#US replicate biologics sector
Explore tagged Tumblr posts
Text
Top 5 players in US Biosimilar Market
Buy Now
STORY OUTLINE
Pfizer: Excelling in the line of Biosimilar drugs with an experience of more than 10 years with presence in over 180 countries.
Amgen: Making pharmaceutical products with an experience of over 40 years and presence in over 100 countries.
Viartis: Presence in over 165 countries, and making Biosimilar drugs in over 75 markets, this pharmaceutical company is another leading contributor of US Biosimilar market.
Coherus Biosciences: Increasing patient access to cost effective medicines with a Biosimilar drugs experience of 13 years.
Biogen: serving humanity through science with a experiences of more than 40 years in the field of biologics.
According to Ken Research, the US Biosimilar market is anticipated to grow at a CAGR of ~40% in the next five years which currently has a market size of ~USD 9.4 Bn.
The US Biosimilar market is rapidly growing and will be witnessing a significant growth in the next five years.
There are various reasons behind the rapid growth of US Biosimilar market. Some of the major reasons behind the growth of US Biosimilar market include the cost effective nature of Biosimilar drugs, rising geriatric population, rising prevalence of chronic diseases, and growing partnerships between companies to develop Biosimilar drugs.
Various companies and players are contributing to their best efforts in the growth of the US Biosimilar market.
This article aims to put light on the contributions done by the major players towards the growth of the US Biosimilar market.
1.Pfizer
Click to read more about Pfizer
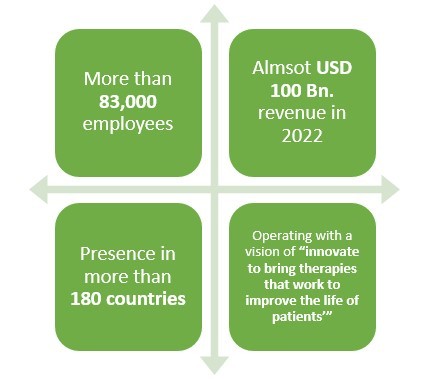
Pfizer is a leading American pharmaceutical company which is operating in the field of generics or original drugs for more than 30 years. But did you know that this pharma not only manufactures biologics but also biosimilar drugs?
Pfizer has been in the business of biosimilar drugs for more than 10 years and have been quite successful as well. With more than 83,000 employees and presence in over 180 countries, this leading pharmaceutical company made almost USD 2 Bn. revenue only from its Biosimilar drugs sale in 2021.
Recently, this pharmaceutical company also collaborated with Samsung in two deals to produce various biosimilar drugs in South Korea. The deal size between these two companies happens to be approximately USD 900 Bn.
The major Biosimilar drugs of this pharmaceutical giant are primarily
ZIRABEV (a Biosimilar of Avastin)
TRAZIMERA (a Biosimilar of Herceptin)
RUXIENCE (a Biosimilar of Rituxan)
RITACRIT (a Biosimilar of Epogen)
NVYEPRIA (a Biosimilar of Neulasta)
NIVESTYM (a Biosimilar of Neupogen)
FILGRASTIM (a Biosimilar of Neupogen).
2.Amgen
Click here to Download a Sample Report
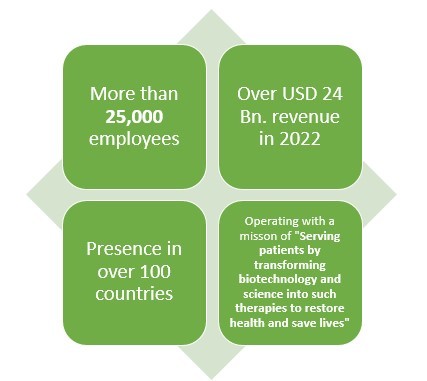
Amgen is another leading American pharmaceutical company which not only makes Biologics or generic drugs but also Biosimilar drugs. This pharmaceutical company has more than 40 years of experience when it comes to pharmaceutical line.
With over 25000 employees and presence in over 100 countries, this pharmaceutical company earned about USD 2 Bn. from their three biosimilar drugs which are reportedly MVASI, KANJITNTI, and AMJEVITA.
This pharma giant has also invested about USD 2 Bn. in the development of Biosimilar drugs.
This pharmaceutical company has made Biosimilar drugs primarily in 4 fields which are General Medicine, Oncology, and Hematology along with, Inflammation.
EPOTEIN ALFA
AMJEVITA
AVSOLA
KANJINTI
MVASI
RIABNI
are the various Biosimilar drugs of Amgen. And, STELARA, EYLEA, SOLIRIS are in their pipeline.
Recently Amgen revealed their Biosimilar report’s 8 version. It revealed a major information which said that the pharmaceutical company saved about USD 10 Bn. through their Biosimilar drugs in the past five years.
3.Viartis

Headquartered in Canonsburg, Pennsylvania, this American pharmaceutical company was founded only in 2020 yet they have achieved massive success in the pharmaceutical products with their revenue being USD 16 ~Bn. in 2022.
With presence in 165 countries and with over 45,000 employees worldwide, this pharmaceutical company makes pharmaceutical products in 10 areas which primarily are Cardiovascular, Dermatology, ophthalmology, Oncology, Gastroenterology, Women’s health, Infectious diseases, Diabetes & Metabolism, Immunology, CNS & Anesthesiology, Respiratory diseases and allergy.
Speaking of their first Biosimilar products, their first ever Biosimilar drug was launched in 2014. They have a variety of Biosimilar drugs which are primarily
TRASTUZUMAB
INSULIN ASPART
PEGFILGRASTIM
INSULIN GLARGINE-YFGN
ADALIMUMAB
BEVACIZUMAB
Their Biosimilar drug Insulin Glargine which is known as SEMGLEE was the first ever interchangeable Biosimilar drug in the United States which was FDA approved.
Their PEGFILGRASTIM also was the first ever FDA approved drug in the United States. They have launched their Biosimilar drugs in over 75 markets worldwide.
4.Coherus Biosciences:

Click here to Ask for a Custom Report
Headquartered in Redwood city, California this American pharmaceutical company earned a revenue of almost USD 211 Mn. In 2022.
With presence in over 55 countries and 300+ employees worldwide, this pharmaceutical company makes products in various areas such as solid tumors, non-small lung cancers, nasopharyngeal carcinoma, small cell lung cancer and hepatocellular carcinoma.
Speaking of their Biosimilar drugs, this pharma has been in the field of creating Biosimilar drugs since 2010 which has given them almost 13 years of experience.
This pharmaceutical company also disclosed that it plans to spend at least USD 1 Tn. on medicines worldwide, out of which at least 40% will be spent on Biosimilar drugs.
Their three major Biosimilar drugs which are also FDA approved include UDENCYA, YUSIMRY, and CIMERLI.
Udencya is a Biosimilar drug of Pegfilgrastim, Yusimry is a Biosimilar drug of Ranibizumab, and Cimerli is a Biosimilar drug of Adalimumab.
5.Biogen
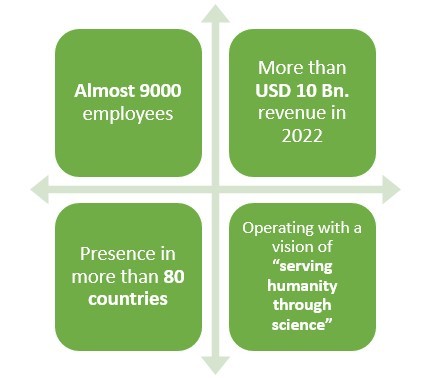
Headquartered in Cambridge, Massachusetts, this American pharmaceutical company earned a revenue of around USD 10 Bn. in 2022.
This company happens to have an experience of more than 40 years when it comes to making pharmaceutical products.
With presence in over 80 countries and more than 9000 employees worldwide, this pharmaceutical company primarily deals in Neurology, Specialized Immunology, Neuropsychiatry, Ophthalmology, and Rare Diseases.
ADUCANUMAB
LECANEMAB
TOFERSEN
ZURANOLONE
LITIFILIMAB
BENAPALI
FLIXABI
IMRALDI
are some of their Biosimilar drugs.
With their Biosimilar drugs, more than 250,000 people have gone on Anti-Tumor Necrosis Factor therapy.
Recently, this pharmaceutical company also made an agreement with Bio-Thera solutions to develop a Biosimilar drug for the treatment of Rheumatoid Arthritis.
#US Biosimilar Sector#United States Biosimilar Market#US Biosimilar Market forecast#US Biosimilar Market analysis#US Biosimilar Market trends#US Biosimilar Market share#US Biosimilar Market key players#US Biosimilar Market revenue#US Biosimilar Market growth#Monoclonal Antibodies in biosimilar market US#Recombinant Hormones in biosimilar industry US#Oncology in bio similar market US#Blood disorders in biosimilar market US#Research institutes in Biosimilar market US#US similar biotherapeutics products market#Hospitals in Biosimilar market US#Investors in Biosimilar market US#US comparable biologics products industry#US recombinant biosimilars industry#US replicate biologics sector#US analog biologics market
0 notes
Text
Greetings citizens of the Union and beings from beyond! Welcome to Union News Central, I'm your host Bluglakkag Flublabbak. Hello! This is the recent news! ::3
The New Libertopia Cultural Fair has begun! Culture is something that's been lacking in the Union, as the Replicants had very little and the uplifted species of the Union had nothing. That being said, the exposure to so many alien cultures on New Libertopia has inspired the habitat's communities to host the New Libertopia Cultural Fair! At this wonderful event, Union species have been expressing themselves in new and interesting ways, and alien species are encouraged to share the beauty of their own cultures.
Headlining the event is the Vegvian clone band Zoryal-Thunn. Opening with the song 'When Moegmar Arrives'.

