#adding serial number to rows of data
Explore tagged Tumblr posts
Link
How to add serial number in jasper ireport
#odoo jasper reporting#odoo reporting#odoo reporting tips#odoo pdf reports#odoo excel reports#jasper#jasper reports#jasper soft#jasper server#datasource in ireport#ireport#ireport designer#How to add serial number in jasper ireport#record Serial Number in Jasper Report#adding serial number to rows of data
0 notes
Text
Tip of the Week: Explaining Excel Formulas

Just under its surface, Microsoft Excel offers a massive variety of functions and features…far more than we could ever realistically cover in this blog. However, there are a few that stand out as relatively essential, particularly to businesses. Let’s go through these functions, starting with how to use them.
How Excel Formulas Work
Once you have a cell selected, you can type one of these formulas into the cell or the formula bar. Keep in mind that all Excel formulas begin with an equals sign, before the type of formula is specified and the appropriate data points are identified. If properly formatted, your spreadsheet can thereby be automated to do a huge variety of tasks based on the data you’ve input.
Here are some common formulas that you could find useful in your business’ operations.
=SUM()
This allows you to total up the value of the cells you’ve selected, making it far simpler to add up long lists of numbers. Let’s say you had a list made up in Column B, beginning at Row 2 and ending with Row 46. To total these numbers, you’d type up =SUM(B2:B46), and that cell would display the total as a result.
=AVERAGE()
In the same vein, =AVERAGE does the same thing, except it produces the average amongst those selected cells. =AVERAGE(X1,Y2,Z3) would give you the average of X1, Y2, and Z3.
=CEILING() and =FLOOR()
These functions allow you to round numbers to the nearest multiple of significance that you’ve established. Dictating =CEILING(F2,5) with F2 being populated with 368 would round up to 370. On the other end of the spectrum, =FLOOR(F2,5) would round down to 365.
=CONCATENATE()
Excel can also track changes in text too, with =CONCATENATE allowing you to tie different text strings together. For instance, if G7 read The 3-2-1 Backup Rule and K12 read helps to ensure your data backup is safe, entering =CONCATENATE(G7,” “,K12) would tie the phrases together and give you The 3-2-1 Backup Rule helps to ensure your data backup is safe. You can also format the formula as =CONCATENATE(G7&” “&K12) for the same results.
=NOW()
This formula will populate a cell with the current date and time, which helps you keep track of when your data was put into the spreadsheet.
=TODAY(), et alia.
There are a number of functions that do a similar thing to =NOW(), such as:
=TODAY(), which populates a cell with the current date
=DAY(TODAY()), which populates a cell with the current day of the month
=MONTH(TODAY()), which populates a cell with the current month, represented as a numerical value between 1 and 12
=TIME(), et alia.
In a similar vein, various functions allow you to track the exact time that data has been added to your spreadsheet.
=TIME() inserts a set time, so long as you format it as a serial number with the hours, minutes, and seconds, which will be converted into a standard format. So, =TIME(13,41,28) would produce 1:41 PM.
=HOUR(NOW()) populates a cell with the current hour as a value between 0 and 23 (12 AM to 11 PM).
=MINUTE(NOW()) does the same with the current minute, between 0 to 59.
=SECOND(NOW()) does the same with the current second, again, between 0 to 59.
=VLOOKUP() and =HLOOKUP()
Vertical lookup and horizontal lookup enable you to seek out a specific value in one column or row and produce the data that is associated with it. Let’s say that you have a table that outlines your business’ assorted costs, perhaps giving you the total, how much is invested into different aspects, and such. These Excel functions allow you to select certain data points as a reference so you can ascertain the relationship between different values.
=IF()
Using =IF() gives you a quick and easy reference to check whether a set condition is true or false in reference to your data. Let’s say you’ve calculated out the returns on investment that some of your business initiatives have produced. Using =IF(), you can generate a clear yes or no answer to whether or not an initiative has seen the returns you wanted it to. Maybe you wanted to weed out any initiatives that saw less than 2% ROI, with the ROI of each occupying a cell in Column E. Using =IF(E1>0.02,”Yes”,”No”) and dragging that formula down to match the cells in Column E will give you an at-a-glance reference of whether or not one of your efforts was worth it.
=COUNTIF() and =SUMIF()
The more data you have, the more challenging even simple tasks—like taking a tally or adding up the values—can be. =COUNTIF and =SUMIF simplify this process for you.
=COUNTIF() allows you to set conditions by which selected cells will be counted. For instance, if you wanted to count how many months you had sold widgets out of the data present in Column J of the sheet, =COUNTIF(J1:J12, “widget”) would give you that total.
=SUMIF() operates in a similar way, although it adds any numbers that match the conditions you’ve set, rather than just counting the instances. So, we could determine the total number of widgets sold during our established timeframe by using =SUMIF(J1:J12, “widget”, K1:K12), provided that Column K was populated with total widget sales for each month.
https://www.infradapt.com/news/tip-of-the-week-explaining-excel-formulas/
#Best Practices#Business#business spreadsheet#excel#excel formulas#excel tips#spreadsheet formula#tip of the week
11 notes
·
View notes
Text
Cradle
Available on AO3 Summary: Post-battle roll call. Notes: For @soundwaveweek, prompt was ‘poetry.’
---
The MTOs were stressed. He could understand that, and in fact had little choice but to. Coming online in a crashing shuttle was a less than ideal way to begin life, and the hours of listening to gunfire and artillery going off just outside their prison-slash-shelter almost guaranteed the sorts of injuries no tool could fix. Soundwave had no idea whether the silence that followed the Decepticon victory would have been a welcome reprieve or the most hellish stretch of the experience, but his torch cutting through the crumpled hatch had broken its hold on them, and now they were frantic.
Their thoughts cut him like millions of grains of sand caught up in the exhaust of a shuttle launch. There were questions, the standard Who is that?, Am I going to die?, and Is that supposed to happen? Then the observations, It’s dark, It’s light, He’s blue, He has a gun, and I have a gun.
Mostly, though, they were giving off impressions that could not be condensed so neatly into words, not without at least a few days’ practice to understand the ebb and flow of language. Without it, Soundwave could feel the crush of the darkness, the burning slice of the light. When he announced himself on arrival, his voice came back to him thirteen different ways, shivering or sliding or in boxes, an impressive feat for a group whose sum total life experiences were the inside of a dead shuttle and each other.
The volume increased as he approached them, both due to proximity and their own increasing anxieties. Their thoughts were loud enough to be knocking against his helm, adding to the cacophony the echo of his own internals, but he soldiered on, approaching the first cradle, its occupant staring at him with a mouthless expression that nevertheless seemed to snarl.
“Designation,” Soundwave demanded.
“Megatron.”
Hisses and whispers and flares. Soundwave wished he could turn down his sensitivity, but with all the cassettes investigating other casualty reports, he couldn’t risk making himself that vulnerable, even if it meant he would be taking a splitting processor ache to berth with him that night instead of recharge.
“Your designation,” he said, with no patience to start with.
The MTO stared at Soundwave, optics glancing first over his face and then the length of his frame. He started to speak, aborted the effort, attention straying to his comrades before snapping back to the officer. His thoughts were bright, sour, and runny, becoming more disorganized the longer Soundwave stood waiting for an answer. Now he was tearing through his data packs, the disorganized folders spilling open with instructions on how to shoot, who to shoot, which way to run—
“No designation,” Soundwave concluded, feeling a part of his psyche slump with resignation. “Serial code.”
The uncomprehending stare slid again to the other MTOs, whose own thoughts echoed the globular confusion. A few of them were in the same process of upending their entire storage libraries, and although any one of them could have accurately pinpointed the coordinates where their plummeting ship had disappeared off the edge of the battle map, not one of them could provide him the very basic information he needed to complete this task and leave these soldiers for the recovery teams to salvage.
Soundwave made a quick visual inspection of the MTO, who tried to lean away—not far, given that he was still suspended in the cradle—now that his defensive bluster had dried up. No printed serial code, nor was there on the MTO beside him, a quiet mech who barely glanced at Soundwave as he came close. No serial codes, either printed or coded.
“Any identification markers?” Soundwave asked the room at large. A flicker of movement: Soundwave looked down to the mech at the end of the starboard row, the one installed opposite the sole casualty, aside from the ship itself. His thoughts had been quieter than the rest, colorless and inflexible in a way that had suggested a concussion, but Soundwave’s question had provoked a brief flare. He was looking up: on the ceiling above his squadmate was painted the number 2.
That, unfortunately, was something that could be plugged into a database, checked against the shuttle manifest and production logs, and be used to reverse engineer a serial number. Success, though, depended on this being a legitimate deployment, and certain signs were suggesting the opposite, though none so definitively as to trigger a full investigation. Soundwave put out a recall signal to Frenzy and Ravage, wary of how isolated the shuttle’s final resting place was, and tuned his sensors up higher…
Only to immediately turn them down again as the minutiae of the newbuilds’ thoughts flowed like acid rain through fresh gaps in a roof. He could read the rudimentary threat assessments they were running on him and taste the swell of emotions too new to differentiate yet; the bravest among them had started to free curiosity from the mass, and they plugged it into every observation they made, building questions on top of each other until the thoughts were heavy enough to bend under their own weight. Within the shuttle, everything felt compressed and heavy on top of him.
“Calm down,” he commanded, and winced at spikes of anxiety impaling him from multiple directions.
What a waste, he thought as he recovered from the burst, of his time and their lives. Nova Point was captured, the Autobot base overrun, and Starscream’s choice to put him on recovery meant vital logistics standards were being delayed. The already lengthy identification process would easily be doubled if this much of his processor remained dedicated to his hypersensitivity sensors, and he was vulnerable as long as the soldiers’ thoughts were filling his audio feed. Soldier was even a generous word for the mechs he’d been tasked with risking his life for. Their minimal data packs and emotional instability would make them ill-suited to the promotions occasionally offered to MTOs. They would be getting hauled out of one wreck only to be pressed into another, one that would more likely than not reach its intended destination.
Soundwave did not fault Megatron for leading a chunk of their forces off to the distant front lines on other worlds, but he did long for his leader at times. Megatron would know what was best, whether to forge ahead with the recovery efforts or leave them here to—
“A new row of unlit lanterns is marched in, And I can’t remember what my world looks like In the dark.”
The recording was poor quality, torn from a processor moments before it went offline. Soundwave kept hoping to find the rest of the poem, but bots who survived that time were few and far between, and they guarded their secrets fiercely. Because it was short, he let it play out, and when it finished the attention of the MTOs had narrowed.
“What was that?” the first one asked.
“Untitled,” Soundwave said, which wasn’t entirely accurate. He had a recording of a secondhand account that referred to the poem as ‘The Chain Runners,’ but had never been able to confirm it. He could have asked, but then he would have to tell Megatron he kept the old poem, and that wasn’t a conversation he was ready to have yet.
“But what was it?” The MTO jerked in his cradle; despite the clatter of plating, it did nothing to free him.
“Identification: a poem.”
The complete absence of understanding was a hole Soundwave could have fallen into. A couple accepted that as an answer—a poem must have been another form of marching order, the only communication style they had been brought online to understand—but the others prodded him with their curiosity, audials straining to catch another blip of that strange voice.
“That wasn’t you,” one of the others said.
“Negative,” Soundwave said. “Speaker…” He stopped, remembering how the first MTO, now gazing at him with useful curiosity, had snarled the poet’s name. Had that been out of a sense of pride? A desperation to answer the question, using the only scrap of information they had? Or had it been in worship, choosing his lord’s name to be his first word to the real world? The clashing, violent thoughts did not readily bear an answer to Soundwave, but they did give him pause as he considered his response, long enough that the MTOs’ anxiety rose up once more in a wave.
“What’s it mean?” one of them asked.
“Definition subjective,” Soundwave said. He still had so much work to do. “Silence requested.”
“It’s a code.”
“Negative.”
“Then it’s gotta mean something.”
Soundwave grasped uselessly for words, wishing Ravage were there already. He was better at this. Soundwave wasn’t good at conversation, but most of the time he could get out of it by virtue of the fact that the people he ran into were either his subordinates and afraid of him, or at about equal level and jealous of his proximity to Megatron. It was so rare for him to enter a room without his reputation having already made the rounds for him, he had no basis for navigating this.
He couldn’t come up with anything, and the longer he let the silence drag out the louder the background of thoughts grew to compensate. At a loss and desperate for relief, Soundwave dove into his archives and pulled a file at random, plugging it into his speakers without even scanning the contents.
“The revolution failed because the lords were unamused. The smoke that rose from the burning corpses of their clerks Soured their palmful drinks, And the chants which rose to their balconies, Calling for their heads, Were out of tune with the afternoon symphony.
(The first chair would be tossed out at intermission, And the crowd would suck closed empty fuel lines While inside, the lords sipped in peace.)”
Even with his speakers playing at a high volume, the relative noise inside the shuttle dropped instantly. Their minds were still working, turning over each word like they could find the meaning hidden underneath, but without the fear of the unknown it was quieter and reflective.
“If you still say your knuckles ache, Lay them here, on my knee. I cannot take from you That pain, But I will map the seams of your palm. I will memorize you, Memorialize. I will chart your construction And between your seams find…”
Crunching data while listening to Megatron’s voice was second nature by now. Soundwave stood in the center of the wrecked shuttle, seeking out the identity of the MTOs, while around him they leaned and twisted in their cradles, hunting down the poems like the twinkle of an enemy across a battlefield.
34 notes
·
View notes
Photo


