#IDSS
Explore tagged Tumblr posts
Text
Christine Ortiz named director of MIT Technology and Policy Program
New Post has been published on https://thedigitalinsider.com/christine-ortiz-named-director-of-mit-technology-and-policy-program/
Christine Ortiz named director of MIT Technology and Policy Program


Christine Ortiz, the Morris Cohen Professor of Materials Science and Engineering at MIT, has been named the next director of the MIT Technology and Policy Program (TPP).
“Christine is a force of nature,” says Fotini Christia, the Ford International Professor of the Social Sciences and director of the MIT Institute for Data, Systems, and Society (IDSS), which houses TPP. “Her years of service to the Institute, her support of grad students in particular, her research focus on innovation and the social good, and her network of connections across academia, industry, and government all make her the right leader for the program. At a time when technology has become such a critical part in informing evidence-based policy, I am confident that Christine will take TPP to the next level.”
Ortiz is a professor, engineer, scientist, entrepreneur, former dean, corporate board director, and foundation trustee. She is an internationally recognized researcher in biotechnology and biomaterials, advanced and additive manufacturing, and sustainable and socially-directed materials design. She has over 30 years of experience in science, engineering, research and development, and technology innovation. She has published more than 210 publications and supervised the research projects of more than 300 students, postdocs, and researchers from 60 different majors and disciplines. She has received more than 30 national and international honors, including the Presidential Early Career Award in Science and Engineering.
Ortiz served as dean for graduate education for MIT between 2010 and 2016, supporting all MIT graduate programs and more than 8,000 graduate students, where she led new initiatives in global education, educational technologies, and mentorship. She founded the nonprofit higher education and research institution Station 1 Laboratory Inc. (Station1), which is focused on socially-directed science and technology education, research, and innovation and maintains national and global reach.
Through her work at MIT and Station1, Ortiz has led the development of programs involving collaborations with more than 100 technology-focused startup companies and social enterprises. She serves on the board of directors of two public companies, Mueller Water Products (a water infrastructure and technology company) and Enovis (a medical technology company); is a member of the Commonwealth of Massachusetts Apprenticeship Council and the MIT Museum Advisory Board; and is a trustee of the Essex County Community Foundation in Massachusetts.
“I am deeply honored to take on the role of director of the TPP program, and inspired by its focus and impressive legacy of contributions related to the integration of responsible technological innovation, policy, community, and societal impact,” says Ortiz. “I look forward to supporting and advancing the TPP mission and collaborating with the incredible TPP students, faculty, alumni, and partners involved in this important and transformative work.”
Ortiz succeeds IDSS and earth, atmospheric, and planetary science Professor Noelle Selin, who was TPP director from 2018 to 2023. IDSS Senior Research Engineer Frank Field served as interim director this past year.
#000#2023#additive manufacturing#biotechnology#board#career#Community#Companies#data#Design#development#DMSE#earth#education#Engineer#engineering#Enterprises#Faculty#focus#Ford#Foundation#Global#Government#IDSS#impact#Industry#Infrastructure#Innovation#integration#leadership
0 notes
Text



idk how to post art
anyway i remembered i had free will and doodled my boyfriend with his partner pokemon :3
the gallade is a redraw of Gallade V illustration rare from lost origin, which is bf’s favorite full art, but i redrew it with his mega Gallade, and his other partner is Phantump :’3c
I’m gonna paint these proper and give them to him,, but y’all get to see the first sketches and scans :’’3
9 notes
·
View notes
Text
Listen. LISTEN
I will never shut up about Pool Boys EVER
But I have to say. This song? This one here?
Not only is it FIRE AS FUCK
But it also matched Mr Sunday HSR SO FUCKING WELL. Please GIVE MY GIRL BAND A CHANCE 💔💔💔
He's a trixie relegated to a lapdog :(((
Trapped inside a clever boy's laptop 💥💥
BETRAYED AND BURIED IN THE NIGHT 🙏
#sunday hsr#hsr#honkai star rail#sunday honkai star rail#PLEEEAASE SEE THE VISION#He feels like a CLIPPED EARED DOBERMAN#SITTIN THERE THINKING. HE'S A DACHSHUND#He feels like A BLEEDING WOMAN#WHOS HANDS ARE TIED WITH EVER LASTING TWINE#GOD SOMEONE PLEASE#Spotify#IDSS REALITY A WAY OF BEING SEEN#AND THE BACKGROUND VOCALS GOD I CANTTT
3 notes
·
View notes
Text








by the gooberest of goober bingas do i fucking LOVEEE THESE NEW IDSS god!!! they are so adorable I feel insane but also the symbolism with these goes hard af to and they really suit ishmael and gregs . (plus pablito plushie!!!)
