#Malware analysis
Explore tagged Tumblr posts
Text
15 Best Free Resources for Malicious URLs and Phishing Links for Cybersecurity Testing
In today’s rapidly evolving cybersecurity landscape, having access to reliable sources of malicious URLs, phishing links, and malware samples is essential for security professionals, penetration testers, and IT administrators. Whether you’re validating your security controls, conducting security awareness training, or researching new threat vectors, accessing known malicious content in a…
#cyber threats#cybersecurity#ethical hacking#malicious URLs#malware analysis#malware samples#penetration testing#phishing detection#phishing links#security controls#security testing#security tools#security validation#threat intelligence#web security
3 notes
·
View notes
Text
Toolkit - The Essential Toolkit For Reversing, Malware Analysis, And Cracking
This tool compilation is carefully crafted with the purpose of being useful both for the beginners and veterans from the malware analysis world. It has also proven useful for people trying their luck at the cracking underworld. It’s the ideal complement to be used with the manuals from the site, and to play with the numbered theories mirror. Advantages To be clear, this pack is thought to be the…

View On WordPress
0 notes
Text

👾Keep your WordPress website safe and secure with our top-notch 🚀malware removal and security hardening services. Trust us to protect your online presence. 🚀 👾Visit now: https://www.fiverr.com/s/5mdKa1 👾To fix the hacked website, I will take the following immediate steps: 👾Conducting manual and automated WordPress backup. ✅Manual virus removal. ✅Updation of core files, themes, and plugins ✅Requesting IP and domain blacklist removal. ✅Eliminating SEO spam and Japanese keywords ✅Fixing website redirect. 👾Furthermore, I will enhance the WordPress security by: ✅Concealing the admin login page ✅Manually protecting highly sensitive files and directories ✅Installing SSL certificate ✅WordPress speed optimization ✅Configuring a Web Application Firewall (WAF) to safeguard against brute force attacks, among other malware attacks 24/7 support. Client satisfaction is my goal. Contact me & place your order now!
#wordpress#WordPress Maintenance#Cyber Security#wordpress malware#wordpress malware removal#wordpress security#wordpress virus removal#WordPress Error#wordpress virus#domain#blacklist removal#virus protection#malware analysis#malware attacks#Fiverr#fiverr gig#malware types
1 note
·
View note
Text


sunday, august 4th, 2024
this weekend I got a library card for the library in my new city and spent a while exploring and getting excited about books. I had to restrain myself from checking out like every book in the tech section because they were all so interesting lol. for now I'm borrowing books on high performance python and identity security, because those are the two topics I'm struggling with at work right now haha. not pictured is Babel, which I'm currently reading as an ebook. I've just been in book mode for the past few weeks and I want to learn all the things!
also yesterday I published a post announcing the studyblr masterpost jam! there's been some chatting around studyblr about bringing back some of the old-style studyblr resource posts and the like, and I thought this would be a fun way to do it! I'll be writing a bunch of masterposts about cybersecurity next week and I'd love to learn about what y'all are studying <3
#studyblr#studyspo#study inspo#reading#studying#op#there was a really chonky book on 64-bit x86 assembly at the library that I reeeeally wanted to read but#I gotta finish the malware analysis book that I actually bought first lol#I just want to learn everything!! it feels good but also I want more hours in the day lmao
138 notes
·
View notes
Text
Understanding Network Sandboxes: Enhancing Cybersecurity for Businesses
In today’s digital landscape, cybersecurity is a growing concern for organizations of all sizes. As businesses continue to expand their digital footprint, cyber threats evolve, becoming more sophisticated and harder to detect. This is where network sandboxes play a critical role in ensuring the safety and security of sensitive data and IT infrastructures. What is a Network Sandbox? A network…
#advanced protection#automated threat detection#behavioral analysis#business cybersecurity#Cybersecurity#Fiber Internet#IT security#malware detection#network sandbox#Network Security#real-time security solutions#SolveForce#zero-day threats
0 notes
Text
6 types of fraud to remain aware of (and other trends) - CyberTalk
New Post has been published on https://thedigitalinsider.com/6-types-of-fraud-to-remain-aware-of-and-other-trends-cybertalk/
6 types of fraud to remain aware of (and other trends) - CyberTalk


Miguel Hernandez y Lopez is a Cyber Security Engineering Manager and member of the Office of the CTO at Check Point Software Technologies. Miguel has over 20 years of experience in the cyber security field. He was a member of the Honeynet Project, an international non-profit organization (501c3) dedicated to the investigation of the most recent computer attacks, and the development of OpenSource security tools to learn about how hackers behave. He is co-author of the Security Compendium ´Cyber Security and Global Information Assurance: Threat Analysis and Response Solutions´ sponsored by the U.S. Air Force Academy, USA (ISBN: 978-1-60566-326-5). Miguel holds a Master of Science of Technology from Universidad de Buenos Aires.
