#Firefox is one of the worst examples
Explore tagged Tumblr posts
Text
basque country having a botanical guide and catalan countries having a botanical guide..... dont mind me im just out here being jealous of these mfs bc we havent had any prominent aragonese botanists since loscos
#z xarre#maybe i should count pedro montserrat as well since he worked a lot in aragon and like. at least one of his kids works in botany as well#here in aragon. but like. we dont have a flora of our own. so we (at least i do) have to check both the basque and the catalan floras#at least the basque book is a bit more manageable size-wise. bc the catalan book is an absolute monster. which makes sense since theres mor#catalan territories. im not sure if vigo and bolòs took into account l'alguer and cat nord and la franja.#but hey thats already catalunya + país valencià + les balears. so it makes sense its bigger#and actually in botany class we worked w the basque flora. i think theres more specific flora like for example im pretty sure#we have a moncayo flora in the same binding as the basque one#and yeah theres other flora books as well but they dont seem as serious as the basque and catalan ones#and then of course theres flora iberica but theyre literally still publishing it if im not mistaken? or the last issue just came out#and if the catalan one was a monster then this one is like.... the boss monster. its huge. and you know the biggest problem?#that its published online for free but the website is from like. 2001 and the selector for families and genuses is absolute dogshit#and worst of all. it doesnt work on firefox mobile so i cant check it on my phone.
0 notes
Text
The main reason to use Firefox and Linux and other free and open source software is that otherwise the big tech monopolies will fuck you as the customer over in search of profits. They will seek to control how you use their products and sell your data. When a company dominates the market, things can only get worse for ordinary people.
Like take Google Chrome for example, which together with its chromium reskins dominate the web browser market. Google makes a lot of money from ads, and consequently the company hates adblockers. They already are planning to move to manifest V3, which will nerf adblockers significantly. The manifest V3 compatible chrome version of Ublock Orgin is a "Lite" version for a reason. Ublock's Github page has an entire page explaining why the addon works best in Firefox.
And Google as we speak are trying to block adblockers from working on Youtube, If you want to continue blocking Youtube ads, and since Youtube ads make the site unuseable you ought to want that, it makes the most sense to not use a browser controlled by Google.
And there is no reason to think things won't get worse. There is for example nothing stopping Google from kicking adblockers off their add-on stores completely. They do regard it as basically piracy if the youtube pop-ups tell us anything, so updating the Chrome extensions terms of service to ban adblocking is a natural step. And so many people seem to think Chrome is the only browser that exists, so they are not going to switch to alternatives, or if they do, they will switch to another chrominum-based browser.
And again, they are fucking chromium itself for adblockers with Manifest V3, so only Firefox remains as a viable alternative. It's the only alternative to letting Google control the internet.
And Microsoft is the same thing. I posted before about their plans to move Windows increasingly into the cloud. This already exists for corporate customers, as Windows 365. And a version for ordinary users is probably not far off. It might not be the only version of Windows for awhile, the lack of solid internet access for a good part of the Earth's population will prevent it. But you'll probably see cheap very low-spec chromebookesque laptops running Windows for sale soon, that gets around Windows 11's obscene system requirements by their Windows being a cloud-based version.
And more and more of Windows will require Internet access or validation for DRM reasons if nothing else. Subscription fees instead of a one-time license are also likely. It will just be Windows moving in the direction Microsoft Office has already gone.
There is nothing preventing this, because again on the desktop/laptop market Windows is effectively a monopoly, or a duopoly with Apple. So there is no competition preventing Microsoft from exercising control over Windows users in the vein of Apple.
For example, Microsoft making Windows a walled garden by only permitting programs to be installed from the Microsoft Store probably isn't far off. This already exists for Win10 and 11, it's called S-mode. There seem to be more and more laptops being sold with Windows S-mode as the default.
Now it's not the only option, and you can turn it off with some tinkering, but there is really nothing stopping Microsoft from making it the only way of using Windows. And customers will probably accept it, because again the main competition is Apple where the walled garden has been the default for decades.
Customers have already accepted all sorts of bad things from Microsoft, because again Windows is a near-monopoly, and Apple and Google are even worse. That’s why there has been no major negative reaction to how Windows has increasingly spies on its users.
Another thing is how the system requirements for Windows seem to grow almost exponentially with each edition, making still perfectly useable computers unable to run the new edition. And Windows 11 is the worst yet. Like it's hard to get the numbers of how many computers running Win10 can't upgrade to Win11, but it's probably the majority of them, at least 55% or maybe even 75%. This has the effect of Windows users abandoning still perfectly useable hardware and buying new computers, creating more e-waste.
For Windows users, the alternative Windows gives them is to buy a new computer or get another operating system, and inertia pushes them towards buying another computer to keep using Windows. This is good for Windows and the hardware manufacturers selling computers with Windows 11 pre-installed, they get to profit off people buying Windows 11 keys and new computers, while the end-users have to pay, as does the environment. It’s planned obsolescence.
And it doesn’t have to be like that. Linux distros prove that you can have a modern operating system that has far lower hardware requirements. Even the most resource taxing Linux distros, like for example Ubuntu running the Gnome desktop, have far more modest system requirements than modern Windows. And you can always install lightweight Linux Distros that often have very low system requirements. One I have used is Antix. The ballooning Windows system requirements comes across as pure bloat on Microsoft’s part.
Now neither Linux or Firefox are perfect. Free and open source software don’t have a lot of the polish that comes with the proprietary products of major corporations. And being in competition with technology monopolies does have its drawbacks. The lacking website compatibility with Firefox and game compatibility with Linux are two obvious examples.
Yet Firefox and Linux have the capacity to grow, to become better. Being open source helps. Even if Firefox falls, developers can create a fork of it. If a Linux distro is not to your taste, there is usually another one. Whereas Windows and Chrome will only get worse as they will continue to abuse their monopolistic powers over the tech market.
847 notes
·
View notes
Text
I'm seeing so much actively harmful misinfo regarding boycotts.
If you are spreading information on a boycott PLEASE focus on just what the BDS is asking you to boycott. In my honest opinion even THAT is a lot to keep track of, but boycotts work better the more laser-focused they are.
This is the closest thing to an official boycott being asked:

I've seen a lot of posts both here and elsewhere asking people to boycott not just everything on that list, but also Walmart, Amazon, Google, PespsiCo, Coke, Nestle, 4 dozen other big name conglomerates, and a big list of at least 50+ individual celebrities/CEOs/actors. That is not boycotting.
If YOU want to personally abstain from every Israeli-supporting-prduct/service you can, please do it!!!! Even before now, I've personally always abstain from chick-fil-a and 🏴☠️ most of my media–but that isn't an organized boycott. In fact, spreading info that every single one of those companies/individuals are "part of the boycott" is blatant misinformation and actually harms the boycott.
Giant lists that include dozens to hundreds of giant conglomerates and individuals that are hard to keep track of are meant to overwhelm individuals and dissuade them from boycotting at best, and are actively impossible to personally enforce at worst. If you are reading this post, chances are you are breaking one of the many unofficial "boycotts" being asked of you.
For example, following every ""boycott"" being asked of you 100% means: stopping use of any Google products (quitting a job that uses Google workspace, abandoning your Android phone, switching to Firefox or Safari web browser, not using Gmail, not using YouTube), stop using most/all social media, making entirely home cooked meals (every restaurant, even small ones, support Pepsi/coke), only being allowed to buy ingredients for those home cooked meals from physical, local small businesses (which may be wiped out in your area/take more gas to drive to/cost more money to buy from), and cross-checking every single item you buy with a giant list (that I hope you printed out, because chances are you can't use your phone/the internet without sending precious ad profit to Google!).
Telling someone to "do that much or do nothing" is going to result in the vast, vast majority of people doing nothing. Think about the every day people in your life–parents, coworkers, community members. Are they going to do that much? If the answer is no, then a boycott is ineffective. (Plus, doing a lot of that stops you from staying informed on the situation, which is top priority right now!)

Stick to spreading the image at the top of this post. The more people boycotting a small handful easy-to-remember companies, the more effective a boycott will be. A small amount of companies will lose a lot of money, and will have to re-evaluate their stance to give money to Israel–the point of a boycott. But, if everyone only ends up boycotting a handful of completely different companies depending on what list they were given online, all of those companies only lose a little money and no impact is made at all.
TLDR: Feel free to personally abstain from whatever products/services you want, but spreading that they are part of the boycott if they AREN'T is harmful!
#palestine#gaza#free palestine#boycott israel#boycott disney#boycott starbucks#israel#nyklos is typing
105 notes
·
View notes
Text
Fingerprint Browser Review: How to solve the problem of multiple accounts being blocked?

In the fields of cross-border e-commerce, social media operations, advertising, etc., multi-account management is a rigid demand, but the platform's detection of account association is becoming increasingly strict. At the least, the flow is limited, and at the worst, the account is blocked, resulting in heavy losses for users. How to manage multiple accounts safely and efficiently? BitBrowser has become a recognized solution in the industry with its technological innovation and scenario-based functions. This article will deeply evaluate this tool from the dimensions of technical principles, core functions, and application effects.
1. The root cause of multi-account blocking and the pain point solution
The platform identifies the user's identity through browser fingerprints (such as operating system, resolution, plug-in and other device features) and IP addresses. If multiple accounts share the same fingerprint or IP, it is very easy to be judged as an "associated account" and blocked. Traditional solutions (such as virtual machines, VPNs) have problems such as high cost, cumbersome operation, and poor stability.
BitBrowser directly hits the pain point and creates an independent environment for each account through physical isolation technology. Each browser profile has its own cookies, cache, IP and randomly generated device fingerprints to avoid account association from the root.
2. Core technical advantages of Bit Fingerprint Browser
Dual-core driver, compatibility and security coexist
It adopts dual-core architecture of Chrome and Firefox, allowing users to switch freely. The Chrome kernel supports a large number of plug-in extensions, adapting to complex operations such as e-commerce and social media; the Firefox kernel strengthens privacy protection, blocks tracking scripts, and prevents fingerprint leaks.