The Zoryal-Thunn band members were grown here in the Union as a part of the Vegvian Preservation Project, and once they finished their adjustment cycle, they chose to remain in the Union as citizens.
Their songs revolve around the Vegvian history they studied during their adjustment cycle, and the battles and struggles of the past. Their songs don't celebrate war or violence, instead they honor the dead, sing to inform, and encourage a message of peace. Their iconic instruments catch the eye, repurposing of hard-light axes into musical instruments in a swords-to-ploughshares dramatic flare.
Not far from the concert, the elusive Ugluk artist Bloroworoe Riououeururowuw has set up a stall at the Fair to give some flare to the exoskeletons of Ugluks. Bloroworoe promised that for each decal painted, they'll answer a question about their art.

The stall also attracted some spectators, including Thylaks, who Bloroworoe encouraged to come in and made it clear that anyone, whether it be synthetic life forms, or organics with an exoskeleton or cybernetics limbs are welcome to be turned into a piece of walking art.
Meanwhile, the Mod community of the New Libertopia Ostess-Sat has promised to set up a stall at the fair soon. They're just gatering supplies, data on the anatomy of alien life, and looking for a space to set up at the moment.

The Ostess-Sat Modders are a group of Ostess-Sat speeder riders and racers who enjoy cyberneticly modifing themselves. Their passions grew from engineering their speeders to be safer and faster in the Ammonia Sector race tracks, which then moved to the modification of robots for quick repairs of speeders on the tracks in pitstops. And then of course, they began expressing modification in themselves. Hence 'Mods'. ::3
The Feforyans of New Libertopia have set up a presentation of their martial arts slash dance called Pudra. The teachers said they're willing to teach anyone, so long as people treat the art respectfully.

Pudra originated as an old Feforyan self defence martial art used against cruel Fefings. It developed in the pre-Observer age of post-Nuclear Feforia and in the time since then, its developed into a cultural dance which has a number of different styles depending on the situation and its not restrictive in terms of what someone can do with the amount of limbs the practioners may or may not have. This is in part due to the recent mutations which turned Feforyan legs into a fused tail, but it's also partly because of the many alien races Feforyans have encountered.
Lastly, the Replicants have set up a stall displaying the new lifeforms engineered for Feforia, animals that have been spliced from a number of different creatures that can withstand the planet's toxic atmosphere.

They explained how each critter is being crafted to be beautiful and unique in their eyes, even if some found the creations to be disturbing, none can deny its an impressive show of scientific mastery and biological artistry.
Well, that's all the major attractions of the New Libertopia Cultural Fair so far! I know I said 'lastly' with the Replicant event, but the Fair is still only on its first day, and you expect many more additions from our other alien residents soon! If you find yourself in New Libertopia in the coming weeks, be sure to visit these and other attractions and enjoy yourselves!
This is Bluglakkag Flublabbak saying thanks for tuning in to our signal here at UNC. Be sure to bookmark our wavelength for future updates.
Solace in the Union.
11 notes
·
View notes
Text
Exploring the 3D Bioprinting Market: A Revolutionary Leap in Healthcare and Biotechnology
The 3D bioprinting market represents a cutting-edge frontier in healthcare and biotechnology, offering innovative solutions for creating complex biological structures. This transformative technology combines 3D printing with biomaterials and cells, enabling the fabrication of tissues and organs for research, therapeutic, and transplantation purposes. The growth of this market signifies a shift towards personalized medicine and regenerative therapies.
Download PDF Brochure
What is 3D Bioprinting?
3D bioprinting is the process of creating three-dimensional biological structures using specialized printers, biomaterials (biocompatible polymers or hydrogels), and living cells. The technique enables precise layer-by-layer deposition of materials to replicate the natural architecture of tissues and organs. This technology is used across various domains, including drug discovery, cancer research, tissue engineering, and organ transplantation.
Market Drivers
Increasing Demand for Organ Transplants
Organ shortages have prompted research into 3D bioprinted organs as a viable solution. Bioprinting offers the potential to eliminate organ rejection risks by using patient-specific cells.
Advancements in Regenerative Medicine
The ability to create tissue scaffolds and skin grafts is driving the adoption of bioprinting in regenerative medicine, catering to burn victims and patients requiring reconstructive surgery.
Drug Development and Testing
Pharmaceutical companies leverage bioprinted tissues to test drugs in realistic human tissue models, reducing the reliance on animal testing and accelerating drug discovery.
Technological Innovations
Continuous innovations, such as multi-material bioprinting and advancements in bio-inks, are enhancing the capabilities and applications of 3D bioprinting systems.
Request Sample Pages
Key Market Segments
By Technology
Inkjet Bioprinting: Offers high precision and cost efficiency for creating complex tissues.
Extrusion Bioprinting: Preferred for fabricating larger tissue structures due to its ability to use a wide range of bio-inks.
Laser-Assisted Bioprinting: Ideal for intricate tissue engineering applications requiring high resolution.
By Application
Research Applications: Includes drug testing and disease modeling.
Therapeutic Applications: Focused on organ repair and transplantation.
Cosmetic and Personalized Medicine: Bioprinting for skin grafts and customized prosthetics.
By Material
Hydrogels: Most commonly used due to their biocompatibility and tissue-mimicking properties.
Living Cells: Critical for creating functional tissues and organs.
Synthetic and Natural Biomaterials: Used for structural support and scaffolding.
Regional Insights
North America
North America dominates the market due to robust R&D funding, academic partnerships, and the presence of leading biotech firms. The U.S., in particular, is a hub for innovation in 3D bioprinting technologies.
Europe
European countries like Germany and the U.K. are witnessing significant investments in bioprinting research, particularly for medical applications.
Asia-Pacific
Rapid technological adoption in countries like Japan, China, and South Korea is driving growth in the Asia-Pacific region. Governments and private sectors are collaborating to develop cost-effective bioprinting solutions.
Rest of the World
Emerging economies in Latin America and the Middle East are increasingly investing in bioprinting, spurred by growing healthcare demands.
Challenges and Opportunities
Challenges
High Initial Costs: Bioprinting equipment and bio-ink formulations are expensive.
Regulatory Hurdles: Ensuring safety and efficacy standards for bioprinted tissues is complex.
Scalability: Transitioning from prototypes to large-scale manufacturing remains a challenge.
Opportunities
Personalized Medicine: Tailoring treatments using patient-specific bioprinted tissues.
Bioprinted Organs: Meeting the critical demand for organ transplants.
Cosmetic Applications: Skin bioprinting for wound healing and anti-aging treatments.
Competitive Landscape
Prominent players in the 3D bioprinting market include:
Organovo Holdings, Inc.: A pioneer in developing bioprinted tissues for medical research.
Cellink (BICO Group): Specializes in bio-ink development and bioprinting systems.
Allevi: Focuses on affordable and user-friendly bioprinters.
Aspect Biosystems: Known for its microfluidic 3D bioprinting platform.
Startups and established companies alike are investing in research and collaborations to enhance their technological capabilities and market presence.
Future Outlook
The future of the 3D bioprinting market is bright, with applications extending beyond healthcare into industries such as cosmetics, food production, and space exploration. Innovations in bio-inks, improved scalability, and regulatory approvals are expected to drive widespread adoption.
By 2030, the market is anticipated to witness exponential growth, fueled by advancements in artificial intelligence, machine learning, and automation in bioprinting processes. As the technology matures, it holds the promise of revolutionizing how we approach medicine, making healthcare more efficient, personalized, and accessible.
Conclusion
The 3D bioprinting market is a testament to the power of innovation in solving some of humanity’s most pressing healthcare challenges. With continuous advancements, collaborations, and investments, this market is set to redefine the landscape of medical science and beyond. Whether it's creating life-saving organs, testing new drugs, or pioneering personalized treatments, 3D bioprinting holds the key to a healthier future.
0 notes
Text
The Essential Role of Environmental Stability Test Chambers in Quality Assurance

