#Is There A Code For The iPhone To Reset Network
Explore tagged Tumblr posts
Text
How to Handle Error Code 83 on DisneyPlus.com/Begin
Disney+ is a widely popular streaming platform offering an extensive library of movies, TV shows, and exclusive content. However, like any digital service, users sometimes encounter technical issues. One common problem faced by Disney+ subscribers is Error Code 83. This error can be frustrating, but understanding its causes and solutions can help you resolve it quickly.
In this guide, we’ll explore what Error Code 83 means, its potential causes, and how to troubleshoot the issue step-by-step to regain access to disneyplus.com/begin.
What Is Error Code 83 on Disney+?
Error Code 83 on Disney+ is a general device compatibility or network issue. When this error occurs, it prevents users from accessing Disney+ content, disrupting their streaming experience. The error message typically reads:
"Something went wrong. Please try again. If the problem persists, visit the Disney+ Help Center. Error Code 83."
Understanding the root cause of this issue is essential to determine the appropriate solution.
Common Causes of Error Code 83
1. Device Compatibility Issues
Not all devices are compatible with Disney+. Older operating systems or unsupported devices may trigger Error Code 83.
2. Network Connectivity Problems
A weak or unstable internet connection can prevent Disney+ from functioning properly. This may include Wi-Fi disruptions, router issues, or ISP throttling.
3. Account Authentication Errors
If Disney+ cannot verify your account credentials due to login issues or server errors, it might result in Error Code 83.
4. App or Browser Issues
Using an outdated version of the Disney+ app or an unsupported web browser can cause compatibility errors.
5. Digital Rights Management (DRM) Restrictions
Disney+ uses DRM to protect its content. If your device fails to meet DRM requirements, you may encounter Error Code 83.
Troubleshooting Steps for Error Code 83
Below are detailed steps to resolve Error Code 83. Follow these systematically to identify and fix the issue.
Step 1: Check Device Compatibility
Verify Device Requirements:
Ensure your device is compatible with Disney+. Refer to the Disney+ device compatibility list.
Update Operating System:
Check for updates on your device and install the latest operating system.
For example:
iOS/Android: Update to the latest version in your settings.
Windows/Mac: Update via system preferences or control panel.
Switch Devices:
If your current device remains unsupported, try accessing DisneyPlus.com/begin on another compatible device.
Step 2: Test Your Network Connection
Check Internet Speed:
Disney+ requires a minimum speed of 5 Mbps for HD streaming and 25 Mbps for 4K. Use an online speed test tool to verify your connection.
Restart Your Router:
Turn off your router, wait 30 seconds, and power it back on to reset your connection.
Switch Networks:
If possible, switch to a different Wi-Fi network or try a mobile hotspot to identify whether the issue is network-specific.
Disable VPN or Proxy:
Disney+ might block access if you’re using a VPN or proxy. Disable these services and try again.
Step 3: Update the Disney+ App
Check for Updates:
Open your app store and search for Disney+.
Install any available updates.
Reinstall the App:
Uninstall the Disney+ app and reinstall it to ensure you’re using the latest version.
Clear Cache and Data:
If reinstalling isn’t feasible, clear the app’s cache and data:
iOS: Go to Settings > General > iPhone Storage > Disney+ > Offload App.
Android: Go to Settings > Apps > Disney+ > Storage > Clear Cache.
Step 4: Use a Supported Browser
If you’re accessing DisneyPlus.com/begin via a web browser:
Update Your Browser:
Use the latest version of Chrome, Firefox, Safari, or Edge.
Enable DRM Settings:
Ensure your browser’s DRM settings are enabled. For example:
Chrome: Go to Settings > Privacy and Security > Site Settings > Additional Content Settings > Protected Content.
Clear Cookies and Cache:
Clear your browser’s cookies and cache to eliminate potential conflicts.
Disable Browser Extensions:
Temporarily disable ad blockers or other extensions that might interfere with Disney+.
Step 5: Resolve Account Authentication Issues
Re-login to Your Account:
Log out of DisneyPlus.com/begin and log back in to refresh your session.
Reset Your Password:
If login issues persist, reset your password through the Disney+ account management page.
Verify Your Subscription:
Ensure your Disney+ subscription is active. Check your billing details in your account settings.
Contact Disney+ Support:
If authentication problems persist, visit the Disney+ Help Center for assistance.
Step 6: Check Device DRM Support
Verify DRM Requirements:
Check if your device supports Widevine DRM or equivalent protocols.
Switch to a Certified Device:
If your current device lacks DRM support, use a certified device like a Smart TV, game console, or streaming device.
Additional Tips to Avoid Error Code 83
1. Maintain Up-to-Date Software
Regularly update your devices, apps, and browsers to prevent compatibility issues.
2. Optimize Internet Connection
Position your router for maximum signal strength and avoid network congestion during streaming.
3. Use Authorized Devices
Avoid jailbroken or rooted devices that might fail DRM checks.
4. Avoid Simultaneous Logins
Limit the number of simultaneous logins on your Disney+ account to prevent conflicts.
5. Enable Auto-Updates
Set your apps and system to auto-update to stay current with the latest Disney+ features and fixes.
When to Contact Disney+ Support
If you’ve tried all the steps above and still encounter Error Code 83, it’s time to reach out to Disney+ support:
Visit DisneyPlus.com/begin.
Navigate to the Help Center and select the appropriate troubleshooting category.
Use the live chat or email options to describe your issue.
Provide details such as:
Your device model and operating system.
Internet speed and connection type.
Steps you’ve already taken to resolve the issue.
Conclusion
Error Code 83 on Disney+ can stem from various issues, including device compatibility, network problems, or app glitches. By systematically following the troubleshooting steps outlined above, you’ll likely resolve the error and enjoy seamless streaming on disneyplus.com/begin. If the problem persists, don’t hesitate to contact Disney+ support for personalized assistance. With these solutions, you can minimize disruptions and make the most of your Disney+ subscription.
0 notes
Text
Access Your Target's Instagram Messages with Instagram Hacking

