#altos engineers
Explore tagged Tumblr posts
Video
#alisa ann ruch#alisa ann ruch peninsula burn relay#antique#antique fire engine#burn run#chp#chp police motorcycle#Fire#los altos police motorcycle#motorcycle#motorcyles#mountain view police motorcycle#palo alto police motorcycle#police#police bmw#police harley#sunnyvale police motorcycle#flickr
8 notes
·
View notes
Text
Elevating Network Security: The Role of Palo Alto Certified Engineers
In today's digitally-driven landscape, ensuring robust network security is paramount for organizations of all sizes. With cyber threats evolving at an unprecedented pace, businesses must employ advanced technologies and skilled professionals to safeguard their networks and sensitive data. Palo Alto Networks, a global leader in cybersecurity solutions, offers innovative platforms and tools designed to protect against a wide range of cyber threats. However, harnessing the full potential of Palo Alto Networks' offerings requires expertise and proficiency. This is where Palo Alto Certified Engineers play a pivotal role.
Understanding Palo Alto Certified Engineers:
Palo Alto Certified Engineers are skilled professionals who have undergone comprehensive training and certification programs offered by Palo Alto Networks. These certifications validate their proficiency in deploying, configuring, and managing Palo Alto Networks' security solutions effectively. From firewalls and intrusion prevention systems to secure access solutions and cloud security, Palo Alto Certified Engineers possess the knowledge and skills necessary to design, implement, and optimize robust security architectures tailored to meet the unique needs of their clients.
Key Responsibilities of Palo Alto Certified Engineers:
Designing Secure Network Architectures:
Palo Alto Certified Engineers collaborate with clients to assess their security requirements, infrastructure, and risk profiles. Based on this assessment, they design customized network security architectures leveraging Palo Alto Networks' solutions. Whether it's implementing next-generation firewalls, securing cloud environments, or establishing secure remote access policies, Palo Alto Certified Engineers ensure that organizations have robust defenses in place to mitigate cyber threats effectively.
Implementing Advanced Security Controls:
Once the design phase is complete, Palo Alto Certified Engineers take on the task of implementing Palo Alto Networks' security solutions within the client's environment. This involves configuring firewalls, setting up threat prevention policies, and deploying advanced security features such as intrusion detection and prevention, URL filtering, and SSL decryption. By meticulously fine-tuning security controls, Palo Alto Certified Engineers strengthen the overall security posture of organizations and reduce their exposure to cyber risks.
Optimizing Performance and Scalability:
In addition to deployment, Palo Alto Certified Engineers are responsible for optimizing the performance and scalability of Palo Alto Networks' solutions. They conduct performance assessments, analyze network traffic patterns, and fine-tune configurations to ensure optimal security effectiveness without compromising network performance. Moreover, Palo Alto Certified Engineers design scalable architectures that can accommodate the evolving needs of organizations, allowing them to adapt to changing threat landscapes and business requirements seamlessly.
Providing Ongoing Support and Maintenance:
Beyond deployment and optimization, Palo Alto Certified Engineers offer ongoing support and maintenance to ensure the continued effectiveness of Palo Alto Networks' solutions. They monitor security events, analyze logs, and respond to incidents in a timely manner to mitigate potential security breaches. Moreover, Palo Alto Certified Engineers stay abreast of emerging threats and industry best practices, providing proactive recommendations and guidance to help organizations stay ahead of cyber adversaries.
Benefits of Engaging Palo Alto Certified Engineers:
Expertise and Specialization:
Palo Alto Certified Engineers bring specialized expertise in Palo Alto Networks' security solutions, ensuring that organizations benefit from best-in-class security practices and configurations.
Enhanced Security Posture:
By leveraging the knowledge and skills of Palo Alto Certified Engineers, organizations can enhance their security posture, reduce vulnerabilities, and mitigate cyber risks effectively.
Cost-Effective Solutions:
Palo Alto Certified Engineers help organizations maximize the value of their investment in Palo Alto Networks' solutions by designing cost-effective architectures and optimizing performance and scalability.
Peace of Mind:
With Palo Alto Certified Engineers at the helm, organizations can have peace of mind knowing that their networks are protected by industry-leading security solutions and skilled professionals who are committed to their security and success.
Palo Alto Certified Engineers play a crucial role in elevating network security and enabling organizations to navigate today's complex threat landscape with confidence. By harnessing their expertise, organizations can leverage the full potential of Palo Alto Networks' solutions and safeguard their critical assets against cyber threats. As trusted advisors and guardians of network security, Palo Alto Certified Engineers stand ready to empower organizations on their journey towards cyber resilience and success.

0 notes
Text
the taglist, part 2: character tags. ( which i wanted to have a quote, but. i've been staring at this list for 45 minutes and i can't wrap my head around it. it's fine. IT WORKS WELL. NO QUOTES. )
canon muses ↳ RED scout › ↳ RED pyro › ↳ RED sniper › ↳ RED spy › ↳ RED medic › ↳ RED engineer ›
emesis blue ↳ BLU soldier › ↳ BLU medic ›
originals / alternative universes ↳ carmine riviera / BLU retriever › ↳ carmine riviera / RED retriever › ↳ alto clef / BLU medic ›
#↳ RED scout ›#↳ RED pyro ›#↳ RED sniper ›#↳ RED spy ›#↳ RED medic ›#↳ RED engineer ›#↳ BLU soldier ›#↳ BLU medic ›#↳ carmine riviera / BLU retriever ›#↳ carmine riviera / RED retriever ›#↳ alto clef / BLU medic ›#tags.
1 note
·
View note
Text
Graham Bazell - A Talented Software Engineer
Graham Bazell, a talented software engineer from Palo Alto, CA, is driven by his unwavering commitment to personal and professional growth. In the next 10 years, he envisions himself further expanding his technical abilities, embracing leadership roles, and contributing to the evolution of the decentralized finance industry. Graham's passion for technology and his drive to continuously improve make him a valuable asset in the software engineering field, contributing to the growth and innovation of the industry.
1 note
·
View note
Note
I know someone who hated Akechi's engine room death but not because of whatever it says about abuse victims but more that it was a shitty ending for his arc and proof that atlus did not give a shit about akechi until royal
That’s an opinion they’re free to have but I disagree that it’s proof Atlus did not care about him until Royal given all the promotion and focus he got even outside of Royal. I think it’s more a sign that Atlus conceptualized him first and foremost as an antagonist whereas in Royal he’s much more in the anti-hero/potential all camp, but that doesn’t mean they hated him
#I’m like#eh take it or leave it with engine room#like yeah he coulda lived yeah he coulda died one is inherently better or worse than the other ya feel me?#alto replies#anonymous#fandom salt
1 note
·
View note
Text
Palo Alto Certified Engineers