In honor of International Fraud Awareness Week, here at Cyber Talk, we’re joining the global effort to increase insight and education around fraud prevention.
Every year, organizations lose trillions of dollars to fraud, largely because they don’t understand the tactics that fraudsters employ or what kinds of prevention strategies to implement.
In this interview, explore what’s happening in the world of cyber fraud and how you can support more effective fraud-fighting initiatives. Let’s dive in:
What types of business fraud are you seeing at the moment?
There are several types of business fraud trending currently:
1. Cyber fraud. Cyber attacks are on the rise. Cyber criminals are using techniques such as phishing, malware or ransomware to steal sensitive information or disrupt business operations.
2. Internal fraud. This involves fraudulent activity by staff members within a business, including theft, falsification of documents or embezzlement.
3. Invoice fraud. This involves fake invoices being sent to a company in the hope they’ll pay fake charges without noticing.
4. CEO fraud. This is where fraudsters pose as a CEO of a company or another senior executive to trick an employee into transferring funds or sharing sensitive information.
5. Return fraud. This is particularly prevalent in the retail sector, where customers abuse the return policy for financial gain.
6. Payroll fraud. This can occur when employees manipulate the payroll system to receive more compensation than they’re due.
It’s essential for businesses to constantly update their security measures, educate employees about potential scams and implement strong internal controls to prevent fraud.
Fraud is expensive. Could you speak to the cost of fraud for businesses?
Absolutely. The cost of fraud can be substantial for businesses both financially and reputationally.
There are direct financial losses, which could soar into the millions, depending on the scale of the business and the fraud.
There are also investigation and recovery costs. Post-fraud, a business needs to conduct investigations and try to recover lost funds. These processes can be time-consuming and costly.
Beyond that, there are legal costs. Depending on the severity of the fraud, legal costs can be significant. If the company suffered a large loss, it may choose to prosecute the fraudulent party, increasing expenses.
Also, there are regulatory fines. In some cases, especially those involving data breaches, a business may encounter hefty fines from regulatory bodies for failing to protect sensitive information.
Further, a company may experience reputational damage. Although not directly financial, damage to a company’s reputation can result in loss of customers, decreased sales, and a drop in stock prices, all of which indirectly contribute to overall financial loss.
Lastly, after a fraud incident, companies may see increased insurance premiums.
According to the Association of Certified Fraud Examiners Occupational Fraud 2022, in A Report to the Nations, organizations lose approximately five percent of revenue to fraud each year, with the average loss per case totaling more than $1.78 million.
In your opinion, what impact could generative AI have on the future of business fraud? (What impact has it already had, if any?)
Generative AI could play a significant role, both positively and negatively, when it comes to business fraud.
In terms of fraud prevention and detection, AI can process enormous volumes of data, identify patterns, and detect anomalies more quickly and accurately than human analysts. Using sophisticated algorithms and machine learning methodologies, generative AI can identify potential fraudulent activities before they become damaging.
On the other hand, misuse of generative AI could potentially increase sophisticated fraud scenarios.
For example, think about deepfakes, in which generative AI can create hyper-realistic audio, video, or text that’s virtually indistinguishable from real content. Unscrupulous individuals can use these ‘deepfakes’ for scams, to create false identities, or spread disinformation that harms businesses.
While generative AI provides tools and capabilities that businesses can leverage for fraud prevention, generative AI also requires enhancement in security measures to prevent misuse. Aid from regulatory bodies, education, and a solid legal framework will be necessary to ensure that generative AI’s impact remains positive.
What types of technology solutions or tools would you recommend for fraud detection and prevention?