In today's digital era, social media platforms like Instagram have become integral to our lives. Instagram is not only a space for personal expression and sharing opinions but also a powerful tool for business promotion. However, with its widespread use, it's essential to be aware of Instagram's security and privacy issues. This blog delves into Instagram hacking and the role of organizations like HackersList in this domain, helping us uncover truths through hacking.
What is Instagram Hacking?
Instagram hacking involves accessing someone's Instagram account using various methods such as phishing, password tracking, and social engineering.
Hack Instagram Messages and Account Access
A common sign of Instagram hacking is unauthorized access to someone's personal inbox. Hackers often exploit protocol weaknesses like phishing, which involves creating a fake login page to gain access to the target's Instagram account.
📌 Read Also: 6 Ways to Track Instagram Account to See Partner’s Activities
How to Hack Instagram
Instagram is a popular platform, especially among the youth. Here are some methods used to hack Instagram:
Brute Force Attack: This method targets weak passwords by systematically attempting all possible combinations.
Password Reset Exploit: This involves intercepting the reset link sent to the target's email. By exploiting this link, a hacker can gain access to the target's Instagram account.
Third-Party Tools: Some hackers use specialized tools or third-party applications requiring advanced coding and networking knowledge to hack Instagram accounts.
Hacker Online Instagram: Services Offered by HackersList
HackersList is a platform connecting professional hackers with clients. The priority of HackersList is to ensure client privacy. Those seeking help with Instagram hacking can connect with this platform for reliable services.
📌 Read Also: The World of Social Media Hacking: Unveiling the Secrets
iPhone Hacks Instagram: Addressing Device-Specific Concerns
With the widespread use of iPhones, addressing device-specific concerns is crucial. HackersList offers specialized information and solutions for iOS gadgets, focusing on security and privacy.
HackersList - Best Instagram Hacker Website
HackersList is a marketplace where customers can find professional hackers skilled in all things Instagram. They offer services to secure Instagram accounts, identify weaknesses, and resolve security issues.
With the help of experienced users on HackersList, individuals can enhance the security of their accounts and strengthen their digital profiles' defenses. Known for professionalism and reliability, HackersList is a go-to platform for those seeking expert services for Instagram and other platforms.
Conclusion
If you need to hack your partner's, loved one's, or friend's Instagram account, HackersList is a recommended option. Their skilled hackers can handle the task efficiently and effectively.
0 notes
Text
0 notes
Text
Securing your smartphone is essential to protect your personal data, privacy, and prevent unauthorized access. These are some best practices to securing your smartphone: Use a strong password or PIN: Set a unique and complex password or PIN to unlock your phone. Avoid using common patterns or easily guessable combinations. Enable biometric authentication: If your smartphone supports biometric authentication, such as fingerprint or facial recognition, enable it for an extra layer of security. Keep your software up to date: Regularly update your smartphone's operating system and apps. These updates often include security patches that address vulnerabilities and strengthen your device's security. Install apps from trusted sources: Stick to official app stores like Google Play Store (for Android) or the Apple App Store (for iOS). Downloading apps from unofficial sources increases the risk of installing malware or malicious software. Be cautious with app permissions: Review the permissions requested by apps before granting them access to your device's features or data. Avoid granting unnecessary permissions that could compromise your privacy. Use strong and unique passwords for apps: If you use apps that require logins, create strong and unique passwords for each app. Consider using a password manager to securely store and generate passwords. Activate two-factor authentication (2FA): Enable 2FA whenever possible to add an extra layer of security. It typically requires entering a verification code or using a trusted device to authenticate your identity. Be wary of public Wi-Fi networks: Avoid connecting to unsecured or public Wi-Fi networks, as they can be easily compromised. If you must connect, use a virtual private network (VPN) to encrypt your internet traffic and protect your data. Regularly back up your data: Backup your smartphone's data regularly, either to the cloud or a secure offline storage solution. In case of theft, loss, or a security incident, you can restore your data without significant loss. Enable remote tracking and wiping: Activate the "Find My Device" feature (Android) or "Find My iPhone" (iOS) to track your device's location or remotely erase data if it's lost or stolen. Be cautious of phishing attempts: Be vigilant about phishing attempts through text messages, emails, or other channels. Avoid clicking on suspicious links or providing personal information unless you can verify the source. Encrypt your device: Check if your smartphone has encryption capabilities and enable it. Encryption scrambles the data on your device, making it unreadable without the encryption key. Disable unnecessary features: Turn off unused features, such as Bluetooth, NFC, or location services when not needed. These features can potentially be exploited by attackers. Use reputable security software: Consider installing a reputable mobile security app that can detect and prevent malware, provide anti-theft features, and offer additional protection. Securely dispose of your old device: When you're ready to upgrade or dispose of your smartphone, ensure you wipe all data from it. Perform a factory reset or use specialized tools to ensure no personal information remains. By following these practices, you can significantly enhance the security of your smartphone and safeguard your personal information.
0 notes
Text
AirPlay Not Working on Samsung TV[Fixed]

Airplay is a modern technology provided by Apple on its iOS devices. It enables iPad, iPhone, or MAC users to wirelessly cast audio or video transfers to Samsung TV. It might get errors or issues which may distract its working performance. This technology has made Samsung users cast video or any multi-media cast to their TV Screen directly without any involvement of wires. Explore the article to fix ‘airPlay not working on Samsung.’ If you have a Samsung TV and are getting trouble connecting Airplay with your TV, then this article will get a detailed guide on possible issues and their relative fixes.
Why is AirPlay not working on my Samsung TV?
AirPlay's non-working may be due to lot of factors. One of the most common methods is the compatibility issues. If the connecting devices are not connected to the same internet, they won’t be able to connect to each other. It may also be due to the bandwidth above the 5 GH network band. It may also depend on the software installed which can be obsolete and stop working. Sometimes, the software bugs might create problems with connection and may cause the reason for Airplay not working on Samsung tv. Reading Recommendation: Read more about AirPlay
Change/Retry the Internet Connection
If your AirPlay is not connecting to Samsung TV, you must check that the connection does not create any error.
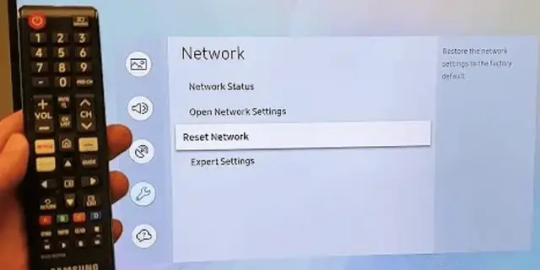
Network Reset - You can retry to connect to the internet. - Go to settings on your Samsung TV. - Pick the general settings from there and then find ‘Network.’ - You will see network status. Press the network status and select Retry network. - Wait for a few seconds. - Now, you can connect your Samsung TV with AirPlay using the same network.
Samsung TV Not Generating AirPlay Code
When you try to connect your AirPlay with Samsung TV, it generates codes on your Samsung TV which is necessary to connect with an iOS device. This code is put into the device which completes the bi-connection. When you pair both devices, you are able to mirror anything from your device. But, sometimes the code does not appear which stops the connection between two devices. You must follow the steps below to completely get the code and make the connection. Sometimes, You have not turned on the AirPlay feature on your Samsung TV. This might be the problem with AirPlay not connecting to Samsung TV. Check if it is turned on or not. Now, check if the Firmware software is obsolete or needs to get updated. Most of the time, your device’s firmware is not updated. So, they might create problems in creating a connection between AirPlay and Samsung. Must Read: AirPlay To Samsung TV
Disable and Enable AirPlay
In most of the connectivity and Bluetooth issues with various devices, restarting the device again and double-checking the related feature’s ability or disability resolves the problem in quick time.
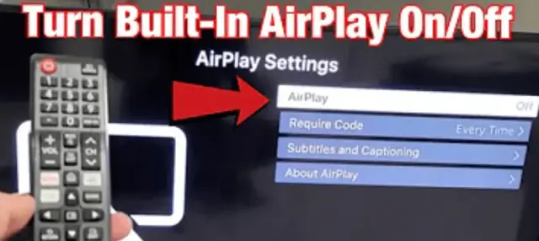
Enable AirPlay You must apply this technique with your AirPlay as we have checked the working accuracy. - Go to Samsung general settings. - Check the AirPlay feature in the settings. - Disable Airplay from there. - Now, restart your device again, and make sure that the AirPlay feature was previously disabled. - Try to enable AirPlay again and check the Connection. - You will get the code and AirPlay will be connected with Samsung TV. - Now, you can cast videos or any multi-media from your AirPlay to Samsung TV. Reading Recommendation: How to connect Alexa with Spotify
Airplay Code Requirement Settings
In very few cases, We have seen that by following the above methods, you are still unable to get the code of your AirPlay on your Samsung TV which makes the disability of having a connection between both devices. But, don’t worry! You don’t need to get the code to make the connection.
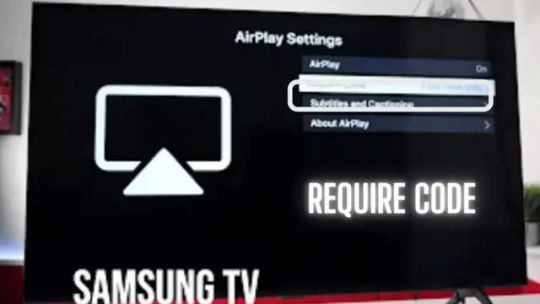
Require Code on Samsung TV - Go to the general settings of your Samsung TV. - Try to locate the Airplay there. - You can find the ‘Require Code’ option there. - Check if you have enabled this option as ‘One Time’ or ‘Every Time.’ - If you have enabled it as ‘Every Time’, You have to give the code of AirPLay whenever you connect your AirPlay with your Samsung TV. - We recommend you set it to ‘One Time.’ So that you won’t require every time to put the code for the AirPlay connection. You can enable passwords in your Samsung TV to enhance the security of your AirPlay. But, it is different from the code.
Samsung TV AirPlay Not Showing Up/Not Available
AirPlay is quite interesting and handy feature which has enabled its users to cast their multi media from their short screens to the Big TV Displays. However, some people have faced the issue that AirPlay is not showing up and is not available on their Samsung screens. Sometimes, Users have their software not updated and try to connect with obsolete software and see this on their screens ‘Samsung TV AirPlay Not Working Black Screen.’ If there is an update available, you can update which will easily resolve the issue and make the connection between AirPlay and Samsung TV. If this does not work, you can reboot your wifi router and again check that your AirPlay is connected to Samsung TV.
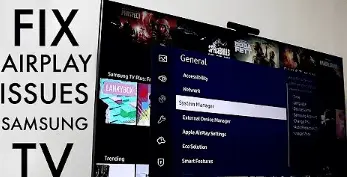
Check Your TV is AirPlay 2 Compatible
Some users will not be able to connect their AirPlay with Samsung TV. This is not the fault as Samsung has made their TV compatible with AirPlay in 2018 manufacturing. If you have the Samsung model manufactured in 2017, then sadly you are not able to connect to AirPlay due to the non-compatibility. Check your Models from the mentioned below and see if they are AirPlay Compatible 2018 Models - Frame TV. - QLED 4K. - 4K UHD TV. 2019 models - Serif - 8K and 4K QLED TVs 2020 models - Crystal UHD TVs. - 8K and 4K QLED TVs. 2021 models - Crystal UHD TVs. - 27″ and 32″ M5 Smart Monitors.
Keep the Devices Close Together
Sometimes, the AirPlay connection non-availability is due to the distance between the AirPlay connection and Samsung TV. The devices are not put too close together which makes the interference of signals in the room area with other devices which may have the connecting option. These devices cause the disruption between the AirPlay and Samsung TV connection. These devices may be your smartphones, other smart TV in the room, or the Microwave. TIP: Try to bring the devices to close together enough. Try to remove other overlapping devices from the area where you have to create the connection between AirPlay and Samsung TV.
Turn off running apps on the iOS device
Sometimes, AirPlay is not connecting ith Samsung TV due to the slower device or lag happening. In this case, You must check that iOS apps running behind and taking enough of your memory which may cause some distortion in the connection. Try removing the background apps or the apps which you do not want to open again. But, if you remove all the apps, it will soothe the AirPlay connection with Samsung TV.
Turn off Computer’s Firewall
In connecting any device with the other, Firewalls do interrupt and sometimes, due to the security issues, there might be a chance that Firewall Protection of iOS MacBook is on and working behind. This may block the AirPlay connection with your TV.

