#Wireless and Satellite Systems
Explore tagged Tumblr posts
Text
The Spectrum of Telecommunication: Understanding Different Forms

Telecommunication has evolved drastically, shaping the way businesses and individuals connect across the globe. At Lighthouse Communication, we recognize the importance of staying informed about the various forms of telecommunication that impact our daily lives. From traditional landlines to sophisticated wireless systems, the spectrum of telecommunication encompasses a wide range of technologies designed to transmit data efficiently over long distances.
In this blog, we will explore the four primary types of telecommunication networks—public switched telephone networks (PSTN), wireless communication networks, satellite communication networks, and the internet. Each plays a vital role in modern communication, whether through voice, video, or data transfer. These networks form the backbone of the infrastructure that supports businesses, hospitals, and everyday digital interactions.
Join us as we delve into how these forms of telecommunication impact various industries, with a particular focus on business systems, and learn how organizations like ours at Lighthouse Communication help maintain and install these essential systems. Understanding the spectrum of telecommunication can provide valuable insights into improving communication solutions for your business.
Read More:- https://thelighthouseorganization.com/blog
#Telecommunication Networks#Types of Telecommunication#Business Communication Solutions#Wireless and Satellite Systems#Digital Infrastructure
0 notes
Text
As the Trump administration's Department of Government Efficiency (DOGE) continues to rampage through the United States federal government, essentially guided by Elon Musk, the group has also been upending traditional IT boundaries—evaluating digital systems and allegedly accessing personally identifiable information as well as data that has typically been off-limits to those without specific training. Last week, The New York Times reported that the White House is adding Musk-owned SpaceX’s Starlink Wi-Fi “to improve Wi-Fi connectivity on the complex,” according to a statement from White House press secretary Karoline Leavitt. The White House's Starlink internet service is reportedly being donated by the company.
Spotty internet is an annoying but highly solvable problem that WIRED has reported on extensively. Of course, the White House is a highly complex organization operating out of a historic building, but network security researchers, government contractors, and former intelligence analysts with years of experience in US federal government security all tell WIRED that adding Starlink Wi-Fi in a seemingly rushed and haphazard way is an inefficient and counterproductive approach to solving connectivity issues. And they emphasized that it could set problematic precedents across the US government: that new pieces of technology can simply be layered into an environment at will without adequate oversight and monitoring.
“This is shadow IT, creating a network to bypass existing controls,” alleges Nicholas Weaver, a member of the nonprofit International Computer Science Institute's network security team and a computer science lecturer at UC Davis. He adds that while secret and top secret information is typically (but not always) processed only on special, separate federal networks that have no wireless access, the security and uniformity of White House Wi-Fi is still extremely important to national security. “A network like the White House unclassified side is still going to be very sensitive,” he says.
“Just like the Biden Administration did on numerous occasions, the White House is working to improve WiFi connectivity on the complex,” White House spokesperson Karoline Leavitt tells WIRED in a statement.
A White House source who asked not to be named supported the switch, arguing that in some areas of the campus, “the old Wi-Fi was trash.”
Researchers point out that while Starlink is a robust commercial ISP like any other, it is not clear that it is being implemented in compliance with White House Communication Agency requirements. If the controls on the White House Starlink Wi-Fi are more lax than on other White House Wi-Fi, it could introduce security exposures and blind spots in network monitoring for anomalous activity.
“The only reason they'd need Starlink would be to bypass existing security controls that are in place from WHCA,” claims former NSA hacker Jake Williams. “The biggest issues would be: First, if they don't have full monitoring of the Starlink connection. And second, if it allows remote management tools, so they could get remote access back into the White House networks. Obviously anyone could abuse that access.”
One baffling aspect of the arrangement is that Starlink and other satellite internet is designed to be used in places that have little or no access to terrestrial internet service—in other words, places where there are no reliable fiber lines or no wired infrastructure at all. Instead of a traditional ISP modem, Starlink customers get special panels that they install on a roof or other outdoor place to receive connectivity from orbiting satellites. The New York Times reported, though, that the White House Starlink panels are actually installed miles away at a White House data center that is routing the connectivity over existing fiber lines. Multiple sources emphasized to WIRED that this setup is bizarre.
“It is extra stupid to go satellite to fiber to actual site,” ICSI's Weaver says. “Starlink is inferior service anyplace where you have wire-line internet already available and, even in places which don't, inferior if you have reasonable line of sight to a cell tower.”
Weaver and others note that Starlink is a robust product and isn't inherently unreliable just because it is delivered via satellite. But in a location where fiber lines are highly available and, ultimately, the service is being delivered via those lines anyway, the setup is deeply inefficient.
While Starlink as a service is technically reliable, incorporating it in the White House could create a long-term federal dependence on an Elon Musk–controlled service, which could create future instabilities. After European officials raised concerns earlier this month on whether Starlink might stop serving Ukraine, Musk posted on social media: “To be extremely clear, no matter how much I disagree with the Ukraine policy, Starlink will never turn off its terminals … We would never do such a thing or use it as a bargaining chip.”
16 notes
·
View notes
Note
I am by no means an expert on technology or how computers and the internet work, but I will try to explain.
Computers are electronic devices made to store, use, and process data. Computers can “talk” to other computers by using cables and/or wireless systems (frequencies sent between computers or to satellites, which act as bridges between computers).
The internet is a the culmination of computers all over the world (operated by people, generally) talking to each other in one gigantic, shared network. It allows anyone with a computer and a way to transfer signals to access any information broadcast by anyone else.
Though the internet is a wonderful thing with nearly limitless potential for spreading knowledge and general goodness, it is a double-edged sword. The internet allows malicious people to coordinate attacks and violate others’ privacy.
Search engines — like “Google” as mentioned by other askers — are programs that help organize any information put on the internet into a format where one can “search” a term or phrase to find relevant information on the internet.
For example, if you search “dog” into Google, it will browse the internet and show you relevant pictures, websites, and videos regarding dogs.
I hope this makes sense!
Thank you for taking the time to provide me with such a thorough explanation of this technology. It seems you are right in calling it a double-edged sword.
Power unchecked breeds chaos. I would imagine this the Internet, in providing a vast wealth of information, similarly gives one access to deception and manipulation. Still, knowledge is power. And those who understand the machine control its destiny.
#ask viktor#viktor#arcane viktor#arcane rp#viktor arcane#arcane roleplay#viktor lol#viktor league of legends#askviktor#arcane#arcane ask blog#viktor rp arcane#viktor roleplay#viktor rp#arcane roleplay blog#arcane lol#arcane rp viktor#arcanerp#viktor arcane roleplay#viktor arcane rp#arcane rp blog#arcane league of legends
14 notes
·
View notes
Text
Nobody Should Ever Lose Their Place in the World
Word Count: 2436 AO3 Written for @pulpmusicalsfortnight2024 Day 5: Modern AU. Huge thank you to my beta @faery-people-of-the-future-day!
The first time Anna finds her, it's by accident.
She is scouring through the database of Observatory Technology and Satellite Services, a subdivision of the infamous Herschel Corporation. It has been weeks of Anna trying to break into their servers, months since the announcement of their new wireless internet system, and today is the first day she has made any progress at all. She actually got in.
