#api for blockchain
Explore tagged Tumblr posts
Text
How to query transactions, balances, etc. in API for blockchain data?

What is API for blockchain data? Blockchain data - also known as "on-chain data" - refers to all publicly available information stored on networks such as Ethereum, BNB Smart Chain (BSC), and Polygon. With this information, it is possible to track the movement of assets, verify transactions, and generate advanced market insights through API for blockchain data analysis. Therefore, blockchain data plays an integral role in building DApps and other Web3 projects! Transaction data: Transaction data is information about each transaction on the API for the blockchain network, including sender and recipient addresses, transfer fees, transaction amounts, etc. Block data: Block data is information about each block in the chain. For example, this includes hashes, transactions, timestamps, miner fees, and so on. Smart contract data: Smart contract data is all the information about smart contracts deployed to the API for the blockchain network. This includes the contract code, status, logs, and emitted events. In summary, blockchain data is all publicly available information stored on Ethereum, BSC, Polygon, and other networks. How do I query data from the API for blockchain? Blockchain data on networks like Ethereum, BSC, and Polygon is public, which means anyone can query the information. However, how exactly does this work? Well, you have a few options when it comes to getting on-chain data: Run the node: The first option to get API for blockchain data is to host the node yourself. This allows you to interact directly with the blockchain network to query data, execute transactions, and deploy smart contracts. Block Explorer: Your second option is to use a block Explorer. Block Explorer is a web-based platform that allows you to seamlessly read all transactions stored on the network. Some prominent examples include Etherscan, PolygonScan, BscScan, etc. Web3API: The last option is to use Web3API. The Web3 API (short for "Application Programming Interface") is a set of protocols, rules, and methods that allow you to interact seamlessly with the network, such as querying API for blockchain data. While all of the above options are effective ways to access API for blockchain data, they each have advantages and disadvantages. For example, running a node and querying information from it requires an underlying infrastructure, which is a tedious and time-consuming setup task. In addition, while blockchain Explorations provide web-based interfaces that allow you to browse and search blockchains, they are not designed for programmatic access or data integration into Dapps. So when it comes to Web3 development, the best and easiest way to query API for blockchain data is to use apis!
0 notes
Text
#kyc uk#kyc solution#kyc api#kyc companies#kyc software#kyc providers#fraud prevention#kyc solutions for crypto#crypto#blockchain#blockchain technology
2 notes
·
View notes
Text

#crypto#cybersecurity#digital banking licenses#digitalbanking#fintech#investors#white label crypto exchange software#bitcoin#digital marketing#financial advisor#cryptoinvesting#blockchain#digitalcurrency#cryptomarket#defi#payment gateway#payment api#payment processing#fiatgateways#cryptogateway#itioinnovex#pcidss#pci dss#datasecurity#cyber security#compliancesoftware#compliance
0 notes
Text
#crypto staking#staking platforms#passive income#crypto rewards#Ethereum staking#liquid staking#staking APY#DeFi#blockchain#proof of stake#staking 2025#staking comparison#secure staking#best APY staking#non-custodial crypto
0 notes
Text
InStep Technologies is a trusted fintech software development company delivering secure, scalable, and innovative financial solutions. We build custom fintech apps, APIs, mobile wallets, blockchain integrations, and automation tools for startups, banks, and enterprises.