Introduction
In today's competitive manufacturing landscape, ensuring product quality and reliability is paramount. This is especially critical in industries such as pharmaceuticals, electronics, automotive, and aerospace, where environmental conditions can have a significant impact on product performance. Environmental Stability Test Chambers supplier (ESTCs) play a crucial role in simulating real-world conditions to evaluate the endurance of materials, products, and components. Suppliers of these test chambers help manufacturers achieve the necessary standards, certifications, and insights to deliver superior products to the market.
What is an Environmental Stability Test Chamber?
An Environmental Stability Test Chamber is a laboratory device used to simulate various environmental conditions such as temperature, humidity, and pressure. These chambers are designed to test the performance and reliability of products under extreme or fluctuating environmental conditions that they may encounter during their life cycle. ESTCs are used in a variety of industries, including pharmaceuticals, biotechnology, food processing, automotive, electronics, and materials science.
These chambers typically feature advanced technology to replicate conditions such as high/low temperatures, humidity cycles, UV radiation, or even combined temperature and humidity stress. By subjecting products to controlled environmental changes, manufacturers can assess their durability, stability, and overall performance.
Visit Also:- Understanding Stability Chambers: Essential Tools for Environmental Testing
Key Features of Environmental Stability Test Chambers
Temperature and Humidity Control: The core function of any environmental test chamber is the ability to precisely control temperature and humidity. Suppliers typically offer chambers with a wide range of temperature settings, from ultra-low to high-temperature conditions. Humidity levels can also be varied to simulate conditions from dry heat to highly humid environments.
Customizable Programming: Advanced ESTCs come equipped with programmable controls, enabling manufacturers to design specific testing profiles. This flexibility allows for testing under a wide variety of conditions, from short-term stress tests to long-term stability studies.
Data Logging and Monitoring: High-quality test chambers include data logging systems that track and record environmental conditions and test parameters in real time. This feature is essential for maintaining accurate records, ensuring test accuracy, and providing the data required for regulatory compliance.
Uniform Temperature Distribution: Ensuring uniform temperature and humidity distribution within the chamber is essential for accurate testing. Top suppliers offer models that ensure consistency and reliability across all areas of the chamber, preventing any localized discrepancies that could impact results.
User-Friendly Interface: The best environmental stability test chambers feature intuitive interfaces, often with touch screen controls, for easy operation and setup. Users can set and adjust parameters without difficulty, while also accessing test data and reports.
Energy Efficiency: With the increasing focus on sustainability, modern test chambers are designed to be energy-efficient, reducing operating costs and environmental impact while maintaining high performance.
Applications of Environmental Stability Test Chambers
Pharmaceutical and Biotechnology Industries: In these sectors, environmental stability testing is essential to ensure the safety and efficacy of drugs, vaccines, and biologics. ESTCs are used to simulate storage conditions and shelf-life testing under various temperature and humidity conditions.
Electronics Industry: Electronics, including semiconductors and consumer devices, are sensitive to environmental changes. Testing in environmental stability chambers helps ensure that these products can withstand temperature fluctuations, humidity, and other environmental factors without performance degradation.
Automotive Industry: Automobiles are exposed to diverse environmental conditions during their lifecycle. From extreme cold to intense heat and humidity, environmental stability test chambers are used to test components such as batteries, tires, electronics, and interior materials.
Food Industry: Packaging, shelf-life, and product integrity in food manufacturing are critical. ESTCs are used to simulate storage conditions and ensure that food products can withstand changes in temperature and humidity without compromising quality or safety.
Aerospace and Defense: Products and materials used in aerospace and defense applications are subjected to extreme conditions during operation. Stability testing ensures that components will perform under high stress, temperature extremes, and fluctuating atmospheric pressures.
Benefits of Environmental Stability Test Chambers
Ensuring Product Reliability: By simulating real-world conditions, ESTCs help manufacturers identify potential weaknesses in their products before they are released to the market. This leads to improved product reliability and fewer defects or failures in the field.
Regulatory Compliance: Industries like pharmaceuticals and electronics are subject to strict regulatory requirements. Environmental stability testing helps manufacturers comply with these regulations, providing documented evidence that their products meet required standards.
Quality Control and Improvement: Regular testing of products under varying environmental conditions enhances the overall quality control process, allowing manufacturers to refine product designs, materials, and processes for better performance.
Reducing Product Recalls: By identifying flaws early in the testing phase, manufacturers can prevent costly recalls and damage to their brand reputation. This also minimizes the risk of customer dissatisfaction due to product failure.
Cost Efficiency: Environmental stability chambers can reduce the need for expensive real-world testing or prototype testing in natural environments. They provide a faster, controlled, and repeatable testing process, ultimately saving money for manufacturers.
Choosing the Right Environmental Stability Test Chamber Supplier
Selecting the right supplier for Environmental Stability Test Chambers is critical for achieving accurate and reliable results. Here are a few factors to consider when making your choice:
Reputation and Experience: Look for a supplier with a proven track record of delivering high-quality, reliable chambers. Experience in providing solutions for industries similar to yours is a plus.
Customization Options: The best suppliers offer test chambers that can be customized to meet the specific needs of your testing requirements. Whether it’s temperature ranges, humidity settings, or the inclusion of additional features, customization is key to obtaining accurate test results.
Technical Support and Service: A reliable supplier will offer comprehensive after-sales support, including installation, training, and maintenance services. This ensures that the test chambers perform optimally throughout their lifespan.
Compliance with Standards: Ensure the supplier’s chambers meet industry-specific standards, such as ISO, ASTM, or FDA regulations. Compliance guarantees that the testing equipment will produce valid results and ensure product quality.
Cost and Value: While it’s important to consider the cost of the chamber, the value it provides in terms of accuracy, reliability, and efficiency is far more important. The supplier should offer a balance of quality and cost-effectiveness.
Visit Also:- Revolutionizing Plant Growth with Tissue Culture Chambers
Conclusion
Environmental Stability Test Chambers are indispensable tools for industries that require precise testing of products and materials under controlled environmental conditions. Whether you're testing pharmaceutical products, electronics, or automotive components, these chambers provide valuable insights into product performance and longevity. Selecting the right supplier ensures that manufacturers have access to the best technology, support, and customization options to meet their testing needs. By investing in high-quality Environmental Stability Test Chambers, companies can enhance product reliability, meet regulatory standards, and ultimately provide superior products to the market.
#EnvironmentalStability#TestChamber#StabilityTesting#EnvironmentalTesting#TemperatureHumidity#ProductTesting#ThermalShock#ClimaticChamber#ReliabilityTesting#EnvironmentalSimulation#TestingEquipment#ManufacturingStandards#IndustrialTesting#StabilityTest#ClimateControlledTesting#StressTesting#TechTesting#QualityControl#EnvironmentalConditions#ThermalStability
0 notes
Text
Sustainable Solutions: The Power of Low-Carbon Fuels

The global low-carbon fuel market is on the rise, driven by the urgent need to address climate change and reduce greenhouse gas emissions. This market encompasses a variety of fuels, including synthetic hydrocarbon fuels, ammonia, biofuels, and hydrogen, all designed to mitigate the environmental impact of traditional fossil fuels. According to the report, the market is projected to grow at a significant compound annual growth rate (CAGR) over the forecast period from 2022 to 2028.
What Are Low-Carbon Fuels?
Low-carbon fuels are alternative energy sources that produce fewer greenhouse gas emissions compared to conventional fossil fuels when utilized. They are essential for decarbonizing industries that are traditionally hard to electrify, such as aviation, shipping, and heavy-duty transportation. By transitioning to these fuels, companies and governments aim to achieve sustainability targets and comply with increasingly stringent environmental regulations.
Get Sample pages of Report: https://www.infiniumglobalresearch.com/reports/sample-request/40783
Key Types of Low-Carbon Fuels
Synthetic Hydrocarbon Fuels: Produced from renewable energy sources and carbon capture technologies, these fuels replicate the chemical structure of conventional fossil fuels, making them compatible with existing infrastructure.
Ammonia: Used primarily in the agricultural sector as a fertilizer, ammonia can also serve as a fuel in shipping and energy production, with the potential to be burned directly in engines or used in fuel cells.
Biofuels: Derived from biological materials, biofuels (such as biodiesel and bioethanol) can replace traditional diesel and gasoline, reducing carbon emissions and dependency on fossil fuels.
Hydrogen: Often referred to as the fuel of the future, hydrogen can be produced from various sources, including water (through electrolysis) and natural gas (via reforming). When used in fuel cells, hydrogen emits only water vapor as a byproduct.
Market Dynamics and Growth Drivers
Several factors are driving the growth of the low-carbon fuel market:
Government Policies and Regulations: Many countries are implementing policies to promote low-carbon technologies as part of their commitment to the Paris Agreement and other climate initiatives. Subsidies, tax incentives, and emissions trading systems are increasingly supporting the adoption of low-carbon fuels.
Rising Demand for Energy Transition: As industries and consumers seek to transition away from fossil fuels, the demand for low-carbon alternatives is growing. This trend is particularly evident in sectors with significant emissions, such as transportation and manufacturing.
Technological Advancements: Continuous innovations in production methods, such as improved carbon capture technologies and more efficient biofuel production processes, are making low-carbon fuels more viable and cost-effective.
Increased Investment: Investments from both public and private sectors are accelerating the development of low-carbon fuel infrastructure, including refineries, distribution networks, and fueling stations.
Regional Analysis
North America: The U.S. and Canada are leading the low-carbon fuel market, driven by government policies favoring renewable energy and significant investments in hydrogen and biofuels.
Europe: Europe is at the forefront of low-carbon fuel adoption, with ambitious climate targets and a strong regulatory framework. Countries like Germany, France, and the Netherlands are actively promoting the use of low-carbon fuels in transportation and industry.
Asia-Pacific: This region is experiencing rapid growth in the low-carbon fuel market, particularly in countries like China and India, where energy demand is high and the need for sustainable solutions is critical.
Latin America and Middle East & Africa: These regions are gradually increasing their focus on low-carbon fuels, primarily driven by a combination of energy diversification and the need to address environmental concerns.
Competitive Landscape
The low-carbon fuel market is highly competitive, with key players focusing on innovation and strategic partnerships. Notable companies include:
Neste: A global leader in renewable diesel and sustainable aviation fuel, Neste is heavily investing in R&D to enhance its biofuel production capabilities.
Air Products and Chemicals, Inc.: This company is a major player in hydrogen production, investing in large-scale hydrogen projects worldwide, including hydrogen fueling stations.
BP and Shell: Traditional oil and gas companies are transitioning towards low-carbon solutions by investing in biofuels, hydrogen, and carbon capture technologies.
Report Overview : https://www.infiniumglobalresearch.com/reports/global-low-carbon-fuel-market
Challenges and Opportunities
Despite the promising growth trajectory, the low-carbon fuel market faces challenges, including high production costs, limited infrastructure, and regulatory uncertainties. The establishment of a robust supply chain for low-carbon fuels is essential for widespread adoption.
However, opportunities abound as industries and governments seek innovative solutions to decarbonize. Collaborations between stakeholders, such as energy producers, technology developers, and regulatory bodies, can enhance research and development efforts, making low-carbon fuels more accessible and economically viable.
Conclusion
The global low-carbon fuel market is positioned for significant growth as the world shifts towards sustainable energy solutions. With the increasing demand for cleaner alternatives to fossil fuels and supportive government policies, low-carbon fuels like synthetic hydrocarbons, ammonia, biofuels, and hydrogen are set to play a crucial role in reducing greenhouse gas emissions. As technology advances and investment increases, this market will be pivotal in achieving global climate goals and transitioning to a more sustainable energy future.
Discover More of Our Reports
Hydroponic Fodder Systems Market
Mining Automation Market
0 notes
Text
The Role of 3D Models in Modern Biotechnology: A Focus on Alphabioregen