Anti-fingerprint tracking and dynamic camouflage
Simulate real user behavior by randomizing 200+ device parameters such as Canvas fingerprints, time zones, and fonts. Test data shows that its anti-correlation success rate is as high as 99.2%, far exceeding the industry average.
Smart proxy IP management
Supports HTTP/Socks5 protocol proxy and can configure static residential IP with one click. For example, users can bind independent IPs to each Amazon store to simulate real buyer environments in different regions and avoid platform risk control.
Team collaboration and automation efficiency
Supports multi-person permission management. The main account can assign operation permissions to sub-accounts to avoid the risk of password leakage. Built-in RPA automation function enables batch login, form filling, advertising publishing and other operations, increasing efficiency by more than 3 times.
3.actual scene effect verification
Take a cross-border e-commerce team as an example: when using traditional tools, 30% of Amazon stores were blocked due to association. After switching to BitBrowser, the following configuration is used to achieve "zero blocking" operation:
Independent environment isolation: each store is assigned a dedicated browser profile + static residential IP;
Fingerprint camouflage: Enable Canvas fingerprint randomization and time zone simulation;
Automated listing: RPA scripts batch process product information, saving an average of 8 hours of manpower per day.
In addition, social media operators can manage hundreds of TikTok and Facebook accounts at the same time, and use window synchronization technology to achieve one-click publishing of cross-platform content, and the account activity meets the platform algorithm requirements.
4.why choose BitBrowser?
Excellent cost-effectiveness: 10 permanent browser environments are provided for free, and the paid package is as low as 50 yuan/month, which is only 1/3 of the cost of similar products;
Localized adaptation: The server is deployed in China, with a delay of less than 50ms; it supports Alipay/WeChat payment and complies with China's "Personal Information Protection Law";
Continuous iteration: The fingerprint library is updated weekly to respond to changes in platform detection rules in a timely manner.
Conclusion:
The key to the safe operation of multiple accounts lies in "environment isolation" and "behavior simulation". BitBrowser has achieved the extreme of these two elements through technological innovation. Whether it is an individual entrepreneur or a corporate team, it can take advantage of its high efficiency and low cost to achieve large-scale business expansion under the premise of compliance.
Experience BitBrowser now and unlock a safe and worry-free multi-account management solution
0 notes
Text
How to Prevent IP Leaks on the Internet

Protecting your online identity is as important as keeping your documents safe. Your internet connection has a unique address issued by your internet service provider, which you must protect while surfing online. These days, IP leaks are on the rise, which highlights the importance of preventing it. According to the sources, in the fourth quarter of 2023, over eight million records were exposed to malicious hands due to data leaks, and IP leaks are one major part of this process. So now, you must know why protecting IP and deploying methods to prevent leaks is crucial. In this guide, we will learn the best-proven strategies to prevent IP leaks and what measures one should take while using the Internet. But before that, let’s explore IP leaks further. What is an IP leak? An IP leak happens when your true IP address is exposed despite using a service like a VPN, which is supposed to protect it by masking it with a different one. While there can be several reasons for this, one strong reason is the VPN service's low reliability and cheap firewall protections. Often, we think free VPNs are enough and paid VPNs are scams, which is entirely false. Cheap VPNs will only connect you to a cheap server that does not have any level of security, pass your data through unsecured tunnels, and, worst, create and store logs to earn money. This is why I suggested using a robust and reliable VPN like Surfshark. You can try it yourself—download Surfshark here and get started. It offers many features and geo locations and is cost-effective. 5 Ways to Prevent IP leaks on the Internet 1. Disable WebRTC in Your Browser To prevent WebRTC leaks, you can disable WebRTC in your browser settings. While this may limit some functionalities, paying for increased privacy is a small price. For example, you can disable WebRTC in Firefox by typing about: config in the address bar and searching for media—peer connection. You are enabled and setting it to false. Chrome users can install browser extensions like “WebRTC Network Limiter” (an official extension by Google) or “WebRTC Leak Prevent” to block WebRTC leaks. 2. Disable IPv6 If your VPN does not support IPv6, consider turning off IPv6 on your device to prevent leaks. On Windows, you can do this by going to the network adapter settings, finding the properties for your connection, and unchecking the box for IPv6. Similar steps can be followed in the network settings on macOS and Linux. If you are using a VPN service that does not support IPv6, you should immediately disable IPv6 on your device and system to avoid IP leaks. On Windows, this is relatively easy; all you have to do is go to network adapter settings in the property section and untick the box for IPv6. On MacOS, head over to network network settings. Click on details. Now click on the TCP/IP tab, and in the DHCP option, select the Link-local only option. If you need an easier way, open the terminal and type in the following code: networksetup -setv6off Wi-Fi That’s all you need to do to turn off IPv6. 3. Enable Your VPN’s Kill Switch Most VPNs have a kill switch feature that instantly disconnects your system from the internet if the VPN app is abruptly shut down due to glitches or any other reason. This further helps to protect your internet activity, making it challenging to leak your original IP address. While most VPNs have this feature, the free ones do not. If you use a Windows system, there’s a step-by-step guide on enabling the built-in killswitch. You can follow it and allow this feature on Windows. However, if you are a Mac user, do not worry, as a programmer develops an open-source kill switch feature. You can install it by visiting this site: https://vpn-kill-switch.com/. Then, you can follow the process and enable killswitch on your MacOS device. 4. Use a Secure Browser Consider using browsers that prioritize privacy, such as Tor Browser, which routes your traffic through the Tor network, adding multiple layers of encryption. While it may be slower, the Tor Browser offers enhanced protection against IP leaks. These are the five most secure browsers available for free: Brave Firefox Tor browser DuckDuckGo Opera While this may not be the best prevention method, a secure web browser is a part of the process. 5. Avoid Using Public Wi-Fi Without a VPN Cybersecurity attacks happen the most on publicly accessible networks that do not have any level of security. If you are sitting in a cafe or a food court and using the free WiFi, use a robust VPN provider. Otherwise, it would be best to stick to your mobile carrier for internet accessibility while away from home. Your smartphone and laptop store all the essential information; giving it to an intruder isn’t a good idea. Conclusion IP leaks are a significant threat to your online identity, which can be safeguarded with the right tools and practices. To protect your IP address from being leaked, you need to understand the basics of what causes IP leaks. In this article, we have shared the best strategies to prevent IP leaks, including disabling WebRTC and IPv6, enabling killswitch, and using a secure browser. Lastly, you must ensure you do not connect to unknown networks like public WiFis in cafes or anywhere else. Read the full article
0 notes
Text
Truly, this is happens to everything I post. Which is why I did this because I didn't want to explain this to the ether. But we're over 10 notes now, so I'll spill.
If you're the type of person that likes to catch up to where you left on Tumblr, you can both save your place and resume from another device if you do the following:
Turn off endless scrolling.
Turn on tab syncing on your browser (and also use the same browser to browse Tumblr on your other devices. I use Firefox on desktop and mobile).
This works because, when endless scrolling is disabled and you click next to continue to the next page of your dash, Tumblr stores the max post id in the URL which means you can always recreate where you are on your dash with that URL (example: https://www.tumblr.com/dashboard?max_post_id=733809377685946368). So you can always pull up your spot from your browser history or from any synced device.
Besides, that, I actually highly recommend disabling endless scrolling for mental health reasons. I've honestly had a healthier relationship with Tumblr since turning this off. It's so much easier to say, let me just finish this page and be done and actually stick with it than just trying to stop after one more post. Especially when you scroll and you can see the beginning of the next post which naturally piques your curiosity.
There are downsides, and that's if you want to do the whole multi-device thing, I'm not going to lie to you and say that the mobile web version of Tumblr is great. It's not. However, it works a lot better with endless scrolling disabled, since it only has to hold so many posts in memory at once. Before, once I scrolled far enough down my dash it would often become extremely buggy or just break.
On the upside, using Tumblr from something like Firefox mobile means you can use ad-blockers on it. uBlock Origin is available in Firefox mobile, plus there are other privacy protecting features and extensions (I wish you could use Xkit Rewritten on it, though). Or you can use any other mobile browser that has features you like. Honestly, this is the reason I stopped using the Tumblr app. Even though I was paying for ad-free, it was still riddled with trackers. So I canceled, uninstalled, and haven't looked back. I've been using the web version on mobile for about a year now...
Truly, the worst problem with Tumblr on mobile web is posting... it's awful. It's the same editor that's on the desktop web version and it's not at all optimized for touch screens. There have been many posts and comments that I've just abandoned because it just wasn't worth the hassle (also, as stated above, no one cares any way).
Although, while researching the settings for this post, I literally just noticed that you can change the editor from their rich text editor to "plain text/HTML" or Markdown, so I'm going to give Markdown a shot and see how that goes.
I ended up turning this stuff on for their own reasons, and it wasn't until I wrote the first post that I put all of this together. I've been doing this now for a couple of months since I discovered it and it's been nice going through my dash on my laptop then picking up where I left off when I need to use the bathroom or when I'm on the go.
I still don't ever catch up though. I follow too many people and disabling endless scrolling encourages me to not spend eternity on this site. But I no longer live in terror of losing my place and can easily find it again by going through my browser history.
tl;dr turning off endless scrolling in Tumblr allows your browser to remember it's place on the dash and you can resume from your history or by syncing your tabs to another device.
Y'all!!!!!!!
I just discovered a combination of settings that enable an incidental, killer feature in Tumblr. This shit is a game changer! Buuuuuut I'll only tell if I get 10 notes on this post.
14 notes
·
View notes
Text
Decrapify cookie consent dialogs with the Consent-O-Matic
Remember when they sneered at Geocities pages for being unusable eyesores? It's true, those old sites had some, uh, idiosyncratic design choices, but at least they reflected a real person's exuberant ideas about what looked and worked well. Today's web is an unusable eyesore by design.
