#2FA Web Security
Explore tagged Tumblr posts
Text
🎮 A reported data breach on May 13, 2025, exposed 89 million Steam accounts, linked to a third-party service, threatening user security. 🎮 Learn about the breach, its risks, and how to safeguard your Steam account from phishing and hijacking 👇🏻
#2FA#data breach#gaming supply chain vulnerabilities 2025#protect Steam account phishing 2025#Steam 2FA codes leak dark web#Steam account security risks 2025#Steam data breach 89 million accounts 2025#Steam Guard setup guide 2025#Steam SMS logs breach risks#Steam Twilio supply chain attack 2025#Steam user data for sale 2025#Twilio denies breach Steam 2025
0 notes
Text
So with the pandora's box of AI being released into the world, cybersecurity has become kind of insane for the average user in a way that's difficult to describe for those who aren't following along. Coding in unfamiliar languages is easier to do now, for better and worse. Purchasable hacking "kits" are a thing on the dark web that basically streamline the process of deploying ransomware. And generative AI is making it much easier for more and more people to obscure their intentions and identities, regardless of their tech proficiency.
The impacts of this have been Really Bad in the last year or two in particular. For example:
(I'm about to link to sources, and you better be hovering and checking those links before clicking on them as a habit)
Ransomware attacks have become increasingly lucrative for private and state-sponsored hacking groups, with at least one hack recently reported to have resulted in a $75 MILLION payout from the victim. This in combination with the aforementioned factors has made it a bigger and bigger risk for companies and organizations holding your most sensitive data.
In the US, the Salt Typhoon hack over the past year or so has compromised virtually all major phone networks--meaning text and phone calls are no longer secure means of communication. While this won't affect most people in day-to-day, it does make basically all the information you share over traditional phone comms very vulnerable. You should avoid sharing sensitive information over the phone when you can.
CISA updated their security recommendations late last year in response to this compromise. One of the recommendations is to use a separate comms app with end-to-end encryption. I personally prefer Signal, since it's open source and not owned by Meta, but the challenge can be getting people you know on the same service. So... have fun with that.
2FA is no longer as secure as it was--because SMS itself is no longer secure, yeah, but even app-based 2FA has been rendered useless in certain circumstances. One reason for this is because...
A modern version of the early-2000's trick of gaining access to people's accounts via hijacked cookies has come back around for Chromium browsers, and hackers are gaining access to people's Google accounts via OAuth session hijacking. Meaning they can get into your already-logged-in accounts without passwords or 2FA even being needed to begin with. This has been achieved both through hackers compromising chrome browser extensions, and via a reinvigorated push to send out compromising links via email.
Thanks to AI, discerning compromised email is harder now. Cybercriminals are getting better at replicating legitimate email forms and website login screens etc., and coming up with ways to time the emails around times when you might legitimately expect them. (Some go so far as to hack into a person's phone to watch for when a text confirmation might indicate a recent purchase has been made via texted shipping alerts, for example)
If you go to a website that asks you to double-click a link or button--that is a major red flag. A potential method of clickjacking sessions is done via a script that has to be run with the end user's approval. Basically, to get around people who know enough to not authenticate scripts they don't recognize, hackers are concealing the related pop ups behind a "double-click" prompt instruction that places the "consent" prompt's button under the user's mouse in disguised UI, so that on the second click, the user will unwittingly elevate the script without realizing they are doing it.
Attachments are also a fresh concern, as hackers have figured out how to intentionally corrupt key areas of a file in a way that bypasses built-in virus check--for the email service's virus checker as well as many major anti-virus installed on endpoint systems
Hackers are also increasingly infiltrating trusted channels, like creating fake IT accounts in companies' Office 365 environment, allowing them to Teams employees instead of simply email them. Meaning when IT sends you a new PM in tools like Zoom, Slack, or Teams, you need to double-check what email address they are using before assuming it's the real IT person in question.
Spearphishing's growing sophistication has accelerated the theft of large, sensitive databases like the United/Change Healthcare hacks, the NHS hack & the recent Powerschool hack. Cybercriminals are not only gaining access to emails and accounts, but also using generative AI tools to clone the voices (written and spoken) of key individuals close to them, in order to more thoroughly fool targets into giving away sensitive data that compromises access to bigger accounts and databases.
This is mostly being used to target big-ticket targets, like company CSO's and other executives or security/IT personnel. But it also showcases the way scammers are likely to start trying to manipulate the average person more thoroughly as well. The amount of sensitive information--like the health databases being stolen and sold on the darkweb--means people's most personal details are up for sale and exploitation. So we're not too far off from grandparents being fooled by weaponized AI trained off a grandchild's scraped tiktok videos or other public-facing social media, for example. And who is vulnerable to believing these scams will expand, as scammers can potentially answer sensitive questions figured out from stolen databases, to be even more convincing.
And finally, Big Tech's interest in replacing their employees with AI to net higher profits has resulted in cybersecurity teams who are overworked, even more understaffed they already were before, and increasingly lacking the long-term industry experience useful to leading effective teams and finding good solutions. We're effectively in an arms race that is burning IT pros out faster and harder than before, resulting in the circumvention of crucial QA steps, and mistakes like the faulty release that created the Crowdstrike outage earlier last year.
Most of this won't impact the average person all at once or to the same degree big name targets with potential for big ransoms. But they are little things that have combined into major risks for people in ways that aren't entirely in our control. Password security has become virtually obsolete at this point. And 2FA's effectiveness is tenuous at best, assuming you can maintain vigilance.
The new and currently best advice to keeping your individual accounts secure is to switch to using Passkeys and FIDO keys like Yubikeys. However, the effectiveness of passkeys are held back somewhat as users are slow to adopt them, and therefore websites and services are required to continue to support passwords on people's accounts anyway--keeping password vulnerabilities there as a back door.
TLDR; it's pretty ugly out there right now, and I think it's going to get worse before it gets better. Because even with more sophisticated EDR and anti-virus tools, social engineering itself is getting more complex, which renders certain defensive technologies as somewhat obsolete.
Try to use a passkey when you can, as well as a password locker to create strong passwords you don't have to memorize and non-SMS 2FA as much as possible. FIDO keys are ideal if you can get one you won't lose.
Change your passwords for your most sensitive accounts often.
Don't give websites more personal info about yourself than is absolutely necessary.
Don't double-click links or buttons on websites/captchas.
Be careful what you click and download on piracy sources.
Try to treat your emails and PMs with a healthy dose of skepticism--double-check who is sending them etc for stealthily disguised typos or clever names. It's not going to be as obvious as it used to be that someone is phishing you.
It doesn't hurt to come up with an offline pass phrase to verify people you know IRL. Really.
And basically brace for more big hacks to happen that you cannot control to begin with. The employees at your insurance companies, your hospital, your telecomms company etc. are all likely targets for a breach.
36 notes
·
View notes
Text
ok but 16 BILLION logins??


like wtf. this isn’t just a small leak it’s the biggest ever.
not clickbait. not fear-mongering.
just 2 days ago, 16B+ login creds combos were dumped on the dark web.
affected? literally everyone:
Google. Apple. Facebook. GitHub. probably even that random app you forgot about.
all stolen using RedLine & Vidar malware, then dumped publicly through something called AlienStealerLogs
(i didn’t even know that existed until now)
what does that mean?
→ your info might already be floating around.
→ your accounts are at risk.
→ your online identity? not safe if you don’t act.
what i did (and you should too):
● changed ALL my important pws
● turned on 2FA (finally)
● checked if my email got pwned on: haveibeenpwned.com
● started using aliases for shady apps
this is not the time to be lazy with your security. if you think “nah bro i’m safe” you’re the first one they’ll get.
screenshot proof below ↓
2 notes
·
View notes
Text
"Taiwan will open a national cybersecurity center in August to counter threats from quantum computing, AI, and state-sponsored cyberattacks"
"Let's say that, in 10 or 20 ...5-15 years, “Future You” logs into your account, only to see that it's been zeroed out.
Your life savings have been transferred elsewhere.
How could this be? What happened to your password, your 2FA, and the security measures that used to help lock down your account?
A hacker used something called a quantum computer to speed past all those safeguards, right to your money.
Tomorrow's quantum computers are expected to be millions of times faster than the device you're using right now. Whenever these powerful computers take hold, it will be like going from a Ford Model T to the Starship Enterprise.
This spike in speed may undo the security measures that protect every piece of data sent over the web today. And it's not just your bank account that could be at risk. This threat could affect everything from military communications to health records. And it would play out on a vastly larger scale than the headline-grabbing data breaches that have affected countless consumers in recent years.
But here's the good news: This apocalyptic, break-the-internet scenario is preventable—if we act now."
Flash forward 5 years- we didn't "act now" and now it's too late. All internet connected banks will be drained by quantum computing. It won't just be them spying on us. They will drain all bank accounts of digital dollars, and we watch Taiwan like we watch the smartest student in class. This quote / link is from 2020-
https://www.rand.org/pubs/articles/2020/quantum-computers-will-break-the-internet-but-only-if-we-let-them.html
3 notes
·
View notes
Text
How to Protect Your WordPress Site from Malware or Hackers?
