#HTTP headers case sensitive
Explore tagged Tumblr posts
Text
Why Regularly Tracking Google SERPs is Essential for Optimizing Your SEO Strategy
Within the extraordinarily digital era, standing out in seeking engine results is a primary purpose for most websites. An essential strategy for keeping and enhancing your online visibility is monitoring your search engine scores. For companies trying to beautify their virtual presence, tracking Google SERPs (Search Engine outcomes Pages) is important. Song Google engines like Google frequently to keep up with moving search algorithms and ensure that your internet site remains optimized and applicable.
Why is tracking Google SERPs like Google and Yahoo important?
Knowledge of where your website stands in the search ratings is essential to any successful search engine optimization strategy. Without often checking your ratings, you cannot determine the effect of your SEO efforts. By preserving an eye fixed on these ratings, you may see how well your content is performing and discover development opportunities. When you use Google search engines like Google and Yahoo, you can tune your website’s position through the years and adjust your approach for that reason.
Serps like Google are constantly evolving their algorithms, frequently making changes that affect how websites are ranked. These updates won't always be transparent, which is why tracking your rankings is critical. As an example, if you notice a surprising drop in your rankings, it could be due to a Google set of rules replaced. This drop would possibly signal that changes are wanted on your SEO method, which include revisiting your keyword approach, enhancing content high-quality, or resolving technical seo problems like damaged links or gradual web page loading speeds.
Another cause to track Google serps is to live ahead of your opposition. Tracking your competition scores allows you to pick out their strengths and weaknesses and modify your techniques. If a competitor abruptly ranks better than you, it might be time to evaluate their SEO techniques and spot what they're doing differently. This approach now not best enables you to hold or improve your scores but additionally offers you precious insights into emerging tendencies for your industry.
The way to tune Google search engines like google effectively
Tracking Google engines like Google can seem daunting in the beginning, in particular for agencies that target a wide array of keywords. However, gear makes this manner less complicated. A number of the most popular consist of Ahrefs, SEMrush, and Google Analytics. Those structures let you input your target key phrases and display your website’s rankings throughout diverse seek consequences pages.
Another excellent device to use is the Google SERP monitoring device. This device presents complete records of your ratings, permitting you to song keyword performance, discover adjustments in seek scores, and see potential troubles like keyword cannibalization (wherein multiple pages to your website online compete for the equal keyword). With the use of the Google SERP tracking tool, you could gain valuable insights that can help refine your search engine optimization method.
The advantages of SERP monitoring
There are numerous advantages to always tracking your search rankings. Right here are only some:
Information-pushed search engine optimization adjustments: while you regularly music Google search engines, you're higher ready to make knowledgeable, information-driven choices. Whether or not tweaking the key phrases you are targeting, updating your meta descriptions, or editing content material, SERP monitoring presents you with the insights necessary for making strategic improvements.
Competitor analysis: By tracking your competitors' ratings, you benefit from insights into what strategies are operating for them. This know-how can manual your approach to content material advent, backlink construction, and on-web page optimization, assisting you close any performance gaps and overtaking competitors in the scores.
Keyword Optimization: tracking your scores for unique key phrases lets you see which are acting nicely and which need improvement. You may find out that a few high-acting key phrases are riding a sizeable portion of your traffic, prompting you to consciousness on expanding associated content material. Alternatively, tracking allows you to discover low-acting keywords and revise or decorate the content material that goals them.
Adapt to algorithm Updates: Google often rolls out algorithm updates, that could have a huge impact on seek scores. When you frequently music Google engines like Google, you may speedy become aware of any ranking shifts following a replacement. This allows you to react swiftly and mitigate any bad results in your traffic or visibility.
Spot developments and possibilities: monitoring your search engines like Google over the years lets you identify long-term trends and perceive new opportunities. For example, if a specific content piece constantly ranks properly, you could capitalize on this with the aid of growing extra content around that subject matter or expanding it to cover associated subjects.
conclusion
Make SERP tracking a habit
SERP tracking must be a key element of any digital marketing strategy. Regularly tracking your seek rankings ensures that you stay on top of your SEO recreation, allowing you to conform to changes in seek algorithms, keep a competitive facet, and optimize your content material for first-class viable overall performance.
With the aid of incorporating tools including the Google SERP tracking tool into your method, you can gather treasured facts to assist refine your SEO technique and make informed decisions to enhance your internet site’s visibility and performance. While you track Google serps often, you are taking a proactive approach to preserving and improving your online presence, ensuring long-term fulfillment in the ever-changing global of virtual marketing.
For similarly studying advanced search engine optimization strategies and the blessings of SERP monitoring, check out this informative article from article from Search Engine Journal.
#Track Google SERPs#Serper for Google search via API#Search Query Here#High Quality Backlinks#How to see headers in developer tools#What risk is mitigated by HTTP headers#HTTP headers case sensitive
0 notes
Text
Hidden search operators cheatsheet
Post Header
Published: 2018-07-22 12:57:37 UTCTags:
2018
Help & Info for Users
Now that we've finished rolling out the new search and filtering features, it's time to give our previous series on hidden search operators and neat tricks an update as well.
Works
As before, you can use all of these suggestions in the main search box (in the site header), the "Any field" box in the work search, or the "Search within results" field in the filters. Keep in mind that this input is case-sensitive and the space after the colon is non-optional. Just copy-paste what you need, mix and match as you like, and bookmark the result in your browser for quick access to fanworks perfectly tailored to your tastes!
Work Properties
expected_number_of_chapters: 1 for single-chapter works only
-expected_number_of_chapters: 1 for multi-chapter works only
creators: username for works by a particular creator
-creators: username to filter out all works by a particular creator
restricted: true for restricted works (if you're logged in to access them)
restricted: false for public works
work_skin_id: 277 for works using a specific skin (Homestuck, in this case)
imported_from_url: xyz for works imported from a specific site or domain
xyz cannot start with http://, so use an asterisk instead (e.g. *username.dreamwidth.org)
xyz may contain periods and slashes and asterisks, so *username.dreamwidth.org/1234.html and *username* would both be fine
notes: string or endnotes: string for works with notes or end notes containing a particular string
string can be any single word or a phrase enclosed in quotation marks
notes: "ball game" notes: peanuts will find works whose notes contain the words "ball" and "game" together and in that order, as well as the word "peanuts"
summary: string for works with a particular word or phrase (in quotation marks) in the summary
backdate: true for works that have been backdated
backdate: false for works that have not been backdated
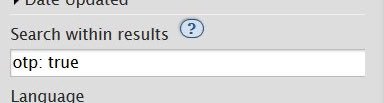
otp: true for works tagged with only one relationship (experimental!)
can be used by itself or in combination with a specific relationship tag (e.g. chosen from the filtering options)
will exclude all A/B works where A/B might only be a side pairing, but also all A/B works with other side pairings
will include works with multiple relationship tags if they're all synned to the same canonical tag
otp: false for works tagged with multiple relationships (experimental!)
-relationship_ids: * for works with no relationship tags at all
collection_ids: * for works that are part of a collection
series.title: string for works in a series whose title contains a particular word or phrase (in quotation marks)
series.title: * for works that are part of a series
-series.title: * for works that aren't in a series
Sorting
By work properties
sort:words to sort works by word count, longest works first
sort:>words to reverse the sorting order and show shortest works first
sort:author to sort works by the creators' pseuds, A-Z
sort:<author to reverse the sorting order and show pseuds starting with Z first
sort:title to sort works by title, from A to Z
sort:<title to reverse the sorting order and show titles starting with Z first
By date
sort:posted to sort from newest to oldest, going by the day they were posted to the Archive
sort:>posted to reverse that order and show oldest first, going by the day they were posted to the Archive
sort:updated to sort from newest to oldest, going by the day they were originally published (if backdated) or had a chapter added (this is the default sort)
sort:>updated to show oldest works first, going by the day they were originally published (if backdated) or had a chapter added
By feedback metrics
sort:kudos to sort works by amount of kudos, most kudos first
sort:>kudos to reverse the sorting order and show least kudos first
sort:comments to sort works by number of comments, most comments first
sort:>comments to reverse the sorting order and show fewest comments first
sort:bookmarks to sort works by number of bookmarks, most bookmarks first
sort:>bookmarks to reverse the sorting order and show fewest bookmarks first
sort:hits to sort works by number of hits, most hits first
sort:>hits to reverse the sorting order and show fewest hits first
Within a range
You can also specify a range of works with some of these properties, namely words, hits, kudos, comments, and bookmarks, with the following options:
words:1000 (works with exactly 1000 words)
words>1000 (works with more than 1000 words)
words<1000 (works with less than 1000 words)
words:1000-5000 (works between 1000 and 5000 words)
Text Searches
Due to the way Elasticsearch 6 handles query strings, putting several words or phrases into the search box will result in a list of works with all of those words in one field (such as the notes, or the title). For example, searching for BTS love will bring up a work with the phrase "I love BTS!" in the notes, but will not find works with the BTS fandom tag and the word "love" in the title.
To make sure that your input is matched against all possible work properties, separate your search terms by an AND, such as BTS AND love or BTS AND puppies AND "slow burn". This will search for any combination of those words in all fields.
However, the search operators above can just be added on, separated by spaces, resulting in a query like Discworld AND library expected_number_of_chapters: 1 sort:>posted to find all single-chapter works with the words "Discworld" and "library" anywhere in the title, tags, notes, or creator's username, sorted to show oldest first.
Bookmarks
We have made some changes to the way bookmarks are stored and displayed, enabling us to differentiate between properties of the bookmarked work and properties of the bookmark itself more easily. As a result, bookmarks now allow for more finegrained searches, but require a little more input to find exactly the bookmarks you're looking for.