Gregor and Ish both witnessing horrors (gregs the war, ish the great lake) that you can only really understand by witnessing it first hand like them. Just like a kid who is scared of a "monster under their bed" since there actually is a monster there, you have to see it to believe it
in their corrosion egos, Gregor is the monster. It represents how he feels about himself, a beast to be weary of.
In Ishmales corrosion ego, I argue that because you can see bits of Ishmaels hair while in Gregors you cannot see a single piece of him, this corrosion is like a sailor warning you of the depths. In her normal ego attack, she tries to warn you of the monsters that lurk by feigning ignorance. in her corrosion however its basically saying "welp you asked for this. i tried to warn you." as if you were persistent about there being a monster.
also something to note is they both have the same eye closed, perhaps representing them trying to feigin ignorance / reassure you to not worry about the monsters luring within
the monsters also representing them (yes ishy too - shes got crazy repressed anger)
Yes I'm normal about limbus. These EGOs unironically go so hard. I love how pjm jumps at the chance to thrown Gregor into a gown when the chance arrives.
#limbus company#not art#shocking i know#project moon#ishmael#lcb ishmael#lcb gregor#gregor samsa#gregor#i love these egos a normal amount#i reallyyy wanna draw christmas heathmael now sighhh
290 notes
·
View notes
Text
JFET差動増幅ブースターにトレブルコントロールを付ける
JFET差動増幅回路を使ったブースターにトレブルコントロールを付けた話です。

前回・前々回の回路でほぼブースターとしての基本機能はできていたのですが、それだけだとちょっと地味なのでトーンコントロール回路を追加しました。また、細かい改善も加えています。回路全体はこんな感じです。
以下、各ブロックを解説していきます。ちなみに「INPUT_B」のように「_B」で終わっているラベルがありますが、これは基板分割を行うために用意したもので、「_B」が付いていないラベルとJ5~J11で接続されています。
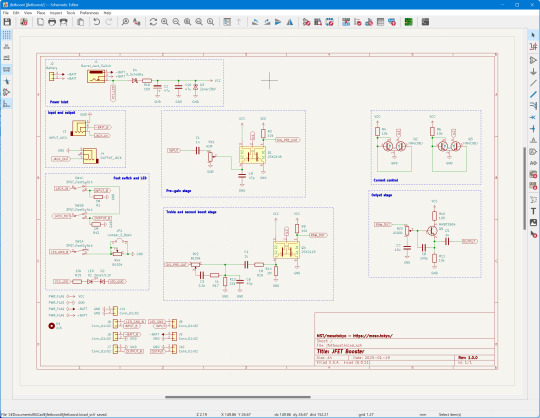
電源ブロック
本回路は消費電力が約4mAと少ないため(実測値)、9V電池駆動でも100時間程度は動かせそうです。そのため、電池駆動を想定した回路にしています。R16、C2、C10は電源ノイズ低減のためのローパスフィルタ(カットオフ周波数は約16.9Hz)です。R16に流れる電流が4mAの場合、ここで0.4Vの電圧降下が発生しますが、この程度であれば許容範囲だと判断しています。