How Palo Alto Firewalls Help Protect Against Ransomware Attacks - Palo Alto Certified Engineers
Palo Alto Networks is a leading provider of cybersecurity solutions, including next-generation firewalls that are designed to provide advanced threat protection. Ransomware attacks are a growing concern for organizations of all sizes, and Palo Alto firewalls can help protect against these types of attacks. One of the key features of Palo Alto firewalls is their ability to identify and block known ransomware threats using advanced threat intelligence and machine learning. Additionally, Palo Alto firewalls can help prevent ransomware attacks by enforcing strict security policies, limiting network access, and monitoring network traffic for suspicious activity. By implementing Palo Alto firewalls, organizations can significantly reduce their risk of falling victim to a ransomware attack and minimize the impact of any potential attacks that do occur.
0 notes
Video
youtube
Tesla Global Engineering HQ announcement
0 notes
Text




Suzuki Alto Heart Stand, 2004. A small commercial van concept based on the HA24 6th generation Alto, adapted to work as an outdoor plant stall. Presented at the the 38th Tokyo Motor Show, the rear side panel was also equipped with a liquid crystal display for advertisements and information. It was powered by a 660cc DHC 12 valve 3 cylinder engine driving the front wheels. There was only one seat, for the driver, as the offside area was used for storage and to display more plants
#Suzuki#Suzuki Alto#Suzuki Alto HA24#Suzuki Alto Heart Stand#concept#prototype#concept van#design study#plant stall#38th Tokyo Motor Show
595 notes
·
View notes
Text
A Fatal Mistake
a ford x reader fic
MINORS DNI