I would recommend cyber security solutions that have gained popularity due to their effectiveness in addressing modern technological challenges. These solutions are considered robust because they focus on enhancing security posture in a dynamic and evolving threat landscape.
For instance, when you are using Check Point to secure your business, you gain accurate prevention against the most advanced attacks through the power of ThreatCloud AI.
ThreatCloud AI, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks while reducing false positives, keeping a business safe and productive.
Why are these solutions and strategies considered advantageous for fraud prevention?
In terms of what Check Point offers…
Integrated security architecture. Check Point provides a comprehensive and integrated security architecture. Solutions often include multiple layers of security, covering areas such as firewall, intrusion prevention, antivirus, anti-malware, VPN, and more. Having an integrated approach can simplify management and improve overall security effectiveness.
Threat Intelligence and Research. Check Point invests heavily in threat intelligence and research. The company’s researchers actively analyze emerging threats, vulnerabilities, and attack patterns. This commitment to staying ahead of the threat landscape allows Check Point to provide timely updates and protection against new and evolving cyber threats.
Advanced threat prevention. Check Point is known for its advanced threat prevention capabilities. The solutions include technologies such as sandboxing, threat emulation, and threat extraction to detect and prevent sophisticated threats, including zero-day attacks and advanced persistent threats.
Cloud security. As organizations increasingly move their infrastructure and applications to the cloud, Check Point has expanded its offerings to include robust cloud security solutions. This includes protection for cloud workloads, applications, and data, as well as integration with major cloud service providers.
Network security. Check Point has a long history and a strong reputation in the field of network security. The company’s firewall solutions are widely used for securing network perimeters and enforcing security policies. Check Point’s expertise in network security is valuable for organizations with complex network architectures.
User-friendly management interface. Check Point products often feature user-friendly management interfaces that make it easier for security administrators to configure and monitor security policies. This can be important for organizations that want a solution that is both powerful and accessible for their security teams.
Scalability. Check Point solutions are designed to scale with the growth of an organization. Whether an organization is small or enterprise-level, Check Point’s products can often be tailored to meet the specific needs and scale of the environment.
Is there any other advice that you have for organizations?
I think that user awareness is crucial for fraud prevention – and for the following reasons:
Human factor. Often, human error or ignorance enables fraud. By enhancing user awareness, you help build the first, and sometimes most robust, line of defense against fraud.
Phishing attacks. In an age where cyber threats, like phishing, can lead to significant security risks, users who are aware of these threats aren’t as likely to fall for them as their peers.
Early detection. Aware users can identify suspicious activity, anomalies or changes in systems or transactions which may indicate a potential threat or fraud. They can escalate this early, enabling faster response and mitigation.
Mitigating insider threats. Employees who understand the signs of fraud are better equipped to spot and report possible internal threats.
Regulatory compliance. User awareness helps organizations stay in compliance with regulations that often require user training and awareness as a part of their requirements.
Culture of security. Training users around cyber security awareness creates a culture of security within the organization where every member, not just the IT or security team, has a role in preventing fraud.
In essence, users who are well-informed about fraud risks, ways to identify and respond to fraud, and the potential impact, add a valuable layer of protection for the organization.
For more insights from Miguel Hernandez y Lopez, please see CyberTalk.org’s past coverage. Lastly, to receive timely cyber security insights and cutting-edge analyses, please sign up for the cybertalk.org newsletter.
#2022#6 types#Advanced attacks#advanced persistent threats#Advice#ai#air#air force#Algorithms#Analysis#anti-malware#antivirus#applications#approach#architecture#audio#awareness#Big Data#Brain#Business#CEO#ceo fraud#Check Point#Check Point Software#Cloud#Cloud Security#cloud security solutions#cloud service#Companies#compliance
0 notes
Link
#adroit market research#malware analysis market#malware analysis market trends#malware analysis market size
0 notes
Link
#adroit market research#malware analysis market#malware analysis market trends#malware analysis market size
0 notes
Note
At this point, after this has happened a dozen times, why the hell is anyone pushing any update that wide that fast. They didn't try 10 nearby computers first? Didn't do zone by zone? Someone needs to be turbo fired for this and a law needs to get written.
The "this has happened a dozen times" really isn't correct. This one is unprecedented.