D3のツェナーダイオードは瞬間的な大電圧(サージ電圧)からの保護目的で入れていますが(参考:過電圧保護に適したツェナーダイオード)、厳密な検証はしていないのでおまじないだと思ってください。
D4のショットキーダイオードは逆電圧保護用です。R16での電圧降下もあるため、可能な限り順方向の電圧低下が少ないものを使いたいところです。
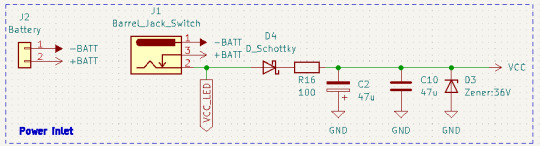
フットスイッチとLEDブロック
ON/OFF切り替えは一般的な3PDTフットスイッチを使用しています。RV4はLEDの明るさを調整するための半固定抵抗器で、D2は電源電圧が低下した場合にLEDを消灯させるためのツェナーダイオードです。電源電圧がD2のツェナー+約2Vを下回るとLEDが光らなくなります。たとえば5.1Vのツェナーダイオードを使用している場合、電源電圧がおよそ7.1Vより小さくなるとLEDが消灯します。
LEDへの電源供給は電源ブロックのD4より手前から分岐して行っています。これは、D4に流す電流を少しでも少なくして、D4での電圧降下を減らすためです。そのため、もし電源をプラスマイナス逆に接続するとLEDにもプラスマイナス逆方向に電圧がかかります。これによる破損を防ぐため、LEDには逆方向にも電圧を加えられる無極性LEDを使用します。ちなみに、LEDに直列に接続している抵抗は抵抗値が10kΩと大きいため、1/4Wの抵抗器を使用していれば理論上はだいたい50Vまでの電圧に耐えられるはずです。
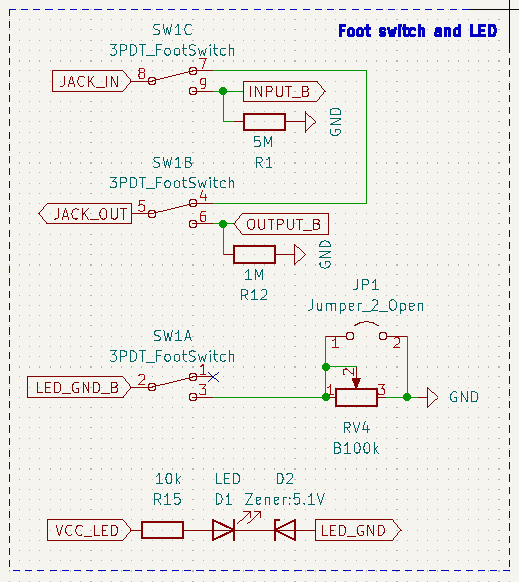
電流制限回路ブロック
カレントミラー回路を使った電流制限回路です(参考:END Japanの記事)。Ic1、Ic2に流れる電流を約0.8mAに制限します。
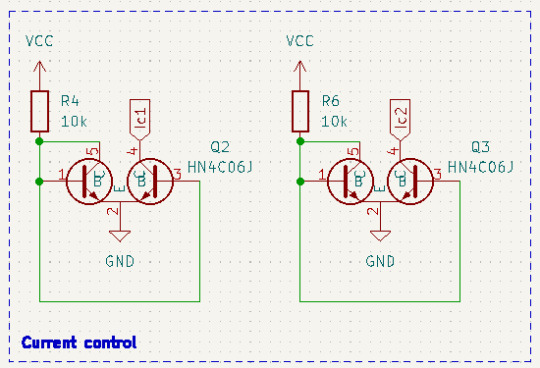
プリゲインブロック
デュアルJFETを使った差動増幅回路です(参考:nahitech.com)。前段に接続する機���によっては信号電圧に直流電圧成分が含まれている場合があるので、誤動作を防ぐためコンデンサ(C1)を入れて入力信号の直流成分をカットしたうえで増幅回路に入力しています。RV1はこのブロックでの増幅率を調整するための、いわゆるゲイン調整ポットになります。また、JFETのゲート・ドレイン間にはわずかに漏れ電流が流れ、これがRV1を経由してノイズ源となります。この漏れ電流をGND側に流して低減するためにC9を入れています。このブロックでの増幅率は約28dB(およそ25倍)です。
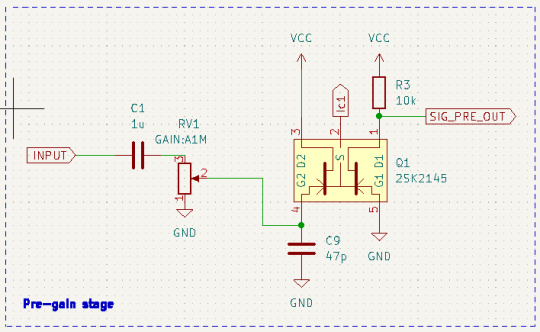
トーンコントロールと後段ゲインブロック
トーンコントロールには可変抵抗器とコンデンサを使ったシンプルな回路を使いました。RV2を反時計回りに回しきった状態では単純に信号の全帯域が6分の1に(20k/120k、約-16dB)減衰します。RV2を時計回りに回していくとC3およびR17にも信号が流れるようになり、この部分は高音域ほど抵抗値が少なくなるため、それによって高音域の減衰が少なくなって結果として相対的に高音域が増えます。また、C6は一定以上の高音域をカットするために入れています。その結果、周波数特性としてはおよそ6kHzあたりをピークとして最大12dBのブーストができるようになっています。
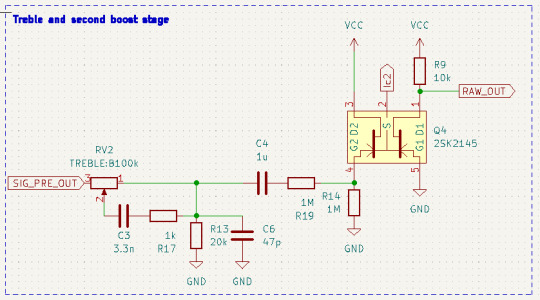
このトーンコントロール回路では全体のゲインを下げたうえで高音域だけを上げる動作になるため、トータルでの出力音量は下がります。それを補うために出力前に信号を再度差動増幅回路で増幅します。ここではすでに信号レベルがある程度大きくなっているので、再度コンデンサ(C4)を通して直流成分をカットしたうえでR14とR19で信号レベルを半分に減衰させています。
出力ブロック
RV3は出力レベル調整用(ボリューム)の可変抵抗器です。C7はRV3で交流成分のみを減衰させるために入れています。また、Q5周辺はトランジスタのエミッタフォロワを使ったバッファ回路になっており、最後にC5を通して再度直流成分をカットして出力しています。
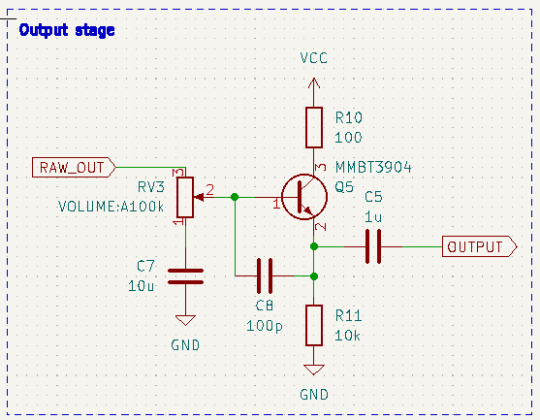
テスト実装
回路規模が小さいので、秋月電子のブレッドボード配線ユニバーサル基板(Dタイプ)上で実装できます。