WordPress is used by millions of websites for blogs, businesses, and online stores. However, because it’s so popular, it’s often a target for hackers and malware. If you have a WordPress site, it’s important to take steps to keep it secure. Here’s a simple guide to help you protect your site from hackers and malware.
How to Protect WordPress Site from Malware or Hackers?
Follow this step list given below to protect WordPress site from malware or hackers
1. Always Keep WordPress Updated
WordPress regularly releases updates to fix bugs and improve security. Hackers often look for websites running old versions of WordPress or outdated plugins, so keeping everything updated helps keep them out.
How to Update:
Check for updates in your WordPress dashboard regularly.
Go to the Dashboard > Updates section and install any available updates for WordPress core, themes, or plugins.
By staying updated, you’re less likely to have security holes in your site that hackers can use.
2. Use Strong Passwords and Change Them Often
Hackers can easily guess weak passwords like "123456" or "admin." To keep your site safe, use strong, unique passwords and change them every few months.
Tips for Strong Passwords:
Use a mix of uppercase and lowercase letters, numbers, and symbols.
Don’t use simple information like your name or "admin."
Consider using a password manager to create and store complex passwords securely.
Strong passwords are one of the simplest ways to add security to your website.
3. Limit Login Attempts
Hackers often try to break into websites by guessing the login password over and over. You can protect your site by limiting the number of login attempts a person (or bot) can make.
How to Limit Login Attempts:
Use plugins like Limit Login Attempts Reloaded or WP Limit Login Attempts.
These plugins lock out users after a certain number of failed login attempts.
This makes it much harder for hackers to keep guessing passwords.
4. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds another layer of security. In addition to entering your password, you’ll also need to input a code sent to your phone or email. Even if someone knows your password, they won’t be able to log in without this extra code.
How to Set Up 2FA:
Install a plugin like Google Authenticator or Two-Factor.
Set it up by scanning a QR code and linking your account to an app like Google Authenticator or Authy.
This ensures that only you can access your site, even if someone steals your password.
5. Use a Security Plugin
A security plugin can protect your WordPress site from different types of attacks, like malware or brute force attempts. These plugins act as your site’s security guard, offering tools like firewalls and malware scanning.
Recommended Security Plugins:
Wordfence Security: Includes a firewall and real-time monitoring.
Sucuri Security: Provides malware removal and a website firewall.
iThemes Security: Offers brute force protection, backups, and two-factor authentication.
Using a security plugin adds strong layers of protection against hackers.
Also Read - What Is Domain Status? What does this mean, & Why should I know?
6. Back Up Your Website Regularly
Even with good security, things can sometimes go wrong. That’s why it’s important to back up your site regularly. If your site gets hacked, a backup will let you restore everything quickly without losing important data.
How to Back Up Your Website:
Use backup plugins like UpdraftPlus or BackupBuddy.
Store your backups in safe places like Google Drive, Dropbox, or a remote server.
Schedule backups daily or weekly, depending on how often you update your site.
Regular backups help ensure you won’t lose everything if something goes wrong.
7. Choose a Secure Hosting Provider
Your web hosting service plays an important role in your website’s security. Some hosts offer strong security features that help protect your site. Make sure to choose a hosting provider that values security.
What to Look for in a Hosting Provider:
Regular backups
Malware scanning and removal
Firewalls
SSL certificates
DDoS protection
Popular and secure WordPress hosting services include SiteGround, Bluehost, and WP Engine.
8. Use HTTPS and SSL Certificates
SSL (Secure Socket Layer) encrypts the data between your website and your visitors. This protects sensitive information, like passwords or credit card numbers. Websites with SSL certificates also have a secure URL that starts with "https://."
How to Install an SSL Certificate:
Most hosting providers offer free SSL certificates with Let’s Encrypt.
You can use plugins like Really Simple SSL to set it up quickly.
SSL certificates keep sensitive data safe and make your site more trustworthy.
9. Remove Unused Themes and Plugins
Unused plugins and themes can create security risks, especially if they aren’t updated. Even if they’re deactivated, they can still be a weak point. It’s best to delete any plugins or themes you don’t use.
How to Delete Unused Themes/Plugins:
Go to your Dashboard > Plugins or Appearance > Themes.
Deactivate and delete anything you no longer need.
This reduces the number of places where hackers might try to get in.
10. Monitor Your Site for Suspicious Activity
It’s important to keep an eye on your site for any unusual behavior. This could include sudden spikes in traffic, unknown files appearing on your server, or unauthorized users trying to log in.
How to Monitor Your Site:
Use a security plugin to track things like failed login attempts and changes to important files.
Regularly check your hosting account for unusual activity.
Review your website users to make sure no unauthorized accounts have been added.
By staying alert, you can catch potential threats before they do any serious damage.
Conclusion
Protecting your WordPress site doesn’t have to be difficult. By following these simple steps—keeping WordPress updated, using strong passwords, installing security plugins, and making regular backups—you can greatly reduce the risk of your site being hacked or infected with malware.
#OZOHosting#lowest price hosting in india#Cheap web hosting jaipur#cheap shared web hosting india#free web hosting india#affordable linux web hosting india
2 notes
·
View notes
Text
What Are the Key Features of Successful Web Applications in Dubai?
Web applications are an essential resource for businesses that want to offer their customers the best in smooth, efficient services in the modern world. Web applications are an important aspect of maintaining business in this area, be it a retail platform, a booking system, or engaging tool in communication. With this in mind, here are some of the vital must-have features of web applications every Dubai business should also incorporate and what makes web applications in Dubai‘s successful innovative technology landscape.
We will examine the key elements of a successful web application in Dubai in this article, highlighting components that can improve functionality, user experience, and business expansion. We’ll also discuss how Dubai’s web application development is changing to satisfy the needs for modern companies.
Key Features of Web Applications
1. User-Friendly Interface
The foundation of any successful web application is an easy-to-use interface (UI). It’s critical that users can use the application with ease and without unnecessary difficulty. A well-designed user interface makes sure that complicated layouts and confusing features aren’t confusing users. In Dubai’s competitive market, where consumers expect efficiency, a clean and simple interface will set your web application apart from others.
Users may do activities more easily with an easy design, whether they are making purchases, scheduling services, or getting important information. Focusing on usability is crucial, making sure that all buttons, menus, and actions are organized logically and are simple to comprehend. This helps improve engagement, leading to higher conversion rates and customer satisfaction.
2. Responsive and Mobile-Optimized Design
Having a responsive web application is now important in Dubai, where mobile usage is extremely strong. Whether a user accesses the application from a desktop, tablet, or smartphone, a responsive web design makes adjustments for different screen sizes and devices, guaranteeing a consistent and ideal experience.
Because so many people in Dubai rely on their mobile devices for business, entertainment, and shopping, mobile optimization is particularly important. A mobile friendly web application will decrease bounce rates, improve user experience overall, and eventually increase user loyalty and engagement. This is a feature that is important for companies trying to grow in the mobile-first world.
3. Fast Loading Speed
Users expect online applications to launch rapidly in a place like Dubai where time is of the importance. High bounce rates and irate clients might be caused by slow loading times. Speed should be the top priority for a successful online application, making sure that it loads smoothly and rapidly even during moments of high traffic.
In order to increase loading speed, web developers in Dubai focus on code optimization, image reduction, and content delivery networks (CDNs). Because consumers are more inclined to interact with a web application that operates fast and efficiently, this improves user experience and retention.
4. Security Features
When it comes to web applications, security is of utmost importance, particularly in an area like Dubai where the financial and e-commerce sectors are flourishing. Strong security elements must be included in a successful online application to safeguard users and companies alike. Two-factor authentication (2FA), secure encryption techniques, secure sockets layer (SSL) certificates, and data protection regulations are all crucial elements that guarantee consumers private information is protected from online attacks.
Strong security measures are crucial for both user protection and local data protection rules in Dubai, where firms handle a substantial volume of financial and personal data. Customers are more likely to make purchases and disclose private information with confidence when a secure web application fosters trust.
Read more about key feature of web application.....................
1 note
·
View note
Text
Balancing Security and Performance: Options for Laravel Developers
Introduction

This is the digital age, and all businesses are aware of the necessity to build a state-of-the-art website, one that is high-performing and also secure. A high-performing website will ensure you stand out from your competitors, and at the same time, high security will ensure it can withstand brutal cyberattacks.
However, implementing high-security measures often comes at the cost of performance. Laravel is one of the most popular PHP frameworks for building scalable, high-performing, and secure web applications. Hence, achieving a harmonious balance between security and performance often presents challenges.
This article provides more details about security vs performance for Laravel applications and how to balance it.
Security in Laravel Applications
Laravel comes equipped with a range of security features that allow developers to build applications that can withstand various cyber threats. It is a robust PHP framework designed with security in mind. However, creating secure applications requires a proactive approach. Here are some key features:
Authentication and Authorization: Laravel’s built-in authentication system provides a secure way to manage user logins, registrations, and roles. The framework uses hashed passwords, reducing the risk of password theft.
