#Web Authentication API
Text
Why Web Security Matters: Why 2FA SMS OTP API Is Vital for Protection

In today’s digital world, web security has become more critical than ever as cyber threats or attacks are increasing day by day. Safeguarding sensitive information is a top priority for businesses and individuals alike. One of the most effective ways to enhance online security is by implementing 2FA (Two-Factor Authentication), particularly through SMS OTP API. Integrating SMS OTP API into your web and mobile applications is essential for your web and mobile app protection.
Why Web Security Important and How It Is Compromise
Robust Web security is the foundation of any online platform, protecting user data, financial transactions, and personal information from unauthorized access. However, there are many reasons for web security breaches. Read the mention below:
1. Weak Passwords: Many users rely on simple, easily guessable passwords, making it easier for hackers to gain unauthorized access to accounts. Don't give a chance to hackers; always use strong passwords and change them on an after-some day.
2. Phishing Attacks: Cyberattackers frequently use phishing emails or websites to trick users into revealing their passwords and other sensitive information. Be aware of fraud Emails and messages.
3. Outdated Software: Using outdated or unpatched software can expose vulnerabilities that hackers can exploit to breach web security.
4. Insufficient Security Measures: Relying solely on passwords without additional layers of security leaves systems vulnerable to attacks.
5. Human Error: Mistakes like sending sensitive information over unsecured networks or clicking on malicious links can also lead to security breaches.
Why 2FA SMS OTP API Is Essential for Online Security
2FA SMS OTP API plays a vital role in strengthening web security by addressing these common vulnerabilities. Here’s how it works:
1. User Authentication: After entering a password, users receive a one-time password (OTP) via SMS, which they must enter to complete the login process. This ensures that even if a password is compromised, unauthorized access is prevented without the OTP.
2. 2FA Authentication: Implementing 2FA Authentication through SMS OTP for web and mobile applications significantly reduces the risk of unauthorized access. It adds an extra layer of security, requiring both something the user knows (password) and something they have (OTP).
3. Ease of Use: SMS OTP services are user-friendly and do not require additional hardware or software. Users receive the OTP directly on their mobile devices, making it a convenient and efficient way to secure online transactions and logins.
4. Versatility: Whether securing a web or mobile app, MyOTP.APP offers a flexible solution that integrates seamlessly into existing systems. This makes it a versatile choice for businesses of all sizes. Check out the SMS OTP Service plan today!
Protecting Your Users and Business
Adopting 2FA SMS OTP API for your businesses can protect your users from potential threats and enhance the overall security of their platforms. This not only builds trust with customers but also helps comply with regulatory requirements for data protection.
Protecting Your Users and Business
Adopting 2FA SMS OTP API for your businesses can protect your users from potential threats and enhance the overall security of their platforms. This not only builds trust with customers but also helps comply with regulatory requirements for data protection.
In conclusion, as web security becomes increasingly vital, integrating 2FA with SMS OTP API is crucial in protecting your digital assets. Whether for web or mobile applications, SMS OTP services provide an effective, easy-to-use solution that significantly enhances security, ensuring your users’ data remains safe from unauthorized access. Visit us today and explore our services with ready-to-use code in any language. MyOtp.App is a trustworthy SMS OTP Service provider visit us today.
#2FA Online Security#2FA Web Security#Web Security Matters#2FA SMS OTP API#SMS OTP Services 2FA#multi-factor authentication
0 notes
Text
Django REST Framework: Authentication and Permissions
Secure Your Django API: Authentication and Permissions with DRF
Introduction
Django REST Framework (DRF) is a powerful toolkit for building Web APIs in Django. One of its key features is the ability to handle authentication and permissions, ensuring that your API endpoints are secure and accessible only to authorized users. This article will guide you through setting up authentication and permissions in DRF, including examples and…
#custom permissions#Django API security#Django JWT integration#Django REST Framework#DRF authentication#Python web development#token-based authentication
0 notes
Text
The Legal Effects of Employer Screening Without Using Criminal Record Lookup

In the modern workplace, employers must run extensive background checks on all new hires. This shields the business from possible legal repercussions while also assisting in ensuring worker safety. A Criminal Record Lookup is a vital component of background checks. We'll talk about the legal ramifications of not doing criminal record checks for hiring purposes in this blog article, as well as why it's so important for businesses to do so.
Let's first clarify what a criminal record check is. It is the procedure to obtain a person's criminal history that is accessible to the general public. Arrests, convictions, and sentences for both felonies and misdemeanors may be included in this data. Thanks to technological advancements, businesses may now obtain this data using Background Verification APIs, which improves the process' accuracy and efficiency.
Now, you might be wondering why running a criminal background check is so important. The possible legal repercussions of not doing so hold the key to the solution. Hiring someone with a criminal record exposes a firm to one of the biggest dangers, particularly if the illegal activity includes violence or fraud. The corporation may be held accountable for negligent hiring if a criminal history employee harms others or commits a crime there. A legal claim known as "negligent hiring" holds an employer accountable for the deeds of its workers if they knew or should have known about their risky inclinations.