また、デュアルトランジスタ(HN4C06J)とデュアルJFET(2SK2145)はDIP化基板を使って実装します。ちなみに秋月電子では2SK2145-BL/GR/Yとドレイン電流(IDSS)が異なる複数バージョンが販売されていますが、差動増幅回路で利用する場合はどれを使っても大きな違いは発生しないはずです。
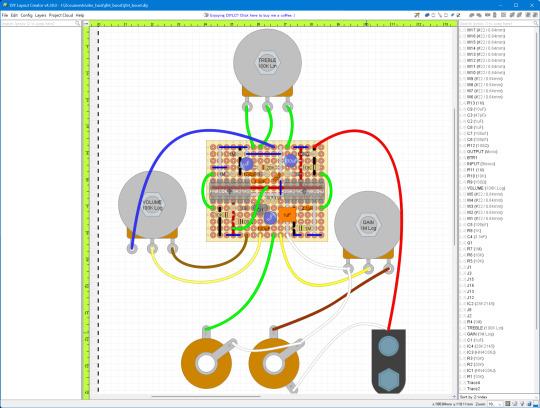
実際に実装したものがこちら。コンデンサはジャンク箱にあったあまりものを使っているのでバラバラです。

これをケースに収めるとこんな感じになります。ケーブルの配線が雑ですが、このようにいわゆる「Bサイズ」のケースに収まります。
回路の差し替えがしやすいようにコネクタを使って配線しているため奥行きがぎりぎりですが、ケーブルの長さを適切にして直接基板にケーブルをはんだ付けすればもう少し奇麗に収まるかと思います。

出音について
接続する楽器にもよりますが、ゲインを12時あたりに設定するとほぼクリーントーンになります。この場合でも最大でおよそ+18dB(8倍)の増幅率ができるので、ブースターとしては十分実用的でしょう。また、トレブルを上げていくとさらにそこから6kHzをピークに高域を最大で約+12dBブーストできます。そこからゲインを上げていくと歪んでいくのですが、信号レベルが増えるにつれて歪みが増えていくソフトクリッピングのため、ピッキングの強さで歪み方をコントロールできる感じです。
高音域は強めにブーストできますが、ローカットはしていないのでベースでも問題なく使えます。ギターで使う場合はトレブルを上げ目にして全体のボリュームを下げると相対的にローが減ってギター向けエフェクターっぽくなるかと思います。
回路のカスタマイズポイント
2つの差動増幅回路どちらも入力レベルが大きくなると歪みが発生するのですが、特に後段では歪みが大きくなりがちです。そのため、後段の差動増幅回路の前でどれだけ信号レベルを下げるか(つまりR14とR19の値)で歪み方が変わります。また、RV2、C3、R13の値の組み合わせでブーストする周波数帯やブースト量を調整できます。このあたりをカスタマイズすることで歪み方や出音を細かく調整できそうです。
4 notes
·
View notes
Note
I HATE THAT SHES SUCH A DUMB NAIVE BIMBO WITHOUT A SPINE but even though I absolutely despise her personality I'm so hooked on this series,like this is smth that happened to someone very dear to me so it hits home.anyways even though I feel like slapping the shit out of her,i LOVE this fic.this isn't meant as a insult or idss to your works,i genuinely love and enjoy reading it albeit I get a little frustrated sometimes
aw i get wym!! thank you veriii much for takin the time to read wht i put out <33 🥹
honestly when i started this series out , i did not intend to make her so spineless , my intention was to present ray of sunshine x solemn frat boy but like i think i lost da plot ?? nd i think we’re n too deep to rewrite her so i dunnooooo 😭
3 notes
·
View notes
Text

Tornado Italian prototype maiden flight on 5 Dec 1975 from Turin. The Aeronautica Militare received 100 Tornado IDSs (16 A-200s were subsequently converted to ECR configuration) As stop-gap for 10yrs Aeronautica Militare additionally operated 24 Tornado ADVs in air defence role.