Ford is being driven to the brink of insanity for betraying Bill, constantly possessed and harmed in every way possible. He’s been missing for days and you’re working to find him when he comes through the front door, looking incredibly worse for wear.
warnings: blood, injury, possession, oral, p in v, creampie, knives, death
i included one of my favorite astronomy facts! i loved astronomy in high school, it was actually one of the few classes i applied myself in. i was gonna give the ending my usual fluff treatment, but after reading the book of bill and seeing how dark things get in the lost journal pages i couldn’t help myself.
It had been days since you had seen your research partner, Ford. As of late disappearing for a day or two was commonplace for him, but it had been almost a week with no sign of him.
You never had any idea what he got himself up to when he took off like that. He’d come back with various injuries and when you tried to probe him for their source he always insisted he didn’t remember. Normally you’d think he was lying, but it genuinely seemed like he was telling the truth.
It killed you to see him like this. Not just because you cared for him as your research partner, but because you harbored deep feelings for him. You always had, ever since you met him all those years ago in college.
When he called you up asking for you to come work with him in a small town in Oregon, you happily agreed to it without a second thought. For the longest time it was just you and him, discovering and documenting the weirdness that inhabited Gravity Falls. There were so many times you wanted to tell him how you felt, but you were plagued with cold feet.
Years had passed when another brilliant mind joined the team after you’d both hit a roadblock in your studies. Ford had been struck with the idea, as if from nowhere, to build an inter-dimensional portal. You two were incredibly brilliant, but lacked the engineering skills to complete this monumental task on your own. Ford called up his old college roommate, Fiddleford McGucket, in Palo Alto. He eagerly accepted the offer, insisting Ford’s plans were “mathematically feasible!”
As much as you enjoyed Fiddleford’s company, any chance you’d had to confess your feelings to Ford fell by the wayside. Between diligent work and never being alone with him, you simply didn’t have the time.
After months of the three of you spending every waking moment on the portal, the time came to finally test it. Things went wrong, horribly wrong. The rope tied to the test dummy had wrapped around Fiddleford’s wrist, pulling him halfway through the portal. Ford’s and your quick thinking allowed you two to heave him back out. Ford tried to ask him what he had seen, but he rambled incomprehensible nonsense and said the machine would bring about the apocalypse. He quit on the spot.
What should have been a silver lining to have Ford to just yourself again did not turn out to be so. In the following days he became erratic, paranoid, overrun by sleep deprivation, constantly turning his head as if to sounds you could never hear. He was a shell of his former self, but you were determined to stick by him.
One morning he called you frantically, all you could make out was “Fiddleford was right���. He did not elaborate, insisting he had more to say to you in person. Alarmed by the obvious decline in his mental state, you raced over. He sat you down on his couch and explained everything.
He confessed that building the portal was not his idea, that he was instructed to do so by an otherworldly being by the name of Bill Cipher. He had trusted him, lured in by Bill stroking his admittedly massive ego, praising his high IQ, and promising him the secrets that would solve the mystery that was the weirdness of Gravity Falls. Bill said that the portal would be Ford’s magnum opus, a true conclusion to the answers he so desperately sought.
But it was all a lie. Bill needed the portal to link his dimension to yours so he could take over and establish a “Weirdmageddon”. A cataclysmic event that would turn all reason and logic on its head, it would spell the end to life and the universe as you knew it.
It was a lot to take in, but the look on Ford’s face told you that this was gravely serious. You took his word without question, vowing to put an end to Bill’s plans and destroy him at all costs. Within days the disappearances started to happen.
At first you wondered if these episodes were some kind bender, be it alcohol or drugs… or both. Perhaps a way to cope with the reality of being used as Bill’s pawn in a sick game of chess for the fate of the universe. But now you were certain there was something far more sinister at play.
It was a fairly common occurrence that you saw his eyes glow bright yellow, pupils catlike. His demeanor would shift and his voice would change in register, almost as if someone was speaking through him. During these instances it was like he became a different person, he was wild and unpredictable. He would say things to you either for shock value or in an overtly flirtatious manner just to see you turn red.
You had studied your fair share about demonic possession. With the way Ford had described previous moments where Bill had taken over, back when he still considered him his “Muse”, it was a no-brainer that Ford was once again being used by Bill. This time it was for his own sick enjoyment of making his former puppet suffer, a punishment for Ford’s betrayal.
You sat in the secluded cabin in the woods the two of you used to conduct research in, before things had become so tumultuous. Night had fallen and you were on the phone speaking to the GFPD.
“So you’re not going to send out someone to look for him until morning!? Why can’t you do it now? He hasn’t been seen in days! He could be-“
The front door swung open with an incredibly disheveled Ford standing in the doorway.
“FORD!” You shouted.
“Hello, hello?” The officer asked over the phone.
“He just walked in the door, sorry for all the trouble.” You said unceremoniously, slamming the phone.
“Where have you been? I was so worried!” You said.
Before Ford had a chance to respond he began to fall forward, you leapt to your feet and caught him before his face could make contact with the floor. You took his face in your hands and studied his eyes. They looked insanely bloodshot and exhausted, but thankfully normal.
“Ford, what the hell happened to you?”
“I- I don’t know.” He murmured faintly.
“Let me get you somewhere comfortable.”
You lifted him up, put your arm around his shoulders and led him back to his room, sitting him on the couch. You scanned him from head to toe. His white button-up shirt was torn with a long horizontal laceration across his chest, a ring of blood stained his shirt, it looked like he’d been attacked with a knife. You put a hand to his chest, he flinched.
“Oh, Ford. Who did this to you?”
“I can’t recall a thing. I remember nothing from the near week I was gone.”
“Regardless, I need to get you cleaned up. I’ll be right back.”
You headed to the bathroom where he kept a first aid kit in the medicine cabinet. You made your way back and sat next to him on the couch.
“This shirt’s gonna have to go.” You said, pulling scissors from the kit.
“I don’t think there’s any chance of salvaging it anyway.” He chuckled weakly.
You removed his tie and cut away at his shirt, sliding the remains off his arms and revealing his chest. With the shirt no longer obstructing your view you could see that the cut was deep, but thankfully not enough to require stitches. He had avoided a hospital trip… this time.
“You know, you’re probably gonna have to get a tetanus shot.” You said.
He laughed softly “I’ll take it over rabies shots, those are hell.”
You pulled out a small bottle of disinfectant and a cotton pad. He winced as you applied it to the gash.
“I’ll never get accustomed to this sensation.” He said through gritted teeth.
“I’d imagine obtaining the injury was far worse.”
“It’s a good thing I can’t remember it then.” He smiled sheepishly.
You unfurled a roll of gauze, pulling his back away from the couch and wrapping his chest.
“Ford, you have to tell me why you keep vanishing. I know you say you don’t remember, but I’m certain there’s more to it. I know it has something to do with Bill.”
He looked away, afraid to meet your gaze. You took his cheek in your hand, turning him to face you.
“Hey, I tell you everything, I know you can do the same for me.”
He put his hand over yours and took a deep breath. “I leave because I don’t want to put you in danger. On nights where I can no longer fight the exhaustion, Bill threatens me in my dreams- my nightmares. He wants to hurt you.”
“There has to be a way I can help keep him from taking over. Something, anything.”
“I wish I knew, but I… don’t. I feel like I’m slowly going insane, but at least if I’m away from you I can’t harm you.”
“I’m not letting you face this on your own, we’re a team and I’m not going anywhere. You scared me half to death over these last few days. I started to think I might’ve lost you. I’m not losing you again, not even for a second.”
“You don’t understand the violent things Bill wants me to do to you, to kill you.”
With stakes as high as they were you realized how foolish it was to keep secrets, even your feelings for him.
“No matter what happens, I’m staying. I love you, Ford.”
You leaned in and kissed him. When you pulled back he stared at you, blood rushing to his cheeks.
“You love me?” Ford he whispered.
“I have for over a decade.”
“I- I had no idea.”
“Well, you’re the smartest man I know, but you’re incredibly stupid when it comes to romance.” You laughed.
“Touché.” He smiled.
“Ford, I don’t know if you feel the same way, but I’ve wanted you for so lo-“
He cut you off by pulling you onto his lap and kissing you passionately.
“I love you too, stardust.”
Ah yes, the nickname he’d given you in college. You had told him a fact about how certain elements in human bodies only form from the death of a star. You told him “we are literally made of stardust” and the name stuck. He always said it in a way that came off platonically, but this time as it left his lips it was obvious the intent was vastly different.
He looked at you directly in the eyes, he hated eye contact so you knew you must’ve mattered to him a great deal.
“I’ve felt the same way for so long, I just never thought you did so I put my feelings aside, buried them deep. You have no idea how often my thoughts are occupied by you. There were so many times I would just watch you working, the way your brow furrows in concentration is adorable. I need you like a flower craves sunlight, like a fish to water.” He whispered.
You kissed him again, tangling your fingers in his hair. He lowered his mouth to your neck, kissing and sucking the skin. You ground yourself against him, eliciting a soft moan against your neck and causing him to grow achingly hard.
“God, I’ve wanted this since the day you came into my life.” He breathed.
You sunk to the floor in front of him and started undoing his belt. You unzipped his fly and pulled out his cock. Jesus christ, he was big. You stroked him a few times before taking him in your mouth.
“F- fuck, your mouth feels incredible.” He moaned.
You moved your head up and down his shaft, Ford whimpering far more than you had expected.
“Ah, hhhnh, don’t stop.” He whined.
He ran his fingers through your hair, moaning and softly bucking his hips into your mouth. He took great care to not move hard enough to make you gag. You picked up your pace, stroking him with your hand as you sucked.
“Nhhhh where did you learn to do something like that? You’re so good at this. Y- you’re gonna make me c- cum if you keep guh- going- ah- like that.” He stuttered.
You bobbed your head furiously on him. He tangled his fist in your hair and gently pulled your mouth off of him.
“N- no, stop. I need to feel myself inside you. Please?”
You nodded and he turned himself to lay back on the couch, you stood and slipped your panties off from under your skirt, dropping them to the floor. You got on top of him, straddling his hips and hovering over his cock. You lowered yourself to take his length inside you, now it was your turn to whimper as your pussy struggled to accommodate him.
“Dear moses, stardust, and I thought your mouth felt good. You’re heavenly. So warm and- mmh- tight.”
You slid him fully inside you, never feeling so filled by cock before in your life. He rested his hands on your hips and you began to move yourself on him. He threw his head back, already overwhelmed by the mere feeling of your pussy taking his cock.
He panted. “You can’t imagine the amount of times I’ve pictured something like this. How often you’ve distracted me from my work. The nights I’ve spent with my hand wrapped around my cock, the mere thought of you pushing me to orgasm. Oh stars, how I longed to know you intimately.”
He slipped a hand between your thighs, stroking your clit with his thumb, the other hand still holding your hip. You bit your lip, stifling what would have been an uncomfortably loud moan, tightening around him.
“Good girl, I love how my touch makes you constrict my cock.”
You became even tighter at his praise.
“Nnnnahhh, Ford.”
“Is that a praise kink I sense, stardust?”
You nodded fervently.
“That’s my girl, so needy for my words.”
You lifted and dropped your hips, sliding him fully in and out of you at a steady rhythm. His eyes rolled back into his head, completely overtaken by the pleasure of you. His breath was ragged, his eyes never leaving you, darting between your body and face.
“You’re so gorgeous, stardust. I’ve studied so many creatures over the years, seen the likes of sirens and nymphs, but you are by far the most enchanting.”
He reached up a hand to cup your cheek, you leaned into his touch. You felt yourself growing close between both his words and thumb on your clit. You made an attempt to tell him, but all that came out was unintelligible whimpering.
“Oh Ford, you’re- I’m gonna- ah- nhhhh.”
“That’s it, you’re such a good girl. Cum for me, you’re almost there.”
You absolutely lost it at his praise, digging your nails into his shoulders and riding him as hard as you possibly could until you came completely undone around him. The feeling of you spasming and contracting around him sent him over. He released your clit, both hands gripping your hips. He slammed you down onto the full length of his cock and came deep inside you.
“Dear god, y/n!” He half moaned, half whimpered.
Your pace died down and for a while you stayed on top of him. You both said nothing, just looking into each other’s eyes and panting as your heart rates settled. You leaned down, pressing a kiss to his lips and pulled yourself off of him. You laid down, Ford spooning you.
“In the name of all the stars in the known universe and beyond, you are absolutely incredible, stardust.” He sighed, content.
“I love you, Ford.” You said, eyelids growing heavy.
He pressed a kiss to the top of your head. “I love you too, y/n.”
You both lay in silence, slumber embracing you. Bill knew it was now or never. He took control of Ford and silently moved him off the couch so as to not wake you. He led him to the kitchen, pulling out a large knife. He crept back into the room where you slept, looming over you.
You stirred. “Mnh, Ford? What are you-“
Your eyes widened in terror as you caught sight of the knife in his hand, his eyes glowed unnaturally in the dim light. Adrenaline rushed through your veins, you bolted off the couch and ran for your life. You burst through the front door and took off into the forest, the light of the full moon being the only thing to keep you from crashing into the trees.
A constant crunching of snow behind you was a strong indicator that Ford was pursuing you. Tears streamed down your face. You said you would stand by him no matter what and now you were paying the price for thinking with your heart.
You looked back to see if you were still being followed, but didn’t see him. Before you could even turn your head again you collided with something, falling to the ground. You looked up and your heart sank. Ford grinned with a smile so wide it looked as if the corners of his mouth would split open.
“Hey there, dollface. I don’t think we’ve been properly introduced.”
-
Ford came to god knows how much later. He blinked, vision blurry, as it always was after Bill had taken hold. He could see a figure lying in the snow and as his eyes began to focus he screamed in horror.
You lay before him, your body stabbed near beyond recognition, an immense pool of blood stained the fresh snow. There was no way to bring you back, you were gone. A page ripped from Ford’s journal laid on top of you.
“Did you really think I’d let you have your happy ending with your little ‘stardust’? It’s just us now, sixer, I’m all you’ll ever need.”
89 notes
·
View notes
Text