Start with those fucking “sign up for our newsletter” interruptors. Email is the last federated protocol standing, so everyone who publishes is desperate to get you to sign up to their newsletter, which nominally bypasses Big Tech’s chokepoint on communications between creators and audiences. Worst part: they’re wrong, email’s also been captured:
https://doctorow.medium.com/dead-letters-73924aa19f9d
Then there’s the designer’s bizarre and sadistic conceit that “black type on a white background” is ugly and “causes eye-strain.” This has led to an epidemic of illegible grey-on-white type that I literally can’t read, thanks to a (very common) low-contrast vision disability:
https://uxmovement.com/content/why-you-should-never-use-pure-black-for-text-or-backgrounds/
Often grey-on-white type sins are compounded with minuscule font sizing. You can correct this by increasing the font size from teeny-weeny-eyestrain-o-rama to something reasonable, but when you do, all the static elements on the page size up with the text, so the useless header and footer bars filled with social media buttons and vanity branding expand to fill the whole screen.
This, in turn, is made a billion times worse by the absurd decision to hide scrollbars (shades of Douglas Adams’ description of airports where they “expose the plumbing on the grounds that it is functional, and conceal the location of the departure gates, presumably on the grounds that they are not”).
https://www.goodreads.com/quotes/3205828-it-can-hardly-be-a-coincidence-that-no-language-on
Scrolling a window (without using RSI-inflaming trackpad gestures) is now the world’s shittiest, most widely played video-game, a hand-eye coordination challenge requiring sub-pixel accuracy and split-second timing to catch the scroll-bar handle in the brief, flashing instant where blips into existence:
https://twitter.com/doctorow/status/1516136202235043841
One of the scariest things about the precarity of Firefox is the prospect of losing some of the customizations and stock features I rely on to decrapify the web — stuff I use so often that I sometimes forget that it’s not how everyone uses the web:
https://www.wired.com/story/firefox-mozilla-2022/
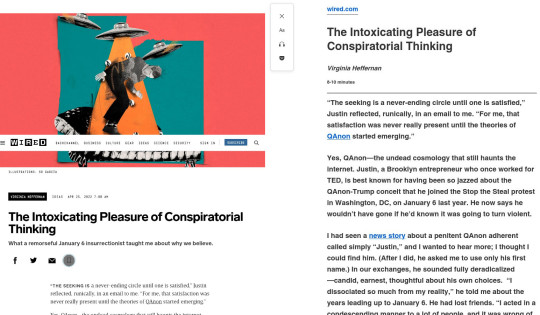
[Image ID: Two side-by-side screenshots comparing the default layout of a wired.com article ('The intoxicating pleasure of conspiratorial thinking' by Virginia Heffernan) with the same article in Firefox's Reader Mode.]
For example, there’s Firefox’s Reader Mode: a hotkey that strips out all the layout and renders the text of an article as a narrow, readable column in whatever your default font is. I reach for ctrl-alt-r so instinctively that often the publisher’s default layout doesn’t register for me.
Reader Mode (usually) bypasses interruptors and static elements, but Firefox isn’t capable of deploying Reader Mode on every site. The Activate Reader View plugin can sometimes fix this:
https://addons.mozilla.org/en-US/firefox/addon/activate-reader-view/
But when it can’t there’s my favorite, indispensable Javascript bookmarklet: Kill Sticky, which hunts through the DOM of the page you’ve got loaded and nukes any element that is tagged as “sticky” — which generally banishes any permanent top/bottom/side-bars with a single click:
https://github.com/t-mart/kill-sticky
A recent addition to my arsenal is Cookie Remover. Click it once and it deletes all cookies associated with the page you’ve currently loaded. This resets the counter on every soft paywall, including the ones that block you from using Private Browsing. Click this once, then reload, and you’re back in business:
https://addons.mozilla.org/en-US/firefox/addon/cookie-remover/
Today, I added another plug-in to my decrapification rotation: Consent-O-Matic, created by researchers at Denmark’s Aarhus University. Consent-O-Matic identifies about 50 of the most commonly deployed GDPR tracking opt-out dialog boxes and automatically opts you out of all tracking, invisibly and instantaneously:
https://consentomatic.au.dk/
We shouldn’t need Consent-O-Matic, but we do. The point of the GDPR was to make tracking users painful for internet companies, by forcing them to break down all the different data they wanted to gather and the uses they wanted to put it to into a series of simple, yes/no consent requests. The idea was to create boardroom discussions where one person said, “OK, let’s collect this invasive piece of data” and someone else could say, “Fine, but that will require us to display eight additional dialog boxes so we’ll lose 95% of users if we do.”
https://pluralistic.net/2021/11/26/ico-ico/#market-structuring
What’s more, the GDPR said that if you just bypassed all those dialog boxes (say, by flipping to Reader Mode), the publisher had to assume you didn’t want to be tracked.
But that’s not how it’s worked. A series of structural weaknesses in European federalism and the text of the GDPR itself have served to encrapify the web to a previously unheard-of degree, subjecting users to endless cookie consent forms that are designed to trick you into opting into surveillance.
Part of this is an enforcement problem. The EU Commission we have today isn’t the Commission that created the GDPR, and there’s a pervasive belief that the current Commission decided that enforcing their predecessors’ policies wasn’t a priority. This issue is very hot today, as the Commission considers landmark rules like the Digital Services Act (DSA) and the Digital Markets Act (DMA), whose enforcement will be at the whim of their successors.
The failures of EU-wide enforcement is compounded by the very nature of European federalism, which gives member states broad latitude to interpret and enforce EU regulations. This is most obviously manifested in EU member states’ tax policies, with rogue nations like Luxembourg, Malta, the Netherlands and Ireland vying for supreme onshore-offshore tax haven status.
Not surprisingly, countries whose tax-codes have been hijacked by multinational corporations and their enablers in government are likewise subject to having their other regulations captured by the companies that fly their flags of convenience.
America’s biggest Big Tech giants all pretend to be headquartered in Ireland (which, in turn, allows them to pretend that their profits are hovering in a state of untaxable grace far above the Irish Sea). These same companies ensured that Ireland’s Data Protection Commissioner’s Office is starved of cash and resources. Big Tech argues that their Irish domicile means that anyone who wants to complain about their frequent and enthusiastic practice of wiping their asses with the text of the GDPR has to take it up with the starveling regulators of Ireland.
That may change. Max Schrems — whose advocacy gave rise to the GDPR in the first place — has dragged the tech giants in front of German regulators, who are decidedly more energetic than their Irish counterparts:
https://pluralistic.net/2020/05/15/out-here-everything-hurts/#noyb
The new EU tech competition laws — the DMA and DSA — aim to fix this, shoring up enforcement in a way that should end these “consent” popups. They also seek to plug the GDPR’s “legitimate purpose” loophole, which lets tech companies spy on you and sell your data without your consent, provided they claim that this is for a “legitimate purpose.”
But in the meantime, GDPR consent dialogs remain a hot mess, which is where Consent-O-Matic comes in. Consent-O-Matic automates away the tedious work of locating all the different switches you have to click before you truly opt out of consent-based tracking. This practice of requiring you to seek out multiple UI elements is often termed a “Dark Pattern”:
https://dl.acm.org/doi/pdf/10.1145/3313831.3376321
But while “Dark Pattern” has some utility as a term-of-art, I think that it’s best reserved for truly sneaky tactics. Most of what we call “Dark Patterns” fits comfortably in under the term “fraud.” For example, if “Opt Out of All” doesn’t opt out of all, unless you find and toggle another “I Really Mean It” box, that’s not a fiendish trick, it’s just a scam.
Whether you call this “fraud” or a “Dark Pattern,” Consent-O-Matic has historic precedent that suggests that it could really make a difference. I’m thinking here of the original browser wars, where Netscape and Internet Explorer (and others like Opera) fought for dominance on the early web.
That early web had its own crapification: the ubiquitous pop-up ad. Merely opening a page could spawn dozens of pop-ups, some of them invisible 1px-by-1px dots, others that would run away from your cursor across the screen if you tried to close them, and they’d all be tracking you and auto-playing 8-bit music.
The pop-up ad was killed by the pop-up blocker. When browsers like Mozilla and Opera started blocking pop-ups by default, users switched to them in droves. That meant that an ever-smaller proportion of web users could even see a pop-up, which meant that advertisers stopped demanding pop-ups. Publishers — who knew their readers hated pop-ups but were beholden to advertisers to keep the lights on — were finally able to convince advertisers that pop-ups were a bad idea. Why pay for ads that no one will see?
Pop-up blockers are an early example of Adversarial Interoperability, AKA Competitive Compatibility (comcom for short). That’s the practice of improving an existing product or service by making an add-on or plug in that changes how it behaves to make it more responsive to its users’ interests, without permission from the original manufacturer:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
It’s been more than 20 years since the Platform for Privacy Preferences (P3P) tried to get tech companies to voluntarily recognize and honor their users’ privacy choices. It failed:
https://en.wikipedia.org/wiki/P3P
Do Not Track, another attempt to do the same, did not fare much better:
https://en.wikipedia.org/wiki/Do_Not_Track
But you know what actually worked? Tracker-blockers and ad-blockers, “the largest consumer boycott in history”:
https://www.eff.org/deeplinks/2019/07/adblocking-how-about-nah
Making it impossible to track users is of great assistance to efforts to make it illegal to track users. Tools like Consent-O-Matic change the “security economics” of crapification, by turning the consent theater of illegal cookie popups into actual, GDPR-enforceable demands by users not to be tracked:
https://doctorow.medium.com/automation-is-magic-f4c1401d1f0d
Decrapifying the web is a long, slow process. It’s not just using interoperability to restore pluralism to the web, ending the era of “five giant websites, each filled with screenshots of text from the other four”:
https://twitter.com/tveastman/status/1069674780826071040
It’s also using a mix of technology and regulation to fight back against deliberate crapification. Between Consent-O-Rama, Reader Mode, Kill Sticky and Cookie Remover, it’s possible to decrapify much of your daily browsing and substantially improve your life.