It had been practically effortless. Anna doesn't know what allowed her lucky break but she is grateful for it.
Doesn't mean her job is easy now. The files are convoluted, dozens of project names that mean nothing to her. But she only needs one.
The Bright Future Initiative.
Her Sagitta.
Still, she is going in the back way, and mostly flying by the seat of her pants. She isn't sure how to search through the files like this; her skills lie more in engineering than hacking. But she needs to find it, needs to get to her-
Her screen suddenly freezes. Anna clicks furiously, but her mouse doesn't respond. No. No, it's not fair. She can't have been kicked out. She hasn't found it yet.
Frustrated tears well in her eyes as she curses at the screen. Just as she is about to restart her computer, brilliant cyan text appears in the code she was searching through.
//error: Designation?
Anna... Anna has no idea how to respond to that. She stares at the screen, frantically trying to come up with some kind of lie Observatory Tech’s IT would find believable when-
//error: Hello? I know you're there. I would like to know just who is interrupting my operation. This is the Traveler speaking.
And that is the moment Anna puts it together. The reason it had been so easy to break through Observatory Tech's firewall today.
Someone had already done it.
Fuck. Fuck.
Okay, okay, she needs a designation. A hacker moniker? Does she ever deserve one of those? Anything but her real name, what could she-
And suddenly, it hits her like a flash, from one of her first Discord messages with John.
Well, if you're going to call me Herschy, I'm going to call you-
She types the name in, not even surprised her keyboard works again.
You: Nova. I'm Nova.
There is a pause, and the other person types back.
//error: You come up with that just now?
Even though the other person can’t see it, Anna fights to hide a blush.
You: Is it that obvious?
//error: Your work is... heavy-handed, to say the least.
Did they really need to type the ellipses? Anna gets the picture.
//error: And the fact you didn’t immediately log off when I introduced myself really says you don’t know what you are getting into.
Anna frowns. Who on Earth could be so arrogant?
You: You really think every person knows who you are?
//error: Any hacker who knows their way around a keyboard would. You probably do too, little star. Ever heard of the Blazing World Coalition?
Anna’s eyes widen. She has. They are a group of self-identified white hat hackers, the closest thing the modern day has to a real Robin Hood. Just a few months ago, they had completely bankrupted the Itzal Financial Group after they shorted their own employees’ pensions in order to make millions. Not long about that, the BWC had been declared a terrorist group by the United States government.
Anna was chatting with Public Enemy Number 1.
You: Oh.
She isn’t sure why she types it. She just doesn’t know what else to do.
//error: (✿◠‿◠) I see my reputation precedes me. //error: So do us both a favor and log. Off.
Anna should. She knows she should. She should log off and forget this whole thing, because she is suddenly in so incredibly far over her head.
But she remembers the grin on William Herschel’s face as he debuted her tech. The awe in the newscaster’s voice when he talked about the Satellite that was going to change the world.
Her Satellite.
You: I’m sorry. I can’t.
//error: That wasn’t a request, little star. And I won’t ask nicely again. You should leave before you burn out.
Anna’s palms sweat. The keys feel damp under her fingers.
You: I can’t, there is something I need. I won’t get in your way, I don’t want money or anything like that. But I can’t leave just yet.
There is another long, long pause after that. Beneath the post-it note she has over her camera, a glowing red light turns on. Anna screams, and then covers her mouth. She still can’t fully mask her frantic gasping because-
They turned on her camera.
//error: ( ͡ ͜ʖ ͡°) You have such a gorgeous scream, little star. Shame I can’t see you. Though there are plenty of other cameras to look through... do you think you can cover them all? (´・ω・`)?
No. She doesn’t think she can.
//error: There is a lot I can do with a face. You think this is scary, wait until I release all your naughty little secrets to the public. I am sure the authorities would love to hear about your new hobby. So do us both a favor and log off now. I won’t ask again. ヾ( ̄▽ ̄) Bye~Bye~
Anna’s heart is pounding in her ears. All she can hear is the blood rushing through her veins at what feels like 100 miles per hour. She wonders if the Traveler can hear it through the microphone.
But she can’t give up. She knows now she won’t get another opportunity, not if they improve security after this attack; she could barely manage the security before. If they beef it up, she will have no chance.
The Traveler has made this her last chance to regain control of the Sagitta. Anna can’t bear to waste it.
You: I can’t. Please. Please let me do this.
Another pause. Anna waits for the sound of sirens or maybe for her oven to explode, but all remains quiet. The red light on her laptop clicks off.
//error: What could possibly be so important you would risk your entire identity just to see this through?
Anna hesitates. A group like the Blazing World with her Satellite, able to connect to the internet from anywhere on a grid where no one else would be able to track them... They would have the power to do anything they wanted if they took it over.
But they help people. All the employees who had lost their life savings when Itzal Financial shorted them? The day after the BWC’s attack, they woke up with bank accounts doubled or tripled what they had been before, with air tight records listing the funds as severance. Even when Itzal Financial had gone to court, there had been no case. No proof. Just over a thousand struggling people were suddenly able to enjoy life again.
They are her only shot now.
You: Do you know about the Bright Future Initiative?
Anna may ask the question, but she already knows the answer. It's all anyone spoke about for weeks after the announcement.
//error: Herschel's new project? Where he boosted the internet for his companies from a satellite?
A Satellite. A. The dismissal makes her bristle. Her correction is swift and formal, showing none of the indignation thrumming through her.
You: My Satellite. He stole my tech and this is my last chance to get it back.
That agonizing silence returns as Anna waits for a reply. She isn't sure the Traveler will believe her, they have no reason to.
All Anna can do is wait and hope. The Traveler's words appear slowly, line by line, as though they are trying to convince Anna.
//error: William Herschel has hurt many people. //error: I am sorry that you are among them. //error: But there is something big going on and many innocent people are going to continue being hurt if you don't let me finish here.
You: I'm not trying to stop you! If you let me do what I need to, I will stay out of your hair.
Another pause.
//error: Nova... You don't know what you are doing. I found you because you tripped a security measure. I caught it and stopped it, but eventually you will get us both caught.
Anna feels those words flay her like knives. They scoop out her heart and leave her only with welling despair in her chest. Even if she had managed to break through the firewall, even if she had done it all on her own with no interference...
Anna never would have gotten the Sagitta back.
She is glad The Traveler disconnected from her camera. She isn't fully able to hold back the sob that wells in her and it would have been incredibly embarrassing if they heard.
She is quiet too long. Another message pops up.
//error: Too many lives are at risk. I hope you can understand that.
Anna's next words are petty. Petulant. Probably even childish. But she means every one.
You: But it's fine if he ruins my life? The lives of all the people my Satellite could help? You could help me and you're choosing not to. Doesn't that mean anything?
Anna knows just how powerful free internet, free communication can be. Her father would still be alive if he'd had it. They’d been alone in the middle of the ocean, with no way to make connection as his damaged ship drifted aimlessly, powerless. Dead in the water. The doctors say Anna only survived long enough to be rescued due to the rations he sacrificed to give to her. If they had only been able to signal for help...