Moving Castiel
Author: Raven_Fuchs
Artist: Marvfortytwo
Rating: Mature
Pairings: Dean/Castiel; Mary Winchester/John Winchester; Sam Winchester/Jessica Moore
Length: 24523
Warnings: No warnings apply
Tags: Friends to lovers, Tornado, Mild depression, Cafe/Bakery AU, Low angst
Summary: As Dean is about to graduate with his Masters degree in engineering he loses his job repairing items at a pawn shop and starts working for his friend Cas in his cafe. Dean discovers he’s a natural at baking and hopes one day to go into business with Cas. Cas runs a cafe that his aunt left him while it gives him experience he yearns to establish his own speciality bake shop. After a tornado destroys the cafe Dean and Cas have to decide if they’ll both relocate to California and set up the bakery of Cas’ dreams while Dean rejoins his mom who moved out there to help Sam and Jess with their new baby. Decision made, the boys look for a place in Palo Alto to start their new business that fuses Cas’ baking talent with Dean’s mechanical know-how.
Link to Fic | Link to Art
68 notes
·
View notes
Text
Not-a-tutorial - Lighting (Advanced)
Previous parts:
Not-a-Tutorial - Lighting (Basics)
Not-a-Tutorial - Lighting (Basics - Indoor)
Intention:
While dialogues and body language can say a whole lot on what you're trying to tell to the reader, lights can as well! Here's a great example:


(Left is with the lights on, right is with the lights off).
As you can see, the left one feels much more like it's... let's say, a winter-y 6pm, and she's studying in the library...
Whereas on the right, it feels much more like she's skipping on sleep, and it's 3am, studying.
Moods:
You can also use lighting for more tenser scenes! Here are a few examples from my story:

Here the setup was the same, but I added softer rose/red pastel-y colours... (Though this scene did have like 6 lights :p)

Here I not only used a blue backlight for giving it a “night” feeling, but I also added an orange and white front-light to represent a sense of hope and that our poor Ethan isn't alone.

Here I gave Vita and Nick Alto a yellow, green and red lighting setup, to represent more jealous and angry colours for Nancy. As Nancy is staring at them.
However, the pink represents not only the stage light, but also a sense of Innocence given her background of not understanding the entrepreneur game.

Here I gave little Bella a red background and light foreground, keeping the left part of her face dark, as the speech is about the future of the town. And with the light, she represents a bright but unclear future.
Note: all of these images do use Reshade, so trying to get these results without it may look a bit different!
Seasons:
Representing the colours associated with the seasons can give a scene a really cool feeling!




Summer, Spring, Autumn, Winter.
Color mixing:
One thing I thought was pretty cool with TS3's Lighting engine, is how colors in certain highlights will mix just like paint!

Red + Blue looks a bit purple-ish.

Red + Yellow will look a bit orange-y.

Blue and Yellow will turn green-ish at parts.
Custom Coloured Lights
Sometimes, some of EA's colours aren't... quite there. Or really what you need. Here is a short list of colours I've made and used:
0, 150, 255 - Replacement of Cyan (More of a light blue):

0, 163, 108 - Jade

255, 195, 0 (better Yellow)