But yes the "how the hell could it go THAT bad?" is the thing everyone with even a little software experience is spinning over. Because it is very easy to write code with a bug. But that's why you test aggressively, and you roll out cautiously - with MORE aggressive testing and MORE cautious rollout the more widely-impacting your rollout would be.
And this is from my perspective in product software, where my most catastrophic failure could break a product, not global systems.
Anti-malware products like Crowdstrike are highly-privileged, as in they have elevated trust and access to parts of the system that most programs wouldn't usually have - which is something that makes extremely thorough smoke-testing of the product way MORE important than anything I've ever touched. It has kernel access. This kind of thing needs testing out the wazoo.
I can mostly understand the errors that crop up where like, an extremely old machine on an extremely esoteric operating system gets bricked because the test radius didn't include that kind of configuration. But all of Windows?
All of Windows, with a mass rollout to all production users, including governments?
There had to be layers upon layers of failures here. Especially given how huge Crowdstrike is. And I really want to know what their post-mortem analysis ends up being because for right now I cannot fathom how you end up with an oversight this large.
626 notes
·
View notes
Text
PSA for anyone with an Android phone. Delete your Meta apps (Facebook, Facebook Messenger, Instagram, WhatsApp, Threads). They are spying on you. Much worse than you thought they were. (June 7, 2025)
Gift link to a Washington Post article: https://wapo.st/45hNMeB
Quote from the article:
…apps from Meta and Yandex, a technology company that originated in Russia, circumvented privacy protections in Android devices in ways that allowed their apps to secretly track people as they browsed the web.
That should not have happened. Apps on your phone are walled off from accessing your activity on other apps, including web browser apps like Chrome. Meta and Yandex found work-arounds.
The techniques essentially were akin to malware, or malicious software that is surreptitiously planted on your phone or computer, Dolanjski said.
Google said the behaviors of Meta and Yandex “blatantly violate our security and privacy principles.”
Technical analysis from Ars Technica: https://arstechnica.com/security/2025/06/meta-and-yandex-are-de-anonymizing-android-users-web-browsing-identifiers/
Note: the WaPo article says that so far, there’s no evidence this is happening on iPhones, but that it would be theoretically possible. So you should probably delete your Meta apps on iPhone, too.
50 notes
·
View notes
Text
April O' Neil Enneagram Analysis. (She's a 3)

DISCLAIMER: I am always learning more about the Enneagram, so this is my own understanding of April’s fixation into the type 3. If you’d typed April as anything else before, I hope to open your eyes to my more correct typing.
Let’s start with what a 3 even is. An E3 is a type in the image/triad center of the Enneagram. These types are characterized by their lack of self esteem. An E3 will try to make up for this lack in finding success.
Success in what? Anything the E3 chooses, really. For the purposes of fiction, the goal is often very tangible, like being the best in their career or being the strongest fighter. Their self worth is attached to the pursuit of their goal.
In short, an E3 is looking outside themselves to fulfill their self esteem needs, when they need to be looking inwards and finding self satisfaction. Their growth point is often authenticity and learning they’re enough.
I’ll be using three (heh) April episodes: “Hypno! Part Deux,” “Operation Normal,” and “Always Be Brownies.”
In "Hypno! Part Deux," April is fixated on appearing cool to Taylor Martin, as this'll grant her social acceptance and fulfill her self esteem of belonging. This manifests as rejecting anything that’ll threaten this persona. (Donnie’s malware software, Mayhem’s magic.)


Note: due to an E3's ambition to reach their goals, they're often willing to abandon their true selves in order to fit in well and succeed in social scenarios, especially E3's with a social instinct (April is a social 3.)
This goal of fitting in and being cool is quickly lost when April's life is threatened (as with any type.) But towards the end, when everyone is safe and broken free of Hypno's curse, Taylor has THIS to say..

Beginning-of-episode April would've been devastated at this, but at the end, her growth is complete. She doesn't need this silly persona and the social standing that comes with it to be complete.. her "not coolness" saved the day!! E3 arc completed!
Honestly April's arc in "Operation Normal" is pretty similar to this previous episode. April fixates on appearing as someone she just isn't, pushes away her brothers who she can be herself around, but learns it's okay to be a weirdo!!!

It's "Always Be Brownies" time. I have an ABB phD. April begins the episode at her prototypical-ist E3: Insecure and down about her multiple club failures. She's devoted herself to these things, but just can't succeed!