On the other hand, running a Public Criminal Records check can also shield businesses from legal action. The employer won't be held accountable if a criminal recorded employee commits a crime outside of the workplace that has nothing to do with their duties. The criminal record check demonstrates that the business takes appropriate precautions to guarantee the security of its workers and clients.
Every company's hiring procedure has to include a criminal background check, since workplace safety and legal compliance are critical in today's society. To learn more call Authenticate at +1 833-283-7439 or visit:- www.authenticate.com!
#Background Checks for Landlords#Web API Identity Authentication#Identity Check API#Criminal Background Check#Background Check API Free
0 notes
Text
0 notes
Text
Working with APIs and Fetching Data from External Sources
View On WordPress
#API authentication#APIs#Best practices#Data Integration#Data Security#External data sources#JSON#Request handling#Web development#XML
0 notes
Text
Easy-To-Use and Developer Friendly Identity Verification Solutions

Identity verification is something people take very seriously nowadays. Whether you're trying to verify a person's identity or have someone verify yours, it's important to find a reliable and secure way of doing it. Authenticate's Identity Verification software gives you this ability. By using the newest technology, we've made something that's both highly effective and affordable. Authenticate is a verification platform that assists in the verification of individuals via a variety of tests; the SDK allows businesses to create custom applications that use these various tests. We currently provide solutions for the iOS and Android platforms, through an SDK and an open API.
Whether you need effective and economical IRS Identity Verification, Photo Id Verification API, or Open Source Background Check API solutions, Authenticate is the right choice for you. We offer a variety of APIs to help businesses verify people's identities and protect themselves from fraud. Our authenticating solutions can be used to verify a person's identity with any number of databases including LinkedIn, social media profiles, and more. Our APIs are scalable, so you can use them for large-scale operations without compromising security or data integrity.
We have the best solutions in the industry and we use state-of-the-art technology to make our services as efficient as possible. We offer a variety of options to fit your needs including user-friendly interfaces and adaptable pricing models. There are many reasons why you might need a personal background check service. You may need to confirm the identity of a potential employee or contractor, or you may be looking for an open-source background check solution to help you Verify Identity of someone who wants to use your services. Whatever the case, Authenticate can help you get what you need from an identity verification service. You can learn more about the various solutions we offer and make an order online at https://authenticate.com/or call on our customer service line at +1 833-283-7439!
#Authenticate#Web Security#Id Verification#Identity Authentication#Photo Id Verification API#Public Criminal Records
0 notes
Note
Hi! I’m a student currently learning computer science in college and would love it if you had any advice for a cool personal project to do? Thanks!
Personal Project Ideas
Hiya!! 💕
It's so cool that you're a computer science student, and with that, you have plenty of options for personal projects that can help with learning more from what they teach you at college. I don't have any experience being a university student however 😅
Someone asked me a very similar question before because I shared my projects list and they asked how I come up with project ideas - maybe this can inspire you too, here's the link to the post [LINK]
However, I'll be happy to share some ideas with you right now. Just a heads up: you can alter the projects to your own specific interests or goals in mind. Though it's a personal project meaning not an assignment from school, you can always personalise it to yourself as well! Also, I don't know the level you are, e.g. beginner or you're pretty confident in programming, if the project sounds hard, try to simplify it down - no need to go overboard!!

