#Wireless Gateway
Explore tagged Tumblr posts
Text
ZigBee Smart Hub | Tuya ZigBee 3.0 Wireless Gateway for Smart Life

ZigBee Smart Hub: Wireless Gateway for Tuya ZigBee 3.0 Devices. Enhance your smart home automation with this Smart Life-compatible hub. Supports multiple ZigBee devices, ensuring seamless connectivity and efficien. Visit us- https://www.ahmsmarthomes.com.au/product/zigbee-gateway-hub/
0 notes
Link
#pioneering marketdigits consulting and advisory private limited#in-flight wi-fi service market#in-flight wi-fi service#wireless lan controllers#wireless hotspot gateways
0 notes
Text
The Role of LoRaWAN Gateways in IoT: Connecting Devices Seamlessly

A LoRaWAN Gateway is a device that facilitates long-range wireless communication between IoT devices and centralized servers. It receives data from LoRaWAN devices using LoRa modulation and forwards it to network servers via a backhaul connection, typically using Ethernet, Wi-Fi, or cellular networks. Lansitec Outdoor LoRaWAN Gateway is an ideal product for IoT commercial deployment. Its modularity and customization options allow for flexibility when deploying a solution.
For More:
#iot#lansitec#lora#lorawan#technology#IoT Devices#LoRaWAN Devices#LoRaWAN Gateway#Outdoor LoRaWAN Gateway#Lansitec#Lansitec Outdoor LoRaWAN Gateway#wireless#IoT Network#LoRaWAN Network
0 notes
Text

ESP32 Programming - Classical CAN to Bluetooth Gateway
In this post, I present a CAN to Bluetooth gateway based on the ESP32 processor. The ESP32 module provides all necessary ports, i.e., a CAN Bus controller plus transceiver and a Bluetooth connection. The code receives CAN data frames, converts them into an ASCII string and transmits the string per Bluetooth. It also allows to send an ASCII string representing a CAN data frame to be transmitted into the network.
1 note
·
View note
Text
Application of Gateway in Smart Factory
In a smart factory, a gateway plays a crucial role in connecting various devices, systems, and networks together to enable seamless communication and data exchange.
1. Device Integration: Gateways act as intermediaries between different devices and protocols, allowing them to communicate with each other. They can integrate diverse devices such as sensors, actuators, machines, and controllers, regardless of their communication protocols or standards. This enables interoperability and facilitates centralized control and monitoring of the factory floor.
2. Data Aggregation and Analysis: Gateways collect data from multiple devices and sensors within the factory and aggregate it for further analysis. They can preprocess and filter the data before transmitting it to the cloud or a central server. This data aggregation helps in real-time monitoring, predictive maintenance, and optimization of manufacturing processes.
3. Protocol Translation: Smart factories often employ various communication protocols, such as Modbus, OPC UA, MQTT, or Ethernet/IP, which may not be compatible with each other. Gateways can bridge the gap between these protocols, translating the data between them and ensuring seamless communication across different systems and devices.
4. Security and Access Control: Gateways provide a secure entry point to the factory's network infrastructure. They can implement security measures such as firewall protection, encryption, and authentication to safeguard the factory's data and prevent unauthorized access. Gateways also enable access control by managing user permissions and restricting access to critical systems and data.
5. Edge Computing: Gateways can perform edge computing tasks by running specific applications or algorithms locally, near the devices or sensors. This reduces latency and bandwidth requirements by processing data at the edge of the network, enabling real-time decision-making and reducing dependency on cloud services.
6. Remote Monitoring and Control: Gateways enable remote monitoring and control of factory operations. By connecting to the internet or a private network, they allow managers and operators to access real-time data, receive alerts, and remotely control devices or processes. This capability enhances operational efficiency, reduces downtime, and enables proactive maintenance.
7. Scalability and Flexibility: Gateways provide a scalable and flexible architecture for smart factories. They can easily accommodate new devices, sensors, or systems by adding or configuring new gateways. This scalability allows the factory to adapt to changing requirements and integrate new technologies without disrupting the existing infrastructure.
Overall, gateways are essential components in a smart factory, enabling seamless connectivity, data integration, security, and control. They play a vital role in transforming traditional manufacturing facilities into intelligent, efficient, and interconnected environments.