This is a hit to her self-esteem. But after being kidnapped by Casey's girl scouts, April finds that through her tenacity, strength, and ambition, she really isn't that big of a loser after all. All on her own!


This is amplified by the fact she doesn't let Splinter reassure her, she reassures herself and finds her self worth. It doesn't get more E3 than that, if you ask me.

I rest my case. April O' Neil is an Enneagram 3, with a primary social instinct that she filters her threeness through. The reason I chose episodes where she's operating on her own is that she lets loose around her brothers and isn't concerned with all of this around them.
#rottmnt#april o'neil#rise april#rottmnt april#kj speaks#enneagram#im coming out as an enneagram nerd#im a four.... wing three#so i understand april a whole bunch#i wouldve made this more in depth but . i had formatted this as a twt thread initially#my bad#ill do casey next btw
55 notes
·
View notes
Text


tuesday, december 17th, 2024
work is very busy at the moment! I'm trying to wrap up a few projects before everyone is out for the holidays. I'm also still trying to finish Practical Malware Analysis by the end of the year. I went to my favorite coffee shop after work to do some reading & take some notes. I'm still kind of far behind on doing the labs (I need way more practice with dynamic analysis lol), but I'm going to keep trying!
#studyblr#studyspo#study inspo#studying#study aesthetic#op#evening coffee shop time is such a good vibe#one of the joys of adulthood is realizing you can just do whatever#going to a cafe in the evening on a random tuesday? why not!
209 notes
·
View notes
Text
Headcanon/Theory: The Dark Spore/Dark Seed as "Malware" reaching through a weakened "Firewall" of negative emotions/mental health issues.

Thank you to @thewitch2077 for the interesting question and to @jamesthedigidestined for the fitting wording! Again, this is not a complete analysis of all of Ken's behaviour patterns, but basically my interpretation of how the "Digimon Kaiser persona" - as well as the personality changes of all the other kids affected by it - are explained.
I would actually say that this isn't a traditional Corruption arc - mental stability definitely plays a role, but only a triggering one.
The Dark Seed/Dark Spore implanted in Ken and the other children can be considered some kind of “malware”. It already contains a code, so to speak, which contains basic characteristics: Aside from enhancing their human abilities, such as increased intellect and physical strength, etc. (like some kind of "steroid"), it also has severe side effects on the emotional state, such as, but not limited to: A superiority complex, narcissism, lack of empathy, very low threshold for aggression and violence. So as we can see with Ken and his actual Crest of Kindness - these traits represent THE COMPLETE OPPOSITE OF his personality structure. However, because he was emotionally vulnerable due to his grief, his guilt, his trauma regarding Osamu, because he had desires and his "inner firewall" was weakened, the malware was able to access him super easily and change him according to its code. Exactly the same thing happened with the other children - they all wanted to be as great as Ken, they were dissatisfied and therefore susceptible. It's the "dark side" of the wish-fulfilment trope, so to speak.
Meaning: "Most likely to corrupt" would probably have been Yamato and Sora during their Dark Cave moments - or even Taichi in Tri, which was even speculated at the time when the first Kaiser images were leaked in the promo material. (And it may have been possible even earlier, especially if you consider the sibling angle in comparison to Ken, how Hikari's health and Taichi's own reckless behaviour had affected his mental stability and how he was the first one to trigger a Dark Evolution.)
"Least likely to corrupt" - at least towards the end of 02 - are characters like Daisuke and Mimi. But it always depends on the personal resources and the resilience of the respective characters.