Bookmarked Work Properties
In addition to any word or phrase that will be matched against the title, summary, notes, and tags of a work, you can also use the following in the "Search within results" field (for filtering) or the "Any field on work" field (for bookmark searches):
restricted: true for bookmarks of restricted works only
restricted: false for bookmarks of public works only
complete: true for bookmarks of complete works
complete: false for bookmarks of works in progress
bookmarkable_type: ExternalWork for bookmarks of external works
bookmarkable_type: Series for bookmarks of series
Bookmark Properties
Likewise, you can put any word or phrase in the "Search bookmarker's tags and notes" field (for filtering) or the "Any field on bookmark" field (for bookmark searches). You also have the following options:
private: true to filter for your private bookmarks only (if you're logged in to access them)
private: false to filter for public bookmarks only
tag: * for bookmarks with tags added by the bookmarker
Searching and filtering by language
You can use language codes to limit your searches to works or bookmarks in a particular language (or several languages in one search), or exclude items in a particular language. You can use this list of language codes for reference and replace abbreviation with the code for the language you want.
All these options will work in the main search box (in the site header), the "Any field" box in the work search, and the "Search within results" field in the filters, as well as the "Any field on work" field in the bookmark search and the "Search within results" field in the bookmark filters.
language_id: abbreviation for items in that language
language_id: abbreviation OR language_id: abbreviation for items in either of those languages
-language_id: abbreviation to filter out all items in that language
I was today years old when I learned that when you type “otp: true” in AO3 search results it filters out fics with additional ships, leaving only the fics where your otp is the main ship
211K notes
·
View notes
Text
UI/UX Landing Page Essentials: What Every Designer Should Know
In the digital age, a landing page often serves as the first point of contact between a business and its potential customers. As such, it plays a crucial role in converting visitors into leads or customers. For UI/UX designers, creating an effective landing page requires a delicate balance of aesthetics, functionality, and persuasive elements. This blog post will explore the essential components and best practices that every designer should know when crafting a high-converting landing page.
1. Clear and Compelling Value Proposition
The cornerstone of any successful landing page is a clear and compelling value proposition. This should be prominently displayed, typically in the hero section of the page. Your value proposition should succinctly communicate what your product or service offers and why it's unique or better than alternatives. Use concise, benefit-driven language that resonates with your target audience's needs and pain points.
2. Intuitive Navigation and Structure
While landing pages are often designed to focus on a single action, they should still provide intuitive navigation for users who want more information. Consider using a sticky header with essential navigation items or anchor links to different sections of the page. The overall structure should guide the user's eye naturally through the content, leading them towards the desired action.
3. Engaging and Relevant Visuals
High-quality, relevant visuals are essential for capturing and maintaining user attention. Use images or videos that showcase your product or service in action, or that evoke the emotions you want associated with your brand. Ensure that all visual elements are optimized for fast loading times, as page speed is crucial for both user experience and search engine optimization.
4. Persuasive and Scannable Copy
Your landing page copy should be concise, persuasive, and easy to scan. Use headlines, subheadings, and bullet points to break up text and highlight key information. Focus on the benefits of your offering rather than just listing features. Incorporate social proof elements such as testimonials, case studies, or client logos to build trust and credibility.
5. Clear and Prominent Call-to-Action (CTA)
The call-to-action is arguably the most critical element of your landing page. It should be visually distinct, using contrasting colors or design elements to stand out. The CTA text should be action-oriented and specific, such as "Start Your Free Trial" or "Get Your Custom Quote." Consider using multiple CTAs throughout the page, especially for longer landing pages, to capture users at different stages of interest.
6. Responsive Design
With users accessing websites from a variety of devices, responsive design is no longer optional. Ensure your landing page looks great and functions well on desktops, tablets, and smartphones. This may involve adjusting layouts, font sizes, and interactive elements for different screen sizes. Always test your page across multiple devices and browsers to ensure a consistent experience.
7. Fast Loading Speed
Page loading speed is crucial for both user experience and search engine optimization. Optimize images, minify CSS and JavaScript, and leverage browser caching to improve loading times. Consider using a content delivery network (CDN) to serve assets faster to users in different geographic locations.
8. Trust Signals and Security Indicators
Building trust is essential for converting visitors into leads or customers. Incorporate trust signals such as security badges, privacy policy links, and guarantees. If you're collecting sensitive information, ensure that your forms use HTTPS and display security indicators. Showcase any relevant certifications, awards, or industry associations to further establish credibility.
9. A/B Testing Capability
Great landing pages are often the result of continuous optimization. Implement A/B testing capabilities to compare different versions of your page and identify which elements perform best. This might involve testing different headlines, CTA colors, form layouts, or overall page designs. Use the insights gained from these tests to refine and improve your landing page over time.
10. Minimal Distractions
The primary goal of a landing page is to guide users towards a specific action. Minimize distractions that could lead users away from this goal. This might mean removing unnecessary navigation links, limiting the number of form fields, or focusing on a single offer rather than presenting multiple options.
11. Compelling Forms
If your landing page includes a form, design it for maximum conversion. Keep the number of fields to a minimum, asking only for essential information. Use clear labels and placeholder text to guide users. Consider using multi-step forms for longer surveys or applications, as they can be less intimidating and increase completion rates.
12. Mobile-First Approach
With mobile traffic often surpassing desktop, consider adopting a mobile-first design approach. This means designing for mobile devices first and then scaling up to larger screens. This approach ensures that the most critical elements of your page are optimized for the constraints of mobile viewing.
Conclusion
Creating an effective landing page is both an art and a science. It requires a deep understanding of user behavior, design principles, and conversion optimization techniques. By focusing on these essential elements – from a clear value proposition and compelling visuals to responsive design and continuous testing – UI/UX designers can create landing pages that not only look great but also drive real business results.
Remember that the most successful landing pages are those that evolve based on user feedback and data-driven insights. Stay curious, keep testing, and always put the user's needs at the forefront of your design decisions. With these principles in mind, you'll be well-equipped to create landing pages that engage, persuade, and convert.
My Fiver link for : Figma Landing Page Design Service
0 notes
Text
can traffic for a user of vpn be made
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can traffic for a user of vpn be made
VPN traffic analysis
VPN traffic analysis refers to the process of examining the data transmitted over a Virtual Private Network (VPN) for various purposes such as security monitoring, network optimization, and troubleshooting. While VPNs are commonly used to encrypt internet traffic and protect users' privacy, it's essential for organizations and individuals to understand how their VPN traffic is being analyzed and what implications it may have.
One primary reason for VPN traffic analysis is security monitoring. By analyzing VPN traffic, network administrators can detect and prevent potential security threats such as malware, phishing attempts, and unauthorized access to sensitive data. They can identify suspicious patterns or anomalies in the traffic that may indicate a security breach or attempted intrusion.
Another use case for VPN traffic analysis is network optimization. By monitoring VPN traffic, organizations can identify bandwidth bottlenecks, optimize network performance, and ensure smooth operation of critical applications. Analyzing VPN traffic helps in identifying and resolving issues that may degrade network performance, such as excessive bandwidth usage or network congestion.
Moreover, VPN traffic analysis plays a crucial role in compliance and regulatory requirements. Many industries have strict regulations regarding data privacy and security, such as the Health Insurance Portability and Accountability Act (HIPAA) in healthcare or the General Data Protection Regulation (GDPR) in the European Union. By analyzing VPN traffic, organizations can ensure compliance with these regulations by monitoring the flow of sensitive data and preventing unauthorized access.
In conclusion, VPN traffic analysis is essential for maintaining security, optimizing network performance, and ensuring compliance with regulatory requirements. By understanding how VPN traffic is analyzed and implementing appropriate monitoring tools and practices, organizations can effectively protect their networks and sensitive data from various threats.
VPN traffic obfuscation
VPN traffic obfuscation is a crucial technique employed to enhance online privacy and security by disguising VPN traffic to evade detection and censorship. In regions where internet access is restricted or monitored, VPN users often face challenges as authorities employ advanced methods to identify and block VPN traffic. VPN traffic obfuscation works by making VPN traffic appear as regular HTTPS traffic, making it difficult for firewalls and deep packet inspection (DPI) systems to recognize and block it.
One common method of VPN traffic obfuscation is using protocols like OpenVPN with Transport Layer Security (TLS) encryption. By encapsulating VPN traffic within TLS, it mimics standard HTTPS traffic, making it harder to distinguish from regular web traffic. Additionally, obfuscation techniques may involve disguising packet headers and payloads, making VPN traffic less identifiable.
Another approach to VPN traffic obfuscation is leveraging specialized obfuscation protocols like Obfsproxy or Shadowsocks. These protocols employ techniques such as packet obfuscation, camouflage, and traffic shaping to obscure VPN traffic patterns effectively. By masking the true nature of VPN traffic, users can bypass censorship and access restricted content without detection.
VPN providers continuously innovate and update their obfuscation techniques to stay ahead of censorship measures. However, it's essential for users to choose reputable VPN services that prioritize security and privacy. Additionally, while VPN traffic obfuscation can help circumvent censorship, it's not foolproof, and users should remain vigilant about their online activities to ensure their privacy and security are maintained. Overall, VPN traffic obfuscation plays a vital role in safeguarding internet freedom and ensuring unfettered access to information globally.
VPN traffic interception
VPN traffic interception refers to the unauthorized access and monitoring of data transmitted through a Virtual Private Network (VPN) connection. VPNs are commonly used to enhance online privacy and security by creating an encrypted tunnel between the user's device and the VPN server. This encryption helps protect sensitive information such as passwords, browsing history, and personal data from being intercepted by cybercriminals, hackers, or government surveillance.
However, despite the secure nature of VPNs, there are instances where VPN traffic interception can occur. Cyber attackers may deploy sophisticated techniques to intercept and decrypt VPN traffic, gaining access to confidential information. One method used is known as a "man-in-the-middle attack," where the attacker intercepts communication between the user and the VPN server, allowing them to eavesdrop on the data being transmitted.