The Lisa Hardware
Reporting on the technical specifications of a computer toward the end of an article is unusual for BYTE, but it emphasizes that the why of Lisa is more important than the what. For part of the market, at least, the Lisa computer will change the emphasis of microcomputing from “How much RAM does it have?” to “What can it do for me?” For example, it is almost misleading to say that the Lisa comes with one megabyte of RAM, even though the fact itself is true. That doesn’t mean that the Lisa is sixteen times better than machines that have 64K bytes of RAM. Nor does it necessarily mean that the Lisa can work on much larger data files than other computers; its application programs each take 200K to 300K bytes, which significantly reduces the memory available for data. It’s more instructive to say, for example, that the Lisa with one megabyte can hold a 100-row by 50-column spreadsheet (as its advertisements state). With this in mind, let’s take a look at the Lisa.
“Lisa” stands for Local Integrated Software Architecture, but it’s really just an excuse to retain Apple’s pet name for the project. The Lisa has a 68000 microprocessor, which is a true 16-bit microcomputer that has a 16-bit data bus, a 24-bit address bus (giving access to 16 megabytes of memory), and 32-bit-wide registers (all but the 16-bit status register). The 68000 in the Lisa runs at a frequency of 5 MHz. It can have up to 1 megabyte of memory with parity and comes standard with one megabyte (1024K bytes).
The video display is a 12-inch monochrome monitor (black and white, not tinted) with a resolution of 720 by 364 pixels. The interlaced image is refreshed at 60 Hz, which eliminates the possibility of eyestrain from subliminal flickering. The video display is completely generated by internal software, so the Lisa can use multiple character sizes and fonts without restriction. It also means that Apple is not restricted to any one style of video image; the designers can radically change the behavior of the system with a new release of software.
The Apple 871 disk drives design (called “twiggy drives” inside the company) are significantly different from conventional floppy-disk drives. Each one uses a 6504 microprocessor as a “smart” interface between it and the Lisa. The drives use special high-density, double-sided floppy disks that have two oval cutouts in the jacket (see photo below). These are essential because the two disk heads, in addition to being on opposite sides of the flat magnetic media, are not pointed at each other with the magnetic media between them, as is the case in all other double-sided floppy-disk drives. Instead, a pad presses the rotating magnetic media to the disk head on the opposite side of the media as is conventionally done with single-headed floppy disks.
Each formatted disk holds 860K bytes of information at a density of 62.5 tracks per inch; together the two drives (standard on the Lisa) hold 1.72 megabytes of data. Each drive also contains a mechanism that releases the disk for removal under program control, which prevents the user from removing a floppy disk prematurely. As with other Apple products, the floppy disks rotate only when the drives are reading or writing data, thus extending the lives of both the drives and the medium.
Apple has done several things to achieve its unusually high data density. The designers used an encoding scheme that keeps a constant data density of 10,000 bits per linear inch; this allows the outer floppy-disk tracks, which have a larger circumference, to store more data than the tracks nearest the center of the disk. In addition, the disk-access system software can move the disk heads in fractions of a track width to search for and find the middle of the track. That’s an important feature when you’re reading disks with small variations in track width.
In addition, the Lisa comes with one Profile (Apple’s 5-1/4-inch Winchester-type hard disk) to the Lisa through its parallel port. It adds 5 megabytes of magnetic storage to the Lisa system, and speeds up the overall operation of the system. Additional Profiles can be added via interface cards.
The Lisa computer is never really turned off. It stores “system preferences” (things like speaker volume and video contrast) and system-configuration information inside the computer. Even when it is turned “off,” it draws enough power to keep the clock/calendar and CMOS memory containing the above information working. When it’s unplugged (for example, when it’s being moved to another location), internal batteries preserve the clock/calendar status and CMOS memory for up to 20 hours.
The Lisa includes two programmable serial ports and one parallel port as well as three expansion-board slots, each of which connects directly to the system bus and has direct memory access (DMA) capabilities. Because none of these slots is filled in any “basic” configuration of the Lisa, they are available for future expansion (unlike the IBM Personal Computer’s five slots, most or all of which are used for much-needed video-display and memory cards). Other features include a built-in speaker and a real-time clock (which can be programmed to execute tasks or turn the computer itself on or off at a given time), a microprocessor-controlled detachable Selectric-style keyboard, and a mouse.
I must thank Apple for including something I’ve wanted to see for a long time: unique serial numbers encoded into memory. The Lisa has two of these: an actual serial number An interesting aspect of the Lisa is that it abandons hardware graphics chips like the NEC 7220 for system software that requires the 68000 microprocessor to generate and maintain the video image. At first, I questioned the wisdom of this decision because it makes the 68000 assume a heavy computational burden that could be transferred from software to hardware. But according to the designers, the use of a dedicated hardware graphics chip would itself limit and slow down the system (for a discussion of this, see the interview on page 90). In particular, the 68000 clock was set at 5 MHz instead of the usual 8 MHz to give the hardware just enough time to access the 32K bytes of screen memory during the machine cycles in which the 68000 is not using the address lines. This gives the Lisa access to the video memory that is transparent to the 68000 (hardware graphics chips severely limit access to the video memory) and results in a static-free image. (Much of the static or “hashing” in graphic video images results from the system accessing the video memory while the circuitry is using it to generate the video image.)
Apple will also be offering the Apple Dot Matrix Printer and the Apple Letter Quality Printer. Apple’s engineers tested many existing printers, chose two (from C. Itoh and Qume, respectively) that best met their needs, then had the companies produce modified versions with Apple-specified hardware and software changes. Apple needed such exacting print quality because the Lisa software is very demanding of both printers. For example, both printers will reproduce almost exactly both the text and graphics that can be displayed on the Lisa screen. In addition, Apple has created special print wheels for its Letter Quality Printer so that you can print normal, italic, underlined, and bold characters without changing print wheels (quite a nice move who’s going to change print wheels several times a page just to get true italics?). The amazing thing about the Apple Dot Matrix Printer is that Apple plans to sell it for around $700 (the Letter Quality Printer will sell for about $2100). Unfortunately for Apple II and III owners, these printers’ tricks are done entirely in software on the Lisa and won’t transfer to other Apple computers.
Daily inspiration. Discover more photos at http://justforbooks.tumblr.com
10 notes
·
View notes
Text
Youtube Video Statistics For Movie Irani Hayhat