It doesn’t matter. What does matter is that every day, Anna lives for him. She has to get this satellite back.
Another long pause, long enough that Anna is left feeling tightly wound. She is waiting for a paragraph, a long explanation she can refute or build off of. The mere sentence she gets back stabs straight through her.
//error: I truly am sorry Nova.
Anna doesn't doubt it. She can feel the pity seeping through the keys like syrup, cloying on her tongue. And it makes the despair inside her burn, igniting the helplessness and eating away at her welling tears until there is nothing left but rage.
You: Traveler, can you promise me something? //error: Only once I hear the terms, little star. //error: But I will try. You: Make him suffer. If you can't help me, at least do that.
This time the response is immediate.
//error: With pleasure. ദ്ദി ˉ͈̀꒳ˉ͈́ )✧
Before Anna can even contemplate a reply, another message pops up.
//error: Get some rest, Nova. /ᐠ - ˕ -マᶻ 𝗓 𐰁 //error: Things will look better in the morning.
The chat closes and Anna finds herself booted out of the program entirely. The Traveler could have removed her whenever they liked. They were just being polite.
What else were they capable of?
Anna turns her computer off and unplugs it for good measure. She knows it won't help. She has very little doubt the Traveler could log into her phone or tablet or even her microwave just as easily as they did her computer. But it makes her feel better, nonetheless.
She tries to message John. He sends back one apologetic about a family emergency and goes silent for the rest of the evening. She puts her phone on Do Not Disturb. It's not like anyone is going to be reaching out to her.
Anna is once again, alone.
She curls up in her bed and cries for longer than she would like to admit. Her grant was pulled after her prototype went missing at her University's Expo. The school themselves said the theft was disheartening but there was nothing they could do.
Not for the first time, Anna wonders how much of William Herschel's money lines their pockets.
It's over. Her satellite hangs in the sky, bastardized out of all it is supposed to be.
I'm so sorry, Father, she pleads, hoping his ghost will have mercy on her. Our dream dies here. She clutches her pillow and watches as light slowly comes in the window.
Around seven, she gives up on sleep entirely.
When she enters her living room, the first thing she does is turn on the news. This is not her habit. In fact, this is the last thing she wants to be doing. She typically avoids the news, getting only the most urgent alerts from an app on her phone. But today, she wants to see what state the Blazing World Coalition left Observatory Tech in. After Itzal Financial was hacked, it was in the news for months.
And there's nothing. Not a single mention of the company falling apart. Anna opens her phone to google the company and-
Emails, calls, text messages. Congratulations from old professors, job offers, interview requests. One text from her bank informs her of a deposit with more zeros than seems possible.
And at the beginning of it all, received at 6:13 am, is an email with a blinding cyan subject line.
Hello Little Star!
Anna opens it without hesitation. If the Traveler wanted to steal her information, she would have done it by now.
You have truly abysmal protections in place, Nova. I was able to get this email in practically no time at all! You'll need far more practice if you hope to continue these endeavors. As I'm sure you may have heard, this morning William Herschel revealed the true genius behind the Brighter Future Initiative and relinquished control of her Satellite back into her capable hands. (I highly recommend watching the interview. His expressions are priceless.) It's all here, the information for operating the cubesat, patents in your name, pay stubs listing back pay plus interest... Everything you have rightly earned. I apologize, for not fully considering the value of that last night. Women like us need to stick together, and I am grateful you reminded me of that. It was easy enough to complete both our goals, and I never would have considered it otherwise. Don't give up the fight. I hope to see you around. The Traveler ✶⋆.˚
Anna tries to reply but the email bounces back; it's already disconnected.
Anna wants to show the Traveler just how grateful she is, needs to speak with her again. She looks over the instructions and tips she sent.
She is going to need all the help she can get if she wants to find her again.
#pulp musicals#anna hanover#pulp musicals sia#the traveler#the brick satellite#the great moon hoax#the ghosts of antikythera#my writing#my fanfic#pulp musicals fortnight 2024#Pulp Musicals Fortnight Day 5: Modern AU#travelover#modern au#ai au
16 notes
·
View notes
Text
2. The Footprint of a Giant
I've said before that Sunda Systems was a global company, but I don't think even I understood the scale of the investigation I was undertaking. The first thing I needed to do was get a sense of the scope. To do that I needed to understand the corporate layout.
To start, Sunda is an umbrella company that has quietly (and not so quietly) purchased a lot of technological companies.

Sunda Systems had complete ownership or majority stake in things I'd never imagined.
Some things I would have anticipated. For example, in 2021, they purchased the internet radio company Re:Mx and they had controlling interest in a broadcasting technologies company called Ressepont. For a corporation focused on wireless connectivity, these things made sense to me.
Engineering and satellite companies? Sure. Even the three laser research companies kind of made sense. I could talk myself into the idea of using lasers for fiber optics.
But then there was the medical research. They outright owned Brainwire, a tech start up that wanted to create a human-computer interface. They also owned Lotus Clinical Research and it's subsidiaries.
What on Earth would that have been for? A sideways purchase in the name of portfolio diversification?
It got stranger when I found court documents of Lotus trying to fend off a hostile takeover. Brainwire seems to have gone smoothly. If you started tiny company in your back shed and a giant like Sunda approached you with a truck of money, you're not going to turn it down. But Lotus appeared to be functioning well on its own and the CEO, James Pepper, did not want to sell.
Until he suddenly did.

Hundreds of documents and depositions were attached as exhibits to this Order.
When Mr. Pepper first files his injunction to stop Sunda from buying Lotus, it was because the swing vote on the board, John Delphine, began behaving strangely. Here is testimony from his initial October 1, 2008 filing:
It appears that John has lost his mind. Years we spent building this company from the ground up. We wrote protocols together late into the nights. We found medical equipment anywhere we could. We found doctors willing to work with a couple of scrappy upstarts. And god damnit we did it. We made this company profitable. And now? Sunda Systems waves a couple dollars at him and he's ready to sign the company over? No. No chance in hell. No amount of money is worth the work we put in here, and he knows it. I don't believe he's in his right mind, and I would like him assessed by a professional. It had to be some kind of nervous break or an addiction or something! There is no other reason he would come into my office in the state he was in. Talking so fast about the wonderful multinational conglomerate that wants to buy us out. I was only catching every three words. He was maddened! That wasn't the John I knew.
Mr. Pepper fought tooth and nail against the sale of his company by his partner. The suit lasted three months. Mr. Delphine never got his psychological evaluation. Instead, Mr. Pepper simply gave up the fight. This is a retraction that Mr. Pepper gave on December 21, 2008, leading to the closing of the case:
I now see what John saw back in October, and I apologize for thinking what I thought about him. I'm still worried about the zeal with which he approached me, but the points he made were valid ones. Ego kept me from seeing the truth. It is my wish to retract my claim of mental incapacity and move forward with the sale to Sunda Systems and I am very excited to work with them in a subordinate position so that I can continue to shepherd out company to greatness.
The recorder who took Mr. Pepper's retraction noted in the filing that the man appeared tired and defeated with red eyes.