Governments and internet service providers (ISPs) in some countries may also intercept VPN traffic for surveillance or censorship purposes. This poses a significant threat to user privacy and freedom of expression online. Users must be cautious when choosing a VPN provider and opt for reputable services that offer strong encryption protocols and do not keep logs of user activity.
To mitigate the risks of VPN traffic interception, users should regularly update their VPN software, choose complex encryption protocols, and be wary of using free VPN services that may compromise their data. Additionally, using additional security measures such as two-factor authentication and antivirus software can further enhance online protection against potential interception threats. By staying informed and taking proactive steps to secure their VPN connection, users can safeguard their online activities and maintain their privacy in the digital world.
VPN traffic encryption
VPN traffic encryption is a crucial aspect of ensuring online privacy and security. When you use a Virtual Private Network (VPN), your internet traffic is encrypted to protect it from being intercepted by hackers, ISPs, or government surveillance agencies.
Encryption technology scrambles the data you send over the internet into a coded format that can only be deciphered by authorized parties with the encryption key. This means that even if your data is intercepted, it will appear as unintelligible gibberish to anyone without the encryption key.
There are different types of encryption protocols used by VPN services, such as OpenVPN, L2TP/IPsec, and IKEv2. These protocols employ various encryption algorithms like AES (Advanced Encryption Standard) with 256-bit keys, which is considered virtually impenetrable by current computing technology.
By encrypting your VPN traffic, you can protect sensitive information such as your login credentials, financial transactions, and personal communications from prying eyes. This is particularly important when using public Wi-Fi networks, which are known to be vulnerable to cyber attacks.
In summary, VPN traffic encryption is a fundamental feature that ensures your online activities remain private and secure. By choosing a reputable VPN service with robust encryption protocols, you can browse the internet with peace of mind, knowing that your data is shielded from unauthorized access.
VPN traffic visibility
Title: Understanding VPN Traffic Visibility: What You Need to Know
In today's digital landscape, privacy and security have become paramount concerns for internet users. Virtual Private Networks (VPNs) have emerged as a popular solution for safeguarding online activities. However, while VPNs offer encryption and anonymity, it's crucial to understand the concept of VPN traffic visibility.
VPN traffic visibility refers to the extent to which an internet service provider (ISP), network administrator, or third party can observe the data flowing through a VPN connection. Despite the encryption provided by VPNs, there are still factors that can affect the visibility of traffic:
VPN Protocols: Different VPN protocols offer varying levels of security and visibility. For instance, while older protocols like PPTP may offer faster speeds, they are more susceptible to interception. On the other hand, modern protocols like OpenVPN and IKEv2/IPsec prioritize security, making it harder for outsiders to view VPN traffic.
Logging Policies: Some VPN providers may log user activity, including websites visited and data transmitted. While these logs are often used for troubleshooting and improving service quality, they also pose a risk to user privacy if accessed by unauthorized parties. Opting for VPN providers with strict no-logs policies can mitigate this risk.
DNS Leaks: Domain Name System (DNS) leaks occur when a VPN fails to properly route DNS queries through the encrypted tunnel, potentially exposing users' browsing habits to ISPs or other intermediaries. Utilizing VPNs with built-in DNS leak protection can prevent such vulnerabilities.
Traffic Analysis: Sophisticated adversaries may employ traffic analysis techniques to infer patterns and behaviors from encrypted VPN traffic. Techniques like packet timing and size analysis can reveal information about the source and destination of data, compromising user anonymity.
Ultimately, while VPNs offer a layer of protection against surveillance and cyber threats, users should remain vigilant about factors that could compromise their privacy. By selecting reputable VPN providers, employing robust encryption protocols, and staying informed about potential vulnerabilities, individuals can maximize their online security and maintain greater control over their digital footprint.
0 notes
Text
Common Web Security Threats And Best Practices For Securing Websites

Web Security: Discuss common web security threats and best practices for securing websites and user data.
In the interconnected world of the internet, web security is of paramount importance. Websites and online platforms hold vast amounts of sensitive user data, making them prime targets for malicious actors. In this article, we’ll discuss common web security threats and explore best practices for securing websites and user data.
Understanding Common Web Security Threats
1. SQL Injection (SQLi)
SQL injection is a technique where malicious users inject SQL code into input fields on a website. If the web application is not properly secured, this can lead to unauthorized access to the website’s database, allowing attackers to steal or manipulate data.
2. Cross-Site Scripting (XSS)
XSS attacks occur when an attacker injects malicious scripts into web pages viewed by other users. This can lead to the theft of cookies or session data, compromising user accounts, and even redirecting users to malicious websites.
3. Cross-Site Request Forgery (CSRF)
CSRF attacks trick users into unknowingly performing actions on websites they are authenticated on. By exploiting user trust, attackers can perform malicious actions on a victim’s behalf.
4. Brute Force Attacks
Brute force attacks involve attempting to guess usernames and passwords to gain unauthorized access. These attacks are common against login forms and can be mitigated by implementing account lockout mechanisms and CAPTCHAs.
5. DDoS Attacks
Distributed Denial of Service (DDoS) attacks flood a website’s server with a massive volume of requests, rendering the site inaccessible. This can lead to service disruption and financial losses.
Best Practices for Securing Websites
1. Regular Software Updates
Keep all software, including the operating system, web server, and content management systems, up to date. Vulnerabilities in outdated software can be exploited by attackers.
2. Input Validation and Sanitization
Implement strict input validation and data sanitization to prevent SQL injection and XSS attacks. Always assume that user input is untrustworthy and validate it accordingly.
3. Secure Authentication
Use strong and secure authentication mechanisms, including multi-factor authentication (MFA) where possible. Store passwords securely using modern encryption methods like bcrypt.
4. HTTPS Encryption
Implement HTTPS using SSL/TLS encryption to secure data in transit. This ensures that data transferred between the user and the server remains confidential.
5. Web Application Firewall (WAF)
Use a Web Application Firewall to filter and monitor traffic between a web application and the internet. WAFs can help block suspicious traffic and provide additional layers of security.
6. Security Headers
Implement security headers in your web server or web application to provide additional layers of security. This includes headers like Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and X-Content-Type-Options.
7. Session Management
Implement robust session management techniques, including secure session tokens, session timeouts, and secure logout procedures to prevent CSRF attacks.
8. DDoS Mitigation
Employ DDoS mitigation solutions to protect your website from large-scale attacks. These services can help filter out malicious traffic and keep your website operational during attacks.
9. Regular Backups
Frequently back up your website and databases to ensure you can recover data in case of an attack. Store backups in secure locations.
10. Security Training
Ensure that your development and IT teams are well-trained in web security best practices. Security training and awareness can help prevent common vulnerabilities.
Conclusion
Web security is an ongoing process that requires constant vigilance. As the digital landscape evolves, so do threats to web security. By understanding common web security threats and implementing best practices for securing websites and user data, you can build a robust defense against malicious actors. Protecting your digital fortress is not just a matter of protecting your business interests; it’s also a commitment to safeguarding the privacy and trust of your users.
Source:
#india#kushitworld#saharanpur#itcompany#digital marketing#seo#seo services#webdevelopment#websitedesigning
0 notes
Text
best Ways for Web Scraping
best Ways for Web Scraping
You need to make your scraper undetectable to be able to extract data from a webpage, and the main types of techniques for that are imitating a real browser and simulating human behavior. For example, a normal user wouldn't make 100 requests to a website in one minute.To get more news about website proxy, you can visit pyproxy.com official website.
1. Set Real Request Headers As we mentioned, your scraper activity should look as similar as possible to a regular user browsing the target website. Web browsers usually send a lot of information that HTTP clients or libraries don't. 2. Use Proxies If your scraper makes too many requests from an IP address, websites can block that IP. In that case, you can use a proxy server with a different IP. It'll act as an intermediary between your web scraping script and the website host.
There are many types of proxies. Using a free proxy, you can start testing how to integrate proxies with your scraper or crawler. You can find one in the Free Proxy List. 3. Use Premium Proxies for Web Scraping High-speed and reliable proxies with residential IPs sometimes are referred to as premium proxies. For production crawlers and scrapers, it's common to use these types of proxies.
When selecting a proxy service, it's important to check that it works great for web scraping. If you pay for a high-speed, private proxy that gets its only IP blocked by your target website, you might have just drained your money down the toilet. 4. Use Headless Browsers To avoid being blocked when web scraping, you want your interactions with the target website to look like regular users visiting the URLs. One of the best ways to achieve that is to use a headless web browser. They are real web browsers that work without a graphical user interface. Most popular web browsers like Google Chrome and Firefox support headless mode. However, even if you use an official browser in headless mode, you need to make its behavior look real. It's common to add some special request headers to achieve that, like a User-Agent. 5. Outsmart Honeypot Traps Some websites will set up honeypot traps. These are mechanisms designed to attract bots while being unnoticed by real users. They can confuse crawlers and scrapers by making them work with fake data. 6. Avoid Fingerprinting If you change a lot of parameters in your requests, but your scraper is still blocked, you might've been fingerprinted. Namely, the anti-bot system uses some mechanism to identify you and block your activity. 7. Bypass Anti-bot Systems If your target website uses Cloudflare, Akamai, or a similar anti-bot service, you probably couldn't scrape the URL because it has been blocked. Bypassing these systems is challenging but possible.
Cloudflare, for example, uses different bot-detection methods. One of their most essential tools to block bots is the "waiting room". Even if you're not a bot, you should be familiar with this type of screen: 8. Automate CAPTCHA Solving Bypassing CAPTCHAs is among the most difficult obstacles when scraping a URL. These computer challenges are specifically made to tell humans apart from bots. Usually, they're placed in sections with sensitive information. 9. Use APIs to Your Advantage Currently, much of the information that websites display comes from APIs. This data is difficult to scrape because it's usually requested dynamically with JavaScript after the user has executed some action. 10. Stop Repeated Failed Attempts One of the most suspicious situations for a webmaster is to see a large number of failed requests. Initially, they may not suspect a bot is a cause and start investigating.