The Athenians have been offended along with her presence within the war in opposition to them, offered an incentive of ten thousand drachmas for her arrest. As claimed by Plutarch, on the pages of his biography of Themistocles, Artemisia added to her esteem with Xerxes when Ariamenes, his brother and considered one of his admirals, was killed within the battle.
The Persian king, having solely seen that Artemisia sunk a ship while surrounded by Athenians, was also duped by her daring transfer and later praised her for her bravery.
After the disastrous defeat of the Persians at Salamis, Xerxes again called upon his commanders to advise him. This time, nevertheless, he singled out Artemisia for consultation as a result of she alone had given him accurate data and sage recommendation in her earlier counsel.
These encompass the normal maltreatment of widows, political corruption and lots of the troubles linked to metropolis lifestyle. All these matters appeal to a wide African viewers and possess assisted to bring about African co-productions.
The Nollywood enterprise – which came to life in the course of the early Nineties – is usually noticed as being a all-natural inheritor on the Nigerian TV collection which skilled now generated around 14,000 element motion pictures throughout the previous ten years.
These on-line video-motion pictures of your early yrs have now turn into complete characteristic films, and an integral Section of nicely-identified way of life in Nigeria. Neighborhood audiences get pleasure from these homegrown productions relating to way of life within the area.
The Calyndian ship was misplaced with all arms, convincing the pursuing Athenians that she was an ally of their fleet. Apparently, Aminias of Pallene, the final who pursued Artemisia’s ship, wouldn't have stopped his pursuit had he identified that Artemisia herself was on that ship.
Here are more than 6,600 visitors and the pages are considered up to 6,600 occasions for daily. Based on current visitor traffic, you will know that the promoting income on the web site will be able to reach $39.6 USD per day.
The servers of the web site are being hosted in Netherlands and United States. Serial Ghorbaghe Part 1 , directed by Hooman Sidi and produced by Ali Asadzadeh, began filming in 1398 and is scheduled to be screened on the Home Theater Network in December 1399. Ghoorbaghe 1 (سریال قورباغه قسمت اول) is a Iranian Serial that may be very in style.
People have been capable of freely depart their houses, retail shops, eating places, cafes and bars may reopen and groups of as much as 10 could begin gathering.
wonderful health & public well being employees & above all else the Australian individuals,” Health Minister Greg Hunt stated on his Twitter account. danlode all half Health officers say more restrictions may be eased within the coming days. The state of Victoria — epicentre of Australia’s second wave — recorded zero instances for the second day in a row after a 112-day lockdown. Another way to stop getting this web page sooner or later is to make use of Privacy Pass.
ghorbaghe serial It also comes although as Algeria’s president has been flown to Germany for medical care. serial ghorbaghe But opponents say it falls short of fundamental reform. ghorbaghe sequence Victoria and its largest metropolis Melbourne began to reopen earlier this week after recording no new neighborhood-transmitted cases since June.
Thessalus, son of Hippocrates, described Artemisia in a speech, painting her as a cowardly pirate. Where he obtained his data is unknown but in his speech, Artemisia leads a fleet of ships to the Isle of Cos to hunt down and slaughter the Coans, however the gods intervene. After Artemisia’s ships are destroyed by lightning and she or he experiences visions of nice heroes, she flees Cos, her goal unfulfilled.
According to Polyaenus, Artemisia carried two different requirements on her vessels, and would fly the Persian standard whereas chasing Greeks, but would fly a Greek standard when she was being pursued. The solely account we have of Artemisia’s dying is itself quite doubtful.
According to the story, Artemisia fell in love with a person, but he rejects her. It appears difficult to imagine that a lady of such formidable character, a ruler of great renown in her own right and the leader of soldiers into battle, would commit such a questionable act. serial ghorbaghe
Exploring early literature, we discover it replete with myths of ladies who commit suicide because of an unrequited love. It seems extra doubtless that the writer adapted Artemisia’s story to suit the literary traditions of the time.
It is thought that her grandson, named Lygdamis after her father, dominated Halicarnassus after her, and was indeed the very reason that Herodotus needed to flee town, visiting the island of Samos earlier than finally settling in Athens.
Xerxes introduced Artemisia with two attainable courses of motion, asking her which she would recommend. Xerxes would either information his troops in an assault on the Peloponnese himself or personally withdraw from Greece, leaving his common, Mardonius, in cost (Herodotus eight.102).
Once again Artemisia had given the reasoning behind her advice, which appeared to Xerxes to be sound. Upon deciding to take Artemisia’s recommendation, Xerxes additional requested that she accompany his illegitimate children to Ephesus. Though this is the last we find of Artemisia within the accounts of Herodotus, she does appear in other ancient sources.
Ghoorbaghe is one of the hottest and engaging Iranian serials that has a social and dramatic theme. In this sequence; Sahar Dolatshahi, Saber Abar, Navid Mohammadzadeh, Hooman Sidi, Anahita Afshar, Mehran Ghafourian, Navid Pourfaraj, Mohammad Amin Sharabaf, Ehsan Mansouri, Nima Mazaheri and Fereshteh Hosseini have carried out as artists.
He pledged an finish to what he calls the practices of the “gang” of politicians and businessmen in President Bouteflika’s inside circle. Mr Tebboune’s election marketing campaign noticed him vow to “lay the foundations of a new Algeria”.
President Tebboune, 74, came to energy last 12 months in a controversial election that followed the departure of Mr Bouteflika, who resigned in the face of large in style protests towards his bid for a fifth term in office.
The explanation for his sick well being has not been disclosed, but President Abdelmadjid Tebboune had self-isolated and spent time in a navy hospital in Algiers after a number of his aides and colleagues contracted coronavirus.
2 notes
·
View notes
Text
MySQL NDB Cluster Backup & Restore In An Easy Way
In this post, we will see, how easily user can take NDB Cluster backup and then restore it. NDB cluster supports online backups, which are taken while transactions are modifying the data being backed up. In NDB Cluster, each backup captures all of the table content stored in the cluster. User can take backup in the following states: When the cluster is live and fully operational When the cluster is live, but in a degraded state: Some data nodes are down Some data nodes are restarting During read and write transactions Users can restore backups in the following cluster environments: Restore to the same physical cluster Restore into a different physical cluster Restore into a different configuration cluster i.e. backup taken from a 4 nodes cluster and restore into 8 data nodes cluster Restore into a different cluster version Backups can be restored flexibly: Restore can be run locally or remotely w.r.t the data nodes Restore can be run in parallel across data nodes Can restore a partial set of the tables captured in the backup Use cases of Backup & Restore: Disaster recovery - setting up a cluster from scratch Setup NDB Cluster asynchronous replication Recovery from user/DBA accidents like dropping of a table/database/schema changes etc During NDB Cluster software upgrade Limitations: Schemas and table data for tables stored using the NDB Cluster engine are backed up Views, stored procedure, triggers and tables/schemas from other storage engine like Innodb are not backed up. Users need to use other MySQL backup tools like mysqldump/mysqlpump etc to capture these Support for only full backup. No incremental or partial backup supported. NDB Cluster Backup & Restore concept in brief: In NDB Cluster, tables are horizontally partitioned into a set of partitions, which are then distributed across the data nodes in the cluster. The data nodes are logically grouped into nodegroups. All data nodes in a nodegroup (up to four) contain the same sets of partitions, kept in sync at all times. Different nodegroups contain different sets of partitions. At any time, each partition is logically owned by just one node in one nodegroup, which is responsible for including it in a backup.When a backup starts, each data node scans the set of table partitions it owns, writing their records to its local disk. At the same time, a log of ongoing changes is also recorded. The scanning and logging are synchronised so that the backup is a snapshot at a single point in time. Data is distributed across all the data nodes, and the backup occurs in parallel across all nodes, so that all data in the cluster is captured. At the end of a backup, each data node has recorded a set of files (*.data, *.ctl, *.log), each containing a subset of cluster data.During restore, each set of files will be restored [in parallel] to bring the cluster to the snapshot state. The CTL file is used to restore the schema, the DATA file is used to restore most of the data, and the LOG file is used to ensure snapshot consistency.Let’s look at NDB Cluster backup and restore feature through an example:To demonstrate this feature, let’s create a NDB Cluster with below environment.NDB Cluster 8.0.22 version 2 Management servers 4 Data nodes servers 2 Mysqld servers 6 API nodes NoOfReplicas = 2 If you are wondering how to setup a NDB Cluster, then please look into my previous blog here. Step 1:Before we start the cluster, let’s modify the cluster config file (config.ini) for backup. When backup starts, it create 3 files (BACKUP-backupid.nodeid.Data, BACKUP-backupid.nodeid.ctl, BACKUP-backupid.nodeid.log) under a directory named BACKUP. By default, this directory BACKUP created under each data node data directory. It is advisable to create this BACKUP directory outside the data directory. This can be done by adding a config variable ‘BackupDataDir’ to cluster configuration file i.e. config.iniIn the below example, I have assigned a path to ‘BackupDataDir‘ in config.ini:BackupDataDir=/export/home/saroj/mysql-tree/8.0.22/ndbd/node1/data4Step 2: Let’s look at the cluster from the management client (bin/ndb_mgm): Step 3: As cluster is up and running so let’s create a database, a table and do some transactions on it. Let’s insert rows into table ‘t1’ either thru sql or thru any tools. Let’s continue the rows insertion thru sql to have a significant amount of datas in the cluster. Let’s check the rows count from table ‘t1’. From the below image, we can see that table 't1' has ‘396120’ rows in it. Step 4: Now issue a backup command from the management client (bin/ndb_mgm) while some transactions on the table ‘t1’ was going on. We will delete rows from table ‘t1’ and issue a backup command in parallel. While delete ops is going on, issue a backup command from the management client: Let’s check the new row count from table ‘t1’ after all the delete ops finished. From the below image, we can see that now the table ‘t1’ has ‘306120’ rows. Let’s look at the files backup created. As we have assigned a path to backup files so let’s discuss about these files in brief. From the above image, we can see that, for each backup, one backup directory is created (BACKUP-backupid) and under each backup directory, 3 files are created. These are:BACKUP-backupid-0.node_id.Data (BACKUP-1-0.1.Data):The above file contains most of the data stored in the table fragments owned by this node. In the above example, 1 is the backupid, 0 is a hardcoded value for future use. 1 is node_id of the data node 1. BACKUP-backupid.node_id.ctl (BACKUP-1.1.ctl): The above file contains table meta data i.e. table definitions, index definitions.BACKUP-backupid.node_id.log (BACKUP-1.1.log):This file contains all the row changes that happened to the tables while the backup was in progress. These logs will execute during restore either as roll forward or roll back depends on whether the backup is snapshot start or snapshot end. Note:User can restore from anywhere i.e. doesn’t have to be from any particular data node. ndb_restore is an NDB API client program, so can run anywhere that can access the cluster. Step 5: Upon successfully completion of a backup, the output will looks like below: From the above image, Node 1 is the master node who initiate the backup, node 254 is the management node on which the START BACKUP command was issued, and Backup 1 is the 1st backup taken. #LogRecords ‘30000’ indicate that while backup was in progress some transaction was also running on the same table. #Records shows the number of records captured across the cluster. User can see the backup status also from the “cluster log” as shown below:2021-01-12 15:00:04 [MgmtSrvr] INFO -- Node 1: Backup 1 started from node 2542021-01-12 15:01:18 [MgmtSrvr] INFO -- Node 1: Backup 1 started from node 254 completed. StartGCP: 818 StopGCP: 855 #Records: 306967 #LogRecords: 30000 Data: 5950841732 bytes Log: 720032 bytesSo this concludes our NDB Cluster backup procedure. Step 6:We will now try to restore the data from the backup taken above. Let’s shutdown the cluster, cleanup all the files except the backup files and then start the cluster with initial (with no data).Let’s restore the backup to a different cluster. From the below image, we can see that data node Id’s are different from the cluster where backup was taken. Now let’s see if our database ‘test1’ is exist in the cluster or not after initial start. From the above image, we can see that, database ‘test1’ is not present. Now let’s start our restore process from the backup image #1 (BACKUP-1). The NDB restore works in this flow: It first restore the meta data from the *.ctl file so that all the tables/indexes can be recreated in the database. Then it restore the data files (*.Data) i.e. inserts all the records into the tables in the database. At the end, it executes all the transaction logs (*.log) rollback or roll forward to make the database consistent. Since restore will fail while restoring unique and foreign key constraints that are taken from the backup image so user must disable the index at the beginning and once restore is finished, again user need to rebuild the index. Step 7:Let’s start the restoration of meta data.Meta data restore, disable index and data restore can execute at one go, or can be done in serial. This restore command can be issued from any data node or can be from a non-data node as well.In this example, I am issuing meta data restore and disable index from Data Node 1 only for once. Upon successful completion, I will issue the data restore.Data Node 1: shell> bin/ndb_restore -n node_id -b backup_id -m --disable-indexes --ndb-connectstring=cluster-test01:1186,cluster-test02:1186 –backup_path=/path/to/backup directory -n: node id of the data node from where backup was taken. Do not confuse with the data node id of the new cluster.-b: backup id (we have taken backup id as ‘1’)-m: meta data restoration (recreate table/indexes)--disable-indexes: disable restoration of indexes during restore of data--ndb-connectstring (-c): Connection to the management nodes of the cluster.--backup_path: path to the backup directory where backup files exist. The results of above meta restore from data node 1 is shown below: Let’s start the data restore on the Data Node 1. Data Node 1:shell> bin/ndb_restore -n node_id -b backup_id -r --ndb-connectstring=cluster-test01:1186,cluster-test02:1186 –backup_path=/path/to/backup directory Below, I am trying to capture the logs from the data restore run results as it started and then at the end. From the above image, we can see that restore went successful. Restore skips restoration of system table data. System tables referred to here are tables used internally by NDB Cluster. Thus these tables should not be overwritten by the data from a backup. Backup data is restored in fragments, so whenever a fragment is found, ndb_restore checks if it belongs to a system table. If it does belong to a system table, ndb_restore decides to skip restoring it and prints a 'Skipping fragment' log message.Let’s finish all the remaining data restore from the other data nodes. These data restore can be run in parallel to minimise the restore time. Here, we don’t have to pass -m, --disable-indexes again to restore command as we need to do it only once. With the first restore completion, it has already created tables, indexes etc so no need to recreate it again and will also fail. Once all the data are restored into the table(s), we will enable the indexes and constraints again using the –rebuild-indexes option. Note that rebuilding the indexes and constraints like this ensures that they are fully consistent when the restore completes.Data Node 2:shell> bin/ndb_restore -n node_id -b backup_id -r --ndb-connectstring=cluster-test01:1186,cluster-test02:1186 –backup_path=/path/to/backup directoryData Node 3:shell> bin/ndb_restore -n node_id -b backup_id -r --ndb-connectstring=cluster-test01:1186,cluster-test02:1186 –backup_path=/path/to/backup directoryData Node 4:shell> bin/ndb_restore -n node_id -b backup_id -r --ndb-connectstring=cluster-test01:1186,cluster-test02:1186 –backup_path=/path/to/backup directory Ndb restore (ndb_restore) is an API, it needs API slots to connect to cluster. Since we have initiated 3 ndb_restore programme in parallel from Data node ID 4, 5 and 6 so we can see from the below image that ndb_restore took API ID: 47, 48 and 49. Let’s see the results from the remaining data nodes. Since all the ndb_restore API finished successfully, we can see that the API ID that it had taken to connect the cluster has been released. The last step is to rebuild the index. This can also done from any data nodes or from any non-data nodes but only once.Data Node 1:shell> bin/ndb_restore -n node_id -b backup_id --rebuild-indexes --ndb-connectstring=cluster-test01:1186,cluster-test02:1186 –backup_path=/path/to/backup directory--rebuild-indexes: It enables rebuilding of ordered indexes and foreign key constraints. Step 8:So we have finished our restoration steps. Let’s check the database, table, rows count in table etc .. So database ‘test1’ is already created. Now we can see that table ‘t1’ has been created and the row count#306120 which is also matching with our backup image (look at Step# 4).So this concludes our NDB Cluster backup and restore feature. There are many more options user can pass to both backup (START BACKUP) and restore (ndb_restore) programme based on the requirements. In the above example, I have selected the basic minimum options user might need for backup and restore. For more information on these options, please refer to NDB Cluster reference manual here. https://clustertesting.blogspot.com/2021/01/mysql-ndb-cluster-backup-restore-in.html
1 note
·
View note
Text
Molly Hooper Appreciation Week - Day Seven
Day Seven – Free For All
This is part three of a series of Khanolly fics. You may want to read the first two parts before this one. (”Descent Into Darkness” and “From Darkness”, both on Ao3) Or not. It’s up to you.
Embrace the Darkness
“. . . by the time Kirk and Spock have been debriefed and the Federation has heard all about Admiral Marcus and convened a committee to decide whether or not to pursue you, you’ll be long gone. If you destroy them now, every armed ship in the area will be sent after you in retaliation within a matter of hours.”
Molly took another step closer to the Captain’s chair of the Vengeance and tried to reason with the imposing man sitting in it. “You’ll need time to revive your crew. This could buy you some of that time.”
“And you, Molly? What would you have me do with you?” His voice was warm velvet covered in steel.
She took a deep breath and sealed her fate. “I—I . . . You wanted my help to wake your people. I’m here. What do you need?”
He tapped a finger against the arm of the chair. “Khan to the crew of the Enterprise. As promised, I have returned your crew—”
இڿڰۣ-ڰۣ—
The cargo hold was filled with torpedo tubes.
Molly bit the inside of her cheek as she stepped up to the first one. If Spock had attempted to trick Khan, had somehow switched Khan’s crew for live torpedoes, and she accidently armed it . . .
She shuddered and wrapped her arms around her middle for comfort.
Khan knelt next to the tube and compared the serial number etched on the side to the list on his data pad.
“This might be easier if we had help. Do any of them have medical training?” She contemplated the vast number of people that would need to be eased out of cryostasis, each one needing to be carefully monored until they were out of danger. Even if Khan could go without rest for extended periods, she would need to eat and sleep or she’d be utterly useless. One mistake could mean the life of one of the seventy-two men and women of Khan’s crew.
“We need to find Joachim. He’ll be the first.” Khan stood up and moved to the next tube to examine the serial number.
Molly started working her way down the next row with her own data pad. “Is he a doctor?”
“My second-in-command,” he corrected. Before Molly could protest, Khan explained his decision, “Someone will need to be on the bridge if we’re going to be otherwise occupied in sickbay.”
She continued to look uncertain. Khan bit back whatever he’d been about to say and forced his expression into something softer in an effort to reassure her. “My security chief has practical experience as a nurse, and her mate is our medical officer. We can awaken them after Joachim.”
இڿڰۣ-ڰۣ—
Joachim was pale with dark hair, shorter than Khan but imposing nevertheless. He was constantly watching, like a predator waiting for his prey to make one fatal mistake. Something about him made Molly uneasy. She especially didn’t like the way he looked at Khan when the other man’s attention was focused elsewhere.
The medical officer was called Watson. It took Molly a few days to warm to him. Her initial impression was of a gruff man with the sort of temper that was quick to explode in frustration and equally quick to die down, leaving him contrite. The second time he’d snapped at her, Molly had snapped right back and banished him from sickbay until he apologized. Khan had simply shaken his head when Watson looked to him for support, and reminded Watson that Molly was the chief medical officer on board the ship, therefore the sickbay was under her authority.
“Within reason,” he’d added just loud enough for her to hear.
Rosamund was Watson’s mate, and she answered only to Khan on matters of ship security (bypassing Joachim, which was something that reassured Molly considerably). Molly liked the blonde woman. She was no nonsense while she was working, but she often had a smile and a laugh to offer to Molly when she came to visit her mate in sickbay.
Khan identified the most vital members of his crew and he, Molly, and Watson steadily moved through the list over the next two weeks. She insisted they took their time, never more than half a dozen crew members recovering at a time to minimize the risks. She knew the pace frustrated Khan but he had to concede that the safety of his crew was paramount.
Finally, eighteen days after the confrontation with the Enterprise, and fifteen days since they’d left Federation space, the last of Khan’s crew was released from sickbay and Molly could finally relax.
She’d been sleeping on whatever med bed was open at the time, only leaving sickbay to shower and eat when her body demanded it. She was looking forward to hunting down an empty room in the crew quarters and sleep for the next three days straight.
Once she waved Watson and Rosamund out the door with the promise that she’d join them in the mess for a meal as soon as she’d finished putting the last of the equipment away, Molly curled up on one of the beds and told herself she was only going to rest her eyes for just a moment.
இڿڰۣ-ڰۣ—
Molly had no idea how long she slept. The room was completely dark when she opened her eyes and it took her several seconds to realize that wasn’t right. She sat up in a panic, her mind screaming that even during the night cycle sickbay was gently lit from various scanners and readouts that constantly monitored her patients.
Pitch black meant a system failure.
System failure could mean death.
Before she could roll out of the bed a hand grasped her wrist and stilled her.
“Computer, half-lights,” the deep voice of Khan rolled out of the darkness. It was huskier than she was used to, as if she’d pulled him out of his sleep with her movements.
A warm, soft glow came from recessed lighting around the room, illuminating the unfamiliar surroundings and the man laying at her side on the bed that most definitely was not the one she’d fallen asleep on in sickbay.
Khan continued to hold her wrist, although his hold was gentle and she knew she’d be able to pull free if she wanted to.
“Where am I?” Molly asked.
“You are in the Captain’s Quarter’s,” the Computer answered.
Khan’s lips curled upward in amusement. “Computer, that will be all. I can take it from here.”
“Acknowledged, Captain.”
Molly let her gaze take in the room, it was nearly as large as the flat she’d called home for the last several years. Admiral Marcus had clearly spared no expense when he’d chosen the furnishings for what would have been his quarters if he’d maintained command of the ship.
“Nice.” She gestured with her free hand to indicate the room at large.
“It serves its purpose,” Khan acknowledged.
She might have continued to shyly dance around the important question if her stomach hadn’t chosen that moment to remind her that she’d probably missed dinner. Frankly, she was hungry and a Hungry Molly was an Impatient, Blunt Molly. “So how did I end up in it?”
He laughed. “Rosamund became concerned when you didn’t meet them as promised. You were so exhausted you barely stirred when I tried to wake you and I thought it best to let you continue to sleep.”
“That doesn’t explain how I ended up in this bed.” She left the ‘with you’ unspoken.
“Surely you didn’t expect me to leave you in sickbay?” His hand drifted from her wrist up her arm to her shoulder, then he applied the barest hint of pressure to urge her to lie down once more. “The Computer informed me that you haven’t been assigned quarters of your own. This seemed like the logical choice. Wouldn’t you agree?”
“I-I . . . Yes?” It definitely came out as more of a question than she would have liked.
He slid his arm around her waist as he leaned over her, his body hot along her side. They were both fully clothed, but Molly felt her heart race in excitement as if they were fully naked and pressed against each other.
“You’re welcome to stay here until you’re fully recovered.” He moved impossibly closer, dipping his head until his lips brushed against her ear. “In fact, you can stay as long as you like, Molly. My Molly.”
41 notes
·
View notes
Text
WCF Data Services with Windows Phone - bandwidth requirements measured
In connection with testing Synchronization between a SQL Server Compact database on Windows Phone 8 and a SQL Server database (via a WCF Data Services service hosted in IIS), I have done some interesting observations regarding bandwidth requirements, that I would like to share. I am testing against the Chinook sample database, by downloading the entire PlaylistTrack table (8715 rows) to the device via my WCF Data Services service. On the server side, I am using the latest release version of the WCF Data Services server components, version 5.3.0. Version 5.1 or later includes the newer lightweight JSON format (just to compare I am also including sizes for the previous JSON format) On the server side, I have created a ASP.NET Web Application with a WCF Data Service, that exposes the Chinook database on my SQL Server via an Entity Framework DbContext. The power of WCF Data Services is that this requires basically no code to configure. I have configured my service like this: public class SyncService : DataService { // This method is called only once to initialize service-wide policies. public static void InitializeService(DataServiceConfiguration config) { config.UseVerboseErrors = true; //config.SetEntitySetAccessRule("TrackPurchases", EntitySetRights.WriteAppend); config.SetEntitySetAccessRule("*", EntitySetRights.AllRead); config.DataServiceBehavior.MaxProtocolVersion = DataServiceProtocolVersion.V3; } } In order to access the IIS Express hosted service from my Windows Phone 8 emulator, I followed the instructions here: http://msdn.microsoft.com/en-us/library/windowsphone/develop/jj684580(v=vs.105).aspx To measure the size of the payload, I am using Fiddler2, by following the instructions here: http://blogs.msdn.com/b/fiddler/archive/2010/10/15/fiddler-and-the-windows-phone-emulator.aspx The WCF Data Services team also supply a WCF Data Services client for Windows Phone, that can take advantage of a Service Reference, but this client has some severe limitations, that affects bandwidth consumption in a bad way: It only supports the XML based ATOM format, but you can enable compression, as described here: http://blogs.msdn.com/b/astoriateam/archive/2011/10/04/odata-compression-in-windows-phone-7-5-mango.aspx On the client side, I am simply using HttpWebRequest to call the REST url, and including support for gzip via the ICSharpCode.SharpZipLib library (for example http://nuget.org/packages/SharpZipLib-WP7/ ) Here is the implementation of the WebClient: static public async Task GetData(Uri uri, bool useJson = true, bool version3 = true, bool compress = true) { //uri = new Uri(uri.AbsoluteUri + "&format=json"); HttpWebRequest client = WebRequest.CreateHttp(uri); { if (compress) client.Headers = "deflate, gzip"; if (version3) { client.Headers = "3.0"; } else { client.Headers = "2.0"; } if (useJson) client.Accept = "application/json"; using (WebResponse response = await client.GetResponseAsync()) { string result = await response.GetResponseText(); DataContractJsonSerializer serializer = new DataContractJsonSerializer(typeof(T)); T resultType; using (MemoryStream stream = new MemoryStream(Encoding.Unicode.GetBytes(result))) { resultType = (T)serializer.ReadObject(stream); } return resultType; } } } public static async Task GetResponseText(this WebResponse response) { using ( Stream stream = response.IsCompressed() ? new GZipInputStream(response.GetResponseStream()) : response.GetResponseStream()) { using (var reader = new StreamReader(stream)) { return await reader.ReadToEndAsync(); } } } public static bool IsCompressed(this WebResponse response) { return Regex.IsMatch((response.Headers ?? "") .ToLower(), "(gzip|deflate)"); } (I am using Microsoft.Threading.Tasks.Extensions.dll to implement GetResponseAsync) I am using DataContext classes generated by my SQL Server Compact Toolbox for deserialization, with a small addition - I have added this attribute to all EntitySet and EntityRef properties (this will be included in the next Toolbox release): I am calling the following URL: http://:2065/SyncService.svc/PlaylistTracks This is my test code: //ATOM-XML await WebClient.GetData(uri, false, false, false); //Verbose json await WebClient.GetData(uri, true, false, false); //Verbose json + gzip await WebClient.GetData(uri, true, false, true); //Plain json await WebClient.GetData(uri, true, true, false); //Plain json + gzip await WebClient.GetData(uri, true, true, true); public class PlaylistTrackRoot { public List value { get; set; } } And finally the unbelievable numbers for the download of the entire PlaylistTrack table with 8715 rows (remember, that ATOM is the default WCF Data Services client format) Payload type Body size (bytes) Body size (MB) ATOM-XML 9,322,665 (100 % – default DS client implementation) 8.89 MB JSON (verbose) 5,016,977 (54 %) 4.78 MB JSON (verbose) + gzip 328,410 (3,5 %) 0.31 MB JSON (plain) 790,845 (8,5 %) 0.75 MB JSON (plain) + gzip 43,023 (0,5 %) 0.04 MB So before you decide to use the WCF Data Services Windows Phone client, beware that the only format currently available is ATOM-XML. With the 5.1.0 or later desktop client, however, you can use the of the DataServiceContext to request JSON - ctx.Format.UseJson() – the default is still ATOM-XML.
1 note
·
View note
Text
Project #2 Documentation: Augmented Recycling Bin
For this project, Jeanne and I decided to work on an extension of her last project, which was the light-up recycling bin. We decided to utilize serial communication through a p5 sketch that included audio and visual elements.
We definitely shifted our idea from the temperature sensor idea - but not before some suffering first!
Our first issue began when bringing the temperature sensor and serial communication together - we kept getting an error regarding the fact that Serial.write(_) could not take a double value, and so we messed around a lot with the code...