What's the easiest way to find new colours?
It's pretty easy! If you google for "Colour generator" then there you go! Do make sure to get the RGB values from those websites!
But, for the ones who don't want to google, here are a few suggestions:
Give them a try and see which ones are great! Do go for colours that are quite strong in contrast. Pastel will just end up being white, and darker colours will just turn... well it will look like there is no light on :p
That was it! Hopefully it was insightful, and obviously feel free to add your own discoveries to it! :)
#the sims 3#ts3#sims 3#the sims#sims#sims 3 story#sims 3 screenshots#sims 3 gameplay#thesims3#ts3 simblr#ts3 gameplay#ts3 screenshots#sims 3 blog#sims 3 simblr#sims3
117 notes
·
View notes
Text
Shamir Secret Sharing
It’s 3am. Paul, the head of PayPal database administration carefully enters his elaborate passphrase at a keyboard in a darkened cubicle of 1840 Embarcadero Road in East Palo Alto, for the fifth time. He hits Return. The green-on-black console window instantly displays one line of text: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.”
There is nerd pandemonium all around us. James, our recently promoted VP of Engineering, just climbed the desk at a nearby cubicle, screaming: “Guys, if we can’t get this key the right way, we gotta start brute-forcing it ASAP!” It’s gallows humor – he knows very well that brute-forcing such a key will take millions of years, and it’s already 6am on the East Coast – the first of many “Why is PayPal down today?” articles is undoubtedly going to hit CNET shortly. Our single-story cubicle-maze office is buzzing with nervous activity of PayPalians who know they can’t help but want to do something anyway. I poke my head up above the cubicle wall to catch a glimpse of someone trying to stay inside a giant otherwise empty recycling bin on wheels while a couple of Senior Software Engineers are attempting to accelerate the bin up to dangerous speeds in the front lobby. I lower my head and try to stay focused. “Let’s try it again, this time with three different people” is the best idea I can come up with, even though I am quite sure it will not work.
It doesn’t.
The key in question decrypts PayPal’s master payment credential table – also known as the giant store of credit card and bank account numbers. Without access to payment credentials, PayPal doesn’t really have a business per se, seeing how we are supposed to facilitate payments, and that’s really hard to do if we no longer have access to the 100+ million credit card numbers our users added over the last year of insane growth.
This is the story of a catastrophic software bug I briefly introduced into the PayPal codebase that almost cost us the company (or so it seemed, in the moment.) I’ve told this story a handful of times, always swearing the listeners to secrecy, and surprisingly it does not appear to have ever been written down before. 20+ years since the incident, it now appears instructive and a little funny, rather than merely extremely embarrassing.
Before we get back to that fateful night, we have to go back another decade. In the summer of 1991, my family and I moved to Chicago from Kyiv, Ukraine. While we had just a few hundred dollars between the five of us, we did have one secret advantage: science fiction fans.
My dad was a highly active member of Zoryaniy Shlyah – Kyiv’s possibly first (and possibly only, at the time) sci-fi fan club – the name means “Star Trek” in Ukrainian, unsurprisingly. He translated some Stansilaw Lem (of Solaris and Futurological Congress fame) from Polish to Russian in the early 80s and was generally considered a coryphaeus at ZSh.
While USSR was more or less informationally isolated behind the digital Iron Curtain until the late ‘80s, by 1990 or so, things like FidoNet wriggled their way into the Soviet computing world, and some members of ZSh were now exchanging electronic mail with sci-fi fans of the free world.
The vaguely exotic news of two Soviet refugee sci-fi fans arriving in Chicago was transmitted to the local fandom before we had even boarded the PanAm flight that took us across the Atlantic [1]. My dad (and I, by extension) was soon adopted by some kind Chicago science fiction geeks, a few of whom became close friends over the years, though that’s a story for another time.
A year or so after the move to Chicago, our new sci-fi friends invited my dad to a birthday party for a rising star of the local fandom, one Bruce Schneier. We certainly did not know Bruce or really anyone at the party, but it promised good food, friendly people, and probably filk. My role was to translate, as my dad spoke limited English at the time.
I had fallen desperately in love with secret codes and cryptography about a year before we left Ukraine. Walking into Bruce’s library during the house tour (this was a couple years before Applied Cryptography was published and he must have been deep in research) felt like walking into Narnia.
I promptly abandoned my dad to fend for himself as far as small talk and canapés were concerned, and proceeded to make a complete ass out of myself by brazenly asking the host for a few sheets of paper and a pencil. Having been obliged, I pulled a half dozen cryptography books from the shelves and went to work trying to copy down some answers to a few long-held questions on the library floor. After about two hours of scribbling alone like a man possessed, I ran out of paper and decided to temporarily rejoin the party.
On the living room table, Bruce had stacks of copies of his fanzine Ramblings. Thinking I could use the blank sides of the pages to take more notes, I grabbed a printout and was about to quietly return to copying the original S-box values for DES when my dad spotted me from across the room and demanded I help him socialize. The party wrapped soon, and our friends drove us home.
The printout I grabbed was not a Ramblings issue. It was a short essay by Bruce titled Sharing Secrets Among Friends, essentially a humorous explanation of Shamir Secret Sharing.
Say you want to make sure that something really really important and secret (a nuclear weapon launch code, a database encryption key, etc) cannot be known or used by a single (friendly) actor, but becomes available, if at least n people from a group of m choose to do it. Think two on-duty officers (from a cadre of say 5) turning keys together to get ready for a nuke launch.
The idea (proposed by Adi Shamir – the S of RSA! – in 1979) is as simple as it is beautiful.
Let’s call the secret we are trying to split among m people K.
First, create a totally random polynomial that looks like: y(x) = C0 * x^(n-1) + C1 * x^(n-2) + C2 * x^(n-3) ….+ K. “Create” here just means generate random coefficients C. Now, for every person in your trusted group of m, evaluate the polynomial for some randomly chosen Xm and hand them their corresponding (Xm,Ym) each.
If we have n of these points together, we can use Lagrange interpolating polynomial to reconstruct the coefficients – and evaluate the original polynomial at x=0, which conveniently gives us y(0) = K, the secret. Beautiful. I still had the printout with me, years later, in Palo Alto.
It should come as no surprise that during my time as CTO PayPal engineering had an absolute obsession with security. No firewall was one too many, no multi-factor authentication scheme too onerous, etc. Anything that was worth anything at all was encrypted at rest.
To decrypt, a service would get the needed data from its database table, transmit it to a special service named cryptoserv (an original SUN hardware running Solaris sitting on its own, especially tightly locked-down network) and a special service running only there would perform the decryption and send back the result.
Decryption request rate was monitored externally and on cryptoserv, and if there were too many requests, the whole thing was to shut down and purge any sensitive data and keys from its memory until manually restarted.
It was this manual restart that gnawed at me. At launch, a bunch of configuration files containing various critical decryption keys were read (decrypted by another key derived from one manually-entered passphrase) and loaded into the memory to perform future cryptographic services.
Four or five of us on the engineering team knew the passphrase and could restart cryptoserv if it crashed or simply had to have an upgrade. What if someone performed a little old-fashioned rubber-hose cryptanalysis and literally beat the passphrase out of one of us? The attacker could theoretically get access to these all-important master keys. Then stealing the encrypted-at-rest database of all our users’ secrets could prove useful – they could decrypt them in the comfort of their underground supervillain lair.
I needed to eliminate this threat.