@ron_eisele via X
4 notes
·
View notes
Text


Conceito
Tagline
Desdobramentos
Campanha de lançamento do IDSS
Agência DPZ
0 notes
Video
youtube
HOF015 Doc Holiday Hall Of Fame Recording Artist Doc Holiday has been inducted into the Independent Superstars ‘Recording Artist’ Hall of Fame. Frans Maritz (Wildhorse Entertainment) signed the official certificate placing Doc into this prestigious organization located in South Africa. Doc Holiday has the distinct honor of being inducted into the IDSS Hall of Fame for his life-time contribution to the Independent Music Industry as a ‘Recording Artist’. Doc is seen holding his award below in the animated Hall Of Fame, confirming his induction into the Hall Of Fame. “Being a recording artist and having the opportunity to do what I love best is such a blessing. I am honored to have worked with some of the best musicians on the west coast, east coast, and overseas. It’s all great! I greatly enjoy the creative process of recording music. A big thank you goes out to Frans Maritz and all those who support me and my music! I want to add that it is a joy knowing that music is part of my life, no matter where I am or what I’m doing thank you.” Doc Holiday
0 notes
Text
Community members receive 2024 MIT Excellence Awards, Collier Medal, and Staff Award for Distinction in Service
New Post has been published on https://thedigitalinsider.com/community-members-receive-2024-mit-excellence-awards-collier-medal-and-staff-award-for-distinction-in-service/
Community members receive 2024 MIT Excellence Awards, Collier Medal, and Staff Award for Distinction in Service


On Wednesday, June 5, 13 individuals and four teams were awarded MIT Excellence Awards — the highest awards for staff at the Institute. Colleagues holding signs, waving pompoms, and cheering gathered in Kresge Auditorium to show their support for the honorees. In addition to the Excellence Awards, staff members were honored with the Collier Medal, the Staff Award for Distinction in Service, and the Gordon Y. Billard Award.
The Collier Medal honors the memory of Officer Sean Collier, who gave his life protecting and serving MIT; it celebrates an individual or group whose actions demonstrate the importance of community. The Staff Award for Distinction in Service is presented to a staff member whose service results in a positive lasting impact on the Institute.
The Gordon Y. Billard Award is given annually to staff, faculty, or an MIT-affiliated individual(s) who has given “special service of outstanding merit performed for the Institute.” This year, for the first time, this award was presented at the MIT Excellence Awards and Collier Medal celebration.
The 2024 MIT Excellence Award recipients and their award categories are:
Innovative Solutions
Nanotechnology Material Core Staff, Koch Institute for Integrative Cancer Research, Office of the Vice President for Research (Margaret Bisher, Giovanni de Nola, David Mankus, and Dong Soo Yun)
Bringing Out the Best
Salvatore Ieni
James Kelsey
Lauren Pouchak
Serving Our Community
Megan Chester
Alessandra Davy-Falconi
David Randall
Days Weekend Team, Department of Custodial Services, Department of Facilities: Karen Melisa Betancourth, Ana Guerra Chavarria, Yeshi Khando, Joao Pacheco, and Kevin Salazar
IMES/HST Academic Office Team, Institute for Medical Engineering and Science, School of Engineering: Traci Anderson, Joseph R. Stein, and Laurie Ward
Team Leriche, Department of Custodial Services, Department of Facilities: Anthony Anzalone, David Solomon Carrasco, Larrenton Forrest, Michael Leriche, and Joe Vieira
Embracing Diversity, Equity, and Inclusion
Bhaskar Pant
Jessica Tam
Outstanding Contributor
Paul W. Barone
Marcia G. Davidson
Steven Kooi
Tianjiao Lei
Andrew H. Mack
2024 MIT Excellence Awards + Collier Medal Ceremony
The 2024 Collier Medal recipient was Benjamin B. Lewis, a graduate student in the Institute for Data, Systems and Society in the MIT Schwarzman College of Computing. Last spring, he founded the Cambridge branch of End Overdose, a nonprofit dedicated to reducing drug-related overdose deaths. Through his efforts, more than 600 members of the Greater Boston community, including many at MIT, have been trained to administer lifesaving treatment at critical moments.
This year’s recipient of the 2024 Staff Award for Distinction in Service was Diego F. Arango (Department of Custodial Services, Department of Facilities), daytime custodian in Building 46. He was nominated by no fewer than 36 staff, faculty, students, and researchers for creating a positive working environment and for offering “help whenever, wherever, and to whomever needs it.”
Three community members were honored with a 2024 Gordon Y. Billard Award
Deborah G. Douglas, senior director of collections and curator of science and technology, MIT Museum
Ronald Hasseltine, assistant provost for research administration, Office of the Vice President for Research
Richard K. Lester, vice provost for international activities and Japan Steel Industry Professor of Nuclear Science and Engineering, School of Engineering
Presenters included President Sally Kornbluth; MIT Chief of Police John DiFava and Deputy Chief Steven DeMarco; Vice President for Human Resources Ramona Allen; Executive Vice President and Treasurer Glen Shor; Provost Cynthia Barnhart; Lincoln Laboratory director Eric Evans; Chancellor Melissa Nobles; and Dean of the School of Engineering Anantha Chandrakasan.