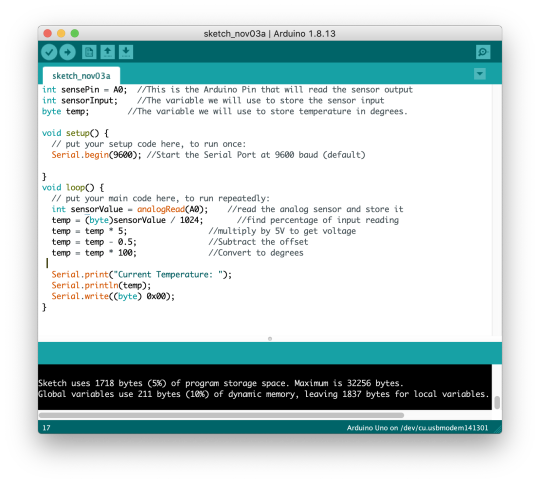
And once we got it working by just using Serial.print() because it can take multiple different data types, we started to get readings of 0 on our sensor
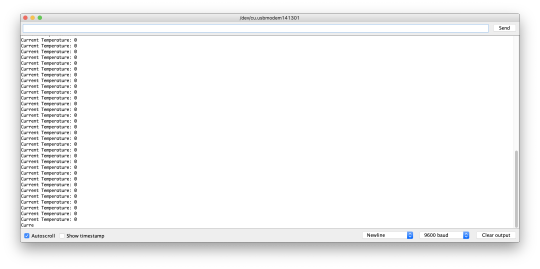
Needless to say, we were angry! After a bit of re-uploading and messing around with the code, we were able to manipulate the circle drawing from the class lab... kind of? It was super jumpy *added above*
We decided our best bet to actually get something done would be to change sensors - though Jeanne had used the break beam sensor for her last project, I was excited to try it out for the first time.

What we have so far is that we manipulated the circle/potentiometer code so that when something passes through the sensor, it the circle appears and a ding sound occurs. Now that we have this base, we will spend the next couple of days playing around with the kinds of things we can generate through this interaction to make it even more engaging!