But here is the list I came up with (some are from my own list):
Personal Finance Tracker
A web app that tracks personal finances by integrating with bank APIs. You can use Python with Flask for the backend and React for the frontend. I think this would be great for learning how to work with APIs and how to build web applications 🏦
Online Food Ordering System
A web app that allows users to order food from a restaurant's menu. You can use PHP with Laravel for the backend and Vue.js for the frontend. This helps you learn how to work with databases (a key skill I believe) and how to build interactive user interfaces 🙌🏾
Movie Recommendation System
I see a lot of developers make this on Twitter and YouTube. It's a machine-learning project that recommends movies to users based on their past viewing habits. You can use Python with Pandas, Scikit-learn, and TensorFlow for the machine learning algorithms. Obviously, this helps you learn about how to build machine-learning models, and how to use libraries for data manipulation and analysis 📊
Image Recognition App
This is more geared towards app development if you're interested! It's an Android app that uses image recognition to identify objects in a photo. You can use Java or Kotlin for the Android development and TensorFlow for machine learning algorithms. Learning how to work with image recognition and how to build mobile applications - which is super cool 👀
Social Media Platform
(I really want to attempt this one soon) A web app that allows users to post, share, and interact with each other's content. Come up with a cool name for it! You can use Ruby on Rails for the backend and React for the frontend. This project would be great for learning how to build full-stack web applications (a plus cause that's a trend that companies are looking for in developers) and how to work with user authentication and authorization (another plus)! 🎭
Text-Based Adventure Game
If you're interested in game developments, you could make a simple game where users make choices and navigate through a story by typing text commands. You can use Python for the game logic and a library like Pygame for the graphics. This project would be great for learning how to build games and how to work with input/output. 🎮
Weather App
Pretty simple project - I did this for my apprenticeship and coding night classes! It's a web app that displays weather information for a user's location. You can use Node.js with Express for the backend and React for the frontend. Working with APIs again, how to handle asynchronous programming, and how to build responsive user interfaces! 🌈
Online Quiz Game
A web app that allows users to take quizzes and compete with other players. You could personalise it to a module you're studying right now - making a whole quiz application for it will definitely help you study! You can use PHP with Laravel for the backend and Vue.js for the frontend. You get to work with databases, build real-time applications, and maybe work with user authentication. 🧮
Chatbot
(My favourite, I'm currently planning for this one!) A chatbot that can answer user questions and provide information. You can use Python with Flask for the backend and a natural language processing library like NLTK for the chatbot logic. If you want to mauke it more beginner friendly, you could use HTML, CSS and JavaScript and have hard-coded answers set, maybe use a bunch of APIs for the answers etc! This project would be great because you get to learn how to build chatbots, and how to work with natural language processing - if you go that far! 🤖

Another place I get inspiration for more web frontend dev projects is on Behance and Pinterest - on Pinterest search for like "Web design" or "[Specific project] web design e.g. shopping web design" and I get inspiration from a bunch of pins I put together! Maybe try that out!
I hope this helps and good luck with your project!

#my asks#resources#programming#coding#studying#codeblr#progblr#studyblr#comp sci#computer science#projects ideas#coding projects#coding study#cs studyblr#cs academia
176 notes
·
View notes
Text

Thousands of Corporate Secrets Were Exposed, and This Researcher Uncovered Them All 🔍🔓
Bill Demirkapi, a freelance security researcher, has discovered a significant amount of corporate secrets left exposed online, revealing major security risks ⚠️. Since 2021, Demirkapi has been employing creative techniques to sift through vast data sources, uncovering developer secrets like passwords, API keys, and authentication tokens that could be exploited by cybercriminals 💻🔑. At the Defcon security conference, he presented his findings, which included over 15,000 developer secrets embedded in software, providing access to sensitive systems such as Nebraska’s Supreme Court and Stanford University’s Slack channels 🏛️📊.
Demirkapi’s investigation also uncovered a common problem with dangling subdomains, identifying 66,000 websites vulnerable to attacks like hijacking 🕵️♂️💥. High-profile websites, including one belonging to The New York Times, were among those at risk 📈📰. By leveraging unconventional datasets, Demirkapi was able to spot thousands of overlooked security flaws, demonstrating the need for innovative approaches in cybersecurity 🔍🔐.
However, fixing these vulnerabilities proved to be a difficult task. While some companies, like OpenAI, collaborated with Demirkapi to revoke exposed secrets, others, such as Amazon Web Services and GitHub, were less responsive ⚙️🔄. Demirkapi had to create alternative methods to report the exposed data effectively. His research highlights the critical need to explore large data sources for security weaknesses, suggesting that there are still many untapped resources that could help bolster cybersecurity efforts on a broader scale 🌐🔍.
#accounting#academia#b&w#astrophotography#biology#100 days of productivity#ao3#digital art#astronomy#art#breaking news#black and white#books#comics#cars#crafts#canon#doodle#bodybuilding#diy#design#drawing#education#ecommerce#entrepreneur#economy#food#fashion#football#film
2 notes
·
View notes
Text
Do You Want Some Cookies?
Doing the project-extrovert is being an interesting challenge. Since the scope of this project shrunk down a lot since the first idea, one of the main things I dropped is the use of a database, mostly to reduce any cost I would have with hosting one. So things like authentication needs to be fully client-side and/or client-stored. However, this is an application that doesn't rely on JavaScript, so how I can store in the client without it? Well, do you want some cookies?
Why Cookies
I never actually used cookies in one of my projects before, mostly because all of them used JavaScript (and a JS framework), so I could just store everything using the Web Storage API (mainly localstorage). But now, everything is server-driven, and any JavaScript that I will add to this project, is to enhance the experience, and shouldn't be necessary to use the application. So the only way to store something in the client, using the server, are Cookies.
TL;DR Of How Cookies Work
A cookie, in some sense or another, is just an HTTP Header that is sent every time the browser/client makes a request to the server. The server sends a Set-Cookie header on the first response, containing the value and optional "rules" for the cookie(s), which then the browser stores locally. After the cookie(s) is stored in the browser, on every subsequent request to the server, a Cookie header will be sent together, which then the server can read the values from.