CSRF Protection: Laravel protects applications from cross-site request forgery (CSRF) attacks using CSRF tokens. These tokens ensure that unauthorized requests cannot be submitted on behalf of authenticated users.
SQL Injection Prevention: Laravel uses Eloquent ORM and query builder to prevent SQL injection by binding query parameters.
Two-Factor Authentication (2FA): Integrate 2FA for an added layer of security.
Secure File Uploads: File uploads can be exploited to execute malicious scripts. There are several ways to protect the files by restricting upload types using validation rules like mimes or mimetypes. Storing files outside the web root or in secure storage services like Amazon S3 and scanning files for malware before saving them will also improve security.
Secure communication between users and the server by enabling HTTPS. Using SSL/TLS certificates to encrypt data in transit and redirecting HTTP traffic to HTTPS using Laravel’s ForceHttps middleware will boost security. Laravel simplifies the implementation of robust security measures, but vigilance and proactive maintenance are essential.
By combining Laravel’s built-in features with best practices and regular updates, developers can build secure applications that protect user data and ensure system integrity.
Optimizing Laravel Application For Performance

Laravel is a versatile framework that balances functionality and ease of use. It is known for its performance optimization capabilities, making it an excellent choice for developers aiming to build high-speed applications. Key performance aspects include database interactions, caching, and efficient code execution. Here are proven strategies to enhance the speed and efficiency of Laravel applications.
Caching: Caching is a critical feature for performance optimization in Laravel. The framework supports various cache drivers, including file, database, Redis, and Memcached.
Database Optimization: Database queries are often the bottleneck in web application performance. Laravel provides tools to optimize these queries.
Utilize Job Batching: Laravel’s job batching feature allows grouping multiple queue jobs into batches to process related tasks efficiently.
Queue Management: Laravel’s queue system offloads time-consuming tasks, ensuring better response times for users.
Route Caching: Route caching improves application performance by reducing the time taken to load routes.
Minifying Assets: Minification reduces the size of CSS, JavaScript, and other static files, improving page load times.
Database Connection Pooling: For high-traffic applications, use a database connection pool like PGBouncer (PostgreSQL) or MySQL’s connection pool for better connection reuse.
Laravel provides a solid foundation for building applications, but achieving top-notch performance requires fine-tuning. By applying these strategies, you can ensure your Laravel application delivers a fast, seamless experience to users.
Security vs Performance For Laravel

Implementing security measures in a Laravel application is crucial for protecting data, maintaining user trust, and adhering to regulations. However, these measures can sometimes impact performance. Understanding this trade-off helps in balancing security and performance effectively. Here’s a breakdown of how Laravel’s security measures can affect performance and visa-versa.
Security measures that affect performance
Input Validation and Sanitization: Laravel’s robust validation and sanitization ensure that user input is secure and free from malicious code. Validating and sanitizing every request can slightly increase processing time, especially with complex rules or high traffic.
Encryption and Hashing: Laravel provides built-in encryption (based on OpenSSL) and hashing mechanisms (bcrypt, Argon2) for storing sensitive data like passwords. Encryption and hashing are computationally intensive, especially for large datasets or real-time operations. Password hashing (e.g., bcrypt) is deliberately slow to deter brute force attacks.
Cross-Site Request Forgery (CSRF) Protection: Laravel automatically generates and verifies CSRF tokens to prevent unauthorized actions.
Performance Impact: Adding CSRF tokens to forms and verifying them for every request incurs minimal processing overhead.
Middleware for Authentication and Authorization: Laravel’s authentication guards and authorization policies enforce secure access controls. Middleware checks add processing steps for each request. In the case of high-traffic applications, this can slightly slow response times.
Secure File Uploads: Validating file types and scanning uploads for security risks adds overhead to file handling processes. Processing large files or using third-party scanning tools can delay response times.
Rate Limiting: Laravel’s Throttle Requests middleware prevents abuse by limiting the number of requests per user/IP. Tracking and validating request counts can introduce slight latency, especially under high traffic.
HTTPS Implementation: Enforcing HTTPS ensures secure communication but introduces a slight overhead due to SSL/TLS handshakes. SSL/TLS encryption can increase latency for each request.
Regular Dependency Updates: Updating Laravel and third-party packages reduces vulnerabilities but might temporarily slow down deployment due to additional testing. Updated libraries might introduce heavier dependencies or new processing logic.
Real-Time Security Monitoring: Tools like Laravel Telescope help monitor security events but may introduce logging overhead. Tracking every request and event can slow the application in real-time scenarios.
Performance optimization that affect security
Caching Sensitive Data:
Performance optimization frequently involves caching data to reduce query times and server load. Storing sensitive data in caches (e.g., session data, API tokens) can expose it to unauthorized access if not encrypted or secured. Shared caches in multi-tenant systems might lead to data leakage.
Reducing Validation and Sanitization:
To improve response times, developers may reduce or skip input validation and sanitization. This can expose applications to injection attacks (SQL, XSS) or allow malicious data to enter the system. Improperly sanitized inputs can lead to broken functionality or exploits.
Disabling CSRF Protection:
Some developers disable Cross-Site Request Forgery (CSRF) protection on high-traffic forms or APIs to reduce processing overhead. Without CSRF protection, attackers can execute unauthorized actions on behalf of authenticated users.
Using Raw Queries for Faster Database Access:
Raw SQL queries are often used for performance but bypass Laravel’s ORM protections. Raw queries can expose applications to SQL Injection attacks if inputs are not sanitized.
Skipping Middleware:
Performance optimization may involve bypassing or removing middleware, such as authentication or Rate limiting, to speed up request processing. Removing middleware can expose routes to unauthorized users or brute force attacks.
Disabling Logging:
To save disk space or reduce I/O operations, developers may disable or minimize logging. Critical security events (e.g., failed login attempts and unauthorized access) may go unnoticed, delaying response to breaches.
Implementing Aggressive Rate Limiting:
While Rate limiting is crucial for preventing abuse, overly aggressive limits might unintentionally turn off security mechanisms like CAPTCHA or block legitimate users. Attackers may exploit misconfigured limits to lock out users or bypass checks.
Over-Exposing APIs for Speed:
In a bid to optimize API response times, developers may expose excessive data or simplify access controls. Exposed sensitive fields in API responses can aid attackers. Insufficient access control can allow unauthorized access.
Using Outdated Libraries for Compatibility:
To avoid breaking changes and reduce the effort of updates, developers may stick to outdated Laravel versions or third-party packages. Older versions may contain known vulnerabilities. For faster encryption and decryption, developers might use less secure algorithms or lower encryption rounds. Weak encryption can be cracked more quickly, exposing sensitive data.
Tips To Balance Security and Performance
There are several options available to balance security and performance while developing a Laravel application. It is essential to strike a balance and develop a robust solution that is not vulnerable to hackers. Seek the help from the professionals, and hire Laravel developers from Acquaint Softttech who are experts at implementing a combination of strategies to obtain the perfect balance.
Layered Security Measures:
Instead of relying solely on one security layer, combine multiple measures:
Use middleware for authentication and authorization.
Apply encryption for sensitive data.
Implement Rate limiting to prevent brute force attacks.
Optimize Middleware Usage:
Middleware in Laravel is a powerful tool for enforcing security without affecting performance excessively. Prioritize middleware execution:
Use route-specific middleware instead of global middleware when possible.
Optimize middleware logic to minimize resource consumption.
Intelligent Caching Strategies:
Cache only what is necessary to avoid stale data issues:
Implement cache invalidation policies to ensure updated data.
Use tags to manage grouped cache items effectively.
Regular Vulnerability Testing:
Conduct penetration testing and code reviews to identify vulnerabilities. Use tools like:
Laravel Debugbar for performance profiling.
OWASP ZAP for security testing.
Enable Logging and Monitoring:
Laravel’s logging capabilities provide insights into application performance and potential security threats:
Use Monolog to capture and analyze logs.
Monitor logs for unusual activity that may indicate an attack.
Implement Rate Limiting:
Laravel’s Rate limiting protects APIs from abuse while maintaining performance:
Use ThrottleRequests middleware to limit requests based on IP or user ID.
Adjust limits based on application needs.
Leverage API Gateway:
An API gateway can act as a security and performance intermediary:
Handle authentication, authorization, and Rate limiting at the gateway level.
Cache responses to reduce server load.
Use Load Balancing and Scaling:
Distribute traffic across multiple servers to enhance both security and performance:
Implement load balancers with SSL termination for secure connections.
Use horizontal scaling to handle increased traffic.
Employ CDN for Static Content:
Offload static resources to a content delivery network:
Reduce server load by serving images, CSS, and JavaScript via CDN.
Enhance security with HTTPS encryption on CDN.
Harden Server Configuration:
Ensure server security without sacrificing performance:
Use firewalls and intrusion detection systems.
Optimize PHP and database server configurations for maximum efficiency.
Placing trust in a Laravel development company for the development of your custom solution will go a long way ensuring you build a top-notch solution.