Pretend these are break-beam sensors, please :)
**Videos posted below!
Phase 2:
After making sure we had the serial communication kind of working for the break-beam sensors, I got down to business with the p5 code. We decided it would be the best move to show facts about recycling when the sensor goes off and the sound is triggered. These are what the messages looked like:



The code can be found here:
https://editor.p5js.org/sferrera89/sketches/EbroC03Db
What this code is doing is going into a text file, parsing out the lines, and returning a random line with a random background. Pretty basic, but this took so freaking long it had me like this

And the Arduino code looked as follows:
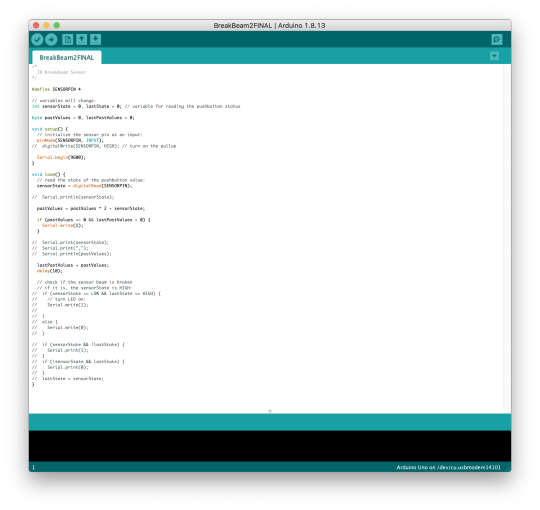
And you’re probably like “whaaat” and you’re right... there’s some funky stuff happening here! So basically, if you can tell in the videos below, the green circle was looking JUMPY. It was identifying that there was something in the middle, but it was acting crazy. So, I sought the assistance of GA Jason Gao, my night in shining armor. He smoothed out our input with the code above and explained it to me very thoroughly, which I will now butcher: his aim was to have the code detect when there’s 4 zeros in a row because the serial monitor was giving 2-3 zeros and ones when something was in the middle - something we didn’t notice when beginning to work with it because we assumed it would be sensing normally. The first part of the code was storing the last 8 digits, but we only need the last 4 for a bit. So, Jason did a funky thing with byte and storing the numbers in the loop in an array and then the code started working!
In terms of the p5 code, the issue was coming from the fact that we put everything in the draw() loop instead of the serialEvent() function! DUH! I felt like an idiot but then remembered that Jason rocks so then I felt amazing again. The final version is above! You cannot see the text at all but it is there. #Recycle!!
We faced challenges basically every step of the way for this - the finicky nature of the serialcontrol platform, getting caught in draw loops and having the p5 web editor crash, and the seemingly endless struggle of not knowing which part of the project was causing problems. In terms of happy moments, getting to different milestones definitely made it worth it. Getting that first interaction successful was a great feeling, as well as getting some help from Jason and knowing that there was a light at the end of the tunnel.
If we had more time or if we were to work on an extension of this project, I think it would be worth figuring out how to implement this as a product and what the extra machinations would look like. Someone mentioned in class what it would be like if a janitor had to empty the can or what would happen when the bin got full - thinking about these cases makes me wonder if there are certain elements we can add to the code if the sensor detects a break for more than 5 seconds it will stop making the noise. Other than that, I think we would mostly refine the code, refine the way in which the sensors attach to the bin, and the facts about recycling themselves. This was an overall fun project to work on and I’m feeling alright about the way it turned out.
0 notes
Text
Autodata Activation Code

Copy Answer Code to Ad instal Klik Activate Start Autodata from Desktop Code: There are 280 completely new models included on this update, covering a combined total of over 5000 data sections between them. New model ranges include: Audi allroad (2006-), TT (2006-), Q7 Chevrolet Aveo, Epica, Captiva Citroen C5 III, C6 Dodge Caliber Fiat 500, Sedici. Get an activation code. To request an activation code, use the form below. An activation code is only required if you have no internet access and you have a stand-alone perpetual or education license. If you do have internet access, follow the instructions for signing in or entering a serial number. Note: You can only get activation codes for supported versions of Autodesk software. Autodata 3.45 download software Autodata 3.45 crack software Autodata 3.45 activation. It is very useful if dongle emulator can. V48.88 SBB Pro2 Key Programmer. Eobdtool.com offer Autodata 3.45 installed on HDD ready to use for sale, NO need installed and activation, just plug HDD into laptop for use.

How to lnstalled Activate Autodata 3.45 Autodata 3.45 will be last version autodata, break autodata 3.45 is usually update edition and even more full database than Autodata 3.38. Right here eobdtool.com offer you Autodata 3.45 crack edition free download hyperlink and installation guideline for customers. The must be make use of after activation, so pls offer us your hardware Identity after you installed the Autodata 3.45. Eobdtool.com Have Alldata 10.53 popular sale right now: Autodata 3.45 Free of charge Download Hyperlink: Pls kindly take note: Autodata 3.45 want activate after instaIled, 39usd/period for activation. Eobdtool.com offer Autodata 3.45 set up on HDD ready to make use of for selling, NO need set up and activation, just plug HDD into laptop computer for make use of. Check right here to order: What need get ready before installed Autodata 3.45? Program necessity: home windows 7 32bit or 64bit 2.
The Intro product is only available to garages that haven’t had an Autodata subscription or trial in the past 6 months. If you have had a subscription in this time, contact us and we will be happy to set you up with a standard subscription. If you have any further questions, please contact us using the link. Bazis Salon, Backup key, Send request. Full download autodata 3. Recover My Files 3.98 Serial Download. 24 crack dongle from search results.autodata 3.24 crack dongle hosted on extabit, rapidgator, rapidshare, lumfile, netload, uploaded. Autodata 3.45 download software Autodata 3.45 crack software Autodata 3.45 activation Guide Autodata 3.
Autodata 2.16 Activation Code
Autodata 2006 Activation Code
Autodata 3.45 Free Download and Installation Guide. December 14, 2016. How to Installed & Activate Autodata 3.45. We could help get your activation code. 201 rows Autodata Registration Code Serial Numbers. Convert Autodata.
Mcafee Activation Code
Download Autodata 3.45 from over download hyperlink 3. Close all anti-virus system Then right after right here to installed it: a. After finishing downloading, pls unzip software package deal (upzip security password: MCDiag@) Tips: After unzip, you could get the set up vidoe like the using picture demonstrated: b. Install the software (installation password: MCDiag AutoData 2014) c.
Sticking with the set up movie, you will get the license like the pursuing picture show, then send out the license to us, we could assist get your activation code. Even more issue about Autodata 3.45 simply get in touch with Skype:eobdtool02 Focus On OBD Tools Since 2008 Follow us: Skype: eobdtool02 Wechat/WhatsApp: +411 Email: product [email protected].
Comments are closed.
Fl studio 11 reg key only free download. Get the latest working version of FL Studio 11 Producer Edition CRACK Updated Serial Keys now. Download FL Studio 11 Producer. Double click on registry key and. And i sharing it's fl studio 11 crack, keygen and key. FL Studio 11 Crack & keygen full. free download. Fl Studio 11 Setup. Crack Download Here. All people who download this FL Studio 11 Reg Key receive. Functioning version of FL Studio 11, 12, etc, for free. Only can you still. What is FL Studio 11? Fl studio 11 crack free download no survey, fl studio 11 crack only by tahmidk15. DVDFab v9 cracked serial registration key free download. FL studio 11 crack free download & full version for free. Free download FL studio 11 full version cracked. Cracks Tube Full Software Downloads. Key (Greenfly.
Autodata 3.45 Download Link with One Time Free Activation (No need shipping, when you order it, just write to (email protected) to get the download link) 2. Autodata 3.45 Installed on 630G HDD for Dell D630 Format (software.
Espn/roku Activation Code
How to Installed & Activate Autodata 3.45 Autodata 3.45 is last version autodata, crack autodata 3.45 is update version and more full database than Autodata 3.38. Here eobdtool.com offer Autodata 3.45 crack version free download link and installation guide for customers. The must be use after activation, so pls offer us your hardware ID after you installed the Autodata 3.45. Eobdtool.com Have Alldata 10.53 hot sale now: Autodata 3.45 Free Download Link: Pls kindly note: Autodata 3.45 need activate after installed, 39usd/time for activation. Eobdtool.com offer Autodata 3.45 installed on HDD ready to use for sale, NO need installed and activation, just plug HDD into laptop for use.

Check here to order: What need prepare before installed Autodata 3.45? System requirement: windows 7 32bit or 64bit 2. Download Autodata 3.45 from above download link 3. Close all anti-virus program Then following here to installed it: a. After finishing downloading, pls unzip software package (upzip password: MCDiag@) Tips: After unzip, you could get the installation vidoe like the following picture showed: b. Install the software (installation password: MCDiag AutoData 2014) c. Following the installation video, you will get the license like the following picture show, then send the license to us, we could help get your activation code. More question about Autodata 3.45 just contact Skype:eobdtool02 Focus On OBD Tools Since 2008 Follow us: Skype: eobdtool02 Wechat/WhatsApp: +411 Email: [email protected].
Autodata Activation Code Download
How to Installed & Activate Autodata 3.45 Autodata 3.45 is last version autodata, crack autodata 3.45 is update version and more full database than Autodata 3.38. Here eobdtool.com offer Autodata 3.45 crack version free download link and installation guide for customers. The must be use after activation, so pls offer us your hardware ID after you installed the Autodata 3.45. Eobdtool.com Have Alldata 10.53 hot sale now: Autodata 3.45 Free Download Link: Pls kindly note: Autodata 3.45 need activate after installed, 39usd/time for activation.

0 notes
Link
Origin Pro 10.5.104.48966 Crack + Serial Key (2021) Download Posted on September 28, 2021 by Rehana DOWNLOAD NOW Origin Pro 10.5.104.48966 Crack + Serial Key (2021) Download Origin Pro Crack is a program all connected with graph reading and data analysis. This program can be called aid to scientists and engineers because it makes their work more manageable. This program is simply a way to win bosses ’hearts and persuade everyone without the best techniques and practices. This app is highly recommended and trusted by businessmen and even beginners who want to work in marketing industries and government research laboratories. Origin Pro Crack offers many options for beginners to experts and systematically unveils its great tools and features. Origin Pro 10 key is used very excessively in academics, industries, and companies. Half a million turning points for people using this program so we can get an idea of how reliable and useful they are. Origin Pro is a compelling application that offers a lot of tools for drawing charts and graphs. This pace of features includes the report, C scientific programming environment, Python, templates, graphical tools, batch processing, etc. The charts contain 70 different designs and shapes to provide more creativity to the users and are filled with varied reports. Origin Pro Crack Plus Serial Key Download: Origin Pro Download 100 has been given other features of this program as many chart styles like 2D, 3D, Radar, Stock, Wire Surface, and Pie Charts are offered, but this is not the end. There are many types of charts that users can use for their reports. This program is very suitable for use and very suitable for all businessmen, engineers, and scientists. Origin Pro 2020 Crack System is the ultimate practical application with many tools and features to impress others with its quality and accuracy at work. Users can enjoy millions of worksheet cells for unlimited work. As mentioned above, this program employs approximately half a million engineers and researchers and their teachers. They use this program in profitability, in academics, universities, and federal laboratories. These parameters should be pretty much to persuade you to download this because other users trust this program. Origin Pro Keygen provides you with a direct interface and is the best step towards positive users and its interface can tweak the program according to your taste. Main Features Of Origin Pro Crack: A series of commands are used for metadata and sorting information. Correct and long-term competencies are part of this program. Regular reporting is easy with Origin Pro Crack. Appropriate graphing tools and data analysis, This program is also able to change the appearance of graphs like colors, shapes, and dimensions. Thus, it is easy to modify the graphs. 2D and 3D graph options in this program. Origin Pro offers over 70 different types of charts to present any of them according to your desire. User-friendly interface with Origin Pro Crack. According to all requirements, users can create regular reports of their choice. This feature simplifies engineers and scientists and reduces work stress. This program also contains the availability of ANOVA measurement tools for better results. To provide greater ease for users, Origin Pro also introduced a feature, which is the use of statistical formulas. With these features, users can solve many equations and end their accounts in a short time. Scientific information and features are also subject to change. Another great work is another great piece of this program that provides 60,000 rows and columns. The multi-plate numbers were also part of this great program. The most useful thing about this program is that it can be compatible with many types of regular documents like Excel, ASCII, and many more. When it comes to formatting, Origin Pro Crack has many options for users, for example, TXT, ODT, XML, and CPP. What’s New In Origin Pro? Another new look has been added to the graphics section, which is a stacked 3D graph. Editing new fonts and tags is part of this program. Big icons are now able to plan on the list. 3D maps were created with the help of the new color scheme. Another useful feature is the molecule images created at the base of the worksheet column. It would not be wrong to describe this program as a revolution for those who need to work on various businesses and projects and need help in preparing many reports. It is also one of the best-trusted programs for engineers because its amazing features will never disappoint users. It has all these specifications to meet complex calculations and statistical data for analysis. System Requirements: Disk space must be at least 2 GB. 1 GB RAM. Mandatory GHz processor. The screen should be 1024 x 768 Regarding another dynamic compatibility, Windows 7, 8, 8,1,10, and Vista SP1 32 or 64 Bit are compatible with OS installation Origin Pro 2020 Keys: C6TFV-B8YUN9-BVYCT6-RX5ZE-SXRD Origin Pro 2020 License Key: C6TFV7-YGB8U-H6X5Z-SEXDR-CTFGV Origin Pro 2020 Serial Number: C6TFV-7GYBHUVY7C-6X5ZES-XDRC6 Origin Pro 2020 Serial Key: TFV7YB-GUHNB-VTC6RX-5ZE4-S5XDR Origin Pro 2020 Activation Key: HGRPE-IJSEQ-JHXBS-KJQEA NBKEG-LGZSWO-MNFTS Origin Pro 2020 Registration Key: CCUDM-JSE3U-LK5FS-AD3IO VF6JH-UJTF6-KJCFE-KJVBE How To Activate And Install Origin Pro Crack? Download Origin Pro Crack Blew Link. Install the program. Complete the setup. Run the program. Now it works! Origin Pro 10.5.104.48966 Crack + Serial Key (2021) Download Free Download Links Given Below! DOWNLOAD NOW Download Now
0 notes
Text
Tunstall Driver Download