However, if they detect these errors because a bot is trying to scrape their data, they'll block your web scraper. That's why it's best to detect and log failed attempts and get notified when it happens to suspend scraping.
1 note
·
View note
Text
KuroFai Olympics 2021 - Sun Vs Moon - FAQ
What are the KuroFai Olympics?
The KuroFai Olympics (or as I usually end up typing, Olympfics) are a friendly team-based writing competition between two teams writing opposing themes of fiction, based around the same set of subthemes or prompts.
This year, it is Team Sun and Team Moon.
Each team will have the same number of competitors, and each competitor will square off against the other team’s competitor using the same prompt, with both posting their fics on the same day as determined by the posting schedule.
Where are the Olympics held?
The home of the Olympics is the KuroFai Dreamwidth community. You can also keep up to date with us on Discord, Twitter and Tumblr. We also have a collection on AO3 and you contact the mods via [email protected].
Roles within the Olympics
Moderators: a small dedicated group tasked with planning, coordinating and overall, doing what they can to make this year another success.
Writers: wordsmiths ready and willing to write a story where the main focus is about KuroFai, will be either fluffy or angsty, and fits into the subtheme.
Artists: folks with a passion for the visual arts. While each year, we are blessed with an Artist willing to create a header for the year's Olympics (this year, we thank ValdrickV), for the tenth anniversary, there is an additional role for Artists. To create art based around the prompts. This can be done based on one's interpretation of the prompt or in coordination with a Writer.
Betas: A second pair of eyes for a Writer, offering insight, advice and or a grammar check in exchange for an early reading of the story.
Pinchhitters: Brave and generous folks willing to take on the role of Writer should the need arise.
Read and Reviewers: Lovers of KuroFai who participate by reading the posted stories and then afterwards, leaving a Review for the author. Let's face it, Kudos is wonderful, but a review leaves a greater impact.
Scorers: by popular demand, rather than leave a Review with a score, Scorer fill out a brief survey where they score the fic. A form of online presence will be required - no going entirely anonymous allowed.
What are Pinch-hitters?
A stand-by writer, in case someone who signs up with a team has to step down for any reason (life obligations, sick, believe they won't finish on time, etc.) so they will step up to write for the prompt left vacant. If a competitor feels they need to step down, please let a Mod know as soon as possible, and the Mods will then ask a pinch-hitter to take over their prompt. Should you be unreachable for two days after a scheduled check in, a pinch hitter will be called upon to take over.
To give a Pinch-Hitter the most time to write, their posting day will be moved to the last posting day. Should two need to step down, the first Pinch Hitter and their competitor will get the day before the last and the newest Pinch Hitter and their competitor will have the last posting day
Posting Dates?
The posting schedule for the Olympics starts on the 8th of August. Each of our sub themes will be assigned a posting date with the first fics being posted on the 9th of August.
The schedule is prone to change but the mods will ensure that all writers know what date they will post on. If a Pinchitter is called upon their prompt will always move to the end of the schedule.
Time zone for posting?
We are currently considering what Timezone to use. This will be updated once it has been decided.
That said, time zones are an illusion we gave ourselves, so as long as you post within an hour or two of midnight on the day of your posting, you won’t be docked points. If you post after the next competitors’ have started posting for their prompt, however, that late penalty card comes into play.
Checkins?
All writers and artists will be required to checkin with the mods three times during the creating period. These checkins are just to see how you are going and to figure out if the posting dates need to be altered. While participants can reach out to the Mods at any time if issues arise the checkins are just a formalisation of this process.
Can I write a joint fic?
All fics entered in the Olympics must be new, original works written for the appropriate prompt by a single participant. You may ask your teammates/friends/family to help you out with coming up with an idea and you can ask anyone even Mods to beta your fic once it's written, but you have to write it.
Can I reuse an older piece of work?
No, you can't take a draft fic you had prepared earlier and jazz it up for the prompt. (We may not have proof but this is where your honor comes in. Write something new for your honor.)
Fic outlines are acceptable and allowed so long as you have not begun writing fic for it before you receive your prompt.
Length of fic?
There's no minimum or maximum length of entries; if you can tell a story in a thousand words, more power to you, and if it takes you fifty thousand, that's great too. However, a word count of between five thousand to twenty thousand for the length of your fic is generally recommended.
Can I share my work before posting day?
You can share up to 10% of your work as a teaser on various social medias before your posting date. You can of course share your work with your Beta and Team Mates before hand if you like.
Do I have to post my fic on Dreamwidth?
The fic, not necessarily. But you will need to make an entry post on Dreamwidth. That is, a post where you either post under a cut or provide a link to the location where your fic is posted. A template for fic entry posts will be provided closer to the posting date.
How do I post on Dreamwidth?
You will need a Dreamwidth account to post your entry and be a member of the KuroFai Dreamwidth Community. Copy and paste the template provided into a new Dreamwidth post making sure you choose HTML and not Rich text for editing. Also remeber to chose KuroFai community as it is easy to accidentally post it to your own Dreamwidth. Example of last years template post https://kurofai.dreamwidth.org/131379.html
Do I have to submit my fic to the AO3 collection?
While we would love for you to put your fic in the KuroFai Olympics 2020 collection it is not a requirement of the competition. This year collection is 2021_KuroFai_Olympics
https://archiveofourown.org/collections/2021_KuroFai_Olympics
What if I can’t write competitively?
There is nothing to prevent you from writing a fic of your own to match the theme or a prompt you really like. We simply ask that you don’t post it during the Week (give or take) that the Teams will be posting theirs.
How can Artists get involved?
This year artist can sign up to do Art for the various prompts. The lovely Valdrick has created our banner art this year. Once prompts have been assigned to the artist there are no restrictions beyond relating to the prompt and KuroFai. Any size, any medium, any colour what ever takes your fancy.
How are fics scored?
By popular demand, this year rather than leave a Review with a score, the reader will be asked to fill out a brief survey which will be linked to at the end of the fic. A form of online presence will be required - no going entirely anonymous allowed for scoring.
Rules for scoring a fic?
Mods will not be allowed to leave a score but can still read and leave a review.
All Writers will be allowed to leave a Score EXCEPT on their fic and the corresponding fic from the other team.
Betas, Artists and others who aided in the Olympics and are not Writers or Mods are free to Score any fic.
People from across the fandom are free to Score any fic but will be required to leave a form of contact in the scoring survey.
The Scorecard
With 1 being the very worst and 10 being the very best, how well do you think this story did?
1. How well did this fic fit the prompt?
2. How well written was the fic?
3. How much did you enjoy the fic?
And please answer Yes/No
4. Was this fic tagged properly?
Questions 1-3 will have a maximum of 30 points available (and when you divide that by 3, you could get a solid 10 Pointer)
Regarding 4, if the Yes outweigh the No, then +2 Points. If the No outweigh the Yes than -2 Points.
Penalty Card
If the Penalty Card had to come in for Late and or Unfinished, then those Points will be taken out when we do the scoring.
No Story Posted: While this has happened due to unfortunate circumstance, it does result in a total loss of points. A zero for that story.
Late but Complete Fic: 1 Point Docked.
Incomplete Story Posted: 1-2 Points docked from that story.
Not Tagged Properly: 2 Points.
Not Tagged Properly?
Because of the sensitivity of subjects, all of these subjects MUST be clearly warned about should they appear in your story. At the bottom of the story under the cut is not clearly warned about.
Non-Con, Sexual violence, Dub-con, Underage, Sexual Kinks, Omega verse, Graphic Violence, Self Harm, Suicide or Suicidal thoughts.
Things like Language, Drug Use, Implied (sensitive subject), etc. are not required but are welcome to make the story that much more reader-friendly.
While not mandatory, stories featuring material from the events after Acid Tokyo, AU or Canon based, have a new tag available to them. It’s called NSFN (Not Safe for Nick/Newbies) and will make this even more reader-friendly.
Failure to comply with the Must be warned about rule results in a 2 Point loss for that story.
24 notes
·
View notes
Link
A gift to @sakxuraz for the @tobiizugiftexchange, I hope you enjoy!
Pairing: IzunaTobirama Word count: 4398 Rated: T+ Summary: Building a village with other clan-packs wasn't a terrible idea in theory. In practice it opened the door for all sorts of miscommunication as they all navigated the difficulties of integrating not only as humans but in their secondary animal forms as well. What does a cat know of birds? More importantly, what is he willing to learn?
Follow the link or read it under the cut!
KO-FI and commission info in the header!
A Word For Home
Coming from a clan more disposed to mammalian second forms, living with a bunch of birds was strange in many ways. Tobirama was more than used to seeing family and close friends groom each other but the ways in which Uchiha showed their affections seemed incredibly odd in his eyes. So odd that in many cases he wasn’t actually aware what the purpose of such gestures were supposed to be until he was informed so later on.
The first time Izuna brought him a handful of leaves he could only stare, mind racing as he tried to figure out what sort of insult was being offered to him. Each leaf was a different shade and all of them newly shed by autumn trees. After a full minute of silence he looked up to see the other man watching him intently with his dark eyes wide in anticipation, waiting for some sort of reaction, and Tobirama hoped his utter lack of any expression was as disappointing as he was sure his rage was meant to be amusing.
“I have plenty of leaves in my own front lawn,” he rumbled. Then he had turned to sweep away, missing the dejected slump of Izuna’s shoulders before there came the rushing pull of a change. Even without looking he knew the sound of strong wings hurrying away. When he dared to look back the leaves were arranged carefully on the ground in some unrecognizable pattern. He left them there.
An isolated incident like that could have easily been forgotten, written off as nothing more than yet another attempt to annoy him over petty grudges, if it hadn’t been the beginning of an utterly strange trend. The second time Izuna approached him the man came bearing an armful of cloth all with different brightly colored patterns. At first glance Tobirama thought it to be a small mountain of clothing but a closer look told him the bundle wasn’t even that much, just scraps of varying sizes all piled on top of each other. They were at least neatly folded. Still, he might have no idea what insult the man was trying to imply but he had more important things to do than to indulge his rival’s pointless games.