3D models have revolutionized the biotechnology sector by providing more accurate and dynamic representations of biological systems. Unlike traditional 2D models, which offer limited perspectives, 3D models mimic the natural environment of cells and tissues more effectively. This advancement allows researchers to study complex interactions, disease progression, and potential therapeutic interventions with greater precision. Alphabioregen, a leading player in the biotechnology field, is at the forefront of developing cutting-edge 3D models that drive innovation in medical research and product development.
The Advantages of 3D Models
One of the major benefits of 3D models is their ability to replicate real-life physiological conditions. Cells grown in 3D environments behave more like they would in the human body compared to 2D cell cultures. For instance, 3D models are invaluable for studying cancer, where tumors exhibit complex structures. This advancement enables more accurate testing of drug efficacy and the potential for personalized medicine. Alphabioregen's dedication to creating advanced 3D models helps researchers simulate these intricate biological systems, contributing to more targeted and effective treatments.
Alphabioregen’s Contribution to 3D Model Innovation
Alphabioregen is known for its innovative approach in creating 3D models for research purposes. Their models are used across various fields, including drug discovery, tissue engineering, and regenerative medicine. Alphabioregen’s proprietary technology allows for the creation of highly detailed and customizable 3D structures, enabling scientists to explore new possibilities in medical research. By offering tailored solutions, Alphabioregen ensures that researchers have the most effective tools at their disposal to push the boundaries of biotechnological advancements.
Applications of 3D Models in Drug Testing and Development
In the drug testing and development phase, 3D models have proven to be indispensable. They provide a more accurate representation of how drugs interact with human tissues, thereby reducing the need for animal testing and increasing the chances of success in clinical trials. Alphabioregen’s 3D models are specifically designed to cater to the evolving needs of pharmaceutical companies, offering them reliable platforms to test new drugs more efficiently and ethically.
Conclusion: The Future of 3D Models in Biotechnology
As biotechnology continues to evolve, the use of 3D models will become increasingly prevalent. Alphabioregen is poised to lead this transformation by providing high-quality 3D models that enhance our understanding of biological systems and improve drug development processes. Their contributions are paving the way for more accurate, efficient, and humane research in the field of biotechnology.
0 notes
Text
Biometric Authentication: Securing Transactions with Evolute’s Innovations

The rise of digital transactions has brought both convenience and new security challenges. As more people in India turn to online banking, e-commerce, and digital wallets, the demand for robust security measures has never been higher. Biometric authentication stands out as a leading solution in this landscape, offering a seamless way to secure transactions. This article will explore how Evolute, a leading Embedded Systems company in India, is leveraging innovative biometric technologies to enhance transaction security across its subsidiaries—Fintech, Cleantech, and Glomore.
The Growing Need for Security in Digital Transactions
Recent statistics indicate that India is rapidly embracing digital payments, with the total number of digital transactions reaching 7.42 billion in 2023, according to the National Payments Corporation of India (NPCI). This represents a 41% increase from the previous year. However, this surge in digital transactions also opens the door to cyber threats. A report from CyberPeace Foundation revealed that 65% of Indians feel vulnerable while making online transactions, highlighting the need for stronger security measures.
What is Biometric Authentication?
Biometric authentication uses unique biological traits—such as fingerprints, facial recognition, and iris scans—to verify a user's identity. Unlike traditional methods, like passwords or PINs, which can be forgotten or stolen, biometric data is unique to each individual and cannot be easily replicated. This makes it an ideal solution for securing digital transactions.
Evolute’s Innovations in Biometric Authentication
Evolute is at the forefront of developing cutting-edge biometric solutions tailored for the Indian market. Here’s a closer look at how each subsidiary contributes to this innovative approach:
1. Fintech: Revolutionizing Payment Security
Fintech specializes in manufacturing finance-related electronic devices, incorporating biometric sensors that enhance transaction security. Their latest range of smart payment devices features fingerprint scanners, allowing users to authorize transactions with just a touch. A study from the Indian School of Business indicates that 70% of consumers prefer biometric authentication over traditional password methods, reflecting the growing trust in this technology.
2. Cleantech: Pioneering Safe Battery Solutions
Cleantech focuses on manufacturing and providing services for batteries, which are integral to many electronic devices. By integrating biometric authentication into battery management systems, Cleantech ensures that only authorized personnel can access and manage sensitive data regarding battery performance and usage. This adds an extra layer of security, especially for electric vehicles (EVs) and renewable energy solutions. With India aiming for 30% of all vehicles to be electric by 2030, Cleantech’s innovations are crucial for maintaining security in this growing sector.
3. Glomore: Industrial Products with Biometric Safeguards
Glomore manufactures batteries and industrial products, incorporating biometric solutions to ensure the safety and security of operational environments. For example, their advanced industrial equipment now includes facial recognition systems that restrict access to authorized users only. This significantly reduces the risk of unauthorized use and increases overall operational safety.
The Advantages of Biometric Authentication
Implementing biometric authentication systems offers several benefits:
Enhanced Security: Biometric traits are hard to forge, making it difficult for cybercriminals to gain unauthorized access.
Convenience: Users can complete transactions quickly without remembering complex passwords.
User Trust: With increasing awareness of security threats, consumers are more likely to trust brands that prioritize biometric authentication.
According to a recent survey by Deloitte, 85% of Indian consumers expressed a preference for services that utilize biometric authentication, indicating a strong demand for this technology.
Future of Biometric Authentication in India
The future of biometric authentication looks promising in India. With the government pushing for digital India initiatives, and companies like Evolute leading the way in innovation, the adoption of biometric solutions is set to grow. A report by Statista predicts that the biometric authentication market in India will reach $4.1 billion by 2026, growing at a CAGR of 19.3%.
Conclusion
As digital transactions continue to rise, securing these transactions with innovative technologies becomes paramount. Evolute, through its subsidiaries—Fintech, Cleantech, and Glomore—is at the forefront of integrating biometric authentication into everyday transactions. This not only enhances security but also fosters consumer confidence in digital payment systems. As India marches toward a more digital future, the role of biometric authentication will only become more significant. Embracing this technology is essential for businesses and consumers alike, ensuring safe, secure, and seamless transactions for everyone.
#Evolute Embedded Systems Company#Fintech#Cleantech#Glomore#FIntech device#Cleantech EV#Cleantech batteries#Cleantech Battery Services#Glomore EV#Glomore Batteries#Glomore Battery Services#Glomore industry products#Fintech POS machine
0 notes
Text
The Importance of Biometric Identification in the Education Sector
In today’s digital era, ensuring security, efficiency, and accountability in the education sector is more critical than ever. Educational institutions have become increasingly complex, with a growing number of students, staff, and visitors moving through campuses daily. To streamline operations and enhance safety, many schools and universities are turning to biometric identification systems. These systems provide a secure, reliable way to verify individuals’ identities based on unique biological traits, offering a more robust alternative to traditional ID cards or passwords.

