#Free Network Security Tutorial
Video
youtube
#7 Free Network Security Tutorial | CheckPoint CCSA | Features in CheckPoint Firewall
➥ Free Network Security Tutorial | CheckPoint Firewall https://www.youtube.com/playlist?list...
#youtube#free network security tutorial#checkpoint ccsa#Features in CheckPoint Firewall#CheckPoint Firewall P7
1 note
·
View note
Video
youtube
#6 Free Network Security Tutorial | CheckPoint CCSA | Configuring VPN in CheckPoint Firewall
➥ Free Network Security Tutorial | CheckPoint Firewall https://www.youtube.com/playlist?list...
#youtube#Free Network Security Tutorial#CheckPoint CCSA#Configuring VPN in CheckPoint Firewall#checkpoint firewall p6
0 notes
Text
02/23/2024 Daily OFMD Recap
TLDR; How To Help; Rotten Tomatoes Reviews/GoggleBox; Cast & Crew Sightings; Taika; Rhys; Leslie Jones; New Watch Party: These Thems; Save OFMD UK Billboard; Transparency policy; RhysDarbyFaction; We'reWolves; Fan Spotlight; Podcasts/Youtube vids; Articles; Love Notes; Daily Darby / Tonight's Taika
Hey all. I'm starting out with the how to help section tonight because there are some things we'd love to see happen to try and help with the renewal.
== HOW TO HELP ==
= Rotten Tomatoes Reviews =
Okay all, this is a big one. It's been brought to my attention by @bzy_hands on twitter, that there are less than 1000 reviews on rotten tomatoes for Season 2. They have an excellent point, Con DID screenshot Season 2. If you haven't already, please go over to Season 2 and review it to help get over that 1000 review mark.
Need help on how to review on RT? @lowrahh Was kind enough to make a tutorial for us, check it out on the repo: Review on Rotten Tomatoes and IMDB

== Let's Get OFMD On Gogglebox ==
Our crew-mate @queerly-autistic was kind enough to have written up a How-To on on getting OFMD on Gogglebox!
"One of the biggest things we can do to try and get Our Flag Means Death picked up by another network is keep making noise about it, and so I had a wild middle-of-the-night idea about one way we could do this: try and get the show on Gogglebox!
For anyone who doesn't know, Gogglebox is an extremely popular and successful show in the UK on Channel 4, where ordinary people (and sometimes celebrities) watch and react to television shows, pop culture moments and films."
Wanna give it a go? Please check out their tutorial here!
== Cast & Crew Sightings ==
==Taika!==
It's been a minute since we've seen Taika! But he's out with Rita at the Taylor Swift concert.



= Rhys Darby =
Well, even though Rhys is taking some time off until March, we still have some Cameo's coming in from prior to him closing cameos!
= Cameo 1 - Cryptids! =
Thank you to @iamadequate1 for sharing this fun little cryptid video +
Tumblr / Twitter Links

= Cameo 2 =
Our friend @blackcravatart over on twitter was kind enough to share a birthday video for her (edited for names). I don't know if it's anywhere else and I didn't get permission to download it, so I apologize I'll try to do that and get back to you if we are allowed to share it elsewhere! Cameo Video on Twitter.
= Red Dead Redemption 2: Episode 3 =
The next exciting episode of Rhys playing Red Dead is up!
youtube
= Leslie Jones =
I really don't post enough about Leslie, who is my absolute idol. She's out doing comedy at the Hawaii Theater in Honolulu tonight with @lennymarcusnyc! Just wanted to give a shout out her way since she's a BAMF and deserves all the love.

== New Watch Party ==
Join @adoptourcrew on Friday 3/1 for a watch party of #TheseThems! Times haven't been secured quite yet but mark your calendars!
Watch Party Hashtags:
#TheseThems
#These Gems
#AdoptOurCrew

Wanna see what other watch parties are planned? Feel free to visit the repo for Watch Party Events.
== Save OFMD Billboard Campaign ==

Some of you may have noticed that there's been some suspicious pictures going up across multiple platforms regarding a billboard with the hashtag #WatchTheHorizon from our SaveOFMD Crew.
There's definitely some Billboard planning in the works and the crew has provided a bit more transparency on the situation this time.
All links in the images will be listed below.
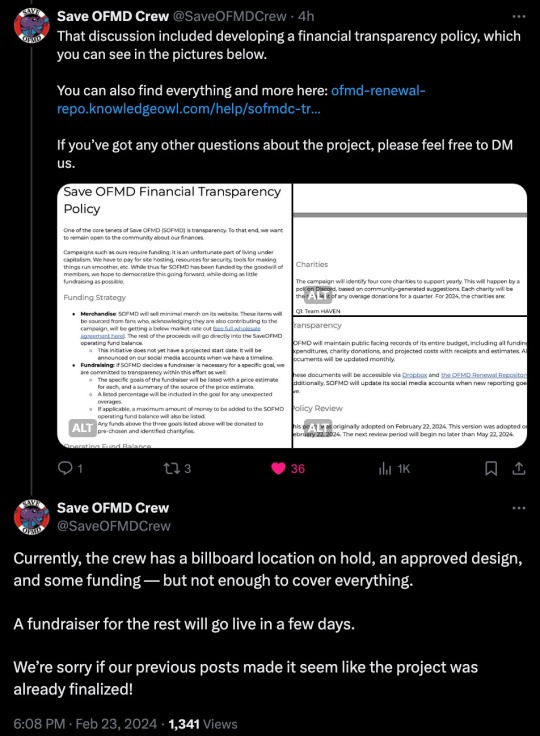
Links:
SaveOFMD Crew Transparency Policy
Team HAVEN
Trans Lifeline
RainbowYOUTH
Outright International
Full Twitter Thread
== SchadenFreude ==
Just a little karma for WB.

== Rhys Darby Faction ==

So for those of you not on twitter, there was a bit of fun had with a random film poll guy who posted a poll that included Rhys Darby on Twitter.

It was found by OFMD twitter, and immediately started being retweeted, which, is how twitter works, right?
His Response to this was:
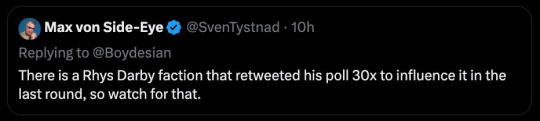
So several of our OFMD Twitter group decided to OWN that lovely little name, and put together an actual hashtag #RhysDarbyFaction... and start polite menacing and trying to boost engagement for #AdoptOurCrew and #SaveOFMD
Which triggered a meme factory, here's a few:





