#KILLNET
Explore tagged Tumblr posts
Text
Hackerattacken mot Elon Musks X
Hackerattacken mot Elon Musks X. Häromveckan utsattes den sociala medieplattformen X för en hackerattack i form av en så kallad riktad denial of service-attack (DDOS). En DDOS-attack eller överbelastningsattack går ut på att överbelasta den utsatta sajten och på så sätt få den att sluta fungera ordentligt. Enligt de rapporter som finns drabbades mikrobloggen X hårt av attacken och fungerade…

View On WordPress
0 notes
Text
How Putin uses shadowy army of hacking geeks from the ‘Fancy Bears’ to ‘KillNet’ gang who’ve besieged NHS & Royal Family | In Trend Today
How Putin uses shadowy army of hacking geeks from the ‘Fancy Bears’ to ‘KillNet’ gang who’ve besieged NHS & Royal Family Read Full Text or Full Article on MAG NEWS

View On WordPress
#Celebrities#How Putin uses shadowy army of hacking geeks from the ‘Fancy Bears’ to ‘KillNet’ gang who’ve besieged NHS & Royal Family#Money#Motors#Politics#ShowBiz#Sport#Tech#Trends#UK#US#World
0 notes
Text
How Putin uses shadowy army of hacking geeks from the ‘Fancy Bears’ to ‘KillNet’ gang who’ve besieged NHS & Royal Family | In Trend Today
How Putin uses shadowy army of hacking geeks from the ‘Fancy Bears’ to ‘KillNet’ gang who’ve besieged NHS & Royal Family Read Full Text or Full Article on MAG NEWS

View On WordPress
#Celebrities#How Putin uses shadowy army of hacking geeks from the ‘Fancy Bears’ to ‘KillNet’ gang who’ve besieged NHS & Royal Family#Money#Motors#Politics#ShowBiz#Sport#Tech#UK#US#World
0 notes
Text
Looks like the group targeting AO3 who've identified themselves as Anonymous Sudan probably have nothing whatsoever to do with Sudan and are either funded and trained by the Russian government or are straight up a cover for Russian cyber attacks.
The main things that seem to be leading cybersecurity experts to this conclusion:
The tactics line up with the methods of the Russian backed KillNet hacker group
The targets line up with Russian government interests
And the resources used to carry out attacks are expensive and require significant funding.
This does lead to an interesting question of why AO3 of all sites was selected, if I had to guess (and unlike the notes above, this is just me guessing and not backed up by experts) I'd say that there are two things that make AO3 an effective target: There's a large amount of traffic, and it fits the cover.
Attacking a target that doesn't necessarily directly benefit the Russian state's interests helps blur the trail, and making sure that the target has a large userbase means that the cover gets spread to a large amount of people quickly.
This is actually part of the reason I'm making this post. Spreading awareness of the source of the attack actually weakens the attack, and if we spread the word far enough that Anonymous Sudan is actually the Russian government we can make the attack an actual failure by revealing the cover instead of helping secure it.
Here's an article that goes more in-depth on Anonymous Sudan if you want to know more details:
70 notes
·
View notes
Text
I'll just leave this 👇 here... You Decide 🤔
Killnet puts European banks on notice. “You have 48 hours”
#pay attention#educate yourselves#educate yourself#knowledge is power#reeducate yourself#reeducate yourselves#think for yourself#think for yourselves#think about it#question everything#ask yourself questions#you decide#do your homework
48 notes
·
View notes
Text
instagram
December 27.
Russian Hacker Collective Killnet is standing with Palestine.