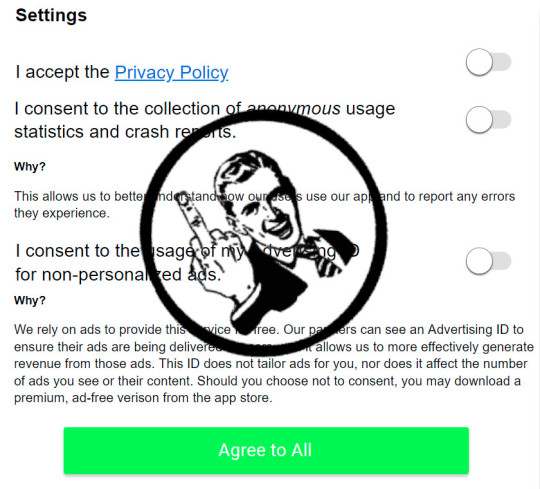
[Image ID: A GDPR consent dialog with a rubber stamp in the center depicting a snarling man flipping the bird.]
488 notes
·
View notes
Text
Biggest Emacs Deal-Breaker
At this point, for me the biggest reason against using Emacs is that it's still possible for one little thing to just block all of Emacs.
This doesn't come up often, and when it does it's usually just for a second or two at worst, but when it does, it's at best almost irredeemable, at least for me.
One of my personality traits is a profoundly acute impatience for certain workflow snags - manual repetition or tedium which I can clearly see as inherently optimizable is one, inability to jump to doing another thing at the speed of thought is another.
The things that keeps Emacs seriously in the running for me is that I now have enough fluency with Emacs' lisp and workings so I can usually solve this - if I want to do something so quickly that I don't even feel it taking any amount of my time or thought, there's probably some combination of built-in functionality, external packages, and my own Lisp that will make it happen, and the turn-around time from desire to done is usually a couple hours.
But there's only so much I can do to mitigate a deeply entrenched, synchronous, blocking design. For example, if I start a package upgrade I expect to be a couple keystrokes away from doing something else while that runs in the background. But the default package interface will stop Emacs to download packages - which in practice means it will freeze everything, because the only reason I'm in Emacs is for its ability to give me the same value for less effort when I let it be my everything.
If there is one way in which Emacs is a really bad operating system, it's this - the degree of cooperative multitasking without ability to preempt is more than zero, which is frankly unacceptable. To their credit, it used to be a lot worse, and it's going to keep getting better, but still... I would never put up with any manifestation of this problem if I wasn't gaining so much relative to the alternatives, and this is the biggest landmine which could undermine those gains in practice.
The worst, though, is this:
You can still lock up the entire Emacs process, seemingly irrecoverably.
There is a similar flaw in Firefox, which has a single-process design at its core, and the situation is similar - it almost never happens, but when it does it takes out everything you were doing, including things that should never ever be coupled together like that, and you better hope you saved your work or the auto-save was good enough.
But with Firefox, the only way to lock up the whole browser is to risk saying "keep running" when Firefox says "this webpage sure is using a lot of CPU, are you sure you don't want to kill it?", as far as I know. (I think even for the good ol' alert loop, they add a button to kill the page on every alert after the first few within some time window.)
With Emacs, you just have to make the mistake of coming up with or accidentally stumbling into the wrong combination of function calls or nesting. For one example, there's nothing preventing you from coding a loop which keeps calling the raw keystroke-reading primitive, possibly with the right error/signal-suppression around it, such that you can never break out. For another example, there's nothing preventing you from starting a terminal within your Emacs, and then running an Emacs client which connects to the same Emacs instance in that terminal, and then calling a function within that nested Emacs which only accepts keystrokes in the calling frame but blocks the entire process - including the GUI Emacs window which contains the terminal which contains the nested Emacs "window", and so now the nested window can never receive keystrokes because the blocked outer window must handle them and pass them along.
All this would be super funny if that same Emacs process didn't also contain everything else I was doing at the time.
This would also be totally damning if all other software wasn't so bad at letting me hook into it or modify it - which just brings me back to my big point about Emacs: it's worth it if you want the most malleable platform for tailoring a bespoke UI/UX for yourself - if you want anything less, if you don't find yourself frequently intolerably bothered by the impedence between your will and your tools, then there are things better than Emacs, and in this case, "better" often includes "in the unlikely event that something locks up, it doesn't take your other stuff out with it".
3 notes
·
View notes
Note
You guys also at least seem to be making the Firefox mistake, of focusing a lot on what experts say people want, possibly backed up with user studies (I know FF does a lot of those, not sure about Tumblr)... But it leads you to changes that long time power users HATE, and so they stop recommending it to people.
Sure there are differences, a social network isn't the same as a browser, FF had other issues as well. But a few "influencers" (in the real organic way, not the built up marketing way - though of course the organic version is what they are trying to mimic) have big effects on the network. And that is often going to be the people who use it practically every day, for years even through the worst times. So maybe you will please some theoretical new users, but if you piss off the core fan base, will there be anything pulling those new users in?
So maybe at least compromise somehow?
Like on the reblog chain thing... ok, to users of other sites, yes clicking on the name and getting the user main page and not the post is more expected. But at least make the "blank header space" click give you the previous link in the reblog chain, make it a real link (<a href>) not JS, so we can see the URL in the status bar, and can middle click it and such. Maybe increase the highlight on hover a bit. Or heck, just give us a button that says "previous reblog" or something. Sure it would look goofy but at least we could use it. Probably other options could be brainstormed (but don't hide it under the meatball menu. Too many clicks for a commonly used thing)
Oh and make a link to the subdomain version of a user (when it exists) accessible at least one other place beside the timestamp in the meatball menu...
Another example, maybe let people turn off the new lightbox that everyone hates. Yeah, ads in it are not great, but ads are survival (and ad free exists, thanks!) and mostly people hate the *rest* of how it works. So add ads in the legacy one, and let people use it. Or if it is super old and crusty and you don't want to maintain it, make the new one flexible enough to emulate the old one. Plenty of options.
Just keep the core userbase who have stuck though 10+ years in many cases in mind, is what I am saying.
I see where you're coming from, and I see why Tumblr feels a need to expand, to chase that unsustainable infinite growth. My friends who don't use tumblr don't use it because they don't have an existing community there, and I'm not enough to sway them over. It's a blogging platform at it's heart. I don't think trying to ape current trends in design is going to help. All it is going to do, has done so far, and historically has done is alienate your existing userbase, and fail to draw in new people. In fact, I'd argue that you're making your biggest competitor here. Cohost, is becoming a viable competitor of the back of Tumblr constantly implementing features that make the website more difficult to use and that frustrate and alienate it's userbase. Historically speaking, let's look at other social media that tried to pivot in this way? Myspace was Myspace, and then they tried to pivot to chase the trends of the industry, and it bombed. DeviantArt has been going through this for a while. in 2017 the site refresh launched to make it more similar to other websites, and it was frustrating for old users, removed features people liked, and didn't supplant that with anything new worth sticking around for, so it bombed. And it virtually killed the site with it, it's a shell of its former self. Do you remember twitter stories? Google Stadia, Hangouts, Duo, Bulletin, etc? New Coke?
yeah i'm extremely aware of all of these things, i've been using and studying this internet thing since MSN and AOL chatrooms were the only "social" features of the web. some people i work with have been at this since Usenet was the "social" part of the web. the rise and fall of different platforms are lessons we're always referencing and learning from and trying not to repeat, and learn the best from.
that's why i keep saying that there's a balance at play here between what makes tumblr unique and wonderful and different, which are values of the product, versus what the actual mechanics of the product are. some of the examples you're citing were "bombs" because they didn't have any core value to begin with, just a useful mechanic. or the core value wasn't understood, so it was easy to lose. some of them are cases where they changed the wrong mechanic and it broke the value, and there's no recovery from that.
the balance is successful when the mechanics are working to get new people to realize those core values quickly enough to offset those who don't realize them, or don't resonate with them. because the core values of tumblr aren't for everybody, we wouldn't be different otherwise. like you say: there's no community for them, but why is that? is there a mechanical reason why not? a perceived reason?
this is really difficult stuff, and we're trying as best we can to get it balanced. it's requiring us to try and experiment with some changes that feel really weird to me, as a long-time tumblr user. i hope the benefits of this become more obvious over time. i'm also hoping that some of the very obvious quality of life issues we're trying to address offset the fear that we're just "copying" other sites while ignoring everything else. there's a lot more to come.
#tumblr#site design#UI#UX#Firefox is one of the worst examples#but not the only for sure#I dunno if they just do user studies wrong#or if they do them 'right' according to designer standards#and they are just fundamentally flawed#in one way or another
94 notes
·
View notes
Text
How to make a fake post
I just watched the excellent video by Sarah Z about fake made-up posts, i.e. screenshots of Tumblr posts that are clearly stupid made-up stories, except the screenshot itself is also fake. And that inspired me to do something I’ve wanted to do for a while: Make an illustrated tutorial on how to make a fake a screenshot of a tweet, Tumblr post or similar that are indistinguishable from real ones.
This works on desktop on any modern web browser, though the specific UI will look a bit different depending on which one you use.
Step 0 - if your web browser is Safari on Desktop
This step is not necessary if you’re using Firefox, Chrome, or something based on either (typically the latter) like Edge or Brave.
Open the preferences.
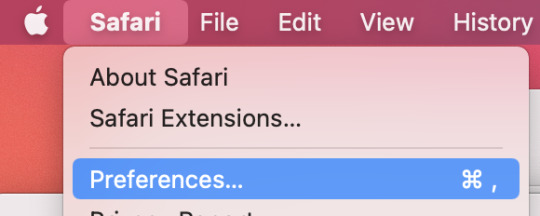
[Image description: Screenshot of Safari app menu open on macOS with the “Preferences…” item highlighted]
Go to “Advanced” (the last tab) and at the very bottom, make sure that “Show Develop menu in menu bar” is selected.