Future Trends in Laravel Security and Performance
As Laravel evolves, so do the tools and technologies to achieve the delicate balance between security and performance. Trust a software development outsourcing company like Acquaint Softtech for secure and future-proof solutions. Besides being an official Laravel partner, our developers also stay abreast with the current technologies.
Future trends include:
AI-Powered Security: AI-driven security tools can automatically detect and mitigate threats in Laravel applications. These tools enhance security without adding significant overhead.
Edge Computing: Processing data closer to the user reduces latency and enhances performance. Laravel developers can leverage edge computing for better scalability and security.
Advanced Caching Mechanisms: Next-generation caching solutions like in-memory databases (e.g., RedisGraph) will enable even faster data retrieval.
Zero-Trust Architecture: Zero-trust models are gaining popularity to enhance security in Laravel applications. This approach treats all traffic as untrusted, ensuring stricter access controls.
Quantum-Resistant Encryption: With advancements in quantum computing, Laravel applications may adopt quantum-resistant encryption algorithms to future-proof security.
Hire remote developers from Acquaint Softtech to implement these strategies. We follow the security best practices and have extensive experience creating state-of-the-art applications that are both secure and high performing. This ensures a smooth and safe user experience.
Conclusion
Balancing security and performance in Laravel development is a challenging yet achievable task. By leveraging Laravel’s built-in features, adopting Laravel security best practices, and staying updated on emerging trends, developers can create applications that are both secure and high-performing.
The key is to approach security and performance as complementary aspects rather than competing priorities. Take advantage of the Laravel development services at Acquaint Softtech. We can deliver robust, scalable, and efficient applications that meet modern user expectations.
1 note
·
View note
Text
Boosting WordPress security is crucial for protecting your website from potential threats. Start by regularly updating your WordPress core, themes, and plugins to ensure you’re using the latest security patches. Outdated software is a common target for hackers, making updates a vital first step in safeguarding your site.
Another essential step is to implement strong passwords and two-factor authentication (2FA) for all user accounts. Weak passwords are easy to crack, while 2FA adds an extra layer of security by requiring a second form of verification. These measures can significantly reduce the risk of unauthorized access to your WordPress site.
#wordpress#web development#wordpress crowdfunding#wordpress development company#best web development company in usa
3 notes
·
View notes
Link
Security Suite is one of 11 professional plugins included with the WordPress Plugin Toolbox. Features of Security Suite: - Enable dual-layered security with biometric and 2FA locks - Create your own dynamic firewall with IP logging - Scan for and implement security recommendations - Scheduled malware scanning - Safe Repair for suspicious files - Comprehensive audit logging - Malware Scanning - Hosted WAF integration - Scheduled Security Reports - Google blocklist monitoring - Pwned Password Check - Force Password Reset - User Agent Banning - Google reCAPTCHA for WooCommerce - Geolocation blocking (block based on location) - Lockout logs - Backup Codes 2FA auth - 2FA integrations: Google Authenticator, Microsoft Authenticator, Authy, and more - Global IP blocklist & monitor - Login protection - Security tweaks and recommendations - Security Headers - Two-factor authentication - IP lockout device - Google reCAPTCHA - Core and plugin code checker - Login masking - Restore and repair changed files - Email Notifications - 404 Lockouts - Manual IP allowlist and blocklist - Config, save current settings, and apply any time - Resolve security recommendations and issues in bulk - Fallback Email 2FA auth - Automatic security keys regeneration - Managing user login duration - Bio metric Authentication See more about Security Suite ⬇ https://t2websolutions.com/plug-ins/security-suite/
3 notes
·
View notes
Text
Top 10 Key Points to Ensure Security for Your Laravel Application

In Laravel web application development, security is one of the essential paramount. As the digital landscape continues to expand, the Importance of security in web applications, particularly those built on the Laravel framework, has reached an all-time high. In this era of interconnectedness, where information flows seamlessly across the virtual realm, the potential threats and vulnerabilities have also escalated.
The landscape of online threats has grown more sophisticated, encompassing various malicious activities ranging from data breaches to identity theft. This evolving threat landscape calls for a steadfast commitment to proactive security measures. Waiting for a security breach before addressing vulnerabilities is a risk no modern developer can afford to take.
The significance of bolstering security in Laravel web application development. While Laravel provides a robust and versatile platform for creating dynamic web applications, it's essential to recognize that even the most advanced framework is not immune to potential security breaches. As your Laravel application evolves, it becomes a showcase of your technological prowess and a potential target for cyber threats.
The Importance of proactive security measures should be highlighted further. Developers and businesses must adopt a security-first mindset when crafting their digital creations, which means staying informed about the latest security trends, continuously updating and patching the application, and adhering to best practices for safeguarding sensitive user data.
We'll delve into 10 critical checkpoints that can significantly enhance the security of your Laravel web application. These checkpoints encompass a comprehensive approach to securing various aspects of your application, from authentication and authorization to protecting against common web vulnerabilities. By diligently implementing these checkpoints, you'll be taking a substantial stride towards fortifying your Laravel web application against the ever-persistent threats lurking in the digital domain.
10 Key Checkpoints to Focus On
Here's your comprehensive Laravel Security Checklist to ensure a robust and safeguarded web application.
1. Secure Authentication and Authorization

In the intricate world of Laravel web application development, security is an indispensable pillar for creating a trustworthy and resilient digital presence. One of the cornerstone elements in this security fortress is the implementation of secure authentication and authorization mechanisms. Let's delve into how these critical aspects are pivotal in fortifying your Laravel application against potential threats.
Secure Authentication: Building the First Line of Defense
Authentication is verifying the identity of users attempting to access your application. It forms the cornerstone of security by ensuring that only authorized individuals can interact with sensitive data and functionalities. In the realm of Laravel, this process is made significantly more manageable through the framework's built-in authentication features.
Implementing secure authentication involves
Strong Password Policies: Enforce complex passwords, combining uppercase and lowercase letters, numbers, and special characters. Laravel provides password validation rules to help you accomplish this.
Two-Factor Authentication (2FA): Enhance security by requiring users to provide an additional authentication factor beyond their password. Laravel offers seamless integration with 2FA for an added layer of protection.
Account Lockouts: Implement mechanisms that lock accounts after a specified number of unsuccessful login attempts, preventing brute-force attacks by temporarily halting further login attempts.
Authorization: Ensuring Granular Access Control
Authorization, however, deals with controlling what authenticated users can do within the application. It's about granting permissions and access rights based on roles and responsibilities, ensuring that sensitive actions are restricted to those who need them.
Key steps in implementing effective authorization include
Role-Based Access Control (RBAC): Define roles such as "admin," "user," or "manager," and associate them with specific permissions. Laravel's RBAC system lets you assign roles and permissions effortlessly.
Middleware Authorization: Leverage Laravel's middleware to restrict access to routes or controllers based on user roles or custom conditions. This is a powerful way to ensure that only authorized users can perform specific actions.
Resource Controllers: Utilize resource controllers to create a consistent and structured approach to handling CRUD operations. These controllers can be easily configured to enforce authorization rules for specific actions.
Dynamic Authorization Policies: Laravel's policy system lets you define authorization logic in a structured manner. It's beneficial for complex access control requirements and allows for fine-grained control over what users can do.
In a world where digital threats are evolving rapidly, securing your Laravel application's authentication and authorization processes is paramount. By implementing robust authentication mechanisms and enforcing precise authorization rules, you're safeguarding sensitive data and building a foundation of trust with your users. Remember, security isn't just a one-time task; it's an ongoing commitment that requires vigilance and adaptability in the face of ever-changing cyber threats.
2. Keep Laravel and Dependencies Updated
In the dynamic realm of Laravel web application development, staying ahead in the security game is an ongoing endeavor. One of the fundamental practices that forms the bedrock of a secure digital presence is the consistent updating of your Laravel framework and its associated dependencies. Let's explore why this practice is essential and how it contributes to the overall security of your application.
The Power of Regular Updates
Technology, much like the world around us, is in a constant state of evolution. This evolution is driven not only by innovation but also by identifying and rectifying vulnerabilities and weaknesses. In the context of Laravel development, regular updates to both the core framework and its dependencies play a pivotal role in ensuring the security and stability of your application.
Why Updates Matter
Security Patches: Vulnerabilities can emerge at any software lifecycle stage. Developers and the open-source community work diligently to identify and address these vulnerabilities. Regular updates ensure that your Laravel application is fortified with the latest security patches, minimizing the risk of exploitation.
Compatibility: As Laravel evolves, updates often improve compatibility with newer PHP versions, web servers, and databases. Staying updated ensures your application remains in sync with the broader web development ecosystem.
Performance and Features: Updates not only fix issues; they also introduce performance enhancements and new features. Embracing these updates can lead to a more efficient application that delivers a better user experience.
Dependencies: Handle with Care
Laravel development heavily relies on various external packages and libraries. While these dependencies contribute to the efficiency and functionality of your application, they can also introduce vulnerabilities if not managed appropriately.