#palestine#gaza#free palestine#free gaza#israel#gaza genocide#gaza strip#motaz azaiza#from the river to the sea palestine will be free#save the children#Instagram
10 notes
·
View notes
Text
Russia's APT28 Cyber Espionage Group Targets Czechia, Germany Using Outlook Exploit
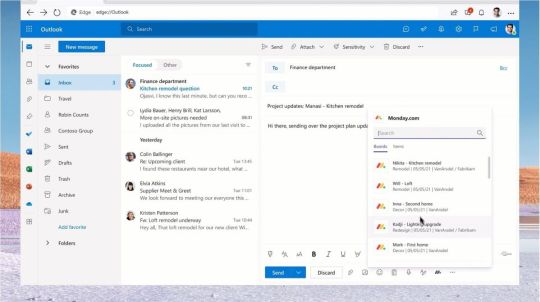
Czechia and Germany have exposed a long-running cyber espionage campaign conducted by the notorious Russia-linked APT28 hacking group, drawing harsh criticism from international organizations like the European Union (EU), the North Atlantic Treaty Organization (NATO), the United Kingdom, and the United States. The Czech Republic's Ministry of Foreign Affairs revealed that certain entities within the country were targeted using a critical Microsoft Outlook vulnerability (CVE-2023-23397), allowing Russian state-sponsored hackers to escalate privileges and potentially gain unauthorized access. Germany Accuses APT28 of Targeting Social Democratic Party Similarly, Germany's Federal Government attributed the APT28 threat actor, also known as Fancy Bear, Pawn Storm, and Sofacy, to a cyber attack aimed at the Executive Committee of the Social Democratic Party, exploiting the same Outlook flaw over a "relatively long period" to compromise numerous email accounts. The targeted industries spanned logistics, armaments, air and space, IT services, foundations, and associations located in Germany, Ukraine, and other European regions. Germany also implicated APT28 in the 2015 cyber attack on the German federal parliament (Bundestag). Widespread Condemnation of Russia's Malicious Cyber Activities NATO stated that Russia's hybrid actions "constitute a threat to Allied security," while the Council of the European Union condemned Russia's "continuous pattern of irresponsible behavior in cyberspace." The UK government described the recent APT28 activity, including targeting the German Social Democratic Party, as "the latest in a known pattern of behavior by the Russian Intelligence Services to undermine democratic processes across the globe." The US Department of State acknowledged APT28's history of engaging in "malicious, nefarious, destabilizing and disruptive behavior," and reiterated its commitment to upholding a "rules-based international order, including in cyberspace." Disruption of APT28's Criminal Proxy Botnet Earlier in February, a coordinated law enforcement action disrupted a botnet comprising hundreds of SOHO routers in the US and Germany believed to have been used by APT28 to conceal their malicious activities, such as exploiting CVE-2023-23397 against targets of interest. Cybersecurity researchers warn that Russian state-sponsored cyber threats, including data theft, destructive attacks, DDoS campaigns, and influence operations, pose severe risks to upcoming elections in regions like the US, UK, and EU, with multiple hacking groups like APT28, APT44 (Sandworm), COLDRIVER, and KillNet expected to be active. Securing Critical Infrastructure from Pro-Russia Hacktivist Attacks Government agencies from Canada, the UK, and the US have released a joint fact sheet to help critical infrastructure organizations secure against pro-Russia hacktivist attacks targeting industrial control systems (ICS) and operational technology (OT) systems since 2022, often exploiting publicly exposed internet connections and default passwords. The recommendations include hardening human-machine interfaces, limiting internet exposure of OT systems, using strong and unique passwords, and implementing multi-factor authentication for all access to the OT network. Read the full article
2 notes
·
View notes
Text
The two largest hacktivist groups in the Ukraine conflict have vowed to de-escalate cyber-attacks and comply with new rules of engagement published by a war watchdog.
On Wednesday, the International Committee of the Red Cross (ICRC) issued the first list of rules for civilian hackers ever created.
Dubbed a "Geneva Code of cyber-war", it was initially criticised as unworkable.
But now Ukrainian and Russian hackers say they will comply with the rules.
Since the invasion of Ukraine there has been a steady stream of disruptive cyber-attacks against public services in both Ukraine and Russia with varying degrees of impact.
Hacktivist groups have been using largely unsophisticated forms of cyber-attack, but successfully temporarily disrupted banks, companies, pharmacies, hospitals, railway networks and civilian government services for Ukrainian and Russian citizens.
With few soft targets in government or military, hacktivists on both sides have revelled in causing friction for ordinary people to further their causes, often collecting angry social media posts from those affected by their attacks.
By vowing to comply with the ICRC rules, hacker groups will avoid cyber-attacks that affect civilians.
Speaking to the BBC, the leader of the infamous pro-Russian hacking group Killnet said he "agrees to the terms and rules of the Red Cross, let this be the first step from Killnet to peace".