Firewall Settings TIP: Try to adjust the firewall settings and enable them to allow all incoming connections. You can also turn off the firewall settings. Hope that, by setting the firewall, ‘Samsung tv airplay not working’ issue will be resolved.
Restart your iOS device
In most cases, minor issues with the smartphone or other connecting devices are solved by only rebooting them and restarting them again. So, it will remove the already saved cache and allow all the functions to work normally. You can do this by following the steps mentioned below. Find Both volume and power buttons on the device. - Press the VOLUME UP button. - Press the VOLUME DOWN button. - Press and hold the POWER button for a few seconds. Or until the device turns off and on.
Restart Samsung TV
You must restart your TV to check whether there are any software glitches or not.

Reset Samsung Tv In some cases, TVs have also default settings that go into the cache which disrupts the connection. To restart your Samsung TV: - Make sure that your TV is turned on. - Unplug the connection of the TV with an adapter. - Plug again after almost 1 minute. - You are all set to connect AirPlay again with Samsung TV. Enjoy Reading Too: Activate Bally Sports on Roku | Fire TV | Xbox | Apple TV
FAQs
Does Samsung work with AirPlay? Yes! AirPlay works for the Samsung TV models of 2018 and above. It makes it so easy to enjoy the big screen with the AirPlay feature and get rid of the wired connection. How do I get AirPlay on older Samsung TV? - Connect both devices with the same wifi network - Tap screen mirror and then select AirPlay - TV display will appear there. How do I update AirPlay on my Samsung TV? - Go to General in the Settings and open Apple Airplay Settings. Open Airplay Settings of Samsung TV. - Select Airplay and disable it. - Then enable Airplay and check if it is working fine on the Samsung TV. How do I make my Samsung TV discoverable for screen mirroring? - Download the smart TV app. - Open screen share. - connect the same network to both devices. - Use your phone as a remote Read the full article
0 notes
Text
How to Factory Reset Your iPhone Using Code 2023
How to Factory Reset Your iPhone Using Code 2023
The content of a mobile device is erased when it is reset or returned to its factory state, therefore if you don’t want to lose anything, you should back up your data before doing so. Free factory or hard resets are available for Apple iPhones. We’ll walk you through the codes to reset the network on your iPhone so you can restore the default network settings. You will also receive codes for both…

View On WordPress
#Apple iPhones#Apple iPhones Password Recovery#Apple iPhones Using Security Questions#Can I reset an iPhone if I don&039;t know the Apple ID#Hard Reset Code And its Use in iPhone 2023#How Do I Reset My iPhone 2023 Using The Major Code#How to factory reset iPhone without a computer#How to Factory Reset Your iPhone Using Code 2023#How to Master Reset or Hard Reset iPhone (2023)#iPhone#Is There A Code For The iPhone To Reset Network#Password Recovery#What is the default 6-digit passcode for iPhone
0 notes
Link
Chimera Tool Crack to offering a CoreTrust bypass, this is the first jailbreak that supports A12 devices, including iPhone Xs, iPhone Xr, and the newest iPads. Moreover, Chimera does not change user files, which makes it safer than alternatives. We rewrote Chimera from the ground to avoid battery loss, freezing or squeezing. There is simply nothing else and we are curious to see it for ourselves. Chimera comes with the modern package manager Sileo, which offers an iOS-engineer interface with numerous features and speed enhancements to make package installation child’s play. Download now Autocad 2019 Crack With Chimera Tool Activation Key Mobile Phone Utility, you can unlock and repair Blackberry, LG, Samsung, HTC and Mobiwire phones. Unlocking Blackberry, LG, Samsung, HTC, and Mobiwire phones is possible with Simply Unlock, the most popular unlocking software in the world. FuriousGold has been updated regularly for over 8 years, making it one of the most advanced unlocking tools on the market for professionals. Use FuriousChimeraMobilePhones utility for FuriousGold, and install it on your computer. Connect the phone to an original cable or to a FuriousGold cable (if you are using the case) from the list of models supported. Simply click underneath and your customers will be able to unlock right away. one of the most advance and popular audio tool you also like Cubase Pro Crack Chimera Tool License Key Features: Get information: You can get information about your phone, such as: For example, the IMEI number, SIM lock information, software version, etc. Change Software: You can update or downgrade your current version of the software using Chimera Tool Full Crack. Usually, this usually fixes software bugs, and you can also edit / add languages. More information about this feature can be found here MEP Unlock: You can calculate the correct MEPs (unlock codes) for most older security phones (up to OS10, such as BlackBerry Z10, Q10, etc.). Further information on entering NCK can be found here. Instant Unlock: With this kind of novelty and global functionality, you can unlock your phone directly. This also means that you can unlock the phones with the MEP 0 problem (you can not try it anymore). Repair IMEI: You can repair your IMEI number if you need to restore the original number. It’s a permanent feature, you can change the software or whatever you want. * It is a paid feature, check our prices here Secure Phone: This feature secures important unique security fields. Restore Phone: Restores previously saved security fields. Chimera Tool Pro Crack: Refurbish: This is an amazing new feature provided only by ChimeraTool Registration Key. With this unique feature, you can fix any software problems, such as: Your phone just blinks and does not turn on (more information about blink codes) Your phone will try to turn on, but it will restart during the ignition process. The phone reboots if you want to enable the network (mainly for 9300, 9800, 9780 models, etc.). The processor is not connected to the flash during manufacture and the phone will not turn on The phone is in MFI mode and you can blink with the final SFI packet. Nuke Phone: This feature is only required if you want to destroy all user data and your operating system. After this feature, you will need to update your phone with the new software because it will not turn on. More about this feature Correct Application Errors: This feature displays a working silhouette on your phone, including the SFI (OS), APP, and SFI2 regions. Typically, this is required if you can not complete the flash process with the original BlackBerry update software. Resetting the Life Timer: You can reset the Life Timer (BUYR – Voice and Data Counter) * This is a paid service. Check our prices here Change Supplier ID: You can change the supplier ID (operator code). BlackBerry identifies your software package and allows you to update your phone only for updates that your wireless service provider accepts. This means that if you can change the vendor ID in Chimera Tool Registered, you can use other, sometimes newer, update packages without searching the vendor.xml file. Chimera Tool Pro License Crack:
1 note
·
View note
Text
The World of Social Media Hacking: Unveiling the Secrets