Best Practices for Dependency Management:
Regular Audits: Periodically review the dependencies your Laravel development company utilizes. Check for any vulnerabilities reported in these packages and prioritize updating them accordingly.
Automated Tools: Leverage automated tools that can scan your project's dependencies for known security issues. This can help you identify potential risks and take corrective action swiftly.
Version Pinning: Specify the exact versions of dependencies your application uses. This prevents unexpected updates that might introduce breaking changes or vulnerabilities.
In the rapidly evolving web application security landscape, treating updates as a proactive security measure is paramount. By ensuring your Laravel framework and dependencies are up to date, you're demonstrating a commitment to maintaining a robust digital fortress for your application. This safeguards sensitive user data and positions your Laravel development company as a conscientious custodian of digital security. Remember, in technology, staying current isn't just an option—it's necessary for a secure and successful future.
3. Validate User Input
The ever-evolving landscape of Laravel development, the adage "Garbage In, Garbage Out" holds immense relevance. One of the pivotal checkpoints in ensuring the robustness of your Laravel application's security is the validation of user input. Let's dive into why validating user input is crucial and how it is a formidable shield against potential vulnerabilities.
The Essence of User Input Validation
User input is the gateway through which your Laravel application interacts with its users. Whether it's a login form, a search bar, or a comment section, user input is integral to the functionality of your application. However, it can also become an entry point for malicious activities if left unchecked.
Why Validate User Input:
Mitigating Injection Attacks: Attackers can exploit unvalidated user input to inject malicious code into your application. This includes infamous threats like SQL injection and cross-site scripting (XSS). Proper validation drastically reduces the risk of such attacks.
Data Integrity: Validating user input ensures that the data flowing into your application is consistent and matches the expected format. This helps maintain data integrity and prevents errors caused by unexpected information.
Enhancing User Experience: You can guide users to input data in the correct format by providing real-time validation feedback. This not only prevents submission errors but also enhances the overall user experience.
Implementing Effective Input Validation in Laravel
Utilize Laravel's Validation Rules: Laravel offers a robust validation system that includes a wide array of predefined rules. These rules cover everything from required fields and email formats to custom validation logic.
Sanitize and Filter Input: Consider sanitizing and filtering user input alongside validation. Sanitization removes potentially harmful characters, while filtering ensures that information adheres to specific formats.
Client-Side Validation: While server-side validation is paramount, supplement it with client-side validation using JavaScript. This provides instant feedback to users and reduces unnecessary server requests.
Best Practices for User Input Validation
Never Trust User Input: Treat all incoming user input as potentially malicious until proven otherwise. Validate and sanitize input even if it seems harmless.
Whitelist Validation: Define an allowlist of allowed characters and formats for each input field. Reject input that doesn't conform to these predefined patterns.
Regular Updates: Like any other security practice, stay updated with Laravel's latest validation features and best practices. This ensures you're using the most effective tools available.
In the intricate realm of Laravel development, user input validation isn't just a technical practice; it's a shield that guards your application against many threats. By diligently validating user input, you're bolstering your application's security and reinforcing trust with your users. In the dynamic world of web development, where innovation meets vulnerability, validation is your steadfast ally in pursuing a secure and seamless user experience.
4. Protect Against SQL Injection

Shielding your digital fortress through meticulous Laravel development services involves a critical step: Protect against SQL injection. This threat arises when user inputs lack proper sanitation, potentially enabling malicious actors to manipulate SQL queries and gain unauthorized database access.
SQL injection attacks can lead to data exposure, alteration, or deletion. Laravel's defences are robust. Its query binding technique parameterizes user inputs, preventing malicious SQL execution. The Eloquent ORM further enhances security by abstracting SQL interactions and automatically escaping values.
Adhering to best practices is paramount. Prioritize parameterized queries over direct concatenation, sanitize inputs, and conduct regular code audits to ensure secure methods. By fortifying your Laravel application against SQL injection, you're erecting a robust barrier against a damaging vulnerability while providing your Laravel development services maintain the utmost integrity and user trust.
5. Cross-Site Scripting (XSS) Prevention
In securing your digital haven with proficient Laravel development practices, countering Cross-Site Scripting (XSS) emerges as a pivotal measure. XSS occurs when malicious code infiltrates a website through unfiltered user inputs, potentially compromising user data and integrity.
The gravity of XSS lies in its ability to expose sensitive information or perform malicious actions under the user's identity. Laravel offers potent tools to thwart such threats:
Blade Templating: Laravel's Blade templating engine automatically escapes variables, preventing unintended script execution.
XSS Middleware: Laravel provides built-in middleware for encoding user inputs, adding an extra layer of protection.
Content Security Policy (CSP): Implementing CSP headers in your Laravel application restricts the sources from which content can be loaded, reducing the risk of XSS attacks.
Adhering to these precautions is essential. Validate and sanitize inputs, embrace Laravel's security features, and implement a robust CSP. By guarding against XSS vulnerabilities, you ensure your Laravel development maintains a resilient and trustworthy digital presence.
6. Implement HTTPS and SSL
In web application development, particularly in Laravel, bolstering security is paramount. A crucial step in this pursuit is the implementation of HTTPS and SSL protocols. These measures are essential to safeguard sensitive data transmitted between users and your application.
HTTPS (Hypertext Transfer Protocol Secure) encrypts the data between users' browsers and your application's server, thwarting potential eavesdropping and tampering. SSL (Secure Sockets Layer) certificates are the foundation of this encryption, ensuring that communication remains confidential.
Advantages of HTTPS and SSL:
Data Encryption: HTTPS encrypts data during transit, preventing unauthorized access to sensitive information.
Trust and SEO: SSL certificates enhance user trust, as indicated by the padlock symbol in browsers. Search engines also favor HTTPS websites, improving SEO rankings.
Authentication: SSL certificates verify your application's authenticity, shielding users from potential phishing sites.
Implementing HTTPS and SSL involves obtaining a valid SSL certificate and configuring your Laravel application for secure connections. By adopting these measures, you're securing your web application development, fostering trust among users, and ensuring compliance with modern security standards.
7. Secure Session Management
In web application development, security isn't just a feature—it's a necessity. A crucial aspect of building a robust and trustworthy application is ensuring secure session management. Sessions are pivotal in maintaining user interactions and data, making their protection paramount.
Laravel offers robust mechanisms to fortify session management:
Session Encryption: Laravel automatically encrypts session data, preventing unauthorized access and ensuring confidentiality.
CSRF Protection: Cross-Site Request Forgery (CSRF) attacks can compromise sessions. Laravel's built-in CSRF protection safeguards against such threats.
Expire and Regenerate: Set session expiration times and periodically regenerate session IDs to minimize the window of vulnerability.
By implementing secure session management practices in your web application development, you create a shield against unauthorized access and data breaches. This preserves user trust and solidifies your commitment to crafting applications that prioritize security and integrity.
8. Protect Against Cross-Site Request Forgery (CSRF)
Safeguarding web applications is a top priority in Laravel development. To fortify your digital haven, countering Cross-Site Request Forgery (CSRF) threats is crucial. CSRF attacks manipulate authenticated users into executing malicious actions unknowingly. Laravel provides a robust defense:
CSRF Tokens: Laravel automatically generates unique tokens for each user session, validating the authenticity of requests.
Middleware Protection: Laravel's built-in CSRF middleware verifies tokens, preventing unauthorized requests from being executed.
By integrating these measures, you fortify your Laravel application against CSRF vulnerabilities. This secures user interactions and demonstrates your commitment to proactive security practices in modern web development.
9. Harden Configuration and File Permissions
In the landscape of Laravel security, enhancing configuration settings and file permissions is a critical stride. Securing sensitive files, such as configuration files, shields against unauthorized access and potential breaches. Laravel's framework offers key tactics:
Restricted Access: Limit access to sensitive configuration files by setting appropriate permissions. This prevents unauthorized users from tampering with vital settings.
Environment Configuration: Store sensitive data in environment files and never expose them in version control. Laravel's .env file shields sensitive variables from prying eyes.
By meticulously configuring permissions and safeguarding critical files, you erect a solid barrier against potential threats. This reflects an unwavering commitment to fortifying your Laravel application and upholding security standards in modern web development.
10. Use Content Security Policy (CSP)
Bolstering security in Laravel involves advanced tactics, including a Content Security Policy (CSP). CSP guards against cross-site scripting (XSS) and data injection attacks. It achieves this by specifying approved content sources, mitigating the risk of malicious script execution. Laravel's integration of CSP fortifies your defense:
Malicious Content Mitigation: CSP curtails the potential impact of XSS attacks by regulating the domains from which content can be loaded.
Policy Customization: Laravel empowers you to tailor CSP rules to suit your application's specific requirements, balancing security and functionality.
By embracing CSP, you establish a robust security framework that exemplifies Laravel's commitment to secure, modern web development practices.
Top Laravel Security Packages for Developers
In the realm of Laravel development, ensuring robust security is paramount. Several key packages aid developers in fortifying their applications. Here are three notable options:
Laravel-ACL: Access Control Lists (ACL) are fundamental to controlling user permissions. This package simplifies ACL implementation, offering granular control over user access to different parts of your application.