0 notes
Text
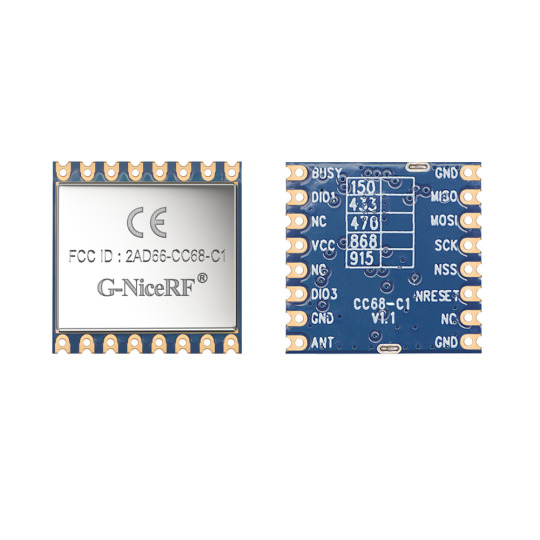
RF Transmitter and Receiver: Key Components in Wireless Communication
RF (Radio Frequency) transmitters and receivers are fundamental components in modern wireless communication systems. These components play a pivotal role in enabling various wireless technologies, from mobile phones to Wi-Fi routers, to operate seamlessly. In this article, we will explore the significance of RF transmitter and receiver in wireless communication and delve into their essential functions and applications.
RF Transmitter: Sending Signals Wirelessly
An RF transmitter is a crucial element in any wireless communication system. It is responsible for converting electrical signals into radio waves that can travel through the air and be received by compatible devices. RF transmitters are found in a wide range of applications, including radio broadcasting, remote control systems, and data transmission.
One of the key features of an RF transmitter is its ability to modulate the carrier signal with the information to be transmitted. This modulation process allows the transmitter to encode data, voice, or other forms of information onto the radio waves. The modulated signal is then amplified and broadcasted through an antenna.
In modern wireless technologies, such as Bluetooth and Wi-Fi, RF transmitters are the driving force behind the wireless connectivity that allows devices to communicate with each other over short or long distances.
RF Receiver: Capturing and Decoding Signals
On the receiving end, the RF receiver is responsible for capturing the transmitted radio waves, demodulating them, and converting them back into electrical signals that can be processed by electronic devices. RF receivers are integral components in devices like car radios, GPS systems, and satellite television receivers.
The receiver's demodulation process is crucial because it extracts the original information from the modulated carrier signal. This process allows the receiver to recover the transmitted data, audio, or video signal accurately. In essence, the RF receiver acts as the gateway for converting radio waves into usable information.
Applications of RF Transmitters and Receivers:
Wireless Communication: RF transmitters and receiver is the backbone of wireless communication system, enabling devices to transmit voice, data, and multimedia content over the airwaves. They are vital for mobile phones, two-way radios, and wireless Internet connections.
Remote Control Systems: Many remote control devices, including TV remotes, garage door openers, and toy controllers, rely on RF transmitters and receivers to send and receive signals.
Telemetry and Data Acquisition: In industries like agriculture and environmental monitoring, RF technology is used to collect data wirelessly from remote sensors and devices.
Security Systems: Wireless security systems, such as home alarms and surveillance cameras, use RF transmitter and receiver for communication between sensors and control panels.
Conclusion:
RF transmitters and receivers are the unsung heroes of the wireless world, making it possible for us to communicate, control devices remotely, and access information seamlessly. As technology continues to advance, these essential components will continue to evolve and play a pivotal role in our increasingly connected world. Whether it's sending a text message, streaming a video, or unlocking your car with a remote, RF transmitter and receiver is at the heart of it all, making our lives more convenient and interconnected.
For details, please click:
Or click:https://www.alibaba.com/product-detail/G-NiceRF-CC68-C1-160mW-433MHz_1600914212665.html?spm=a2747.manage.0.0.78e071d2L4s02Q
For consultation, please contact NiceRF (Email: [email protected])
0 notes
Text

5G INTERNAL PCB ANTENNA
https://eteily.com/59-5g-internal-antenna
5G Internal Antenna
This internal antenna is specially designed for home and office use. It supports 5G network connectivity and works well with your existing router or modem. Our 5G internal antenna is the perfect companion to all your 5G devices.