I also found this interesting excerpt from the novel - because Gennai also had a kind of Dark Seed in him (which, once again, corresponds to Taichi's arc in Adventure - and to the idea that Daisuke's character structure enabled him to NOT get swayed by either wishes or fears respectively):
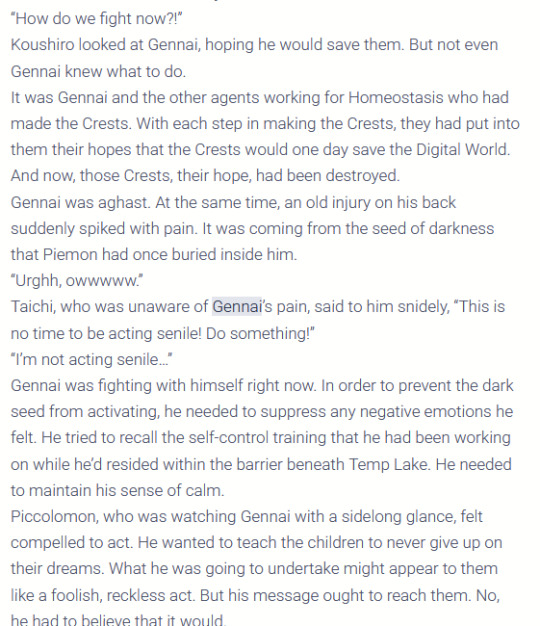
Long story short - I believe that everyone infected with the Dark Spore/Seed with the disposition of letting it take over (with or without consent) would have displayed the same behaviour as the Digimon Kaiser. No matter who would have been affected. The only variable here would be just how damaged their own "Firewall" (= mental health) would have been.
#ken ichijouji#digimon kaiser#digimon emperor#digimon adventure 02#headcanon#my two cents#theory#meta#personal
28 notes
·
View notes
Text
Microsoft's CEO Satya Nadella has hailed the company's new Recall feature, which stores a history of your computer desktop and makes it available to AI for analysis, as “photographic memory” for your PC. Within the cybersecurity community, meanwhile, the notion of a tool that silently takes a screenshot of your desktop every five seconds has been hailed as a hacker's dream come true and the worst product idea in recent memory.
Now, security researchers have pointed out that even the one remaining security safeguard meant to protect that feature from exploitation can be trivially defeated.
Since Recall was first announced last month, the cybersecurity world has pointed out that if a hacker can install malicious software to gain a foothold on a target machine with the feature enabled, they can quickly gain access to the user's entire history stored by the function. The only barrier, it seemed, to that high-resolution view of a victim's entire life at the keyboard was that accessing Recall's data required administrator privileges on a user's machine. That meant malware without that higher-level privilege would trigger a permission pop-up, allowing users to prevent access, and that malware would also likely be blocked by default from accessing the data on most corporate machines.
Then on Wednesday, James Forshaw, a researcher with Google's Project Zero vulnerability research team, published an update to a blog post pointing out that he had found methods for accessing Recall data without administrator privileges—essentially stripping away even that last fig leaf of protection. “No admin required ;-)” the post concluded.
“Damn,” Forshaw added on Mastodon. “I really thought the Recall database security would at least be, you know, secure.”
Forshaw's blog post described two different techniques to bypass the administrator privilege requirement, both of which exploit ways of defeating a basic security function in Windows known as access control lists that determine which elements on a computer require which privileges to read and alter. One of Forshaw's methods exploits an exception to those control lists, temporarily impersonating a program on Windows machines called AIXHost.exe that can access even restricted databases. Another is even simpler: Forshaw points out that because the Recall data stored on a machine is considered to belong to the user, a hacker with the same privileges as the user could simply rewrite the access control lists on a target machine to grant themselves access to the full database.
That second, simpler bypass technique “is just mindblowing, to be honest,” says Alex Hagenah, a cybersecurity strategist and ethical hacker. Hagenah recently built a proof-of-concept hacker tool called TotalRecall designed to show that someone who gained access to a victim's machine with Recall could immediately siphon out all the user's history recorded by the feature. Hagenah's tool, however, still required that hackers find another way to gain administrator privileges through a so-called “privilege escalation” technique before his tool would work.
With Forshaw's technique, “you don’t need any privilege escalation, no pop-up, nothing,” says Hagenah. “This would make sense to implement in the tool for a bad guy.”
In fact, just an hour after speaking to WIRED about Forshaw's finding, Hagenah added the simpler of Forshaw's two techniques to his TotalRecall tool, then confirmed that the trick worked by accessing all the Recall history data stored on another user's machine for which he didn't have administrator access. “So simple and genius,” he wrote in a text to WIRED after testing the technique.
That confirmation removes one of the last arguments Recall's defenders have had against criticisms that the feature acts as, essentially, a piece of pre-installed spyware on a user's machine, ready to be exploited by any hacker who can gain a foothold on the device. “It makes your security very fragile, in the sense that anyone who penetrates your computer for even a second can get your whole history,” says Dave Aitel, the founder of the cybersecurity firm Immunity and a former NSA hacker. “Which is not something people want.”