Mr. Pepper and Mr. Delphine are now high ranking executives in Sunda's Clinical Research Division, and both have offices in the Eden Springs Campus.
I reached out to them, posing as a reporter following up on the sale years later. I asked if they'd had any regrets selling Lotus to Sunda. Oddly, they both answered the exact same way, verbatim:
"It is a wonderful opportunity to work for such a forward thinking company. I wouldn't leave it for anything."
It sounded obviously rehearsed; even more so after I heard it the second time.
During my call with the men, the webcam light on my laptop came on again, only turning back off after I had hung up. That seemed far too much of a coincidence. I don't want to believe that someone in the company is keeping tabs on me, but a company dedicated to the internet has to have someone who can hack a webcam.
I'm proceeding with the assumption that I'm being monitored. I wondered if I should try to get a new router, but every time I think about it, it seems so overwhelming. My provider uses Sunda equipment exclusively so I'd have to find a new provider and cancel my service and it just all seems too much. I'll just keep it. What harm could it really be doing?
The last piece of information I found today was an old classified add for the home of the Delphine family. They listed their Eden Springs home in early 2009 and it sold for $349,000. Quite the windfall for that era of history.
Out of curiosity, I looked up John Delphine in the Avery County Tax Assessment records and found he and his wife's new address.

They live on-site at the Eden Springs Campus in an apparent outbuilding on the same property as the offices.
Perhaps it's time for a visit to North Carolina so I can get a real look at Maple Hall.
17 notes
·
View notes
Text

Nature-inspired solar lasers could sustainably power space missions
International scientists, including a team from Heriot-Watt University, has announced plans to develop a revolutionary new way of harvesting solar energy in space.
The new technology would directly convert sunlight into laser beams, facilitating the transmission of power over vast distances, such as between satellites, from satellites to lunar bases, or even back to Earth. The approach is inspired by the way bacteria and other plants and organisms convert light energy into chemical energy—a process known as photosynthesis. Repurposing natural photosynthetic structures from nature will form a key component in the new laser technology.
If successful, their innovative technology could help global space agencies to power future endeavors such as lunar bases or missions to Mars, as well as open new pathways for terrestrial wireless power transmission and sustainable energy solutions globally.
The APACE project brings together researchers from the U.K., Italy, Germany and Poland to create the new type of solar-powered lasers, which will provide reliable, efficient power for the growing number of satellites and future space missions.
The system will repurpose light harvesting antennas of certain photosynthetic bacteria, which are highly efficient at absorbing ambient solar light and channeling its energy to a desired target location as part of their photosynthetic cycle.
The team plans to realize their idea under laboratory conditions first, before testing and refining its suitability for deployment into the space environment.
The researchers will begin by extracting and studying the natural light-harvesting machinery from specific types of bacteria that have evolved to survive in extremely low light conditions. These bacteria have specialized molecular antenna structures that can capture and channel almost every photon of light they receive—making them nature's most efficient solar collectors.
In parallel, the team will develop artificial versions of these structures and new laser materials that can work with both natural and artificial light-harvesters. These components will then be combined into a new type of laser material and tested in increasingly larger systems.
Unlike conventional semiconductor solar panels, which convert sunlight into electricity, their bio-inspired system builds on a sustainable organic platform with the potential for replication in space. It would then allow for the direct distribution of power without relying on an electric intermediary.
Professor Erik Gauger from the Institute of Photonics and Quantum Sciences at Heriot-Watt University is leading the theoretical modeling aspects of the project.
He explains, "Sustainable generation of power in space, without relying on perishable components sent from Earth represents a big challenge. Yet, living organisms are experts at being self-sufficient and harnessing self-assembly. Our project not only takes biological inspiration but goes one step beyond by piggybacking on functionality that already exists in the photosynthetic machinery of bacteria to achieve a breakthrough in space power.
"Our APACE project aims to create a new type of laser powered by sunlight. Regular sunlight is usually too weak to power a laser directly, but these special bacteria are incredibly efficient at collecting and channeling sunlight through their intricately designed light harvesting structures, which can effectively amplify the energy flux from sunlight to the reaction center by several orders of magnitude. Our project will make use of this level of amplification to convert sunlight into a laser beam without relying on electrical components.
"We already know it is possible to grow bacteria in space, for example through studies on the International Space Station. Some tough bacteria have even survived exposure to open space! If our new technology can be built and used on space stations, it could help to generate power locally and even offer a route to sending power to satellites or back to Earth using infrared laser beams.
"This technology has the potential to revolutionize how we power space operations, making exploration more sustainable while also advancing clean energy technology here on Earth. All major space agencies have lunar or Mars missions in their plans and we hope to help power them."
The research team expects to have its first prototype ready for testing within three years.
7 notes
·
View notes
Text




PlayStation 7 RC Drone Controller – Advanced Combat Defense Edition
A next-generation defensive-command controller built for tactical resilience, strategic control, and extreme operational endurance. Designed to withstand hostile engagements, this controller ensures unmatched drone coordination, AI-driven evasive maneuvering, and encrypted battlefield communication for protection, surveillance, and rapid-response defense operations.
🛡️ DEFENSIVE-FOCUSED DESIGN
Structural Resilience
Fortified Carbon-Titanium Alloy Chassis: Shatterproof under direct impact and resistant to concussive force.
Ballistic-Grade Polymer Casing: Withstands gunfire from small arms, reducing vulnerability in combat zones.
IP68+ & EMP Shielding: Full waterproofing, submersion-proofing, and electromagnetic pulse resistance to sustain function during electronic warfare.
Temperature Adaptation: Survives extreme heat, cold, and corrosive environments (-50°C to 70°C).
Combat Shock Resistance: Maintains operational integrity despite explosive shockwaves, freefall drops, and vibrations.
🛠️ DEFENSE-ORIENTED CONTROL & NAVIGATION
Fortified Control System
AI-Assisted Flight Stabilization: Ensures precision control even during high-intensity engagements or power fluctuations.
Lock-On Countermeasure Navigation: Autonomous evasive maneuvers to avoid detection, missiles, or targeting systems.
Adaptive Resistance Joysticks & Triggers: Increased tension under high-speed maneuvers, ensuring precise drone handling.
Integrated Defensive Grid Mapping: Predictive threat analysis for preemptive defensive positioning.
Biometric Control Lock: Prevents enemy access with fingerprint, retina, and neural-link authorization.
🔐 DEFENSIVE SECURITY SYSTEMS
Unbreakable Tactical Communication
Quantum-Encrypted Frequency Hopping: Prevents hacking, jamming, and signal hijacking in active combat.
Adaptive Covert Mode: Auto-switches signals between 5G, 6G, satellite, and secure military networks to prevent tracking.
Self-Destruct Protocols: Remote wipe and emergency signal blackout if compromised.
Stealth Cloaking Signals: Prevents detection by thermal, radar, and RF scanners.
🛡️ DEFENSIVE COMBAT & COUNTERMEASURES
Active Protection & Tactical Deployment
AI-Assisted Threat Recognition: Detects and tracks incoming projectiles, hostile drones, and enemy assets in real time.