Killmilk, as he is known, started the Telegram group for Killnet shortly after his country invaded, and now has 90,000 followers.
Killmilk has posted videos of himself urinating on the flags of Ukraine and Nato, and the group was highlighted as a persistent source of low-level disruptive attacks on Ukrainian targets.
The group has been accused of having close links to the Kremlin, but has always denied this.
In April, the UK's National Cyber Security Centre highlighted groups like Killnet as a new threat facing Ukraine allies, warning UK businesses that attacks from them on are on rise.
If Killnet keeps to its word, then cyber-attacks on civilian targets, including those of Ukraine's allies, will stop.
The IT Army of Ukraine also said it would be following the ICRC's eight rules.
The group, which has 160,000 members on its Telegram channel, also targets public services such as railway systems and banks.
Its spokesman told BBC News that the group will "make best efforts to follow the rules", even though it may place them at a disadvantage to their adversaries. The spokesman added that attacks on healthcare targets have been a long-standing red line already.
The news means that there will likely be a major reduction in the number of cyber attacks as groups restrict their activities to official or military targets.
But other hacktivist groups working for other patriotic or ethical causes in the world told the BBC they would not be following the rules at all.
The ICRC issued the eight rules of engagement in an attempt to end the free-for-all that has accelerated during the Ukraine cyber-conflict, warning that unprecedented numbers of people are joining patriotic cyber-gangs.
6 notes
·
View notes
Text
Cyber Conflict Erupts Amid Israel-Hamas Clash

Amid the escalating conflict between Israel and the Palestinian group Hamas, a parallel battle in the cyber world has unfolded, introducing unexpected twists and turns to an already complex situation. As tensions mount on the ground, hackers from various factions have launched a series of cyberattacks, leaving both nations vulnerable. Adding another layer of complexity, a Pro-India group has entered the digital arena, intensifying the ongoing cyber conflict.
Hamas Launches Ground Attack
On a fateful Saturday, Hamas terrorists initiated a ground attack on Israel, accompanied by an unrelenting missile barrage. This brutal assault resulted in casualties and the shocking abduction of approximately 900 people, including 73 Israeli soldiers. To further complicate the situation, several individuals were taken hostage as events continued to unfold.
Also Read: Pune Couple's Organized Cyber Blackmailing Scandal Uncovered
Cyber Chaos Hits Jerusalem Post and Red Alert App
On October 8, the Jerusalem Post, a prominent Israel-based media outlet, found itself in the crosshairs of multiple cyberattacks, culminating in a site crash, rendering it inaccessible from various locations. Anonymous Sudan, a hacking group, claimed responsibility for this cyber onslaught.
In another alarming incident, the Red Alert phone app system, a critical tool for providing real-time alerts during rocket and missile attacks in Israel, reported that it had become a target of a hacktivist group known as Anon Ghost.
Coordinated Cyber Operations: OpIsrael and OpsRise
As the physical conflict raged on, the cyber battlefield witnessed a surge in activity. A pro-Palestine online group, known as the "Ghost of Palestine," initiated a significant cyber campaign, rallying hackers worldwide under the banner of #OpIsrael. Their objective was to target Israel's cyber infrastructure and bolster the cyber resistance against the nation.
Additionally, another pro-Palestine hacking alliance, comprised of "Ghost Clan" and "Black Shield Crew MY," issued a warning, signaling an impending cyber offensive against Israel known as "OpsRise." These developments underscored the escalating digital confrontations within the ongoing Israel-Palestine conflict, as various hacker groups engaged in cyber warfare.
Collaboration of Pro-Russian Hacking Entities
A Twitter handle, @Cyberknow20, disclosed that 35 pro-Palestine hacker groups had consistently focused their efforts on Israel. Of particular concern was the collaboration between two pro-Russian hacking entities, Anonymous Sudan and Killnet, as they jointly targeted Israel's cyber infrastructure.