Laravel Security: As the name suggests, this package enhances overall security. It provides features like XSS protection, safe redirects, and content filtering, contributing to a fortified application.
Laravel Security Component: This package takes security up a notch by integrating robust security components. It includes encryption, hashing, validation, and more tools, streamlining your security efforts.
For a Laravel development agency, these packages are invaluable assets. By incorporating them into your development process, you expedite security implementation and establish a strong foundation for crafting secure, reliable applications that clients can trust.
Conclusion
In the intricate realm of Laravel security, these checkpoints act as sentinels, fortifying your application's defenses. Secure authentication, vigilant updates, meticulous validation, and shielded configurations create a robust bastion. Protection against threats like SQL injection, XSS, and CSRF forms an unbreachable wall. Implementation of HTTPS, secure session handling, and CSP reinforce your fortifications. Familiarity with essential security packages like Laravel-ACL, Laravel Security, and Security Component adds the final layer. As a Laravel developer, embracing these measures ensures your applications are secured, and your expertise is unwavering in the face of evolving threats.
Source: Top 10 Key Points to Ensure Security for Your Laravel Application
2 notes
·
View notes
Text
𝗪𝗲𝗲𝗸𝗹𝘆 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 & 𝗧𝗵𝗿𝗲𝗮𝘁𝘀 𝗥𝗼𝘂𝗻𝗱𝘂𝗽 | 𝟭𝟬 𝗙𝗲𝗯 - 𝟭𝟲 𝗙𝗲𝗯 𝟮𝟬𝟮𝟱

1️⃣ 𝗙𝗜𝗡𝗔𝗟𝗗𝗥𝗔𝗙𝗧 𝗠𝗮𝗹𝘄𝗮𝗿𝗲 𝗘𝘅𝗽𝗹𝗼𝗶𝘁𝘀 𝗠𝗶𝗰𝗿𝗼𝘀𝗼𝗳𝘁 𝗚𝗿𝗮𝗽𝗵 𝗔𝗣𝗜 FINALDRAFT is targeting Windows and Linux systems, leveraging Microsoft Graph API for espionage. Source: https://www.elastic.co/security-labs/fragile-web-ref7707
2️⃣ 𝗦𝗸𝘆 𝗘𝗖𝗖 𝗗𝗶𝘀𝘁𝗿𝗶𝗯𝘂𝘁𝗼𝗿𝘀 𝗔𝗿𝗿𝗲𝘀𝘁𝗲𝗱 𝗶𝗻 𝗦𝗽𝗮𝗶𝗻 𝗮𝗻𝗱 𝗧𝗵𝗲 𝗡𝗲𝘁𝗵𝗲𝗿𝗹𝗮𝗻𝗱𝘀 Four distributors of the criminal-encrypted service Sky ECC were arrested in Spain and the Netherlands. Source: https://www.bleepingcomputer.com/news/legal/sky-ecc-encrypted-service-distributors-arrested-in-spain-netherlands/
3️⃣ 𝗔𝘀𝘁𝗮𝗿𝗼𝘁𝗵: 𝗡𝗲𝘄 𝟮𝗙𝗔 𝗣𝗵𝗶𝘀𝗵𝗶𝗻𝗴 𝗞𝗶𝘁 𝗧𝗮𝗿𝗴𝗲𝘁𝘀 𝗠𝗮𝗷𝗼𝗿 𝗘𝗺𝗮𝗶𝗹 𝗣𝗿𝗼𝘃𝗶𝗱𝗲𝗿𝘀 The Astaroth phishing kit is used to bypass 2FA and steal credentials from Gmail, Yahoo, AOL, O365, and third-party logins. Source: https://slashnext.com/blog/astaroth-a-new-2fa-phishing-kit-targeting-gmail-yahoo-aol-o365-and-3rd-party-logins/
4️⃣ 𝗥𝗮𝗻𝘀𝗼𝗺𝗛𝘂𝗯 𝗕𝗲𝗰𝗼𝗺𝗲𝘀 𝟮𝟬𝟮𝟰’𝘀 𝗧𝗼𝗽 𝗥𝗮𝗻𝘀𝗼𝗺𝘄𝗮𝗿𝗲 𝗚𝗿𝗼𝘂𝗽 RansomHub overtook competitors in 2024, hitting over 600 organisations worldwide. Source: https://www.group-ib.com/blog/ransomhub-never-sleeps-episode-1/
5️⃣ 𝗕𝗮𝗱𝗣𝗶𝗹𝗼𝘁 𝗖𝗮𝗺𝗽𝗮𝗶𝗴𝗻: 𝗦𝗲𝗮𝘀𝗵𝗲𝗹𝗹 𝗕𝗹𝗶𝘇𝘇𝗮𝗿𝗱 𝗧𝗮𝗿𝗴𝗲𝘁𝘀 𝗚𝗹𝗼𝗯𝗮𝗹 𝗡𝗲𝘁𝘄𝗼𝗿𝗸𝘀 The Seashell Blizzard subgroup runs a multiyear global operation for continuous access and data theft. Source: https://www.microsoft.com/en-us/security/blog/2025/02/12/the-badpilot-campaign-seashell-blizzard-subgroup-conducts-multiyear-global-access-operation/
Additional Cybersecurity News:
🟢 𝗔𝗽𝗽𝗹𝗲 𝗙𝗶𝘅𝗲𝘀 𝗔𝗰𝘁𝗶𝘃𝗲𝗹𝘆 𝗘𝘅𝗽𝗹𝗼𝗶𝘁𝗲𝗱 𝗭𝗲𝗿𝗼-𝗗𝗮𝘆 Apple patches a critical zero-day vulnerability affecting iOS devices. Source: https://www.techspot.com/news/106731-apple-fixes-another-actively-exploited-zero-day-vulnerability.html
🟠 𝗝𝗮𝗽𝗮𝗻 𝗜𝗻𝘁𝗿𝗼𝗱𝘂𝗰𝗲𝘀 "𝗔𝗰𝘁𝗶𝘃𝗲 𝗖𝘆𝗯𝗲𝗿 𝗗𝗲𝗳𝗲𝗻𝗰𝗲" 𝗕𝗶𝗹𝗹 Japan is moving towards offensive cybersecurity tactics with a new legislative push. Source: https://www.darkreading.com/cybersecurity-operations/japan-offense-new-cyber-defense-bill
🔴 𝗖𝗿𝗶𝘁𝗶𝗰𝗮𝗹 𝗡𝗩𝗜𝗗𝗜𝗔 𝗔𝗜 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗶𝗹𝗶𝘁𝘆 𝗗𝗶𝘀𝗰𝗼𝘃𝗲𝗿𝗲𝗱 A severe flaw in NVIDIA AI software has been discovered, enabling container escapes. Source: https://www.wiz.io/blog/nvidia-ai-vulnerability-deep-dive-cve-2024-0132
6 notes
·
View notes
Text
okay to anyone that does want some practical advice. just in case.
1. Password manager. For storing passwords like these:

You wouldn’t want to remember that by yourself. Nobody would. A password manager doesn’t care though, and ideally it’ll also have a generator that helps create passwords like this securely (there are insecure random number generators that you shouldn’t use for passwords, and password managers usually use secure ones instead).
Personally I recommend Bitwarden. When you’re looking for a password manager, it’s best to have something where both the frontend (the browser extension / app that you use) and the backend (servers that actually store your passwords) are open source. This means that people can independently audit them, and you don’t have to trust their own claims. You can actually run Bitwarden on your own server if you really want to, though there’s not much you’d gain out of it. (Just don’t use LastPass and you’ll probably be fine. Also, your browser’s native ‘save this password’ feature is the worst password manager you can use, even behind LastPass, because it’s likely completely unencrypted, and any malware you install would be able to access it).
So that’ll be alright for your web passwords, but you have some things (like the passwords to your devices, and the one to your password manager itself) where you’ll still need to remember them yourself. So for that, you want to set up some:
2. Passphrases. Basically a set of at least four random words separated by spaces as a password. That might sound like it isn’t that safe, but actually, there are quite a few words, so it’s safer than the usual recommendations you’ll get, like making substitutions for symbols. This xkcd (936) is a common way to show why you should use passphrases instead of complex passwords:
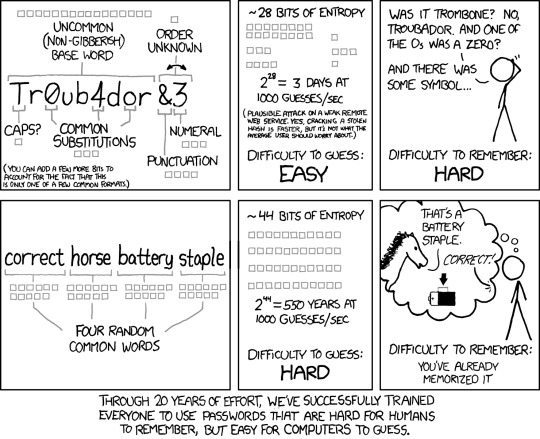
You can compare the real-world strength of passwords and passphrases on Use A Passphrase. This uses a (decade old, but still pretty realistic) algorithm to estimate how long it would take to crack any password you put in.