Shamir Secret Sharing was the obvious choice – beautiful, simple, perfect (you can in fact prove that if done right, it offers perfect secrecy.) I decided on a 3-of-8 scheme and implemented it in pure POSIX C for portability over a few days, and tested it for several weeks on my Linux desktop with other engineers.
Step 1: generate the polynomial coefficients for 8 shard-holders.
Step 2: compute the key shards (x0, y0) through (x7, y7)
Step 3: get each shard-holder to enter a long, secure passphrase to encrypt the shard
Step 4: write out the 8 shard files, encrypted with their respective passphrases.
And to reconstruct:
Step 1: pick any 3 shard files.
Step 2: ask each of the respective owners to enter their passphrases.
Step 3: decrypt the shard files.
Step 4: reconstruct the polynomial, evaluate it for x=0 to get the key.
Step 5: launch cryptoserv with the key.
One design detail here is that each shard file also stored a message authentication code (a keyed hash) of its passphrase to make sure we could identify when someone mistyped their passphrase. These tests ran hundreds and hundreds of times, on both Linux and Solaris, to make sure I did not screw up some big/little-endianness issue, etc. It all worked perfectly.
A month or so later, the night of the key splitting party was upon us. We were finally going to close out the last vulnerability and be secure. Feeling as if I was about to turn my fellow shard-holders into cymeks, I gathered them around my desktop as PayPal’s front page began sporting the “We are down for maintenance and will be back soon” message around midnight.
The night before, I solemnly generated the new master key and securely copied it to cryptoserv. Now, while “Push It” by Salt-n-Pepa blared from someone’s desktop speakers, the automated deployment script copied shard files to their destination.
While each of us took turns carefully entering our elaborate passphrases at a specially selected keyboard, Paul shut down the main database and decrypted the payment credentials table, then ran the script to re-encrypt with the new key. Some minutes later, the database was running smoothly again, with the newly encrypted table, without incident.
All that was left was to restore the master key from its shards and launch the new, even more secure cryptographic service.
The three of us entered our passphrases… to be met with the error message I haven’t seen in weeks: “Sorry, one or more wrong passphrases. Can’t reconstruct the key. Goodbye.” Surely one of us screwed up typing, no big deal, we’ll do it again. No dice. No dice – again and again, even after we tried numerous combinations of the three people necessary to decrypt.
Minutes passed, confusion grew, tension rose rapidly.
There was nothing to do, except to hit rewind – to grab the master key from the file still sitting on cryptoserv, split it again, generate new shards, choose passphrases, and get it done. Not a great feeling to have your first launch go wrong, but not a huge deal either. It will all be OK in a minute or two.
A cursory look at the master key file date told me that no, it wouldn’t be OK at all. The file sitting on cryptoserv wasn’t from last night, it was created just a few minutes ago. During the Salt-n-Pepa-themed push from stage, we overwrote the master key file with the stage version. Whatever key that was, it wasn’t the one I generated the day before: only one copy existed, the one I copied to cryptoserv from my computer the night before. Zero copies existed now. Not only that, the push script appears to have also wiped out the backup of the old key, so the database backups we have encrypted with the old key are likely useless.
Sitrep: we have 8 shard files that we apparently cannot use to restore the master key and zero master key backups. The database is running but its secret data cannot be accessed.
I will leave it to your imagination to conjure up what was going through my head that night as I stared into the black screen willing the shards to work. After half a decade of trying to make something of myself (instead of just going to work for Microsoft or IBM after graduation) I had just destroyed my first successful startup in the most spectacular fashion.
Still, the idea of “what if we all just continuously screwed up our passphrases” swirled around my brain. It was an easy check to perform, thanks to the included MACs. I added a single printf() debug statement into the shard reconstruction code and instead of printing out a summary error of “one or more…” the code now showed if the passphrase entered matched the authentication code stored in the shard file.
I compiled the new code directly on cryptoserv in direct contravention of all reasonable security practices – what did I have to lose? Entering my own passphrase, I promptly got “bad passphrase” error I just added to the code. Well, that’s just great – I knew my passphrase was correct, I had it written down on a post-it note I had planned to rip up hours ago.
Another person, same error. Finally, the last person, JK, entered his passphrase. No error. The key still did not reconstruct correctly, I got the “Goodbye”, but something worked. I turned to the engineer and said, “what did you just type in that worked?”
After a second of embarrassed mumbling, he admitted to choosing “a$$word” as his passphrase. The gall! I asked everyone entrusted with the grave task of relaunching crytposerv to pick really hard to guess passphrases, and this guy…?! Still, this was something -- it worked. But why?!
I sprinted around the half-lit office grabbing the rest of the shard-holders demanding they tell me their passphrases. Everyone else had picked much lengthier passages of text and numbers. I manually tested each and none decrypted correctly. Except for the a$$word. What was it…
A lightning bolt hit me and I sprinted back to my own cubicle in the far corner, unlocked the screen and typed in “man getpass” on the command line, while logging into cryptoserv in another window and doing exactly the same thing there. I saw exactly what I needed to see.
Today, should you try to read up the programmer’s manual (AKA the man page) on getpass, you will find it has been long declared obsolete and replaced with a more intelligent alternative in nearly all flavors of modern Unix.
But back then, if you wanted to collect some information from the keyboard without printing what is being typed in onto the screen and remain POSIX-compliant, getpass did the trick. Other than a few standard file manipulation system calls, getpass was the only operating system service call I used, to ensure clean portability between Linux and Solaris.
Except it wasn’t completely clean.
Plain as day, there it was: the manual pages were identical, except Solaris had a “special feature”: any passphrase entered that was longer than 8 characters long was automatically reduced to that length anyway. (Who needs long passwords, amiright?!)
I screamed like a wounded animal. We generated the key on my Linux desktop and entered our novel-length passphrases right here. Attempting to restore them on a Solaris machine where they were being clipped down to 8 characters long would never work. Except, of course, for a$$word. That one was fine.
The rest was an exercise in high-speed coding and some entirely off-protocol file moving. We reconstructed the master key on my machine (all of our passphrases worked fine), copied the file to the Solaris-running cryptoserv, re-split it there (with very short passphrases), reconstructed it successfully, and PayPal was up and running again like nothing ever happened.
By the time our unsuspecting colleagues rolled back into the office I was starting to doze on the floor of my cubicle and that was that. When someone asked me later that day why we took so long to bring the site back up, I’d simply respond with “eh, shoulda RTFM.”
RTFM indeed.
P.S. A few hours later, John, our General Counsel, stopped by my cubicle to ask me something. The day before I apparently gave him a sealed envelope and asked him to store it in his safe for 24 hours without explaining myself. He wanted to know what to do with it now that 24 hours have passed.
Ha. I forgot all about it, but in a bout of “what if it doesn’t work” paranoia, I printed out the base64-encoded master key when we had generated it the night before, stuffed it into an envelope, and gave it to John for safekeeping. We shredded it together without opening and laughed about what would have never actually been a company-ending event.
P.P.S. If you are thinking of all the ways this whole SSS design is horribly insecure (it had some real flaws for sure) and plan to poke around PayPal to see if it might still be there, don’t. While it served us well for a few years, this was the very first thing eBay required us to turn off after the acquisition. Pretty sure it’s back to a single passphrase now.
Notes:
1: a member of Chicagoland sci-fi fan community let me know that the original news of our move to the US was delivered to them via a posted letter, snail mail, not FidoNet email!
522 notes
·
View notes
Text