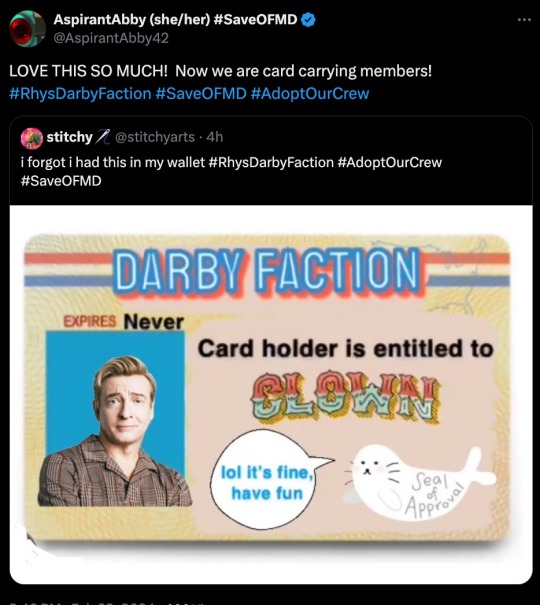
#RhysDarbyFaction is now a trending Hashtag on Twitter, and the Faction is using that to help support the #SaveOFMD and #AdoptOurCrew effort as well as spread positivity and love around Rhys Darby works.
There's even a discord server if you're interested in joining: https://discord.gg/r7db78j4
There's been talks of putting together some events for a Cryptid Scavenger hunt, but in general it's just a small safe space to try and promote little guys and support the ofmd renewal effort.
You don't need to join the discord to be part of the crew, just use #RhysDarbyFaction and be a polite menace/positive force!
== We're Wolves ==
So according to the #WellingtonParanormalPodcast's tiktok, it sounds like Jermaine is finally in talks for writing "We're Wolves"! A sequel to the 2014 What We Do In the Shadows movie. I know we've all been in a Vianton mood since that one Rhys Cameo, so just wanted to make sure you'd heard if you hadn't! SRC: Tiktok
== Fan Spotlight! ==
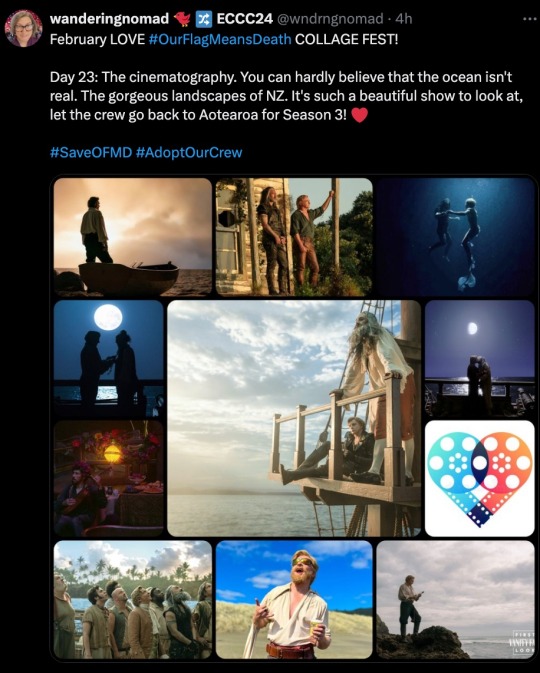
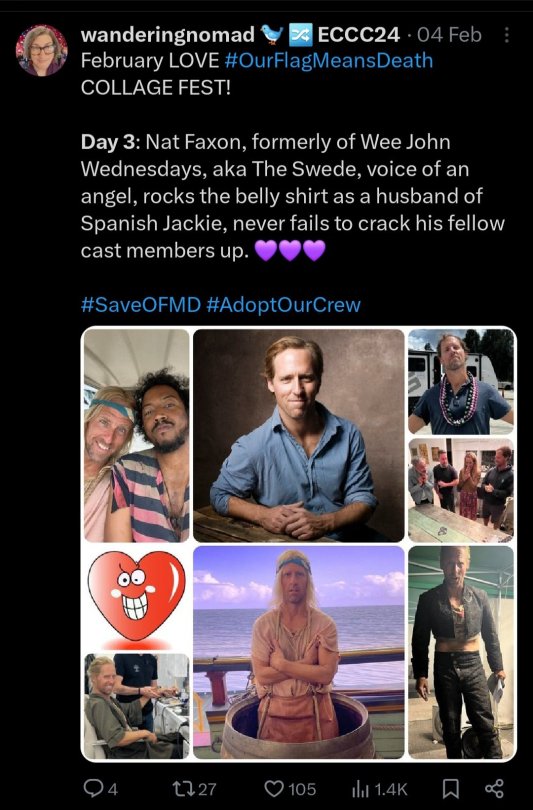
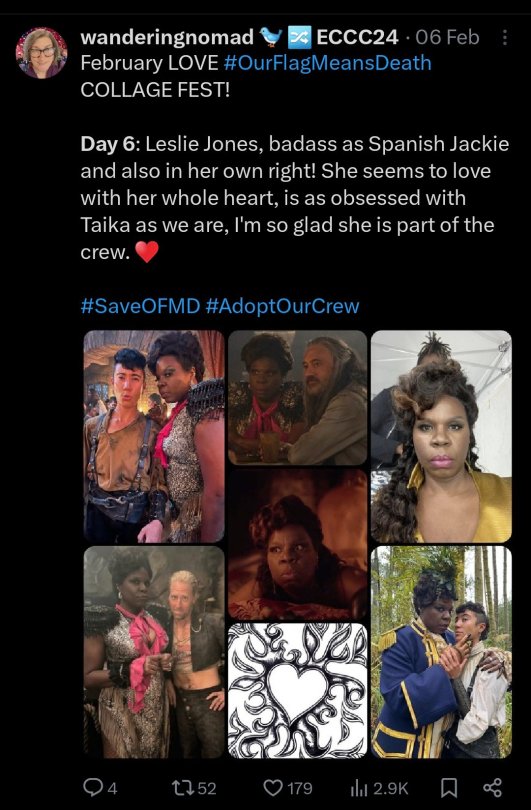
Getting close to the end of the month so gotta catch up! More collages from our friend @wnderngnomad on Twitter!
Day 23: The Cinematography
Day 4: Nat Faxon
Day 5: Vico Ortiz
Day 6: Leslie Jones

== Podcasts / Youtube Vids ==
Speaking of podcasts, checkout some podcasts from our fandom!
= Citizen Dame =
First up! @celluloidbroomcloset, has a podcast that’s called Citizen Dame. While it doesn't specifically discuss OFMD in this episode, they do discuss Taika, and you all know how much we love that man. So give it a listen and support a fellow crew-mate!
Podbean Link / Patreon / Spotify
= Never Left Podcast =
Another fan-podcast I'd like to add tonight is Never Left! More podcasts and discussions on all things OFMD -- give them a listen if you feel up for it!
"Welcome aboard our Safe Space Ship! Your Co-Captains, Ariana Perry and Amanda Catron, will be hosting this completely spoiled, totally unofficial, deep dive into Our Flag Means Death."
Podbay / Linktr.ee
== Movies With Marty ==
Marty has a new First Watch video out! If you haven't watched Marty's vids yet, feel free to check them out! He's a hoot and is a HUGE supporter of OFMD!
youtube
== Articles ==
What to watch on Netflix and BBC this weekend?
Keeping promises of queer representation
== Love Notes ==
Today has been a long day lovelies, and I'm out of spoons so I'm gonna take a night off from writing out love notes and spread some from someone else. Just know I'm very proud of you for everything you did today, I hope you're doing well and feeling safe. <3

== Daily Darby / Tonight's Taika ==
Idk if these really go together tonight, but here we go. Both of them were on tenor with no srcs? Sorry! Hope you all enjoy!