The key thing to remember here are that you should only use passphrases when you have to remember a password - for a website, you should use your password manager to generate a much more random password so that you don’t have all those things to remember, and importantly, so you don’t get into the habit of reusing passwords.
Only put a passphrase on your devices and your password manager. Everything else should use those random passwords. (By the way, ‘your devices’ especially includes your phone - it’s likely that it’s what handles most of your data, but you’re still securing it with six digits. Most phones sold today are end-to-end encrypted, meaning that you need the passcode after first turning it on to access any data on it, but if someone steals your phone or you’re involved in a criminal investigation, there are tools available to get around the delay after putting an incorrect password in and try all of the potential 1,000,000 6-digit passcodes in a few seconds. Use a passphrase for this too - it might be a bit inconvenient sometimes, but as long as you have biometric unlock, it will get out of your way most of the time and potentially save you from a very bad night).
3. 2FA. I recommend Ente Auth because you’ll still be able to use it if you don’t have your phone.
So there’s really not a lot you need to do to start securing everything better. You also don’t have to do it all in one leap - get a password manager, change your device passwords to passcodes, and get a 2FA app at first. You can do all of these three things pretty easily. Then, everything else can be pretty slow. You can start to gradually reset your online passwords to random ones generated and stored in your password manager, turn 2FA on, do some research, just little bits whenever you get a moment, and if you do this, you’ll eventually have a moment when you realise like. Yeah I can’t even remember how bad what I was doing before was. It’s all in here. It’s all very convenient and poggers and I’m also much safer now.

32K notes
·
View notes
Text
Robinhood® Sign in - Login to App | Official Site® Account Access
🔐 Robinhood Sign In: Secure Login & Account Access Guide
Robinhood Sign In is your secure gateway to trading stocks, ETFs, options, and cryptocurrencies without paying commissions. Whether you're a beginner or an experienced trader, signing into your Robinhood account is essential for managing your investments. This guide explains everything about how to log in, troubleshoot common issues, and access your account quickly and safely.
🚀 How to Sign In to Your Robinhood Account – Step-by-Step
Follow these steps to securely sign in to Robinhood:
Visit the Official Website: Go to https://robinhood.com
Click “Sign In” Located at the top-right corner of the homepage.
Enter Login Details
Email address
Password
Complete Two-Factor Authentication (2FA) A security code will be sent to your registered device.
Access Your Dashboard Start managing your trades, portfolio, and assets securely.
📊 Robinhood Sign In Methods (Table)
PlatformSign In MethodSecurityWeb BrowserVia https://robinhood.com2FA, encryptionMobile App (iOS)Download via Apple App StoreBiometric login supportedMobile App (Android)Download via Google Play StoreBiometric login supported
🎯 Why Robinhood Login is Secure
🔒 Two-Factor Authentication (2FA)
🔐 256-bit encryption for data protection
📲 Biometric login options (Face ID, fingerprint)
🔔 Real-time account alerts for suspicious activity
🛡️ Tips for Safe Robinhood Sign In
Always sign in from official sources like https://robinhood.com
Use unique, strong passwords.
Enable two-factor authentication.
Avoid using public Wi-Fi when signing in.
📱 Key Features After Robinhood Sign In
Once logged in, users get access to:
Real-time trading of stocks, ETFs, crypto
Instant deposits and fast withdrawals
Live market data and alerts
Secure asset tracking
Zero commission trades
⚙️ Common Robinhood Login Issues & Fixes
Forgot password? Click “Forgot Password” on the login screen to reset.
Didn’t receive 2FA code? Check spam folders or try resending the code.
App not working?
Clear app cache.
Update to the latest version.
Try reinstalling.
🔄 Benefits of Using Robinhood Sign In Portal
No commissions on trades
Access from web or mobile
Secure and fast login process
Real-time market tracking
Supports stock, ETF, crypto, and options trading
Single login for all assets
📌 FAQs – Robinhood Sign In
❓ How do I reset my Robinhood password?
Click “Forgot Password” on the login page at https://robinhood.com/login, enter your email, and follow the reset instructions.
❓ Is Robinhood login safe?
Yes. Robinhood employs encryption, two-factor authentication (2FA), and biometric verification for secure login.
❓ Can I use my Robinhood login on multiple devices?
Yes. You can log in via mobile and web with the same credentials, but for security, Robinhood might ask for additional verification when using a new device.
❓ What if I can't sign in to my Robinhood account?
Reset your password.
Ensure your app is updated.
Contact Robinhood customer support if issues persist.
📊 Robinhood vs. Competitors: Login Features Comparison
FeatureRobinhoodCompetitor Apps2FA Security✅ Yes✅ YesBiometric Login✅ Yes✅ PartialInstant Deposits✅ Yes❌ NoCommission-Free Trades✅ Yes❌ Often Fees
🎯 Conclusion: Why Robinhood Sign In Matters
Your Robinhood sign in account is more than just a login—it's your access point to secure, commission-free investing. Robinhood’s simple yet robust sign-in process ensures that your assets stay protected while giving you the freedom to trade across devices seamlessly.
Whether you're trading crypto or building your stock portfolio, Robinhood ensures every login is safe, fast, and efficient.
1 note
·
View note
Text
2025年07月12日の記事一覧
(全 33 件)
AIコーディングツールは生産性を19%も低下させているという調査結果、AI出力の評価・手直し・再出力などで無駄な時間が大量発生か
Beeceptor - Rest & SOAP API Mock Server
Passkey への道 #0: Intro | blog.jxck.io
Passkey への道 #1: 平成の Password 感 | blog.jxck.io
White Noise - Secure Private Messenger
Passkey への道 #2: 2FA/TOTP | blog.jxck.io
GeForce RTX 5090を持ち運べる!ASUSが外付けGPUドック
バッファロー、全ポート10Gbps対応スイッチの8ポート版「LXW-10G8」発売
人に「共感するふり」だけでも、十分意味がある。
ソニー、小型軽量で機動性の高いプロ向けショットガンマイク
サブスクの解約を簡単に…米国で施行目前だった「クリック・トゥ・キャンセル」規則がお流れに【やじうまWatch】
ローカルLLM実行環境LM Studio、企業・組織での商用利用を無料に | gihyo.jp
Stay ahead of the curve with Feedly AI
Claude Codeなんもわからんので、AI縛りでiOSアプリを開発してみた | DevelopersIO
X元CEOによるネットなしで使えるメッセージアプリ「bitchat」。Bluetoothで直接通信
ネットトラフィックの37%がボット、うち9割が悪意あるもの――Fastly調査
OpenAI、Webブラウザ発表へ Chromeに対抗
Perplexity、AI搭載Webブラウザ「Comet」公開 まずはMaxユーザーに
あの「サンディスク」のSSDが使いやすい理由。性能、デザイン、安全性の三拍子で申し分ない | ライフハッカー・ジャパン
開発人生25年で学んだ7つのソフトウェア原則(翻訳)|TechRacho by BPS株式会社
YouTube、“大量生産”動画の収益化を制限
TOPPING、ESS「ES9039Q2M」デュアル搭載のフルバランスデスクトップDACアンプ「DX5II」。
GitHubのSecret scanningでリポジトリに混入した機密情報を検出してみた | DevelopersIO
Microsoft Regional Director (2025)
Reverse proxy deep dive
将棋AIの大会をめちゃめちゃにできる定跡が発見された | やねうら王 公式サイト
AIでプログラマ不要になるというのは、プログラミング言語構文わかればプログラム組めるという誤解に基づくのでは - きしだのHatena
ECM-778 Shotgun Microphones Hi-Res Audio Super cardioid - Sony Pro
Amazon S3 へデータ転送速度が早いと噂の s5cmd を使って aws s3 cp と比べてみた | DevelopersIO
When can I use Temporal
OpenAI's Windsurf deal is off – and its CEO is going to Google
「どの都道府県の給与が高いか」や「人口と給与は関係あるのか」など日本の膨大な情報を見やすく表示するダッシュボード「Japan Dashboard」をデジタル庁が公開したので使ってみた
Anthropic Is Bleeding Out
0 notes
Text
API Providers: Purchase Crypto.com Accounts – A Ultimate Guide in 2025
Discover how to purchase verified Crypto.com accounts in 2025 through trusted API providers. Secure, fast delivery available now at usabuysmm. com

Introduction: The Need for Verified Crypto.com Accounts in 2025
As crypto adoption continues to rise in 2025, platforms like Crypto.com have become central to digital asset management, trading, and DeFi integration. However, account verification requirements and regional restrictions often prevent users from accessing full features — especially for developers, marketers, and international crypto users.
For those looking to scale operations or bypass regional limits, purchasing a verified Crypto.com account from trusted API providers is a practical and secure solution. That’s where usabuysmm.com comes in — offering ready-to-use, KYC-verified Crypto.com accounts with instant delivery and API compatibility.