Pretty much all websites use cookies some way or another, they're one of the first implementations of state/storage on the web, and every browser supports them pretty much. Also, fun note, because it was one of the first ways to know what user is accessing the website, it was also heavy abused by companies to track you on any website, the term "third-party cookie" comes from the fact that a cookie, without the proper rules or browser protection, can be [in summary] read from any server that the current websites calls. So things like advertising networks can set cookies on your browser to know and track your profile on the internet, without you even knowing or acknowledging. Nowadays, there are some regulations, primarily in Europe with the General Data Privacy Regulation (GDPR), that's why nowadays you always see the "We use Cookies" pop-up in websites you visit, which I beg you to actually click "Decline" or "More options" and remove any cookie labeled "Non-essential".
Small Challenges and Workarounds
But returning to the topic, using this simple standard wasn't so easy as I thought. The code itself isn't that difficult, and thankfully Go has an incredible standard library for
handling HTTP requests and responses. The most difficult part was working around limitations and some security concerns.
Cookie Limitations
The main limitation that I stumbled was trying to have structured data in a cookie. JSON is pretty much the standard for storing and transferring structured data on the web, so that was my first go-to. However, as you may know, cookies can't use any of these characters: ( ) < > @ , ; : \ " / [ ] ? = { }. And well, when a JSON file looks {"like":"this"}, you can think that using JSON is pretty much impossible. Go's http.SetCookie function automatically strips " from the cookie's value, and the other characters can go in the Set-Cookie header, but can cause problems.
On my first try, I just noticed about the stripping of the " character (and not the other characters), so I needed to find a workaround. And after some thinking, I started to try implementing my own data structure format, I'm learning Go, and this could be an opportunity to also understand how Go's JSON parsing and how mostly struct tags works and try to implement something similar.
My idea was to make something similar to JSON in one way or another, and I ended up with:
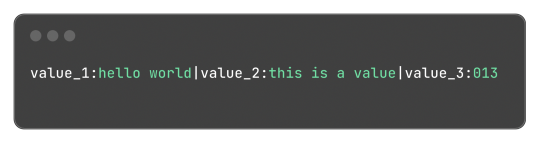
Which, for reference, in JSON would be:
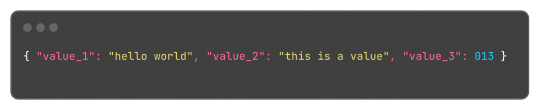
This format is something very easy to implement, just using strings.Split does most of the job of extracting the values and strings.Join to "encode" the values back. Yes, this isn't a "production ready" format or anything like that, but it is hacky and just a small fix for small amounts of structured data.
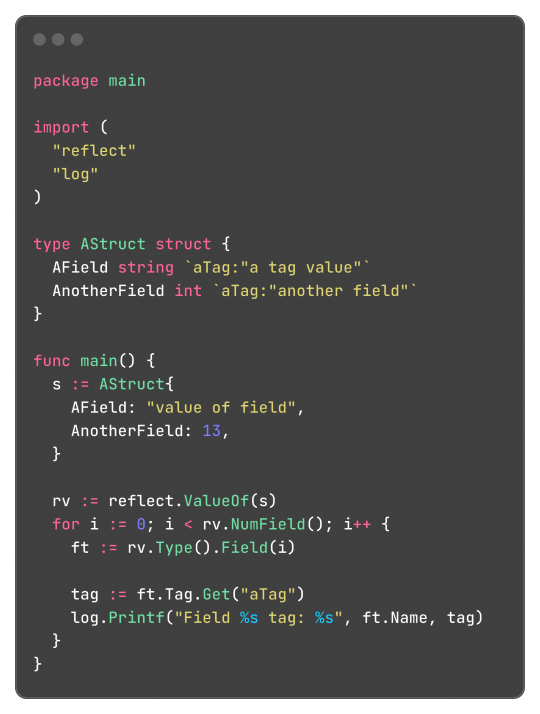
Go's Struct Tags
Go has an interesting and, to be honest, very clever feature called Struct Tags, which are a simple way to add metadata to Structs. They are simple strings that are added to each field and can contain key-value data:
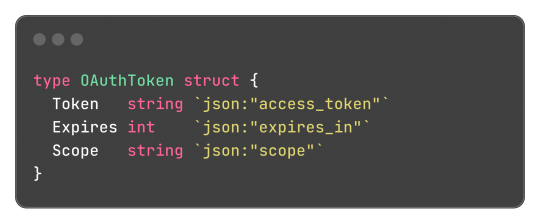
Said metadata can be used by things such the encoding/json package to transform said struct into a JSON object with the correct field names:

Without said tags, the output JSON would be:
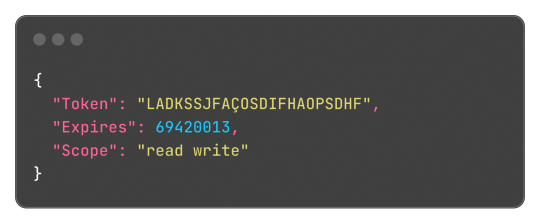
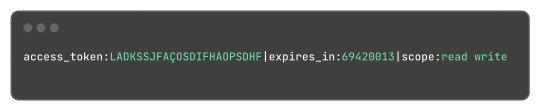
This works both for encoding and decoding the data, so the package can correctly map the JSON field "access_token" to the struct field "Token".