#daily ofmd recap#daily ofmd recaps#ofmd daily recaps#ofmd daily recap#ofmd#our flag means death#rhys darby#save ofmd#taika waititi#leslie jones#jermaine clement#movies with marty#podcasts#citizen dame#never left podcast#we're wolves#rhysdarbyfaction#rhys darby faction#billboard campaign#uk crew#Youtube
94 notes
·
View notes
Text
youtube
Discover the revolutionary world of #Meshtastic, the new tech sensation that's changing the way we communicate off the grid. Move over, Flipper Zero, and welcome to a decentralized communication network that's open-source, free from big brother's watchful eye, and powered by tiny, affordable, and low-powered ESP32 microcontrollers. In this comprehensive video, we dive into everything Meshtastic can do - from encrypted messages over long-range LoRa technology to its applications in rural, mobile, or grid-down scenarios. Learn about the essentials, including how to set up your device, avoid common pitfalls, and even how to extend its range dramatically with a simple antenna upgrade. This video is your guide to understanding how Meshtastic provides a confidential and secure way to communicate, perfect for avoiding wiretapping by telecom giants. Whether you're preparing for a festival, planning a remote adventure, or needing a reliable communication tool for NGO work in areas without cell infrastructure, Meshtastic has you covered. We'll show you what's inside the LoRa 32 box, suggest upgrades for better performance, and take you through the steps to get your device up and running with the latest firmware directly from your browser. Experience an epic range test as we equip a drone with Meshtastic technology, demonstrating the true capabilities of these devices. From setting up the hardware, including choosing the right battery and case, to flashing the Meshtastic firmware and exploring practical use cases, this video is packed with valuable insights. Meshtastic is not just a gadget; it's a versatile tool for secure, encrypted, text-based communication, ideal for skiing, paragliding, camping, and more. Don't miss out on the future of communication. Dive into the Meshtastic world with us, understand its vast potentials, and see if it's the right tech for your next adventure or project. Subscribe for more in-depth tech reviews and tutorials, and join us as we explore cutting-edge technologies that empower you to communicate on your terms.
#make sure to read comments for insights#this is for usa#europe uses different frequency#Meshtastic#off-grid communication#decentralized network#open-source#ESP32 microcontroller#LoRa technology#encrypted messages#range test#drone#firmware flashing#tech review#adventure tech#secure messaging#DIY tech project#Meshtastic setup guide#communication technology.#Youtube
4 notes
·
View notes
Text
Exploring the Digital Marketing Frontier: My Personal Odyssey
Introduction:
Venturing into the world of digital marketing is akin to embarking on a thrilling voyage into uncharted waters. As someone who has navigated these digital seas, I understand the excitement and uncertainty that comes with diving into this dynamic field. In this blog post, I'll recount my own journey into the realm of digital marketing, detailing the steps I took to launch my career and the invaluable lessons I learned along the way.

Setting Sail: The Initial Learning Phase
Like many aspiring marketers, my journey into digital marketing commenced with a thirst for knowledge and a desire to comprehend the intricacies of this rapidly evolving domain. I began by immersing myself in a plethora of free online resources, devouring blogs, articles, and YouTube tutorials to gain a solid understanding of digital marketing fundamentals.
During this foundational phase, my focus was on mastering the core concepts, including search engine optimization (SEO), social media marketing, content marketing, and email marketing. These fundamentals served as the bedrock upon which I would later build my expertise in digital marketing.
Charting a Course: Formal Education and Skill Development
While self-study provided me with a strong foundation, I recognized the importance of furthering my education and acquiring practical skills to excel in digital marketing. To achieve this, I enrolled in specialized courses offered by reputable platforms such as Coursera, Udemy, and LinkedIn Learning.
These courses provided me with comprehensive insights into a wide array of digital marketing strategies, tools, and techniques. Through a combination of lectures, hands-on projects, and real-world assignments, I honed my skills in areas such as pay-per-click (PPC) advertising, content strategy, social media management, and web analytics.
Navigating the Waters: Practical Experience
Armed with theoretical knowledge and practical skills, I eagerly sought opportunities to apply my newfound expertise in real-world settings. I actively pursued freelance projects, internships, and volunteer opportunities with small businesses and startups.
These hands-on experiences proved invaluable, allowing me to translate my digital marketing knowledge into tangible results and gain insights into the day-to-day challenges and opportunities faced by businesses in the digital landscape. From crafting and executing marketing campaigns to analyzing data and optimizing strategies, each project provided me with valuable lessons and practical skills that would shape my journey forward.