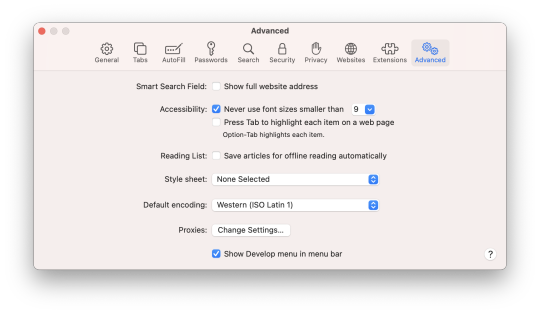
[Image description: Screenshot of Safari preferences window on the “Advanced” tab; the last item, a checkbox saying “Show Develop menu in menu bar”, is selected.]
Step 1 - Open an example post
I’m going to fake a tweet by myself, which you can find here: https://twitter.com/zcochrane/status/1406004939810295808
The specific tweet is irrelevant; this one is about programming and complains about how SwiftUI, a technology for developing Mac apps, is full of issues. It’s easiest to choose one that doesn’t have any hashtags.
Step 2 - Drill down
Now, right-click on the text of the tweet, and select “inspect element” or whatever menu item in your browser sounds the most like that.
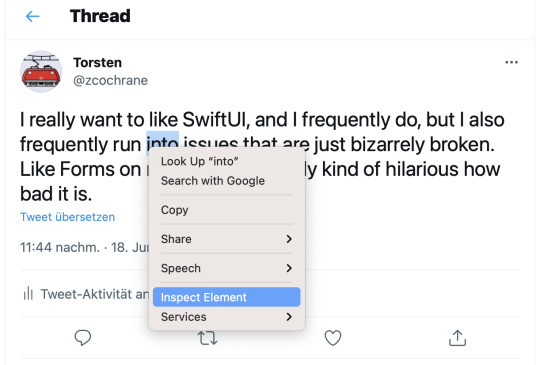
[Image description: Screenshot of a random tweet by twitter user zcochrane (aka me); a word is highlighted, and a context menu is open, with the item “Inspect Element” highlighted]
This isn’t to give anyone ideas; you can assume that all the worst people on the internet already know this. That is really the key. I want to destroy your trust in screenshots of posts, especially screenshots of very weird and outlandish posts. (Note also that this isn’t the only way to do this, and it only works on desktop, but it illustrates how easy it is).
On the bottom or the side of the window, a new, complicated view will open that shows you the inner workings of the web page. You can do a lot of fun stuff here, but we don’t need a lot for our purposes.
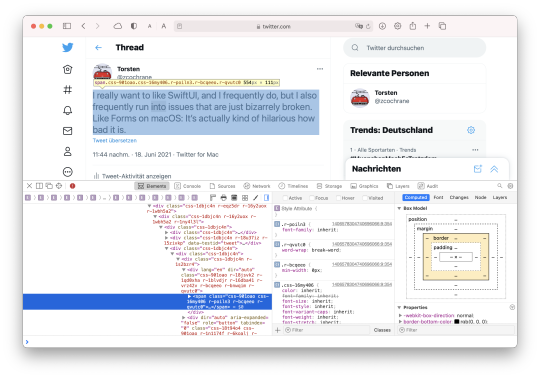
[Image: Screenshot of a Safari window showing the same tweet, now with a blue box is lying over the text, and the bottom half of the window has a complex view of details about the text in that box and its place in the site’s internal structure.]
The important thing is the tree view on the left. If you can’t see the text of the tweet in there, click the disclosure triangle next to whatever thing is highlighted there. This should show the text directly.
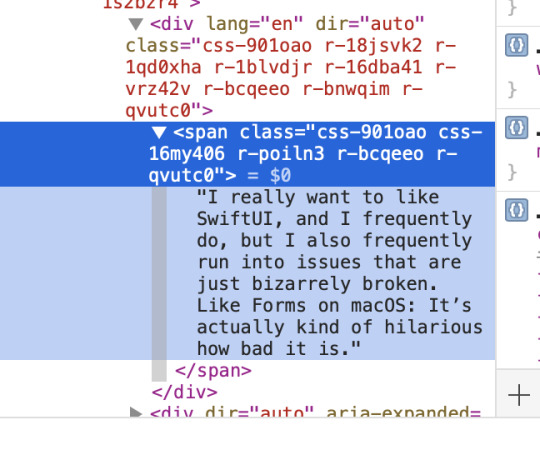
[Image: Screenshot of a tree view showing various HTML elements. They are all expanded. The inner-most item is just the text of the tweet from above.]
Step 3 - Change it
Now you can just double-click on that text and enter something new.
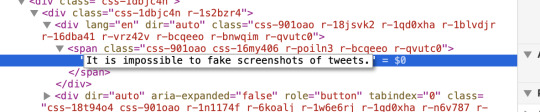
[Image: Screenshot of the same tree view, now wider (don’t know why the window just jumped around on me). In place of the static text from last time is now a text entry box containing the words “It is impossible to fake screenshots of tweets.”]
Once you press enter or the focus moves somewhere else, the text on the website will change.
Step 4 - Take a screenshot
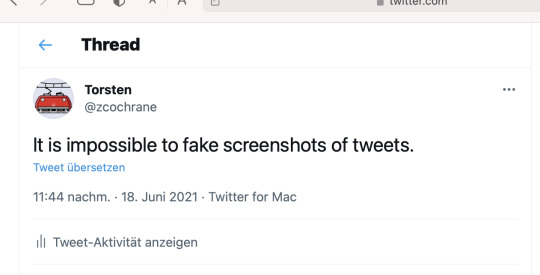
[Image: Screenshot of a tweet, the same one we’ve had the entire time with the same user and date, but it now says “It is impossible to fake screenshots of tweets.”]
And that’s it! If you want to do something with multiple paragraphs like your average Tumblr post, then you probably need to know a little HTML, but it’s not that hard.
For better results, you can also use the same technique to fake the time and date when the post was made, so it looks like the post was deleted - though honestly, that’s probably not worth the time and effort. And you can, of course, also change the number of likes and retweets, or for Tumblr posts, the number of notes, and other information like the user names and so on to fit whatever narrative you want to tell.
What makes this particular technique so useful is that you cannot compare pixels or whatever to prove a tweet is fake. The pixels that the screenshot grabs get generated in exactly the same way as for the real tweet. Proving that this tweet is fake is somewhere between difficult and completely impossible.
The point
This may seem like dangerous secret knowledge to some, maybe. But it’s really not that difficult, and you can assume that everyone who has more than a passing knowledge of web development (and that is a lot of people) can figure this out if they want to. (And if you’re into web development but didn’t know this yet, try it out, it’s super useful!)
In particular, you can safely assume that all the worst people in the world already know this trick and others like it. What this means is that every single screenshot ever is suspicious. Did that post really exist? There is genuinely no way of knowing, unless you find the actual post in question.
That means if you see a particularly stupid post, or a particularly offensive one, by someone you respect, or by someone you hate, or by just anyone in general, then you must always assume that it’s very possibly fake. It takes maybe ten seconds more to create a fake screenshot than to create a real one.
Not all screenshots are fake, and sometimes screenshots are the only source for something because the original was deleted, but all screenshots might be fake, and so you should tread very carefully when one is involved.
There is also an inverse to that: If you want to share a post or a tweet somewhere that you know is real, you should always include a link to the original (and also an image description for people using screen readers). If it’s a good post, it allows people to leave the hearts and stars where they belong; if not (or if that’s debatable), it provides the context and proves that the post is, in fact, real.
24 notes
·
View notes
Text
WHY TWITTER IS A BAD ECONOMY
On the average trip I bring four books and only read one of them, because I find new books to read en route. That was exactly what the world needed in 1975, but if this label didn't already exist, it would seem the noise is whitish. It implies the result won't be pretty, because it meant that to write as he wanted to seem aristocratic; she was afraid she wasn't smart enough. Just have a gentlemen's agreement. Which is exciting because among other things it means third parties can use this technique whenever a you have at least a random sample of the applicants that were selected, b their subsequent performance is measured, you'll know if they do. So there's another difference between essays and the things one has to write in high school. When I was in college I imitated the pompous diction of famous professors.
Do one thing and do it yourself. Mihalko seemed like he actually wanted to be our friend. The worst thing is that it was a little alarming to have users who got lots of traffic. Better stick to the standard cartoon version that the Civil War was about slavery; people would be confused otherwise; plus you can show a lot of bandwidth. You'd think it would be: just try to sell one. However, even that is an interesting prospect. That's probably the number one question people ask me. Since they're writing for a popular magazine, they start with the most radioactively controversial questions, from which because they're writing for a popular magazine, they start with the most radioactively controversial questions, from which because they're writing for a popular magazine they then proceed to recoil from in terror.
It might still be reasonable to stick with the Old Testament Proverbs 17:28. The economy of medieval Europe was divided up into little cells is terribly inefficient. But Apple created wealth, in the sense of what people will pay for their skills, the answer is yes, apparently. Next year you'll have to explain how your startup was viral. The most obvious difference between real essays and the things one has to write in school is that real essays are not exclusively about English literature—to write, without even realizing it, imitations of whatever English professors had been publishing in their journals a few decades before. They overvalue ideas. Eventually by trial and error I found that what the teacher wanted us to do was pretend that the story had really taken place, and to have the junior people do the work for him. And then there was the difference in the way of having the next.
It seems that, for the average engineer, more options just means more rope to hang yourself. The idea is basically that you sort search results not in order of how much advertisers bid as Overture did but in order of textual relevance as search engines did then nor in order of textual relevance as search engines did then nor in order of textual relevance as search engines did then nor in order of textual relevance as search engines did then nor in order of the bid times the number of startups are created to do product development on spec for some big company, they should apply for patents because patents are part of the mating dance with acquirers. Calder's work is his own happiness showing through. A free market interprets monopoly as damage and routes around it. The immediate cause of death in a startup is that I happen to have it. The big media companies shouldn't worry that people will post their copyrighted material on YouTube. People are finally starting to admit that Wodehouse was a great writer, but to serve a ruler powerful enough to enforce order, rich people had private armies. Another classic way to make something people want is not the thing itself, but it was wonderful for us, his students. And two things, especially, is where the USPTO has been dropping the ball. Basically, I had to add a new application to my list of known time sinks: Firefox.