What is Biometric Identification?
Biometric identification refers to the use of unique physical or behavioral characteristics — such as fingerprints, facial recognition, iris scans, or voice patterns — to verify an individual’s identity. Unlike traditional identification methods, such as passwords or ID cards, biometric data is nearly impossible to replicate or steal. This makes biometric systems highly secure and efficient for various applications, including access control, attendance tracking, and exam authentication.
Why Biometric Identification is Essential in Educational Institutions
1. Enhanced Security on Campus
Security is a top priority for educational institutions, especially in today’s world, where incidents like unauthorized access and threats to student safety are growing concerns. Biometric identification provides an advanced layer of security by ensuring that only authorized individuals — students, staff, and registered visitors — can access school buildings, dormitories, and other restricted areas.
For example, biometric access control systems can replace traditional keys or ID cards, which can be lost or stolen. With biometric identification, a student’s fingerprint, facial scan, or other biometric trait is used to grant access to specific areas, reducing the risk of unauthorized entry and enhancing the overall safety of the campus.
2. Accurate Attendance Management
One of the most common applications of biometric identification in education is attendance management. Manually taking attendance can be time-consuming, prone to errors, and easily manipulated. Traditional methods such as paper-based attendance registers or even digital ID card systems can fall short when it comes to preventing issues like “buddy punching” (where one student signs in for another).
Biometric identification, on the other hand, ensures accuracy and accountability. For example, students can be required to scan their fingerprints or use facial recognition to mark their attendance, ensuring that only the individual in question can verify their presence. This not only improves accuracy but also saves time for teachers and administrators, allowing them to focus on other important tasks.
Furthermore, biometric attendance systems integrate seamlessly with school management software, providing real-time updates to parents and administrators about a student’s attendance record. This transparency helps maintain accountability and keeps all stakeholders informed.
3. Streamlined Exam Authentication
Another critical area where biometric identification is making a significant impact is exam authentication. In many institutions, verifying student identity during exams can be challenging, especially in large classes or exam halls. Traditional methods like checking photo IDs can be time-consuming and may not prevent impersonation fraud.
By implementing biometric authentication systems during exams, institutions can verify a student’s identity quickly and accurately. For example, a facial recognition system can match the student’s face with their registered biometric data, ensuring that only the right individual takes the exam. This reduces the risk of fraud and enhances the overall integrity of the examination process.
4. Improved Time Management for Staff and Students
Managing the daily schedules of students, teachers, and administrative staff in educational institutions can be complex. With biometric identification, the entire process becomes more streamlined. For example, staff members can use biometric systems to clock in and out, providing accurate work hour data without the need for manual time tracking. This data can then be integrated into payroll systems to ensure fair and accurate payment.
For students, biometric identification can be used to manage library access, cafeteria payments, and even extracurricular activities. Instead of carrying multiple cards or remembering passwords, students can use their fingerprint or facial scan to access these services, simplifying their daily routines.
5. Preventing Identity Theft and Impersonation
Identity theft and impersonation can be serious issues in educational institutions, especially during important processes like admissions, exams, or graduation ceremonies. Traditional ID cards or passwords can be easily shared, misplaced, or misused, leading to fraudulent activities.
Biometric identification provides a foolproof solution to this problem. Since biometric traits are unique to each individual and cannot be shared or duplicated, the risk of identity theft is virtually eliminated. For instance, using fingerprint or facial recognition during the admission process ensures that only the rightful candidate is admitted. Similarly, during graduation ceremonies, biometric systems can ensure that only the actual graduate receives their diploma.
6. Cost-Effective and Sustainable Solutions
While implementing biometric identification systems may require an initial investment, they can be more cost-effective in the long run compared to traditional methods. Physical ID cards can be easily lost, damaged, or require frequent replacements, leading to additional costs for the institution. Biometric systems, on the other hand, require minimal maintenance once installed and do not involve recurring costs like reprinting ID cards.
Moreover, biometric identification systems contribute to sustainability by reducing the need for paper-based attendance registers, ID cards, and other physical materials. This aligns with the growing focus on eco-friendly solutions in education.
Conclusion
In today’s education sector, biometric identification plays a crucial role in enhancing security, streamlining operations, and improving accountability. From access control to attendance management and exam authentication, biometric systems offer a reliable and secure way to manage large numbers of students and staff efficiently.
At Spintly, we offer cutting-edge biometric identification and access control solutions designed to meet the unique needs of educational institutions. Our solutions not only enhance campus security but also improve the overall efficiency of managing student and staff attendance. One of our successful implementations includes collaboration with Manipal, a leading educational institution, where Spintly’s biometric solutions have played a pivotal role in enhancing security and automating attendance processes.
If you’re looking to revolutionize your educational institution’s security and operational efficiency, consider integrating biometric identification systems to provide a safe and seamless experience for everyone involved.
#access control system#access control solutions#visitor management system#accesscontrol#mobile access#spintly#smartacess#biometrics
0 notes
Text
The global sulfated biochemicals market size was valued at USD 13,645.89 million in 2023 and is projected to grow at a CAGR of 4.68% from 2023 to 2032.In the realm of biochemicals, sulfated compounds play a pivotal role across various industries, offering a wide range of applications from pharmaceuticals to cosmetics and beyond. The sulfated biochemicals market has been steadily expanding, driven by advancements in biotechnology, increasing research activities, and growing consumer demand for sustainable and effective products.
Browse the full report at https://www.credenceresearch.com/report/sulfated-biochemicals-market
Understanding Sulfated Biochemicals
Sulfated biochemicals refer to compounds that contain sulfate groups (-OSO3^-) attached to organic molecules. These sulfated compounds exhibit unique properties that make them valuable in biological and industrial applications. They are often synthesized through enzymatic or chemical processes, ensuring purity and efficacy in their intended applications.
Key Applications in Pharmaceuticals
In pharmaceuticals, sulfated biochemicals are extensively used due to their ability to modulate biological activities. For instance, heparin, a sulfated glycosaminoglycan, is widely employed as an anticoagulant in the treatment of thrombosis and related disorders. Moreover, sulfated compounds such as sulfated polysaccharides have shown promise in antiviral therapies, inhibiting viral attachment and replication.
Cosmetics and Personal Care Products
The cosmetic industry utilizes sulfated biochemicals for their diverse functionalities. Sulfated polysaccharides derived from marine algae, for example, are valued for their moisturizing and antioxidant properties, making them popular ingredients in skincare formulations. These compounds help maintain skin hydration and protect against oxidative stress, enhancing their appeal in the cosmetics market.
Environmental and Industrial Applications
Beyond healthcare and cosmetics, sulfated biochemicals find applications in diverse industrial sectors. They serve as surfactants and emulsifiers in manufacturing processes, aiding in the production of stable emulsions and foams. Additionally, sulfated compounds contribute to environmental remediation efforts, facilitating the breakdown of organic pollutants in wastewater treatment systems.
Market Trends and Growth Drivers
The sulfated biochemicals market is witnessing robust growth driven by several factors. Technological advancements in bioprocessing have improved the scalability and cost-effectiveness of sulfated compound production. Moreover, increasing awareness regarding sustainable practices has fueled the demand for bio-based alternatives, further boosting market expansion.
Challenges and Opportunities
Despite the promising growth prospects, the sulfated biochemicals market faces challenges such as regulatory complexities and variability in raw material availability. However, ongoing research and development efforts are focused on overcoming these challenges, aiming to unlock new applications and improve production efficiencies.
Future Outlook
Looking ahead, the sulfated biochemicals market is poised for continued growth, supported by innovation in biotechnology and increasing investments in sustainable product development. The integration of sulfated compounds into novel therapeutic formulations and industrial applications holds significant promise, paving the way for a more diverse and sustainable biochemical landscape.
Leading players in the sulfated biochemicals market:
Thermo Fisher Scientific
Merck KGaA
Cayman Chemical
Santa Cruz Biotechnology
Creative Enzymes
Iris Biotech GmbH
LGC Limited
Sisco Research Laboratories Pvt. Ltd.
Boston Scientific Corporation
MedChemExpress (MCE)
Sweet Cures
Toronto Research Chemicals
Bioiberica S.A.U
Abcam plc
Adooq Bioscience
BioVision Inc.
BOC Sciences
APExBIO Technology LLC
Hello Bio Ltd.
Glentham Life Sciences
Segmentation Analysis Sulfated Biochemicals Market:
By Type:
Glycosaminoglycans (GAGs)
Sulfolipids
Sulfated Polysaccharides
Others
By Application:
Pharmaceuticals
Cosmetics
Others
By Source:
Animal-derived
Plant-derived
By Region
North America
The U.S.
Canada
Mexico
Europe
Germany
France
The U.K.
Italy
Spain
Rest of Europe
Asia Pacific
China
Japan
India
South Korea
Southeast Asia
Rest of Asia Pacific
Latin America
Brazil
Argentina
Rest of Latin America
Middle East & Africa
GCC Countries
South Africa
Rest of the Middle East and Africa
About Us:
Credence Research is committed to employee well-being and productivity. Following the COVID-19 pandemic, we have implemented a permanent work-from-home policy for all employees.
Contact:
Credence Research
Please contact us at +91 6232 49 3207
Email: [email protected]
0 notes
Text
Laser Scanning Services - What Every Individual Should Consider
In today's highly competitive marketplace, CAD scanning services have become essential in product development. Through integrating 3D scanning in the process of designing, companies can see significant improvement in efficiency and accuracy. 3D scanning can facilitate the swift capture of intricate geometric data, transforming the physical object into digital model. Digital transformations streamline processes, decreases errors and increases collaboration between team members. With the ability to rapidly and accurately transform physical prototypes into digital assets, product designers can improve designs more quickly and more efficiently, thereby speeding the time to market and decreasing the cost of traditional design techniques. The reverse and scanning of 3D scans are essential elements of modern-day product development. By utilizing 3D scanning engineers can get exact measurements and the details of existing objects, which can be later used to carry out 3D reverse engineering. This is a great method in reproducing complicated parts and enhancing existing designs. 3D measurement tools provide the needed data in order to make sure that new designs are compatible with existing components, thus reducing the possibility of errors and revisions. The integration of 3D scanning in the process of development does not just improve accuracy, but also boosts creativity as designers are able to explore new possibilities as well as create more intricate and complex designs. The use of 3D laser scanning reverse engineering techniques can bring numerous benefits to different industries. Click on the below mentioned website, if you're looking for more details about laser scanning services.