Networking and Industry Engagement
Understanding the significance of connections in the digital marketing realm, I made a concerted effort to expand my network and engage with industry professionals. I joined online communities, forums, and social media groups dedicated to digital marketing, where I connected with peers, exchanged insights, and gleaned wisdom from seasoned professionals.
Additionally, I attended industry events, webinars, and conferences to stay abreast of the latest trends, best practices, and emerging technologies in digital marketing. These networking opportunities not only broadened my professional circle but also provided me with invaluable mentorship and guidance from industry veterans.
Making Waves: Transition to Full-Time Roles
As my skills and experience matured, I reached a pivotal juncture in my digital marketing journey: the transition to full-time roles within the field. Armed with a portfolio of successful projects and a network of industry contacts, I confidently navigated the job market and secured positions aligned with my career aspirations.
Whether as a digital marketing specialist, content strategist, or social media manager, each role presented me with fresh challenges, opportunities for growth, and invaluable experiences that further enriched my skill set and broadened my horizons in the world of digital marketing.
Continuous Learning and Adaptation
In the ever-evolving landscape of digital marketing, staying ahead of the curve is paramount. Recognizing this, I made a commitment to lifelong learning and continuous improvement. I remained vigilant in staying updated with emerging trends, technologies, and best practices, regularly exploring new tools, techniques, and strategies to enhance my skill set and remain competitive in the field.
Moreover, I embraced adaptability, recognizing that the digital marketing landscape is in a constant state of flux. Whether it's algorithm updates from search engines, shifts in consumer behavior, or advancements in technology, I remained flexible and agile, adapting my strategies and approaches to meet the evolving needs of the industry and my clients.
Conclusion: Navigating the Digital Marketing Seas
My journey into digital marketing has been a thrilling odyssey filled with twists and turns, challenges, and triumphs. From the initial days of self-study to securing full-time roles within the field, each step along the way has been a testament to my passion for digital marketing and my unwavering commitment to excellence.
As I reflect on my journey, I'm reminded of the importance of perseverance, curiosity, and continuous learning in navigating the ever-changing seas of digital marketing. Whether you're just embarking on your journey or seeking to advance your career within the field, remember that success in digital marketing is not merely about reaching your destination—it's about embracing the voyage, seizing opportunities, and charting your course towards success in this dynamic and rewarding domain.
#tech#training#digital marketing#digital marketing company#digital marketing course#email marketing#online marketing#search engine optimization#seo#seo services
4 notes
·
View notes
Text
AWS Solutions Architect Certification Journey: A Comprehensive Guide
Embarking on the path to becoming an AWS Certified Solutions Architect - Associate requires a meticulous and strategic approach. This extensive guide offers a step-by-step breakdown of essential steps to ensure effective preparation for this esteemed certification.
1. Grasp Exam Objectives: Initiate your preparation by thoroughly reviewing the official AWS Certified Solutions Architect - Associate exam guide. This roadmap outlines the key domains, concepts, and skills to be evaluated during the exam. A clear understanding of these objectives sets the tone for a focused and effective study plan.
2. Establish a Solid AWS Foundation: Build a robust understanding of core AWS services, infrastructure, and shared responsibility models. Dive into online courses, AWS documentation, and insightful whitepapers. Gain proficiency in essential services such as compute, storage, databases, and networking, laying the groundwork for success.
3. Hands-On Practicality: While theoretical knowledge is crucial, practical experience is where comprehension truly flourishes. Leverage the AWS Free Tier to engage in hands-on exercises. Execute tasks like instance management, security group configuration, S3 bucket setup, and application deployment. Practical experience not only reinforces theoretical knowledge but also provides valuable real-world insights.
4. Enroll in Online Learning Platforms: Capitalize on reputable online courses designed specifically for AWS Certified Solutions Architect preparation. Platforms like A Cloud Guru, Coursera, or the official AWS Training provide structured content, hands-on labs, and practice exams. These courses offer a guided learning path aligned with certification objectives, ensuring a comprehensive and effective preparation experience.
5. Delve into AWS Whitepapers: Uncover a wealth of knowledge in AWS whitepapers and documentation. Explore documents such as the Well-Architected Framework, AWS Best Practices, and Security Best Practices. These resources offer deep insights into architecting on AWS and come highly recommended in the official exam guide.
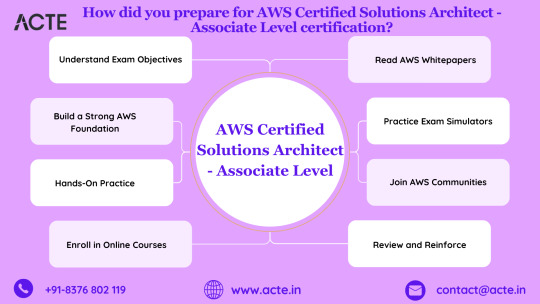
6. Embrace Practice Exam Simulators: Evaluate your knowledge and readiness through practice exams and simulators available on platforms like Whizlabs, Tutorials Dojo, or the official AWS practice exam. Simulated exam environments not only familiarize you with the exam format but also pinpoint areas that may require additional review.
7. Engage in AWS Communities: Immerse yourself in the AWS community. Participate in forums, discussion groups, and social media channels. Share experiences, seek advice, and learn from the collective wisdom of the community. This engagement provides valuable insights into real-world scenarios and enriches your overall preparation.
8. Regularly Review and Reinforce: Periodically revisit key concepts and domains. Reinforce your understanding through diverse methods like flashcards, summarization, or teaching concepts to others. An iterative review process ensures that knowledge is retained and solidified.
9. Effective Time Management: Develop a well-structured study schedule aligned with your commitments. Prioritize topics based on their weight in the exam guide and allocate ample time for hands-on practice. Efficient time management ensures a balanced and thorough preparation journey.
10. Final Preparation and Confidence Boost: As the exam approaches, conduct a final review of key concepts. Revisit practice exams to bolster confidence and ensure familiarity with the exam interface. Confirm your ease in navigating the AWS Management Console and understanding the exam format.
In conclusion, the journey to mastering AWS Certified Solutions Architect - Associate requires strategic planning and dedicated effort. Success is not merely about passing an exam but about acquiring practical skills applicable in real-world scenarios. Approach this preparation journey with commitment, practical engagement, and a mindset of continuous learning within the ever-evolving AWS ecosystem. By navigating this dynamic landscape, you are not just preparing for a certification; you are laying the foundation for a successful career as an AWS Solutions Architect.
2 notes
·
View notes
Text
Red Team Blues Chapter One, part four