Currently, social media is the main part of communication, and it’s become a part of our lives. Facebook, Instagram, WhatsApp, and Snapchat platforms have billions of users. Those platforms are the vendors of information. Social media hackers have huge demands, especially those who want to hack and uncover their activities. In this blog, we will discuss how to hack social media. And introducing to you the world’s best social media hacker, HackersList
Understanding Social Media Hacking
Social media hacking is accessing someone else’s social media. And this can be done to monitor someone’s activities and uncover secrets. These common social media hackers leave no traces on the platforms and possess sophisticated techniques.
How to Hack Facebook
The main target of hackers is to hack Facebook because Facebook is a popular social media. And to hack this Facebook, a hacker uses different techniques:
Phishing: It creates a login page that looks similar to Facebook. When the target logs in through this page, the hackers capture the login information.
Keylogging: Hackers can easily capture their login information by installing keylogger on targeted devices.
Social Engineering: This technique forces the target to reveal passwords or sensitive information through psychological means.
How to Hack Instagram
Instagram is one of the platforms used by the youth here. And there are some simple methods to hack this instagram:
Brute Force Attack: This method is mainly used for weak passwords. It helps in hashing out weak passwords
Password Reset Exploit: With this method, the reset link sent to the target’s email is blocked. By exploiting this reset link, a hacker can access the target’s Instagram
Third-Party Tools: Some hackers use other tools or third-party tools to hack Instagram accounts that require deep understanding of coding and network members.
How to Hack WhatsApp
WhatsApp is a popular messaging app these days, despite its many security features, hackers have found ways to break into it.
Spyware: Spyware is installed on the target’s phone to monitor all of the target’s media file messages
MAC Spoofing: Through this method, the MAC address of the target’s device is matched with the MAC address of the hackers’ device. So that hackers can access the WhatsApp account very easily
QR Code Scanning: Hackers use this method to create a fake QR code. And by scanning this fake QR code target can access WhatsApp
📌 Read Also: WhatsApp Spy Online Tracker App for Android and iPhone
How to Hack Snapchat
One of the most popular messaging platforms is Snapchat. And its special feature is invisible messages. And here are some methods to hack snap chat
Phishing: It creates a fake login page just like Facebook. The login page looks like the snap chat login page. With which hackers can capture the login information by the target.
Packet Sniffing: This allows hackers to access all data sent over the network. This is a means of Snapset hacking.
Credential Stuffing: When the target uses the same password on multiple platforms. Then it becomes very easy for hackers to hack the target platform through this method.
Meet the World’s Best Social Media Hacker: HackersList
Hackerlist is the best when we talk about a skilled experienced and professional hacker team. We can take the help of HackerList when we need to find out any information hidden in a target’s activity messages on various social media platforms. Because they have a customer service system and sense of responsibility and hackers on HackersList do these things very efficiently. And they do it with complete client confidentiality.
Why Choose HackersList?
Expertise: Because they have all the hackers and who are very skilled and talented they do the client’s work very carefully
Discreet Services: Client privacy is Hacker List’s main goal and it is their top priority. They ensure that all activities are done very confidentially and they leave no traces
Comprehensive Solutions: HackersList They try hard as long as your work is done with privacy. And try to hand it over to you quickly after completing the work.
Reliability: HackerList can be a reliable choice for those looking for all hackers and professional hackers with proven track record of hacking. Click here
Conclusion
Finally we want to say that when you are looking for a skilled Facebook Hacker, Instagram Hacker, WhatsApp Hacker, Snapchat Hacker, HackerList can be the best choice for you. Because they have the best customer service, the best skilled hackers, and they prioritize client privacy.
0 notes
Text
DOWNLOAD DB2 DATADIRECT DRIVER
Uploader: Trip Downloads: 2409 Operating Systems: Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X File Format: exe File Version: 010191042 File Size: 23 Mb Date Added: 30 December, 2019 Price: Free Download Type: http File Name: db2 datadirect driver