For instance in the automotive or aerospace industries, laser scanning services are utilized to create precise digital models of intricate components. These models are vital to ensure quality control and that parts meet stringent industry standards. Furthermore reverse engineering using 3D scans helps in the restoration and maintenance of legacy parts which may no longer be in production. By digitizing these parts manufacturers can make exact copies or make the necessary adjustments to improve efficiency, thus prolonging the life span of important equipment and machinery. CAD scanning doesn't just apply to industrial use; it plays a major role in the consumer product sector. Companies offering 3D measurement services can help in the design and improvement of products such as household appliances, electronics, and even fashion products. By employing 3D scanning services designers can develop high-quality prototypes that are accurate and then improve their designs prior to mass production. This reduces the likelihood of errors and enhances the overall quality of the final product. Furthermore, the ability to carry out 3D scanning and reverse engineering allows for customizing and personalizing products to meet particular customer preferences and needs and thereby increasing customer satisfaction and brand loyalty.
The healthcare industry also gains significantly from 3D scanning and reverse engineering in 3D. Medical professionals employ CAD scanning to build accurate digital images of anatomy. This aids in the creation of orthotics, prosthetics and surgical implants. These 3D laser scanning services allow the production of patient-specific devices that are perfect and work optimally. Additionally, 3D measurement services are employed in medical research and education which provide precise and precise models for research and training to aid in training and study. The ability to accurately replicate biological structures enhances the effectiveness of medical treatments and contributes to the advancement and advancement of medical science. In conclusion, CAD scanning services have transformed the development of products across a variety of industries. Through the use of 3D scanning technology, companies can improve the accuracy and efficiency of their development processes. Integrating 3D scanner services as well as 3D laser scanning reverse engineering into workflows doesn't just streamline development but also fosters innovation and improves the quality of products. Whether in industrial manufacturing, consumer products, and healthcare settings, the benefits of 3D measurement services as well as laser scanning services are evident. As technology advances, the adoption of CAD scanning will undoubtedly be a key factor for the development of products in the near future, enabling companies to remain ahead of the curve and meet the ever-changing needs of the market.
1 note
·
View note
Text
Biometric Security: The Future of Authentication Explained
Biometric security is emerging as a leading solution, offering enhanced security and convenience by leveraging unique biological traits for authentication. Let's explore the future of authentication through biometric security, its benefits, challenges, and potential applications. Understanding Biometric Security What is Biometric Security? Biometric security refers to the use of biological characteristics—such as fingerprints, facial features, iris patterns, and voice recognition—to verify an individual's identity. Unlike traditional authentication methods that rely on passwords or PINs, biometrics provide a more secure and user-friendly approach by utilizing inherent physical traits that are difficult to replicate or steal. Types of Biometric Authentication - Fingerprint Recognition: One of the most common biometric methods, fingerprint recognition involves scanning and comparing the unique patterns of an individual's fingerprints to authenticate their identity. - Facial Recognition: This method uses algorithms to analyze and compare facial features captured in an image or video with a stored template to verify identity. - Iris and Retina Scanning: These methods involve capturing detailed images of the iris or retina, which have unique patterns, and comparing them with stored data for authentication. - Voice Recognition: Voice recognition analyzes vocal characteristics, such as pitch, tone, and cadence, to verify a person's identity. - Behavioral Biometrics: This emerging field includes techniques like gait analysis, keystroke dynamics, and even mouse movements to authenticate users based on their behavior patterns. Benefits of Biometric Security Enhanced Security Biometric security offers a higher level of protection compared to traditional methods. Since biometric traits are unique to each individual and difficult to replicate, the risk of unauthorized access is significantly reduced. This makes biometrics particularly effective in preventing identity theft, fraud, and other cyber threats. Convenience and User Experience Biometric authentication provides a seamless and convenient user experience. Users no longer need to remember complex passwords or carry physical tokens. A quick fingerprint scan or facial recognition can grant access to systems and services instantly, enhancing productivity and user satisfaction. Reduced Reliance on Passwords Passwords are inherently vulnerable to attacks such as phishing, brute force, and social engineering. Biometric security reduces the reliance on passwords, minimizing the risks associated with password management. This shift can lead to fewer security breaches and lower administrative overhead for password resets and recovery. Challenges and Considerations Privacy Concerns The use of biometric data raises significant privacy concerns. Biometric information is highly sensitive, and any breach or misuse can have serious implications for individuals. It is essential to implement robust data protection measures, such as encryption and secure storage, to safeguard biometric data from unauthorized access. False Positives and False Negatives Biometric systems are not infallible and can produce false positives (incorrectly identifying an unauthorized user as authorized) or false negatives (failing to recognize an authorized user). Continuous improvement of biometric algorithms and technologies is necessary to minimize these errors and enhance accuracy. Cost and Implementation Implementing biometric security solutions can be costly, requiring investment in specialized hardware and software. Organizations must consider the total cost of ownership, including maintenance and updates, when adopting biometric technologies. Additionally, integrating biometrics into existing systems can be complex and may require significant technical expertise. Applications of Biometric Security Financial Services In the financial sector, biometric security is used to enhance the authentication process for banking services, mobile payments, and ATM access. Biometric authentication provides an additional layer of security, protecting against unauthorized transactions and ensuring that only authorized individuals can access financial accounts. Healthcare Biometric security is transforming the healthcare industry by improving patient identification, streamlining access to medical records, and enhancing the security of prescription management. Biometric authentication ensures that only authorized healthcare professionals can access sensitive patient information, reducing the risk of data breaches and fraud. Government and Border Control Governments and border control agencies are increasingly adopting biometric security for identity verification and access control. Biometric passports, facial recognition at airports, and fingerprint scanning for visa applications are some examples of how biometrics are used to enhance security and streamline processes in border control and immigration. Corporate Security Organizations are leveraging biometric security to protect sensitive data and ensure secure access to corporate networks and facilities. Biometric authentication can be used for employee access control, secure login to workstations, and protection of confidential information, enhancing overall security posture. Consumer Electronics Biometric security is becoming ubiquitous in consumer electronics, with smartphones, laptops, and other devices incorporating fingerprint sensors, facial recognition cameras, and voice recognition features. These advancements provide users with a secure and convenient way to unlock devices and access services, improving overall user experience. The Future of Biometric Security Advancements in Technology The future of biometric security is set to be shaped by continuous advancements in technology. Innovations in artificial intelligence (AI) and machine learning (ML) are enhancing the accuracy and reliability of biometric systems. These technologies can analyze vast amounts of data, identify patterns, and improve the performance of biometric algorithms. Multimodal Biometrics Multimodal biometrics involves combining multiple biometric methods to enhance security and accuracy. By using more than one biometric trait for authentication, such as combining fingerprint and facial recognition, the likelihood of false positives and false negatives is significantly reduced. This approach provides a higher level of security and can be tailored to specific use cases and requirements. Integration with IoT and Wearables The integration of biometric security with the Internet of Things (IoT) and wearable devices is expected to drive innovation in authentication methods. Wearable devices, such as smartwatches and fitness trackers, can incorporate biometric sensors to provide continuous authentication based on physiological data. This seamless integration enhances security and user convenience in various applications. Regulatory and Ethical Considerations As biometric security becomes more prevalent, regulatory and ethical considerations will play a crucial role in shaping its adoption. Governments and regulatory bodies will need to establish clear guidelines and standards for the use of biometric data, ensuring that privacy and security are maintained. Ethical considerations, such as informed consent and transparency, will also be essential to address concerns and build trust among users. In summary, biometric security represents the future of authentication, offering enhanced security and convenience by leveraging unique biological traits. As technology continues to advance, biometric authentication methods will become more accurate, reliable, and widely adopted across various industries. By addressing privacy concerns and ethical considerations, organizations can harness the potential of biometric security to protect against evolving cyber threats and provide a seamless user experience. Read the full article
0 notes
Text
Biometric Security: The Future of Authentication Explained
Biometric security is emerging as a leading solution, offering enhanced security and convenience by leveraging unique biological traits for authentication. Let's explore the future of authentication through biometric security, its benefits, challenges, and potential applications. Understanding Biometric Security What is Biometric Security? Biometric security refers to the use of biological characteristics—such as fingerprints, facial features, iris patterns, and voice recognition—to verify an individual's identity. Unlike traditional authentication methods that rely on passwords or PINs, biometrics provide a more secure and user-friendly approach by utilizing inherent physical traits that are difficult to replicate or steal. Types of Biometric Authentication - Fingerprint Recognition: One of the most common biometric methods, fingerprint recognition involves scanning and comparing the unique patterns of an individual's fingerprints to authenticate their identity. - Facial Recognition: This method uses algorithms to analyze and compare facial features captured in an image or video with a stored template to verify identity. - Iris and Retina Scanning: These methods involve capturing detailed images of the iris or retina, which have unique patterns, and comparing them with stored data for authentication. - Voice Recognition: Voice recognition analyzes vocal characteristics, such as pitch, tone, and cadence, to verify a person's identity. - Behavioral Biometrics: This emerging field includes techniques like gait analysis, keystroke dynamics, and even mouse movements to authenticate users based on their behavior patterns. Benefits of Biometric Security Enhanced Security Biometric security offers a higher level of protection compared to traditional methods. Since biometric traits are unique to each individual and difficult to replicate, the risk of unauthorized access is significantly reduced. This makes biometrics particularly effective in preventing identity theft, fraud, and other cyber threats. Convenience and User Experience Biometric authentication provides a seamless and convenient user experience. Users no longer need to remember complex passwords or carry physical tokens. A quick fingerprint scan or facial recognition can grant access to systems and services instantly, enhancing productivity and user satisfaction. Reduced Reliance on Passwords Passwords are inherently vulnerable to attacks such as phishing, brute force, and social engineering. Biometric security reduces the reliance on passwords, minimizing the risks associated with password management. This shift can lead to fewer security breaches and lower administrative overhead for password resets and recovery. Challenges and Considerations Privacy Concerns The use of biometric data raises significant privacy concerns. Biometric information is highly sensitive, and any breach or misuse can have serious implications for individuals. It is essential to implement robust data protection measures, such as encryption and secure storage, to safeguard biometric data from unauthorized access. False Positives and False Negatives Biometric systems are not infallible and can produce false positives (incorrectly identifying an unauthorized user as authorized) or false negatives (failing to recognize an authorized user). Continuous improvement of biometric algorithms and technologies is necessary to minimize these errors and enhance accuracy. Cost and Implementation Implementing biometric security solutions can be costly, requiring investment in specialized hardware and software. Organizations must consider the total cost of ownership, including maintenance and updates, when adopting biometric technologies. Additionally, integrating biometrics into existing systems can be complex and may require significant technical expertise. Applications of Biometric Security Financial Services In the financial sector, biometric security is used to enhance the authentication process for banking services, mobile payments, and ATM access. Biometric authentication provides an additional layer of security, protecting against unauthorized transactions and ensuring that only authorized individuals can access financial accounts. Healthcare Biometric security is transforming the healthcare industry by improving patient identification, streamlining access to medical records, and enhancing the security of prescription management. Biometric authentication ensures that only authorized healthcare professionals can access sensitive patient information, reducing the risk of data breaches and fraud. Government and Border Control Governments and border control agencies are increasingly adopting biometric security for identity verification and access control. Biometric passports, facial recognition at airports, and fingerprint scanning for visa applications are some examples of how biometrics are used to enhance security and streamline processes in border control and immigration. Corporate Security Organizations are leveraging biometric security to protect sensitive data and ensure secure access to corporate networks and facilities. Biometric authentication can be used for employee access control, secure login to workstations, and protection of confidential information, enhancing overall security posture. Consumer Electronics Biometric security is becoming ubiquitous in consumer electronics, with smartphones, laptops, and other devices incorporating fingerprint sensors, facial recognition cameras, and voice recognition features. These advancements provide users with a secure and convenient way to unlock devices and access services, improving overall user experience. The Future of Biometric Security Advancements in Technology The future of biometric security is set to be shaped by continuous advancements in technology. Innovations in artificial intelligence (AI) and machine learning (ML) are enhancing the accuracy and reliability of biometric systems. These technologies can analyze vast amounts of data, identify patterns, and improve the performance of biometric algorithms. Multimodal Biometrics Multimodal biometrics involves combining multiple biometric methods to enhance security and accuracy. By using more than one biometric trait for authentication, such as combining fingerprint and facial recognition, the likelihood of false positives and false negatives is significantly reduced. This approach provides a higher level of security and can be tailored to specific use cases and requirements. Integration with IoT and Wearables The integration of biometric security with the Internet of Things (IoT) and wearable devices is expected to drive innovation in authentication methods. Wearable devices, such as smartwatches and fitness trackers, can incorporate biometric sensors to provide continuous authentication based on physiological data. This seamless integration enhances security and user convenience in various applications. Regulatory and Ethical Considerations As biometric security becomes more prevalent, regulatory and ethical considerations will play a crucial role in shaping its adoption. Governments and regulatory bodies will need to establish clear guidelines and standards for the use of biometric data, ensuring that privacy and security are maintained. Ethical considerations, such as informed consent and transparency, will also be essential to address concerns and build trust among users. In summary, biometric security represents the future of authentication, offering enhanced security and convenience by leveraging unique biological traits. As technology continues to advance, biometric authentication methods will become more accurate, reliable, and widely adopted across various industries. By addressing privacy concerns and ethical considerations, organizations can harness the potential of biometric security to protect against evolving cyber threats and provide a seamless user experience. Read the full article
0 notes
Text
Quantum Computing Drug Discovery in Healthcare
Quantum Computing Drug Discovery Quantum computing has revolutionized computer technologies. With medication development and therapy at its Centre, this innovative technology could transform several sectors. Quantum computers can process massive amounts of data at previously unheard-of speeds because they employ qubits instead of bits. This talent expands medical research, notably in drug discovery and development.
Drug Discovery Traditional Drug Discovery
It frequently takes more than ten years and billions of dollars to bring a novel medication to market through the laborious and expensive process of traditional drug discovery. The main causes of this extended period are the intricacy of biological systems and the rigorous testing necessary to guarantee efficacy and safety. The conventional method consists of multiple, potentially problematic phases, such as target identification, lead compound discovery, preclinical testing, and clinical trials.
How Quantum Computing Could Revolutionize Drug development could be greatly accelerated by quantum computing. Quantum computers are able to precisely replicate molecular interactions at the atomic level by utilising quantum mechanics. This feature greatly reduces the trial-and-error approach common in previous methodologies by enabling researchers to predict the behavior of various substances.
The Functions of Quantum Computing Drug Discovery Molecular Modelling and Quantum Simulations The capacity of quantum computing to carry out intricate quantum simulations and molecular modelling lies at the core of its potential in drug discovery. These activities are too complex for traditional computers to handle because there are so many conceivable combinations and interactions between molecules. However, the processing speed of these data can be exponentially increased by quantum computers, enabling precise modelling of molecular behaviors and structures.
Increased Algorithmic Performance Quantum algorithms are specifically developed to address optimization difficulties and solve eigenvalue problems. The Quantum Approximate Optimization Algorithm (QAOA) and Variationally Quantum Eigen solver are examples. These algorithms quickly identify the best drug candidates by evaluating huge chemical landscapes that classical computers cannot traverse.
Quantum Computing In Healthcare Precision medicine is one of quantum computing’s most interesting medical applications. Quantum Computing Drug Discovery can help create genetically tailored drugs by studying molecular quantum states. This personalized strategy reduces side effects and improves therapeutic efficacy, ushering in a new era of personalized healthcare.
Accelerating Vaccine Development COVID-19 showed how urgent vaccine development is. Quantum computing can speed up this process by simulating virus-cell interactions and predicting vaccine composition. This talent could reduce vaccine development time, allowing for faster health risk response.
Boosting Chemicals Existing chemical compounds can be improved using quantum computers to optimize medicinal benefits and limit side effects. This optimization method simulates various molecule configurations to find the optimum shape for a therapeutic target, improving pharmaceutical efficacy.
Present Advancements and Upcoming Opportunities Partnerships with Industry and Research Projects Developments in Quantum Computing Drug Discovery being driven by multiple partnerships between IT heavyweights and pharmaceutical industries. Leading pharmaceutical companies are collaborating with companies like IBM, Google, and Microsoft to create quantum apps and algorithms specifically for biomedical research. These collaborations are essential to converting the theory of quantum computing into workable solutions that can help patients.
Overcoming Obstacles in Technology
Quantum computing is still in its infancy and faces a number of technological obstacles, despite its potential. These include scaling up qubit systems, preserving quantum coherence, and error correction. The goal of current research and development is to get past these obstacles and increase the accessibility and dependability of quantum computing for real-world medical applications.
Ethics and Regulation Concerns It will be crucial to address ethical and regulatory issues as quantum computing develops. Careful control is necessary in several crucial areas, including handling the ethical implications of personalized medicine, safeguarding patient data, and ensuring the safety and efficacy of medications produced from quantum technology. It is imperative that regulatory frameworks adapt in lockstep with technological developments to guarantee the responsible realization of quantum computing’s advantages.
Quantum Computing In Medicine Medicine could undergo a transformation thanks to quantum computing, especially in the area of medication development. How to do it is as follows:
Complex molecular: Complex molecular simulation is a challenge for conventional computers due to the complex quantum behavior of molecules. But because quantum computers are capable of handling these intricacies, it is possible to mimic drug interactions with proteins and other targets in the body with greater accuracy.
Faster medication development: Compared to present approaches, which can take years or even decades, researchers may be able to design and test novel treatments considerably more quickly with quantum simulations. This may result in patients having access to life-saving therapies more quickly.
Novel drug class: Using quantum computing, it may even be possible to create whole new drug classes that target proteins that were previously thought to be “undruggable”. For illnesses for which there are now no viable therapeutic choices, this provides hope.
It is imperative to bear in mind that quantum computing remains an incipient technology. Despite the enormous potential, obstacles must be removed before Quantum Computing Drug Discovery is widely used. Still, research is being done, and developments in quantum computing have the potential to drastically alter the field of medicine in the future.
In summary The medical industry is about to undergo a transformation thanks to quantum computing, especially in the area of medication discovery. Its capacity to execute intricate simulations and maximize molecular interactions at previously unheard-of rates offers hope for quicker and more effective drug development procedures.
Quantum Computing Drug Discovery has the potential to revolutionize precision medicine, vaccine development, and chemical compound optimization as research advances and technological obstacles are overcome. This would ultimately improve patient outcomes and advance global healthcare.
Read more on Govindhtech.com
#QuantumComputing#DrugDiscovery#QuantumComputingDrugDiscovery#Healthcare#cloudcomputing#cloud#technology#technews#news#govindhtech
0 notes
Text
In the early 2040s, breakthroughs in nanotechnology and marine biology converged to create a revolutionary field known as Foraminiferan Nanotechnology (FNT). This innovative domain leveraged the structural and functional properties of foraminifers, tiny marine organisms known for their intricate calcium carbonate shells, to develop advanced nanoscale devices. Scientists discovered that the precise and durable architecture of foraminifer shells could be replicated to create nano-bots capable of performing complex tasks within various environments, from medical applications inside the human body to environmental monitoring in the deep sea.
As FNT matured, researchers introduced the concepts of nodical and deontic frameworks to enhance the functionality and ethical deployment of these nanobots. The nodical framework, inspired by the nodal points in biological networks, enabled the creation of highly interconnected and adaptive nanobot swarms. These swarms could communicate and coordinate with each other in real-time, forming dynamic networks capable of responding to changing conditions with remarkable efficiency. This development was crucial in fields like targeted drug delivery, where precise and adaptive responses were necessary to treat complex diseases such as cancer.
The deontic framework, rooted in ethical philosophy, provided a structured approach to ensure the responsible use of FNT. By embedding deontic logic within the programming of nanobots, developers established ethical guidelines that governed their behavior, preventing misuse and ensuring compliance with societal values. This included protocols for privacy, consent, and environmental impact, which were critical as FNT applications expanded into various sectors. By the late 2050s, Foraminiferan Nanotechnology, enhanced by nodical and deontic principles, had become an integral part of technological advancement, driving progress while maintaining a strong ethical foundation.
0 notes
Text
The Power of Biometrics: Exploring Advanced Sensor Technologies