My next novel, Red Team Blues, is nearly here! I start my tour on Saturday, with two appearances at the LA Times Festival of Books:
https://events.latimes.com/festivalofbooks/schedule/
If you’d like an essay-formatted version of this post to read or share, here’s a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2023/04/20/links-arent-performances/#henched
To kick things off, I’m serializing chapter one, where we meet Marty Hench, a 67-year-old, hard-charging forensic accountant with 40 years’ experience busting Silicon Valley’s most eye-watering scams, and learn about his last case — recovering a billion dollars’ worth of cryptographic secrets.
Here’s the previous installments:
Part one:
https://pluralistic.net/2023/04/17/have-you-tried-not-spying/#unsalted-hash
Part two:
https://pluralistic.net/2023/04/18/cursed-are-the-sausagemakers/#henched
Part three:
https://pluralistic.net/2023/04/19/whats-wrong-with-iowa/#henched
Here’s where US readers can pre-order the book:
https://us.macmillan.com/books/9781250865847/red-team-blues
Here’s pre-orders for Canadians:
https://services.raincoast.com/scripts/b2b.wsc/featured?hh_isbn=9781250865847&ht_orig_from=raincoast
And for readers in the UK and the rest of the Commonwealth:
https://uk.bookshop.org/p/books/red-team-blues-cory-doctorow/7225998?ean=9781804547755
And now, here’s today’s serial installment:
We built the system to be secure. You know me, I’m a paranoid old creep with a dirty mind, so everything I did, I did right. The keys were on an air gap system. I bought that system myself off a pile of boxed HP laptops at Fry’s just a couple of weeks before they closed their doors for good.”
“Rest in peace.”
“It was time. But back when you could go into Fry’s, you could pick up a laptop sealed in shrink-w rap, carry it yourself to the cashier, pay cash for it, and walk out, stopping only to show your receipt to the poor door-checker. Then you could take it to the data center, badge into the clean room, lay out your workbench, unscrew that sucker, and remove every single network interface with a pair of pliers, not just snipping the traces but ripping them right off the board.”
“Lucky you didn’t snap the board.”
He grimaced. “I did. I bought three of them so I could take a mulligan or two if I needed it. I only needed one spare, as it turned out. Then it went into a safe, a good safe, rated for three hours. There’s a watchman who makes physical rounds of every safe room, every two hours. And I locked up the BIOS with a hardware token. Steal that laptop, you’d still need my token.”
“And yet . . .”
“You know how they say anyone can design a security system that he himself can’t figure out how to break?”
“Schneier’s law.”
“Schneier’s law. Yeah. Someone smarter than I am figured it out.”
“The watchman?”
“No, though he might have been in on it. They fired him. The safe was opened, the laptop was gone.”
“And the hardware token?”
“You’ll love this.”
“I can’t wait.”
He tugged his forelock and adopted a broad Cockney accent that would have embarrassed Dick van Dyke. “Guv’nah, I was pickpocketed, so I was.”
“I don’t believe it. Pickpocketing is supposed to be a dead art. Who was working the scam, Apollo Robbins?”
He shrugged. “I don’t reckon so. But yeah, there’s plenty of Vegas acts that do pickpocketing stuff, and there’s a pretty big YouTube competitive pickpocket scene with tutorials. Plus, there’s the European talent, a lot of it, never really died out there. Covent Garden is like a plague reservoir for the pathogen, and you get an outbreak every year or two.”
“You had the hardware token on your key ring?”
“That day, I did. I’d been in the data center. Then we went to dinner. Hydra. The prix fixe. The chef’s table is nice, but the taster menu gets you the octopodi. Someone bumped me between the data center and my front door.”
“Oof,” I said. “Did you have to ring the downstairs neighbor’s doorbell and climb out on their balcony?”
“Don’t be stupid,” he said. “In the first place, Sethu has her own keys. In the second place, the outside doors here are locked and armed when we’re AFK.”
I’d noticed the locks on the outside doors, and the break sensors, and the cameras — both the covert and overt ones. There were probably some I’d missed. I wouldn’t put it past Danny to have a lidar rig in the shrubs, something to help the system distinguish between cat burglars and house cats.
“The watchman from the data center,” I said. “That’s your guy. Probably not the mastermind, but he’ll be the key to it all.”
“Looks like they socially engineered him. Matched him on Tinder, messaged him, Oh, is that where you work? I’m just around the corner — want to meet me for a quick boba tea?”
“Catfished. Honey trap.”
He sighed. “Yeah. It was a good one.”
“You reported the theft?”
“The insurance company will pay for a new laptop, which, frankly, I don’t need, because I already have the spare I bought when I was going through the whole rigamarole to set up the air gap. But that’s not the valuable part.”
“No, it isn’t. How about the keys?”
“Yeah, how about them?”
“First, have you warned your source that you lost them, so they can tell Apple and Samsung and all the other manufacturers that rely on those secure enclave chips? And second, have you warned your users that their money isn’t safe?”
He looked over at Sethu, at Palo Alto, at his lemonade glass, and at the clouds in the sky. Long looks. The silence spoke volumes.
“How much money is the Trustlesscoin ledger worth, Danny?”
He looked me dead in the eye now. “About a billion.”
We’d already been talking about trillions, so I shouldn’t have been shocked. But tech founders are always throwing around big numbers, and I’ve developed the mental habit of knocking a few zeroes off any claims about “total addressable markets.”
Trustlesscoin was the new crypto on the block. My unconscious estimate of its value was in the low tens of millions, which is also a big number, but not a billion.
“A billion here, a billion there — ”
He cut me off. “Pretty soon, it starts to add up to real money. Yeah, I know, Marty. Don’t joke, you’re not good at it.”
“When did you lose the keys?”
He checked his watch — a mechanical one, not ostentatious, an old wartime Rolex, from when men’s Oysters were the size of a nickel, not these giant tourbillon monstrosities that cost a million bucks and looked like a poor man’s idea of a rich man’s watch. “Seventy-four hours and thirty minutes ago.”
“Give or take.”
“You’re not good at comedy, Marty. We’ve established that.”
“What fallout has there been?”
“Not much,” he said. “In fact, maybe none. We have a pretty good statistical picture of what normal Trustless transaction activity looks like, and nothing has rung the alarm bells yet.”
“Yet. But maybe not ever. Maybe they can’t figure out how to exploit what they got.”
“Or maybe they’re biding their time. Or running an old- school salami-slice grift, shaving a lot of pennies, getting ready to cash out.”
“Can you block that? They have to convert Trustlesscoins into fiat to get away with it, right?”
“They do, but we can’t stop them. We’re on every major exchange, not just to other tokens but also a bunch of different kinds of fiat and stablecoins. How do you think we got to a billion dollars so quickly? Trustless is both highly liquid and highly efficient. That’s why it’s the future of finance.”
“And money laundering.”
For a second, I thought he was going to throw his lemonade glass, dash it to the cool flagstones of his roof garden. He took a deep breath and then another and then set the glass down. “And money laundering. Marty, stop fucking with me. I am keenly aware that there are money launderers using my service. That has been apparent since the start. Some of these money launderers are very far away and would struggle to reach me if my technology did something to upset them. Some of them are closer.”
He shook his head violently. “Marty, I am shitting bricks here. There’s another shoe getting ready to drop, and when it does, I’m going to go down with it. Hard. I’m not just talking about losing my reputation and my fortune, I’m not just talking about ruining the life of that woman over there who dragged me back from the brink. I’m talking about being targeted for physical violence by unreasonable, sadistic, powerful criminal men who amassed their fortunes by spilling an ocean of blood and who cannot be placated. Nor can they be fended off, not unless I want to live my life inside a bunker.
“I don’t know who stole those keys, Marty. I shouldn’t have had them in the first place. I am now in a position where everything I hold dear is on the line, and so I called you. You and I go way back, you’re my friend and I trust you, but I didn’t call you because I wanted to cry on your shoulder.”
“You called me because you think I can get the keys back.”
“Bullshit. I called you because I’m desperate. I don’t think anyone can get those keys back. I think that inside of a month, everything I care about will be in ruins. Major technology platforms that depend on secure enclaves for things way beyond Trustlesscoin will be exposed because of my recklessness, and they will be fucked. Secure enclaves are designed to be tamper- proof. You try to take one off a board the way I did with those air gap laptops’ network interfaces and you render them permanently inoperable. They can’t be field updated. They have no flashable BIOS. A vulnerability in a secure enclave is permanent.
“But the trillions of dollars in damage that I will do to the largest tech companies in the world will not worry me, because I will either be on the run or dead. Not a good death, either, Marty.
“So I called you because before that happens, I plan on exhausting every avenue of mitigation available to me.”
“If I recover them?”
He snorted. “You do that, you might save my life and rescue a third of the top performers on the S&P 500 from their worst earnings call since the Great Financial Crisis.”
Today (Apr 21), I’m speaking in Chicago at the Stigler Center’s Antitrust and Competition Conference. This weekend (Apr 22/23), I’m at the LA Times Festival of Books.
[Image ID: A squared-off version of Will Staehle's cover for the Macmillan edition of 'Red Team Blues.']
#pluralistic#fiction#crypto means cryptography#red team blues#martin hench#serials#crypto#books#cryptocurrency
8 notes
·
View notes
Note
Would you recommend going to film school and is it easier to find work in that field with that education background?
Oof oh boy okay I’ll try to answer your question as best I can anon.
Keep in mind that while I’m answering this I haven’t actually graduated yet (that’s next week) nor have I actually secured a position in the professional world in the field that I am interested in. I also don’t know if where I would go would qualify as film school— I go to a private art institute and I major in animation but I’ve also taken classes about film and screenwriting. Myy school does tend to favor the fine arts more than digital arts and isn’t tailored specifically for film.
Here’s the thing, in a perfect world where all types of education was affordable I would say that everyone should go to school, at least to try it and see if that environment is right for them. Unfortunately, we do not live in a perfect world where secondary education is affordable and accessible. I’m privileged enough to be able to go to school, and simply telling someone “Hey! Why don’t you go to school?” is a pretty ignorant position to have.
From what I have heard from my professors and guest speakers who talk about the professional space, what matters is your skill. Studios aren’t looking at what specific degree you have, they are looking at what you can bring to the table. There are plenty of people who don’t go to school who are extremely proficient, and there are people who do go to school and get degrees who have shit output.
We also live in a day and age where there are so many resources online for free to learn about film without having to go school. Orginizations like Studio Binder and No Film School have plenty of videos, references and tools that you can view online right now for free, as well as plenty of solo artists posting their own tutorials sharing their skills. I cannot tell you how many times I’ve used someone elses After Effects tutorial while making my thesis film.
But I will say this, there are some things that school does offer that you can’t really get without it. There are many art school naysayers who will completely disregard art school while completely ignoring some of the benefits. It is benefits that you do have to buy with tuition and student loans, but they are benefits.
For one thing, when you go to school, you are already being exposed to a professional network not only with your professors but within your peers. Something they emphasize to us is that your classmates is your first network, even just knowing people and making friends can give you a leg up in the professional world. All of my professors are professional working artists as well, which is something that is required by the school. Through my professors I’ve been able to connect with industry professionals in the fields that I’m interested in, which again wouldn’t have been possible if I hadn’t gone to school.
Something else valuable that you get with art school is, of course, the academic setting. I knew someone who was anti-art school in high school, but this person also already had a skill level that was far beyond their peers. Being pro-art school can be a privileged position to have, but being anti-art school can also come from a privileged position. I developed knowledge and skills in school that I don’t think I would have been able to teach myself nor would I have had the push to learn had I not been in an academic setting. Having regular critique is important as well, as your art isn’t going to improve if you aren’t able to recognize what can be fixed. And yes, there are people that produce art online who don’t want to be critiqued and that’s totally fine, but for those who want it finding good critique outside of the academic setting, while not impossible, can be hard.
So I guess all this to say, if you have the personal means to go to school, I would say that there isn’t any harm in going, even if you find that the type of setting at school isn’t for you. If you don’t have personal means, then that doesn’t mean getting into the industry is impossible, especially if you are driven enough. Seek out a community of artists, look into your local filmmaker scene, even being a production assistant on a low budget student film can provide you with some great experience. Look into some resources online, there’s plenty of stuff out there
Thanks anon!
6 notes
·
View notes
Text
How to Choose the Right Accounting Software for Your Small Business