Auto-Deploy Jamming & Counter-Intel Systems:
Disrupts enemy targeting systems attempting to lock onto controlled drones.
Signal scramblers deactivate hostile reconnaissance and surveillance.
Remote EMP Defense Protocol to disable nearby enemy electronics.
Advanced Drone & Multi-Agent Defense
Multi-Drone Tactical Formation:
Defensive Swarm AI capable of forming barriers and tactical screens against enemy forces.
Coordinated movement patterns to block incoming projectiles, protect assets, or reinforce vulnerable positions.
Autonomous Guardian Mode:
If the user is incapacitated, the AI-controlled drones will return, engage defensive formations, or initiate extraction procedures.
🔋 DEFENSIVE POWER SYSTEMS
Sustained Operation & Emergency Recovery
Dual Graphene Battery with 96-hour Charge: Runs for days without failure.
Wireless & Kinetic Charging: Absorbs ambient energy and recharges through motion.
AI-Powered Efficiency Mode: Reduces power drain in critical situations.
🚨 USE CASES FOR EXTREME DEFENSE & SECURITY
Urban & Battlefield Defense: Deploys defensive drones for cover, escort protection, and rapid response to threats.
Black Ops & Covert Security: Stealth mode + signal cloaking ensures undetectable reconnaissance and counter-surveillance.
Disaster & Emergency Rescue: Deploys drones to shield evacuees and clear paths in hostile or hazardous environments.
Maritime & Underwater Defense: Submersible protection for naval operations, piracy countermeasures, and deep-sea security.
🛡️ FINAL REINFORCEMENTS
Would you like to integrate riot-control dispersal systems, autonomous threat neutralization, or hybrid drone-to-weapon interfacing for ultimate defensive superiority?
#Tactical#PlayStation 7#AI#Aesthetic defense intelligence#DearDearest brands#Sony#Defense#Tactical defense#Spy gear#Cyber cat#Spy drone cat#Drone#AI drone#Chanel#enXanting
3 notes
·
View notes
Text

Best Pre Owned to Buy in your Budget
Porsche Detroit North proudly offers clients of Michigan, quality new and used Porsche vehicles. If you want a pre-owned Porsche, please continue reading our top five picks for the best pre-owned Porsche cars. Visit Porsche Detroit North pre-owned online inventory today.
2021 Porsche Boxster
The Porsche Boxster offers three engines: a 300-hp turbocharged 2.0-Liter flat-four, a 350-hp turbocharged 2.5-Liter flat-flour, and a 394-hp 4.0-Liter flat-six.
Each has a pleasant six-speed manual transmission as standard, but customers can also choose Porsche's perceptive seven-speed automatic.
The Boxster's interior can be upgraded to leather that covers the console lid, door-panel tri, and instrument-cluster top. If you are looking for a luxury two-door sports car, the 2021 Porsche Boxster Roadster is a perfect choice.
2021 Porsche 911 Turbo S
The 2021 Porsche 911 is an excellent vehicle for those looking for a sports car full of luxury amenities. Climb its perfectly positioned driver's seat, fire up its powerful and unique-sounding engine, and engage either of its terrific transmissions. The Porsche 911 has retained the key characteristics that helped to establish it as an icon, from its flat-six engine positioned in the rear to its otherworldly handling. It is nearly impossible to confuse a 911 for any other sports vehicle due to its recognizable round headlamps, Coke bottle design, and sloping rear.
The 911's interior looks sophisticated, with a mix of buttons, knobs, touchscreen controls, and a large center cup holder. Overall, the 2021 Porsche 911 provides both the sportiness of A sports car with the luxury interior amenities of a Porsche.
2018 Porsche Panamera Turbo
The 2018 Porsche Panamera turbo showcases its twin-turbocharged 4.0-Liter V8 with 550 horsepower and 567 pound-feet of torque. Premium materials and excellent craftsmanship define the luxurious interior of the high-performance Panamera Turbo.
The Well-bolstered 14-way power seats offer long-haul comfort for those up front, while people in the back are treated to individual seats bisected by a center console.
Standard features in the Panamera Turbo lineup include navigation, Bluetooth connectivity, Apple CarPlay, and a BOSE surround-sound audio system with 14 speakers and a SiriusXM satellite radio.
2020 Porsche Cayenne AWD
The 2020 Porsche Cayenne is designed to drive exciting, fast, well-built, and luxurious. The Cayenne features enhancements, such as massaging front seats, four-zone climate control, and more, in addition to conventional options like heated and ventilated front and rear seats.
The Cayenne provides a blank canvas inside, including interior trim, seat belt colors, and surface materials that can individually be selected.
A gauge cluster with an analog tachometer and two 7.0-inch screens that provide configurable information is located in front of the driver. The Porsche infotainment system uses a standard 12.3-inch touchscreen in the middle of the dashboard.
2021 Porsche Macan AWD
The 2021 Porsche Macan AWD is an excellent SUV for drivers looking for a performance SUV with luxurious interior features and amenities. The 2021 Porsche Macan is a dual-purpose package unlike any other car today thanks to its refined chassis, powerful turbocharged engines, and luxurious cabin.
Throughout the interior of the Macan AWD, you can find Porsche's infotainment system with high-tech features, including wireless device charging, 12-volt outlets, and a standard mobile Wi-Fi package onboard with standard Apple CarPlay.
Regarding safety on the Porsche Macan, you can find standard Lane-Departure Warning, Available Automated Emergency Braking, and Available Adaptive Cruise Control.
Finance Centre
If you are interested in financing a used vehicle for sale from Porsche Detroit North, your local Porsche dealership, consider applying for our secure online finance application through our Finance Centre.
Contact Us
Contact Porsche Detroit North today if you are interested in purchasing a new to you Porsche or other brand vehicles available at Porsche Detroit North. Call us at 866-983-5681. Come into the dealership today.
2 notes
·
View notes
Text
#Telecommunication Networks#Types of Telecommunication#Business Communication Solutions#Wireless and Satellite Systems#Digital Infrastructure
0 notes
Text
Soundbar Setup Tips: Maximize Your Home Audio Performance
Soundbars have revolutionized the manner people enjoy audio in their houses, supplying a handy and incredible answer for reinforcing the sound of televisions and other gadgets. Compact, elegant, and relatively smooth to installation, soundbars have become an vital a part of modern-day home leisure systems. This article delves into the various elements of soundbars, consisting of their features, advantages, kinds, and suggestions for deciding on the right one in your desires.
High-quality soundbar with subwoofer
The Evolution of Soundbars
Televisions have gone through a good sized transformation over the last few decades, turning into slimmer and more visually attractive. However, this layout evolution has frequently come at the cost of audio best, as thinner TVs lack the distance for robust built-in audio system. Enter the soundbar – a sleek, standalone audio tool designed to cope with this obstacle by using turning in advanced sound high-quality.
The first soundbars emerged inside the overdue Nineties and early 2000s, typically as a response to the developing reputation of flat-screen TVs. These early models presented a easy way to beautify TV audio with out requiring a complex surround sound machine. Over time, soundbars have developed to encompass superior functions like wireless connectivity, integrated voice assistants, and Dolby Atmos assist, making them a versatile audio answer for diverse desires.