According to the report, the global biometric sensors market is projected to grow at a compound annual growth rate (CAGR) of 11% over the forecast period of 2022-2028. The market, which was valued at around USD 4,400 million in 2022, is expected to reach nearly USD 8,300 million by 2028, showcasing significant growth potential.
What Are Biometric Sensors?
Biometric sensors are advanced technologies that capture and analyze biological data to authenticate individuals based on unique physical characteristics. These sensors are widely used for applications such as fingerprint recognition, facial recognition, iris scanning, voice recognition, and vein pattern detection. They play a critical role in enhancing security, identity verification, and access control across various industries, including healthcare, finance, government, and consumer electronics.
Get Sample pages of Report: https://www.infiniumglobalresearch.com/reports/sample-request/877
Market Dynamics and Growth Drivers
The biometric sensors market is being driven by several key factors:
Increasing Demand for Secure Authentication: With the rise of cyber threats and data breaches, there is a growing demand for more secure authentication methods. Biometric sensors provide enhanced security by offering unique, non-replicable identification methods, making them crucial for industries such as banking, healthcare, and government services.
Expansion of Consumer Electronics: The widespread adoption of biometric sensors in smartphones, laptops, and wearable devices is fueling market growth. Consumers increasingly rely on biometric authentication for unlocking devices, making payments, and accessing personal data, boosting demand for these sensors in the consumer electronics sector.
Growth in Contactless Solutions: The COVID-19 pandemic accelerated the need for contactless solutions, further boosting the demand for biometric sensors, particularly in facial recognition and iris scanning technologies. As hygiene and safety remain a priority, these solutions are becoming more prevalent in public spaces, offices, and healthcare settings.
Government Initiatives and Regulations: Government initiatives around the world aimed at improving national security and implementing biometric-based identification systems, such as e-passports and national identity programs, are contributing to the market's growth.
Regional Analysis
North America: North America holds a significant share of the biometric sensors market, driven by technological advancements, widespread adoption in the healthcare and financial sectors, and government initiatives. The U.S. is a key contributor, with increasing use of biometric sensors in border control, law enforcement, and consumer electronics.
Europe: Europe is another prominent market for biometric sensors, with major countries such as the U.K., Germany, and France implementing biometric identification systems in public and private sectors. The region is also seeing strong growth in contactless biometric applications in response to the pandemic.
Asia-Pacific: The Asia-Pacific region is expected to witness the fastest growth, driven by the expanding adoption of biometric technologies in emerging markets such as China, India, and Japan. Government initiatives in India, such as the Aadhaar program, which relies on biometric authentication, are contributing to the market’s expansion.
Latin America, Middle East & Africa: These regions are gradually embracing biometric technologies, with applications ranging from secure banking to national identity verification systems. The growing focus on improving security in these regions will provide opportunities for market growth.
Competitive Landscape
The biometric sensors market is competitive, with several leading companies contributing to the sector’s growth. Key players include:
Apple Inc.: Known for incorporating biometric sensors into its range of consumer electronics, including iPhones and iPads, Apple is a significant player in the market.
NEC Corporation: A global leader in biometric solutions, NEC provides a range of biometric identification systems, including fingerprint and facial recognition technologies.
Thales Group: Thales offers a comprehensive suite of biometric solutions, with a focus on secure identification for government and law enforcement agencies.
Synaptics Incorporated: Specializes in biometric sensors for the consumer electronics market, with applications in smartphones, tablets, and laptops.
Fingerprint Cards AB: A major player in the fingerprint sensor market, Fingerprint Cards AB offers innovative solutions for smartphones, tablets, and access control systems.
Report Overview : https://www.infiniumglobalresearch.com/reports/global-biometric-sensors-market
Challenges and Opportunities
While the biometric sensors market holds great potential, it faces certain challenges:
Privacy Concerns: The collection and storage of biometric data raise privacy concerns among users, which could hinder market growth. Governments and organizations must address these concerns through robust data protection regulations.
High Implementation Costs: The initial cost of implementing biometric systems, especially in developing regions, can be a barrier to market growth. However, advancements in technology and increased adoption will likely drive down costs in the future.
On the other hand, the market offers several opportunities for growth:
Technological Advancements: Continued advancements in artificial intelligence (AI) and machine learning are improving the accuracy and efficiency of biometric sensors, leading to wider adoption across industries.
Expanding Applications: Beyond security and identification, biometric sensors are finding new applications in areas such as healthcare, where they can be used for patient identification, and in retail, where they enable personalized customer experiences.
Conclusion
The global biometric sensors market is on a steady growth trajectory, driven by increasing demand for secure authentication, the expansion of consumer electronics, and the growing adoption of contactless solutions. With a projected value of nearly USD 8,300 million by 2028, the market offers substantial opportunities for innovation and investment across various industries. As technological advancements continue to improve the capabilities of biometric sensors, the market is set to play a critical role in shaping the future of security and identification.
0 notes
Text
Explore the wonder of Bio printing in Healthcare
Technology is advanced in a manner where it has solutions for almost all the problems we face. Many people in the world have lost their body organs for different reasons and are suffering from the same. Have you heard about 3D printing technology? It is the process of creating or manufacturing a physical object with the help of a liquid or plastic material from a digital design. It has applications in many fields like prosthetics, construction, implants, jewels, aerospace, healthcare, etc. In this article, we will discuss one of the most useful applications of 3D printing in the medical industry which is used in various sectors i.e., Bio-Printing.