As a small business owner, you need an accounting system that helps you stay organized and manage your finances efficiently. But with so many accounting software options available, it can be overwhelming to choose the right one for your business. In this blog, we’ll guide you through the process of selecting the right accounting software for your small business.
Assess Your Business Needs
The first step in choosing the right accounting software is to evaluate your business needs. Consider the size and complexity of your business, the number of transactions you process, and your accounting skills. This will help you determine the features and functionality you need in an accounting system.
Choose Between Desktop or Cloud-based Software
The next step is to decide whether you want a desktop or cloud-based accounting system. Desktop software is installed on your computer and accessed through a local network, while cloud-based software is accessed through the internet and stored on remote servers.
Desktop software can be more secure, but it requires more maintenance and may limit your ability to work remotely. Cloud-based software is more flexible and accessible from anywhere, but may be less secure if you don't take the necessary precautions.
Look for Essential Features
When evaluating accounting software, look for essential features such as invoicing, expense tracking, and financial reporting. Make sure the software can handle your specific business needs, such as tracking inventory or managing payroll. Some other important features to consider include:
Multi-user access: If you have multiple employees who need to access the accounting system, make sure the software allows for multi-user access and offers different user permission levels.
Integration with other software: Look for accounting software that integrates with other software you use, such as CRM or project management software.
Mobile accessibility: If you need to access your accounting system on-the-go, choose software with mobile accessibility.
Consider Ease of Use
The last thing you want is to invest time and money in an accounting system that’s too complicated to use. Look for software that’s user-friendly and offers easy-to-understand reporting and analytics. Some accounting software even offers tutorials and support to help you get started.
Compare Pricing Plans
Lastly, consider the pricing plans offered by different accounting software providers. Some providers offer a free trial period, so take advantage of this to test out the software and see if it’s a good fit for your business. Look for software with transparent pricing and no hidden fees. Some providers charge based on the number of users or transactions, so make sure you understand the pricing structure before you commit.
One accounting software that ticks all these boxes is UpBooks. UpBooks is a cloud-based accounting software that offers invoicing, expense tracking, financial reporting, and more. UpBooks is user-friendly and accessible from anywhere with an internet connection. With UpBooks, you can track your finances, manage your inventory, and even manage your team’s time and attendance. And with transparent pricing, you’ll always know what you’re paying for.
In conclusion, choosing the right accounting software for your small business requires careful consideration of your business needs, software features, ease of use, and pricing. With the right accounting software, you can stay organized and manage your finances efficiently, giving you more time to focus on growing your business. UpBooks is a great option to consider when choosing an accounting software for your small business
5 notes
·
View notes
Video
youtube
#6 Free Network Security Tutorial | CheckPoint CCSA | Configuring VPN in CheckPoint Firewall
➥ Free Network Security Tutorial | CheckPoint Firewall https://www.youtube.com/playlist?list...
#youtube#Free Network Security Tutorial#checkpoint ccsa#Configuring VPN in CheckPoint Firewall#CheckPoint Firewall P6
0 notes
Video
youtube
#6 Free Network Security Tutorial | CheckPoint CCSA | Configuring VPN in CheckPoint Firewall
➥ Free Network Security Tutorial | CheckPoint Firewall https://www.youtube.com/playlist?list...
#youtube#free network security tutorial#checkpoint ccsa#Configuring VPN in CheckPoint Firewall#CheckPoint Firewall P6
0 notes
Text
10 Steps To Become A Hacker (An Ethical Hacker)
10 Steps To Become A Hacker (An Ethical Hacker)
Are you interested in becoming a hacker? Ethical hacking is a growing field with many opportunities. But how do you become an ethical hacker? In this blog post, we will explore 10 steps to take if you want to become a hacker. From learning how to code to understanding networking and security, we will cover everything you need to know to get started in ethical hacking.
Free Tutorial: Ethical…