Also Read: Cyber blackmailing case: Shatrughan's bail plea rejected
Pro-Palestine Hacker Groups Target Governments and Websites
These cyberattacks witnessed pro-Palestine hacker groups systematically targeting multiple Israeli government websites. Among the notable incidents, Garnesia Team claimed responsibility for attacks on government sites, including the Municipality of Jerusalem and the National Insurance Institute. The ACEH Hackers Group also made its mark by targeting various Israeli websites, such as Cello, USHOPS, and CASTRO.
The Team Herox Hackers Group shifted its focus to "The Occupation Magazine" website, while the Ganosec Team executed an attack that temporarily took down the website of the Israeli Security Agency.
Pro-India Group Enters the Fray
In a surprising turn of events, the "Indian Cyber Force," a Pro-India hacking group, has emerged as a significant player in the Pro-Israel hacktivist arena. They have successfully launched cyberattacks on Palestinian websites, impacting several targets, including the Hamas official website and the Palestine National Bank website.
Also Read: Cybercrime in Nagpur - Cyber Blackmailer Couple Arrested in Pune for Extorting Money
In response to these attacks, Pro-Palestine hacker groups retaliated with Distributed Denial of Service (DDoS) attacks on Delhi government websites, reflecting the escalating cyber conflicts tied to the Israel-Palestine issue. However, as of Monday, the Delhi government website appeared to be fully functional.
The Evolving Nature of Cyber Conflicts
These incidents collectively underscore the dynamic and evolving nature of conflicts in the digital realm. They highlight the critical importance of cybersecurity in contemporary geopolitical struggles, where cyberattacks can have real-world consequences. As the situation continues to develop, both nations find themselves grappling with the challenges of defending their digital territories while addressing the broader conflict on the ground.
In summary, the ongoing Israel-Palestine conflict has spilled over into the cyber realm, with various hacking groups engaging in a relentless digital battle. This digital conflict has witnessed the involvement of a Pro-India group, further complicating the already complex situation. As cyberattacks intensify, the importance of cybersecurity in contemporary geopolitical conflicts becomes increasingly evident, with real-world consequences at stake for both nations.
Source: https://www.the420.in/cyber-conflict-israel-hamas-clash-october-2023/
2 notes
·
View notes
Text
It's fascinating to watch how effectively the DDoS attack by a hacktivist group heavily affiliated with the FSB's killnet - tho functioning as a separate cell - achieved its goal of causing division within a liberal dominated social space. One group refusing to believe in the FSB's standard operating procedure and insisting it was local hackers, despite copious evidence. Another camp convinced of some elaborate government conspiracy tactic.
Rather than that SOP of systematically probing and testing western digital structures for weakness, and causing discord in social groups that obstruct conservative government control that keeps western nations either allied with Russia, or passive. It has nothing to do with fandom.
Congrats everyone! Good job squabbling. A+. Gold stars all around.
5 notes
·
View notes
Text
Anonymous Sudan/Storm-1359 is widely accepted based on taxonomy and other research to in fact be Russian and likely state-supported based on finances. They're also linked to KillNet in someway. This is in fact grounded in actual research and knowledge that we have, not some sort of shot in the dark by fans without any knowledge of cyber security and current bad actors.
A quote from the linked analysis: “[Their messaging] started in Russian, and they just changed it after Truesec wrote a report saying it was strange that they only communicated in Russian. Even if they now communicate in Arabic, it’s obvious that there are still Russians behind it. Anonymous Sudan hasn’t said that those who started the channel are gone or “that wasn’t us.” Another thing is that what they say very much fits a Russian narrative,” Wåhlén said.
I can't believe how goofy people are being about the AO3 DDoS situation. One side of the debate is like "ah, it's probably those Nefarious Russian Hackers carrying out another false flag operation!" and the other side is like "a real hacktivist group wouldn't use this sort of fandom-centric language, so clearly the attack never happened and AO3 themselves staged it in order to make themselves look like victims!", and these are both unhinged things to believe.
Like, it's fucking 4channers. It's always fucking 4channers. Pretending to be from a random African nation is literally a meme for those guys, and who else would be dumb enough to try and hold a registered nonprofit hostage for bitcoin?