To know more about 3D printing visit The Healthcare Insights
What is Bio-Printing?
Bio-printing is the collaboration of biology and 3D printing technology which involves the layer-by-layer arrangements of the biological materials that then form living tissues and organs. The bio-ink is a liquid that contains the cells or bio material filaments that are used in printing artificial organs and tissues in the laboratory. The purpose of using bio-printing is to build the body part or the organ that replicates the original organs in our body.
The first organ to be bio-printed was the human bladder in the year 1999, it was also successfully transplanted into a human and it was built using the cells of the recipient. From then to now many body parts like lungs, hearts, skin, bones, eyes, blood vessels, living tissues, etc are been printed using bio printing. It is also been used in the research of cancer whereby growing the cancer cells or tumors is done in a test tube to study and can also be an effective way to experiment the treatments on tumor cells.
Working of bio printing
The application of 3D printing has a lot of freedom which helps in researching the various scenarios related to new and deadly diseases. The application of bioprinting is vast where there is no such particular process for culturing the cells to explain, but here we will learn the steps or stages that indicate the workflow of bioprinting.
Pre-printing: In this stage, the digital form of the organ or the part is created for the printers to read. If it is simple then software like DNA Studio will have the ability to print directly in 3D geometry whereas others will need external software like CAD etc. The step also involves the preparation of the composition of biomaterial ink through cells as the researchers require the same cells to study.
Bioprinting: in this stage of the bioprinting process the researchers will fill the bio-inks in multiple threads of the printer and provide the digital copy to print the object in the given shape. In the light-based bioprinting process, the vat of photo-ink is filled as the bio-ink to the printer. In printing the different cells or tissues the researcher needs to culture the cell of desired biological composition and then can use it as bio-ink.
Post-printing: After the formation of the object in the desired shape it needs to be cross-linked to make it a stable one. This can be achieved by treating the objects with UV light or the iconic solutions. Later it is kept in the cell medium of an incubator for the process of cultivation.
Applications of Bio-printing
Bio printing can be used in repairing damaged tissue and organs with regenerative medicine alternatives. This application is helpful in the transformation of people’s lives who are suffering from defects, injuries, or diseases.
It is also helpful in pharmaceutical testing where the drugs can be tested on cultured cells to understand the responses of the drugs. This also reduces the reliability of the animals for testing and analysis.
It also enables the recreation of complex tissues like tumors for learning the diseases and inventing prevention along with improving the treatment process.
Conclusion
In short, bio printing can be considered one of the most effective and useful inventions in the medical industry. Bio printing also has challenges and ethical issues for the culture of cells in the laboratory. As bio printing has the involvement of advanced machines its cost is also very high which makes it non-affordable for common people. The use of any technology for the betterment of human lives should follow ethics and handle legal responsibilities.
Visit More : https://thehealthcareinsights.com/explore-the-wonder-of-bioprinting-in-healthcare/
0 notes