Visit the MIT Human Resources website for more information about the award recipients, categories, and to view photos and video of the event.
#2024#Administration#Awards#honors and fellowships#Building#Cancer#Chancellor#Collections#college#Community#computing#data#diversity#drug#engineering#Environment#equity#Facilities#Faculty#human#human resources#IDSS#impact#inclusion#Industry#Institute for Medical Engineering and Science (IMES)#it#Japan#Koch Institute#life
0 notes
Text
0 notes
Text
MIT researchers develop an efficient way to train more reliable AI agents
New Post has been published on https://sunalei.org/news/mit-researchers-develop-an-efficient-way-to-train-more-reliable-ai-agents/
MIT researchers develop an efficient way to train more reliable AI agents

Fields ranging from robotics to medicine to political science are attempting to train AI systems to make meaningful decisions of all kinds. For example, using an AI system to intelligently control traffic in a congested city could help motorists reach their destinations faster, while improving safety or sustainability.
Unfortunately, teaching an AI system to make good decisions is no easy task.
Reinforcement learning models, which underlie these AI decision-making systems, still often fail when faced with even small variations in the tasks they are trained to perform. In the case of traffic, a model might struggle to control a set of intersections with different speed limits, numbers of lanes, or traffic patterns.
To boost the reliability of reinforcement learning models for complex tasks with variability, MIT researchers have introduced a more efficient algorithm for training them.
The algorithm strategically selects the best tasks for training an AI agent so it can effectively perform all tasks in a collection of related tasks. In the case of traffic signal control, each task could be one intersection in a task space that includes all intersections in the city.
By focusing on a smaller number of intersections that contribute the most to the algorithm’s overall effectiveness, this method maximizes performance while keeping the training cost low.
The researchers found that their technique was between five and 50 times more efficient than standard approaches on an array of simulated tasks. This gain in efficiency helps the algorithm learn a better solution in a faster manner, ultimately improving the performance of the AI agent.
“We were able to see incredible performance improvements, with a very simple algorithm, by thinking outside the box. An algorithm that is not very complicated stands a better chance of being adopted by the community because it is easier to implement and easier for others to understand,” says senior author Cathy Wu, the Thomas D. and Virginia W. Cabot Career Development Associate Professor in Civil and Environmental Engineering (CEE) and the Institute for Data, Systems, and Society (IDSS), and a member of the Laboratory for Information and Decision Systems (LIDS).
She is joined on the paper by lead author Jung-Hoon Cho, a CEE graduate student; Vindula Jayawardana, a graduate student in the Department of Electrical Engineering and Computer Science (EECS); and Sirui Li, an IDSS graduate student. The research will be presented at the Conference on Neural Information Processing Systems.
Finding a middle ground
To train an algorithm to control traffic lights at many intersections in a city, an engineer would typically choose between two main approaches. She can train one algorithm for each intersection independently, using only that intersection’s data, or train a larger algorithm using data from all intersections and then apply it to each one.
But each approach comes with its share of downsides. Training a separate algorithm for each task (such as a given intersection) is a time-consuming process that requires an enormous amount of data and computation, while training one algorithm for all tasks often leads to subpar performance.
Wu and her collaborators sought a sweet spot between these two approaches.
For their method, they choose a subset of tasks and train one algorithm for each task independently. Importantly, they strategically select individual tasks which are most likely to improve the algorithm’s overall performance on all tasks.
They leverage a common trick from the reinforcement learning field called zero-shot transfer learning, in which an already trained model is applied to a new task without being further trained. With transfer learning, the model often performs remarkably well on the new neighbor task.
“We know it would be ideal to train on all the tasks, but we wondered if we could get away with training on a subset of those tasks, apply the result to all the tasks, and still see a performance increase,” Wu says.
To identify which tasks they should select to maximize expected performance, the researchers developed an algorithm called Model-Based Transfer Learning (MBTL).
The MBTL algorithm has two pieces. For one, it models how well each algorithm would perform if it were trained independently on one task. Then it models how much each algorithm’s performance would degrade if it were transferred to each other task, a concept known as generalization performance.
Explicitly modeling generalization performance allows MBTL to estimate the value of training on a new task.
MBTL does this sequentially, choosing the task which leads to the highest performance gain first, then selecting additional tasks that provide the biggest subsequent marginal improvements to overall performance.
Since MBTL only focuses on the most promising tasks, it can dramatically improve the efficiency of the training process.
Reducing training costs
When the researchers tested this technique on simulated tasks, including controlling traffic signals, managing real-time speed advisories, and executing several classic control tasks, it was five to 50 times more efficient than other methods.