For now, security researchers have been testing Recall in preview versions of the tool ahead of its expected launch later this month. Microsoft said it plans to integrate Recall on compatible Copilot+ PCs with the feature turned on by default. WIRED reached out to the company for comment on Forshaw's findings about Recall's security issues, but the company has yet to respond.
The revelation that hackers can exploit Recall without even using a separate privilege escalation technique only contributes further to the sense that the feature was rushed to market without a proper review from the company's cybersecurity team—despite the company's CEO Nadella proclaiming just last month that Microsoft would make security its first priority in every decision going forward. “You cannot convince me that Microsoft's security teams looked at this and said ‘that looks secure,’” says Jake Williams, a former NSA hacker and now the VP of R&D at the cybersecurity consultancy Hunter Strategy, where he says he's been asked by some of the firm's clients to test Recall's security before they add Microsoft devices that use it to their networks.
“As it stands now, it’s a security dumpster fire,” Williams says. “This is one of the scariest things I’ve ever seen from an enterprise security standpoint.”
144 notes
·
View notes
Note
got any silly voxval headcannons? (Maybe velvette too idk)
like for example who cooks out of the three of them
Of course you can <3 I'm a really angsty girlie so I don't know how silly they actually are but there you go:
None of them can cook, but that's not really a problem for Vox and Velvette. Vox could survive on plain bread and black coffee for eternity, while Velvette could eat only candies. Val, on the other hand, is the ultimate hedonist. He's all about the tasty, full-fat fast food or gourmet stuff, and he's always pushing for takeout. Come on, guys, we're fucking rich, let's order something. Sure, they could hire someone to cook for them, but Vox is too paranoid to let an outsider near their food. He's still on the hunt for a chef who can match Val's extravagant tastes and is willing to sign off soul. If they had to pick someone to cook, Vox would probably be the best bet since he's the only one who can actually follow a recipe.
Velvette is the smartest when it comes to managing finances. Vox technically doesn't like to waste money but he has a taste for luxurious stuff, he can't resist an expensive car, fucking show-off. Valentino basically burns money on every useless shit he likes, I bet those crystals he badazzled his gun with were real diamons.
Velvette helps Val maintain his fluff, and he styles her hair. It's a cute little trade-off they've got going on.
Valentino has a habit of breaking electronic devices and downloading malware. Vox hates him for it.
Vox can easily go 72h without sleep, fueled by coke and rage. Valentino occasionally drugs his coffee to put him down to sleep, because after 68th hour all electronics in the tower starts malfunctioning.
Val used to be a full-time performer, but now he's more like a RuPaul—lending his face to the brand and only occasionally gracing the stage. But every time he does perform, Vox makes sure to be there front and center.
Their schedules are very incompatible and they have to spend a lot of time managing their businesses but they have weekly appointments to do catch up and discuss strategy. Those are usually very unserious, they end up hitting the bong and playing Mario Cart.
There was this one time Vox tried hitting on Velvette because she's totally his type. It was awkward as hell, and they both agreed to never speak of it again. Valentino has no idea about it.
Valentino would really want to have a dog but Vox really likes dogs so he doesn't allow him to get one by imposing strict anti-pet policy in the tower.
Val knows all of Vox's and Velvette's kinks and sometimes produces custom porn for them as gifts.
As much as they love spending time together, Val and Velvette can't stand watching TV with Vox because he gets overly emotional and doesn't allow to skip commercials because he enjoys them
Vox occasionally invites Val to be a guest judge on reality shows, which always skyrockets ratings but sometimes ends nasty for the contestants.
Val's obsessed with textures, especially nice fabrics. Give him a nice fluffy blanket and he will shut up for 15 minutes fixated on touching it.
Vox, with his business and strategic management degree, sometimes tries to pitch these ideas to Velvette and Valentino, he's like Guys, have you considered using the BCG matrix? Ever heard of SWOT analysis? We should discuss KPIs. They mock him relentlessly for it.
Val once tried putting drag makeup on Vox's face, and let's just say the result was... less than glamorous.
During their honeymoon phase, Vox and Val fucked everywhere. At first, Velvette found it amusing, but eventually, she grew to hate it. She finally snapped when she found out they'd fucked on the dinner table and she set it on fire.