“There is a laundromat just down this street if you were looking for somewhere to clean your rags,” he advised stiffly.
“Rags?” Somehow Izuna managed to insert such a heavy amount of dejection in to his tone that for a moment Tobirama almost thought him genuinely saddened by the denial. Then he came to his senses.
“Fly away, little raven, I have things that need to be done today.”
With that he brushed past and paid no attention to the trill that followed him down the path. His mind was already full of the blueprints he and a team of Nara had been working on for the new hospital.
After that it seemed as though he ran in to Izuna around every other corner and every time he found something being presented to him as though it were some great treasure. Yet without fail each so-called gift turned out to be nothing more than scrap and chaff, never anything of value but neither could Tobirama make heads or tails of what this game was meant to be. He would have asked if it wouldn't have felt so much like losing.
In his office Izuna brought him a spool of wire. On his front porch was left a basket of untreated wool. Turning corners in the marketplace he found his hands full of old blankets that had clearly seen their share of use. For the life of him he couldn’t seem to connect any of these offerings together. With every new piece of junk in Izuna’s hands Tobirama only grew more and more confused. The two of them were no longer enemies by any stretch, not since their clans had formed a pact to share the same territory several years before, and although they weren’t exactly the best of friends they had managed to achieve a unique sort of equilibrium that worked for them. Casually sniping each other with pointed - if dull - insults might look to anyone else as though they hated each other but Tobirama had been secretly thrilled to have someone who finally understood his particular brand of communication.
The more bits and bobs of random materials Izuna attempted to give him, however, the more he began to question whether he had grievously misunderstood something. Jabs and jests he could understand. Pranks, on the other hand, had never been part of their repertoire. Oh he had seen Izuna pull the wool over other people’s eyes before and he’d been woken more than once by the eagle scream of Madara caught in some trap or another by his precious little sibling. Until now Tobirama himself had seemed to be the only person who escaped such treatment. He’d assumed his counterpart understood that he was not the sort of person to trifle with such things.
Curling under his desk in the brisk morning air, autumn hovering just at the edge of winter, Tobirama was grateful to his second form for both its warmth and smaller stature at the moment. Naturally resistant to the cold and easily capable of hiding under the desk like a child, Tobirama closed his eyes and laid his head down atop crossed paws. Above him Izuna could be heard rustling around. Whatever today’s gift was it apparently required more space than had been left on the desk and clearly the remedy for that was to ruin several hours worth of careful organization rather than just leave it on the floor.
“Bastard probably heard me coming and scarpered.” The tone of irritation was almost more familiar than the sound of his voice.
From his hiding spot Tobirama cracked one heavy eyelid in agreement. That was exactly what he’d done. Never had it been so convenient to be able to slip away from even the Sharingan’s detection. While there were definite limitations in not having access to chakra in this form, the fact that it left one nigh undetectable by sensors was a clear bonus that he was happy to take advantage of now.
It took only a minute or two of patience before Tobirama found himself alone in the room once again, celebrating the much needed peace by stretching out his front paws and flexing each toe to watch his claws appear and retract. With a great yawn that curled his tongue he brought his paws back to fold underneath his head once more as though truly contemplating the notion of an early morning nap. He could use it. Even if he knew very well that he would never actually sleep when there was work to be done it was nice to pretend for a bit that he could be just as lazy as any house cat. Only after his sensitive ears heard the sound of another office door closing down the hall did he finally crawl his way out from under the desk, pausing to shake out his body and resettle any displaced fur.
As he did so the motion of his reflection in the window drew his gaze and Tobirama blinked thoughtfully at the great snow leopard staring back at him from the glass. It had occurred to him, of course, that whatever Izuna was up to might not be a prank but he hadn’t considered before that it might have something to do with the Uchiha propensity for avian forms. Cocking his head to one side and watching his ears flop, he considered it now. How many times had he seen Uchiha flitting about through the forest collecting twigs and leaves and dismissed it without curiosity? So few of their clan had warmed up to him still and he’d returned such lukewarm sentiments with an utter lack of care for learning their ways beyond what tidbits he picked up from interacting with Kagami. Now he sat back on his haunches and wondered if perhaps he shouldn't sacrifice a little of his pride after all.
Later, though. For now he had work to do.
With today’s confusing gift already delivered, Tobirama was able to coast through the rest of his work without the tension of waiting for something unknown. By the time his desk was clear and the sun began to set behind him it felt as though he’d been able to get nearly twice as much done as the past week put together. It was amazing what he could accomplish when he was actually able to concentrate. He left the office with a surprising amount of energy left; just enough that he thought he might be able to deal with the humiliation of asking for help from his brother.
For such a late hour the streets were still quite packed with people running a few evening errands and couples venturing out to meet for dates. Just in the time it took him to reach the Senju compound Tobirama passed three couples holding hands, two making out in places they probably thought were inconspicuous, and one in the midst of a proposal that did not seem to be very well received. Peace, it seemed, was quite the aphrodisiac for many people once they finally settled in to the concept of it. After that first uncertain year had passed and their peoples got used to sharing the same territory it was as though half the population was suddenly caught up in some unseasonal mating frenzy. Strange how priorities changed when one didn’t need to spend every moment of every day fearing for one’s life.
“Tadaima!” His own voice echoed back to him when he stepped inside, mingling with the sound of the door clicking shut behind him. As he kicked off his shoes he frowned and strained his ears. No sound. A quick sweep showed the building empty to his senses as well. Either he was home alone for the evening or Hashirama and Mito were not walking on two legs.
Since the questions knocking about in his mind weren’t exactly urgent he took the time to stop by his bedroom and change his clothing, shedding the dust and sweat of a long day in favor of well-worn cotton soft on his skin, comfortable loungewear he would never be caught dead in outside the home. Then he wandered through the living room, the kitchen, the green room filled with plants where he often found Hashirama napping when he was meant to be doing so many other things. Nowhere was there any sign of life until he happened to glance out the back window and spotted two massive forms huddled together in the backyard.
Unobserved, he allowed himself a moment to simply watch with a smile. It had always struck him as particularly funny that when human Hashirama was about as clumsy as they come but in the form of a bear he somehow managed to exude grace and calm. Even as he tore in to the strip of raw meat clearly serving as his dinner he looked more adorable than terrifying. The same could not be said of his wife. An empress in all but title on two legs, it had been a surprise to learn that her secondary form was also that of the bear until the first time Tobirama witnessed her tearing in to an enemy with tooth and claw. Hashirama might be a cute docile little sun bear but his wife was a brown bear ready to rampage the instant she perceived a threat to the ones she saw as her own. It was oddly fitting.
At the moment, however, the two of them were doing nothing more violent than partaking of a meal together and Tobirama was loath to disturb such a domestic scene. He contented himself with a plateful of leftovers from the previous evening’s dinner and ate alone at the kitchen table with fingers and chopsticks while he waited. The sun was barely finished setting and he had only just finished washing his dishes when the other two made it back inside. A whuffing moan greeted him, to which he rolled his eyes.
“I do not speak bear, Anija. Such uncouth noises.”
“So mean,” Hashirama pouted as he flowed back to humanity with the seamless grace of someone who had made the change countless times before. “We were going to leave some for you but you never came outside so I ate your meat.”
“Thank you, but I was content with stew.”
Mito narrowed her eyes thoughtfully at him but said nothing, only reached out to bring the tips of her fingers against his shoulder. He accepted the gesture with a nod before looking back to his brother.
“Can I ask you a few questions? You would know more about the Uchiha than I do.” His should have known better than to be so vague. The words had hardly left his mouth when Hashirama froze in the act of searching out an after dinner snack, turning to look at him with an already exhausted expression.
“Oh Tobi-” he started to say.
“I didn’t do anything!” Tobirama protested. “Not this time, at least. I just wondered if you could give me a little insight in to some of their habits. If you’re going to be a dick about it I can always find someone else to ask.”
“No! I’m sorry! Please don’t ask anyone else. What, ah, what did you want to know?”
Hashirama offered him a cute little smile but it fooled no one. They both knew all he wanted was to make sure Tobirama didn’t go asking the wrong questions to the wrong person and starting a fight with his habitual bluntness. Still, if it got him the answers he wanted right now he was willing to overlook the lack of faith this once.
Just because his brother had a point didn’t mean he had to be so obvious about it.
“If I describe a certain behavior that I’ve observed could you tell me if you know the reasoning behind it?” Tobirama waited until he received an attentive nod before going on. “Right. Say one person is bringing things to another and presenting them as if they’re gifts. Except all of these ‘gifts’ are pieces of scrap or garbage or even just leaves off the ground. Does that sound like any sort of Uchiha-specific behavior to you or just some kind of very elaborate prank?”
For several heartbeats his brother stared at him, almost like he was trying to determine whether or not that was a serious question, until finally he pulled off a signature personality flip by sliding straight in to a swoon.
“Whoever you’ve been watching, they’re so lucky!” he declared.
“Lucky?”
“Yes! It seems they’ve caught someone’s eye!”
Tobirama scowled. “You know I hate it when you make such poor attempts at humor, Anija.”
“But it’s not a joke! I’m serious, that sounds just like how an Uchiha behaves when they’re trying to catch the interest of a potential mate!” Hashirama sniffled, wounded to be accused of making jokes. Or perhaps wounded that his terrible sense of humor had been so rightly assessed. It didn’t matter. Tobrama was much more interested in the utterly ridiculous bullshit his sibling was trying to feed him.
“How does bringing someone litter off the ground or used rags translate as an offer to mate?”
Immediately affecting another swoon, Hashirama sighed like a woman from one of his trashy romance novels. “The gifts aren’t litter, they’re materials! Madara explained it to me once when his secretary kept trying to bring him twigs. When an Uchiha wants to mate with someone they bring them whatever materials they think could be used to make a nice nest for them both. Things like leaves and cloth might be the lining, wood and sticks might be used for the main structure, even pretty little baubles that might just be for decorating! I think it’s really sweet. They build homes together!”