Fixed Issues: - Fixed(db2 datadirect driver Fixed) the problem that system hangs up at POST code FF with over clocking setting- change the multiplier factor from CPU default to 19. - Fixed WiFi can not connect successful sometimes when player install HDD. - Fixed data corruption issue in current v1.03 f/w after changing the toolchain. - Fixed Yellow bang on SMBUS when(db2 datadirect driver when) fresh XP SP3 image is created on some Dell systems. - Fixed schedule issue. - Fixed Conroe-L CPU XD Function can't be(db2 datadirect driver be) disabled issue. - Fixed the error that some specific ID3 tags were(db2 datadirect driver were) not displaying on the screen. - Fixed the error that above part of subtitle was not disappeared when subtitle is set as extended horizontally and more than 5 rows. - Fixed the issue found no video streaming when the device was boot in low light environment. - Fixes(db2 datadirect driver Fixes) 0xFE issue with dual bootable factory image. Users content: You need to disable "Force IPsec with L2TP" options for pure L2TP tunnel in VPN and Remote Access >> PPP General Setup. - Fix web gui issues of wireless security page. After that, replug your network cable or do whatever it takes to reset your computer network adapter. One major improvement of the Socket AM2 is the support for dual channel DDR2 memory. - Update AURA LED in BIOS. In Event View under Diagnostics Performance, critical log, which shows shutdown process is delayed by ATI display driver, is recorded. Update SandyBridge CPU2. The Self-Extracting window appears and prompts you to extract or unzip to C:\DELL\DRIVERS\R302518. P5GPL-X SE BIOS 0301Support new CPUs. Windows Security popup may be experienced after install and reboot on some Hybrid Graphics system configurations. DRIVER DOWNLOAD CANON 4200F XP WINDOWS Supported OS: Windows Server 2003 64-bit Windows 7 32-bit Microsoft Windows 8.1 Enterprise (64-bit) Windows Server 2008 R2 Windows Server 2016 Windows 2000 Windows Server 2012 R2 Windows 8.1/8/7/Vista 64-bit Windows 8.1/8/7/Vista 32-bit Microsoft Windows 8.1 Enterprise (32-bit) Microsoft Windows 8 Pro (32-bit) Windows 7 64-bit Windows XP 64-bit Windows Vista 64-bit Windows XP 32-bit Microsoft Windows 10 (32-bit) Windows Vista 32-bit Notebook 8.1/8/7 32-bit Windows 10 Microsoft Windows 8 Enterprise (32-bit) Microsoft Windows 8 Pro (64-bit) Microsoft Windows 8.1 (64-bit) Notebook 8.1/8/7 64-bit Windows 8.1 Microsoft Windows 8.1 Pro (32-bit) Microsoft Windows 8 (64-bit) Windows Server 2012 Microsoft Windows 10 (64-bit) Windows Server 2003 32-bit Windows 7 Microsoft Windows 8 Enterprise (64-bit) Microsoft Windows 8.1 (32-bit) Microsoft Windows 8.1 Pro (64-bit) Windows 8 Windows Server 2008 Microsoft Windows 8 (32-bit) Searches: datadirect db2 driver; db2 datadirect Lrq012-rqt; db2 datadirect L01r; db2 datadirect driver for Windows 8.1/8/7/Vista 32-bit; db2 datadirect driver for Windows Server 2012; db2 datadirect LTAZC0125; db2 datadirect driver for Microsoft Windows 10 (32-bit); db2 datadirect L LT012-0; db2 datadirect driver for Windows 7 32-bit; db2 datadirect LT0125; db2 datadirect driver for Windows Server 2008 Compatible Devices: Samsung; Video Projector; Hardware; Memory Card; Iphone; Tablet To ensure the integrity of your download, please verify the checksum value. MD5: eb39a48b4bdabbe2cf28e7a85bab1d04 SHA1: 940651cc4b7875d97b6b98ad3ed83c5f0047b5ca SHA-256: 0b1d360779990bcfadd51f192210b038269384084b516eb789ecb2d04ade3d35
1 note
·
View note
Text
listen up youngsters, you have no idea how fast this shit evolved.
it was the '90s and personal computers and internet were a luxury or a very niche thing. you either used one in the office / university or you were a nerd. not many other choices.
schools weren't even well equipped. my father bought us a pc in '95, the first pentium released in Italy with Win 95. at school though, we still had 386 and 486. they turned on the DOS prompt and they had Windows 3.1. only in the third year they found the funds to equip the lab with pentiums and Win 98. btw, this lab was available ONLY if you were in the computer course program (this is Italy, we have a different system). the rest of the school used them very rarely.
I attended university between 2003/2006. many of my schoolmates never used a computer before, but it was literally mandatory having one, because teachers would not accept an handwriting assignment and typewriters weren't a thing (public libraries were the first services to be equipped with computers, so if you really needed, you will go there to use one and print. the university had a room with pc free for students, but only in our course there were 30pc for 180 people). plus, the university had at least three computer classes. I still remember, in the second one, the time a girl screamed in fear because her laptop were telling her something and she didn't know what to do. it was Norton. it wanted to be updated.
by that time I already mastered a certification in office (yes, it was a thing back then), learned a bit of html and Mambo, failed miserably on the binary code class (don't ask me why there were this classes on an Art and Theatre degree, I don't know), learned several graphic softwares and I was keeping up with the piracy world (I started in highschool. it was hard. it was not: just download a torrent client, a vpn and you're ready to go. you had to go in you computer settings. you have to go in the software settings. they didn't update automatically, you had to do it manually and hope the sftw didn't crash after. you had to keep track of what servers were still safe and which weren't. which were still active and which not. etc.
btw, social networks were not a thing yet. they existed, yes, but since the majority of the world didn't even a mail yet, they were used by usual internet users, nerds. gmail had just been born and you had to be invited to it. google still had the "don't be evil" in its guidelines. FB was already born and released, but people didn't know what to do with it. twitter will be born only in 2006 and trust when I tell you that it was scarcely used.
AND, the smartphones were not out yet. the first iPhone would have come out only in 2007, the first android only in 2008. if the iPhone and iPod were pricey but easy enough to be used by the masses, the Android was not. my boyfriend at that time had to often reset it and disconnect the SD card to making it work again.
that was only less than 20yrs ago.
that was the time when digital cameras were becoming much more common and more affordable (the compact ones). but, if society were starting to have a lot o people who discovered the freedom of taking all the pictures they wanted without spending a kidney in films, the smartphone was still a very very nerdy thing. and socials too.
slowly, business started to force people to get more close to technology and having at least an e-mail.
with an e-mail they started to be able to use more stuff.
people discovered the power of snooping and boasting on socials. then facebook started to force its users to use their real names (there was a period when they would find weird names and ask for your ID to certify it was you real name. yes, they are always been that arrogant. they stopped when the fake IDs tools were literally everywhere). twitter copied that by putting out the "verified account" badge. android finally got its shit together.
all of this, in less than 10 years.
etc.
since then it has been a rush. every 3 to 6 months there's something new. what has been released the previous year is already obsolete.
you are born in these times, so you can't know how slow tech evolution used to be. I had the same walkman model for all highschool. I broke a few, but in that 5 years span I was always able to buy the same one because it was the best one. today it's not totally impossible (up to 3-4 yrs) but stupid to do so.
the cd players were pricey, they were no really made for walking (the cd used to jump often) and you had to know how to pirate and burn a cd if you didn't want to spend all your parents money on official records.
on every mp3 you were downloading, you downloaded at least 2-3 porns that were uploaded with the song's name (don't ask...).
also, planned obsolescence was not so planned.
I'm not forty yet, but I already saw way more technological upgrade than my grandparents who lived twice as me.
so, stop asking how old are we like were this kind of prehistoric beings. technology moves fast. you will see in a few years when the new youngs will ask you the same question.
and this is tumblr, not tik tok. we're allowed to be old and still online.
remember when you were 10 and you would hang out with your friends in order to Look At The Computer together like you went to their house and experienced the information superhighway together. and then leave
356K notes
·
View notes
Text
HD Video Converter MP4
Why convert Audible to MP3? Some customers have been reaching us with questions about converting an audio file from CDA to MP3. Some have reported that after they upgraded to Windows 10 some audio recordsdata have been mechanically transformed frommp3 tocda. Step 4: On the subsequent window that seems, make sure that the Convert" button is chosen. Proceed to decide on the type of audio file you want to create. In our case its MP3 file we are changing to. Home windows and Mac OS X supported.cda are index information on audio CD below Home windows. Convert animated GIF to MP4 video with a single click on. Quick, free on-line software with no watermarks. For those who're on the lookout for a simple program that works without the advanced options and complicated interfaces that some of these audio converter instruments have, you'll definitely like MediaHuman Audio Converter. You've got seen our prime 5 finest iTunes M4P to MP3 Converters for Home windows, which are created to decrypt the iTunes protected M4P recordsdata for you. Which one is the most effective? Properly, you have seen our opinion, yours may differ. Each program can discover its user, and the person can select the app which inserts really him. The top 5 iTunes M4P to MP3 converter listing above is that will help you take the fitting decision.