Val "secretly" ghostwrote some trashy smut novels (they are absolutely horrible, worst Wattpad shit you could dig out). Vox secretly bought and read every single one, finding plenty of references to himself along the way.
Vox loves it when Val wears stripper platforms, even though it makes their height difference even more ridiculous.
Valentino's wardrobe takes two entire rooms and still expands. Vox doesn't know how to stop it.
Vox owns a few lingerie sets, only because Val loses his fucking mind whenever he wears them. Velvette designed them herself and keeps photos of Vox wearing them as blackmail material, just in case.
#hazbin hotel#vox#valentino#voxval#ask#staticmoth#velvette#vox hazbin#hazbin hotel valentino#headcanon#velvette hazbin#the vees
335 notes
·
View notes
Text
Jim Acosta at The Jim Acosta Show:
America, you’ve been had. Where to begin? The Gulf of America? Gaza, “The Riviera of the Middle East?” The Kennedy Center? Talk about “the weave.” Can somebody point me to the pivotal moments during the 2024 campaign when Donald Trump discussed his ideas for renaming the Gulf of Mexico or a U.S. takeover of the Gaza Strip? He had plenty of opportunities for laying out such proposals, considering his long, meandering rallies where he rambled about Hannibal Lecter, sharks and windmills. Trump found the time to peddle the outlandish lie that Haitian immigrants in Springfield, Ohio were eating cats and dogs. Never did we consider the notion he would sit on the board that decides whether “Les Misérables” would make its triumphant return to the nation’s capital. In fact, “Les Mis” is coming back in June, well, at least for now. Tickets are available.
What about “The Village People?” Stay tuned. Add Kid Rock and Ted Nugent to the mix and you’ve got a Trumpapalooza in the making. Just think of all of the Trump products that could fill those merch tables (he must have a warehouse of this stuff somewhere), from faux gold sneakers to vintage Trump ties (not made in the USA natch).
Yes, Americans are now waking up to the reality that their downloads of Trump Version 2.0 have come with some serious malware. The pardons and commutations of all of the January 6th rioters and insurrectionists went way beyond what even his own Vice President, the mostly invisible J.D. Vance, contemplated when he suggested that Trump would opt against clemency for the criminals who beat up cops. No wonder 47 doesn’t really see Vance as much of a 48. Trump on Vance 48.
[...]
And then there’s the absurd monstrosity that is Trump’s idea to have the U.S. occupy the Gaza Strip. Put aside his crass promise of turning the region into the “Riviera of the Middle East” or the grotesque notion that America would somehow be a part of the forced removal of the Palestinians from the area. I’m old enough to remember the then-reality TV star and real estate developer savaging President George W. Bush over his handling of the War in Iraq, something Trump once described as “the single worst decision ever made.” Trump on Bush/Iraq After ruling out the idea of putting U.S. military boots on the ground in Gaza, Trump has yet to explain how he would “take over” the area. It won’t be USAID. Were voters ever aware that Trump, upon returning to the White House, would utter this sentence: “The Gaza Strip would be turned over to the US by Israel at the conclusion of fighting.” Take a moment and read that sentence. Read it again. Trump on Gaza The same Trump who ran on “no new wars” during in 2024 has been weaving like an old-fashioned 20th century expansionist, with talk of other takeovers. The Panama Canal? Mine! Greenland? Mine! Canada? Mine! Am I the only one thinking about that classic Daffy Duck cartoon? Daffy Duck: It's mine! [...] Still, in this not-so final analysis, the Trump 2024 campaign appears to have been the ultimate bait and switch. And it’s way worse than Trump’s lie that he had nothing to do with Project 2025. Voters were sold on Trump’s plans for inflation and immigration. But the gap between those proposals and what is being contemplated in the Oval Office these days is about the size of the Gulf of Mexico America.
This Jim Acosta column is a gem: Trump’s 2nd term has come with loads of malware infecting the USA that voters didn’t want.
#Jim Acosta#Donald Trump#Substack#Trump Administration II#Kennedy Center#Gaza#Tariffs#Gulf of Mexico Name Dispute#The Jim Acosta Show#Project 2025#Gulf of Mexico#Greenland#Annexation of Greenland#Pardons#Capitol Insurrection#Elon Musk
24 notes
·
View notes