#fintech software development#custom fintech solutions#financial technology apps#fintech development company#banking app development#blockchain in finance#secure payment software#finance automation tools#investment software solutions#fintech API integration
0 notes
Text
Dynamic Fee Adjustment Algorithms: Algoritmi pentru Tranzacții Optimizate
Introducere În rețeaua Bitcoin, costurile de tranzacționare sunt determinate în mare măsură de comisioanele plătite de utilizatori pentru a include tranzacțiile în blocuri. Cu cât rețeaua este mai aglomerată și spațiul disponibil în blocuri este mai limitat, cu atât comisioanele cresc, influențând timpii de confirmare și experiența utilizatorilor. În acest context, optimizarea costurilor de…
#fee market#monitorizare tranzacții#feedback în timp real#algoritmi hibrizi#predictibilitate#algoritmi de ajustare#interfață utilizator#comisioane Bitcoin#estimare dinamică#inovație cripto#Bitcoin Core#fee optimization tools#Dynamic Fee Adjustment#Tranzacții Optimizate#Fee Estimation#Algoritmi de Machine Learning#Standardizare API#blockchain efficiency#Automatizare#"finanțe descentralizate"#dezvoltare blockchain#Lightning Network#soluții Layer 2#performanță rețea#securitate tranzacții#portofele Bitcoin#bitcoin#mempool#costuri de tranzacționare#evoluție cripto
0 notes
Text
#venly io#blockchain#venlys wallet#nft token apis#venly payment#business owners#small business owners#web3
1 note
·
View note
Text
0 notes
Text
Lavorare con i Servizi Internet: Tecnologie, Sicurezza e Opportunità. Come i servizi web, le tecnologie cloud e l’e-commerce stanno trasformando il nostro modo di vivere e lavorare
Nell’era digitale, i servizi Internet sono diventati una parte essenziale della nostra vita quotidiana, trasformando settori come l’istruzione, l’economia e la comunicazione
Nell’era digitale, i servizi Internet sono diventati una parte essenziale della nostra vita quotidiana, trasformando settori come l’istruzione, l’economia e la comunicazione. Questo articolo, elaborato da Umarov Bekzod Azizovich, docente presso il Dipartimento di Matematica Applicata e Informatica dell’Università Statale di Fergana, e da Mukhsinova Sevinchhon Ikromjon, studente del 3° anno,…
#Alessandria news#Alessandria today#Amazon#Api#autenticazione a due fattori#blockchain#commercio digitale#commercio online#comunicazioni globali#connessioni globali#Criptovalute#crittografia SSL#dati personali#Digitalizzazione#Dropbox#e-commerce#Futuro Digitale#Gmail#Google Drive#Google News#impatto economico#Innovazione tecnologica#Internet e sicurezza#italianewsmedia.com#Microsoft Teams#moderni servizi digitali#PayPal#piattaforme di comunicazione#Pier Carlo Lava#protezione dati
0 notes
Text
Blockchain Development Simplified with a Unified API
Learn how a Unified Blockchain API simplifies development across Bitcoin, Solana, and Ethereum. Streamline transactions, real-time monitoring, and integration with ease.
Blockchain development is often seen as complex and fragmented, especially when working across networks like Bitcoin, Solana, and Ethereum. Developers face challenges with diverse protocols, real-time monitoring, and transaction management. This is where Blockchain Development Simplified comes into play. By using a Unified Blockchain API, developers can streamline their workflows, reduce…
#Bitcoin API#Blockchain Development#Blockchain Integration#Cross-Chain Development#Ethereum API#Solana API#Unified Blockchain API
0 notes
Text
How can Application chains reshape the future of API for blockchain technology?

Application-specific APIs for blockchains (AppChains) have become a transformative force in the blockchain space. These specialized blockchain solutions are revolutionizing the way developers handle decentralized applications. In a world where blockchain ecosystems are constantly evolving, application chains are rapidly gaining importance and poised to reshape the future of blockchain technology. As the need for tailor-made solutions intensifies, application chains have become the focus of attention. This Cryptopolitan guide walks through the complex field of AppChains, revealing their importance and multifaceted applications. It delves into their unique properties, exploring how they can address the limitations of traditional blockchains and drive innovation. What are AppChains? In essence, AppChain represents a specialized API for blockchain that focuses on a specific application or use case. Unlike generic application chains, application chains are not subject to a one-size-fits-all approach. Instead, they are fine-tuned to provide the best infrastructure needed to power a particular application. The differentiating factor is specialization. While general-purpose blockchains, such as Ethereum or Bitcoin, struggle to accommodate a myriad of applications, application chains are precision tools built for a single purpose. This distinction has profound implications. By customizing API for blockchains to the unique needs of a particular application, developers unlock a realm of possibilities, including optimized performance, customization, and scalability. AppChains embody the idea of "tools for work." They provide a professional, finely tuned solution that goes beyond the limitations of