And well, these tokens aren't limited or some sort of special syntax, any key-value pair can be added and accessed by the reflect package, something like this:
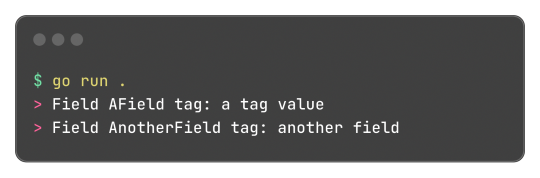
Learning this feature and the reflect package itself, empowered me to do a very simple encoding and decoding of the format where:
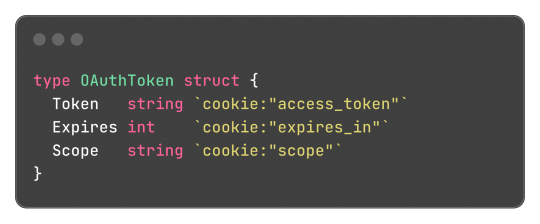
Can be transformed into:
And that's what I did, and the [basic] implementation source code just has 150 lines of code, not counting the test file to be sure it worked. It works, and now I can store structured data in cookies.
Legacy in Less Than 3 Weeks
And today, I found that I can just use url.PathEscape, and it escapes all ( ) < > @ , ; : \ " / [ ] ? = { } characters, so it can be used both in URLs and, surprise, cookie values. Not only that, but something like base64.URLEncoding would also work just fine. You live, and you learn y'know, that's what I love about engineering.
Security Concerns and Refactoring Everything
Another thing that was a limitation and mostly worry about me, is storing access tokens on cookies. A cookie by default isn't that secure, and can be easily accessed by JavaScript and browser extensions, there are ways to block and secure cookies, but even then, you can just open the developer tools of the browser and see them easily. Even though the only way to something malicious end up happening with these tokens are if the actual client end up being compromised, which means the user has bigger problems than just a social media token being leaked, it's better to try preventing these issues nonetheless (and learn something new as always).
The encryption and decryption part isn't so difficult, Go already provides packages for encryption under the crypto module. So I just implemented an encryption that cyphers a string based on a key environment variable, which I will change every month or so to improve security even more.
Doing this encryption on every endpoint would be repetitive, so adding a middleware would be a solution. I already made a small abstraction over the default Go's router (the DefaultMuxServer struct), which I'm going to be honest, wasn't the best abstraction, since it deviated a lot from Go's default HTTP package conventions. This deviation also would difficult the implementation of a generic middleware that I could use in any route or even any function that handles HTTP requests, a refactor was needed. Refactoring made me end up rewriting a lot of code and simplifying a lot of the code from the project. All routes now are structs that implement the http.Handler interface, so I can use them outside the application router and test them if needed; The router ends up being just a helper for having all routes in a struct, instead of multiple mux.HandleFunc calls in a function, and also handles adding middlewares to all routes; Middlewares end up being just a struct that can return a wrapped HandlerFunc function, which the router calls using a custom/wrapped implementation of the http.ResponseWriter interface, so middlewares can actually modify the content and headers of the response. The refactor had 1148 lines added, and 524 removed, and simplified a lot of the code.
For the encryption middleware, it encrypts all cookie values that are set in the Set-Cookie header, and decrypts any incoming cookie. Also, the encrypted result is encoded to base64, so it can safely be set in the Set-Cookie header after being cyphered.
---
And that's what I worked in around these last three days, today being the one where I actually used all this functionality and actually implemented the OAuth2 process, using an interface and a default implementation that I can easily reimplement for some special cases like Mastodon's OAuth process (since the token and OAuth application needs to be created on each instance separately). It's being interesting learning Go and trying to be more effective and implement things the way the language wants. Everything is being very simple nonetheless, just needing to align my mind with the language mostly.
It has been a while since I wrote one of these long posts, and I remembered why, it takes hours to do, but it's worth the work I would say. Unfortunately I can't write these every day, but hopefully they will become more common, so I can log better the process of working on the projects. Also, for the 2 persons that read this blog, give me some feedback! I really would like to know if there's anything I could improve in the writing, anything that ended up being confusing, or even how I could write the image description for the code snippets, I'm not sure how to make them more accessible for screen reader users.
Nevertheless, completing this project will also help to make these post, since the conversion for Markdown to Tumblr's NPF in the web editor sucks ass, and I know I can do it better.