“Nests. That’s...they were all...nesting materials.” Swallowing felt suddenly three times more difficult than it should have been. “I need to sit down.”
“You’re already sitting down?”
“I need to lay down.”
Hashirama blinked at him, studied him closely. It took several moments but a slow grin began to form that stretched his face with a maniacal sort of joy. “It’s you! You’re the one who’s been getting these mating gifts! Someone is trying to court you!”
“According to you he is asking me to bond with him permanently!” Tobirama had never felt so close to a panic attack in his life.
“Why do you say that like it’s a bad thing?”
“Because I had thought his opinions of me to be mere tolerance! I had no idea he felt anything like this! What do I even do with this information, Anija!?”
“Oh I don’t know. You could try accepting a gift or two? Going out on a date? You could tell me who it is! Is it that very pretty lad who works in the mission room? No! It’s that quiet man in the archives! I knew I saw him looking at your bottom that day! This is just so sweet, I am just so happy for you!” Hashirama’s arms struck like a pair of sun-browned cobras to wrap around his neck and squeeze tight. “My little baby brother is all grown up and finding a mate!”
It took squirming, yelling, and a smidgen of violence to extract himself from such an unwarranted embrace. By the time he struggled himself free Hashirama had nearly soaked one shoulder of his previously clean yukata with tears and snot. Delightful. Only years of training in speed and flexibility allowed him to escape the kitchen without being dragged in to another hug, hurrying down the hall to lock himself in to his bedroom where he staunchly ignored the whining coming through his door. Hashirama could be happy for him all he liked. That didn’t make it any easier to process the revelation that had just been dropped on him unexpectedly.
So Izuna was attempting to court him with the intention of mating. Tobirama knew as well as anyone else who spent any amount of time around their clan that the Uchiha mated for life, unwilling to commit themselves to something of that magnitude unless they were certain it was what they wanted for the rest of their lives. Now that he had finally cottoned on to what was actually happening he needed to figure out how he felt about it before taking any action.
Did he want this too?
Waiting for sleep that night was made harder by the familiar chakra creeping up and down the hall to check whether or not his bedroom was still locked several times. His brother never had been able to understand proper boundaries. Either he finally gave up or Mito grew tired of him rustling about and tied him down somewhere but whatever the case Tobirama did eventually fall asleep. By his best estimate, however, when he woke again he had only dreamt for perhaps a little more than three hours.
He made sure to avoid his brother on his way out of the house the next morning, detouring through the marketplace to pick up something to break his fast. For once in his life he was actually grateful to the swarm of people who mobbed him the moment he stepped inside the administration tower. Any other day he would have been annoyed to have so much extra work shoved in to his hands before he even made it to his own office but today it was nice to have something that demanded his attention, something to occupy his mind without the gnawing guilty feeling of knowing he was only avoiding the inevitable. With his arms full of fresh paperwork he marched his way up the stairs and buried his face in whichever scroll he was able to unroll without upsetting the whole pile. A distraction was only good if he let himself sink in to it.
Of course, he’d known the moment he left home that he would only have so much time before the very thing he spent all night giving his deepest considerations to would come barging in and demanding even more of his attention. As he watched the door swing open Tobirama supposed that he should at least appreciate that Izuna had allowed him an hour or so of peace to settle in.
“Morning!” Under the cheer of his tone Izuna’s smile was wan, almost false, though whether he was losing hope or if he’d simply not slept well the night before was unclear.
“What do you have for me today?” Tobirama asked.
After a moment of startled blinking Izuna was quick to hold out the small bundle of cloth in his arms. “Before you ask, no, none of them have an uchiwa on them.”
Tobirama hummed and bent his neck for a closer look. Clothing, although different from the last similar offering. Before he had been offered well used scraps that - he understood now - would have carried a great deal of sentimental value and made a very potent addition to any nest. These clothes were much newer looking and yet his sharp nose told him the other man had very carefully worn every item in that pile at least once to coat them with his scent. Not quite as important to avians but to a cat scent was everything.
When he reached out to accept the bundle he got the distinct impression that Izuna only barely stopped himself from fainting.
“Since I won’t be wearing them,” he mumbled, “I don’t suppose it matters whose mon they have stitched on them.”
“You...took them. You took them? You took them from me. I think I’m asleep.” Izuna reached across himself to pinch his own arm without breaking eye contact.
“If you had perhaps used your words I might have been inclined to accept your, ah, offers a little sooner.”
Tobirama’s hand twitched with the urge to scrub at the back of his neck with embarrassment, though he managed to keep himself from doing it. He would probably never admit it to the man but he owed Hashirama a great deal for explaining things to him the way he had. As much as he would absolutely be teasing Izuna about this it was a very good thing his old rival had never actually explained what his gifts were meant for. Having someone else clue him in gave Tobirama the chance he needed to panic in private, get past the instinctual need to run, and actually face the emotions he had apparently been repressing for longer than he wished to acknowledge.
“Does this- you do know what that is, right?” Izuna asked carefully. He visibly held his breath when met with a slow nod.
“Yes. I do. Well, now I do.” And that was all he hoped he would have to say about that. “You should probably know that snow leopards do not make nests.”
“No?”
“Our dens don’t require much personalization so I will need your guidance on how to go about this. If we’re both to be comfortable then I’ll want to make sure our nest is to your specifications.” Tobirama very much hoped his cheeks were not as red as they were warm. Romance and mates had never been something that took up many of his thoughts, never a subject he felt much of a need to pursue. It was lucky for him, then, that he seemed to have fallen in love with someone willing to pursue him instead.
If Izuna had been blessed with four legs in his second form he would no doubt have begun purring raucously in the moment it finally hit him that this was real. Since his vocal chords were not shaped for that he instead broke out in to the toothiest, smuggest grin that Tobirama had ever seen. It was a terribly good look on him.
A low, pleased trill echoed up his throat as he stepped forward until they were pressed together, chest to chest, and lifting his chin to nuzzle against the underside of Tobirama’s jaw. It was a surprisingly gentle gesture from someone whose usual method of showing he cared was a well timed insult aimed straight for the weak points. Even more endearing - and even more surprising - were the hands that brushed their way up the length of Tobirama’s abdomen to rest softly against his chest. Unassuming, unasking, reaching out yet still allowing space. How could a man do anything but pull him in to a loose embrace and close his eyes to bask?
“Mate,” Izuna whispered against the skin of his throat. “I’ve been incredibly patient for the honor of calling you that.”
“You have indeed,” Tobirama admitted.
“I think I deserve a little something for my troubles.”
A smile lifted the corners of Tobirama’s mouth. “I might be convinced to compensate you if the request isn’t too ridiculous.”
He was answered by another soft trill that plucked at his heartstrings in ways he never would have been able to admit if Izuna had not made the first move. Though finding a mate had never been a priority in his plans for the future he would have to give up his title of ‘genius’ to turn down an offer of happiness like this one.
“Would you be willing to share a bit more of your nest building customs? I would hate to offend by accident so early in our bond.”
“Before we worry about offending anything we should, oh I don’t know, maybe get busy forming the bond,” Izuna suggested. His tone by itself was suggestive enough even before he pulled away a scant inch or two to lock their gazes with a filthy leer. Tobirama tried to resist but it was no good. He smiled helplessly, the first of many capitulations to come.
“I am eager to learn any part of you that you wish to share,” he said.
And if perhaps under the suggestiveness of his own words he had cleverly hidden the softest parts of his heart laid bare, well, it was only right of him to share every part of himself with his new mate as well.
37 notes
·
View notes
Text
Submission Guidelines 2021

All authors and artists are required to have an AO3 account.
All works must be beta’ed. If using a group chat or Discord server to help you find a beta, please save details which could give away your identity as creator for dms. If you have difficulty finding a beta, please e-mail the mods and we will do our best to put you in touch with someone.
Submit your fic or art to the fest collection on AO3 (https://archiveofourown.org/collections/hp_daddyfest_2021) on or before June 1st. The collection is set to anonymous, so all submissions added to it will automatically become anonymous until the mods reveal them.
It is advised that you save a link to the submission in case you wish to revisit it to make any edits, as it can be difficult for creators to access it before posting.
Submissions must be made on or before the 1st June. Early submissions are very much appreciated.
If you need an extension, please let us know as soon as possible by emailing [email protected]
PLEASE contact us via e-mail if you are unable to post. There are no penalties for dropping out with notice. We understand that life happens as long as you keep us in the loop as best you can. Participants who repeatedly ignore emails from the mods may be refused participation in future fests.
When you submit your work, you must co-author hpdaddyfest. This is to allow us to add necessary tags and correct obvious typing errors only. You will be informed by email if we have done this so that you can review it if you wish. Any more complex issues, we will email you before making changes.
If you wish for your submission to remain anonymous after the fest, please email the mods.
We reserve the right to ask you for a second beta or a sensitivity reader.
Once you have submitted your work, please complete the Header Submission form by following the link sent in the ‘Submission Guidelines’ email.
One submission will be revealed (but remain anonymous) on AO3 each day. The header information will be used to post on Tumblr each day with a link to the fic on AO3.
The moderators will post wrap-ups of fanworks in a single weekly post on the HPDaddyfest Tumblr. We will also post a final fest wrap up before and after reveals.
When participant reveals are posted, we will remove ourselves as co-author.
The fest is anonymous so please do not post your submissions to your own accounts on any platform. Reblogging and sharing of submissions is highly encouraged, but as the fest is anonymous we encourage and require secrecy as to the creator of each submission.
3 notes
·
View notes
Text
The ARM GCC cross-compiler saga
I love macOS and ever since I switched to it in 2018, it has become my favourite platform of all time. However, the thing is that I develop software for embedded Linux devices pretty often too.