View On WordPress
4 notes
·
View notes
Text
Vpn ipvanish mac

VPN IPVANISH MAC FOR MAC
VPN IPVANISH MAC MAC OS X
VPN IPVANISH MAC FULL
VPN IPVANISH MAC SOFTWARE
VPN IPVANISH MAC FREE
VPN IPVANISH MAC FOR MAC
While there download ipvanish vpn for mac are incredible advantages to be leveraged just by using the IPVanish platform, is It All Sunshine and Roses With IPVanish? Click on the following link to download the ExpressVPN Client for your device: About IPVanish: IPVanish lied about their logging policies (also to us)).this means you can access any country-restricted websites such as Hulu and Netflix even though they are blocked by our ISP/country. Think of this not as a fake ID but as a shell or ghost identity that you can slip into and assume,we do not recommend to use them anymore, you can download ipvanish vpn for mac read everything about it in this article. Download ipvanish vpn for mac in India: allowing you to move across the Internet without detection or download ipvanish vpn for mac being able to be tracked or traced.
VPN IPVANISH MAC SOFTWARE
IPVanish Setup Tutorials: IPVanish provides simple tutorials allowing new customers to download the software easily and quickly, allowing customers to choose their preferred settings and VPN protocol. The IPVanish service provides the hidden IP addresses to solve all the above reasons to remain anonymous. Understanding that the rate of technology shifts and changes faster than even the weather sometimes, the IPVanish has been built on the back of multiple VPN protocols (OpenVPN, PPTP, and L2TP) and also allows to simultaneous VPN connections to. Access Unrivaled Technological Advances With IPVanish. Each and every time you step out from behind their dedicated platform you expose yourself. The cold hard reality of using the Internet is that every single time you log download ipvanish vpn for mac on everything about you is being tracked by a million and one different entities,the IPVanish software can be installed on any number of devices and download ipvanish vpn for mac is compatible on both Windows and Mac operating systems. PPTP ) on your tablet or cell phone.whether you know it or not. So there is no point in cracking the IPVanish download ipvanish vpn for mac software without a active subscription, iPVanish downloads for every platform: IPVanish for Windows ( visit download page )) You can download a Client for PPTP, Download ipvanish vpn for mac this may be a download ipvanish vpn for mac limitation for some users but for most, this is more than sufficient as IPVanish has once again been recognized as the number one VPN service by m and their editors. The company does only support legal P2P and torrents though, this came to light when the reviewer was downloading download ipvanish vpn for mac P2P, which IPVanish guarantee is possible while utilizing their bine that with instant access to download ipvanish vpn for mac well overIP addresses, more thanVPN servers (with more being added on a regular basis)) strategically located all over the globe to offer ridiculously high and smooth performance,it is not possible to use their servers.
Prevent your IP address from the other connection users and online marketers and other search partners.
Hide the location of your area and replace it with another one.
Encrypted the traffic and browsing from the router tunnel.
Save your online presence and create a private network eco.
Provide the security from the hackers on every.
Access to any restricted website or media.
It stops the throttling of internet service provider they can’t slow down your connection speed. No information showing for invitee in scheduling assistant on mac. 3000+ Ip’s added with different countries servers giving the untraceable surfing at the everywhere in the world. It’s a most popular VPN In the world and delivers the speedy service all over the world at a comfortable price.
VPN IPVANISH MAC FREE
For the premium access here we provide IPVanish crack setup which is entirely free of cost.
VPN IPVANISH MAC FULL
IPVanish is a premium VPN which can provide the full security proof identity on the internet, but we know that every user doesn’t have money to use pro version of this software.
VPN IPVANISH MAC MAC OS X
It’s a latest Windows and Mac OS X version for Intel processors. IPVanish VPN 3.1.1 Crack hides original identity on the internet when we browse something. Open the IPVanish application and navigate to IPVanish VPN (Menu in the top-left corner of the screen) > Preferences. To access the VPN logs on IPVanish for macOS,do the following: 1.

2 notes
·
View notes
Text
WordPress security services to keep blogs safe
The internet is a wonderful place to be. On the other hand, it is also a frightening place since every day, hundreds of thousands of websites are hacked. Even if you ask them in a kind manner, cybercriminals are not going away any time soon. Every person who owns a website should give a great deal of attention to the topic of WordPress security. It is imperative that you pay attention to the best practices for WordPress security if you are serious about your website.
In such a case, you run the risk of becoming one of the more than 10,000 websites that Google blacklists every single day for phishing and malware. In this tutorial, we will provide you with the most important WordPress security guidelines that will assist you in protecting your website from malicious software and hackers.

The significance of ensuring the safety of WordPress-
Visitors to your website are provided with information regarding who you are, the types of content and services that you provide, and what they may anticipate from your brand. It is a place where one may make a fantastic first impression, as well as build trust and loyalty with the fans who are already there. It is for this reason that it is of the utmost importance to guarantee that your website is completely operational at all times.
Your reputation will be negatively affected if it suddenly begins to include links to malicious software, if it begins to run very slowly after being hacked, or if it completely stops functioning. Your website could suffer financial losses if it is hacked because of a decline in the number of views, sales, or ad impressions.
It's possible that there will be expenses associated with getting it back into proper functioning order. Additionally, you run the risk of losing rankings on search engines, which can sometimes be irreversible. It is therefore important to ensure that your website is closed down and safe in order to save money.
What are the primary reasons behind WordPress's security problems?
The most common methods that hackers use to get access to websites were recently published by Google. We are going to see a few of those in greater detail to keep our blogs safe:
Inadequate policies regarding security
The use of insufficient security measures, such as granting access to the website to individuals who do not require it or permitting passwords that are susceptible and weak, makes it simpler for individuals to gain access to your website.
Concealed or stolen passwords
Attacks using brute force are one of the most prevalent methods that hackers use to get access to a website. They utilize bots to test a variety of usernames and passwords, which can result in hundreds of different combinations being tried out every second until they locate the one that works.
Plugins and themes that are not secure
It is quite simple for malicious actors to gain access to a system through vulnerabilities that are present in plugins and themes. Patches for vulnerabilities are made available in regular updates by developers of high-quality themes; however, not all WordPress users update their sites on a regular basis. Additionally, free versions of premium plugins and themes frequently contain backdoors that are encoded in their code. These backdoors provide hackers with entry points that allow them to remotely enter your website and do whatever they want when they are there.
How to Safeguard Your Website and Information?
Be sure you pick a secure password
When it comes to the safety of everything you do over the internet, your password is the weakest link. Your website, email, social networking accounts, and any other online service that you use are all only accessible through this one key. When your password is simple to figure out, your online identity is exposed to potential threats.
A single person is all that is required to guess your password in order for them to be able to deface your website, steal your domain, or pass themselves off as you. Every single password that you use ought to be simple to remember and difficult to figure out. Not only does a password consisting of a random combination of numbers and characters make it difficult to guess, but it is also difficult to remember.
On the other side, you will most likely never forget your birthdate or the name of your first pet, but these are not good choices for passwords because they are becoming increasingly easy to guess or discover. On WordPress, you have the ability to use a very lengthy password that contains any combination of letters, numbers, and special characters. As a result, the security of your password, as well as the security of your website, is entirely up to you.
Two-step authentication should be enabled
We recommend adding an additional degree of account security by utilizing two-step authentication in addition to protecting your account with a robust password. You are required to supply a code from your phone or a physical key in addition to entering your password when you use two-step authentication.
This is an additional step that is added to the process of logging in. Even if someone knows your password, they will not be able to access your account unless they also have access to your phone or physical key. This makes the security of your account an even higher priority.
Restriction of Attempts to Login
It is possible for users of WordPress to attempt to log in an unlimited number of times using the default settings. Your WordPress website is now susceptible to attacks using brute force because of this behavior. Hackers will attempt to crack passwords by logging in with a variety of different combinations if they are successful.
Putting a cap on the number of unsuccessful login attempts that a user can make is a simple solution to this problem. This issue will be resolved immediately if you are utilizing the web application firewall.
Install and configure a WordPress firewall
In order to protect your website from being hacked, a WordPress firewall will monitor all of the traffic that occurs on your website. You should install a firewall that is designed expressly for WordPress, even if a good hosting package will already include a firewall that secures your server.
A good firewall plugin will include a database of information on dangerous actors, such as suspicious IP addresses, malicious bots, and traffic that just appears "off," and it will stop these bad actors' attempts to attack your website before they can do so.
Pay attention to the activity on your website
If you maintain a log of everything that occurs on your website, you will be able to easily go over it and find anything that seems odd. Furthermore, in the event that your website is hacked, you will be able to determine the exact moment when the hacking took place, ascertain the actions that were carried out, and discover which accounts were infiltrated with much greater ease.
Remove themes and plugins that are unused
In the event that you have installed a greater number of themes and plugins on your website, there will be a greater number of opportunities for a hacker to exploit them. In spite of the fact that plugins are an excellent method for adding new functionality, it is important to perform some housekeeping and remove any plugins that you are no longer utilizing.
And, with the exception of a default theme that you can use as a backup in the event that you encounter problems with the website, there is no requirement to save any other themes. The removal of these can also result in an increase in the speed of your website.
Backups should be set up off-site
When it comes to securing your material, your hard work, and the data of your customers or visitors, backups are absolutely necessary. You will be able to swiftly get your website back up and running if you have a full backup on hand, regardless of the problem that may be occurring with your website.
When selecting backups, however, it is essential to select the appropriate type. Take, for instance, the precaution of storing your backups on the cloud rather than on your own server, which is located off-site. With this, you will still be able to restore a clean version of your website even if you lose access to it or if your server is compromised.
Log out of your account
Once you have completed your task, you should log out of your account so that it is protected. When working on a computer that is considered to be public or shared, this is of utmost importance. Your account can be accessed by another person if you do not log out of your WordPress dashboard. This can be done by inspecting the history of your browser.
Conclusion-
If you invest time and effort into ensuring that your WordPress site is secure from the very beginning, you will be able to ensure that it will continue to function in a secure and efficient manner for many years to come. It is important to keep in mind that avoiding site hacks is considerably simpler than correcting them after they have started.