This means they could arrive at the same solution by training on far less data. For instance, with a 50x efficiency boost, the MBTL algorithm could train on just two tasks and achieve the same performance as a standard method which uses data from 100 tasks.
“From the perspective of the two main approaches, that means data from the other 98 tasks was not necessary or that training on all 100 tasks is confusing to the algorithm, so the performance ends up worse than ours,” Wu says.
With MBTL, adding even a small amount of additional training time could lead to much better performance.
In the future, the researchers plan to design MBTL algorithms that can extend to more complex problems, such as high-dimensional task spaces. They are also interested in applying their approach to real-world problems, especially in next-generation mobility systems.
The research is funded, in part, by a National Science Foundation CAREER Award, the Kwanjeong Educational Foundation PhD Scholarship Program, and an Amazon Robotics PhD Fellowship.
0 notes
Text


high_octane_RIAA PRE HI FI BASSO RUMORE CON FET MOS TRANSISTOR Questo è lo schema del pre phono ad alto numero di ottani.
Forse avrei dovuto dire prima che non rispetta affatto le attuali regole di "buona" progettazione di circuiti: usa bjt invece di jfet RIAA attiva invece di una passiva un feedback piuttosto negativo invece di eseguire un ciclo aperto Almeno utilizza un regolatore shunt come alimentatore😉
Può essere inserito in una scatola grande 10x8cm. Il punto di partenza per questo circuito single ended è un circuito a 3 transistor di HP Walker e risale agli anni '60. Ci sono alcune informazioni anche nel libro di Douglas Self sulla progettazione di piccoli segnali!
A margine, il regolatore shunt opamp con le sue eccellenti prestazioni è originariamente di Ovidiu (sinestesia) e il particolare schema di compensazione della frequenza di Edmond Stuart.
I punti indicati come SENSE sono per il telerilevamento utilizzato dal regolatore shunt, in modo che la tensione sia regolata direttamente al primo stadio! Il preamplificatore phono ad alto numero di ottani Benvenuti al preamplificatore phono ad alto numero di ottani! 25-10-2015 / Aggiornamento del 10-06-2017 Hannes Allmaier Questo sito ha lo scopo di aiutare a costruire questo preamplificatore phono. Il circuito è stato originariamente pubblicato in Linear Audio n. 6: http://linearaudio.net/article-detail/2159 e il thread del forum dedicato è disponibile all'indirizzo http://www.diyaudio.com/forums/analo…no-preamp.html dove tutti sono calorosamente invitati a contribuire! Schemi Lo schema del preamplificatore phono ad alto numero di ottani pubblicato in LinearAudio: È stato anche pubblicato qui: http://www.diyaudio.com/forums/analo…ml#post3631742 Le schede Si prega di notare che le schede regalate sono realizzate 1:1 dalla mia costruzione del prototipo finale. Pertanto, anche queste hanno qualche verruca, bug e tutto il resto, niente di serio, ma vorrai leggere le seguenti note di costruzione. In termini di transistor , è possibile l'uso di molti transistor bipolari a basso rumore, anche se ovviamente consiglio l'uso delle parti specificate originariamente nonostante siano difficili da ottenere. Se si utilizzano transistor diversi, controllare il pin-out e regolare di conseguenza l'orientamento del transistor, se necessario. Il 2SC2547 utilizzato segue il pinout Emettitore-Collettore-Base (ECB) se visto frontalmente . Si noti che il transistor CCS di uscita Q4/Q104 è una parte piuttosto speciale, vale a dire un MOSFET a modalità di svuotamento, che è normalmente acceso. Dalle caratteristiche elettriche è simile ai comuni JFET ma con un IDSS molto più elevato. Grazie alle sue proprietà speciali è difficile da sostituire e si consiglia l'uso del DN2540 originale. Questa parte è in piena produzione e può essere ottenuta negli Stati Uniti da Mouser e Digikey. Se avete domande, inviatemi un'e-mail e cercherò di aiutarvi. Spero che questo piccolo circuito vi piaccia tanto quanto a me! Buona costruzione! Si prega di notare la nota dell'editore di LinearAudio: questo documento fornisce note e informazioni per la costruzione del preamplificatore phono High-Octane come pubblicato in Linear Audio Vol 6 (settembre 2013). L'autore ha anche gentilmente fornito i file Gerber del PCB per uso personale e/o di studio. Si prega di contattare l'autore se si prevede di utilizzare questo progetto o parti di esso per uno scopo commerciale. Note di costruzione Le schede sono identiche a quella che ho utilizzato per il mio prototipo (versione v3e), che è stata migliorata durante i test. Quindi questa versione manca di alcune piccole modifiche per renderla la versione finale 'f'. Lo schema mostrato nell'articolo è corretto e considera tutte queste modifiche. Regolatore di tensione: NON inserire CP1 (danneggerà l'amplificatore operazionale) e NON mettere a terra la sua seconda gamba (che è collegata all'ingresso dell'amplificatore operazionale); lo schema mostra correttamente come dovrebbe essere collegato CP1 (o semplicemente ometterlo) Ingressi amplificatore: omettere C6/C106 (C6/C106 è un residuo del circuito originale in cui formava la capacità di carico della cartuccia, sostituita in questa versione dai condensatori di carico commutabili); Ingressi amplificatore: collegare R2/R102 con un ponticello;
1 note
·
View note
Text
Most Trusted Online Higher Education Company | Jaro Education
In the evolving landscape of online education, Jaro Education has emerged as a trusted leader in India, specializing in online higher education and executive programs. Founded in 2009 by Dr. Sanjay Salunkhe, Jaro Education stands out not only for its extensive program offerings but also for its commitment to quality, career advancement, and student satisfaction. With a focus on the needs of working professionals, Jaro has pioneered executive education programs in collaboration with some of the most prestigious institutions in India and abroad, making it one of India’s most respected EdTech companies.