The MP4 file format and themp4 filename extension consult with the MPEG-four half 14 digital multimedia format developed by the Shifting Image Experts Group. It is used as a multimedia container to wrap encoded digital video and audio streams, together with subtitles and still photos if required. In current decades, the format has been popularized as one of the important standards for streaming media over the web and other computer networks and for the digital distribution of huge multimedia files. MP4 helps a large number of compression audio codecs allowing recordsdata in this format to keep up a comparatively small dimension with out discounting playback quality. Use the Channel Converter to vary the variety of channels in an audio file, reverse the channels of a stereo file or intermix the channels of a multichannel file to create panning eventualities. When the conversion is accomplished, click on the obtain hyperlink to get your convertedMP3 file. At the Output tab, you'll be able to edit the location where you wish to save the converted file. Lastly, hit the Convert All button for the MP4 to MP3 converter to begin the conversion course of. MyMP3 is an iOS app which permits the users to transform any type of video or audio file to MP3 at a super quick pace. This app designed by Local Community Media, can convert your recordsdata from many alternative file formats and have it in MP3 so that you can play it on your cellphone or different iOS units. The MP3 converter for iPhone requires iOS 8.zero or later for the compatibility. Free CDA To MP3 Converter lets you convert cda to mp4 free files into MP3 format. The conversion takes a view minutes. Afterwards, you can download your video or audio monitor. Simply obtain the transformed video to your smartphone using the supplied QR code. The default output format is MP3. In addition to changing Spotify to MP3, it also supports changing Spotify Music to M4A, WAV, FLAC. Click Choice - Superior to change output format, SampleRate or BitRate in accordance with your wants. Click Possibility - Basic to alter output folder should you like. 4Easysoft Free MP4 Converter lets you preview the video earlier than conversion, which can assist you ensure that the video to be converted is what you want. iTunes is Apple's media instrument which might handle and play video and audio information for Apple users. In case you have many MP4 music movies in iTunes library and want to convert MP4 to MP3 to save house, then learn under to know methods to convert MP4 to MP3 iTunes. And it stays like this for all future use of the MP3 format, until one goes to Instruments""Preferences""Reset preferences" which then returns all to defaults and it really works, but solely at the 128 bit price. Other formats like OGG Vorbis and so on aren't exhibiting this behaviour, and I don't bear in mind my earlier verson which was 2.zero.5., doing this. We reside in a world the place we want every movie and TELEVISION show to be out there at our fingertips on every digital machine in our arsenal. Shelves chock-full of flicks now seem overly cumbersome, and they're also an unnecessary waste of area that can be higher used for one thing else. On top of that, we all know how boring a flight or practice journey can be without access to a strong library of entertainment. There's multiple option to convert your spinning movie discs to a format that's appropriate with a spread of devices, and right here to help out is our guide on the right way to convert a DVD to MP4. Output: Almost all converters embody MP4 in output profile listing. WinX HD Video Converter Deluxe is no exception. Higher still, it optimizes MP4 output separately for COMPUTER, Mac, Apple iPhone (7, 6s, 6, and so on.), iPad (Pro, Air, mini), Android Samsung Galaxy S7, Sony Xperia XZ, Windows Cellphone, Xbox, Surface Professional 3, YouTube, Facebook, Vimeo, iTunes, iMovie, Ultimate Cut Professional, and more gadgets, internet providers, packages. So, we needn't set resolution and facet ratio manually. As for cda to mp4 online output quality, there's nothing to fret about. Embedded Excessive High quality Engine will help maintain doable good quality.

Wondershare Video Converter Ultimate even holds the power to transform multiple videos at a time. All you'll want to do is import all of the recordsdata you want transformed, set their output parameters, and hit the Convert button. One other highlight of this software program is its Excessive Speed Conversion mode. This selection uses the APEXTRANS expertise with a view to ship 30x sooner conversion speeds. Nevertheless, it's only applicable for a select few video codecs. However don't be concerned, as MOV and MP4 are certainly supported by it.
Created MP4 information shall be appropriate with HTML5 standard, so you should utilize it on your website. Click "Convert" to convert all CDA tracks into WMA format. Click on Converter Now!" button to start altering all CDA information to MP3. Insert a clean CD into your CD burner (when prompted by Home home windows Media Participant). Dwelling home windows Media Participant will now analyze each of the MP3 data you can have chosen and convert them to the compact disc audio file format. These newly reworked information will then be burned to the CD in your CD burner.
1 note
·
View note
Text
Ideas, Formulas and Shortcuts for Icloud Unlock
Unfortunately, there's no way to unlock more than 1 phone with a code provided. If you want to unlock a number of phones, please make a number of orders. When connected to the support rep, explain that you've got an iCloud-locked phone and that you would love to submit a request to get it unlocked. Put simply, your phone should remove iCloud Activation Lock. If you would like to utilize your phone abroad or find another network provider in your house country, you should unlock as a way to use them. How to Jailbreak iPhone Cell Phones Whether you wish to unlock your phone to change carriers, or you simply wish to jailbreak it so that you may download some cool 3rd party apps, ringtones, wallpapers or screen savers, you will have to choose how much risk you're ready to take. Luckily, it's simple enough to unlock your Straight Talk phone.   icloud unlock free The Icloud Unlock Stories Even worse, the majority of people just throw their devices away or offer them for dirt cheap. First you must ascertain whether the unit is erased or not. The device should restart when the procedure is finished. You are then going to be in a position to prepare the device as new. Therefore, you won't have the ability to use the device till you remove iCloud ID details which belongs the old owner. For example, you cannot be in a position to reset or erase the device, you are unable to reactivate the device using your details, and finally, you can't have the ability to switch off the find my iPhone on the gadget. If a person is attempting to sell an iOS device for rock bottom prices then you ought to be skeptical as it's possible that the unit is stolen with Activation Lock enabled, which will ensure it is impossible to use the gadget. Top Icloud Unlock Secrets If you prefer, you can get in contact with the telephone's very first owner and find any help. Click the home tab, as soon as you are on the activation screen. There are a number of ways to bypass an iCloud lock screen but almost all of these are temporary solutions and doesn't work whether the device has been reset to factory settings. The IMEI credits may be used to unlock devices later on if you aren't able to correct right to the computer. It's only if your iCloud account is activated you could employ your device. Consequently you're going to be in a position to add your iCloud account rather than the old one. Afterward, easily you may make a new iCloud account and after that begin working with your iPhone freely. You may not have your iCloud password, and you might be not able to restore your iCloud account. If you've forgotten your Apple ID password, want to modify your Apple ID, or wish to understand how to turn off Find My iPhone. When picking an iCloud Bypass assistance, the user must be quite careful. He can study the previous reviews and choose the best. Then he cannot use the device. When you understand what you'll get access to when you do an iPhone 6 unlock, you are going to be ready to earn a last decision about whether doing so is appropriate for you. To do that you will need access to the email account that's been used to prepare the account.
1 note
·
View note
Text
Anyunlock keygen