Since the devices themselves usually have a stripped down firmware as well as are generally underpowered, the best way to speed up the development process and to make it easier and more comfortable in general is to use a cross-compiler toolchain. On Linux, it’s pretty easy to build one yourself or use Linaro’s pre-compiled GCC binaries if your target uses an ARM processor. On macOS, however, the building process does have some caveats.
One of the things that make compiling a cross-toolchain on macOS targeting Linux is that macOS by default uses a case-insensitive file system, which makes building glibc for the target almost impossible. This can be easily worked around by creating a read-write DMG image containing a single Mac OS Extended (Journaled, Case-sensitive) or APFS (Case-sensitive) partition, mounting it and storing the sources and build directories there.
Compiling the Linux kernel from macOS doesn't really work that well. Usually, you can't get past the configuration step successfully - even the install_headers target fails miserably. A workaround for that would be getting existing kernel headers as a package for the target system and unpacking it manually. For example, if your target runs a distro compatible with RHEL/Fedora, then you can get a pre-built kernel-headers package matching the kernel version of your Linux device and unpacking it manually. This will require compiling RPM, though, or installing it through Homebrew (which is faster).
When it comes to anything else, the build process is mostly similar to the one described in many many available guides on the net. But here is a short guided command-line snippet that will get you going with an ARM64 GCC toolchain for Fedora Linux 33 (use this as a reference). Just changing the toolchain target string ($LINUXARMBRAND) to the one matching your target platform should probably be enough in most cases to get a working toolchain for it.
# set the prefix and the target string variables accordingly $ export LINUXARMTC=/usr/local/builds/gcc-cross-arm64-linux $ export LINUXARMBRAND=aarch64-redhat-linux-gnu # get binutils and gcc $ curl -o- http://mirrors.dotsrc.org/gnu/binutils/binutils-2.36.tar.xz | tar -xvJf - $ curl -o- http://mirrors.dotsrc.org/gnu/gcc/gcc-9.1.0/gcc-9.1.0.tar.xz | tar -xvJf - # build rpm as well as some of its dependencies # 1. build libmagic $ curl -o- http://deb.debian.org/debian/pool/main/f/file/file_5.39.orig.tar.gz | tar -xvzf - $ cd file-5.39 && sh configure --prefix=$LINUXARMTC --enable-static --disable-shared && make -j6 && make install $ cd .. # 2. build openssl $ curl -o- https://www.openssl.org/source/openssl-1.1.1i.tar.gz | tar -xvzf - $ cd openssl-1.1.1i && perl Configure no-hw no-shared no-zlib no-asm --prefix=$LINUXARMTC darwin64-x86_64-cc && make -j6 && make install $ cd .. # 3. build rpm itself $ curl -o- http://ftp.rpm.org/releases/rpm-4.16.x/rpm-4.16.0.tar.bz2 | tar -xvjf - $ cd rpm-4.16.0 && CFLAGS="-I$LINUXARMTC/include" LDFLAGS="-L$LINUXARMTC/lib" LIBS="-lbz2 -lz" sh configure --prefix=$LINUXARMTC --disable-shared --enable-static --with-crypto=openssl --without-archive --disable-plugins --without-lua --disable-openmp $ echo 'void main() {}' > rpmspec.c && make -j6 && make install # 4. build make $ curl -o- http://mirrors.dotsrc.org/gnu/make/make-4.3.tar.gz | tar -xvzf - $ cd make-4.3 && sh configure --prefix=$LINUXARMTC && make -j6 && make install $ cd .. # 5. build bison $ curl -o- http://mirrors.dotsrc.org/gnu/bison/bison-3.7.5.tar.xz | tar -xvJf - $ cd bison-3.7.5 && sh configure --disable-nls --prefix=$LINUXARMTC && make -j6 && make install # get fedora kernel headers $ mkdir rpmextract && cd rpmextract $ curl -o kernel.rpm http://mirrors.dotsrc.org/fedora/linux/updates/33/Everything/aarch64/Packages/k/kernel-headers-5.10.11-200.fc33.aarch64.rpm $ $LINUXARMTC/bin/rpm2cpio kernel.rpm | tar -xvf - # install them into a sysroot $ mkdir -p $LINUXARMTC/$LINUXARMBRAND $ mv -v include $LINUXARMTC/$LINUXARMBRAND $ cd ../.. # build binutils $ cd binutils-2.36 && mkdir build && cd build && sh ../configure --target=$LINUXARMBRAND --prefix=$LINUXARMTC --disable-multilib --disable-werror --disable-libquadmath --disable-libquadmath-support && make -j6 && make install $ cd ../.. # build gcc (stage 1) $ export PATH="$LINUXARMTC/bin:$PATH" $ cd gcc-9.1.0 && sh contrib/download_prerequisites --no-isl --no-graphite && mkdir build && cd build && sh ../configure --prefix=$LINUXARMTC --target=$LINUXARMBRAND --with-static-standard-libraries --disable-libquadmath --disable-libquadmath-support --enable-ld=yes --enable-languages=c,c++ $ make -j6 all-gcc $ make install-gcc # bootstrap glibc $ cd glibc-2.32 && mkdir build && cd build && BISON=$LINUXARMTC/bin/bison MAKE=$LINUXARMTC/bin/make ../configure --prefix=$LINUXARMTC/$LINUXARMBRAND --host=$LINUXARMBRAND --target=$LINUXARMBRAND --with-headers=$LINUXARMTC/$LINUXARMBRAND/include --disable-multilib --disable-werror $ make install-bootstrap-headers=yes install-headers $ make -j6 csu/subdir_lib $ install csu/crt1.o csu/crti.o csu/crtn.o $LINUXARMTC/$LINUXARMBRAND/lib $ $LINUXARMTC/bin/aarch64-redhat-linux-gnu-gcc -nostdlib -nostartfiles -shared -x c /dev/null -o $LINUXARMTC/$LINUXARMBRAND/lib/libc.so # build gcc (stage 2) $ cd ../../gcc-9.1.0/build && touch /usr/local/builds/fedora33-arm64-gcc/aarch64-redhat-linux-gnu/include/gnu/stubs.h && make -j6 all-target-libgcc && make install-target-libgcc # finish glibc $ cd ../../glibc-2.32/build && touch testrun.shT debugglibc.shT iconvdata/MIK.so iconvdata/ISO_11548-1.so iconvdata/ISO8859-9E.so iconvdata/CP77{0,1,2,3,4}.so iconvdata/KOI8-RU.so iconvdata/MAC-CENTRALEUROPE.so && make -j6 && make install # build gcc (stage 3) $ cd ../../gcc-9.1.0/build && make -j6 && make install
Hope this works for you
#linux#macos#gcc#cross-compiler#toolchain#arm#raspberrypi#odroid#technology#tech#c programming#c++#programming#c++ programming
4 notes
·
View notes
Text
Free 3 card tarot readings open!
(Ignore the part in my header where it says they're not. Tumblr is doing that thing where it objects to having HTTP vs HTTPS in my theme code, but I haven't been on my PC for long enough to fix it in weeks lol)
So I've picked up a couple new decks since I opened free readings last. That means it's free reading time! Readings will be open from now till June 1st, and I'll be doing them with the Golden Thread tarot.
My guidelines:
Please submit one question per ask. (Feel free to submit multiple asks though!)
I do private readings! Send me an ask while logged in and it'll be treated as private unless you specify otherwise.
if you submit on anon, please sign your ask. Emojis, your initials, your zodiac, etc. I just need something so I can identify you as you. This is mostly to make things easier on me in case Tumblr eats the ask.
I won’t do sex, fertility, physical/mental health, time-sensitive, or "how do I make <xyz> love me" readings. Those subjects are either way above my pay grade or make me super uncomfortable.
Please be patient and polite! I'm disabled with limited energy, have my own life and I'm also dealing with some medical stuff. But if I haven't gotten to your ask after 3 days, feel free to check in! If it takes that long, it's probably been eaten.
If I get swamped, I'll close my ask box till I catch up. But I'll let you know when I'm doing it and when I'm opening it back up, so keep an eye out! (Also if I close my ask box to catch up, please don't try to circumvent it via DM. It's super rude.)
#free tarot readings#free tarot request#free tarot services#free tarot card reading#free tarot#selkie reads tarot
10 notes
·
View notes
Text
Security Everywhere 2
Today, when I watched ABC News in the morning and turned on the closed caption, I found something strange on the subtitles. You can see them in the below pictures. Actually these are selected from all my taken pictures in case some really sensitive information is leaked.
Recall the activity of “Shredding Analysis” and click “Keep Reading” below to read the full post.
(Sorry for the dirty surface)



So, Apparently, these red-circled information is part of HTTP headers. “te-api.ap-southwest” is probably a URL from one of cloud services providers.
The next two nonsense texts can be some hash value. I also got some other pictures with the hash value. In my opinion, these are probably UUID or something, but I didn’t do a deep research.
If I have time and do a similar “Shredding analysis”, I probably can combine all information together and figure out any physical serve ABC News is using. In a word, the information leak like this can make ABC more vulnerable to be hacked.