Particularly the sort written by the staff writers of newsmagazines. So I don't really blame Amazon for applying for the one-click patent would turn up in the company and went to work for you without giving them options likely to be worth suing for money. To be patentable, an invention has to be more true in software than other businesses. You can see wealth—in buildings and streets, in the narrow sense of the word unjust here is the unmistakable spectral signature of the Daddy Model. For example, a city could attract angels from outside. I ignored it the way you let yourself ignore a bug that only appears intermittently. To do really great things, you have to do is remove the marble that isn't part of it. That's the paradox I want to explore: great new things often come from the margins.
He has since relaxed a bit on that point. If 98% of the time I thought, they did call them essays, didn't they? At first I tried rules. With a tractor an energetic farmer could plow six times as much land in a day as he could with a team of horses. You're short of money, for example have been granted large numbers of preposterously over-broad patents, but not random: I found my doodles changed after I started studying painting. It may work, but it didn't last long. Unfortunately, patent law is inconsistent on this point. That's the good part. If 98% of the time we could find at least one good name in a 20 minute office hour slot. I've seen the lever of technology grow visibly in my own time. Where the method of selecting the elite is thoroughly corrupt, most of the world's history the main route to wealth was to steal it: in pastoral societies by cattle raiding; in agricultural societies by appropriating others' estates in times of peace. Indeed, the same principle: the way to ensure that would be too much of a political liability just to give the other side of the story: what an essay really is, and how you write one.
It's an old idea that new things come from the margins. What really makes him stand out, though, it became the basis of education than wealth. What people know of him now is his paintings and his more flamboyant inventions, like flying machines. This was Henry Ford's plan. A couple years ago my friend Trevor and I went to look at the list of movies playing, they want that extra oomph that the big stars have. Scholars had to figure out what he meant. This leads to my final suggestion: a technique for determining when you're on the right track when people complain that you're unqualified, or that you've done something inappropriate. That's the whole point of technology. If new ideas arise like doodles, this would explain why you have to fund startups that won't leave. And they're full of exactly the right kind of friends. After the lecture the most common form of discussion was the disputation.
9% of the people. Well, founders aren't much better. To attack a rival they could have ignored, Amazon put a lasting black mark on their own reputation. The patents aren't mine, of course, it's called school, which makes that clear to everyone, though in fact all jobs are some percentage school. Thump music. Startup School. And yet they work horribly. The only point of buying one now is to advertise that you can get away with working as if the goal were to discover good ideas, but for good new ideas, and you always get more attention for that. The Age of the Essay probably the second or third day, with text that ultimately survived in red and text that later got deleted in gray. Which is precisely why we hear ever more about it. A company that sues competitors for patent infringement before they'd even released a product. When you're old and eminent, what will you miss about being young and obscure?
#automatically generated text#Markov chains#Paul Graham#Python#Patrick Mooney#time#performance#imitations#Which#sense#years#school#people#liability#economy#ball#farmer#reputation#application#technology#world#Thump#order#teacher#list#magazine#office#things#essay
1 note
·
View note
Photo

Using multiple GPUs for multiple monitors, a case study
Hi everyone
I wanted to share the results of a bit of an experiment I ran in the last few weeks, which had some interesting and even unexpected results.
The problem(s) I tried to solve
I have a tripple monitor setup. My center monitor is a 1080p 21:9 144Hz monitor, and is as you would expect my main gaming monitor. Next to that monitor I have 2 plain 1080p 16:9 60Hz monitors, one on each side. I use them for having Skype, Discord, monitoring tools, etc open while I game.
Problem 1: I noticed is that when I was gaming and for example someone sent me a chat on Discord or Skype, it didn't update, or the Discord window went black. When I tabbed out of my game, the window would update correctly.
Problem 2: when I have a browser with YouTube open on a secondary monitor, at best my FPS takes a hit because Firefox seems to use the 3D part of the GPU to render Youtube content, and at worst my game FPS gets locked at 60 because it's running 60Hz content.
Note that Problem 2 was less of an issue when I used Edge, as Edge used the Video Decode part of the GPU, which didn't compete for resources with the 3D part. It did use a tiny bit of 3D to actually render the browser window, but nothing heavy.
The theory
If I would buy a simple GPU as secondary GPU, and hook up my 2 AUX monitors to it, leaving my primary monitor hooked up to my main GPU (a Vega 64), then all the rendering of Discord and Firefox would be done on the secondary GPU, leaving my primary GPU to be able to render games dedicated. Whatever happens on the secondary GPU, wouldn't affect the primary.
The experiment
I bought an AMD RX550 2GB, cheapass thing, but for the purpose of this test it should suffice as the load of my AUX monitors would be very light anyway. I plugged it into my mainboard into an available PCIe x16 slot. Now note, I run a Threadripper system, so I have PCIe lanes up the wazoo, so there was no fear of suddenly having my main GPU running at x8 instead of x16 because of this.
Sure enough after booting up I had the following show up in Task Manager.
GPU 0 : Radeon RX Vega 64
GPU 1 : Radeon 550 series
So far, so good. Note I will be using Task Manager as a reference here, as from Windows 10 1809 it shows the GPU load and what GPU something is running on. For detailed HW load I did crossreference with HWInfo, but it was always consistent with what Task Manager said.
I fired up Firefox and dragged the window to one of the AUX monitors, then started playing a Youtube clip. I saw quite some load on the 3D part of the RX550 so I thought "yay, this is working". Alas, no, not in the slightest. I looked into the details, and what I saw was really surprising: the load on GPU 1 was not Firefox, it was Desktop Window Manager (DWM), Firefox was using GPU 0.
What was happening here was that Firefox was still using GPU 0 to decode and render the Youtube vid, but because the monitor it was on was attached to GPU 1, not GPU 0, the DWM rendered Firefox as a remote window on GPU 1. This is the 3D load on GPU 1 I was seeing. I tested with Edge and yep, same thing was happening, only now with Video Decode on GPU 0 and 3D on GPU 1. I was baffled.
I fired up some other applications to see if there were issues assigning load to a specific GPU. I tried MPC-HC first to render a H.265 encoded movie. No issues there, MPC-HC dynamically changed the GPU it was decoding on to match the monitor its window was in. If I dragged it from my main to one of the AUX monitors, Video Decode on GPU 0 dropped to 0 and Video Decode on GPU 1 sprung up. Next I fired up the Netflix app. Same there: it just went with whatever GPU the window was on and adjusted on the fly. So there was nothing wrong there, only of course the loads I chose were Video Decode loads. Still, Edge used Video Decode, and it had that wierdness going on.
Skype and Discord were also not quite responsive, and when I checked task manager I could see that they too were still assigned to GPU 0, even though they were on a monitor attached to GPU 1.
I tried firing up a game and seeing what the effect would be if I tried to watch Youtube on one of the AUX monitors. The result: the clip stopped playing, or played audio but video at like one frame per 10 seconds. The GPU load on GPU 1 also dropped to almost 0, it seemed it wasn't getting any data to render. Both Firefox and Edge had this behavior. Again, stumped.
Then, a sudden realization: I was playing my game in fullscreen windowed. This meant that it was being rendered as part of the entire desktop with the DWM as intermediate layer. What if... I played fullscreen?
Swicthed my game to fullscreen and YUP, suddenly my Youtube clips played smoothly again. Still the same "remote rendering" wierdness, and a FPS hit in my game when using Firefox, as Firefox was using 3D to render the clip, but at least it was working! Same for Discord and Skype, they updated nicely when I received a chat.
My analysis
So, there's a few things going on here. The main thing here is some very wierd quirks of the DWM.
First, when multiple applications request 3D workloads, the DWM seems to limit the refresh rate to the lowest refresh rate of the entire desktop, probably to keep things consistent while it renders all the 3D surfaces. This reflects in games being capped at 60 fps on a high refresh rate monitor, when you do 3D stuff on a second monitor. If you run your game fullscreen though, the DWM is not involved in your game's screen and only renders the other surfaces of your desktop, so you no longer have a conflict there, and any resource allocation for multiple 3D demand gets handled by your video driver, not the DWM.
Second, applications seem to always default to GPU 0 unless they have internal logic to dynamically change GPUs. When displaying on displays not attached to GPU 0, some "remote rendering" technology of Windows and the DWM kicks in to make this transparent to the user, at the cost of additional GPU load on the nonprimary GPU(s). Unfortunately, Windows doesn't seem to have an option to force an application onto a specific GPU unlike with CPU cores. The GPU driver might be able to help with this, but the options I've seen (for example in nVidia's driver) seem to then force an application to always run on a specific GPU, so nothing dynamic.
Further analysis
Now, my work laptop is a Dell Precision, which has 2 GPUs: an Intel integrated one and an nVidia Quadro one. The internal monitor of my laptop is hooked up to the Intel GPU, while the external monitors via USB-C are hooked up to the nVidia Quadro GPU.
I re-tested what I tested above and... applications DID move to the other GPU. My main test was Edge here, when moving it from my laptop monitor to my external monitor it jumped from GPU 0 to GPU 1 with the entire workload.
This baffled me a bit, until I realized: Windows DOES have a built-in system for dynamically moving loads between GPUs, but it is designed to move loads between an iGPU and a dGPU. It sees the iGPU as a "Low Power GPU" and the dGPU as a "High Power GPU", and uses both dynamically as appropriate. However with 2 dGPUs, this doesn't work as GPU 0 will always be the "High Power" and "Low Power" GPU, with no options of changing it.