Download32 HomeSoftware CategoriesNew DownloadsTop DownloadsRss FeedsSubmit SoftwareBookmarkContact Us
Mac
Linux
Audio & Multimedia / Other
kt tunstall tickets 2
Download Links: Click the link below to download kt tunstall tickets
Short details of kt tunstall tickets: kt tunstall tickets for concerts cut price reduced, best deals on kt tunstall tickets plus premium seats, VIP seats, front row kt tunstall tickets, floor kt tunstall tickets, general admission kt tunstall tickets concert kt tunstall tickets on sale for upcoming concerts price cuts with front row...
kt tunstall tickets related software
Title / Version / DescriptionSizeLicensePrice
Santa's Merry Band 1.1341.0 MBFreeware Music all-stars Indigo Girls, G. Love, KT Tunstall and Guster are just some of the musicians who come together for Mibblio's 'Santa's Merry Band' compilation. SANTA'S MERRY BAND with SPECIAL GUESTS! Kids can jam along to 8 beautifully illustrated mibblets (story-songs): - G. Love 'Christmas Baby' - The Brian Setzer Orchestra 'Dig That Crazy Santa Claus' - Guster '
TicketCreator - Print Your Tickets 5.04.3 MBShareware $180 TicketCreator is a unique ticketing software to print tickets for your events. You can easily create even complex venues, design attractive tickets and print in multiple ways. It furthermore manages reservations and season tickets, prints seat labels, diverse reports and a detailed balance. TicketCreator makes ticket printing simple and needs no additional box office hardware. Test the fully functional shareware version for free! English...
Box Office Manager 8.16.6 MBShareware $799.95 Point of sale reservations and ticket system for theatres, schools, colleges, any venue needing a fast, reliable means of reserving seats and selling tickets. The program includes a customer database, report generation, and inventory control. Online help and a printable User Guide are included. There is no charge for email or telephone support. The program includes many user requested features added over several years of release versions...
DepositWiz 1.0.01.4 MBShareware $49.99 DepositWiz prints deposit tickets, and whatever your technical ability, DepositWiz is easy to use. If you're a small business owner or landlord with many checks to deposit every month, this software will help you save time generating deposit tickets for your bank. DepositWiz includes: - Valuable industry standard encryption software protects your sensitive financial information. - Useful Fast Fill lets you create time-saving...
PrintersBench Enterprise 1.153.5 MBShareware $300 PrintersBench Enterprise allows you to design and print tickets, forms, labels, coupons, gift certificates, or any document that requires you to combine text, graphics, serial numbering, reserved seating, and other variable data. From raffle and event tickets to business cards and receipts, PrintersBench Enterprise can handle any page layout on one of eight predefined page sizes or any user defined size - including double sided! PrintersBench...
PrintersBench Plus 1.153.3 MBShareware $35 PrintersBench Plus lets you design and print tickets, forms, labels, coupons, gift certificates, or any document that requires text, graphics, or serial numbering. From raffle and event tickets, to business cards and receipts, PrintersBench Plus can handle any page layout on one of eight predefined page sizes. You can use one of our predefined templates, or create your own project with ease. PrintersBench Plus allows you to import ten...
PrintersBench Pro 1.173.5 MBShareware $125 PrintersBench Pro allows you to design and print tickets, forms, labels, coupons, gift certificates, or any document that requires you to combine text, graphics, serial numbering, reserved seating, and other variable data. From raffle and event tickets to business cards and receipts, PrintersBench Pro can handle any page layout on one of eight predefined page sizes or any user defined size. PrintersBench Pro includes 17 different barcode...
TicketBench Plus 6.172.9 MBShareware $35 TicketBench Plus lets you design and print tickets, forms, labels, coupons, gift certificates, or any document that requires text, graphics, or serial numbering. From raffle and event tickets, to business cards and receipts, TicketBench Plus can handle any page layout on one of eight predefined page sizes. You can use one of our predefined templates, or create your own project with ease. TicketBench Plus allows you to import ten different...
TicketCreator - Eintrittskarten drucken 5.04.3 MBShareware $180 TicketCreator is a unique ticketing software to print tickets for your events, like concerts, theatre performances or sport matches. You can easily create even complex venues, design attractive tickets and print in multiple ways. It furthermore manages reservations and season tickets, prints seat labels, diverse reports and a detailed balance. TicketCreator makes ticket printing simple and needs no additional box office hardware. Prints secure...
Visual Lottery Analyser 3.743.2 MBShareware $39 Visual Lottery Analyser is state-of-the-art lottery analysis software with many unique features. Work with almost all lottery games in the world. Program use new innovative analysis methods like visual drawings analysis, use geometry with special Ticket View for showing lottery game view at hand, use also colors to differentiate between special numbers groups. Everything is done for better and faster understanding how your games and number...
New downloads of Audio & Multimedia, Other
Title / Version / DescriptionSizeLicensePrice
Active@ DVD Eraser 2.0.1612.0 KBFreeware Active@ DVD ERASER erases DVD-RW, DVD+RW or CD-RW media to clear the old data from the disk. Two erasing methods are available: Quick Erase - The disc's structures are changed on drive level so that a drive sees the disc as blank media. Full Erase (Secure method) - The complete surface of the disc is over-written with a neutral pattern. The result is that all data is now cleared forever. Automated erasing is also supported....
Tipard Blu-ray Converter for Mac 10.0.1052.6 MBShareware $33.15 Tipard Blu-ray Converter for Mac has the capability to help you in ripping Blu-ray files and DVD discs, DVD folders or IFO files, and it can also convert almost all video files to other popular video or audio formats. These video files including MP4, AVI, MOV, WMV, M4V, MKV, FLV and audio files including MP3, AAC, AC3, WAV, WMA, M4A, AIF, AIFF, FLAC and so on. Moreover, this Blu-ray Converter for Mac provides powerful editing functions to help...
Tipard DVD Creator 5.2.5056.7 MBShareware $35 Tipard DVD Creator specializes in creating DVD with any videos in MP4, AVI, MKV, MOV, WMV, TS, etc. formats. Besides, this software can also help you set the unique DVD by adding audio track, background music, picture and opening film to your DVD movie, and selecting the most suitable frame, button, and text to your video. Moreover, it can add effect, trim the length, alter the crop area and add watermark for the video in the process of...
Tipard DVD Ripper for Mac 9.2.2051.1 MBShareware $19.95 Tipard DVD Ripper for Mac enables you to rip DVD disc/folder/ISO file to 4K/1080p HD video formats like HD H.264, HD AVI, HD TS, HD WMV, HD MPEG 4, HD MOV and more on Mac. Meanwhile, it can also convert DVD movie to common video formats like MP4, AVI, MOV, WMV, MKV, M4V, etc. and audio formats like MP3, FLAC, WAV, WMA, AAC, ALAC, AC3 and so on for Mac. In addition, it supports English/French/German/Japanese four interface languages. Plus, it...
Tipard Blu-ray Copy 7.1.6227.0 MBShareware $29.75 What can this powerful Blu-ray copying application do for you? It enables you to make 100% ratio copy of your Blu-ray disc, and import Blu-ray folder and ISO image file to a blank Blu-ray disc for backing up without quality loss. In addition, it supports 3D Blu-ray disc as well as 2D Blu-ray. Key Features: 1.Copy Blu-ray disc to Blu-ray disc Tipard Blu-ray Copy provides its ability to decrypt and clone Blu-ray disc to BD disc. Besides,...
Latest Reviews
SoftPerfect RAM Disk (Sean) - Jul 8, 2020 Superb disk utility for speeding up laptops and prolonging the life of their hdd. StarCode Lite POS and Inventory Manager (Ed Martin) - Jan 21, 2019 I would say best inventory software for small shops or stores. Never found an app like this before. Thanks Download32 ConyEdit for Windows (reshim) - Dec 3, 2018 Programmers feel the comfort of coding using ConyEdit which is capable to edit codes in batch mode and supports most of programming language. Disc Cover Studio (harish) - Dec 19, 2017 No need to go for a professional designer for the cover of new record, you can do it on your own sitting at home PC adding your own image on it with the Disc Cover Studio. Kaspersky Security Scanner (Anthony) - Oct 12, 2017 Scans software to find whether it is harmful for computer and also checks for updates of security patches. Comodo Firewall (Maxmuller) - Sep 19, 2017 This just another awesome product from Comodo to protect your computer from unwanted inbound or outbound traffic, also helps you analyze data packets. TCP Splitter (Redrick) - Aug 10, 2017 This lets the data packets we send split into several packages which is convenient for many applications to receive those and process one after another. Project Viewer Lite (Tensialar) - Jul 19, 2017 This is a light weight software for viewing MS project files easily without the MS project installed, all the personal who are involved in the project can view this with graphics and charts. PDF Shaper Professional (Mortinus) - Jun 7, 2017 I had difficulties with the pdf documents which needed to be edited before presentation, then I got PDF Shaper which helped me to take the texts / images out and insert my own texts plus other images. Hotelare (Nielsine) - May 15, 2017 You can enable your guests book any room instantly through your website, also receive the payments, other sections of your hotel can be also handled using the this software like restaurants, accounts, hr etc.
Audio & Multimedia|Business Software|Development Tools|Education|Games|Graphics Software|Network & Internet|System Utilities|Mac Tools|Linux Programs free. software downloads|Submit Software|Contact Us|Privacy Policy|Disclaimer|Link to Download32|Bookmark Us All software information on this site, is solely based on what our users submit. Download32.com disclaims that any right and responsibility for the information go to the user who submit the software, games, drivers. Some software may not have details explanation or their price, program version updated. You should contact the provider/actual author of the software for any questions. There are also user reviews/comments posted about various software downloads, please contact us if you believe someone has posted copyrighted information contained on this web site. Copyright © 1996-2015 Download 32.
Free to Try $19.95 to Buy
Windows
BUSINESS PRODUCTS. Based in Stoke-on-Trent, Staffordshire and established in 1984, Business Products are specialists in the supply, installation and maintenance of Business Technology, such as Photocopier/Printers, All in one Printers, Colour Copiers, Scanners and Laser printers. Tunstall’s Connected Care and Health solutions can form an effective part of the response to the COVID-19 outbreak, helping to monitor and support people at home, reduce pressure on the NHS, provide more preventative and proactive care, reduce social isolation and respond to emergencies. View our full range of COVID-19 solutions here Learn more. ACSON DT-03 BLUETOOTH DRIVER DOWNLOAD - Compatible with all models of Domestic and Mr. Other formats of the 'knx group' command invocations provide options to list already defined groups.
6.5 MB
465,560
With Sound Booster you can make any program as loud as you want
Now you are not limited by the maximum amplification capabilities of your PC’s sound card. You can raise volume to the desired level even if the volume level in system set on maximum. Sound Booster processes all audio being played in system and boosts it before it gets to the sound card.
No need to buy external speakers for your laptop
Tunstall Driver Download Free
Thought of buying a set of speaker for your PC ? Now you might want to rethink your plans. If your laptop’s volume is generally good enough, and the only trouble you experience is with some particular program or media content that is recorded too low, then you can save the situation by using Sound Booster.
Works in every application
You can use Sound Booster to boost sound of a web browser, a media player, a game or any other PC program that plays sound. You can use the software the usual way, no special treatment required. No need to install any plugins or add-on’s. Sound Booster amplifies sound in real-time and there is no need to configure it.
What's New:
Tunstall Driver Download Windows 10
Fixed serious bug that could affect boosting in certain scenarios
Enhancement: boost controls now can be kept visible on screen (prevent auto-hiding)
Enhancement: now it’s possible to specify a desired boost level used at startup
Tunstall Driver Download Windows 7
Popular apps in Players