2 notes
·
View notes
Text
Best Practices for Designing RESTful Services
RESTful services are integral to modern web applications, enabling seamless system communication via HTTP. Effective design involves clear resource naming (e.g., /users), correct use of HTTP methods (GET, POST, PUT, DELETE), and plural nouns for collections (/users). Consistent naming conventions, graceful error handling (e.g., 404), versioning (e.g., /v1/users), comprehensive documentation, robust authentication (OAuth, JWT), performance optimization (caching, pagination), scalability design (load balancing, indexing), HATEOAS for dynamic navigation, and API usage monitoring ensure reliability and security. These practices ensure APIs are robust, secure, and user-friendly.
3 notes
·
View notes
Text
🌟 Embracing the Future of Mobile App Development 🌟
Hey Tumblr fam! 📱✨ As we dive into 2024, the world of mobile app development is buzzing with exciting trends that are shaping the way we interact with technology. Here’s a glimpse into what’s on the horizon:
AI & Machine Learning: Apps are getting smarter, thanks to AI and ML, offering personalized experiences and predictive insights.
5G Revolution: With 5G, expect faster speeds and enhanced capabilities for apps, paving the way for immersive AR, VR, and IoT applications.
Cross-Platform Development: Tools like Flutter and React Native make it easier to develop apps that work seamlessly across different devices and platforms.
AR & VR Experiences: From virtual shopping to interactive gaming, AR and VR are transforming how users engage with apps.
Blockchain Integration: Enhancing security and transparency in mobile apps through decentralized solutions.
IoT Connectivity: Apps that connect with smart devices, offering seamless control and monitoring.
Progressive Web Apps (PWAs): Combining the best of web and mobile apps for a responsive and engaging user experience.
Enhanced Mobile Security: Biometric authentication, encryption, and secure APIs to protect user data.
Wearable Tech Integration: Apps that sync with smartwatches and fitness trackers, offering personalized health insights.
Voice-Activated Interfaces: Hands-free interaction with apps through virtual assistants like Siri and Alexa.
💡 Want to dive deeper into the world of mobile app development? Check out this insightful article on Warticles.com. It covers the top 10 key features to consider when choosing the best mobile app builder.
And if you’re thinking of building your own app, explore MageNative- Mobile App Builder on Shopify! It’s packed with features to streamline your development process.

Stay tuned for more updates and insights on technology trends. Follow for the latest in mobile app development and beyond! 📲💬
2 notes
·
View notes
Text
Building a RESTful API with Django REST Framework
Learn how to build a RESTful API with Django REST Framework. This guide covers setup, models, serializers, views, authentication, and best practices for creating efficient APIs
Introduction
Django REST Framework (DRF) is a powerful and flexible toolkit for building Web APIs in Django. It simplifies the process of creating RESTful APIs and provides tools for serialization, authentication, and view handling. This guide will walk you through building a RESTful API with DRF, covering everything from setting up the project to creating endpoints and handling…
#API development#authentication#best practices#Django#Django REST Framework#Python#RESTful API#serialization#web development
0 notes
Text
Protect Your Business with Authenticate's Comprehensive Background Checks & Identity Verification API

In today's digital age, protecting sensitive information and verifying identities is crucial for any business. With the rise of fraud and cybercrime, it has become more important than ever to have reliable and effective tools for background checks and identity verification. This is where Authenticate comes in – your go-to source for an API for Advanced Background Checks and identity verification.
At Authenticate, we understand the importance of keeping your business and customers safe. That's why we offer a comprehensive API and SDK for multi-factor verifications. Our API and SDK are designed to be user-friendly, making it easy for businesses of all sizes to integrate into their existing systems.
Our Advanced Background Checks allow you to perform thorough and efficient background checks on potential employees, clients, or partners. Our advanced technology and algorithms gather information from various sources, including criminal records, credit history, and social media, to provide a detailed report within seconds. This not only saves time but also ensures that you have all the necessary information to make informed decisions.
But that's not all – our API goes beyond just background checks. With our API, you can also perform identity verification, ensuring that the person you are dealing with is who they claim to be. This is especially crucial for businesses in the financial and healthcare industries, where the risk of identity theft and fraud is high.
Our API For Background Checks uses a multi-factor authentication process, which includes document verification, facial recognition, and biometric data matching. This comprehensive approach ensures a high level of accuracy and reliability, giving you peace of mind knowing that your business and customers' information is secure.
Moreover, our API is constantly updated with the latest security protocols, keeping up with the ever-evolving landscape of cyber threats. This means that you can trust Authenticate to provide the most advanced and secure API for all your background check and identity verification needs.
But what sets us apart from other API providers is our commitment to user experience. We understand that not everyone is a tech expert, and that's why our API and SDK are designed to be user-friendly and easily integrated into your existing systems. Our team of experts is also available to provide support and assistance whenever needed.
Authenticate is your one-stop solution for an API for Advanced Background Checks and API Identity Verification. Our API and SDK offer a comprehensive and reliable way to protect your business and your customers. With our easy-to-use interface and constantly updated security protocols, you can trust Authenticate to provide the best background check and identity verification services. Don't wait any longer call us today at +1 833-283-7439 or visit www.authenticate.com.