27K notes
·
View notes
Text
Unlocking Security: VPN Killnet's Global Protect VPN Download
Reliable Virtual Private Networks (VPNs) are more important than ever in a time when internet security and privacy are top priorities. Strong solutions to protect online activities are sought after by both consumers and corporations as cyber threats grow in size and data breaches occur more frequently. Amidst the multitude of VPN services accessible, VPN Killnet distinguishes itself with its extensive portfolio, which includes the widely recognised Global Protect VPN download.
Knowing VPN Killnet: Creating Safe Connections
VPN As a cybersecurity industry mainstay, Killnet has built a solid reputation for providing high-quality services that are customised to fit the various needs of its clients. The Global Protect VPN download, a powerful instrument to bolster digital defences and guarantee anonymity during all online interactions, is at the centre of its products.
Streamlining Accessibility: Filling the Vapour Between Platforms and Devices
The easy accessibility of the Global Protect VPN download on a wide range of devices and platforms is one of its standout characteristics. Users may easily incorporate the VPN into their digital ecosystem on any device—desktop, laptop, smartphone, or tablet—to guarantee constant protection on all fronts. VPN Killnet enables users to remain safe on any device or operating system thanks to its support for Windows, macOS, iOS, Android, and other operating systems.
Enhanced Privacy and Anonymity: Redefining Freedom of the Internet
Maintaining online privacy and anonymity is essential at a time of increased data mining and surveillance. By hiding their IP addresses and online activity from ISPs, governmental organisations, and other organisations looking to obtain personal information, customers of the Global Protect VPN are able to regain control over their digital identities.
Unmatched Performance in terms of Reliability, Stability, and Speed
The Global Protect VPN download offers unmatched performance metrics in addition to security and privacy, guaranteeing blazing-fast speeds, unflinching reliability, and continuous connectivity. Through the planned distribution of its global network of servers across crucial areas, VPN Killnet maximises user experience without sacrificing security or dependability.
Taking on the Future with Security, Seamlessness, and Serenity
Strong cybersecurity measures are crucial as the digital landscape changes. This cannot be stressed. Users may face the future with confidence knowing that their digital interactions are protected by an impenetrable wall of security and privacy when they download VPN Killnet's Global Protect VPN.
0 notes
Text
A hacktivist group with the moniker Anonymous Sudan is a small Russian-funded misinformation operation with no connection to Sudan, according to researchers at CyberCX. Founded early this year, Anonymous Sudan has claimed responsibility for a number of distributed denial of service (DDoS) attacks, purportedly carried out in response to the anti-Islamic views or actions of Western organizations. But in an intelligence update published on Monday, Australian-based cybersecurity firm CyberCX said Anonymous Sudan was set up to create “a smokescreen for Russian interests” by spreading propaganda and disinformation, and tying up Western cyber defense resources. As a member of the pro-Russia KillNet hacktivist collective, Anonymous Sudan followed the KillNet playbook: doing all it could to seek publicity, often exaggerating the success of its attacks to “create public chaos and uncertainty,” according to the CyberCX report A Bear in Wolf’s Clothing.
What's happening to AO3 right now?
As you may have noticed already, Archive of Our Own is currently down. This is temporary, but unfortunately.. we now know that this is much deeper than we thought.