A Strong Foundation in Quality and Trust
Jaro Education has built its reputation on the foundations of trust, quality, and industry relevance. As an EdTech company, Jaro was among the first to introduce executive and online education to the Indian market, setting new standards for remote learning. This commitment to quality and transparency has been recognized by prestigious awards, including the Leading EdTech Company of the Year by Times Business Award 2024 and India’s Most Trusted Online Higher Education accolade from Outlook Business Icon 2023. These awards underscore Jaro’s mission to make high-quality education accessible, effective, and rewarding.
Collaboration with Top Universities
One of Jaro Education’s core strengths is its collaboration with top-ranked universities and institutes, both in India and internationally. Through partnerships with institutions like the Massachusetts Institute of Technology’s Institute for Data, Systems, and Society (MIT IDSS), The Wharton Business School’s Wharton Interactive, and top Indian institutions such as IIM Ahmedabad, IIM Kozhikode, and IIT Madras, Jaro brings cutting-edge courses to learners. These partnerships ensure that students have access to updated curricula, industry-relevant skills, and esteemed faculty, making Jaro’s programs credible and impactful.
Programs Designed for Career Advancement
Jaro Education offers a diverse range of over 150 programs in fields like management, technology, and techno-functional studies, all geared toward career growth. By providing flexible, online courses, Jaro caters to professionals across various career stages, from entry-level roles to C-suite executives. Many of these programs focus on areas with high industry demand, such as data analytics, digital marketing, finance, and leadership development. With 23+ learning centers across India, Singapore, and the USA, Jaro Education aims to transform careers by offering programs that provide real-world value.
Empowering Professionals through Innovation and Support
Jaro’s approach to online education includes a strong emphasis on innovation and support, creating an engaging learning experience that meets students’ needs. The company’s support infrastructure ensures that learners have access to resources, mentorship, and guidance, whether they’re new to online learning or seasoned professionals looking to upgrade their skills. Jaro’s use of technology allows for seamless content delivery, regular assessments, and networking opportunities, creating a supportive and effective educational environment.
A Vision for the Future of Education
As Jaro Education continues to grow, its vision remains focused on transforming professional education by blending traditional academic rigor with modern, technology-driven solutions. By nurturing an ecosystem where quality, accessibility, and industry alignment come together, Jaro Education empowers learners to thrive in today’s competitive job market. With its established credibility and ongoing commitment to student success, Jaro Education is well-positioned to shape the future of online higher education in India and beyond.
1 note
·
View note
Text
vimeo
2024.10.02 NET CDE Training - Deployment After Dark
Resources and products mentioned:
In depth presentations by Ed Kraus which go into more depth: Power to the People! Planning for Emergency Electricity Part 1 - How to connect things together, how to use power safely, and how to calculate the power and energy you need to function Part 2 - How we can generate and store power for home and for our NET team, so we can keep going more than one or two operational periods
Dark Adaptation of the Human Eye and the Value of Red Flashlights
Hourly weather forecast
IDSS Forecast Points
Clackamas Town Center AAR
Hurricane Helene amateur radio repeater broadcast
Products mentioned and suggested by NETs (not endorsed by PBEM):
3 battery replacement cartridge
Swift RL Headlamp
DanForce USB Rechargeable LED Headlamp
Olight Arkfeld Adjustable Right-angle Pocket Flashlight
Nebo Slide King 4K Work Light & Flashlight
Nebo Slim+ 1200 Pocket Light, Laser, and Power Bank
0 notes
Text
This is a strategic decision that may improve the quality, efficiency, and success of your engineering projects. It is a cost-saving tactic to outsource Civil 3D expertise. By partnering up with a reputable company such as IDSS Global gives you access to a plethora of knowledge, state-of-the-art equipment, and a dedication to quality that guarantees the best possible results for your projects. This benefit can be the difference between an expensive and successful project in the highly competitive profession of civil engineering.
0 notes