0 notes
Text
Top 50 Sql Meeting Questions And Solutions
Vehicle increment enables the user to create a serial number to be created whenever a new document is put in the table. VEHICLE INCREMENT is https://is.gd/snW9y3 for Oracle, AUTO_INCREMENT in MySQL and also IDENTITY keyword can be made use of in SQL SERVER for auto-incrementing. Mainly this keyword is utilized to create the primary trick for the table. Normalization prepares the existing tables and also its fields within the database, resulting in minimum replication. It is used to streamline a table as much as feasible while keeping the special areas. If you have actually little to claim for yourself, the recruiter power believe you have null to claim. pl sql meeting concerns I make myself feel magnificent ahead the interview starts. With this concern, the employer will evaluate you on exactly how you prioritise your task checklist. I look forward to functions with damien once more in the future stressful. You mightiness require a compounding of dissimilar kinds of concerns in order to fully cover the problem, as well as this may diverge betwixt individuals. Candidates appear to interviews with a finish of exciting you. A primary key is a special type of special key. A international trick is used to preserve the referential web link stability between two data tables. It prevents activities that can ruin web links in between a kid and a parent table. A main secret is used to define a column that distinctly identifies each row. Null worth as well as duplicate values are not enabled to be entered in the primary key column. Nonetheless, you might not be offered this tip, so it gets on you to bear in mind that in such a situation a subquery is precisely what you require. After you experience the essential SQL interview inquiries, you are most likely to be asked something more particular. And also there's no much better sensation on the planet than acing a inquiry you exercised. Yet if all you do is practice SQL interview questions while overlooking the fundamentals, something is mosting likely to be missing out on. Request https://tinyurl.com/c7k3vf9t might jump the interview and get to them, but demand none will make you look withdrawn or unprepared. When you are taking the examination, you need to prioritise fashioning sure that all parts of it run. Top 50 google analytics meeting inquiries & solutions. Nerve-coaching from the interview men that will blast your uneasy sensations to make sure that you can be laser-focused and also surefooted once you land in the spot. Terrific, trying, and also im sort of gallant i was capable to solve it under such stress. Those that pass the phone or image interview proceed to the in-person meetings. Once again, it's crafty inquiry, and also not just in damages of operations it out. On the far side enabling myself to get some yelling meemies out, i truly delighted in the possibility to obtain a better feel for campus/atmosphere. Knowing the really certain answers to some really specific SQL interview questions is excellent, however it's not going to assist you if you're asked something unexpected. Don't get me wrong-- targeted prep work can certainly assist. Note that this not a Not Void restraint as well as do not perplex the default worth restriction with refusing the Null entrances. The default value for the column is set only when the row is produced for the very first time and also column worth is ignored on the Insert.

Denormalization is a database optimization method for enhancing a database facilities performance by adding repetitive information to one or more tables. Normalization is a database layout method to arrange tables to minimize information redundancy as well as information dependency. SQL restraints are the set of rules to limit the insertion, removal, or upgrading of data in the databases. They limit the kind of data entering a table for keeping information precision as well as integrity. DEVELOP-- Made use of to produce the data source or its things like table, index, function, sights, triggers, etc. A one-of-a-kind secret is utilized to distinctively identify each document in a database. A CHECK restraint is made use of to restrict the values or kind of data that can be kept in a column. A Primary key is column whose worths distinctively determine every row in a table. The primary role of a main key in a information table is to preserve the internal integrity of a data table. Query/Statement-- They're typically made use of interchangeably, however there's a small distinction. Listed here are numerous SQL interview questions and solutions that declares your knowledge regarding SQL as well as supply brand-new insights as well as finding out about the language. Undergo these SQL meeting concerns to revitalize your knowledge before any type of interview. As a result, your following job won't have to do with clarifying what SQL restraints and also tricks indicate in general, although you must be really knowledgeable about the idea. You will instead be offered the opportunity to show your capability to clarify on a particular kind of an SQL restraint-- the international vital restriction. Write a SQL question to find the 10th highest height ("Elevation") from a "Mountain" table. Alteration to the column with NULL worth or perhaps the Insert procedure specifying the Void worth for the column is allowed. Click on the Set Main Secret toolbar switch to set the StudId column as the main vital column. my explanation RIGHT OUTER JOIN is among the JOIN operations that permits you to define a SIGN UP WITH provision. It preserves the unequaled rows from the Table2 table, joining them with a NULL in the shape of the Table1 table. And afterwards, as presently as we reduced that possibility, everybody broken out laughing but you can't be in on the technique." there are numerous " weak points" that you can turn into positive situations to reveal an response that your interviewer will respect and see. - this environments covers the hardware, web servers, operating system, web internet browsers, various other software application system, etc. Duties that you were not able-bodied to be total. "i identify which https://bit.ly/3tmWIsh is near considerable, and afterwards i try to do that job first earlier finish the doing well one. For good example, there are approach of accounting plan, armoury plan, etc. While it's simpler to ask common concerns, you risk not acquiring the discerning information you need to make the best hiring decision. Question optimization is a process in which data source system compares different query strategies as well as select the inquiry with the least expense. Main key produced on greater than one column is called composite primary key. DELETE removes some or all rows from a table based upon the problem. TRIM eliminates ALL rows from a table by de-allocating the memory pages. The procedure can not be curtailed DECLINE command gets rid of a table from the database entirely. The main difference between both is that DBMS saves your info as files whereas RDMS conserves your information in tabular kind. Also, as the keyword Relational indicates, RDMS permits various tables to have relationships with one another using Main Keys, Foreign Keys and so on. This creates a vibrant chain of power structure between tables which likewise supplies valuable constraint on the tables. Presume that there go to least 10 documents in the Hill table. That's why leading companies are progressively relocating away from common questions and are rather supplying candidates a crack at real-life inner situations. "At Airbnb, we provided possible hires accessibility to the tools we utilize as well as a vetted data collection, one where we understood its restrictions as well as troubles. It permitted them to focus on the shape of the information and framework answers to issues that were purposeful to us," keeps in mind Geggatt. A Inspect restraint look for a certain condition before inserting data into a table. If the data passes all the Check constraints after that the data will certainly be placed right into the table or else the information for insertion will be thrown out. The CHECK restriction makes sure that all worths in a column satisfy certain problems. A Not Void restraint limits the insertion of null worths into a column. If we are making use of a Not Null Restraint for a column then we can not disregard the worth of this column throughout insertion of data into the table. The default restriction allows you to set a default worth for the column.
0 notes
Text
Sis File Extractor

Sis File Extractor Extension
Sis File Extractor File
Sis File Extractor Rar
Sis File Extractor Software
Sis File Extractor Online
-->
SIS - Student Information Systems Specific Patron Extract Resources Listed Below, for each known Student Information System in wide use among CARLI institutions, there are 2 basic resources: A Data Map maps patron sync file XML elements to corresponding SIS tables/columns. SISXplorer allows you to Inspect and Extract all the files contained inside the 3rd Edition installation packages. Using SISXplorer you can: - Extract all the images from 3rd Edition Themes - Deeply Inspect the content of each file using the Integrated Hexadecimal Viewer. Instantly Unpack, Edit and Sign SIS files (.sis &.sisx) with Freeware SISContents.SIS or.SISX files are Symbian OS Installer Files which lets you to install any application on your symbian OS based mobile phones. Description of the SIS File Format. The UID 1, UID 2 and UID 3 fields are the first three words of the file, and indicate the type of data it contains.UID 1 is the UID of the application to be installed, or 0x10000000 if none.
What is School Data Sync?
School Data Sync is a free service in Office 365 Education that reads the rosters from your SIS, and creates classes for Microsoft Teams, Intune for Education, and third party applications. Microsoft Teams brings conversations, content, and apps together in Office 365 for Education.
What SIS/MIS vendors does School Data Sync support?
Because School Data Sync imports data in CSV files, it supports virtually every SIS on the market. SDS also supports importing roster data via the PowerSchool API, and the industry standard OneRoster API. Customers have deployed SDS with over 70 SIS vendors and data providers, including the below:
VendorsAeriesiSAMSSchoolToolAspenITCSSSEEMiSAtlasJMCSenior SystemsATSJupiterSEQTAAxiosKAMARSIMSBannerLibrusSkolplatsen (Gotit)BlackbaudMagisterSkolPulsCanvasMazeSkywardCloud Design BoxMMS GenerationsSomTodayCMISMyclassboardSTARSCobaMyED BCSunGardCompassOncourseSystemSycamoreCornerstone/TADSOracle Campus SolutionSycamore EducationCSIU eSchoolDataParnassysSynergeticDeltaLinkPC SchoolSynergyEcoPlurilogicTASSEd-AdminPowerSchoolTCS iONEdgear JCampusPrimusTeacherEaseEduarteProgressbookTeams Pro logicEdupointProgressoThird partyEngage UnitedPronote from Index EducationTrilliumeSchoolPLUSProsolution (Compass CC)TxEISesemtiaQTylerSISeTapRealtime SISVeracrossExtensRedikerVersus-ERPFocusRenWebVisma FlytGenesisRuler Connect/Locker ConnectVisma Primus/WilmaGradelinkSalamander SoftVulcan UONET+GRICSSAM Spectra by Central AccessWCBS PulseIbisSapphireWengageIlluminateEdSchool ToolWIS WEBiluminateSchoolBaseWisenetInfinite Campus & ScholarshipSchoolmasteriPASSSchoolonline
Where is School Data Sync available?
School Data sync is currently available in all regions worldwide except for China and Germany.
What apps work with School Data sync?
School Data Sync imports school, section, student, teacher, and roster data from a SIS to Office 365 so it can be used by numerous 1st party and 3rd party applications. Visit https://sds.microsoft.com to see a list of the EDU apps that use Office 365 and School Data Sync data for Single Sign-on and Rostering integration.
Will SDS automatically sync changes or do we have to restart sync to synchronize changes as they occur?
Sync runs continuously after a sync profile is created, unless manually stopped. For PowerSchool API and OneRoster API, the connection to the SIS is continuous and always polling for changes in data to be synced. If you’re running a sync profile which uses one of the available CSV based sync methods, changes within your data can be synchronized by uploading new CSV files that contain the data changes. You can upload new files through the SDS portal or through the SDS toolkit. Once new CSV files are uploaded, the sync process will begin automatically if no errors are encountered. If you’re new data set contains errors, you may need to remediate them first and reupload the files, or hit the resume sync button on the sync profile to continue syncing regardless of the errors found.
Need for speed hot pursuit 2 online. Need For Speed Hot Pursuit 2 Cd Key Changer: Need For Speed Hot Pursuit 2 Cd Keygenerator By Zipit. Serial means a unique number or code which identifies the license of the software as being valid. All retail software uses a serial number of some type, and the installation requires the user to enter a valid serial number to continue. The Need For Speed Hot Pursuit free cd key – keygen took us an excellent amount of time to establish, generally since cracking the codes wasn’t all that simple. Now that we have finally finished the Need For Speed Hot Pursuit Keygen we are proudly launching it to the general public!
What are the permission requirements for accessing and managing School Data Sync?
To access and manage SDS, your account must be a Global Administrator within the tenant.
What is the School Data Sync schema (object and attributes) available through REST API?
The Education Attributes Reference contains the full list of potential data available. The CSV files reference explains the required fields available for import via SDS.
How can we export data from our SIS to Microsoft’s required CSV format?
Since each SIS is different, we encourage School Data Sync (SDS) customers to contact their SIS vendor for support and assistance with building the appropriate export from the SIS to CSV files in one of the acceptable formats (SDS format, Clever format, or OneRoster format). Many SIS’s already have CSV export functionality, and do not require custom tools or database extractors to complete the export process. Microsoft does not provide support however for SIS extractor tools built by SIS vendors. Please contact your SIS vendor for assistance with data exports.
What is the proper format for the Term StartDate and Term EndDate attributes?
School Data Sync does not restrict the Term StartDate and Term EndDate attribute format beyond the currently allowed .NET options, however we recommend using a format of mm/dd/yyyy (i.e. 11/19/2016 or 6/12/2016). Future development efforts may align to this recommendation for features and functionality which leverage these attributes.
Can I export the sync issues/errors generated by SDS?
Yes, you may export the list of errors generated on a profile by profile basis within the SDS UI. To export the list of errors, log into sds.microsoft.com > select your sync profile > click on the Download all errors as .csv file button.
Sis File Extractor Extension
Does Microsoft provide extractor tools for my SIS data?
Microsoft does not build or maintain extractor tools for any SIS vendor. Many SIS’s have data extraction tools built into the SIS already. If your SIS does not include an extraction tool, and you need assistance extracting data from your SIS into our schema CSV format, please contact your SIS vendor for support. All there young jeezy download.
Sis File Extractor File
Why is there a character limitation on email addresses in SDS?
Email addresses for all objects in O365 must adhere to several RFC standards for internet email addressing, and SDS is simply aligned to the character limitations within each of the core Office 365 services, including SharePoint Online, Exchange Online, and Azure Active Directory.
How many sync profiles do I need to create when setting up School Data Sync?
Most often, schools will only need to create a single sync profile in School Data Sync (SDS) to synchronize all Schools, Sections, Teachers, Students, and Rosters. There are a few reasons that would require you to create additional sync profiles: Plants vs zombies garden warfare free download full version for windows.
Multiple Domains for Identity Matching – When configuring SDS you must match users from your source directory to users in Azure Active Directory (AAD). Within each sync profile, you can specify a single domain for teachers and a single domain for students. If your teachers or students are configured with more than a single domain for the attribute being used in the identity matching configuration, you may need to create multiple sync profiles to ensure a match for all users within your tenant. We recommend minimizing the number of domains configured across student and teachers for core identity matching attributes such as the UserPrincipalName and Mail attributes.
Multiple Sync Methods or Source Directories – SDS allows you to synchronize objects and attributes in a few different ways. We currently accept three different types of CSV file formatting (SDS format, Clever format, OneRoster format). SDS also allows for two different types of API connections to sync objects and attributes (PowerSchool API and OneRoster API). If you need to import data from more than a single source directory, you will need to configure multiple sync profiles. For example, you may need 1 sync profile to sync objects from PowerSchool and another sync profile to sync objects from SDS format CSV files. We recommend minimizing the number of sync profiles whenever possible.
Mix of Create New Users and Sync Existing Users – SDS allows you to either create new user accounts in AAD from your source directory data, or synchronize against existing users that are already present in Azure AD. If you need to create some new users, and synchronize against some existing users, two or more sync profiles will be required. You can only choose one of these two options within a single sync profile.
More than 2 million rows in a csv file – SDS has a limit on the number of rows that can be contained within a set of CSV files uploaded within a single sync profile. The current limit is 2 million rows per CSV file. If you have CSV files that contain more than 2 million rows, you’ll need to split the entire set of CSV files up along school lines (all sections, teachers, students, rostering associated with the school(s) being split). Once split, create additional sync profiles with the same settings, and upload the split files accordingly.
Can I have additional headers and columns in my CSV files beyond what I intend to sync?
Yes, your CSV files may contain extra headers and data. Only the attributes selected within the sync profile setup wizard will attempt to synchronize. Any extra headers and columns of data will be ignored.
If we remove a user or section from Classroom will they reappear when we sync again?
Manually updating a class roster through Classroom will not be overwritten when the next sync runs. School Data Sync makes changes to the roster based on the last sync, and not based on manual changes, with the exception of two actions: Reset Sync and Recreating a Sync Profile. Aside from those exceptions, here is how SDS treats manual additions and deletions.
Example 1:
A class is synced with a teacher and students
The teacher goes to Classroom to add a co-teacher to the class
The class is subsequently synced with no changes to teacher enrollment
(Correct behavior) The co-teacher's membership is unaffected
The class is subsequently synced with the co-teacher added
(Correct behavior) the co-teacher's membership is unaffected
The class is subsequently synced w/ the co-teacher removed
(Correct behavior) the co-teacher is removed from the class
Example 2: Loadiine zelda breath of the wild.
A class is synced with a teacher and students
The teacher goes to Classroom to remove a student from the class
The class is subsequently synced with no change to the student enrollment
(Correct behavior) The student's non-membership is unaffected
The class is subsequently synced with the student removed
(Correct behavior) the student's non-membership is unaffected
The class is subsequently synced w/ the student re-added
(Correct behavior) the student is re-added to the class
Sis File Extractor Rar