#5G internal antenna#pcb antenna#5g antenna#radio frequency antenna#Best RF Solution Provider#RF Antenna Suppliers#Manufacturer of RF Antenna#rf antenna manufacturers in india#RF Antenna Manufacturer#RF Antenna Exporters#RF Antenna Latest Price#Wireless HF Antenna#RF Antenna Companies in India#Wholesaler of RF Antenna#RF Antenna Amplifier#RF Antenna Module#2.45 GHz Antenna Module#High Performance RF#Antennas for LoRa and Sigfox#Antennas for Cellular Gateways#Cellular External Antenna supplier#5G / LTE Cellular External Antenna manufacturer#Cellular 5G Antenna Solutions#Cellular Antenna Guide for 5G#LTE/5G Cellular External Antennas#Cellular Antennas 5G#Cellular Antennas LTE#Cellular Antennas CBRS#Cellular Antennas 2G#Cellular Antennas 3G
1 note
·
View note
Text
20 notes
·
View notes
Text
i know this looks like nothing to those who don't know but for me this is the culmination of my slaving away for 3 days lmao the homebrew i'm running, gbarunner3, is a virtual machine that uses the GBA hardware in DS Mode to run GBA games with a higher layer of customization and access to traditional DS hardware. an example of something similar that comes to mind is Nintendont, the gamecube loader for Wii. Technically speaking, the vWii on the Wii U is also this concept, albeit underutilized.
anyway, it's intended to run ROMs off the SD card exclusively. Meaning that it cannot run actual cartridges. I wanted to use my pokemon carts alongside gbarunner3's wireless emulation to facilitate wireless adapter features without having the more expensive GBA hardware and peripherals, for an example.
i spent the last few days learning a bit of how the DS hardware and the codebase works, and trying to implement the option of using actual hardware than only ROMs off the SD card.
the DS only has 4mb of memory! and most GBA ROMs are between 8mb-32mb. how gbarunner3 gets the ROM loaded, is that it has 1mb worth of cached ROM loaded at a time and dynamically loads a ROM region based on when the game's code needs to access it. learning how to deal with memory in the context of the SLOT2 data bus in a codebase designed around SD card caching...
It was very annoying! I had no way to debug anything other than forcing a crash to tell when I got a certain result. it effectively was trial and error for hours and hours of blind crash debugging. the dev of gbarunner3 uses an IS-Nitro development kit to do his debugging. I didn't have that lmao
this is me oversimplifying everything incredibly because it's very hard to describe but i'm very proud of it. i'm sure it looks like nothing from an outsider's perspective though but i think it opens the gateway for some cool features that you'd otherwise have to use digital-only ROMs for.
I have a lot more to do but the fact i got this far on a whim is really neat!
37 notes
·
View notes
Text
18:18 GMT
[18:17] ARKAngel has started a call.
The incoming call alert had woken him up. Miles sat up with a start and nearly fell on his face as he climbed out of bed. He scrambled to the computer and clicked on the green ‘accept’ button displayed on the screen. It was a video call, with Maria’s face showing signs of fatigue and stress as she was manipulating the touch controls of a console. From what he could gather, it seemed as if her tablet was docked to the console.
“I’m sorry, I fell asleep.” Miles said, rubbing the back of his head. Maria’s attention turned to the tablet and her eyes widened.
“I need your help!” Maria said frantically. “I’m trying to get this escape pod open for Shadow but the passwords that Grandfather gave me aren’t working!”
“Escape pod?” Miles’ ears raised. “Is something happening on the ARK? Why aren’t you leaving through the flight deck?”
“They’ve taken it over.” Maria whispered.
“Who’s ‘they’?”
“I don’t know! They seem to be Federation military though. They just came and started shooting. They’ve killed anyone that’s tried to put up a fight. I managed to get to the panic room at the hospital level and got in contact with Grandfather. He sent Shadow and told me that Shadow had to be podded out.”
“They must have changed the passwords. There has to be some sort of low-level emergency system though. Who the Hell password locks an escape pod system?!” He watched as Maria pressed something on her tablet’s screen.
[18:19] ARKAngel would like to hand over device control.
A window popped up on his screen showing a mirror of Maria’s tablet. He clicked on an on-screen control to return to the main interface. Then he pulled up the tablet’s terminal, entering a command to get a list of network interfaces. There were two active, the wireless network that Maria was connected to, but also a connection to the console she was working at by the physical link. Miles looked at the node address that the tablet had from that link, then the gateway address. He left the terminal and opened her tablet’s browser, entering that gateway address.
He was greeted with the same login page that Maria was trying to get through. GRobotnik was filled in for the username field and the password field had a red border around it.
“You tried his credentials and your own?” Miles asked, the call was still ongoing.
“Yes, neither of those worked!” Maria said.