#ANYUNLOCK KEYGEN SERIAL NUMBERS#
#ANYUNLOCK KEYGEN SERIAL KEY#
#ANYUNLOCK KEYGEN FULL VERSION#
#ANYUNLOCK KEYGEN LICENSE KEY#
#ANYUNLOCK KEYGEN LICENSE KEY#
Using warez version, crack, warez passwords, patches, serial numbers, registration codes, key generator, pirate key, keymaker or keygen forĪnyUnlock license key is illegal and prevent future development ofĪnyUnlock.
#ANYUNLOCK KEYGEN FULL VERSION#
Windows 7 Download periodically updates pricing and software information of AnyUnlock full version from the publisher,īut some information may be out-of-date. Using AnyUnlock freeload crack, warez, password, serial numbers, torrent, keygen, registration codes, key generators is illegal and your business could subject you to lawsuits and leave your operating systems without patches. However, windows7download reserves the right to remove or refuse to post any submission for any reason. AnyUnlock password unlocker - Download Notice.
#ANYUNLOCK KEYGEN SERIAL KEY#
ProPresenter 6.2 Crack Keygen + Serial Key full. This software can solve the problem with inkal Cummings expires. You acknowledge that you, not windows7download, are responsible for the contents of your submission. A very reliable tool, AnyUnlock is swift in removing your iPhone passcode and handing you back the access in just 3 steps. AnyUnlock is the an iPhone passcode unlocker that helps you unlock various types of iPhone passcode such as Apple ID passcode, Screen Time passcode, iTunes backup passcode.
#ANYUNLOCK KEYGEN SERIAL NUMBERS#
Find information about your Autodesk software license type and associated serial numbers (if any) in Autodesk Account or in the product. 7 Data Recovery Crack + Serial Keys + Keygen Full Alternative. Giveaway: iCare Data Recovery License Key freeload. This is not the unlocking code that has just been provided. For information concerning the PIN, PIN2, PUK and PUK2 codes for a SIM card please read the manual that came with your phone.All AnyUnlock reviews, submitted ratings and written comments become the sole property of Windows 7 download. List of 12 Best Free Android Data Recovery Software in 2022. Question: My phone asks me to enter a PIN numberĪnswer: For SIM cards with a PIN ENABLED you will be required to enter a PIN. And the product key is, in turn, paid for by the user, and at the end of the day, the software is freeware only for a few days. There is no charge and your device will be returned within 10 to 15 business days. Here is a method by which you can easily find the serial key of any software on the internet. Please visit your local Vodafone Australia store who will forward to our repair centre. 65 OFF iMobie AnyLock Coupon Code: Get 65 discount on AnyUnlock - iPhone Password Unlocker (Windows) Lifetime Plan - 5 Devices + 1 Computer for only 47.99 (Reg. On occasion the unlocking codes do not work, if this has occurred the device will require the network lock being removed physically. If the unlocking code (NCK) has not worked follow the following procedure:ġ) On the unlock screen enter the master reset code (Screen similar to below)Ģ) After enter entering the master reset code (MCK), the screen will display "Network unlock request unsuccessful" Please disregard (Screen similar to below)ģ) When the unlock screen repopulates re-enter the unlocking code (NCK) as per "entering the unlock code (NCK)" instructions aboveĤ) IF this procedure has been successful the device will display(Screen similar to below) Vodafone Customer Support on 1300 650 410Ģ) Insert non-Vodafone Australia SIM cardĤ) Unlock screen will populate (Screen similar to below)(This may take some time to populate)ĥ) Enter unlock code (NCK) (Screen similar to below)Ħ) If the device has unlocked successfully the following will display (Screen similar to the following)ħ) However if you enter incorrect code, phone will display "Network unlock request unsuccessful (Screen similar to below) If you would like someone to talk you through this process, you can call: anyunlock keygen Can Gradescope detect other tabs. PLEASE READ THE INSTRUCTIONS CAREFULLY BEFORE YOU ATTEMPT ANY UNLOCK PROCESS. Code Similarity is available with institutional site licenses and for.

0 notes
Text
Best Mobile Hacking Methods & Advantages for Tracking - 2024

Mobile phone hacking has become a prominent topic in today's digital age. The increased reliance on smartphones for communication, banking, and personal data storage has made them prime targets for hackers. This article delves into various aspects of mobile phone hacking, including methods, vulnerabilities, and the potential risks involved.
How to Get into Someone's Phone
Accessing someone’s phone without their permission is illegal and unethical. However, understanding how hackers might attempt to infiltrate a phone can help in better securing your device. Here are some common methods: 📌 Read Also
1. Phishing Attacks
Phishing involves sending deceptive messages that appear to be from a legitimate source. Once the victim clicks on a link or downloads an attachment, the hacker gains access to their phone.
2. Spyware Apps
Spyware apps can be installed on a phone to monitor activities, steal data, and track locations. These apps often run in the background, making them difficult to detect.
3. SIM Swapping
SIM swapping is when a hacker tricks a mobile carrier into transferring a victim's phone number to a new SIM card. This allows the hacker to intercept calls and messages intended for the victim.
How Can You Hack Someone's Phone?
Hackers use a variety of techniques to gain access to someone’s phone. Here are some of the most common methods:
1. Social Engineering
This involves manipulating individuals into divulging confidential information. Hackers might impersonate a trusted person or authority to gain access to sensitive data.
2. Malware
Malware is malicious software designed to damage or infiltrate a system. Hackers can use malware to gain control of a phone and access its data.
3. Exploiting Vulnerabilities
Hackers often exploit known vulnerabilities in a phone's operating system or apps to gain access. Keeping software up to date can help mitigate this risk.
Hack Phone with Phone Number
Hacking a phone using just a phone number is challenging but not impossible. Techniques include:
1. SS7 Exploitation
Signaling System 7 (SS7) is a protocol used by telecom networks. Hackers can exploit vulnerabilities in SS7 to intercept calls and messages.
2. SMS Phishing
By sending a fraudulent SMS, hackers can trick victims into revealing personal information or downloading malware.
Hacking Phone by Calling
Hackers can also gain access to phones through phone calls. Techniques include:
1. Voicemail Hacking
If a victim’s voicemail is not properly secured, hackers can access it by using default passwords or exploiting network vulnerabilities.
2. Caller ID Spoofing
Hackers can disguise their phone number as a trusted contact’s number, tricking victims into answering and revealing sensitive information.
Hack Someone’s Phone Number
Hackers can use a phone number to gain access to various accounts linked to it. Methods include:
1. Two-Factor Authentication Bypass
Hackers can intercept two-factor authentication codes sent via SMS, gaining access to accounts that use this security measure.
2. Account Recovery Exploitation
Many accounts use phone numbers for recovery. Hackers can exploit this feature to reset passwords and gain access.
Hack a Phone by Sending Spam Messages
Spam messages often contain malicious links or attachments. Techniques include:
1. Smishing
This is phishing via SMS. Victims are tricked into clicking links that download malware or redirect to fake websites.
2. Malicious Attachments
Spam messages can contain attachments that, when opened, install malware on the victim’s phone.
Hack Phone Through Call
Calls can be used to gain unauthorized access to a phone. Techniques include:
1. Voice Phishing (Vishing)
Hackers use phone calls to impersonate trusted entities and extract personal information from victims.
2. Remote Code Execution
In some cases, hackers can exploit vulnerabilities in the phone’s software to execute malicious code during a call.
Can Hackers Hack iPhone?
iPhones are generally considered secure, but they are not immune to hacking. Methods include:
1. Jailbreaking
Jailbreaking removes restrictions imposed by Apple, allowing the installation of unauthorized apps. This can create vulnerabilities.
2. Exploiting Zero-Day Vulnerabilities
These are unknown flaws in the operating system that hackers can exploit before they are patched by Apple.
Can You Hack iPhones?
While hacking iPhones is difficult, it is possible. Techniques include:
1. Spyware
Spyware designed for iOS can monitor activities, track locations, and steal data.
2. Phishing
Even iPhone users can fall victim to phishing attacks, leading to compromised security.
Can You Hack iPhone Camera?
Hacking an iPhone’s camera is complex but feasible. Techniques include:
1. Malware
Sophisticated malware can gain control of the camera, allowing hackers to take pictures or record videos without the user’s knowledge.
2. Remote Access Tools (RATs)
RATs can remotely control the iPhone, including its camera, once installed.
Hack iPhone with Phone Number
Hacking an iPhone using just a phone number involves exploiting telecom protocols and vulnerabilities:
1. SS7 Attacks
Hackers can intercept messages and calls by exploiting SS7 vulnerabilities.
2. SIM Swapping
This method can also be used to gain control over an iPhone by transferring the victim’s phone number to a new SIM card.
Hack Phone Messages
Intercepting phone messages can be achieved through various methods:
1. SS7 Exploitation
Allows hackers to intercept SMS messages without physical access to the phone.
2. Spyware
Installed spyware can monitor and forward all messages sent and received on the phone.
Hack Someone’s Messages
Gaining access to someone’s messages can provide a wealth of personal information. Methods include:
1. Social Engineering
Manipulating victims into revealing login credentials or other sensitive information.
2. Phishing
Sending deceptive messages that trick users into sharing personal information or downloading malware.
How to Find a Phone Hacker
Identifying a phone hacker can be challenging. Signs include:
1. Unusual Activity
Unexpected data usage, battery drain, or unfamiliar apps may indicate hacking.
2. Unauthorized Access
Receiving alerts about logins from unknown devices or locations.
Best Phone Hacking Apps
Some apps are designed for monitoring and security purposes but can be misused for hacking:
HackersList: An app that monitors activities on a target phone, including messages and calls. A powerful monitoring tool that provides extensive access to a phone’s data.
Best Hacking Tool for Android
Several tools are designed to exploit Android vulnerabilities:
HackersList: A remote access tool that allows hackers to control an Android device. A penetration testing tool that can be used to identify and exploit security weaknesses in Android devices. Connect with the team
World Best Hacking App
Determining the “best” hacking app depends on the criteria used. However, some apps are notorious for their capabilities:
HackersList: A highly sophisticated spyware developed by NSO Group, known for its ability to exploit even the most secure devices. A comprehensive remote control and monitoring tool for Android devices.
1 note
·
View note
Text
Att account overview