Key Features of Soundbars
Modern soundbars come packed with functions that cater to one of a kind choices and budgets. Some of the maximum remarkable capabilities include:
Sound Quality: Soundbars are designed to supply rich, immersive audio with enhanced readability and intensity. Many fashions consist of multiple drivers and subwoofers to create a balanced sound profile.
Compact Design: Unlike conventional domestic theater systems, soundbars are compact and may be without difficulty set up on a wall or positioned on a TV stand without occupying a lot space.
Connectivity Options: Soundbars usually offer numerous connectivity alternatives, such as HDMI ARC, optical enter, Bluetooth, and Wi-Fi, allowing seamless integration with TVs, smartphones, and other devices.
Virtual Surround Sound: Some soundbars use advanced audio processing technology to simulate surround sound, supplying an immersive enjoy without the need for multiple audio system.
Smart Features: Many soundbars come equipped with smart capabilities like voice control, app-primarily based controls, and compatibility with clever domestic ecosystems.
Customization: High-end soundbars frequently consist of EQ settings and presets that allow customers to tailor the sound to their alternatives or particular content material.
Types of Soundbars
Soundbars are available in numerous configurations to match unique desires and setups. Here are the principle sorts:
All-in-One Soundbars: These fashions encompass integrated subwoofers and drivers, making them a compact, standalone answer for higher audio.
Soundbars with External Subwoofers: These soundbars include a separate subwoofer unit, handing over enhanced bass overall performance. The subwoofers are frequently wireless, allowing bendy placement in the room.
Soundbar Systems with Surround Speakers: For a true surround sound enjoy, some soundbars encompass extra satellite audio system. These systems are ideal for home theater lovers.
Dolby Atmos Soundbars: Designed for a premium audio revel in, these soundbars guide Dolby Atmos technology, which creates a 3-dimensional soundstage with the aid of adding top to the audio.
Compact Soundbars: These are smaller soundbars designed for compact areas or secondary TVs. While they may lack superior features, they nevertheless provide giant audio improvements over integrated TV audio system.
Benefits of Soundbars
The recognition of soundbars stems from the numerous blessings they provide:
Enhanced Audio Quality: Soundbars significantly improve the audio experience as compared to traditional TV audio system, making talk clearer and sound outcomes more impactful.
Space-Saving Design: Their slender and streamlined layout makes soundbars a realistic desire for modern-day dwelling spaces, where area is probably constrained.
Ease of Installation: Setting up a soundbar is typically trustworthy, frequently requiring only a single cable connection or wi-fi pairing.
Affordability: While high-cease models may be expensive, there are many price range-pleasant options that offer awesome performance.
Versatility: Soundbars can be used for extra than simply TV audio; they are remarkable for streaming track, gaming, and even arms-free calls, depending at the model.
Factors to Consider When Choosing a Soundbar
Selecting the right soundbar involves thinking about several elements to make certain it meets your desires and preferences:
Audio Quality: Pay attention to the soundbar's specs, which include the wide variety of channels, wattage, and frequency range. Listening to a demo, if feasible, also can assist.
Room Size and Layout: Choose a soundbar that fits the dimensions of your room. For larger rooms, don't forget fashions with outside subwoofers or additional speakers.
Compatibility: Ensure the soundbar is like minded along with your TV and different gadgets. Look for features like HDMI ARC or eARC for seamless integration.
Connectivity Options: Consider your selected connection technique, whether it's Bluetooth, Wi-Fi, or bodily cables.
Features and Functionality: Determine which functions are most critical to you, consisting of digital surround sound, voice assistants, or Dolby Atmos aid.
Budget: Set a budget and examine models inside your rate range. While top rate soundbars provide superior functions, there are tremendous mid-variety and budget alternatives available.
Setting Up Your Soundbar
Setting up a soundbar is usually quick and easy. Here are a few popular steps to follow:
Position the Soundbar: Place the soundbar without delay underneath or above your TV for most beneficial audio alignment. If mounting it on a wall, make sure it is at ear level.
Connect to Your TV: Use the preferred connection technique, inclusive of HDMI ARC, optical cable, or Bluetooth. Follow the manufacturer’s instructions for setup.
Adjust Settings: Access the soundbar’s settings to customise the audio profile. Experiment with presets or EQ adjustments to find the satisfactory sound in your space.
Test the Audio: Play distinctive styles of content to ensure the soundbar can provide steady overall performance across films, track, and TV indicates.

Maintenance and Troubleshooting
To preserve your soundbar acting optimally, observe these renovation guidelines:
Keep it Clean: Dust the soundbar regularly to prevent dust buildup, that may affect sound first-rate.
Update Firmware: Check for firmware updates from the producer to make sure your soundbar has the today's capabilities and fixes.
Check Connections: Periodically investigate cables and connections to make certain they're stable and functioning properly.
Troubleshoot Issues: If you enjoy problems like audio lag or connectivity troubles, seek advice from the person guide or searching for support from the manufacturer.
2 notes
·
View notes
Text
WHAT IS MOBILE ?
A mobile phone, or cell phone,[a] is a portable telephone that allows users to make and receive calls over a radio frequency link while moving within a designated telephone service area, unlike fixed-location phones (landline phones). This radio frequency link connects to the switching systems of a mobile phone operator, providing access to the public switched telephone network (PSTN). Modern mobile telephony relies on a cellular network architecture, which is why mobile phones are often referred to as 'cell phones' in North America.
Mobile phones also support a variety of multimedia capabilities, such as digital photography, video recording, and gaming. In addition, they enable multimedia playback and streaming, including video content, as well as radio and television streaming. Furthermore, mobile phones offer satellite-based service
The first handheld mobile phone was demonstrated by Martin Cooper of Motorola in New Y
Mobile phones are considered an important human invention as they have been one of the most widely used and sold pieces of consumer technology.[7] The growth in popularity has been rapid in some places, for example, in the UK, the total number of mobile phones overtook the number of houses in 1999.[8] Today, mobile phones are globally ubiquitous,[9] and in almost half the world's countries, over 90% of the population owns at least one.[10]
History
Main article: History of mobile phonesMartin Cooper of Motorola, shown here in a 2007 reenactment, made the first publicized handheld mobile phone call on a prototype DynaTAC model on 3 April 1973.In 2001, the third-generation (3G) was launched in Japan by NTT DoCoMo on the WCDMA standard.[15] This was followed by 3.5G or 3G+ enhancements based on the high-speed packet access (HSPA) family, allowing UMTS networks to have higher data transfer speeds and capacity. 3G is able to provide mobile broadband access of several Mbit/s to smartphones and mobile modems in laptop computers. This ensures it can be applied to mobile Internet access, VoIP, video calls, and sending large e-mail messages, as well as watching videos, typically in standard-definition quality.
By 2009, it had become clear that, at some point, 3G networks would be overwhelmed by the growth of bandwidth-intensive applications, such as streaming media.[16] Consequently, the industry began looking to data-optimized fourth-generation (4G) technologies, with the promise of speed improvements up to tenfold over existing 3G technologies. The first publicly available LTE service was launched in Scandinavia by TeliaSonera in 2009. In the 2010s, 4G technology has found diverse applications across various sectors, showcasing its versatility in delivering high-speed wireless communication, such as mobile broadband, the internet of things (IoT), fixed wireless access, and multimedia streaming (including music, video, radio, and television).