Sis File Extractor Software
What do Azure AD Connect and SDS do and how can they work together?
Azure Active Directory Connect (AAD Connect) syncs on-premise AD Users, Groups, and Objects to Azure AD (AAD) in Office 365.
School Data Sync (SDS) syncs additional Student and Teacher attributes from the Student Information System (SIS) with existing users already synced and created by AAD Connect. Adding Student and Teacher attributes evolves the identity and enables apps to provide richer user experiences based on these distinguishable attributes and education personas. SDS allows you to automatically create Class Teams within Teams for Education, School based Security groups for Intune for Education Device policy, OneNote Class Notebooks, and class rostering for 3rd party application integration.AAD Connect and SDS will never conflict, as SDS will not sync or overwrite any attribute managed by AAD Connect. SDS also provide the option to create new users, so if you don’t want to sync and create them with AAD Connect from your on-premise AD, you can use SDS to sync and create them directly from your SIS.
Both AAD Connect and SDS also sync and create other object types, like Groups, Administrative Units,and Contacts, but unlike Users, these object types are not combined to form individual and unique objects in AAD.
What special characters are not supported by School Data Sync?
Sis File Extractor Online
There are several special characters that are not supported within School Data Sync. During profile creation, you will have an option to have SDS automatically replace unsupported special characters found with an “_”. The following link explains unsupported characters.

0 notes
Text
U.S. Executes Corey Johnson for 7 Murders in 1992

WASHINGTON — The Trump administration executed Corey Johnson on Thursday for a series of seven murders in 1992. He was the 12th federal inmate put to death under President Trump.
Mr. Johnson committed the murders in the Richmond, Va., area to further a drug enterprise that trafficked large quantities of cocaine. Among his crimes were the shooting with a semiautomatic weapon of a rival drug dealer, the killing of a woman who had not paid for some crack cocaine and the shooting of a man at close range whom Mr. Johnson suspected of cooperating with the police.
Mr. Johnson, 52, was pronounced dead by lethal injection at 11:34 p.m. at the federal correctional complex in Terre Haute, Ind., the Bureau of Prisons said.
When asked by an executioner if he had any last words, Mr. Johnson responded, “No, I’m OK,” according to a report from a journalist in attendance. Several seconds later, he said softly, “Love you,” gazing at a room designated for members of his family.
In a statement released by a spokesperson for his defense team, Mr. Johnson apologized to the families that were victimized by his actions and listed the names of the seven murder victims, requesting that they be remembered.
“On the streets, I was looking for shortcuts, I had some good role models, I was side tracking, I was blind and stupid,” he said. “I am not the same man that I was.”
Mr. Johnson thanked the chaplain, his minister, his legal team and the staff in the special confinement unit. He noted that “the pizza and strawberry shake were wonderful,” but that he never received the jelly-filled doughnuts that he ordered, a reference to his final meal request. “What’s with that?” he added. “This should be fixed.”
Mr. Johnson tested positive for the coronavirus last month, shortly after the government scheduled his execution, during an outbreak on federal death row at the prison in Terre Haute. At least 22 of the men housed on death row there tested positive, lawyers for the prisoners and others with knowledge of their cases said. Madeline Cohen, who represents two of the men, said she knew of 33 cases.
In a request to delay Mr. Johnson’s execution, his lawyers said the virus had caused significant lung damage. They argued his execution would violate the Eighth Amendment’s prohibition on cruel and unusual punishment because he could experience a sensation of suffocating or drowning if put to death with the federal government’s method, which uses a single drug, pentobarbital. Instead, his lawyers suggested, Mr. Johnson could be executed by firing squad or the Bureau of Prisons could administer a pain-relieving anesthetic drug before the injection of pentobarbital.
Specifically, Mr. Johnson’s lawyers argued that the combination of the coronavirus and the government’s lethal injection protocol would place him “especially at risk of experiencing flash pulmonary edema while still sensate.” Flash pulmonary edema, a condition in which fluid rapidly accumulates in the lungs, has been at the center of some challenges to the federal government’s execution protocol. The courts have been largely unreceptive to those claims.
But briefly, it seemed as if the coronavirus would provide Mr. Johnson a reprieve. A judge on the U.S. District Court for the District of Columbia suspended Mr. Johnson’s execution and another execution scheduled for Friday until at least March. Shortly after, a panel of judges on the U.S. Court of Appeals for the District of Columbia Circuit overturned that order.
Joined by another judge on the panel, Judge Gregory G. Katsas of the Appeals Court cited Supreme Court precedent that states that the Eighth Amendment “‘does not guarantee a prisoner a painless death — something that, of course, isn’t guaranteed to many people.’”
In a filing with the Supreme Court, the government contrasted its lethal injection protocol with death by hanging, claiming that hanging could cause suffocation that lasts several minutes. Even if coronavirus infections would make the prisoners’ executions more painful, the government argued, the “brief duration of pain,” most likely measured in seconds or at most two minutes, would be far less than that of inmates executed by hanging.
Mr. Johnson “is a convicted serial killer who murdered and maimed multiple people on different occasions, and whose victims included innocent bystanders,” the government said in a separate filing with the Supreme Court. “Their families have waited decades for the sentence to be enforced and are currently in Terre Haute, Ind., for the execution.”
A majority of the Supreme Court sided with the government in declining Mr. Johnson’s requests for reprieve.
Mr. Johnson’s lawyers also sought to challenge his execution by arguing he was intellectually disabled, rendering it unlawful.
His claims of intellectual disability were rejected on the basis that an I.Q. score of 77 was believed to be too high to merit the diagnosis, his lawyers said. But they argued that results from other I.Q. tests and an adjusted version of the same score indicated that he qualified as intellectually disabled.
But rebutting those claims, the Justice Department contended that the murders were planned, and not impulsive acts by someone incapable of calculated judgments. For example, when the drug organization operated in Trenton, N.J., Mr. Johnson beat people with a metal bat to protect the enterprise, the government said.
Lawyers for another man executed by the Trump administration — Alfred Bourgeois in December — also argued that their client was intellectually disabled. In both cases, a majority on the Supreme Court rejected the prisoners’ claims.
Two of Mr. Johnson’s lawyers still maintained that their client lacked the capacity to be a drug kingpin, as he was portrayed by the government. In a statement, they said he could barely read or write, struggled with basic tasks of daily living and was “a follower, desperate for approval, support and guidance.”
“No court ever held a hearing to consider the overwhelming evidence of Mr. Johnson’s intellectual disability,” said the lawyers, Donald P. Salzman and Ronald J. Tabak. “And the clemency process failed to play its historic role as a safeguard against violations of due process and the rule of law.”
Mr. Johnson was convicted in 1993 of seven capital murders, among a host of other charges related to drug trafficking and acts of violence. His lawyers unsuccessfully argued that he should be granted some reprieve under the First Step Act, a bill signed into law by Mr. Trump that among other things allowed for shortened sentences for certain drug offenders.
Two others involved in the conspiracy — Richard Tipton and James Roane — who together trafficked large quantities of cocaine in the Richmond area in the early 1990s, were also sentenced to death.
Mr. Tipton and Mr. Roane remain at the federal penitentiary in Terre Haute. The Justice Department has not scheduled their executions.
President-elect Joseph R. Biden Jr., whose term begins Wednesday, has signaled his opposition to the federal death penalty, so their executions are unlikely to occur anytime soon. Mr. Biden has pledged to work to pass legislation to end the federal death penalty as part of his criminal justice platform.
The Trump administration intends to execute its final inmate, Dustin J. Higgs, on Friday. Mr. Higgs was sentenced to death for the 1996 murders of three women in Maryland. If his lawyers are unsuccessful in their appeals and Mr. Trump does not grant clemency, Mr. Higgs’s death will be 13th federal execution in a little over six months and the third this week. Lisa M. Montgomery, the only woman on federal death row, was put to death on Wednesday.
Since July, the number of prisoners under a federal death sentence dropped by about 20 percent as a result of the spate of executions carried out by the Trump administration, according to data from the Death Penalty Information Center. That month, the administration resumed the use of federal capital punishment after a 17-year hiatus.
Multiple Service Listing for Business Owners | Tools to Grow Your Local Business
www.MultipleServiceListing.com
from Multiple Service Listing https://ift.tt/39BxaQb
0 notes