#Identity Authentication#Identity Verification And Authentication#Irs Identity Verification#Photo Id Verification API#Public Criminal Record Search#Web API Identity Authentication#Identity Background Verification#Background Check API Integration#API For Background Checks
0 notes
Text


18.02.2024 | 16:04
I've started to work on a backend project which was actually a home task for .NET Backend Dev position with aim of developing REST API. Also started to read 'An Introduction to APIs' by Brian Cooksey'(I wish I discovered this while I was still studying, clear explanation for absolute beginners) because I figured that my C# and web skills got rusty a bit since I was using Python for a long time for both Flask projects and autonomous robot development. Application works fine right now, I tested via Postman but wanna try testing via Swagger one more time to learn what it is because the company I applied was using that. I am also planning to apply JWT authentication today and we will see how it will go.
3 notes
·
View notes
Text
20 Best Android Development Practices in 2023
Introduction:
In today's competitive market, creating high-quality Android applications requires adherence to best development practices. Android app development agencies in Vadodara (Gujarat, India) like Nivida Web Solutions Pvt. Ltd., play a crucial role in delivering exceptional applications. This article presents the 20 best Android development practices to follow in 2023, ensuring the success of your app development projects.

1. Define Clear Objectives:
Begin by defining clear objectives for your Android app development project. Identify the target audience, the app's purpose, and the specific goals you aim to achieve. This clarity will guide the development process and result in a more focused and effective application.
2. Embrace the Material Design Guidelines:
Google's Material Design guidelines provide a comprehensive set of principles and guidelines for designing visually appealing and intuitive Android applications. Adhering to these guidelines ensures consistency, enhances usability, and delivers an optimal user experience.
3. Optimize App Performance:
Performance optimization is crucial for user satisfaction. Focus on optimizing app loading times, minimizing network requests, and implementing efficient caching mechanisms. Profiling tools like Android Profiler can help identify performance bottlenecks and improve overall app responsiveness.
4. Follow a Modular Approach:
Adopting a modular approach allows for easier maintenance, scalability, and code reusability. Breaking down your app into smaller, manageable modules promotes faster development, reduces dependencies, and enhances collaboration among developers.
5. Implement Responsive UI Designs:
Designing a responsive user interface (UI) ensures that your app adapts seamlessly to various screen sizes and orientations. Utilize Android’s resources, such as ConstraintLayout, to create dynamic and adaptive UIs that provide a consistent experience across different devices.
6. Prioritize Security:
Android app security is of paramount importance. Employ secure coding practices, authenticate user inputs, encrypt sensitive data, and regularly update libraries and dependencies to protect your app against vulnerabilities and potential attacks.
7. Opt for Kotlin as the Preferred Language:
Kotlin has gained immense popularity among Android developers due to its conciseness, null safety, and enhanced interoperability with existing Java code. Embrace Kotlin as the primary programming language for your Android app development projects to leverage its modern features and developer-friendly syntax.
8. Conduct Thorough Testing:
Testing is crucial to ensure the reliability and stability of your Android applications. Employ a combination of unit testing, integration testing, and automated UI testing using frameworks like Espresso to catch bugs early and deliver a robust app to your users.
9. Optimize Battery Consumption:
Battery life is a significant concern for Android users. Optimize your app's battery consumption by minimizing background processes, reducing network requests, and implementing efficient power management techniques. Android's Battery Optimization APIs can help streamline power usage.
10. Implement Continuous Integration and Delivery (CI/CD):
Adopting CI/CD practices facilitates frequent code integration, automated testing, and seamless deployment. Tools like Jenkins and Bitrise enable developers to automate build processes, run tests, and deploy app updates efficiently, resulting in faster time-to-market and improved quality.
11. Leverage Cloud Technologies:
Integrating cloud technologies, such as cloud storage and backend services, can enhance your app's scalability, performance, and reliability. Services like Firebase offer powerful tools for authentication, database management, push notifications, and analytics.
12. Ensure Accessibility:
Make your Android app accessible to users with disabilities by adhering to accessibility guidelines. Provide alternative text for images, support screen readers, and use colour contrast appropriately to ensure inclusivity and a positive user experience for all users.
13. Optimize App Size:
Large app sizes can deter users from downloading and installing your application. Optimize your app's size by eliminating unused resources, compressing images, and utilizing Android App Bundles to deliver optimized APKs based on device configurations.
14. Implement Offline Support:
Provide offline capabilities in your app to ensure users can access essential features and content even when offline. Implement local caching, synchronize data in the background, and notify users of limited or no connectivity to deliver a seamless user experience.
15. Implement Analytics and Crash Reporting:
Integrate analytics and crash reporting tools, such as Google Analytics and Firebase Crashlytics, to gain insights into user behaviour, identify areas for improvement, and address crashes promptly. This data-driven approach helps in refining your app's performance and user engagement.
