(Microlearning system)=
[...]
(Alternate planet)=
[...]
(END)
4 notes
·
View notes