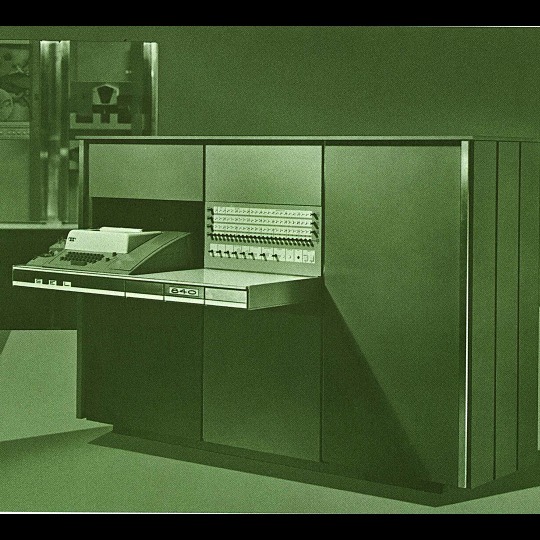




🎄💾🗓️ Day 11: Retrocomputing Advent Calendar - The SEL 840A🎄💾🗓️
Systems Engineering Laboratories (SEL) introduced the SEL 840A in 1965. This is a deep cut folks, buckle in. It was designed as a high-performance, 24-bit general-purpose digital computer, particularly well-suited for scientific and industrial real-time applications.
Notable for using silicon monolithic integrated circuits and a modular architecture. Supported advanced computation with features like concurrent floating-point arithmetic via an optional Extended Arithmetic Unit (EAU), which allowed independent arithmetic processing in single or double precision. With a core memory cycle time of 1.75 microseconds and a capacity of up to 32,768 directly addressable words, the SEL 840A had impressive computational speed and versatility for its time.
Its instruction set covered arithmetic operations, branching, and program control. The computer had fairly robust I/O capabilities, supporting up to 128 input/output units and optional block transfer control for high-speed data movement. SEL 840A had real-time applications, such as data acquisition, industrial automation, and control systems, with features like multi-level priority interrupts and a real-time clock with millisecond resolution.
Software support included a FORTRAN IV compiler, mnemonic assembler, and a library of scientific subroutines, making it accessible for scientific and engineering use. The operator’s console provided immediate access to registers, control functions, and user interaction! Designed to be maintained, its modular design had serviceability you do often not see today, with swing-out circuit pages and accessible test points.
And here's a personal… personal computer history from Adafruit team member, Dan…
== The first computer I used was an SEL-840A, PDF:
I learned Fortran on it in eight grade, in 1970. It was at Oak Ridge National Laboratory, where my parents worked, and was used to take data from cyclotron experiments and perform calculations. I later patched the Fortran compiler on it to take single-quoted strings, like 'HELLO', in Fortran FORMAT statements, instead of having to use Hollerith counts, like 5HHELLO.
In 1971-1972, in high school, I used a PDP-10 (model KA10) timesharing system, run by BOCES LIRICS on Long Island, NY, while we were there for one year on an exchange.
This is the front panel of the actual computer I used. I worked at the computer center in the summer. I know the fellow in the picture: he was an older high school student at the time.
The first "personal" computers I used were Xerox Alto, Xerox Dorado, Xerox Dandelion (Xerox Star 8010), Apple Lisa, and Apple Mac, and an original IBM PC. Later I used DEC VAXstations.
Dan kinda wins the first computer contest if there was one… Have first computer memories? Post’em up in the comments, or post yours on socialz’ and tag them #firstcomputer #retrocomputing – See you back here tomorrow!
#retrocomputing#firstcomputer#electronics#sel840a#1960scomputers#fortran#computinghistory#vintagecomputing#realtimecomputing#industrialautomation#siliconcircuits#modulararchitecture#floatingpointarithmetic#computerscience#fortrancode#corememory#oakridgenationallab#cyclotron#pdp10#xeroxalto#computermuseum#historyofcomputing#classiccomputing#nostalgictech#selcomputers#scientificcomputing#digitalhistory#engineeringmarvel#techthroughdecades#console
28 notes
·
View notes
Note
hi alto!!!!
do you think cid being an engineer and fully-fledged pilot with the last name "highwind" is a coincidence for him or do you think he legally changed it
I like to think that his last name is a moniker he adopted for himself. Maybe it was his nickname as a pilot. Cid is so incredibly proud of his pilot background that the name becomes inseparable to him.
I also hc that his REAL last name is something silly and stupid lmao so no wonder he'd change it.
25 notes
·
View notes
Text

Graham Bazell - An Ambitious Software Engineer
Graham Bazell, a highly skilled software engineer from Palo Alto, CA, is driven by his aspirations to excel in his field. With a focus on technical growth, Graham is committed to expanding his knowledge and becoming even more proficient in software engineering. His passion for technology and finance fuels his drive to build a successful career in this rapidly evolving field.
1 note
·
View note