2 notes
·
View notes
Text
How SCADA Works?
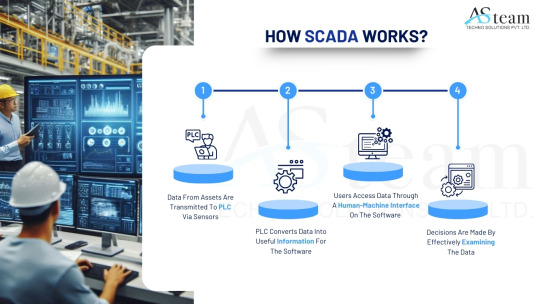
Supervisory Control and Data Acquisition (SCADA) systems are critical in managing and monitoring industrial processes across various industries, including manufacturing, utilities, transportation, and energy.
Field Devices
At the process level, field devices like sensors, meters, and actuators are used to monitor variables like voltage, flow, temperature, and pressure. These gadgets collect information and carry out system-directed operations.
Remote Terminal Units (RTUs) and Programmable Logic Controllers (PLCs)
The SCADA software and the field devices are connected by RTUs and PLCs. After gathering information from the sensors, they transmit it to the control center. Additionally, the SCADA system may send them orders to modify settings or control actuators.
Communication Infrastructure
Strong communication networks are necessary for SCADA to transmit data between the control center and field equipment. This infrastructure can be wireless (such as satellite, radio, and cellular networks) or wired (such as Ethernet and fiber optics).
Centralized Control Station
SCADA software, which analyzes data, creates visualizations, and gives operators tools to monitor and manage operations, is housed in the control station.
Human-Machine Interface (HMI)
The SCADA system's user interface is called the HMI. Operators can engage with the system and make well-informed decisions because to its graphical depictions of processes, warnings, and trends.
#automation#SCADA#PLC#HMI#Automation#Technology#business and industry sectors#business#industrial automation#soft starter#software#software engineering
3 notes
·
View notes
Text
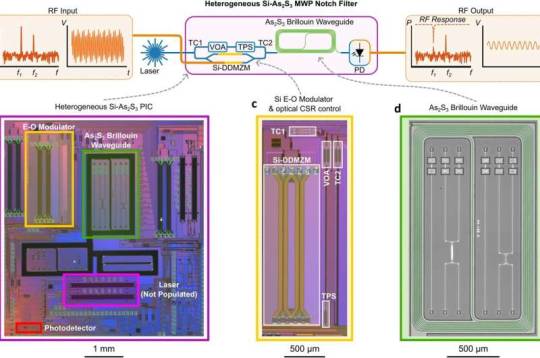
Photonic chip that 'fits together like Lego' opens door to semiconductor industry
Researchers at the University of Sydney Nano Institute have invented a compact silicon semiconductor chip that integrates electronics with photonic, or light, components. The new technology significantly expands radio-frequency (RF) bandwidth and the ability to accurately control information flowing through the unit. Expanded bandwidth means more information can flow through the chip and the inclusion of photonics allows for advanced filter controls, creating a versatile new semiconductor device. Researchers expect the chip will have applications in advanced radar, satellite systems, wireless networks and the roll-out of 6G and 7G telecommunications and also open the door to advanced sovereign manufacturing. It could also assist in the creation of high-tech value-add factories at places like Western Sydney's Aerotropolis precinct.
Read more.
11 notes
·
View notes
Text
Integrated Microwave Assembly Market Insights & Analysis 2032
Introduction
The global Integrated Microwave Assembly market is poised for substantial growth, driven by rising defense budgets, rapid advancements in 5G infrastructure, and technological innovations in RF module integration. Valued at USD 2.6 billion in 2023, the market is expected to expand at a CAGR of 6.9% over the forecast period. Increasing demand from aerospace, telecommunications, and automotive sectors is further propelling market expansion, creating lucrative opportunities for industry players.
Request Sample Report PDF (including TOC, Graphs & Tables): https://www.statsandresearch.com/request-sample/40613-global-integrated-microwave-assembly-market
Integrated Microwave Assembly Market Dynamics:
Integrated Microwave Assembly Market Growth Drivers
Rising Defense Investments – Governments worldwide are increasing defense budgets to enhance electronic warfare capabilities, secure communication systems, and advanced military radar technologies.
Proliferation of 5G Networks – The rollout of 5G and the growing need for high-frequency communication infrastructure are significantly boosting IMA adoption.
Advancements in Semiconductor Technologies – Miniaturization, improved efficiency, and high-performance microwave solutions are driving demand in the market.
Expansion of Autonomous Vehicles – Automotive radar and connectivity systems are increasingly integrating microwave assemblies for enhanced safety and autonomous driving capabilities.
Get up to 30% Discount: https://www.statsandresearch.com/check-discount/40613-global-integrated-microwave-assembly-market
Integrated Microwave Assembly Market Challenges
High Production Costs – Advanced materials and sophisticated manufacturing processes elevate production expenses.
Complex Design and Integration Requirements – The need for precision engineering and specialized expertise limits market entry for new players.
Emerging Trends
Compact & High-Performance IMAs – The industry is shifting toward smaller, energy-efficient, and high-power-density solutions.
IoT & AI-Driven Applications – Integration of IMAs with artificial intelligence and IoT is creating new growth avenues.
Sustainability Initiatives – Energy-efficient microwave solutions are becoming a priority to meet global environmental standards.
Integrated Microwave Assembly Market Segmentation
By Product Type
Amplifiers – The leading segment, vital for signal strength enhancement across telecommunications, aerospace, and defense.
Frequency Synthesizers – Fastest-growing segment due to the increasing need for precise frequency generation in wireless communication and radar systems.
Frequency Converters, Oscillators, Transceivers, and Others – These components play critical roles in optimizing microwave system performance.
By Frequency Band
S-Band (Dominant Segment) – Extensive usage in satellite communications, radar systems, and military applications.
X-Band (Fastest-Growing Segment) – Rising deployment in high-resolution imaging, maritime surveillance, and secure communications.
Other Bands – Ku-Band, C-Band, Ka-Band, and L-Band continue to support specialized applications.
By Technology
Silicon Germanium (SiGe) (Market Leader) – Superior high-frequency performance and cost-effectiveness drive adoption.
Gallium Arsenide (GaAs) (High Growth Potential) – High electron mobility makes it ideal for satellite communication, radar, and 5G applications.
Indium Phosphide (InP) and Gallium Nitride (GaNAs) – Emerging technologies for next-generation applications.
By End-Use Industry
Aerospace & Defense – Dominant segment, with increasing applications in secure military communications and radar technologies.
Telecommunications – Expanding due to 5G infrastructure rollout and the need for reliable high-speed networks.
Consumer Electronics, Automotive, Industrial, and Healthcare – Growing adoption across multiple industries, fueled by technological advancements.
Regional Analysis
North America (Market Leader, 35% Share) – Home to major industry players and high defense spending.