general-purpose API for blockchains, unlocking the full potential of blockchain technology for specific applications or use cases. Advantages of AppChains In the dynamic landscape of API for blockchain technology, application chains shine as specialized tools that offer numerous advantages. These tailor-made blockchain solutions have garnered attention for their ability to unlock new possibilities while solving key challenges. AppChains has become a compelling solution in the blockchain space with the following advantages: expandability One of the most important advantages of AppChains is its ability to alleviate congestion and increase throughput. In traditional API for blockchain ecosystems, applications often find themselves competing for limited block space, resulting in increased delays and fees. AppChains removes this bottleneck by dedicating the entire API for blockchain to a specific application or use case. This isolation ensures that applications can run at peak efficiency without the performance issues that plague general-purpose blockchains. The result is fast transaction processing, reduced congestion, and significantly improved scalability. Custom AppChains offers developers unprecedented freedom and flexibility. Unlike generic API for blockchains, which have fixed parameters, developers working on AppChains are free to customize key aspects of the blockchain to suit the specific requirements of their application. This customization extends to choosing consensus mechanisms, designing governance structures, and defining economic models. This autonomy enables developers to innovate and create API for blockchain-based applications exactly as envisioned, unconstrained by one-size-fits-all solutions. interoperability In the interconnected world of API for blockchain, interoperability is crucial. AppChains excels in this by seamlessly integrating into the broader blockchain ecosystem. Thanks to common protocols and standards, applications running on AppChains can communicate and exchange value with other blockchain networks. This interconnectivity promotes a diverse and collaborative ecosystem where applications can take advantage of different blockchains. The application chain becomes a channel to facilitate the flow of data and assets in a decentralized environment, enhancing the overall utility of blockchain technology.
0 notes
Text
The Future of Payments: Real-Time Embedded Finance Solutions
Embedded finance is transforming the way businesses and consumers interact with financial services. By integrating APIs and digital solutions directly into platforms, embedded finance allows for seamless, real-time payments, insurance, and banking experiences. With AI, machine learning, and blockchain paving the way, industries such as retail, e-commerce, and telecommunications are at the forefront of this financial revolution. Discover how this rapidly growing sector is reshaping financial services.
#embeddedfinance#fintech#digitalpayments#AI#blockchain#APIs#ecommerce#financialinclusion#retailtech#realtimepayments
0 notes
Text

Leveraging AI in Salesforce Development
Artificial Intelligence (AI) is revolutionizing Salesforce development by infusing intelligence into traditional CRM processes. AI allows Salesforce to evolve from a static data management platform into a dynamic, insight-driven system that can predict, recommend, and automate key functions. With AI, Salesforce development is now more about building solutions that are not just reactive but proactive.
Know more at: https://www.cyberswift.com/blog/leveraging-ai-in-salesforce-development/
#generative ai in salesforce#salesforce ai cloud#salesforce einstein gpt#ai-powered crm solutions#bill cipher#salesforce automation with ai#predictive analytics in salesforce#ai-driven customer insights#ai-enhanced salesforce workflows#salesforce lightning and ai integration#chatbots and salesforce crm#salesforce consulting services#salesforce crm solutions#custom salesforce development#salesforce lightning development#salesforce app development#salesforce api integration#salesforce cloud services#salesforce automation solutions#salesforce migration services#salesforce support and maintenance#low-code salesforce development#ai-powered salesforce solutions#iot integration with salesforce#salesforce blockchain integration
1 note
·
View note
Text
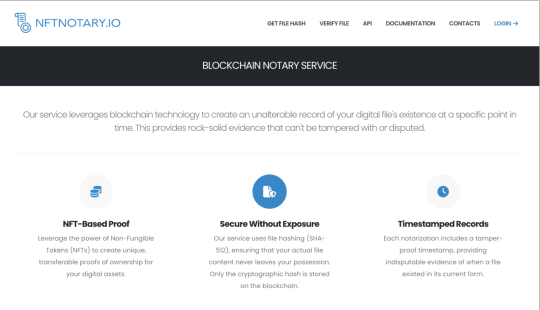
🌐 BLOCKCHAIN NOTARY SERVICE 🌐
Unlock the future of digital asset management with our innovative blockchain notary service https://nftnotary.io/ ! Our platform harnesses the power of blockchain technology to create an unalterable record of your digital file's existence at a specific point in time. This provides rock-solid evidence that is tamper-proof and indisputable. 💪✨
🔹 NFT-Based Proof Leverage the incredible capabilities of Non-Fungible Tokens (NFTs) to establish unique, transferable proofs of ownership for your digital assets. Each NFT serves as a digital certificate, validating your ownership like never before! 🎟
🔹 Secure Without Exposure Rest assured, your actual file content never leaves your possession. Our service uses file hashing (SHA-512), meaning only the cryptographic hash is securely stored on the blockchain 🔒. Your privacy is our priority!