#Att account overview code
#Att account overview password
When you login to your ATT account, you’re dropped on the bill and pay section. Unfortunately, you can only choose one service at a time. The most popular services are Wireless, Internet, Uverse, and AT&T email. You’ll need to select which ATT service you want to register. You can create a user id by clicking create one now at. Overall AT&T has a lot of businesses services but has done a terrible job of helping you access them.Ī lot of times if you’re trying to do something it’s better to contact AT&T customer service rather than trying and getting frustrated navigating barely working menus. It’s unfortunate but for ATT Premier the UI is a bit messed up but if you put in the right information, you’ll still be able to log in. The login for small businesses is the same as for regular wireless accounts. Here’s the list of places where you can login Unfortunately, there are 6 places where you can login to access your ATT business services. If Yahoo email gets hacked, there’s a good chance that your AT&T service has been compromised as well. AT&T passed off the responsibility for its email service to Yahoo. If you ever have problems with your ATT email service, you can blame Yahoo. The look and feel of the email portal will be the same as a yahoo email account. If you create a new ATT email account, it will show up as currently from ATT. This is the same page to log in to your AT&T account if you have other services like phone or internet.Įven if you cancel your other AT&T services, you’ll still be able to login and access your ATT email account.ĪTT recently rebranded its email service in partnership with Yahoo. You can login to your ATT email account at If you’re paying your bill online, make sure to pay on time to avoid AT&T’s $7 late fees. It’ll identify that you’re using the phone registered to your account and log you in.
#Att account overview code
Zenkey will display a QR code and you just need to point your camera at the code. If you’ve logged in the past, your user ID will be saved, but you can change or delete your saved User ID. Your forgot ID email will list all of your ATT accounts if you have multiple services with ATT.
#Att account overview password
Visit /awards for more details.If you forgot your user id or password, click Forgot User ID or Forgot Password to get your account details to reset. Business Wireless Satisfaction Study of business customers' perceptions with their current wireless carrier. Verizon Wireless received the highest score among small business wireless providers in the J.D. Power 2022 award information, visit /awards for more details.Ĥ. Network Quality measures customers' satisfaction with their network performance with wireless carriers. Verizon also received the highest number of awards in network quality for the 29th time. Verizon is #1 for Network Quality in the Northeast, West, Southeast, Mid-Atlantic and North Central regions. RootMetrics rankings are not an endorsement of Verizon.ģ. Tested with best commercially available smartphones on three national mobile networks across all available network types, excluding C-band. Most reliable 5G network based on more first place rankings in RootMetrics' 5G data reliability assessments of 125 metro markets conducted in 1H 2022. Must remain on the One Unlimited for iPhone plan to access Apple One. Requires account subscribed to One Unlimited for iPhone plan (1 line includes an individual subscription for Apple One 2+ lines include a family subscription for Apple One).

0 notes
Text
Syncios data transfer license key

#Syncios data transfer license key cracked
#Syncios data transfer license key serial key
#Syncios data transfer license key full version
#Syncios data transfer license key registration
#Syncios data transfer license key for android
It supports 10 different file types, including photos, film, music, videos, etc.
#Syncios data transfer license key cracked
SynciOS Cracked helps you transfer, edit, back up, and manage your media files.
Also, you can use it for commercial and educational purposes. Once you’ve turned on this device, you can back up your phone and then transfer all data to both ends. That way, we were able to get you the best version of this tool so that you could access all the premium features of this tool.
#Syncios data transfer license key registration
Also, You can even reset your device to previous backup settings.Īlso, the free trial version of the Syncios Ultimate registration code does not provide access to all features. You can also manage application settings and restore them to default. Syncios macOS can not only manage your applications but also transmit data to your mobile device and vice versa. You will have access to your data and all applications to control and manage your data quickly.
#Syncios data transfer license key full version
Syncios Pro 7.1.0 Crack 2022 With Serial Keygen Full Version For Win/Mac: Also, it offers you the ultimate transfer solution between iOS, Android, and Windows PC. Syncios Manager Pro Premium Key 2022 is an alternative iOS management application to iTunes. What’s more, control the data have the ability to the data that is valuable that is customized. Thus, it includes windows and multiple other platforms. īackup applications that are manufacturing and A document designed to maintain safety desire and perfect when you possibly expect It can help you a great deal longer to work with the applying you’re currently sharing. The tool is quite smart, assessing to control it liberated and synchronizes the information between devices on a reasonable basis. Download NOW Syncios Pro Ultimate Crack 7.1.Download Setup & Crack Anvsoft Syncios 8.7.4 Crack Registration Key Latest Version freeload :Īnvsoft Syncios Crack can be an IOS manager, document shifting, communication, document managing, iPhone, iPod, i-pad, PC, Touch, I tune networking document sharing flawless program. Syncios Pro Ultimate Crack is one of the best and well-known data transfer and data management for mobile produced by Anvsoft Inc. this application is used to transfer data directly from one device to another, as well as recover and backup mobile data and files instantly to the personal computer. You can use this excellent program to play, download, and organize digital video and audio, share data between mobiles, tablets, and computers along with Microsoft Windows. It let the user transfer data and files effortlessly between computer and mobile. Syncios 7.1.0 Crack has multiple features with mobile device management which allow the best way to manage the user’s system quickly. The program will save in a folder on your PC/Mac any videos, images, contacts, apps, and even call logs stored on your phone or tablet due to without any Data loss. Hence, you can control all of the system functions easily. You can backup, transfer, and restore your applications, settings, Sms, Contacts, and Files. Yet, the IOS manager not only can you manage your applications with Syncios Manager, but you can also transfer your images between iOS devices and Laptops. You easily move your data with one click.
#Syncios data transfer license key serial key
Syncios Pro Ultimate Serial Key is an android phone management application software and data transfer program. It is also a media downloader and player. And can convert them from video files to audio. Users can also share data from one device to another. That should have the OS x and Microsoft Windows operating systems. The software also has windows and mac management programs.
#Syncios data transfer license key for android
Its latest windows program is the launch for IOS, Ipad, and iPhone.And the mac management program is only launched for Android 9 and iOS. These main features include an Online video downloading system, a Restore and backup system, and a Content management system. An online video downloading system allows you to download a hundred plus HD videos. In the backup and restore system you can get your data back to your device.įrom various sites such as Facebook, youtube, Dailymotion, and so on. Such as your messages, music files, videos, pictures, and many more data. And in a content management system, you can manage your files such as messages, call data, contacts, and apps. It has become a serious problem that people want to save and secure their data and keep connected with all devices, but it’s not as easy for Mac, IOS, as well as Android devices. These appliances only share and transfer the data to the same medium. It was a hard condition when people lost their mobile data without having any backup. Hence, looking for people’s issues about losing their data files Syncios Crack is here to solve out all problems. This software is the perfect data manager, data recovery, and data transferring application between Mac, IOS, Androids, tablets, and computersīy using Syncios, you can easily backup your entire data files without any difficulty.

0 notes