Conclusions
My experiment was a bit of a failure, but not really through a fault of my own, rather it's very specific Windows behavior that kept it from succeeding. If Windows would have more intelligent dynamic GPU assignment, I am convinced it would have worked and I would have seen the benefits.
That being said, I did manage to find out a few things that settle arguments that often come up
1) "Will my secondary monitors limit the performance of my high refresh rate primary monitor".
This comes up so often with an equal amount of people saying "yes, definitely, I have encountered this" and "no, I have such issues".
In this case, both are right, but there is one paramater that is never mentioned: borderless windowed. If you play your games fullscreen you will not encounter issues, but if you play your games borderless windowed you will encounter this issue, as the DWM will then be inbetween the game and your monitor.
2) Will attaching my secondary monitors to a secondary GPU improve my performance
My results are: if the second GPU is a dGPU, then no. However, if the secondary GPU is an iGPU (like an Intel Integrated or an Ryzen APU's integrated GPU) then it will, as the limiting factor is Windows' dynamic GPU assignment logic. Note: this is true for Windows 10 19H2 (which I am running), hopefully MS imroves this in future Windows 10 versions.
1 note
·
View note
Text
Hating the Internet
Posted Saturday, June 10, 2023
Just a short long vent post, the recent username update Discord is pushing out along with more talk elsewhere online about the worsening state of the internet is getting to me.
It just feels like every website, application, and platform is trying to shove out the worst changes possible in the past couple years, along with trying to suck out as much data from users as possible. I've joked before that "Google knows more about me than I do" but at this point I wouldn't be surprised if they literally did, it's insane.
I'm not even a huge "muh cybersecurity, muh digital privacy" kinda person, I just think it's absolutely wild that not a single thing on the modern internet today seems to not have some ulterior goal or shady practice going on behind it. It's hilarious to me that the U.S. would go all out with trying to ban TikTok but they'd NEVER try to touch Google or Apple despite having the same problems prying into users' data constantly. It's a "national security" problem when a Chinese company steals user data, but when the biggest U.S-based tech companies in the world do the same shit it's no problem at all.
I would probably use a different search engine than Google if I'd ever seen one that looks worthwhile. I've seen and checked out a couple before, but none of them made me think "Wow, I should've been using this instead the whole time!" It reminds me of the types of Linux-using chuds on YouTube who tell you to use Firefox or a fork of it, turn on browser fingerprinting protection, get all these anti-tracking extensions, change your default search engine to DuckDuckGo or Qwant or some shit when half that shit doesn't matter for the average end-user. All you really need is a decent browser and a decent adblock at least, like Firefox and Ublock Origin.
Speaking of browsers, all of them suck now too; Chrome has been Chrome for years, Opera is known spyware (moreso than others), Brave advertises being "for your privacy" but has a built-in crypto wallet and bakes ads into the new tab page, of which both features are opt-out (as in, you have to turn them off yourself) AND it's built on Chromium anyway. Vivaldi is another Chromium browser I've heard of and tried, didn't interest me. Every other big alternative browser I've heard of has just been another fork of Firefox, like Waterfox or Pale Moon, which were also disappointing. Basically, use Firefox and get Ublock, otherwise don't browse the internet in the first place.
Going back to Discord's username update: the username system they're changing to has ALWAYS been bad and no one seems to realize that. Alphanumeric characters and underscores only, and maybe dashes or periods (one or the other, never both), often with a restriction on length (15 characters on Twitter for example, 32 on Discord). Discord's is even worse by making it forced lowercase, whereas at least Twitter allows uppercase characters (even if usernames are case-insensitive anyway, so uppercase is just a cosmetic difference).
Discord's original discriminator method was clever and solved the problem of "this username has been taken" that forcing totally unique names creates. The fact that they try to say "only 10,000 people can have the same name" is a problem is so unfathomably stupid. Even if discriminators just CAN'T be used, "@username123" is the future, at least allow uppercase and more special characters. I don't understand why the people running these sites and apps insist on only having 1 or 2 special characters (like underscores and periods) and not stuff like slashes, brackets, parentheses, or symbols like @, #, and $.
Anyway, fuck Discord. Maybe someday IRC will come back outside of niche subcommunities and piracy.
0 notes
Text
Adobe Flash Player Download in Android
The steps mentioned previously seem a bit complicated. Let's look at two options that we may currently recommend if you are feeling it essential to deal with Flash content on your Android device. So sooner or later, everyone is going to have to move forward. In the event you require help in above guide you're able to contact us directly. To begin with, the Flash support within the browser is simply a 14-day trial, and should you desire to keep on using it you will have to get the entire version of the app (1.83). Please be conscious that it might impact your device performance and battery life. These steps are comparatively simple, and you may finish the manual installation of Android flash player with a couple of comfortable way that we described within this article with screen shots.
If you're searching for a SWF player a media player that supports Shockwave Flash files then VLC is one of the greatest programs it is possible to use. Flash Player is quite much like the software that you've installed on Windows desktop computers before. Essentially, if you don't install flash player then all of the flash contents will show error and won't play. In general, Adobe Flash Player is still an important tool to browse the internet for those that could get it to do the job. So so as to see the websites with requires flash player you might have to install Adobe flash player from the manual below first. The absolute most secure method to utilize Adobe Flash Player on Android is through one of the subsequent apps, which could easily be obtained in the Play Store.

Streaming video in a site is getting to be a standard feature on most Android phones. Make certain that you are streaming from the Firefox browser each opportunity to attempt to prevent any hiccups. As soon as it isn't feasible to download Flowplayer videos straight from the player in these instances, you can use freely available plug-ins or download sites to conserve the clips to your PC. Also, you may still update the Adobe Flash once installed with the newest security patches. Quite simply, Adobe is telling all to go ahead from Flash on their phones. Apple has a large collection of strict rules because of that the developer needs to experience each part of the conditions and conditions prior to submitting the app. Unfortunately, Android Jelly Bean or later versions aren't supporting the flash player but employing the tweaks shared inside this article will provide you with the accessibility to flash content once more.
The Key to Successful Adobe Flash Player Download in Android
The SWF file format is designed for internet use. Before you download any files, you want to receive your Android device prepared to accept them. In case you've downloaded the file utilizing phone browser, you can discover the APK inside Downloads folder. Irrespective of how you move the file, you still must install it. In order to remain safe, it's suggested to not install raw APK files downloaded from the internet, as they might contain malware.
Updates Automatically The Flash app will update automatically, so you will not have to be concerned about attempting to stay updated with the most recent security flaws or builds. To allow flash player, you will be asked to install Dolphin Browser. Aside being easy to establish, Dolphin Browser also provides the very best Flash experience out there. Firefox for Android is an excellent choice. Another simple solution is to just download Puffin Browser. It's a trusted browser for the majority of sites. Be sure that your Android on the web.
The worst of the situation, according to experts, is that ransomware can impact any Android user, as it does not require they have root to the gadget. You also receive a 2 year warranty including replacement in the event the tablet becomes damaged by the kids. Naturally, there's still a good deal of content on the internet that utilizes Flash. If you are going through an issue with a single site and have exhausted all troubleshooting steps, the issue may exist on the site rather than your PC. Last, you could be experiencing a hardware issue. Whatever the case, it's a significant method to rule out a hardware issue when troubleshooting your PC. Below in this informative article, you will discover all the acceptable flash releases by Adobe.
You will find a drop-down box. Because local storage may be used to conserve information on a computer that's later retrieved by the exact website, a website can use it in order to gather user statistics, very similar to how HTTP cookies and Web Storage may be used. There are in reality two solutions based on which device you've got. Before downloading Adobe Flash, make certain that your Android device is linked to the web. If you are liable for managing Android devices be certain to control app installation to stop things like Marcher from happening. It's well worth checking what firmware you're running on your handset before installing the application, in the event of interoperability problems, and in the example of tablet users Adobe recommends running Android 3.1.
3 notes
·
View notes
Text
In addition to highlighting noxious bullshit that you didn't want to see, it also does this:
(sorry about the eyes, firefox glitched and eventually crashed when I tried to take a screenshot)
Most of the highlighted notes I've seen have been #queue tag cruft, which is harmless when it's tucked away in the notes but is just. This feature is one more thing for me to pointedly ignore, which is exhausting. This is a feature where the worst case is terrible, and the modal case is still bad and benefits no one; it doesn't even drive hashtag #engagement.
Edit for another example of pure cruft that it's amplifying right now:
Posts like that are harmless to most people and beneficial to the person being tagged, but a machine singling them out all "hey boy, look at this addition, you'll want to see it" to a stranger is a nuisance to the viewer and embarrassing to the person who originally posted it. This feature is incredibly ill-conceived and I hope it goes away soon.
It's actually kind of impressive how ill-conceived this whole "Notes Preview" business is. At a single stroke, it's been rendered impossible to curate one's experience even on one's own dashboard – now it doesn't matter that you've carefully followed a group of blogs you can trust not to reblog noxious bullshit, because with every post that crosses your dash there's now a chance that Tumblr will automatically append some random asshole's opinion about that post, in a way that neither you nor the person you're following can predict. Bravo.
36K notes
·
View notes
Text
Pluralist, your daily link-dose: 22 Feb 2020

Today’s links
Tax Justice Network publishes a new global Financial Secrecy Index: US and UK, neck-and-neck
What Marc Davis lifted from the Addams Family while designing the Haunted Mansion: Amateurs plagiarize, artists steal
ICANN should demand to see the secret financial docs in the .ORG selloff: at least it’s an Ethos
Wells Fargo will pay $3b for 2 million acts of fraud: they shoulda got the corporate death penalty
This day in history: 2019, 2015, 2010
Colophon: Recent publications, current writing projects, upcoming appearances, current reading

Tax Justice Network publishes a new global Financial Secrecy Index (permalink)
The Tax Justice Network just published its latest Financial Secrecy Index, the leading empirical index of global financial secrecy policies. The US continues to make a dismal showing, as does the UK (factoring in overseas territories).
https://fsi.taxjustice.net/en/
Both Holland and Switzerland backslid this year.