🔹 Timestamped Records Every notarization comes with a tamper-proof timestamp, providing indisputable evidence of when a file existed in its current form. ⏰ Trust in the authenticity of your records!
🔹 Notarize Any Digital File Whether it's a document, image, video, or any other digital file, our service can create a blockchain-verified record of its existence and your ownership. 📄📸🎥
🔹 Simple Proof Checking Verify the authenticity and ownership of any registered file instantly, anytime, anywhere, using our user-friendly verification portal. 🔍✨
🔹 Easy Integration Seamlessly integrate our notary service into your existing workflows with our comprehensive API, enabling automated certification processes. 🤖📈
Web App & API Our web app streamlines the process of creating and managing notarized NFTs, making it ideal for businesses and individuals handling large volumes of digital assets. 💼
Affordable Pricing: With a minimum payment of just $10 and NFT prices starting from as low as $0.20 each, managing your digital assets has never been more economical! 💵 API Integration: Effortlessly integrate with your existing systems for automated NFT generation and management.
Customizable Templates: Create and manage templates for certificate PDFs and NFT images for consistent branding. 🖼
Export Functionality: Easily export created NFTs and their details to Excel or PDF for record-keeping and reporting. 📊
Free NFT: Register and notarize one digital file for free—only your email is required for registration! 🎉
Native Apps Experience the power of blockchain notarization on the go with our suite of native apps! 📲 Available for mobile devices, WeChat, Telegram, and more, these streamlined applications offer a hassle-free way to create and manage your NFTs.
Simplified Interface: Our native apps feature an intuitive UI designed for quick and easy NFT creation, even for those new to blockchain technology. 🌟 No Registration: Jump straight into creating NFTs without lengthy sign-up processes. Your blockchain wallet is all you need! 💼
Affordable Pricing: Create NFTs starting from just $1 each, making it cost-effective for individual users.
Step into the future with us and take control of your digital assets today https://nftnotary.io/ ! 🚀✨
#Blockchain#NotaryService#NFT#DigitalAssets#SecureRecords#Timestamp#FileVerification#APIs#MobileApps#WeChat#Telegram#Crypto#AffordableNFTs#DigitalOwnership#Innovation#TechForGood
0 notes
Text
🌐 BLOCKCHAIN NOTARY SERVICE 🌐
Unlock the future of digital asset management with our innovative blockchain notary service https://nftnotary.io/ ! Our platform harnesses the power of blockchain technology to create an unalterable record of your digital file's existence at a specific point in time. This provides rock-solid evidence that is tamper-proof and indisputable. 💪✨
🔹 NFT-Based Proof Leverage the incredible capabilities of Non-Fungible Tokens (NFTs) to establish unique, transferable proofs of ownership for your digital assets. Each NFT serves as a digital certificate, validating your ownership like never before! 🎟
🔹 Secure Without Exposure Rest assured, your actual file content never leaves your possession. Our service uses file hashing (SHA-512), meaning only the cryptographic hash is securely stored on the blockchain 🔒. Your privacy is our priority!
🔹 Timestamped Records Every notarization comes with a tamper-proof timestamp, providing indisputable evidence of when a file existed in its current form. ⏰ Trust in the authenticity of your records!
🔹 Notarize Any Digital File Whether it's a document, image, video, or any other digital file, our service can create a blockchain-verified record of its existence and your ownership. 📄📸🎥
🔹 Simple Proof Checking Verify the authenticity and ownership of any registered file instantly, anytime, anywhere, using our user-friendly verification portal. 🔍✨
🔹 Easy Integration Seamlessly integrate our notary service into your existing workflows with our comprehensive API, enabling automated certification processes. 🤖📈
Web App & API Our web app streamlines the process of creating and managing notarized NFTs, making it ideal for businesses and individuals handling large volumes of digital assets. 💼
Affordable Pricing: With a minimum payment of just $10 and NFT prices starting from as low as $0.20 each, managing your digital assets has never been more economical! 💵 API Integration: Effortlessly integrate with your existing systems for automated NFT generation and management.