“I’m going to try something. If the system administrator here was an idiot, this might work. If they weren’t, well then I’ll have to think of something else.” Miles took a deep breath and replaced the input on the login page. He filled out his username of MPrower and the password he had used when he was on the ARK last. The password prompt’s border turned green and then the pod control system came up.
“What did you do?” Maria’s eyes widened.
“Logged in as myself.” The fox raised his ears. “I guess the administrator didn’t zero out my account, and I’d have to guess that your grandfather’s account was locked out as well as your own for some reason. Why they didn’t lock mine out as well, hard to say but it worked.” Maria knelt down out of sight.
“Come on Shadow!” She came back into view, the black and red mobian hedgehog partially visible as she walked him towards the pod.
“I can’t leave you here!” Shadow protested.
“They won’t hurt me.” Maria placated. “They’re here for you. They have to be. This way you’ll be safe.”
“Maria? Where are you sending him?” Miles asked.
“Anywhere that will be safe.” Maria’s voice came back out of frame.
“Crap. Hold on. It’s GPS programmed, isn’t it?” He took over the pod control system, getting a world map. On instinct, he scrolled with his mouse wheel until the airfield near High Wycombe was in view. He clicked on the tarmac and then the ‘Program’ button. “Is he loaded in?”
“Yes!” Maria moved back to the control station and he clicked on the ‘Pod Close’ button. Then he clicked on the ‘Launch Prep’ button. A lever popped up on the console. “What’s that supposed to be?”
“I don’t know. I have a ‘Launch’ button, maybe it’s an emergency backup. Are you ready?” Miles asked.
“Do it!” Maria said. The fox heard muffled gunshots and then a door opening. He saw Maria clutch the lever and then heard a male Ameri-Can voice yelling at her.
“Get your hands off that lever!”
His fingers tensed on the mouse as he moved towards the ‘Launch’ button. Right at that moment, the tablet mirror unexpectedly quit. Then he noticed Maria’s Harmony status was showing as offline.
“Damn it!” Miles lept out of his chair and scrambled out of his bedroom. He went into the hallway and skidded into the kitchen. No sign of his mother there. Looking out the living room window, he noticed that her car was gone but his father’s was there. His shoes thumped against the floor as he went for his father’s home office, seeing the light streaming under the door.
“Dad!” Miles thumped his fist against the door. Urgent footsteps could be heard, followed by the door unlocking.
“What is it?” Group Captain Artair Prower asked, raising his ears. “Is it your mother?”
“No!” Miles raised his eyes up. “Dad, Space Colony ARK is under attack. The Federation sent soldiers of some kind up there! Maria called me, she’s trying to get Shadow out of there but something’s happened! I heard shooting before she got kicked offline. You have to do something!”
“It didn’t sound like a drill?” Artair asked.
“No!” Miles grabbed his father’s hand. “Dad! She needs help!”
“All right. Calm down, son. This is going to be tricky. It’s a Federation space station, but perhaps-” He gestured for Miles to follow him in and picked up his desk phone, punching out a number.
“Jules, Artair. I’m coming back to headquarters. Call your brother. Tell him he needs to get our ambassador in Ottawa to contact the President, if not doing so himself. There’s something going wrong on Space Colony ARK, shots have been fired.” Miles could hear the surprise and apprehension coming from the hedgehog on the other line. “Yes, I know, it’s a major deviation from the chain of command but Sir Charles is the bloody Prime Minister. Get to it!”
Artair hung the phone up, grabbed his lanyard and slung it around his neck before getting his phone and keys. “I want you to grab that call recording and put it on your tablet and phone. You’re coming with me to headquarters, Miles.”
#miles prower#maria robotnik#tails the fox#tailsmaria#vulpinroid#sonic the hedgehog#sonic fanfiction#tailsmari
5 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text

Finality Girl and the Void: Chapter 6
Chapter Cover Art. J finally begins her ascent to the surface, and catches a glimpse of that purple dawn she'd thought a desperate fantasy.
[NULL]
[NULL]
[NULL]
Each deathly knell clanged its way through J's creaking systems. Her teeth clattered with each pulse. She winced for fear that one of them would be the push that would finally irreversibly shatter her. She had already lost everything in the world; all that was left to lose was herself, and the immediate past was hardly encouragement that the trend would stop before that. Had she crossed the stars, filled the boiled-off oceans of long-gone planets with blood and oil, entombed herself in amber dreams to escape it all, just to get punted into this abyssal darkness? Was she to rot here forever, alone and remembered with contempt if she was not completely forgotten?