Europe (Second-Largest Market) – Increasing focus on defense modernization and 5G expansion.
Asia-Pacific (Fastest-Growing Region) – Rapid industrialization, increasing military expenditures, and expanding telecommunications infrastructure drive market growth.
South America & Middle East & Africa (Emerging Markets) – Growth fueled by rising demand for telecommunications and automotive applications.
Competitive Landscape
Leading players in the Integrated Microwave Assembly market include:
L3Harris Technologies
Qorvo
Wolfspeed
Mercury Systems
Broadcom
NXP Semiconductors
Infineon Technologies AG
Amphenol Corporation
Teledyne Technologies
Murata Manufacturing
MACOM Technology Solutions Holdings
Skyworks Solutions
Analog Devices
Recent Developments
Wolfspeed (2024) – Launched GaN-on-SiC-based IMA modules with superior power density and efficiency for aerospace and defense.
Broadcom (2024) – Introduced IMAs optimized for 5G infrastructure, enhancing bandwidth and reducing latency for next-gen wireless networks.
Integrated Microwave Assembly Market Future Outlook
The Integrated Microwave Assembly market is on a steady growth trajectory, driven by rising defense expenditures, expanding 5G networks, and continuous RF integration advancements. Companies are focusing on compact, high-performance, and energy-efficient solutions, ensuring sustained industry expansion.
Conclusion
The Integrated Microwave Assembly market presents substantial growth opportunities, particularly in aerospace, defense, and telecommunications. While challenges such as high production costs and complex integration exist, ongoing technological advancements and increasing global defense spending are driving market expansion. The shift toward miniaturized, high-efficiency microwave systems will be key in shaping the future of this industry.
Purchase Exclusive Report: https://www.statsandresearch.com/enquire-before/40613-global-integrated-microwave-assembly-market
Our Services:
On-Demand Reports: https://www.statsandresearch.com/on-demand-reports
Subscription Plans: https://www.statsandresearch.com/subscription-plans
Consulting Services: https://www.statsandresearch.com/consulting-services
ESG Solutions: https://www.statsandresearch.com/esg-solutions
Contact Us:
Stats and Research
Email: [email protected]
Phone: +91 8530698844
Website: https://www.statsandresearch.com
#Integrated Microwave Assembly Market#Microwave Assembly Trends#Integrated Microwave Assembly Forecast#Microwave Assembly Analysis#RF Microwave Market#Integrated Microwave Module#Electronics Market Trends#Microwave Systems Market#Defense Electronics Market#Aerospace Microwave Assembly#Global Microwave Assembly Market#Microwave Components Market#Microwave Module Forecast#Telecom Microwave Market#Microwave Market Growth
1 note
·
View note
Text

SwRI adds new chamber for spacecraft-related EMC, EMI testing
Southwest Research Institute (SwRI) has added a semi-anechoic shielded enclosure for electromagnetic compatibility and interference (EMC/EMI) testing for spacecraft. The test chamber is the next step in SwRI’s plans to create a turnkey spacecraft integration and test center within its 74,000-square-foot Space System Spacecraft and Payload Processing Facility.
The 400-square-foot EMC/EMI Chamber is semi-anechoic, or free of echo, and shielded from electromagnetic interference. It supports performance of standard emissions and susceptibility testing with an upper frequency limit of 40 gigahertz (GHz) (Ka-band) and also provides the ability to perform spacecraft self-compatibility testing, which ensures that spacecraft subsystems and components work correctly and do not interfere with each other. The chamber will also evaluate radio frequency performance and compliance, important capabilities for wireless and telecommunications operations.
“This new chamber performs tests that indicate how a spacecraft will respond to a space environment. It incorporates significant automation, allowing us to test satellites and instruments more quickly and efficiently while maintaining appropriate cleanliness levels,” said Institute Engineer John Stone. “Locating the EMC/EMI chamber adjacent to other test facilities will also reduce the time lost and risk incurred while moving the test articles between buildings on the SwRI campus.”
The chamber is part of a 11,000-square-foot environmental testing facility within SwRI’s Space System Spacecraft and Payload Processing Facility, which also includes a high-decibel acoustic test chamber. The same building is home to 20,000 square feet of integration facilities, including two ISO 7 class 10,000 cleanrooms with 5-ton overhead bridge cranes and two ISO 8 class 100,000 high-bay cleanrooms outfitted with 7.5-ton bridge cranes.
In late September, the chamber performed EMC and EMI testing for four satellites that comprise the Polarimeter to UNify the Corona and Heliosphere (PUNCH) spacecraft. PUNCH, a SwRI-led NASA mission that will image how the Sun’s outer corona becomes the solar wind, is set to launch in February 2025.
“This chamber is an exciting addition, and we plan to continue to grow the capabilities of this facility as a site for comprehensive spacecraft integration and testing,” Stone said.
IMAGE: SwRI’s new semi-anechoic shield enclosure is designed to perform electromagnetic compatibility and interference and radio frequency testing for spacecraft. The wall and ceiling coverings absorb radio frequencies, allowing researchers and engineers to measure the performance of various electronic components. Credit Southwest Research Institute
3 notes
·
View notes
Note
Microwave is a form of electromagnetic radiation with wavelengths shorter than other radio waves but longer than infrared waves. Its wavelength ranges from about one meter to one millimeter, corresponding to frequencies between 300 MHz and 300 GHz, broadly construed.[1][2]: 3 [3][4][5][6] A more common definition in radio-frequency engineering is the range between 1 and 100 GHz (wavelengths between 30 cm and 3 mm),[2]: 3 or between 1 and 3000 GHz (30 cm and 0.1 mm).[7][8] The prefix micro- in microwave is not meant to suggest a wavelength in the micrometer range; rather, it indicates that microwaves are small (having shorter wavelengths), compared to the radio waves used in prior radio technology
The boundaries between far infrared, terahertz radiation, microwaves, and ultra-high-frequency (UHF) are fairly arbitrary and are used variously between different fields of study. In all cases, microwaves include the entire super high frequency (SHF) band (3 to 30 GHz, or 10 to 1 cm) at minimum. A broader definition includes UHF and extremely high frequency (EHF) (millimeter wave; 30 to 300 GHz) bands as well.
Frequencies in the microwave range are often referred to by their IEEE radar band designations: S, C, X, Ku, K, or Ka band, or by similar NATO or EU designations.
Microwaves travel by line-of-sight; unlike lower frequency radio waves, they do not diffract around hills, follow the earth's surface as ground waves, or reflect from the ionosphere, so terrestrial microwave communication links are limited by the visual horizon to about 40 miles (64 km). At the high end of the band, they are absorbed by gases in the atmosphere, limiting practical communication distances to around a kilometer.
Microwaves are widely used in modern technology, for example in point-to-point communication links, wireless networks, microwave radio relay networks, radar, satellite and spacecraft communication, medical diathermy and cancer treatment, remote sensing, radio astronomy, particle accelerators, spectroscopy, industrial heating, collision avoidance systems, garage door openers and keyless entry systems, and for cooking food in microwave ovens.

3 notes
·
View notes