16. Keep Up with Android OS Updates:
Stay up to date with the latest Android OS updates, new APIs, and platform features. Regularly update your app to leverage new functionalities, enhance performance, and ensure compatibility with newer devices.
17. Provide Localized Versions:
Cater to a global audience by providing localized versions of your app. Translate your app's content, user interface, and notifications into different languages to expand your user base and increase user engagement.
18. Ensure App Store Optimization (ASO):
Optimize your app's visibility and discoverability in the Google Play Store by utilizing appropriate keywords, engaging app descriptions, compelling screenshots, and positive user reviews. ASO techniques can significantly impact your app's download and conversion rates.
19. Follow Privacy Regulations and Guidelines:
Adhere to privacy regulations, such as GDPR and CCPA, and ensure transparent data handling practices within your app. Obtain user consent for data collection, storage, and usage, and provide clear privacy policies to establish trust with your users.
20. Regularly Update and Maintain Your App:
Continuously monitor user feedback, track app performance metrics, and release regular updates to address bugs, introduce new features, and enhance user experience. Regular maintenance ensures that your app remains relevant, competitive, and secure.
Conclusion:
Adopting these 20 best Android development practices in 2023 will help Android app development companies in India, create exceptional applications. By focusing on objectives, embracing Material Design, optimizing performance, and following modern development approaches, your Android apps will stand out in the market, delight users, and achieve long-term success. Also by partnering with an Android App Development Company in India (Gujarat, Vadodara) you can leverage their expertise.
#Android App development company in India#Android App development agencies in India#Android App development companies in India#Android App development company in Gujarat#Android App development company in Vadodara#Android App development agencies in Vadodara#Android App development agencies in Gujarat#Android App development companies in Vadodara#Android App development companies in Gujarat
7 notes
·
View notes
Text
The Dynamic Role of Full Stack Developers in Modern Software Development
Introduction: In the rapidly evolving landscape of software development, full stack developers have emerged as indispensable assets, seamlessly bridging the gap between front-end and back-end development. Their versatility and expertise enable them to oversee the entire software development lifecycle, from conception to deployment. In this insightful exploration, we'll delve into the multifaceted responsibilities of full stack developers and uncover their pivotal role in crafting innovative and user-centric web applications.

Understanding the Versatility of Full Stack Developers:
Full stack developers serve as the linchpins of software development teams, blending their proficiency in front-end and back-end technologies to create cohesive and scalable solutions. Let's explore the diverse responsibilities that define their role:
End-to-End Development Mastery: At the core of full stack development lies the ability to navigate the entire software development lifecycle with finesse. Full stack developers possess a comprehensive understanding of both front-end and back-end technologies, empowering them to conceptualize, design, implement, and deploy web applications with efficiency and precision.
Front-End Expertise: On the front-end, full stack developers are entrusted with crafting engaging and intuitive user interfaces that captivate audiences. Leveraging their command of HTML, CSS, and JavaScript, they breathe life into designs, ensuring seamless navigation and an exceptional user experience across devices and platforms.
Back-End Proficiency: In the realm of back-end development, full stack developers focus on architecting the robust infrastructure that powers web applications. They leverage server-side languages and frameworks such as Node.js, Python, or Ruby on Rails to handle data storage, processing, and authentication, laying the groundwork for scalable and resilient applications.
Database Management Acumen: Full stack developers excel in database management, designing efficient schemas, optimizing queries, and safeguarding data integrity. Whether working with relational databases like MySQL or NoSQL databases like MongoDB, they implement storage solutions that align with the application's requirements and performance goals.

API Development Ingenuity: APIs serve as the conduits that facilitate seamless communication between different components of a web application. Full stack developers are adept at designing and implementing RESTful or GraphQL APIs, enabling frictionless data exchange between the front-end and back-end systems.
Testing and Quality Assurance Excellence: Quality assurance is paramount in software development, and full stack developers take on the responsibility of testing and debugging web applications. They devise and execute comprehensive testing strategies, identifying and resolving issues to ensure the application meets stringent performance and reliability standards.
Deployment and Maintenance Leadership: As the custodians of web applications, full stack developers oversee deployment to production environments and ongoing maintenance. They monitor performance metrics, address security vulnerabilities, and implement updates and enhancements to ensure the application remains robust, secure, and responsive to user needs.
Conclusion: In conclusion, full stack developers embody the essence of versatility and innovation in modern software development. Their ability to seamlessly navigate both front-end and back-end technologies enables them to craft sophisticated and user-centric web applications that drive business growth and enhance user experiences. As technology continues to evolve, full stack developers will remain at the forefront of digital innovation, shaping the future of software development with their ingenuity and expertise.
#full stack course#full stack developer#full stack software developer#full stack training#full stack web development
2 notes
·
View notes