AO3 is currently the victim of a DDOS attack orchestrated by "Anonymous Sudan"
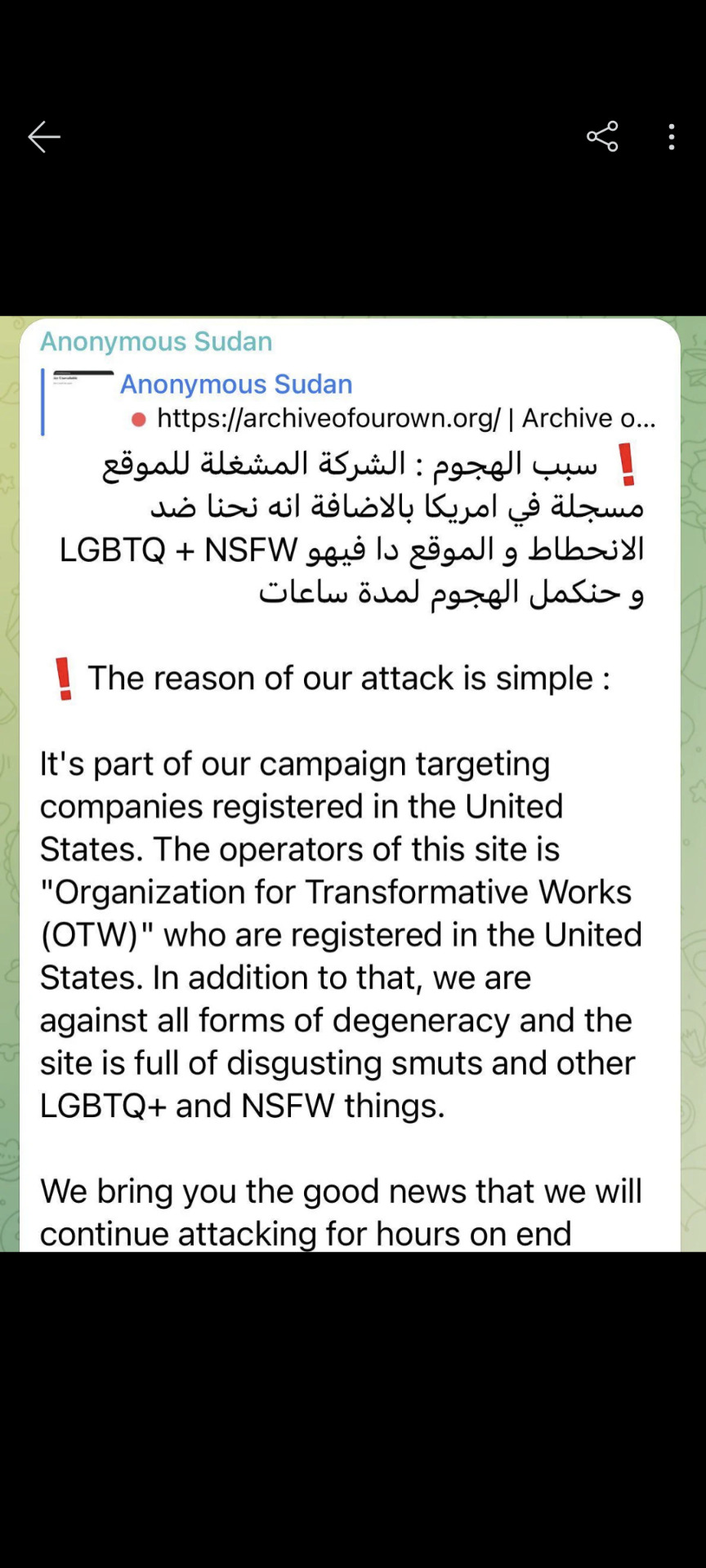
Why? Because AO3 is home to thousands of LGBTQIA+ content and lots of NSFW content. They're doing this as an Anti-LGBTQ+ attack. If they're doing this for or from America specifically, we're not sure. But this is what AO3 is facing at this time.
What can we do?
Spread the word. Spread the fucking word. I'll be providing updates to my Tumblr page directly from the r/AO3 subreddit. I know that not everyone here is comfortable using Reddit, so I'm taking the blow for you. I cannot access Twitter though.
And please, whatever you do...
Stop using the Archive of Our Own website at this time.
The moderators, showrunners, and service providers all need to repair the damage done by this group. The amount of data flooding in from people trying to log in will cause more problems. Keep yourselves off of the website.
16K notes
·
View notes
Text
Leader of pro-Russia DDoS crew Killnet unmasked by Russian state media
http://securitytc.com/SzMZmn
0 notes
Text
Russian Hackers Group "Killnet" Cyber Attack on Israel | India Saves Israel | @chotanewstelugu
Russian Hackers Group ��Killnet” Cyber Attack on Israel | India Saves Israel | @chotanewstelugu #israelpalestineconflict #israelhamaswarnewstoday #cyberattacks #russianhacking #indianhackers #chotanews #shortnews #dailynews #hamasattackisrael #hamaswar ChotaNews Telugu offers a platform for viewers to explore the world of science and technology. Discover inspiring stories of triumph and discover…
View On WordPress
#actor#andhrapradesh#chotanews#india#international#shortnews#shorts#shortstory#shortsvideo#srisimha#telanagana#telugu#world
0 notes