Customizable Templates: Create and manage templates for certificate PDFs and NFT images for consistent branding. 🖼
Export Functionality: Easily export created NFTs and their details to Excel or PDF for record-keeping and reporting. 📊
Free NFT: Register and notarize one digital file for free—only your email is required for registration! 🎉
Native Apps Experience the power of blockchain notarization on the go with our suite of native apps! 📲 Available for mobile devices, WeChat, Telegram, and more, these streamlined applications offer a hassle-free way to create and manage your NFTs.
Simplified Interface: Our native apps feature an intuitive UI designed for quick and easy NFT creation, even for those new to blockchain technology. 🌟 No Registration: Jump straight into creating NFTs without lengthy sign-up processes. Your blockchain wallet is all you need! 💼
Affordable Pricing: Create NFTs starting from just $1 each, making it cost-effective for individual users.
Step into the future with us and take control of your digital assets today https://nftnotary.io/ ! 🚀✨

#Blockchain#NotaryService#NFT#DigitalAssets#SecureRecords#Timestamp#FileVerification#APIs#MobileApps#WeChat#Telegram#Crypto#AffordableNFTs#DigitalOwnership#Innovation#TechForGood
0 notes
Text
🌐 BLOCKCHAIN NOTARY SERVICE 🌐
Unlock the future of digital asset management with our innovative blockchain notary service https://nftnotary.io/ ! Our platform harnesses the power of blockchain technology to create an unalterable record of your digital file's existence at a specific point in time. This provides rock-solid evidence that is tamper-proof and indisputable. 💪✨
🔹 NFT-Based Proof Leverage the incredible capabilities of Non-Fungible Tokens (NFTs) to establish unique, transferable proofs of ownership for your digital assets. Each NFT serves as a digital certificate, validating your ownership like never before! 🎟
🔹 Secure Without Exposure Rest assured, your actual file content never leaves your possession. Our service uses file hashing (SHA-512), meaning only the cryptographic hash is securely stored on the blockchain 🔒. Your privacy is our priority!
🔹 Timestamped Records Every notarization comes with a tamper-proof timestamp, providing indisputable evidence of when a file existed in its current form. ⏰ Trust in the authenticity of your records!
🔹 Notarize Any Digital File Whether it's a document, image, video, or any other digital file, our service can create a blockchain-verified record of its existence and your ownership. 📄📸🎥
🔹 Simple Proof Checking Verify the authenticity and ownership of any registered file instantly, anytime, anywhere, using our user-friendly verification portal. 🔍✨
🔹 Easy Integration Seamlessly integrate our notary service into your existing workflows with our comprehensive API, enabling automated certification processes. 🤖📈
Web App & API Our web app streamlines the process of creating and managing notarized NFTs, making it ideal for businesses and individuals handling large volumes of digital assets. 💼
Affordable Pricing: With a minimum payment of just $10 and NFT prices starting from as low as $0.20 each, managing your digital assets has never been more economical! 💵 API Integration: Effortlessly integrate with your existing systems for automated NFT generation and management.
Customizable Templates: Create and manage templates for certificate PDFs and NFT images for consistent branding. 🖼
Export Functionality: Easily export created NFTs and their details to Excel or PDF for record-keeping and reporting. 📊
Free NFT: Register and notarize one digital file for free—only your email is required for registration! 🎉
Native Apps Experience the power of blockchain notarization on the go with our suite of native apps! 📲 Available for mobile devices, WeChat, Telegram, and more, these streamlined applications offer a hassle-free way to create and manage your NFTs.
Simplified Interface: Our native apps feature an intuitive UI designed for quick and easy NFT creation, even for those new to blockchain technology. 🌟 No Registration: Jump straight into creating NFTs without lengthy sign-up processes. Your blockchain wallet is all you need! 💼
Affordable Pricing: Create NFTs starting from just $1 each, making it cost-effective for individual users.
Step into the future with us and take control of your digital assets today https://nftnotary.io/ ! 🚀✨

#Blockchain#NotaryService#NFT#DigitalAssets#SecureRecords#Timestamp#FileVerification#APIs#MobileApps#WeChat#Telegram#Crypto#AffordableNFTs#DigitalOwnership#Innovation#TechForGood
0 notes