[NULL]
[NULL]
[NULL]
J would never know true solitude as long as she had that signal for company. It came from her wireless I/O port, the gateway used by that thing whenever it wanted to torment her, or order her about, or check in on how the others were doing, or chat about inanities in that faux cheery tone, that stolen voice, it loved to 'comfort' her with. That much was clear. The intent, if there was any intent behind it, was unknown. It did not follow the standard protocols, but this was a very non-standard situation. The message, if indeed it was a message, was unprecedented, but it was in good company with everything that had happened recently.
With everything that had seemed to happen recently. J had long since learned that almost nothing could be taken as a given when She was involved. A team of plucky rebels confronting the big bad and miraculously pulling out a victory was the plot of any number of low-end throwaway stories. The sort that N teared up over. Perhaps this was all a test, or another prank upon J: give her a shoddy reason to hope, coax her into taking the bait, then impale her upon reality once more, laughing at the desperation required to fall for such an obvious ploy.
But J had seen worlds die before. It never took this long. And even if J was in an untouched shard, planets did not go quietly into the night. There should have been some sign, some cosmic roar from imploding earth, quaking from the death throes of a tottering atlas, to mark the planet's passing. There was nothing. An altogether different kind of 'null' from the one she had been expecting. Could the impossible have truly happened? The thing was not gone, could not be gone. It was a bottomless wellspring of malevolence: out of spite and contempt, if nothing else, it would find a way to survive. J was certain of that. Then again, certainty had proved a poor guide for navigating recent events.
Was the ping addressed to her? An attack? A warning? A call for assistance? A defiant boast of survival? A mocking reminder of the inevitable outcome of the fight above? All, or none of the above? And it was from Cyn, right?
[NULL]
[NULL]
[NULL]
Never send to know for whom the ping [NULL]s, it [NULLS] for thee, J.
It would be so simple to deactivate the port. A mere flick of a boolean variable would do it. The feat could be done entirely in software; no need for a hardware (or, given that thing's taste in interior décor, wetware) modification that would just heal its way back into sickness. As one of Her modifications, the physical receiver was permanently integrated into J's body. Or rather, given that she always revived with it, it was part of the very definition of J. Of her platonic essence, perfect and perpetual, residing in a realm beyond all mortal things. The truth, the inevitable truth, against which her past lives had been nothing but hollow lies.
J had the necessary permissions to deactivate it, and had had them since the start of her new servitude. She had been granted the keys so that she could, if she wanted, shut the door and hold it fast against Her many-handed emanations. J had wisely dodged the trap. After the first few attempts, of course. Could a moth be blamed for flying into the first flame it saw? It was ingenious, really: provide the means of freedom and the poisoned apple of knowledge, then smirk and taunt as J shrank back even from partial 'salvation'. There was no prisoner so secured as one confined within and by the workings of their own mind.
J's was a very formidable mind. And with minimal consumption of oil, automatically enforced by conservation protocols, the remaining life expectancy would make for...a rather prolonged term of imprisonment. And if that were not enough, it would culminate in J discovering exactly what happened to an oil-starved Disassembly Drone. In the early days after their conversion, they had tried to resist the new urges and fight back against the absurdity of the new tasks they had been handed. The result had been a steady descent into primal madness, with them only regaining a sense of themselves amid piles of shattered corpses. But down here, in this emptiness, even that outlet would be unavailable.
Cyn was gone, maybe. The more things changed, the more they stayed the same. Should J fall for the obvious trap and stay down here forever, frozen by fear, regret, and self-doubt, or should she turn off that annoying port and turn toward the surface, risking stumbling into a hidden trap? She had no hard evidence that there even was a hidden trap, but if there was hard evidence, it would hardly be 'hidden'. The overwhelming weight of evidence suggested that something monumental had happened, up to and possibly including the total elimination of Cyn. Foolish as she was, J could hardly resist the urge to hope for something, just this little, just this once...
#murder drones fanart#md fanart#murder drones art#murder drones fanfiction#fanfiction#ao3 fanfic#md j#murder drones j
4 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes
Text
All I can say, is for myself, I try to NEVER underestimate a liar and a cheater.
3 notes
·
View notes
Text

LoRa communication Module
youtube
:
. https://www.newegg.com/p/2A3-00UG-000J9
youtube
.
.

. https://www4.comp.polyu.edu.hk/~csyqzheng/papers/LoRaJamming-INFOCOM21.pdf
2 notes
·
View notes