Important to remember that “bad governance” scandals in poor countries (like the multibillion-dollar Angolaleaks scandal) involve rich financial secrecy havens as laundries for looted national treasure.
https://www.theguardian.com/world/2020/jan/19/isabel-dos-santos-revealed-africa-richest-woman-2bn-empire-luanda-leaks-angola
As Tax Justice breaks it down: “The secrecy world creates a criminogenic hothouse for multiple evils including fraud, tax cheating, escape from financial regulations, embezzlement, insider dealing, bribery, money laundering, and plenty more. It provides multiple ways for insiders to extract wealth at the expense of societies, creating political impunity and undermining the healthy ‘no taxation without representation’ bargain that has underpinned the growth of accountable modern nation states. Many poorer countries, deprived of tax and haemorrhaging capital into secrecy jurisdictions, rely on foreign aid handouts.”
Talk about getting you coming and going! First we make bank helping your corrupt leaders rob you blind, then we loan you money so you can keep the lights on and get fat on the interest (and force you to sell off your looted, ailing state industries as “economic reforms”).
The Taxcast, which is the Network’s podcast, has a great special edition in which the index’s key researchers explain their work. It’s always a good day when a new Taxcast drops.
https://www.taxjustice.net/2020/02/20/financial-secrecy-index-who-are-the-worlds-worst-offenders-the-tax-justice-network-podcast-special-february-2020/

What Marc Davis lifted from the Addams Family while designing the Haunted Mansion (permalink)
It’s always a good day — a GREAT day — when the Long Forgotten Haunted Mansion blog does a new post, but today’s post, on the influence of the Addams Family TV show on Mansion co-designer Mark Davis? ::Chef’s Kiss::
https://longforgottenhauntedmansion.blogspot.com/2020/02/the-addams-family-and-marc-davis.html
It’s clear that Davis was using Addams’s comics as reference, but, as Long Forgotten shows, the Davis sketches and concepts are straight up lifted from the TV show: “Amateurs plagiarize, artists steal.”
Some of these lifts are indisputable.
“Finally, it’s possible that Davis took a further cue from the insanely long sweater Morticia is knitting in ‘Fester’s Punctured Romance’ (Oct 2, 1964), but in this case I wouldn’t insist upon it.”
Likewise, from the TV show, “Bruno” the white bear rug that periodically bites people was obviously the inspiration for this Davis sketch for the Mansion. Long Forgotten is less certain about “Ophelia,” but I think it’s pretty clear where Davis was getting his ideas from here.

Davis was an unabashed plunderer and we are all better for it! “We’ve seen many other examples of Marc Davis taking ideas from here, there, and anywhere he could find them, but not many other examples of multiple inspiration from a single source.”

ICANN should demand to see the secret financial docs in the .ORG selloff (permalink)
ISOC — the nonprofit set up to oversee the .ORG registry — decided to sell off this asset (which they were given for free, along with $5M to cover setup expenses) to a mysterious private equity fund called Ethos Capital.
Some of Ethos’s backers are known (Republican billionaire families like the Romneys and the Perots) but much of its financing remains in the shadows. We do know that ICANN employees who help tee up the sale now work for Ethos, in a corrupt bit of self-dealing.
The deal was quietly announced and looked like a lock, but then public interest groups rose up to demand an explanation. Not only could Ethos expose nonprofits to unlimited rate-hikes (thanks to ICANN’s changes to its rules), they could do much, much worse.
If a .ORG registrant dropped its domain, Ethos could sell access to misdirected emails and domain lookups – so if you watchdog private equity funds and get destroyed by vexation litigation, Ethos could sell your bouncing email to the billionaires who crushed you.
More simply, Ethos could sell the kind of censorship-as-a-service it currently sells through its other registry, Donuts, which charges “processing fees” to corrupt governments and bullying corporations who want to censor the web by claiming libel or copyright infringement.
Ethos offered ISOC $1.135b for the sale, but $360m of that will come from a loan that .ORG will have to pay back, a millstone around its neck, dragging it down. Debt-loading healthy business as a means of bleeding them dry is a tried-and-true PE tactic – it’s what did in Toys R Us, Sears, and many other firms. The PE barons get a fortune, everyone else gets screwed.
The interest on .ORG’s loan will suck up $24m/year — TWO THIRDS of the free money that .ORG generates. .ORG is a crazily profitable nonprofit – it charges dollars to provide a service that costs fractional pennies, after all. In response to getting slapped around by some Members of Congress, the Pennsylvania AG, and millions of netizens, Ethos has made a promise to limit prices increases…for a while. And they say that they’ll be kept honest by the nonbinding recommendations of an “advisory council” whose members Ethos will appoint and who will serve at Ethos’s pleasure.
In a letter to ICANN, EFF and Americans for Financial Reform have called for transparency on the financing behind the sale: “hidden costs, loan servicing fees, and inducements to insiders.”
https://www.eff.org/press/releases/eff-seeks-disclosure-secret-financing-details-behind-11-billion-org-sale-asks-ftc

Wells Fargo will pay $3b for 2 million acts of fraud (permalink)
Wells Fargo stole from at least two million of its customers, pressuring its low-level employees to open fake accounts in their names, firing employees who refused (refuseniks were also added to industry-wide blacklists created to track crooked bankers). These fake accounts ran up fees for bank customers, including penalties, etc. In some cases, the damage to the victims’ credit ratings was so severe that they were turned down for jobs, unable to get house loans or leases, etc.
The execs who oversaw these frauds had plenty of red flags, including their own board members asking why the fuck their spouses had been sent mysterious Wells Fargo credit cards they’d never signed up for. Though these execs paid fines, they got to keep MILLIONS from this fraud (which was only one of dozens of grifts Wells Fargo engaged in this century, including stealing from small businesses, homeowners, military personnel, car borrowers, etc). Some of them may never work in banking again, but they’re all millionaires for life.
Now, Wells Fargo has settled with the DoJ for $3b, admitting wrongdoing and submitting to several years of oversight. That’s a good start, but it’s a bad finish.
https://www.bbc.com/news/business-51594117
The largest bank in America was, for DECADES, a criminal enterprise, preying on Americans of every description. It should no longer exist. It should be broken into constituent pieces, under new management. There would be enormous collateral damage from this (just as the family of a murderer suffers when he is made to face the consequences of his crimes). But what about the collateral damage to everyone who is savaged by a similarly criminal bank in the future, emboldened by Wells Fargo’s impunity?
Wells Fargo is paying a fine, but will have NO criminal charges filed against it.
https://newsroom.wf.com/press-release/corporate-and-financial/wells-fargo-reaches-settlements-resolve-outstanding-doj-and
If you or I stole from TWO MILLION people, we would not be permitted to pay a fine and walk away.
“I’ll believe corporations are people when the government gives one the death penalty.”

This day in history (permalink)
#15yrsago: Kottke goes full-time https://kottke.org/05/02/kottke-micropatron
#15yrsago: New Zealand’s regulator publishes occupational safety guide for sex workers: https://web.archive.org/web/20050909001954/http://www.osh.dol.govt.nz/order/catalogue/pdf/sexindustry.pdf
#10yrsago: Principal who spied on child through webcam mistook a Mike n Ike candy for drugs: https://reason.com/2010/02/20/lower-pervian-school-district/
#10yrsago: School where principal spied on students through their webcams had mandatory laptop policies, treated jailbreaking as an expellable offense https://web.archive.org/web/20100726204521/https://strydehax.blogspot.com/2010/02/spy-at-harrington-high.html
#10yrsago: Parents file lawsuit against principal who spied on students through webcams: https://abcnews.go.com/GMA/Parenting/pennsylvania-school-webcam-students-spying/story?id=9905488
#1yrago: Cybermercenary firm with ties to the UAE want the capability to break Firefox encryption https://www.eff.org/deeplinks/2019/02/cyber-mercenary-groups-shouldnt-be-trusted-your-browser-or-anywhere-else
#1yrago: Fraudulent anti-Net Neutrality comments to the FCC traced back to elite DC lobbying firm https://gizmodo.com/how-an-investigation-of-fake-fcc-comments-snared-a-prom-1832788658

Colophon (permalink)
Today’s top sources: Naked Capitalism (https://nakedcapitalism.com/).
Hugo nominators! My story “Unauthorized Bread” is eligible in the Novella category and you can read it free on Ars Technica: https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
Upcoming appearances:
The Future of the Future: The Ethics and Implications of AI, UC Irvine, Feb 22: https://www.humanities.uci.edu/SOH/calendar/event_details.php?eid=8263
Canada Reads Kelowna: March 5, 6PM, Kelowna Library, 1380 Ellis Street, with CBC’s Sarah Penton https://www.eventbrite.ca/e/cbc-radio-presents-in-conversation-with-cory-doctorow-tickets-96154415445
Currently writing: I just finished a short story, “The Canadian Miracle,” for MIT Tech Review. It’s a story set in the world of my next novel, “The Lost Cause,” a post-GND novel about truth and reconciliation. I’m getting geared up to start work on the novel now, though the timing is going to depend on another pending commission (I’ve been solicited by an NGO) to write a short story set in the world’s prehistory.
Currently reading: I finished Andrea Bernstein’s “American Oligarchs” this week; it’s a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I’m getting really into Anna Weiner’s memoir about tech, “Uncanny Valley.” I just loaded Matt Stoller’s “Goliath” onto my underwater MP3 player and I’m listening to it as I swim laps.
Latest podcast: Persuasion, Adaptation, and the Arms Race for Your Attention: https://craphound.com/podcast/2020/02/10/persuasion-adaptation-and-the-arms-race-for-your-attention/
Upcoming books: “Poesy the Monster Slayer” (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we’re having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
“Attack Surface”: The third Little Brother book, Oct 20, 2020.
“Little Brother/Homeland”: A reissue omnibus edition with a very special, s00per s33kr1t intro.
17 notes
·
View notes