Why Developers & Businesses Use Verified Crypto.com Accounts
Access to Crypto.com API for Automation API access requires a fully verified account. Developers use this for trading bots, portfolio trackers, and automated crypto strategies.
Bypass Regional Restrictions Certain countries face limitations on crypto services. A verified account from a different region helps unlock the full platform.
Speed Up KYC Process Instead of waiting days for KYC approval, businesses buy pre-verified accounts for instant use.
Multiple Account Management Agencies and institutions managing multiple clients often use several Crypto.com accounts for better fund separation and tracking.
What You Get with a Purchased Crypto.com Account from usabuysmm. com
FeatureDetails
Verification Level
KYC Level 2 (ID, Selfie, Address Verified)
Country Options
USA, UK, Canada, EU
Compatibility
API Access Enabled
Delivery Time
Within 15–30 Minutes
Security Measures
Clean device, IP, browser fingerprint
Replacement Guarantee
48 Hours
Step-by-Step: How to get Crypto.com Account
Go to usabuysmm.com
Navigate to the Crypto.com account purchase section
Choose your preferred region (e.g., US, UK, EU)
Proceed to checkout with Crypto, PayPal, or Card
Receive account details securely in your email
How API Providers Integrate Crypto.com Accounts
API providers and developers require verified accounts to:
Authenticate trading bots
Fetch balance and transaction data
Enable automated buy/sell orders
Manage portfolios using third-party apps
Purchasing a verified account unlocks this functionality immediately, without waiting for approval or risking rejection.
Security Tips for Using Your New Crypto.com Account
Access using a VPN from the same region as the account
Do not immediately change core identity information
Enable Two-Factor Authentication (2FA)
Avoid suspicious transfers that may flag the account
Never use for illegal or dark web activities
Common Questions (FAQ)
Q1: Is buying a Crypto.com account legal? Buying is not illegal, but it may violate Crypto.com's Terms of Service. Use responsibly.
Q2: Are the accounts safe and unique? Yes, all accounts from usabuysmm.com are created fresh and verified with unique details.
Q3: Will I get API access credentials? Yes. Upon delivery, you receive full account credentials including access to API settings.
Q4: What if the account is limited? You are protected by our 48-hour replacement policy.
Final Words: Grow Your Crypto Projects with Verified Accounts
Whether you're building a crypto automation tool, running a trading bot, or expanding your blockchain services, having a verified Crypto.com account with API access is a must in 2025.
usabuysmm com offers safe, fast, and affordable access to such accounts — already trusted by developers and marketers around the globe.
1 note
·
View note
Text
Why Startups Choose Ready-Made Crypto Exchange Software

Introduction
In today’s fast-paced digital economy, launching a cryptocurrency exchange has become a lucrative opportunity. But here’s the catch—developing an exchange from scratch is time-consuming, expensive, and technically demanding. That’s where ready-made crypto exchange software comes in.
For startups with limited time, resources, or technical teams, choosing a Cryptocurrency Exchange Script offers a powerful shortcut. These pre-built solutions provide the features, security, and scalability needed to launch quickly—without reinventing the blockchain wheel.
Let’s explore why more startups are going with these ready-to-deploy scripts to power their crypto trading platforms.
What Is a Cryptocurrency Exchange Script?
A Cryptocurrency Exchange Script is a pre-developed, customizable software package that includes all the core functionalities of a crypto exchange. It helps entrepreneurs launch platforms similar to Binance, Coinbase, or Kraken—without building everything from scratch.
These scripts support key functions like:
User registration & KYC
Cryptocurrency trading engine
Wallet integration (hot and cold wallets)
Admin and user dashboards
Liquidity management
Security features (2FA, encryption, etc.)
Why Startups Are Choosing Ready-Made Solutions
1. Faster Time to Market
Launching a custom-built exchange can take months—or even years. With a Crypto Exchange Script, startups can get their platform up and running within a few weeks.
Startups love the speed because in crypto, timing is everything. Markets move fast, and being first often means gaining a competitive edge.
2. Affordable Development Costs
Developing a cryptocurrency exchange from scratch can cost anywhere between $100,000 to $500,000, depending on features and complexity. On the other hand, White Label Bitcoin Exchange Scripts offer similar functionalities at a fraction of the price.
Key cost savings include:
No need to build from scratch
No large in-house dev teams
Fewer testing phases
Reusable and battle-tested code
3. Easy Customization
Despite being pre-built, most cryptocurrency trading scripts are fully customizable. This means startups can:
Add their own branding and UI/UX
Integrate specific coins or tokens
Choose the trading pairs
Set custom transaction fees
Enable specific security layers
Customization allows businesses to tailor the user experience to match their vision and target audience.
4. Proven Security and Reliability
Security is non-negotiable in crypto. With Bitcoin Exchange Software that’s been tested across multiple use cases, startups can avoid the risks of zero-day vulnerabilities or untested code.
Most quality scripts come with:
Encrypted wallet systems
Two-factor authentication (2FA)
DDOS protection
SQL injection and XSS prevention
Secure APIs
5. Ongoing Tech Support and Upgrades
Top vendors don’t just sell a script—they offer ongoing support, updates, and patches. This is especially useful for startups without in-house blockchain engineers.
Some even offer:
Free bug fixes
Version upgrades
Technical consultation
Performance optimization tips
Popular Features in Today’s Exchange Scripts
Startups are attracted to Altcoin Exchange Scripts because they come loaded with features such as:
✅ Multi-Currency Wallets
Support for multiple cryptocurrencies, including Bitcoin, Ethereum, altcoins, and stablecoins.
✅ Advanced Trading Engine
Capable of handling real-time buy/sell orders, order matching, market, and limit trading options.
✅ KYC/AML Compliance Tools
Integrated tools for verifying user identity and following local regulatory standards.
✅ Mobile and Web Interface
Responsive front-ends for both desktop and mobile users with clean, intuitive navigation.
✅ Liquidity Management
Integrates with other exchanges or liquidity pools to ensure smooth trading and minimize slippage.
Benefits Beyond the Code
Choosing a cryptocurrency trading platform script means more than just software—it means access to an entire business ecosystem. Startups gain:
Scalability – Easily handle growing users and trading volume
Faster ROI – Quick launch means quicker monetization
Low Risk – Start small, scale fast
White-labeling – Rebrand and go live under your own name
Who Should Consider a Cryptocurrency Exchange Script?
Ready-made crypto exchange software is ideal for:
Entrepreneurs entering the crypto space with minimal technical knowledge
Startups looking to test an idea or MVP before committing large investments
Traditional financial companies expanding into digital assets
Crypto influencers or communities launching niche or token-based exchanges
How to Choose the Right Script
Not all exchange scripts are created equal. Here’s what to look for:
✔️ Clean, Modular Code
So you can update or replace components as needed.
✔️ Strong Demo & Documentation
Ensure you can test the script and understand how it works before purchase.
✔️ Regulatory Readiness
Make sure the script helps you comply with the laws of your operating country.
✔️ Customization & Integration
Check that you can easily modify features and connect third-party services.
✔️ Customer Support
Choose a provider that offers tech support during and after launch.
Real-World Use Case: A Startup Success Story
Let’s say a fintech startup in Singapore wanted to launch a niche altcoin trading platform. Instead of spending six months on development, they opted for a white label crypto exchange script. Within 45 days, they were live with:
User-friendly UI
Trading pairs for regional altcoins
24/7 trading with liquidity support
Regulatory compliance tools for KYC
Within 6 months, the platform reached 50,000+ active users—all thanks to a fast, affordable, and reliable software base.
Conclusion: Launch Smart with a Crypto Exchange Script
For startups stepping into the booming world of crypto, using a Cryptocurrency Exchange Script isn’t just a shortcut—it’s a strategic decision. It combines speed, cost-effectiveness, and flexibility, all while offering a strong technical foundation.
With reliable features, security protocols, and white-label capabilities, ready-made crypto exchange software empowers entrepreneurs to launch confidently and scale fast.
🚀 Ready to Start Your Crypto Exchange?
If you’re a startup exploring the crypto space, now is the time to act. Choose a Crypto Exchange Script that fits your needs, customize it to match your brand, and go live in weeks—not months.
Explore your options today and start building the future of finance.
FAQ Summary
What is a Cryptocurrency Exchange Script? A ready-made, customizable software for launching a crypto trading platform.
Is it secure to use a pre-built crypto exchange? Yes—if sourced from a trusted provider. Look for security features like 2FA, encryption, and DDoS protection.
Can I customize the script? Absolutely. Most scripts are white-label and highly customizable.
How much does it cost? Costs range from $5,000 to $50,000 depending on features and support options.
How long does it take to launch? With a ready-made script, your exchange can go live in as little as 2–4 weeks.
#Cryptocurrency Exchange Script#White Label Bitcoin Exchange Script#Cryptocurrency Trading Platform#Bitcoin Exchange Software#Altcoin Exchange Script#Crypto Exchange Script
0 notes