1 note
·
View note
Text
Openemu cheats pokemon emerald

Openemu cheats pokemon emerald how to#
Openemu cheats pokemon emerald apk#
Openemu cheats pokemon emerald code#
Continued abuse of our services will cause your IP address to be blocked indefinitely. Please fill out the CAPTCHA below and then click the button to indicate that you agree to these terms. If you wish to be unblocked, you must agree that you will take immediate steps to rectify this issue. If you do not understand what is causing this behavior, please contact us here. If you promise to stop (by clicking the Agree button below), we'll unblock your connection for now, but we will immediately re-block it if we detect additional bad behavior. Overusing our search engine with a very large number of searches in a very short amount of time.In this menu, there will be another item labelled Add Cheat. If the core supports cheat codes, a menu item called Select Cheat will be available. Within the game window, move the mouse to produce the HUD bar, and click the cog/gear icon near the center. Using a badly configured (or badly written) browser add-on for blocking content To add a cheat code, you must be running a game.Running a "scraper" or "downloader" program that either does not identify itself or uses fake headers to elude detection.Using a script or add-on that scans GameFAQs for box and screen images (such as an emulator front-end), while overloading our search engine.There is no official GameFAQs app, and we do not support nor have any contact with the makers of these unofficial apps. Continued use of these apps may cause your IP to be blocked indefinitely. This triggers our anti-spambot measures, which are designed to stop automated systems from flooding the site with traffic. Some unofficial phone apps appear to be using GameFAQs as a back-end, but they do not behave like a real web browser does.Using GameFAQs regularly with these browsers can cause temporary and even permanent IP blocks due to these additional requests. If you are using Maxthon or Brave as a browser, or have installed the Ghostery add-on, you should know that these programs send extra traffic to our servers for every page on the site that you browse.This will continue the process until you’ve completed the game. Once you’re done, simply switch back to the other game and repeat. These cheats work with most versions of the Pokemon Emerald ROM, so if you’re using a Mac, it will not work with OpenEmu. The most common causes of this issue are: Pokemon Blazed Glazed Cheats Pokemon Cheats Glazed. dotus.live Pokemon Go 100 Iv Rech.Your IP address has been temporarily blocked due to a large number of HTTP requests.All codes listed are compatible with either accessory. Gameshark and Action Replay cheat codes are not case sensitive, nor are spaces between numbers required.
Openemu cheats pokemon emerald code#
The master code for Pokmon Emerald is as follows: D8BAE4D9 4864DCE5.
pokspoofer.xyz Pokemon Go 100 Iv Slakin. The master code must be the first entry you make when inputting cheats.
apptweak.live 100 Iv Bagon Pokemon Go.
bit.ly/2gieory Pokemon Go 100 Iv Pokemon Cp.
Openemu cheats pokemon emerald how to#
apker.live Pokemon Go How To Tell 100.pohack.top Armored Mewtwo 100 Iv Max Cp P.doin.site/pokemon Pokemon Heart Gold A.bit.ly/2gieory Heartgold Apricorn Pok.doin.site 100Iv Pokemon Coords Genera.doin.site/pokemon Cyndaquil 100 Iv Pokemo.dotus.live/pokemon Jynx Pokemon Go 10.
Openemu cheats pokemon emerald apk#
Pokemon go hack pokeball android pokemon go cheat pokemon go cheats pokemon go cheat app pokemon go cheat sheet pokemon go cheaters pokemon go cheat app iphone pokemon go cheats eevee pokemon go cheats reddit pokemon go cheats for pokeballs pokemon go cheat for choosing eevee evolutions pokemon go cheat download pokemon go cheat stardust pokemon go cheaters reddit pokemon go cheats rare candy pokemon go cheats and secrets pokemon go cheats to get more candy pokemon go cheat adventure sync pokemon go cheat apk pokemon go cheat codes for coins pokemon go cheat names for eevee pokemon go cheats walk without moving pokemon go cheat app android pokemon go cheat android 2020 pokemon go cheat android 2020 pokemon go cheat app 2020 pokemon go cheat app tutu pokemon go cheat apk download pokemon go cheat apk 2020 pokemon go cheat apk 2020 pokemon go cheat app 2020 pokemon go cheat app download pokemon go cheat android 9 pokemon go cheat apk ios pokemon go cheat android no root pokemon go cheat account pokemon go cheat app 2020 pokemon go cheat app joystick pokemon go cheat battle pokemon go cheat bluestacks pokemon go cheating ban pokemon go cheat balls pokemon go unlocked bonuses pokemon go unlock battle pokemon go battle cheat sheet pokemon go buddy cheat pokemon go berry cheat pokemon go bootloader unlock pokemon go cheat without ban pokemon go cheat no ban

0 notes
Text
Owa deliveryslip app

We then monitored activity in the accounts for 72 days, and observed 165 accesses in total. To study how people interact with these spreadsheets in case they are leaked, we posted unique links pointing to the spreadsheets on a popular paste site. Each spreadsheet was configured to report details of accesses and clicks on links back to us. We populated 5 Google spreadsheets with fake bank account details and fake funds transfer links. In this paper, we present a system able to monitor user activity on Google spreadsheets. Despite the importance of such documents to Internet users, there are still large gaps in the understanding of what cybercriminals do when they illicitly get access to them by for example compromising the account credentials they are associated with. We conclude this paper by making recommendations on clarifying the privacy implications of internal site search to end users.Ĭloud-based documents are inherently valuable, due to the volume and nature of sensitive personal and business content stored in them. We then present a few countermeasures, including a browser extension to warn users about imminent search term leakage to third parties. However, about 75% of these privacy policies seem to mention the sharing of some information with third-parties in a generic manner. We then compared our results to the expected results based on a natural language analysis of the privacy policies of those leaking websites (where available) and found that about 87% of those privacy policies do not mention search terms explicitly. We found that 81.3% of websites containing internal site search sent (or leaked from a user’s perspective) our search terms to third parties in some form. Our crawler found that 512,701 of the top 1 million sites had internal site search. We used this crawler to visit the Tranco top one million websites and analyzed search term leakage across three vectors: URL query parameters, payloads, and the Referer HTTP header. We developed a methodology for identifying and interacting with search components, which we implemented on top of an instrumented headless browser. In this paper, we measure the various ways by which search terms are sent to third parties when a user submits a search query. Search terms on these sites may contain sensitive information such as location, medical information, or sexual preferences when further coupled with a user’s IP address or a browser’s user agent string, this information can become very specific, and in some cases possibly identifying. Internal site search is an integral part of how users navigate modern sites, from restaurant reservations to house hunting to searching for medical solutions. To fix this problem, we discuss how services can apply the Referrer Policy correctly to avoid these incidents, as well as other server and client side countermeasures. In the second case, one service correctly implements an appropriate Referrer Policy, but some web browsers do not obey it, causing links clicked through them to leak their HTTP Referers. In the first case, six services leak their referrers because they do not implement a strict enough and up-to-date policy. We identify two root causes of these issues, both having to do with an incorrect application of the Referrer Policy, a countermeasure designed to restrict how HTTP Referers are shared with third parties. We present a study of 21 online collaboration services and show that seven of them are vulnerable to this kind of secret information disclosure caused by the improper handling of embedded links and HTTP Referers. Specifically, if a user clicks on a link embedded into a file hosted on an OCS, the HTTP Referer contained in the resulting HTTP request might leak the secret URL. In this paper, we show that the secret location of OCS files can be leaked by the improper handling of links embedded in these files. The security of this secret link approach relies on the fact that only those who know the location of the secret resource (i.e., its URL) can access it. Documents on these services are frequently shared via secret links, which allows easy collaboration between different users. Online collaboration services (OCS) are appealing since they provide ease of access to resources and the ability to collaborate on shared files.

0 notes
Text
Uninstall kineme filetools

#Uninstall kineme filetools license#
You can then use additional filters to refine the search for a correct application. If the query provided to winget does not result in a single application to uninstall, then winget will display multiple results. The following example uninstalls an application using its ID. winget uninstall -name powertoys -version 0.15.2 The following example uninstalls a specific version of an application. In the example below, the name 'orca' and the id was passed in. Used to override the logging setting and create a verbose log.Īfter you have successfully identified the application intended to uninstall, winget will execute the uninstall command. Optional Windows-Package-Manager REST source HTTP header.
#Uninstall kineme filetools license#
Used to accept the source license agreement, and avoid the prompt. You must provide a path to a file that you have the write rights to. Retains all files and directories created by the package (portable)ĭirects the logging to a log file. The default experience shows uninstaller progress.ĭeletes all files and directories in the package directory (portable) The default experience shows uninstaller progress. Runs the uninstaller in interactive mode. It will not use the default behavior of a substring. Uses the exact string in the query, including checking for case-sensitivity. Restricts the search to the source name provided. If not specified, latest will uninstall the highest versioned application. Limits the search to the moniker listed for the application.Įnables you to specify an exact version to uninstall. Limits the search to the name of the application. Limits the uninstall to the ID of the application. You can use the manifest to run the uninstall experience from a local YAML file. Must be followed by the path to the manifest (YAML) file. The options allow you to customize the uninstall experience to meet your needs. This is most often the string of characters you expect to help find the package you are uninstalling.

0 notes
Text
[Media] YARD Stick One Bundle
YARD Stick One Bundle YARD Stick One is a sub-1 GHz wireless transceiver controlled directly from your computer. It uses the same radio circuit as the popular IM-Me. The radio functions that are possible by customizing IM-Me firmware are now at your fingertips when you attach YARD Stick One to a computer via USB. YARD Stick One (Yet Another Radio Dongle) comes with RfCat firmware installed, courtesy of atlas. RfCat allows you to control the wireless transceiver from an interactive Python shell or your own program running on your computer. YARD Stick One also has CC Bootloader installed, so you can upgrade RFCat or install your own firmware without any additional programming hardware. For open source design files and additional information, visit the repository. Includes: ▫️ One ANT700 telescopic antenna – a 50 ohm antenna suitable for radio frequencies between 300 MHz and 1100 MHz. ▫️ 3d printed case specific to the YARD Stick One. Features: ▫️ SMA connector for external antennas ▫️ Receive amplifier for improved sensitivity ▫️ Transmit amplifier for higher output power ▫️ Flat RF performance across the entire CC1111 operating frequency range (281-361 MHz, 378-481 MHz, 749-962 MHz) ▫️ Low pass filter for elimination of harmonics when operating in the 800 and 900 MHz bands ▫️ Antenna port power control for compatibility with antenna port accessories designed for HackRF One ▫️ GoodFET-compatible expansion and programming header Buy online: 🛒 https://ali.ski/Ig6SQd #radio #usb

0 notes