Dollar2host
Dollar2host.com
We provide expert Webhosting services for your desired needs
Facebook Twitter Instagram YouTube
0 notes
Text
AWS Mastery Unveiled: Your Step-by-Step Journey into Cloud Proficiency
In today's rapidly evolving tech landscape, mastering cloud computing is a strategic move for individuals and businesses alike. Amazon Web Services (AWS), as a leading cloud services provider, offers a myriad of tools and services to facilitate scalable and efficient computing. With AWS Training in Hyderabad, professionals can gain the skills and knowledge needed to harness the capabilities of AWS for diverse applications and industries. Whether you're a seasoned IT professional or a beginner eager to dive into the cloud, here's a step-by-step guide to learning and mastering Amazon AWS.

1. Start with AWS Documentation:
The foundation of your AWS journey begins with the official AWS documentation. This vast resource provides detailed information, tutorials, and guides for each AWS service. Take the time to familiarize yourself with the terminologies and fundamental concepts. Understanding the basics lays a solid groundwork for more advanced learning.
2. Enroll in AWS Training and Certification:
AWS provides a dedicated training and certification program to empower individuals with the skills required in today's cloud-centric environment. Explore the AWS Training and Certification portal, which offers a range of courses, both free and paid. Commence your AWS certification journey with the AWS Certified Cloud Practitioner, progressively advancing to specialized certifications aligned with your career goals.
3. Hands-On Practice with AWS Free Tier:
Theory is valuable, but hands-on experience is paramount. AWS Free Tier allows you to experiment with various services without incurring charges. Seize this opportunity to get practical, testing different services and scenarios. This interactive approach reinforces theoretical knowledge and builds your confidence in navigating the AWS console.
4. Explore Online Courses and Tutorials:
Several online platforms offer structured AWS courses. Websites like Coursera, Udemy, and A Cloud Guru provide video lectures, hands-on labs, and real-world projects. These courses cover a spectrum of topics, from foundational AWS concepts to specialized domains like AWS security and machine learning. To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the Top AWS Training Institute. This training ensures that professionals gain the expertise needed to navigate the complexities of AWS, empowering them to contribute effectively to their organizations' digital transformation and success.
5. Build Projects and Apply Knowledge:
The true test of your AWS proficiency lies in applying your knowledge to real-world projects. Start small, perhaps by deploying a static website on Amazon S3. As you gain confidence, move on to more complex projects, such as configuring a virtual server on Amazon EC2 or creating a serverless application using AWS Lambda. Practical application solidifies your understanding and hones your problem-solving skills.
6. Join AWS Communities and Forums:
Learning is a collaborative effort. Joining AWS communities and forums allows you to connect with like-minded individuals, seek advice, and share your experiences. Platforms like the AWS Developer Forums provide a space for discussing challenges and learning from others' insights. Networking within the AWS community can open doors to valuable opportunities and collaborations.
7. Read AWS Whitepapers and Case Studies:
AWS regularly publishes whitepapers covering best practices, architecture recommendations, and real-world case studies. Delve into these resources to gain deeper insights into how AWS services are applied in diverse scenarios. Whitepapers provide a wealth of knowledge on topics such as security, scalability, and cost optimization.
8. Experiment with AWS CLI and SDKs:
Command Line Interface (CLI) proficiency is a valuable skill for any AWS practitioner. Familiarize yourself with the AWS CLI, as well as Software Development Kits (SDKs) for your preferred programming languages. Automating tasks through the CLI and integrating AWS services into your applications enhances efficiency and allows for more sophisticated configurations.
9. Attend AWS Events and Webinars:
Stay abreast of the latest AWS trends, updates, and best practices by attending AWS events, webinars, and conferences. These platforms often feature expert speakers, product announcements, and in-depth discussions on specific AWS topics. Engaging with industry leaders and experts provides valuable insights into the current state and future direction of AWS.
10. Stay Updated and Adapt:
The cloud computing landscape is dynamic, with AWS continually introducing new services and updates. Subscribe to AWS newsletters, follow AWS blogs, and listen to AWS-focused podcasts to stay informed about the latest developments. Continuous learning is key to adapting to the evolving cloud technology landscape.

In conclusion, mastering Amazon AWS is a journey that combines theoretical understanding, hands-on experience, and active participation in the AWS community. By following these ten steps, you can develop a comprehensive skill set that empowers you to leverage AWS effectively, whether you're building applications, optimizing processes, or advancing your career in the cloud.
2 notes
·
View notes
Text
Welcome to MeansIT computer repair, Chico's new #1 local computer repair shop. I provide everything you need for home desktop, laptop, and mobile phone repair including networking and entertainment center setup. Best of all, I use an adjustable pricing structure that affords substantial discounts to students, veterans, and the elderly.
Do you need computer service in Chico California? Just give me a call at 530-433-9420 and set up an appointment today. Prices begin at $120 with $20 discounts for students, veterans, and the elderly! YES, THEY STACK. Minimum $60 service gets you pickup and drop-off INCLUDED FOR FREE!
Looking for computer literacy classes? Guess what I do that too! If you're concerned that your child or self or even your dog needs help with how to operate a computer, stay safe on the internet, or use particular software, I can help with that too. Affordable hourly rates are fair and adjusted to the situation; please get in touch for more information by calling 530-433-9420.

This website will also include numerous pro-tips on how to keep your computer secure and stable. You will find everything from tutorials on how to do updates correctly, how to disable updates if you're tired of them, how to do your own hardware installs, how to install ad blockers to protect your computer, and more how to's than you can shake a stick at.
MeansIT will soon become your number one stop for tech service and tech advice in Chico California, maybe anywhere online.
See you soon!
1 note
·
View note